Cisco Firepower 1140 Quick guide

Cisco Firepower 1100 Series Getting Started Guide
First Published: 2019-06-13
Americas Headquarters
Cisco Systems, Inc. 170 West Tasman Drive
San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000
800 553-NETS (6387) Fax: 408 527-0883

C H A P T E R 1
Firepower Threat Defense Deployment with FDM
TheCiscoFirepower1100SeriesisastandalonemodularsecurityservicesplatformthatincludestheFirepower 1120 and Firepower 1140 security appliances. This chapter describes how to deploy a Firepower 1100 Series FTD with Firepower Device Manager (FDM) in your network and how to perform initial configuration.
Important The Firepower 1100 Series supports Cisco Firepower software version 6.4 and later.
Note Privacy Collection Statement—The Firepower 1100 Series does not require or actively collect personally-identifiable information. However, you can use personally-identifiable information in the configuration, for example for usernames. In this case, an administrator might be able to see this information when working with the configuration or when using SNMP.
•Is This Chapter for You?, on page 1
•End-to-End Procedure, on page 2
•Review the Network Deployment and Default Configuration, on page 3
•Cable the Device, on page 4
•Power on the Device, on page 5
•Log Into FDM, on page 6
•Complete the Initial Configuration, on page 6
•Configure Licensing, on page 8
•Configure the Device in Firepower Device Manager, on page 14
•Access the FTD and FXOS CLI, on page 17
•Power Off the Device, on page 19
•What's Next, on page 20
Is This Chapter for You?
This chapter explains how to complete the initial set up and configuration of your Firepower Threat Defense (FTD) device using the Firepower Device Manager (FDM) web-based device setup wizard.
Cisco Firepower 1100 Series Getting Started Guide
1

Firepower Threat Defense Deployment with FDM
End-to-End Procedure
FDM lets you configure the basic features of the software that are most commonly used for small networks. It is especially designed for networks that include a single device or just a few, where you do not want to use a high-powered multiple-device manager to control a large network containing many FDM devices.
If you are managing large numbers of devices, or if you want to use the more complex features and configurations that FTD allows, use the Firepower Management Center (FMC) instead.
End-to-End Procedure
See the following tasks to deploy FTD with FDM on your chassis.
Review the Network Deployment and Default Configuration, on page 3.
Cable the Device, on page 4.
Cisco Firepower 1100 Series Getting Started Guide
2

Firepower Threat Defense Deployment with FDM
Review the Network Deployment and Default Configuration
Power on the Device, on page 5.
Log Into FDM, on page 6.
Complete the Initial Configuration, on page 6.
(Optional) Configure Licensing, on page 8: Obtain feature licenses.
Configure Licensing, on page 8: Generate a license token.
Configure Licensing, on page 8: Register the device with the Smart
Licensing Server.
Configure the Device in Firepower Device Manager, on page 14.
Review the Network Deployment and Default Configuration
The following figure shows the default network deployment for Firepower Threat Defense using Firepower Device Manager on a Firepower 1100 series appliance using the default configuration.
Figure 1: Suggested Network Deployment
Firepower 1100 Series Default Configuration
Forcompleteinformationaboutthedefaultconfiguration,seethe CiscoFirepowerThreatDefenseConfiguration Guide for Firepower Device Manager. The default configuration for the Firepower 1100 series with Firepower Threat Defense using FDM enables the above network deployment with the following behavior:
•inside --> outside traffic flow
•outside IP address from DHCP
Cisco Firepower 1100 Series Getting Started Guide
3

Firepower Threat Defense Deployment with FDM
Cable the Device
•DHCP for clients on inside. There is a DHCP server on the inside interface. You can plug your managementcomputerdirectlyintotheinsideinterfaceandgetanaddressonthe192.168.1.0/24network.
HTTPS access is enabled on the inside interface, so you can open FDM through the inside interface at the default address, 192.168.1.1.
•Alternatively, you can connect to Management 1/1 to set up and manage the device using the FDM. There is a DHCP server on the management interface. You can plug your management computer directly into this interface and get an address on the 192.168.45.46 - 192.168.45.254 network.
HTTPS access is enabled on the management interface, so you can open FDM through the management interface at the default address, 192.168.45.45.
Note The physical management interface is shared between the Management logical interface and the Diagnostic logical interface; see the Interfaces chapter of the Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager.
•The Firepower Threat Defense system requires Internet access for licensing and updates. The system can obtain system database updates through the gateway for the outside interface. You do not need to have an explicit route from the management port or network to the Internet. The default is to use internal routes through the data interfaces.
Cable the Device
The default configuration assumes that certain interfaces are used for the inside and outside networks. Initial configuration will be easier to complete if you connect network cables to the interfaces based on these expectations.
To cable the above scenario on the Firepower 1100 series see the following illustration, which shows a simple topology using a management computer connected to the inside network. Other topologies can be used and your deployment will vary depending on your basic logical network connectivity, ports, addressing, and configuration requirements..
Cisco Firepower 1100 Series Getting Started Guide
4

