Ricoh Aficio MP C4501 User Manual

Aficio MP C4501/C5501 series
Security Target
Author : RICOH COMPANY, LTD.
Date : 2011-07-18
Version : 1.00
Portions of Aficio MP C4501/C5501 series Security Target are reprinted with written permission from IEEE, 445 Hoes Lane, Piscataway, New Jersey 08855, from IEEE 2600.1, Protection Profile for Hardcopy Devices, Operational Environment A, Copyright © 2009 IEEE. All rights reserved.
This document is a translation of the evaluated and certified security target written in Japanese.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 1 of 93
Revision History
Version |
Date |
Author |
Detail |
1.00 |
2011-07-18 |
RICOH COMPANY, LTD. |
Publication version. |
|
|
|
|
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

|
|
Page 2 of 93 |
|
|
|
|
|
|
|
|
Table of Contents |
1 ST Introduction ................................................................................................................... |
7 |
|
1.1 |
ST Reference ................................................................................................................ |
7 |
1.2 |
TOE Reference ............................................................................................................. |
7 |
1.3 |
TOE Overview .............................................................................................................. |
8 |
|
1.3.1 |
TOE Type ..................................................................................................................... |
8 |
||
|
1.3.2 |
TOE Usage................................................................................................................... |
8 |
||
|
1.3.3 |
Major Security Features of TOE .............................................................................. |
10 |
||
|
1.4 |
TOE Description......................................................................................................... |
11 |
||
|
1.4.1 |
Physical Boundary of TOE ........................................................................................ |
11 |
||
|
1.4.2 |
Guidance Documents ................................................................................................ |
14 |
||
|
1.4.3 |
Definition of Users .................................................................................................... |
18 |
||
|
|
1.4.3.1. |
Direct User ......................................................................................................... |
18 |
|
|
|
1.4.3.2. |
Indirect User ...................................................................................................... |
19 |
|
|
1.4.4 |
Logical Boundary of TOE ......................................................................................... |
21 |
||
|
|
1.4.4.1. |
Basic Functions.................................................................................................. |
21 |
|
|
|
1.4.4.2. |
Security Functions............................................................................................. |
24 |
|
|
1.4.5 |
Protected Assets ........................................................................................................ |
26 |
||
|
|
1.4.5.1. |
User Data ........................................................................................................... |
26 |
|
|
|
1.4.5.2. |
TSF Data ............................................................................................................ |
27 |
|
|
|
1.4.5.3. |
Functions ............................................................................................................ |
27 |
|
|
1.5 |
Glossary...................................................................................................................... |
27 |
||
|
1.5.1 |
Glossary for This ST ................................................................................................. |
27 |
||
2 |
Conformance Claim........................................................................................................... |
31 |
|||
|
2.1 |
CC Conformance Claim .............................................................................................. |
31 |
||
|
2.2 |
PP Claims................................................................................................................... |
31 |
||
|
2.3 |
Package Claims .......................................................................................................... |
31 |
||
|
2.4 |
Conformance Claim Rationale.................................................................................... |
32 |
||
|
2.4.1 |
Consistency Claim with TOE Type in PP................................................................ |
32 |
||
|
2.4.2 |
Consistency Claim with Security Problems and Security Objectives in PP......... |
32 |
||
|
2.4.3 |
Consistency Claim with Security Requirements in PP.......................................... |
33 |
||
3 |
Security Problem Definitions ............................................................................................ |
36 |
|||
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

|
|
|
|
Page 3 of 93 |
|
|
|
|
|
|
|
|
|
|
|
3.1 |
Threats ....................................................................................................................... |
36 |
|
|
3.2 |
Organisational Security Policies ................................................................................ |
37 |
|
|
3.3 |
Assumptions............................................................................................................... |
37 |
|
4 |
Security Objectives............................................................................................................ |
39 |
||
|
4.1 |
Security Objectives for TOE ....................................................................................... |
39 |
|
|
4.2 |
Security Objectives of Operational Environment ....................................................... |
40 |
|
|
4.2.1 |
IT Environment......................................................................................................... |
40 |
|
|
4.2.2 |
Non-IT Environment................................................................................................. |
41 |
|
|
4.3 |
Security Objectives Rationale..................................................................................... |
42 |
|
|
4.3.1 |
Correspondence Table of Security Objectives ......................................................... |
42 |
|
|
4.3.2 |
Security Objectives Descriptions ............................................................................. |
43 |
|
5 |
Extended Components Definition...................................................................................... |
47 |
||
|
5.1 |
Restricted forwarding of data to external interfaces (FPT_FDI_EXP) ....................... |
47 |
|
6 |
Security Requirements...................................................................................................... |
49 |
||
|
6.1 |
Security Functional Requirements............................................................................. |
49 |
|
|
6.1.1 |
Class FAU: Security audit ........................................................................................ |
49 |
|
|
6.1.2 |
Class FCS: Cryptographic support .......................................................................... |
52 |
|
|
6.1.3 |
Class FDP: User data protection ............................................................................. |
53 |
|
|
6.1.4 |
Class FIA: Identification and authentication ......................................................... |
58 |
|
|
6.1.5 |
Class FMT: Security management........................................................................... |
61 |
|
|
6.1.6 |
Class FPT: Protection of the TSF............................................................................. |
67 |
|
|
6.1.7 |
Class FTA: TOE access ............................................................................................. |
68 |
|
|
6.1.8 |
Class FTP: Trusted path/channels........................................................................... |
68 |
|
|
6.2 |
Security Assurance Requirements.............................................................................. |
68 |
|
|
6.3 |
Security Requirements Rationale............................................................................... |
69 |
|
|
6.3.1 |
Tracing ....................................................................................................................... |
69 |
|
|
6.3.2 |
Justification of Traceability...................................................................................... |
71 |
|
|
6.3.3 |
Dependency Analysis ................................................................................................ |
77 |
|
|
6.3.4 |
Security Assurance Requirements Rationale.......................................................... |
79 |
|
7 |
TOE Summary Specification............................................................................................. |
80 |
||
|
7.1 |
Audit Function ........................................................................................................... |
80 |
|
|
7.2 |
Identification and Authentication Function ............................................................... |
82 |
|
|
|
|
|
|
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

|
|
Page 4 of 93 |
7.3 |
Document Access Control Function............................................................................ |
84 |
7.4 |
Use-of-Feature Restriction Function .......................................................................... |
86 |
7.5 |
Network Protection Function ..................................................................................... |
87 |
7.6 |
Residual Data Overwrite Function............................................................................. |
87 |
7.7 |
Stored Data Protection Function................................................................................ |
88 |
7.8 |
Security Management Function ................................................................................. |
