TP-Link ER7206 Manual

User Guide
Omada Gigabit VPN Router
© 2021 TP-Link REV1.0.1 1910012985
CONTENTS |
|
About This Guide |
|
Intended Readers................................................................................................................................................................. |
1 |
Conventions........................................................................................................................................................................... |
1 |
More Information.................................................................................................................................................................. |
1 |
Accessing the Router |
|
Determine the Management Method............................................................................................................................ |
3 |
Web Interface Access........................................................................................................................................................ |
4 |
Viewing Status Information |
|
System Status....................................................................................................................................................................... |
7 |
Traffic Statistics ................................................................................................................................................................... |
8 |
Viewing the Interface Statistics......................................................................................................................................................... |
8 |
Viewing the IP Statistics......................................................................................................................................................................... |
9 |
Configuring Network |
|
Overview............................................................................................................................................................................... |
12 |
Supported Features............................................................................................................................................................................... |
12 |
WAN Configuration........................................................................................................................................................... |
13 |
Configuring the Number of WAN Ports...................................................................................................................................... |
13 |
Configuring the WAN Connection................................................................................................................................................. |
13 |
LAN Configuration............................................................................................................................................................. |
23 |
Configuring the IP Address of the LAN Port............................................................................................................................ |
23 |
Configuring the DHCP Server.......................................................................................................................................................... |
24 |
Viewing the DHCP Client List........................................................................................................................................................... |
26 |
MAC Configuration........................................................................................................................................................... |
28 |
Configuring MAC Address................................................................................................................................................................. |
28 |
Switch Configuration........................................................................................................................................................ |
30 |
Viewing the Statistics (only for certain devices).................................................................................................................... |
30 |
Configuring Port Mirror........................................................................................................................................................................ |
31 |
Configuring Rate Control (only for certain devices)............................................................................................................. |
32 |
Configuring Port Config....................................................................................................................................................................... |
33 |
Viewing Port Status................................................................................................................................................................................ |
34 |
VLAN Configuration.......................................................................................................................................................... |
35 |
Creating a VLAN...................................................................................................................................................................................... |
35 |
Configuring the PVID of a Port......................................................................................................................................................... |
36 |
Configuring Preferences |
|
Overview............................................................................................................................................................................... |
39 |
IP Group Configuration ................................................................................................................................................... |
40 |
Adding IP Address Entries................................................................................................................................................................. |
40 |
Grouping IP Address Entries............................................................................................................................................................. |
41 |
Time Range Configuration............................................................................................................................................. |
42 |
VPN IP Pool Configuration............................................................................................................................................. |
44 |
Service Type Configuration........................................................................................................................................... |
45 |
Configuring Transmission |
|
Transmission....................................................................................................................................................................... |
49 |
Overview....................................................................................................................................................................................................... |
49 |
Supported Features............................................................................................................................................................................... |
49 |
NAT Configurations.......................................................................................................................................................... |
51 |
Configuring the One-to-One NAT................................................................................................................................................. |
51 |
Configuring the Virtual Servers....................................................................................................................................................... |
52 |
Configuring the Port Triggering...................................................................................................................................................... |
53 |
Configuring the NAT-DMZ................................................................................................................................................................. |
54 |
Configuring the ALG.............................................................................................................................................................................. |
54 |
Bandwidth Control Configuration................................................................................................................................ |
56 |
Session Limit Configurations........................................................................................................................................ |
58 |
Configuring Session Limit.................................................................................................................................................................. |
58 |
Viewing the Session Limit Information........................................................................................................................................ |
59 |
Load Balancing Configurations.................................................................................................................................... |
60 |
Configuring the Load Balancing...................................................................................................................................................... |
60 |
Configuring the Link Backup............................................................................................................................................................. |
61 |
Configuring the Online Detection.................................................................................................................................................. |
62 |
Routing Configurations................................................................................................................................................... |
63 |
Configuring the Static Routing........................................................................................................................................................ |
63 |
Configuring the Policy Routing........................................................................................................................................................ |
64 |
Viewing the Routing Table.................................................................................................................................................................. |
65 |
Configuration Examples.................................................................................................................................................. |
66 |
Example for Configuring NAT........................................................................................................................................................... |
66 |
Network Requirements........................................................................................................................................................... |
66 |
Network Topology..................................................................................................................................................................... |
66 |
Configuration Scheme........................................................................................................................................................... |
66 |
Configuration Procedure....................................................................................................................................................... |
67 |
Example for Configuring Load Balancing.................................................................................................................................. |
68 |
Network Requirements........................................................................................................................................................... |
68 |
Network Topology..................................................................................................................................................................... |
69 |
Configuration Scheme........................................................................................................................................................... |
69 |
Configuration Procedure....................................................................................................................................................... |
69 |
Example for Configuring Virtual Server....................................................................................................................................... |
70 |
Network Requirements........................................................................................................................................................... |
70 |
Network Topology..................................................................................................................................................................... |
70 |
Configuration Scheme........................................................................................................................................................... |
70 |
Configuration Procedure....................................................................................................................................................... |
70 |
Example for Configuring Policy Routing..................................................................................................................................... |
71 |
Network Requirements........................................................................................................................................................... |
71 |
Network Topology..................................................................................................................................................................... |
72 |
Configuration Scheme........................................................................................................................................................... |
72 |
Configuration Procedure....................................................................................................................................................... |
72 |
Configuring Firewall |
|
Firewall................................................................................................................................................................................... |
76 |
Overview....................................................................................................................................................................................................... |
76 |
Supported Features............................................................................................................................................................................... |
76 |
Firewall Configuration...................................................................................................................................................... |
78 |
Anti ARP Spoofing.................................................................................................................................................................................. |
78 |
Adding IP-MAC Binding Entries......................................................................................................................................... |
78 |
Enable Anti ARP Spoofing.................................................................................................................................................... |
81 |
Configuring Attack Defense.............................................................................................................................................................. |
83 |
Configuring Access Control............................................................................................................................................................. |
85 |
Configuration Examples.................................................................................................................................................. |
87 |
Example for Anti ARP Spoofing....................................................................................................................................................... |
87 |
Network Requirements........................................................................................................................................................... |
87 |
Configuration Scheme........................................................................................................................................................... |
87 |
Configuration Procedure....................................................................................................................................................... |
88 |
Example for Access Control............................................................................................................................................................. |
90 |
Network Requirements........................................................................................................................................................... |
90 |
Configuration Scheme........................................................................................................................................................... |
91 |
Configuration Procedure....................................................................................................................................................... |
91 |
Configuring Behavior Control |
|
Behavior Control................................................................................................................................................................ |
97 |
Overview....................................................................................................................................................................................................... |
97 |
Supported Features............................................................................................................................................................................... |
97 |
Behavior Control Configuration................................................................................................................................... |
98 |
Configuring Web Filtering................................................................................................................................................................... |
98 |
Configure Web Group Filtering.......................................................................................................................................... |
98 |
Configuring URL Filtering................................................................................................................................................... |
101 |
Configuring Web Security............................................................................................................................................................... |
103 |
Configuration Examples................................................................................................................................................ |
105 |
Example for Access Control.......................................................................................................................................................... |
105 |
Network Requirements........................................................................................................................................................ |
105 |
Configuration Scheme........................................................................................................................................................ |
105 |
Configuration Procedure.................................................................................................................................................... |
106 |
