Dell PowerEdge VRTX User Manual

PowerEdge VRTX 1Gb Switch Module
R1-2401
User Guide
Regulatory Model: E12M
Regulatory Type: E12M001

Notes, Cautions, and Warnings
NOTE: A NOTE indicates important information that helps you make better use of your computer.
CAUTION: A CAUTION indicates either potential damage to hardware, or loss of data and tells you how to avoid the problem.
WARNING: A WARNING indicates a potential for property damage, personal injury, or death.
____________________
Information in this publication is subject to change without notice. © 2013 Dell Inc. All rights reserved.
Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden.
Trademarks used in this text: Dell™, the DELL logo, Dell Precision™, OptiPlex™, Latitude™, PowerEdge™, PowerVault™, PowerConnect™, OpenManage™, EqualLogic™, KACE™, FlexAddress™ and Vostro™ are trademarks of Dell Inc. Intel, Pentium, Xeon, Core™ and Celeron are registered trademarks of Intel Corporation in the U.S. and other countries. AMD is a registered trademark and AMD Opteron™, AMD Phenom™, and AMD Sempron™ are trademarks of Advanced Micro Devices, Inc. Microsoft®, Windows®, Windows Server®, MS-DOS® and Windows Vista® are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. Red Hat Enterprise Linux® and Enterprise Linux® are registered trademarks of Red Hat, Inc. in the United States and/or other countries. Novell® is a registered trademark and SUSE ™ is a trademark of Novell Inc. in the United States and other countries. Oracle® is a registered trademark of Oracle Corporation and/or its affiliates. Citrix®, Xen®, XenServer® and XenMotion® are either registered trademarks or trademarks of Citrix Systems, Inc. in the United States and/or other countries. VMware®, Virtual SMP®, vMotion®, vCenter®, and vSphere® are registered trademarks or trademarks of VMWare, Inc. in the United States or other countries.
Other trademarks and trade names may be used in this publication to refer to either the entities claiming the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own.
Regulatory Model: E12M
Regulatory Type: E12M001
April 2013 P/N 56NT1 Rev. A03

Contents
1 Preface . . . . . . . . . . . . . . . . . . . . . . . . . . |
11 |
2 Features . . . . . . . . . . . . . . . . . . . . . . . . . . |
13 |
IP Version 6 (IPv6) Support . . . . . . . . . . . . . . . |
14 |
Head of Line Blocking Prevention. . . . . . . . . . . . |
14 |
Back Pressure Support . . . . . . . . . . . . . . . . . |
14 |
Virtual Cable Testing (VCT) . . . . . . . . . . . . . . . |
14 |
Auto-Negotiation . . . . . . . . . . . . . . . . . . . . |
14 |
MDI/MDIX Support. . . . . . . . . . . . . . . . . . . . |
15 |
MAC Address Supported Features . . . . . . . . . . . |
15 |
Layer 2 Features . . . . . . . . . . . . . . . . . . . . . |
16 |
IGMP Snooping . . . . . . . . . . . . . . . . . . . . . |
16 |
Port Mirroring . . . . . . . . . . . . . . . . . . . . . . |
17 |
Broadcast Storm Control . . . . . . . . . . . . . . . . |
17 |
VLAN Supported Features . . . . . . . . . . . . . . . . |
17 |
Spanning Tree Protocol Features . . . . . . . . . . . . |
19 |
Link Aggregation. . . . . . . . . . . . . . . . . . . . . |
20 |
Quality of Service Features . . . . . . . . . . . . . . . |
21 |
Device Management Features. . . . . . . . . . . . . . |
22 |
Contents 3

Security Features . . . . . . . . . . . . . . . . . . . . |
25 |
Port Profile (CLI Macro) . . . . . . . . . . . . . . . . . |
27 |
DHCP Server . . . . . . . . . . . . . . . . . . . . . . . |
28 |
Protected Ports. . . . . . . . . . . . . . . . . . . . . . |
28 |
Proprietary Protocol Filtering . . . . . . . . . . . . . . |
28 |
3 Hardware and Initial Configuration . . . . 29
Switch Hardware . . . . . . . . . . . . . . . . . . . . |
29 |
Initial Configuration of the Switch . . . . . . . . . . . |
32 |
4 Using the CLI . . . . . . . . . . . . . . . . . . . . . 35
Using the CLI . . . . . . . . . . . . . . . . . . . . . . . |
35 |
CLI Command Conventions. . . . . . . . . . . . . . . . |
38 |
Accessing the Device Through the CLI . . . . . . . . . |
39 |
Retrieving an IP Address. . . . . . . . . . . . . . . . . |
40 |
Security Management and Password Configuration . . |
42 |
Configuring Login Banners . . . . . . . . . . . . . . . |
44 |
Startup Menu Procedures . . . . . . . . . . . . . . . . |
46 |
Software Download . . . . . . . . . . . . . . . . . . . |
48 |
5 Network Administrator. . . . . . . . . . . . . . 53
Starting the Application . . . . . . . . . . . . . . . . . 53
4 Contents

