Page 1

NBG-318S
Powerline Ethernet Series
User’s Guide
Version 3.60
6/2007
Edition 1
DEFAULT LOGIN
IP Address http://192.168.1.1
Password 1234
www.zyxel.com
Page 2

Page 3
About This User's Guide
About This User's Guide
Intended Audience
This manual is intended for people who want to configure the NBG-318S using the web
configurator. You should have at least a basic knowledge of TCP/IP networking concepts and
topology.
Related Documentation
• Quick Start Guide
The Quick Start Guide is designed to help you get up and running right away. It contains
information on setting up your network and configuring for Internet access.
• Web Configurator Online Help
Embedded web help for descriptions of individual screens and supplementary
information.
" It is recommended you use the web configurator to configure the NBG-318S.
• Supporting Disk
Refer to the included CD for support documents.
• ZyXEL Web Site
Please refer to www.zyxel.com for additional support documentation and product
certifications.
User Guide Feedback
Help us help you. Send all User Guide-related comments, questions or suggestions for
improvement to the following address, or use e-mail instead. Thank you!
The Technical Writing Team,
ZyXEL Communications Corp.,
6 Innovation Road II,
Science-Based Industrial Park,
Hsinchu, 300, Taiwan.
E-mail: techwriters@zyxel.com.tw
NBG-318S User’s Guide
3
Page 4
Document Conventions
Document Conventions
Warnings and Notes
These are how warnings and notes are shown in this User’s Guide.
1 Warnings tell you about things that could harm you or your device.
" Notes tell you other important information (for example, other things you may
need to configure or helpful tips) or recommendations.
Syntax Conventions
• The NBG-318S may be referred to as the “NBG-318S”, the “device”, the “product” or the
“system” in this User’s Guide.
• Product labels, screen names, field labels and field choices are all in bold font.
• A key stroke is denoted by square brackets and uppercase text, for example, [ENTER]
means the “enter” or “return” key on your keyboard.
• “Enter” means for you to type one or more characters and then press the [ENTER] key.
“Select” or “choose” means for you to use one of the predefined choices.
• A right angle bracket ( > ) within a screen name denotes a mouse click. For example,
Maintenance > Log > Log Setting means you first click Maintenance in the navigation
panel, then the Log sub menu and finally the Log Setting tab to get to that screen.
• Units of measurement may denote the “metric” value or the “scientific” value. For
example, “k” for kilo may denote “1000” or “1024”, “M” for mega may denote “1000000”
or “1048576” and so on.
4
NBG-318S User’s Guide
Page 5

Document Conventions
Icons Used in Figures
Figures in this User’s Guide may use the following generic icons. The NBG-318S icon is not
an exact representation of your device.
NBG-318S Computer Notebook computer
Server DSLAM Firewall
Telephone Switch Router
Modem
NBG-318S User’s Guide
5
Page 6

Safety Warnings
Safety Warnings
1 For your safety, be sure to read and follow all warning notices and instructions.
• Do NOT use this product near water, for example, in a wet basement or near a swimming
pool.
• Do NOT expose your device to dampness, dust or corrosive liquids.
• Do NOT store things on the device.
• Do NOT install, use, or service this device during a thunderstorm. There is a remote risk
of electric shock from lightning.
• Connect ONLY suitable accessories to the device.
• Do NOT open the device or unit. Opening or removing covers can expose you to
dangerous high voltage points or other risks. ONLY qualified service personnel should
service or disassemble this device. Please contact your vendor for further information.
• Make sure to connect the cables to the correct ports.
• Place connecting cables carefully so that no one will step on them or stumble over them.
• Always disconnect all cables from this device before servicing or disassembling.
• Use ONLY an appropriate power adaptor or cord for your device.
• Connect the power adaptor or cord to the right supply voltage (for example, 110V AC in
North America or 230V AC in Europe).
• Do NOT allow anything to rest on the power adaptor or cord and do NOT place the
product where anyone can walk on the power adaptor or cord.
• Do NOT use the device if the power adaptor or cord is damaged as it might cause
electrocution.
• If the power adaptor or cord is damaged, remove it from the power outlet.
• Do NOT attempt to repair the power adaptor or cord. Contact your local vendor to order a
new one.
• Do not use the device outside, and make sure all the connections are indoors. There is a
remote risk of electric shock from lightning.
• Do NOT obstruct the device ventilation slots, as insufficient airflow may harm your
device.
• Antenna Warning! This device meets ETSI and FCC certification requirements when
using the included antenna(s). Only use the included antenna(s).
• If you wall mount your device, make sure that no electrical lines, gas or water pipes will
be damaged.
6
This product is recyclable. Dispose of it properly.
NBG-318S User’s Guide
Page 7
Safety Warnings
NBG-318S User’s Guide
7
Page 8