88 |
7.9 |
Software Verification Function................................................................................... |
93 |
7.10 |
Fax Line Separation Function.................................................................................... |
93 |
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

|
Page 5 of 93 |
List of Figures |
|
Figure 1 : Example of TOE Environment........................................................................................................ |
9 |
Figure 2 : Hardware Configuration of the TOE............................................................................................. |
12 |
Figure 3 : Logical Scope of the TOE............................................................................................................. |
21 |
List of Tables |
|
Table 1 : Identification Information of TOE.................................................................................................... |
7 |
Table 2 : Guidance for English Version-1...................................................................................................... |
14 |
Table 3 : Guidance for English Version-2...................................................................................................... |
15 |
Table 4 : Guidance for English Version-3...................................................................................................... |
17 |
Table 5 : Guidance for English Version-4...................................................................................................... |
17 |
Table 6 : Definition of Users ......................................................................................................................... |
19 |
Table 7 : List of Administrative Roles........................................................................................................... |
19 |
Table 8 : Definition of User Data .................................................................................................................. |
26 |
Table 9 : Definition of TSF Data ................................................................................................................... |
27 |
Table 10 : Specific Terms Related to This ST ............................................................................................... |
27 |
Table 11 : Rationale for Security Objectives ................................................................................................. |
42 |
Table 12 : List of Auditable Events ............................................................................................................... |
49 |
Table 13 : List of Cryptographic Key Generation ......................................................................................... |
53 |
Table 14 : List of Cryptographic Operation................................................................................................... |
53 |
Table 15 : List of Subjects, Objects, and Operations among Subjects and Objects (a) ................................. |
54 |
Table 16 : List of Subjects, Objects, and Operations among Subjects and Objects (b) ................................. |
54 |
Table 17 : Subjects, Objects and Security Attributes (a) ............................................................................... |
54 |
Table 18 : Rules to Control Operations on Document Data and User Jobs (a).............................................. |
55 |
Table 19 : Additional Rules to Control Operations on Document Data and User Jobs (a)............................ |
56 |
Table 20 : Subjects, Objects and Security Attributes (b) ............................................................................... |
57 |
Table 21 : Rule to Control Operations on MFP Applications (b) .................................................................. |
57 |
Table 22 : List of AuthenticationEvents of Basic Authentication............................................................... |
..58 |
Table 23 : List of Actionsfor Authentication Failure .......................................................................... |
..........58 |
Table 24 : List of Security Attributes for Each User That Shall Be Maintained............................................ |
59 |
Table 25 : Rules for Initial Association of Attributes .................................................................................... |
61 |
Table 26 : User Roles for Security Attributes (a)........................................................................................... |
62 |
Table 27 : User Roles for Security Attributes (b) .......................................................................................... |
63 |
Table 28 : Authorised Identified Roles Allowed to Override Default Values ................................................ |
64 |
Table 29 : List of TSF Data ........................................................................................................................... |
65 |
Table 30 : List of Specification of Management Functions................................................................ |
.......66 |
Table 31 : TOE Security Assurance Requirements (EAL3+ALC_FLR.2) .................................................... |
69 |
Table 32 : Relationship between Security Objectives and Functional Requirements.................................... |
70 |
Table 33 : Results of Dependency Analysis of TOE Security Functional Requirements .............................. |
77 |
Table 34 : List of Audit Events...................................................................................................................... |
80 |
Table 35 : List of Audit Log Items ................................................................................................................ |
81 |
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

|
|
Page 6 of 93 |
Table 36 : Unlocking Administrators for Each User Role ............................................................................. |
83 |
|
Table 37 : Stored Documents Access Control Rules for Normal Users......................................................... |
85 |
|
Table 38 |
: Encrypted Communications Provided by the TOE....................................................................... |
87 |
Table 39 |
: List of Cryptographic Operations for Stored Data Protection ...................................................... |
88 |
Table 40 |
: Management of TSF Data............................................................................................................. |
89 |
Table 41 |
: List of Static Initialisation for Security Attributes of Document Access Control SFP ................. |
92 |
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 7 of 93
1 ST Introduction
This section describes ST Reference, TOE Reference, TOE Overview and TOE Description.
1.1ST Reference
The following are the identification information of this ST.
Title |
: Aficio MP C4501/C5501 series Security Target |
Version |
: 1.00 |
Date |
: 2011-07-18 |
Author |
: RICOH COMPANY, LTD. |
1.2TOE Reference
This TOE is identified by the following: digital multi function product (hereafter "MFP") and Fax Controller Unit (hereafter "FCU"), all of which constitute the TOE. The MFP is identified by its product name and version. Although the MFP product names vary depending on sales areas and/or sales companies, the components are identical. MFP versions consist of software and hardware versions. The FCU is identified by its name and version. Table 1 shows the identification information of the TOE.
Table 1 : Identification Information of TOE
|
Names |
|
|
Versions |
|
|
|
|
|
MFPs |
|
|
|||
|
|
|
|
|
|
|
|
|
Ricoh Aficio MP C4501, |
|
|
Software |
|
|
|
|
Ricoh Aficio MP C5501, |
|
|
|
|
|
|
|
|
|
System/Copy |
|
2.02 |
|
|
|
Ricoh Aficio MP C4501G, |
|
|
|
|
|
|
|
|
|
Network Support |
|
10.54 |
|
|
|
Ricoh Aficio MP C5501G, |
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
Scanner |
|
01.11.1 |
|
|
|
Gestetner MP C4501, |
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
Printer |
|
1.01 |
|
|
|
Gestetner MP C5501, |
|
|
|
|
||
|
|
|
|
|
|
|
|
|
Lanier MP C4501, |
|
|
Fax |
|
02.01.00 |
|
|
Lanier MP C5501, |
|
|
RemoteFax |
|
01.00.00 |
|
|
Lanier LD645C, |
|
|
|
|
|
|
|
|
|
Web Support |
|
1.06 |
|
|
|
Lanier LD655C, |
|
|
|
|
|
|
|
|
|
Web Uapl |
|
1.01 |
|
|
|
Lanier LD645CG, |
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
NetworkDocBox |
|
1.01 |
|
|
|
Lanier LD655CG, |
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
animation |
|
1.00 |
|
|
|
nashuatec MP C4501, |
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
PCL |
|
1.02 |
|
|
|
nashuatec MP C5501, |
|
|
|
|
||
|
Rex-Rotary MP C4501, |
|
|
OptionPCLFont |
|
1.02 |
|
|
Rex-Rotary MP C5501, |
|
|
|
|
|
|
|
|
|
Engine |
|
1.03:04 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

|
|
|
|
|
|
|
|
Page 8 of 93 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Names |
|
|
Versions |
|
|
|
|
infotec MP C4501, |
|
|
OpePanel |
|
1.06 |
|
||
|
infotec MP C5501, |
|
|
|
|
|
|
||
|
|
|
LANG0 |
|
1.06 |
|
|||
|
Savin C9145, |
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
LANG1 |
|
1.06 |
|
|
|
Savin C9155, |
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Data Erase Std |
|
1.01x |
|
|
|
Savin C9145G, |
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Hardware |
|
|
||
|
Savin C9155G |
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Ic Key |
|
01020700 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Ic Ctlr |
|
03 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Options |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
FCU name |
|
Fax Option Type C5501 |
|
|
GWFCU3-21(WW) |
|
03.00.00 |
|
|
|
|
|
|
|
|
|||
Keywords |
: Digital MFP, Documents, Copy, Print, Scanner, Network, Office, Fax |
|
|
||||||
1.3TOE Overview
This section defines TOE Type, TOE Usage and Major Security Features of TOE.
1.3.1TOE Type
This TOE is a digital multi function product (hereafter "MFP"), which is an IT device that inputs, stores, and outputs documents.
