Cisco Registrar 3.5 User Manual

Cisco Access Registrar 3.5 Concepts and
Reference Guide
July 2004
Corporate Headquarters
Cisco Systems, Inc. 170 West Tasman Drive
San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000
800 553-NETS (6387) Fax: 408 526-4100
Customer Order Number:
Text Part Number: OL-2683-02
THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Cisco Access Registrar 3.5 Concepts and Reference Guide
Copyright © 2002, 2003, 2004 Cisco Systems, Inc.
All rights reserved.

C O N T E N T S
|
|
|
About This Guide |
ix |
|
|
|
|
|
|
|
|
|
|
|
|
|
Obtaining Documentation |
ix |
|
|
|
|
|
|
|
|||
|
|
|
World Wide Web |
ix |
|
|
|
|
|
|
|
|
||
|
|
|
Ordering Documentation |
x |
|
|
|
|
|
|
||||
|
|
|
Documentation Feedback |
x |
|
|
|
|
|
|
||||
|
|
|
Obtaining Technical Assistance |
|
x |
|
|
|
|
|
||||
|
|
|
Cisco.com |
x |
|
|
|
|
|
|
|
|
|
|
|
|
|
Technical Assistance Center |
xi |
|
|
|
|
|
|||||
|
|
|
Contacting TAC by Using the Cisco TAC Website |
xi |
||||||||||
|
|
|
Contacting TAC by Telephone |
xi |
|
|
|
|
||||||
|
|
Overview 1-1 |
|
|
|
|
|
|
|
|
|
|
|
|
C H A P T E R |
1 |
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
RADIUS Protocol |
1-1 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Steps to Connection |
1-2 |
|
|
|
|
|
|
|
|||
|
|
|
Types of RADIUS Messages |
1-3 |
|
|
|
|
|
|||||
|
|
|
Packet Contents |
1-3 |
|
|
|
|
|
|
|
|||
|
|
|
The Attribute Dictionary |
1-4 |
|
|
|
|
|
|||||
|
|
|
Proxy Servers |
1-4 |
|
|
|
|
|
|
|
|
||
|
|
|
Basic Authentication and Authorization |
1-5 |
|
|
|
|
||||||
|
|
Understanding Cisco Access Registrar |
|
|
|
|
|
|||||||
C H A P T E R |
2 |
2-1 |
|
|
|
|
||||||||
|
|
|
Cisco Access Registrar Hierarchy |
2-1 |
|
|
|
|
|
|||||
|
|
|
UserLists and Groups |
2-2 |
|
|
|
|
|
|
||||
|
|
|
Profiles |
2-2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Scripts 2-2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Services |
2-2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Session Management Using Resource Managers 2-3 |
|||||||||||
|
|
|
Cisco AR Directory Structure |
2-4 |
|
|
|
|
|
|
||||
|
|
|
Program Flow |
2-4 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Scripting Points |
2-5 |
|
|
|
|
|
|
|
|
||
|
|
|
Client or NAS Scripting Points |
2-5 |
|
|
|
|
||||||
|
|
|
Authentication and/or Authorization Scripting Points 2-6 |
|||||||||||
|
|
|
Session Management |
2-7 |
|
|
|
|
|
|
||||
|
|
|
Failover by the NAS and Session Management |
2-7 |
|
|
|
|||||||
|
|
|
|
|
|
|
|
|
|
Cisco Access Registrar 3.5 Concepts and Reference Guide |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
OL-2683-02 |
|
|
|
|
|
|
|
|
|
|
iii |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||

Contents
|
|
|
|
|
Script Processing Hierarchy |
2-8 |
|
|
|
||||
|
|
|
|
|
Cross Server Session and Resource Management |
2-9 |
|
||||||
|
|
|
|
|
Overview 2-9 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Session-Service Service Step and Radius-Session Service 2-10 |
||||||||
|
|
|
|
|
Configuring a Front Line Cisco Access Registrar |
2-10 |
|
||||||
|
|
|
|
|
Configure Central AR |
2-11 |
|
|
|
|
|||
|
|
Cisco Access Registrar Scripts |
|
|
|
|
|||||||
C H A P T E R 3 |
|
3-1 |
|
|
|
||||||||
|
|
|
|
|
Using Cisco AR Scripts |
3-1 |
|
|
|
|
|||
|
|
|
|
|
ACMEOutgoingScript |
3-1 |
|
|
|
|
|||
|
|
|
|
|
AltigaIncomingScript |
3-1 |
|
|
|
|
|||
|
|
|
|
|
AltigaOutgoingScript |
3-2 |
|
|
|
|
|||
|
|
|
|
|
ANAAAOutgoing |
3-2 |
|
|
|
|
|
||
|
|
|
|
|
AscendIncomingScript |
3-2 |
|
|
|
|
|||
|
|
|
|
|
AscendOutgoingScript |
3-2 |
|
|
|
|
|||
|
|
|
|
|
AuthorizePPP |
3-2 |
|
|
|
|
|
|
|
|
|
|
|
|
AuthorizeService |
3-2 |
|
|
|
|
|
||
|
|
|
|
|
AuthorizeSLIP |
|
3-2 |
|
|
|
|
|
|
|
|
|
|
|
AuthorizeTelnet |
3-3 |
|
|
|
|
|
||
|
|
|
|
|
CabletronIncoming |
3-3 |
|
|
|
|
|||
|
|
|
|
|
CabletronOutgoing |
3-3 |
|
|
|
|
|||
|
|
|
|
|
CiscoIncoming |
|
3-3 |
|
|
|
|
|
|
|
|
|
|
|
CiscoOutgoing |
|
3-3 |
|
|
|
|
|
|
|
|
|
|
|
CiscoWithODAPIncomingScript 3-3 |
|
|
||||||
|
|
|
|
|
ExecCLIDRule |
|
3-3 |
|
|
|
|
|
|
|
|
|
|
|
ExecDNISRule |
|
3-4 |
|
|
|
|
|
|
|
|
|
|
|
ExecFilterRule |
|
3-4 |
|
|
|
|
|
|
|
|
|
|
|
ExecNASIPRule |
|
3-4 |
|
|
|
|
|
|
|
|
|
|
|
ExecRealmRule |
|
3-4 |
|
|
|
|
|
|
|
|
|
|
|
ExecTimeRule |
|
3-4 |
|
|
|
|
|
|
|
|
|
|
|
LDAPOutage |
3-5 |
|
|
|
|
|
|
|
|
|
|
|
|
MapSourceIPAddress |
3-5 |
|
|
|
|
|||
|
|
|
|
|
ParseAAARealm |
3-5 |
|
|
|
|
|
||
|
|
|
|
|
ParseAAASRealm |
3-5 |
|
|
|
|
|
||
|
|
|
|
|
ParseAARealm |
|
3-5 |
|
|
|
|
|
|
|
|
|
|
|
ParseAASRealm |
3-5 |
|
|
|
|
|
||
|
|
|
|
|
ParseProxyHints |
3-6 |
|
|
|
|
|
||
|
|
|
|
|
ParseServiceAndAAARealmHints |
3-6 |
|
|
|||||
|
|
|
|
|
ParseServiceAndAAASRealmHints |
3-6 |
|
|
|||||
|
|
|
|
Cisco Access Registrar 3.5 Concepts and Reference Guide |
|
|
|
||||||
|
|
|
|
|
|
|
|||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
iv |
|
|
|
|
|
|
|
|
|
|
OL-2683-02 |
|
|
|
|
|
|
|
|
|
|
|
|
|
||

