D-Link DWC-1000 User Manual

User Manual
Wireless Controller
D-Link Corporation
Copyright © 2011.
http://www.dlink.com

Wireless Controller |
User Manual |
|
|
User Manual
DWC-1000
Wireless Controller
Version 1.3
Copyright © 2011
Copyright Notice
This publication, including all photographs, illustrations and software, is protected under international copyright laws, with all rights reserved. Neither this manual, nor any of the material contained herein, may be reproduced without written consent of the author.
Disclaimer
The information in this document is subject to change without notice. The manufacturer makes no representations or warranties with respect to the contents hereof and specifically dis claim any implied warranties of merchantability or fitness for any particular purpose. The manufacturer reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of the manufacturer to noti fy any person of such revision or changes.
Limitations of Liability
UNDER NO CIRCUMSTANCES SHALL D -LINK OR ITS SUPPLIERS BE LIABLE FOR DAMAGES OF ANY CHARACTER (E.G. DAMAGES FOR LOSS OF PROFIT, SOFTWARE RESTORATION, WORK STOPPAGE, LOSS OF SAVED DATA OR AN Y OTHER COMMERCIAL DAMAGES OR LOSSES) RESULTING FROM THE APPLICATION OR IMPROPER USE OF THE D-LINK PRODUCT OR FAILURE OF THE PRODUCT, EVEN IF D-LINK IS INFORMED OF THE POSSIBILITY OF SUCH DAMAGES. FURTHERMORE, D - LINK WILL NOT BE LIABLE FOR THIRD -PARTY CLAIMS AGAINST CUSTOMER FOR LOSSES OR DAMAGES. D-LINK WILL IN NO EVENT BE LIABLE FOR ANY DAMAGES IN EXCESS OF THE AMOUNT D-LINK RECEIVED FROM THE END-USER FOR THE PRODUCT.
1

Wireless Controller User Manual
Table of Contents
Chapter |
1. |
Introduction ............................................................................................................................. |
9 |
|
|
|
1.1 |
About this User Manual............................................................................................ |
9 |
|
|
1.2 |
Typographical Conventions ................................................................................... |
10 |
Chapter |
2. |
Configuring Your Network: ................................................................................................. |
11 |
|
|
|
2.1 |
LAN Configuration................................................................................................... |
11 |
|
|
2.1.1 |
LAN Configuration in an IPv6 Network ................................................................ |
14 |
|
|
2.1.2 |
Configuring IPv6 Router Advertisements ............................................................ |
17 |
|
|
2.2 |
VLAN Configuration ................................................................................................ |
19 |
|
|
2.2.1 |
Associating VLANs to ports ................................................................................... |
20 |
|
|
2.3 |
Configurable Port: DMZ Setup.............................................................................. |
22 |
|
|
2.4 |
Universal Plug and Play (UPnP)........................................................................... |
23 |
|
|
2.5 |
Captive Portal .......................................................................................................... |
25 |
|
|
2.6 |
WLAN global configuration .................................................................................... |
25 |
|
|
2.6.1 |
Wireless Discovery configuration ......................................................................... |
28 |
|
|
2.6.2 |
AP Profile Global Configuration ............................................................................ |
31 |
Chapter |
3. |
Connecting to the Internet: WAN Setup ........................................................................... |
35 |
|
|
|
3.1 |
Internet Setup Wizard............................................................................................. |
35 |
|
|
3.2 |
WAN Configuration ................................................................................................. |
36 |
|
|
3.2.1 |
WAN Port IP address ............................................................................................. |
37 |
|
|
3.2.2 |
WAN DNS Servers ................................................................................................. |
37 |
|
|
3.2.3 |
DHCP WAN ............................................................................................................. |
37 |
|
|
3.2.4 |
PPPoE ...................................................................................................................... |
38 |
|
|
3.2.5 |
Russia L2TP and PPTP WAN............................................................................... |
41 |
|
|
3.2.6 |
WAN Configuration in an IPv6 Network............................................................... |
42 |
|
|
3.2.7 |
Checking WAN Status............................................................................................ |
44 |
|
|
3.3 |
Features with Multiple WAN Links........................................................................ |
45 |
|
|
3.3.1 |
Auto Failover............................................................................................................ |
46 |
|
|
3.3.2 |
Load Balancing........................................................................................................ |
46 |
|
|
3.3.3 |
Protocol Bindings .................................................................................................... |
48 |
|
|
3.4 |
Routing Configuration............................................................................................. |
49 |
|
|
3.4.1 |
Routing Mode .......................................................................................................... |
49 |
|
|
3.4.2 |
Dynamic Routing (RIP) .......................................................................................... |
52 |
|
|
3.4.3 |
Static Routing .......................................................................................................... |
53 |
|
|
3.5 |
WAN Port Settings .................................................................................................. |
54 |
Chapter |
4. |
Monitoring Status and Statistics ........................................................................................ |
56 |
|
|
|
4.1 |
System Overview .................................................................................................... |
56 |
|
|
4.1.1 |
Device Status .......................................................................................................... |
56 |
|
|
4.1.2 |
Resource Utilization................................................................................................ |
58 |
|
|
4.2 |
Traffic Statistics ....................................................................................................... |
60 |
|
|
4.2.1 |
Wired Port Statistics ............................................................................................... |
60 |
|
|
4.3 |
Active Connections ................................................................................................. |
61 |
|
|
4.3.1 |
Sessions through the controller ............................................................................ |
61 |
|
|
4.3.2 |
LAN Clients .............................................................................................................. |
63 |
|
|
4.3.3 |
Active VPN Tunnels................................................................................................ |
63 |
2

Wireless Controller |
User Manual |
||
|
|
|
|
|
4.4 |
Access Point status ................................................................................................ |
64 |
|
4.5 |
Global Status ........................................................................................................... |
69 |
|
4.6 |
Wireless Client Status ............................................................................................ |
75 |
|
4.7 |
AP Management ..................................................................................................... |
83 |
|
4.8 |
Associated Client Status/Statistics ....................................................................... |
95 |
Chapter 5. |
Securing the Private Network ............................................................................................ |
97 |
|
|
5.1 |
Firewall Rules .......................................................................................................... |
97 |
|
5.2 |
Defining Rule Schedules ....................................................................................... |
98 |
|
5.3 |
Configuring Firewall Rules..................................................................................... |
99 |
|
5.3.1 |
Firewall Rule Configuration Examples............................................................... |
103 |
|
5.4 |
Security on Custom Services .............................................................................. |
107 |
|
5.5 |
ALG support........................................................................................................... |
107 |
|
5.6 |
VPN Passthrough for Firewall ............................................................................. |
108 |
|
5.7 |
Application Rules .................................................................................................. |
109 |
|
5.8 |
Web Content Filtering........................................................................................... |
110 |
|
5.8.1 |
Content Filtering.................................................................................................... |
110 |
|
5.8.2 |
Approved URLs ..................................................................................................... |
111 |
|
5.8.3 |
Blocked Keywords ................................................................................................ |
112 |
|
5.8.4 |
Export Web Filter .................................................................................................. |
113 |
|
5.9 |
IP/MAC Binding ..................................................................................................... |
114 |
|
5.10 |
Protecting from Internet Attacks ......................................................................... |
115 |
Chapter 6. |
IPsec / PPTP / L2TP VPN ................................................................................................ |
117 |
|
|
6.1 |
VPN Wizard ........................................................................................................... |
119 |
|
6.2 |
Configuring IPsec Policies ................................................................................... |
121 |
|
6.2.1 |
Extended Authentication (XAUTH)..................................................................... |
124 |
|
6.2.2 |
Internet over IPSec tunnel ................................................................................... |
124 |
|
6.3 |
Configuring VPN clients ....................................................................................... |
125 |
|
6.4 |
PPTP / L2TP Tunnels........................................................................................... |
125 |
|
6.4.1 |
PPTP Tunnel Support .......................................................................................... |
125 |
|
6.4.2 |
L2TP Tunnel Support ........................................................................................... |
127 |
|
6.4.3 |
OpenVPN Support ................................................................................................ |
128 |
Chapter 7. |
SSL VPN ............................................................................................................................. |
131 |
|
|
7.1 |
Groups and Users................................................................................................. |
133 |
|
7.1.1 |
Users and Passwords .......................................................................................... |
139 |
|
7.2 |
Using SSL VPN Policies ...................................................................................... |
140 |
|
7.2.1 |
Using Network Resources ................................................................................... |
143 |
|
7.3 |
Application Port Forwarding ................................................................................ |
144 |
|
7.4 |
SSL VPN Client Configuration ............................................................................ |
146 |
|
7.4.1 |
Creating Portal Layouts ....................................................................................... |
148 |
Chapter 8. |
Advanced Configuration Tools......................................................................................... |
151 |
|
|
8.1 |
USB Device Setup ................................................................................................ |
151 |
|
8.2 |
Authentication Certificates ................................................................................... |
152 |
|
8.3 |
WIDS Security ....................................................................................................... |
154 |
3

