ZyXEL NBG420N User Manual

PART VI
Appendices and
Index
Product Specifications and Wall-Mounting Instructions (273)
Pop-up Windows, JavaScripts and Java Permissions (279)
IP Addresses and Subnetting (285)
Setting up Your Computer’s IP Address (293)
Wireless LANs (309)
Services (321)
Legal Information (325)
Customer Support (329)
Index (335)
271
272
APPENDIX A
Product Specifications and Wall-
Mounting Instructions
The following tables summarize the NBG420N’s hardware and firmware features.
Table 113 Hardware Features
Dimensions (W x D x H) 115 x 162 x 33 mm
Weight 250g
Power Specification Input: 120~240 AC, 50~60 Hz
Output: 12 V AC 1 A
Ethernet ports Auto-negotiating: 10 Mbps or 100 Mbps in either half-duplex or full-duplex
4-5 Port Switch A combination of switch and router makes your NBG420N a cost-effective
LEDs PWR, LAN1-4, WAN, WLAN, WPS
Reset Button The reset button is built into the rear panel. Use this button to restore the
WPS button Press the WPS on two WPS enabled devices within 120 seconds for a
Antenna The NBG420N is equipped with two 2dBi (2.4GHz) detachable antennas to
Operation Environment Temperature: 0º C ~ 40º C
Storage Environment Temperature: -20º C ~ 60º C
Distance between the
centers of the holes on
the device’s back.
Screw size for wallmounting
mode.
Auto-crossover: Use either crossover or straight-through Ethernet cables.
and viable network solution. You can add up to four computers to the
NBG420N without the cost of a hub when connecting to the Internet through
the WAN port. You can add up to five computers to the NBG420N when you
connect to the Internet in AP mode. Add more than four computers to your
LAN by using a hub.
NBG420N to its factory default settings. Press for 1 second to restart the
device. Press for 5 seconds to restore to factory default settings.
security-enabled wireless connection.
provide clear radio transmission and reception on the wireless network.
Humidity: 20% ~ 95% RH (Non-condensing)
Humidity: 20% ~ 95% RH (Non-condensing)
120 mm
M4 Tap Screw
NBG420N User’s Guide
273

Appendix A Product Specifications and Wall-Mounting Instructions
Table 114 Firmware Features
FEATURE DESCRIPTION
Default IP Address 192.168.1.1
Default Subnet Mask 255.255.255.0 (24 bits)
Default Password 1234
DHCP Pool 192.168.1.33 to 192.168.1.64
Wireless Interface Wireless LAN
Default Wireless SSID Wireless LAN: ZyXEL
Wireless LAN when WPS enabled: ZyXEL WPS
Default Wireless IP Address Wireless LAN: Same as LAN (192.168.1.1)
Default Wireless Subnet
Mask
Default Wireless DHCP
Pool Size
Device Management Use the web configurator to easily configure the rich range of features on
Wireless Functionality Allows IEEE 802.11b and/or IEEE 802.11g and/or IEEE 802.11n wireless
Wireless LAN: Same as LAN (255.255.255.0)
Wireless LAN: Same as LAN (32 from 192.168.1.33 to 192.168.1.64)
the NBG420N.
clients to connect to the NBG420N wirelessly. Enable wireless security
(WEP, WPA(2), WPA(2)-PSK) and/or MAC filtering to protect your
wireless network.
Note: The NBG420N may be prone to RF (Radio
Frequency) interference from other 2.4 GHz devices
such as microwave ovens, wireless phones,
Bluetooth enabled devices, and other wireless LANs.
Firmware Upgrade Download new firmware (when available) from the ZyXEL web site and
use the web configurator, an FTP or a TFTP tool to put it on the
NBG420N.
Note: Only upload firmware for your specific model!
Configuration Backup &
Restoration
Network Address
Translation (NAT)
Firewall You can configure firewall on the NBG420N for secure Internet access.
Content Filter The NBG420N blocks or allows access to web sites that you specify and
Make a copy of the NBG420N’s configuration and put it back on the
NBG420N later if you decide you want to revert back to an earlier
configuration.
Each computer on your network must have its own unique IP address.
Use NAT to convert a single public IP address to multiple private IP
addresses for the computers on your network.
When the firewall is on, by default, all incoming traffic from the Internet to
your network is blocked unless it is initiated from your network. This
means that probes from the outside to your network are not allowed, but
you can safely browse the Internet and download files for example.
blocks access to web sites with URLs that contain keywords that you
specify. You can define time periods and days during which content
filtering is enabled. You can also include or exclude particular computers
on your network from content filtering.
You can also subscribe to category-based content filtering that allows
your NBG420N to check web sites against an external database.
274
NBG420N User’s Guide
Appendix A Product Specifications and Wall-Mounting Instructions
Table 114 Firmware Features
FEATURE DESCRIPTION
IPSec VPN This allows you to establish a secure Virtual Private Network (VPN)
Bandwidth Management You can efficiently manage traffic on your network by reserving
Wireless LAN Scheduler You can schedule the times the Wireless LAN is enabled/disabled.
Time and Date Get the current time and date from an external server when you turn on
Port Forwarding If you have a server (mail or web server for example) on your network,
DHCP (Dynamic Host
Configuration Protocol)
Dynamic DNS Support With Dynamic DNS (Domain Name System) support, you can use a
IP Multicast IP Multicast is used to send traffic to a specific group of computers. The
IP Alias IP Alias allows you to subdivide a physical network into logical networks
Logging and Tracing Use packet tracing and logs for troubleshooting. You can send logs from
PPPoE PPPoE mimics a dial-up Internet access connection.
PPTP Encapsulation Point-to-Point Tunneling Protocol (PPTP) enables secure transfer of
Universal Plug and Play
(UPnP)
tunnel to connect with business partners and branch offices using data
encryption and the Internet without the expense of leased site-to-site
lines. The NBG420N VPN is based on the IPSec standard and is fully
interoperable with other IPSec-based VPN products.
bandwidth and giving priority to certain types of traffic and/or to particular
computers.
your NBG420N. You can also set the time manually. These dates and
times are then used in logs.
then use this feature to let people access it from the Internet.
Use this feature to have the NBG420N assign IP addresses, an IP
default gateway and DNS servers to computers on your network.
fixed URL, www.zyxel.com for example, with a dynamic IP address. You
must register for this service with a Dynamic DNS service provider.
NBG420N supports versions 1 and 2 of IGMP (Internet Group
Management Protocol) used to join multicast groups (see RFC 2236).
over the same Ethernet interface with the NBG420N itself as the
gateway for each subnet.
the NBG420N to an external syslog server.
data through a Virtual Private Network (VPN). The NBG420N supports
one PPTP connection at a time.
The NBG420N can communicate with other UPnP enabled devices in a
network.
Table 115 Feature Specifications
FEATURE SPECIFICATION
Number of Static Routes 7
Number of Port Forwarding Rules 12
Number of NAT Sessions 2048
Number of Address Mapping Rules 10
Number of VPN Tunnels 2
Number of Bandwidth Management
Classes
Number of DNS Name Server Record
Entries
NBG420N User’s Guide
3
3
275

Appendix A Product Specifications and Wall-Mounting Instructions
"
The following list, which is not exhaustive, illustrates the standards supported in the
NBG420N.
Table 116 Standards Supported
STANDARD DESCRIPTION
RFC 867 Daytime Protocol
RFC 868 Time Protocol.
RFC 1058 RIP-1 (Routing Information Protocol)
RFC 1112 IGMP v1
RFC 1305 Network Time Protocol (NTP version 3)
RFC 1631 IP Network Address Translator (NAT)
RFC 1723 RIP-2 (Routing Information Protocol)
RFC 2236 Internet Group Management Protocol, Version 2.
RFC 2516 A Method for Transmitting PPP Over Ethernet (PPPoE)
RFC 2766 Network Address Translation - Protocol
IEEE 802.11 Also known by the brand Wi-Fi, denotes a set of Wireless LAN/WLAN
IEEE 802.11b Uses the 2.4 gigahertz (GHz) band
IEEE 802.11g Uses the 2.4 gigahertz (GHz) band
IEEE 802.11n
IEEE 802.11d Standard for Local and Metropolitan Area Networks: Media Access
IEEE 802.11x Port Based Network Access Control.
IEEE 802.11e QoS IEEE 802.11 e Wireless LAN for Quality of Service
Microsoft PPTP MS PPTP (Microsoft's implementation of Point to Point Tunneling
MBM v2 Media Bandwidth Management v2
standards developed by working group 11 of the IEEE LAN/MAN
Standards Committee (IEEE 802).