Understanding the Interface. . . . . . . . . . . . . . . |
53 |
Using the Network Administrator Buttons . . . . . . . |
54 |
Field Definitions . . . . . . . . . . . . . . . . . . . . . |
55 |
Common GUI Features . . . . . . . . . . . . . . . . . . |
56 |
GUI Terms . . . . . . . . . . . . . . . . . . . . . . . . |
57 |
6 Configuring System Information . . . . . . . |
59 |
General Switch Information . . . . . . . . . . . . . . . |
59 |
Time Synchronization . . . . . . . . . . . . . . . . . . |
64 |
Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . |
86 |
IP Addressing . . . . . . . . . . . . . . . . . . . . . . |
98 |
Diagnostics . . . . . . . . . . . . . . . . . . . . . . . |
129 |
Management Security . . . . . . . . . . . . . . . . . . |
131 |
SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . |
161 |
File Management . . . . . . . . . . . . . . . . . . . . |
182 |
7 Network Security . . . . . . . . . . . . . . . . . 203
Port Security . . . . . . . . . . . . . . . . . . . . . . . |
203 |
ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . |
206 |
ACL Binding . . . . . . . . . . . . . . . . . . . . . . . |
222 |
Proprietary Protocol Filtering . . . . . . . . . . . . . . |
224 |
Time Range. . . . . . . . . . . . . . . . . . . . . . . . |
225 |
Contents 5

Dot1x Authentication. . . . . . . . . . . . . . . . . . |
228 |
8 Ports. . . . . . . . . . . . . . . . . . . . . . . . . . . . |
249 |
Overview . . . . . . . . . . . . . . . . . . . . . . . . |
249 |
Jumbo Frames . . . . . . . . . . . . . . . . . . . . . |
251 |
Green Ethernet Configuration . . . . . . . . . . . . . |
252 |
Protected Ports . . . . . . . . . . . . . . . . . . . . |
255 |
Port Profile . . . . . . . . . . . . . . . . . . . . . . . |
257 |
Port Configuration . . . . . . . . . . . . . . . . . . . |
262 |
LAG Configuration . . . . . . . . . . . . . . . . . . . |
268 |
Storm Control . . . . . . . . . . . . . . . . . . . . . |
271 |
Port Mirroring . . . . . . . . . . . . . . . . . . . . . |
273 |
9 Address Tables . . . . . . . . . . . . . . . . . . . |
277 |
Overview . . . . . . . . . . . . . . . . . . . . . . . . |
277 |
Static Addresses . . . . . . . . . . . . . . . . . . . . |
277 |
Dynamic Addresses . . . . . . . . . . . . . . . . . . |
279 |
10 GARP . . . . . . . . . . . . . . . . . . . . . . . . . . . |
283 |
GARP Overview . . . . . . . . . . . . . . . . . . . . |
283 |
GARP Timers . . . . . . . . . . . . . . . . . . . . . . |
284 |
6 Contents
11 |
Spanning Tree . . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . |
287 |
|
|
|
Spanning Tree Protocol Overview. . |
. |
. |
. |
. |
. |
. |
. . . . |
287 |
|
|
|
Global Settings. . . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
289 |
|
|
|
STP Port Settings . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
292 |
|
|
|
STP LAG Settings . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
296 |
|
|
|
Rapid Spanning Tree . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
299 |
|
|
|
Multiple Spanning Tree . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
301 |
|
|
12 VLANs . . . . . . . . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . |
311 |
|
|
|
|
Virtual LAN Overview . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
311 |
|
|
|
VLAN Membership . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
315 |
|
|
|
Port Settings . . . . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
317 |
|
|
|
LAG Settings . . . . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
321 |
|
|
|
Protocol Groups . . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
323 |
|
|
|
Protocol Port . . . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
326 |
|
|
|
GVRP Parameters . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
327 |
|
|
|
Private VLAN . . . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
329 |
|
|
|
Voice VLAN . . . . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
332 |
|
|
13 |
Link Aggregation . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . |
339 |
|
|
|
Link Aggregation Overview . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
339 |
|
|
|
LACP Parameters . . . . . . . . . . |
. |
. |
. |
. |
. |
. |
. . . . |
340 |
|
|
|
|
|
|
|
|
|
|
Contents |
|
7 |
|
|
|
|
|
|
|
|
|
|
|||

