Xerox 80, 3100, 2100, 180, 800I User Manual
...
Xerox®
Security Guide
Entry Production Color Presses
Versant® |
Versant® 80/180 |
ColorPress® |
2100/3100 |
Color Digital Press |
Production Press |
Color Digital Press |
|
|
|
|
|
Versant 2100 Press, |
Versant 80 Press, |
Color 800/1000 Press |
Versant 3100 Press |
Versant 180 Press |
Color 800i/1000i Press |
Xerox® Application Security Guide and Information Assurance Disclosure
Xerox® Security Guide for Entry Production Color Class Products
© 2019 Xerox Corporation. All rights reserved. Xerox and Xerox and Design® are trademarks of Xerox Corporation in the United States and/or other countries. BR26363
Other company trademarks are also acknowledged.
Document Version: 1.0 (February 2019).
Copyright protection claimed includes all forms and matters of copyrightable material and information now allowed by statutory or judicial law or hereinafter granted including without limitation, material generated from the software programs which are displayed on the screen, such as icons, screen displays, looks, etc.
Changes are periodically made to this document. Changes, technical inaccuracies, and typographic errors will be corrected in subsequent editions.

Xerox® Security Guide for Entry Production Color Class Products
Table of Contents
1 |
INTRODUCTION ................................................................................................................................ |
|
1-3 |
|
PURPOSE ................................................................................................................................................. |
|
1-3 |
|
TARGET AUDIENCE ................................................................................................................................... |
|
1-3 |
|
DISCLAIMER.............................................................................................................................................. |
|
1-3 |
|
PHYSICAL COMPONENTS ........................................................................................................................... |
|
1-3 |
|
ARCHITECTURE......................................................................................................................................... |
|
1-4 |
|
USER INTERFACE...................................................................................................................................... |
|
1-4 |
|
SCANNER ................................................................................................................................................. |
|
1-4 |
|
MARKING ENGINE ..................................................................................................................................... |
|
1-4 |
|
CONTROLLER ........................................................................................................................................... |
|
1-5 |
|
OPTIONAL EQUIPMENT .............................................................................................................................. |
|
1-5 |
2 |
USER DATA PROTECTION .............................................................................................................. |
|
2-7 |
|
USER DATA PROTECTION WHILE WITHIN PRODUCT ...................................................................................... |
|
2-7 |
|
USER DATA IN TRANSIT ............................................................................................................................. |
|
2-8 |
3 |
NETWORK SECURITY .................................................................................................................... |
|
3-10 |
|
TCP/IP PORTS & SERVICES.................................................................................................................... |
|
3-10 |
|
NETWORK ENCRYPTION .......................................................................................................................... |
|
3-11 |
|
NETWORK ACCESS CONTROL.................................................................................................................. |
|
3-16 |
|
CONTEXTUAL ENDPOINT CONNECTION MANAGEMENT............................................................................... |
|
3-17 |
|
FIPS140-2 COMPLIANCE VALIDATION...................................................................................................... |
|
3-17 |
|
ADDITIONAL NETWORK SECURITY CONTROLS .......................................................................................... |
|
3-17 |
4 DEVICE SECURITY: BIOS, FIRMWARE, OS, RUNTIME, AND OPERATIONAL SECURITY |
|||
CONTROLS ............................................................................................................................................. |
|
4-19 |
|
|
FAIL SECURE VS FAIL SAFE..................................................................................................................... |
|
4-19 |
|
PRE-BOOT SECURITY.............................................................................................................................. |
|
4-20 |
|
BOOT PROCESS SECURITY...................................................................................................................... |
|
4-20 |
|
RUNTIME SECURITY ................................................................................... |