Wireless Controller |
User Manual |
|
8.3.1 |
WIDS AP configration ............................................................................................ |
154 |
8.3.2 |
WIDS Client Configuration..................................................................................... |
157 |
Chapter 9. Administration & Management......................................................................................... |
161 |
|
9.1 |
Remote Management........................................................................................... |
161 |
9.2 |
CLI Access ............................................................................................................. |
161 |
9.3 |
SNMP Configuration............................................................................................. |
162 |
9.4 |
Configuring Time Zone and NTP........................................................................ |
163 |
9.5 |
Log Configuration.................................................................................................. |
164 |
9.5.1 |
Defining What to Log ............................................................................................ |
165 |
9.5.2 |
Sending Logs to E-mail or Syslog ...................................................................... |
168 |
9.5.3 |
Event Log Viewer in GUI ..................................................................................... |
171 |
9.6 |
Backing up and Restoring Configuration Settings ........................................... |
172 |
9.7 |
Upgrading wirelesss controller Firmware .......................................................... |
173 |
9.8 |
Dynamic DNS Setup............................................................................................. |
174 |
9.9 |
Using Diagnostic Tools ........................................................................................ |
175 |
9.9.1 |
Ping ......................................................................................................................... |
176 |
9.9.2 |
Trace Route ........................................................................................................... |
176 |
9.9.3 |
DNS Lookup .......................................................................................................... |
176 |
9.9.4 |
Router Options ...................................................................................................... |
177 |
9.10 |
License ................................................................................................................... |
177 |
Appendix A. Glossary .............................................................................................................................. |
178 |
|
Appendix B. Factory Default Settings ................................................................................................... |
180 |
|
4

Wireless Controller |
User Manual |
List of Figures |
|
Figure 1: Setup page for LAN TCP/IP settings ...................................................................................... |
13 |
Figure 2: IPv6 LAN and DHCPv6 configuration ..................................................................................... |
15 |
Figure 3: Configuring the Router Advertisement Daemon ................................................................... |
18 |
Figure 4: IPv6 Advertisement Prefix settings ......................................................................................... |
19 |
Figure 5: Adding VLAN memberships to the LAN ................................................................................. |
20 |
Figure 6: Port VLAN list ............................................................................................................................. |
21 |
Figure 7: Configuring VLAN membership for a port .............................................................................. |
22 |
Figure 8: DMZ configuration ..................................................................................................................... |
23 |
Figure 9: UPnP Configuration................................................................................................................... |
24 |
Figure 10: Active Runtime sessions ........................................................................................................ |
25 |
Figure 11: WLAN global configuration..................................................................................................... |
26 |
Figure 12: Configuring the Wireless Discovery ...................................................................................... |
29 |
Figure 13: Wireless Discovery status ...................................................................................................... |
30 |
Figure 14: AP Profile Global Configuration ............................................................................................. |
31 |
Figure 15: AP Profile List........................................................................................................................... |
33 |
Figure 16: Internet Connection Setup Wizard ........................................................................................ |
35 |
Figure 17: Manual Option1 configuration ................................................................................................ |
38 |
Figure 18: PPPoE configuration for standard ISPs ............................................................................... |
39 |
Figure 19: Option1 configuration for Japanese Multiple PPPoE (part 1) ........................................... |
40 |
Figure 20: Option1 configuration for Multiple PPPoE (part 2).............................................................. |
41 |
Figure 21: Russia L2TP ISP configuration.............................................................................................. |
42 |
Figure 22: IPv6 WAN Setup page ............................................................................................................ |
43 |
Figure 23: Connection Status information of Option1 ........................................................................... |
45 |
Figure 24: Load Balancing is available when multiple WAN ports are configured and Protocol |
|
Bindings have been defined ................................................................................................... |
48 |
Figure 25: Protocol binding setup to associate a service and/or LAN source to a WAN and/or |
|
destination network .................................................................................................................. |
49 |
Figure 26: Routing Mode is used to configure traffic routing between WAN and LAN, as well as |
|
Dynamic routing (RIP) ............................................................................................................. |
51 |
Figure 27: Static route configuration fields ............................................................................................. |
54 |
Figure 28: Physical WAN port settings .................................................................................................... |
55 |
Figure 29: Device Status display.............................................................................................................. |
57 |
Figure 30: Device Status display (continued) ......................................................................................... |
58 |
Figure 31: Resource Utilization statistics ................................................................................................ |
59 |
Figure 32: Resource Utilization data (continued)................................................................................... |
59 |
5

Wireless Controller |
User Manual |
Figure 33: Physical port statistics............................................................................................................. |
61 |
Figure 34: List of current Active Firewall Sessions ................................................................................ |
62 |
Figure 35: List of LAN hosts...................................................................................................................... |
63 |
Figure 36: List of current Active VPN Sessions ..................................................................................... |
64 |
Figure 37: AP status................................................................................................................................... |
65 |
Figure 38: Managed AP status ................................................................................................................. |
67 |
Figure 39: AP RF Scan Status.................................................................................................................. |
69 |
Figure 40: Peer Controller Status............................................................................................................. |
70 |
Figure 41: Peer Controller Configuration Status .................................................................................... |
71 |
Figure 42: Peer Controller Managed AP Status..................................................................................... |
72 |
Figure 43: Configuration Receive Status ................................................................................................ |
74 |
Figure 44: Associated Client Status......................................................................................................... |
75 |
Figure 45: Associated Client SSID Status .............................................................................................. |
76 |
Figure 46: Associated Client VAP Status................................................................................................ |
77 |
Figure 47: Controller Associated Client Status ...................................................................................... |
78 |
Figure 48: Detected Client Status ............................................................................................................ |
79 |
Figure 49: Pre-Auth History....................................................................................................................... |
81 |
Figure 50: Detected Client Roam History ............................................................................................... |
82 |
Figure 51: Valid Access Point Configuration .......................................................................................... |
83 |
Figure 52: Add a Valid Access Point ....................................................................................................... |
84 |
Figure 53: RF configuration....................................................................................................................... |
87 |
Figure 54: Channel Plan History .............................................................................................................. |
89 |
Figure 55: Manual Channel Plan.............................................................................................................. |
90 |
Figure 56: Manual Power Adjustment Plan ............................................................................................ |
92 |
Figure 57: Access Point Software Download ......................................................................................... |
93 |
Figure 58: Local OUI Database ................................................................................................................ |
94 |
Figure 59: Managed AP Statistics ............................................................................................... |
95 |
Figure 60: WLAN Associated Clients ...................................................................................................... |
96 |
Figure 61: List of Available Firewall Rules .............................................................................................. |
98 |
Figure 62: List of Available Schedules to bind to a firewall rule .......................................................... |
99 |
Figure 63: Example where an outbound SNAT rule is used to map an external IP address |
|
(209.156.200.225) to a private DMZ IP address (10.30.30.30) ...................................... |
102 |
Figure 64: The firewall rule configuration page allows you to define the To/From zone, service, |
|
action, schedules, and specify source/destination IP addresses as needed. ............... |
103 |
Figure 65: Schedule configuration for the above example. ................................................................ |
106 |
Figure 66: List of user defined services. ............................................................................................... |
107 |
6

