
See the tables describing the fields in the Access Point and Bridge operating modes for
descriptions of the fields in this screen.
6.5 Technical Reference
This section provides technical background information about the topics covered in this
chapter. Refer to Appendix E on page 153 for further readings on Wireless LAN.
6.5.1 WMM QoS
WMM (Wi-Fi MultiMedia) QoS (Quality of Service) ensures quality of service in wireless
networks. It controls WLAN transmission priority on packets to be transmitted over the
wireless network.
WMM QoS prioritizes wireless traffic according to the delivery requirements of the individual
and applications. WMM QoS is a part of the IEEE 802.11e QoS enhancement to certified WiFi wireless networks.
On APs without WMM QoS, all traffic streams are given the same access priority to the
wireless network. If the introduction of another traffic stream creates a data transmission
demand that exceeds the current network capacity, then the new traffic stream reduces the
throughput of the other traffic streams.
Chapter 6 Wireless Settings Screen
The ZyXEL Device uses WMM QoS to prioritize traffic streams according to the IEEE 802.1q
or DSCP information in each packet’s header. The ZyXEL Device automatically determines
the priority to use for an individual traffic stream. This prevents reductions in data
transmission for applications that are sensitive to latency and jitter (variations in delay).
6.5.2 Spanning Tree Protocol (STP)
STP detects and breaks network loops and provides backup links between switches, bridges or
routers. It allows a bridge to interact with other STP-compliant bridges in your network to
ensure that only one route exists between any two stations on the network.
6.5.2.1 Rapid STP
The ZyXEL Device uses IEEE 802.1w RSTP (Rapid Spanning Tree Protocol) that allow faster
convergence of the spanning tree (while also being backwards compatible with STP-only
aware bridges). Using RSTP topology change information does not have to propagate to the
root bridge and unwanted learned addresses are flushed from the filtering database. In RSTP,
the port states are Discarding, Learning, and Forwarding.
6.5.2.2 STP Terminology
The root bridge is the base of the spanning tree; it is the bridge with the lowest identifier value
(MAC address).
ZyXEL NWA-1100 User’s Guide
71
Chapter 6 Wireless Settings Screen
Path cost is the cost of transmitting a frame onto a LAN through that port. It is assigned
according to the speed of the link to which a port is attached. The slower the media, the higher
the cost - see the following table.
Table 12 STP Path Costs
LINK SPEED
Path Cost 4Mbps 250 100 to 1000 1 to 65535
Path Cost 10Mbps 100 50 to 600 1 to 65535
Path Cost 16Mbps 62 40 to 400 1 to 65535
Path Cost 100Mbps 19 10 to 60 1 to 65535
Path Cost 1Gbps 4 3 to 10 1 to 65535
Path Cost 10Gbps 2 1 to 5 1 to 65535
On each bridge, the root port is the port through which this bridge communicates with the root.
It is the port on this switch with the lowest path cost to the root (the root path cost). If there is
no root port, then this bridge has been accepted as the root bridge of the spanning tree network.
For each LAN segment, a designated bridge is selected. This bridge has the lowest cost to the
root among the bridges connected to the LAN.
RECOMMENDED
VALUE
RECOMMENDED
RANGE
ALLOWED
RANGE
6.5.2.3 How STP Works
After a bridge determines the lowest cost-spanning tree with STP, it enables the root port and
the ports that are the designated ports for connected LANs, and disables all other ports that
participate in STP. Network packets are therefore only forwarded between enabled ports,
eliminating any possible network loops.
STP-aware bridges exchange Bridge Protocol Data Units (BPDUs) periodically. When the
bridged LAN topology changes, a new spanning tree is constructed.
Once a stable network topology has been established, all bridges listen for Hello BPDUs
(Bridge Protocol Data Units) transmitted from the root bridge. If a bridge does not get a Hello
BPDU after a predefined interval (Max Age), the bridge assumes that the link to the root
bridge is down. This bridge then initiates negotiations with other bridges to reconfigure the
network to re-establish a valid network topology.
6.5.2.4 STP Port States
STP assigns five port states (see next table) to eliminate packet looping. A bridge port is not
allowed to go directly from blocking state to forwarding state so as to eliminate transient
loops.
Table 13 STP Port States
PORT STATES DESCRIPTIONS
Disabled STP is disabled (default).
Blocking Only configuration and management BPDUs are received and processed.
Listening All BPDUs are received and processed.
Learning All BPDUs are received and processed. Information frames are submitted to the
Forwarding All BPDUs are received and processed. All information frames are received and
learning process but not forwarded.
forwarded.
72
ZyXEL NWA-1100 User’s Guide
6.5.3 Additional Wireless Terms
Table 14 Additional Wireless Terms
TERM DESCRIPTION
Intra-BSS Traffic This describes direct communication (not through the ZyXEL Device)
between two wireless devices within a wireless network. You might disable
this kind of communication to enhance security within your wireless network.
RTS/CTS Threshold In a wireless network which covers a large area, wireless devices are
Preamble A preamble affects the timing in your wireless network. There are two
Fragmentation
Threshold
Roaming If you have two or more ZyXEL Devices (or other wireless access points) on
Antenna An antenna couples Radio Frequency (RF) signals onto air. A transmitter
sometimes not aware of each other’s presence. This may cause them to
send information to the AP at the same time and result in information colliding
and not getting through.
By setting this value lower than the default value, the wireless devices must
sometimes get permission to send information to the ZyXEL Device. The
lower the value, the more often the devices must get permission.
If this value is greater than the fragmentation threshold value (see below),
then wireless devices never have to get permission to send information to the
ZyXEL Device.
preamble modes: long and short. If a device uses a different preamble mode
than the ZyXEL Device does, it cannot communicate with the ZyXEL Device.
A small fragmentation threshold is recommended for busy networks, while a
larger threshold provides faster performance if the network is not very busy.
your wireless network, you can enable this option so that wireless devices
can change locations without having to log in again. This is useful for devices,
such as notebooks, that move around a lot.
within a wireless device sends an RF signal to the antenna, which propagates
the signal through the air. The antenna also operates in reverse by capturing
RF signals from the air.
Positioning the antennas properly increases the range and coverage area of
a wireless LAN.
Chapter 6 Wireless Settings Screen
ZyXEL NWA-1100 User’s Guide
73

Chapter 6 Wireless Settings Screen
74
ZyXEL NWA-1100 User’s Guide
CHAPTER 7
Wireless Security Screen
7.1 Overview
This chapter describes how to use the Wireless Security screen. This screen allows you to
configure the security mode for your ZyXEL Device.
Wireless security is vital to your network. It protects communications between wireless
stations, access points and the wired network.
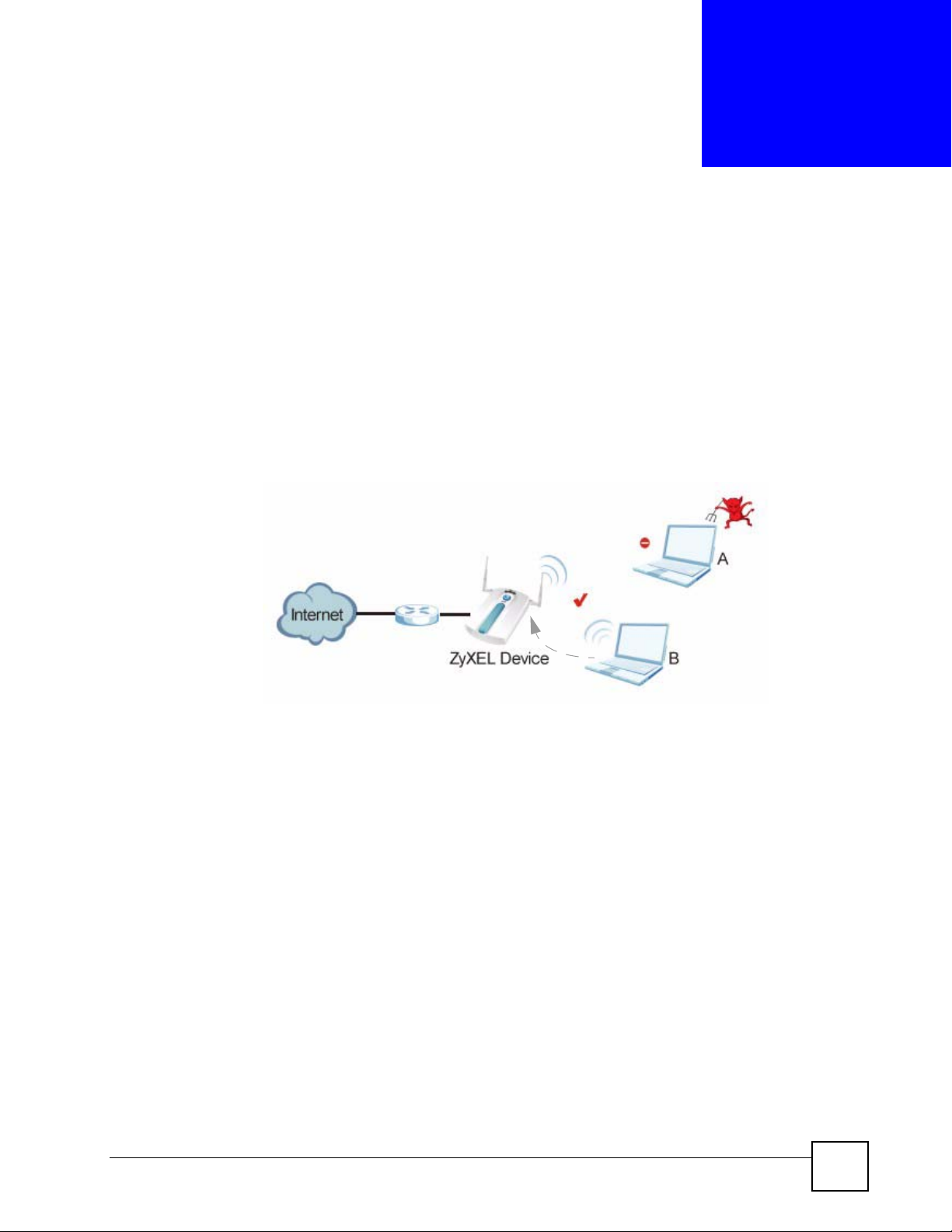
Figure 31 Securing the Wireless Network
In the figure above, the ZyXEL Device checks the identity of devices before giving them
access to the network. In this scenario, Computer A is denied access to the network, while
Computer B is granted connectivity.
