Avaya ERS 1600, ERS 8300, ERS 2500, ERS 8600, ERS 5500 Technical Configuration Manual
...
Authentication, Authorization and
Accounting (AAA) for ERS and ES
Technical Configuration Guide
E.M.E.A. IP Core Sales Engineering
Document Date: November 2010
Document Number : NN48500-558
Document Version: 1.1
Ethernet Routing Switch
1600, 8300, 8600, 2500, 4500, 5500
Ethernet Switch
460/470
Engineering
2
November 2010
avaya.com
© 2010 Avaya Inc.
All Rights Reserved.
Notices
While reasonable efforts have been made to ensure that the information in this document is complete and accurate at the time of
printing, Avaya assumes no liability for any errors. Avaya reserves the right to make changes and corrections to the information in
this document without the obligation to notify any person or organization of such changes.
Documentation disclaimer
Avaya shall not be responsible for any modifications, additions, or deletions to the original published version of this documentation
unless such modifications, additions, or deletions were performed by Avaya. End User agree to indemnify and hold harmless Avaya,
Avaya’s agents, servants and employees against all claims, lawsuits, demands and judgments arising out of, or in connection with,
subsequent modifications, additions or deletions to this documentation, to the extent made by End User.
Link disclaimer
Avaya is not responsible for the contents or reliability of any linked Web sites referenced within this site or documentation(s)
provided by Avaya. Avaya is not responsible for the accuracy of any information, statement or content provided on these sites and
does not necessarily endorse the products, services, or information described or offered within them. Avaya does not guarantee that
these links will work all the time and has no control over the availability of the linked pages.
Warranty
Avaya provides a limited warranty on this product. Refer to your sales agreement to establish the terms of the limited warranty. In
addition, Avaya’s standard warranty language, as well as information regarding support for this product, while under warranty, is
available to Avaya customers and other parties through the Avaya Support Web site: http://www.avaya.com/support
Please note that if you acquired the product from an authorized reseller, the warranty is provided to you by said reseller and not by
Avaya.
Licenses
THE SOFTWARE LICENSE TERMS AVAILABLE ON THE AVAYA WEBSITE, HTTP://SUPPORT.AVAYA.COM/LICENSEINFO/
ARE APPLICABLE TO ANYONE WHO DOWNLOADS, USES AND/OR INSTALLS AVAYA SOFTWARE, PURCHASED FROM
AVAYA INC., ANY AVAYA AFFILIATE, OR AN AUTHORIZED AVAYA RESELLER (AS APPLICABLE) UNDER A COMMERCIAL
AGREEMENT WITH AVAYA OR AN AUTHORIZED AVAYA RESELLER. UNLESS OTHERWISE AGREED TO BY AVAYA IN
WRITING, AVAYA DOES NOT EXTEND THIS LICENSE IF THE SOFTWARE WAS OBTAINED FROM ANYONE OTHER THAN
AVAYA, AN AVAYA AFFILIATE OR AN AVAYA AUTHORIZED RESELLER, AND AVAYA RESERVES THE RIGHT TO TAKE
LEGAL ACTION AGAINST YOU AND ANYONE ELSE USING OR SELLING THE SOFTWARE WITHOUT A LICENSE. BY
INSTALLING, DOWNLOADING OR USING THE SOFTWARE, OR AUTHORIZING OTHERS TO DO SO, YOU, ON BEHALF OF
YOURSELF AND THE ENTITY FOR WHOM YOU ARE INSTALLING, DOWNLOADING OR USING THE SOFTWARE
(HEREINAFTER REFERRED TO INTERCHANGEABLY AS "YOU" AND "END USER"), AGREE TO THESE TERMS AND
CONDITIONS AND CREATE A BINDING CONTRACT BETWEEN YOU AND AVAYA INC. OR THE APPLICABLE AVAYA
AFFILIATE ("AVAYA").
Copyright
Except where expressly stated otherwise, no use should be made of the Documentation(s) and Product(s) provided by Avaya. All
content in this documentation(s) and the product(s) provided by Avaya including the selection, arrangement and design of the
content is owned either by Avaya or its licensors and is protected by copyright and other intellectual property laws including the sui
generis rights relating to the protection of databases. You may not modify, copy, reproduce, republish, upload, post, transmit or
distribute in any way any content, in whole or in part, including any code and software. Unauthorized reproduction, transmission,
dissemination, storage, and or use without the express written consent of Avaya can be a criminal, as well as a civil offense under
the applicable law.
Third Party Components
Certain software programs or portions thereof included in the Product may contain software distributed under third party agreements
("Third Party Components"), which may contain terms that expand or limit rights to use certain portions of the Product ("Third Party
Terms"). Information regarding distributed Linux OS source code (for those Products that have distributed the Linux OS source
code), and identifying the copyright holders of the Third Party Components and the Third Party Terms that apply to them is available
on the Avaya Support Web site: http://support.avaya.com/Copyright.
