Konica Minolta bizhub C250 User Manual

User’s Guide
[Network Scanner Operations]

Introduction
Introduction
Thank you for choosing this machine.
This user’s guide contains details on the operation of the network connection
and scanner functions of the bizhub C250, precautions on its use, and basic
troubleshooting procedures. In order to ensure that this machine is used correctly and efficiently, carefully read this user’s guide before using the machine. After reading the manual, store it in the designated holder so that it
can easily be referred to when questions or problems arise during operation.
The illustrations used in this manual may appear slightly different from views
of the actual equipment.
Energy Star
As an ENERGY STAR® Partner, we have determined that this machine meets
the ENERGY STAR
What is an ENERGY STAR
An ENERGY STAR
ically switch to a “low-power mode” after a period of inactivity. An ENERGY
STAR
and helps protect the environment.
®
®
Guidelines for energy efficiency.
®
Product?
®
product has a special feature that allows it to automat-
®
product uses energy more efficiently, saves you money on utility bills
C250 x-1

Trademarks and Registered Trademarks
KONICA MINOLTA, KONICA MINOLTA Logo, and The essentials of imaging
are registered trademarks or trademarks of KONICA MINOLTA HOLDINGS,
INC.
PageScope and bizhub are registered trademarks or trademarks of KONICA
MINOLTA BUSINESS TECHNOLOGIES, INC.
Netscape Communications, the Netscape Communications logo, Netscape
Navigator, Netscape Communicator, and Netscape are trademarks of Netscape Communications Corporation.
This machine and PageScope Box Operator are based in part on the work of
the Independent JPEG Group.
Compact-VJE
Copyright 1986-2003 VACS Corp.
RC4® is a registered trademark or trademark of RSA Security Inc. in the United States and/or other countries.
RSA® is a registered trademark or trademark of RSA Security Inc. RSA
®
BSAFE
United States and/or other countries.
is a registered trademark or trademark of RSA Security Inc. in the
License information
This product includes RSA BSAFE Cryptographic software
from RSA Security Inc.
Introduction
OpenSSL Statement
OpenSSL License
Copyright © 1998-2000 The OpenSSL Project. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must
display the following acknowledgment:
“This product includes software developed by the OpenSSL Project for
use in the OpenSSL Toolkit. (http://www.openssl.org/)”
x-2 C250

Introduction
4. The names “OpenSSL Toolkit” and “OpenSSL Project” must not be used
5. Products derived from this software may not be called “OpenSSL” nor
6. Redistributions of any form whatsoever must retain the following ac-
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT “AS IS” AND
ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT
SHALL THE OpenSSL PROJECT OR ITS CONTRIBUTORS BE LIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY
WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written by Eric Young
(eay@crypt-Soft.com). This product includes software written by Tim Hudson (tjh@cryptsoft.com).
Original SSLeay License
Copyright © 1995-1998 Eric Young (eay@cryptsoft.com) All rights reserved.
This package is an SSL implementation written by Eric Young (eay@cryptsoft.com).
The implementation was written so as to conform with Netscapes SSL.
This library is free for commercial and non-commercial use as long as the following conditions are aheared to. The following conditions apply to all code
found in this distribution, be it the RC4, RSA, Ihash, DES, etc., code; not just
the SSL code.
The SSL documentation included with this distribution is covered by the
same copyright terms except that the holder is Tim Hudson (tjh@cryptsoft.com).
Copyright remains Eric Young’s, and as such any Copyright notices in the
code are not to be removed. If this package is used in a product, Eric Young
should be given attribution as the author of the parts of the library used. This
can be in the form of a textual message at program startup or in documentation (online or textual) provided with the package.
to endorse or promote products derived from this software without prior
written permission. For written permission, please contact opensslcore@openssl.org.
may “OpenSSL” appear in their names without prior written permission
of the OpenSSL Project.
knowledgment:
“This product includes software developed by the OpenSSL Project for
use in the OpenSSL Toolkit (http://www.openssl.org/)”
C250 x-3

Introduction
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the copyright notice, this list
of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must
display the following acknowledgement:
“This product includes cryptographic software written by Eric Young
(eay@crypt-soft.com)”
The word ‘cryptographic’ can be left out if the rouines from the library being used are not cryptographic related.
4. If you include any Windows specific code (or a derivative thereof) from
the apps directory (application code) you must include an acknowledgement:
“This product includes software written by Tin Hudson (tjh@cryptsoft.com)”
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
The licence and distribution terms for any publically available version or derivative of this code cannot be changed. i.e. this code cannot simply be copied and put under another distribution licence [including the GNU Public
Licence.]
All other product names mentioned are trademarks or registered trademarks
of their respective companies
x-4 C250

Introduction
Contents
Introduction
Energy Star® ..................................................................................... x-1
What is an ENERGY STAR
Trademarks and Registered Trademarks ...................................... x-2
Contents ............................................................................................ x-5
About This Manual .......................................................................... x-14
Structure of the Manual ................................................................x-14
Notation .........................................................................................x-14
Screens, Windows and Dialog Boxes ...........................................x-14
Explanation of Manual Conventions ............................................. x-15
User’s Guides .................................................................................. x-16
User’s Guide [Copy Operations] ...................................................x-16
User’s Guide [Network Scanner Operations] <this manual> ........x-16
User’s Guide [Box Operations] .....................................................x-16
User’s Guide [Enlarge Display Operations] ...................................x-16
User’s Guide [FK-502 Facsimile Operations] ................................x-16
User’s Guide [Network Facsimile Operations] ..............................x-16
User’s Guide [Print Operations] ....................................................x-17
Quick Guide [Print Operations] .....................................................x-17
®
Product? ............................................x-1
1 Before Using the Scan Functions
1.1 Environment Required for Using the Scan Functions ................... 1-2
1.2 Available Scanning Functions ......................................................... 1-3
Sending the Scanned Data in an E-Mail Message ......................... 1-3
Sending the Scanned Data as Files (FTP) ...................................... 1-4
Sending the Scanned Data to a Computer on the Network
(SMB) ............................................................................................. 1-5
Saving the Scanned Data in Boxes ................................................ 1-6
Using the Machine as a Scanner ................................................... 1-7
1.3 Settings for Using Network/Scanning Functions .......................... 1-8
Specifying Network Settings .......................................................... 1-8
Registering Destinations and Specifying Their Settings ................ 1-8
Setting the From Address .............................................................. 1-9
Specifying the Scan Settings ......................................................... 1-9
Specifying Program Settings ....................................................... 1-10
Specifying Default Scan Settings ................................................. 1-10
1.4 Connecting to the Network ........................................................... 1-11
Network Connection .................................................................... 1-11
C250 x-5