The ZyXEL Device secure communications via data encryption, wireless client authentication
and MAC address filtering. It can also hide its identity in the network.
7.2 What You Can Do in the Wireless Security Screen
Use the Wireless > Security screen (see Section 7.4 on page 77) to choose the security mode
for your ZyXEL Device.
ZyXEL NWA-1100 User’s Guide
75

Chapter 7 Wireless Security Screen
7.3 What You Need To Know About Wireless Security
User Authentication
Authentication is the process of verifying whether a wireless device is allowed to use the
wireless network. You can make every user log in to the wireless network before they can use
it. However, every device in the wireless network has to support IEEE 802.1x to do this.
For wireless networks, you can store the user names and passwords for each user in a RADIUS
server. This is a server used in businesses more than in homes. If you do not have a RADIUS
server, you cannot set up user names and passwords for your users.
Unauthorized wireless devices can still see the information that is sent in the wireless network,
even if they cannot use the wireless network. Furthermore, there are ways for unauthorized
wireless users to get a valid user name and password. Then, they can use that user name and
password to use the wireless network.
The following table shows the relative effectiveness of wireless security methods:.
Table 15 Wireless Security Levels
SECURITY
LEVEL
Least
S e c u r e
Most Secure
SECURITY TYPE
Unique SSID (Default)
Unique SSID with Hide SSID Enabled
MAC Address Filtering
WEP Encryption
IEEE802.1x EAP with RADIUS Server Authentication
Wi-Fi Protected Access (WPA)
WPA2
The available security modes in your ZyXEL Device are as follows:
• None. No data encryption.
• WEP. Wired Equivalent Privacy (WEP) encryption scrambles the data transmitted
between the wireless stations and the access points to keep network communications
private.
• 802.1x-Only. This is a standard that extends the features of IEEE 802.11 to support
extended authentication. It provides additional accounting and control features. This
option does not support data encryption.
• 802.1x-Static64. This provides 802.1x-Only authentication with a static 64bit WEP
key and an authentication server.
• 802.1x-Static128. This provides 802.1x-Only authentication with a static 128bit WEP
key and an authentication server.
• WPA. Wi-Fi Protected Access (WPA) is a subset of the IEEE 802.11i standard.
• WPA2. WPA2 (IEEE 802.11i) is a wireless security standard that defines stronger
encryption, authentication and key management than WPA.
• WPA2-MIX. This commands the ZyXEL Device to use either WPA2 or WPA
depending on which security mode the wireless client uses.
• WPA2-PSK. This adds a pre-shared key on top of WPA2 standard.
76
ZyXEL NWA-1100 User’s Guide

Chapter 7 Wireless Security Screen
• WPA2-PSK-MIX. This commands the ZyXEL Device to use either WPA-PSK or
WPA2-PSK depending on which security mode the wireless client uses.
" In Bridge and Bridge + AP operating modes, the only available security modes
are WEP and WPA2-PSK.
Passphrase
A passphrase functions like a password. In WEP security mode, it is further converted by the
ZyXEL Device into a complicated string that is referred to as the “key”. This key is requested
from all devices wishing to connect to a wireless network.
PSK
The Pre-Shared Key (PSK) is a password shared by a wireless access point and a client during
a previous secure connection. The key can then be used to establish a connection between the
two parties.
Encryption
Wireless networks can use encryption to protect the information that is sent in the wireless
network. Encryption is like a secret code. If you do not know the secret code, you cannot
understand the message. Encryption is the process of converting data into unreadable text.
This secures information in network communications. The intended recipient of the data can
“unlock” it with a pre-assigned key, making the information readable only to him. The ZyXEL
Device when used as a wireless client employs Temporal Key Integrity Protocol (TKIP) data
encryption.
EAP
Extensible Authentication Protocol (EAP) is a protocol used by a wireless client, an access
point and an authentication server to negotiate a connection.
The EAP methods employed by the ZyXEL Device when in Wireless Client operating mode
are Transport Layer Security (TLS), Protected Extensible Authentication Protocol (PEAP),
Lightweight Extensible Authentication Protocol (LEAP) and Tunneled Transport Layer
Security (TTLS). The authentication protocol may either be Microsoft Challenge Handshake
Authentication Protocol Version 2 (MSCHAPv2) or Generic Token Card (GTC).
Further information on these terms can be found in Appendix E on page 153.
7.4 The Security Screen
Use this screen to choose the security mode for your ZyXEL Device.
Click Wireless > Security. The screen varies depending upon the security mode you select.
ZyXEL NWA-1100 User’s Guide
77
Chapter 7 Wireless Security Screen
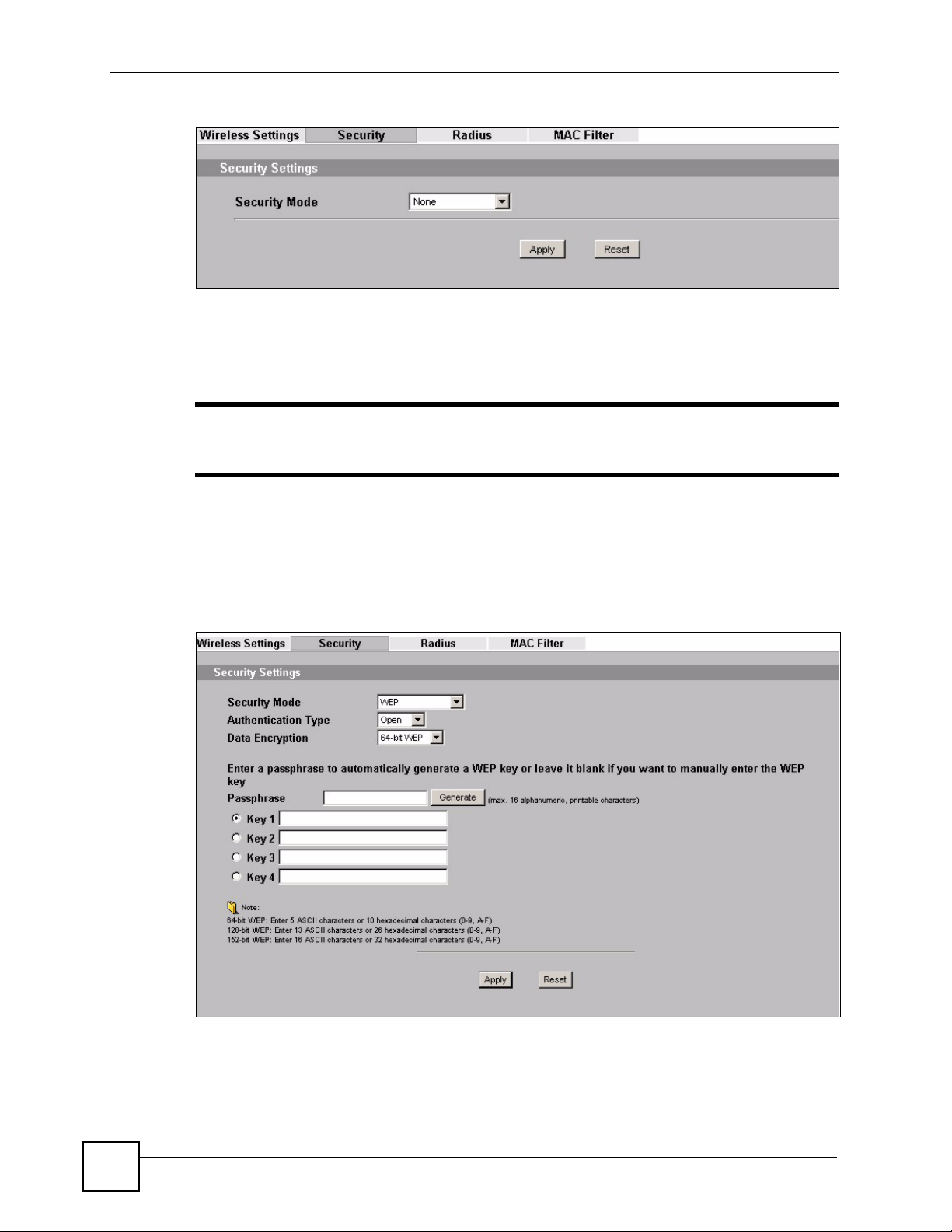
Figure 32 Security: None
The default security mode is set to None.
