Alcatel-Lucent OMNISWITCH 6600 Management Guide

Part No. 060180-10, Rev. E
March 2005
OmniSwitch 6600 Family
Switch Management Guide
www.alcatel.com

This user guide documents release 5.1.6 of the OmniSwitch 6600 Family. The functionality described in this guide is subject to change without notice.
Copyright © 2005 by Alcatel Internetworking, Inc. All rights reserved. This document may not be reproduced in whole or in part without the express written permission of Alcatel Internetworking, Inc.
Alcatel® and the Alcatel logo are registered trademarks of Alcatel. Xylan®, OmniSwitch®, OmniStack®, and Alcatel OmniVista® are registered trademarks of Alcatel Internetworking, Inc.
OmniAccess™, Omni Switch/Router™, PolicyView™, RouterView™, SwitchManager™, VoiceView™, WebView™, X-Cell™, X-Vision™, and the Xylan logo are trademarks of Alcatel Internetworking, Inc.
This OmniSwitch product contains components which may be covered by one or more of the following U.S. Patents:
•U.S. Patent No. 6,339,830
•U.S. Patent No. 6,070,243
•U.S. Patent No. 6,061,368
•U.S. Patent No. 5,394,402
•U.S. Patent No. 6,047,024
•U.S. Patent No. 6,314,106
•U.S. Patent No. 6,542,507
26801 West Agoura Road
Calabasas, CA 91301
(818) 880-3500 FAX (818) 880-3505 info@ind.alcatel.com
US Customer Support—(800) 995-2696 International Customer Support—(818) 878-4507 Internet—http://eservice.ind.alcatel.com
ii |
OmniSwitch 6600 Family Switch Management Guide March 2005 |

Contents
|
About This Guide .......................................................................................................... |
xi |
|
Supported Platforms .......................................................................................................... |
xi |
|
Who Should Read this Manual? ....................................................................................... |
xii |
|
When Should I Read this Manual? ................................................................................... |
xii |
|
What is in this Manual? .................................................................................................... |
xii |
|
What is Not in this Manual? ............................................................................................. |
xii |
|
How is the Information Organized? ................................................................................ |
xiii |
|
Documentation Roadmap ................................................................................................ |
xiii |
|
Related Documentation .................................................................................................... |
xv |
|
User Manual CD ............................................................................................................. |
xvi |
|
Technical Support ........................................................................................................... |
xvi |
Chapter 1 |
Logging Into the Switch ............................................................................................ |
1-1 |
|
In This Chapter ................................................................................................................ |
1-1 |
|
Login Specifications ........................................................................................................ |
1-2 |
|
Login Defaults ................................................................................................................. |
1-2 |
|
Quick Steps for Logging Into the Switch ........................................................................ |
1-3 |
|
Overview of Switch Login Components ......................................................................... |
1-4 |
|
Management Interfaces ............................................................................................ |
1-4 |
|
Logging Into the CLI ......................................................................................... |
1-4 |
|
Using the WebView Management Tool ............................................................ |
1-5 |
|
Using SNMP to Manage the Switch .................................................................. |
1-5 |
|
User Accounts .......................................................................................................... |
1-5 |
|
Using Telnet .................................................................................................................... |
1-6 |
|
Logging Into the Switch Via Telnet ......................................................................... |
1-6 |
|
Starting a Telnet Session from the Switch ............................................................... |
1-6 |
|
Using FTP ....................................................................................................................... |
1-7 |
|
Using FTP to Log Into the Switch ........................................................................... |
1-7 |
|
Using Secure Shell .......................................................................................................... |
1-8 |
|
Secure Shell Components ......................................................................................... |
1-8 |
|
Secure Shell Interface ........................................................................................ |
1-8 |
|
Secure Shell File Transfer Protocol ................................................................... |
1-8 |
|
Secure Shell Application Overview ......................................................................... |
1-9 |
|
Secure Shell Authentication ................................................................................... |
1-10 |
|
Protocol Identification ..................................................................................... |
1-10 |
|
Algorithm and Key Exchange ......................................................................... |
1-10 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |
iii |

|
|
Contents |
|
|
|
|
|
|
|
Authentication Phase ....................................................................................... |
1-10 |
|
Connection Phase ............................................................................................ |
1-11 |
|
Starting a Secure Shell Session .............................................................................. |
1-11 |
|
Closing a Secure Shell Session .............................................................................. |
1-13 |
|
Log Into the Switch with Secure Shell FTP ........................................................... |
1-13 |
|
Closing a Secure Shell FTP Session ...................................................................... |
1-14 |
|
Modifying the Login Banner ......................................................................................... |
1-15 |
|
Modifying the Text Display Before Login ............................................................. |
1-16 |
|
Configuring Login Parameters ...................................................................................... |
1-17 |
|
Configuring the Inactivity Timer .................................................................................. |
1-17 |
|
Enabling the DNS Resolver .......................................................................................... |
1-18 |
|
Verifying Login Settings ............................................................................................... |
1-18 |
Chapter 2 |
Managing System Files ............................................................................................. |
2-1 |
|
In This Chapter ................................................................................................................ |
2-1 |
|
File Management Specifications ..................................................................................... |
2-2 |
|
Switch Administration Overview .................................................................................... |
2-3 |
|
File Transfer ............................................................................................................. |
2-3 |
|
Switch Directories .................................................................................................... |
2-4 |
|
File and Directory Management ...................................................................................... |
2-5 |
|
Using Wildcards ....................................................................................................... |
2-7 |
|
Multiple Characters ........................................................................................... |
2-7 |
|
Single Characters ............................................................................................... |
2-7 |
|
Directory Commands ............................................................................................... |
2-8 |
|
Determining Your Location in the File Structure .............................................. |
2-8 |
|
Changing Directories ......................................................................................... |
2-9 |
|
Displaying Directory Contents ........................................................................ |
2-10 |
|
Making a New Directory ................................................................................. |
2-11 |
|
Displaying Directory Contents Including Subdirectories ................................ |
2-12 |
|
Copying an Existing Directory ........................................................................ |
2-12 |
|
Removing a Directory and its Contents ........................................................... |
2-13 |
|
File Commands ...................................................................................................... |
2-14 |
|
Creating or Modifying Files ............................................................................ |
2-14 |
|
Copy an Existing File ...................................................................................... |
2-14 |
|
Move an Existing File or Directory ................................................................. |
2-15 |
|
Change File Attribute and Permissions ........................................................... |
2-16 |
|
Delete an Existing File .................................................................................... |
2-16 |
|
Managing Files on Non Primary Switches ...................................................... |
2-16 |
|
Utility Commands .................................................................................................. |
2-17 |
|
Displaying Free Memory Space ...................................................................... |
2-17 |
|
Performing a File System Check ..................................................................... |
2-17 |
|
Deleting the Entire File System ....................................................................... |
2-18 |
|
Loading Software onto the Switch ................................................................................ |
2-19 |
|
Using the Switch as an FTP Server ........................................................................ |
2-19 |
|
Using the Switch as an FTP Client ......................................................................... |
2-21 |
|
Using Secure Shell FTP ......................................................................................... |
2-23 |
|
Closing a Secure Shell FTP Session ...................................................................... |
2-23 |
ivOmniSwitch 6600 Family Switch Management Guide March 2005