Safety Warnings
8
NBG-318S User’s Guide
Page 9

Contents Overview
Contents Overview
Introduction ............................................................................................................................27
Getting to Know Your NBG-318S .............................................................................................. 29
Introducing the Web Configurator .............................................................................................. 33
Connection Wizard .................................................................................................................... 45
Wireless Tutorial ........................................................................................................................ 61
Network ...................................................................................................................................67
Wireless LAN ............................................................................................................................. 69
WAN .......................................................................................................................................... 89
LAN ............................................................................................................................................ 99
HomePlug AV .......................................................................................................................... 105
DHCP .......................................................................................................................................111
Network Address Translation (NAT) .........................................................................................115
Dynamic DNS .......................................................................................................................... 125
Security .................................................................................................................................129
Firewall .................................................................................................................................... 131
Content Filtering ...................................................................................................................... 137
Management .........................................................................................................................143
Static Route Screens ............................................................................................................... 145
Bandwidth Management .......................................................................................................... 149
Remote Management ..............................................................................................................161
Universal Plug-and-Play (UPnP) ............................................................................................. 167
Maintenance and Troubleshooting .....................................................................................179
System ..................................................................................................................................... 181
Logs ......................................................................................................................................... 185
Tools ........................................................................................................................................ 199
Configuration Mode ................................................................................................................. 205
Sys Op Mode ........................................................................................................................... 207
Troubleshooting ....................................................................................................................... 209
Appendices and Index ......................................................................................................... 217
NBG-318S User’s Guide
9
Page 10

Contents Overview
10
NBG-318S User’s Guide
Page 11

Table of Contents
Table of Contents
About This User's Guide ..........................................................................................................3
Document Conventions............................................................................................................4
Safety Warnings........................................................................................................................6
Contents Overview ...................................................................................................................9
Table of Contents....................................................................................................................11
List of Figures .........................................................................................................................19
List of Tables...........................................................................................................................23
Part I: Introduction................................................................................. 27
Chapter 1
Getting to Know Your NBG-318S...........................................................................................29
1.1 Overview .............................................................................................................................. 29
1.1.1 Secure Broadband Internet Access ........................................................................... 29
1.1.2 Wireless LAN Application ........................................................................................... 29
1.1.3 HomePlug AV ............................................................................................................. 30
1.2 Ways to Manage the NBG-318S ......................................................................................... 30
1.3 Good Habits for Managing the NBG-318S .......................................................................... 31
1.4 LEDs .................................................................................................................................... 31
Chapter 2
Introducing the Web Configurator ........................................................................................33
2.1 Web Configurator Overview ................................................................................................. 33
2.2 Accessing the Web Configurator ......................................................................................... 33
2.3 Resetting the NBG-318S .....................................................................................................35
2.3.1 Procedure to Use the Reset Button ........................................................................... 35
2.4 Navigating the Web Configurator ...................................................................................... 35
2.4.1 The Status Screen ..................................................................................................... 35
2.4.2 Navigation Panel ........................................................................................................ 38
2.4.3 Summary: Any IP Table .............................................................................................. 40
2.4.4 Summary: Bandwidth Management Monitor ........................................................... 41
2.4.5 Summary: DHCP Table ........................................................................................... 41
2.4.6 Summary: Packet Statistics ..................................................................................... 42
NBG-318S User’s Guide
11
Page 12

