TP-LINK TL-SG3109, TL-SG3452 User Manual


TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
Table of Contents
Section 1. Using the CLI..................................................................................................... |
10 |
||
1.1 |
CLI Command Modes............................................................................................................. |
10 |
|
|
1.1.1 |
Introduction............................................................................................................................... |
10 |
|
1.1.2 |
User EXEC Mode ..................................................................................................................... |
11 |
|
1.1.3 |
Privileged EXEC Mode ............................................................................................................. |
11 |
|
1.1.4 |
Global Configuration Mode....................................................................................................... |
12 |
|
1.1.5 Interface Configuration and Specific Configuration Modes ...................................................... |
12 |
|
1.2 |
Starting the CLI....................................................................................................................... |
13 |
|
1.3 |
Editing Features ..................................................................................................................... |
14 |
|
|
1.3.1 |
Entering Commands................................................................................................................. |
14 |
Section 2. |
AAA Commands ................................................................................................ |
17 |
|
aaa authentication login ........................................................................................................ |
17 |
||
aaa authentication enable..................................................................................................... |
19 |
||
login authentication ............................................................................................................... |
21 |
||
enable authentication............................................................................................................ |
22 |
||
ip http authentication............................................................................................................. |
23 |
||
ip https authentication ........................................................................................................... |
24 |
||
show authentication methods ............................................................................................... |
25 |
||
password............................................................................................................................... |
|
26 |
|
enable password................................................................................................................... |
27 |
||
username .............................................................................................................................. |
|
28 |
|
Section 3. Address Table Commands ................................................................................ |
29 |
||
bridge address ...................................................................................................................... |
29 |
||
bridge multicast filtering ........................................................................................................ |
30 |
||
bridge multicast address ....................................................................................................... |
31 |
||
bridge multicast forbidden address ....................................................................................... |
32 |
||
bridge multicast forward-all ................................................................................................... |
33 |
||
bridge multicast forbidden forward-all ................................................................................... |
34 |
||
bridge aging-time .................................................................................................................. |
35 |
||
clear bridge |
........................................................................................................................... |
36 |
|
port security .......................................................................................................................... |
37 |
||
port security routed secure-address ..................................................................................... |
38 |
||
show bridge address-table.................................................................................................... |
39 |
||
show bridge address-table static .......................................................................................... |
40 |
||
show bridge address-table count .......................................................................................... |
41 |
||
show bridge multicast address-table..................................................................................... |
42 |
||
show bridge multicast filtering............................................................................................... |
44 |
||
Page 1

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide |
|
show ports security ............................................................................................................... |
45 |
Section 4. Clock.................................................................................................................. |
47 |
clock set ................................................................................................................................ |
47 |
clock source .......................................................................................................................... |
48 |
clock timezone ...................................................................................................................... |
49 |
clock summer-time................................................................................................................ |
50 |
sntp authentication-key ......................................................................................................... |
52 |
sntp authenticate................................................................................................................... |
53 |
sntp trusted-key .................................................................................................................... |
54 |
sntp client poll timer .............................................................................................................. |
55 |
sntp broadcast client enable ................................................................................................. |
56 |
sntp anycast client enable..................................................................................................... |
57 |
sntp client enable (Interface)................................................................................................. |
58 |
sntp unicast client enable...................................................................................................... |
59 |
sntp unicast client poll........................................................................................................... |
60 |
sntp server ............................................................................................................................ |
61 |
show clock ............................................................................................................................ |
62 |
show sntp configuration ........................................................................................................ |
63 |
show sntp status ................................................................................................................... |
64 |
Section 5. Configuration and Image Files........................................................................... |
65 |
copy ...................................................................................................................................... |
65 |
delete .................................................................................................................................... |
68 |
delete startup-config ............................................................................................................. |
69 |
show running-config.............................................................................................................. |
70 |
show startup-config............................................................................................................... |
71 |
Section 6. Ethernet Configuration Commands ................................................................... |
72 |
interface ethernet .................................................................................................................. |
72 |
interface range ethernet........................................................................................................ |
73 |
shutdown............................................................................................................................... |
74 |
description............................................................................................................................. |
75 |
speed .................................................................................................................................... |
76 |
duplex ................................................................................................................................... |
77 |
negotiation ............................................................................................................................ |
78 |
flowcontrol............................................................................................................................. |
79 |
mdix ...................................................................................................................................... |
80 |
back-pressure ....................................................................................................................... |
81 |
clear counters ....................................................................................................................... |
82 |
set interface active ................................................................................................................ |
83 |
show interfaces advertise ..................................................................................................... |
84 |
Page 2 |
|