ERROR! BOOKMARK NOT DEFINED. |
|
|
EVENT MONITORING & LOGGING ............................................................................................................. |
|
4-20 |
|
OPERATIONAL SECURITY......................................................................................................................... |
|
4-21 |
|
BACKUP & RESTORE (CLONING) .............................................................................................................. |
|
4-21 |
|
EIP APPLICATIONS.................................................................................................................................. |
|
4-21 |
5 CONFIGURATION & SECURITY POLICY MANAGEMENT SOLUTIONS |
.....................................5-22 |
||
6 IDENTIFICATION, AUTHENTICATION, AND AUTHORIZATION .................................................. |
|
6-23 |
|
|
AUTHENTICATION .................................................................................................................................... |
|
6-23 |
|
AUTHORIZATION (ROLE BASED ACCESS CONTROLS) ................................................................................ |
|
6-25 |
7 ADDITIONAL INFORMATION & RESOURCES.............................................................................. |
|
7-26 |
|
|
SECURITY @ XEROX® ............................................................................................................................ |
|
7-26 |
|
RESPONSES TO KNOWN VULNERABILITIES ............................................................................................... |
|
7-26 |
|
ADDITIONAL RESOURCES ........................................................................................................................ |
|
7-26 |
APPENDIX A: PRODUCT SECURITY PROFILES................................................................................ |
|
7-27 |
|
|
VERSANT® 80/180 ................................................................................................................................ |
|
7-28 |
|
VERSANT® 2100/3100 ........................................................................................................................... |
|
7-31 |
|
March 2019 |
|
Page 1-1 |
Xerox® Security Guide for Entry Production Color Class Products |
|
COLORPRESS® 800/1000/800I/1000I .................................................................................................... |
7-35 |
APPENDIX B: SECURITY EVENTS ...................................................................................................... |
7-39 |
XEROX VERSANT® 80/180 SECURITY EVENTS ........................................................................................ |
7-39 |
XEROX VERSANT® 2100/3100 SECURITY EVENTS .................................................................................. |
7-41 |
COLORPRESS® SECURITY EVENTS ......................................................................................................... |
7-43 |
March 2019 |
Page 1-2 |

Xerox® Security Guide for Entry Production Color Class Products
Introduction
Purpose
The purpose of this document is to disclose information for the Xerox ® Entry Production Color Presses (hereinafter referred to as “the product” or “the system”) with respect to product security. Product Security, for this paper, is defined as how image data is stored and transmitted, how the product behaves in a network environment, and how the product may be accessed both locally and remotely. Furthermore, this document is provided to inform Xerox customers of the design, functions, and features of the product with respect to Information Assurance. This document does not provide tutorial level information about security, connectivity, or the product’s features and functions as this information is readily available elsewhere. We assume the reader has a working knowledge of the topics contained within.
Target Audience
The target audience for this document is Xerox field personnel and customers concerned with IT security.
Disclaimer
The information in this document is accurate to the best knowledge of the authors and is provided without warranty of any kind. In no event shall Xerox be liable for any damages whatsoever resulting from user's use or disregard of the information provided in this document including direct, indirect, incidental, consequential, loss of business profits or special damages, even if Xerox has been advised of the possibility of such damages.
Product Description
Physical Components
Versant® products consist of an input document handler and scanner, marking engine, controller, and user interface. ColorPress® products do not have an input document handler or scanner. A typical configuration is depicted below. Please note that options including finishers, paper trays, document handers, etc. may vary configuration, however, they are not relevant to security and are not discussed.
1. |
HCF. |
8. |
Main Right Front Door. |
2. |
Bypass paper feed tray. |
9. |
Paper Tray Module |
3. |
Front USB Port(s)* |
10. |
Offset Catch Tray |
4. |
Touch screen user interface. |
*Denotes a security related component |
|
5.Toner Door Cover.
March 2019 |
Page 1-3 |
Xerox® Security Guide for Entry Production Color Class Products
6.Main Left Front Door.
7.Main Middle Front Door.
