Konica Minolta bizhub C364e User Manual

User’s Guide
Security Operations
2013. 5 Ver. 1.02

Contents
1 |
Security |
|
|
|
1.1 |
Introduction ..................................................................................................................................... |
1-2 |
|
|
Compliance with the ISO15408 Standard ......................................................................................... |
1-2 |
|
|
Operating Precautions ....................................................................................................................... |
1-2 |
|
|
INSTALLATION CHECKLIST.............................................................................................................. |
1-3 |
|
1.2 |
Security Functions .......................................................................................................................... |
1-4 |
|
|
Check Count Clear Conditions .......................................................................................................... |
1-4 |
|
1.3 |
Data to be Protected ...................................................................................................................... |
1-5 |
|
1.4 |
Precautions for Operation Control ................................................................................................ |
1-6 |
|
|
Roles and Requirements of the Administrator................................................................................... |
1-6 |
|
|
Password Usage Requirements ........................................................................................................ |
1-6 |
|
|
Network Connection Requirements for the Machine......................................................................... |
1-6 |
|
|
Security function operation setting operating requirements.............................................................. |
1-6 |
|
|
Operation and control of the machine ............................................................................................... |
1-6 |
|
|
Machine Maintenance Control........................................................................................................... |
1-7 |
|
|
Implementing digital signature properly............................................................................................. |
1-7 |
|
|
Operating conditions for the IC card and IC card reader .................................................................. |
1-7 |
|
|
IC card owner requirements .............................................................................................................. |
1-7 |
|
1.5 |
Miscellaneous.................................................................................................................................. |
1-8 |
|
|
Password Rules ................................................................................................................................. |
1-8 |
|
|
Precautions for Use of Various Types of Applications....................................................................... |
1-8 |
|
|
Encrypting communications .............................................................................................................. |
1-8 |
|
|
Items of Data Cleared by Overwrite All Data Function ...................................................................... |
1-8 |
|
|
Fax functions...................................................................................................................................... |
1-9 |
|
|
General functions and operations...................................................................................................... |
1-9 |
2 |
Administrator Operations |
|
|
|
2.1 |
Accessing the Administrator Settings .......................................................................................... |
2-2 |
|
2.1.1 |
Accessing the Administrator Settings................................................................................................ |
2-2 |
|
2.1.2 |
Accessing the User Mode.................................................................................................................. |
2-4 |
|
2.2 |
Enhancing the Security Function................................................................................................... |
2-6 |
|
2.2.1 |
Items cleared by HDD Format ........................................................................................................... |
2-7 |
|
2.2.2 |
Setting the Password Rules............................................................................................................... |
2-8 |
|
2.2.3 |
Setting the Enhanced Security Mode .............................................................................................. |
2-10 |
|
2.3 |
Preventing Unauthorized Access ................................................................................................ |
2-12 |
|
|
Setting Prohibited Functions When Authentication Error ................................................................ |
2-12 |
|
2.4 |
Setting the External Server .......................................................................................................... |
2-14 |
|
|
Setting the External Server .............................................................................................................. |
2-14 |
|
2.5 |
System Auto Reset Function ....................................................................................................... |
2-17 |
|
|
Setting the System Auto Reset function.......................................................................................... |
2-17 |
|
2.6 |
Changing the Administrator Password....................................................................................... |
2-19 |
|
|
Changing the Administrator Password ............................................................................................ |
2-19 |
|
2.7 |
Protecting Data in the HDD.......................................................................................................... |
2-21 |
|
2.7.1 |
Setting the Encryption Key (encryption word) ................................................................................. |
2-21 |
|
2.7.2 |
Changing the Encryption Key .......................................................................................................... |
2-25 |
|
2.8 |
Overwrite All Data Function ......................................................................................................... |
2-27 |
|
|
Setting the Overwrite All Data function............................................................................................ |
2-27 |
|
2.9 |
S/MIME Communication Setting Function ................................................................................. |
2-29 |
|
|
Setting the S/MIME Communication ............................................................................................... |
2-29 |
|
2.10 |
PC-Fax RX Setting Function ........................................................................................................ |
2-32 |
|
|
PC-Fax RX Setting ........................................................................................................................... |
2-32 |
|
2.11 |
TSI User Box Setting Function..................................................................................................... |
2-34 |
|
|
TSI User Box Setting........................................................................................................................ |
2-34 |
bizhub C554e/C454e/C364e/C284e/C224e |
Contents-1 |