Example for Web Security............................................................................................................................................................... |
109 |
Network Requirements........................................................................................................................................................ |
109 |
Configuration Scheme........................................................................................................................................................ |
109 |
Configuration Procedure.................................................................................................................................................... |
109 |
Configuring VPN |
|
VPN....................................................................................................................................................................................... |
112 |
Overview.................................................................................................................................................................................................... |
112 |
Supported Features............................................................................................................................................................................ |
113 |
IPSec VPN Configuration.............................................................................................................................................. |
116 |
Configuring the IPSec Policy......................................................................................................................................................... |
116 |
Configuring the Basic Parameters................................................................................................................................ |
116 |
Configuring the Advanced Parameters..................................................................................................................... |
118 |
Verifying the Connectivity of the IPSec VPN tunnel......................................................................................................... |
120 |
L2TP Configuration......................................................................................................................................................... |
122 |
Configuring the VPN IP Pool.......................................................................................................................................................... |
122 |
Configuring L2TP Globally.............................................................................................................................................................. |
123 |
Configuring the L2TP Server......................................................................................................................................................... |
123 |
Configuring the L2TP Client........................................................................................................................................................... |
124 |
(Optional) Configuring the L2TP Users.................................................................................................................................... |
126 |
Verifying the Connectivity of L2TP VPN Tunnel................................................................................................................. |
127 |
PPTP Configuration........................................................................................................................................................ |
128 |
Configuring the VPN IP Pool.......................................................................................................................................................... |
128 |
Configuring PPTP Globally.............................................................................................................................................................. |
129 |
Configuring the PPTP Server......................................................................................................................................................... |
129 |
Configuring the PPTP Client.......................................................................................................................................................... |
130 |
(Optional) Configuring the PPTP Users.................................................................................................................................... |
131 |
Verifying the Connectivity of PPTP VPN Tunnel................................................................................................................. |
132 |
Configuration Examples................................................................................................................................................ |
134 |
Example for Configuring IPSec VPN.......................................................................................................................................... |
134 |
Network Requirements........................................................................................................................................................ |
134 |
Network Topology.................................................................................................................................................................. |
134 |
Configuration Scheme........................................................................................................................................................ |
134 |
Configuration Procedure.................................................................................................................................................... |
135 |
Example for Configuring L2TP VPN........................................................................................................................................... |
138 |
Network Requirements........................................................................................................................................................ |
138 |
Configuration Scheme........................................................................................................................................................ |
139 |
Configuration Procedure.................................................................................................................................................... |
139 |
Example for Configuring PPTP VPN.......................................................................................................................................... |
141 |
Network Requirements........................................................................................................................................................ |
141 |
Configuration Scheme........................................................................................................................................................ |
141 |
Configuration Procedure.................................................................................................................................................... |
141 |
Configuring Authentication |
|
Overview............................................................................................................................................................................. |
145 |
Typical Topology.................................................................................................................................................................................. |
145 |
Portal Authentication Process...................................................................................................................................................... |
146 |
Supported Features............................................................................................................................................................................ |
146 |
Supported Web Server....................................................................................................................................................... |
147 |
Supported Authentication Server................................................................................................................................. |
147 |
Guest Resources.................................................................................................................................................................... |
147 |
Local Authentication Configuration......................................................................................................................... |
148 |
Configuring the Authentication Page....................................................................................................................................... |
148 |
Configuring the Local User Account......................................................................................................................................... |
151 |
Configuring the Local User Account........................................................................................................................... |
151 |
(Optional) Configuring the Backup of Local Users............................................................................................... |
154 |
Radius Authentication Configuration....................................................................................................................... |
155 |
Configuring Radius Authentication............................................................................................................................................ |
155 |
Onekey Online Configuration...................................................................................................................................... |
158 |
Configuring the Authentication Page....................................................................................................................................... |
158 |
Guest Resources Configuration................................................................................................................................ |
160 |
Configuring the Five Tuple Type.................................................................................................................................................. |
160 |
Configuring the URL Type............................................................................................................................................................... |
162 |
Viewing the Authentication Status........................................................................................................................... |
164 |
Configuration Example.................................................................................................................................................. |
165 |
Network Requirements..................................................................................................................................................................... |
165 |
Configuration Scheme...................................................................................................................................................................... |
165 |
Configuration Procedures............................................................................................................................................................... |
166 |
Configuring the Authentication Page.......................................................................................................................... |
166 |
Configuring Authentication Accounts for the Guests....................................................................................... |
167 |
Managing Services |
|
Services.............................................................................................................................................................................. |
169 |
Overview.................................................................................................................................................................................................... |
169 |
Support Features................................................................................................................................................................................. |
169 |
Dynamic DNS Configurations..................................................................................................................................... |
170 |
Configure and View Peanuthull DDNS...................................................................................................................................... |
170 |
Configure and View Comexe DDNS.......................................................................................................................................... |
171 |
Configure and View DynDNS......................................................................................................................................................... |
172 |
Configure and View NO-IP DDNS............................................................................................................................................... |
174 |
UPnP Configuration........................................................................................................................................................ |
176 |
Configuration Example for Dynamic DNS.............................................................................................................. |
177 |
Network Requirement........................................................................................................................................................................ |
177 |
Configuration Scheme...................................................................................................................................................................... |
177 |
Configuration Procedure................................................................................................................................................................. |
177 |
Specifying the IP Address of the Host........................................................................................................................ |
177 |
Configuring the DDNS function...................................................................................................................................... |
177 |
System Tools |
|
System Tools.................................................................................................................................................................... |
180 |
Overview.................................................................................................................................................................................................... |
180 |
Support Features................................................................................................................................................................................. |
180 |
Admin Setup...................................................................................................................................................................... |
181 |
Admin Setup........................................................................................................................................................................................... |
181 |
Remote Management........................................................................................................................................................................ |
182 |
System Setting...................................................................................................................................................................................... |
182 |
Controller Settings.......................................................................................................................................................... |
184 |
Enable Cloud-Based Controller Management..................................................................................................................... |
184 |
Configure Controller Inform URL................................................................................................................................................. |
185 |
Management..................................................................................................................................................................... |
186 |
Factory Default Restore................................................................................................................................................................... |
186 |
Backup & Restore................................................................................................................................................................................. |
186 |
Reboot........................................................................................................................................................................................................ |
187 |
Firmware Upgrade............................................................................................................................................................................... |
187 |
SNMP.................................................................................................................................................................................... |
188 |
Diagnostics........................................................................................................................................................................ |
189 |
Diagnostics.............................................................................................................................................................................................. |
189 |
Configuring Ping...................................................................................................................................................................... |
189 |
Configuring Traceroute....................................................................................................................................................... |
190 |
Remote Assistance............................................................................................................................................................................. |
191 |
Time Settings.................................................................................................................................................................... |
192 |
Setting the System Time................................................................................................................................................................. |
192 |
Getting time from the Internet Automatically......................................................................................................... |
192 |
Setting the System Time Manually............................................................................................................................... |
193 |
Setting the Daylight Saving Time................................................................................................................................................ |
193 |
Predefined Mode.................................................................................................................................................................... |
193 |
Recurring Mode....................................................................................................................................................................... |
194 |
Date Mode.................................................................................................................................................................................. |
195 |
System Log........................................................................................................................................................................ |
196 |
About This Guide |
Intended Readers |
About This Guide
This User Guide provides information for managing Omada Gigabit VPN Router. Please read this guide carefully before operation.