Contents
|
|
|
|
|
|
|
.......................................................................................................Using Zmodem |
2-24 |
|
Registering Software Image Files ................................................................................. |
2-26 |
|
Directories on the Switch ....................................................................................... |
2-26 |
|
Using the Install Command .................................................................................... |
2-27 |
|
Available Image Files ............................................................................................. |
2-28 |
|
Application Examples for File Management ................................................................ |
2-29 |
|
Transferring a File to the Switch Using FTP ......................................................... |
2-29 |
|
Creating a File Directory on the Switch ................................................................. |
2-30 |
|
FTP Client Application Example .................................................................... |
2-31 |
|
Creating a File Directory Using Secure Shell FTP ................................................ |
2-32 |
|
Transfer a File Using Secure Shell FTP ................................................................. |
2-34 |
|
Closing a Secure Shell FTP Session ...................................................................... |
2-34 |
|
Verifying Directory Contents ........................................................................................ |
2-34 |
|
Setting the System Clock .............................................................................................. |
2-35 |
|
Setting Date and Time ............................................................................................ |
2-35 |
|
Date .................................................................................................................. |
2-35 |
|
Time Zone ....................................................................................................... |
2-35 |
|
Time ................................................................................................................. |
2-36 |
|
Daylight Savings Time Configuration ................................................................... |
2-37 |
|
Enabling DST .................................................................................................. |
2-38 |
Chapter 3 |
Configuring Network Time Protocol (NTP) .......................................................... |
3-1 |
|
In This Chapter ................................................................................................................ |
3-1 |
|
NTP Specifications .......................................................................................................... |
3-2 |
|
NTP Defaults Table ......................................................................................................... |
3-2 |
|
NTP Quick Steps ............................................................................................................. |
3-3 |
|
NTP Overview ................................................................................................................ |
3-4 |
|
Stratum ..................................................................................................................... |
3-5 |
|
Using NTP in a Network .......................................................................................... |
3-5 |
|
Authentication .......................................................................................................... |
3-7 |
|
Configuring NTP ............................................................................................................. |
3-8 |
|
Configuring the OmniSwitch as a Client ................................................................. |
3-8 |
|
NTP Servers ............................................................................................................. |
3-9 |
|
Using Authentication .............................................................................................. |
3-10 |
|
Verifying NTP Configuration ....................................................................................... |
3-11 |
Chapter 4 |
Managing CMM Directory Content ........................................................................ |
4-1 |
|
In This Chapter ................................................................................................................ |
4-1 |
|
CMM Specifications ....................................................................................................... |
4-2 |
|
CMM Files ...................................................................................................................... |
4-3 |
|
CMM Software Directory Structure ......................................................................... |
4-3 |
|
Where is the Switch Running From? ................................................................. |
4-4 |
|
Software Rollback Feature ....................................................................................... |
4-4 |
|
Software Rollback Configuration Scenarios for a Single Switch ..................... |
4-5 |
|
Redundancy .............................................................................................................. |
4-9 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |
v |

|
|
Contents |
|
|
|
|
|
|
|
Redundancy Scenarios ....................................................................................... |
4-9 |
|
Managing the Directory Structure (Non-Redundant) ................................................... |
4-13 |
|
Rebooting the Switch ............................................................................................. |
4-13 |
|
Copying the Running Configuration to the Working Directory ............................ |
4-15 |
|
Rebooting from the Working Directory ................................................................. |
4-17 |
|
Copying the Working Directory to the Certified Directory ................................... |
4-20 |
|
Copying the Certified Directory to the Working Directory ................................... |
4-21 |
|
Show Currently Used Configuration ...................................................................... |
4-22 |
|
Show Switch Files .................................................................................................. |
4-23 |
|
Managing Redundancy in a Stack ................................................................................. |
4-24 |
|
Rebooting the Switch ............................................................................................. |
4-24 |
|
Copying the Working Directory to the Certified Directory ................................... |
4-25 |
|
Synchronizing the Primary and Secondary CMMs ................................................ |
4-26 |
|
Swapping the Primary CMM for the Secondary CMM ......................................... |
4-28 |
|
Show Currently Used Configuration ...................................................................... |
4-28 |
|
Emergency Restore of the boot.cfg File ........................................................................ |
4-30 |
|
Can I Restore the boot.file While Running from Certified? .................................. |
4-30 |
|
Displaying CMM Conditions ........................................................................................ |
4-31 |
Chapter 5 |
Using the CLI ............................................................................................................... |
5-1 |
|
CLI Specifications ........................................................................................................... |
5-2 |
|
CLI Overview .................................................................................................................. |
5-2 |
|
Online Configuration ................................................................................................ |
5-2 |
|
Offline Configuration Using Configuration Files .................................................... |
5-3 |
|
Command Entry Rules and Syntax ................................................................................. |
5-3 |
|
Text Conventions ..................................................................................................... |
5-3 |
|
Using “Show” Commands ....................................................................................... |
5-4 |
|
Using the “No” Form ............................................................................................... |
5-4 |
|
Using “Alias” Commands ........................................................................................ |
5-4 |
|
Partial Keyword Completion .................................................................................... |
5-5 |
|
Command Help ............................................................................................................... |
5-5 |
|
Tutorial for Building a Command Using Help ......................................................... |
5-7 |
|
CLI Services .................................................................................................................... |
5-9 |
|
Command Line Editing ............................................................................................ |
5-9 |
|
Deleting Characters ........................................................................................... |
5-9 |
|
Recalling the Previous Command Line ........................................................... |
5-10 |
|
Inserting Characters ......................................................................................... |
5-10 |
|
Syntax Checking .................................................................................................... |
5-11 |
|
Prefix Recognition .................................................................................................. |
5-11 |
|
Example for Using Prefix Recognition ........................................................... |
5-12 |
|
Prefix Prompt ................................................................................................... |
5-13 |
|
Command History .................................................................................................. |
5-13 |
|
Logging CLI Commands and Entry Results ................................................................. |
5-15 |
|
Enabling Command Logging .......................................................................... |
5-15 |
|
Disabling Command Logging ......................................................................... |
5-15 |
|
Viewing the Current Command Logging Status ............................................. |
5-16 |
|
Viewing Logged CLI Commands and Command Entry Results .................... |
5-16 |
viOmniSwitch 6600 Family Switch Management Guide March 2005

Contents
|
|
|
|
|
|
|
...................................................................................Customizing the Screen Display |
5-17 |
|
Changing the Screen Size ....................................................................................... |
5-17 |
|
Changing the CLI Prompt ...................................................................................... |
5-17 |
|
Displaying Table Information ................................................................................ |
5-18 |
|
Filtering Table Information .................................................................................... |
5-19 |
|
Multiple User Sessions .................................................................................................. |
5-20 |
|
Listing Other User Sessions ................................................................................... |
5-20 |
|
Listing Your Current Login Session ...................................................................... |
5-21 |
|
Terminating Another Session ................................................................................. |
5-22 |
|
Application Example ..................................................................................................... |
5-23 |
|
Using a Wildcard to Filter Table Information ........................................................ |
5-23 |
|
Verifying CLI Usage ..................................................................................................... |
5-24 |
Chapter 6 |
Working With Configuration Files ......................................................................... |
6-1 |
|
In This Chapter ................................................................................................................ |
6-1 |
|
Configuration File Specifications ................................................................................... |
6-2 |
|
Tutorial for Creating a Configuration File ...................................................................... |
6-2 |
|
Quick Steps for Applying Configuration Files ............................................................... |
6-4 |
|
Setting a File for Immediate Application ................................................................. |
6-4 |
|
Setting an Application Session for a Date and Time ............................................... |
6-4 |
|
Setting an Application Session for a Specified Time Period ................................... |
6-5 |
|
Configuration Files Overview ......................................................................................... |
6-6 |
|
Applying Configuration Files to the Switch ............................................................ |
6-6 |
|
Verifying a Timed Session ................................................................................ |
6-6 |
|
Cancelling a Timed Session .............................................................................. |
6-7 |
|
Configuration File Error Reporting ................................................................... |
6-7 |
|
Setting the Error File Limit ............................................................................... |
6-8 |
|
Syntax Checking ................................................................................................ |
6-8 |
|
Displaying a Text File .............................................................................................. |
6-9 |
|
Text Editing on the Switch ....................................................................................... |
6-9 |
|
Invoke the “Vi” Editor ....................................................................................... |
6-9 |
|
Creating Snapshot Configuration Files ......................................................................... |
6-10 |
|
Snapshot Feature List ............................................................................................. |
6-10 |
|
User-Defined Naming Options ........................................................................ |
6-11 |
|
Editing Snapshot Files ..................................................................................... |
6-11 |
|
Verifying File Configuration ......................................................................................... |
6-14 |
Chapter 7 |
Managing Switch User Accounts ............................................................................ |
7-1 |
|
In This Chapter ................................................................................................................ |
7-1 |
|
User Database Specifications .......................................................................................... |
7-2 |
|
User Account Defaults .................................................................................................... |
7-2 |
|
Overview of User Accounts ............................................................................................ |
7-3 |
|
Startup Defaults ........................................................................................................ |
7-4 |
|
Quick Steps for Network Administrator User Accounts .......................................... |
7-5 |
|
Quick Steps for Creating Customer Login User Accounts ...................................... |
7-6 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |
vii |