|
|
|
|
|
|
|
|
|
2.12 |
...............................................................................................................TCP/IP Setting Function |
2-36 |
|
2.12.1 |
Setting the IP Address ..................................................................................................................... |
2-36 |
|
2.12.2 |
Registering the DNS Server ............................................................................................................. |
2-36 |
|
2.13 |
NetWare Setting Function ............................................................................................................ |
2-37 |
|
|
Making the NetWare Setting............................................................................................................ |
2-37 |
|
2.14 |
SMB Setting Function................................................................................................................... |
2-38 |
|
|
Setting the SMB Host Name............................................................................................................ |
2-38 |
|
2.15 |
E-Mail Setting Function ................................................................................................................ |
2-39 |
|
|
Setting the SMTP Server (E-Mail Server) ......................................................................................... |
2-39 |
3 |
User Operations |
|
|
|
3.1 |
User Authentication Function ........................................................................................................ |
3-2 |
|
|
User authentication using the IC card ............................................................................................... |
3-2 |
|
3.2 |
Encrypted Document Function...................................................................................................... |
3-4 |
|
|
Accessing the Encrypted document.................................................................................................. |
3-4 |
|
3.3 |
Scan to Me Function....................................................................................................................... |
3-5 |
|
|
Scan to Me procedure ....................................................................................................................... |
3-5 |
bizhub C554e/C454e/C364e/C284e/C224e |
Contents-2 |

1
Security

1.1 |
|
|
|
|
Introduction |
1 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
1 Security
1.1Introduction
Thank you for purchasing our product.
This User’s Guide contains the operating procedures and precautions to be used when using the security functions offered by the bizhub C554e/C454e/C364e/C284e/C224e machine. To ensure the best possible performance and effective use of the machine, read this manual thoroughly before using the security functions. The administrator of the machine should keep this manual for ready reference. The manual should be of great help in finding solutions to operating problems and questions.
This User’s Guide (Ver. 1.02) describes bizhub C554e/bizhub C454e/bizhub C364e/bizhub C284e/bizhub C224e PKI Card System Control Software (MFP Controller: A5C10Y0-0100-G00-17pki).
Compliance with the ISO15408 Standard
When the Enhanced Security Mode on this machine is set to [ON], more enhanced security functions are available.
The security functions offered by the bizhub C554e/C454e/C364e/C284e/C224e machine comply with ISO/IEC15408 (level: EAL3).
Operating Precautions
The machine gives an alarm message or an alarm sound (peep) when a wrong operation is performed or a wrong entry is made during operation of the machine. (No "peep" alarm sound is issued if a specific sound setting in Sound Setting of Accessibility Setting is set to [OFF].) If the alarm message or alarm sound is given, perform the correct operation or make the correct entry according to the instructions given by the message or other means.
The administrator of the machine should exit from the current mode to return to the basic screen whenever the access to that mode is completed or if he or she leaves the machine with the mode screen left displayed.
The administrator of the machine should make sure that each individual general user exits from the current mode to return to the basic screen whenever the access to that mode is completed or if the user leaves the machine with the mode screen left displayed.
If an error message appears during operation of the machine, perform steps as instructed by the message. For details of the error messages, refer to the User’s Guide furnished with the machine and that furnished with the Authentication Unit. If the error cannot be remedied, contact your service representative.
bizhub C554e/C454e/C364e/C284e/C224e |
1-2 |