Control (MAC) Bridges
Protocol)
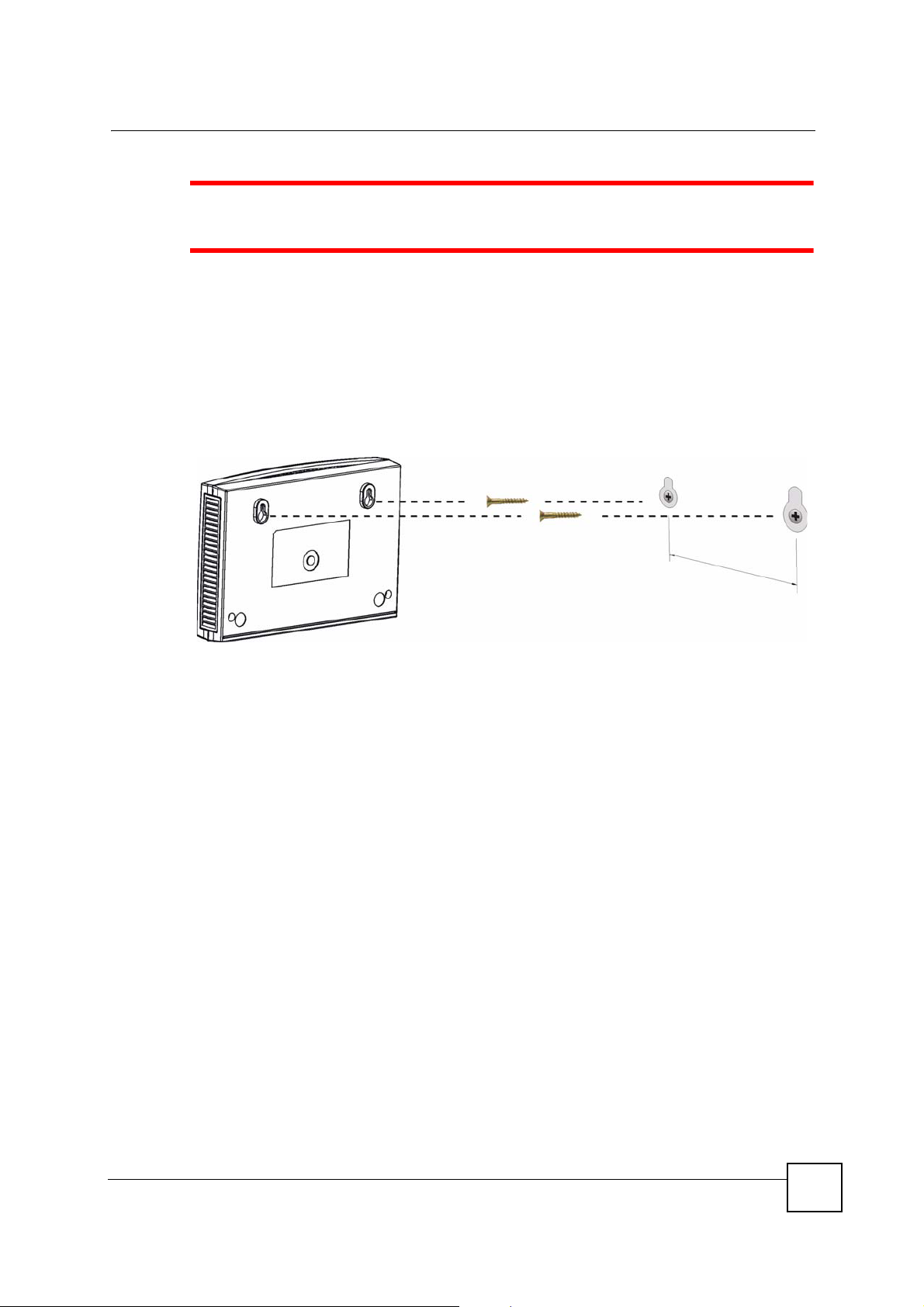
Wall-mounting Instructions
Do the following to hang your NBG420N on a wall.
See the Figure 167 on page 278 for the size of screws to use and how far
apart to place them.
1 Locate a high position on a wall that is free of obstructions. Use a sturdy wall.
2 Drill two holes for the screws. Make sure the distance between the centers of the holes
matches what is listed in the product specifications appendix.
276
NBG420N User’s Guide
1
Appendix A Product Specifications and Wall-Mounting Instructions
Be careful to avoid damaging pipes or cables located inside the wall when
drilling holes for the screws.
3 Do not screw the screws all the way into the wall. Leave a small gap of about 0.5 cm
between the heads of the screws and the wall.
4 Make sure the screws are snugly fastened to the wall. They need to hold the weight of
the NBG420N with the connection cables.
5 Align the holes on the back of the NBG420N with the screws on the wall. Hang the
NBG420N on the screws.
Figure 166 Wall-mounting Example
The following are dimensions of an M4 tap screw and masonry plug used for wall mounting.
All measurements are in millimeters (mm).
NBG420N User’s Guide
277
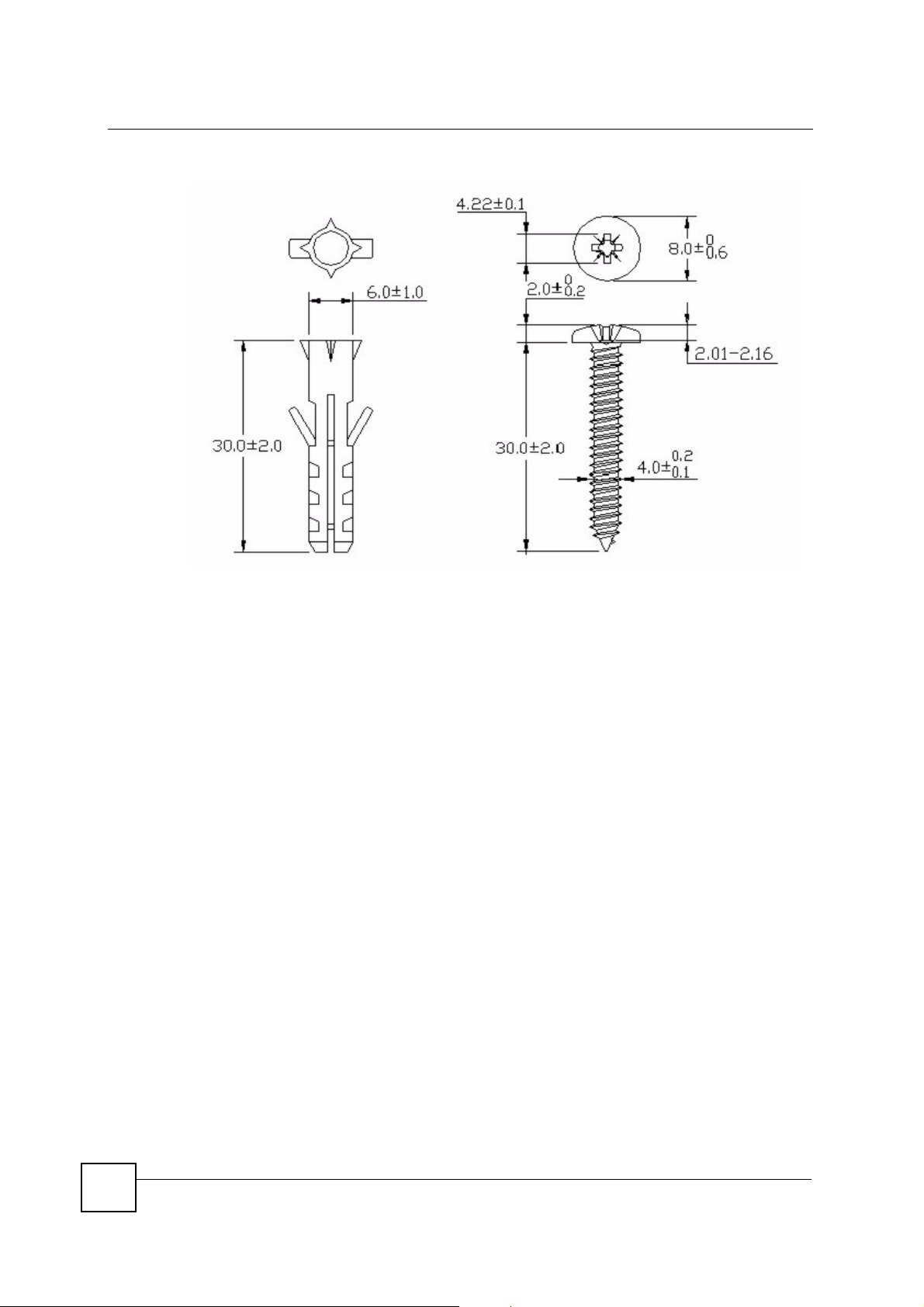
Appendix A Product Specifications and Wall-Mounting Instructions
Figure 167 Masonry Plug and M4 Tap Screw
278
NBG420N User’s Guide

APPENDIX B
"
Pop-up Windows, JavaScripts
and Java Permissions
In order to use the web configurator you need to allow:
• Web browser pop-up windows from your device.
• JavaScripts (enabled by default).
• Java permissions (enabled by default).