Firepower Threat Defense Deployment with FDM
Power on the Device
Figure 2: Cabling the Firepower 1100 Series
Procedure
Step 1 Connect the Ethernet 1/1 (outside) interface to your ISP/WAN modem or other outside device. By default, the IP address is obtained using DHCP, but you can set a static address during initial configuration.
Step 2 Connect Ethernet 1/2 to your workstation, the one you will use to configure the device.
Step 3 Configure the workstation to obtain an IP address using DHCP. The workstation gets an address on the 192.168.1.0/24 network.
Note You have a couple of other options for connecting the management workstation. You can also directly connect it to the Management port. The workstation gets an address through DHCP on the 192.168.45.0/24 network. Another option is to leave your workstation attached to a switch, and attach that switch to one of the inside ports such as Ethernet1/2. However, you must ensure that no other device on the switch's network is running a DHCP server, because it will conflict with the one running on the inside bridge group, 192.168.1.1.
Power on the Device
System power is controlled by a rocker power switch located on the rear of the device. The power switch is implemented as a soft notification switch that supports graceful shutdown of the system to reduce the risk of system software and data corruption.
Procedure
Step 1 Attach the power cord to the device, and connect it to an electrical outlet.
Step 2 Turn the power on using the standard rocker-type power on/off switch located on the rear of the chassis, adjacent to the power cord.
Cisco Firepower 1100 Series Getting Started Guide
5

Firepower Threat Defense Deployment with FDM
Log Into FDM
Step 3 Check the Power LED on the back of the device; if it is solid green, the device is powered on.
Step 4 Check the Status LED on the back of the device; after it is solid green, the system has passed power-on diagnostics.
Note WhentheswitchistoggledfromONtoOFF,itmaytakeseveralsecondsforthesystemtoeventually power off. During this time, the Power LED on the front of the chassis blinks green. Do not remove the power until the Power LED is completely off.
Log Into FDM
Log into FDM to configure your FTD.
Before you begin
• Use a current version of Firefox, Chrome, Safari, Edge, or Internet Explorer.
Procedure
Step 1 Enter the following URL in your browser.
•https://192.168.1.1—Inside (Ethernet 1/2) interface IP address.
•https://192.168.45.45—Management interface IP address.
Step 2 Log in with the username admin, and the default password Admin123.
What to do next
• Run through the FDM initial configuration; see Complete the Initial Configuration, on page 6.
Complete the Initial Configuration
Use the setup wizard when you first log into FDM to complete the initial configuration. After you complete the setup wizard, you should have a functioning device with a few basic policies in place:
• An outside (Ethernet1/1) and an inside interface (Ethernet1/2).
Cisco Firepower 1100 Series Getting Started Guide
6