Wireless Controller |
User Manual |
|
Figure 67: Available ALG support on the controller............................................................................. |
|
108 |
Figure 68: Passthrough options for VPN tunnels................................................................................. |
|
109 |
Figure 69: List of Available Application Rules showing 4 unique rules ............................................ |
|
110 |
Figure 70: Content Filtering used to block access to proxy servers and prevent ActiveX controls |
||
from being downloaded ......................................................................................................... |
|
111 |
Figure 71: Two trusted domains added to the Approved URLs List ................................................. |
|
112 |
Figure 72: One keyword added to the block list ................................................................................... |
|
113 |
Figure 73: Export Approved URL list ..................................................................................................... |
|
114 |
Figure 74: The following example binds a LAN host’s MAC Address to an IP address serv |
||
DWC-1000. If there is an IP/MAC Binding violation, the violating packet will be dropped |
||
and logs will be captured ...................................................................................................... |
|
115 |
Figure 75: Protecting the controller and LAN from internet attacks .................................................. |
|
116 |
Figure 76: Example of Gateway-to-Gateway IPsec VPN tunnel using two DWC controllers |
|
|
connected to the Internet ...................................................................................................... |
|
117 |
Figure 77: Example of three IPsec client connections to the internal network through the DWC |
|
|
IPsec gateway ........................................................................................................................ |
|
118 |
Figure 78: VPN Wizard launch screen .................................................................................................. |
|
119 |
Figure 79: IPsec policy configuration..................................................................................................... |
|
122 |
Figure 80: IPsec policy configuration continued (Auto policy via IKE).............................................. |
|
123 |
Figure 81: IPsec policy configuration continued (Auto / Manual Phase 2) ...................................... |
|
124 |
Figure 82: PPTP tunnel configuration –PPTP Client.......................................................................... |
|
126 |
Figure 83: PPTP VPN connection status .............................................................................................. |
|
126 |
Figure 84: PPTP tunnel configuration –PPTP Server ........................................................................ |
|
127 |
Figure 85: L2TP tunnel configuration –L2TP Server.......................................................................... |
|
128 |
Figure 86: OpenVPN configuration ........................................................................................................ |
|
130 |
Figure 87: Example of clientless SSL VPN connections to the DWC-1000..................................... |
|
132 |
Figure 88: List of groups .......................................................................................................................... |
|
133 |
Figure 89: User group configuration ...................................................................................................... |
|
134 |
Figure 90: SSLVPN Settings................................................................................................................... |
|
135 |
Figure 91: Group login policies options ................................................................................................. |
|
136 |
Figure 92: Browser policies options ....................................................................................................... |
|
137 |
Figure 93: IP policies options.................................................................................................................. |
|
138 |
Figure 94: Available Users with login status and associated Group ................................................. |
|
139 |
Figure 95: User configuration options.................................................................................................... |
|
140 |
Figure 96: List of SSL VPN polices (Global filter) ................................................................................ |
|
141 |
Figure 97: SSL VPN policy configuration .............................................................................................. |
|
142 |
Figure 98: List of configured resources, which are available to assign to SSL VPN policies ....... |
144 |
|
7

Wireless Controller |
User Manual |
Figure 99: List of Available Applications for SSL Port Forwarding.................................................... |
146 |
Figure 100: SSL VPN client adapter and access configuration ......................................................... |
147 |
Figure 101: Configured client routes only apply in split tunnel mode ............................................... |
148 |
Figure 102: SSL VPN Portal configuration ........................................................................................... |
150 |
Figure 103: USB Device Detection ........................................................................................................ |
152 |
Figure 104: Certificate summary for IPsec and HTTPS management ............................................. |
154 |
Figure 105: W IDS AP Configuration ......................................................................................... |
157 |
Figure 106: WIDS Client Configuration ................................................................................................. |
160 |
Figure 107: Remote Management ......................................................................................................... |
161 |
Figure 108: SNMP Users, Traps, and Access Control........................................................................ |
162 |
Figure 109: SNMP system information for this controller ................................................................... |
163 |
Figure 110: Date, Time, and NTP server setup ................................................................................... |
164 |
Figure 111: Facility settings for Logging ............................................................................................... |
166 |
Figure 112: Log configuration options for traffic through controller................................................... |
168 |
Figure 113: E-mail configuration as a Remote Logging option.......................................................... |
170 |
Figure 114: Syslog server configuration for Remote Logging (continued)....................................... |
171 |
Figure 115: VPN logs displayed in GUI event viewer ......................................................................... |
172 |
Figure 116: Restoring configuration from a saved file will result in the current configuration being |
|
overwritten and a reboot ....................................................................................................... |
173 |
Figure 117: Firmware version information and upgrade option ......................................................... |
174 |
Figure 118: Dynamic DNS configuration............................................................................................... |
175 |
Figure 119: Controller diagnostics tools available in the GUI ............................................................ |
176 |
Figure 120: Install License ...................................................................................................................... |
177 |
. Figure 121: After activating the License.............................................................................................. |
177 |
8

Wireless Controller |
User Manual |
|
|
Chapter 1. Introduction
D-Link Wireless Controller (DWC), DWC-1000, is a full-featured wireless LAN controller designing for small network environment. The centralized control function contains various access point management functions, such as fast -roaming, inter-subnet roaming, automatic channel and power adjustment, self -healing etc. The advanced wireless security function, including rouge AP detection, captive portal, wireless intrusion detection system (WIDS), offers a strong wireless network protection avoiding attacks from hackers. Optimal network security is provided via features such as virtual private network (VPN) tunnels, IP Security (IPsec), Point -to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), and Secure Sockets Layer (SSL). Empower your road warriors with clientless remote access anywhere and anytime using SSL VPN tunnels.
Comprehensive Management Capabilities
The DWC include dual-WAN Gigabit Ethernet which provides policy -based service management ensuring maximum productivity for your business operations. The failover feature maintains data traffic without disconnecting when a landline connection is lost. The Outbound Load Balancing feature adjusts outgoing traffic across two WAN interfaces and optimizes the system performance resulting in high availabil ity. The second WAN port can be configured as a DMZ port allowing you to isolate servers from your LAN.
Robust VPN features
A fully featured virtual private network (VPN) provides your mobile workers and branch offices with a secure link to your network. DWC is capable of simultaneously managing 20 Secure Sockets Layer (SSL) VPN tunnels respectively, empowering your mobile users by providing remote access to a central corporate database. Site -to-site VPN tunnels use IP Security (IPsec) Protocol, Point-to-Point Tunneling Protocol (PPTP), or Layer 2 Tunneling Protocol (L2TP) to facilitate branch office connectivity through encrypted virtual links. The DWC support 75 simultaneous IPSec VPN tunnels respectively.
1.1About this User Manual
This document is a high level manual to allow new D-Link Wireless Controller users to configure connectivity, WLAN configuration, setup VPN tunnels, establish firewall rules and AP management and perform general administrative tasks. Typical deployment and use case scenarios are described in each section. For more detailed setup instructions and explanations of each configuration parameter, refer to the online help that can be accessed from each page in the controller GUI.
9

Wireless Controller |
User Manual |
|
|
1.2 Typographical Conventions
The following is a list of the various terms, followed by an example of how that term is represented in this document:
Product Name – D-Link Wireless Controller. o Model numbers DWC-1000
GUI Menu Path/GUI Navigation – Monitoring > Controller Status
Important note –
10