Internet Explorer 6 screens are used here. Screens for other Internet Explorer
versions may vary.
Internet Explorer Pop-up Blockers
You may have to disable pop-up blocking to log into your device.
Either disable pop-up blocking (enabled by default in Windows XP SP (Service Pack) 2) or
allow pop-up blocking and create an exception for your device’s IP address.
Disable pop-up Blockers
1 In Internet Explorer, select Too ls , Pop-up Blocker and then select Turn Off Pop-up
Blocker.
Figure 168 Pop-up Blocker
You can also check if pop-up blocking is disabled in the Pop-up Blocker section in the
Privacy tab.
1 In Internet Explorer, select Too ls , Internet Options, Privacy.
NBG420N User’s Guide
279
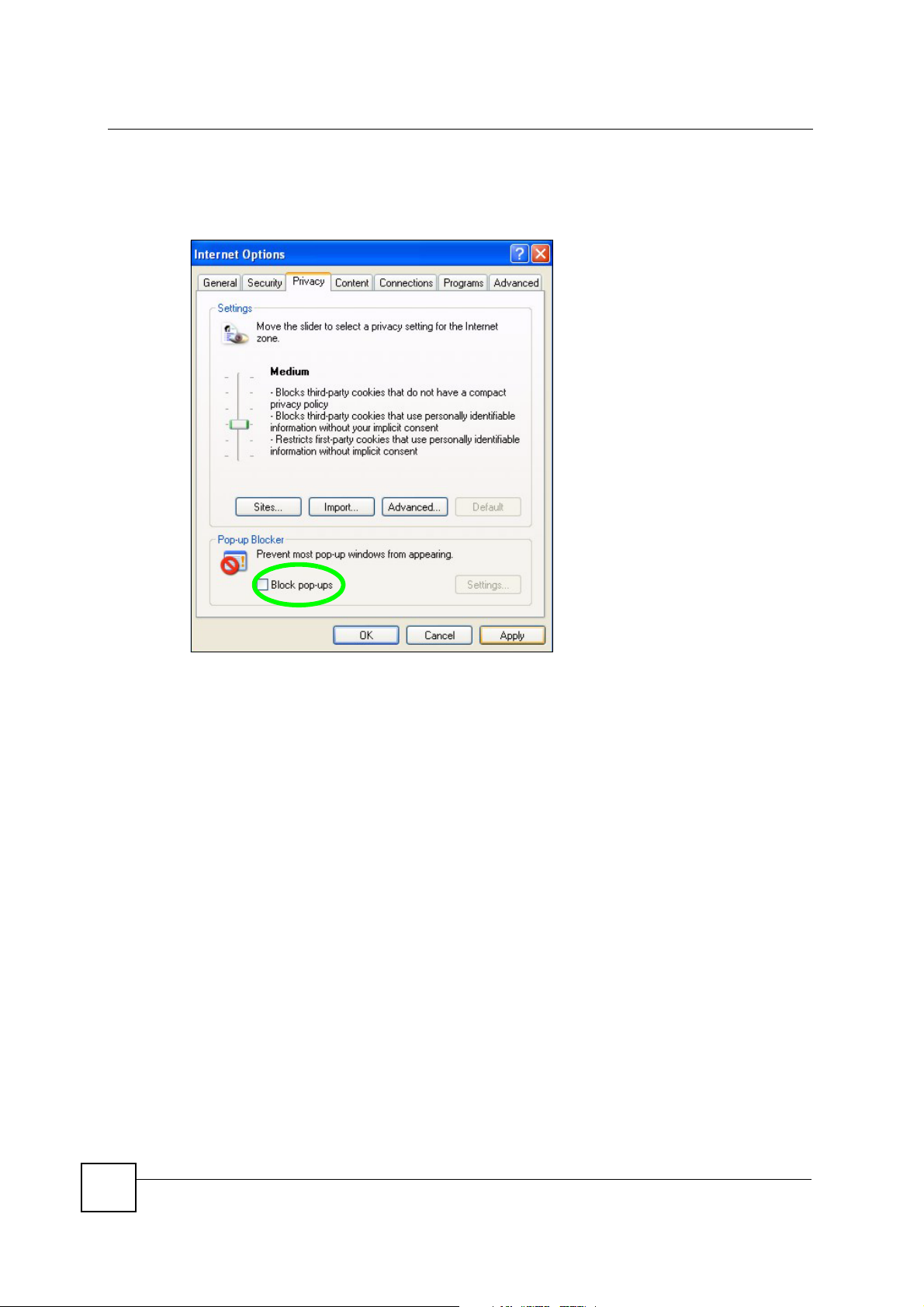
Appendix B Pop-up Windows, JavaScripts and Java Permissions
2 Clear the Block pop-ups check box in the Pop-up Blocker section of the screen. This
disables any web pop-up blockers you may have enabled.
Figure 169 Internet Options: Privacy
3 Click Apply to save this setting.
Enable pop-up Blockers with Exceptions
Alternatively, if you only want to allow pop-up windows from your device, see the following
steps.
1 In Internet Explorer, select Too ls , Internet Options and then the Privacy tab.
2 Select Settings…to open the Pop-up Blocker Settings screen.
280
NBG420N User’s Guide
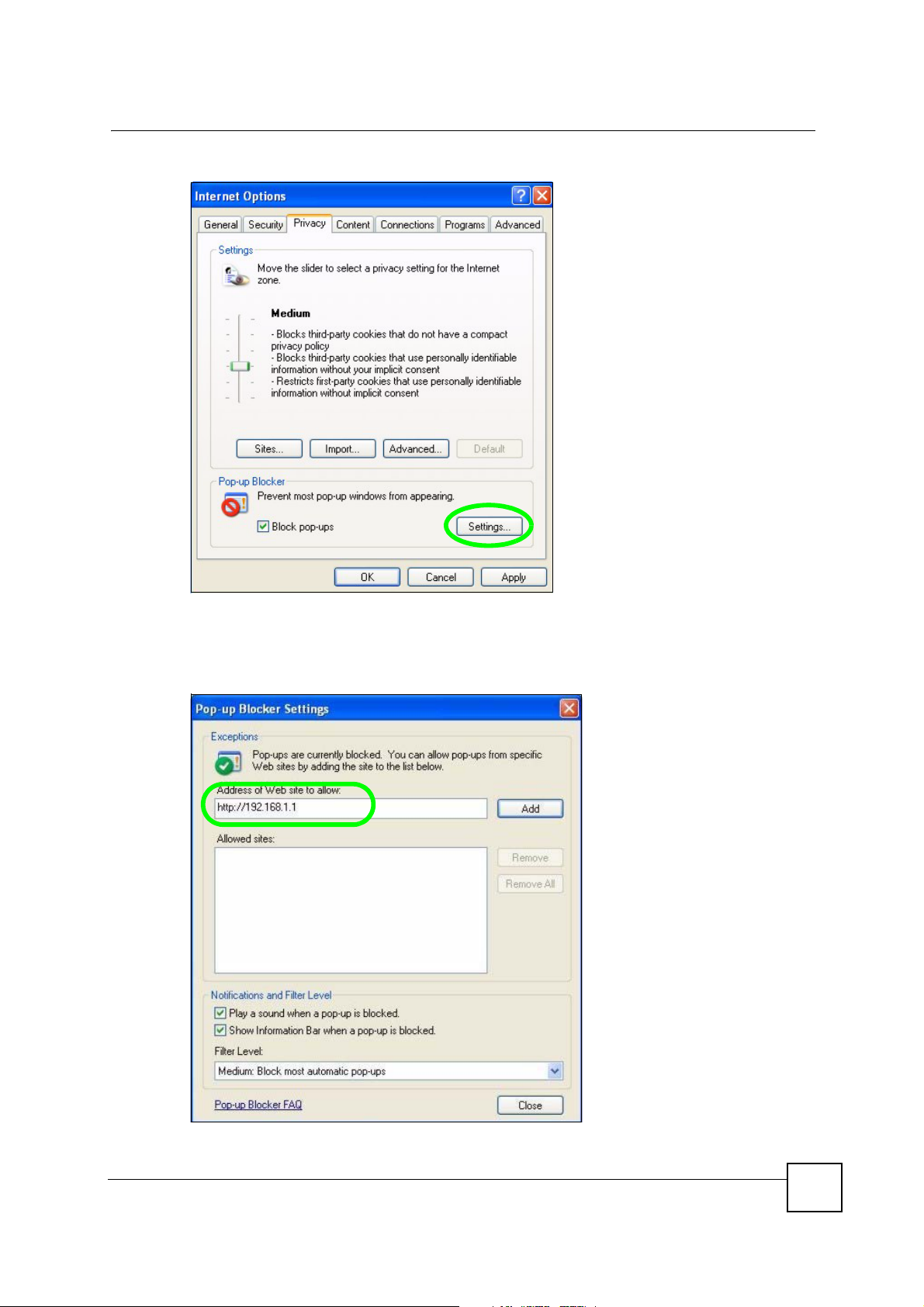
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Figure 170 Internet Options: Privacy
3 Type the IP address of your device (the web page that you do not want to have blocked)
with the prefix “http://”. For example, http://192.168.167.1.
