HP Jetdirect 175x Print Server series User Manual

User’s Guide
HP J6035B Jetdirect 175x external print server/Internet connector for USB
HP J6038A Jetdirect 310x external print server/Internet connector for USB
Contents of this User’s Guide
1.Get a general product description of the print server (below)
2.Learn the basics of networking and network printing
3.Install the print server
4.Configure and manage the print server
5.Troubleshoot the print server
6.Get support for the print server
7.Limited warranty for the print server
8.Specifications and regulatory statements for the print server
General product information
The HP Jetdirect 175x and 310x models are external print servers with USB connections. That is, they plug into the USB ports of printers (and multifunction peripherals) to provide network connections for those printers.
(A label on the end of the product’s box lists printers that are tested and supported. Newer models may also be supported.)
Each of these print servers connects to an Ethernet (IEEE 802.3i 10Base-T) or Fast Ethernet (IEEE 802.3u 100Base-TX) network, attached at the RJ-45 connector using twisted-pair cabling.
The two print servers are similar in operation and performance. The 310x offers all the features of the 175x; in addition, it supports several additional network operating systems, additional management tools,

and has upgradable firmware.
The 175x print server supports both peer-to-peer and client/server printer networking under TCP/IP; it supports peer-to-peer printer networking under IPX/SPX (direct mode), Apple EtherTalk, and LPD printing. Operating system support includes Windows (95, 98, 2000, ME, NT 4.0, and XP) and MacOS (v 8.6 and later). See the section on specifications for details of which operating systems support which protocols.
The 310x print server includes all the protocol support of the 175x, as well as client/server support for IPX/SPX under Novell NetWare and support of DLC/LLC, FTP and IPP printing. These protocols are, in various combinations, supported on these operating systems: Windows (95, 98, 2000, ME, NT 4.0, and XP), MacOS, Novell NetWare, HP-UX, Solaris (on SPARC systems), SCO UNIX, LINUX, IBM AIX, MPE-IX, and Artisoft LANtastic. See the section on specifications for details of which operating
systems support which protocols.
Both print servers include an embedded Web server that allows remote management through a Web browser.
The embedded Web server, which allows you to monitor and manage the print server remotely, requires Microsoft Internet Explorer 4.0 or later, or Netscape Navigator 5.0 or later.
See the specifications section for more details on the print servers.
Contents of the product package
The HP Jetdirect 175x and 310x products include:
●print server module, with detachable mounting clip and mounting tape
●power module
●USB cable
●HP Jetdirect CD (includes installation software, manuals, and troubleshooting)
●Startup Guide poster
©2000, 2001, 2002 Hewlett-Packard Company
Networking Basics
Please click on a title to view a document.
The Network Basics Tutorial
A brief overview of:
●Networks
●Network Printing
●Installing a Network Printer
Tips on Getting Started
Answers to common questions:
●Which CD should I use?
●Where do I find the printer driver?
●When do I stop?

The
Network Basics
Tutorial
This tutorial tells you about:
●Networks
●Network Printing
●Installing a Network Printer
Click the button to continue. 

Section 1:
Networks
Click the button to continue. 

NETWORKS
What you want . . .
. . . is for all your computers to be able to:
●Communicate -- send and receive e-mail, and participate in conferences
●Share information -- transfer files among systems, and get information from central databases
●Share resources -- use shared printers, scanners, and servers

NETWORKS
The problem is . . .
. . . standalone computers have no way to talk to each other, so attempts at communication fail.
NETWORKS
The solution: a local area network
A local area network (or LAN) provides connections that tie the computers together and allow them to communicate. (The most common type of local area network may also be referred to as an Ethernet LAN or an Ethernet.)
Local area networks can be either wired (as shown here) or wireless. We will look at the different types in the next few pages.