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
show interfaces configuration ............................................................................................... |
86 |
show interfaces status .......................................................................................................... |
87 |
show interfaces description................................................................................................... |
89 |
show interfaces counters ...................................................................................................... |
90 |
port storm-control include-multicast ...................................................................................... |
93 |
port storm-control broadcast enable ..................................................................................... |
94 |
port storm-control broadcast rate.......................................................................................... |
95 |
show ports storm-control....................................................................................................... |
96 |
Section 7. GVRP Commands ............................................................................................. |
97 |
gvrp enable (Global) ............................................................................................................. |
97 |
gvrp enable (Interface).......................................................................................................... |
98 |
garp timer.............................................................................................................................. |
99 |
gvrp vlan-creation-forbid ..................................................................................................... |
100 |
gvrp registration-forbid ........................................................................................................ |
101 |
clear gvrp statistics ............................................................................................................. |
102 |
show gvrp configuration ...................................................................................................... |
103 |
show gvrp statistics............................................................................................................. |
104 |
show gvrp error-statistics .................................................................................................... |
105 |
Section 8. IGMP Snooping Commands............................................................................ |
106 |
ip igmp snooping (Global) ................................................................................................... |
106 |
ip igmp snooping (Interface) ............................................................................................... |
107 |
ip igmp snooping host-time-out........................................................................................... |
108 |
ip igmp snooping mrouter-time-out ..................................................................................... |
109 |
ip igmp snooping leave-time-out ......................................................................................... |
110 |
show ip igmp snooping mrouter .......................................................................................... |
111 |
show ip igmp snooping interface......................................................................................... |
112 |
show ip igmp snooping groups ........................................................................................... |
113 |
Section 9. IP Addressing Commands............................................................................... |
114 |
ip address ........................................................................................................................... |
114 |
ip address dhcp................................................................................................................... |
115 |
ip default-gateway............................................................................................................... |
116 |
show ip interface ................................................................................................................. |
117 |
arp....................................................................................................................................... |
118 |
arp timeout .......................................................................................................................... |
119 |
clear arp-cache ................................................................................................................... |
120 |
show arp ............................................................................................................................. |
121 |
ip domain-name .................................................................................................................. |
122 |
ip name-server .................................................................................................................... |
123 |
ip host ................................................................................................................................. |
124 |
Page 3

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide |
|
clear host ............................................................................................................................ |
125 |
clear host dhcp.................................................................................................................... |
126 |
show hosts .......................................................................................................................... |
127 |
Section 10. LACP Commands............................................................................................ |
128 |
lacp system-priority ............................................................................................................. |
128 |
lacp port-priority .................................................................................................................. |
129 |
lacp timeout......................................................................................................................... |
130 |
show lacp ethernet.............................................................................................................. |
131 |
show lacp port-channel ....................................................................................................... |
133 |
Section 11. Line Commands .............................................................................................. |
134 |
line ...................................................................................................................................... |
134 |
speed .................................................................................................................................. |
135 |
exec-timeout ....................................................................................................................... |
136 |
history ................................................................................................................................. |
137 |
history size .......................................................................................................................... |
138 |
terminal history.................................................................................................................... |
139 |
terminal history size ............................................................................................................ |
140 |
show line ............................................................................................................................. |
141 |
Section 12. Management ACL............................................................................................ |
142 |
management access-list ..................................................................................................... |
142 |
permit (Management).......................................................................................................... |
144 |
deny (Management)............................................................................................................ |
145 |
management access-class ................................................................................................. |
146 |
show management access-list............................................................................................ |
147 |
show management access-class ........................................................................................ |
148 |
Section 13. PHY Diagnostics Commands |
.......................................................................... 149 |
test copper-port tdr.............................................................................................................. |
149 |
show copper-ports tdr ......................................................................................................... |
150 |
show copper-ports cable-length.......................................................................................... |
151 |
show fiber-ports optical-transceiver .................................................................................... |
152 |
Section 14. Port Channel Commands ................................................................................ |
153 |
interface port-channel ......................................................................................................... |
153 |
interface range port-channel ............................................................................................... |
154 |
channel-group ..................................................................................................................... |
155 |
show interfaces port-channel .............................................................................................. |
156 |
|
Page 4 |

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
Section 15. Port Monitor Commands.................................................................................. |
157 |
port monitor......................................................................................................................... |
157 |
port monitor vlan-tagging .................................................................................................... |
158 |
show ports monitor.............................................................................................................. |
159 |
Section 16. QoS Commands.............................................................................................. |
160 |
qos ...................................................................................................................................... |
160 |
show qos............................................................................................................................. |
161 |
priority-queue out num-of-queues....................................................................................... |
162 |
show qos interface .............................................................................................................. |
163 |
traffic-shape ........................................................................................................................ |
165 |
wrr-queue cos-map ............................................................................................................. |
166 |
qos map dscp-queue .......................................................................................................... |
167 |
qos trust (Global) ................................................................................................................ |
168 |
qos trust (Interface)............................................................................................................. |
169 |
qos cos................................................................................................................................ |
170 |
show qos map..................................................................................................................... |
171 |
Section 17. Radius Commands.......................................................................................... |
172 |
radius-server host ............................................................................................................... |
172 |
radius-server key ................................................................................................................ |
174 |
radius-server retransmit ...................................................................................................... |
175 |
radius-server source-ip ....................................................................................................... |
176 |
radius-server timeout .......................................................................................................... |
177 |
radius-server deadtime ....................................................................................................... |
178 |
show radius-servers............................................................................................................ |
179 |
Section 18. RMON Commands .......................................................................................... |
180 |
show rmon statistics............................................................................................................ |
180 |
rmon collection history ........................................................................................................ |
182 |
show rmon collection history............................................................................................... |
183 |
show rmon history............................................................................................................... |
184 |
rmon alarm.......................................................................................................................... |
187 |
show rmon alarm ................................................................................................................ |
189 |
rmon event .......................................................................................................................... |
191 |
show rmon events............................................................................................................... |
192 |
show rmon log..................................................................................................................... |
193 |
rmon table-size ................................................................................................................... |
195 |
Page 5