Table of Contents
2.4.7 Summary: Wireless Station Status ......................................................................... 43
2.4.8 Summary: My HomePlug Network Status .................................................................. 43
Chapter 3
Connection Wizard .................................................................................................................45
3.1 Wizard Setup ....................................................................................................................... 45
3.2 Connection Wizard: STEP 1: System Information ............................................................... 46
3.2.1 System Name ............................................................................................................. 46
3.2.2 Domain Name ............................................................................................................ 47
3.3 Connection Wizard: STEP 2: Wireless LAN ........................................................................ 47
3.3.1 Basic (WEP) Security ................................................................................................. 49
3.3.2 Extend (WPA-PSK or WPA2-PSK) Security ............................................................... 50
3.4 Connection Wizard: STEP 3: Internet Configuration ........................................................... 50
3.4.1 Ethernet Connection .................................................................................................. 51
3.4.2 PPPoE Connection .................................................................................................... 51
3.4.3 PPTP Connection ....................................................................................................... 52
3.4.4 Your IP Address ......................................................................................................... 54
3.4.5 WAN IP Address Assignment ..................................................................................... 54
3.4.6 IP Address and Subnet Mask ..................................................................................... 55
3.4.7 DNS Server Address Assignment .............................................................................. 55
3.4.8 WAN IP and DNS Server Address Assignment ......................................................... 56
3.4.9 WAN MAC Address .................................................................................................... 57
3.5 Connection Wizard: STEP 4: Bandwidth management ....................................................... 58
3.6 Connection Wizard Complete .............................................................................................. 58
Chapter 4
Wireless Tutorial .....................................................................................................................61
4.1 Example Parameters ........................................................................................................... 61
4.2 Configuring the AP .............................................................................................................. 61
4.3 Configuring the Wireless Client ........................................................................................... 63
4.3.1 Connecting to a Wireless LAN ................................................................................... 63
Part II: Network....................................................................................... 67
Chapter 5
Wireless LAN...........................................................................................................................69
5.1 Wireless Network Overview ................................................................................................. 69
5.2 Wireless Security Overview .................................................................................................71
5.2.1 SSID ........................................................................................................................... 71
5.2.2 MAC Address Filter .................................................................................................... 71
5.2.3 User Authentication .................................................................................................... 72
12
NBG-318S User’s Guide
Page 13