1.5 Flow Chart of Setup and Scanning Operations ............................1-12
2 Scanning Documents
2.1 Control Panel .....................................................................................2-2
2.2 Displaying the Scan Screen ..............................................................2-5
2.3 Sending Data in an E-Mail Message (Scan to E-Mail) ....................2-6
Scan to E-Mail ................................................................................2-6
Using Programs ..............................................................................2-6
Selecting Group Addresses ............................................................2-9
Selecting Destinations From the Address Book ...........................2-12
Searching the Destination .............................................................2-13
To search the destination .............................................................2-15
Entering the Addresses Directly ...................................................2-16
2.4 Sending Data to a Server (Scan to FTP) ........................................2-19
Scan to FTP ..................................................................................2-19
Using Programs ............................................................................2-19
Selecting Group Addresses ..........................................................2-21
Selecting Destinations From the Address Book ...........................2-24
Entering the Addresses Directly ...................................................2-27
2.5 Sending Data to a PC on the Network (Scan to SMB) .................2-31
Scan to SMB .................................................................................2-31
SMB Transmission to Windows File Sharing (Mac OS X)/Samba
(Linux/Unix) ...................................................................................2-31
SMB Transmission to Windows 98 SE/Windows Me ...................2-31
Using Programs ............................................................................2-32
Selecting Group Addresses ..........................................................2-34
Selecting Destinations From the Address Book ...........................2-36
Entering the Addresses Directly ...................................................2-39
2.6 Specifying the Scan Settings ..........................................................2-42
Available Settings .........................................................................2-42
File Type ........................................................................................2-43
To specify the File Type settings ..................................................2-45
Resolution .....................................................................................2-47
Simplex/Duplex .............................................................................2-48
To specify the Simplex/Duplex setting .........................................2-48
Original Type .................................................................................2-49
To specify the Original Type setting .............................................2-49
Scan Size ......................................................................................2-51
To specify the Scan Size setting ...................................................2-51
Color .............................................................................................2-53
To specify the Color setting ..........................................................2-54
Background Removal ...................................................................2-55
Original Setting .............................................................................2-56
Introduction
x-6 C250

Introduction
To specify the Original Settings ................................................... 2-56
Book Scanning (Application) ........................................................ 2-58
To use the “Book Scan” function ................................................. 2-59
Frame Erase (Application) ............................................................ 2-61
Annotation (Application) ............................................................... 2-63
Separate Scan .............................................................................. 2-64
File Name ..................................................................................... 2-65
To change the file name ............................................................... 2-65
2.7 Checking the Settings .................................................................... 2-67
Checking the Settings .................................................................. 2-67
To check a job .............................................................................. 2-67
Deleting Unneeded Destinations ................................................. 2-72
Specifying E-Mail Settings ........................................................... 2-74
To change the e-mail settings ...................................................... 2-75
2.8 Checking the Scanner Transmission Log .................................... 2-76
Displaying the Current Jobs List .................................................. 2-76
Displaying the Job History List .................................................... 2-77
Displayed Information .................................................................. 2-78
3 Specifying Settings From the Control Panel
3.1 Settings on the Control Panel ......................................................... 3-2
Utility Types ................................................................................... 3-2
Other Related Settings ................................................................... 3-4
3.2 Displaying Setup Screens ................................................................ 3-5
To display the Scan screen ............................................................ 3-5
To display the User Setting screen ................................................ 3-7
To display the Administrator Setting screen .................................. 3-8
3.3 Registering Abbreviated Destinations .......................................... 3-10
E-Mail Destinations ...................................................................... 3-10
FTP Destinations .......................................................................... 3-12
SMB Destinations ........................................................................ 3-17
Box Destinations .......................................................................... 3-20
3.4 Registering Group Destinations .................................................... 3-22
To register a group destination .................................................... 3-22
3.5 Registering Program Destinations ................................................ 3-24
To register a program destination ................................................ 3-24
3.6 Specifying E-Mail Settings ............................................................. 3-27
Subject ......................................................................................... 3-27
Text .............................................................................................. 3-29
3.7 Setting the Main Scan Mode Screen ............................................ 3-31
Default Tab ................................................................................... 3-31
C250 x-7

Introduction
Program Default ............................................................................3-32
Address Book Default Index .........................................................3-33
Address Type Symbol Display ......................................................3-34
3.8 Setting the Save Format of the Data to Be Scanned ...................3-35
JPEG Compression Level .............................................................3-35
To specify the compression level .................................................3-35
Black Compression Level .............................................................3-36
To specify the compression level .................................................3-36
TWAIN Lock Time .........................................................................3-37
3.9 One-Touch Registration List ..........................................................3-39
Address Book List .........................................................................3-39
Group List .....................................................................................3-40
Program List .................................................................................3-41
E-Mail Subject/Text List ................................................................3-42
3.10 Creating Annotation User Boxes ...................................................3-44
To create annotation user boxes ..................................................3-45
3.11 TCP/IP Settings ...............................................................................3-48
Before Specifying the Settings .....................................................3-48
Items To Be Specified ...................................................................3-49
To specify TCP/IP settings ...........................................................3-50
IP Filtering .....................................................................................3-53
RAW Port No. ................................................................................3-54
3.12 NetWare Settings .............................................................................3-55
NetWare Parameters .....................................................................3-55
To specify NetWare settings .........................................................3-56
Status ............................................................................................3-59
3.13 http Server Settings ........................................................................3-60
IPP and http Parameters ...............................................................3-60
To specify IPP and http settings ...................................................3-61
Support Operation ........................................................................3-63
Printer Information ........................................................................3-64
3.14 FTP Settings .....................................................................................3-67
FTP Parameters ............................................................................3-67
To specify FTP settings ................................................................3-68
3.15 SMB Settings ...................................................................................3-70
SMB Parameters ...........................................................................3-70
To specify SMB settings ...............................................................3-71
3.16 AppleTalk Settings ..........................................................................3-74
AppleTalk Parameters ...................................................................3-74
To specify AppleTalk settings .......................................................3-74
x-8 C250