NETWORKS
Wired LANs
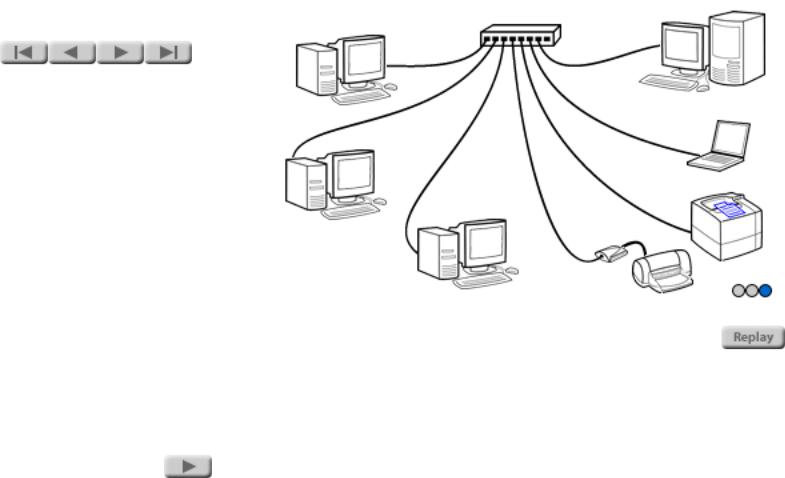
As the name implies, a wired LAN connects computers (and other network devices) physically, using wires. A typical LAN uses twisted-pair wiring (similar to telephone wiring) to connect each computer to a central hub. The hub transmits network communications between computers.
Wired LANs offer high-speed communication, as well as reasonable security and reliability. In general, however, they are not as flexible as wireless LANs.
Most wired LANs conform to the IEEE 802.3 standard. The most common wiring schemes use twisted-pair wiring or thin coaxial wiring.
 Click on these links for more details on LAN wiring:
Click on these links for more details on LAN wiring:
●Detail: twisted-pair wiring
●Detail: thin coaxial wiring
●Detail: computer connections
NETWORKS
DETAIL
Wiring: twisted-pair
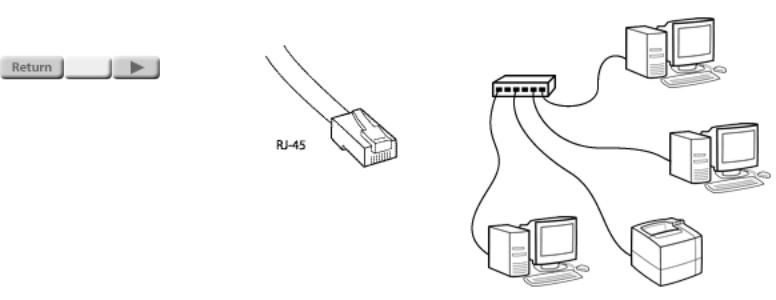
The most common wiring used for LANs is twisted-pair wiring, similar to the wiring used for telephones. This wiring connects the computers or other network devices to a central hub. The use of telephone-type wiring makes it easy for the persons who administer your telephone wiring to administer the network wiring as well.
RJ-45 connectors are used to connect the twisted-pair wiring to the computer and to the hub. The wire for a network can be graded in a number of categories; Category 5 wiring is the most popular grade. Category 5 wiring has superior electrical characteristics, and we strongly recommend it for all twisted-pair networking applications. The wire grade is usually marked on the cable jacket.
The equipment for a twisted-pair LAN commonly operates at a data rate of either 10 Mbps (megabits per second) or 100 Mbps. Category 5 wiring is required for 100-Mbps operation. A 10-Mbps LAN can run on either Category 3 or Category 5 wiring (though we strongly recommend Category 5). At either data rate, cables may extend up to 100 meters (328 feet) from the hub to the computer.
A twisted-pair network running at 10 Mbps is called a type 10Base-T network. A twistedpair network running at 100 Mbps is called a type 100Base-T network.


NETWORKS
DETAIL
Wiring: thin coax
An alternative to twisted-pair wiring is thin coaxial cabling, often called thin coax. This cabling is known as RG-58A or RG-58U cable, and has an impedance of 50 ohms. (It looks similar to the 75-ohm thin coaxial cable used in television installations, but the television cable will not work in a network.)
The connectors used with thin coax are BNC connectors. The cable is a continuous cable, up to 185 meters (606 feet) long, made up of shorter segments with BNC connectors at each end. It connects to computers and other devices along its length using BNC "T" connectors, and there is a 50-ohm terminator at each end of the cable. This cabling scheme does not use a hub.
A thin coaxial LAN operates at a data rate of 10 mbps (megabits per second), and is known as a type 10Base2 network.