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide |
|
Section 19. SNMP Commands........................................................................................... |
196 |
snmp-server community...................................................................................................... |
196 |
snmp-server view................................................................................................................ |
198 |
snmp-server group.............................................................................................................. |
199 |
snmp-server user ................................................................................................................ |
200 |
snmp-server engineID local ................................................................................................ |
202 |
snmp-server enable traps ................................................................................................... |
204 |
snmp-server filter ................................................................................................................ |
205 |
snmp-server host ................................................................................................................ |
206 |
snmp-server v3-host ........................................................................................................... |
207 |
snmp-server trap authentication ......................................................................................... |
208 |
snmp-server contact ........................................................................................................... |
209 |
snmp-server location........................................................................................................... |
210 |
snmp-server set .................................................................................................................. |
211 |
show snmp.......................................................................................................................... |
212 |
show snmp engineid ........................................................................................................... |
214 |
show snmp views................................................................................................................ |
215 |
show snmp groups.............................................................................................................. |
216 |
show snmp filters ................................................................................................................ |
218 |
show snmp users ................................................................................................................ |
219 |
Section 20. Spanning-Tree Commands ............................................................................. |
220 |
spanning-tree ...................................................................................................................... |
220 |
spanning-tree mode ............................................................................................................ |
221 |
spanning-tree forward-time ................................................................................................. |
222 |
spanning-tree hello-time ..................................................................................................... |
223 |
spanning-tree max-age ....................................................................................................... |
224 |
spanning-tree priority .......................................................................................................... |
225 |
spanning-tree disable.......................................................................................................... |
226 |
spanning-tree cost .............................................................................................................. |
227 |
spanning-tree port-priority................................................................................................... |
228 |
spanning-tree portfast ......................................................................................................... |
229 |
spanning-tree link-type........................................................................................................ |
230 |
spanning-tree pathcost method .......................................................................................... |
231 |
spanning-tree bpdu ............................................................................................................. |
232 |
clear spanning-tree detected-protocols............................................................................... |
233 |
spanning-tree guard root..................................................................................................... |
234 |
spanning-tree mst priority ................................................................................................... |
235 |
spanning-tree mst max-hops .............................................................................................. |
236 |
spanning-tree mst port-priority ............................................................................................ |
237 |
spanning-tree mst cost........................................................................................................ |
238 |
spanning-tree mst configuration.......................................................................................... |
239 |
instance (mst) ..................................................................................................................... |
240 |
|
Page 6 |

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
name (mst).......................................................................................................................... |
241 |
revision (mst) ...................................................................................................................... |
242 |
show (mst) .......................................................................................................................... |
243 |
exit (mst) ............................................................................................................................. |
244 |
abort (mst)........................................................................................................................... |
245 |
show spanning-tree............................................................................................................. |
246 |
Section 21. Syslog Commands .......................................................................................... |
248 |
logging on ........................................................................................................................... |
248 |
logging ................................................................................................................................ |
249 |
logging console ................................................................................................................... |
250 |
logging buffered .................................................................................................................. |
251 |
logging buffered size........................................................................................................... |
252 |
clear logging........................................................................................................................ |
253 |
logging file........................................................................................................................... |
254 |
clear logging file .................................................................................................................. |
255 |
aaa logging ......................................................................................................................... |
256 |
file-system logging .............................................................................................................. |
257 |
management logging .......................................................................................................... |
258 |
show logging ....................................................................................................................... |
259 |
show logging file ................................................................................................................. |
261 |
show syslog-servers ........................................................................................................... |
263 |
Section 22. System Management....................................................................................... |
264 |
ping ..................................................................................................................................... |
264 |
traceroute............................................................................................................................ |
266 |
reload .................................................................................................................................. |
268 |
hostname ............................................................................................................................ |
269 |
show users.......................................................................................................................... |
270 |
show system ....................................................................................................................... |
271 |
show version ....................................................................................................................... |
272 |
show system id ................................................................................................................... |
273 |
system language web.......................................................................................................... |
274 |
Section 23. User Interface .................................................................................................. |
275 |
enable ................................................................................................................................. |
275 |
disable................................................................................................................................. |
276 |
login .................................................................................................................................... |
277 |
configure ............................................................................................................................. |
278 |
exit (Configuration).............................................................................................................. |
279 |
exit ...................................................................................................................................... |
280 |
Page 7