4 Click Add to move the IP address to the list of Allowed sites.
Figure 171 Pop-up Blocker Settings
NBG420N User’s Guide
281
Appendix B Pop-up Windows, JavaScripts and Java Permissions
5 Click Close to return to the Privacy screen.
6 Click Apply to save this setting.
JavaScripts
If pages of the web configurator do not display properly in Internet Explorer, check that
JavaScripts are allowed.
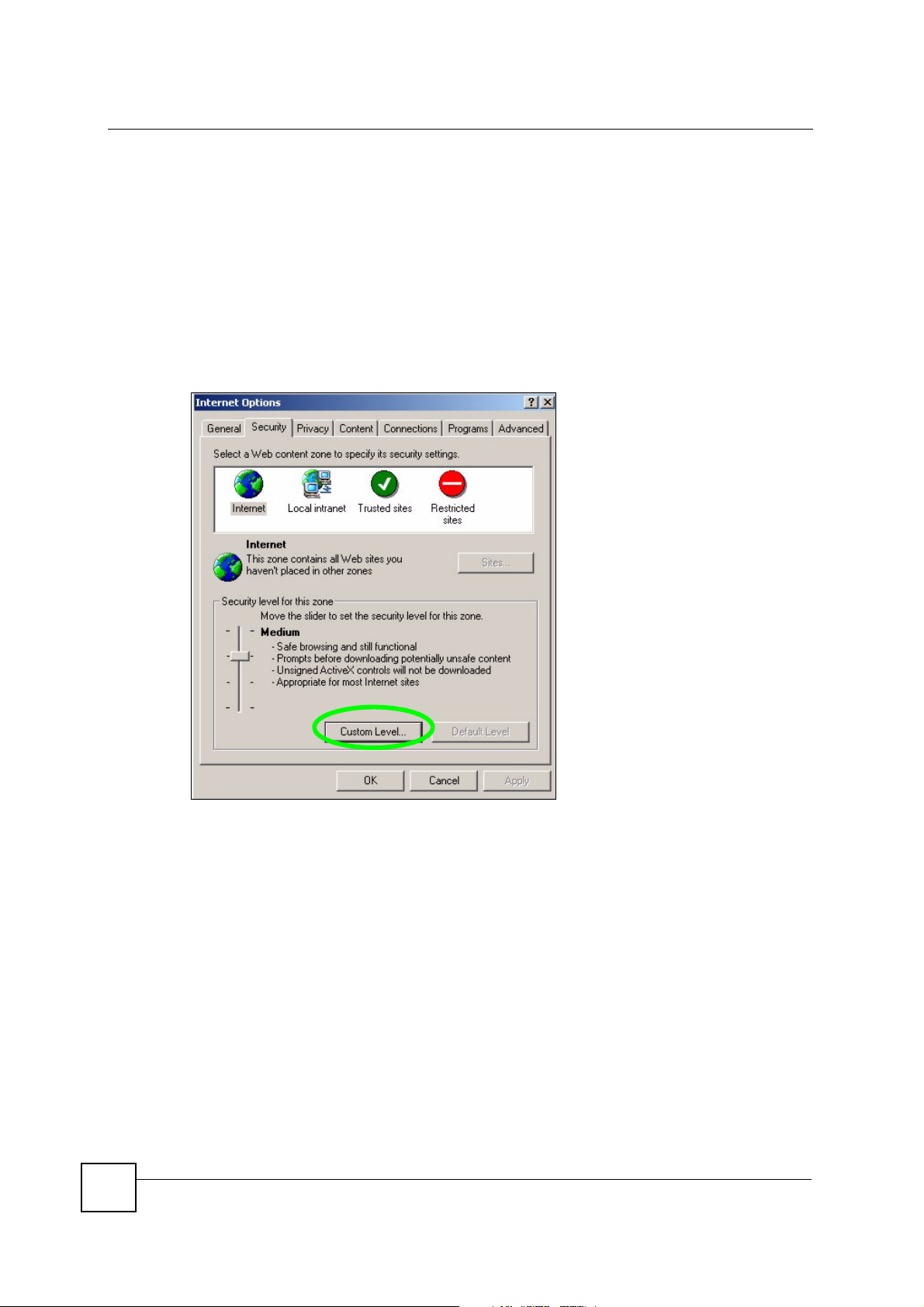
1 In Internet Explorer, click Tools, Internet Options and then the Security tab.
Figure 172 Internet Options: Security
282
2 Click the Custom Level... button.
3 Scroll down to Scripting.
4 Under Active scripting make sure that Enable is selected (the default).
5 Under Scripting of Java applets make sure that Enable is selected (the default).
6 Click OK to close the window.
NBG420N User’s Guide
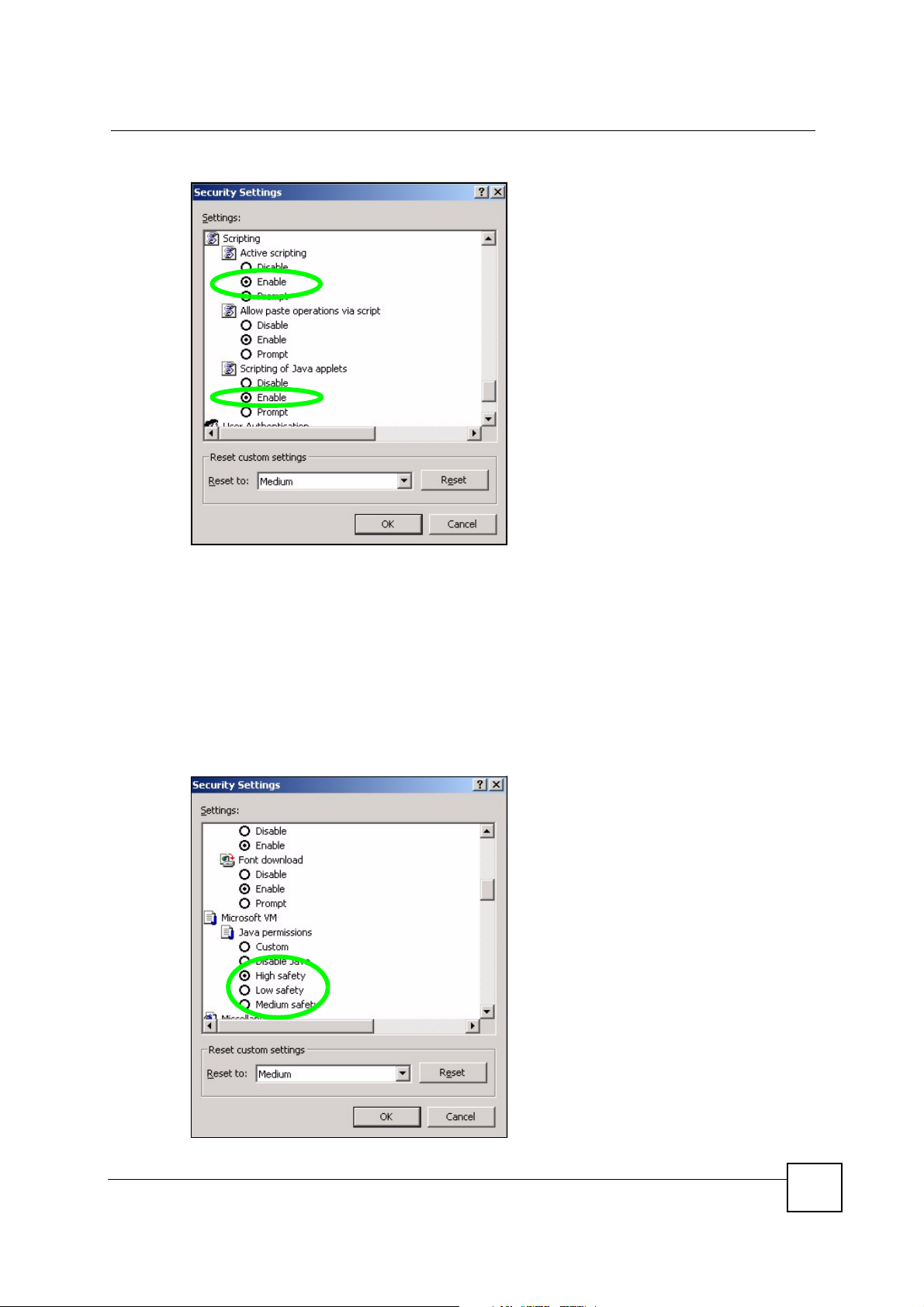
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Figure 173 Security Settings - Java Scripting