Trademarks
The trademarks, logos and service marks ("Marks") displayed in this site, the documentation(s) and product(s) provided by Avaya
are the registered or unregistered Marks of Avaya, its affiliates, or other third parties. Users are not permitted to use such Marks
without prior written consent from Avaya or such third party which may own the Mark. Nothing contained in this site, the
documentation(s) and product(s) should be construed as granting, by implication, estoppel, or otherwise, any license or right in and
to the Marks without the express written permission of Avaya or the applicable third party. Avaya is a registered trademark of Avaya
Inc. All non-Avaya trademarks are the property of their respective owners.
Downloading documents
For the most current versions of documentation, see the Avaya Support. Web site: http://www.avaya.com/support.
Contact Avaya Support
Avaya provides a telephone number for you to use to report problems or to ask questions about your product. The support
telephone number is 1-800-242-2121 in the United States. For additional support telephone numbers, see the Avaya Web site:
http://www.avaya.com/support.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

3
November 2010
avaya.com
Abstract
This document provides examples on configuring RADIUS & TACACS+ on the ERS 1600, 8300,
8600, 2500, 4500, 5500 and ES 460/470. This document covers some of the more popular Radius &
TACACS+ commands and attributes how to configure server and client side. It gives also various
examples with different users and details log files on client and server side. Finally some sniffer
traces show how protocols exchange data between server and client.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
4
November 2010
avaya.com
Table of Contents
1. Overview .............................................................................................................................................. 6
2. RADIUS ................................................................................................................................................. 6
2.1 Feature Operation ......................................................................................................................... 6
2.2 Avaya Switches RADIUS Support............................................................................................... 11
2.3 RADIUS Server Configuration – Using FreeRadius.................................................................... 12
2.4 RADIUS Client Configuration ...................................................................................................... 14
2.5 RADIUS Server & Client Log Files .............................................................................................. 17
2.6 Sniffer Traces on RADIUS Server............................................................................................... 32
3. TACACS+ ........................................................................................................................................... 39
3.1 Terminology................................................................................................................................. 39
3.2 Feature Operation ....................................................................................................................... 40
3.3 Avaya Switches TACACS+ Support ........................................................................................... 43
3.4 TACACS+ Server Configuration – Using tac_plus ...................................................................... 45
3.5 TACACS+ Client Configuration ................................................................................................... 47
3.6 TACACS+ Server & Client Log Files ........................................................................................... 49
3.7 Sniffer Traces on TACACS+ Server ........................................................................................... 59
4. Customer service .............................................................................................................................. 71
4.1 Getting technical documentation ................................................................................................. 71
4.2 Getting product training ............................................................................................................... 71
4.3 Getting help from a distributor or reseller .................................................................................... 71
4.4 Getting technical support from the Avaya Web site .................................................................... 71
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
5
November 2010
avaya.com
Tip – Highlights a configuration or technical tip.
Note – Highlights important information to the reader.
Warning – Highlights important information about an action that may result in equipment
damage, configuration or data loss.
Bold text indicates emphasis.
Italic text in a Courier New font indicates text the user must enter or select in a menu item, button
or command:
ERS5520-48T# show running-config
Output examples from Avaya devices are displayed in a Lucinda Console font:
ERS5520-48T# show running-config
! Embedded ASCII Configuration Generator Script
! Model = Ethernet Routing Switch 5520-24T-PWR
! Software version = v5.0.0.011
enable
configure terminal
Conventions
This section describes the text, image, and command conventions used in this document.
Symbols:
Text:
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
6
November 2010
avaya.com
1. Overview
Access control is the way you control who is allowed access to the network server and what services they
are allowed to use once they have access. Authentication, authorization, and accounting (AAA) network
security services provide the primary framework through which you set up access control on your network
device or access server.
Network professionals have always been challenged with having many individuals manage multiple
network devices with a single account. When problems occur it is nearly impossible to trace back
accountability and identify what changes were made by whom. RADIUS was designed to combat the
authentication and accounting (logging tied to user) problem; however, authorization (what an
authenticated user was allowed to do) controls were still missing. TACACS+ (latest implementation of
TACACS) has the ability to do authentication, authorization and accounting.
2. RADIUS
Remote Access Dial-In User Services (RADIUS) is a distributed client/server system that assists in
securing networks against unauthorized access, allowing a number of communication servers and clients
to authenticate user identities through a central database. The database within the RADIUS server stores
information about clients, users, passwords, and access privileges, protected with a shared secret.
RADIUS is a fully open and standard protocol defined by RFCs (authentication [RFC 2865] and
accounting [RFC 2866]). RADIUS protocol is an AAA protocol using IP framing with UDP port 1812 for
authentication and port 1813 for accounting.
2.1 Feature Operation
A RADIUS application has two components:
RADIUS server : A computer equipped with RADIUS server software (for example, a UNIX*
workstation) that is located at a central office or campus. It has authentication and access
information in a form that is compatible with the client. Typically, the database in the RADIUS
server stores client information, user information, password, and access privileges, including the
use of shared secret. A network can have at minimum one server for both authentication and
accounting, or one server for each service.