Firepower Threat Defense Deployment with FDM
Complete the Initial Configuration
•Security zones for the inside and outside interfaces.
•An access rule trusting all inside to outside traffic.
•An interface NAT rule that translates all inside to outside traffic to unique ports on the IP address of the outside interface.
•A DHCP server running on the inside interface.
Procedure
Step 1 You are prompted to read and accept the End User License Agreement and change the admin password.
You must complete these steps to continue.
Step 2 Configure the following options for the outside and management interfaces and click Next.
Note Yoursettingsaredeployedtothedevicewhenyouclick Next. Theinterfacewillbenamed“outside” and it will be added to the “outside_zone” security zone. Ensure that your settings are correct.
a)Outside Interface—This is the data port that you connected to your gateway router. You cannot select an alternative outside interface during initial device setup. The first data interface is the default outside interface.
Configure IPv4—The IPv4 address for the outside interface. You can use DHCP or manually enter a static IP address, subnet mask, and gateway. You can also select Off to not configure an IPv4 address.
Configure IPv6—The IPv6 address for the outside interface. You can use DHCP or manually enter a static IP address, prefix, and gateway. You can also select Off to not configure an IPv6 address.
b)Management Interface
DNS Servers—The DNS server for the system's management address. Enter one or more addresses of DNS servers for name resolution. The default is the OpenDNS public DNS servers. If you edit the fields and want to return to the default, click Use OpenDNS to reload the appropriate IP addresses into the fields.
Firewall Hostname—The hostname for the system's management address.
Step 3 Configure the system time settings and click Next.
a)Time Zone—Select the time zone for the system.
b)NTP Time Server—Select whether to use the default NTP servers or to manually enter the addresses of your NTP servers. You can add multiple servers to provide backups.
Step 4 Configure the smart licenses for the system.
You must have a smart license account to obtain and apply the licenses that the system requires. Initially, you can use the 90-day evaluation license and set up smart licensing later.
To register the device now, click the link to log into your Smart Software Manager account, and see Configure Licensing, on page 8.
To use the evaluation license, select Start 90 day evaluation period without registration.
Step 5 Click Finish.
Cisco Firepower 1100 Series Getting Started Guide
7

Firepower Threat Defense Deployment with FDM
Configure Licensing
What to do next