Intended Readers
This Guide is intended for network managers familiar with IT concepts and network terminologies.
Conventions
When using this guide, notice that features available in SafeStream series products may vary by model and software version. Availability of SafeStream series products may also vary by region or ISP. All images, steps, and descriptions in this guide are only examples and may not reflect your actual experience.
Some models featured in this guide may be unavailable in your country or region. For local sales information, visit https://www.tp-link.com.
The information in this document is subject to change without notice. Every effort has been made in the preparation of this document to ensure accuracy of the contents, but all statements, information, and recommendations in this document do not constitute the warranty of any kind, express or implied. Users must take full responsibility for their application of any products.
In this Guide, the following conventions are used:
■■ The symbol  stands for Note. Notes contain suggestions or references that helps you make better use of your device.
stands for Note. Notes contain suggestions or references that helps you make better use of your device.
■■ Menu Name > Submenu Name > Tab page indicates the menu structure. Status > Traffic Statistics > Interface Statistics means the Interface Statistics page under the Traffic Statistics menu option that is located under the Status menu.
■■ Bold font indicates a button, toolbar icon, menu or menu item.
More Information
■■ The latest software and documentations can be found at Download Center at https://www.tp-link.com/support.
■■ The Installation Guide (IG) can be found where you find this guide or inside the package of the router.
■■ Specifications can be found on the product page at https://www.tp-link.com.
■■ To ask questions, find answers, and communicate with TP-Link users or engineers, please visit https://community.tp-link.com to join TP-Link Community.
■■ Our Technical Support contact information can be found at the Contact Technical Support page at https://www.tp-link.com/support.
User Guide 
 1
1
Part 1
Accessing the Router
CHAPTERS
1.Determine the Management Method
2.Web Interface Access

Accessing the Router |
Determine the Management Method |
1Determine the Management Method
Before building your network, choose a proper method to manage your router based on your actual network situation. The router supports two configuration options: Standalone Mode or Controller Mode.
■■ Controller Mode
If you want to configure and manage a large-scale network centrally, which consists of mass devices such as access points, switches, and gateways, Controller Mode is recommended. In Controller Mode, the router can be centrally configured and monitored via Omada SDN Controller.
To prepare the router for Omada SDN Controller Management, refer to Controller Settings. For detailed instructions about the network topology in such situations and how to use Omada SDN Controller, refer to the User Guide of Omada SDN Controller. The guide can be found on the download center of our official website: https://www.tp-link.com/support/download/.
■■ Standalone Mode
If you have a relatively small-sized network and only one or just a small number of devices need to be managed, Standalone Mode is recommended. In Standalone Mode, you can access and manage the router using the GUI (Graphical User Interface, also called web interface in this text). The router uses two built-in web servers, HTTP server and HTTPS server, for user authentication.
This User Guide introduces how to configure and monitor the router in Standalone Mode.
 Note:
Note:
The GUI is inaccessible while the router is managed by a controller. To turn the router back to Standalone Mode and access its GUI, you can forget the router on the controller or reset the router.
User Guide  3
3
Accessing the Router |
Web Interface Access |
2Web Interface Access
The following example shows how to log in via the web browser.
1)Connect a PC to a LAN port of the router with an RJ45 port properly. If your computer is configured with a fixed IP address, change it to “Obtain an IP address automatically“.
2)Open a web browser and type the default management address http://192.168.0.1 in the address field of the browser, then press the Enter key.
Figure 2-1 Enter the router's IP Address In the Browser
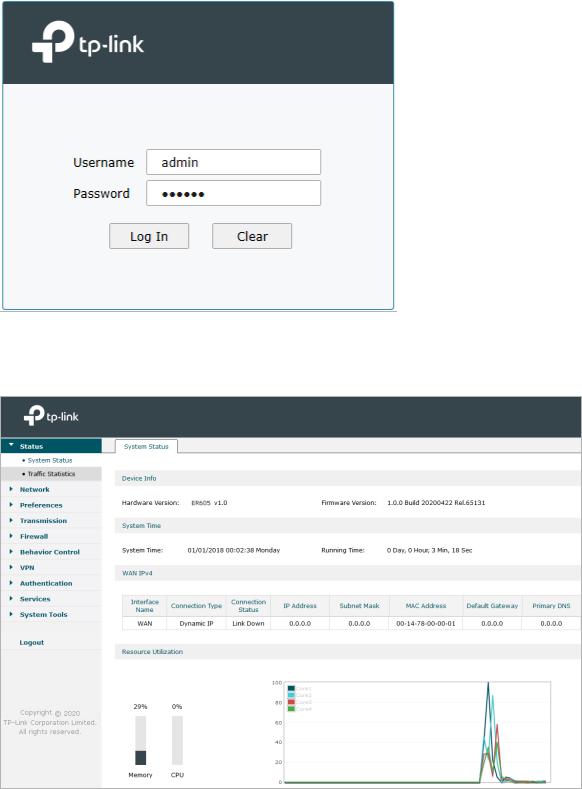
3) Create a username and a password for subsequent login attempts.
Figure 2-2 Create a Username and a Password
User Guide 
 4
4
Accessing the Router |
Web Interface Access |
4) Use the username and password set above to log in to the webpage.
Figure 2-3 Login Authentication
5)After a successful login, the main page will appear as shown below, and you can configure the function by clicking the setup menu on the left side of the screen.
Figure 2-4 Web Interface
User Guide 
 5
5
Part 2
Viewing Status Information
CHAPTERS
1.System Status
2.Traffic Statistics
Viewing Status Information |
System Status |
1System Status
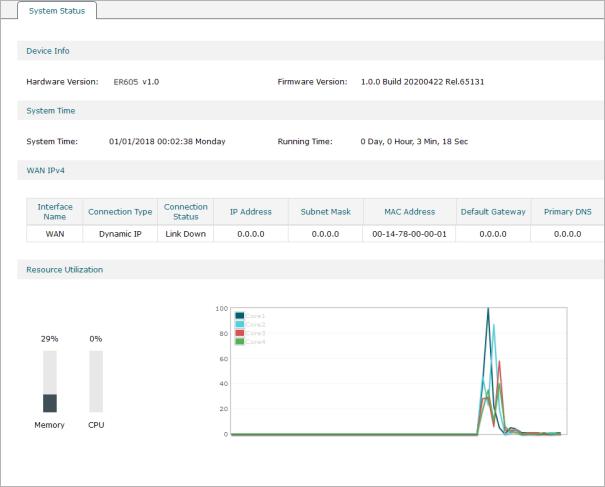
The System Status page displays the basic system information (like the hardware version, firmware version and system time) and the running information (like the WAN interface status, memory utilization and CPU utilization).