|
|
Contents |
|
|
|
|
|
|
|
Default User Settings ............................................................................................... |
7-7 |
|
How User Settings Are Saved .................................................................................. |
7-7 |
|
Creating a User ................................................................................................................ |
7-8 |
|
Removing a User ...................................................................................................... |
7-8 |
|
User-Configured Password ...................................................................................... |
7-8 |
|
Setting a Minimum Password Size ........................................................................... |
7-9 |
|
Configuring Password Expiration ............................................................................ |
7-9 |
|
Default Password Expiration ............................................................................. |
7-9 |
|
Specific User Password Expiration ................................................................. |
7-10 |
|
Configuring Privileges for a User ................................................................................. |
7-11 |
|
Setting Up SNMP Access for a User Account .............................................................. |
7-12 |
|
SNMP Access Without Authentication/Encryption ............................................... |
7-12 |
|
SNMP Access With Authentication/Encryption .................................................... |
7-13 |
|
Removing SNMP Access From a User .................................................................. |
7-13 |
|
Setting Up End-User Profiles ........................................................................................ |
7-14 |
|
Creating End-User Profiles .................................................................................... |
7-15 |
|
Setting Up Port Ranges in a Profile ....................................................................... |
7-15 |
|
Setting Up VLAN Ranges in a Profile ................................................................... |
7-15 |
|
Associating a Profile With a User .......................................................................... |
7-16 |
|
Removing a Profile From the Configuration .......................................................... |
7-16 |
|
Verifying the User Configuration ................................................................................. |
7-16 |
Chapter 8 |
Managing Switch Security ........................................................................................ |
8-1 |
|
In This Chapter ................................................................................................................ |
8-1 |
|
Switch Security Specifications ........................................................................................ |
8-2 |
|
Switch Security Defaults ................................................................................................. |
8-2 |
|
Switch Security Overview ............................................................................................... |
8-3 |
|
Authenticated Switch Access .......................................................................................... |
8-4 |
|
AAA Servers—RADIUS or LDAP .......................................................................... |
8-4 |
|
Authentication-only—ACE/Server .......................................................................... |
8-4 |
|
Interaction With the User Database ......................................................................... |
8-5 |
|
ASA and Authenticated VLANs .............................................................................. |
8-5 |
|
Configuring Authenticated Switch Access ..................................................................... |
8-6 |
|
Quick Steps for Setting Up ASA .................................................................................... |
8-7 |
|
Setting Up Management Interfaces for ASA .................................................................. |
8-9 |
|
Enabling Switch Access ......................................................................................... |
8-10 |
|
Configuring the Default Setting ............................................................................. |
8-10 |
|
Using Secure Shell ................................................................................................. |
8-11 |
|
Configuring Accounting for ASA ................................................................................. |
8-12 |
|
Verifying the ASA Configuration ................................................................................. |
8-13 |
viiiOmniSwitch 6600 Family Switch Management Guide March 2005

Contents
|
|
|
|
|
|
Chapter 9 |
...........................................................................................................Using WebView |
9-1 |
|
In This Chapter ................................................................................................................ |
9-1 |
|
WebView CLI Defaults ................................................................................................... |
9-2 |
|
Browser Setup ................................................................................................................. |
9-2 |
|
WebView CLI Commands .............................................................................................. |
9-3 |
|
Enabling/Disabling WebView .................................................................................. |
9-3 |
|
Enabling/Disabling SSL ........................................................................................... |
9-3 |
|
Quick Steps for Setting Up WebView ............................................................................ |
9-4 |
|
WebView Overview ........................................................................................................ |
9-4 |
|
WebView Page Layout ............................................................................................. |
9-4 |
|
Banner ................................................................................................................ |
9-5 |
|
Toolbar .............................................................................................................. |
9-5 |
|
Feature Options ................................................................................................. |
9-6 |
|
View/Configuration Area .................................................................................. |
9-6 |
|
Configuring the Switch With WebView ......................................................................... |
9-7 |
|
Accessing WebView ................................................................................................ |
9-7 |
|
Home Page ............................................................................................................... |
9-8 |
|
Configuration Page ................................................................................................... |
9-9 |
|
Global Configuration Page ................................................................................ |
9-9 |
|
Table Configuration Page ................................................................................ |
9-10 |
|
Table Features ................................................................................................. |
9-12 |
|
Adjacencies ............................................................................................................ |
9-16 |
|
WebView Help .............................................................................................................. |
9-17 |
|
General WebView Help ......................................................................................... |
9-17 |
|
Specific-page Help ................................................................................................. |
9-17 |
Chapter 10 |
Using SNMP ............................................................................................................... |
10-1 |
|
In This Chapter .............................................................................................................. |
10-1 |
|
SNMP Specifications .................................................................................................... |
10-2 |
|
SNMP Defaults ............................................................................................................. |
10-2 |
|
Quick Steps for Setting Up An SNMP Management Station ....................................... |
10-3 |
|
Quick Steps for Setting Up Trap Filters ........................................................................ |
10-4 |
|
Filtering by Trap Families ...................................................................................... |
10-4 |
|
Filtering by Individual Traps .................................................................................. |
10-5 |
|
SNMP Overview ........................................................................................................... |
10-6 |
|
SNMP Operations .................................................................................................. |
10-6 |
|
Using SNMP for Switch Management ................................................................... |
10-7 |
|
Setting Up an SNMP Management Station ..................................................... |
10-7 |
|
SNMP Versions ...................................................................................................... |
10-7 |
|
SNMPv1 .......................................................................................................... |
10-7 |
|
SNMPv2 .......................................................................................................... |
10-8 |
|
SNMPv3 .......................................................................................................... |
10-8 |
|
SNMP Traps Table ................................................................................................. |
10-9 |
|
Using SNMP For Switch Security .............................................................................. |
10-26 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |
ix |