1.3.2TOE Usage
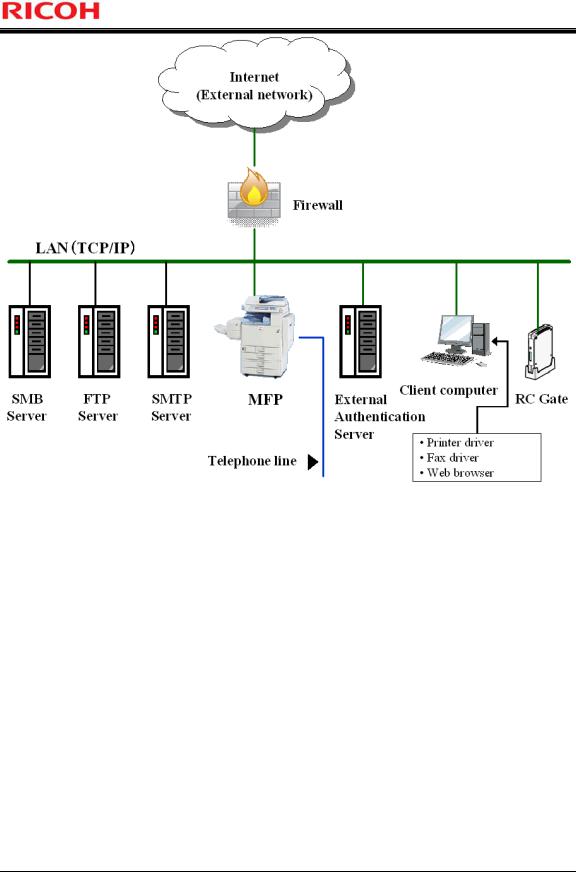
The operational environment of the TOE is illustrated below and the usage of the TOE is outlined in this section.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.
Page 9 of 93
Figure 1 : Example of TOE Environment
The TOE is used by connecting to the local area network (hereafter "LAN") and telephone lines, as shown in Figure 1. Users can operate the TOE from the Operation Panel of the TOE or through LAN communications. Below, explanations are provided for the MFP, which is the TOE itself, and hardware and software other than the TOE.
MFP
A machinery that is defined as the TOE. The MFP is connected to the office LAN, and users can perform the following operations from the Operation Panel of the MFP:
-Various settings for the MFP,
-Copy, fax, storage, and network transmission of paper documents,
-Print, fax, network transmission, and deletion of the stored documents.
Also, the TOE receives information via telephone lines and can store it as a document.
LAN
Network used in the TOE environment.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 10 of 93
Client computer
Performs as a client of the TOE if it is connected to the LAN, and users can remotely operate the MFP from the client computer. The possible remote operations from the client computer are as follows:
-Various settings for the MFP using a Web browser installed on the client computer,
-Operation of documents using a Web browser installed on the client computer,
-Storage and printing of documents using the printer driver installed on the client computer,
-Storage and faxing of documents using the fax driver installed on the client computer.
Telephone line
A public line for the TOE to communicate with external faxes.
Firewall
A device to prevent the office environment from network attacks via the Internet.
FTP Server
A server used by the TOE for folder transmission of the stored documents in the TOE to its folders.
SMB Server
A server used by the TOE for folder transmission of the stored documents in the TOE to its folders.
SMTP Server
A server used by the TOE for e-mail transmission of the stored documents in the TOE.
External Authentication Server
A server that identifies and authenticates the TOE user with Windows authentication (Kerberos authentication method). This server is only used when External Authentication is applied. The TOE identifies and authenticates the user by communicating with the external authentication server via LAN.
RC Gate
An IT device used for @Remote. The function of RC Gate for @Remote is to relay communications between the MFP and maintenance centre. A transfer path to other external interface for input information from the RC Gate via network interface is not implemented in the TOE. The RC Gate products include Remote Communication Gate A, Remote Communication Gate Type BN1, and Remote Communication Gate Type BM1.
1.3.3Major Security Features of TOE
The TOE stores documents in it, and sends and receives documents to and from the IT devices connected to the LAN. To ensure provision of confidentiality and integrity for those documents, the TOE has the following security features:
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 11 of 93
-Audit Function
-Identification and Authentication Function
-Document Access Control Function
-Use-of-Feature Restriction Function
-Network Protection Function
-Residual Data Overwrite Function
-Stored Data Protection Function
-Security Management Function
-Software Verification Function
-Fax Line Separation Function
1.4TOE Description
This section describes Physical Boundary of TOE, Guidance Documents, Definition of Users, Logical Boundary of TOE, and Protected Assets.
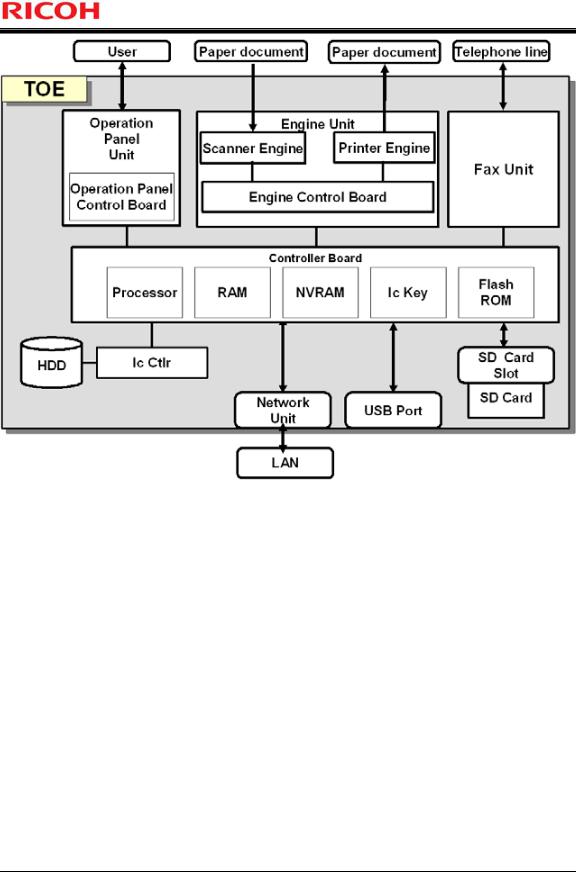
1.4.1Physical Boundary of TOE
The physical boundary of the TOE is the MFP, which consists of the following hardware components (shown in Figure 2): Operation Panel Unit, Engine Unit, Fax Unit, Controller Board, HDD, Ic Ctlr, Network Unit, USB Port, SD Card Slot, and SD Card.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.
Page 12 of 93
Figure 2 : Hardware Configuration of the TOE
Controller Board
The Controller Board is a device that contains Processors, RAM, NVRAM, Ic Key, and FlashROM. The Controller Board sends and receives information to and from the units and devices that constitute the MFP, and this information is used to control the MFP. The information to control the MFP is processed by the MFP Control Software on the Controller Board. The following describes the components of the Controller Board:
-Processor
A semiconductor chip that performs basic arithmetic processing for MFP operations.
-RAM
A volatile memory medium which is used as a working area for image processing such as compressing/decompressing the image data. It can also be used to temporarily read and write internal information.
-NVRAM
A non-volatile memory medium in which TSF data for configuring MFP operations is stored.