Architecture
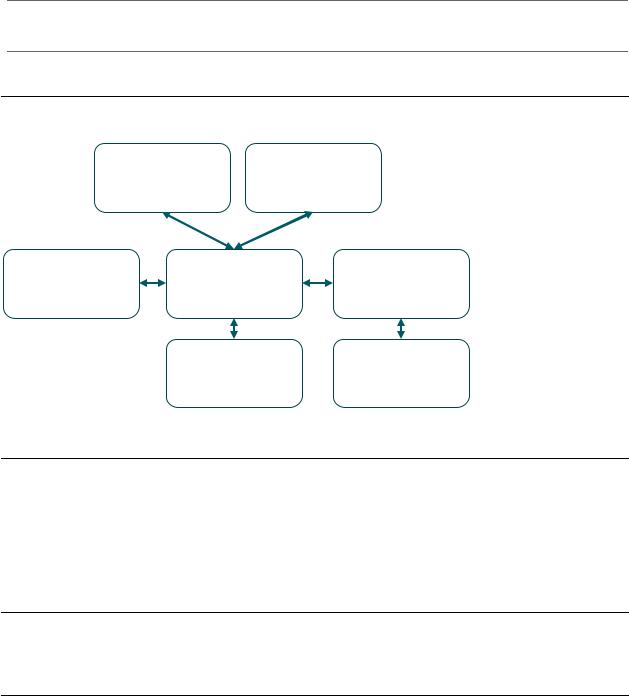
Versant® and ColorPress® products share a common architecture which is depicted below. The following sections describe components in detail.
User Scanner
Interface
Device |
Controller |
External |
|
Storage |
Interfaces |
||
|
|||
|
Marking |
Optional |
|
|
Engine |
Interfaces |
User Interface TRUE FOR VERSANT BUT NOT FOR COLOR PRESS NOTE (There is no Scanner on Color Press or Versant 2100/3100)
The user interface detects soft and hard button actuations and provides text and graphical prompts to the user. The user interface is sometimes referred to as the Graphical User Interface (GUI) or Local UI (LUI) to distinguish it from the remote web server interface (WebUI).
The user interface allows users to access product services and functions. Users with administrative privileges can manage the product configuration settings. User permissions are configurable through Role Based Access Control (RBAC) policies, described in section 6 Identification, Authentication, and Authorization
Scanner
The scanner converts documents from hardcopy to electronic data. A document handler moves originals into a position to be scanned. The scanner provides enough image processing for signal conditioning and formatting. The scanner does not store scanned images.
Marking Engine
The Marking Engine performs copy/print paper feeding and transport, image marking, fusing, and document finishing. The marking engine is comprised of paper supply trays and feeders, paper transport, LED scanner, xerographics, and paper output and finishing. The marking engine is only accessible to the Controller via inter-chip communication with no other access and does not store user data.
March 2019 |
Page 1-4 |

Xerox® Security Guide for Entry Production Color Class Products
Controller
The controller manages document processing using proprietary hardware and algorithms to process documents into high-quality electronic and/or printed reproductions. Documents may be temporarily buffered in RAM during processing. Some models may be equipped with additional storage options such as magnetic Hard Disk Drive (HDD), Solid State Disk (SSD), SD Card, or Flash media. For model specific details please see Appendix A: Product Security Profiles. Versant® and ColorPress® products encrypt user data and include media sanitization (overwrite) options that ensure that erased data cannot be recovered, described further in section 2 User Data Protection.
In addition to managing document processing the controller manages all network functions and services. Details can be found in section Network Security.
The controller handles all I/O communications with connected products. The following section provides a description of each interface. Please note that not all interfaces are supported on all models; details about each model can be found in Appendix A: Product Security Profiles.
Controller External Interfaces
Front Panel USB (Type A) port(s)
One or more USB ports may be located on the front of the product, near the user interface. Front USB ports may be enabled or disabled by a system administrator. The front USB port supports the following:
Walk-up users may insert a USB thumb drive to store or retrieve documents for scanning and/or printing(Versant cannot print from USB – not an option. from a FAT formatted USB device. The controller will only allow reading/writing of a limited set of known document types (such as DOC, PDF, PNG, JPEG, TIFF, etc.). Other file types including binary executables are not supported.
Note that features that use the front USB ports (such as Scan to USB) can be disabled independently or restricted using role-based access controls.
Connection of optional equipment such as NFC or CAC readers.
Firmware updates may be submitted through the front USB ports. (Note that the product must be configured to allow local firmware updates, or the update will not be processed.
10/100/1000 MB Ethernet RJ-45 Network Connector
This is a standard RJ45 Ethernet network connector and confirms to IEEE Ethernet 802.3 standards.
Rear USB (Type B) Target port
A USB type B port located on the controller board at the rear of the product. This port supports the following:
USB target connector used for service.
Note: This port can be disabled completely by a system administrator.