|
|
|
Contents |
|
|
|
|
|
|
|
|
|
Community Strings (SNMPv1 and SNMPv2) ..................................................... |
10-26 |
|
|
|
Configuring Community Strings ................................................................... |
10-26 |
|
Encryption and Authentication (SNMPv3) .......................................................... |
10-27 |
|
|
|
Configuring Encryption and Authentication ................................................. |
10-27 |
|
|
Setting SNMP Security ................................................................................. |
10-28 |
|
Working with SNMP Traps ........................................................................................ |
10-29 |
|
|
Trap Filtering ........................................................................................................ |
10-29 |
|
|
|
Filtering by Trap Families ............................................................................. |
10-29 |
|
|
Filtering By Individual Trap .......................................................................... |
10-29 |
|
Authentication Trap .............................................................................................. |
10-30 |
|
|
Trap Management ................................................................................................ |
10-30 |
|
|
|
Replaying Traps ............................................................................................. |
10-30 |
|
|
Absorbing Traps ............................................................................................ |
10-30 |
|
|
Sending Traps to WebView ........................................................................... |
10-30 |
|
SNMP MIB Information ............................................................................................. |
10-31 |
|
|
MIB Tables ........................................................................................................... |
10-31 |
|
|
|
MIB Table Description .................................................................................. |
10-31 |
|
Industry Standard MIBs ....................................................................................... |
10-32 |
|
|
Enterprise (Proprietary) MIBs .............................................................................. |
10-36 |
|
|
Verifying the SNMP Configuration ............................................................................ |
10-39 |
|
Appendix A |
Software License and Copyright Statements .................................................... |
A-1 |
|
|
Alcatel License Agreement ............................................................................................ |
A-1 |
|
|
ALCATEL INTERNETWORKING, INC. (“AII”) |
|
|
|
SOFTWARE LICENSE AGREEMENT ............................................................... |
A-1 |
|
|
Third Party Licenses and Notices .................................................................................. |
A-4 |
|
|
A. Booting and Debugging Non-Proprietary Software .......................................... |
A-4 |
|
|
B. The OpenLDAP Public License: Version 2.4, 8 December 2000 ..................... |
A-4 |
|
|
C. Linux .................................................................................................................. |
A-5 |
|
|
D. GNU GENERAL PUBLIC LICENSE: Version 2, June 1991 .......................... |
A-5 |
|
|
E. University of California ................................................................................... |
A-10 |
|
|
F. Carnegie-Mellon University ............................................................................ |
A-10 |
|
|
G. Random.c ......................................................................................................... |
A-10 |
|
|
H. Apptitude, Inc. ................................................................................................. |
A-11 |
|
|
I. |
Agranat ............................................................................................................. |
A-11 |
|
J. |
RSA Security Inc. ............................................................................................ |
A-11 |
|
K. Sun Microsystems, Inc. .................................................................................... |
A-11 |
|
|
L. Wind River Systems, Inc. ................................................................................ |
A-12 |
|
|
M. Network Time Protocol Version 4 ................................................................... |
A-12 |
|
|
Index |
...................................................................................................................... |
Index-1 |
xOmniSwitch 6600 Family Switch Management Guide March 2005

About This Guide
This OmniSwitch 6600 Family Switch Management Guide describes basic attributes of your switch and basic switch administration tasks. The software features described in this manual are shipped standard with your OmniSwitch 6600 Family switch. These features are used when readying a switch for integration into a live network environment.
Supported Platforms
This information in this guide applies to the following products:
•OmniSwitch 6624
•OmniSwitch 6648
•OmniSwitch 6600-U24
•OmniSwitch 6600-P24
•OmniSwitch 6602-24
•OmniSwitch 6602-48
OmniSwitch 6600 Family switches are next generation enterprise edge/workgroup switches. The OmniSwitch 6624 and 6602-24 offer 24 copper 10/100 ports, the 6600-P24 offers 24 copper 10/100 Power over Ethernet (PoE) ports, the 6648 and 6602-48 offer 48 copper 10/100 ports, and the 6600-U24 offers 24 fiber 100 ports.
In addition, OmniSwitch 6624/6600-U24/6648 switches have one expansion port that can be used for a Gigabit Ethernet uplink module and another expansion port that can be used for a Gigabit Ethernet uplink or a stacking module while the 6602-24/6602-48 switches offer fixed Gigabit Ethernet uplinks and fixed stacking ports. The stacking ports on all OmniSwitch 6600 Family switches allow two to eight OmniSwitch 6600 Family switches to be configured as one virtual chassis known as a stack.
Note. All references to OmniSwitch 6624 and 6648 switches also apply to the OmniSwitch 6600-U24, 6600-P24, 6602-24, and 6602-48 unless specified otherwise.
Unsupported Platforms
The information in this guide does not apply to the following products:
•OmniSwitch 6800, 7700, 7800, or 8800
•OmniSwitch (original version with no numeric model name)
•Omni Switch/Router
•OmniStack
•OmniAccess
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page xi |

Who Should Read this Manual? |
About This Guide |
|
|
|
|
Who Should Read this Manual?
The audience for this user guide is network administrators and IT support personnel who need to configure, maintain, and monitor switches and routers in a live network. However, anyone wishing to gain knowledge on how fundamental software features are implemented in the OmniSwitch 6600 Family will benefit from the material in this configuration guide.
When Should I Read this Manual?
Read this guide as soon as your switch is up and running and you are ready to familiarize yourself with basic software functions. You should have already stepped through the first login procedures and read the brief software overviews in the OmniSwitch 6600 Family Getting Started Guide.
You should have already set up a switch password and be familiar with the very basics of the switch software. This manual will help you understand the switch’s directory structure, the Command Line Interface (CLI), configuration files, basic security features, and basic administrative functions. The features and procedures in this guide will help form a foundation that will allow you to configure more advanced switching features later.
What is in this Manual?
This configuration guide includes information about the following features:
•Basic switch administrative features, such as file editing utilities, procedures for loading new software, and setting up system information (name of switch, date, time).
•Configurations files, including snapshots, off-line configuration, time-activated file download.
•The CLI, including on-line configuration, command-building help, syntax error checking, and line editing.
•Basic security features, such as switch access control and customized user accounts.
•SNMP
•Web-based management (WebView)
What is Not in this Manual?
The configuration procedures in this manual primarily use Command Line Interface (CLI) commands in examples. CLI commands are text-based commands used to manage the switch through serial (console port) connections or via Telnet sessions. This guide does include introductory chapters for alternative methods of managing the switch, such as web-based (WebView) and SNMP management. However the primary focus of this guide is managing the switch through the CLI.
Further information on WebView can be found in the context-sensitive on-line help available with that application.
This guide does not include documentation for the OmniVista network management system. However, OmniVista includes a complete context-sensitive on-line help system.
page xii |
OmniSwitch 6600 Family Switch Management Guide March 2005 |

About This Guide |
How is the Information Organized? |
|
|
|
|
This guide provides overview material on software features, how-to procedures, and tutorials that will enable you to begin configuring your OmniSwitch. However, it is not intended as a comprehensive reference to all CLI commands available in the OmniSwitch. For such a reference to all OmniSwitch 6600 Family CLI commands, consult the OmniSwitch CLI Reference Guide.
How is the Information Organized?
Each chapter in this guide includes sections that will satisfy the information requirements of casual readers, rushed readers, serious detail-oriented readers, advanced users, and beginning users.
Quick Information. Most chapters include a specifications table that lists RFCs and IEEE specifications supported by the software feature. In addition, this table includes other pertinent information such as minimum and maximum values and sub-feature support. Some chapters include a defaults table that lists the default values for important parameters along with the CLI command used to configure the parameter. Many chapters include Quick Steps sections, which are procedures covering the basic steps required to get a software feature up and running.
In-Depth Information. All chapters include overview sections on software features as well as on selected topics of that software feature. Topical sections may often lead into procedure sections that describe how to configure the feature just described. Many chapters include tutorials or application examples that help convey how CLI commands can be used together to set up a particular feature.
Documentation Roadmap
The OmniSwitch user documentation suite was designed to supply you with information at several critical junctures of the configuration process. The following section outlines a roadmap of the manuals that will help you at each stage of the configuration process. Under each stage, we point you to the manual or manuals that will be most helpful to you.
Stage 1: Using the Switch for the First Time
Pertinent Documentation: OmniSwitch 6600 Family Getting Started Guide
Release Notes
A hard-copy OmniSwitch 6600 Family Getting Started Guide is included with your switch; this guide provides all the information you need to get your switch up and running the first time. This guide provides information on unpacking the switch, rack mounting the switch, installing uplink and stacking modules, unlocking access control, setting the switch’s IP address, setting up a password, and setting up stacks. It also includes succinct overview information on fundamental aspects of the switch, such as hardware LEDs, the software directory structure, stacking, CLI conventions, and web-based management.
At this time you should also familiarize yourself with the Release Notes that accompanied your switch. This document includes important information on feature limitations that are not included in other user guides.
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page xiii |