-Ic Key
A security chip that has the functions of random number generation, cryptographic key generation
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 13 of 93
and digital signature. It has the memory medium inside, and the signature root key is installed before the TOE is shipped.
-FlashROM
A non-volatile memory medium in which the following software components are installed: System/Copy, Network Support, Scanner, Printer, Fax, RemoteFax, Web Support, Web Uapl, NetworkDocBox, animation, PCL, OptionPCLFont, LANG0, and LANG1. These are part of the TOE and are included in the MFP Control Software.
Operation Panel Unit (hereafter "Operation Panel")
The Operation Panel is a user interface installed on the TOE and consists of the following devices: key switches, LED indicators, an LCD touch screen, and Operation Control Board. The Operation Control Board is connected to the key switches, LED indicators, and LCD touch screen. The Operation Panel Control Software is installed on the Operation Panel Control Board. The Operation Panel Control Software performs the following:
1.Transfers operation instructions from the key switches and the LCD touch screen to the Controller Board.
2.Controls the LEDs and displays information on the LCD touch screen according to display instructions from the Controller Board.
OpePanel, which is one of the components that constitute the TOE, is the identifier for the Operation Panel Control Software.
Engine Unit
The Engine Unit consists of Scanner Engine that is an input device to read paper documents, Printer Engine that is an output device to print and eject paper documents, and Engine Control Board. The Engine Control Software is installed in the Engine Control Board. The Engine Control Software sends status information about the Scanner Engine and Printer Engine to the Controller Board, and operates the Scanner Engine or Printer Engine according to instructions from the MFP Control Software. Engine, which is one of the components that constitute the TOE, is the identifier for the Engine Control Software.
Fax Unit
The Fax Unit is a unit that has a modem function for connection to a telephone line. It also sends and receives fax data to and from other fax devices using the G3 standard for communication. The Fax Unit sends and receives control information about the Controller Board and Fax Unit and fax data. FCU, which is one of the components that constitute the TOE, is the identifier of the Fax Unit.
HDD
The HDD is a hard disk drive that is a non-volatile memory medium. It stores documents, login user names and login passwords of normal users.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 14 of 93
Ic Ctlr
The Ic Ctlr is a board that implements data encryption and decryption functions. It is provided with functions for HDD encryption realisation.
Network Unit
The Network Unit is an external interface to an Ethernet (100BASE-TX/10BASE-T) LAN.
USB Port
The USB Port is an external interface to connect a client computer to the TOE for printing directly from the client computer. During installation, this interface is disabled.
SD Card/SD Card Slot
The SD Card is a memory medium in which Data Erase Std (MFP Control Software) are stored. When used, the SD Card is inserted into the SD Card Slot that is inside the MFP. Only the customer engineer is allowed to open the cover and insert the SD Card into the SD Card Slot during installation.
1.4.2Guidance Documents
The following sets of user guidance documents are available for this TOE: [English version-1], [English version-2], [English version-3], and [English version-4]. Selection of the guidance document sets depends on the sales area and/or sales company. Guidance document sets will be supplied with individual TOE component. Details of the document sets are as follows.
[English version-1]
|
Table 2 : Guidance for English Version-1 |
||
|
|
|
|
TOE |
|
Guidance Documents for Product |
|
Components |
|
|
|
MFP |
- C9130/C9135/C9145/C9145A/C9155/C9155A |
||
|
C9130G/C9135G/C9145G/C9145AG/C9155G/C9155AG |
||
|
LD630C/LD635C/LD645C/LD645CA/LD655C/LD655CA |
||
|
LD630CG/LD635CG/LD645CG/LD645CAG/LD655CG/LD655CAG |
||
|
Aficio MP C3001/C3501/C4501/C4501A/C5501/C5501A |
||
|
Aficio MP C3001G/C3501G/C4501G/C4501AG/C5501G/C5501AG |
||
|
Operating Instructions |
|
|
|
About This Machine |
D088-7603A |
|
|
- C9130/C9135/C9145/C9145A/C9155/C9155A |
||
|
C9130G/C9135G/C9145G/C9145AG/C9155G/C9155AG |
||
|
LD630C/LD635C/LD645C/LD645CA/LD655C/LD655CA |
||
|
LD630CG/LD635CG/LD645CG/LD645CAG/LD655CG/LD655CAG |
||
|
Aficio MP C3001/C3501/C4501/C4501A/C5501/C5501A |
||
|
Aficio MP C3001G/C3501G/C4501G/C4501AG/C5501G/C5501AG |
||
|
|
|
|
|
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved. |
||

Page 15 of 93
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Operating Instructions |
|
|
|
|
|
|
|
Troubleshooting |
D088-7653A |
|
|
|
||
|
- Quick Reference Copy Guide |
D088-7526 |
|
|
|
||
|
- Quick Reference Printer Guide |
D088-7805 |
|
|
|
||
|
- Quick Reference Scanner Guide |
D088-7886 |
|
|
|
||
|
- App2Me Start Guide |
D085-7906B |
|
|
|
||
|
- Notes for Users |
D088-7608 |
|
|
|
||
|
- Notes for Users |
D088-7759A |
|
|
|
||
|
- Notes for Users |
D572-7010 |
|
|
|
||
|
- Manuals for Users |
|
|
|
|
|
|
|
Aficio MP C3001/MP C3001G/MP C3501/MP C3501G/MP C4501/MP C4501G/MP |
||||||
|
C4501A/MP C4501AG/MP C5501/MP C5501G/MP C5501A/MP C5501AG |
||||||
|
C9130/C9130G/C9135/C9135G/C9145/C9145G/C9145A/C9145AG/C9155/C9155G/C9 |
||||||
|
155A/C9155AG |
|
|
|
|
|
|
|