|
LAG Membership. . . . . . . . . . . . . . . . . . . . |
342 |
14 |
Multicast . . . . . . . . . . . . . . . . . . . . . . . . |
345 |
|
Multicast Support Overview. . . . . . . . . . . . . . |
345 |
|
Global Parameters . . . . . . . . . . . . . . . . . . . |
346 |
|
Bridge Multicast Groups. . . . . . . . . . . . . . . . |
347 |
|
Bridge Multicast Forward All . . . . . . . . . . . . . |
350 |
|
IGMP Snooping . . . . . . . . . . . . . . . . . . . . |
352 |
|
Unregistered Multicast . . . . . . . . . . . . . . . . |
358 |
|
Multicast TV VLAN . . . . . . . . . . . . . . . . . . |
359 |
15 |
LLDP . . . . . . . . . . . . . . . . . . . . . . . . . . . |
363 |
|
LLDP Overview . . . . . . . . . . . . . . . . . . . . . |
363 |
|
LLDP Properties . . . . . . . . . . . . . . . . . . . . |
364 |
|
LLDP Port Settings . . . . . . . . . . . . . . . . . . . |
366 |
|
MED Network Policy . . . . . . . . . . . . . . . . . |
368 |
|
MED Port Settings . . . . . . . . . . . . . . . . . . . |
369 |
|
Neighbors Information . . . . . . . . . . . . . . . . . |
373 |
16 |
Dynamic ARP Inspection . . . . . . . . . . . |
377 |
|
Dynamic ARP Inspection Overview . . . . . . . . . . |
377 |
|
Global Settings . . . . . . . . . . . . . . . . . . . . . |
378 |
8 Contents

|
Dynamic ARP Inspection List . . . . . . . . . . . . . . |
379 |
|
Dynamic ARP Inspection Entries . . . . . . . . . . . . |
380 |
|
VLAN Settings . . . . . . . . . . . . . . . . . . . . . . |
382 |
|
Trusted Interface . . . . . . . . . . . . . . . . . . . . . |
382 |
17 DHCP Snooping . . . . . . . . . . . . . . . . . . |
385 |
|
|
DHCP Snooping Overview . . . . . . . . . . . . . . . . |
385 |
|
Global Parameters . . . . . . . . . . . . . . . . . . . . |
387 |
|
VLAN Settings . . . . . . . . . . . . . . . . . . . . . . |
389 |
|
Trusted Interface . . . . . . . . . . . . . . . . . . . . |
390 |
|
Snooping Binding Database . . . . . . . . . . . . . . . |
391 |
18 |
Statistics/RMON . . . . . . . . . . . . . . . . . . |
395 |
|
Table Views . . . . . . . . . . . . . . . . . . . . . . . |
395 |
|
RMON . . . . . . . . . . . . . . . . . . . . . . . . . . |
407 |
|
Charts . . . . . . . . . . . . . . . . . . . . . . . . . . |
419 |
19 |
Quality of Service . . . . . . . . . . . . . . . . . |
423 |
|
QoS Features and Components . . . . . . . . . . . . . |
423 |
|
General. . . . . . . . . . . . . . . . . . . . . . . . . . |
425 |
|
QoS Basic Mode . . . . . . . . . . . . . . . . . . . . . |
434 |
|
QoS Advanced Mode . . . . . . . . . . . . . . . . . . |
439 |
Contents 9

QoS Statistics . . . . . . . . . . . . . . . . . . . . . |
453 |
10 Contents

1
Preface
The R1-2401is a modular switch that is part of the Plasma chassis.
This guide contains the information needed for installing, configuring, and maintaining the device through the web-based network administrator. In addition, it contains a subset of the CLI available.
The CLI Reference Guide, which is available on a documentation CD, provides additional information about the CLI commands.
Preface 11