1.1 |
Introduction |
1 |
|
|
|
INSTALLATION CHECKLIST
This Installation Checklist contains items that are to be check by the Service Engineer installing this machine. The Service Engineer should check the following items, then explain each checked item to the administrator of the machine.
To Service Engineer
Make sure that each of these items is properly carried out by checking the box on the right of each item.
1. Perform the following steps before installing this machine. |
Completed |
Check with the administrator to determine if the security functions of this machine should be enhanced. If the functions should be enhanced, check the following.
If the security functions are not to be enhanced, quit the operation without checking the following.
I swear that I would never disclose information as it relates to the settings of this machine to anybody, or perform malicious or intentional act during setup and service procedures for the machine.
When giving the User’s Guide Security Operations to the administrator of the machine, check that the User’s Guide is the security-compatible version and explain to the administrator that it is security-compatible.
2.After this machine is installed, refer to the Service Manual and perform the following steps.
Check that the Firmware version (MFP Controller, CheckSum) indicated in the Service Manual matches the values shown in the Firmware Version screen.
If there is a mismatch in the Firmware version number, explain to the administrator of the machine that upgrading of the Firmware is necessary and perform upgrading of the Firmware.
Set the CE Password.
Make the service settings necessary for the Enhanced Security Mode.
Check that the SSD mounted on the machine is the type for the exclusive use for this machine.
Check that the Fax Kit has been mounted and set up properly, if fax functions are to be used.
3.After this machine is installed, refer to this User’s Guide and perform the following steps.
Check that the Administrator Password has been set by the administrator of the machine.
Check that the Encryption Key has been set by the administrator of the machine.
Check that external server has been set by the administrator of the machine.
Let the administrator of the machine set Enhanced Security Mode to [ON].
The language, in which the contents of the User’s Guide Security Operations have been evaluated, is English.
Explain the way how to get the manual in the language, in which it is evaluated.
Explain to the administrator that the settings for the security functions for this machine have been specified.
When the above steps have been properly carried out, the Service Engineer should make a copy of this page and give the original of this page to the administrator of the machine. The copy should be kept at the corresponding Service Representative for filing.
Product Name |
|
Company Name |
User Division Name |
Person in charge |
|
|
|
|
|
Customer (Administrator of Machine) |
|
|
|
|
|
|
|
|
|
Service Representative |
|
- |
|
|
|
|
|
|
|
bizhub C554e/C454e/C364e/C284e/C224e |
1-3 |

1.2 |
Security Functions |
1 |
|
|
|
1.2Security Functions
Setting the Enhanced Security Mode to [ON] will validate the security function of this machine. For details of the settings of different security functions to be changed by turning [ON] the Enhanced Security Mode, see page 2-10.
A password that can be set must the Password Rules. The machine does not accept setting of an easily decipherable password. For details of the Password Rules, see page 1-8.
If a wrong password is entered, during password authentication, a predetermined number of times (once to three times) or more set by the administrator of the machine, the machine determines that it is unauthorized access through Prohibited Functions When Authentication Error, prohibiting any further entry of the password. By prohibiting the password entry operation, the machine prevents unauthorized use or removal of data, thereby ensuring secured used of the machine.
By setting the Encryption Key, the data saved in the HDD is encrypted, thereby protecting the data in the HDD. Note, however, that the Encryption Key does not prevent the HDD from being physically removed. Make sure of a good operation control.
When the machine is to be discarded or use of a leased machine is terminated at the end of the leasing contract, the Overwrite All Data function overwrites and erases all data stored in all spaces of the HDD. The function also resets all passwords saved in the memory area on the MFP board and the SSD board to factory settings, preventing data from leaking. For details of the Overwrite All Data function, see page 2-27. For details of items to be cleared by Overwrite All Data function, see page 1-8.
Check Count Clear Conditions
The following are the conditions for clearing or resetting the check count of the number of wrong entries at the time of authentication by the Enhanced Security Mode.
<Administrator Settings>
-Authentication of Administrator Settings is successful.
bizhub C554e/C454e/C364e/C284e/C224e |
1-4 |