Choose the menu Status > System Status > System Status to load the following page.
Figure 1-1 System Status
User Guide 
 7
7
Viewing Status Information |
Traffic Statistics |
2Traffic Statistics
Traffic Statistics displays detailed information relating to the data traffic of interfaces and IP addresses. You can monitor the traffic and locate faults according to this information.
With the Traffic Statistics function, you can:
■■ View the traffic statistics on each interface.
■■ Specify an IP address range, and view the traffic statistics of the IP addresses in this range.
2.1Viewing the Interface Statistics
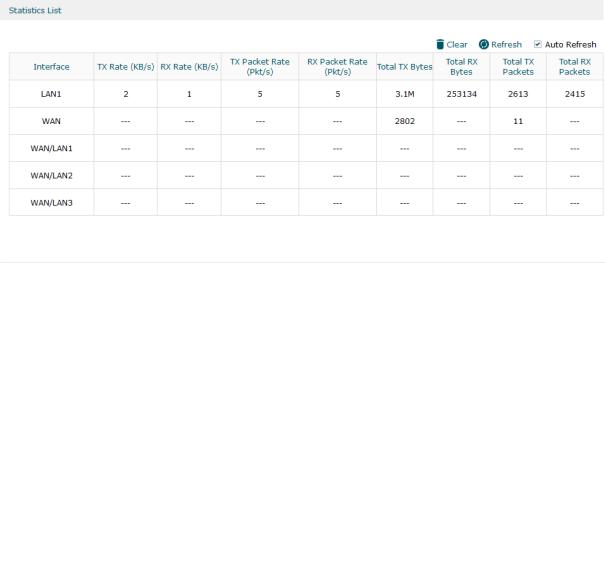
Choose the menu Status > Traffic Statistics > Interface Statistics to load the following page.
Figure 2-1 Interface Statistics
View the detailed traffic information of each interface in the statistics list.
|
TX Rate (KB/s) |
Displays the rate for transmitting data in kilobytes per second. |
|
|
|
|
|
|
RX Rate (KB/s) |
Displays the rate for receiving data in kilobytes per second. |
|
|
|
|
|
|
TX Packet Rate |
Displays the rate for transmitting data in packets per second. |
|
|
(Pkt/s) |
|
|
|
RX Packet Rate |
Displays the rate for receiving data in packets per second. |
|
|
(Pkt/s) |
|
|
|
Total TX Bytes |
Displays the bytes of packets transmitted on the interface. |
|
|
|
|
|
|
Total RX Bytes |
Displays the bytes of packets received on the interface. |
|
|
|
|
|
|
Total TX Packets |
Displays the number of packets transmitted on the interface. |
|
|
|
|
|
|
Total RX Packets |
Displays the number of packets received on the interface. |
|
|
|
|
|
User Guide 
 8
8
Viewing Status Information |
Traffic Statistics |
You can enable Auto Refresh or click Refresh to get the latest statistics information, or click Clear to clear the current statistics information.
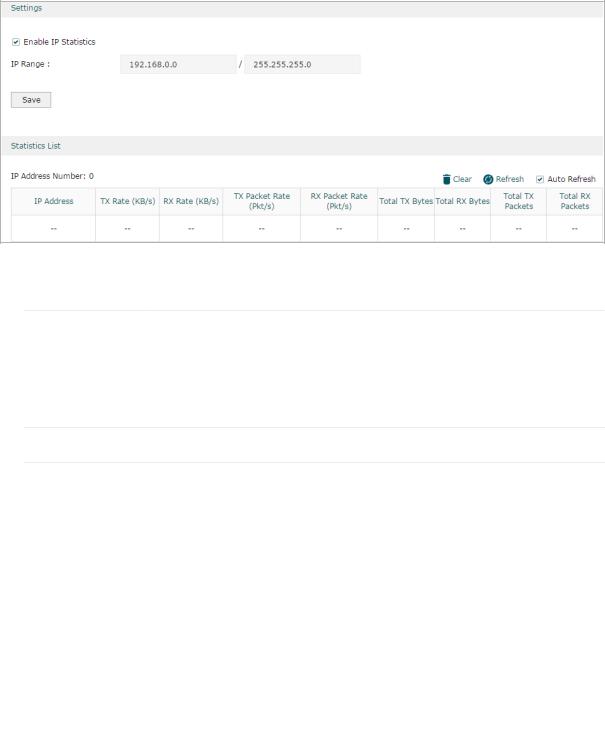
2.2Viewing the IP Statistics
Choose the menu Status > Traffic Statistics > IP Statistics to load the following page.
Figure 2-2 IP Statistics
Follow these steps to view the traffic statistics of the specific IP addresses:
1) In the Settings section, enable IP Statistics and specify an IP range to monitor.
Enable IP |
Check the box to enable IP Statistics. |
Statistics |
|
IP Range |
Specify an IP range. The gateway will monitor the packets whose source |
|
IP addresses or destination IP addresses are in this range, and display the |
|
statistics information in Statistics List. |
2) In the Statistics List section, view the detailed traffic information of the IP addresses.
|
IP Address |
Displays the number of active users whose IP address is in the specified IP |
|
|
Number |
range. |
|
|
TX Rate (KB/s) |
Displays the rate for transmitting data in kilobytes per second. |
|
|
|
|
|
|
RX Rate (KB/s) |
Displays the rate for receiving data in kilobytes per second. |
|
|
|
|
|
|
TX Packet Rate |
Displays the rate for transmitting data in packets per second. |
|
|
(Pkt/s) |
|
|
|
RX Packet Rate |
Displays the rate for receiving data in packets per second. |
|
|
(Pkt/s) |
|
|
|
Total TX Bytes |
Displays the bytes of packets transmitted by the user who owns the IP address. |
|
|
|
|
|
|
Total RX Bytes |
Displays the bytes of packets received by the user who owns the IP address. |
|
|
|
|
|
User Guide 
 9
9

Viewing Status Information |
Traffic Statistics |
||
|
|
|
|
|
|
Total TX Packets |
Displays the number of packets transmitted by the user who owns the IP |
|
|
|
address. |
|
|
Total RX Packets |
Displays the number of packets received by the user who owns the IP address. |
You can enable Auto Refresh or click Refresh to get the latest statistics information, or click Clear to clear the current statistics information.
User Guide 
 10
10
Part 3
Configuring Network
CHAPTERS
1.Overview
2.WAN Configuration
3.LAN Configuration
4.MAC Configuration
5.Switch Configuration
6.VLAN Configuration
Configuring Network |
Overview |
1Overview
The Network module provides basic router functions, including WAN connection, DHCP service, VLAN and more.
1.1Supported Features
WAN
You can configure up to four WAN ports for your network. Each WAN port has its own internet connection, providing link backup and load balancing.
LAN
For LAN configuration, you can configure the LAN IP address and DHCP (Dynamic Host Configuration Protocol) server. With its DHCP server enabled, the router can automatically assign IP addresses to hosts in the LAN.
MAC
You can change the default MAC address of the WAN port or LAN port according to your needs.