12 Preface

2
Features
This section describes the features of the R1-2401 switch.
For a complete list of all updated device features, see the latest software version Release Notes.
This section describes the following features:
•IP Version 6 (IPv6) Support
•Head of Line Blocking Prevention
•Back Pressure Support
•Virtual Cable Testing (VCT)
•Auto-Negotiation
•MDI/MDIX Support
•MAC Address Supported Features
•Layer 2 Features
•IGMP Snooping
•Port Mirroring
•Broadcast Storm Control
•VLAN Supported Features
•Spanning Tree Protocol Features
•Link Aggregation
•Quality of Service Features
•Device Management Features
•Security Features
•DHCP Server
•Protected Ports
•Proprietary Protocol Filtering
Features 13

IP Version 6 (IPv6) Support
The device functions as an IPv6-compliant host, as well as an IPv4 host (also known as dual stack). This enables device operation in a pure IPv6 network as well as in a combined IPv4/IPv6 network.
For more information, see "IP Addressing" on page 98.
Head of Line Blocking Prevention
Head of Line (HOL) blocking results in traffic delays and frame loss caused by traffic competing for the same egress port resources. To prevent HOL blocking, the device queues packets, and packets at the head of the queue are forwarded before packets at the end of the queue.
Back Pressure Support
On half-duplex links, the receiving port prevents buffer overflows by occupying the link so that it is unavailable for additional traffic.
For more information, see "Back Pressure" on page 251.
Virtual Cable Testing (VCT)
VCT detects and reports copper link cabling faults, such as open cables and cable shorts.
For more information, see "Diagnostics" on page 129.
Auto-Negotiation
Auto-negotiation enables the device to advertise modes of operation. The auto-negotiation function enables an exchange of information between two devices that share a point-to-point link segment, and automatically configures both devices to take maximum advantage of their transmission capabilities.
The IOM ARC-II devices enhances auto-negotiation by providing port advertisement. Port advertisement enables the system administrator to configure the port speeds that are advertised.
14 Features

For more information, see "Port Configuration" on page 262 or "LAG Configuration" on page 268.
MDI/MDIX Support
Standard wiring for end stations is known as Media-Dependent Interface (MDI), and standard wiring for hubs and switches is known as MediaDependent Interface with Crossover (MDIX).
If auto-negotiation is enabled, the device automatically detects whether the cable connected to an RJ-45 port is MDIX (crossed) or MDI (straight). This enables both types to be used interchangeably.
If auto-negotiation is not enabled, only MDI (straight) cables can be used.
For more information, see "Port Configuration" on page 262 or "LAG Configuration" on page 268.
MAC Address Supported Features
MAC Address Capacity Support
The device supports up to 16K MAC addresses and it reserves specific MAC addresses for system use.
Static MAC Entries
MAC entries can be manually entered in the Bridging Table, as an alternative to learning them from incoming frames. These user-defined entries are not subject to aging, and are preserved across resets and reboots.
For more information, see "Address Tables" on page 277.
Self-Learning MAC Addresses
The device enables controlled MAC address learning from incoming packets. The MAC addresses are stored in the Bridging Table.
For more information, see "Dynamic Addresses" on page 279.
Automatic Aging for MAC Addresses
MAC addresses from which no traffic is received for a given period, are aged out. This prevents the Bridging Table from overflowing.
Features 15

For more information, see "Dynamic Addresses" on page 279.
VLAN-Aware MAC-Based Switching
The device always performs VLAN-aware bridging. Classic bridging (IEEE802.1D), in which frames are forwarded based only on their destination MAC address, is not performed. However, a similar functionality can be configured for untagged frames. Frames addressed to a destination MAC address that is not associated with any port are flooded to all ports of the relevant VLAN.
MAC Multicast Support
Multicast service is a limited Broadcast service that enables one-to-many and many-to-many connections for information distribution. In Layer 2 Multicast service, a single frame is addressed to a specific Multicast address, from which copies of the frame are transmitted to the relevant ports. When Multicast groups are statically enabled, you can set the destination port of registered groups, as well as define the behavior of unregistered Multicast frames.
For more information, see "Multicast" on page 345.
Layer 2 Features
IGMP Snooping
Internet Group Membership Protocol (IGMP) Snooping examines IGMP frame contents, when they are forwarded by the device from work stations to an upstream Multicast router. From the frame, the device identifies work stations configured for Multicast sessions, and which Multicast routers are sending Multicast frames. The IGMP Querier simulates the behavior of a Multicast router. This enables snooping of the Layer 2 Multicast domain even if there is no Multicast router.
For more information, see "IGMP Snooping" on page 352.
16 Features

