TP-Link TL-SG5412F, TL-SG5428 CLI Reference Guide

TL-SG5428
24-Port Gigabit L2 Managed Switch with 4 SFP Slots
TL-SG5412F
12-Port Gigabit SFP L2 Managed Switch with 4 Combo 1000BASE-T Ports
REV2.1.1
1910010847
COPYRIGHT & TRADEMARKS
Specifications are subject to change without notice.  is a registered trademark of TP-LINK TECHNOLOGIES CO., LTD. Other brands and product names are trademarks or registered trademarks of their respective holders.
is a registered trademark of TP-LINK TECHNOLOGIES CO., LTD. Other brands and product names are trademarks or registered trademarks of their respective holders.
No part of the specifications may be reproduced in any form or by any means or used to make any derivative such as translation, transformation, or adaptation without permission from TP-LINK TECHNOLOGIES CO., LTD. Copyright © 2013 TP-LINK TECHNOLOGIES CO., LTD. All rights reserved.
http://www.tp-link.com
I
CONTENTS
Preface ………………………………………………………………………………….1
Chapter 1 Using the CLI......................................................................................... |
4 |
||
1.1 Accessing the CLI.............................................................................................................. |
4 |
||
|
1.1.1 Logon by a console port..................................................................................... |
4 |
|
|
1.1.2 |
Logon by Telnet.................................................................................................. |
6 |
1.2 |
CLI Command Modes ................................................................................................... |
11 |
|
1.3 |
Security Levels ............................................................................................................. |
13 |
|
1.4 |
Conventions.................................................................................................................. |
13 |
|
|
1.4.1 |
Format Conventions......................................................................................... |
13 |
|
1.4.2 |
Special Characters........................................................................................... |
13 |
|
1.4.3 |
Parameter Format............................................................................................ |
14 |
Chapter 2 |
User Interface...................................................................................... |
15 |
|
enable.................................................................................................................................... |
|
15 |
|
enable password ................................................................................................................... |
15 |
||
disable................................................................................................................................... |
|
16 |
|
configure................................................................................................................................ |
|
16 |
|
exit......................................................................................................................................... |
|
|
16 |
end ........................................................................................................................................ |
|
|
17 |
Chapter 3 IEEE 802.1Q VLAN Commands.......................................................... |
18 |
||
vlan........................................................................................................................................ |
|
|
18 |
interface vlan ......................................................................................................................... |
18 |
||
name ..................................................................................................................................... |
|
19 |
|
switchport mode .................................................................................................................... |
19 |
||
switchport access vlan........................................................................................................... |
20 |
||
switchport trunk allowed vlan................................................................................................. |
20 |
||
switchport general allowed vlan............................................................................................. |
21 |
||
switchport pvid....................................................................................................................... |
22 |
||
show vlan summary............................................................................................................... |
22 |
||
show vlan brief ...................................................................................................................... |
23 |
||
show vlan .............................................................................................................................. |
|
23 |
|
Chapter 4 Protocol VLAN Commands.................................................................. |
24 |
||
protocol-vlan template ........................................................................................................... |
24 |
||
protocol-vlan vlan .................................................................................................................. |
24 |
||
II
protocol-vlan.......................................................................................................................... |
25 |
|
show protocol-vlan template.................................................................................................. |
26 |
|
show protocol-vlan vlan ......................................................................................................... |
26 |
|
show protocol-vlan interface.................................................................................................. |
26 |
|
Chapter 5 |
VLAN - VPN Commands ....................................................................... |
28 |
dot1q-tunnel .......................................................................................................................... |
28 |
|
dot1q-tunnel tpid.................................................................................................................... |
28 |
|
switchport dot1q-tunnel enable.............................................................................................. |
29 |
|
switchport dot1q-tunnel mode uplink ..................................................................................... |
29 |
|
show dot1q-tunnel ................................................................................................................. |
30 |
|
show dot1q-tunnel interface .................................................................................................. |
30 |
|
show dot1q-tunnel uplink....................................................................................................... |
31 |
|
Chapter 6 Voice VLAN Commands ...................................................................... |
32 |
|
voice vlan |
.............................................................................................................................. |
32 |
voice vlan .............................................................................................................aging time |
32 |
|
voice vlan .........................................................................................................mac-address |
33 |
|
switchport ...................................................................................................voice vlan mode |
34 |
|
switchport ................................................................................................voice vlan security |
34 |
|
show voice .....................................................................................................................vlan |
35 |
|
show voice ...............................................................................................................vlan oui |
35 |
|
show voice ....................................................................................................vlan switchport |
35 |
|
Chapter 7 ....................................................................Private VLAN Commands |
37 |
|
private-vlan ...............................................................................................................primary |
37 |
|
private-vlan ..........................................................................................................secondary |
37 |
|
private-vlan .........................................................................................................association |
38 |
|
switchport ...........................................................................................................private-vlan |
38 |
|
switchport ................................................................................private-vlan host-association |
39 |
|
switchport ............................................................................................private-vlan mapping |
40 |
|
show vlan ...........................................................................................................private-vlan |
40 |
|
Chapter 8 ............................................................................... |
GVRP Commands |
42 |
gvrp(global) ........................................................................................................................... |
42 |
|
gvrp(interface) ....................................................................................................................... |
42 |
|
gvrp registration..................................................................................................................... |
43 |
|
gvrp timer .............................................................................................................................. |
|
43 |
show gvrp ...................................................................................................................global |
44 |
|
|
|
III |
show gvrp interface ............................................................................................................... |
45 |
Chapter 9 Etherchannel Commands .................................................................... |
46 |
channel-group ....................................................................................................................... |
46 |
port-channel load-balance ..................................................................................................... |
47 |
lacp system-priority ............................................................................................................... |
47 |
lacp port-priority..................................................................................................................... |
48 |
show etherchannel ................................................................................................................ |
48 |
show etherchannel load-balance........................................................................................... |
49 |
show lacp .............................................................................................................................. |
49 |
show lacp sys-id .................................................................................................................... |
50 |
Chapter 10 User Manage Commands.................................................................... |
51 |
user name ............................................................................................................................. |
51 |
user access-control ip-based................................................................................................. |
52 |
user access-control mac-based............................................................................................. |
52 |
user access-control port-based ............................................................................................. |
53 |
user max-number .................................................................................................................. |
54 |
user idle-timeout.................................................................................................................... |
54 |
line......................................................................................................................................... |
55 |
password ............................................................................................................................... |
56 |
login....................................................................................................................................... |
56 |
login local .............................................................................................................................. |
57 |