Contents
ParseServiceAndAARealmHints 3-6
ParseServiceAndAASRealmHints 3-6
ParseServiceAndProxyHints 3-6
ParseServiceHints 3-7
ParseTranslationGroupsByCLID 3-7
ParseTranslationGroupsByDNIS 3-7
ParseTranslationGroupsByRealm 3-7
|
|
UseCLIDAsSessionKey |
3-7 |
|
|
|
|
|
|||
|
|
USRIncomingScript |
3-7 |
|
|
|
|
|
|||
|
|
USRIncomingScript-IgnoreAccountingSignature 3-7 |
|||||||||
|
|
USROutgoingScript |
3-8 |
|
|
|
|
|
|||
|
Understanding Replication |
|
|
|
|
|
|
||||
C H A P T E R 4 |
4-1 |
|
|
|
|
|
|||||
|
|
Replication Overview |
4-1 |
|
|
|
|
|
|
||
|
|
How Replication Works |
4-2 |
|
|
|
|
|
|||
|
|
Replication Data Flow |
4-2 |
|
|
|
|
|
|||
|
|
Master Server |
4-2 |
|
|
|
|
|
|||
|
|
Slave Server |
4-3 |
|
|
|
|
|
|
||
|
|
Security |
4-3 |
|
|
|
|
|
|
|
|
|
|
Replication Archive |
4-3 |
|
|
|
|
|
|||
|
|
Ensuring Data Integrity |
4-3 |
|
|
|
|
|
|||
|
|
Transaction Data Verification |
4-4 |
|
|
|
|||||
|
|
Transaction Order |
4-4 |
|
|
|
|
|
|||
|
|
Automatic Resynchronization |
4-4 |
|
|
|
|||||
|
|
Full Resynchronization |
4-5 |
|
|
|
|
|
|||
|
|
Understanding Hot-Configuration |
4-5 |
|
|
|
|||||
|
|
Replication’s Impact on Request Processing 4-5 |
|||||||||
|
|
Replication Configuration Settings |
4-5 |
|
|
|
|
||||
|
|
RepType |
4-6 |
|
|
|
|
|
|
|
|
|
|
RepTransactionSyncInterval |
4-6 |
|
|
|
|
||||
|
|
Master 4-6 |
|
|
|
|
|
|
|
||
|
|
Slave |
4-6 |
|
|
|
|
|
|
|
|
|
|
RepTransactionArchiveLimit |
4-6 |
|
|
|
|
||||
|
|
RepIPAddress |
4-7 |
|
|
|
|
|
|
|
|
|
|
RepPort |
4-7 |
|
|
|
|
|
|
|
|
|
|
RepSecret |
4-7 |
|
|
|
|
|
|
|
|
|
|
RepIPMaster |
4-7 |
|
|
|
|
|
|
|
|
|
|
RepMasterIPAddress |
4-7 |
|
|
|
|
|
|||
|
|
RepMasterPort |
4-7 |
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
Cisco Access Registrar 3.5 Concepts and Reference Guide |
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
OL-2683-02 |
|
|
|
|
|
|
|
|
v |
|
|
|
|
|
|
|
|
|
|
|
||

Contents
|
|
|
|
|
Rep Members Subdirectory |
4-8 |
|
|
|
|
||||
|
|
|
|
|
Rep Members/Slave1 |
4-8 |
|
|
|
|
|
|||
|
|
|
|
|
Name |
4-8 |
|
|
|
|
|
|
|
|
|
|
|
|
|
IPAddress |
4-8 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Port |
4-8 |
|
|
|
|
|
|
|
|
|
|
|
Understanding SNMP 5-1 |
|
|
|
|
|
|
|||||
C H A P T E R |
5 |
|
|
|
|
|
|
|
||||||
|
|
|
|
|
Overview |
5-1 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Supported MIBs |
5-1 |
|
|
|
|
|
|
|
|
|
|
|
|
|
RADIUS-AUTH-CLIENT-MIB 5-1 |
|
|
|
|
|||||
|
|
|
|
|
RADIUS-AUTH-SERVER-MIB 5-2 |
|
|
|
||||||
|
|
|
|
|
RADIUS-ACC-CLIENT-MIB 5-2 |
|
|
|
|
|||||
|
|
|
|
|
RADIUS-ACC-SERVER-MIB 5-2 |
|
|
|
|
|||||
|
|
|
|
|
SNMP Traps 5-2 |
|
|
|
|
|
|
|
||
|
|
|
|
|
Supported Traps |
5-3 |
|
|
|
|
|
|
||
|
|
|
|
|
carServerStart |
5-3 |
|
|
|
|
|
|||
|
|
|
|
|
carServerStop |
5-3 |
|
|
|
|
|
|
||
|
|
|
|
|
carInputQueueFull |
5-3 |
|
|
|
|
|
|||
|
|
|
|
|
carInputQueueNotVeryFull |
5-3 |
|
|
|
|||||
|
|
|
|
|
carOtherAuthServerNotResponding |
5-4 |
|
|||||||
|
|
|
|
|
carOtherAuthServerResponding |
5-4 |
|
|||||||
|
|
|
|
|
carOtherAccServerNotResponding |
5-4 |
|
|||||||
|
|
|
|
|
carOtherAccServerResponding |
5-5 |
|
|
||||||
|
|
|
|
|
carAccountingLoggingFailure |
5-5 |
|
|
||||||
|
|
|
|
|
Configuring Traps |
5-5 |
|
|
|
|
|
|
||
|
|
|
|
|
Directories Searched 5-5 |
|
|
|
|
|||||
|
|
|
|
|
Configuration File Types |
5-6 |
|
|
|
|||||
|
|
|
|
|
Switching Configuration Files in Mid-File 5-6 |
|||||||||
|
|
|
|
|
Community String |
5-7 |
|
|
|
|
|
|
||
|
|
|
Prepaid Billing Solution |
|
|
|
|
|
|
|
||||
C H A P T E R |
6 |
|
6-1 |
|
|
|
|
|
|
|||||
|
|
|
|
|
Overview |
6-1 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Configuring Prepaid Billing |
6-3 |
|
|
|
|
|
|||
|
|
|
|
|
Generic Call Flow |
6-4 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Call Flow Details |
6-4 |
|
|
|
|
|
|
||
|
|
|
|
|
Access-Request (Authentication) |
6-5 |
|
|||||||
|
|
|
|
|
Access-Accept (Authentication) |
6-6 |
|
|
||||||
|
|
|
|
|
Access-Request (Authorization) |
6-6 |
|
|
||||||
|
|
|
|
|
Access-Accept (Authorization) |
6-6 |
|
|
||||||
|
|
|
|
Cisco Access Registrar 3.5 Concepts and Reference Guide |
|
|
|
|
|
|||||
|
|
|
|
|
|
|
|
|
||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
vi |
|
|
|
|
|
|
|
|
|
|
|
OL-2683-02 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||