RADIUS client : A switch, router, or a remote access device equipped with RADIUS client
software that sends the authentication request to the RADIUS server upon a user attempting to
login via the RADIUS client. The client is the network access point between the remote users and
the server.
The RADIUS process includes:
RADIUS authentication, which you can use to identify remote users before you give them access
to a central network site.
RADIUS accounting, which enables data collection on the server during a remote user’s dial-in
session with the client.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

7
November 2010
avaya.com
802.1x (EAP), if enabled, has a mandatory requirement to authenticate users by Radius.
Hence, Layer two switches supporting 802.1x (EAP) support RADIUS authentication.
RADIUS
SERVER
Authentication
Service
RADIUS
CLIENT
AUTHENTICATION
USER LOGIN
(Console/Telnet/SSH)
ACCESS REQUEST
USER NAME
(User Password :
128bits keyed MD5)
CLIENT ID
PORT ID
ACCESS CHALLENGE
STATE (1)
ACCESS ACCEPT
CONFIG VALUES
(1) Used when Radius server requires additional information such as
SecurID number.
2.1.1 RADIUS Authentication
With RADIUS authentication, a remote RADIUS client can authenticate users attempting to log in. The
RADIUS server also provides access authority. RADIUS assists network security and authorization by
managing a database of users. The switch can use the database to verify user names and passwords, as
well as information about the type of access priority available to the user.
When the RADIUS client sends an authentication request, if the RADIUS server requires additional
information, such as a SecurID number, it sends a challenge-response. Along with the challengeresponse, a reply-message attribute is sent. The reply-message is a text string, such as "Please enter the
next number on your SecurID card". The maximum length of each reply-message attribute is 253
characters (as defined by the RFC). If you have multiple instances of reply-message attributes that
together form a large message which can be displayed to the user, the maximum total length is 2000
characters.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

8
November 2010
avaya.com
UDP frame official port number is 1812, not 1645 (conflicts with the
"datametrics" service)
RADIUS Attributes Cont.
13 Framed-Compression
14 Login-IP-Host
15 Login-Service
16 Login-TCP-Port
18 Reply-Message
19 Callback-Number
20 Callback-Id
22 Framed-Route
23 Framed-IPX-Network
24 State
25 Class
26 Vendor-Specific
27 Session-Timeout
28 Idle-Timeout
29 Termination-Action
30 Called-Station-Id
31 Calling-Station-Id
32 NAS-Identifier
33 Proxy-State
34 Login-LAT-Service
35 Login-LAT-Node
36 Login-LAT-Group
37 Framed-AppleTalk-Link
38 Framed-AppleTalk-Network
39 Framed-AppleTalk-Zone
60 CHAP-Challenge
61 NAS-Port-Type
62 Port-Limit
63 Login-LAT-Port
0 8 31
16
Code
Identifier Length
Response Authenticator
Attributes...
RADIUS Codes
1 Access-Request
2 Access-Accept
3 Access-Reject
11 Access-Challenge
12 Status-Server (experimental)
13 Status-Client (experimental)
255 Reserved
RADIUS Attributes
1 User-Name
2 User-Password
3 CHAP-Password
4 NAS-IP-Address
5 NAS-Port
6 Service-Type
7 Framed-Protocol
8 Framed-IP-Address
9 Framed-IP-Netmask
10 Framed-Routing
11 Filter-Id
12 Framed-MTU …/…
RADIUS Packet Format – RFC 2865
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

9
November 2010
avaya.com
RADIUS
SERVER
Accounting
Service
RADIUS
CLIENT
ACCOUNTING
USER LOGIN
(Console/Telnet/SSH)
ACCOUTING ON REQUEST
ACCOUNTING ON
(configuration)
ACCOUNTING OFF
(configuration)
ACCOUTING OFF REQUEST
ACCOUTING START
REQUEST
USER LOGOUT
(Console/Telnet/SSH)
ACCOUTING STOP REQUEST
(Specific to the user)
Duration/Bytes/Packets
ACCOUTING INTERIM
REQUEST (1)
(Specific to the user)
(1) an Accounting Interim Request is sent every time the internal buffer
used to save user modifications is full (40 commands)
2.1.2 RADIUS Accounting
RADIUS accounting logs all of the activity of each remote user in a session on the centralized RADIUS
accounting server. Session IDs for each RADIUS account are generated as 12-character strings. The first
four characters in the string form a random number in hexadecimal format. The last eight characters in
the string indicate, in hexadecimal format, the number of user sessions started since reboot.
The Network Access Server (NAS) IP address for a session is the address of the switch interface to which
the remote session is connected over the network. For a console session, modem session, and sessions
running on debug ports, this value is set to 0.0.0.0 (as is done with RADIUS authentication).
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

10
November 2010
avaya.com
Radius Attribute 40 : Acct-Status-Type.