1.3 |
Data to be Protected |
1 |
|
|
|
1.3Data to be Protected
The underlying concept of this machine toward security is "to protect data that can be disclosed against the intention of users."
The following types of image files that have been saved in the machine and made available for use by its users are protected while the machine is being used.
-Encrypted document transmitted to the machine using a dedicated printer driver and an IC card from the client PC and saved in the machine
-Image files which have been scanned for transmission to a user mail address through e-mail (S/MIME)
The following types of data saved in the HDD are protected when use of a leased machine is terminated at the end of the leasing contract, the machine is to be discarded, or when the HDD is stolen.
-Encrypted document
-Scanned image files
-Image files other than Encrypted document
-Image files of jobs in the queue state other than Scanned image files
-Data files left in the HDD data space, used as image files and not deleted through the general deletion operation
-Temporary data files generated during print image file processing
bizhub C554e/C454e/C364e/C284e/C224e |
1-5 |

1.4 |
Precautions for Operation Control |
1 |
|
|
|
1.4Precautions for Operation Control
This machine and the data handled by this machine should be used in an office environment that meets the following conditions. The machine must be controlled for its operation under the following conditions to protect the data that should be protected.
Roles and Requirements of the Administrator
The administrator should take full responsibility for controlling the machine, thereby ensuring that no improper operations are performed.
<To Achieve Effective Security>
-A person who is capable of taking full responsibility for controlling the machine should be appointed as the administrator to make sure that no improper operations are performed.
-When using an SMTP server (mail server) or an DNS server, each server should be appropriately managed by the administrator and should be periodically checked to confirm that settings have not been changed without permission.
Password Usage Requirements
The administrator must control the Administrator Password and Encryption Key appropriately so that they may not be leaked. These passwords should not be ones that can be easily guessed.
<To Achieve Effective Security>
-Make absolutely sure that only the administrator knows the Administrator Password and Encryption Key.
-The administrator must change the Administrator Password and Encryption Key at regular intervals.
-The administrator should make sure that any number that can easily be guessed from birthdays, employee identification numbers, and the like is not set for the Administrator Password and Encryption Key.
-If the Administrator Password has been changed by the Service Engineer, the administrator should change the Administrator Password as soon as possible.
Network Connection Requirements for the Machine
If the LAN is to be connected to an outside network, no unauthorized attempt to establish connection from the external network should be permitted.
<To Achieve Effective Security>
-If the LAN, in which the machine is installed, is connected to an outside network, install a firewall or similar network device to block any access to the machine from the outside network and make the necessary settings.
Security function operation setting operating requirements
The administrator of the machine should observe the following operating conditions.
-The administrator should make sure that the machine is operated with the settings described in the installation checklist made properly in advance.
-The administrator should make sure of correct operation control so that the machine is used with the Enhanced Security Mode set to [ON].
-When the Enhanced Security Mode is turned [OFF], the administrator is to make various settings according to the installation checklist and then set the Enhanced Security Mode to [ON] again. For details of settings made by the service engineer, contact your service representative.
-When the machine is to be discarded or use of a leased machine is terminated at the end of the leasing contract, the administrator should use the Overwrite All Data function to thereby prevent data to be protected from leaking.
Operation and control of the machine
The administrator of the machine should perform the following operation control.
-The administrator of the machine should log off from the Administrator Settings whenever the operation in the Administrator Settings is completed. The administrator of the machine should also make sure that each individual user logs off from the User Authentication mode after the operation in the User Authentication mode is completed, including operation of the Encrypted document.
bizhub C554e/C454e/C364e/C284e/C224e |
1-6 |