Contents
Accounting Start 6-7 |
|
Data Flow 6-7 |
|
Access-Request (Quota Depleted) |
6-8 |
Accept-Accept (Quota Depleted) |
6-8 |
Accounting Stop (Session End) 6-9 |
|
Accounting Response (Final Status) |
6-9 |
Vendor-Specific Attributes 6-10
G L O S S A R Y
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
OL-2683-02 |
vii |
|

Contents
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
viii |
OL-2683-02 |
|
|
|

About This Guide
This document provides information to help you understand RADIUS concepts and to help you develop a better understanding of the Cisco Access Registrar 3.0 server. This document contains the following chapters:
•Chapter 1, “Overview,” overview of the RADIUS server, including connection steps, RADIUS message types, and using Cisco Access Registrar as a proxy server.
•Chapter 2, “Understanding Cisco Access Registrar,” describes the Cisco Access Registrar object structure, and explains when Cisco Access Registrar references each of these objects during the processing of client requests.
•Chapter 3, “Cisco Access Registrar Scripts,” describes the scripts provided with Cisco Access Registrar.
•Chapter 4, “Understanding Replication,” describes Cisco Access Registrar's configuration replication features, functions, limitations and operation.
•Chapter 5, “Understanding SNMP,” provides information about Cisco Access Registrar support for SNMP.
•Chapter 6, “Prepaid Billing Solution,” describes the generic call flow between the three components required to support a prepaid billing solution using the RADIUS protocol: the AAA client, the Cisco Access Registrar 3.0 server, and a prepaid billing server.
This guide also contains a Glossary and an Index.
Obtaining Documentation
The following sections provide sources for obtaining documentation from Cisco Systems.
World Wide Web
You can access the most current Cisco documentation on the World Wide Web at the following sites:
•http://www.cisco.com
•http://www-china.cisco.com
•http://www-europe.cisco.com
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
OL-2683-02 |
ix |
|

About This Guide
Obtaining Technical Assistance
Ordering Documentation
Cisco documentation is available in the following ways:
•Registered Cisco Direct Customers can order Cisco Product documentation from the Networking Products MarketPlace:
http://www.cisco.com/cgi-bin/order/order_root.pl
•Registered Cisco.com users can order the Documentation CD-ROM through the online Subscription Store:
http://www.cisco.com/go/subscription
•Nonregistered Cisco.com users can order documentation through a local account representative by calling Cisco corporate headquarters (California, USA) at 408 526-7208 or, in North America, by calling 800 553-NETS(6387).
Documentation Feedback
If you are reading Cisco product documentation on the World Wide Web, you can submit technical comments electronically. Click Feedback in the toolbar and select Documentation. After you complete the form, click Submit to send it to Cisco.
You can e-mail your comments to bug-doc@cisco.com.
To submit your comments by mail, use the response card behind the front cover of your document, or write to the following address:
Attn Document Resource Connection
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-9883
We appreciate your comments.
Obtaining Technical Assistance
Cisco provides Cisco.com as a starting point for all technical assistance. Customers and partners can obtain documentation, troubleshooting tips, and sample configurations from online tools. For Cisco.com registered users, additional troubleshooting tools are available from the TAC website.
Cisco.com
Cisco.com is the foundation of a suite of interactive, networked services that provides immediate, open access to Cisco information and resources at anytime, from anywhere in the world. This highly integrated Internet application is a powerful, easy-to-use tool for doing business with Cisco.
Cisco.com provides a broad range of features and services to help customers and partners streamline business processes and improve productivity. Through Cisco.com, you can find information about Cisco and our networking solutions, services, and programs. In addition, you can resolve technical issues with online technical support, download and test software packages, and order Cisco learning materials and merchandise. Valuable online skill assessment, training, and certification programs are also available.
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
x |
OL-2683-02 |
|
|
|

About This Guide
Obtaining Technical Assistance
Customers and partners can self-register on Cisco.com to obtain additional personalized information and services. Registered users can order products, check on the status of an order, access technical support, and view benefits specific to their relationships with Cisco.
To access Cisco.com, go to the following website:
http://www.cisco.com
Technical Assistance Center
The Cisco TAC website is available to all customers who need technical assistance with a Cisco product or technology that is under warranty or covered by a maintenance contract.
Contacting TAC by Using the Cisco TAC Website
If you have a priority level 3 (P3) or priority level 4 (P4) problem, contact TAC by going to the TAC website:
http://www.cisco.com/tac
P3 and P4 level problems are defined as follows:
•P3—Your network performance is degraded. Network functionality is noticeably impaired, but most business operations continue.
•P4—You need information or assistance on Cisco product capabilities, product installation, or basic product configuration.
In each of the above cases, use the Cisco TAC website to quickly find answers to your questions.
To register for Cisco.com, go to the following website:
http://www.cisco.com/register/
If you cannot resolve your technical issue by using the TAC online resources, Cisco.com registered users can open a case online by using the TAC Case Open tool at the following website:
http://www.cisco.com/tac/caseopen
Contacting TAC by Telephone
If you have a priority level 1 (P1) or priority level 2 (P2) problem, contact TAC by telephone and immediately open a case. To obtain a directory of toll-free numbers for your country, go to the following website:
http://www.cisco.com/warp/public/687/Directory/DirTAC.shtml
P1 and P2 level problems are defined as follows:
•P1—Your production network is down, causing a critical impact to business operations if service is not restored quickly. No workaround is available.
•P2—Your production network is severely degraded, affecting significant aspects of your business operations. No workaround is available.
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
OL-2683-02 |
xi |
|