Chapter 2. Configuring Your Network:
It is assumed that the user has a machine for management connected to the LAN to the controller. The LAN connection may be through the wired Ethernet ports available on the controller, or once the initial setup is complete, the DWC may also be managed through its wireless interface as it is bridged with the LAN. Access the controller‘s graphical user interface (GUI) for management by using any web browser, such as Microsoft Internet Explorer or Mozilla Firefox:
Go to http://192.168.10.1 (default IP address) to display the controller‘s management login screen.
Default login credentials for the management GUI:
Username: admin
Password: admin
If the controller‘s LAN IP address was changed, use that IP address in the navigation bar of the browser to access the controller‘s management UI.
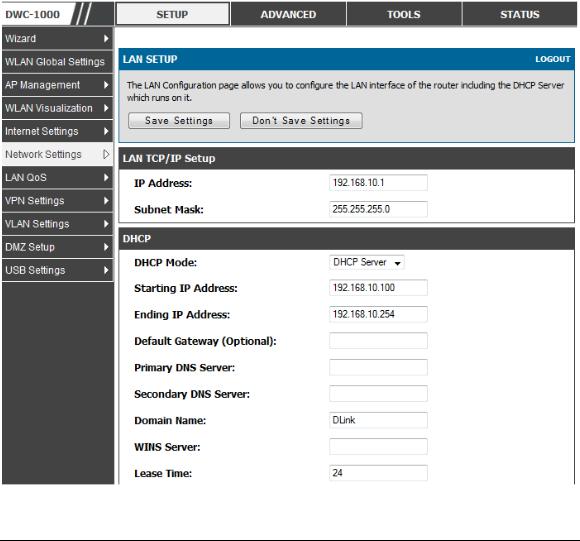
2.1 LAN Configuration
Setup > Network Settings > LAN Setup Configuration
By default, the controller functions as a Dynamic Host Configuration Protocol (DHCP) server to the hosts on the WLAN or LAN network. With DHCP, PCs and other LAN devices can be assigned IP addresses as well as addresses for DNS servers, Windows Internet Name Service (WINS) servers, and the default gatewa y. With the DHCP server enabled the controller‘s IP address serves as the gateway address for LAN and WLAN clients. The PCs in the LAN are assigned IP addresses from a pool of addresses specified in this procedure. Each pool address is tested before it is assigned to avoid duplicate addresses on the LAN.
For most applications the default DHCP and TCP/IP settings are satisfactory. If you want another PC on your network to be the DHCP server or if you are manually configuring the network settings of all of yo ur PCs, set the DHCP mode to ‗none‘. DHCP relay can be used to forward DHCP lease information from another LAN device that is the network‘s DHCP server; this is particularly useful for wireless clients.
Instead of using a DNS server, you can use a Windows Internet Naming Service (WINS) server. A WINS server is the equivalent of a DNS server but uses the NetBIOS protocol to resolve hostnames. The controller includes the WINS server IP address in the DHCP configuration when acknowledging a DHCP request from a DHCP client.
You can also enable DNS proxy for the LAN. When this is enabled the controller then as a proxy for all DNS requests and communicates with the ISP‘s DNS servers. When disabled all DHCP clients receive the DNS IP addresses of the ISP.

Wireless Controller |
User Manual |
|
|
To configure LAN Connectivity, please follow the steps below:
1.In the LAN Setup page, enter the following information for your controller:
IP address: (factory default: 192.168.10.1).
If you change the IP address and click Save Settings, the GUI will not respond. Open a new connection to the new IP address and log in again. Be sure the LAN host (the machine used to manage the controller) has obtained IP address from newly assigned pool (or has a static IP address in the controller‘s LAN subnet) before accessing the controller via changed IP address.
Subnet mask: (factory default: 255.255.255.0).
2.In the DHCP section, select the DHCP mode:
None: the controller‘s DHCP server is disabled for the LAN
DHCP Server. With this option the controller assigns an IP address within the specified range plus additional specified information to any LAN device that requests DHCP served addresses.
DHCP Relay: With this option enabled, DHCP clients on the LAN can receive IP address leases and corresponding information from a DHCP server on a different subnet. Specify the Relay Gateway, and when LAN clients make a DHCP request it will be passed along to the server accessible via the Relay Gateway IP address.
If DHCP is being enabled, enter the following DHCP server parameters:
Starting and Ending IP Addresses: Enter the first and last continuous addresses in the IP address pool. Any new DHCP client joining the LAN is assigned an IP address in this range. The default starting address is 192.168.10.100. The default ending address is 192.168.10.254. These addresses should be in the same IP address subnet as the controller‘s LAN
IP address. You may wish to save part of the subnet range for devices with statically assigned IP addresses in the LAN .
Default Gateway (Optional): Enter the IP address of the controller which you want to make it as a default other than DWC -1000
Primary and Secondary DNS servers : If configured domain name system (DNS) servers are available on the LAN enter their IP addresses here.
12
Wireless Controller |
User Manual |
|
|
Domain Name: Enter domain name
WINS Server (optional): Enter the IP address for the WINS server or, if present in your network, the Windows NetBios server.
Lease Time: Enter the time, in hours, for which IP addresses are leased to clients.
Enable DNS Proxy: To enable the controller to act as a proxy for all DNS requests and communicate with the ISP‘s DNS servers, click the checkbox.
Relay Gateway: Enter the gateway address. This is the only configuration parameter required in this section when DHCP Relay is selected as its DHCP mode
3.Click Save Settings to apply all changes.
Figure 1: Setup page for LAN TCP/IP settings
13

Wireless Controller User Manual
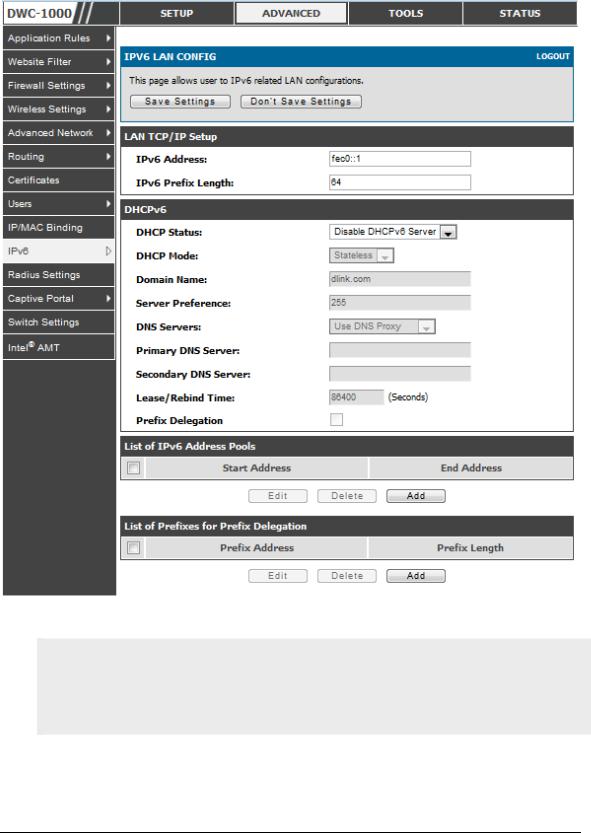
2.1.1 LAN Configuration in an IPv6 Network
Advanced > IPv6 > IPv6 LAN > IPv6 LAN Config
In IPv6 mode, the LAN DHCP server is enabled by default (similar to IP v4 mode). The DHCPv6 server will serve IPv6 addresses from configured address pools with the IPv6 Prefix Length assigned to the LAN.
IPv4 / IPv6 mode must be enabled in the Advanced > IPv6 > Routing mode to enable IPv6 configuration options.
LAN Settings
The default IPv6 LAN address for the router is fec0::1. You can change this 128 bit IPv6 address based on your network requirements. The other field that defines the LAN settings for the router is the prefix length. The IPv6 network (subnet) is identified by the initial bits of the address called the prefix. By default this is 64 bits long. All hosts in the network have common initial bits for their IPv6 address; the number of common initial bits in the network‘s addresses is set by the prefix length field.
14
Wireless Controller |
User Manual |
|
|
Figure 2: IPv6 LAN and DHCPv6 configuration
If you change the IP address and click Save Settings, the GUI will not respond. Open a new connection to the new IP address and log in again. Be sure the LAN host (the machine used to manage the router) has obtained IP address from newly assigned pool (or has a static IP address in the router‘s LAN subnet) before accessing the router via changed IP address.
As with an IPv4 LAN network, the router has a DHCPv6 server. If enabled, the router assigns an IP address within the specified range plus additional specified information to any LAN PC that requests DHCP served addresses.
15