Table of Contents
5.2.4 Encryption .................................................................................................................. 72
5.3 Roaming .............................................................................................................................. 73
5.3.1 Requirements for Roaming ........................................................................................ 74
5.4 Quality of Service ................................................................................................................ 74
5.4.1 WMM QoS ..................................................................................................................75
5.5 General Wireless LAN Screen ............................................................................................ 75
5.5.1 No Security ................................................................................................................. 76
5.5.2 WEP Encryption ......................................................................................................... 77
5.5.3 WPA-PSK/WPA2-PSK ................................................................................................ 79
5.5.4 WPA/WPA2 ................................................................................................................ 80
5.6 MAC Filter ............................................................................................................................ 82
5.7 Wireless LAN Advanced Screen ......................................................................................... 83
5.8 Quality of Service (QoS) Screen ......................................................................................... 84
5.8.1 Application Priority Configuration ............................................................................... 86
Chapter 6
WAN..........................................................................................................................................89
6.1 WAN Overview .................................................................................................................... 89
6.2 WAN MAC Address ............................................................................................................. 89
6.3 Multicast .............................................................................................................................. 89
6.4 Internet Connection ............................................................................................................. 90
6.4.1 Ethernet Encapsulation .............................................................................................. 90
6.4.2 PPPoE Encapsulation ................................................................................................ 92
6.4.3 PPTP Encapsulation .................................................................................................. 94
6.5 Advanced WAN Screen ....................................................................................................... 97
Chapter 7
LAN...........................................................................................................................................99
7.1 LAN Overview ...................................................................................................................... 99
7.1.1 IP Pool Setup ............................................................................................................. 99
7.1.2 System DNS Servers ................................................................................................. 99
7.2 LAN TCP/IP ......................................................................................................................... 99
7.2.1 Factory LAN Defaults ................................................................................................. 99
7.2.2 IP Address and Subnet Mask ................................................................................... 100
7.2.3 Multicast ................................................................................................................... 100
7.2.4 Any IP ....................................................................................................................... 100
7.3 LAN IP Screen ................................................................................................................... 102
7.4 LAN IP Alias ..................................................................................................................... 102
7.5 Advanced LAN Screen ...................................................................................................... 103
Chapter 8
HomePlug AV ........................................................................................................................ 105
8.1 Overview ............................................................................................................................ 105
NBG-318S User’s Guide
13
Page 14

Table of Contents
8.2 Privacy and Powerline Adapters ........................................................................................ 106
8.2.1 Setting Up a Private Powerline Network .................................................................. 106
8.2.2 Setting Up Multiple Powerline Networks. ................................................................. 107
8.3 Configuring Your HomePlug AV Devices ........................................................................... 108
Chapter 9
DHCP...................................................................................................................................... 111
9.1 DHCP .................................................................................................................................111
9.2 DHCP Server General Screen ............................................................................................111
9.3 DHCP Server Advanced Screen .....................................................................................112
9.4 Client List Screen ...............................................................................................................113
Chapter 10
Network Address Translation (NAT).................................................................................... 115
10.1 NAT Overview ................................................................................................................115
10.2 Using NAT .........................................................................................................................115
10.2.1 Port Forwarding: Services and Port Numbers .........................................................115
10.2.2 Configuring Servers Behind Port Forwarding Example ...........................................116
10.3 General NAT Screen .........................................................................................................116
10.4 NAT Application Screen ..................................................................................................117
10.4.1 Game List Example .................................................................................................119
10.5 Trigger Port Forwarding ...................................................................................................120
10.5.1 Trigger Port Forwarding Example .......................................................................... 120
10.5.2 Two Points To Remember About Trigger Ports ...................................................... 121
10.6 NAT Advanced Screen .................................................................................................... 121
Chapter 11
Dynamic DNS ........................................................................................................................ 125
11.1 Dynamic DNS Introduction .............................................................................................. 125
11.1.1 DynDNS Wildcard .................................................................................................. 125
11.2 Dynamic DNS Screen .................................................................................................... 125
Part III: Security.................................................................................... 129
Chapter 12
Firewall...................................................................................................................................131
12.1 Introduction to ZyXEL’s Firewall .................................................................................... 131
12.1.1 What is a Firewall? ................................................................................................. 131
12.1.2 Stateful Inspection Firewall .................................................................................... 131
12.1.3 About the NBG-318S Firewall ................................................................................ 131
12.1.4 Guidelines For Enhancing Security With Your Firewall .......................................... 132
14
NBG-318S User’s Guide
Page 15