Optional Equipment
RJ-11 Analog Fax and Telephone
The analog fax module connects to the controller. The fax connection supports the Fax Modem T.30 protocol only and will not accept data or voice communication attempts. An external (EXT) is available to connect an external handset. In this configuration, the FAX card acts as a passive relay.
Wireless Network Connector
Xerox Versant® and ColorPress® products do not offer a wireless connector option.
March 2019 |
Page 1-5 |
Xerox® Security Guide for Entry Production Color Class Products
Near Field Communications (NFC) Reader
The system supports an installable RFID reader for authentication and convenience in certain configurations. Versant® products accept the RFID reader via USB on the front of the product. This communication cannot write or change any settings on the system. The data exchanged is not encrypted and may include information including system network status, IP address and product location. NFC functionality can be disabled using the embedded web server of the product. NFC functionality requires a software plugin that can be obtained from Xerox sales and support. NFC functionality is supported via optional touch screen user interface or optional dedicated NFC USB dongle.
Information shared over NFC includes: IPv4 address, IPv6 address, MAC address, UUID (a unique identifier on the NFC client), and fully qualified domain name
SMART CARD – CAC/PIV
All Versant® products support CAC/PIV login by enabling the Versant® Plug-in feature and then enabling the appropriate plug-in. Additional plug-ins can be downloaded from Xerox.com in the Support area online.
Foreign Product Interface
This port is used to connect optional equipment to control access to the machine. A typical application is a coin-operated product where a user must deposit money to enable the machine to print. The information available via the Foreign Product Interface is limited to optically-isolated pulses that can be used to count impressions marked on hardcopy sheets. No user data is transmitted to or from this interface.
March 2019 |
Page 1-6 |

Xerox® Security Guide for Entry Production Color Class Products
User Data Protection
Xerox Entry Production Color Presses receive, process, and may optionally store user data from several sources including: local print, scan, fax NO FAX ON VERSANT OR CP1000, or copy jobs or mobile and cloud applications, etc. Xerox products protect user data being processed by employing strong encryption. When the data is no longer needed, the Image Overwrite (IIO) feature automatically erases and overwrites the data on magnetic media, rendering it unrecoverable. As an additional layer of protection, an extension of IIO called On-Demand Image Overwrite (ODIO) can be invoked to securely wipe all user data from magnetic media.
User Data protection while within product
This section describes security controls that protect user data while it is resident within the product. For a description of security controls that protect data in transit please refer to the following section that discusses data in transit; also, the Network Security section of this document.
Encryption
All user data being processed or stored on the product is encrypted by default. Note that encryption may be disabled to enhance performance on both Versant® and ColorPress® products (though this is not recommended in secure environments).
The algorithm used in the product is AES-256. The encryption key is automatically created at start up and stored in the RAM. The key is deleted by a power-off, due to the physical characteristics of the RAM.
TPM Chip
Some models include a Trusted Platform Module (TPM). The TPM is compliant with ISO/IEC 11889, the international standard for a secure cryptoprocessor, dedicated to secure cryptographic keys. The TPM is used to securely hold the product storage encryption key. Please refer to Appendix A: Product Security Profiles for model specific information.
Media Sanitization (Image Overwrite)
ColorPress® and Versant® products equipped with magnetic hard disk drives are compliant with NIST Special Publication 800-88 Rev1: Guidelines for Media Sanitization. User data is securely erased using a three-pass algorithm as described in the following link: https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-88r1.pdf
Note: Solid State storage media such as Solid-State Disk, eMMC, SD-Card, and Flash media cannot be completely sanitized by multi-pass overwriting methods due to the memory wear mapping that occurs. Additionally, attempts to do so would also greatly erode the operational lifetime of solid state media. Solid State media is therefore not recommended for use in highly secure environments. Please refer to NIST-800-88 “Table A-8: Flash Memory-Based Storage Product
Sanitization” for technical details.
Immediate Image Overwrite
When enabled, Immediate Image Overwrite (IIO) will overwrite any temporary files that were created on the magnetic hard disk that may contain user data. The feature provides continuous automatic overwriting of sensitive data with minimal impact to performance, robust error reporting, and logging via the Audit Log.