NETWORKS
DETAIL
Computer connections
For twisted-pair LANs: A desktop computer connects to a twisted-pair LAN through a network interface card (NIC) that resides in a slot in the computer, or through a similar interface built in to the computer itself. The RJ-45 plug of the network cable plugs into an RJ-45 jack on the card or in the computer. A portable computer may have a built-in connection using an RJ45 jack, or it may use a PC card that inserts into a PC card slot in the computer. (Some PC cards take up two slots and have room for an RJ-45 jack that is integral with the card; others take up only a single slot but require a short cable that provides the RJ-45 jack.)
For thin coaxial LANs: A desktop computer typically connects to a thin coaxial LAN through a network interface card (NIC) ; built-in BNC connections are uncommon. Portable computers connecting to thin coaxial LANs use a PC card with a short cable that provides a BNC connection. In all cases, the LAN cable connects to the computer through a BNC "T" connector.
Hidden network cables and equipment: In many network installations, the hubs are kept in equipment closets and the cables are hidden in the walls. In these installations, wall outlets with RJ45 jacks are the only visible components of the network wiring. For such a network, you use a short length of network cable to connect from the computer to the wall jack.

NETWORKS
Wireless LANs
In a wireless LAN, information travels through the air in radiofrequency signals instead of through wires. This makes wireless LANs very flexible, and setup and reconfiguration are very easy. Communication speeds on wireless LANs, however, tend to be slower than on wired LANs, and it generally takes more work to make a wireless LAN as secure as a wired LAN.
Most wireless LANs conform to one of the subsets of the IEEE 802.11 standard; the most common subset is currently 802.11b. Data rates for 802.11b LANs can be as high as 11 Mbps (megabits per second). Typically a wireless device in an 802.11b LAN can transmit signals across a distance of about 30 meters (100 feet) in a semi-open office (no walls) and still maintain a data rate of 11 Mbps. It is possible to extend the range to about 100 meters (300 feet), but at such a distance the data rate drops off to 1 Mbps.
802.11b wireless LANs operate in the 2.4 GHz frequency band. There are several channels (frequencies) that wireless LANs can use in this range. Government regulations prescribe which channels may be used in various parts of the world.
There are two basic wireless networking topologies -- infrastructure mode and ad hoc mode; these are described in the detail pages (see below).

 Click on these links for more details on wireless LAN topologies:
Click on these links for more details on wireless LAN topologies:
●Detail: infrastructure mode
●Detail: ad hoc mode
●Detail: standalone peripheral connections
●Detail: computer connections

NETWORKS
DETAIL
Infrastructure mode
Terminology: Infrastructure mode is referred to as a "basic service set" (BSS). It's topology is sometimes called a "star topology", and it may also be called "enterprise mode" because it is the preferred topology for large networks. On a network of Apple Macintosh computers, it may be called an "Airport network".
Topology: In infrastructure mode, all signals travel through an access point. Like the hub in a wired LAN, the access point resends the incoming signals out to the computers and other devices on the network. (The access point performs additional functions when a wireless LAN is connected to a wired LAN.) Infrastructure mode is suitable for wireless LANs of all sizes.
In infrastructure mode the access point sets the channel for all device that communicate through it.
A wireless LAN can have multiple access points. This can expand the capacity of the network and extend its range, allowing users to roam with their portable computers and still stay connected to the network.

NETWORKS
DETAIL
Ad hoc mode
Terminology: Infrastructure mode is referred to as an "independent basic service set" (IBSS). It is sometimes called "peer-to-peer mode". On a network of Apple Macintosh computers, it may be called "computer-to-computer mode".
Topology: In ad hoc mode the wireless devices on a network communicate directly with each other, and access points are not used. Ad hoc mode is used for very small networks. Performance in an ad hoc network degrades as you add more devices to the network; typically, ad hoc networks connect no more than six devices.
In ad hoc mode you can select the channel. Make sure that all devices on the network are set to the same channel.

NETWORKS
DETAIL
Standalone peripherals
Not all wireless connections are network connections. Though the distinctions may often be somewhat blurry, some wireless technologies -- such as the Bluetooth technology that is becoming popular in mobile phones and handheld computers -- are more about connecting a computing device to a peripheral, rather than connecting computers and other devices in a network.
For instance, when a handheld computer connects with a walkup wireless printer, or when a mobile phone connects with a vending machine, the interactions between them are typical of a standalone computer talking to a peripheral device. In essence, the wireless connection replaces the cable in a standard peripheral connection. Compared to network connections, such wireless peripheral connections work at short ranges and slow speeds.
(In this tutorial, we will concentrate on the networking that is typified by 802.3-type wired networks and 802.11b-type wireless networks.)