About This Guide
Obtaining Technical Assistance
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
xii |
OL-2683-02 |
|
|
|

C H A P T E R 1
Overview
The chapter provides an overview of the RADIUS server, including connection steps, RADIUS message types, and using Cisco Access Registrar as a proxy server.
Cisco Access Registrar is a RADIUS (Remote Authentication Dial-In User Service) server that allows multiple dial-in Network Access Server (NAS) devices to share a common authentication, authorization, and accounting database.
Cisco Access Registrar handles the following tasks:
•Authentication—determines the identity of users and whether they may be allowed to access the network
•Authorization—determines the level of network services available to authenticated users after they are connected
•Accounting—keeps track of each user’s network activity
•Session and resource management—tracks user sessions and allocates dynamic resources
Using a RADIUS server allows you to better manage the access to your network, as it allows you to store all security information in a single, centralized database instead of distributing the information around the network in many different devices. You can make changes to that single database instead of making changes to every network access server in your network.
RADIUS Protocol
Cisco Access Registrar is based on a client/server model, which supports AAA (authentication, authorization, and accounting). The client is the Network Access Server (NAS) and the server is Cisco Access Registrar. The client passes user information on to the RADIUS server and acts on the response it receives. The server, on the other hand, is responsible for receiving user access requests, authenticating and authorizing users, and returning all of the necessary configuration information the client can then pass on to the user.
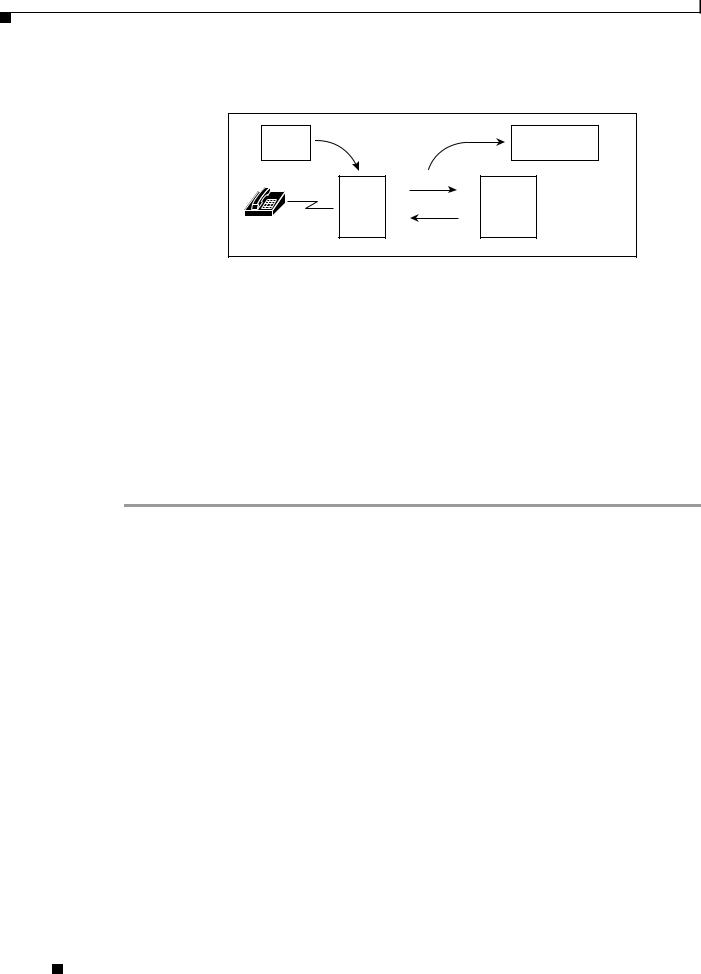
The protocol is a simple packet exchange in which the NAS sends a request packet to the Cisco Access Registrar with a name and a password. Cisco Access Registrar looks up the name and password to verify it is correct, determines for which dynamic resources the user is authorized, then returns an accept packet that contains configuration information for the user session (Figure 1-1).
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
OL-2683-02 |
1-1 |
|
|
|
Chapter 1 Overview
RADIUS Protocol
Figure 1-1 Packet Exchange Between User, NAS, and RADIUS
Jane |
Name=Jane |
xyz |
Password=xyz |
|
request |
N |
Radius |
A |
|
S |
response |
|
|
|
22036 |
Cisco Access Registrar can also reject the packet if it needs to deny network access to the user. Or, Cisco Access Registrar may issue a challenge that the NAS sends to the user, who then creates the proper response and returns it to the NAS, which forwards the challenge response to Cisco Access Registrar in a second request packet.
In order to ensure network security, the client and server use a shared secret, which is a string they both know, but which is never sent over the network. User passwords are also encrypted between the client and the server to protect the network from unauthorized access.
Steps to Connection
Three participants exist in this interaction: the user, the NAS, and the RADIUS server. The following steps describe the receipt of an access request through the sending of an access response.
Step 1 The user, at a remote location such as a branch office or at home, dials into the NAS, and supplies a name and password.
Step 2 The NAS picks up the call and begins negotiating the session.
a.The NAS receives the name and password.
b.The NAS formats this information into an Access-Request packet.
c.The NAS sends the packet on to the Cisco Access Registrar server.
Step 3 The Cisco Access Registrar server determines what hardware sent the request (NAS) and parses the packet.
d.It sets up the Request dictionary based on the packet information.
e.It runs any incoming scripts, which are user-written extensions to Cisco Access Registrar. An incoming script can examine and change the attributes of the request packet or the environment variables, which can affect subsequent processing.
f.Based on the scripts or the defaults, it chooses a service to authenticate and/or authorize the user.
Step 4 Cisco Access Registrar’s authentication service verifies the username and password is in its database. Or, Cisco Access Registrar delegates the authentication (as a proxy) to another RADIUS server, an LDAP, or TACACS server.
Step 5 Cisco Access Registrar’s authorization service creates the response with the appropriate attributes for the user’s session and puts it in the Response dictionary.
Step 6 If you are using Cisco Access Registrar session management at your site, the Session Manager calls the appropriate Resource Managers that allocate dynamic resources for this session.
Step 7 Cisco Access Registrar runs any outgoing scripts to change the attributes of the response packet.
Cisco Access Registrar 3.5 Concepts and Reference Guide
1-2 |
OL-2683-02 |
|
|