Switch
The router supports some basic switch port management functions, like Port Mirror, Rate Control, Flow Control and Port Negotiation, to help you monitor the traffic and manage the network effectively.
VLAN
The router supports 802.1Q VLAN, which can divide the LAN into multiple VLANs, helping manage the network more effectively.
User Guide 
 12
12
Configuring Network |
WAN Configuration |
2WAN Configuration
You can configure multiple WAN ports for your network. Each WAN port can have its own WAN connection, providing link backup and load balancing.
To complete WAN configuration, follow these steps:
1)Configure the number of WAN ports.
2)Configure the WAN connection.
2.1Configuring the Number of WAN Ports
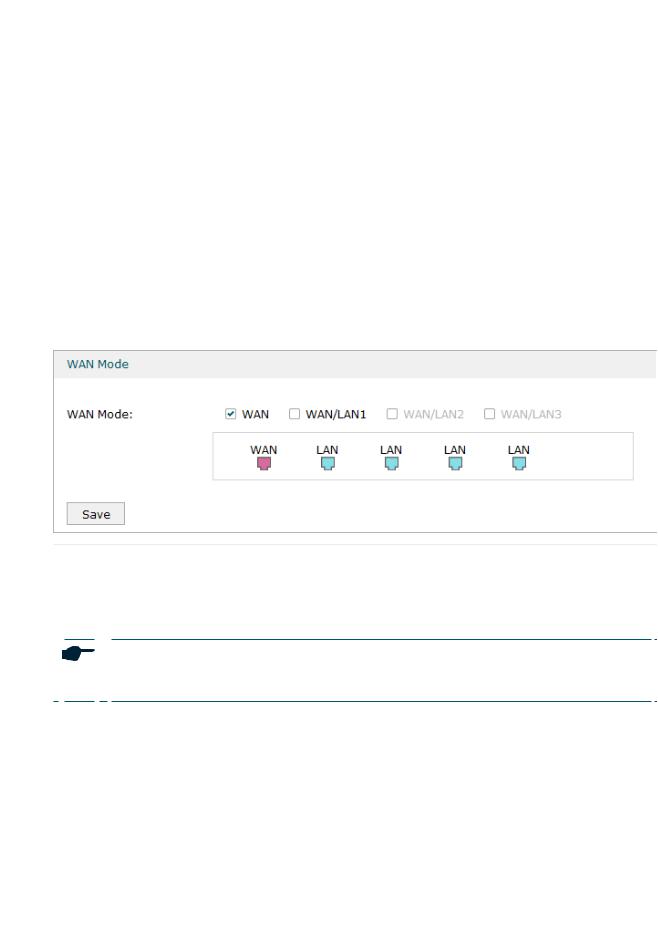
Choose the menu Network > WAN > WAN Mode to load the following page.
Figure 2-1 Configuring the WAN Mode
|
WAN Mode |
Click the check box to enable the port as a WAN port. To configure multiple WAN |
||
|
|
|
|
ports, enable the ports one by one. |
|
|
|
|
For certain devices, you can configure one SFP port as the WAN port. |
|
|
|
|
|
|
|
|
|
|
Note:
The router will reboot after switching the WAN mode.
2.2Configuring the WAN Connection
The router supports five connection types: Static IP, Dynamic IP, PPPoE, L2TP, PPTP, you can choose one according to the service provided by your ISP.
Static IP: If your ISP provides you with a fixed IP address and the corresponding parameters, choose Static IP.
Dynamic IP: If your ISP automatically assigns the IP address and the corresponding parameters, choose Dynamic IP.
User Guide 
 13
13
Configuring Network |
WAN Configuration |
PPPoE: If your ISP provides you with a PPPoE account, choose PPPoE.
L2TP: If your ISP provides you with an L2TP account, choose L2TP.
PPTP: If your ISP provides you with a PPTP account, choose PPTP.
Note:
The number of configurable WAN ports is decided by WAN Mode. To configure Wan Mode, refer to
Configuring the Number of WAN Ports.
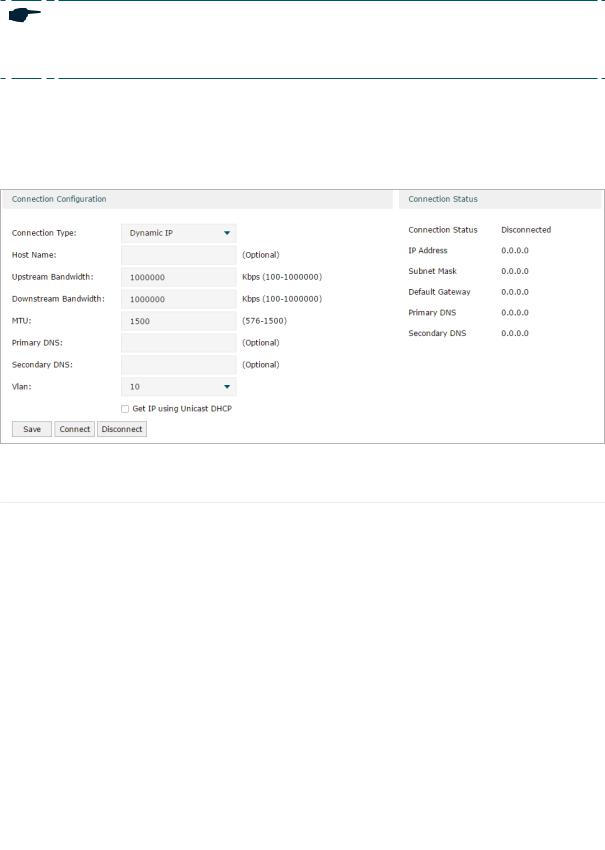
■■ Configuring the Dynamic IP
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-2 Configuring the Dynamic IP
In the Connection Configuration section, select the connection type as Dynamic IP. Enter the corresponding parameters and click Save.