Note that some screens display differently depending on the operating mode selected in the
Wireless > Wireless Settings screen.
" You must enable the same wireless security settings on the ZyXEL Device and
on all wireless clients that you want to associate with it.
7.4.1 Security: WEP
Use this screen to use WEP as the security mode for your ZyXEL Device. Select WEP in the
Security Mode field to display the following screen.
Figure 33 Security: WEP
78
ZyXEL NWA-1100 User’s Guide
Chapter 7 Wireless Security Screen
The following table describes the labels in this screen.
Table 16 Security: WEP
LABEL DESCRIPTION
Security Mode Choose WEP in this field.
Authentication
Method
Data Encryption Select Disable to allow wireless stations to communicate with the access points
Passphrase Enter the passphrase or string of text used for automatic WEP key generation on
Generate Click this to get the keys from the Passphrase you entered.
Key 1 to
Key 4
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
Select Open or Shared Key from the drop-down list box.
The default setting is Auto.
without any data encryption.
Select 64-bit WEP, 128-bit WEP or 152-bit WEP to enable data encryption.
wireless client adapters.
The WEP keys are used to encrypt data. Both the ZyXEL Device and the wireless
stations must use the same WEP key for data transmission.
If you chose 64-bit WEP, then enter any 5 ASCII characters or 10 hexadecimal
characters ("0-9", "A-F").
If you chose 128-bit WEP, then enter 13 ASCII characters or 26 hexadecimal
characters ("0-9", "A-F").
If you chose 152-bit WEP, then enter 16 ASCII characters or 32 hexadecimal
characters ("0-9", "A-F").
You must configure all four keys, but only one key can be activated at any one
time. The default key is key 1.
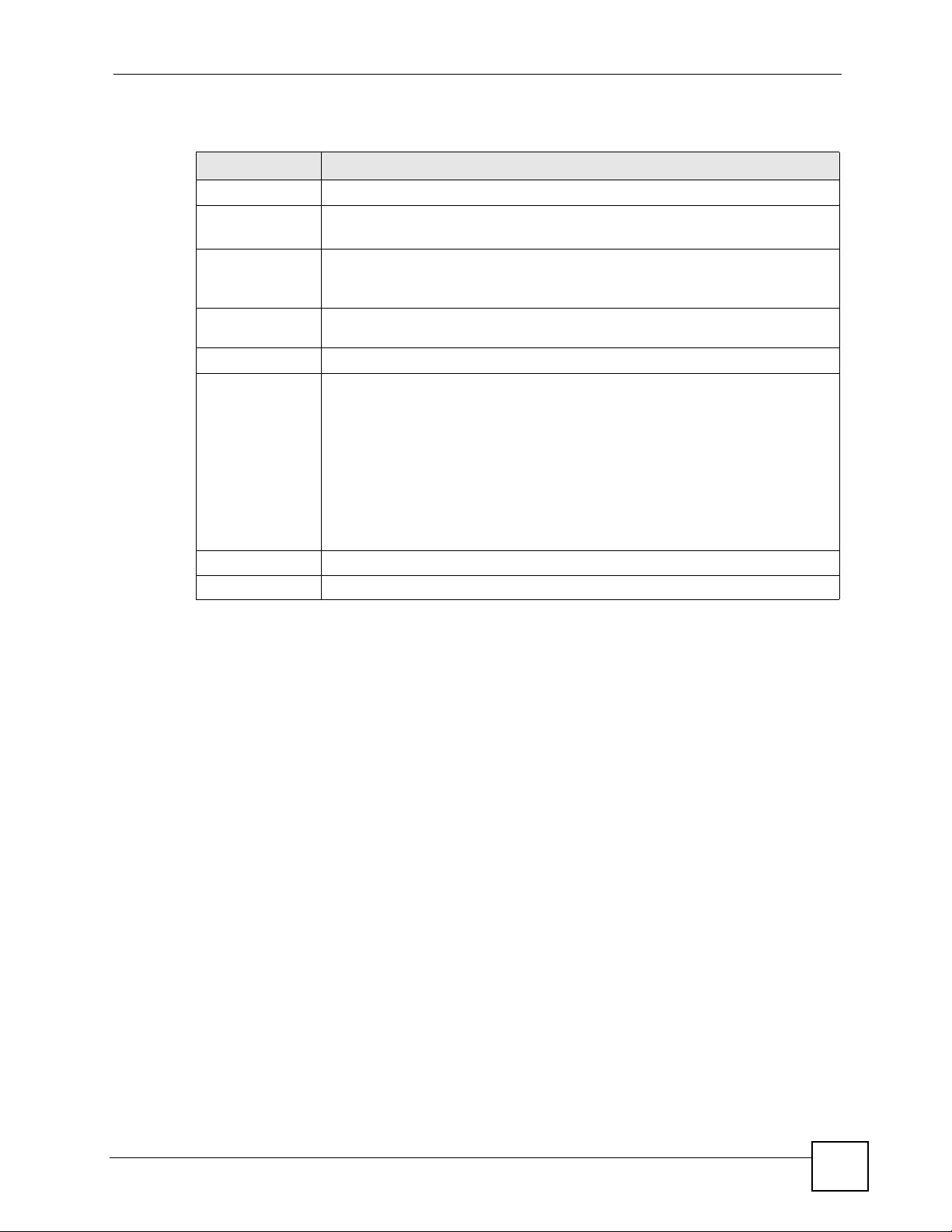
7.4.2 Security: 802.1x Only
This screen varies depending on whether you select Access Point or Wireless Client in the
Wireless > Wireless Settings screen.
7.4.2.1 Access Point
Use this screen to use 802.1x-Only security mode for your ZyXEL Device that is in Access
Point operating mode. Select 802.1x-Only in the Security Mode field to display the following
screen.
ZyXEL NWA-1100 User’s Guide
79
Chapter 7 Wireless Security Screen
Figure 34 Security: 802.1x Only for Access Point
The following table describes the labels in this screen.
Table 17 Security: 802.1x Only for Access Point
LABEL DESCRIPTION
Security Mode Choose 802.1x Only in this field.
ReAuthentication
Time
Specify how often wireless stations have to resend user names and passwords in
order to stay connected.
Enter a time interval between 10 and 9999 seconds. The default time interval is
1800 seconds (30 minutes). Alternatively, enter “0” to turn reauthentication off.