•Although you can continue using the evaluation license, we recommend that you register and license your device; see Configure Licensing, on page 8.
•You can also choose to configure the device; see Configure the Device in Firepower Device Manager, on page 14.
Configure Licensing
The FTD uses Cisco Smart Software Licensing, which lets you purchase and manage a pool of licenses centrally.
When you register the chassis, the License Authority issues an ID certificate for communication between the chassis and the License Authority. It also assigns the chassis to the appropriate virtual account.
The Base license is included automatically. Smart Licensing does not prevent you from using product features that you have not yet purchased, but you should purchase the following optional feature licenses to be in compliance:
•Threat—Security Intelligence and Cisco Firepower Next-Generation IPS
•Malware—Advanced Malware Protection for Networks (AMP)
•URL—URL Filtering
•RA VPN—AnyConnect Plus, AnyConnect Apex, or AnyConnect VPN Only.
In addition to the above licenses, you also need to buy a matching subscription to access updates for 1, 3, or 5 years.
For complete information on licensing your system, see the FDM configuration guide.
Before you begin
•Have a master account on the Cisco Smart Software Manager.
If you do not yet have an account, click the link to set up a new account. The Smart Software Manager lets you create a master account for your organization.
•Your Cisco Smart Software Licensing account must qualify for the Strong Encryption (3DES/AES) license to use some features (enabled using the export-compliance flag).
Procedure
Step 1 Make sure your Smart Licensing account contains the available licenses you need.
When you bought your device from Cisco or a reseller, your licenses should have been linked to your Smart SoftwareLicenseaccount. However,ifyouneedtoaddlicensesyourself,usethe Find Products and Solutions search field on the Cisco Commerce Workspace. Search for the following license PIDs:
Cisco Firepower 1100 Series Getting Started Guide
8
Firepower Threat Defense Deployment with FDM
Configure Licensing
Figure 3: License Search
Note If a PID is not found, you can add the PID manually to your order.
•Threat, Malware, and URL license combination:
•L-FPR1120T-TMC=
•L-FPR1140T-TMC=
•Threat, Malware, and URL subscription combination:
•L-FPR1120T-TMC-1Y
•L-FPR1120T-TMC-3Y
•L-FPR1120T-TMC-5Y
•L-FPR1140T-TMC-1Y
•L-FPR1140T-TMC-3Y
•L-FPR1140T-TMC-5Y
•RA VPN—See the Cisco AnyConnect Ordering Guide.
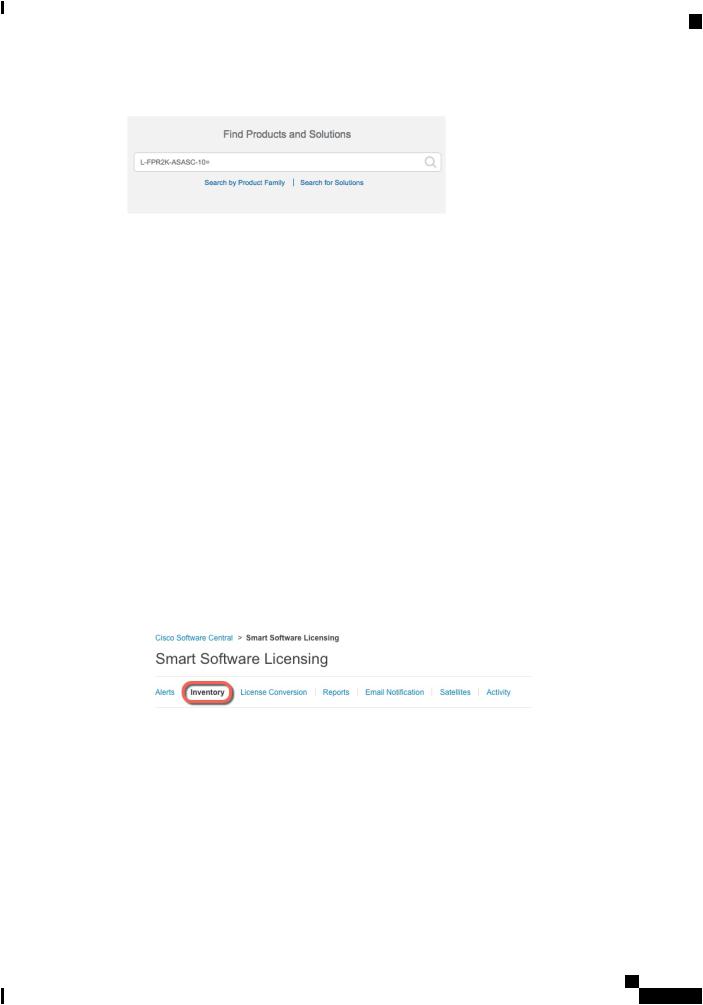
Step 2 In the Cisco Smart Software Manager, request and copy a registration token for the virtual account to which you want to add this device.
a) Click Inventory.
b) On the General tab, click New Token.
Cisco Firepower 1100 Series Getting Started Guide
9