Documentation Roadmap |
About This Guide |
|
|
|
|
Stage 2: Gaining Familiarity with Basic Switch Functions
Pertinent Documentation: OmniSwitch 6600 Family Hardware Users Guide
OmniSwitch 6600 Family Switch Management Guide
Once you have your switch up and running, you will want to begin investigating basic aspects of its hard ware and software. Information about OmniSwitch 6600 Family hardware is provided in the OmniSwitch 6600 Family Hardware Users Guide. This guide provides specifications, illustrations, and descriptions of all hardware components—chassis, power supplies, uplink and stacking modules, and cooling fans. They also include steps for common procedures, such as removing and installing switch components.
The OmniSwitch 6600 Family Switch Management Guide is the primary user guide for the basic software features on a single switch. This guide contains information on the switch directory structure, basic file and directory utilities, switch access security, SNMP, and web-based management. It is recommended that you read this guide before connecting your switch to the network.
Note. The OmniSwitch 6600 Family Switch Management Guide was originally known as the “OmniSwitch 6624/6648 Switch Management Guide.”
Stage 3: Integrating the Switch Into a Network
Pertinent Documentation: OmniSwitch 6600 Family Network Configuration Guide OmniSwitch 6600 Family Advanced Routing Configuration Guide
When you are ready to connect your switch to the network, you will need to learn how the OmniSwitch implements fundamental software features, such as 802.1Q, VLANs, Spanning Tree, and network routing protocols. The OmniSwitch 6600 Family Network Configuration Guide contains overview information, procedures and examples on how standard networking technologies are configured in the OmniSwitch 6600 Family.
Note. The OmniSwitch 6600 Family Network Configuration Guide was originally known as the “OmniSwitch 6624/6648 Network Configuration Guide.”
The OmniSwitch 6600 Family Advanced Routing Configuration Guide includes configuration information for networks using Open Shortest Path First (OSPF).
Note. The OmniSwitch 6600 Family Advanced Routing Configuration Guide was originally known as the “OmniSwitch 66/24/6648 Advanced Routing Configuration Guide”
Anytime
The OmniSwitch CLI Reference Guide contains comprehensive information on all CLI commands supported by the switch. This guide includes syntax, default, usage, example, related CLI command, and CLI-to-MIB variable mapping information for all CLI commands supported by the switch. This guide can be consulted anytime during the configuration process to find detailed and specific information on each CLI command.
page xiv |
OmniSwitch 6600 Family Switch Management Guide March 2005 |

About This Guide |
Related Documentation |
|
|
|
|
Related Documentation
The following are the titles and descriptions of all the OmniSwitch 6600 Family user manuals:
•OmniSwitch 6600 Family Getting Started Guide
Describes the hardware and software procedures for getting an OmniSwitch 6600 Family switch up and running. Also provides information on fundamental aspects of OmniSwitch software and stacking architecture.
•OmniSwitch 6600 Family Hardware Users Guide
Complete technical specifications and procedures for all OmniSwitch 6600 Family chassis, power supplies, fans, and uplink and stacking modules.
•OmniSwitch CLI Reference Guide
Complete reference to all CLI commands supported on the OmniSwitch 6600, 6800, 7700, 7800, and 8800. Includes syntax definitions, default values, examples, usage guidelines, and CLI-to-MIB variable mappings.
•OmniSwitch 6600 Family Switch Management Guide
Includes procedures for readying an individual switch for integration into a network. Topics include the software directory architecture, image rollback protections, authenticated switch access, managing switch files, system configuration, using SNMP, and using web management software (WebView).
•OmniSwitch 6600 Family Network Configuration Guide
Includes network configuration procedures and descriptive information on all the major software features and protocols included in the base software package. Chapters cover Layer 2 information (Ethernet and VLAN configuration), Layer 3 information, security options (authenticated VLANs), Quality of Service (QoS), and link aggregation.
•OmniSwitch 6600 Family Advanced Routing Configuration Guide
Includes network configuration procedures and descriptive information on all the software features and protocols included in the advanced routing software package OSPF.
•Technical Tips, Field Notices
Includes information published by Alcatel’s Customer Support group.
•Release Note
Includes critical Open Problem Reports, feature exceptions, and other important information on the features supported in the current release and any limitations to their support.
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page xv |
User Manual CD |
About This Guide |
|
|
|
|
User Manual CD
All user guides for the OmniSwitch 6600 Family are included on the User Manual CD that accompanied your switch. This CD also includes user guides for other Alcatel data enterprise products. In addition, it contains a stand-alone version of the on-line help system that is embedded in the OmniVista network management application.
Besides the OmniVista documentation, all documentation on the User Manual CD is in PDF format and requires the Adobe Acrobat Reader program for viewing. Acrobat Reader freeware is available at www.adobe.com.
Note. In order to take advantage of the documentation CD’s global search feature, it is recommended that you select the option for searching PDF files before downloading Acrobat Reader freeware.
To verify that you are using Acrobat Reader with the global search option, look for the following button in the toolbar:
Note. When printing pages from the documentation PDFs, de-select Fit to Page if it is selected in your print dialog. Otherwise pages may print with slightly smaller margins.
Technical Support
An Alcatel service agreement brings your company the assurance of 7x24 no-excuses technical support. You’ll also receive regular software updates to maintain and maximize your Alcatel product’s features and functionality and on-site hardware replacement through our global network of highly qualified service delivery partners. Additionally, with 24-hour-a-day access to Alcatel’s Service and Support web page, you’ll be able to view and update any case (open or closed) that you have reported to Alcatel’s technical support, open a new case or access helpful release notes, technical bulletins, and manuals. For more information on Alcatel’s Service Programs, see our web page at eservice.ind.alcatel.com, call us at 1-800-995- 2696, or email us at support@ind.alcatel.com.
page xvi |
OmniSwitch 6600 Family Switch Management Guide March 2005 |

1 Logging Into the Switch
Logging into the switch may be done locally or remotely. Management tools include: the Command Line Interface (CLI), which may be accessed locally via the console port, or remotely via Telnet; WebView, which requires an HTTP client (browser) on a remote workstation; and SNMP, which requires an SNMP manager (such as Alcatel’s OmniVista or HP OpenView) on the remote workstation. Secure sessions are available using the Secure Shell interface. File transfers can be done via FTP or Secure Shell FTP.
In This Chapter
This chapter describes the basics of logging into the switch to manage the switch through the CLI. It includes information about using Telnet, FTP, and Secure Shell for logging into the switch as well as information about using the switch to start a Telnet or Secure Shell session on another device. It also includes information about managing sessions and specifying a DNS resolver. For more details about the syntax of referenced commands, see the OmniSwitch CLI Reference Guide.
Configuration procedures described in this chapter include:
•“Quick Steps for Logging Into the Switch” on page 1-3
•“Using Telnet” on page 1-6
•“Using FTP” on page 1-7
•“Using Secure Shell” on page 1-8
•“Modifying the Login Banner” on page 1-15
•“Configuring Login Parameters” on page 1-17
•“Enabling the DNS Resolver” on page 1-18
Management access is disabled (except through the console port) unless specifically enabled by a network administrator. For more information about management access and methods, use the table here as a guide:
For more information about... |
See... |
|
|
Enabling or “unlocking” management interfaces |
Getting Started Guide or |
on the switch |
Chapter 8, “Managing Switch Security” |
|
|
Authenticating users to manage the switch |
Chapter 8, “Managing Switch Security” |
|
|
Creating user accounts directly on the switch |
Chapter 7, “Managing Switch User Accounts” |
|
|
Using the CLI |
Chapter 5, “Using the CLI” |
|
|
Using WebView to manage the switch |
Chapter 9, “Using WebView” |
|
|
Using SNMP to manage the switch |
Chapter 10, “Using SNMP” |
|
|
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page 1-1 |