On-Demand Image Overwrite
Complementing the Immediate Image Overwrite is On-Demand Overwrite (ODIO). While IIO overwrites individual files, ODIO overwrites entire partitions. The ODIO feature can be invoked at any time and optionally may be scheduled to run automatically.
March 2019 |
Page 2-7 |

Xerox® Security Guide for Entry Production Color Class Products
User Data in Transit
This section focuses on the protection of user data (print/scan/other jobs) in transit as they are submitted to the product for processing and/or are sent from the product to other systems. Additional protections are also discussed in the Network Security section of this document.
Inbound User Data
Print Job Submission
In addition to supporting network level encryption including IPSec and WPA, Xerox products also support encryption of print job data at the time of submission. This can be used to securely transmit print jobs over unencrypted connections or to enhance existing network level security controls.
Encrypted Transport |
Description |
|
|
IPPS (TLS) |
Submit print jobs via Secure Internet Printing Protocol. This protocol is |
|
based on HTTP and utilizes the TLS suite to encrypt data. |
|
|
HTTPS (TLS) |
Securely submit a print job directly to product via the built-in web server. |
|
|
Xerox Print Stream |
The Xerox Global Print Driver® supports document encryption when |
Encryption |
submitting Secure Print jobs to enabled products. Simply check the box to |
|
Enable Encryption when adding the Passcode to the print job. |
|
|
Outbound User Data
Scanning to Network Repository, Email, Fax Server
Versant® digital press products support scanning of hardcopy documents to external network locations including file repositories and email and facsimile services. In addition to supporting network level encryption including IPSec and WPA, Xerox products support the following:
Protocol |
Encryption |
Description |
|
|
|
HTTP |
N/A |
Unencrypted HTTP protocol |
|
|
|
HTTPS (TLS) |
TLS |
HTTP encrypted by TLS |
|
|
|
FTP |
N/A |
Unencrypted FTP |
|
|
|
SFTP (SSH) |
SSH |
FTP encrypted by SSH |
|
|
|
SMBv3 |
Optional |
Encryption may be enabled on a Windows share. |
|
|
Versant® and ColorPress® products currently support SMB |
|
|
encryption. |
|
|
|
SMBv2 |
N/A |
Unencrypted SMB |
|
|
|
SMBv1 |
N/A |
Not used as a transport protocol. Used for network discovery only. |
|
|
|
SMTP (email) |
S/MIME |
The product uses SMTP to transmit data to the email server. Email |
|
|
authentication, encryption, and signing are supported. Please refer |
|
|
to the Network Security section of this document for details. |
|
|
|
Scanning to User Local USB Storage Product
Scan data is transferred directly to the user’s USB product. Filesystem encryption of user products are not supported.
March 2019 Page 2-8
Xerox® Security Guide for Entry Production Color Class Products
Add on AppsCloud, Google, DropBox, and others
Xerox Versant® Color Presses support the Xerox App Gallery® which contains several additional applications that extend the capabilities of Xerox products. Discussion of App security is beyond the scope of this document. Xerox Apps utilize the security framework provided by the 3rd party vendor. (For example, Microsoft O365 or Google apps would utilize Microsoft & Google’s security mechanisms respectively). Please consult documentation for individual Apps and 3rd party security for details.