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide |
|
end....................................................................................................................................... |
281 |
help...................................................................................................................................... |
282 |
terminal data-dump ............................................................................................................. |
283 |
show history ........................................................................................................................ |
284 |
show privilege ..................................................................................................................... |
285 |
Section 24. VLAN Commands............................................................................................ |
286 |
vlan database...................................................................................................................... |
286 |
vlan ..................................................................................................................................... |
287 |
interface vlan....................................................................................................................... |
288 |
interface range vlan ............................................................................................................ |
289 |
name ................................................................................................................................... |
290 |
switchport mode.................................................................................................................. |
291 |
switchport access vlan ........................................................................................................ |
292 |
switchport trunk allowed vlan .............................................................................................. |
293 |
switchport trunk native vlan................................................................................................. |
294 |
switchport general allowed vlan .......................................................................................... |
295 |
switchport general pvid ....................................................................................................... |
296 |
switchport general ingress-filtering disable ......................................................................... |
297 |
switchport general acceptable-frame-type tagged-only ...................................................... |
298 |
switchport forbidden vlan .................................................................................................... |
299 |
switchport protected............................................................................................................ |
300 |
ip internal-usage-vlan.......................................................................................................... |
301 |
show vlan ............................................................................................................................ |
302 |
show vlan internal usage .................................................................................................... |
303 |
show interfaces switchport.................................................................................................. |
304 |
Section 25. Web Server...................................................................................................... |
307 |
ip http server ....................................................................................................................... |
307 |
ip http exec-timeout.............................................................................................................. |
308 |
ip https server ..................................................................................................................... |
309 |
ip http port ........................................................................................................................... |
310 |
ip https port ......................................................................................................................... |
311 |
show ip http......................................................................................................................... |
312 |
Section 26. 802.1x Commands .......................................................................................... |
313 |
aaa authentication dot1x..................................................................................................... |
313 |
dot1x system-auth-control................................................................................................... |
314 |
dot1x port-control ................................................................................................................ |
315 |
dot1x re-authentication ....................................................................................................... |
316 |
Page 8