Introduction
3.17 Enabling LDAP Settings ................................................................. 3-76
Enabling LDAP Parameters .......................................................... 3-76
To specify Enabling LDAP settings .............................................. 3-76
3.18 Setting Up LDAP Settings .............................................................. 3-78
LDAP Server Registration Parameters ......................................... 3-78
To specify Setting Up LDAP settings ........................................... 3-81
Initial Setting for Search Details ................................................... 3-85
3.19 Search Default Setting ................................................................... 3-87
To specify the detect default server settings ............................... 3-87
3.20 E-Mail TX (SMTP) Settings ............................................................. 3-88
E-Mail TX (SMTP) Parameters ...................................................... 3-88
To specify E-Mail TX (SMTP) settings .......................................... 3-89
SMTP Server Address .................................................................. 3-92
SMTP Detail ................................................................................. 3-93
SMTP Authentication ................................................................... 3-94
3.21 E-Mail RX (POP) Settings ............................................................... 3-96
E-Mail RX (POP) Parameters ........................................................ 3-96
To specify E-Mail RX (POP) settings ............................................ 3-97
POP Server Address .................................................................... 3-99
3.22 Device Settings ............................................................................. 3-100
Device Parameters ..................................................................... 3-100
To specify device settings ......................................................... 3-100
3.23 Time Adjustment Settings ........................................................... 3-102
Time Adjustment Parameters ..................................................... 3-102
To specify time adjustment settings .......................................... 3-102
NTP Server Address ................................................................... 3-103
3.24 Status Notification Settings ......................................................... 3-105
Status Notification Parameters .................................................. 3-105
To specify status notification settings ....................................... 3-105
Notification Item Setting ............................................................ 3-106
3.25 Total Counter Report Setting ...................................................... 3-107
To specify the total counter report settings ............................... 3-107
Schedule Setting ........................................................................ 3-108
To specify the notification address settings .............................. 3-110
Notification Address Setting ...................................................... 3-110
3.26 PING Confirmation ........................................................................ 3-112
PING Confirmation Parameters ................................................. 3-112
To specify PING confirmation settings ...................................... 3-112
PING TX Address ....................................................................... 3-114
3.27 SLP Settings .................................................................................. 3-116
To specify SLP settings ............................................................. 3-116
C250 x-9

Introduction
3.28 LPD Settings ..................................................................................3-117
To specify LPD settings ..............................................................3-117
3.29 Prefix/Suffix Settings ....................................................................3-118
Prefix/Suffix Parameters .............................................................3-118
To specify the prefix/suffix settings ............................................3-118
Prefix/Suffix Setting ....................................................................3-120
3.30 Job for the disable proof ..............................................................3-122
To specify the Job for the disable proof settings .......................3-122
3.31 SNMP Settings ...............................................................................3-124
SNMP Parameters ......................................................................3-124
To specify SNMP settings ..........................................................3-125
v1/v2c Setting .............................................................................3-126
v3 Setting ....................................................................................3-127
To specify the v3 settings ...........................................................3-128
3.32 Bonjour Setting ..............................................................................3-130
To specify the Bonjour settings ..................................................3-130
3.33 TCP Socket Setting .......................................................................3-132
To specify the TCP socket settings ............................................3-132
3.34 OpenAPI Settings ..........................................................................3-134
Access Setting ............................................................................3-134
Port No. .......................................................................................3-135
SSL .............................................................................................3-136
Authentication .............................................................................3-137
3.35 External Server Authentication ....................................................3-139
Using Active Directory ................................................................3-139
To specify the external server authentication settings ...............3-140
Using Novell NDS .......................................................................3-144
To specify the settings for using Novell NDS .............................3-144
Using NTLM v1/NTLM v2 ...........................................................3-146
To specify the settings for using NTLM v1/NTLM v2 .................3-146
4 Specifying Settings Using PageScope Web Connection
4.1 Items That Can Be Specified Using PageScope Web
Connection .........................................................................................4-2
User Mode ......................................................................................4-2
Administrator Mode ........................................................................4-3
4.2 Using PageScope Web Connection .................................................4-5
Operating Environment ...................................................................4-5
Accessing PageScope Web Connection ........................................4-5
Page Structure ................................................................................4-6
Web Browser Cache .......................................................................4-8
x-10 C250

Introduction
For Internet Explorer ...................................................................... 4-8
For Netscape Navigator ................................................................. 4-8
4.3 Logging On and Logging Off ........................................................... 4-9
Logging Off .................................................................................... 4-9
To log off ........................................................................................ 4-9
Logging On to User Mode (Public User) ...................................... 4-10
Logging On to User Mode
(Registered User/Box Administrator) ........................................... 4-12
To log on as a registered user/Box Administrator ....................... 4-12
Logging On to Administrator Mode ............................................. 4-13
To log on to Administrator mode ................................................. 4-14
4.4 User Authentication (User Mode) .................................................. 4-16
Changing the User Password ...................................................... 4-16
To change the user password ..................................................... 4-16
Checking the User Registration Information ................................ 4-17
4.5 Account Track (User Mode) ........................................................... 4-18
To check the account track information ...................................... 4-18
4.6 Address Book .................................................................................. 4-19
Registering New Destinations ...................................................... 4-19
To register new destinations ........................................................ 4-22
Editing abbreviated destinations .................................................. 4-23
Deleting the Address Book .......................................................... 4-23
4.7 Group Destination ........................................................................... 4-24
To register group destinations ..................................................... 4-24
4.8 Program Registration ..................................................................... 4-26
To register new destinations ........................................................ 4-33
4.9 Temporary One-Touch Registration ............................................. 4-35
To register temporary destinations .............................................. 4-35
4.10 Subject Registration ....................................................................... 4-37
To register the subject ................................................................. 4-38
4.11 Text Registration ............................................................................ 4-39
To register text ............................................................................. 4-40
4.12 Administrator Mode ........................................................................ 4-41
Basic Operation ........................................................................... 4-41
4.13 Network TWAIN (Administrator Mode) ......................................... 4-42
Setting the Operation Lock Time for TWAIN ................................ 4-42
4.14 User Authentication (Administrator Mode) .................................. 4-43
User Registration ......................................................................... 4-43
To register a user ......................................................................... 4-44
Checking or Changing the Registered User Information ............. 4-46
C250 x-11

Introduction
To check or change the registered user information ....................4-47
To delete a registered user ...........................................................4-49
Default Function Permission .........................................................4-50
To specify the default function permission settings .....................4-50
4.15 Account Track Registration (Administrator Mode) ......................4-51
Account Track Registration ..........................................................4-51
To register an account ..................................................................4-52
Checking or Changing the Registered Account Information ........4-54
To check or change the registered account information ..............4-54
To delete registered accounts ......................................................4-56
4.16 Application Registration .................................................................4-57
Registering an Application ............................................................4-57
New Registration Items of an Application .....................................4-59
To register an application .............................................................4-61
Items that can Be Specified in Edit Application ............................4-64
To edit a registered application ....................................................4-69
To delete a registered application ................................................4-71
4.17 Prefix/Suffix ......................................................................................4-72
To register prefixes and suffixes ...................................................4-72
4.18 Import/Export ...................................................................................4-74
Importing .......................................................................................4-74
Exporting .......................................................................................4-74
4.19 Other .................................................................................................4-75
4.20 TCP/IP ...............................................................................................4-76
TCP/IP ...........................................................................................4-77
IP Address Filtering .......................................................................4-79
4.21 NetWare ............................................................................................4-80
NetWare Status .............................................................................4-81
4.22 IPP .....................................................................................................4-82
4.23 FTP ....................................................................................................4-84
FTP TX ..........................................................................................4-84
FTP Server ....................................................................................4-85
4.24 SNMP ................................................................................................4-86
4.25 SMB ..................................................................................................4-87
WINS Setting ................................................................................4-87
Client Setting ................................................................................4-88
Print Setting ..................................................................................4-89
4.26 AppleTalk .........................................................................................4-90
4.27 Bonjour Setting ................................................................................4-91
x-12 C250