Java Permissions
1 From Internet Explorer, click Too ls , Internet Options and then the Security tab.
2 Click the Custom Level... button.
3 Scroll down to Microsoft VM.
4 Under Java permissions make sure that a safety level is selected.
5 Click OK to close the window.
Figure 174 Security Settings - Java
NBG420N User’s Guide
283
Appendix B Pop-up Windows, JavaScripts and Java Permissions
JAVA (Sun)
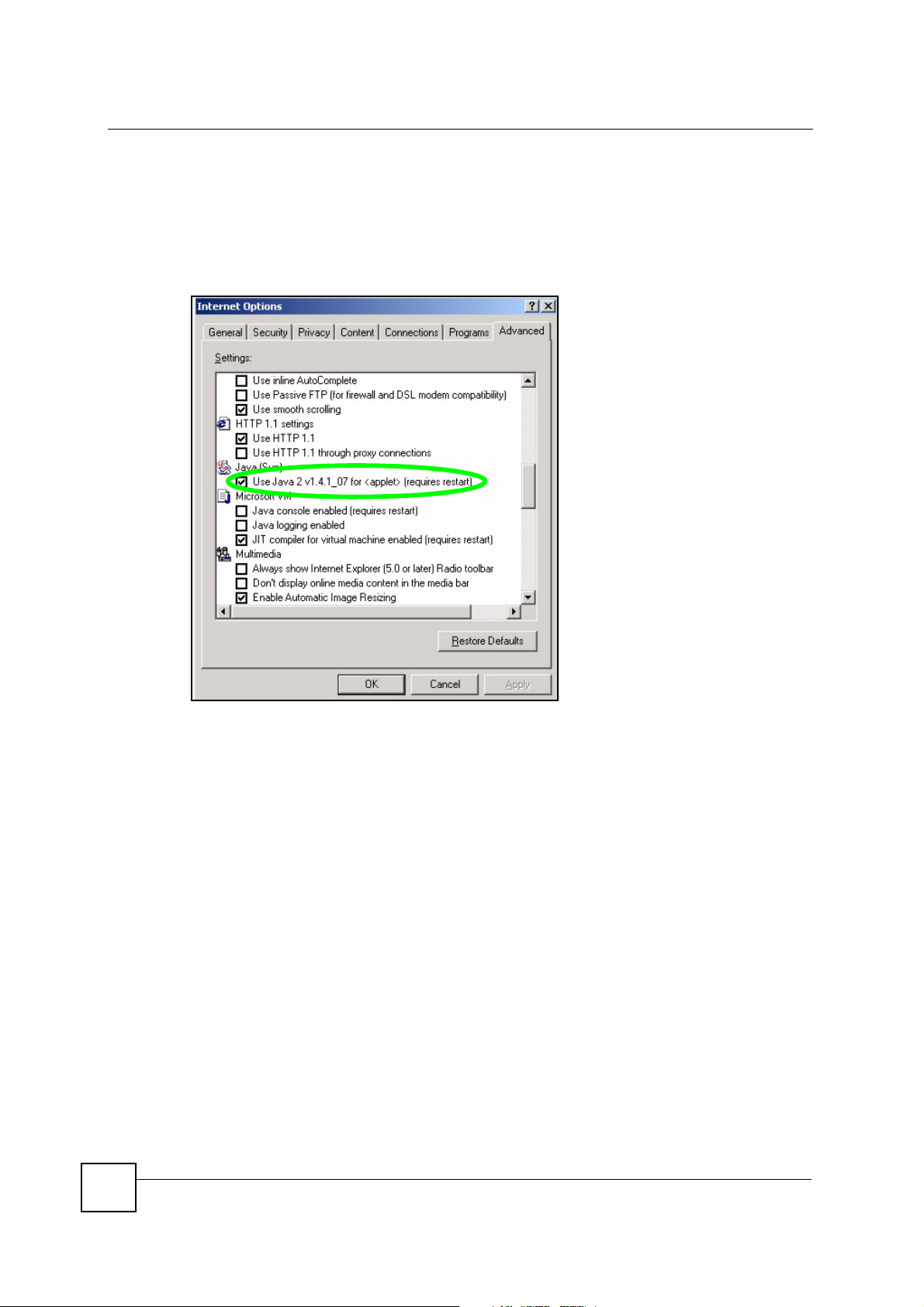
1 From Internet Explorer, click Too ls , Internet Options and then the Advanced tab.
2 Make sure that Use Java 2 for <applet> under Java (Sun) is selected.
3 Click OK to close the window.
Figure 175 Java (Sun)
284
NBG420N User’s Guide

APPENDIX C
IP Addresses and Subnetting
This appendix introduces IP addresses and subnet masks.
IP addresses identify individual devices on a network. Every networking device (including
computers, servers, routers, printers, etc.) needs an IP address to communicate across the
network. These networking devices are also known as hosts.
Subnet masks determine the maximum number of possible hosts on a network. You can also
use subnet masks to divide one network into multiple sub-networks.
Introduction to IP Addresses
One part of the IP address is the network number, and the other part is the host ID. In the same
way that houses on a street share a common street name, the hosts on a network share a
common network number. Similarly, as each house has its own house number, each host on the
network has its own unique identifying number - the host ID. Routers use the network number
to send packets to the correct network, while the host ID determines to which host on the
network the packets are delivered.
Structure
An IP address is made up of four parts, written in dotted decimal notation (for example,
192.168.1.1). Each of these four parts is known as an octet. An octet is an eight-digit binary
number (for example 11000000, which is 192 in decimal notation).
Therefore, each octet has a possible range of 00000000 to 11111111 in binary, or 0 to 255 in
decimal.
The following figure shows an example IP address in which the first three octets (192.168.1)
are the network number, and the fourth octet (16) is the host ID.
NBG420N User’s Guide
285
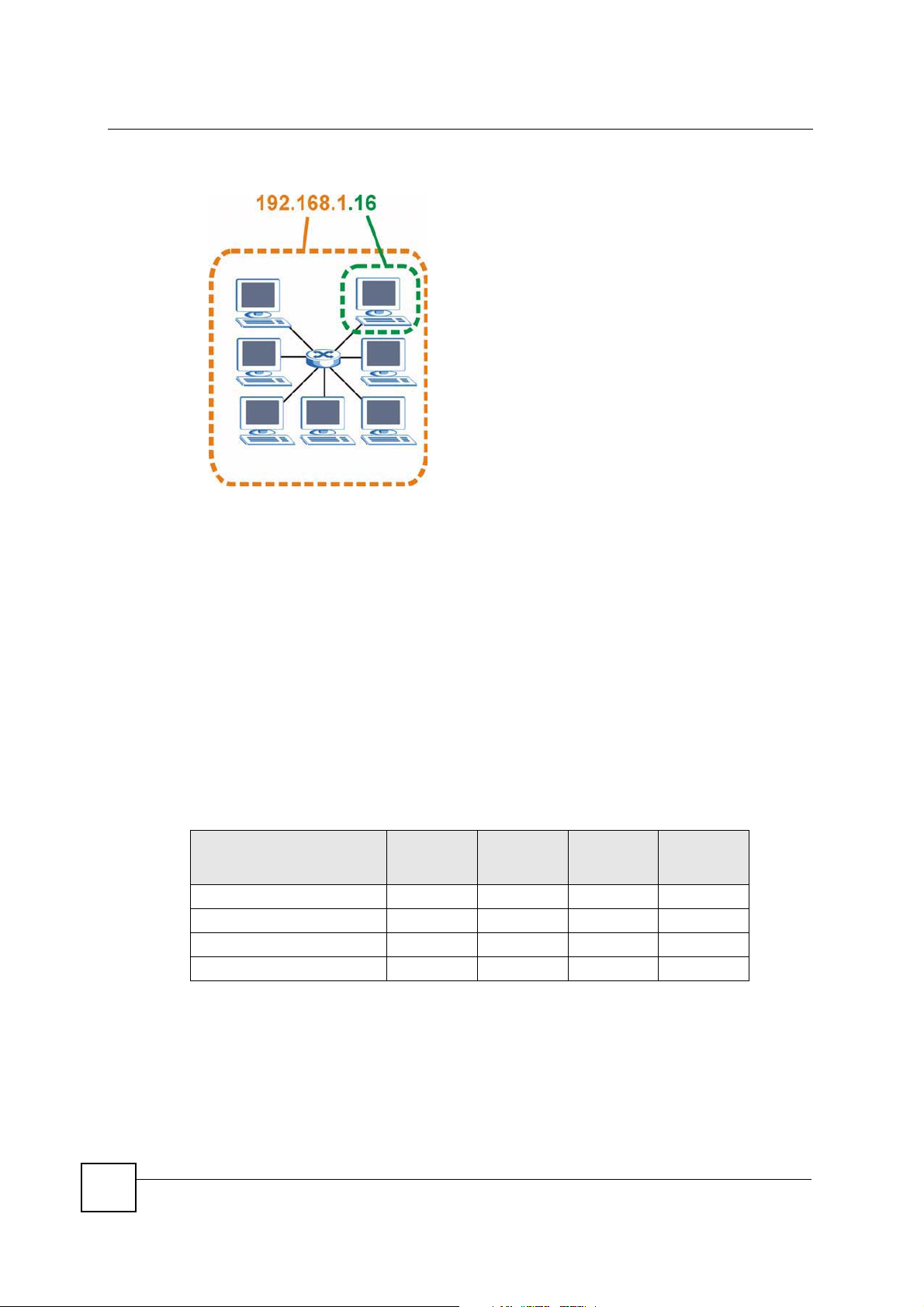
Appendix C IP Addresses and Subnetting
Figure 176 Network Number and Host ID
How much of the IP address is the network number and how much is the host ID varies
according to the subnet mask.