Length : 6
Value : The Value field is four octets.
1 Start
2 Stop
3 Interim-Update
7 Accounting-On
8 Accounting-Off
9-14 Reserved for Tunnel Accounting
15 Reserved for Failed
UDP frame official port number is 1813, not 1646 (conflicts with
the "sa-msg-port" service)
0 8 31
16
Code
Identifier Length
Response Authenticator
Attributes ...
RADIUS Attributes
40 Acct-Status-Type
41 Acct-Delay-Time
42 Acct-Input-Octets
43 Acct-Output-Octets
44 Acct-Session-Id
45 Acct-Authentic
46 Acct-Session-Time
47 Acct-Input-Packets
48 Acct-Output-Packets
49 Acct-Terminate-Cause
50 Acct-Multi-Session-Id
51 Acct-Link-Count
RADIUS Codes
4 Accounting-Request
5 Accounting-Response
RADIUS Packet Format – RFC 2866
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
11
November 2010
avaya.com
RADIUS
authenti-
cation
802.1x
(EAP)
RADIUS
authenti-
cation
RADIUS
accoun-
ting
802.1x
(EAP)
RADIUS
accoun-
ting
RADIUS
accounting for CLI
commands
RADIUS
user
access
profile
RADIUS
SNMP
accoun-
ting
ERS 8600
Yes
Yes
Yes
Yes
Yes
Yes
Yes
ERS 8300
Yes
Yes
Yes
Yes
Yes
Yes
No
ERS 1600
Yes
Yes
Yes
Yes
Yes
Yes
No
ES 460/470
Yes
Yes
No
No
No
No
No
ERS 2500
Yes
Yes
No
Yes
No
No
No
ERS 4500
Yes
Yes
No
Yes
No
No
No
ERS 5500
Yes
Yes
No
Yes
No
No
No
2.1.3 RADIUS Accounting for 802.1x (EAP)
Ethernet Routing Switch 1600, 8600, 8300, 5500 and 4500 supports accounting for 802.1x ( EAP)
sessions using RADIUS accounting protocol. A user session is defined as the interval between the
instance at which a user is successfully authenticated (port moves to authorized state) and the instance
at which the port moves out of the authorized state.
2.1.4 RADIUS Accounting for CLI Commands
RADIUS accounting will keep track of user, session duration, number of octects and packets (in and out).
This feature allows you to keep track of all CLI commands typed by user during session.
2.1.5 RADIUS User Access Profile
As a network administrator, you can override a user’s access to specific CLI commands by configuring
the RADIUS server for user authentication. You must still give access based on the existing six access
levels in the ERS 8600, but you can customize user access by permitting and preventing access to
specific CLI commands.
2.1.6 RADIUS SNMP Accounting
RADIUS accounting will record the duration of the SNMP version 1, 2 or 3 session and the number of
packets/octets sent and received during the SNMP session.
2.2 Avaya Switches RADIUS Support
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

12
November 2010
avaya.com
client 10.10.50.1 {
secret = Dda
shortname = 8600
}
client 10.10.44.5 {
secret = Dda
shortname = 4548GT-PWR
}
$INCLUDE /usr/share/freeradius/dictionary.nortel
VENDOR Nortel 1584
BEGIN-VENDOR Nortel
ATTRIBUTE Access-Priority 192 integer
VALUE Access-Priority none 0
VALUE Access-Priority ro 1
VALUE Access-Priority l1 2
VALUE Access-Priority l2 3
VALUE Access-Priority l3 4
VALUE Access-Priority rw 5
VALUE Access-Priority rwa 6
#CLI Commands
ATTRIBUTE Cli-Commands 193 string
2.3 RADIUS Server Configuration – Using FreeRadius
The following RADIUS Server configuration is based on FreeRadius, www.freeradius.org. Once installed
on a Linux host, there are several configuration files to edit as shown below
2.3.1 /etc/raddb/client.conf
This file contains the NAS list with shared secret.
2.3.2 /etc/raddb/dictionary
This file contains the dictionary file for all clients. You have to create a specific dictionary file
(dictionary.nortel) for user access level and add an include statement in the /etc/raddb/dictionary file.