Introduction
4.28 LDAP Setting ................................................................................... 4-92
LDAP Setting ................................................................................ 4-92
LDAP Server Registration ............................................................ 4-93
4.29 E-Mail Setting .................................................................................. 4-96
E-Mail RX (POP) ........................................................................... 4-96
E-Mail TX (SMTP) ......................................................................... 4-97
4.30 SSL/TLS ......................................................................................... 4-100
SSL/TLS Setting ......................................................................... 4-102
To create a certificate ................................................................ 4-103
SSL/TLS Setting — Install a Certificate ..................................... 4-105
Set an Encryption Strength ........................................................ 4-106
Remove a Certificate .................................................................. 4-107
Set Mode using SSL .................................................................. 4-108
Processing Mode ....................................................................... 4-109
To specify the mode using SSL ................................................. 4-109
4.31 Authentication ............................................................................... 4-110
User Authentication/Account Track ........................................... 4-110
To specify the user authentication and account track
settings ....................................................................................... 4-111
Auto Logout ............................................................................... 4-112
4.32 OpenAPI ......................................................................................... 4-113
4.33 TCP Socket Setting ...................................................................... 4-114
To specify the TCP socket settings ........................................... 4-115
5 Scan Function Troubleshooting
5.1 Error List ............................................................................................ 5-2
6 Appendix
6.1 Product Specifications ..................................................................... 6-2
Scanning Functions ....................................................................... 6-2
Network Function ........................................................................... 6-3
6.2 Entering text ...................................................................................... 6-5
To type text .................................................................................... 6-7
List of Available Characters ........................................................... 6-7
6.3 Glossary ............................................................................................. 6-8
6.4 Index ................................................................................................ 6-14
C250 x-13
About This Manual
This User’s Guide covers the bizhub C250 network and scanning functions.
This section introduces the structure of the manual and notations used for
product names, etc.
This manual is intended for users who understand the basic operations of
computers and the machine. For operating procedures of the Windows or
Macintosh operating system and application programs, refer to the respective manuals.
Structure of the Manual
This manual consists of the following chapters.
Chapter 1 Before Using the Scan Functions
Chapter 2 Scanning Documents
Chapter 3 Specifying Settings From the Control Panel
Chapter 4 Specifying Settings Using PageScope Web Connection
Chapter 5 Scan Function Troubleshooting
Chapter 6 Appendix
Lists the product specifications and the characters that can be entered from
the control panel.
Introduction
Notation
Product Name Notation in the Manual
bizhub C250 This machine, C250
Microsoft Windows 98 Windows 98
Microsoft Windows Me Windows Me
Microsoft Windows NT 4.0 Windows NT 4.0
Microsoft Windows 2000 Windows 2000
Microsoft Windows XP Windows XP
When the operating systems above are written
together
Windows 98/Me
Windows NT 4.0/2000/XP
Windows 98/Me/NT 4.0/2000/XP
Screens, Windows and Dialog Boxes
The touch panel screens and PageScope Web Connection windows and dialog boxes that appear in this manual show a machine with optional ADF (automatic document feeder) DF-601 installed.
x-14 C250
Introduction
Explanation of Manual Conventions
Note
Text highlighted in this manner
contains references and supplemental
information concerning operating
procedures and other descriptions.
We recommend that this information
be read carefully.
[]
Names highlighted as shown above
indicate keys on the control panel
and buttons in the touch panel.
Touch panel screens are shown to
check the actual display.
Reminder
Text highlighted in this manner
indicates operation precautions.
Carefully read and observe this
type of information.
Detail
Text highlighted in this manner
provides more detailed information
concerning operating procedures or
references to sections containing
additional information. If necessary,
refer to the indicated sections.
Titles indicate the contents of the section.
Basic Copy Operations
3.6 Selecting a Paper Setting
The paper size can be selected automaticall y according to the document
size or it can be specified manually. Specify the paper si ze according to the
corresponding procedure, depending on the desired copy settings.
Note
The default setting is Auto Paper Select.
Automatically Selecting the Paper Size (Au to Paper Select Setting)
The size of the loaded document is detected, and copies are produced using
paper of the same size.
1 In the Basic screen, touch [P aper].
The Paper screen appears.
Reminder
Be careful that your fingers are not pinched when the front door is closed.
Detail
For details on the positions of paper misfee ds, refer to Paper Misfeed Indications on page5-7.
CAUTION
Metallic parts on the inside of the upper cover are very hot.
C250 3-31
Touching any part other than the paper may result in
burns.
3
Basic Copy Operations Chapter 3
WARNING , CAUTION
Text highlighted in this manner indicates precautions to ensure safe use of this machine.
"Warning" indicates instructions that, when not observed, may result in fatal or critical injuries.
"Caution" indicates instructions that, when not observed, may result in serious injuries or
property damage.
(The page shown above is an example only.)
C250 x-15

User’s Guides
The following User’s Guides have been prepared for this machine.
User’s Guide [Copy Operations]
This manual contains details on basic operations and the operating procedures for the various copy functions.
- Refer to this User’s Guide for details on operating procedures for copy
functions, including precautions on installation/use, turning the machine
on/off, loading paper, and troubleshooting operations such as clearing
paper misfeeds.
User’s Guide [Network Scanner Operations] <this manual>
This manual contains details on specifying network settings for standard
equipment and on operations for scanning functions.
- Refer to this User’s Guide for details on operating procedures for network
functions and for using Scan to E-Mail, Scan to FTP and Scan to SMB.
User’s Guide [Box Operations]
This manual contains details on operating procedures for using the boxes.
- Refer to this User’s Guide for details on operating procedures for using
the boxes on the hard disk.
Introduction
User’s Guide [Enlarge Display Operations]
This manual contains details on operating procedures for using copy, network scanner and fax functions in Enlarge Display mode.
- Refer to this User’s Guide for details on operating procedures in Enlarge
Display mode.
User’s Guide [FK-502 Facsimile Operations]
This manual contains details on operating procedures for faxing.
- Refer to this User’s Guide for details on operating procedures for fax
functions when the fax kit is installed.
User’s Guide [Network Facsimile Operations]
This manual contains details on operating procedures for network faxing.
- Refer to this User’s Guide for details on operating procedures for using
the network fax functions (Internet faxing, SIP faxing and IP address faxing).
x-16 C250