LD630C/LD630CG/LD635C/LD635CG/LD645C/LD645CG/LD645CA/LD645CAG/ |
||||||
|
LD655C/LD655CG/LD655CA/LD655CAG |
D089-6906A |
|||||
|
- Manuals for Administrators |
|
|
|
|
||
|
Aficio MP C3001/MP C3001G/MP C3501/MP C3501G/MP C4501/MP C4501G/MP |
||||||
|
C4501A/MP C4501AG/MP C5501/MP C5501G/MP C5501A/MP C5501AG |
||||||
|
C9130/C9130G/C9135/C9135G/C9145/C9145G/C9145A/C9145AG/C9155/C9155G/C9 |
||||||
|
155A/C9155AG |
|
|
|
|
|
|
|
LD630C/LD630CG/LD635C/LD635CG/LD645C/LD645CG/LD645CA/LD645CAG/ |
||||||
|
LD655C/LD655CG/LD655CA/LD655CAG |
D089-6907A |
|||||
|
- To Users of This Machine |
D029-7904 |
|
|
|
||
|
- Operating Instructions Notes on Security Functions |
D088-7706 |
|||||
|
- Notes for Administrators: Using this Machine in a Network Environment Compliant |
||||||
|
with IEEE Std. 2600.1TM-2009 |
D088-7707 |
|
|
|
||
|
- Help |
83NHBUENZ1.20 v116 |
|
|
|
||
|
|
|
|
|
|
||
FCU |
- Quick Reference Fax Guide |
D545-8506 |
|
|
|
||
|
|
|
|
|
|
|
|
[English version-2]
|
Table 3 : Guidance for English Version-2 |
|
|
|
|
TOE |
Guidance Documents for Product |
|
Components |
|
|
MFP |
- C9130/C9135/C9145/C9145A/C9155/C9155A |
|
|
C9130G/C9135G/C9145G/C9145AG/C9155G/C9155AG |
|
|
LD630C/LD635C/LD645C/LD645CA/LD655C/LD655CA |
|
|
LD630CG/LD635CG/LD645CG/LD645CAG/LD655CG/LD655CAG |
|
|
|
|
|
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved. |
|

Page 16 of 93
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Aficio MP C3001/C3501/C4501/C4501A/C5501/C5501A |
|
|
||||
|
Aficio MP C3001G/C3501G/C4501G/C4501AG/C5501G/C5501AG |
||||||
|
Operating Instructions |
|
|
|
|
|
|
|
About This Machine |
D088-7609 |
|
|
|
||
|
- C9130/C9135/C9145/C9145A/C9155/C9155A |
|
|
|
|||
|
C9130G/C9135G/C9145G/C9145AG/C9155G/C9155AG |
|
|
||||
|
LD630C/LD635C/LD645C/LD645CA/LD655C/LD655CA |
||||||
|
LD630CG/LD635CG/LD645CG/LD645CAG/LD655CG/LD655CAG |
||||||
|
Aficio MP C3001/C3501/C4501/C4501A/C5501/C5501A |
|
|
||||
|
Aficio MP C3001G/C3501G/C4501G/C4501AG/C5501G/C5501AG |
||||||
|
Operating Instructions |
|
|
|
|
|
|
|
Troubleshooting |
D088-7657 |
|
|
|
||
|
- Quick Reference Copy Guide |
D088-7529 |
|
|
|||
|
- Quick Reference Printer Guide |
D086-7800 |
|
|
|||
|
- Quick Reference Scanner Guide |
D088-7889 |
|
|
|||
|
- App2Me Start Guide |
D085-7905B |
|
|
|
||
|
- Notes for Users |
D572-7010 |
|
|
|
||
|
- Manuals for Users |
|
|
|
|
|
|
|
Aficio MP C3001/MP C3001G/MP C3501/MP C3501G/MP C4501/MP C4501G/MP |
||||||
|
C4501A/MP C4501AG/MP C5501/MP C5501G/MP C5501A/MP C5501AG |
||||||
|
C9130/C9130G/C9135/C9135G/C9145/C9145G/C9145A/C9145AG/C9155/C9155G/C9 |
||||||
|
155A/C9155AG |
|
|
|
|
|
|
|
LD630C/LD630CG/LD635C/LD635CG/LD645C/LD645CG/LD645CA/LD645CAG/LD |
||||||
|
655C/LD655CG/LD655CA/LD655CAG |
D089-6906A |
|||||
|
- Manuals for Administrators |
|
|
|
|
||
|
Aficio MP C3001/MP C3001G/MP C3501/MP C3501G/MP C4501/MP C4501G/MP |
||||||
|
C4501A/MP C4501AG/MP C5501/MP C5501G/MP C5501A/MP C5501AG |
||||||
|
C9130/C9130G/C9135/C9135G/C9145/C9145G/C9145A/C9145AG/C9155/C9155G/C9 |
||||||
|
155A/C9155AG |
|
|
|
|
|
|
|
LD630C/LD630CG/LD635C/LD635CG/LD645C/LD645CG/LD645CA/LD645CAG/LD |
||||||
|
655C/LD655CG/LD655CA/LD655CAG |
D089-6907A |
|||||
|
- Notes for Users |
D088-7404 |
|
|
|
||
|
- To Users of This Machine |
D029-7903 |
|
|
|
||
|
- Operating Instructions Notes on Security Functions |
D088-7708 |
|||||
|
- Notes for Administrators: Using this Machine in a Network Environment Compliant |
||||||
|
with IEEE Std. 2600.1TM-2009 |
D088-7709 |
|
|
|||
|
- Help |
83NHBUENZ1.20 v116 |
|
|
|
||
|
|
|
|
|
|
||
FCU |
- Quick Reference Fax Guide |
D545-8506 |
|
|
|
||
|
|
|
|
|
|
|
|
[English version-3]
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.
Page 17 of 93
Table 4 : Guidance for English Version-3
TOE |
|
Guidance Documents for Product |
||
Components |
|
|
|
|
MFP |
- Safety Information for MP C3001/MP C3501/MP C4501/MP C4501A/MP C5501/MP |
|||
|
C5501A/Aficio MP C3001/Aficio MP C3501/Aficio MP C4501/Aficio MP |
|||
|
C4501A/Aficio MP C5501/Aficio MP C5501A |
D088-7400A |
||
|
- Quick Reference Copy Guide |
D088-7525 |
|
|
|
- Quick Reference Fax Guide |
D545-8505 |
|
|
|
- Quick Reference Printer Guide |
D088-7804 |
|
|
|
- Quick Reference Scanner Guide |
D088-7885 |
|
|
|
- App2Me Start Guide |
D085-7904B |
|
|
|
- Manuals for This Machine |
D081-7602 |
|
|
|
- Notes for Users |
D088-7430 |
|
|
|
- Notes for Users |
D088-7420 |
|
|
|
- To Users of This Machine |
D029-7904 |
|
|
|
- Manuals for Users |
|
|
|
|
Aficio MP C3001/MP C3501/MP C4501/MP C4501A/MP C5501/MP C5501A |
|||
|
MP C3001/MP C3501/MP C4501/MP C4501A/MP C5501/MP C5501A |
|||
A D089-6931A
-Manuals for Administrators Security Reference
Aficio MP C3001/MP C3501/MP C4501/MP C4501A/MP C5501/MP C5501A
MP C3001/MP C3501/MP C4501/MP C4501A/MP C5501/MP C5501A D089-6933A
|
|
- Operating Instructions Notes on Security Functions |
D088-7704 |
|||
|
|
- Notes for Administrators: Using this Machine in a Network Environment Compliant |
||||
|
|
with IEEE Std. 2600.1TM-2009 |
D088-7705 |
|
|
|
|
|
- Help |
83NHBUENZ1.20 v116 |
|
|
|
|
|
|
|
|
|
|
FCU |
|
|
- |
|
|
|
|
|
|
|
|
|
|
[English version-4] |
|
|
|
|
|
|
|
|
|
Table 5 : Guidance for English Version-4 |
|
|
|
|
|
|
|
|
||
TOE |
|
|
Guidance Documents for Product |
|||
Components |
|
|
|
|
|
|
MFP |
|
- MP C3001/C3501/C4501/C4501A/C5501/C5501A |
|
|
||
|
|
MP C3001/C3501/C4501/C4501A/C5501/C5501A |
|
|
||
|
|
Aficio MP C3001/C3501/C4501/C4501A/C5501/C5501A |
|
|
||
|
|
|
|
|
|
|
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.