show user account-list........................................................................................................... |
57 |
show user configuration......................................................................................................... |
58 |
Chapter 11 Binding Table Commands.................................................................... |
59 |
ip source binding ................................................................................................................... |
59 |
ip dhcp snooping ................................................................................................................... |
60 |
ip dhcp snooping global......................................................................................................... |
61 |
ip dhcp snooping information option...................................................................................... |
62 |
ip dhcp snooping information strategy................................................................................... |
62 |
ip dhcp snooping information remote-id................................................................................. |
63 |
ip dhcp snooping information circuit-id .................................................................................. |
63 |
ip dhcp snooping trust ........................................................................................................... |
64 |
ip dhcp snooping mac-verify.................................................................................................. |
65 |
ip dhcp snooping limit rate..................................................................................................... |
65 |
ip dhcp snooping decline ....................................................................................................... |
66 |
show ip source binding .......................................................................................................... |
66 |
|
IV |
show ip dhcp snooping.......................................................................................................... |
67 |
show ip dhcp snooping information ....................................................................................... |
67 |
show ip dhcp snooping interface gigabitEthernet .................................................................. |
68 |
Chapter 12 ARP Inspection Commands................................................................. |
69 |
ip arp inspection(global) ........................................................................................................ |
69 |
ip arp inspection trust ............................................................................................................ |
69 |
ip arp inspection(interface) .................................................................................................... |
70 |
ip arp inspection limit-rate...................................................................................................... |
71 |
ip arp inspection recover ....................................................................................................... |
71 |
show ip arp inspection........................................................................................................... |
72 |
show ip arp inspection interface ............................................................................................ |
72 |
show ip arp inspection statistics ............................................................................................ |
73 |
clear ip arp inspection statistics............................................................................................. |
73 |
Chapter 13 IP Verify Source Commands................................................................ |
74 |
ip verify source ...................................................................................................................... |
74 |
show ip verify source............................................................................................................. |
74 |
Chapter 14 DoS Defend Command ....................................................................... |
76 |
ip dos-prevent........................................................................................................................ |
76 |
ip dos-prevent type................................................................................................................ |
76 |
show ip dos-prevent .............................................................................................................. |
77 |
Chapter 15 IEEE 802.1X Commands..................................................................... |
78 |
dot1x system-auth-control ..................................................................................................... |
78 |
dot1x auth-method ................................................................................................................ |
78 |
dot1x guest-vlan(global) ........................................................................................................ |
79 |
dot1x quiet-period.................................................................................................................. |
80 |
dot1x timeout......................................................................................................................... |
80 |
dot1x max-reauth-req ............................................................................................................ |
81 |
dot1x...................................................................................................................................... |
81 |
dot1x guest-vlan(interface) .................................................................................................... |
82 |
dot1x port-control .................................................................................................................. |
82 |
dot1x port-method ................................................................................................................. |
83 |
radius..................................................................................................................................... |
84 |
radius server-account............................................................................................................ |
85 |
show dot1x global.................................................................................................................. |
85 |
show dot1x interface ............................................................................................................. |
86 |
V |
|
show radius accounting......................................................................................................... |
86 |
|
show radius authentication .................................................................................................... |
87 |
|
Chapter 16 System Log Commands ...................................................................... |
88 |
|
logging buffer......................................................................................................................... |
88 |
|
logging file flash..................................................................................................................... |
89 |
|
clear logging .......................................................................................................................... |
89 |
|
logging host index ................................................................................................................. |
90 |
|
show logging local-config ...................................................................................................... |
91 |
|
show logging loghost............................................................................................................. |
91 |
|
show logging buffer ............................................................................................................... |
91 |
|
show logging flash................................................................................................................. |
92 |
|
Chapter 17 |
SSH Commands.................................................................................. |
93 |
ip ssh server .......................................................................................................................... |
93 |
|
ip ssh version ........................................................................................................................ |
93 |
|
ip ssh timeout ........................................................................................................................ |
94 |
|
ip ssh max-client.................................................................................................................... |
94 |
|
ip ssh download..................................................................................................................... |
95 |
|
show ip ssh............................................................................................................................ |
95 |
|
Chapter 18 |
SSL Commands .................................................................................. |
97 |
ip http secure-server.............................................................................................................. |
97 |
|
ip http secure-server download certificate ............................................................................. |
97 |
|
ip http secure-server download key....................................................................................... |
98 |
|
show ip http secure-server .................................................................................................... |
99 |
|
Chapter 19 |
MAC Address Commands .................................................................. |
100 |
mac address-table static...................................................................................................... |
100 |
|
mac address-table aging-time ............................................................................................. |
101 |
|
mac address-table filtering .................................................................................................. |
101 |
|
mac address-table max-mac-count ..................................................................................... |
102 |
|
show mac address-table address........................................................................................ |
103 |
|
show mac address-table aging-time.................................................................................... |
103 |
|
show mac address-table max-mac-count interface gigabitEthernet .................................... |
104 |
|
show mac address-table interface gigabitEthernet.............................................................. |
104 |
|
show mac address-table mac-num...................................................................................... |
105 |
|
show mac address-table mac.............................................................................................. |
105 |
|
show mac address-table vlan .............................................................................................. |
106 |
|
|
VI |
|
Chapter 20 System Configuration Commands...................................................... |
107 |
system-time manual ............................................................................................................ |
107 |
system-time ntp ................................................................................................................... |
107 |
system-time dst predefined ................................................................................................. |
109 |
system-time dst date ........................................................................................................... |
109 |
system-time dst recurring .................................................................................................... |
110 |
hostname............................................................................................................................. |
111 |
location................................................................................................................................ |
112 |
contact-info.......................................................................................................................... |
112 |
ip management-vlan............................................................................................................ |
113 |
ip address............................................................................................................................ |
113 |
ip address-alloc dhcp .......................................................................................................... |
114 |
ip address-alloc bootp ......................................................................................................... |