NETWORKS
DETAIL
Computer connections
Connections at the computer for wireless networking connections are simpler than wired ones just because there are no wires to connect.
Wireless connections are most common in portable computers. Increasingly, notebook computers come with built-in wireless networking. For notebook computers that don't have built-in networking, you can plug a wireless networking card into the computer's PC card (PCMCIA) slot. (Wireless networking is based on radio technology, and in many add-on cards the antenna protrudes slightly from the PC card slot.)
Desktop PCs can have wireless networking, too. A typical arrangement is for an adapter in a desktop PC to contain a PC card slot, into which you plug the same kind of wireless networking card that you would use in a notebook computer.

NETWORKS
Mixed LANs
Mixed LANs combine wired and wireless LANs, taking advantage of the strong points of each. For example, a mixed LAN can provide the flexible connections of wireless with the high overall throughput of a wired LAN. Such an arrangement makes it particularly easy for mobile workers to connect their notebook computers to the network.
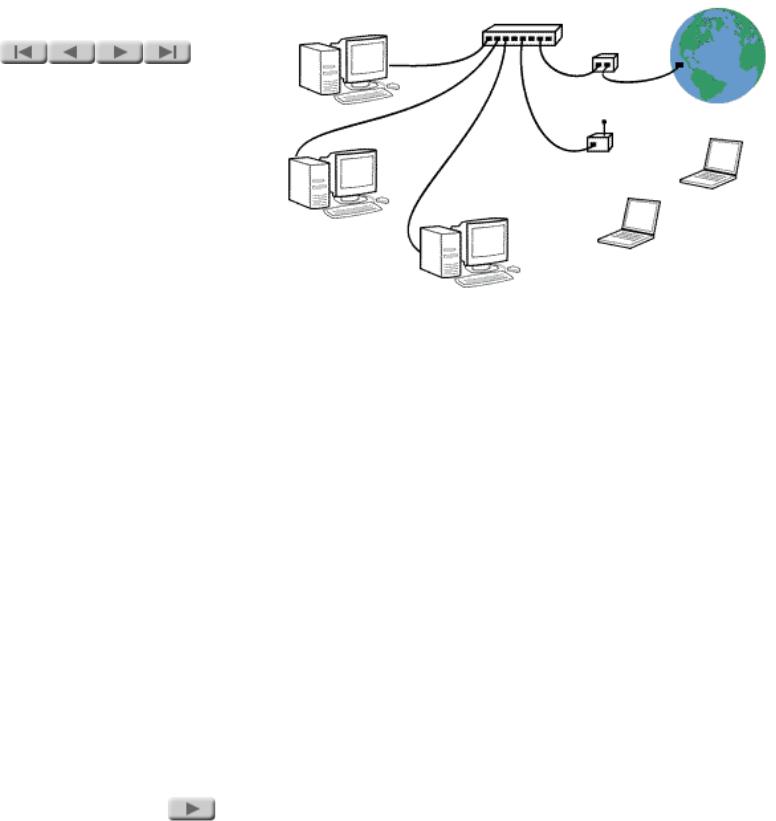
You create a mixed LAN by plugging the network cable from a wired LAN into a port on a wireless access point. In addition to acting as a hub for the wireless portion of the network, the access point acts as a bridge to the wired portion. In a typical case, when a computer with a wireless LAN card comes within range of the access point, it connects through the access point to the LAN (both the wired and wireless portions) and to all the computers and other resources on the LAN.
NETWORKS
L is for Local
The "local" in "local area network" means that the network is in a single location. A LAN can be small enough to serve a home office or a small business, or it can be large enough to serve a school, a hospital, or a substantial business or public office. It can cover several buildings, as long as they can all be connected into a single network. Several types of LAN equipment are available to expand a LAN beyond the workgroup-sized unit typically served by a single hub.
Note that the definition of a local area network does not include broader networks such as the Internet or a corporate network with locations in many cities or countries. These broader networks are often called WANs, or wide area networks. It is possible for a LAN to connect to such a network through a gateway -- a device that connects different types of networks. The gateway can be a separate piece of equipment, or it can include the LAN hub. (This latter type of gateway is becoming increasingly common for Internet connections, particularly for highspeed DSL connections.)
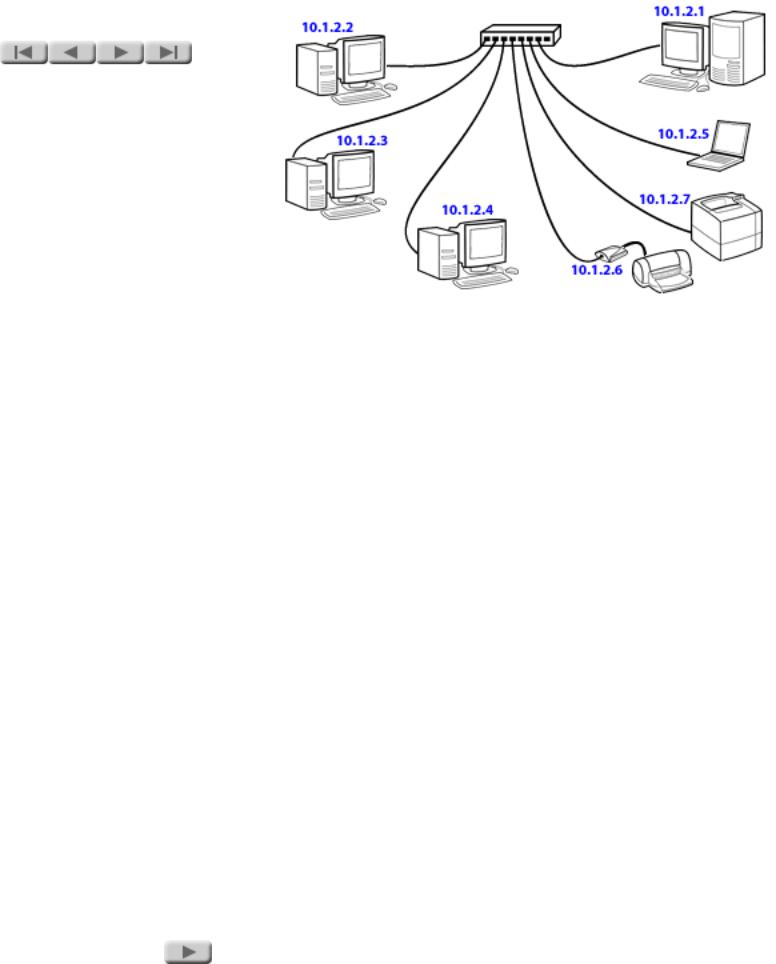
NETWORKS
Addresses
Each device on the network has a unique address. This allows you to communicate with a specific computer (or other device, such as a printer). That way, your e- mail doesn't go to everybody, and your print job doesn't get printed simultaneously on all printers on the network.
There are several addressing schemes for networks. Of these, the most popular is that of the Internet Protocol (IP). In addition to being used on the Internet, IP addressing can also be used for standalone networks that don't connect to the Internet. The network addresses shown in the illustration are sample IP addresses.
Other network addressing schemes you may encounter include IPX (used with Novell NetWare networks), DLC, and AppleTalk. In this tutorial, we limit our discussion of network addressing to IP addressing, as it is the most popular.
The number of possible IP addresses is huge. So is the number of Internet users, and the possibility of conflicts is a real one. If you use IP addresses on your LAN and that LAN connects to the Internet, you must be careful to use addresses that have come from a reliable source, such as your Internet service provider (ISP).