Page 18 of 93
Operating Instructions |
|
About This Machine |
D088-7605A |
- MP C3001/C3501/C4501/C4501A/C5501/C5501A MP C3001/C3501/C4501/C4501A/C5501/C5501A
Aficio MP C3001/C3501/C4501/C4501A/C5501/C5501A
Operating Instructions |
|
|
Troubleshooting |
D088-7655A |
|
- Quick Reference Copy Guide |
D088-7527 |
|
- Quick Reference Printer Guide |
D088-7805 |
|
- Quick Reference Scanner Guide |
D088-7887 |
|
- Notes for Users |
D088-7608 |
|
- Notes for Users |
D088-7759A |
|
- App2Me Start Guide |
D085-7906B |
|
- Manuals for Users
Aficio MP C3001/MP C3501/MP C4501/MP C4501A/MP C5501/MP C5501A
MP C3001/MP C3501/MP C4501/MP C4501A/MP C5501/MP C5501A D089-6908A
- Manuals for Administrators
Aficio MP C3001/MP C3501/MP C4501/MP C4501A/MP C5501/MP C5501A
MP C3001/MP C3501/MP C4501/MP C4501A/MP C5501/MP C5501A D089-6909A
|
- To Users of This Machine |
D029-7904 |
|
||
|
- Notes for Users |
D060-7781 |
|
||
|
- Operating Instructions Notes on Security Functions |
D088-7706 |
|||
|
- Notes for Administrators: Using this Machine in a Network Environment Compliant |
||||
|
with IEEE Std. 2600.1TM-2009 |
D088-7707 |
|
||
|
- Help |
83NHBUENZ1.20 v116 |
|
||
|
|
|
|
||
FCU |
- Quick Reference Fax Guide |
D545-8507 |
|
||
1.4.3Definition of Users
This section defines the users related to the TOE. These users include those who routinely use the TOE (direct users) and those who do not (indirect users). The direct users and indirect users are described as follows:
1.4.3.1.Direct User
The "user" referred to in this ST indicates a direct user. This direct user consists of normal users, administrators, and RC Gate. The following table (Table 6) shows the definitions of these direct users.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

|
|
|
|
|
Page 19 of 93 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 6 : Definition of Users |
|
|
|
|
|
|
|
|
|
|
Definition of |
|
|
Explanation |
|
|
|
Users |
|
|
|
|
|
|
|
|
|
A user who is allowed to use the TOE. A normal user is provided with a login user |
|
|
|
Normal user |
|
|
name and can use Copy Function, Fax Function, Scanner Function, Printer Function, |
|
|
|
|
|
|
and Document Server Function. |
|
|
|
|
|
|
|
|
|
|
Administrator |
|
|
A user who is allowed to manage the TOE. An administrator performs management |
|
|
|
|
|
operations, which include issuing login names to normal users. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
An IT device connected to networks. RC Gate performs the @Remote Service Function |
|
|
|
RC Gate |
|
|
of the TOE via RC Gate communication interface. Copy Function, Fax Function, |
|
|
|
|
|
Scanner Function, Printer Function, Document Server Function, and Management |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Function cannot be used. |
|
|
|
|
|
|
|
|
The administrator means the user registered for TOE management. According to its roles, the administrator can be classified as the supervisor and the MFP administrator. Up to four MFP administrators can be registered and selectively authorised to perform user management, machine management, network management, and file management. Therefore, the different roles of the management privilege can be allocated to multiple MFP administrators individually. The "MFP administrator" in this ST refers to the MFP administrator who has all management privileges (Table 7).
Table 7 : List of Administrative Roles
|
Definition of |
|
|
Management Privileges |
|
|
Explanation |
|
|
|
|
Administrator |
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
Supervisor |
|
|
Supervisor |
|
|
Authorised to delete and |
register |
the login |
|
|
|
|
|
|
password of the MFP administrator. |
|
|
|||
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
Authorised to manage normal users. This |
|
||
|
|
|
|
User management privilege |
|
|
privilege allows configuration of normal user |
|
||
|
|
|
|
|
|
|
settings. |
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
Authorised to specify MFP device behaviour |
|
||
|
|
|
|
Machine management |
|
|
(network behaviours excluded). This privilege |
|
||
|
|
|
|
privilege |
|
|
allows configuration of device settings and |
|
||
|
MFP administrator |
|
|
|
|
|
view of the audit log. |
|
|
|
|
|
|
|
Network management |
|
|
Authorised to manage networks and configure |
|
||
|
|
|
|
|
|
LAN settings. This |
privilege |
allows |
|
|
|
|
|
|
privilege |
|
|
|
|||
|
|
|
|
|
|
configuration of network settings. |
|
|
||
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
Authorised to manage stored documents. This |
|
||
|
|
|
|
File management privilege |
|
|
privilege allows access management of stored |
|
||
|
|
|
|
|
|
|
documents. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
1.4.3.2.Indirect User
Responsible manager of MFP
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 20 of 93
The responsible manager of MFP is a person who is responsible for selection of the TOE administrators in the organisation where the TOE is used.
Customer engineer
The customer engineer is a person who belongs to the organisation which maintains TOE operation. The customer engineer is in charge of installation, setup, and maintenance of the TOE.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.
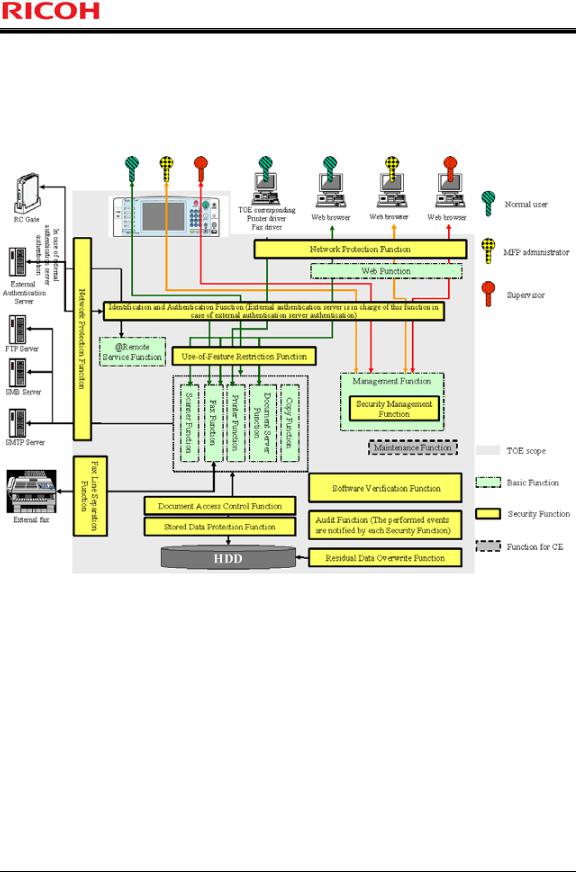
Page 21 of 93
1.4.4Logical Boundary of TOE
The Basic Functions and Security Functions are described as follows:
Figure 3 : Logical Scope of the TOE
1.4.4.1.Basic Functions
The overview of the Basic Functions is described as follows:
Copy Function
The Copy Function is to scan paper documents and copy scanned image data from the Operation Panel. Magnification and other editorial jobs can be applied to the copy image. It can also be stored on the HDD as a Document Server document.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 22 of 93
Printer Function
The Printer Function of TOE is to print or store the documents the TOE receives from the printer driver installed on the client computer. It also allows users to print and delete the stored documents from the Operation Panel or a Web browser.