114 |
reset .................................................................................................................................... |
115 |
reboot .................................................................................................................................. |
115 |
copy running-config startup-config ...................................................................................... |
116 |
copy startup-config tftp ........................................................................................................ |
116 |
copy tftp startup-config ........................................................................................................ |
117 |
firmware upgrade ................................................................................................................ |
117 |
ping ..................................................................................................................................... |
119 |
tracert .................................................................................................................................. |
119 |
loopback interface ............................................................................................................... |
120 |
show system-time................................................................................................................ |
120 |
show system-time dst.......................................................................................................... |
121 |
show system-time ntp.......................................................................................................... |
121 |
show system-info................................................................................................................. |
122 |
show cable-diagnostics interface......................................................................................... |
122 |
Chapter 21 Ethernet Configuration Commands .................................................... |
123 |
interface gigabitEthernet...................................................................................................... |
123 |
interface range gigabitEthernet ........................................................................................... |
123 |
description ........................................................................................................................... |
124 |
shutdown ............................................................................................................................. |
124 |
flow-control .......................................................................................................................... |
125 |
media-type........................................................................................................................... |
125 |
duplex.................................................................................................................................. |
126 |
speed................................................................................................................................... |
126 |
storm-control broadcast....................................................................................................... |
127 |
VII |
|
storm-control multicast ........................................................................................................ |
128 |
storm-control unicast ........................................................................................................... |
128 |
storm-control rate ................................................................................................................ |
129 |
bandwidth ............................................................................................................................ |
129 |
clear counters...................................................................................................................... |
130 |
show interface status........................................................................................................... |
130 |
show interface counters....................................................................................................... |
131 |
show interface description ................................................................................................... |
131 |
show interface flowcontrol ................................................................................................... |
132 |
show interface configuration................................................................................................ |
132 |
show storm-control .............................................................................................................. |
133 |
show bandwidth................................................................................................................... |
133 |
Chapter 22 QoS Commands................................................................................. |
135 |
qos ...................................................................................................................................... |
135 |
qos cos................................................................................................................................ |
135 |
qos dscp.............................................................................................................................. |
136 |
qos queue cos-map............................................................................................................. |
136 |
qos queue dscp-map........................................................................................................... |
137 |
qos queue mode.................................................................................................................. |
138 |
show qos interface .............................................................................................................. |
139 |
show qos cos-map .............................................................................................................. |
140 |
show qos dscp-map ............................................................................................................ |
140 |
show qos queue mode ........................................................................................................ |
140 |
show qos status................................................................................................................... |
141 |
Chapter 23 Port Mirror Commands ....................................................................... |
142 |
monitor session destination interface .................................................................................. |
142 |
monitor session source interface......................................................................................... |
143 |
show monitor session.......................................................................................................... |
144 |
Chapter 24 Port Isolation Commands ................................................................... |
145 |
port isolation ........................................................................................................................ |
145 |
show port isolation interface ................................................................................................ |
145 |
Chapter 25 Loopback Detection Commands ........................................................ |
147 |
loopback-detection(global) .................................................................................................. |
147 |
loopback-detection interval.................................................................................................. |
147 |
loopback-detection recovery-time........................................................................................ |
148 |
VIII |
|
loopback-detection(interface) .............................................................................................. |
148 |
|
loopback-detection config.................................................................................................... |
149 |
|
loopback-detection recover ................................................................................................. |
149 |
|
show loopback-detection global .......................................................................................... |
150 |
|
show loopback-detection interface ...................................................................................... |
150 |
|
Chapter 26 |
ACL Commands ................................................................................. |
152 |
time-range ........................................................................................................................... |
152 |
|
absolute |
............................................................................................................................... |
152 |
periodic................................................................................................................................ |
|
153 |
holiday................................................................................................................................. |
|
154 |
holiday(global) ..................................................................................................................... |
154 |
|
access-list .................................................................................................................create |
155 |
|
mac access ....................................................................................................................-list |
155 |
|
access-list .............................................................................................................standard |
156 |
|
access-list ............................................................................................................extended |
157 |
|
rule ...................................................................................................................................... |
|
158 |
access-list ........................................................................................................policy name |
159 |
|
access-list .......................................................................................................policy action |
160 |
|
redirect interface.................................................................................................................. |
160 |
|
s-condition ........................................................................................................................... |
161 |
|
s-mirror ................................................................................................................................ |
|
161 |
access-list ....................................................................................................bind(interface) |
162 |
|
access-list ...........................................................................................................bind(vlan) |
162 |
|
show time ..................................................................................................................-range |
163 |
|
show holiday........................................................................................................................ |
163 |
|
show access ..................................................................................................................-list |
163 |
|
show access ........................................................................................................-list policy |
164 |
|
show access ..........................................................................................................-list bind |
164 |
|
Chapter 27 .............................................................................. |
MSTP Commands |
166 |
spanning ...........................................................................................................-tree(global) |
166 |
|
spanning ......................................................................................................-tree(interface) |
166 |
|
spanning .............................................................................................-tree common-config |
167 |
|
spanning .............................................................................................................-tree mode |
168 |
|
spanning ..........................................................................................-tree mst configuration |
168 |
|
instance ............................................................................................................................... |
|
169 |
name ................................................................................................................................... |