Introduction
User’s Guide [Print Operations]
This manual contains details on operating procedures using the standard
built-in printer controller.
- For details on the printing functions, refer to User’s Guide (PDF file) on
Quick Guide [Print Operations]
This manual contains details on operating procedures using the standard
built-in printer controller.
- Refer to this Quick Guide for basic operating procedures for the printing
User Software CD-ROM.
functions.
C250 x-17

Introduction
x-18 C250

1
Before Using the Scan
Functions
Before Using the Scan Functions Chapter 1

1
Before Using the Scan Functions
1 Before Using the Scan Functions
1.1 Environment Required for Using the Scan Functions
The following conditions are required to use the network and scanning functions of this machine.
- The machine is connected to the network. (required)
The functions can be used over a TCP/IP network. For details on the connection, refer to “Connecting to the Network” on page 1-11. Also, network parameters such as the IP address of this machine must be
specified in order to use the machine on the network. For details, refer to
“Settings for Using Network/Scanning Functions” on page 1-8.
- The driver software is installed on the computer.
In order to use this machine as a scanner, the dedicated
KONICA MINOLTA TWAIN must be installed. For details, refer to the
Before Using the Scan Functions Chapter 1
TWAIN driver manual that is on the User Software CD-ROM.
1-2 C250
Before Using the Scan Functions
1.2 Available Scanning Functions
“Scanning” refers to the operation of reading the image of a document fed
through the ADF (optional) or placed on the original glass. The scanning
functions can be used to temporarily store the scanned data in the internal
memory of the machine and transmit the data in an e-mail message over the
network or upload the data to a file server.
In addition, the data can be stored on the internal hard disk of this machine.
This function can be used from the Box mode, which is described in the User’s Guide [Box Operations].
Furthermore, this machine can be used simply as a scanner.
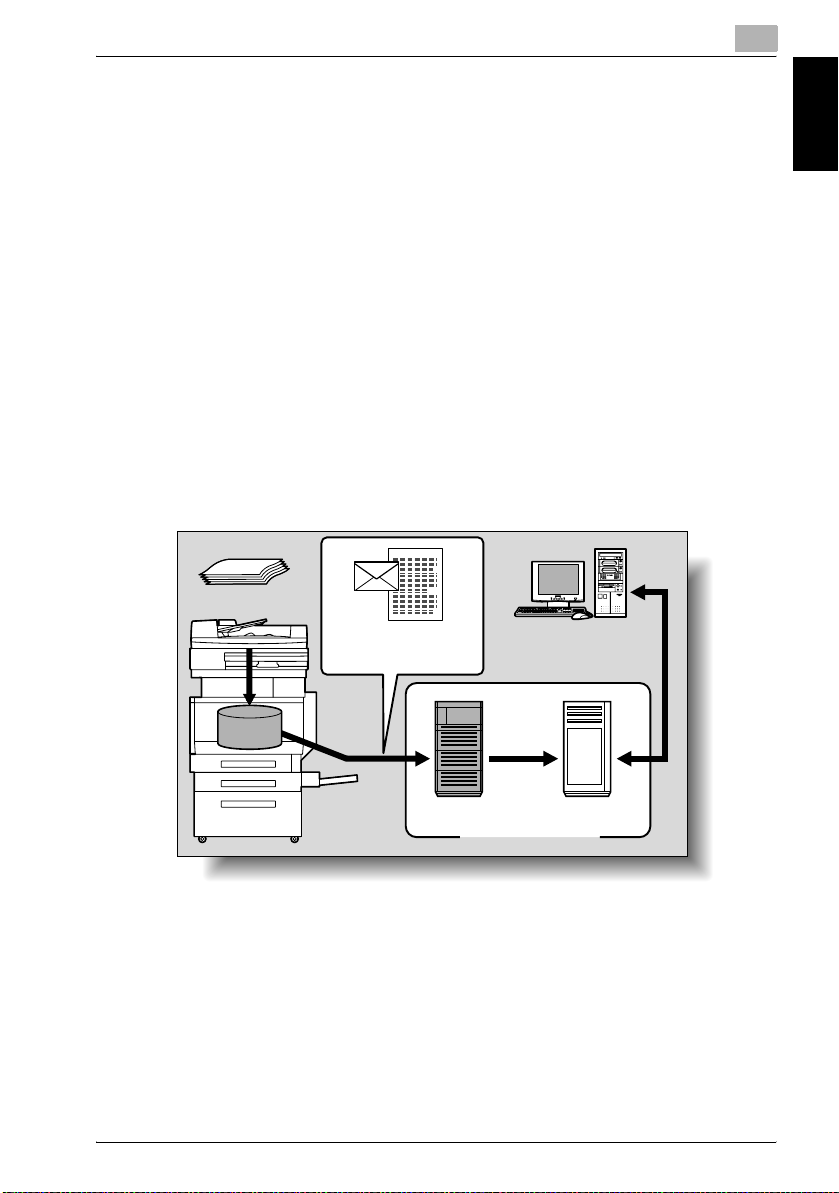
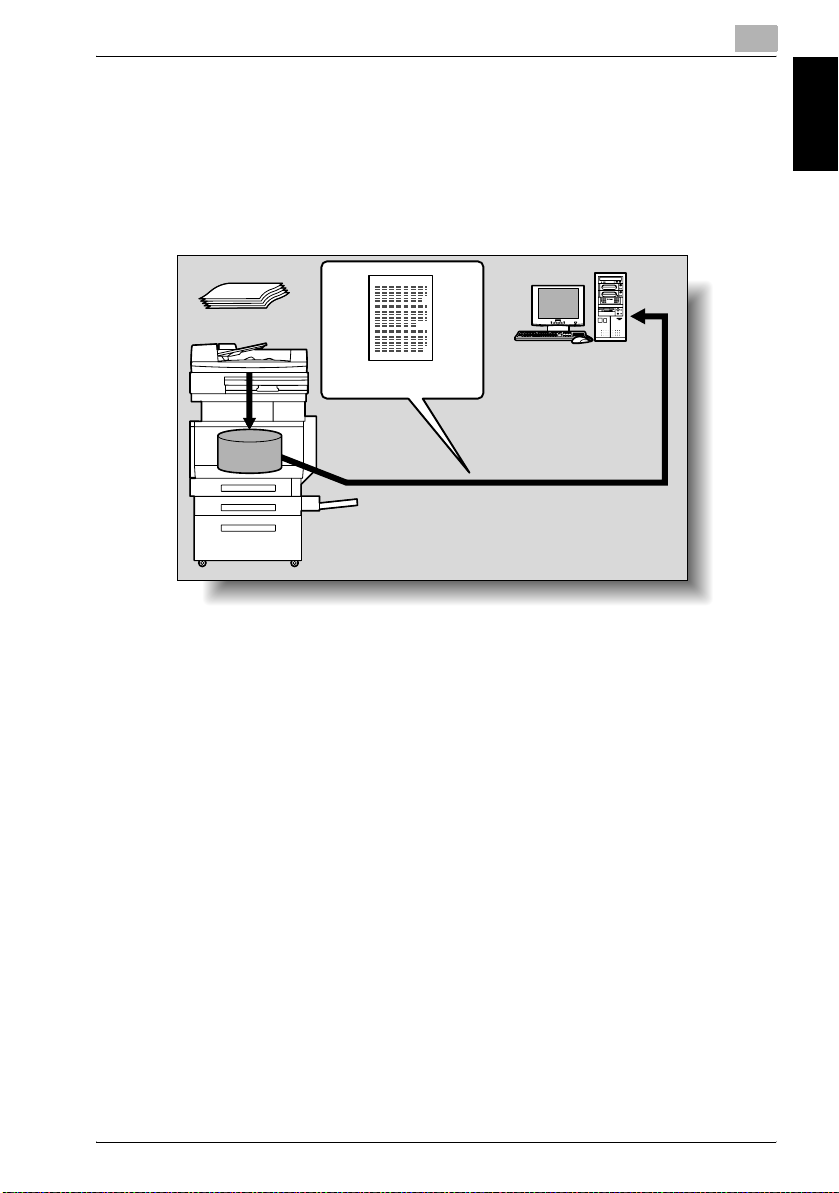
Sending the Scanned Data in an E-Mail Message
The scanned data can be sent to a specified e-mail address. The destination
is specified from the touch panel of this machine, and the scanned data is
sent as an e-mail attachment.