|
|
Versant® 80/180 Press |
Versant® 2100/3100 |
Color 800/100 Press® |
|
|
|
Press |
|
|
|
Versant 80 Press, Versant |
Versant 2100 Press, |
Color 800/1000 Presses, |
|
|
180 Press |
Versant 3100 Press |
Color 800i/1000i Presses |
|
|
|
|
|
Local Data Encryption (HDD, SDD, IC, SD Card) |
AES-256 |
AES-256 |
AES-256 |
|
|
|
|
|
|
Federal Information Protection Standard 140-2 |
Yes |
Yes |
Yes |
|
|
|
|
|
|
Media Sanitization NIST 800-171 (Image Overwrite) |
All models use magnetic |
Models with magnetic |
Models with magnetic |
|
|
|
HDD |
HDD. See Appendix A: |
HDD. See Appendix A: |
|
|
|
Product Security Profiles |
Product Security Profiles |
Print Submission |
|
|
|
|
|
|
|
|
|
|
IPPS (TLS) |
Supported |
Supported |
Supported |
|
|
|
|
|
|
HTTPS (TLS) |
Supported |
Supported |
Supported |
|
|
|
|
|
|
Xerox Print Stream Encryption |
Supported |
(Not currently supported) |
(Not currently supported) |
|
|
|
|
|
Scan to Repository Server |
|
|
|
|
|
|
|
|
|
|
HTTPS (TLS) |
1.1/1.2 |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
SFTP (SSH) |
SSH-2 |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
SMB (unencrypted) |
v1, v2, v3 |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
SMB (with share encryption enabled) |
V3 |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
HTTP (unencrypted) |
Supported |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
FTP (unencrypted) |
Supported |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
Scan to Fax Server |
|
|
|
|
|
|
|
|
|
|
HTTPS (TLS) |
1.1/1.2 |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
SFTP (SSH) |
SSH-2 |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
SMB (unencrypted) |
v1, v2, v3 |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
SMB (with share encryption enabled) |
V3 |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
S/MIME |
Supported |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
HTTP (unencrypted) |
Supported |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
FTP (unencrypted) |
Supported |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
SMTP (unencrypted) |
Supported |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
Scan to Email |
|
|
|
|
|
|
|
|
|
|
S/MIME |
Supported |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
|
SMTP (unencrypted) |
Supported |
(Not Applicable) |
(Not Applicable) |
|
|
|
|
|
March 2019 |
Page 2-9 |

Xerox® Security Guide for Entry Production Color Class Products
Network Security
Xerox products are designed to offer a high degree of security and flexibility in almost any network environment. This section describes several aspects of the product related to network security.
TCP/IP Ports & Services
Xerox devices are robust, offering support for a wide array of services and protocols. The devices are capable of hosting services as well as acting as a client for others. The diagram below presents a highlevel overview of inbound communications (from other hosts on the network into listening services on the device) and outbound connections initiated by the device (acting as a client to external network services).
Inbound (Listening Services)
Print Services
LPR, IPP, Raw IP, etc.
Management Services
SNMP, Web interface, WebServices, etc.
Infrastructure & Discovery Services IPSEC, SSDP, WSD, mDNS, NetBIOS, etc.
Out Bound (Network Client)
Built-in Scan Services
FTP, HTTP & HTTPS (TLS), SFTP (SSH), SMB, CIFS, SMTP & SMTPS, POP3 & POPS, etc.
Authentication Services
LDAP & LDAPS, SMB, Kerberos.
Infrastructure
ISAKMP (IPSec), DHCP & DHCPv6, etc.
Cloud Services
No direct APE to the above.
Listening services (inbound ports)