Wireless Controller |
User Manual |
|
|
The following settings are used to configure the DHCPv6 server:
DHCP Mode: The IPv6 DHCP server is either state less or stateful. If stateless is selected an external IPv6 DHCP server is not required as the IPv6 LAN hosts are auto-configured by this controller. In this case the controller advertisement daemon (RADVD) must be configured on this device and ICMPv6 controller discovery messages are used by the host for auto -configuration. There are no managed addresses to serve the LAN nodes. If stateful is selected the IPv6 LAN host will rely on an external DHCPv6 server to provide required configuration settings
The domain name of the DHCPv6 server is an optional setting
Server Preference is used to indicate the preference level of this DHCP server. DHCP advertise messages with the highest server preference value to a LAN host are preferred over other DHCP server advertise messages . The default is 255.
The DNS server details can be manually entered here (primary/secondary options. An alternative is to allow the LAN DHCP client to receive the DNS server details from the ISP directly. By selecting Use DNS proxy, this router acts as a proxy for all DNS requests and communicates with the ISP‘s DNS servers (a WAN configuration parameter).
Primary and Secondary DNS servers: If there are configured domain name system (DNS) servers available on the LAN enter the IP addresses here.
Lease/Rebind time sets the duration of the DHCPv6 lease from this router to the LAN client.
IPv6 Address Pools
This feature allows you to define the IPv6 delegation prefix for a range of IP addresses to be served by the gateway‘s DHCPv6 server. Using a delegation p refix you can automate the process of informing other networking equipment on the LAN of DHCP information specific for the assigned prefix.
Prefix Delegation
The following settings are used to configure the Prefix Delegation:
Prefix Delegation: Select this option to enable prefix delegation in DHCPv6 server. This option can be selected only in Stateless Address Auto Configuration mode of DHCPv6 server.
Prefix Address: IPv6 prefix address in the DHCPv6 server prefix pool
Prefix Length: Length prefix address
16