2.3.3 /usr/share/freeradius/dictionary.nortel
This file contains specific statements for ERS 8600, 8300 and 1600.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
13
November 2010
avaya.com
#CLI profile
ATTRIBUTE Command-Access 194 integer
VALUE Command-Access False 0
VALUE Command-Access True 1
#CLI Commands
ATTRIBUTE Commands 195 string
#802 priority (value: 0-7)
ATTRIBUTE EAP-Port-Priority 1 integer
END-VENDOR Nortel
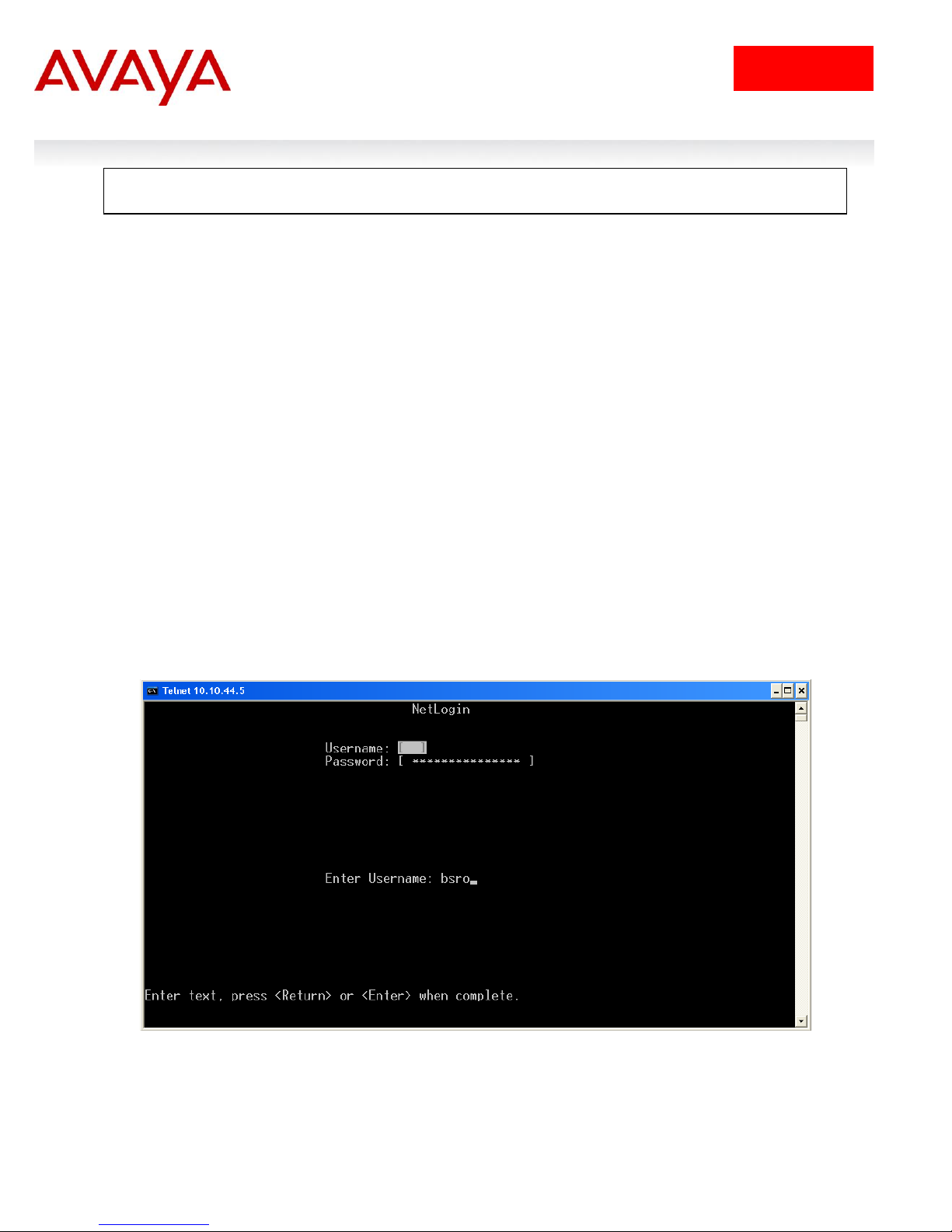
bsro Auth-Type == Local,User-Password == "bsro"
Service-Type = NAS-Prompt-User
bsrw Auth-Type == Local,User-Password == "bsrw"
Service-Type = Administrative-User
ro Auth-Type == Local,User-Password == "ro"
Access-Priority = ro
rwa Auth-Type == Local,User-Password == "rwa"
Access-Priority = rwa
eap Auth-Type == EAP,User-Password == "eap"
Tunnel-Type = 13,
Tunnel-Medium-Type = 6,
Tunnel-private-Group-Id = 51,
EAP-port-Priority = 3
The ES 460/470 and ERS 2500, 4500, 5500 switches each has two user access levels:
read-only or read-write
The ERS 1600, 8300 and 8600 switches each has six different user access levels: ro,
l1, l2, l3, rw and rwa
2.3.4 /etc/raddb/users
This file contains the users list with user rights and specific parameters. It can also contain the VLAN ID
and port priority for 802.1x (EAP) clients – please see ―eap‖ user shown below as an example which
defines VLAN ID 51 and port priority 3.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

14
November 2010
avaya.com
[root@linux2 raddb]# /etc/rc2.d/S96radiusd restart
ERS 4548GT-PWR
FreeRadius
Server
10.10.50.40
10.10.44.5
10.10.50.1
802.1x (EAP) User
Telnet/SSH/CLI
Administrative User
802.1x (EAP) User
ERS 8600
Share secret = Dda
2.3.5 /etc/raddb/radiusd.conf
This file is the main configuration file for the RADIUS server. You can enable or disable authentication
(eap, pap, mschap etc ….) and you can also add extra login information. You will need to uncomment the
line detail auth_log {.