|
170 |
|
|
IX |
revision ................................................................................................................................ |
170 |
spanning-tree mst instance ................................................................................................. |
171 |
spanning-tree mst................................................................................................................ |
171 |
spanning-tree priority........................................................................................................... |
172 |
spanning-tree tc-defend....................................................................................................... |
173 |
spanning-tree timer.............................................................................................................. |
173 |
spanning-tree hold-count..................................................................................................... |
174 |
spanning-tree max-hops...................................................................................................... |
175 |
spanning-tree bpdufilter....................................................................................................... |
175 |
spanning-tree bpduguard .................................................................................................... |
176 |
spanning-tree guard loop..................................................................................................... |
176 |
spanning-tree guard root ..................................................................................................... |
177 |
spanning-tree guard tc......................................................................................................... |
177 |
spanning-tree mcheck ......................................................................................................... |
178 |
show spanning-tree active................................................................................................... |
178 |
show spanning-tree bridge .................................................................................................. |
179 |
show spanning-tree interface .............................................................................................. |
179 |
show spanning-tree interface-security ................................................................................. |
180 |
show spanning-tree mst ...................................................................................................... |
181 |
Chapter 28 IGMP Commands ............................................................................... |
182 |
ip igmp snooping(global) ..................................................................................................... |
182 |
ip igmp snooping(interface) ................................................................................................. |
182 |
ip igmp snooping immediate-leave ...................................................................................... |
183 |
ip igmp snooping drop-unknown.......................................................................................... |
183 |
ip igmp snooping vlan-config ............................................................................................... |
184 |
ip igmp snooping multi-vlan-config ...................................................................................... |
185 |
ip igmp snooping filter add-id............................................................................................... |
186 |
ip igmp snooping filter(global).............................................................................................. |
187 |
ip igmp snooping filter(interface) ......................................................................................... |
187 |
ip igmp snooping filter maxgroup......................................................................................... |
188 |
ip igmp snooping filter mode................................................................................................ |
188 |
show ip igmp snooping........................................................................................................ |
189 |
show ip igmp snooping interface ......................................................................................... |
189 |
show ip igmp snooping vlan ................................................................................................ |
190 |
show ip igmp snooping multi-vlan........................................................................................ |
191 |
show ip igmp snooping groups ............................................................................................ |
191 |
show ip igmp snooping filter ................................................................................................ |
192 |
|
X |
Chapter 29 |
SNMP Commands.............................................................................. |
193 |
snmp-server ........................................................................................................................ |
193 |
|
snmp-server view ................................................................................................................ |
193 |
|
snmp-server group .............................................................................................................. |
194 |
|
snmp-server user ................................................................................................................ |
195 |
|
snmp-server community ...................................................................................................... |
197 |
|
snmp-server host................................................................................................................. |
197 |
|
snmp-server engineID ......................................................................................................... |
199 |
|
snmp-server traps snmp...................................................................................................... |
199 |
|
snmp-server traps link-status............................................................................................... |
200 |
|
snmp-server traps................................................................................................................ |
201 |
|
snmp-server traps mac........................................................................................................ |
202 |
|
snmp-server traps vlan ........................................................................................................ |
202 |
|
rmon history......................................................................................................................... |
203 |
|
rmon event .......................................................................................................................... |
204 |
|
rmon alarm .......................................................................................................................... |
205 |
|
show snmp-server ............................................................................................................... |
206 |
|
show snmp-server view ....................................................................................................... |
207 |
|
show snmp-server group ..................................................................................................... |
207 |
|
show snmp-server user ....................................................................................................... |
207 |
|
show snmp-server community............................................................................................. |
208 |
|
show snmp-server host ....................................................................................................... |
208 |
|
show snmp-server engineID................................................................................................ |
208 |
|
show rmon history ............................................................................................................... |
209 |
|
show rmon event ................................................................................................................. |
209 |
|
show rmon alarm................................................................................................................. |
210 |
|
Chapter 30 |
LLDP Commands ............................................................................... |
211 |
lldp....................................................................................................................................... |
|
211 |
lldp hold-multiplier................................................................................................................ |
211 |
|
lldp timer.............................................................................................................................. |
|
212 |
lldp receive .......................................................................................................................... |
213 |
|
lldp transmit ......................................................................................................................... |
213 |
|
lldp snmp-trap...................................................................................................................... |
214 |
|
lldp tlv-select........................................................................................................................ |
214 |
|
show lldp ............................................................................................................................. |
|
215 |
show lldp interface............................................................................................................... |
215 |
|
show lldp local-information interface.................................................................................... |
216 |
|
|
|
XI |
show lldp neighbor-information interface |
.............................................................................216 |
show lldp traffic interface ..................................................................................................... |
217 |
Chapter 31 Cluster Commands............................................................................. |
218 |
cluster ndp........................................................................................................................... |
218 |
cluster ntdp.......................................................................................................................... |
219 |
cluster explore ..................................................................................................................... |
220 |
cluster.................................................................................................................................. |
220 |
cluster ip pool ...................................................................................................................... |
221 |
cluster commander.............................................................................................................. |
221 |
cluster manage.................................................................................................................... |
222 |
cluster member.................................................................................................................... |
222 |
cluster candidate ................................................................................................................. |
223 |
cluster individual.................................................................................................................. |
223 |
show cluster ndp.................................................................................................................. |
224 |
show cluster ntdp................................................................................................................. |
224 |
show cluster neighbour........................................................................................................ |
225 |
show cluster ........................................................................................................................ |
225 |
show cluster member .......................................................................................................... |
226 |
show cluster manage role.................................................................................................... |
226 |
XII
Preface
This Guide is intended for network administrator to provide referenced information about CLI (Command Line Interface). The device mentioned in this Guide stands for TL-SG5428/TL-SG5412F JetStream L2 Managed Switch.
Overview of this Guide
Chapter 1: Using the CLI
Provide information about how to use the CLI, CLI Command Modes, Security Levels and some Conventions.