Port Mirroring
Port mirroring monitors network traffic by forwarding copies of incoming and outgoing packets from a monitored port to a monitoring port. Users specify which target port receives copies of all traffic passing through a specified source port.
For more information, see "Port Mirroring" on page 273.
Broadcast Storm Control
Storm Control enables limiting the number of Multicast and Broadcast frames accepted by and forwarded by the device.
When Layer 2 frames are forwarded, Broadcast and Multicast frames are flooded to all ports on the relevant VLAN. This occupies bandwidth, and loads all nodes connected on all ports.
For more information, see "Storm Control" on page 271.
VLAN Supported Features
VLAN Support
VLANs are collections of switching ports that comprise a single Broadcast domain. Packets are classified as belonging to a VLAN, based on either the VLAN tag or on a combination of the ingress port and packet contents.
Packets sharing common attributes can be grouped in the same VLAN. For more information, see "VLANs" on page 311.
Port-Based Virtual LANs (VLANs)
Port-based VLANs classify incoming packets to VLANs, based on their ingress port.
For more information, see "VLAN Membership" on page 315.
Full 802.1Q VLAN Tagging Compliance
IEEE 802.1Q defines an architecture for virtual, bridged LANs, the services provided in VLANs, and the protocols and algorithms involved in the provision of these services.
Features 17

For more information, see "Virtual LAN Overview" on page 311.
GVRP Support
GARP VLAN Registration Protocol (GVRP) provides IEEE 802.1Qcompliant VLAN pruning and dynamic VLAN creation on 802.1Q trunk ports. When GVRP is enabled, the device registers and propagates VLAN membership on all ports that are part of the active underlying Spanning Tree Protocol topology.
For more information, see "GVRP Parameters" on page 327.
Voice VLAN
Voice VLAN enables network administrators to enhance VoIP service by configuring ports to carry IP voice traffic from IP phones on a specific VLAN. VoIP traffic has a preconfigured OUI prefix in the source MAC address. Network administrators can configure VLANs from which voice IP traffic is forwarded. Non-VoIP traffic is dropped from the Voice VLAN in Auto-Voice VLAN Secure mode. Voice VLAN also provides QoS to VoIP, ensuring that the quality of voice does not deteriorate if the IP traffic is received unevenly.
For more information, see "Voice VLAN" on page 332.
Guest VLAN
Guest VLAN provides limited network access to unauthorized ports. If a port is denied network access via port-based authorization, but the Guest VLAN is enabled, the port receives limited network access through the Guest VLAN.
For more information, see "Dot1x Authentication" on page 259.
Private VLAN
The Private VLAN feature provides Layer 2 isolation between ports that share the same Broadcast domain, or in other words, it creates a point-to- multipoint Broadcast domain. The ports can be located anywhere in the Layer 2 network.
For more information, see "Private VLAN" on page 329.
18 Features

Multicast TV VLAN
The Multicast TV VLAN feature provides the ability to supply multicast transmissions to Layer 2-isolated subscribers, without replicating the multicast transmissions for each subscriber VLAN. The subscribers are the only receivers of the multicast transmissions.
For more information, see "Multicast TV VLAN" on page 359.
Spanning Tree Protocol Features
Spanning Tree Protocol (STP)
802.1d Spanning tree is a standard Layer 2 switch requirement that enables bridges to automatically prevent and resolve Layer 2 forwarding loops. Switches exchange configuration messages using specifically-formatted frames, and selectively enable and disable forwarding on ports.
For more information, see "Spanning Tree" on page 287.
Fast Link
STP can take 30–60 seconds to converge. During this time, STP detects possible loops, enabling time for status changes to propagate and for relevant devices to respond. This period of 30-60 seconds is considered too long a response time for many applications. The Fast Link option bypasses this delay, and can be used in network topologies, where forwarding loops do not occur.
For more information on enabling Fast Link for ports and LAGs, see "STP Port Settings" on page 292.
IEEE 802.1w Rapid Spanning Tree
Spanning Tree takes 30–60 seconds for each host to decide whether its ports are actively forwarding traffic. Rapid Spanning Tree (RSTP) detects uses of network topologies to enable faster convergence, without creating forwarding loops.
For more information, see "Spanning Tree" on page 287.
Features 19