The following table summarizes all potentially open ports on the product. These ports can be enabled/disabled within the product configuration.
Port |
|
|
Type |
Service Name |
|
|
|
|
|
20 |
|
|
TCP |
• FTP data (Active) - Client - |
|
|
|
||
|
|
|
|
|
21 |
|
|
TCP |
• FTP – Client - |
|
|
|
||
|
|
|
|
|
25 |
|
|
TCP |
• SMTP |
|
|
|
||
|
|
|
|
|
53 |
|
|
TCP/UDP |
• DNS – Client - |
|
|
|
||
|
|
|
|
|
67 |
|
|
UDP |
• BOOTP/DHCP – Client |
|
|
|
||
|
|
|
|
|
80 |
|
|
TCP |
• HTTP(CWIS) |
|
|
|
||
|
|
|
|
|
80 |
|
|
TCP |
• HTTP(SESAMi Manager) |
|
|
|
||
|
|
|
|
|
80 |
|
|
TCP |
• HTTP(WebDAV) |
|
|
|
||
|
|
|
|
|
88 |
|
|
UDP |
• Kerberos – Client - |
|
|
|
||
|
|
|
|
|
March 2019 |
|
|
Page 3-10 |
|

Xerox® Security Guide for Entry Production Color Class Products
110 |
TCP |
• POP3 – Client - |
|
||
|
|
|
123 |
UDP |
• SNTP – Client - |
|
||
|
|
|
137 |
UDP |
• NETBIOS – Name Service |
|
||
|
|
|
138 |
UDP |
• NETBIOS – Datagram Service |
|
||
|
|
|
161 |
UDP |
• SNMP |
|
||
|
|
|
162 |
UDP |
• SNMP trap |
|
||
|
|
|
389 |
TCP |
• LDAP – Client - |
|
||
|
|
|
427 |
TCP/UDP |
• SLP |
|
||
|
|
|
443 |
TCP |
• HTTP(CWIS) |
|
||
|
|
|
500 |
UDP |
• ISAKMP |
|
||
|
|
|
547 |
UDP |
• DHCPv6 – Client |
|
||
|
|
|
636 |
TCP |
• LDAPS – Client - |
|
||
|
|
|
995 |
TCP |
• POPS – Client - |
|
||
|
|
|
1824 |
TCP |
• HTTPS(OffBox Validation) – Client - |
|
||
|
|
|
1824 |
TCP |
• Xerox Secure Access |
|
||
|
|
|
1900 |
UDP |
• SSDP |
|
||
|
|
|
5353 |
UDP |
• Mdns |
|
||
|
|
|
9100 |
TCP |
• raw IP |
|
||
|
|
|
15000 |
TCP |
• Loopback port for the control of SMTP server |
|
||
|
|
|
Network Encryption
IPSec
Internet Protocol Security (IPsec) is a network security protocol capable of providing encryption and authentication at the packet level. ColorPress® and Versant® products support IPSec for both IPv4 and IPv6 protocols.
|
|
Versant® 80/180 Press |
Versant® 2100/3100 |
|
Color 800/100 Press® |
|
|
|
Press |
|
|
|
|
Versant 80 Press, Versant 180 |
Versant 2100 Press, Versant |
|
Color 800/1000 Presses, Color |
|
|
Press |
3100 Press |
|
800i/1000i Presses |
IPSec |
|
|
|
|
|
|
|
|
|
|
|
|
Supported IP Versions |
IPv4, IPv6 |
IPv4, IPv6 |
|
IPv4, IPv6 |
|
|
|
|
|
|
|
Key exchange authentication method |
Preshared Key & digital |
Preshared Key & digital |
|
Preshared Key & digital |
|
|
signature, device |
signature |
|
signature |
|
|
authentication certificate, |
|
|
|
|
|
server validation certificate |
|
|
|
|
Transport Mode |
Transport & Tunnel mode |
Transport mode only |
|
Transport mode only |
|
|
|
|
|
|
|
Security Protocol |
ESP & AH |
ESP only |
|
ESP only |
|
|
|
|
|
|
|
ESP Encryption Method |
AES, 3DES, Null |
AES, 3DES, DES |
|
AES, 3DES, DES |
|
|
|
|
|
|
|
ESP Authentication Methods |
SHA1, SHA256, None |
SHA1, SHA256, None |
|
SHA1, SHA256, None |
|
|
|
|
|
|
March 2019 |
|
|
Page 3-11 |
||
Xerox® Security Guide for Entry Production Color Class Products
Wireless 802.11 Wi-Fi Protected Access (WPA)
Xerox Versant® and ColorPress® products do not offer a wireless network connector option.
TLS
Versant® and ColorPress® products support the latest version, TLS 1.2.
|
|
Versant® 80/180 Press |
Versant® 2100/3100 |
Color 800/100 Press® |
|
|
|
Press |
|
|
|
Versant 80 Press, Versant |
Versant 2100 Press, |
Color 800/1000 Presses, |
|
|
180 Press |
Versant 3100 Press |
Color 800i/1000i Presses |
|
|
|
|
|
TLS Versions Supported |
|
|
|
|
|
|
|
|
|
|
Product Web Interface |
1.2, 1.1, 1.0 |
1.2, 1.1, 1.0 |
1.2, 1.1, 1.0 |
|
|
|
|
|
|
Product Web Services |
1.2, 1.1, 1.0 |
1.2, 1.1, 1.0 |
1.2, 1.1, 1.0 |
|
|
|
|
|
|
Product IPPS printing |
1.2, 1.1, 1.0 |
1.2, 1.1, 1.0 |
1.2, 1.1, 1.0 |
|
|
|
|
|
|
Remote control |
1.2 |
1.2 |
1.2 |
|
|
|
|
|
March 2019 |
Page 3-12 |
 Loading...
Loading...