This will create a file with the following format
detailfile = ${radacctdir}/%{Client-IP-Address}/auth-detail-%Y%m%d
2.3.6 /etc/init.d/radiusd
This file is the startup file for RADIUS process. Please check that you have a link to
/etc/rcX.d/S96radiusd (X can be 2, 3 or 5 depending on your run level). Also check that radiusd is
started with –y flag. You will write details about every authentication request in the radius.log file.
When you modify the configuration file, you have to restart RADIUS process using command
2.4 RADIUS Client Configuration
Two different product lines, ES 460/470 Series and ERS 2500, 4500, 5500 each has the same logic for
configuration whereas the ERS 1600, 8300 and 8600 each has a different logic for configuration.
Network diagram with RADIUS client and server can be simplified and summarized in the following
diagram.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

15
November 2010
avaya.com
To configure RADIUS
4548GT-PWR# conf t
Enter configuration commands, one per line. End with CNTL/Z.
4548GT-PWR(config)# radius-server host 10.10.50.40
4548GT-PWR(config)# radius-server key Dda
4548GT-PWR(config)# radius-server password fallback
4548GT-PWR(config)# cli password switch telnet radius
4548GT-PWR(config)# radius accounting enable
To display RADIUS configuration
4548GT-PWR(config)# show radius-server
Password Fallback: Enabled
Primary Host: 10.10.50.40
Secondary Host: 0.0.0.0
Port: 1812
Time-out: 2
Key: ***************
Radius Accounting is Enabled
AcctPort: 1813
4548GT-PWR(config)# show cli password type
Console Switch Password Type: None
Console Stack Password Type: None
Telnet/WEB Switch Password Type: RADIUS Authentication
Telnet/WEB Stack Password Type: None
The source IP address sent by the switch (Layer 2 operation) is always the Management IP
address configured on the switch when sending a RADIUS client authentication request.
There is no way to change source RADIUS IP address. When the switch is configured in routed
mode, it uses interface IP address where frame is sent. Hence, if you have multiple IP interfaces
facing the core network where a RADIUS request could be sent, you will have to configure the
RADIUS server with each IP address.
With the ES 460/470 and ERS 2500, 4500, 5500 switches, you can configure two RADIUS
servers, a primary server and a secondary server. If all servers are not reachable (no answers)
then local authentication is done if Password Fallback feature is enabled. You get the following
message at console:
Querying RADIUS server, please wait...
no response from RADIUS servers
2.4.1 ES 460/470 Series and ERS 2500, 4500, 5500
ACLI or JDM (Java Device Manager) can be used to configure the switch. For simplicity and readability,
we will document command line interface commands assuming the RADIUS server IP address is
10.10.50.40, and the client shared secret is ―Dda‖ for telnet access authentication.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
16
November 2010
avaya.com
To configure RADIUS
8600A:6# config radius server create 10.10.50.40 secret Dda
8600A:6# config radius server create 10.10.50.40 secret Dda usedby eapol
8600A:6# config radius enable true
8600A:6# config radius acct-enable true
8600A:6# config radius acct-include-cli-commands true
To display RADIUS configuration
8600A:6# show radius info
Sub-Context: clear config dump monitor show test trace wsm asfm sam
Current Context:
acct-attribute-value : 193
acct-enable : true
acct-include-cli-commands : true
access-priority-attribute : 192
auth-info-attr-value : 91
command-access-attribute : 194
cli-commands-attribute : 195
cli-cmd-count : 40
cli-profile-enable : false
enable : true
igap-passwd-attr : standard
igap-timeout-log-fsize : 512
maxserver : 10
mcast-addr-attr-value : 90
sourceip-flag : false
8600A:6# show radius server config
Sub-Context: clear config dump monitor show test trace wsm asfm sam
Current Context:
create :
Name Usedby Secret Port Prio Retry Timeout Enabled
Acct-port Acct-enabled source-ip
10.10.50.40 cli Dda 1812 10 1 3 true
1813 true 0.0.0.0
10.10.50.40 eapol Dda 1812 10 1 3 true
1813 true 0.0.0.0
2.4.2 ERS 1600, 8300 and 8600
ACLI is or JDM (Java Device Manager) can be used to configure the switch, for simplicity and readability,
we will document command line interface commands
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
17
November 2010
avaya.com
delete : N/A
set : N/A
With the ERS 1600, 8300, and 8600, you can change the RADIUS source IP address by using
the following command :
8000A:6# config radius server create <ipaddr> secret <value> [usedby
<value>] [port <value>] [priority <value>] [retry <value>] [timeout
<value>] [enable <value>] [acct-port <value>] [acct-enable <value>]
[source-ip <value>]
With the ERS 1600, 8300, and 8600, you can configure up to ten RADIUS servers (each server
is assigned a priority and is contacted in that order). If all servers are not reachable (no answer)
then local authentication is done and you will receive the following message:
No reply from RADIUS server "10.10.50.40(1812)"All RADIUS servers are
unreachable.