IEEE 802.1s Multiple Spanning Tree
Multiple Spanning Tree (MSTP) operation maps VLANs into STP instances. MSTP provides a different load balancing scenario. Packets assigned to various VLANs are transmitted along different paths within MSTP Regions (MST Regions). Regions are one or more MSTP bridges by which frames can be transmitted. The standard lets administrators assign VLAN traffic to
unique paths.
For more information, see "Spanning Tree" on page 287.
STP BPDU Guard
BPDU Guard is used as a security mechanism, to protect the network from invalid configurations.
BPDU Guard is usually used either when fast link ports (ports connected to clients) are enabled or when the STP feature is disabled. When it is enabled on a port, the port is shut down if a BPDU message is received and an appropriate SNMP trap is generated.
For more information, see "Spanning Tree" on page 287.
Link Aggregation
Up to 32 Aggregated Links may be defined, each with up to eight member ports, to form a single Link Aggregated Group (LAG). This enables:
•Fault tolerance protection from physical link disruption
•Higher bandwidth connections
•Improved bandwidth granularity
•High bandwidth server connectivity
A LAG is composed of ports with the same speed, set to full-duplex operation.
For more information, see "LAG Configuration" on page 268.
20 Features

Link Aggregation and LACP
LACP uses peer exchanges across links to determine, on an ongoing basis, the aggregation capability of various links, and continuously provides the maximum level of aggregation capability achievable between a given pair of devices. LACP automatically determines, configures, binds, and monitors the port binding within the system.
For more information, see "Link Aggregation" on page 339.
BootP and DHCP Clients
DHCP enables additional setup parameters to be received from a network server upon system startup. DHCP service is an on-going process. DHCP is an extension of BootP.
For more information, see "IPv6 Interfaces" on page 105.
Quality of Service Features
Class of Service 802.1p Support
The IEEE 802.1p signaling technique is an OSI Layer 2 standard for marking and prioritizing network traffic at the data link/MAC sub-layer. 802.1p traffic is classified and sent to the destination. No bandwidth reservations or limits are established or enforced. 802.1p is a spin-off of the 802.1Q (VLANs) standard. 802.1p establishes eight levels of priority, similar to the IP Precedence IP Header bit-field.
For more information about QoS, see "Quality of Service" on page 423.
Advanced QoS
Frames that match an ACL and were permitted entrance are implicitly labeled with the name of the ACL that permitted their entrance. Advanced mode QoS actions defined in network policies can then be applied to these flows.
The switch can set DSCP values and map IPv6 DSCP to egress queues in the same way it does for IPv4. The switch detects IPv6 frames by the IPv6 ethertype.
For more information about Advanced QoS, see "QoS Advanced Mode" on page 439.
Features 21

TCP Congestion Avoidance
The TCP Congestion Avoidance feature activates an algorithm that breaks up or prevents TCP global synchronization on a congested node, where the congestion is due to multiple sources sending packets with the same byte count.
For more information, see "TCP Congestion Avoidance" on page 433.
Device Management Features
SNMP Alarms and Trap Logs
The system logs events with severity codes and timestamps. Events are sent as SNMP traps to a Trap Recipient List.
For more information, see "SNMP" on page 178.
SNMP Versions 1, 2, and 3
Simple Network Management Protocol (SNMP) over the UDP/IP protocol controls access to the system. A list of community entries is defined, each consisting of a community string and its access privileges. There are three levels of SNMP security: read-only, read-write, and super. Only a super user can access the Community table.
For more information, see "SNMP" on page 178.
Web-Based Management
Web-based management enables managing the system from any web browser. The system contains an Embedded Web Server (EWS) that serves HTML pages, through which the system can be monitored and configured. The system internally converts web-based input into configuration commands, MIB variable settings, and other management-related settings.
Management IP Address Conflict Notification
This feature validates the uniqueness of the switch's IP address, whether it is assigned manually or through DHCP. If the IP address is not unique, the switch performs actions according to the address type. If the IP address is
22 Features