Chapter 1 Overview
RADIUS Protocol
Step 8 Cisco Access Registrar formats the response based on the Response dictionary and sends it back to the client (NAS).
Step 9 The NAS receives the response and communicates with the user, which may include sending the user an IP address to indicate the connection has been successfully established.
Types of RADIUS Messages
The client/server packet exchange consists primarily of the following types of RADIUS messages:
•Access-Request—sent by the client (NAS) requesting access
•Access-Reject—sent by the RADIUS server rejecting access
•Access-Accept—sent by the RADIUS server allowing access
•Access-Challenge—sent by the RADIUS server requesting more information in order to allow access. The NAS, after communicating with the user, responds with another Access-Request.
When you use RADIUS accounting, the client and server can also exchange the following two types of messages:
•Accounting-Request—sent by the client (NAS) requesting accounting
•Accounting-Response—sent by the RADIUS server acknowledging accounting
Packet Contents
The information in each RADIUS message is encapsulated in a UDP (User Datagram Protocol) data packet. A packet is a block of data in a standard format for transmission. It is accompanied by other information, such as the origin and destination of the data.
lists each message packet which contains the following five fields:
Table 1-1 RADIUS Packet Fields
Fields |
Description |
|
|
Code |
Indicates what type of message it is: Access-Request, |
|
Access-Accept, Access-Reject, Access-Challenge, |
|
Accounting-Request, or Accounting-Response. |
|
|
Identifier |
Contains a value that is copied into the server’s response so the |
|
client can correctly associate its requests and the server’s responses |
|
when multiple users are being authenticated simultaneously. |
|
|
Length |
Provides a simple error-checking device. The server silently drops |
|
a packet if it is shorter than the value specified in the length field, |
|
and ignores the octets beyond the value of the length field. |
|
|
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
OL-2683-02 |
1-3 |
|
|
|

Chapter 1 Overview
RADIUS Protocol
Table 1-1 |
RADIUS Packet Fields (continued) |
||
|
|
|
|
|
Fields |
|
Description |
|
|
|
|
|
Authenticator |
Contains a value for a Request Authenticator or a Response |
|
|
|
|
Authenticator. The Request Authenticator is included in a client’s |
|
|
|
Access-Request. The value is unpredictable and unique, and is |
|
|
|
added to the client/server shared secret so the combination can be |
|
|
|
run through a one-way algorithm. The NAS then uses the result in |
|
|
|
conjunction with the shared secret to encrypt the user’s password. |
|
|
|
|
|
Attribute(s) |
Depends on the type of message being sent. The number of |
|
|
|
|
attribute/value pairs included in the packet’s attribute field is |
|
|
|
variable, including those required or optional for the type of service |
|
|
|
requested. |
|
|
|
|
The Attribute Dictionary
The Attribute dictionary contains a list of preconfigured authentication, authorization, and accounting attributes that can be part of a client’s or user’s configuration. The dictionary entries translate an attribute into a value Cisco Access Registrar uses to parse incoming requests and generate responses. Attributes have a human-readable name and an enumerated equivalent from 1-255.
Sixty three standard attributes exist, which are defined in RFCs 2865, 2866, 2867, 2868, and 2869. There also are additional vendor-specific attributes that depend on the particular NAS you are using.
Some sample attributes include:
•User-Name—the name of the user
•User-Password—the user’s password
•NAS-IP-Address—the IP address of the NAS
•NAS-Port—the NAS port the user is dialed in to
•Framed Protocol—such as SLIP or PPP
•Framed-IP-Address—the IP address the client uses for the session
•Filter-ID—vendor-specific; identifies a set of filters configured in the NAS
•Callback-Number—the actual callback number.
Proxy Servers
Any one or all of the RADIUS server’s three functions: authentication, authorization, or accounting can be subcontracted to another RADIUS server. Cisco Access Registrar then becomes a proxy server. Proxying to other servers enables you to delegate some of the RADIUS server’s functions to other servers.
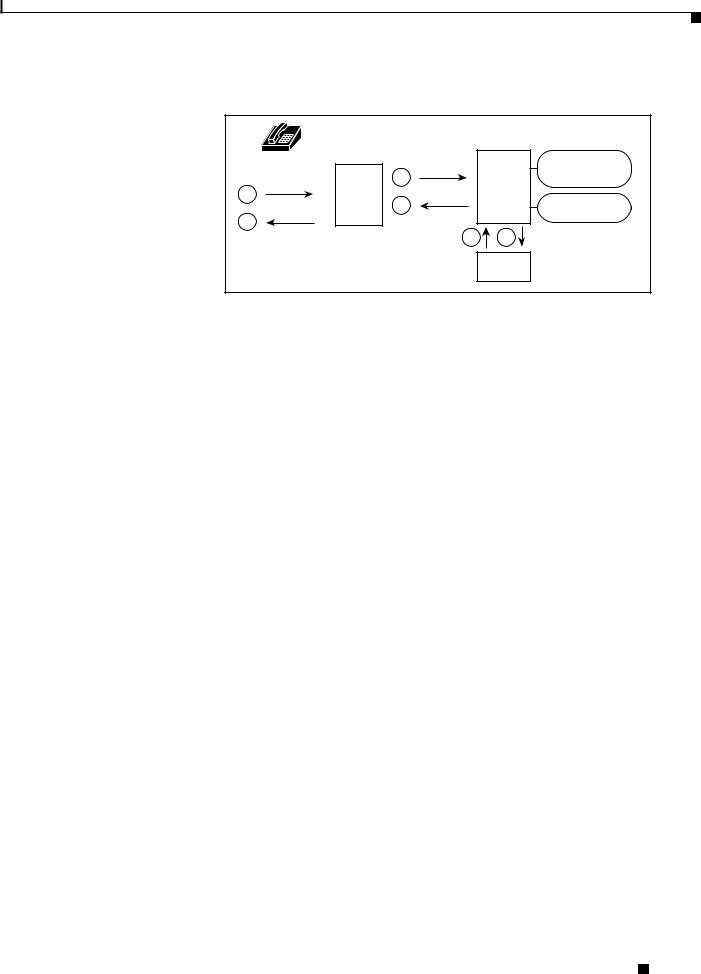
You can use Cisco Access Registrar to “proxy” to an LDAP server for access to directory information about users in order to authenticate them. Figure 1-2 shows user joe initiating a request, the Cisco Access Registrar server proxying the authentication to the LDAP server, and then performing the authorization and accounting processing in order to enable joe to log in.
Cisco Access Registrar 3.5 Concepts and Reference Guide
1-4 |
OL-2683-02 |
|
|
Chapter 1 Overview
Basic Authentication and Authorization
Figure 1-2 Proxying to an LDAP Server for Authentication
user=joe |
|
|
request |
Access |
Authorization |
password=xyz |
NAS |
2 |
|
registrar |
accounting |
1 |
|
5 |
|
|
Authentication |
|
|
response |
|
||
6 |
|
|
|
|
|
|
|
|
3 |
4 |
|
LDAP
22035
Basic Authentication and Authorization
This section provides basic information about how Cisco Access Registrar performs the basic RADIUS functions of authentication and authorization as defined in Internet RFC 2865.
•Authentication—determining the identity of a user of a client NAS through user identification and password validation and deciding whether to grant access
•Authorization—determining the level of network services available to authenticated users after a connection has been established
The Cisco Access Registrar (AR) server provides authentication and authorization service to clients which are network access servers (NAS). The following paragraphs describe the steps to a connection.
1.The process begins when user dials into the NAS and enters a user name and a password. The NAS creates an Access-Request containing attributes such as the user's name, the user's password, the ID of the client, and the Port ID the user is accessing.
2.The Cisco AR server determines which hardware (client NAS) sent the request, parses the packet, and determines whether to accept the request.
The Cisco AR server checks to see if the client's IP address is listed in
/Radius/Clients/<Name>/<IPAddress>.
3.After accepting the request, the Cisco AR server does the following:
–Sets up the Request Dictionary based on the packet information
–Runs any incoming scripts (user-written extensions to Cisco Access Registrar)
An incoming script can examine and change the attributes of the request packet or the environmental variables which can affect subsequent processing.
–Based on default values or scripts, it chooses a service to authenticate and authorize the user.
The Cisco AR server directs the request to the appropriate service, which then performs authentication and/or authorization according to the type specified in
/Radius/Services/<Name>/<Type>.
–Performs session management, directing the request to the appropriate Session Manager.
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
OL-2683-02 |
1-5 |
|
|
|