Please note that there is no Administrative RADIUS accounting for ES460/470 Series and ERS
2500, 4500, 5500.
RADIUS accounting is only available for 802.1x (EAP) users.
2.5 RADIUS Server & Client Log Files
In this section, we will demonstrate RADIUS server and client logging on the switch. We will demonstrate
a client logging onto a switch, issuing several commands and checking if they are allowed or not based
on authentication rights.
2.5.1 ES 460/470 Series and ERS 2500, 4500, 5500 – Read-Only user
Connect to the device via telnet using read-only user (bsro).
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
18
November 2010
avaya.com
Telnet to Switch with read-only user (bsro) type some commands
4548GT-PWR# show clock
Current SNTP time : 2008-02-21 15:52:36 GMT+01:00
Daylight saving time is DISABLED
Time zone is set to 'METD', offset from UTC is 01:00
4548GT-PWR# conf t
^
% Invalid input detected at '^' marker.
4548GT-PWR# exit
Read-only user in this example does not have access to switch configuration.
Log file on RADIUS server - /var/log/radius/radius.log
Thu Feb 21 15:52:09 2008 : Auth: Login OK: [bsro] (from client 4548GT-PWR
port 0)
Log file on RADIUS server - /var/log/radius/radacct/10.10.44.5/auth-detail-20080221
Optional file, need to configure /etc/raddb/radiusd.conf
Thu Feb 21 15:52:09 2008
NAS-IP-Address = 10.10.44.5
Service-Type = Administrative-User
User-Name = "bsro"
Client-IP-Address = 10.10.44.5
Timestamp = 1203605529
Please note that the client-IP-Address is equal to NAS-IP-Address which is not correct. The
client-IP-Address is the station where telnet has been issued, which is 10.10.50.10. The reason
is the switch does not provide a Client-IP-address field (see sniffer trace). Application artificially
copy field.
Log file on RADIUS client
4548GT-PWR# show log
I 2008-02-21 15:52:21 GMT+01:00 115 #1 Session opened(radius auth)
from IP add: 10.10.50.10, access mode: read-only
I 2008-02-21 15:53:50 GMT+01:00 116 #1 Session closed (user logout),
IP address: 10.10.50.10, access mode: read-only
I 2008-02-21 15:53:50 GMT+01:00 117 #1 Connection closed (user
logout),
IP address: 10.10.50.10
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

19
November 2010
avaya.com
Please note that the log file only displays the user access level (read-only). The log file does not
contain any session statistics.
Telnet to Switch with read-write user (bsrw) type some commands
4548GT-PWR# en
4548GT-PWR# conf t
Enter configuration commands, one per line. End with CNTL/Z.
4548GT-PWR(config)# interface fastEthernet all
4548GT-PWR(config-if)# exit
4548GT-PWR(config)# exit
4548GT-PWR# exit
Read-Write user in this example does have access to switch configuration.
Log file on RADIUS server - /var/log/radius/radius.log
Thu Feb 21 16:54:24 2008 : Auth: Login OK: [bsrw] (from client 4548GT-PWR
port 0)
Log file on RADIUS server - /var/log/radius/radacct/10.10.44.5/auth-detail-20080221
Optional file, need to configure /etc/raddb/radiusd.conf
Thu Feb 21 16:54:24 2008
NAS-IP-Address = 10.10.44.5
Service-Type = Administrative-User
User-Name = "bsrw"
Client-IP-Address = 10.10.44.5
Timestamp = 1203609264
Please note that the client-IP-Address is equal to NAS-IP-Address which is not correct. The
client-IP-Address is the station where telnet has been issued, which is 10.10.50.10. The reason
is the switch does not provide a Client-IP-address field (see sniffer trace). Application artificially
copy field.
Log file on RADIUS client
I 2008-02-21 16:54:25 GMT+01:00 124 #1 Session opened(radius auth)
from IP add: 10.10.50.10, access mode: read-write
I 2008-02-21 16:55:17 GMT+01:00 125 #1 Session closed (user logout),
IP address: 10.10.50.10, access mode: read-write
I 2008-02-21 16:55:17 GMT+01:00 126 #1 Connection closed (user
logout), IP address: 10.10.50.10
2.5.2 ES 460/470 Series and ERS 2500, 4500, 5500 – Read-Write User
Connect to the device with telnet using read-only user (bsrw).
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
20
November 2010
avaya.com
Please note that the log file only displays the user access level (read-only). The log file does not
contain any session statistics.
