Cisco MaaS360 User Manual

Integrating Fiberlink MaaS360 with Cisco Identity Services Engine
Revised: August 6, 2013

2
ALL DESIGNS, SPECIFICATIONS, STATEMENTS, INFORMATION, AND RECOMMENDATIONS (COLLECTIVELY, "DESIGNS") IN THIS MANUAL ARE PRESENTED "AS IS," WITH ALL FAULTS. CISCO AND ITS SUPPLIERS DISCLAIM ALL WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THE DESIGNS, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
THE DESIGNS ARE SUBJECT TO CHANGE WITHOUT NOTICE. USERS ARE SOLELY RESPONSIBLE FOR THEIR APPLICATION OF THE DESIGNS. THE DESIGNS DO NOT CONSTITUTE THE TECHNICAL OR OTHER PROFESSIONAL ADVICE OF CISCO, ITS SUPPLIERS OR PARTNERS. USERS SHOULD CONSULT THEIR OWN TECHNICAL ADVISORS BEFORE IMPLEMENTING THE DESIGNS. RESULTS MAY VARY DEPENDING ON FACTORS NOT TESTED BY CISCO.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco’s trademarks can be found at http://www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1005R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
Integrating Fiberlink MaaS360 with Cisco Identity Services Engine
© 2013 Cisco Systems, Inc. All rights reserved.
Integrating Fiberlink MaaS360 with Cisco Identity Services Engine |
3 |
|
|

Integrating Fiberlink MaaS360 with Cisco
Identity Services Engine
This document supplements the Cisco Bring Your Own Device (BYOD) CVD (http://www.cisco.com/en/US/docs/solutions/Enterprise/Borderless_Networks/Unified_Access/BYOD _Design_Guide.html) and provides mobile device management (MDM) partner-specific information as needed to integrate with Cisco ISE. In an effort to maintain readability, some of the information presented in the CVD is repeated here. However this document is not intended to provide standalone BYOD guidance. Furthermore, only a subset of the Fiberlink MaaS360 functionality is discussed. Features not required to extend ISE’s capabilities may be mentioned, but not in the detail required for a comprehensive understanding. The reader should be familiar with the Fiberlink MaaS360 Administrator’s guide.
This document is targeted at existing or new Fiberlink MaaS360 customers. Information necessary to select an MDM partner is not offered in this document. The features discussed are considered to be core functionality present in all MDM software and are required to be compatible with the ISE API.
Overview
Fiberlink MaaS360 secures and manages BYOD and company provided smartphones and tablets. This cloud-based service provides IT administrators the ability to quickly on-board and proactively secure iOS, Android, BlackBerry, and Kindle devices. Fiberlink MaaS360 also provides pre-built integrations with critical enterprise security, identity, email, and mobility infrastructure for a seamless enterprise mobility and collaboration experience on both campus WLAN and carrier networks.
Fiberlink MaaS360 Capabilities and Features
Fiberlink MaaS360 provides the life-cycle management capabilities and features highlighted in Table 1.
Corporate Headquarters:
Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706 USA
Copyright © 2013 Cisco Systems, Inc. All rights reserved.
Table 1 |
Fiberlink MaaS360—Key Capabilities |
||
|
|
|
|
Capability |
|
Features |
|
|
|
|
|
Architecture and |
|
• |
SaaS delivery model |
Adminintration |
|
• |
Multi-tenant, scalable, and redundant cloud architecture |
|
|
||
|
|
• Independent SOC2 Type II cloud compliance audit conducted annually |
|
|
|
• Safe Harbor Certification for European Union Directive on Data Protection |
|
|
|
• Authority to operate (OTA) in accordance with U.S. Federal Information Security Management |
|
|
|
|
Act (FISMA) |
|
|
• Role-based admin access to Fiberlink MaaS360 Admin Portal |
|
|
|
• |
Custom branding capabilities |
|
|
• |
API support |
|
|
• Multiple mobile OS support including iOS, Android, BlackBerry, Windows, and Kindle |
|
|
|
|
|
Device Enrollment |
• |
Select device management services and configure device enrollment settings on Fiberlink |
|
|
|
|
MaaS360 Admin Portal |
|
|
• Send enrollment requests over the air using SMS, email, or a custom URL |
|
|
|
• Authenticate users against Active Directory/LDAP, onetime passcode, or SAML |
|
|
|
• Create and distribute customized acceptable use policies and End User License Agreements |
|
|
|
|
(EULA) |
|
|
• Enroll both corporate and employee owned (BYOD) devices |
|
|
|
• Initiate either individual or bulk device enrollments |
|
|
|
• Apply or modify default device policy settings |
|
|
|
|
|
Proactive Device |
• |
Require passcode policies with configurable quality, length, and duration |
|
Security |
|
• |
Enforce encryption and password visibility settings |
|
|
||
|
|
• Set device restrictions on features, camera, applications, iCloud, and content ratings |
|
|
|
• Detect and restrict jail broken and rooted devices |
|
|
|
• Remotely locate, lock, and wipe lost or stolen devices |
|
|
|
• Selectively wipe corporate data, leaving personal data intact |
|
|
|
• Define and implement real-time compliance rules with automated actions |
|
|
|
• Enable geo-fencing rules to enforce location related compliance |
|
|
|
|
|
Central Policy |
|
• |
Configure email, calendar, contacts, Wi-Fi, and VPN profiles over-the-air (OTA) |
Management |
|
• |
Approve or quarantine new mobile devices on the network |
|
|
||
|
|
• Create custom groups for granular or role-based policy management |
|
|
|
• Define role-based administrative portal access rights to Fiberlink MaaS360 Admin Portal |
|
|
|
• Decommission devices by removing corporate data and mobile device management control |
|
|
|
|
|
Integrating Fiberlink MaaS360 with Cisco Identity Services Engine |
5 |
|
|