Group-Key
Update
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
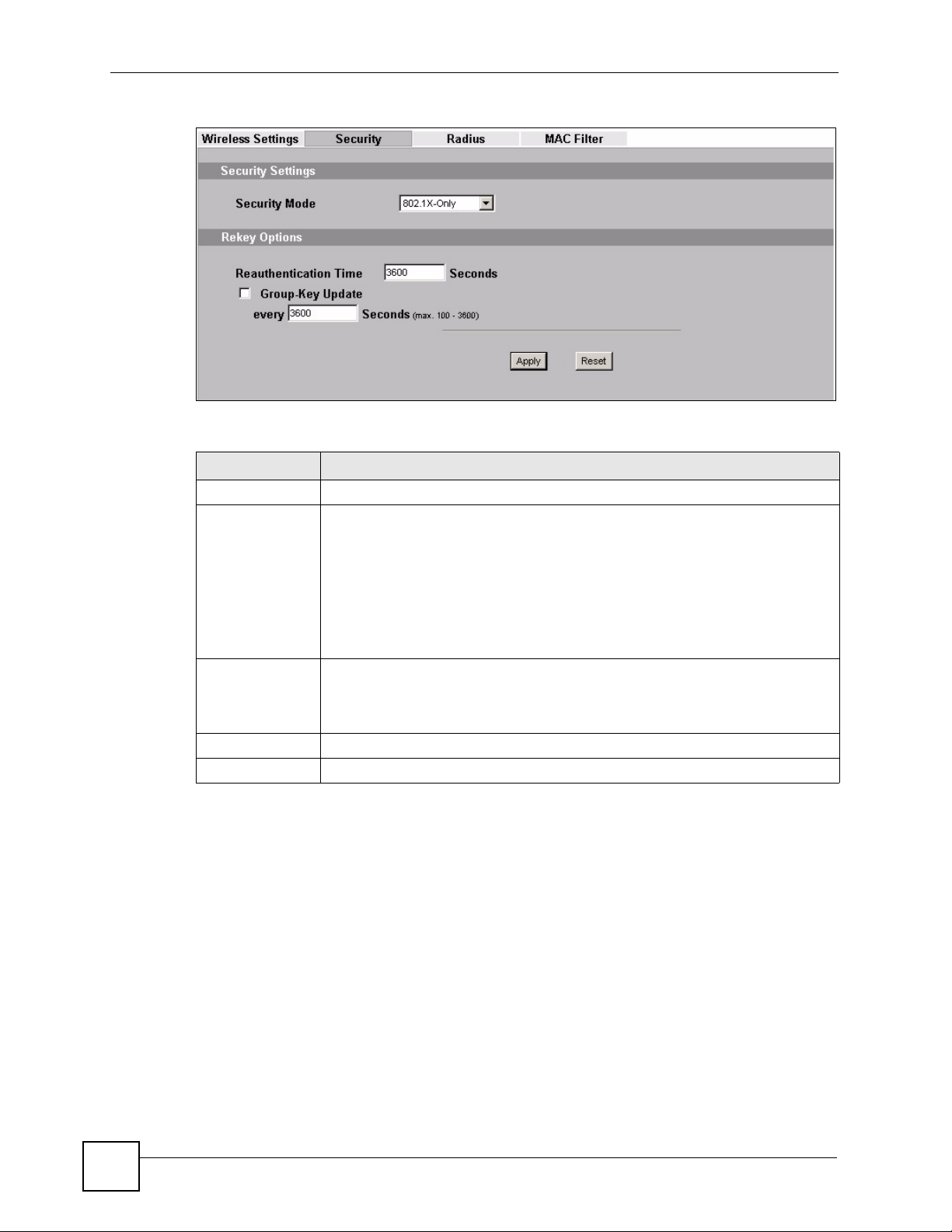
7.4.2.2 Wireless Client
Use this screen to use 802.1x-Only security mode for your ZyXEL Device that is in Wireless
Client operating mode. Select 802.1x-Only in the Security Mode field to display the
following screen.
Note: If wireless station authentication is done using a
RADIUS server, the reauthentication timer on the
RADIUS server has priority.
The ZyXEL Device automatically disconnects a wireless station from the wired
network after a period of inactivity. The wireless station needs to enter the user
name and password again before access to the wired network is allowed.
The default time interval is 3600 seconds (or 1 hour).
80
ZyXEL NWA-1100 User’s Guide
Chapter 7 Wireless Security Screen
Figure 35 Security: 802.1x Only for Wireless Client
The following table describes the labels in this screen.
Table 18 Security: 802.1x Only for Wireless Client
LABEL DESCRIPTION
Security Mode Choose the same security mode used by the AP.
Data Encryption Select between None and Dynamic WEP. Refer to Section on page 161 for
IEEE802.1x
Authentication
EAP Type The options on the left refer to EAP methods. You can choose either TLS, LEAP,
User Information
Username Supply the username of the account created in the RADIUS server.
Password Supply the password of the account created in the RADIUS server.
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
information on using Dynamic WEP.
PEAP or TTLS. The default value is PEAP.
The options on the right refer to authentication protocols. You can choose
between MSCHAPv2 and GT C .The default value is MSCHAPv2.
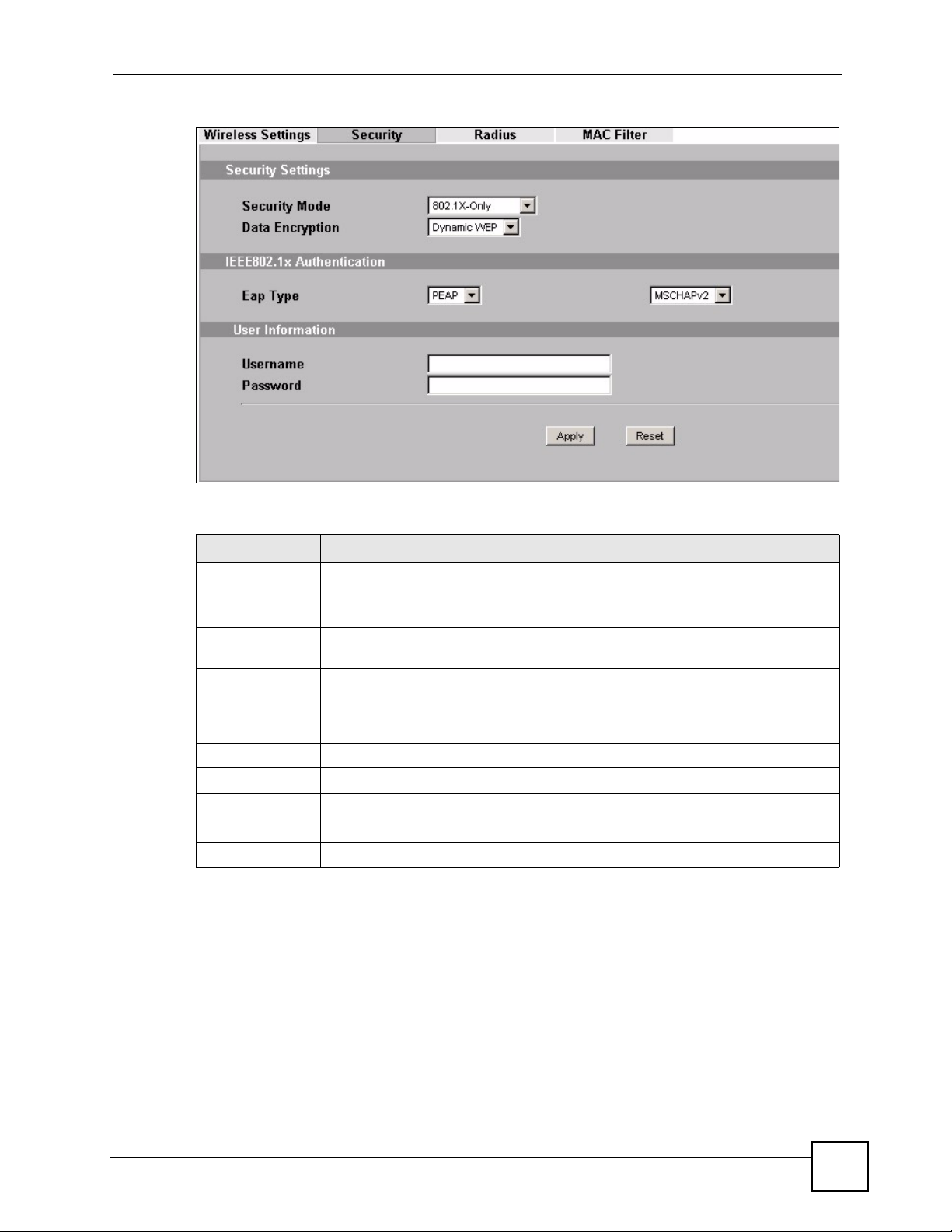
7.4.3 Security: 802.1x Static 64-bit, 802.1x Static 128-bit
Use this screen to use 802.1x Static 64 or 802.1x Static 128 security mode for your ZyXEL
Device. Select 802.1x Static 64 or 802.1x Static 128 in the Security Mode field to display the
following screen.
ZyXEL NWA-1100 User’s Guide
81
Chapter 7 Wireless Security Screen
Figure 36 Security: 802.1x Static 64-bit, 802.1x Static 128-bit (AP mode)
The following table describes the labels in this screen.
Table 19 Security: 802.1x Static 64-bit, 802.1x Static 128-bit
LABEL DESCRIPTION
Security Mode Choose 802.1x Static 64 or 802.1x Static 128 in this field.