|
Connection Type |
Choose the connection type as Dynamic IP if your ISP automatically assigns the IP |
|
|
|
address. |
|
|
Host Name |
(Optional) Enter a name for the router. It is null by default. |
|
|
|
|
|
|
Upstream |
Specify the upstream bandwidth of the WAN port. The value configured here is the |
|
|
Bandwidth |
upper limit of the “Maximum Upstream Bandwidth” on Transmission > Bandwidth |
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
ensure this parameter is set correctly. |
|
|
Downstream |
Specify the downstream bandwidth of the WAN port. The value configured here is the |
|
|
Bandwidth |
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth |
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
ensure this parameter is set correctly. |
|
|
MTU |
Specify the MTU (Maximum Transmission Unit) of the WAN port. |
|
|
|
MTU is the maximum data unit transmitted in the physical network. When Dynamic |
|
|
|
IP is selected, MTU can be set in the range of 576-1500 bytes. The default value is |
|
|
|
1500. |
|
User Guide 
 14
14
Configuring Network |
WAN Configuration |
|||
|
|
|
|
|
|
|
Primary/ |
(Optional) Enter the IP address of the DNS server provided by your ISP. |
|
|
|
Secondary DNS |
|
|
|
|
VLAN |
Add the WAN port to a VLAN. Generally, you don’t need to manually configure it |
|
|
|
|
unless required by your ISP. |
|
|
|
|
By default, the WAN port is automatically assigned to a VLAN, and the egress rule of |
|
|
|
|
the VLAN is UNTAG, so the packets are transmitted by the WAN port without VLAN |
|
|
|
|
tags. If you want the WAN port to transmit packets with VLAN tag, you need to create |
|
|
|
|
the corresponding VLAN first and configure its egress rule as TAG, then manually |
|
|
|
|
add the WAN port to that VLAN. To create VLANs, go to Network > VLAN > VLAN. |
|
|
|
Get IP using |
The broadcasting requirement may not be supported by a few ISPs. Select this |
|
|
|
Unicast DHCP |
option if you can not get the IP address from your ISP even with a normal network |
|
|
|
|
connection. This option is not required generally. |
|
|
|
Connect/ |
Click the button to active/terminate the connection. |
|
|
|
Disconnect |
|
|
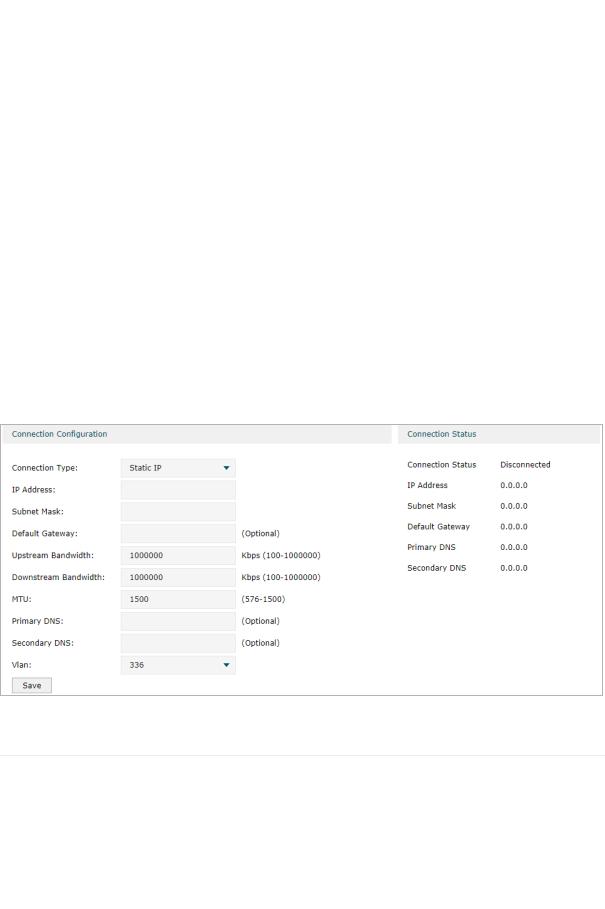
■■ Configuring the Static IP
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-3 Configuring the Static IP
In Connection Configuration section, select the connection type as Static IP. Enter the corresponding parameters and click Save.
|
Connection Type |
Choose the connection type as Static IP if your ISP has offered you a fixed IP |
|
|
|
address. |
|
|
IP Address |
Enter the IP address provided by your ISP. |
|
|
|
|
|
|
Subnet Mask |
Enter the subnet mask provided by your ISP. |
|
|
|
|
|
|
Default Gateway |
Enter the default gateway provided by your ISP. |
|
|
|
|
|
User Guide 
 15
15
Configuring Network |
WAN Configuration |
|||
|
|
|
|
|
|
|
Upstream |
Specify the downstream bandwidth of the WAN port. The value configured here is the |
|
|
|
Bandwidth |
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth |
|
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
|
ensure this parameter is set correctly. |
|
|
|
Downstream |
Specify the downstream bandwidth of the WAN port. The value configured here is the |
|
|
|
Bandwidth |
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth |
|
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
|
ensure this parameter is set correctly. |
|
|
|
MTU |
Specify the MTU (Maximum Transmission Unit) of the WAN port. |
|
|
|
|
MTU is the maximum data unit transmitted in the physical network. When Static IP is |
|
|
|
|
selected, MTU can be set in the range of 576-1500 bytes. The default value is 1500. |
|
|
|
Primary/ |
(Optional) Enter the IP address of the DNS server provided by your ISP. |
|
|
|
Secondary DNS |
|
|
|
|
VLAN |
Add the WAN port to a VLAN. Generally, you don’t need to manually configure it |
|
|
|
|
unless required by your ISP. |
|
|
|
|
By default, the WAN port is automatically assigned to a VLAN, and the egress rule of |
|
|
|
|
the VLAN is UNTAG, so the packets are transmitted by the WAN port without VLAN |
|
|
|
|
tags. If you want the WAN port to transmit packets with VLAN tag, you need to create |
|
|
|
|
the corresponding VLAN first and configure its egress rule as TAG, then manually |
|
|
|
|
add the WAN port to that VLAN. To create VLANs, go to Network > VLAN > VLAN. |
|
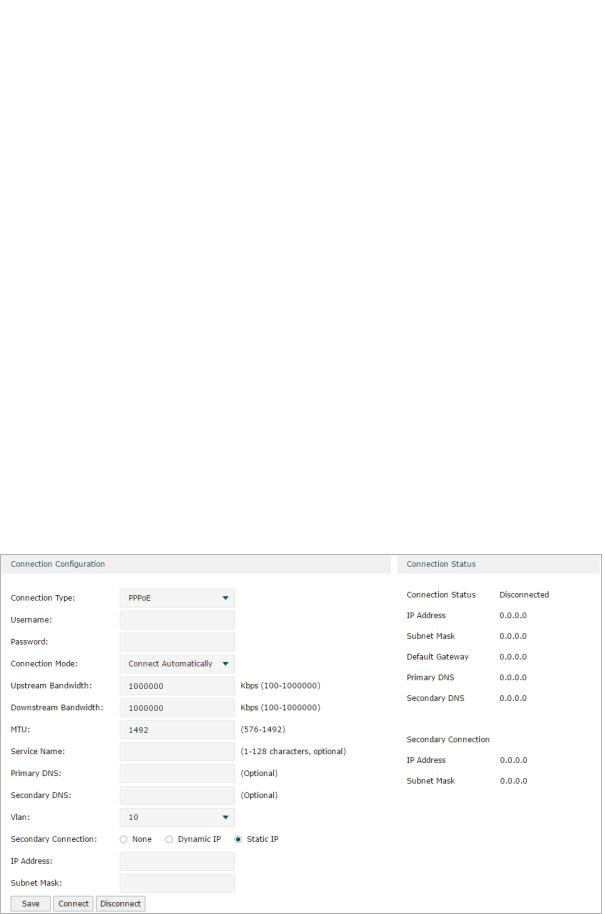
■■ Configuring the PPPoE
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-4 Configuring the PPPoE
User Guide 
 16
16

Configuring Network |
WAN Configuration |
In the Connection Configuration section, select the connection type as PPPoE. Enter the corresponding parameters and click Save.