NETWORKS
Wireless security
Wireless networks are inherently less secure than wired ones. In a wired environment an intruder needs to gain physical access to your network wiring to break into your network; in a wireless environment, he just needs to be in range of the radio waves that carry the network traffic. Since these waves penetrate building walls and easily carry for tens of meters, an intruder sitting in a car in your parking lot could monitor the traffic on the wireless LAN in your building.
To frustrate intruders, a number of standards have been developed to make security for a wireless network more-or-less equivalent to that of wired networks. These standards work in three areas:
Network name (SSID): A network name, or service set identifier (SSID) is an alphanumeric character string that provides basic access control on a wireless network. To transmit onto the network, the network name of a computer or other device must match the name configured into the access point.
Authentication:
Authentication verifies the identity of a user or device before the user or device is allowed to transmit onto the network. There are several different schemes of authentication that you might encounter when installing an HP Jetdirect print server:
●Open system: No authentication.
●Shared key: Each device
uses the same shared key (a shared password value) for network access.
Server-based authentication: A server on the network authenticates each client that requests a connection to the network. There are several protocols available, all based on the Extensible Authentication Protocol (EAP). Briefly described, they are:
LEAP
(Lightweight Extensible Authentication Protocol) -- a proprietary protocol from Cisco Systems that uses passwords for mutual authentication (that is, the client and the server authenticate each other).
PEAP
(Protected Extensible Authentication Protocol) -- a mutual authentication protocol that uses digital certificates for server authentication and passwords for client authentication. For additional security, the authentication exchanges are encapsulated within TLS (Transport Level Security).
EAP-MD5 (EAP
using Message Digest algorithm 5) -- a one-way authentication protocol that authenticates the client using a password protected by the MD5 algorithm.
EAP-TLS (EAP using Transport Level Security) -- a mutual authentication protocol based on digital certificates.
EAP-TTLS
(EAP using Tunneled Transport Level Security) -- a mutual authentication protocol that uses digital certificates for server authentication and passwords for client authentication. For additional security, the authentication exchanges are encapsulated within TLS (Transport Level Security).
Encryption: Encryption methods encode the traffic on the network, rendering it unintelligible to an intruder who is monitoring it. WEP (wired equivalency privacy) is an IEEE 802.11 encryption scheme that provides basic access control and data privacy on your wireless network. Under WEP, you supply encryption keys that are used to encrypt the data stream.
In addition, some of the authentication protocols, such as