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
dot1x timeout re-authperiod ................................................................................................ |
317 |
dot1x re-authenticate .......................................................................................................... |
318 |
dot1x timeout quiet-period .................................................................................................. |
319 |
dot1x timeout tx-period ....................................................................................................... |
320 |
dot1x max-req ..................................................................................................................... |
321 |
dot1x timeout supp-timeout................................................................................................. |
322 |
dot1x timeout server-timeout .............................................................................................. |
323 |
show dot1x.......................................................................................................................... |
324 |
show dot1x users ................................................................................................................ |
327 |
show dot1x statistics ........................................................................................................... |
329 |
ADVANCED FEATURES.................................................................................................... |
331 |
dot1x auth-not-req............................................................................................................... |
331 |
dot1x multiple-hosts ............................................................................................................ |
332 |
dot1x single-host-violation .................................................................................................. |
333 |
dot1x guest-vlan.................................................................................................................. |
334 |
dot1x guest-vlan enable...................................................................................................... |
335 |
show dot1x advanced ......................................................................................................... |
336 |
Troubleshooting .................................................................................................................. |
338 |
Page 9
TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
Section 1. Using the CLI
This chapter describes how to start using the CLI and describes implemented command editing features to assist in using the CLI.
1.1CLI Command Modes
1.1.1Introduction
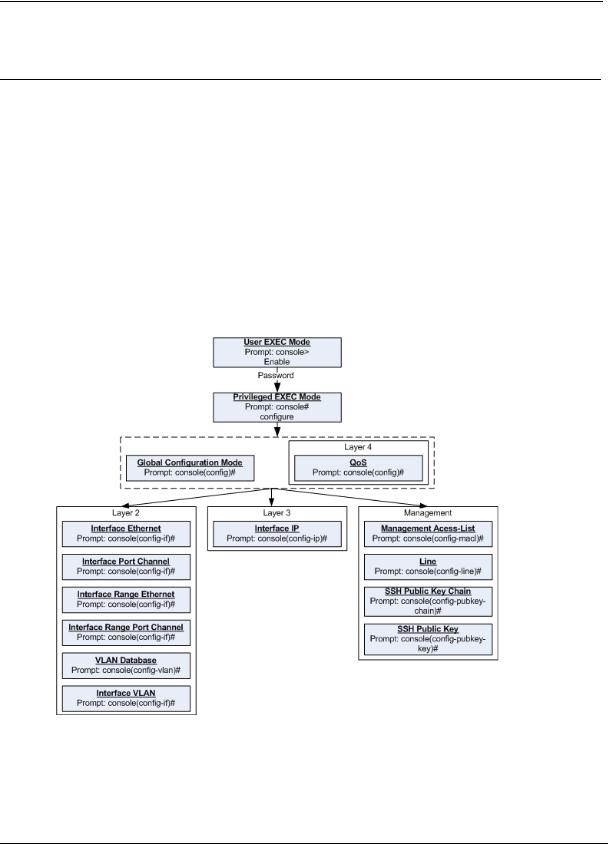
To assist in configuring the device, the Command Line Interface (CLI) is divided into different command modes. Each command mode has its own set of specific commands. Entering a question mark "?" at the system prompt (console prompt) displays a list of commands available for that particular command mode.
From each mode, a specific command is used to navigate from one command mode to another. The standard order to access the modes is as follows: User EXEC mode, Privileged EXEC mode, Global Configuration mode, and Interface Configuration mode. The following figure illustrates the command mode access path.
When starting a session, the initial mode is the User EXEC mode. Only a limited subset of commands is available in User EXEC mode. This level is reserved for tasks that do not change the configuration. To enter the next level, the Privileged EXEC mode, a password is required.
The Privileged EXEC mode gives access to commands that are restricted on User EXEC mode and provides access to the device Configuration mode.
Page 10
TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
The Global Configuration mode manages the device configuration on a global level.
The Interface Configuration mode configures specific interfaces in the device.
1.1.2User EXEC Mode
After logging into the device, the user is automatically in User EXEC command mode unless the user is defined as a privileged user. In general, the User EXEC commands allow the user to perform basic tests, and list system information.
The user-level prompt consists of the device host name followed by the angle bracket (>).
Console>
The default host name is Console unless it has been changed using the hostname command in the Global Configuration mode.
1.1.3Privileged EXEC Mode
Privileged access is password protected to prevent unauthorized use because many of the privileged commands set operating system parameters. The password is not displayed on the screen and is case sensitive.
Privileged users enter directly into the Privileged EXEC mode. To enter the Privileged EXEC mode from the User EXEC mode, perform the following steps:
1.At the prompt enter the enable command and press <Enter>. A password prompt is displayed.
2.Enter the password and press <Enter>. The password is displayed as *. The Privileged EXEC mode prompt is displayed. The Privileged EXEC mode prompt consists of the device host name followed by #.
Console#
To return from the Privileged EXEC mode to the User EXEC mode, use the disable command. The following example illustrates how to access the Privileged EXEC mode and return to the User EXEC mode:
Console> enable
Enter Password: ******
Console#
Console# disable
Console>
The exit command is used to return from any mode to the previous mode except when returning to the User EXEC mode from the Privileged EXEC mode. For example, the exit command is used to return from the Interface Configuration mode to the Global Configuration mode.
Page 11
TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
1.1.4Global Configuration Mode
Global Configuration mode commands apply to features that affect the system as a whole, rather than just a specific interface. The configure Privileged EXEC mode command is used to enter the Global Configuration mode.
To enter the Global Configuration mode perform the following steps:
1.At the Privileged EXEC mode prompt enter the configure command and press <Enter>. The Global Configuration mode prompt is displayed. The Global Configuration mode prompt consists of the device host name followed by (config) and #.
Console(config)#
To return from the Global Configuration mode to the Privileged EXEC mode, the user can use one of the following commands:
•exit
•end
•<Ctrl+Z>
The following example illustrates how to access the Global Configuration mode and return to the Privileged EXEC mode:
Console#
Console# configure
Console(config)# exit
Console#
1.1.5Interface Configuration and Specific Configuration Modes
Interface Configuration mode commands modify specific interface operations. The following are the Interface Configuration modes:
•Line Interface — Contains commands to configure the management connections. These include commands such as line timeout settings, etc. The line Global Configuration mode command is used to enter the Line Configuration command mode.
•VLAN Database — Contains commands to create a VLAN as a whole. The vlan database Global Configuration mode command is used to enter the VLAN Database Interface Configuration mode.
•Management Access List — Contains commands to define management access-lists. The management access-list Global Configuration mode command is used to enter the Management Access List Configuration mode.
•Ethernet — Contains commands to manage port configuration. The interface ethernet Global Configuration mode command is used to enter the Interface Configuration mode to configure an Ethernet type interface.
•Port Channel — Contains commands to configure port-channels, for example, assigning ports to a portchannel. Most of these commands are the same as the commands in the Ethernet interface mode, and are used to manage the member ports as a single entity. The interface port-channel Global Configuration mode command is used to enter the Port Channel Interface Configuration mode.
•SSH Public Key-chain — Contains commands to manually specify other device SSH public keys. The crypto key pubkey-chain ssh Global Configuration mode command is used to enter the SSH Public Keychain Configuration mode.
•QoS — Contains commands related to service definitions. The qos Global Configuration mode command is used to enter the QoS services configuration mode.
Page 12

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
•MAC Access-List — Configures conditions required to allow traffic based on MAC addresses. The mac access-list Global Configuration mode command is used to enter the MAC access-list configuration mode..
1.2Starting the CLI
The device can be managed over a direct connection to the device console port or via a Telnet connection. The device is managed by entering command keywords and parameters at the prompt. Using the device commandline interface (CLI) is very similar to entering commands on a UNIX system.
If access is via a Telnet connection, ensure that the device has a defined IP address, corresponding management access is granted, and the workstation used to access the device is connected to the device prior to using CLI commands.
Note
The following steps are for use on the console line only.
To start using the CLI, perform the following steps:
1.Connect the DB9 null-modem or cross over cable to the RS-232 serial port of the device to the RS-232 serial port of the terminal or computer running the terminal emulation application.
Note
The default data rate is 38400.
a)Set the data format to 8 data bits, 1 stop bit, and no parity.
b)Set Flow Control to none.
c)Under Properties, select VT100 for Emulation mode.
d)Select Terminal keys for Function, Arrow, and Ctrl keys. Ensure that the setting is for Terminal keys (not Windows keys).
Note
When using HyperTerminal with Microsoft® Windows 2000,ensure that Windows® 2000 Service Pack 2 or later is installed.With Windows 2000 Service Pack 2, the arrow keys function properly in HyperTerminal’s VT100 emulation. Go to www.microsoft.com for information on Windows 2000 service packs.
2.Enter the following commands to begin the configuration procedure:
Console> enable
Console# configure
Console(config)#
3.Configure the device and enter the necessary commands to complete the required tasks.
4.When finished, exit the session with the exit command.
When a different user is required to log onto the system, use the login Privileged EXEC mode command. This effectively logs off the current user and logs on the new user.
Page 13