Passphrase
Generate
Key 1 to Key 4 If you chose 802.1x Static 64, then enter any 5 characters (ASCII string) or 10
ReAuthentication
Timer
Enter the passphrase or string of text used for automatic WEP key generation on
wireless client adapters (AP mode).
Click this to get the keys from the Passphrase you entered (AP mode).
hexadecimal characters ("0-9", "A-F") preceded by 0x for each key.
If you chose 802.1x Static 128-bit, then enter 13 characters (ASCII string) or 26
hexadecimal characters ("0-9", "A-F") preceded by 0x for each key.
There are four data encryption keys to secure your data from eavesdropping by
unauthorized wireless users. The values for the keys must be set up exactly the
same on the access points as they are on the wireless stations.
The preceding “0x” is entered automatically. You must configure all four keys, but
only one key can be activated at any one time. The default key is key 1.
Specify how often wireless stations have to resend user names and passwords in
order to stay connected.
Enter a time interval between 10 and 9999 seconds. The default time interval is
1800 seconds (30 minutes). Alternatively, enter “0” to turn reauthentication off.
Note: If wireless station authentication is done using a
RADIUS server, the reauthentication timer on the
RADIUS server has priority.
82
ZyXEL NWA-1100 User’s Guide
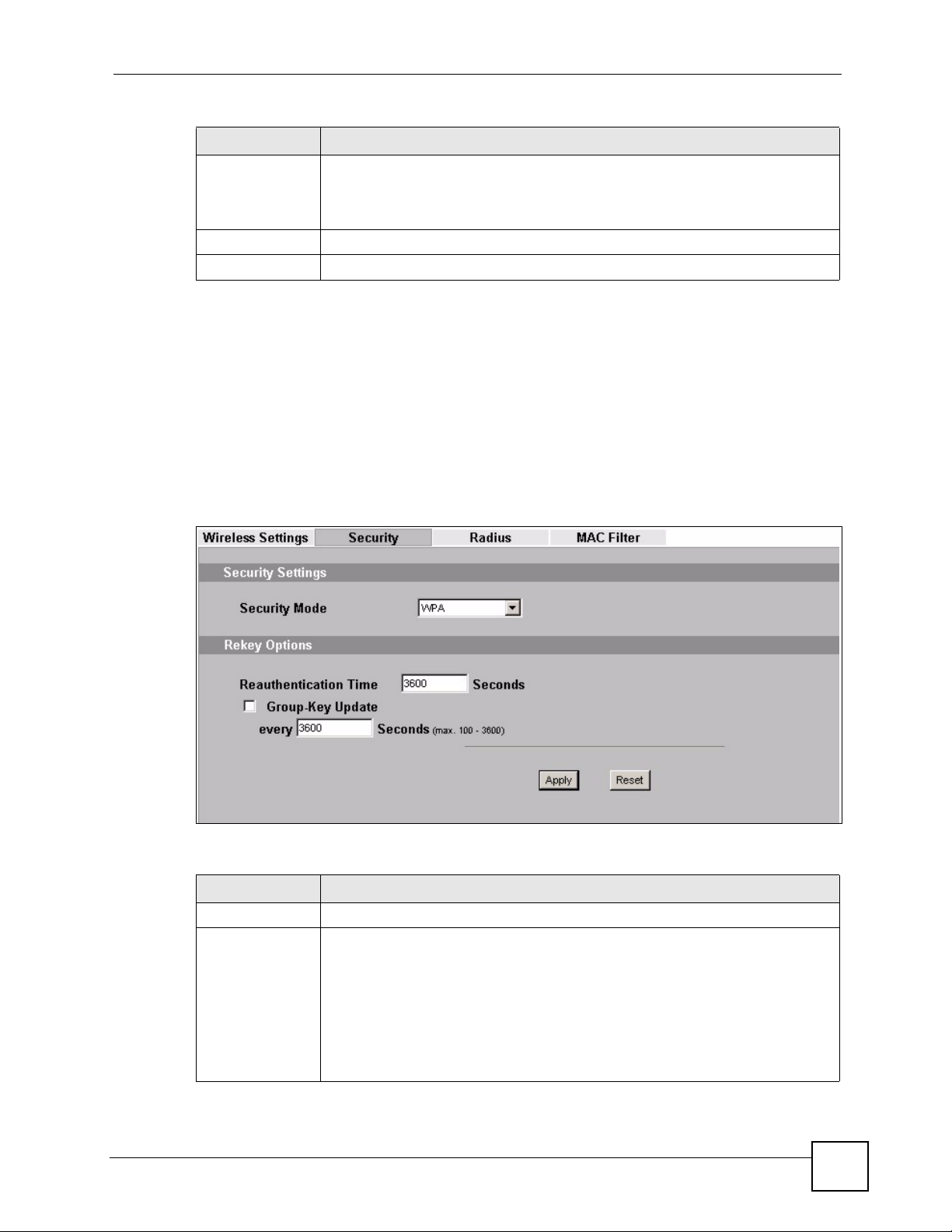
Table 19 Security: 802.1x Static 64-bit, 802.1x Static 128-bit
LABEL DESCRIPTION
Group-Key
Update
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
7.4.4 Security: WPA
This screen varies depending on whether you select Access Point or Wireless Client in the
Wireless > Wireless Settings screen.
7.4.4.1 Access Point
Use this screen to employ WPA as the security mode for your ZyXEL Device that is in Access
Point operating mode. Select WPA in the Security Mode field to display the following
screen.
Chapter 7 Wireless Security Screen
The ZyXEL Device automatically disconnects a wireless station from the wired
network after a period of inactivity. The wireless station needs to enter the user
name and password again before access to the wired network is allowed.
The default time interval is 3600 seconds (or 1 hour).
Figure 37 Security: WPA for Access Point
The following table describes the labels in this screen.
Table 20 Security: WPA for Access Point
LABEL DESCRIPTION
Security Mode Choose WPA in this field.
ReAuthentication
Timer
Specify how often wireless stations have to resend user names and passwords in
order to stay connected.
Enter a time interval between 10 and 9999 seconds. The default time interval is
1800 seconds (30 minutes). Alternatively, enter “0” to turn reauthentication off.
ZyXEL NWA-1100 User’s Guide
Note: If wireless station authentication is done using a
RADIUS server, the reauthentication timer on the
RADIUS server has priority.
83
Chapter 7 Wireless Security Screen
Table 20 Security: WPA for Access Point
LABEL DESCRIPTION
Group Key
Update
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
The Group Key Update Timer is the rate at which the AP sends a new group key
out to all clients. The re-keying process is the WPA equivalent of automatically
changing the group key for an AP and all stations in a WLAN on a periodic basis.
Setting of the Group Key Update Timer is also supported in WPA-PSK mode.
The ZyXEL Device default is 3800 seconds (or 1 hour).
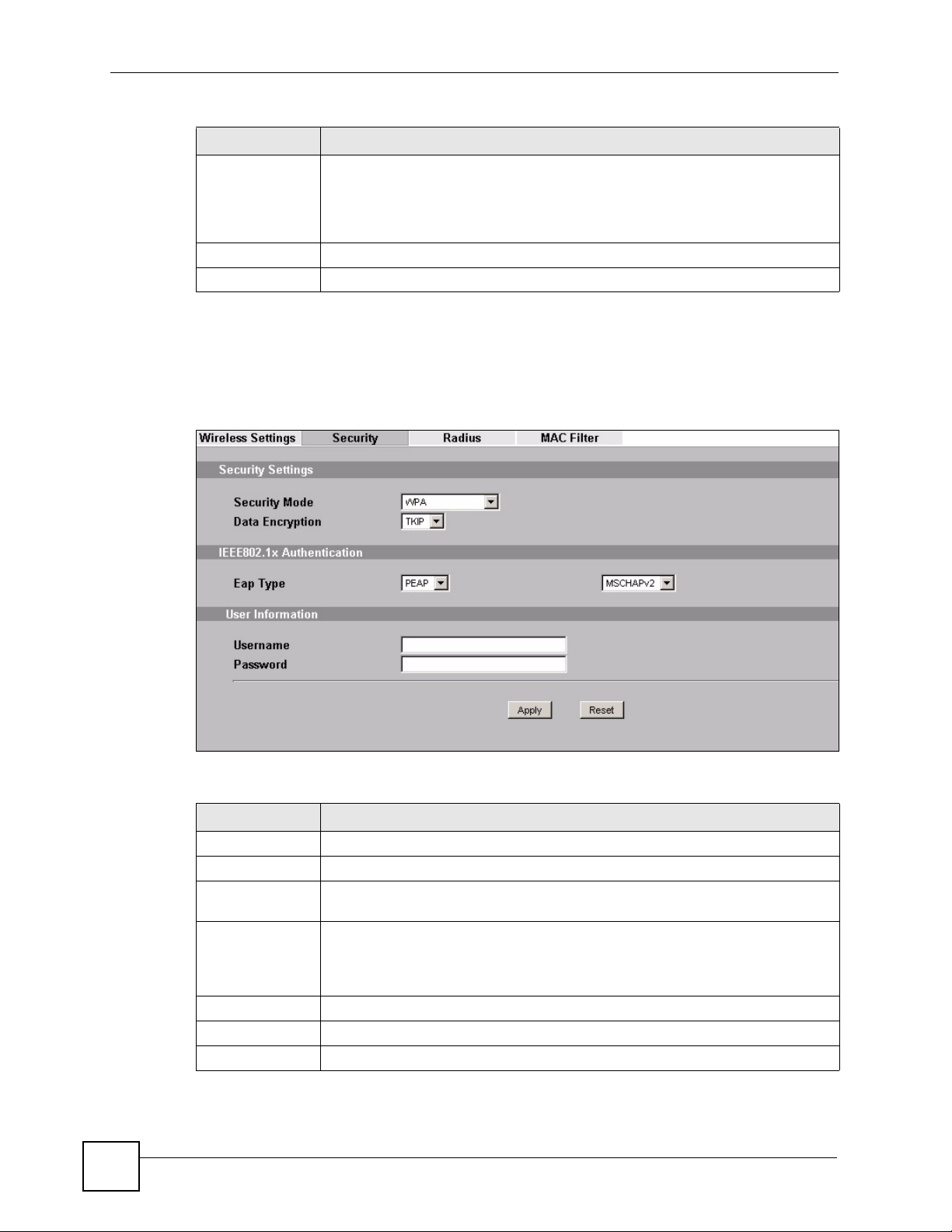
7.4.4.2 Wireless Client
Use this screen to employ WPA as the security mode for your ZyXEL Device that is in
Wireless Client operating mode. Select WPA in the Security Mode field to display the
following screen.