Table 1 Fiberlink MaaS360—Key Capabilities
Enterprise Application |
• Manage and distribute third-party and in-house mobile apps from the Fiberlink MaaS360 Admin |
|
Catalog |
Portal |
|
|
• Develop a catalog of recommended mobile apps on iOS and Android devices |
|
|
• Users can view apps, install, and be alerted to updated apps on private app catalog |
|
|
• Manage lifecycle of app workflow: |
|
|
– Real-time software inventory reports |
|
|
– App distribution and installation tracking |
|
|
– |
App update publishing |
|
– |
Provisioning profile management |
|
• Administer mobile app security and compliance policies: |
|
|
– Blacklist and whitelist mobile apps downloaded from Apple App Store and Google Play |
|
|
– Enforce out-of compliance rules by sending user alerts, blocking email or VPN, and remote |
|
|
|
wiping |
|
– Limit native apps available on the device such as YouTube |
|
|
– Require user authentication and authorization before they download in-house apps |
|
|
– Detailed reporting across app compliance events and remediation actions |
|
|
• Host and distribute in-house mobile apps on Fiberlink MaaS360 Cloud |
|
|
• Support for volume purchase programs on Apple App Store: |
|
|
– Automatically upload redemption codes in Fiberlink MaaS360 Cloud |
|
|
– Track provisioning, manage licenses, monitor compliance, and eliminate manual VPP |
|
|
|
management |
|
|
|
Secure Content |
• Securely access, view, and share documents in the Doc Catalog on iPads, iPhones, and Android |
|
Distribution |
Devices |
|
|
• Add additional security with native device encryption, passcode, and remote wipe of lost or |
|
|
stolen devices |
|
|
• Support for multiple document formats including: |
|
|
– |
Microsoft |
|
– |
|
|
– |
Apple Productivity Suites |
|
– PDF, web, audio, and video files |
|
|
• Host documents on a corporate network or on Fiberlink MaaS360 Cloud |
|
|
• Block documents from being opened in file sharing or word processing applications for data loss |
|
|
prevention |
|
|
• Set policies on certain documents to restrict them from being emailed from corporate or personal |
|
|
accounts |
|
|
• Alert users on new or updated content in their Doc Catalog without the need to manually check |
|
|
for updates |
|
|
• Generate reports on documents, users, and devices to monitor status and usage for compliance |
|
|
|
|
6 Integrating Fiberlink MaaS360 with Cisco Identity Services Engine
Table 1 |
Fiberlink MaaS360—Key Capabilities |
||
|
|
|
|
Monitoring and |
|
• |
Detailed hardware and software inventory reports |
Reporting |
|
• |
Configuration and vulnerability details |
|
|
||
|
|
• Integrated smart search capabilities across any attribute |
|
|
|
• Customizable watch lists to track and receive alerts |
|
|
|
• BYOD privacy settings block collection of personally identifiable information |
|
|
|
• Mobile expense management for real-time data usage monitoring and alerting |
|
|
|
|
|
Enterprise |
|
• |
Instant discovery of devices accessing enterprise systems with Fiberlink MaaS360 Connector |
Integrations |
|
• |
Integrate with Microsoft Exchange, Lotus Notes, and Microsoft Office 365 including: |
|
|
||
|
|
|
– Microsoft Exchange 2007 and 2010 |
|
|
|
– BPOS and Office 365 |
|
|
|
– Lotus Traveler 8.5.2 |
|
|
• Integrate with existing Active Directory/LDAP and Certificate Authorities |
|
|
|
• Manage BlackBerry Enterprise Server policies on BlackBerry Enterprise Server 5.0 and higher |
|
|
|
• Connect with other operational systems through web APIs |
|
|
|
|
|
The Fiberlink MaaS360 solution has three main components:
•Portals (Administration and End User)
•Fiberlink MaaS360 Server in the Cloud that manages policies and compliance rules
•Fiberlink MaaS360 Agent software that runs on mobile devices
Beyond these, there is an additional component for enterprise integration called Fiberlink MaaS360 Cloud Extender that integrates with AD, LDAP, email servers, and the PKI infrastructure. The majority of the base functionality is available through the MDM API built into the mobile device operating system. Fiberlink MaaS360 requires the client software to detect some conditions, such as jail-broken or rooted devices. Because ISE tests for these conditions, the Fiberlink MaaS360 server is configured to treat the client software as a required application and will install the software during the on-boarding process.
Deployment Models
Fiberlink MaaS360 offers only a cloud-based service model. To integrate with enterprise backend systems, customers need to install Fiberlink MaaS360 Cloud Extender software on either a physical or virtual machine within their network. Fiberlink MaaS360 Cloud Extender is lightweight software that establishes outbound connection with the Fiberlink MaaS360 cloud. There is no requirement to open any inbound firewall ports to support the Fiberlink MaaS360 Cloud Extender.
Integrating Fiberlink MaaS360 with Cisco Identity Services Engine |
7 |
|
|