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
1.3Editing Features
1.3.1Entering Commands
A CLI command is a series of keywords and arguments. Keywords identify a command, and arguments specify configuration parameters. For example, in the command show interfaces status ethernet e8, show, interfaces and status are keywords, ethernet is an argument that specifies the interface type, and 8 specifies the port.
To enter commands that require parameters, enter the required parameters after the command keyword. For example, to set a password for the administrator, enter:
Console(config)# username admin password smith
When working with the CLI, the command options are not displayed. The command is not selected from a menu, but is manually entered. To see what commands are available in each mode or within an interface configuration, the CLI does provide a method of displaying the available commands, the command syntax requirements and in some instances parameters required to complete the command. The standard command to request help is ?.
There are two instances where help information can be displayed:
•Keyword lookup — The character ? is entered in place of a command. A list of all valid commands and corresponding help messages are is displayed.
•Partial keyword lookup — If a command is incomplete and or the character ? is entered in place of a parameter. The matched keyword or parameters for this command are displayed.
To assist in using the CLI, there is an assortment of editing features. The following features are described:
•Terminal Command Buffer
•Command Completion
•Keyboard Shortcuts
1.3.1.1Terminal Command Buffer
Every time a command is entered in the CLI, it is recorded on an internally managed Command History buffer. Commands stored in the buffer are maintained on a First In First Out (FIFO) basis. These commands can be recalled, reviewed, modified, and reissued. This buffer is not preserved across device resets.
Keyword |
Description |
|
|
Up-arrow key |
Recalls commands in the history buffer, beginning with the most recent com- |
Ctrl+P |
mand. Repeats the key sequence to recall successively older commands. |
|
|
Down-arrow key |
Returns to more recent commands in the history buffer after recalling com- |
|
mands with the up-arrow key. Repeating the key sequence will recall succes- |
|
sively more recent commands. |
By default, the history buffer system is enabled, but it can be disabled at any time. For information about the command syntax to enable or disable the history buffer, see history.
There is a standard default number of commands that are stored in the buffer. The standard number of 10 commands can be increased to 216. By configuring 0, the effect is the same as disabling the history buffer system. For information about the command syntax for configuring the command history buffer, see history size.
To display the history buffer, see show history.
Page 14

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
1.3.1.2Negating the Effect of Commands
For many configuration commands, the prefix keyword no can be entered to cancel the effect of a command or reset the configuration to the default value. This guide describes the negation effect for all applicable commands.
1.3.1.3Command Completion
If the command entered is incomplete, invalid or has missing or invalid parameters, then the appropriate error message is displayed. This assists in entering the correct command. By pressing the <Tab> button, an incomplete command is entered. If the characters already entered are not enough for the system to identify a single matching command, press ? to display the available commands matching the characters already entered.
1.3.1.4Keyboard Shortcuts
The CLI has a range of keyboard shortcuts to assist in editing the CLI commands. The following table describes the CLI shortcuts.
Keyboard Key |
Description |
|
|
Up-arrow key |
Recalls commands from the history buffer, beginning with the most recent command. |
|
Repeat the key sequence to recall successively older commands. |
|
|
Down-arrow key |
Returns the most recent commands from the history buffer after recalling commands with |
|
the up arrow key. Repeating the key sequence will recall successively more recent com- |
|
mands. |
|
|
Ctrl+A |
Moves the cursor to the beginning of the command line. |
|
|
Ctrl+E |
Moves the cursor to the end of the command line. |
|
|
Ctrl+Z / End |
Returns back to the Privileged EXEC mode from any configuration mode. |
|
|
Backspace key |
Deletes one character left to the cursor position. |
|
|
1.3.1.5CLI Command Conventions
When entering commands there are certain command entry standards that apply to all commands. The following table describes the command conventions.
Convention |
Description |
|
|
[ ] |
In a command line, square brackets indicates an optional entry. |
|
|
{ } |
In a command line, curly brackets indicate a selection of compulsory parameters sepa- |
|
rated by the | character. One option must be selected. For example: flowcontrol |
|
{auto|on|off} means that for the flowcontrol command either auto, on or off must be |
|
selected. |
|
|
Italic font |
Indicates a parameter. |
|
|
<Enter> |
Any individual key on the keyboard. For example click <Enter>. |
|
|
Ctrl+F4 |
Any combination keys pressed simultaneously on the keyboard. |
|
|
Page 15
TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
Screen Display |
Indicates system messages and prompts appearing on the console. |
all |
When a parameter is required to define a range of ports or parameters and all is an |
|
option, the default for the command is all when no parameters are defined. For exam- |
|
ple, the command interface range port-channel has the option of either entering a |
|
range of channels, or selecting all. When the command is entered without a parameter, |
|
it automatically defaults to all. |
_______________________________________________________________________________________
Page 16