Table of Contents
12.2 Triangle Routes ............................................................................................................... 132
12.2.1 Triangle Routes and IP Alias .................................................................................. 132
12.3 General Firewall Screen ............................................................................................... 133
12.4 Services Screen ............................................................................................................. 134
Chapter 13
Content Filtering ...................................................................................................................137
13.1 Introduction to Content Filtering ...................................................................................... 137
13.2 Restrict Web Features .....................................................................................................137
13.3 Days and Times ............................................................................................................... 137
13.4 Filter Screen .................................................................................................................... 137
13.5 Schedule .......................................................................................................................... 139
13.6 Customizing Keyword Blocking URL Checking ............................................................... 140
13.6.1 Domain Name or IP Address URL Checking ......................................................... 140
13.6.2 Full Path URL Checking ......................................................................................... 140
13.6.3 File Name URL Checking ....................................................................................... 140
Part IV: Management............................................................................ 143
Chapter 14
Static Route Screens............................................................................................................145
14.1 Static Route Overview .....................................................................................................145
14.2 IP Static Route Screen ....................................................................................................145
14.2.1 Static Route Setup Screen ................................................................................... 146
Chapter 15
Bandwidth Management.......................................................................................................149
15.1 Bandwidth Management Overview ................................................................................. 149
15.2 Application-based Bandwidth Management .................................................................... 149
15.3 Subnet-based Bandwidth Management .......................................................................... 149
15.4 Application and Subnet-based Bandwidth Management ................................................. 150
15.5 Bandwidth Management Priorities ................................................................................... 150
15.6 Predefined Bandwidth Management Services ................................................................. 151
15.6.1 Services and Port Numbers ................................................................................... 152
15.7 Default Bandwidth Management Classes and Priorities .................................................. 154
15.8 Bandwidth Management General Configuration ............................................................. 154
15.9 Bandwidth Management Advanced Configuration .......................................................... 155
15.9.1 Rule Configuration with the Pre-defined Service ................................................ 156
15.9.2 Rule Configuration with the User-defined Service .............................................. 157
15.10 Bandwidth Management Monitor ................................................................................ 158
NBG-318S User’s Guide
15
Page 16

Table of Contents
Chapter 16
Remote Management............................................................................................................ 161
16.1 Remote Management Overview ...................................................................................... 161
16.1.1 Remote Management Limitations .......................................................................... 161
16.1.2 Remote Management and NAT .............................................................................. 162
16.1.3 System Timeout .................................................................................................... 162
16.2 WWW Screen ............................................................................................................... 162
16.3 Telnet ............................................................................................................................... 162
16.4 Telnet Screen ................................................................................................................... 163
16.5 FTP Screen ..................................................................................................................... 164
16.6 DNS Screen .................................................................................................................. 164
Chapter 17
Universal Plug-and-Play (UPnP).......................................................................................... 167
17.1 Introducing Universal Plug and Play ............................................................................... 167
17.1.1 How do I know if I'm using UPnP? ......................................................................... 167
17.1.2 NAT Traversal ........................................................................................................ 167
17.1.3 Cautions with UPnP ............................................................................................... 167
17.2 UPnP and ZyXEL ............................................................................................................168
17.3 UPnP Screen ................................................................................................................... 168
17.4 Installing UPnP in Windows Example .............................................................................. 169
Part V: Maintenance and Troubleshooting ........................................ 179
Chapter 18
System ...................................................................................................................................181
18.1 System Overview ............................................................................................................. 181
18.2 System General Screen ................................................................................................. 181
18.3 Time Setting Screen ........................................................................................................ 182
Chapter 19
Logs .......................................................................................................................................185
19.1 View Log ......................................................................................................................... 185
19.2 Log Settings ..................................................................................................................... 186
19.3 Log Descriptions .............................................................................................................. 189
Chapter 20
Tools.......................................................................................................................................199
20.1 Firmware Upload Screen ................................................................................................. 199
20.2 Configuration Screen ....................................................................................................... 200
20.2.1 Backup Configuration ............................................................................................. 201
16
NBG-318S User’s Guide
Page 17