For details, refer to “Sending Data in an E-Mail Message (Scan to E-Mail)” on
page 2-6.
Original
Machine
1
Before Using the Scan Functions Chapter 1
E-mail and scan data
Memory
SMTP server POP server
C250 1-3
E-mail reception
Internet
1
Before Using the Scan Functions
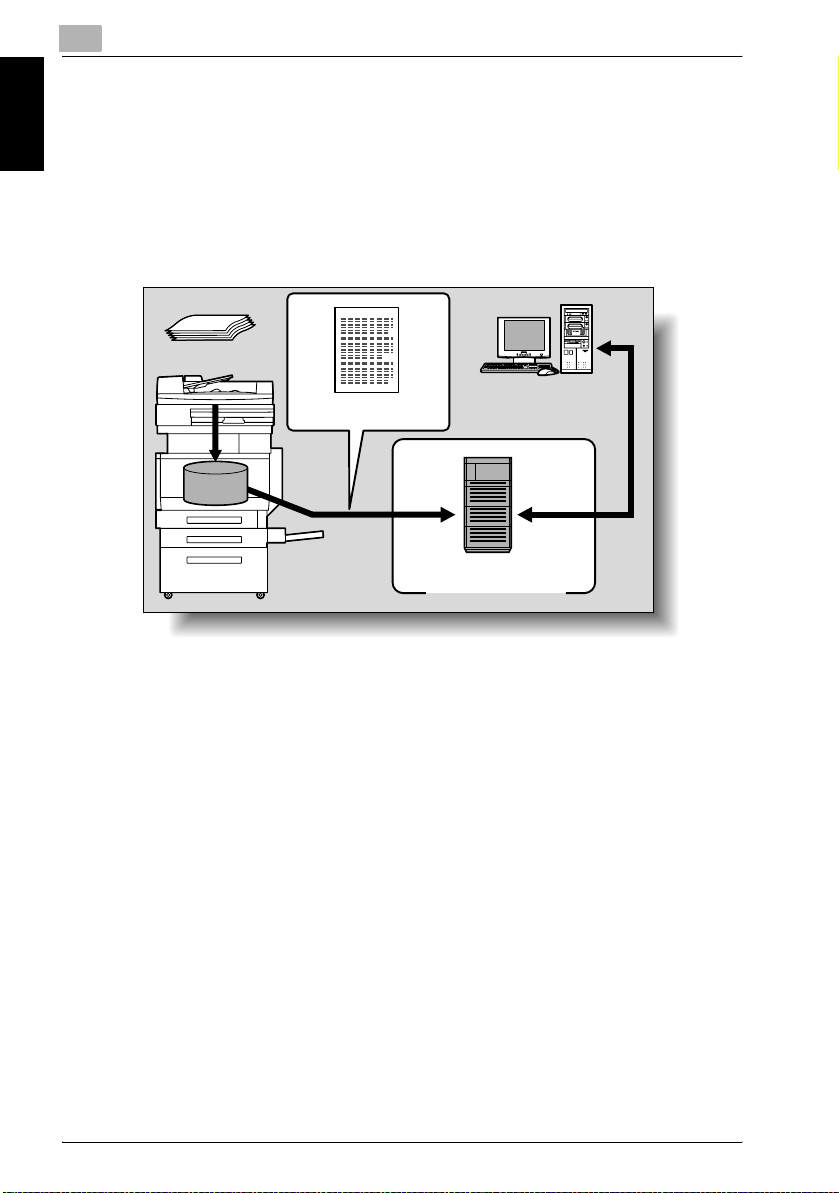
Sending the Scanned Data as Files (FTP)
The scanned data is uploaded to a specified FTP server. The FTP server address, login password, and other information are entered from the touch
panel of this machine.
The data files uploaded to the FTP server can be downloaded from a computer on the network.
For details, refer to “Sending Data to a Server (Scan to FTP)” on page 2-19.
Original
Machine
Before Using the Scan Functions Chapter 1
Memory
Scan data
Download
FTP server
Internet
1-4 C250
Before Using the Scan Functions
Sending the Scanned Data to a Computer on the Network (SMB)
The scanned data can be sent to a shared folder on a specified computer.
The name of the destination computer, login password, and other information are entered from the touch panel of this machine.
For details, refer to “Sending Data to a PC on the Network (Scan to SMB)”
on page 2-31.
Original
Machine
1
Scan data
Memory
Save to a shared folder
Before Using the Scan Functions Chapter 1
C250 1-5
1
Before Using the Scan Functions Chapter 1
Before Using the Scan Functions
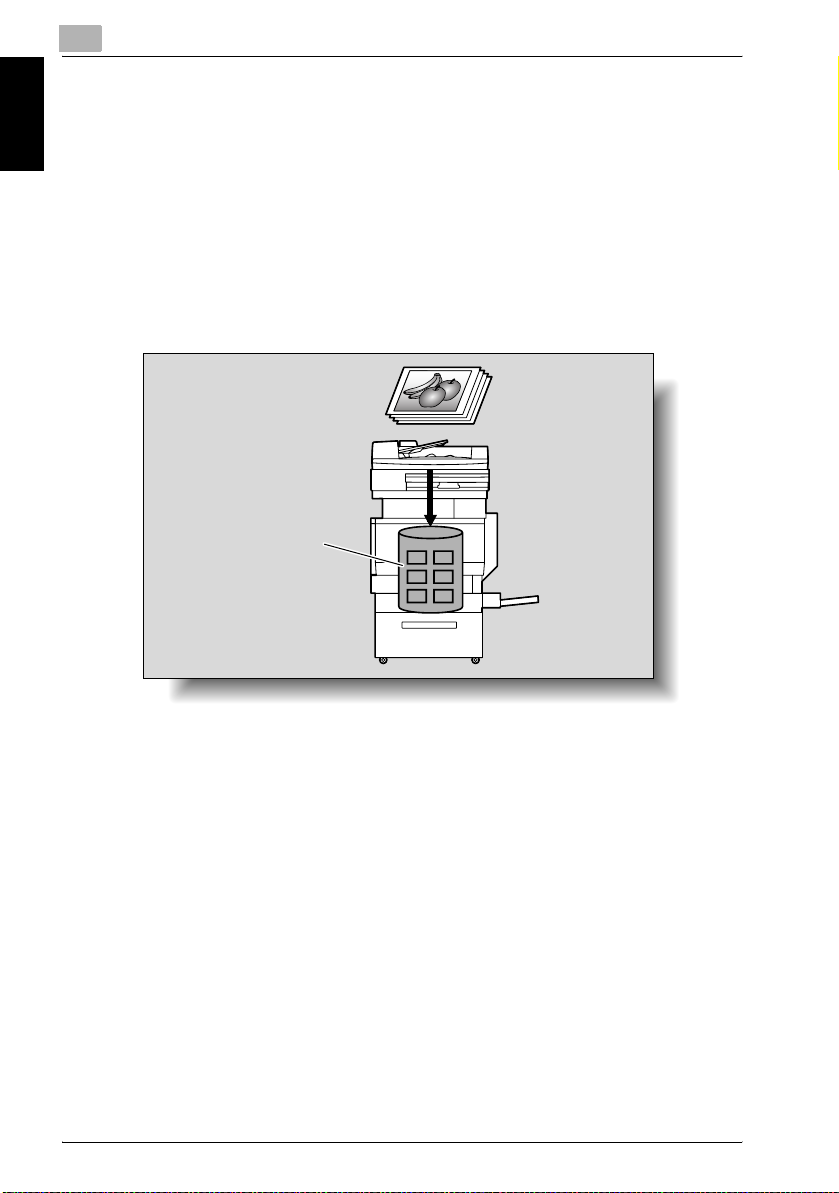
Saving the Scanned Data in Boxes
The scanned data can be saved in boxes created on the machine’s internal
hard disk. The data can be used in other applications. The file name can be
entered from the touch panel of the machine.
In addition, if the scanned data is saved in “Annotation User box”, you can
deliver it over the Internet by adding any domain name and the delivery date
and time.
For the procedure to save in an annotation user box, refer to “Annotation
(Application)” on page 2-63. For saving other data in a box or reusing the
data that has been saved, refer to User’s Guide “Box Operations”.
Machine
Hard disk
1-6 C250
Before Using the Scan Functions
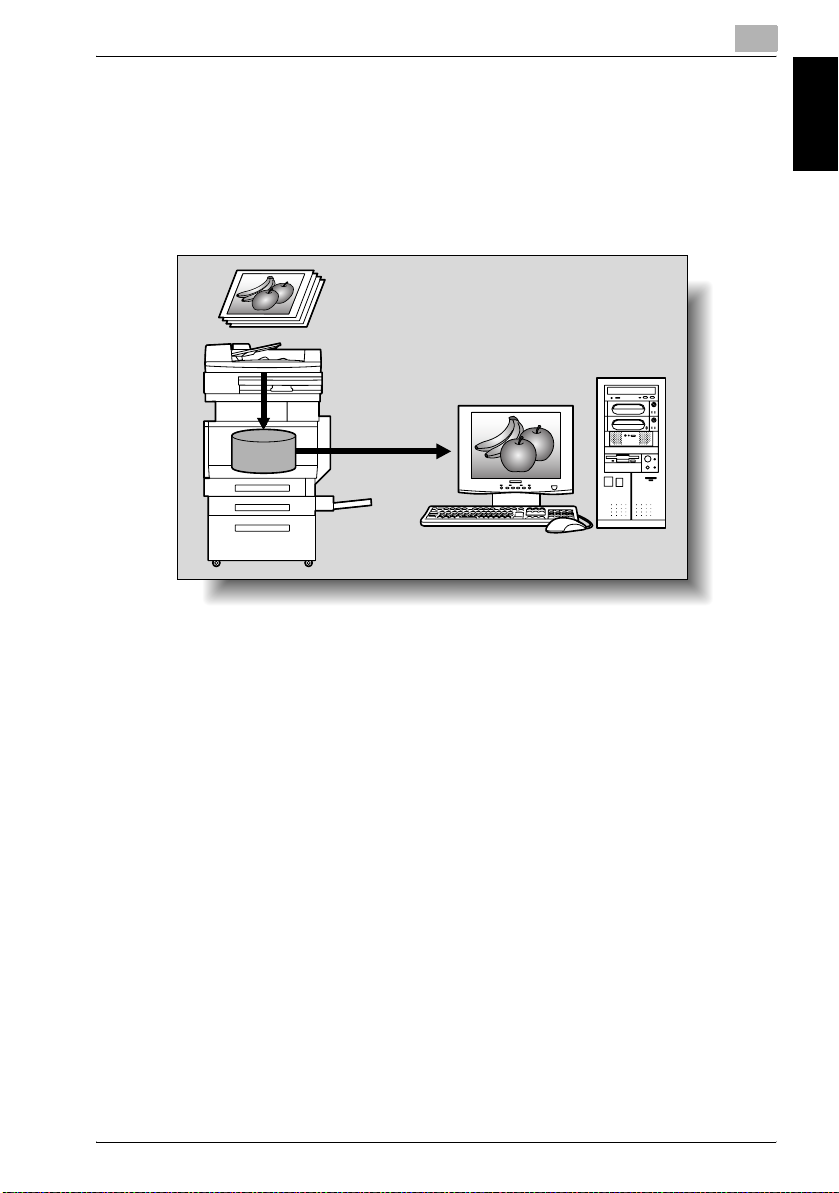
Using the Machine as a Scanner
This machine can be used as a scanner. The scanner can be controlled from
a computer connected to the network, and the scanned image can be loaded
into an application on the computer to be processed.
For details, refer to the TWAIN driver manual that is on the User Software CDROM.
Original
Machine
Memory
1
Before Using the Scan Functions Chapter 1
C250 1-7