Chapter 2: User Interface
Provide information about the commands used to switch between five CLI Command Modes.
Chapter 3: IEEE 802.1Q VLAN Commands
Provide information about the commands used for configuring IEEE 802.1Q VLAN.
Chapter 4: Protocol VLAN Commands
Provide information about the commands used for configuring Protocol VLAN.
Chapter 5: VLAN-VPN Commands
Provide information about the commands used for configuring VLAN-VPN (Virtual Private Network) function.
Chapter 6: Voice VLAN Commands
Provide information about the commands used for configuring Voice VLAN.
Chapter 7: Private VLAN Commands
Provide information about the commands used for configuring Private VLAN.
Chapter 8: GVRP Commands
Provide information about the commands used for configuring GVRP (GARP VLAN registration protocol).
Chapter 9: EtherChannel Commands
Provide information about the commands used for configuring LAG (Link Aggregation Group) and LACP (Link Aggregation Control Protocol).
Chapter 10: User Manage Commands
Provide information about the commands used for user management.
Chapter 11: Binding Table Commands
Provide information about the commands used for binding the IP address, MAC address, VLAN and the connected Port number of the Host together.
1
Chapter 12: ARP Inspection Commands
Provide information about the commands used for protecting the switch from the ARP cheating or ARP Attack.
Chapter 13: IP Verify Source Commands
Provide information about the commands used for guarding the IP Source by filtering the IP packets based on the IP-MAC Binding entries.
Chapter 14: DoS Defend Command
Provide information about the commands used for DoS defend and detecting the DoS attack.
Chapter 15: IEEE 802.1X Commands
Provide information about the commands used for configuring IEEE 802.1X function.
Chapter 16: System Log Commands
Provide information about the commands used for configuring system log.
Chapter 17: SSH Commands
Provide information about the commands used for configuring and managing SSH (Security Shell).
Chapter 18: SSL Commands
Provide information about the commands used for configuring and managing SSL (Secure Sockets Layer).
Chapter 19: MAC Address Commands
Provide information about the commands used for Address configuration.
Chapter 20: System Configuration Commands
Provide information about the commands used for configuring the System information and System IP, reboot and reset the switch, upgrade the switch system and commands used for device diagnose, including loopback test and cable test.
Chapter 21: Ethernet Configuration Commands
Provide information about the commands used for configuring the Bandwidth Control, Negotiation Mode, and Storm Control for ethernet ports.
Chapter 22: QoS Commands
Provide information about the commands used for configuring the QoS function.
Chapter 23: Port Mirror Commands
Provide information about the commands used for configuring the Port Mirror function.
Chapter 24: Port Isolation Commands
Provide information about the commands used for configuring Port Isolation function.
Chapter 25: Loopback Detection Commands
Provide information about the commands used for configuring the Loopback Detection function.
2
Chapter 26: ACL Commands
Provide information about the commands used for configuring the ACL (Access Control List).
Chapter 27: MSTP Commands
Provide information about the commands used for configuring the MSTP (Multiple Spanning Tree Protocol).
Chapter 28: IGMP Commands
Provide information about the commands used for configuring the IGMP Snooping (Internet Group Management Protocol Snooping).
Chapter 29: SNMP Commands
Provide information about the commands used for configuring the SNMP (Simple Network Management Protocol) functions.
Chapter 30: LLDP Commands
Provide information about the commands used for configuring LLDP function.
Chapter 31: Cluster Commands
Provide information about the commands used for configuring the Cluster Management function.
3
Chapter 1 Using the CLI
1.1 Accessing the CLI
You can log on to the switch and access the CLI by the following two methods:
1.Log on to the switch by the console port on the switch.
2.Log on to the switch remotely by a Telnet or SSH connection through an Ethernet port.
1.1.1 Logon by a console port
To log on to the switch by the console port on the switch, please take the following steps:
1.Connect the PCs or Terminals to the console port on the switch by a provided cable.
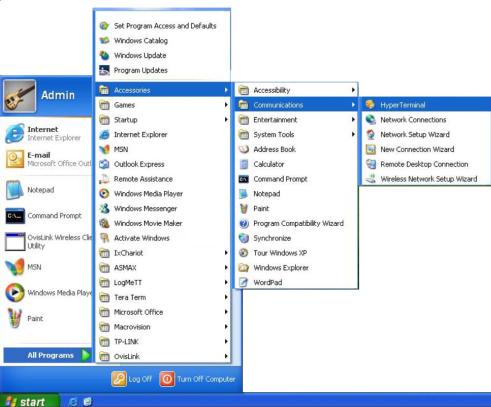
2.Click Start →All Programs →Accessories→Communications →Hyper Terminal to open the Hyper Terminal as the Figure 1-1 shown.
Figure 1-1 Open Hyper Terminal
3.The Connection Description Window will prompt as Figure 1-2 shown. Enter a name into the Name field and click OK.
4
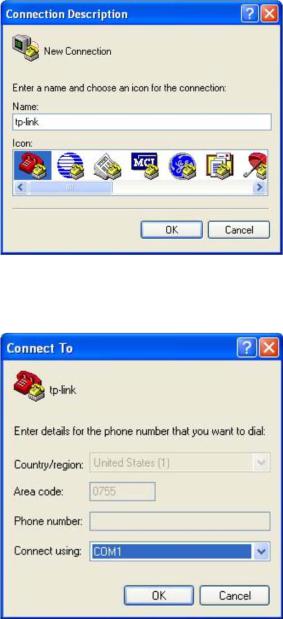
Figure 1-2 Connection Description
4.Select the port to connect in Figure 1-3, and click OK.
Figure 1-3 Select the port to connect
5.Configure the port selected in the step above as the following Figure 1-4 shown. Configure Bits per second as 38400, Data bits as 8, Parity as None, Stop bits as 1,
Flow control as None, and then click OK.