Wireless Controller |
User Manual |
|
|
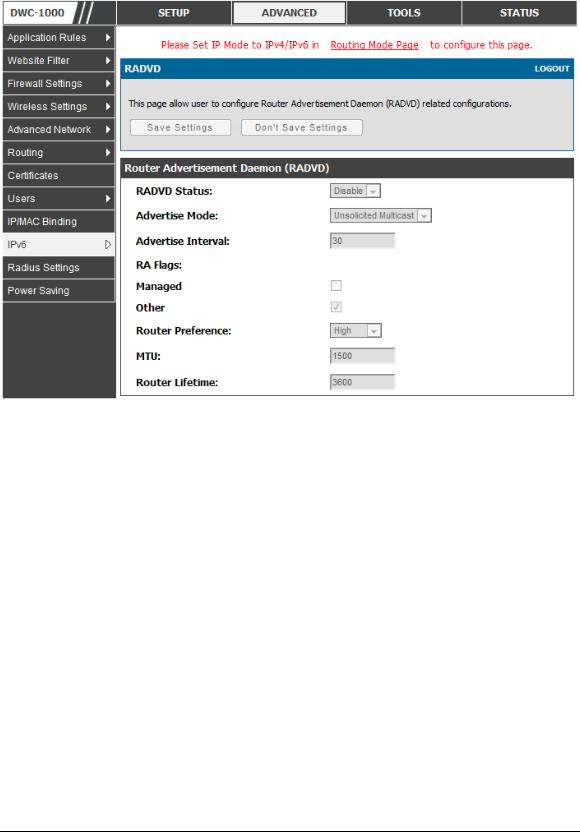
2.1.2 Configuring IPv6 Router Advertisements
Router Advertisements are analogous to IPv4 DHCP assignments for LAN clients, in that the router will assign an IP address and supporting network information to devices that are configured to accept such details. Rout er Advertisement is required in an IPv6 network is required for stateless auto configuration of the IPv6 LAN. By configuring the Router Advertisement Daemon on this router, the DWC-1000 will listen on the LAN for router solicitations and respond to these L AN hosts with router advisements.
RADVD
Advanced > IPv6 > IPv6 LAN > Router Advertisement
To support stateless IPv6 auto configuration on the LAN, set the RADVD status to Enable. The following settings are used to configure RADVD:
Advertise Mode: Select Unsolicited Multicast to send router advertisements
(RA‘s) to all interfaces in the multicast group. To restrict RA‘s to well known IPv6 addresses on the LAN, and thereby reduce overall network traffic, select Unicast only.
Advertise Interval: When advertisements are unsolicited multicast packets, this interval sets the maximum time between advertisements from the interface. The actual duration between advertisements is a random value between one third of this field and this field. The default is 30 seconds.
RA Flags: The router advertisements (RA‘s) can be sent with one or both of these flags. Chose Managed to use the administered /stateful protocol for address auto configuration. If the Other flag is selected the host uses administered/stateful protocol for non-address auto configuration.
Router Preference: this low/medium/high parameter determines the preference associated with the RADVD process of the router. This is useful if there are other RADVD enabled devices on the LAN as it helps avoid conflicts for IPv6 clients.
MTU: The router advertisement will set this maximum transmission unit (MTU) value for all nodes in the LAN that are autoconfigured by the router. The default is 1500.
Router Lifetime: This value is present in RA‘s and indicates the usefulnes s of this router as a default router for the interface. The default is 3600 seconds. Upon expiration of this value, a new RADVD exchange must take place between the host and this router.
17
Wireless Controller |
User Manual |
|
|
Figure 3: Configuring the Router Advertisem ent Daemon
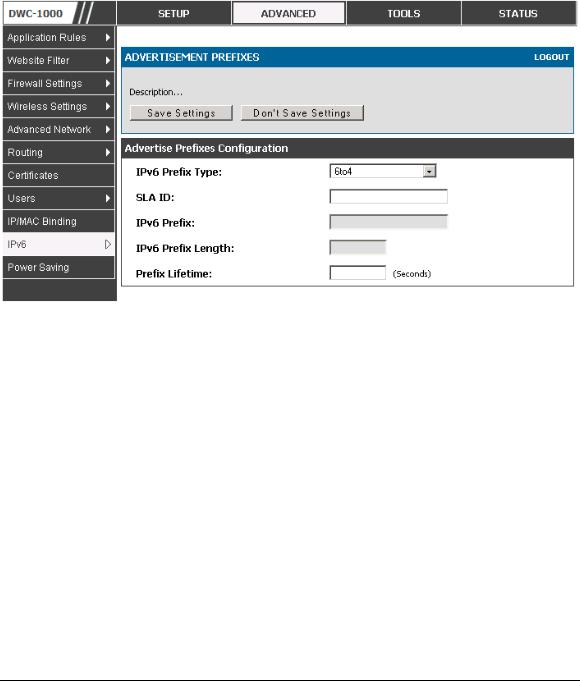
Advertisement Prefixes
Advanced > IPv6 > IPv6 LAN > Advertisement Prefixes
The router advertisements configured with advertisement prefixes allow this router to inform hosts how to perform stateless address auto configuration. Router advertisements contain a list of subnet prefixes that allow the router to determine neighbors and whether the host is on the same link as the router.
The following prefix options are available for the router advertisements:
IPv6 Prefix Type: To ensure hosts support IPv6 to IPv4 tunnel select the 6to4 prefix type. Selecting Global/Local/ISATAP will allow the nodes to support all other IPv6 routing options
SLA ID: The SLA ID (Site-Level Aggregation Identifier) is available when 6to4 Prefixes are selected. This should be the interface ID of the router‘s
LAN interface used for router advertisements.
IPv6 Prefix: When using Global/Local/ISATAP prefixes, this field is used to define the IPv6 network advertised by this router.
18
Wireless Controller |
User Manual |
|
|
IPv6 Prefix Length: This value indicates the number contiguous, higher order bits of the IPv6 address that define up the network portion of the address. Typically this is 64.
Prefix Lifetime: This defines the duration (in seconds) that the requesting node is allowed to use the advertised prefix. It is analogous to DHCP lease time in an IPv4 network.
Figure 4: IPv6 Advertisement Prefix settings
2.2 VLAN Configuration
The controller supports virtual network isolation on the LAN with the use of VLANs. LAN devices can be configured to communicate in a subnetwork defined by VLAN identifiers. LAN ports can be assigned unique VLAN IDs so that traffic to and from that physical port can be isolated from the general LAN. VLAN filtering is particularly useful to limit broadcast packets of a device in a large network
VLAN support is disabled by default in the controller. In the VLAN Configuration page, enable VLAN support on the controller and then proceed to the next section to define the virtual network.
Setup > VLAN Settings > Available VLAN
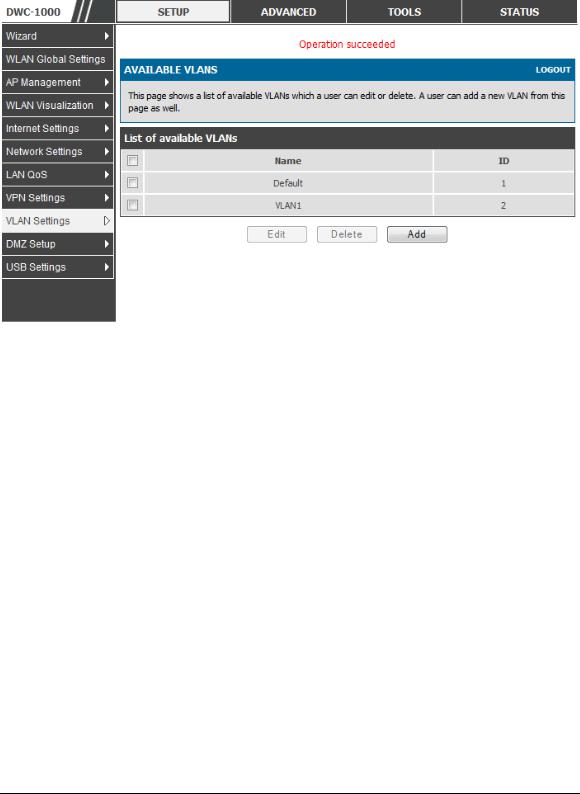
The Available VLAN page shows a list of configured VLANs by name and VLAN ID. A VLAN membership can be created by clicking the Add button below the List of Available VLANs.
A VLAN membership entry consists of a VLAN identifier and the numerical VLAN ID which is assigned to the VLAN membership. The VLAN ID value can be any number from 2 to 4091. VLAN ID 1 is reserved for the default VLAN, which is used for untagged frames received on the interface. By enabling Inter VLAN Routing, you
19
Wireless Controller |
User Manual |
|
|
will allow traffic from LAN hosts belonging to this VLAN ID to pass through to other configured VLAN IDs that have Inter VLAN Routing enabled.
Figure 5: Adding VLAN memberships to the LAN
2.2.1 Associating VLANs to ports
In order to tag all traffic through a specific LAN port with a VLAN ID, you can associate a VLAN to a physical port.
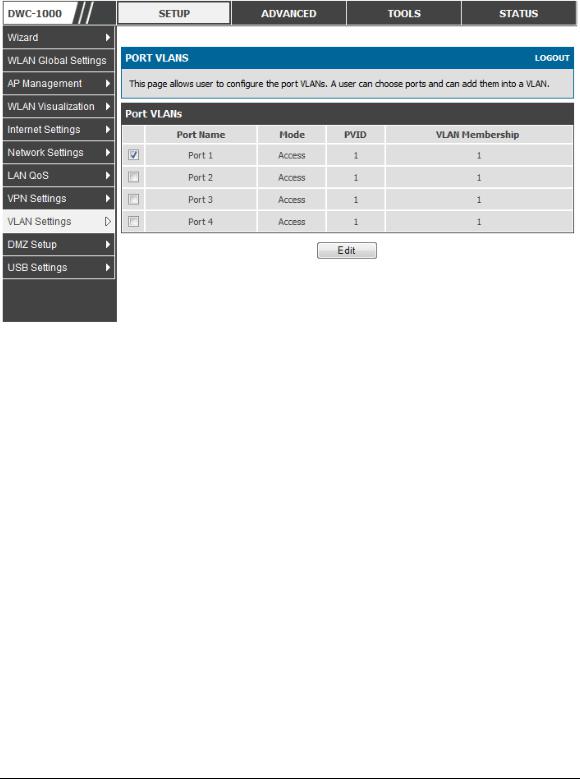
Setup > VLAN Settings > Port VLAN
VLAN membership properties for the LAN and wireless LAN are listed on this page. The VLAN Port table displays the port identifier, the mode setting for that port and VLAN membership information. The configuration page is accessed by selecting one of the four physical ports or a configured access point and clicking Edit.
The edit page offers the following configuration options:
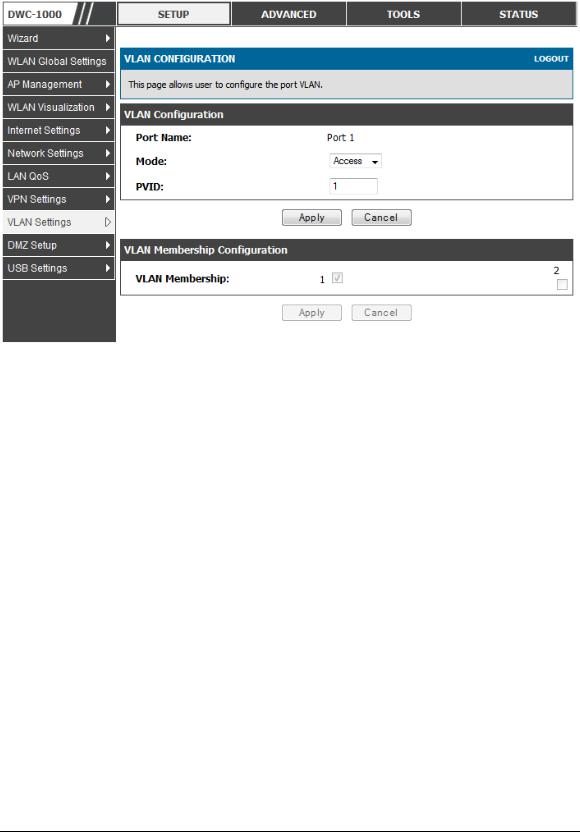
Mode: The mode of this VLAN can be General, Access, or Trunk. The default is access.
In General mode the port is a member of a user selectable set of VLANs. The port sends and receives data that is tagged or untagged with a VLAN ID. If the data into the port is untagged, it is assigned the defined PVID. In the configuration from Figure 4, Port 3 is a General port with PVID 3, so untagged data into Port 3 will be assigned PVID 3. All tagged data sent out of the port with the same PVID will be untagged. This is mode is typically used with IP Phones that have dual Ethernet ports. Data coming from phone
20
Wireless Controller |
User Manual |
|
|
to the switch port on the controller will be tagged. Data passing through the phone from a connected device will be untagged.
Figure 6: Port VLAN list
In Access mode the port is a member of a single VLAN (and only one). All data going into and out of the port is untagged. Traffic through a port in access mode looks like any other Ethernet frame.
In Trunk mode the port is a member of a user selectable set of VLANs. All data going into and out of the port is tagged. Untagged coming into the port is not forwarded, except for the default VLAN with PVID=1, which is untagged. Trunk ports multiplex traffic for multiple VLANs over the s ame physical link.
Select PVID for the port when the General mode is selected.
Configured VLAN memberships will be displayed on the VLAN Membership Configuration for the port. By selecting one more VLAN membership options for a General or Trunk port, traf fic can be routed between the selected VLAN membership IDs
21
Wireless Controller |
User Manual |
|
|
Figure 7: Configuring VLAN membership for a port
2.3 Configurable Port: DMZ Setup
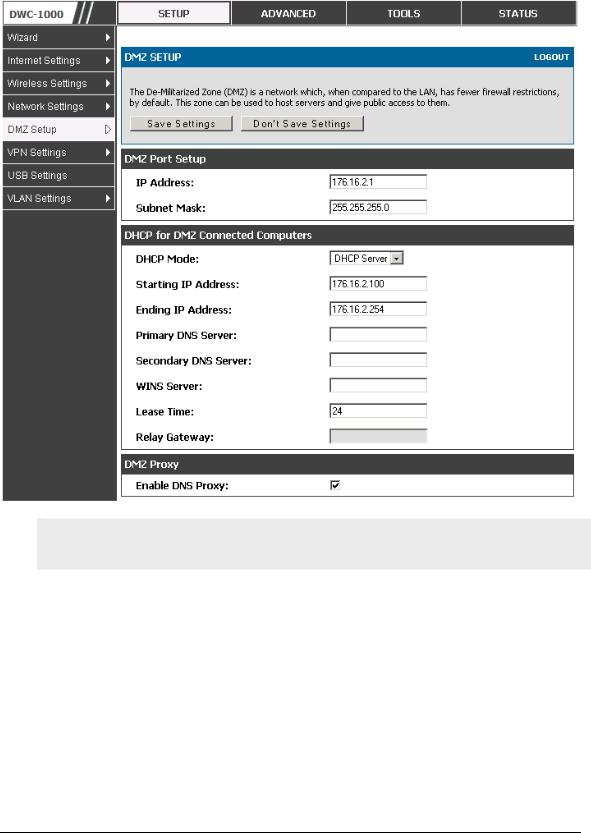
This controller supports one of the physical ports to be configured as a secondary WAN Ethernet port or a dedicated DMZ port. A DMZ is a subnetwork that is open to the public but behind the firewall. The DMZ adds an additional layer of security to the LAN, as specific services/ports that are exposed to the internet on the DMZ do not have to be exposed on the LAN. It is recommended that hosts that must be exposed to the internet (such as web or email servers) be placed in the DMZ network. Firewall rules can be allowed to permit access specific services/ports to the DMZ from both the LAN or WAN. In the event of an attack to any of the DMZ nodes, the LAN is not necessarily vulnerable as well.
Setup > DMZ Setup > DMZ Setup Configuration
DMZ configuration is identical to the LAN configuration. There are no restrictions on the IP address or subnet assigned to the DMZ port, other than the fact that it cannot be identical to the IP address given to the LAN interface of this gateway.
22
Wireless Controller |
User Manual |
|
|
Figure 8: DMZ configuration
In order to configure a DMZ port, the controller configurable port must be set to
DMZ in the Setup > Internet Settings > Configurable Port page.
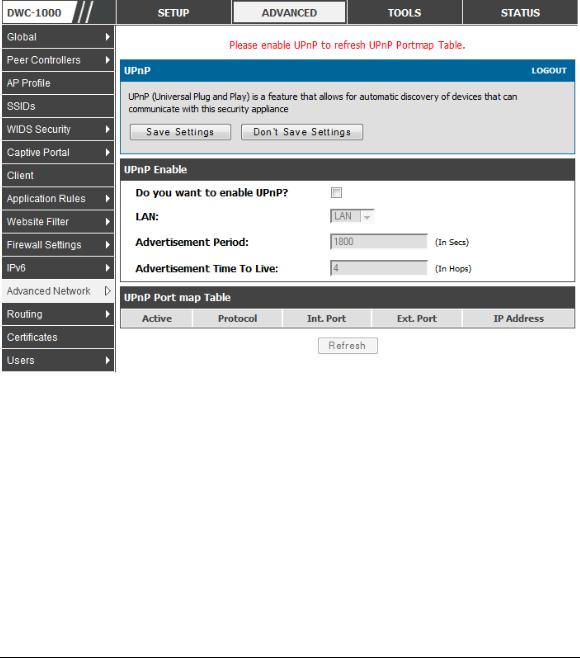
2.4 Universal Plug and Play (UPnP)
Advanced > Advanced Network > UPnP
Universal Plug and Play (UPnP) is a feature that allows the controller to discovery devices on the network that can communicate with the controller and allow for auto configuration. If a network device is detected by UPnP, the controller can open internal or external ports for the traffic protocol required by that network device.
Once UPnP is enabled, you can configure the controller to detect UPnP-supporting devices on the LAN (or a configured VLAN). If disabled, the controller will not allow for automatic device configuration.
Configure the following settings to use UPnP:
23
Wireless Controller |
User Manual |
|
|
Advertisement Period: This is the frequency that the controller broadcasts UPnP information over the network. A large value will minimize network traffic but cause delays in identifying new UPnP devices to the network.
Advertisement Time to Live: This is expressed in hops for each UPnP packet. This is the number of steps a packet is allowed to propagate before being discarded. Small values will limit the UPnP broadcast range. A default of 4 is typical for networks with few switches.
Figure 9: UPnP Configuration
UPnP Port map Table
The UPnP Port map Table has the details of UPnP devices that respond to the controller advertisements. The following information is displayed for each detected device:
Active: A yes/no indicating whether the port of the UPnP device that established a connection is currently active
Protocol: The network protocol (i.e. HTTP, FTP, etc.) used by the DWC
Int. Port (Internal Port): The internal ports opened by UPnP (if any)
Ext. Port (External Port): The external ports opened by UPnP (if any)
IP Address: The IP address of the UPnP device detected by this controller
Click Refresh to refresh the portmap table and search for any new UPnP devices
24
Wireless Controller |
User Manual |
|
|
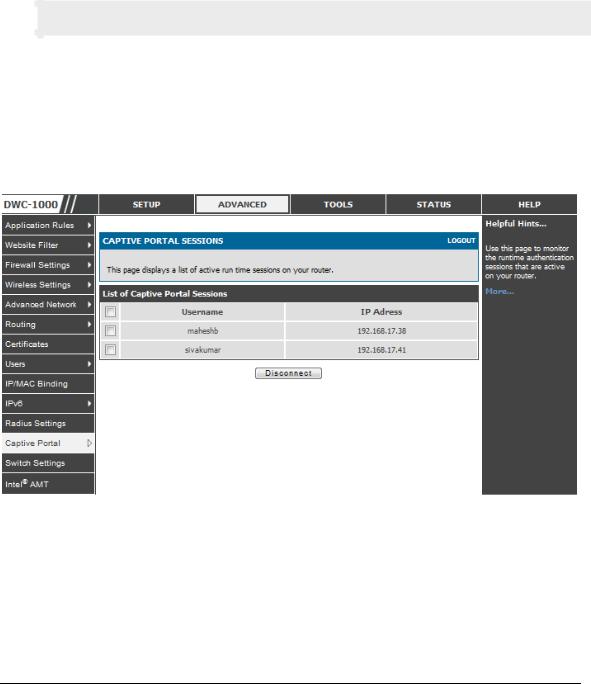
2.5 Captive Portal
LAN users can gain internet access via web portal authentication with the DWC. Also referred to as Run-Time Authentication, a Captive Portal is ideal for a web café scenario where users initiate HTTP connection requests for web access but are not interested in accessing any LAN services. Firewall policies underneath will define which users require authentication for HTTP access, and when a matching user request is made the DWC will intercept the request and prompt for a username / password. The login credentials are compared against the RunTimeAuth users in user database prior to granting HTTP access.
Captive Portal is available for LAN users only and not for DM Z hosts.
Advanced > Captive Portal >Captive Portal Sessions
The Active Runtime internet sessions through the controller firewall are listed in the below table. These users are present in the local or external user database and have had their login credentials approved for internet access. A ‗Disconnect‘ button allows the DWC-1000 admin to selectively drop an authenticated user.
Figure 10: Active Runtime sessions
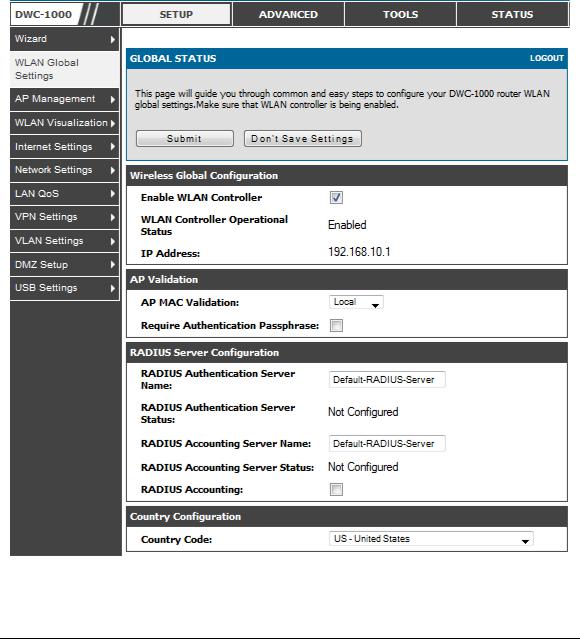
2.6 WLAN global configuration
Setup > WLAN Global Settings
Following are the options available to enable the WLAN function on DWC -1000
Enable WLAN Controller: Select this option to enable WLAN controller functionality on the system. Clear the option to administratively disable the WLAN controller. If you clear the option, all peer controller and APs that are associated with this controller are disassociated.
25
Wireless Controller |
User Manual |
|
|
Disabling the WLAN controller does not affect non-WLAN features on the controller, such as VLAN or STP functionality.
WLAN Controller Operational Status: Shows the operational status of the controller
. The status can be one of the following values:
•Enabled
•Enable-Pending
•Disabled
•Disable-Pending
Figure 11: WLAN global configuration
IP Address: This field shows the IP address of the WLAN interface on the controller. If the controller does not have the Routing Package installed, or if routing is disabled, the IP address is the network interface. If the routing package is
26