-Receiving documents from the printer driver installed on the client computer.
The TOE receives documents from the printer driver installed on the client computer. Printing methods for documents is selected by users from the printer driver. The printing methods include direct print, Document Server storage, locked print, stored print, hold print, and sample print.
For direct print, documents received by the TOE will be printed. The documents will not be stored in the TOE.
For Document Server storage, the received documents will be stored on the HDD as Document Server documents.
For locked print, stored print, hold print, and sample print, the received documents will be stored on the HDD as printer documents. A dedicated password, which is used for locked print, is not subject to this evaluation.
-Operating from the Operation Panel
The TOE can print or delete printer documents according to the operations by users from the Operation Panel.
-Operating from a Web browser
The TOE can print or delete printer documents according to the operations by users from a Web browser.
-Deleting printer documents by the TOE
The deletion of printer documents by the TOE differs depending on printing methods. If locked print, hold print, or sample print is specified, the TOE deletes printer documents when printing is complete. If stored print is specified, the TOE does not delete printer documents even when printing is complete.
According to the guidance document, users first install the specified printer driver on their own client computers, and then use this function.
Scanner Function
The Scanner Function is to scan paper documents by using the Operation Panel. The scanned documents will be sent to folders or by e-mail. The documents to be sent to folders or by e-mail will be stored in the TOE, so that they can be transmitted afterwards. The documents stored in the TOE are called scanner documents. Scanner documents can be sent to folders or by e-mail, or deleted from the Operation Panel or a Web browser.
Folder transmission can be applied only to the destination folders in a server that the MFP administrator pre-registers in the TOE and with which secure communication can be ensured. E-mail transmission is possible only with the mail server and e-mail addresses that the MFP administrator pre-registers in the TOE and with which secure communication can be ensured.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 23 of 93
Fax Function
The Fax Function is to send paper documents and documents received from the fax driver installed on the client computer to external faxes (Fax Transmission Function). Also, this function can be used to receive documents from external faxes (Fax Reception Function).
Documents to be sent by fax can be stored in the TOE. Those documents stored in the TOE for fax transmission are called fax documents. Fax documents can be sent by fax, and they also can be printed, deleted, and sent to folders.
The documents received by fax can be stored in the TOE, printed, deleted from the TOE, and downloaded to the client computer.
-Fax Transmission Function
A function to send paper documents, documents in the client computer, and fax documents to external faxes over a telephone line.
Paper documents will be scanned and sent by fax using the Operation Panel. The documents in the client computer are sent by fax from the fax driver installed on the client computer. Fax documents are sent by fax from the Operation Panel or a Web browser. Documents can be sent by fax only to the telephone numbers that are pre-registered in the TOE.
-Fax Data Storage Function
A function to temporarily store paper documents or documents in the client computer for fax transmission in the TOE. Those documents stored in the TOE are called fax documents. Paper documents will be scanned and stored using the Operation Panel. The documents in the client computer are sent to and stored in the TOE by operating the fax driver installed on the client computer.
-Operation Function for Fax Documents
A function to print or delete fax documents. This function can be used from the Operation Panel or a Web browser.
-Folder Transmission Function of Fax Data
A function to send fax documents to folders by using the Operation Panel.
The MFP administrator must pre-register the destination server that provides secure communication with the TOE. Users select the destination server from the servers that the MFP administrator pre-registers, and send data to the folder.
-Fax Reception Function
A function to receive documents from external faxes via the telephone line and store the received documents in the TOE. Those stored documents in the TOE are called received fax documents.
-Operation Function for Received Fax Documents
A function to operate the received fax documents from the Operation Panel or a Web browser. Documents can be printed and deleted using the Operation Panel, while they can be printed, deleted and downloaded from a Web browser.
According to the guidance document, users first install the specified fax driver on their own client computers,
and then use this function.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 24 of 93
Document Server Function
The Document Server Function is to operate documents stored in the TOE by using the Operation Panel and a Web browser.
From the Operation Panel, users can store, print and delete Document Server documents. Also, users can print and delete fax documents.
From a Web browser, users can print and delete Document Server documents, fax, print, download, and delete fax documents. Also, users can send scanner documents to folders or by e-mail, download and delete them.
Management Function
The Management Function is to control the MFP's overall behaviour. This function can be implemented using the Operation panel or a Web browser.
Maintenance Function
The Maintenance Function is to perform maintenance service for the MFP if it is malfunctioning. When analysing causes of the malfunction, a customer engineer performs this function from the Operation Panel. The customer engineer will implement this function following the procedures that are allowed to customer engineers only. If the MFP administrator sets the Service Mode Lock Function to "ON", the customer engineer cannot use this function.
In this ST, the Service Mode Lock Function is set to "ON" for the target of evaluation.
Web Function
A function for the TOE user to remotely control the TOE from the client computer. To control the TOE remotely, the TOE user needs to install the designated Web browser on the client computer following the guidance documents and connect the client computer to the TOE via the LAN.
@Remote Service Function
A function for the TOE to communicate with RC Gate via networks for @Remote Service. As for the configuration of this TOE, this function has no access to the protected assets.
1.4.4.2.Security Functions
The Security Functions are described as follows:
Audit Function
The Audit Function is to generate the audit log of TOE use and security-relevant events (hereafter, "audit events"). Also, this function provides the recorded audit log in a legible fashion for users to audit. This function can be used only by the MFP administrator to view and delete the recorded audit log. To view and delete the audit log, the Web Function will be used.
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 25 of 93
Identification and Authentication Function
The Identification and Authentication Function is to verify persons before they use the TOE. The persons are allowed to use the TOE only when confirmed as the authorised user.
Users can use the TOE from the Operation Panel or via the network. By the network, users can use the TOE from a Web browser, printer/fax driver, and RC Gate.
To use the TOE from the Operation Panel or a Web browser, a user will be required to enter his or her login user name and login password so that the user can be verified as a normal user, MFP administrator, or supervisor.
To use the Printer or Fax Function from the printer or fax driver, a user will be required to enter his or her login user name and login password received from the printer or fax drivers, so that the user can be verified as a normal user.
To use the @Remote Service Function from the RC Gate communication interface, it will be verified whether the communication request is sent from RC Gate.
Methods to verify normal users are Basic Authentication and external server authentication. The users will be verified by the MFP administrator-specified procedure, whereas the MFP administrator and supervisor can be verified only by the Basic Authentication.
This function includes protection functions for the authentication feedback area, where dummy characters are displayed if a login password is entered using the Operation Panel. In addition to this and for the Basic Authentication only, this function can be used to register passwords that fulfil the requirements of the Minimum Character No. (i.e. minimum password length) and obligatory character types the MFP administrator specifies, so that the lockout function can be enabled and login password quality can be protected.
Document Access Control Function
The Document Access Control Function is to authorise the operations for documents and user jobs by the authorised TOE users who are authenticated by Identification and Authentication Function. It allows user's operation on the user documents and user jobs based on the privileges for the user role, or the operation permissions for each user.
Use-of-Feature Restriction Function
The Use-of-Feature Restriction Function is to authorise the operations of Copy Function, Printer Function, Scanner Function, Document Server Function and Fax Function by the authorised TOE users who are authenticated by Identification and Authentication Function. It authorises the use of functions based on the user role and the operation permissions for each user.