1.4 |
Precautions for Operation Control |
1 |
|
|
|
-The administrator of the machine should set the Encryption Key according to the environment, in which this machine is used.
-The administrator should control the operation of the machine by setting an appropriate value for the Ticket Hold Time Setting.
–To set the Ticket Hold Time Setting, touch [Utility] - [Administrator Settings] - [User Authentication/Account Track] - [General Settings] - [↓] - [Ticket Hold Time Setting] on the MFP control panel.
Machine Maintenance Control
The administrator of the machine should perform the following maintenance control activities.
-Provide adequate control over the machine to ensure that only the Service Engineer is able to perform physical service operations on the machine.
-Provide adequate control over the machine to ensure that any physical service operations performed on the machine by the Service Engineer are overseen by the administrator of the machine.
-Some options require that Enhanced Security Mode be turned [OFF] before they can be used on the machine. If you are not sure whether a particular option to be additionally purchased is fully operational with the Enhanced Security Mode turned [ON], contact your Service Representative.
Implementing digital signature properly
The administrator of the machine should make the setting for adding a digital signature by selecting either [Always add signature] or [Select when sending]. He or she should make sure that the digital signature is added whenever an IC card owner sends highly confidential image data to the client PC.
Operating conditions for the IC card and IC card reader
The machine supports the following types of IC card and IC card reader.
-The types of IC cards supported by the machine are the Common Access Card (CAC) and Personal Identity Verification (PIV).
-The type of IC card reader supported by the machine is AU-211P. Be sure to use the IC card reader provided by the Service Representative. For details, contact your Service Representative.
The service representative is to install the IC card reader to the USB port on the rear right side of the machine. The administrator of the machine should make sure that the user will not relocate the IC card reader to any other USB port. Operation through any other USB port is not guaranteed.
IC card owner requirements
The administrator of the machine should make sure that operating rules that specify the following operations exist within the organization and that the operations are implemented according to the rules.
-The person responsible within the organization that uses the machine should distribute the IC card issued for use by the organization to a specific person who is authorized to own the IC card.
-The person responsible within the organization that uses the machine should prohibit the user from transferring or lending the IC card to any third person and make sure that the user reports any lost IC card. If the IC card is lost, the system is at risk of being illegally accessed. In such cases, the registered user in question should be deleted from the external server, so that the lost IC card is disabled for authentication.
-The person responsible within the organization that uses the machine should make sure that each IC card user removes his or her IC card from the card reader and never leaves the card in the card reader after he or she completes the operation of the machine.
bizhub C554e/C454e/C364e/C284e/C224e |
1-7 |

1.5 |
Miscellaneous |
1 |
|
|
|
1.5Miscellaneous
Password Rules
According to certain Password Rules, registration of a password consisting of a string of a single character or change of a password to one consisting of a string of a single character is rejected for the Administrator Password and Encryption Key. For the Administrator Password and Encryption Key, the same password as that currently set is not accepted.
Study the following table for more details of the number and types of characters that can be used for each password. For details of the settings of the Password Rules, see page 2-8.
Types of passwords |
Number of |
Types of characters |
|
characters |
|
Administrator Password |
8 to 64 |
• Numeric characters: 0 to 9 |
|
characters* |
• Alpha characters: upper and lower case letters |
|
|
• Symbols: !, #, $, %, &, ', (, ), *, ,, -, ., /, :, ;, <, =, >, |
|
|
?, @, [, \, ], ^, _, `, {, |, }, ~, + |
|
|
• Special characters (68 characters) |
|
|
Selectable from among a total of 161 characters |
|
|
|
Encryption Key |
20 characters |
• Numeric characters: 0 to 9 |
|
|
• Alpha characters: upper and lower case letters |
|
|
• Symbols: !, #, $, %, &, ', *, +, -, ., /, =, <, @, ^, _, `, |
|
|
{, |, }, ~ |
|
|
Selectable from among a total of 83 characters |
|
|
|
*: The minimum number of characters set in [Set Minimum Password Length] must be set for the password. The default value is 12.
Precautions for Use of Various Types of Applications
When the Encrypted document function is to be used, be sure to install the dedicated printer driver in the client PC.
Encrypting communications
Effective 2014, do not use the 1024-bit RSA and SHA-1. Or, an increased risk results of falsification and leakage of data to be protected.
Items of Data Cleared by Overwrite All Data Function
The Overwrite All Data function clears the following items of data.
Items of Data Cleared |
Description |
Password Rules |
Sets [Invalid] and disables [Set Minimum Password Length] |
|
|
Encrypted document |
Deletes all Encrypted document saved in Encrypted document User Box |
|
|
Scanned image files |
Deletes all Scanned image files |
|
|
Image files |
• Image files other than Encrypted document |
|
• Image files of jobs in the queue state other than Scanned image files |
|
• Data files left in the HDD data space, used as image files and not deleted |
|
through the general deletion operation |
|
• Temporary data files generated during print image file processing |
|
|
Encryption Key |
Clears the currently set Encryption Key |
|
|
Administrator Password |
Clears the currently set password, resetting it to the factory setting |
|
(1234567812345678) |
|
|
S/MIME certificate |
Deletes the currently set S/MIME certificate |
|
|
External Server |
Deletes the currently set external server |
|
|
Loadable driver |
Deletes the currently set loadable driver |
|
|
Daylight Saving Time |
Set to [No] |
|
|
Time Adjustment Setting |
Set to [OFF] |
(NTP) |
|
|
|
bizhub C554e/C454e/C364e/C284e/C224e |
1-8 |