Wireless Controller |
User Manual |
|
|
installed and enabled, this is the IP address of the routing or loo pback interface you configure for the controller features.
AP MAC Validation Method: Add the MAC address of the AP to the Valid AP database, which can be kept locally on the controller or in an external RADIUS server. When the controller discovers an AP that is not managed by another ccontroller, it looks up the MAC address of the AP in the Valid AP database. If it finds the MAC address in the database, the controller validates the AP and assumes management. Select the database to use for AP validation and , optionally, for authentication if the Require Authentication Passphrase option is selected.
•Local: If you select this option, you must add the MAC address of each AP to the local Valid AP database.
•RADIUS: If you select this option, you must configur e the MAC address of each AP in an external RADIUS server.
Require Authentication Passphrase: Select this option to require APs to be authenticated before they can associate with the controller. If you select this option, you must configure the passphrase on the AP while it is in standalone mode as well as in the Valid AP database.
RADIUS Authentication Server Name : Enter the name of the RADIUS server used for AP and client authentications. The name can contain up to 32 alphanumeric characters. Spaces, underscores, and dashes are also permitted. The controller acts as the RADIUS client and performs all RADIUS transactions on behalf of the APs and wireless clients.
RADIUS Authentication Server Configured: Indicates whether the RADIUS authentication server is configured.
RADIUS Accounting Server Name : Enter the name of the RADIUS server used for reporting wireless client associations and disassociations. The name can contain up to 32 alphanumeric characters. Spaces, underscores, and dashes are also permitted.
RADIUS Accounting Server Configured: Indicates whether the RADIUS accounting server is configured.
RADIUS Accounting: Select this option to enable RADIUS accounting for wireless clients.
Country Code: Select the country code that represents the country w here your controller and APs operate. When you click Submit, a pop -up message asks you to confirm the change. Wireless regulations vary from country to country. Make sure you select the correct country code so that your WLAN system complies with the regulations in your country.
27