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
Section 2. AAA Commands
aaa authentication login
The aaa authentication login Global Configuration mode command defines login authentication. To return to the default configuration, use the no form of this command.
Syntax
aaa authentication login {default | list-name} method1 [method2...] no aaa authentication login {default | list-name}
Parameters
•default — Uses the listed authentication methods that follow this argument as the default list of methods when a user logs in.
•list-name — Character string used to name the list of authentication methods activated when a user logs in. (Range: 1-12 characters).
•method1 [method2...] — Specify at least one from the following table:
Keyword |
Description |
|
|
enable |
Uses the enable password for authentication. |
|
|
line |
Uses the line password for authentication. |
|
|
local |
Uses the local username database for authentication. |
|
|
none |
Uses no authentication. |
|
|
radius |
Uses the list of all RADIUS servers for authentication. |
|
|
Default Configuration
The local user database is checked. This has the same effect as the command aaa authentication login listname local.
Note
On the console, login succeeds without any authentication check if the authentication method is not defined.
Command Mode
Global Configuration mode
Page 17

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
User Guidelines
The default and optional list names created with the aaa authentication login command are used with the login authentication command.
Create a list by entering the aaa authentication login list-name method command for a particular protocol, where list-name is any character string used to name this list. The method argument identifies the list of methods that the authentication algorithm tries, in the given sequence.
The additional methods of authentication are used only if the previous method returns an error, not if it fails. To ensure that the authentication succeeds even if all methods return an error, specify none as the final method in the command line.
Example
The following example configures the authentication login.
Console(config)# aaa authentication login default radius local enable none
Page 18

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
aaa authentication enable
The aaa authentication enable Global Configuration mode command defines authentication method lists for accessing higher privilege levels. To return to the default configuration, use the no form of this command.
Syntax
aaa authentication enable {default | list-name} method1 [method2...] no aaa authentication enable {default | list-name}
Parameters
•default — Uses the listed authentication methods that follow this argument as the default list of methods, when using higher privilege levels.
•list-name — Character string used to name the list of authentication methods activated, when using access higher privilege levels (Range: 1-12 characters).
•method1 [method2...] — Specify at least one from the following table:
Keyword |
Description |
|
|
enable |
Uses the enable password for authentication. |
|
|
line |
Uses the line password for authentication. |
|
|
none |
Uses no authentication. |
|
|
radius |
Uses the list of all RADIUS servers for authentication. Uses username $enabx$., |
|
where x is the privilege level. |
|
|
Default Configuration
If the default list is not set, only the enable password is checked. This has the same effect as the command aaa authentication enable default enable.
On the console, the enable password is used if it exists. If no password is set, the process still succeeds. This has the same effect as using the command aaa authentication enable default enable none.
Command Mode
Global Configuration mode
User Guidelines
The default and optional list names created with the aaa authentication enable command are used with the enable authentication command.
The additional methods of authentication are used only if the previous method returns an error, not if it fails. To ensure that the authentication succeeds even if all methods return an error, specify none as the final method in the command line.
All aaa authentication enable default requests sent by the device to a RADIUS server include the username $enabx$., where x is the requested privilege level.
Page 19

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
Example
The following example sets the enable password for authentication when accessing higher privilege levels.
Console(config)# aaa authentication enable default enable
Page 20
TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
login authentication
The login authentication Line Configuration mode command specifies the login authentication method list for a remote telnet or console. To return to the default configuration specified by the aaa authentication login command, use the no form of this command.
Syntax
login authentication {default | list-name} no login authentication
Parameters
•default — Uses the default list created with the aaa authentication login command.
•list-name — Uses the indicated list created with the aaa authentication login command.
Default Configuration
Uses the default set with the command aaa authentication login.
Command Mode
Line Configuration mode
User Guidelines
Changing login authentication from default to another value may disconnect the telnet session.
Example
The following example specifies the default authentication method for a console.
Console(config)# line console
Console(config-line)# login authentication default
Page 21
TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
enable authentication
The enable authentication Line Configuration mode command specifies the authentication method list when accessing a higher privilege level from a remote telnet or console. To return to the default configuration specified by the aaa authentication enable command, use the no form of this command.
Syntax
enable authentication {default | list-name} no enable authentication
Parameters
•default — Uses the default list created with the aaa authentication enable command.
•list-name — Uses the indicated list created with the aaa authentication enable command.
Default Configuration
Uses the default set with the aaa authentication enable command.
Command Mode
Line Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example specifies the default authentication method when accessing a higher privilege level from a console.
Console(config)# line console
Console(config-line)# enable authentication default
Page 22