Table of Contents
20.2.2 Restore Configuration ............................................................................................ 201
20.2.3 Back to Factory Defaults ........................................................................................ 202
20.3 Restart Screen ................................................................................................................. 202
Chapter 21
Configuration Mode..............................................................................................................205
Chapter 22
Sys Op Mode .........................................................................................................................207
22.1 Selecting System Operation Mode .................................................................................. 207
Chapter 23
Troubleshooting....................................................................................................................209
23.1 Power, Hardware Connections, and LEDs ...................................................................... 209
23.2 NBG-318S Access and Login .......................................................................................... 210
23.3 Internet Access .................................................................................................................211
23.4 Resetting the NBG-318S to Its Factory Defaults ............................................................. 213
23.5 Wireless Router/AP Troubleshooting ............................................................................... 213
23.6 HomePlug AV Troubleshooting ........................................................................................ 214
23.7 Advanced Features .........................................................................................................215
Part VI: Appendices and Index ........................................................... 217
Appendix A Product Specifications and Wall-Mounting Instructions ....................................219
Appendix B Pop-up Windows, JavaScripts and Java Permissions ......................................225
Appendix C IP Addresses and Subnetting ...........................................................................231
Appendix D Setting up Your Computer’s IP Address ...........................................................239
23.7.1 Verifying Settings ................................................................................................... 254
Appendix E Wireless LANs ..................................................................................................255
23.7.2 WPA(2)-PSK Application Example ......................................................................... 264
23.7.3 WPA(2) with RADIUS Application Example ........................................................... 264
Appendix F Services ............................................................................................................ 267
Appendix G Legal Information ..............................................................................................271
Appendix H Customer Support............................................................................................. 275
Index.......................................................................................................................................281
NBG-318S User’s Guide
17
Page 18

Table of Contents
18
NBG-318S User’s Guide
Page 19

List of Figures
List of Figures
Figure 1 Secure Internet Access .......................................................................................................... 29
Figure 2 WLAN Application Example ..................................................................................................... 30
Figure 3 HomePlug AV Internet Connection Example .......................................................................... 30
Figure 4 Front Panel ............................................................................................................................... 31
Figure 5 Change Password Screen ........................................................................................................ 34
Figure 6 Web Configurator Status Screen ............................................................................................. 36
Figure 7 Any IP Table ............................................................................................................................ 40
Figure 8 Summary: BW MGMT Monitor ................................................................................................. 41
Figure 9 Summary: DHCP Table ............................................................................................................ 41
Figure 10 Summary: Packet Statistics ................................................................................................... 42
Figure 11 Summary: Wireless Association List ...................................................................................... 43
Figure 12 Summary: My Homeplug Network. ......................................................................................... 43
Figure 13 Select Wizard or Advanced Mode .......................................................................................... 45
Figure 14 Select a Language ................................................................................................................. 46
Figure 15 Welcome to the Connection Wizard ....................................................................................... 46
Figure 16 Wizard Step 1: System Information ........................................................................................ 47
Figure 17 Wizard Step 2: Wireless LAN ................................................................................................. 48
Figure 18 Wizard Step 2: Basic (WEP) Security ..................................................................................... 49
Figure 19 Wizard Step 2: Extend (WPA-PSK or WPA2-PSK) Security ................................................... 50
Figure 20 Wizard Step 3: ISP Parameters. ............................................................................................. 51
Figure 21 Wizard Step 3: Ethernet Connection ...................................................................................... 51
Figure 22 Wizard Step 3: PPPoE Connection ........................................................................................ 52
Figure 23 Wizard Step 3: PPTP Connection .......................................................................................... 53
Figure 24 Wizard Step 3: Your IP Address ............................................................................................. 54
Figure 25 Wizard Step 3: WAN IP and DNS Server Addresses ............................................................. 56
Figure 26 Wizard Step 3: WAN MAC Address ........................................................................................ 57
Figure 27 Wizard Step 4: Bandwidth Management ............................................................................... 58
Figure 28 Connection Wizard Save ....................................................................................................... 59
Figure 29 Connection Wizard Complete ................................................................................................. 59
Figure 30 Network > Wireless LAN > General ....................................................................................... 62
Figure 31 Network > Wireless LAN > General ....................................................................................... 62
Figure 32 AP: Status: WLAN Station Status ........................................................................................... 63
Figure 33 ZyXEL Utility: Security Settings ............................................................................................. 64
Figure 34 ZyXEL Utility: Confirm Save ................................................................................................... 65
Figure 35 ZyXEL Utility: Link Info .......................................................................................................... 65
Figure 36 Example of a Wireless Network ............................................................................................. 69
Figure 37 Roaming Example .................................................................................................................. 74
Figure 38 Network > Wireless LAN > General ...................................................................................... 76
NBG-318S User’s Guide
19
Page 20