Chapter 1 Overview
Basic Authentication and Authorization
–Performs resource management for each Resource Manager in the Session Manager. The Cisco AR server directs the request to the appropriate resource manager listed in
/Radius/SessionManagers/<Name>/<ResourceManagers>/<Name>. The resource manager then allocates or checks the resource according to the type listed in
/Radius/<ResourceManagers>/<Name>/<Type>.
4.The Cisco AR server finally creates and formats an Access-Accept, Access Reject, or Access Challenge response, then sends it to the client (NAS).
Cisco Access Registrar 3.5 Concepts and Reference Guide
1-6 |
OL-2683-02 |
|
|

C H A P T E R 2
Understanding Cisco Access Registrar
This chapter describes the Cisco Access Registrar object structure, and explains when Cisco Access Registrar references each of these objects during the processing of client requests.
Cisco Access Registrar lets you manipulate configuration objects, which define the properties or behavior of the RADIUS server. Cisco Access Registrar also lets you invoke custom scripts to affect the behavior of the RADIUS server.
To better understand the role each of these objects plays in the program, it is helpful to look at the steps Cisco Access Registrar performs from receipt of an Access-Request packet to the sending of an Access-Response packet.
Cisco Access Registrar Hierarchy
Cisco Access Registrar’s operation and configuration is based on a set of objects. These objects are arranged in a hierarchical structure much like the Windows 95 Registry or the UNIX directory structure. Cisco Access Registrar’s objects can themselves contain subobjects, just as directories can contain subdirectories.
These objects include the following:
•Radius— the root of the configuration hierarchy
•UserLists—contains individual UserLists which in turn contain users
•UserGroups—contains individual UserGroups
•Clients—contains individual Clients
•Vendors—contains individual Vendors
•Scripts—contains individual Scripts
•Services—contains individual Services
•SessionManagers—contains individual Session Managers
•ResourceManagers—contains individual Resource Managers
•Profiles—contains individual Profiles
•RemoteServers—contains individual RemoteServers
•Advanced—contains Ports, Interfaces, Reply Messages, and the Attribute dictionary.
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
OL-2683-02 |
2-1 |
|
|
|

Chapter 2 Understanding Cisco Access Registrar
Cisco Access Registrar Hierarchy
UserLists and Groups
Cisco Access Registrar lets you organize your user community through the configuration objects
UserLists, users, and UserGroups.
•Use UserLists to group users by organization, such as Company A and Company B. Each list contains the actual names of the users.
•Use users to store information about particular users, such as name, password, group membership, base profile, and so on.
•Use UserGroups to group users by function, such as PPP, Telnet, or multiprotocol users. Groups allow you to maintain common authentication and authorization requirements in one place, and have them referenced by many users.
For more information about UserLists and UserGroups, refer to Access Registrar Server Objects in the
Cisco Access Registrar User’s Guide.
Profiles
Cisco Access Registrar uses Profiles that allow you to group RADIUS attributes to be included in an Access-Accept packet. These attributes include values that are appropriate for a particular user class, such as PPP or Telnet user. The user’s base profile defines the user’s attributes, which are then added to the response as part of the authorization process.
Although you can use Group or Profile objects in a similar manner, choosing whether to use one rather than the other depends on your site. If you require some choice in determining how to authorize or authenticate a user session, then creating specific profiles, and specifying a group that uses a script to choose among the profiles is more flexible. In such a situation, you might create a default group and then write a script that selects the appropriate profile based on the specific request. The benefit to this technique is each user can have a single entry, and use the appropriate profile depending on the way they log in.
For more information about Profiles, refer to Access Registrar Server Objects in the Cisco Access Registrar User’s Guide.
Scripts
Cisco Access Registrar allows you to create scripts you can execute at various points within the processing hierarchy.
•Incoming scripts—enable you to read and set the attributes of the request packet, and set or change the Environment dictionary variables. You can use the environment variables to control subsequent processing, such as specifying the use of a particular authentication service.
•Outgoing scripts—enable you to modify attributes returned in the response packet.
For more information about Scripts, refer to Access Registrar Server Objects in the Cisco Access Registrar User’s Guide.
Services
Cisco Access Registrar uses Services to let you determine how authentication, authorization, and/or accounting are performed.
Cisco Access Registrar 3.5 Concepts and Reference Guide
2-2 |
OL-2683-02 |
|
|