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
ip http authentication
The ip http authentication Global Configuration mode command specifies authentication methods for HTTP server users. To return to the default configuration, use the no form of this command.
Syntax
ip http authentication method1 [method2...] no ip http authentication
Parameters
•method1 [method2...] — Specify at least one from the following table:
Keyword |
Description |
|
|
local |
Uses the local username database for authentication. |
|
|
none |
Uses no authentication. |
|
|
radius |
Uses the list of all RADIUS servers for authentication. |
|
|
Default Configuration
The local user database is checked. This has the same effect as the command ip http authentication local.
Command Mode
Global Configuration mode
User Guidelines
The additional methods of authentication are used only if the previous method returns an error, not if it fails. To ensure that the authentication succeeds even if all methods return an error, specify none as the final method in the command line.
Example
The following example configures the HTTP authentication.
Console(config)# ip http authentication radius local
Page 23

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
ip https authentication
The ip https authentication Global Configuration mode command specifies authentication methods for HTTPS server users. To return to the default configuration, use the no form of this command.
Syntax
ip https authentication method1 [method2...] no ip https authentication
Parameters
•method1 [method2...] — Specify at least one from the following table:
Keyword |
Source or destination |
|
|
local |
Uses the local username database for authentication. |
|
|
none |
Uses no authentication. |
|
|
radius |
Uses the list of all RADIUS servers for authentication. |
|
|
Default Configuration
The local user database is checked. This has the same effect as the command ip https authentication local.
Command Mode
Global Configuration mode
User Guidelines
The additional methods of authentication are used only if the previous method returns an error, not if it fails. To ensure that the authentication succeeds even if all methods return an error, specify none as the final method in the command line.
Example
The following example configures HTTPS authentication.
Console(config)# ip https authentication radius local
Page 24
TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
show authentication methods
The show authentication methods Privileged EXEC mode command displays information about the authentication methods.
Syntax
show authentication methods
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
The following example displays the authentication configuration.
Console# show authentication methods
Login Authentication Method Lists
---------------------------------
Default: Radius, Local, Line
Console_Login: Line, None
Enable Authentication Method Lists
----------------------------------
Default: Radius, Enable
Console_Enable: Enable, None
Line |
Login Method List |
Enable Method List |
-------------- |
----------------- |
------------------ |
Console |
Console_Login |
Console_Enable |
Telnet |
Default |
Default |
SSH |
Default |
Default |
http: Radius, Local |
|
|
https: Radius, Local |
|
|
dot1x: Radius |
|
|
Page 25

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
password
The password Line Configuration mode command specifies a password on a line. To remove the password, use the no form of this command.
Syntax
password password [encrypted] no password
Parameters
•password — Password for this level (Range: 1-159 characters).
•encrypted — Encrypted password to be entered, copied from another device configuration.
Default Configuration
No password is defined.
Command Mode
Line Configuration mode
User Guidelines
If a password is defined as encrypted, the required password length is 32 characters.
Example
The following example specifies password secret on a console.
Console(config)# line console
Console(config-line)# password secret
Page 26

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
enable password
The enable password Global Configuration mode command sets a local password to control access to user and privilege levels. To remove the password requirement, use the no form of this command.
Syntax
enable password [level level] password [encrypted] no enable password [level level]
Parameters
•password — Password for this level (Range: 1-159 characters).
•level — Level for which the password applies. If not specified the level is 15 (Range: 1-15).
•encrypted — Encrypted password entered, copied from another device configuration.
Default Configuration
No enable password is defined.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example sets local level 15 password secret to control access to user and privilege levels.
Console(config)# enable password level 15 secret
Page 27

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
username
The username Global Configuration mode command creates a user account in the local database. To remove a user name, use the no form of this command.
Syntax
username name [password password] [level level] [encrypted] no username name
Parameters
•name — The name of the user (Range: 1- 20 characters).
•password — The authentication password for the user (Range: 1-159 characters).
•level — The user level (Range: 1-15).
•encrypted — Encrypted password entered, copied from another device configuration.
Default Configuration
No user is defined.
Command Mode
Global Configuration mode
User Guidelines
User account can be created without a password.
Example
The following example configures user bob with password lee and user level 15 to the system.
Console(config)# username bob password lee level 15
Page 28

TL-SG3109/TL-SL3452 Gigabit Managed Switch Family CLI Reference Guide
Section 3. Address Table Commands
bridge address
The bridge address Interface Configuration (VLAN) mode command adds a MAC-layer station source address to the bridge table. To delete the MAC address, use the no form of this command.
Syntax
bridge address mac-address {ethernet interface | port-channel port-channel-number} [permanent | delete-on- reset | delete-on-timeout | secure]
no bridge address [mac-address]
Parameters
•mac-address — A valid MAC address.
•interface — A valid Ethernet port.
•port-channel-number — A valid port-channel number.
•permanent — The address can only be deleted by the no bridge address command.
•delete-on-reset — The address is deleted after reset.
•delete-on-timeout — The address is deleted after "age out" time has expired.
•secure — The address is deleted after the port changes mode to unlock learning (no port security command). This parameter is only available when the port is in the learning locked mode.
Default Configuration
No static addresses are defined. The default mode for an added address is permanent.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
Using the no form of the command without specifying a MAC address deletes all static MAC addresses belonging to this VLAN).
Example
The following example adds a permanent static MAC-layer station source address 3aa2.64b3.a245 on port 7 to the bridge table.
Console(config)# interface vlan 2
Console(config-if)# bridge address 3aa2.64b3.a245 ethernet e7 permanent
Page 29
 Loading...
Loading...