Firepower Threat Defense Deployment with FDM
Configure Licensing
c) On the Create Registration Token dialog box enter the following settings, and then click Create Token:
•Description
•Expire After—Cisco recommends 30 days.
•Allow export-controlled functionaility on the products registered with this token—Enables the export-compliance flag.
The token is added to your inventory.
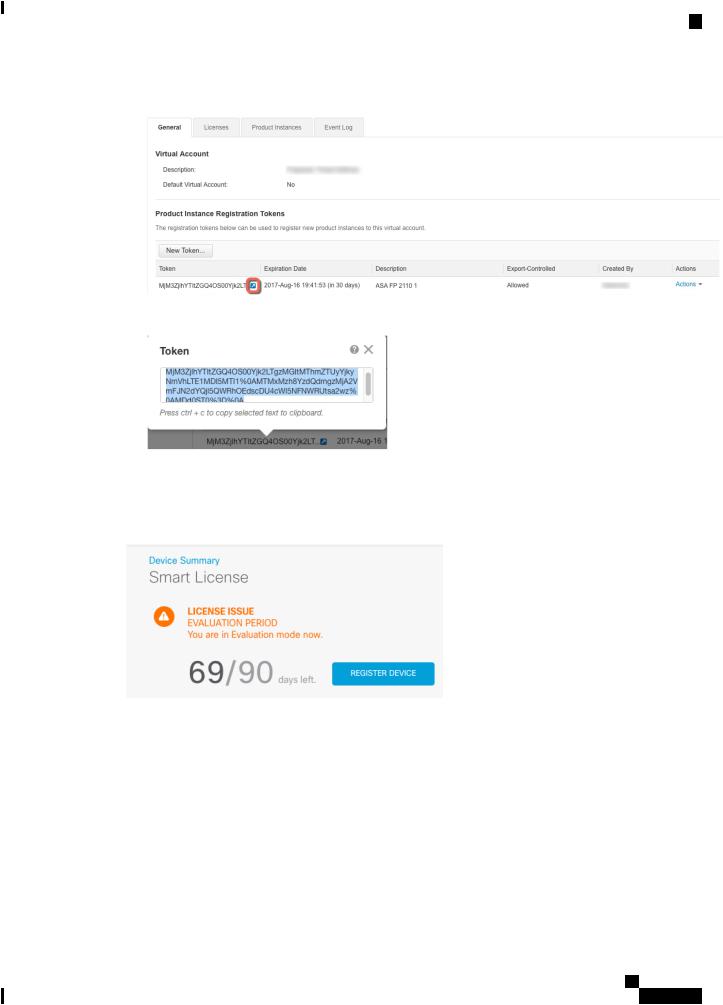
d)Click the arrow icon to the right of the token to open the Token dialog box so you can copy the token ID to your clipboard. Keep this token ready for later in the procedure when you need to register the ASA.
Cisco Firepower 1100 Series Getting Started Guide
10
Firepower Threat Defense Deployment with FDM
Configure Licensing
Figure 4: View Token
Figure 5: Copy Token
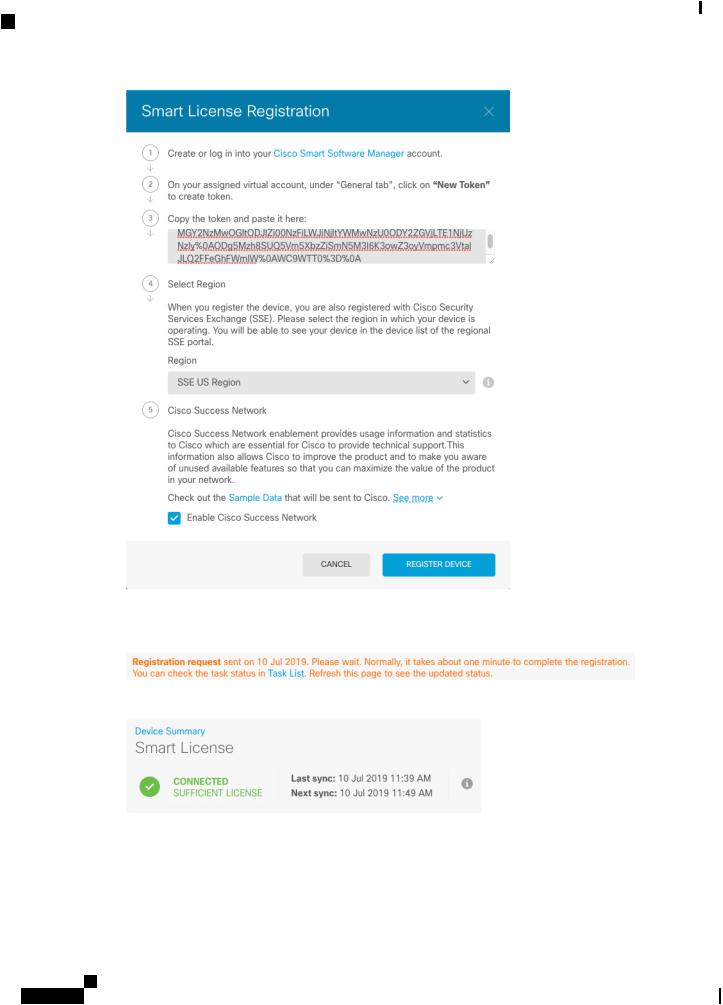
Step 3 In FDM, click Device, and then in the Smart License summary, click View Configuration. You see the Smart License page.
Step 4 Click Register Device.
Then follow the instructions on the Smart License Registration dialog box to paste in your token.:
Cisco Firepower 1100 Series Getting Started Guide
11
Firepower Threat Defense Deployment with FDM
Configure Licensing
Step 5 Click Register Device.
You return to the Smart License page. While the device registers, you see the following message:
After the device successfully registers and you refresh the page, you see the following:
Step 6 Click the Enable/Disable control for each optional license as desired.
Cisco Firepower 1100 Series Getting Started Guide
12

Firepower Threat Defense Deployment with FDM
Configure Licensing
•Enable—RegistersthelicensewithyourCiscoSmartSoftwareManageraccountandenablesthecontrolled features. You can now configure and deploy policies controlled by the license.
•Disable—Unregisters the license with your Cisco Smart Software Manager account and disables the controlled features. You cannot configure the features in new policies, nor can you deploy policies that use the feature.
•If you enabled the RA VPN license, select the type of license you want to use: Plus, Apex, VPN Only, or Plus and Apex.
After you enable features, if you do not have the licenses in your account, you will see the following non-compliance message after you refresh the page:
Step 7 Choose Resync Connection from the gear drop-down list to synchronize license information with Cisco Smart Software Manager.
Cisco Firepower 1100 Series Getting Started Guide
13
 Loading...
Loading...