1.5 |
Miscellaneous |
|
1 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Items of Data Cleared |
Description |
|
|
|
Time/date data |
Varies corrected data, if the time-of-day data is corrected due to, for exam- |
|
|
|
|
ple, the daylight saving time |
|
|
|
|
|
|
Fax functions
An optional Fax Kit is required for using fax functions. Contact your Service Representative.
General functions and operations
For details of general functions and settings of this machine, refer to the User's Guide furnished with the machine.
bizhub C554e/C454e/C364e/C284e/C224e |
1-9 |

2 Administrator Operations

2.1 |
|
|
|
|
Accessing the Administrator Settings |
2 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
2 Administrator Operations
2.1Accessing the Administrator Settings
In Administrator Settings, the settings for the machine system and network can be registered or changed.
This machine implements authentication of the user of the Administrator Settings function through the Administrator Password that verifies the identity as the administrator of the person who accesses the function. During the authentication procedure, the Administrator Password entered for the authentication purpose appears as "*" or "-" on the display.
When the Enhanced Security Mode is set to [ON], the number of times in which authentication fails is counted.
NOTICE
Make sure that none of the general users of the machine will know the Administrator Password.
If the Administrator Password is forgotten, it must be set again by the Service Engineer. Contact your Service Representative.
2.1.1Accessing the Administrator Settings
The machine does not accept access to the Administrator Settings under any of the following conditions. Wait for some while before attempting to gain access to the Administrator Settings again.
-The Administrator Settings has been logged on to through access made from the PC.
-A remote operation is being performed from an application on the PC.
-There is a job being executed by the machine.
-There is a reserved job (timer TX, fax redial waiting, etc.) in the machine.
-Immediately after the main power switch has been turned ON.
-A malfunction code is displayed on the machine.
0Do not leave the machine with the setting screen of Administrator Settings left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Administrator Settings.
1Touch [Menu] ö [Utility].
2Touch [Administrator Settings].
bizhub C554e/C454e/C364e/C284e/C224e |
2-2 |