Getting Fiberlink MaaS360 Ready for ISE
The first requirement is to establish basic connectivity between the Cisco ISE server and the Fiberlink MaaS360 MDM server. A firewall is typically located between ISE and the Fiberlink MaaS360 cloud. The firewall should be configured to allow an HTTPS session from ISE located in the data center to the Fiberlink MaaS360 server located in the public Internet. The session is established outbound from ISE towards the MDM where ISE takes the client role. This is a common direction for web traffic over corporate firewalls.
Figure 1 |
Traffic Through Firewall |
Cisco ISE
AD/LDAP
FiberLink
Cloud
Certificate
Authority
Cloud
Extender
294297
Import MDM Certificate to ISE
The Fiberlink MaaS360 MDM server incorporates an HTTPS portal to support the various users of the system. In the case of a cloud service, this website will be provided to the enterprise and ISE must establish trust with this website. Even though the cloud website is authenticated with a publicly signed certificate, ISE does not maintain a list of trusted root CAs. Therefore the administrator must establish the trust relationship. The simplest approach is to export the MDM site certificate, then import the certificate into a local cert store in ISE. Most browsers allow this. Internet explorer is shown in Figure 2 with a cloud-based MDM deployment.
8 Integrating Fiberlink MaaS360 with Cisco Identity Services Engine
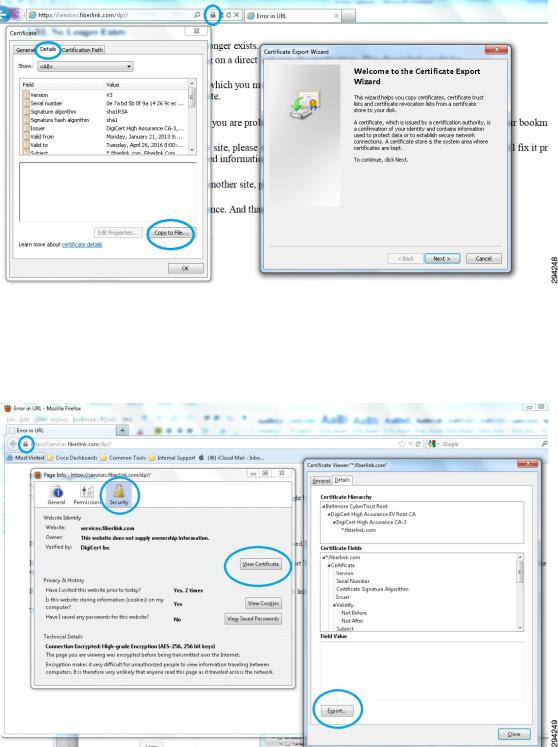
Figure 2 |
Exporting the MDM Site Certificate with Internet Explorer |
Fiberlink MaaS360 utilizes a wildcard certificate that is valid for all portal websites belonging to the Fiberlink MaaS360 portals domain.
Exporting a certificate from Firefox is covered in the CVD and repeated in Figure 3.
Figure 3 |
Exporting the MDM Site Certificate with Firefox |
Integrating Fiberlink MaaS360 with Cisco Identity Services Engine |
9 |
|
|