Network Protection Function
The Network Protection Function is to prevent information leakage through wiretapping on the LAN and detect data tampering. The protection function can be enabled using a Web browser to specify the URL for possible encrypted communication. If the Printer Function is used, the protection function can be enabled using the printer driver to specify encrypted communication. If the folder transmission function of Scanner Function is used, the protection function can be enabled through encrypted communication. If the e-mail
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

Page 26 of 93
transmission function of Scanner Function is used, the protection function can be enabled through encrypted communication with communication requirements that are specified for each e-mail address. If the LAN-Fax Transmission Function of Fax Function is used, the protection function can be enabled using the fax driver to specify encrypted communication. When communicating with RC Gate, encrypted communication is used.
Residual Data Overwrite Function
The Residual Data Overwrite Function is to overwrite specific patterns on the HDD and disable the reusing of the residual data included in deleted documents, temporary documents and their fragments on the HDD.
Stored Data Protection Function
The Stored Data Protection Function is to encrypt the data on the HDD and protect the data so that data leakage can be prevented.
Security Management Function
The Security Management Function is to control operations for TSF data in accordance with user role privileges or user privileges allocated to normal users, MFP administrator, and supervisor.
Software Verification Function
The Software Verification Function is to verify the integrity of the executable codes of the MFP Control Software and FCU Control Software and to ensure that they can be trusted.
Fax Line Separation Function
The Fax Line Separation Function is to restrict input information from the telephone lines so that only fax data can be received and unauthorised intrusion from the telephone lines (same as the "fax line") can be prevented. Also, this function can be used to prohibit transmissions of received faxes so that unauthorised intrusion from the telephone lines to the LAN can be prevented.
1.4.5Protected Assets
Assets to be protected by the TOE are user data, TSF data, and functions.
1.4.5.1.User Data
The user data is classified into two types: document data and function data. Table 8 defines user data according to these data types.
|
|
|
Table 8 : Definition of User Data |
|
|
|
|
|
|
|
Type |
|
Description |
|
|
Document |
|
Digitised documents, deleted documents, temporary documents and their |
|
|
data |
|
fragments, which are managed by the TOE. |
|
|
|
|
|
|
|
Function |
|
Jobs specified by users. In this ST, a "user job" is referred to as a "job". |
|
|
|
|
|
|
|
|
|
|
|
|
|
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved. |
|
|

Page 27 of 93
data
1.4.5.2.TSF Data
The TSF data is classified into two types: protected data and confidential data. Table 9 defines TSF data according to these data types.
|
Table 9 : Definition of TSF Data |
|
|
Type |
Description |
Protected data |
This data must be protected from changes by unauthorised persons. No security |
|
threat will occur even this data is exposed to the public. In this ST, "protected |
|
data", listed below, is referred to as "TSF protected data". |
|
Login user name, Number of Attempts before Lockout, settings for Lockout |
|
Release Timer, lockout time, date settings (year/month/day), time settings, |
|
Minimum Character No., Password Complexity Setting, S/MIME user |
|
information, destination folder, stored and received document user, document |
|
user list, available function list, and user authentication procedures. |
|
|
Confidential data |
This data must be protected from changes by unauthorised persons and reading by |
|
users without viewing permissions. In this ST, "confidential data", listed below, is |
|
referred to as "TSF confidential data". |
|
Login password, audit log, and HDD cryptographic key. |
|
|
1.4.5.3.Functions
The MFP applications (Copy Function, Document Server Function, Printer Function, Scanner Function, and Fax Function) that are for management of the document data of user data are classified as protected assets, whose use is subject to restrictions.
1.5Glossary
1.5.1Glossary for This ST
For clear understanding of this ST, Table 10 provides the definitions of specific terms.
|
Table 10 : Specific Terms Related to This ST |
|
|
Terms |
Definitions |
MFP Control Software |
A software component installed in the TOE. This component is stored in |
|
FlashROM and SD Card. The components that identify the TOE include |
|
System/Copy, Network Support, Scanner, Printer, Fax, RemoteFax, Web |
|
Support, Web Uapl, NetworkDocBox, animation, PCL, OptionPCLFont, |
|
LANG0, LANG1 and Data Erase Std. |
|
|
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.

|
Page 28 of 93 |
|
|
|
|
|
|
Terms |
Definitions |
Login user name |
An identifier assigned to each normal user, MFP administrator, and supervisor. |
|
The TOE identifies users by this identifier. |
|
|
Login password |
A password associated with each login user name. |
|
|
Lockout |
A type of behaviour to deny login of particular users. |
|
|
Auto logout |
A function for automatic user logout if no access is attempted from the |
|
Operation Panel or Web Function before the predetermined auto logout time |
|
elapses. |
|
Auto logout time for the Operation Panel: |
|
Time specified by the MFP administrator within 60 to 999 seconds. |
|
Auto logout time for the Web Function: |
|
30 minutes (this cannot be changed by users). This auto logout time is also |
|
referred to as "fixed auto logout time". |
|
|
Minimum Character No. |
The minimum number of registrable password digits. |
|
|
Password Complexity |
The minimum combination of the characters and symbols that can be used as |
Setting |
registrable passwords. |
|
There are four types of characters: uppercase and lower case alphabets, digits |
|
and symbols. |
|
There are Level 1 and Level 2 Password Complexity Settings. Level 1 requires a |
|
password to be a combination of two or more types of characters and symbols |
|
specified above. Level 2 requires a password to be a combination of three or |
|
more types of characters and symbols specified above. |
|
|
Basic Authentication |
One of the procedures for identification and authentication of TOE users who |
|
are authorised to use the TOE. The TOE authenticates TOE users by using the |
|
login user names and the login passwords registered on the TOE. |
|
|
External Authentication |
One of the procedures for identification and authentication of TOE users who |
|
are authorised to use the TOE. The TOE authenticates TOE users by using the |
|
login user names and the login passwords registered on the external |
|
authentication server connected to the MFP via LAN. External Authentication |
|
implemented in the TOE includes Windows Authentication, LDAP |
|
Authentication, and Integration Server Authentication. Windows Authentication |
|
supports NTLM Authentication and Kerberos Authentication. As for this ST, the |
|
term "External Authentication" refers to Windows Authentication using |
|
Kerberos Authentication method. |
|
|
HDD |
An abbreviation of hard disk drive. In this document, unless otherwise specified, |
|
"HDD" indicates the HDD installed on the TOE. |
|
|
User job |
A sequence of operations of each TOE function (Copy Function, Document |
|
Server Function, Scanner Function, Printer Function and Fax Function) from |
|
beginning to end. A user job may be suspended or cancelled by users during |
|
operation. If a user job is cancelled, the job will be terminated. |
|
|
Documents |
General term for paper documents and electronic documents used in the TOE. |
|
|
Document data |
Attributes of document data, such as +PRT, +SCN, +CPY, +FAXOUT, |
attributes |
+FAXIN, and +DSR. |
|
|
+PRT |
One of the document data attributes. Documents printed from the client |
|
computer, or documents stored in the TOE by locked print, hold print, and |
|
sample print using the client computer. |
|
|
|
|
Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.
 Loading...
Loading...