Log file on RADIUS server - /var/log/radius/radius.log
Thu Feb 21 17:17:22 2008 : Auth: Login OK: [eap] (from client 4548GT-PWR port
1 cli 00-12-3F-1A-1B-68)
Log file on RADIUS server - /var/log/radius/radacct/10.10.44.5/auth-detail-20080221
Optional file, need to configure /etc/raddb/radiusd.conf
Thu Feb 21 17:17:22 2008
NAS-IP-Address = 10.10.44.5
NAS-Port-Type = Ethernet
Service-Type = Framed-User
Message-Authenticator = 0x88721799b12354d60b8336ab285dda67
NAS-Port = 1
Framed-MTU = 1490
User-Name = "eap"
Calling-Station-Id = "00-12-3F-1A-1B-68"
EAP-Message = 0x02ff000801656170
Client-IP-Address = 10.10.44.5
Timestamp = 1203610642
Thu Feb 21 17:17:22 2008
NAS-IP-Address = 10.10.44.5
NAS-Port-Type = Ethernet
Service-Type = Framed-User
Message-Authenticator = 0xf59f53234959a19e91f76475e3d9ab6d
NAS-Port = 1
Framed-MTU = 1490
User-Name = "eap"
Calling-Station-Id = "00-12-3F-1A-1B-68"
State =
0x554445eb4da34e4372ab674424c945d712a4bd47826574a783596a949d917a931b1f5c81
EAP-Message = 0x0200001904108317b45b9526d49bd52c243c7b96bd1c656170
Client-IP-Address = 10.10.44.5
Timestamp = 1203610642
2.5.3 ERS 2500, 4500, 5500 – 802.1x (EAP) User
For this example, we will connect an 802.1x (EAP) supplicant to the switch, authenticate the EAP
supplicant, generate some traffic, and then disconnect.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
21
November 2010
avaya.com
Log file on RADIUS server - /var/log/radius/radacct/10.10.44.5/detail-20080221
Thu Feb 21 17:17:23 2008
NAS-IP-Address = 10.10.44.5
NAS-Port-Type = Ethernet
NAS-Port = 1
User-Name = "eap"
Acct-Session-Id = "85000001"
Acct-Status-Type = Start
Client-IP-Address = 10.10.44.5
Acct-Unique-Session-Id = "3e7408b4904a799d"
Timestamp = 1203610643
Thu Feb 21 17:18:08 2008
NAS-IP-Address = 10.10.44.5
NAS-Port-Type = Ethernet
NAS-Port = 1
User-Name = "eap"
Acct-Session-Id = "85000001"
Acct-Status-Type = Stop
Acct-Input-Octets = 11722
Acct-Output-Octets = 7387
Acct-Input-Packets = 100
Acct-Output-Packets = 78
Acct-Session-Time = 45
Acct-Terminate-Cause = Lost-Carrier
Client-IP-Address = 10.10.44.5
Acct-Unique-Session-Id = "3e7408b4904a799d"
Timestamp = 1203610688
802.1x (EAP) user has accounting start & stop records in accounting log file
Log file on RADIUS client
I 2008-02-21 17:16:41 GMT+01:00 137 EAP Mac AuthFail - unitPort 0x1
macHi 123f1a macLo 1b68
Please note that only 802.1x (EAP) login authentication failure are logged, not successful
authentication.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide

22
November 2010
avaya.com
Telnet to Switch with read-only user (ro) type some commands
8600A:6> show date
local time: THU FEB 21 18:08:44 2008 METDST
hardware time: THU FEB 21 17:08:44 2008 UTC
8600A:6> config ?
Sub-Context: cli log
Current Context:
Info
8600A:6> exit
Read-only user in this example does not have access to switch configuration.
Log file on RADIUS server - /var/log/radius/radius.log
Thu Feb 21 18:08:07 2008 : Auth: Login OK: [ro] (from client 8600 port 1)
Log file on RADIUS server - /var/log/radius/radacct/10.10.50.1/auth-detail-20080221
Optional file, need to configure /etc/raddb/radiusd.conf
Thu Feb 21 18:08:07 2008
User-Name = "ro"
NAS-IP-Address = 10.10.50.1
NAS-Port = 1
Client-IP-Address = 10.10.50.1
Timestamp = 1203613687
Please note that the client-IP-Address is equal to NAS-IP-Address which is not correct. The
client-IP-Address is the station where telnet has been issued, which is 10.10.50.10. The reason
is the switch does not provide a Client-IP-address field (see sniffer trace). Application artificially
copy field.
Log file on RADIUS server - /var/log/radius/radacct/10.10.50.1/detail-20080221
Thu Feb 21 18:08:07 2008
Acct-Status-Type = Start
NAS-IP-Address = 10.10.50.1
Acct-Session-Id = "1ef400000012"
User-Name = "ro"
Client-IP-Address = 10.10.50.1
Acct-Unique-Session-Id = "fae1055b429ca034"
Timestamp = 1203613687
2.5.4 ERS 1600, 8300 and 8600 – Read-Only User
For this example, we will connect to the switch using telnet via a read-only (ro) user.
Authentication, Authorization and Accounting (AAA) for ERS and ES
Technical Configuration Guide
 Loading...
Loading...