Subnet Masks
A subnet mask is used to determine which bits are part of the network number, and which bits
are part of the host ID (using a logical AND operation). The term “subnet” is short for “subnetwork”.
A subnet mask has 32 bits. If a bit in the subnet mask is a “1” then the corresponding bit in the
IP address is part of the network number. If a bit in the subnet mask is “0” then the
corresponding bit in the IP address is part of the host ID.
The following example shows a subnet mask identifying the network number (in bold text)
and host ID of an IP address (192.168.1.2 in decimal).
Table 117 Subnet Mask - Identifying Network Number
IP Address (Binary) 11000000 10101000 00000001 00000010
Subnet Mask (Binary) 11111111 11111111 11111111 00000000
Network Number 11000000 10101000 00000001
Host ID 00000010
By convention, subnet masks always consist of a continuous sequence of ones beginning from
the leftmost bit of the mask, followed by a continuous sequence of zeros, for a total number of
32 bits.
1ST OCTET:
(192)
2ND
OCTET:
(168)
3RD
OCTET:
(1)
4TH OCTET
(2)
286
Subnet masks can be referred to by the size of the network number part (the bits with a “1”
value). For example, an “8-bit mask” means that the first 8 bits of the mask are ones and the
remaining 24 bits are zeroes.
NBG420N User’s Guide
Subnet masks are expressed in dotted decimal notation just like IP addresses. The following
examples show the binary and decimal notation for 8-bit, 16-bit, 24-bit and 29-bit subnet
masks.
Table 118 Subnet Masks
8-bit mask 11111111 00000000 00000000 00000000 255.0.0.0
16-bit mask 11111111 11111111 00000000 00000000 255.255.0.0
24-bit mask 11111111 11111111 11111111 00000000 255.255.255.0
29-bit mask 11111111 11111111 11111111 11111000 255.255.255.248
Network Size
The size of the network number determines the maximum number of possible hosts you can
have on your network. The larger the number of network number bits, the smaller the number
of remaining host ID bits.
An IP address with host IDs of all zeros is the IP address of the network (192.168.1.0 with a
24-bit subnet mask, for example). An IP address with host IDs of all ones is the broadcast
address for that network (192.168.1.255 with a 24-bit subnet mask, for example).
BINARY
1ST
OCTET
2ND
OCTET
3RD
OCTET
Appendix C IP Addresses and Subnetting
DECIMAL
4TH OCTET
As these two IP addresses cannot be used for individual hosts, calculate the maximum number
of possible hosts in a network as follows:
Table 119 Maximum Host Numbers
Notation
Since the mask is always a continuous number of ones beginning from the left, followed by a
continuous number of zeros for the remainder of the 32 bit mask, you can simply specify the
number of ones instead of writing the value of each octet. This is usually specified by writing
a “/” followed by the number of bits in the mask after the address.
For example, 192.1.1.0 /25 is equivalent to saying 192.1.1.0 with subnet mask
255.255.255.128.
The following table shows some possible subnet masks using both notations.
Table 120 Alternative Subnet Mask Notation
SUBNET MASK HOST ID SIZE MAXIMUM NUMBER OF HOSTS
8 bits 255.0.0.0 24 bits 2
16 bits 255.255.0.0 16 bits 2
24 bits 255.255.255.0 8 bits 2
29 bits 255.255.255.248 3 bits 2
SUBNET MASK
255.255.255.0 /24 0000 0000 0
255.255.255.128 /25 1000 0000 128
ALTERNATIVE
NOTATION
LAST OCTET
(BINARY)
24
– 2 16777214
16
– 2 65534
8
– 2 254
3
– 2 6
LAST OCTET
(DECIMAL)
NBG420N User’s Guide
287
Appendix C IP Addresses and Subnetting
Table 120 Alternative Subnet Mask Notation (continued)
SUBNET MASK
255.255.255.192 /26 1100 0000 192
255.255.255.224 /27 1110 0000 224
255.255.255.240 /28 1111 00 00 240
255.255.255.248 /29 1111 10 00 248
255.255.255.252 /30 1111 1100 252
ALTERNATIVE
NOTATION
Subnetting
You can use subnetting to divide one network into multiple sub-networks. In the following
example a network administrator creates two sub-networks to isolate a group of servers from
the rest of the company network for security reasons.
In this example, the company network address is 192.168.1.0. The first three octets of the
address (192.168.1) are the network number, and the remaining octet is the host ID, allowing a
maximum of 2
8
– 2 or 254 possible hosts.
LAST OCTET
(BINARY)
LAST OCTET
(DECIMAL)
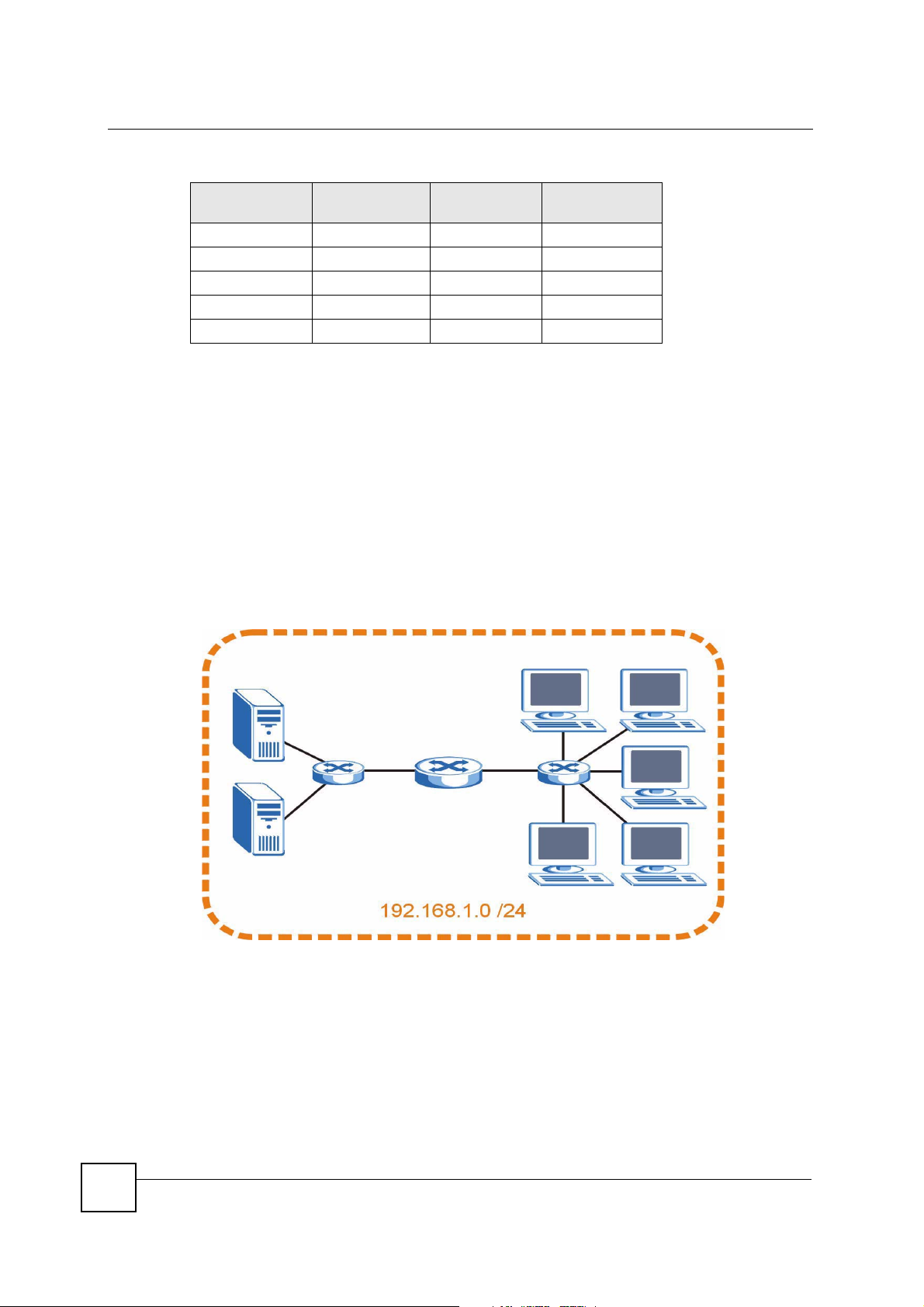
The following figure shows the company network before subnetting.