5
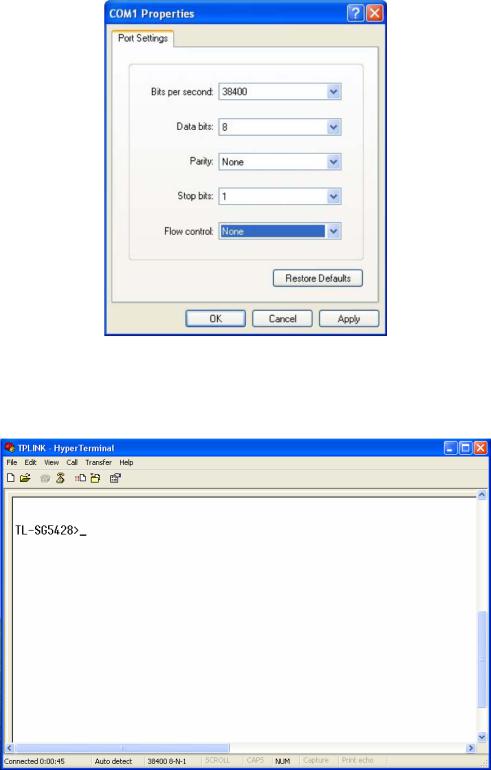
Figure 1-4 Port Settings
6.The DOS prompt ”TL-SG5428>” will appear after pressing the Enter button as Figure 1-5 shown. It indicates that you can use the CLI now.
Figure 1-5 Log in the Switch
1.1.2 Logon by Telnet
To successfully create Telnet connection, firstly CLI commands about configuring Telnet login mode, login authentication information and Privileged EXEC Mode password should be configured through Console connection.
Telnet login has the following two modes. You can choose one according to your needs:
6

Login local Mode: It requires username and password, which are both admin by default.
Login Mode: It requires no username and password, but a connection password is required.
Note:
1.Before Telnet login, you are required to configure Telnet login mode and login authentication information through Console connection. The relevant CLI commands should be entered in the prompted DOS screen shown in Figure 1-5 Log in the Switch.
2.You will enter to User EXEC Mode after Telnet connection is successfully created, but for switch security concerns, you are required to set a password which functions to further access to Privileged EXEC Mode when you configure the login mode.
Login Local Mode
Firstly, configure the Telnet login mode as “login local” and set the password for entering into the Privileged EXEC Mode as 123 in the prompted DOS screen shown in Figure 1-6.
Figure 1-6 Configure login local mode
Now, you can logon by Telnet in login local mode.
1.Make sure the switch and the PC are in the same LAN. Click Start → Run to open the Run window, and type cmd in the prompt Run window as Figure 1-7 and click OK.
Figure 1-7 Run Window
7
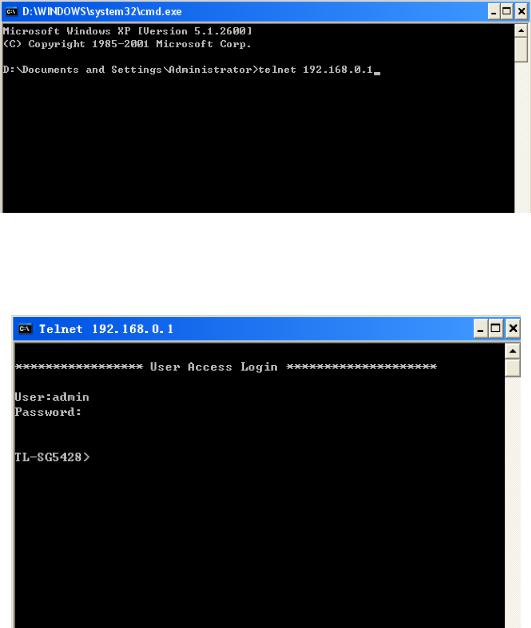
2.Open Telnet, then type telnet 192.168.0.1 in the command prompt shown as Figure 1-8, and press the Enter button.
Figure 1-8 Connecting to the Switch
3.Type the default user name and password admin/admin, then press the Enter button so as to enter User EXEC Mode.
Figure 1-9 Enter into the User EXEC Mode
Now you can manage your switch with CLI commands through Telnet connection.
4.Type enable command to enter Privileged EXEC Mode. A password that you have set through Console port connection is required. Here the password is set as 123.
8
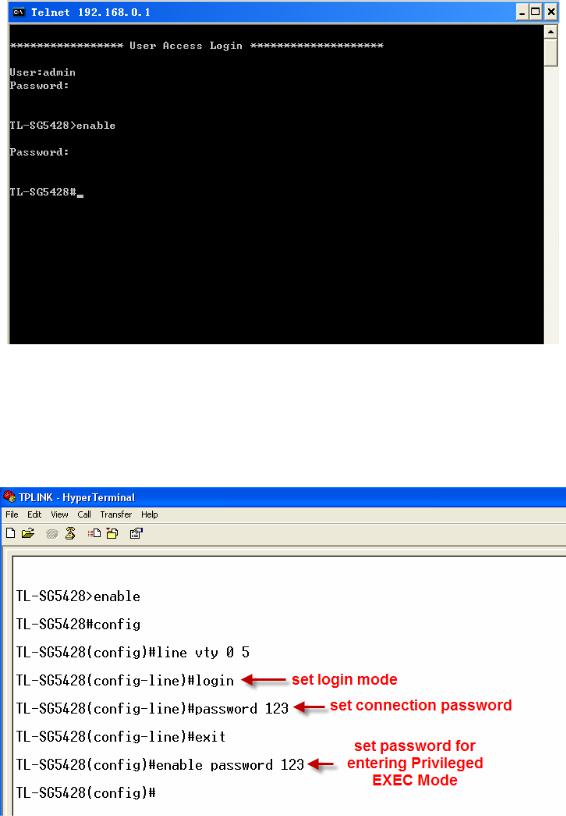
Figure 1-10 Enter into the Privileged EXEC Mode
Login Mode
Firstly configure the Telnet login mode as “login”, and both the connection password and the Privileged EXEC Mode password as 123 in the prompted DOS screen shown in Figure 1-11.