Figure 38 Security: WPA for Wireless Client
84
The following table describes the labels in this screen.
Table 21 Security: WPA for Wireless Client
LABEL DESCRIPTION
Security Mode Choose the same security mode used by the AP.
Data Encryption Select between None and TKIP.
IEEE802.1x
Authentication
EAP Type The options on the left refer to EAP methods. You can choose either TLS, LEAP,
PEAP or TTLS. The default value is PEAP.
The options on the right refer to authentication protocols. You can choose
between MSCHAPv2 and GT C .The default value is MSCHAPv2.
User Information
Username Supply the username of the account created in the RADIUS server.
Password Supply the password of the account created in the RADIUS server.
ZyXEL NWA-1100 User’s Guide
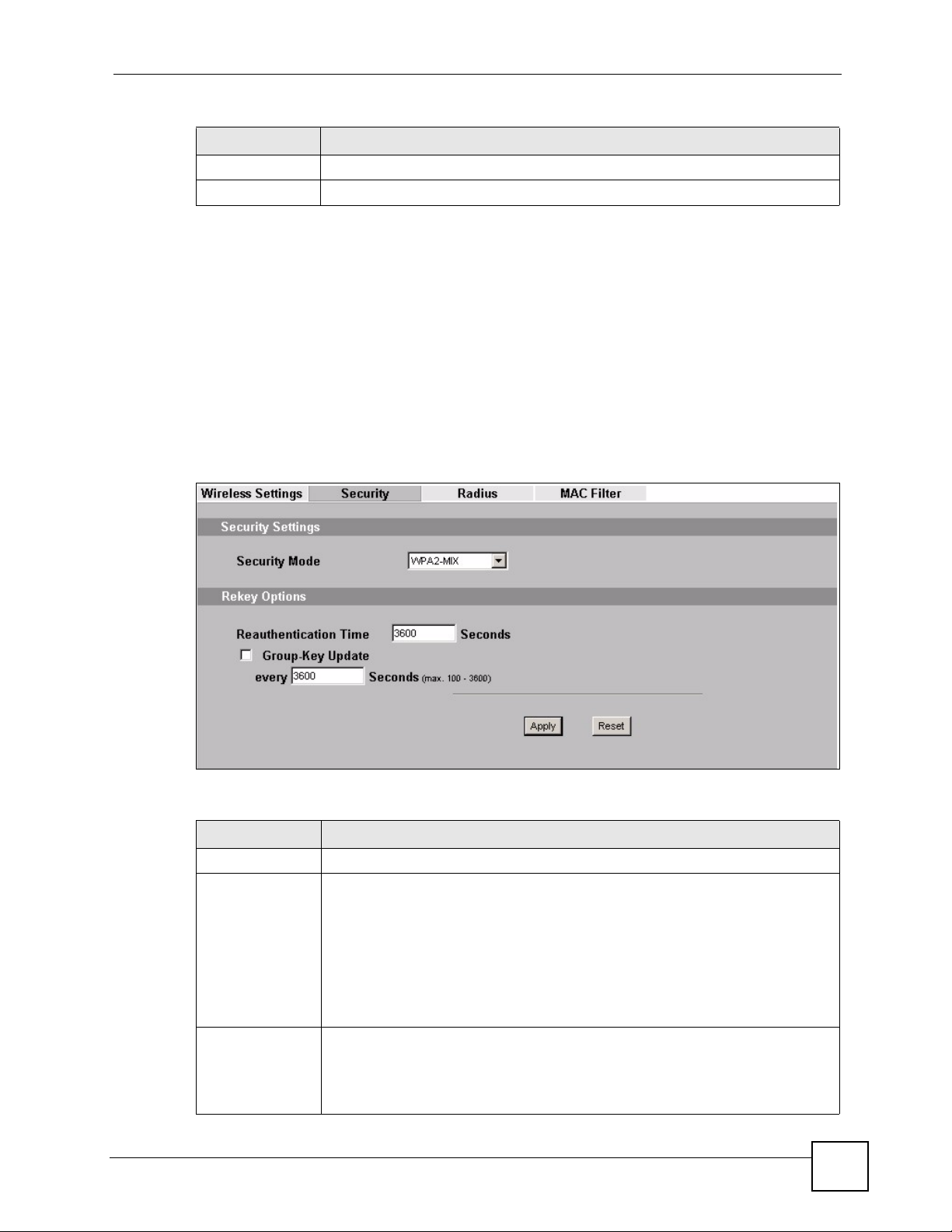
Table 21 Security: WPA for Wireless Client
LABEL DESCRIPTION
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
7.4.5 Security: WPA2 or WPA2-MIX
This screen varies depending on whether you select Access Point or Wireless Client in the
Wireless > Wireless Settings screen.
7.4.5.1 Access Point
Use this screen to use WAP2 or WPA2-MIX as the security mode for your ZyXEL Device that
is in Access Point operating mode. Select WPA2 or WPA2-MIX in the Security Mode field
to display the following screen.
Figure 39 Security:WPA2 or WPA2-MIX for Access Point
Chapter 7 Wireless Security Screen
The following table describes the labels not previously discussed
Table 22 Security: WPA2 or WPA2-MIX for Access Point
LABEL DESCRIPTIONS
Security Mode Choose WPA2 or WPA2-MIX in this field.
ReAuthentication
Timer
Group Key
Update Timer
ZyXEL NWA-1100 User’s Guide
Specify how often wireless stations have to resend usernames and passwords in
order to stay connected.
Enter a time interval between 10 and 9999 seconds. The default time interval is
1800 seconds (30 minutes). Alternatively, enter “0” to turn reauthentication off.
Note: If wireless station authentication is done using a
RADIUS server, the reauthentication timer on the
RADIUS server has priority.
The Group Key Update Timer is the rate at which the AP sends a new group key
out to all clients. The re-keying process is the WPA equivalent of automatically
changing the group key for an AP and all stations in a WLAN on a periodic basis.
Setting of the Group Key Update Timer is also supported in WPA-PSK mode.
The ZyXEL Device‘s default is 3600 seconds (or 1 hour).