Figure 177 Subnetting Example: Before Subnetting
You can “borrow” one of the host ID bits to divide the network 192.168.1.0 into two separate
sub-networks. The subnet mask is now 25 bits (255.255.255.128 or /25).
The “borrowed” host ID bit can have a value of either 0 or 1, allowing two subnets;
192.168.1.0 /25 and 192.168.1.128 /25.
288
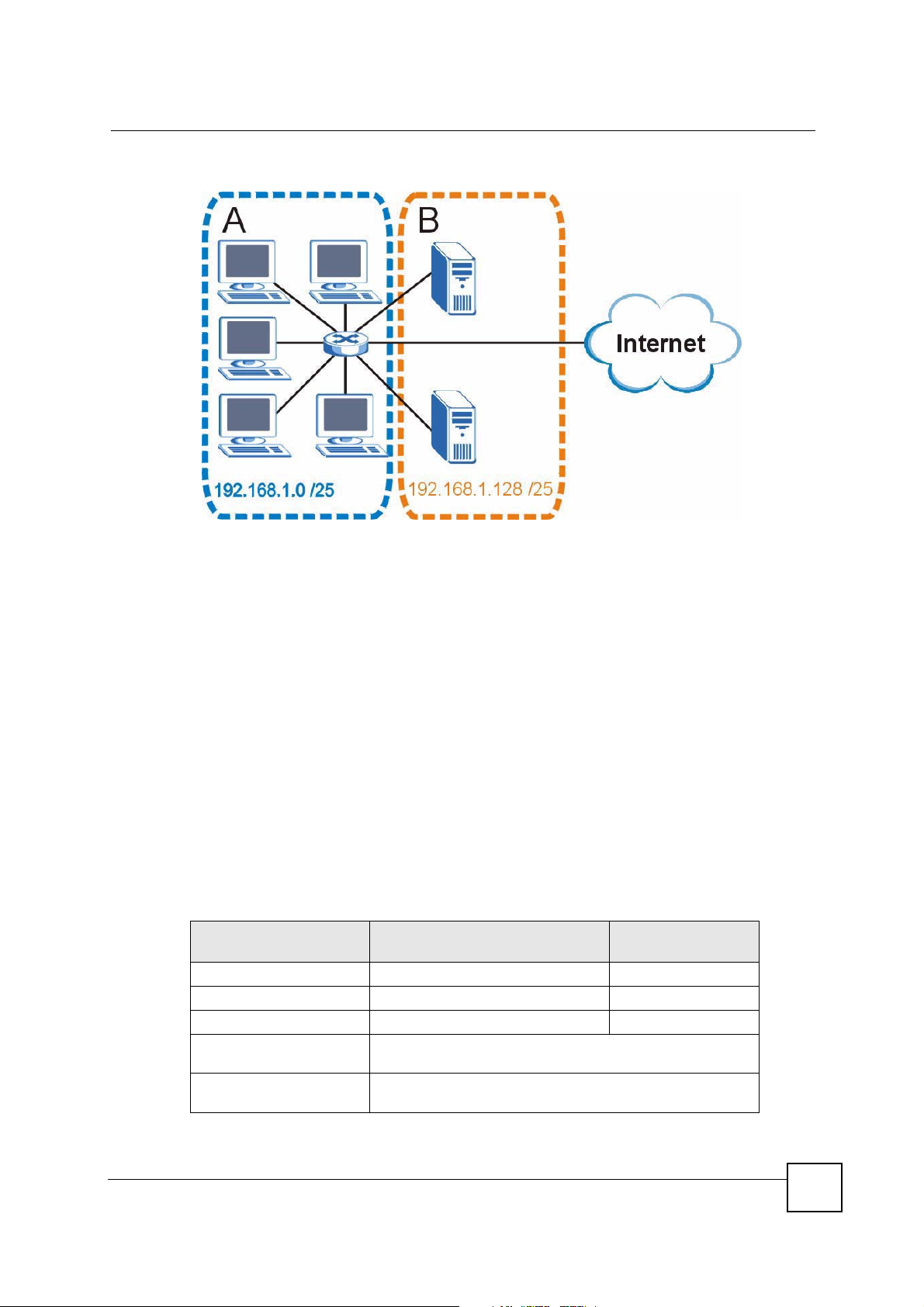
The following figure shows the company network after subnetting. There are now two subnetworks, A and B.
NBG420N User’s Guide
Appendix C IP Addresses and Subnetting
Figure 178 Subnetting Example: After Subnetting
In a 25-bit subnet the host ID has 7 bits, so each sub-network has a maximum of 27 – 2 or 126
possible hosts (a host ID of all zeroes is the subnet’s address itself, all ones is the subnet’s
broadcast address).
192.168.1.0 with mask 255.255.255.128 is subnet A itself, and 192.168.1.127 with mask
255.255.255.128 is its broadcast address. Therefore, the lowest IP address that can be assigned
to an actual host for subnet A is 192.168.1.1 and the highest is 192.168.1.126.
Similarly, the host ID range for subnet B is 192.168.1.129 to 192.168.1.254.
Example: Four Subnets
The previous example illustrated using a 25-bit subnet mask to divide a 24-bit address into two
subnets. Similarly, to divide a 24-bit address into four subnets, you need to “borrow” two host
ID bits to give four possible combinations (00, 01, 10 and 11). The subnet mask is 26 bits
(11111111.11111111.11111111.11000000) or 255.255.255.192.
Each subnet contains 6 host ID bits, giving 2
zeroes is the subnet itself, all ones is the subnet’s broadcast address).
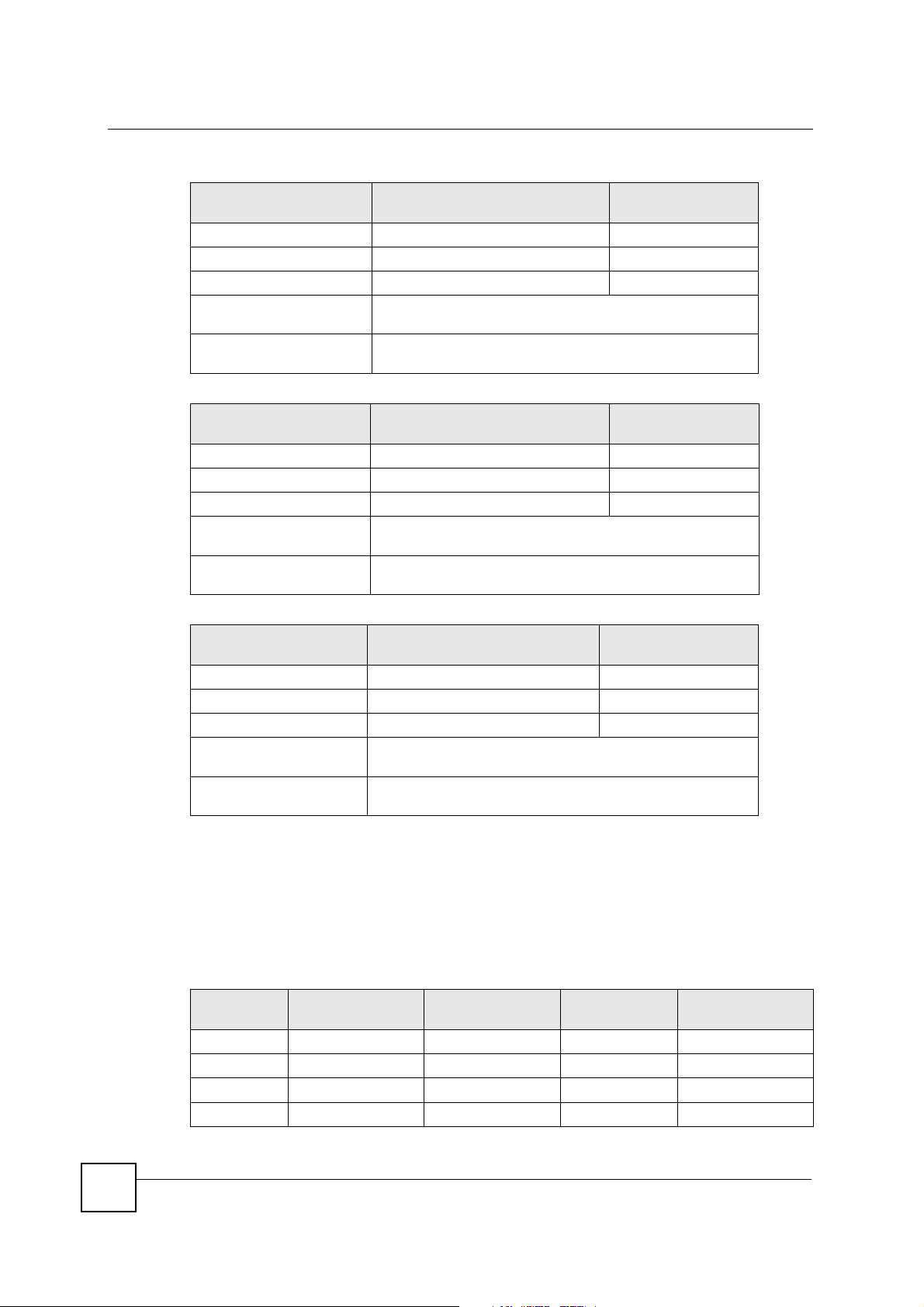
Table 121 Subnet 1
IP/SUBNET MASK NETWORK NUMBER
IP Address (Decimal) 192.168.1. 0
IP Address (Binary) 11000000.10101000.00000001. 00000000
Subnet Mask (Binary) 11111111. 11111111.11111111. 11000000
Subnet Address:
192.168.1.0
Broadcast Address:
192.168.1.63
6
- 2 or 62 hosts for each subnet (a host ID of all
Lowest Host ID: 192.168.1.1
Highest Host ID: 192.168.1.62
LAST OCTET BIT
VAL UE
NBG420N User’s Guide
289
Appendix C IP Addresses and Subnetting
Table 122 Subnet 2
IP/SUBNET MASK NETWORK NUMBER
IP Address 192.168.1. 64
IP Address (Binary) 11000000.10101000.00000001. 01000000
Subnet Mask (Binary) 11111111.11111111.11111111. 11000000
Subnet Address:
192.168.1.64
Broadcast Address:
192.168.1.127
Table 123 Subnet 3
IP/SUBNET MASK NETWORK NUMBER