Figure 1-11 Configure login mode
Now, you can logon by Telnet in login mode:
1.Open Telnet, then type telnet 192.168.0.1 in the command prompt shown as Figure 1-12, and press the Enter button.
9
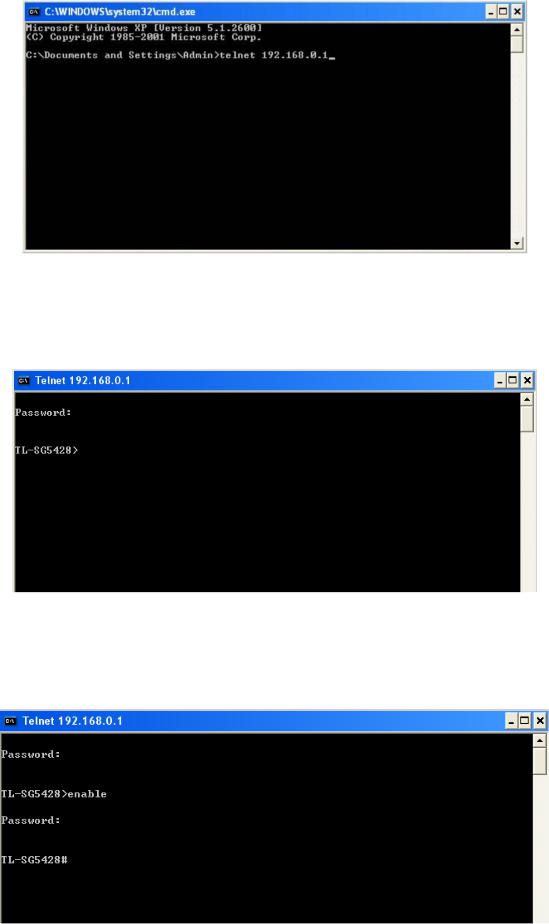
Figure 1-12 Connecting to the Switch
2.You are prompted to enter the connection password 123 you have set through Console port connection, and then you are in User EXEC Mode.
Figure 1-13 Enter into the User EXEC Mode
3.When entering enable command to access Privileged EXEC Mode, you are required to give the password 123 you have set through Console port connection.
Figure 1-14 Enter into the Privileged EXEC Mode
10

Now you can manage your switch with CLI commands through Telnet connection.
Note:
You can refer to Chapter 10 User Manage Commands for detailed commands information of the Telnet connection configuration.
1.2CLI Command Modes
The CLI is divided into different command modes: User EXEC Mode, Privileged EXEC Mode, Global Configuration Mode, Interface Configuration Mode and VLAN Configuration Mode. Interface Configuration Mode can also be divided into Interface gigabitEthernet, Interface link-aggregation and some other modes, which is shown as the following diagram.
The following table gives detailed information about the Accessing path, Prompt of each mode and how to exit the current mode and access the next mode.
|
Mode |
|
Accessing Path |
|
Prompt |
|
Logout or Access the next mode |
||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Use the exit command to disconnect the |
||
|
User EXEC |
|
Primary mode |
once it |
|
|
switch (except that |
the switch is |
|||
|
|
|
|
connected through the Console port). |
|||||||
|
Mode |
|
is connected |
with the |
|
TL-SG5428> |
|||||
|
|
switch. |
|
|
|
|
|
Use the enable command to access |
|||
|
|
|
|
|
|
|
|
||||
|
|
|
|
|
|
|
|
|
Privileged EXEC mode. |
|
|
|
|
|
|
|
|
|
|
|
|
||
|
Privileged |
|
Use |
the |
|
enable |
|
|
Enter the disable or exit command to |
||
|
|
command to enter this |
|
TL-SG5428# |
|
return to User EXEC mode. |
|||||
|
EXEC Mode |
|
mode from User EXEC |
|
|
Enter configure command to access |
|||||
|
|
|
|
|
|||||||
|
|
|
mode. |
|
|
|
|
|
|
Global Configuration mode. |
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
Use the exit or the end command or |
||
|
|
|
|
|
|
|
|
|
press Ctrl+Z to return to Privileged |
||
|
|
|
Use |
the |
configure |
|
|
EXEC mode. |
|
||
|
Global |
|
|
|
Use the interface gigabitEthernet port |
||||||
|
Configuration |
|
command to enter this |
|
TL-SG5428(config)# |
or interface range |
gigabitEthernet |
||||
|
|
mode |
from |
Privileged |
|
||||||
|
Mode |
|
|
|
port-list command to access interface |
||||||
|
|
EXEC mode. |
|
|
|
||||||
|
|
|
|
|
|
|
|
|
Configuration mode. |
|
|
|
|
|
|
|
|
|
|
|
Use the vlan vlan-list to access VLAN |
||
|
|
|
|
|
|
|
|
|
Configuration mode. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
11 |
|
|
|
|
|
Mode |
|
Accessing Path |
|
Prompt |
|
Logout or Access the next mode |
||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Use |
the |
interface |
|
|
|
Use the end command or press Ctrl+Z |
||
|
|
|
gigabitEthernet |
port |
|
|
|
||||
|
Interface |
|
or interface |
range |
|
TL-SG5428(config-if) |
|
to return to Privileged EXEC mode. |
|
||
|
|
|
|
Enter the exit or the # command |
to |
||||||
|
Configuration |
|
gigabitEthernet |
|
|
# or |
|
||||
|
|
port-list command to |
|
TL-SG5428(config-if- |
return to Global Configuration mode. |
|
|||||
|
Mode |
|
|
|
|||||||
|
|
enter |
this |
mode from |
|
range)# |
|
A port number must be specified in the |
|||
|
|
|
|
|
|||||||
|
|
|
Global |
Configuration |
|
|
|
interface command. |
|
||
|
|
|
mode. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
VLAN |
|
Use the vlan vlan-list |
|
|
|
Use the end command or press Ctrl+Z |
||||
|
|
TL-SG5428(config- |
to return to Privileged EXEC mode. |
|
|||||||
|
Configuration |
|
command to enter this |
|
|||||||
|
|
mode |
from |
Global |
|
vlan)# |
Enter the exit or the # command |
to |
|||
|
Mode |
|
|
||||||||
|
|
Configuration mode. |
|
|
|
return to Global configuration mode. |
|
||||
|
|
|
|
|
|
|
|||||
|
|
|
|
|
|
|
|
|
|
|
|
Note:
1.The user is automatically in User EXEC Mode after the connection between the PC and the switch is established by a console port or by a telnet connection.