Chapter 2 Understanding Cisco Access Registrar
Cisco Access Registrar Hierarchy
For example, to use Services for authentication:
•When you want the authentication to be performed by the Cisco Access Registrar RADIUS server, you can specify the local service. In this, case you must specify a specific UserList.
•When you want the authentication performed by another server, which may run an independent application on the same or different host than your RADIUS server, you can specify either a radius, ldap, or tacacs-udp service. In this case, you must list these servers by name.
When you have specified more than one authentication service, Cisco Access Registrar determines which one to use for a particular Access-Request by checking the following:
•When an incoming script has set the Environment dictionary variable Authentication-Service with the name of a Service, Cisco Access Registrar uses that service.
•Otherwise, Cisco Access Registrar uses the default authentication service. The default authentication service is a property of the Radius object.
Cisco Access Registrar chooses the authentication service based on the variable Authentication-Service, or the default. The properties of that Service, specify many of the details of that authentication service, such as, the specific user list to use or the specific application (possibly remote) to use in the authentication process.
For more information about Services, refer to Access Registrar Server Objects in the Cisco Access Registrar User’s Guide.
Session Management Using Resource Managers
Cisco Access Registrar lets you track user sessions, and/or allocate dynamic resources to users for the lifetime of their session. You can define one or more Session Managers, and have each one manage the sessions for a particular group or company.
Session Managers use Resource Managers, which in turn manage resources of a particular type as described below.
•IP-Dynamic—manages a pool of IP addresses and allows you to dynamically allocate IP addresses from that pool
•IP-Per-NAS-Port—allows you to associate ports to specific IP addresses, and thus ensure each NAS port always gets the same IP address
•IPX-Dynamic—manages a pool of IPX network addresses
•Group-Session-Limit—manages concurrent sessions for a group of users; that is, it keeps track of how many sessions are active and denies new sessions once the configured limit has been reached
•User-Session-Limit—manages per-user concurrent sessions; that is, it keeps track of how many sessions each user has and denies the user a new session once the configured limit has been reached
•USR-VPN—manages Virtual Private Networks (VPNs) that use USR NAS Clients.
For more information about Session Managers, refer to Access Registrar Server Objects in the Cisco Access Registrar User’s Guide.
If necessary, you can create a complex relationship between the Session Managers and the Resource Managers.
When you need to share a resource among Session Managers, you can create multiple Session Managers that refer to the same Resource Manager. For example, if one pool of IP addresses is shared by two departments, but each department has a separate policy about how many users can be logged in
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
OL-2683-02 |
2-3 |
|
|
|

Chapter 2 Understanding Cisco Access Registrar
Cisco AR Directory Structure
concurrently, you might create two Session Managers and three Resource Managers. One dynamic IP Resource Manager that is referenced by both Session Managers, and two concurrent session Resource Managers, one for each Session Manager.
In addition, Cisco Access Registrar lets you pose queries about sessions. For example, you can query Cisco Access Registrar about which session (and thus which NAS-Identifier, NAS-Port and/or User-Name) owns a particular resource, as well as query Cisco Access Registrar about how many resources are allocated or how many sessions are active.
Cisco AR Directory Structure
The installation process populates the /opt/CSCOar directory with the subdirectories listed in Table 2-1.
Note This directory structure is different from that of previous version of Cisco AR.
Table 2-1 /opt/CSCOar Subdirectories
Subdirectory |
Description |
|
|
.system |
Contains ELFs, or binary SPARC executables that should not be run directly |
|
|
bin |
Contains shell scripts and programs frequently used by a network |
|
administrator; programs that can be run directly |
|
|
conf |
Contains configuration files |
|
|
data |
Contains the radius directory, which contains session backing files; and the |
|
db directory, which contains configuration database files |
|
|
examples |
Contains documentation, sample configuration scripts, and shared library |
|
scripts |
|
|
lib |
Contains Cisco Access Registrar software library files |
|
|
logs |
Contains system logs and is the default directory for RADIUS accounting |
|
|
odbc |
Contains Cisco Access Registrar ODBC files |
|
|
scripts |
Contains sample scripts that you can modify to automate configuration, and |
|
to customize your RADIUS server |
|
|
temp |
Used for temporary storage |
|
|
ucd-snmp |
Contains the UCD-SNMP software Cisco Access Registrar uses |
|
|
usrbin |
Contains a symbolic link that points to bin. |
|
|
Program Flow
When a NAS sends a request packet to Cisco Access Registrar with a name and password, Cisco Access Registrar performs the following actions. Note, Table 2-2 describes the flow without regard to scripting points.
Cisco Access Registrar 3.5 Concepts and Reference Guide
2-4 |
OL-2683-02 |
|
|