Figure 4 |
Importing the Certificate in ISE |
Grant ISE Access to the Fiberlink MaaS360 API
The Fiberlink MaaS360 API is protected by HTTPS and requires an administrator account that has been granted permission to the API. Ideally a specific account would be configured for ISE with a very strong password. In addition to this account, only a limited number of administrator accounts should be granted the ability to create new administrators or assign administrator roles.
Before the user is created, an API role should be created for ISE, as shown in Figure 5. This role will then be tied to an administrator account assigned to ISE along with a location group for the account. Administrators can manage the system settings assigned to their role, which can be selected on a per role basis. Additional details concerning location groups are available in the Fiberlink MaaS360 documentation. A local administrator account is required for the REST MDM API roles to function properly.
10 Integrating Fiberlink MaaS360 with Cisco Identity Services Engine
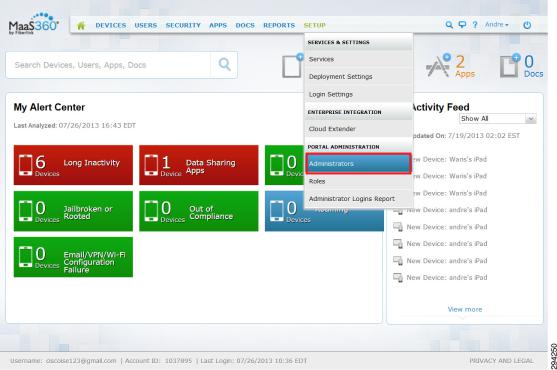
Figure 5 |
Manage Administrator Account |
Each account type can be assigned roles entitling that user to specific features of the system. Also the role of service administrator can be used to manage the API from ISE.
Integrating Fiberlink MaaS360 with Cisco Identity Services Engine |
11 |
|
|

Figure 6 |
Add Account |
The MDM role created for ISE requires the REST API features. The list shown in Figure 7 identifies the rights which should be selected.
12 Integrating Fiberlink MaaS360 with Cisco Identity Services Engine

Figure 7 |
Assign Role to the Account |
Once the role as been added, an admin account can be created for ISE.
Add MDM Server to ISE
Once the account has been defined on the Fiberlink MaaS360 MDM server with the proper roles, ISE can be configured to use this account when querying the MDM for device information. ISE will contact the MDM to gather posture information about devices or to issue device commands, such as corporate wipe or lock. The session is initiated from ISE towards the MDM server. As shown in Figure 8, the URL for the Fiberlink MaaS360 server and the configuration is illustrated. This is configured under Administration > Network resources > MDM.
Integrating Fiberlink MaaS360 with Cisco Identity Services Engine |
13 |
|
|
 Loading...
Loading...