|
Connection Type |
Choose the connection type as PPPoE if your ISP provides you with a PPPoE |
|
|
|
account. |
|
|
Username |
Enter the PPPoE username provided by your ISP. |
|
|
|
|
|
|
Password |
Enter the PPPoE password provided by your ISP. |
|
|
|
|
|
|
Connection |
Choose the connection mode, including Connect Automatically, Connect Manually |
|
|
Mode |
and Time-Based. |
|
|
|
Connect Automatically: The router will activate the connection automatically when |
|
|
|
the router reboots or the connection is down. |
|
|
|
Connect Manually: You can manually activate or terminate the connection. |
|
|
|
Time-Based: During the specified period, the router will automatically activate the |
|
|
|
connection. |
|
|
Time |
Choose the effective time range when the Connection Mode is chosen as Time- |
|
|
|
Based. To create the time range, go to Preferences > Time Range > Time Range. |
|
|
Upstream |
Specify the upstream bandwidth of the WAN port. The value configured here is the |
|
|
Bandwidth |
upper limit of the “Maximum Upstream Bandwidth” on Transmission > Bandwidth |
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
ensure this parameter is set correctly. |
|
|
Downstream |
Specify the downstream bandwidth of the WAN port. The value configured here is the |
|
|
Bandwidth |
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth |
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
ensure this parameter is set correctly. |
|
|
MTU |
Specify the MTU (Maximum Transmission Unit) of the WAN port. |
|
|
|
MTU is the maximum data unit transmitted in the physical network. When PPPoE is |
|
|
|
selected, MTU can be set in the range of 576-1492 bytes. The default value is 1492. |
|
|
Service Name |
(Optional) Enter the service name. This parameter is not required unless provided by |
|
|
|
your ISP. It is null by default. |
|
|
Primary/ |
(Optional) Enter the IP address of the DNS server provided by your ISP. |
|
|
Secondary DNS |
|
|
|
VLAN |
Add the WAN port to a VLAN. Generally, you don’t need to manually configure it |
|
|
|
unless required by your ISP. |
|
|
|
By default, the WAN port is automatically assigned to a VLAN, and the egress rule of |
|
|
|
the VLAN is UNTAG, so the packets are transmitted by the WAN port without VLAN |
|
|
|
tags. If you want the WAN port to transmit packets with VLAN tag, you need to create |
|
|
|
the corresponding VLAN first and configure its egress rule as TAG, then manually |
|
|
|
add the WAN port to that VLAN. To create VLANs, go to Network > VLAN > VLAN. |
|
User Guide 
 17
17
Configuring Network |
WAN Configuration |
|
Secondary |
Secondary connection is required by some ISPs. Select the connection type required |
|
|
Connection |
by your ISP. |
|
|
|
None: Select this if the secondary connection is not required by your ISP. |
|
|
|
Dynamic IP: Select this if your ISP automatically assigns the IP address and subnet |
|
|
|
mask for the secondary connection. |
|
|
|
Static IP: Select this if your ISP provides you with a fixed IP address and subnet mask |
|
|
|
for the secondary connection. |
|
|
Connect/ |
Click the button to active/terminate the connection. |
|
|
Disconnect |
|
|
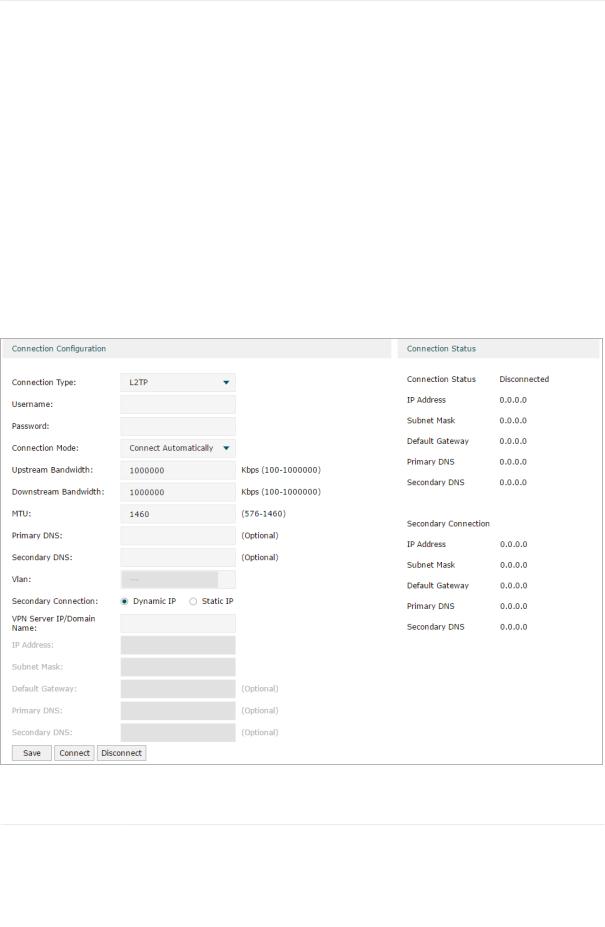
■■ Configuring the L2TP
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-5 Configuring the L2TP
In the Connection Configuration section, select the connection type as L2TP. Enter the corresponding parameters and click Save.
|
Connection Type |
Choose the connection type as L2TP if your ISP provides you with an L2TP account. |
|
|
|
|
|
|
Username |
Enter the L2TP username provided by your ISP. |
|
|
|
|
|
|
Password |
Enter the L2TP password provided by your ISP. |
|
|
|
|
|
User Guide 
 18
18

Configuring Network |
WAN Configuration |
|
Connection |
Choose the connection mode, including Connect Automatically, Connect Manually |
|
|
Mode |
and Time-Based. |
|
|
|
Connect Automatically: The router will activate the connection automatically when |
|
|
|
the router reboots or the connection is down. |
|
|
|
Connect Manually: You can manually activate or terminate the connection. |
|
|
|
Time-Based: During the specified period, the router will automatically activate the |
|
|
|
connection. |
|
|
Time |
Choose the effective time range when the Connection Mode is chosen as Time- |
|
|
|
Based. To create the time range, go to Preferences > Time Range > Time Range. |
|
|
Upstream |
Specify the upstream bandwidth of the WAN port. The value configured here is the |
|
|
Bandwidth |
upper limit of the “Maximum Upstream Bandwidth” on Transmission > Bandwidth |
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
ensure this parameter is set correctly. |
|
|
Downstream |
Specify the downstream bandwidth of the WAN port. The value configured here is the |
|
|
Bandwidth |
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth |
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
ensure this parameter is set correctly. |
|
|
MTU |
Specify the MTU (Maximum Transmission Unit) of the WAN port. |
|
|
|
MTU is the maximum data unit transmitted in the physical network. When L2TP is |
|
|
|
selected, MTU can be set in the range of 576-1460 bytes. The default value is 1460. |
|
|
Primary/ |
(Optional) Enter the IP address of the DNS server provided by your ISP. |
|
|
Secondary DNS |
|
|
|
VLAN |
Add the WAN port to a VLAN. Generally, you don’t need to manually configure it |
|
|
|
unless required by your ISP. |
|
|
|
By default, the WAN port is automatically assigned to a VLAN, and the egress rule of |