85
Chapter 7 Wireless Security Screen
Table 22 Security: WPA2 or WPA2-MIX for Access Point
LABEL DESCRIPTIONS
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
7.4.5.2 Wireless Client
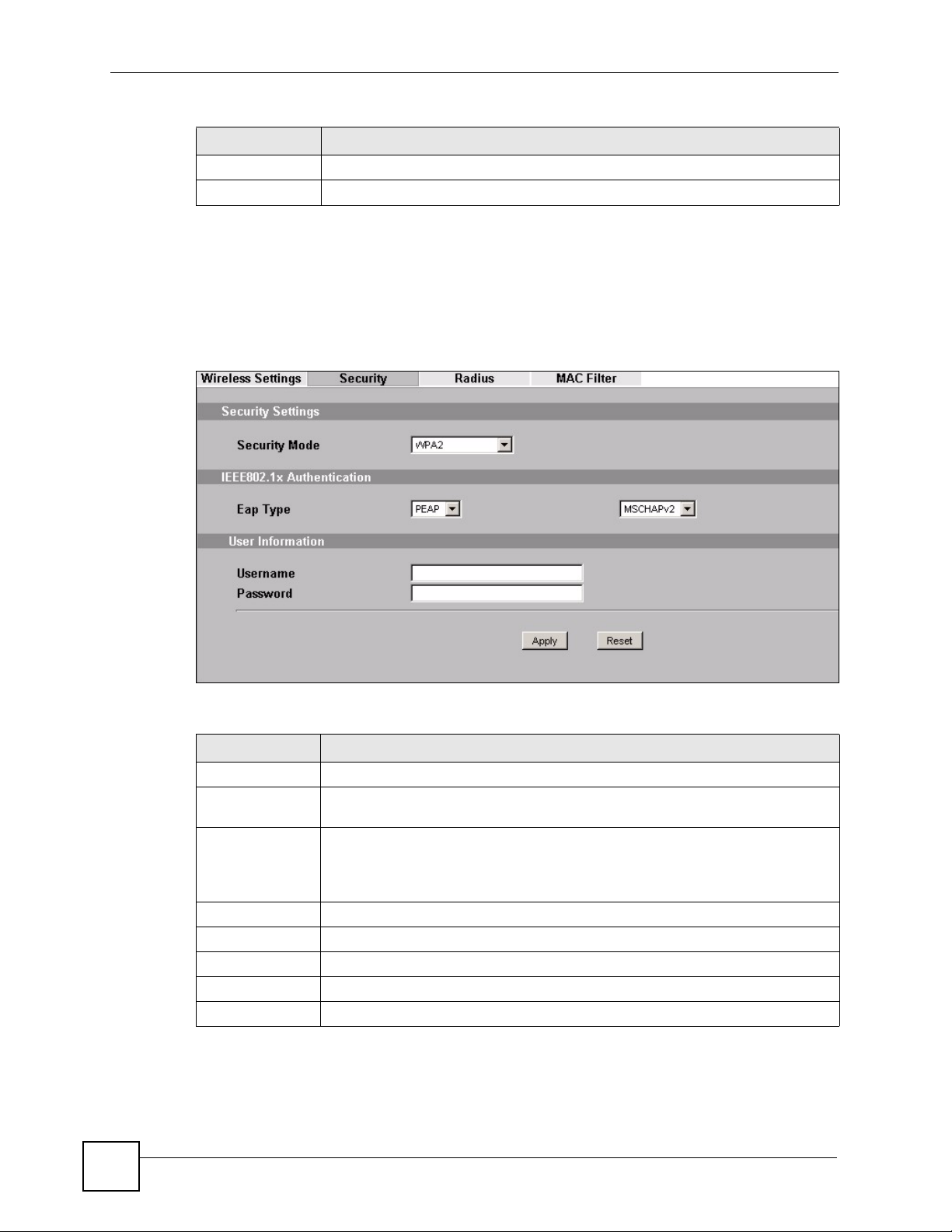
Use this screen to employ WPA2 or WPA2-MIX as the security mode of your ZyXEL Device
that is in Wireless Client operating mode. Select WPA2 or WPA2-MIX in the Security
Mode field to display the following screen.
Figure 40 Security: WPA2 or WPA2-MIX for Wireless Client
The following table describes the labels in this screen.
Table 23 Security: WPA2 or WPA2-MIX for Wireless Client
LABEL DESCRIPTION
Security Mode Choose the same security mode used by the AP.
IEEE802.1x
Authentication
EAP Type The options on the left refer to EAP methods. You can choose either TLS, LEAP,
User Information
Username Supply the username of the account created in the RADIUS server.
Password Supply the password of the account created in the RADIUS server.
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
PEAP or TTLS. The default value is PEAP.
The options on the right refer to authentication protocols. You can choose
between MSCHAPv2 and GT C .The default value is MSCHAPv2.
86
ZyXEL NWA-1100 User’s Guide
Chapter 7 Wireless Security Screen
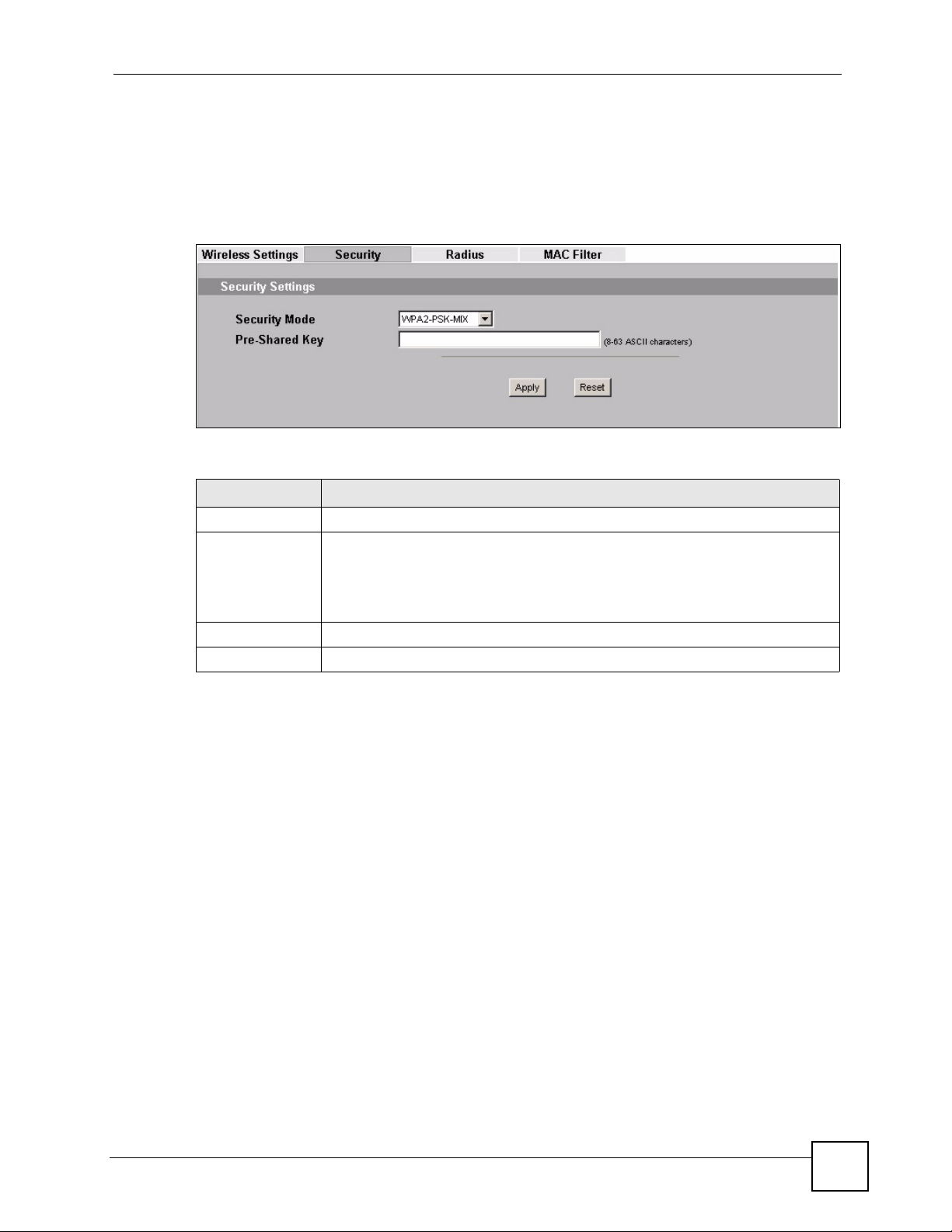
7.4.6 Security: WPA-PSK, WPA2-PSK, WPA2-PSK-MIX
Use this screen to employ WPA-PSK, WPA2-PSK or WPA2-PSK-MIX as the security mode
of your ZyXEL Device. Select WPA-PSK, WPA2-PSK or WPA2-PSK-MIX in the Security
Mode field to display the following screen.
Figure 41 Security: WPA-PSK, WPA2-PSK or WPA2-PSK-MIX
The following table describes the labels not previously discussed
Table 24 Security: WPA-PSK, WPA2-PSK or WPA2-PSK-MIX
LABEL DESCRIPTION
Security Mode Choose WPA-PSK, WPA2-PSK or WPA2-PSK-MIX in this field.
Pre-Shared Key The encryption mechanisms used for WPA and WPA-PSK are the same. The only
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
difference between the two is that WPA-PSK uses a simple common password,
instead of user-specific credentials.