2.1 |
Accessing the Administrator Settings |
2 |
|
|
|
3
4
5
Enter the Administrator Password from the keyboard.
%Touch [C] to clear all characters.
%Touch [Delete] to delete the last character entered.
%Touch [Shift] to show the upper case/symbol screen.
%Touch [Cancel] to go back to the previous screen.
Touch [OK].
%If a wrong Administrator Password is entered, a message that tells that the Administrator Password does not match appears. Enter the correct Administrator Password.
%If the Enhanced Security Mode is set to [ON], entry of a wrong password is counted as unauthorized access. If a wrong Administrator Password is entered a predetermined number of times (once to three times) or more set by the administrator of the machine, a message appears saying that the machine accepts no more Administrator Passwords because of unauthorized access for any subsequent entry of the Administrator Password. The machine is then set into an access lock state. To cancel the access lock state, settings must be made by the Service Engineer; or, turn off, and then turn on, the main power switch of the machine. If the main power switch is turned off and on, the access lock state is canceled after the lapse of time set for [Release Time Settings]. When the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. If there is no wait period between turning the main power switch off, then on again, the machine may not function properly.
Here is the sequence, through which the main power switch and sub power key are turned on and off:
Turn off the sub power key ö Turn off the main power switch ö Turn on the main power switch ö Turn on the sub power key
Press the [Reset] key to log off from the Administrator Settings.
bizhub C554e/C454e/C364e/C284e/C224e |
2-3 |
2.1 |
Accessing the Administrator Settings |
2 |
|
|
|
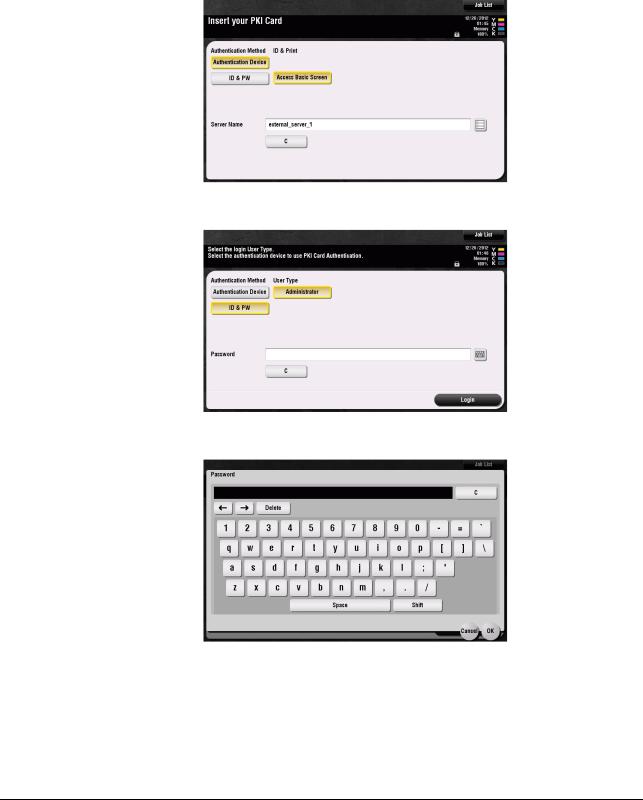
2.1.2Accessing the User Mode
You can log on to the User Mode as an administrator. In the User Mode, you can check or delete a job, which is disabled in Administrator Settings.
Reference
-The authority relating to box settings is the same as that of Administrator Settings.
0Do not leave the machine with the User Mode setting screen left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the User Mode.
1Touch [ID & PW].
2 Touch the keyboard icon in the [User Name] field.
3 Enter the Administrator Password from the keyboard.
%Touch [C] to clear all characters
%Touch [Delete] to delete the last character entered.
%Touch [Shift] to show the upper case/symbol screen.
%Touch [Cancel] to go back to the previous screen.
4 Touch [OK].
bizhub C554e/C454e/C364e/C284e/C224e |
2-4 |

2.1 |
Accessing the Administrator Settings |
2 |
|
|
|
5
6
Touch [Access] or [Login].
%If a wrong Administrator Password is entered, a message that tells that the authentication has failed appears. Enter the correct Administrator Password.
%If the Enhanced Security Mode is set to [ON], entry of a wrong password is counted as unauthorized access. If a wrong Administrator Password is entered a predetermined number of times (once to three times) or more set by the administrator of the machine, a message appears saying that the machine accepts no more Administrator Passwords because of unauthorized access for any subsequent entry of the Administrator Password. The machine is then set into an access lock state. To cancel the access lock state, settings must be made by the Service Engineer; or, turn off, and then turn on, the main power switch of the machine. If the main power switch is turned off and on, the access lock state is canceled after the lapse of time set for [Release Time Settings]. When the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. If there is no wait period between turning the main power switch off, then on again, the machine may not function properly.
Here is the sequence, through which the main power switch and sub power key are turned on and off:
Turn off the sub power key ö Turn off the main power switch ö Turn on the main power switch ö Turn on the sub power key
Touch [Access] or [Close] to log off from the User Mode.
bizhub C554e/C454e/C364e/C284e/C224e |
2-5 |