LEAP and EAP-TLS, can manage encryption keys for the network administrator.
Wireless print server security: As you set up your wireless print server, the wireless setup wizard will make it easy to match the print server's security settings to those of your network. The wizard's help pages provide considerable detail on the process.

Section 2:
Network Printing
Click the button to continue. 
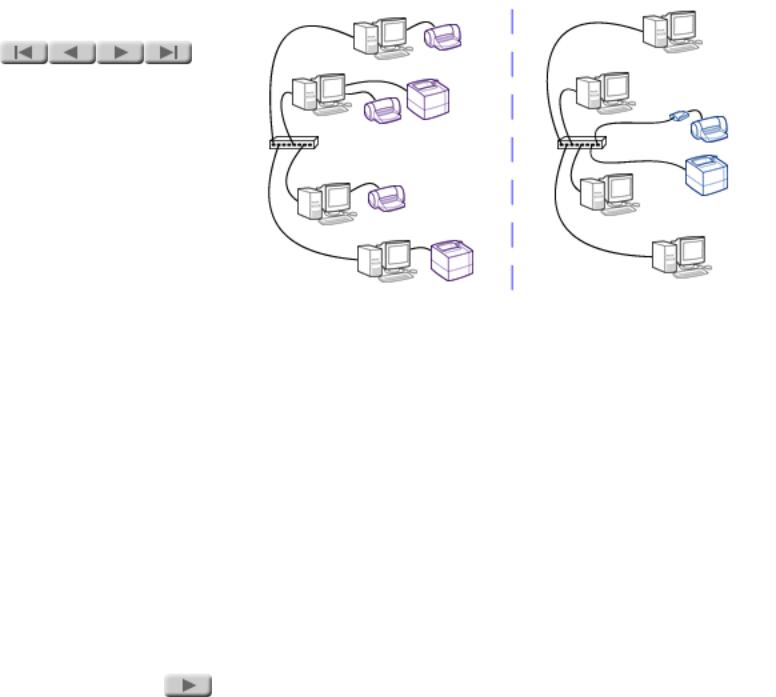
NETWORK PRINTING
Why use network printers?
Using network printers lets you meet your computer users' printing needs more efficiently. By sharing printers among several users, you reduce the number of printers you need. This approach
●saves money -- there's less equipment to buy
●saves space -- users don't need to make space for a printer
●saves maintenance -- fewer printers mean less bother
all with little inconvenience to users. (In fact, shared printers may be more convenient: nobody has to go without a printer or change to a different computer just to print; and sharing may save enough money to let you purchase printers with more functions or greater speed.)

NETWORK PRINTING
Why use a print server?
A print server provides your printer with connection to the network. You could get the same connection using a computer -- your network server -- but it would cost more and be more complex. Using a print server saves you money and frees up your network server for other tasks, such as file storage.
You might want to use a network server for management of print jobs, a function that may be useful for larger networks. In such an application you will still probably want to use a print server, because its small size gives you location flexibility. Using a print server, you can easily place your printers near your users, while keeping the network server out of the way in a central computer area. (You will see this application in the notes on the client/server topology, a couple of pages later in this tutorial.)
 Loading...
Loading...