Schneider Electric M340 Security Notification
Modicon Quantum processors
COPRO
140NOE771x1 versions prior to V7.1
140NOC77101 versions prior to V1.08
Schneider Electric Security Notification
Web Server on Modicon M340, Legacy Offers Modicon Quantum and
Modicon Premium and associated Communication Modules
8 December 2020
Overview
Schneider Electric is aware of multiple vulnerabilities in the web server of the Modicon M340,
Modicon Quantum and Modicon Premium Legacy offers and associated communication modules.
The Modicon Ethernet Programmable Automation controller
industrial process and infrastructure.
Failure to apply the fix provided below may risk a disclosure of information and a Denial of
Service attack, which could result in the unavailability of the controller.
products are controllers for
Affected Products and Versions
Product Version
Modicon M340 CPUs BMXP34* versions prior to V3.30
Modicon M340 Ethernet
Communication modules
Modicon Premium
communication modules
Modicon Premium processors
with integrated Ethernet
COPRO
BMXNOE0100 (H) versions prior to V3.3
BMXNOE0110 (H) versions prior to V6.5
BMXNOC0401 (H) versions prior to V2.10
TSXETY4103 versions prior to V6.2
TSXETY5103 versions prior to V6.4
TSXP574634 versions prior to V6.1
TSXP575634 versions prior to V6.1
TSXP576634 versions prior to V6.1
with integrated Ethernet
Modicon Quantum
communication modules
Vulnerability Details
CVE ID: CVE-2020-7541
CVSS v3.0 Base Score 5.3 | Medium | CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N
A CWE-425: Direct Request ('Forced Browsing') vulnerability exists that could cause disclosure
of sensitive data when sending a specially crafted request to the controller over HTTP.
8-Dec-20 Document Reference Number – SEVD-2020-343-03 Page 1 of 5
140CPU65xx0 versions prior to V6.1
140NOC78x00 versions prior to V1.74

Schneider Electric Security Notification
CVE ID: CVE-2020-7539