Login Specifications Logging Into the Switch
Login Specifications
Telnet clients supported |
Any standard Telnet client. |
|
|
FTP clients supported |
Any standard FTP client. |
|
|
HTTP (WebView) clients supported |
– Internet Explorer for Windows NT, Windows |
|
XP, and Windows 2000, version 5.5 |
|
– Netscape for Windows NT, Windows XP, and |
|
Windows 2000, version 4.7 |
|
– Netscape for Sun OS 2.8, version 4.7 |
|
– Netscape for HP-UX 11.0, version 4.7. |
|
|
Secure Shell clients supported |
Any standard Secure Shell client (Secure Shell |
|
Version 2). |
|
|
SNMP clients supported |
Any standard SNMP manager (such as HP Open- |
|
View). |
|
|
Login Defaults
Access to managing the switch is always available for the admin user through the console port, even if management access to the console port is disabled
Parameter Description |
Command |
Default |
|
|
|
Session login attempts allowed |
session login-attempt |
3 attempts |
before the TCP connection is |
|
|
closed. |
|
|
|
|
|
Timeout period allowed for |
session login-timeout |
55 seconds |
session login before the TCP |
|
|
connection is closed. |
|
|
|
|
|
Inactivity timeout period. The |
session timeout |
4 minutes |
length of time the switch can |
|
|
remain idle during a login |
|
|
session before the switch will |
|
|
close the session. |
|
|
|
|
|
page 1-2 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |

Logging Into the Switch |
Quick Steps for Logging Into the Switch |
|
|
|
|
Quick Steps for Logging Into the Switch
The following procedure assumes that you have set up the switch as described in your OmniSwitch Getting Started Guide and Hardware Users Guide. Setup includes:
•Connecting to the switch via the console port.
•Setting up the Ethernet Management Port (EMP) through the switch’s boot prompt.
•Enabling (or “unlocking”) management interfaces types (Telnet, FTP, HTTP, SNMP, and Secure Shell) through the aaa authentication command for the interface you are using. Note that Telnet, FTP, and Secure Shell are used to log into the switch’s Command Line Interface (CLI). For detailed information about enabling session types, see Chapter 8, “Managing Switch Security.”
1If you are connected to the switch via the console port, your terminal will automatically display the switch login prompt. If you are connected remotely, you must enter the switch IP address in your Telnet, FTP, or Secure Shell client (typically the IP address of the EMP). The login prompt then displays.
2At the login prompt, enter the admin username. At the password prompt, enter the switch password. (Alternately, you may enter any valid username and password.) The switch’s default welcome banner will display, followed by the CLI prompt.
Welcome to the Alcatel OmniSwitch 6000
Software Version 5.1 Development, September 2, 2002.
Copyright(c), 1994-2002 Alcatel Internetworking Inc. All Rights reserved.
OmniSwitch(TM) is a trademark of Alcatel Internetworking, Inc. registered in the United States Patent and Trademark Office.
You are now logged into the CLI. For information about changing the welcome banner, see “Modifying the Login Banner” on page 1-15.
For information about changing the login prompt, see Chapter 5, “Using the CLI.”
For information about setting up additional user accounts locally on the switch, see Chapter 7, “Managing Switch User Accounts.”
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page 1-3 |
Overview of Switch Login Components |
Logging Into the Switch |
|
|
|
|
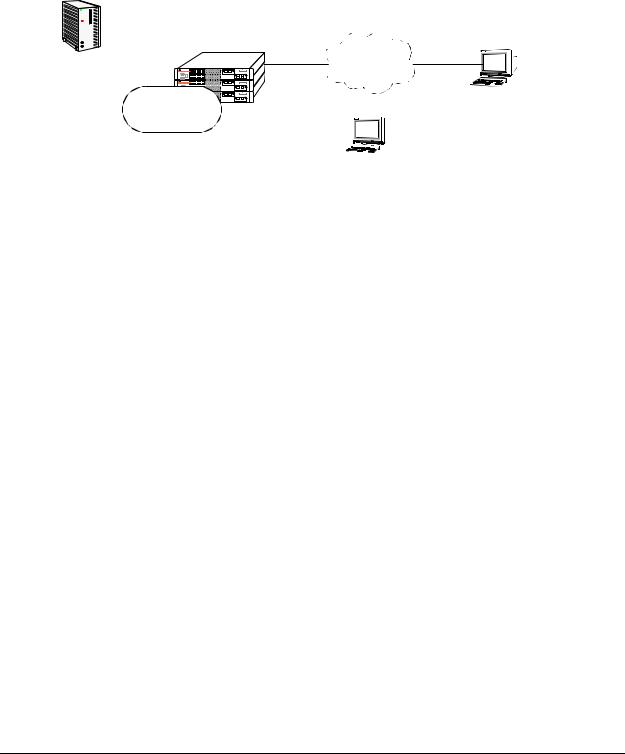
Overview of Switch Login Components
Switch access components include access methods (or interfaces) and user accounts stored on the local user database in the switch and/or on external authentication servers. Each access method, except the console port, must be enabled or “unlocked” on the switch before users can access the switch through that interface.
OmniSwitch
Authentication
Server
local user |
database |
remote user
Login via Secure Shell, Telnet, FTP, HTTP, or SNMP
local user
Login via the console port.
Switch Login Components
Management Interfaces
Logging into the switch may be done locally or remotely. Remote connections may be secure or insecure, depending on the method. Management interfaces are enabled using the aaa authentication command. This command also requires specifying the external servers and/or local user database that will be used to authenticate users. The process of authenticating users to manage the switch is called Authenticated Switch Access (ASA). Authenticated Switch Access is described in detail in Chapter 8, “Managing Switch Security.”
An overview of management methods is listed here:
Logging Into the CLI
•Console port—A direct connection to the switch through the console port. The console port is always enabled for the default user account. For more information about connecting to the console port, see your OmniSwitch Hardware Users Guide.
•Telnet—Any standard Telnet client may be used for remote login to the switch. This method is not secure. For more information about using Telnet to access the switch, see “Using Telnet” on page 1-6.
•FTP—Any standard FTP client may be used for remote login to the switch. This method is not secure. See “Using FTP” on page 1-7.
•Secure Shell—Any standard Secure Shell client may be used for remote login to the switch. See “Using Secure Shell” on page 1-8.
page 1-4 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |

Logging Into the Switch |
Overview of Switch Login Components |
|
|
|
|
Using the WebView Management Tool
•HTTP—The switch has a Web browser management interface for users logging in via HTTP. This management tool is called WebView. For more information about using WebView, see Chapter 9, “Using WebView.”
Using SNMP to Manage the Switch
•SNMP—Any standard SNMP browser may be used for logging into the switch. See Chapter 10, “Using SNMP.”
User Accounts
User accounts may be configured and stored directly on the switch, and user accounts may also be configured and stored on an external authentication server or servers.
The accounts include a username and password. In addition, they also specify the user’s privileges or enduser profile, depending on the type of user account. In either case, the user is given read-only or read-write access to particular commands.
• Local User Database
The user command creates accounts directly on the switch. See Chapter 7, “Managing Switch User Accounts,”for information about creating accounts on the switch.
• External Authentication Servers
The switch may be set up to communicate with external authentication servers that contain user information. The user information includes usernames and passwords; it may also include privilege information or reference an end-user profile name.
For information about setting up the switch to communicate with external authentication servers, see the
OmniSwitch 6600 Family Network Configuration Guide.
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page 1-5 |
Using Telnet |
Logging Into the Switch |
|
|
|
|
Using Telnet
Telnet may be used to log into the switch from a remote station. All of the standard Telnet commands are supported by software in the switch. When Telnet is used to log in, the switch is acting as a Telnet server.
A Telnet session may also be initiated from the switch itself during a login session. In this case, the switch is acting as a Telnet client.
Logging Into the Switch Via Telnet
Before you can log into the OmniSwitch using a Telnet interface, the telnet option of the aaa authentication command must be enabled. Once enabled, any standard Telnet client may be used to log into the switch. To log into the switch, open your Telnet application and enter the switch’s IP address (the IP address will typically be the same as the one configured for the EMP). The switch’s welcome banner and login prompt display.
Note. A Telnet connection is not secure. Secure Shell is recommended instead of Telnet or FTP as a secure method of accessing the switch.
Starting a Telnet Session from the Switch
At any time during a login session on the switch, you can initiate a Telnet session to another switch (or some other device) by using the telnet CLI command and the relevant IP address. The following shows an example of telnetting to another OmniSwitch with an IP address of 10.255.10.123.
-> telnet 10.255.10.123 Trying 10.255.10.123...
Connected to 10.255.10.123. Escape character is '^]'. login :
Here, you must enter a valid username and password. Once login is completed, the OmniSwitch welcome banner will display as follows:
login : admin password :
Welcome to the Alcatel OmniSwitch 6000 Software Version 5.1.2.125, December 13, 2002.
Copyright(c), 1994-2002 Alcatel Internetworking, Inc. All Rights reserved.
OmniSwitch(TM) is a trademark of Alcatel Internetworking, Inc. registered in the United States Patent and Trademark Office.
page 1-6 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |

Logging Into the Switch |
Using FTP |
|
|
|
|
Using FTP
The OmniSwitch can function as an FTP server. Any standard FTP client may be used.
Note. An FTP connection is not secure. Secure Shell is recommended instead of FTP or Telnet as a secure method of accessing the switch.
Using FTP to Log Into the Switch
You can access the OmniSwitch with a standard FTP application. To login to the switch, start your FTP client. Where the FTP client asks for “Name”, enter the IP address of your switch. Where the FTP client asks for “User ID”, enter the username of your login account on the switch. Where the FTP client asks for “Password”, enter your switch password.
Note. If you are using Authenticated Switch Access (ASA), the port interface must be authenticated for FTP use and the username profile must have permission to use FTP. Otherwise the switch will not accept an FTP login. For information about ASA, refer to Chapter 8, “Managing Switch Security.”
Note. You must use the binary mode (bin) to transfer image files via FTP.
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page 1-7 |

Using Secure Shell |
Logging Into the Switch |
|
|
|
|
Using Secure Shell
The OmniSwitch Secure Shell feature provides a secure mechanism that allows you to log in to a remote switch, to execute commands on a remote device, and to move files from one device to another. Secure Shell provides secure, encrypted communications even when your transmission is between two untrusted hosts or over an unsecure network. Secure Shell protects against a variety of security risks including the following:
•IP spoofing
•IP source routing
•DNS spoofing
•Interception of clear-text passwords and other data by intermediate hosts
•Manipulation of data by users on intermediate hosts
Note. The OmniSwitch supports Secure Shell Version 2 only.
Secure Shell Components
The OmniSwitch includes both client and server components of the Secure Shell interface and the Secure Shell FTP file transfer protocol. SFTP is a subsystem of the Secure Shell protocol. All Secure Shell FTP data are encrypted through a Secure Shell channel.
Since Secure Shell provides a secure session, the Secure Shell interface and SFTP are recommended instead of the Telnet program or the FTP protocol for communications over TCP/IP for sending file transfers. Both Telnet and FTP are available on the OmniSwitch but they do not support encrypted passwords.
Note. Secure Shell may only be used to log into the switch to manage the switch. It cannot be used for Layer 2 authentication through the switch.
Secure Shell Interface
The Secure Shell interface is invoked when you enter the ssh command. After the authentication process between the client and the server is complete, the remote Secure Shell interface runs in the same way as Telnet. Refer to “Starting a Secure Shell Session” on page 1-11 to for detailed information.
Secure Shell File Transfer Protocol
Secure Shell FTP is the standard file transfer protocol used with Secure Shell version 2. Secure Shell FTP is an interactive file transfer program (similar to the industry standard FTP) which performs all file transfer operations over a Secure Shell connection.
You invoke the Secure Shell FTP protocol by using the sftp command. Once the authentication phase is completed, the Secure Shell FTP subsystem runs. Secure Shell FTP connects and logs into the specified host, then enters an interactive command mode. Refer to “Starting a Secure Shell Session” on page 1-11 for detailed information.
page 1-8 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |
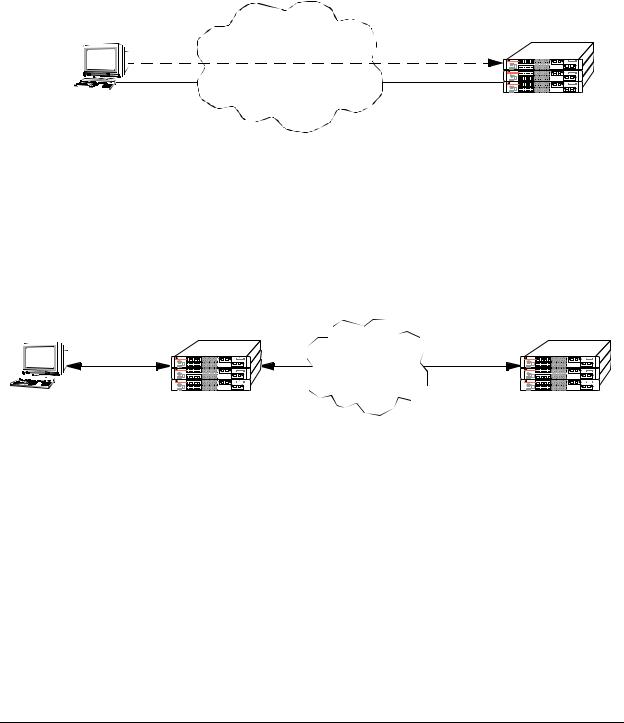
Logging Into the Switch |
Using Secure Shell |
|
|
|
|
Secure Shell Application Overview
Secure Shell is an access protocol used to establish secured access to your OmniSwitch. The Secure Shell protocol can be used to manage an OmniSwitch directly or it can provide a secure mechanism for managing network servers through the OmniSwitch.
The drawing below illustrates the Secure Shell being used as an access protocol replacing Telnet to manage the OmniSwitch. Here, the user terminal is connected through the network to the switch.
Secure Shell
Network
Terminal |
OmniSwitch |
Secure Shell Used as an Access Protocol
The drawing below shows a slightly different application. Here, a terminal connected to a single OmniSwitch acting as a Secure Shell client as an entry point into the network. In this scenario, the client portion of the Secure Shell software is used on the connecting OmniSwitch and the server portion of Secure Shell is used on the switches or servers being managed.
Secure Shell |
|
Access Protocol |
Secure Shell |
|
|
|
Network |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Terminal |
OmniSwitch Secure |
Secure Shell |
|
||||||||||||||||
|
Shell Client |
|
Server |
|
|||||||||||||||
|
|
|
|
||||||||||||||||
OmniSwitch as a Secure Shell Client
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page 1-9 |