Chapter 2 Understanding Cisco Access Registrar
Program Flow
Table 2-2 From Access-Request to Access-Accept
Cisco AR Server Action |
Explanation |
|
|
Receives an Access-Request |
The Cisco Access Registrar server receives an Access-Request packet from a NAS |
|
|
Determines whether to accept |
The Cisco Access Registrar server checks to see if the client’s IP address is listed in |
the request |
/Radius/Clients/<Name>/<IPAddress> |
|
|
Invokes the policy SelectPolicy |
The Cisco ARPolicy Engine provides an interface to define and configure a policy and |
if it exists |
to apply the policy to the corresponding access-request packets |
|
|
Performs authentication and/or |
Directs the request to the appropriate service, which then performs authentication and/or |
authorization |
authorization according to the type specified in /Radius/Services/<Name>/<Type> |
|
|
Performs session management |
Directs the request to the appropriate Session Manager |
|
|
Performs resource management |
Directs the request to the appropriate resource manager listed in |
for each Resource Manager in |
/Radius/SessionManagers/<Name>/<ResourceManagers>/<Name>, which then |
the SessionManager |
allocates or checks the resource according to the type listed in |
|
/Radius/<ResourceManagers>/<Name>/<Type> |
|
|
Sends an Access-Accept |
Creates and formats the response, and sends it back to the client (NAS) |
|
|
Scripting Points
Cisco Access Registrar lets you invoke scripts you can use to affect the Request, Response, or
Environment dictionaries.
Client or NAS Scripting Points
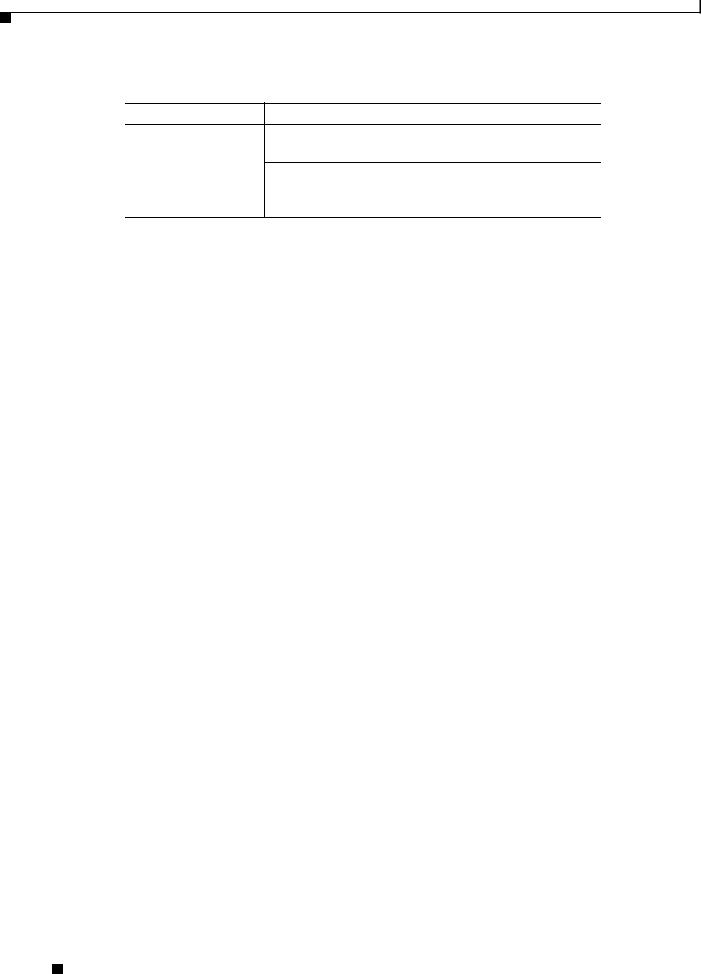
Table 2-3 shows the location of the scripting points within the section that determines whether to accept the request from the client or NAS. Note, the scripting points are indicated with the asterisk (*) symbol.
Table 2-3 Client or NAS Scripting Points
Action |
Explanation |
|
|
Receives an |
The Cisco Access Registrar RADIUS server receives an |
Access-Request. |
Access-Request packet from a NAS. |
|
|
Determines whether to |
The client’s IP address listed in |
accept the request. |
/Radius/Clients/<Name>/IPAddress. |
|
|
*Executes the server’s |
A script referred to in /Radius/IncomingScript. |
incoming script. |
|
|
|
*Executes the vendor’s |
The vendor listed in /Radius/Clients/Name/Vendor, and is |
incoming script. |
a script referred to in |
|
/Radius/Vendors/<Name>/IncomingScript. |
|
|
*Executes the client’s |
A script referred to in |
incoming script. |
/Radius/Clients/<Name>/IncomingScript. |
|
|
Determines whether to accept requests from this specific NAS.
Cisco Access Registrar 3.5 Concepts and Reference Guide
|
OL-2683-02 |
2-5 |
|
|
|
Chapter 2 Understanding Cisco Access Registrar
Program Flow
Table 2-3 Client or NAS Scripting Points (continued)
Action |
Explanation |
/Radius/Advanced/RequireNASsBehindProxyBeInClie ntList set to TRUE.
The NAS’s Identifier listed in /Radius/Clients/<Name>, or its NAS-IP-Address listed in
/Radius/Clients/<Name>/IPAddress.
If the client’s IP address listed in /Radius/Clients/<Name>/IPAddress is different:
*Executes the vendor’s |
The vendor listed in /Radius/Clients/Name/Vendor, and is |
incoming script. |
a script referred to in |
|
/Radius/Vendors/<Name>/IncomingScript. |
|
|
*Executes the client’s |
The client listed in the previous /Radius/Clients/Name, and |
incoming script. |
is a script referred to in |
|
/Radius/Clients/Name/IncomingScript. |
|
|
Authentication and/or Authorization Scripting Points
Table 2-4 shows the location of the scripting points within the section that determines whether to perform authentication and/or authorization.
Table 2-4 Authentication and Authorization Scripting Points
Action |
Explanation |
|
|
|
|
Determines Service to |
The Service name defined in the Environment dictionary |
|
use for authentication |
variable Authentication-Service, and is the same as the |
|
and/or authorization. |
Service defined in the Environment dictionary variable |
|
|
Authorization-Service. |
|
|
|
|
|
The Service name referred to by |
|
|
/Radius/DefaultAuthenticationService, and is the same |
|
|
as the Service defined in |
|
|
/Radius/DefaultAuthorizationService. |
|
|
|
|
Performs |
If the Services are the same, perform authentication and |
|
authentication and/or |
authorization. |
|
authorization. |
|
|
If the Services are different, just perform authentication. |
||
|
||
|
|
|
*Executes the |
A script referred to in |
|
Service’s incoming |
/Radius/Services/<Name>/IncomingScript. |
|
script. |
|
|
|
|
|
Performs |
Based on the Service type defined in |
|
authentication and/or |
/Radius/Services/<Name>/<Type>. |
|
authorization. |
|
|
|
|
|
*Executes the |
A script referred to in |
|
Service’s outgoing |
/Radius/Services/<Name>/OutgoingScript. |
|
script. |
|
|
|
|
Cisco Access Registrar 3.5 Concepts and Reference Guide
2-6 |
OL-2683-02 |
|
|
 Loading...
Loading...