CVSS v3.0 Base Score 7.5 | High | CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
A CWE-754 Improper Check for Unusual or Exceptional Conditions vulnerability exists that
could cause a denial of service vulnerability when a specially crafted packet is sent to the
controller over HTTP.
Remediation
These vulnerabilities have been fixed in the versions listed below.
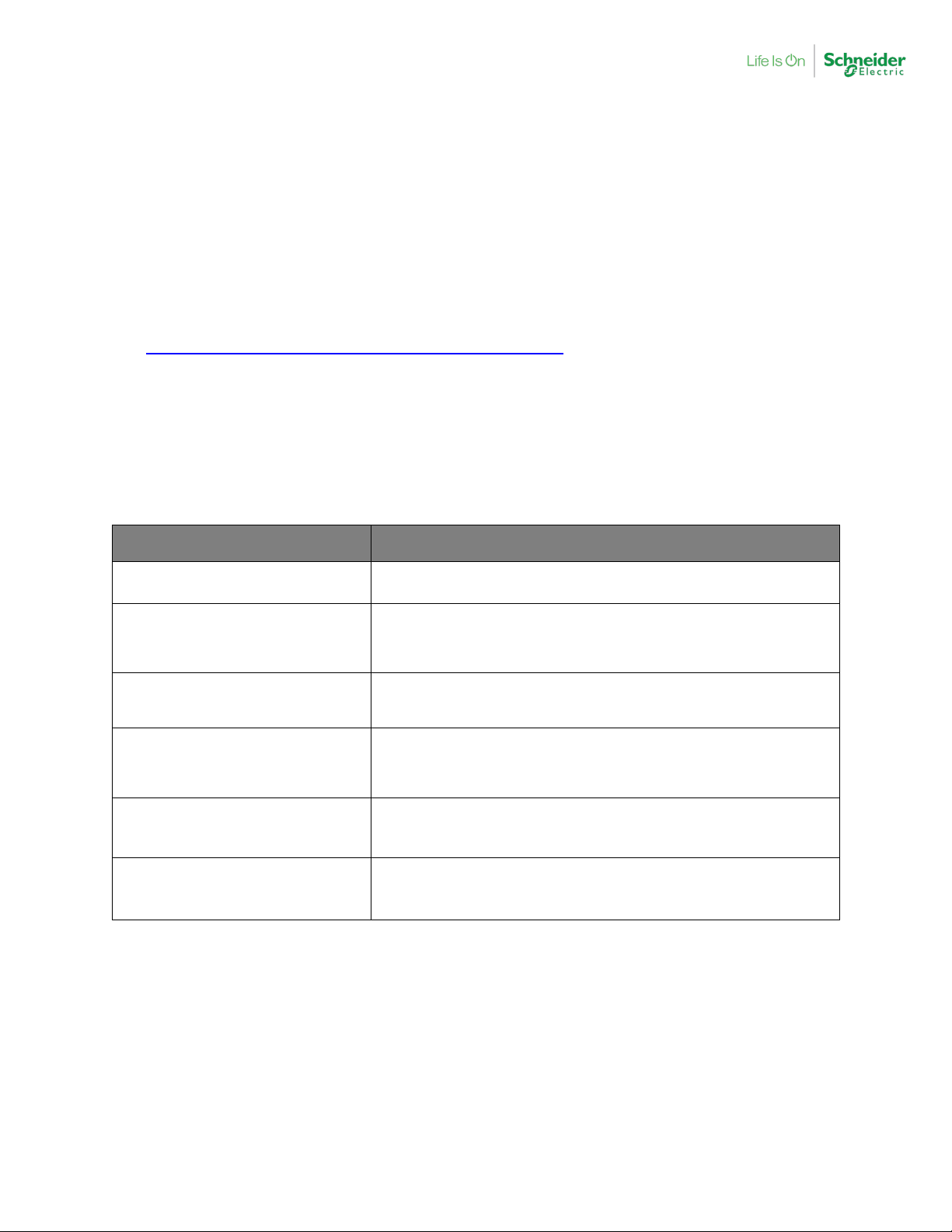
Affected Product & Version Remediation
Firmware version 3.30 is available for all the product
Modicon M340 CPU
BMXP34* versions prior to V3.30
references. Follow this link and find the right firmware
file based on model used.
https://www.se.com/ww/en/product-range/1468modicon-m340/?parent-subcategory-id=3950
Modicon M340 Ethernet
Communication modules
BMXNOE0100 (H) versions prior to
V3.3
Modicon M340 Ethernet
Communication modules
BMXNOE0110 (H versions prior to
V6.5
Modicon M340 Ethernet
Communication modules
BMXNOC0401(H) versions prior to
V2.10
Modicon Premium processors with
integrated Ethernet COPRO:
TSXP574634 versions prior to V6.1
TSXP575634 versions prior to V6.1
TSXP576634 versions prior to V6.1
Modicon Premium communication
modules TSXETY4103 versions
prior to V6.2
Firmware version 3.3 is available for download below
https://www.se.com/ww/en/download/document/BMXN
OE0100 Exec and Release Notes/
Firmware version 6.5 is available for download below
https://www.se.com/ww/en/download/document/BMXN
OE0110 Exec and Release Notes/
Firmware version 2.10 is available for download below
https://www.se.com/ww/en/download/document/BMXN
OC0401 Exec and Release Notes/
Firmware version 6.1 is available for download below
https://www.se.com/ww/en/download/document/TSXP
574634M Premium Copro Exec and Release Notes/
Firmware version 6.2 is available for download below
https://www.se.com/ww/en/download/document/TSXE
TY4103 Exec and Release Notes/
8-Dec-20 Document Reference Number – SEVD-2020-343-03 Page 2 of 5
 Loading...
Loading...