Type a pre-shared key from 8 to 63 case-sensitive ASCII characters (including
spaces and symbols).
7.5 Technical Reference
This section provides technical background information on the topics discussed in this chapter.
The following is a general guideline in choosing the security mode for your ZyXEL Device.
• Use WPA(2)-PSK if you have WPA(2)-aware wireless clients but no RADIUS server.Use
WPA(2) security if you have WPA(2)-aware wireless clients and a RADIUS server. WPA
has user authentication and improved data encryption over WEP.
• Use WPA(2)-PSK if you have WPA(2)-aware wireless clients but no RADIUS server.
• If you don’t have WPA(2)-aware wireless clients, then use WEP key encrypting. A higher
bit key offers better security. You can manually enter 64-bit, 128-bit or 152-bit WEP keys.
More information on Wireless Security can be found in Appendix E on page 153.
ZyXEL NWA-1100 User’s Guide
87

Chapter 7 Wireless Security Screen
88
ZyXEL NWA-1100 User’s Guide
CHAPTER 8
RADIUS Screen
8.1 Overview
This chapter describes how you can use the Wireless > RADIUS screen.
Remote Authentication Dial In User Service (RADIUS) is a protocol that can be used to
manage user access to large networks. It is based on a client-server model that supports
authentication, authorization and accounting. The access point is the client and the server is
the RADIUS server.
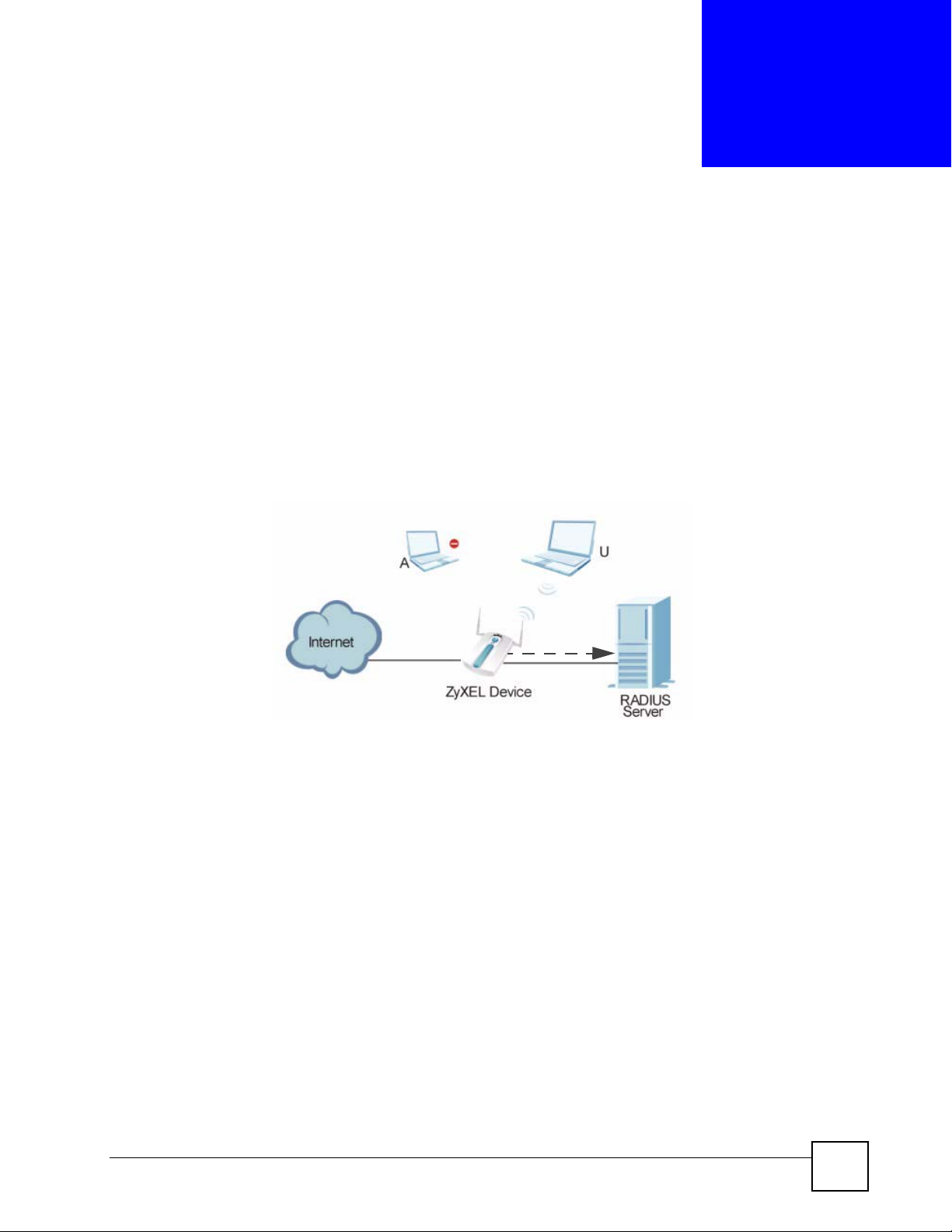
Figure 42 RADIUS Server Setup
Authentication
In the figure above, wireless clients A and B are trying to access the Internet via the ZyXEL
Device. The ZyXEL Device in turn queries the RADIUS server if the identity of clients A and
U are allowed access to the Internet. In this scenario, only client U’s identity is verified by the
RADIUS server and allowed access to the Internet.
8.2 What You Can Do in the RADIUS Screen
Use the Security > RADIUS screen (see Section 7.4.1 on page 78) if you want to authenticate
wireless users using a RADIUS Server and/or Accounting Server.
8.3 What You Need to Know About RADIUS
The RADIUS server handles the following tasks:
• Authentication which determines the identity of the users.
• Authorization which determines the network services available to authenticated users
once they are connected to the network.
ZyXEL NWA-1100 User’s Guide
89

Chapter 8 RADIUS Screen
• Accounting which keeps track of the client’s network activity.
RADIUS is a simple package exchange in which your AP acts as a message relay between the
wireless client and the network RADIUS server.
You should know the IP addresses, ports and share secrets of the external RADIUS server and/
or the external RADIUS accounting server you want to use with your ZyXEL Device. You can
configure a primary and backup RADIUS and RADIUS accounting server for your ZyXEL
Device.
8.4 The RADIUS Screen
Use this screen to set up your ZyXEL Device’s RADIUS server settings. Click Wireless >
RADIUS. The screen appears as shown.
Figure 43 Wireless > RADIUS
90
The following table describes the labels in this screen.
Table 25 Wireless > RADIUS
LABEL DESCRIPTION
Primary Configure the fields below to set up user authentication and accounting.
Backup If the ZyXEL Device cannot communicate with the Primary accounting server,
RADIUS Option
Active Select the check box to enable user authentication through an external
RADIUS Server IP
Address
you can have the ZyXEL Device use a Backup RADIUS server. Make sure
the Active check boxes are selected if you want to use backup servers.
The ZyXEL Device will attempt to communicate three times before using the
Backup servers. Requests can be issued from the client interface to use the
backup server. The length of time for each authentication is decided by the
wireless client or based on the configuration of the ReAuthentication Timer
field in the Security Settings screen.
authentication server. This check box is not available when you select
Internal.
Enter the IP address of the external authentication server in dotted decimal
notation. This field is not available when you select Internal.
ZyXEL NWA-1100 User’s Guide
Chapter 8 RADIUS Screen
Table 25 Wireless > RADIUS
LABEL DESCRIPTION
RADIUS Server Port Enter the port number of the external authentication server. The default port
number is 1812. You need not change this value unless your network
administrator instructs you to do so. This field is not available when you select
Internal.
Share Secret Enter a password (up to 128 alphanumeric characters) as the key to be
shared between the external authentication server and the ZyXEL Device.
The key must be the same on the external authentication server and your
ZyXEL Device. The key is not sent over the network. This field is not available
when you select Internal.
Active Select the check box to enable user accounting through an external
authentication server.
Accounting Server IP
Address
Accounting Server
Port
Share Secret Enter a password (up to 128 alphanumeric characters) as the key to be
Apply Click Apply to save your changes.
Reset Click Reset to begin configuring this screen afresh.
Enter the IP address of the external accounting server in dotted decimal
notation.
Enter the port number of the external accounting server. The default port
number is 1813. You need not change this value unless your network
administrator instructs you to do so with additional information.
shared between the external accounting server and the ZyXEL Device. The
key must be the same on the external accounting server and your ZyXEL
Device. The key is not sent over the network.
ZyXEL NWA-1100 User’s Guide
91
 Loading...
Loading...