2.2 |
Enhancing the Security Function |
2 |
|
|
|
2.2Enhancing the Security Function
When access to the machine by the administrator of the machine through the Administrator Settings from the control panel is authenticated, the machine enables setting of the Enhanced Security Mode that allows settings for enhancing each of different security functions to be converted all at once.
In the Enhanced Security Mode, the machine allows selection of whether to use the Enhanced Security Mode or not. If the Enhanced Security Mode is set to [ON], a count is taken of the number of unauthorized accesses to the Administrator Settings. A function is also set that determines whether Administrator Password meets predetermined requirements. The security function is thus enhanced in the Enhanced Security Mode.
The following settings must first be made before the Enhanced Security Mode is set to [ON].
NOTICE
First, set the Encryption Key. To set the Encryption Key, HDD Format must first be executed. Execution of the HDD Format clears various setting values. For details of items that are cleared by HDD Format, see page 2-7.
If initialization is executed by the Service Engineer, the Password Rules are set to [Invalid] and the Administrator Password is reset to the factory setting (1234567812345678). To set the Administrator Password and turn [ON] the Enhanced Security Mode again.
Settings to be Made in Advance |
Description |
Administrator Password |
Meet the Password Rules. |
|
The factory setting is "1234567812345678." |
|
|
Encryption Key |
Set the Encryption Key. |
|
|
Service settings |
Calls for setting made by the Service Engineer. For details, contact |
|
your Service Representative. |
|
|
Setting the Enhanced Security Mode to [ON] changes the setting values of the following functions.
NOTICE
If an attempt is made to change a setting that has been changed as a result of setting the Enhanced Security Mode to [ON], a screen may appear indicating that the Enhanced Security Mode is to be canceled. Note that executing this screen will cancel the Enhanced Security Mode.
The description "not to be changed" given in parentheses in the table below indicates that the specific setting cannot be changed with the Enhanced Security Mode set to [ON].
Function Name |
Factory Setting |
When Enhanced Security Mode is set to [ON] |
Password Rules |
Invalid |
Enable (not to be changed) |
|
|
If [Enable] is set for Password Rules, the types and num- |
|
|
ber of characters to be used for each password are lim- |
|
|
ited. |
|
|
For details of the Password Rules, see page 1-8. |
|
|
|
Prohibited Functions |
Mode 1 |
Mode 2 (not to be changed): Three times is set. |
When Authentication Er- |
|
* The number of times can be changed to once, twice, |
ror |
|
or three times. |
|
|
|
Release Time settings |
5 min. |
The setting value should be 5 min. or more |
|
|
(no value less than 5 can be set) |
|
|
|
Public User Access |
Restrict |
Restrict (not to be changed) |
|
|
|
User Box Administrator |
Restrict |
Restrict (not to be changed) |
Setting |
|
|
|
|
|
S/MIME Encryption |
3DES |
3DES (not to be changed to DES or RC-2) |
Method |
|
|
|
|
|
FTP Server |
ON |
OFF (not to be changed) |
|
|
|
SNMPv1/v2c Settings |
Read setting: |
Read setting: Enable, Write setting: Invalid |
|
Enable |
(not to be changed) |
|
Write setting: |
|
|
Invalid |
|
|
|
|
SNMP v3 Settings |
Restrict |
Restrict (not to be changed) |
|
|
|
Print Data Capture |
Allow |
Restrict (not to be changed) |
|
|
|
bizhub C554e/C454e/C364e/C284e/C224e |
2-6 |
 Loading...
Loading...