2.Each command mode has its own set of specific commands. To configure some commands, you should access the corresponding command mode firstly.
Global Configuration Mode: In this mode, global commands are provided, such as the Spanning Tree, Schedule Mode and so on.
Interface Configuration Mode: In this mode, users can configure one or several ports, different ports corresponds to different commands
a). Interface gigabitEthernet: Configure parameters for an Ethernet port, such as Duplex-mode, flow control status.
b). Interface range gigabitEthernet: The commands contained are the same as that of the Interface Ethernet. Configure parameters for several Ethernet ports.
c). Interface link-aggregation: Configure parameters for a link-aggregation, such as broadcast storm.
d). Interface range link-aggregation: Configure parameters for multi-trunks. e). Interface vlan: Configure parameters for the vlan-port.
Vlan Configuration Mode: In this mode, users can create a VLAN and add a specified port to the VLAN.
3.Some commands are global, that means they can be performed in all modes:
show: Displays all information of switch, for example: statistic information, port information, VLAN information.
history: Displays the commands history.
12
1.3Security Levels
This switch’s security is divided into two levels: User level and Admin level.
User level only allows users to do some simple operations in User EXEC Mode; Admin level allows you to monitor, configure and manage the switch in Privileged EXEC Mode, Global Configuration Mode, Interface Configuration Mode and VLAN Configuration Mode.
Users get the privilege to the User level once connecting console port with the switch or logging in by Telnet. However, Guest users are restricted to access the CLI.
Users can enter Privileged EXEC mode from User EXEC mode by using the enable command. In default case, no password is needed. In Global Configuration Mode, you can configure password for Admin level by enable password command. Once password is configured, you are required to enter it to access Privileged EXEC mode.
1.4Conventions
1.4.1 Format Conventions
The following conventions are used in this Guide:
Items in square brackets [ ] are optional
Items in braces { } are required
Alternative items are grouped in braces and separated by vertical bars. For example: speed {10 | 100 | 1000 }
Bold indicates an unalterable keyword. For example: show logging
Normal Font indicates a constant (several options are enumerated and only one can be selected). For example: switchport type { access | trunk | general }
Italic Font indicates a variable (an actual value must be assigned). For example: bridge aging-time aging-time
1.4.2 Special Characters
You should pay attentions to the description below if the variable is a character string:
These six characters ” < > , \ & can not be input.
If a blank is contained in a character string, single or double quotation marks should be used, for example ’hello world’, ”hello world”, and the words in the quotation marks will be identified as a string. Otherwise, the words will be identified as several strings.
13
1.4.3 Parameter Format
Some parameters must be entered in special formats which are shown as follows:
MAC Address must be entered in the format of xx:xx:xx:xx:xx:xx
One or several values can be typed for a port-list or a vlan-list using comma to separate. Use a hyphen to designate a range of values, for instance 1, 3-5,7 indicates choosing 1,3,4,5,7.
The port number should format as 1/0/3, meaning unit/slot/port. The unit number is always 1, and slot number is always 0 and the port number is a variable (an actual value must be assigned).
14

Chapter 2 User Interface
enable
Description
The enable command is used to access Privileged EXEC Mode from User EXEC Mode.
Syntax
enable
Command Mode
User EXEC Mode
Example
If you have set the password to access Privileged EXEC Mode from User EXEC Mode:
TL-SG5428> enable
Enter password
TL-SG5428#
enable password
Description
The enable password command is used to set the password for users to access Privileged EXEC Mode from User EXEC Mode. To return to the default configuration, please use no enable password command.
Syntax
enable password password no enable password
Parameter
password —— super password which contains 16 characters at most, composing digits, English letters and underlines only. By default, it is empty.
Command Mode
Global Configuration Mode
Example
Set the super password as admin to access Privileged EXEC Mode from User EXEC Mode:
TL-SG5428(config)# enable password admin
15

disable
Description
The disable command is used to return to User EXEC Mode from Privileged EXEC Mode.
Syntax
disable
Command Mode
Privileged EXEC Mode
Example
Return to User EXEC Mode from Privileged EXEC Mode:
TL-SG5428# disable
TL-SG5428>
configure
Description
The configure command is used to access Global Configuration Mode from Privileged EXEC Mode.
Syntax
configure
Command Mode
Privileged EXEC Mode
Example
Access Global Configuration Mode from Privileged EXEC Mode:
TL-SG5428# configure
TL-SG5428(config)#
exit
Description
The exit command is used to return to the previous Mode from the current
Mode.
Syntax
exit
16

Command Mode
Privileged EXEC Mode and Any Configuration Mode
Example
Return to Global Configuration Mode from Interface Configuration Mode, and then return to Privileged EXEC Mode:
TL-SG5428 (config-if)# exit
TL-SG5428(config)# exit
TL-SG5428#
end
Description
The end command is used to return to Privileged EXEC Mode.
Syntax
end
Command Mode
Any Configuration Mode
Example
Return to Privileged EXEC Mode from Interface Configuration Mode:
TL-SG5428(config-if)# end
TL-SG5428#
17
 Loading...
Loading...