static, see more information about this in "IPv4 Interface Parameters" on page 100. If the IP address is dynamic, see more information about this in"IPv6 Interfaces" on page 105.
Configuration File Download and Upload
The device configuration is stored in a configuration file. The configuration file includes both system-wide and port-specific device configuration. The system can display configuration files as a collection of CLI commands that are stored and manipulated as text files.
Auto-Update of Configuration/Image File
This feature facilitates installation of new devices. When you enable the various auto-update options, the device automatically downloads a new image or configuration file when it receives its IP address from a TFTP server, and automatically reboots, using the image or configuration file it received.
For more information, see "Auto-Update/Configuration Feature" on page 184.
TFTP Trivial File Transfer Protocol
The device supports boot image, software, and configuration upload/download via TFTP.
For more information, see "File Management" on page 182.
Remote Monitoring
Remote Monitoring (RMON) is an extension to SNMP that provides comprehensive network traffic monitoring capabilities. RMON is a standard MIB that defines MAC-layer statistics and control objects, enabling real-time information to be captured across the entire network.
For more information, see "Statistics/RMON" on page 397.
Command Line Interface
Command Line Interface (CLI) syntax and semantics conform as much as possible to common, industry standards. CLI is composed of mandatory and optional elements. The CLI interpreter provides command and keyword completion to assist users and save typing.
Features 23

SYSLOG
Syslog is a protocol that enables event notifications to be sent to a set of remote servers, where they can be stored, examined, and acted upon. The system sends notifications of significant events in real time, and keeps a record of these events for after-the-fact usage.
For more information on SYSLOG, see "Logs" on page 86.
SNTP
The Simple Network Time Protocol (SNTP) assures accurate network Ethernet Switch clock time synchronization up to the millisecond. Time synchronization is performed by a network SNTP server. Time sources are prioritized by strata. Strata define the distance from the reference clock. The higher the stratum (where zero is the highest), the more accurate the clock.
For more information, see "Time Synchronization" on page 64.
Domain Name System
Domain Name System (DNS) converts user-defined domain names into IP addresses. Each time a domain name is assigned, the DNS service translates the name into a numeric IP address. For example, www.ipexample.com is translated into 192.87.56.2. DNS servers maintain domain name databases containing their corresponding IP addresses.
For more information, see "Domain Name System" on page 121.
802.1ab (LLDP-MED)
The Link Layer Discovery Protocol (LLDP) enables network managers to troubleshoot, and enhances network management by discovering and maintaining network topologies over multi-vendor environments. LLDP discovers network neighbors by standardizing methods for network devices to advertise themselves to other systems, and to store discovered information. The multiple advertisement sets are sent in the packet Type Length Value (TLV) field. LLDP devices must support chassis and port ID advertisement, as well as system name, system ID, system description, and system capability advertisements.
24 Features

LLDP Media Endpoint Discovery (LLDP-MED) increases network flexibility by enabling various IP systems to co-exist on a single network LLDP. It provides detailed network topology information, emergency call service via IP phone location information, and troubleshooting information.
For more information, see "LLDP" on page 363.
Security Features
SSL
Secure Socket Layer (SSL) is an application-level protocol that enables secure transactions of data through privacy, authentication, and data integrity. It relies upon certificates and public and private keys.
Port-Based Authentication (Dot1x)
Port-based authentication enables authenticating system users on a per-port basis via an external server. Only authenticated and approved system users can transmit and receive data. Ports are authenticated via the Remote Authentication Dial-In User Service (RADIUS) server using the Extensible Authentication Protocol (EAP). Dynamic VLAN Assignment (DVA) enables network administrators to automatically assign users to VLANs during the RADIUS server authentication.
For more information, see "Dot1x Authentication" on page 259.
Locked Port Support
Locked Port increases network security by limiting access on a specific port to users with specific MAC addresses. These addresses are either manually defined or learned on that port. When a frame is seen on a locked port, and the frame source MAC address is not tied to that port, the protection mechanism is invoked.
For more information, see "Port Security" on page 234.
RADIUS Client
RADIUS is a client/server-based protocol. A RADIUS server maintains a user database that contains per-user authentication information, such as user name, password, and accounting information.
Features 25

RADIUS Accounting
This feature enables recording device management sessions (Telnet, serial, and WEB but not SNMP) and/or 802.1x authentication sessions.
Due to the complexity of 802.1x setup and configuration, many mistakes can be made that might cause loss of connectivity or incorrect behavior. The 802.1x Monitor mode enables applying 802.1x functionality to the switch, with all necessary RADIUS and/or domain servers active, without actually taking any action that may cause unexpected behavior. In this way, the user can test the 802.1x setup before actually applying it.
For more information, see "RADIUS" on page 156.
SSH
Secure Shell (SSH) is a protocol that provides a secure, remote connection to a device. SSH version 2 is currently supported. The SSH server feature enables an SSH client to establish a secure, encrypted connection with a device. This connection provides functionality that is similar to an inbound telnet connection. SSH uses RSA and DSA Public Key cryptography for device connections and authentication.
For more information, see "Security Management and Password Configuration" on page 64.
TACACS+
TACACS+ provides centralized security for validation of users accessing the device. TACACS+ provides a centralized, user management system, while still retaining consistency with RADIUS and other authentication processes.
For more information, see "TACACS+" on page 153.
Password Management
Password management provides increased network security and improved password control. Passwords for SSH, Telnet, HTTP, HTTPS, and SNMP access are assigned security features.
The switch provides the ability to demand strong passwords, meaning that they must contain both upper and lower-case letters, numbers, and punctuation marks.
For more information, see "Password Management" on page 142.
26 Features