1
Before Using the Scan Functions
1.3 Settings for Using Network/Scanning Functions
It is recommended that the settings described below be specified before using the network/scanning functions. The network settings described in
“Specifying Network Settings” must be specified first. Set other items as
necessary.
!
Detail
For details on specifying network settings, refer to the chapters listed below.
“TCP/IP Settings” on page 3-48
“E-Mail TX (SMTP) Settings” on page 3-88
“4 Specifying Settings Using PageScope Web Connection”
Specifying Network Settings
An IP address must be assigned to the machine and settings such as the
Before Using the Scan Functions Chapter 1
SMTP server must be specified to use the machine on the network. Be sure
to set them.
There are two methods for specifying settings. One method is to specify the
settings from the touch panel of this machine. The other method is to use PageScope Web Connection from a Web browser on a computer on the network.
Registering Destinations and Specifying Their Settings
The destinations (recipients) of scanned data must be registered.
The following registration methods are available.
- Register from the touch panel of the machine.
- Use PageScope Web Connection from a computer on the network.
The following types of destinations can be registered.
Type Description
Abbreviated Destination The destination can be selected with one button.
Group Multiple destinations can be registered in groups. E-mail, FTP,
SMB, and box destinations can be registered together in a single
group.
2
Note
The destination can also be entered before scanning. This is called “direct input”. For details, refer to “Entering the Addresses Directly” on
page 2-16.
1-8 C250
Before Using the Scan Functions
!
Detail
For details on registering destinations and specifying settings, refer to the
sections listed below.
“Registering Abbreviated Destinations” on page 3-10
“Registering Group Destinations” on page 3-22
Setting the From Address
To perform Scan to E-Mail, the From address must be registered. The From
address is the address that indicates the sender when data is sent. Normally,
it is recommended that the e-mail address of administrator registration be
used.
If the e-mail address of administrator registration is not specified, the sender
e-mail address must be entered for each Scan to E-mail operation. Note that
Scan to E-Mail is not possible if the From address is not entered.
1
2
Note
When the user authentication setting is enabled, the e-mail address that
is specified for each user becomes the From address.
Specifying the Scan Settings
The following scan settings can be specifying when scanning a document.
These settings are specified from the touch panel of the machine.
Item Description
File Type Sets the file type to be saved.
Resolution Sets the scan resolution.
Simplex/Duplex Selects whether to scan one side of the document or both sides.
Original Type Sets the type of image to be scanned.
Scan Size Sets the size to be scanned.
Color Sets the color of the scanned document.
Background Removal Adjusts the density of the background (blank areas) of the document.
Original Setting Specifies the type and characteristics of the loaded document.
Application Provides functions for adjusting the print image, for example, for scan-
ning books and for erasing the surrounding area.
Before Using the Scan Functions Chapter 1
C250 1-9