|
|
|
the VLAN is UNTAG, so the packets are transmitted by the WAN port without VLAN |
|
|
|
tags. If you want the WAN port to transmit packets with VLAN tag, you need to create |
|
|
|
the corresponding VLAN first and configure its egress rule as TAG, then manually |
|
|
|
add the WAN port to that VLAN. To create VLANs, go to Network > VLAN > VLAN. |
|
|
Secondary |
Select the secondary connection type provided by your ISP. If you select the |
|
|
Connection |
secondary connection type as Static IP, you need to configure IP Address, Subnet |
|
|
|
Mask, Default Gateway, Primary/Second DNS. |
|
|
|
The secondary connection is required for L2TP connection. The router will get |
|
|
|
some necessary information after the secondary connection succeeded. These |
|
|
|
information will be used in the L2TP connection process. |
|
|
VPN Server/ |
Enter the VPN Server/Domain Name provided by your ISP. |
|
|
Domain Name |
|
|
|
IP Address |
Enter the IP address provided by your ISP for the secondary connection. |
|
|
|
|
|
|
Subnet Mask |
Enter the subnet mask provided by your ISP for the secondary connection. |
|
|
|
|
|
User Guide  19
19
Configuring Network |
WAN Configuration |
|||
|
|
|
|
|
|
|
Default Gateway |
Enter the default gateway provided by your ISP for the secondary connection. |
|
|
|
|
|
|
|
|
Primary/ |
Enter the primary/secondary DNS provided by your ISP for the secondary |
|
|
|
Secondary DNS |
connection. |
|
|
|
Connect/ |
Click the button to active/terminate the connection. |
|
|
|
Disconnect |
|
|
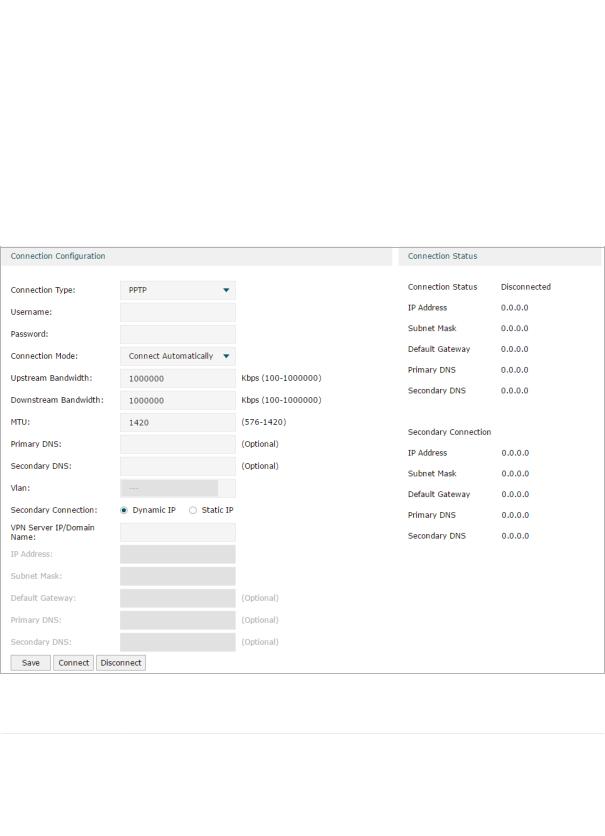
■■ Configuring the PPTP
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-6 Configuring the PPTP
In Connection Configuration section, select the connection type as PPTP. Enter the corresponding parameters and click Save.
|
Connection Type |
Choose the connection type as PPTP if your ISP provides you with a PPTP account. |
|
|
|
|
|
|
Username |
Enter the PPTP username provided by your ISP. |
|
|
|
|
|
|
Password |
Enter the PPTP password provided by your ISP. |
|
|
|
|
|
User Guide 
 20
20

Configuring Network |
WAN Configuration |
|
Connection |
Choose the connection mode, including Connect Automatically, Connect Manually |
|
|
Mode |
and Time-Based. |
|
|
|
Connect Automatically: The router will activate the connection automatically when |
|
|
|
the router reboots or the connection is down. |
|
|
|
Connect Manually: You can manually activate or terminate the connection. |
|
|
|
Time-Based: During the specified period, the router will automatically activate the |
|
|
|
connection. |
|
|
Time |
Choose the effective time range when the Connection Mode is chosen as Time- |
|
|
|
Based. To create the time range, go to Preferences > Time Range > Time Range. |
|
|
Upstream |
Specify the upstream bandwidth of the WAN port. The value configured here is the |
|
|
Bandwidth |
upper limit of the “Maximum Upstream Bandwidth” on Transmission > Bandwidth |
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
ensure this parameter is set correctly. |
|
|
Downstream |
Specify the downstream bandwidth of the WAN port. The value configured here is the |
|
|
Bandwidth |
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth |
|
|
|
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please |
|
|
|
ensure this parameter is set correctly. |
|
|
MTU |
Specify the MTU (Maximum Transmission Unit) of the WAN port. |
|
|
|
MTU is the maximum data unit transmitted in the physical network. When PPTP is |
|
|
|
selected, MTU can be set in the range of 576-1420 bytes. The default value is 1420. |
|
|
Primary/ |
(Optional) Enter the IP address of the DNS server provided by your ISP. |
|
|
Secondary DNS |
|
|
|
VLAN |
Add the WAN port to a VLAN. Generally, you don’t need to manually configure it |
|
|
|
unless required by your ISP. |
|
|
|
By default, the WAN port is automatically assigned to a VLAN by default, and the |
|
|
|
egress rule of the VLAN is UNTAG, so the packets are transmitted by the WAN port |
|
|
|
without VLAN tags. If you want the WAN port to transmit packets with VLAN tag, you |
|
|
|
need to create the corresponding VLAN first and configure its egress rule as TAG, |
|
|
|
then manually add the WAN port to that VLAN. To create VLANs, go to Network > |
|
|
|
VLAN > VLAN. |
|
|
Secondary |
Select the secondary connection type provided by your ISP. If you select the |
|
|
Connection |
secondary connection type as Static IP, you need to configure IP Address, Subnet |
|
|
|
Mask, Default Gateway, Primary/Second DNS. |
|
|
|
The secondary connection is required for PPTP connection. The router will get |
|
|
|
some necessary information after the secondary connection succeeded. These |
|
|
|
information will be used in the PPTP connection process. |
|
|
VPN Server/ |
Enter the VPN Server/Domain Name provided by your ISP. |
|
|
Domain Name |
|
|
|
IP Address |
Enter the IP address provided by your ISP for the secondary connection. |
|
|
|
|
|
|
Subnet Mask |
Enter the subnet mask provided by your ISP for the secondary connection. |
|
|
|
|
|
User Guide  21
21

Configuring Network |
WAN Configuration |
|||
|
|
|
|
|
|
|
Default Gateway |
Enter the default gateway provided by your ISP for the secondary connection. |
|
|
|
|
|
|
|
|
Primary/ |
Enter the primary/secondary DNS provided by your ISP for the secondary |
|
|
|
Secondary DNS |
connection. |
|
|
|
Connect/ |
Click the button to active/terminate the connection. |
|
|
|
Disconnect |
|
|
User Guide 
 22
22
 Loading...
Loading...