Access Control Lists (ACL)
Access Control Lists (ACL) enable network managers to define classification actions and rules for specific ingress ports. Packets entering an ingress port with an active ACL, are either admitted or denied entry and the ingress port is disabled. If they are denied entry, the user can disable the port.
For more information, see "Password Management" on page 142
Dynamic ACL/Dynamic Policy Assignment (DACL/DPA)
The network administrator can specify the user's ACL in the RADIUS server. After successful authentication, the user is assigned that ACL.
For more information, see "ACLs" on page 237.
DHCP Snooping
DHCP Snooping expands network security by providing firewall security between untrusted interfaces and DHCP servers. By enabling DHCP Snooping, network administrators can differentiate between trusted interfaces connected to end-users or DHCP servers and untrusted interfaces located beyond the network firewall.
For more information, see "DHCP Snooping" on page 387.
ARP Inspection
Dynamic ARP inspection is a security feature that validates ARP packets in a network. It intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from certain man-in- the-middle attacks.
For more information, see "Dynamic ARP Inspection" on page 377.
Port Profile (CLI Macro)
Macros provide a convenient way to save and share a common configuration. A macro is a set of CLI commands with a unique name. When a macro is applied to a port, the CLI commands contained within it are executed and added to the Running Configuration file.
For more information, see "Port Profile" on page 257.
Features 27

DHCP Server
Dynamic Host Configuration Protocol (DHCP) provides a means of passing configuration information (including the IP address of a TFTP server and a configuration file name) to hosts on a TCP/IP network. The switch can serve as a DHCP server or client.
For more information on the device serving as a DHCP server, see "SNMP" on page 161.
Protected Ports
The Protected Ports feature provides Layer 2 isolation between interfaces (Ethernet ports and LAGs) that share the same Broadcast domain (VLAN) with other interfaces.
For more information, see "Protected Ports" on page 255.
Proprietary Protocol Filtering
This feature enables user control over the filtering of packets with proprietary protocols such as CDP, VTP, DTP, UDLD, PaGP, and SSTP. The user can select any combination of the protocols to be filtered, for example: CDP and VTP.
For more information, see "Proprietary Protocol Filtering" on page 255.
Identifying a Switch via LED
The switch provides the ability to turn on a LED (through the GUI interface) for a specific length of time.
For more information, see LED Definitions.
28 Features
3
Hardware and Initial Configuration
This section describes the R1-2401 switch and how it is initially installed and configured.
It contains the following topics:
•Switch Hardware
•Initial Configuration of the Switch
Switch Hardware
This section describes the ports and LEDs on the device.
It contains the following topics:
•Switch Ports
•Front Panel LEDs
Hardware and Initial Configuration |
|
29 |
|
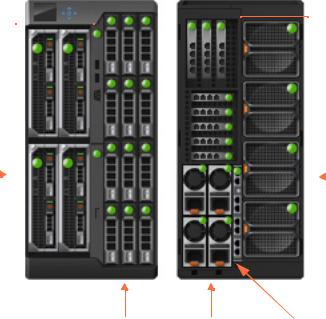
Switch Ports
Figure 3-1 shows the R1-2401device within the chassis. Only the switch hardware is described in this guide.
Figure 3-1. R1-2401
Blade |
|
|
|
|
|
|
|
|
Fan |
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
Trays |
||
Servers |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Shared |
Power |
R1-2401 |
Storage |
Supplies |
|
Types of Ports
The following ports are found on the switch:
•24 x 1 Gigabit/s Ethernet Ports. These consist of:
–8 external ports—Connected to network (visible when the switch is in the chassis)
–16 internal ports—Connected to blade servers (not visible when the switch is in the chassis)
30 |
|
Hardware and Initial Configuration |
|
 Loading...
Loading...