Wireless Controller User Manual
2.6.1 Wireless Discovery configuration
The wireless controller can discover, validate, authenticate, or monitor the following system devices:
•Peer wireless controllers
•APs
•Wireless clients
•Rogue APs
•Rogue wireless clients
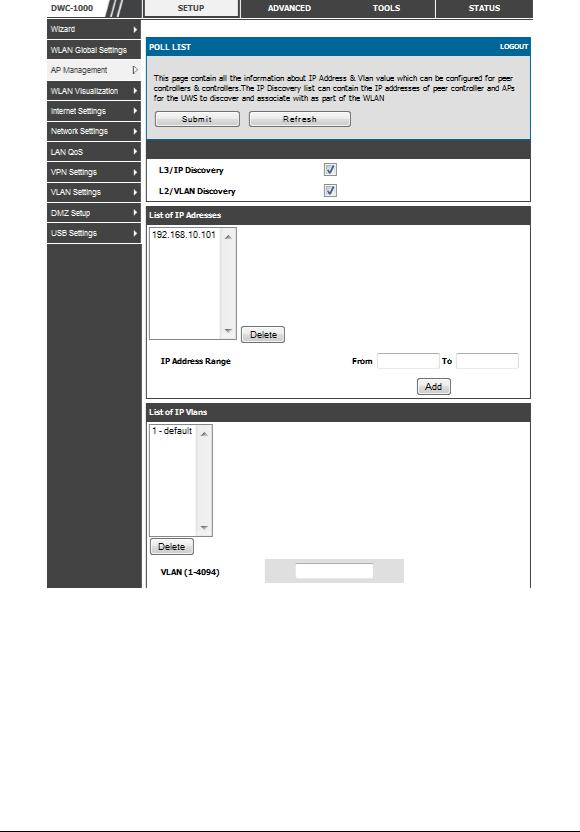
Setup > AP Management > Poll List
The wireless controller can discover peer wireless controller and APs regardless of whether these devices are connected to each other, located in the same Layer 2 broadcast domain, or attached to different IP subnets. In order for the controller to discover other WLAN devices and establish communication with them, the devices must have their own IP address, must be able to find other WLAN devices, and must be compatible. When the controller discovers and validates APs, the controller takes over the management of the AP. If you configure the AP in Standalone mode, the existing AP configuration is replaced by the default AP Profile configuration on the controller.
L3/IP Discovery: Select or clear this option to enable or disable IP -based discovery of access points and peer wireless controller. When the L3/IP Discovery option is selected, IP polling is enabled and the controller will periodically poll each address in the configured IP List. By default, L3/IP Discovery is enabled.
List of IP address: Shows the list of IP addresses configured for discovery.
To remove entries from the list, select one or more entries and click Delete.
Hold the "shift" key or ―control‖ key to select specific entry.
IP Address Range: This text field is used to add a range of IP address entries to the IP List. Enter the IP address at the start of the address range in the From field, and enter the IP address at the end of the range in the To field, then click Add. All IP addresses in the range are added to the IP List. Only the last octet is allowed to differ between the From address and the To address.
28
Wireless Controller |
User Manual |
|
|
Figure 12: Configuring the Wireless Discovery
L2/VLAN Discovery: The D-Link Wireless Device Discovery Protocol is a good discovery method to use if the controller and APs are located in the same Layer 2 multicast domain. The wireless controller periodically sends a multicast packet containing the discovery message on each VLAN enabled for discovery
This page includes the following buttons:
•Add—Adds the data in the IP Address or VLAN field to the appropriate list.
•Delete—Deletes the selected entry from the IP or VLAN list.
29
 Loading...
Loading...