1
Before Using the Scan Functions
!
Detail
For details on the scan settings, refer to “Specifying the Scan Settings”
on page 2-42.
Specifying Program Settings
The destination and scan settings can be registered together as a single program. This is convenient for frequently scanning documents and sending
data under the same conditions.
These settings are specified from the touch panel of the machine.
!
Detail
For details, refer to “Registering Program Destinations” on page 3-24.
Before Using the Scan Functions Chapter 1
Specifying Default Scan Settings
The settings that are selected when [Scan] in the control panel is touched
can be specified.
!
Detail
For details, refer to “Setting the Save Format of the Data to Be Scanned”
on page 3-35.
1-10 C250
Before Using the Scan Functions
1.4 Connecting to the Network
The machine can be connected to the network.
2
Reminder
The machine can be connected via a parallel or USB connection (optional). However, be sure to connect to the network to use the scanner function.
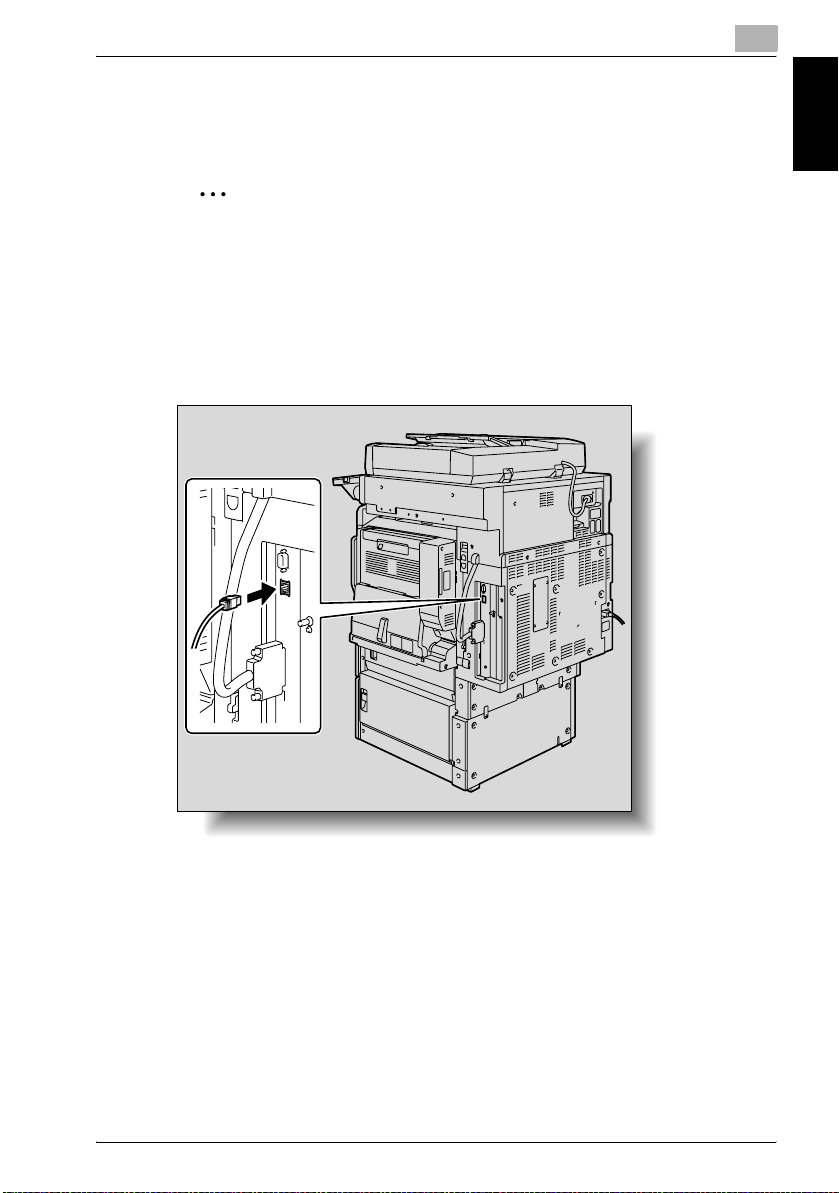
Network Connection
Connect a UTP cable (category 5 or later recommended) from the network to
the Ethernet connector on the machine.
1
Before Using the Scan Functions Chapter 1
C250 1-11
 Loading...
Loading...