IP Address 192.168.1. 128
IP Address (Binary) 11000000.10101000.00000001. 10000000
Subnet Mask (Binary) 11111111 .11111111.11111111. 11000000
Subnet Address:
192.168.1.128
Broadcast Address:
192.168.1.191
LAST OCTET BIT
VAL UE
Lowest Host ID: 192.168.1.65
Highest Host ID: 192.168.1.126
LAST OCTET BIT
VAL UE
Lowest Host ID: 192.168.1.129
Highest Host ID: 192.168.1.190
Table 124 Subnet 4
IP/SUBNET MASK NETWORK NUMBER
IP Address 192.168.1. 192
IP Address (Binary) 11000000.10101000.00000001. 11000000
Subnet Mask (Binary) 11111111. 11111111.11111111 . 11 000000
Subnet Address:
192.168.1.192
Broadcast Address:
192.168.1.255
Example: Eight Subnets
Similarly, use a 27-bit mask to create eight subnets (000, 001, 010, 011, 100, 101, 110 and
111).
The following table shows IP address last octet values for each subnet.
Table 125 Eight Subnets
SUBNET
1 0 1 30 31
2 32 33 62 63
3 64 65 94 95
4 96 97 126 127
SUBNET
ADDRESS
Lowest Host ID: 192.168.1.193
Highest Host ID: 192.168.1.254
FIRST ADDRESS
LAST OCTET BIT
VALUE
LAST
ADDRESS
BROADCAST
ADDRESS
290
NBG420N User’s Guide
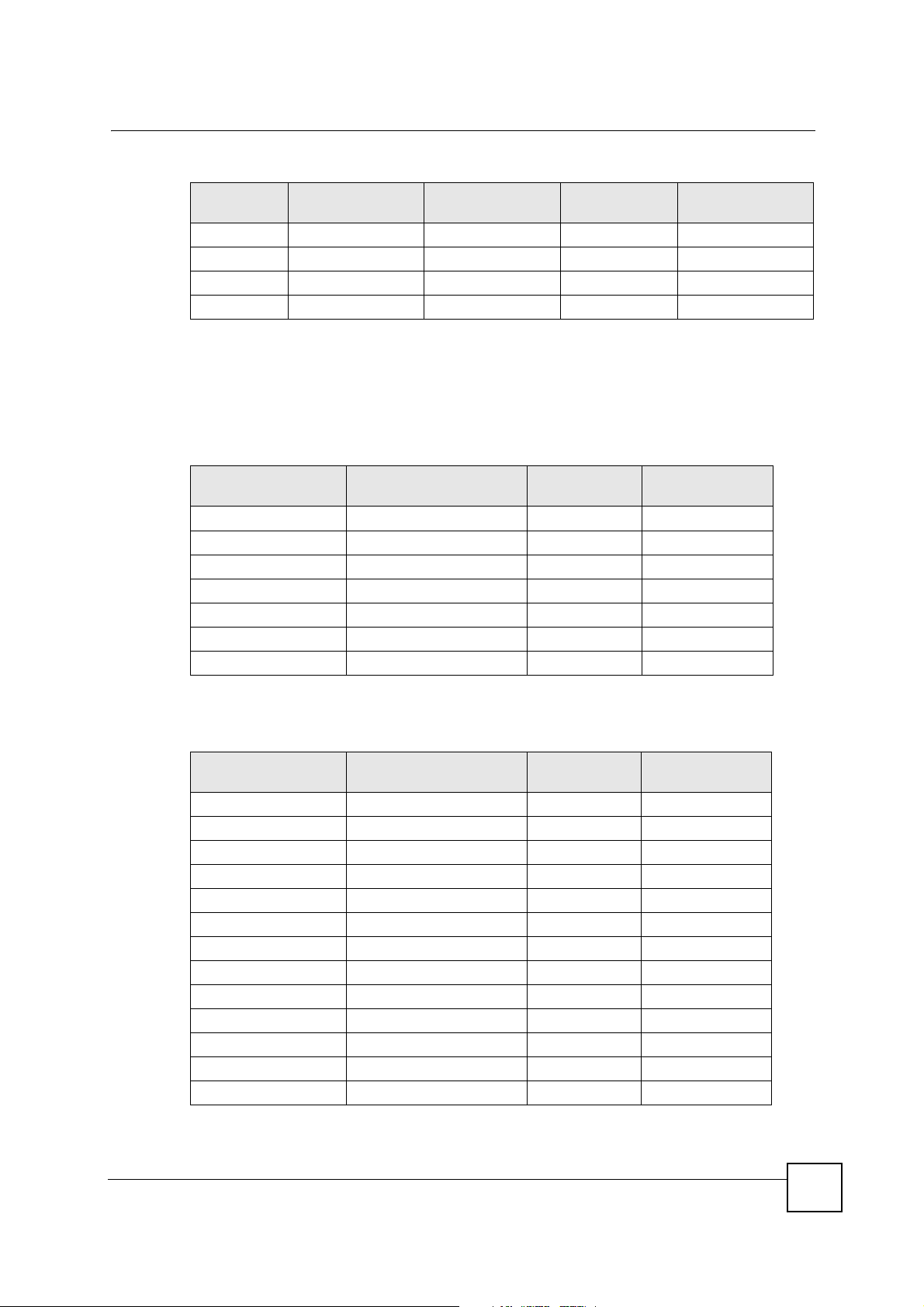
Table 125 Eight Subnets (continued)
SUBNET
5 128 129 158 159
6 160 161 190 191
7 192 193 222 223
8 224 225 254 255
Subnet Planning
The following table is a summary for subnet planning on a network with a 24-bit network
number.
Table 126 24-bit Network Number Subnet Planning
NO. “BORROWED”
HOST BITS
1 255.255.255.128 (/25) 2 126
2 255.255.255.192 (/26) 4 62
3 255.255.255.224 (/27) 8 30
4 255.255.255.240 (/28) 16 14
5 255.255.255.248 (/29) 32 6
6 255.255.255.252 (/30) 64 2
7 255.255.255.254 (/31) 128 1
SUBNET
ADDRESS
Appendix C IP Addresses and Subnetting
FIRST ADDRESS
SUBNET MASK NO. SUBNETS
LAST
ADDRESS
BROADCAST
ADDRESS
NO. HOSTS PER
SUBNET
The following table is a summary for subnet planning on a network with a 16-bit network
number.
Table 127 16-bit Network Number Subnet Planning
NO. “BORROWED”
HOST BITS
1 255.255.128.0 (/17) 2 32766
2 255.255.192.0 (/18) 4 16382
3 255.255.224.0 (/19) 8 8190
4 255.255.240.0 (/20) 16 4094
5 255.255.248.0 (/21) 32 2046
6 255.255.252.0 (/22) 64 1022
7 255.255.254.0 (/23) 128 510
8 255.255.255.0 (/24) 256 254
9 255.255.255.128 (/25) 512 126
10 255.255.255.192 (/26) 1024 62
11 255.255.255.224 (/27) 2048 30
12 255.255.255.240 (/28) 4096 14
13 255.255.255.248 (/29) 8192 6
SUBNET MASK NO. SUBNETS
NO. HOSTS PER
SUBNET
NBG420N User’s Guide
291
 Loading...
Loading...