Using Secure Shell |
Logging Into the Switch |
|
|
|
|
Secure Shell Authentication
Secure Shell authentication is accomplished in several phases using industry standard algorithms and exchange mechanisms. The authentication phase is identical for Secure Shell and Secure Shell SFTP. The following sections describe the process in detail.
Protocol Identification
When the Secure Shell client in the OmniSwitch connects to a Secure Shell server, the server accepts the connection and responds by sending back an identification string. The client will parse the server’s identification string and send an identification string of its own. The purpose of the identification strings is to validate that the attempted connection was made to the correct port number. The strings also declare the protocol and software version numbers. This information is needed on both the client and server sides for debugging purposes.
At this point, the protocol identification strings are in human-readable form. Later in the authentication process, the client and the server switch to a packet-based binary protocol, which is machine readable only.
Algorithm and Key Exchange
The OmniSwitch Secure Shell server is identified by one or several host-specific DSA keys. Both the client and server process the key exchange to choose a common algorithm for encryption, signature, and compression. This key exchange is included in the Secure Shell transport layer protocol. It uses a key agreement to produce a shared secret that cannot be determined by either the client or the server alone. The key exchange is combined with a signature and the host key to provide host authentication. Once the exchange is completed, the client and the server turn encryption on using the selected algorithm and key. The following elements are supported:
Host Key Type |
DSA |
|
|
Cipher Algorithms |
AES, Blowfish, Cast, 3DES, Arcfour, Rijndael |
|
|
Signature Algorithms |
MD5, SHA1 |
|
|
Compression Algorithms |
None Supported |
|
|
Key Exchange Algorithms |
diffie-hellman-group-exchange-sha1 |
|
diffie-hellman-group1-sha1 |
|
|
Note. The OmniSwitch generates a 512 bit DSA host key at initial startup. The DSA key on the switch is made up of two files contained in the /flash/network directory; the public key is called ssh_host_dsa_key.pub, and the private key is called ssh_host_dsa_key. To generate a different DSA key, use the Secure Shell tools available on your Unix or Windows system and copy the files to the /flash/ network directory on your switch. The new DSA key will take effect after the OmniSwitch is rebooted.
Authentication Phase
When the client tries to authenticate, the server determines the process used by telling the client which authentication methods can be used. The client has the freedom to attempt several methods listed by the server. The server will disconnect itself from the client if a certain number of failed authentications are attempted or if a timeout period expires. Authentication is performed independent of whether the Secure Shell interface or the SFTP file transfer protocol will be implemented.
page 1-10 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |

Logging Into the Switch |
Using Secure Shell |
|
|
|
|
Connection Phase
After successful authentication, both the client and the server process the Secure Shell connection protocol. The OmniSwitch supports one channel for each Secure Shell connection. This channel can be used for a Secure Shell session or a Secure Shell FTP session.
Starting a Secure Shell Session
To start a Secure Shell session from an OmniSwitch, issue the ssh command and identify the IP address for the device you are connecting to.
Note. You can only use a host name instead of an IP address if the DNS resolver has been configured and enabled. If not, you must specify an IP address. See Chapter 2, “Managing System Files,” for details.
Note. Use of the cmdtool OpenWindows support facility is not recommended over Secure Shell connections with an external server.
The following command establishes a Secure Shell interface from the local OmniSwitch to IP address 11.333.30.135.
-> ssh 11.333.30.135 login as:
You must have a login and password that is recognized by the IP address you specify. When you enter your login, the device you are logging in to will request your password as shown here.
-> ssh 11.333.10.135 login as: rrlogin1
rrlogin1's password for keyboard-interactive method:
Once the Secure Shell session is established, you can use the remote device specified by the IP address on a secure connection from your OmniSwitch.
Note. The login parameters for Secure Shell session login parameters can be affected by the session loginattempt and session login-timeout CLI commands.
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page 1-11 |
Using Secure Shell |
Logging Into the Switch |
|
|
|
|
The following drawing shows an OmniSwitch, using IP address 11.233.10.145, establishing a Secure Shell session across a network to another OmniSwitch, using IP address 11.333.30.135. To establish this session from the console in the figure below, you would use the CLI commands shown in the examples above.
Once you issue the correct password, you are logged into the OmniSwitch at IP address 11.333.30.135.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
OmniSwitch |
|
|
|
|
OmniSwitch |
|||||||
Console |
11.233.10.145 |
11.333.30.135 |
||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
Secure Shell Session between Two OmniSwitches
page 1-12 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |

Logging Into the Switch |
Using Secure Shell |
|
|
|
|
To view the parameters of the Secure Shell session, issue the who command. The following will display.
-> who
Session number = 0
User name = (at login),
Access type = console,
Access port = Local,
IP address |
= 0.0.0.0, |
|
Read-only domains |
= None, |
|
Read-only families |
= , |
|
Read-Write domains |
= None, |
|
Read-Write families |
= , |
|
End-User profile |
= |
|
Session number = 1 |
|
|
User name |
= rrlogin1, |
|
Access type = ssh, |
|
|
Access port = NI, |
|
|
IP address |
= 11.233.10.145, |
|
Read-only domains |
= None, |
|
Read-only families |
= , |
|
Read-Write domains |
= All , |
|
Read-Write families |
= , |
|
End-User profile |
= |
|
This display shows two sessions currently running on the remote OmniSwitch at IP address 11.333.30.135. Session number 0 is identified as the console session. Session number 1 indicates the User name is rrlogin1, the IP address is 11.233.10.145, and the Access type is “ssh” which indicates a Secure Shell session.
Closing a Secure Shell Session
To terminate the Secure Shell session, issue the exit command. The following will display:
-> exit
Connection to 11.333.30.135 closed.
Using the example shown above, this display indicates the Secure Shell session between the two switches is closed. At this point, the user is logged into the local OmniSwitch at IP address 11.233.10.145.
Log Into the Switch with Secure Shell FTP
To open a Secure Shell FTP session from a local OmniSwitch to a remote device, proceed as follows:
1 Log on to the OmniSwitch and issue the sftp CLI command. The command syntax requires you to identify the IP address for the device to which you are connecting. The following command establishes a Secure Shell FTP interface from the local OmniSwitch to IP address 10.222.30.125.
-> sftp 10.222.30.125 login as:
2 You must have a login and password that is recognized by the IP address you specify. When you enter your login, the device you are logging in to will request your password as shown here.
-> sftp 10.222.30.125 login as: rrlogin2
rrlogin2's password for keyboard-interactive method:
OmniSwitch 6600 Family Switch Management Guide March 2005 |
page 1-13 |

Using Secure Shell |
Logging Into the Switch |
|
|
|
|
3 After logging in, you will receive the sftp> prompt. You may enter a question mark (?) to view available Secure Shell FTP commands and their definitions as shown here.
sftp>?
Available commands: |
|
cd path |
Change remote directory to 'path' |
lcd path |
Change local directory to 'path' |
chmod mode path |
Change permissions of file 'path' to 'mode' |
help |
Display this help text |
get remote-path [local-path] |
Download file |
lls [path]] |
Display local directory listing |
ln oldpath newpath |
Symlink remote file |
lmkdir path |
Create local directory |
lpwd |
Print local working directory |
ls [path] |
Display remote directory listing |
mkdir path |
Create remote directory |
put local-path [remote-path] |
Upload file |
pwd |
Display remote working directory |
exit |
Quit sftp |
quit |
Quit sftp |
rename oldpath newpath |
Rename remote file |
rmdir path |
Remove remote directory |
rm path |
Delete remote file |
symlink oldpath newpath |
Symlink remote file |
version |
Show SFTP version |
? |
Synonym for help |
Note. Although Secure Shell FTP has commands similar to the industry standard FTP, the underlying protocol is different. See Chapter 2, “Managing System Files,” for a Secure Shell FTP application example.
Closing a Secure Shell FTP Session
To terminate the Secure Shell FTP session, issue the exit command. The following will display:
-> exit
Connection to 11.333.30.135 closed.
This display indicates the Secure Shell FTP session with IP address 11.333.20.135 is closed. The user is now logged into the OmniSwitch as a local device with no active remote connection.
page 1-14 |
OmniSwitch 6600 Family Switch Management Guide March 2005 |
 Loading...
Loading...