List of Figures
Figure 39 Network > Wireless LAN > General: No Security ................................................................... 77
Figure 40 Network > Wireless LAN > General: Static WEP ................................................................... 78
Figure 41 Network > Wireless LAN > General: WPA-PSK/WPA2-PSK .................................................. 79
Figure 42 Network > Wireless LAN > General: WPA/WPA2 ................................................................... 80
Figure 43 Network > Wireless LAN > MAC Filter ................................................................................... 82
Figure 44 Network > Wireless LAN > Advanced ....................................................................................83
Figure 45 Network > Wireless LAN > QoS ............................................................................................ 85
Figure 46 Network > Wireless LAN > QoS: Application Priority Configuration ....................................... 86
Figure 47 Network > WAN > Internet Connection: Ethernet Encapsulation ........................................... 90
Figure 48 Network > WAN > Internet Connection: PPPoE Encapsulation ............................................. 93
Figure 49 Network > WAN > Internet Connection: PPTP Encapsulation ............................................... 95
Figure 50 Network > WAN > Advanced ................................................................................................. 97
Figure 51 Any IP Example .................................................................................................................... 101
Figure 52 Network > LAN > IP ............................................................................................................. 102
Figure 53 Network > LAN > IP Alias .................................................................................................... 103
Figure 54 Network > LAN > Advanced .............................................................................................. 103
Figure 55 Expand Your Network ........................................................................................................... 105
Figure 56 Powerline Network Scenario ................................................................................................ 107
Figure 57 Two Private Powerline Networks on One Circuit .................................................................. 108
Figure 58 Network > HomePlug > Network Settings ............................................................................ 108
Figure 59 Network > HomePlug > Edit .................................................................................................110
Figure 60 Network > DHCP Server > General ................................................................................... 111
Figure 61 Network > DHCP Server > Advanced ..................................................................................112
Figure 62 Network > DHCP Server > Client List ................................................................................113
Figure 63 Multiple Servers Behind NAT Example .................................................................................116
Figure 64 Network > NAT > General ....................................................................................................116
Figure 65 Network > NAT > Application ...............................................................................................118
Figure 66 Game List Example .............................................................................................................. 120
Figure 67 Trigger Port Forwarding Process: Example .......................................................................... 121
Figure 68 Network > NAT > Advanced ................................................................................................ 122
Figure 69 Dynamic DNS ....................................................................................................................... 126
Figure 70 Using IP Alias to Solve the Triangle Route Problem ............................................................ 133
Figure 71 Security > Firewall > General l ............................................................................................. 133
Figure 72 Security > Firewall > Services ............................................................................................. 135
Figure 73 Security > Content Filter > Filter .......................................................................................... 138
Figure 74 Security > Content Filter > Schedule .................................................................................... 139
Figure 75 Example of Static Routing Topology ..................................................................................... 145
Figure 76 Management > Static Route > IP Static Route ..................................................................... 146
Figure 77 Management > Static Route > IP Static Route: Static Route Setup ..................................... 147
Figure 78 Subnet-based Bandwidth Management Example ................................................................ 150
Figure 79 Management > Bandwidth MGMT > General .................................................................... 154
Figure 80 Management > Bandwidth MGMT > Advanced .................................................................. 155
Figure 81 Management > Bandwidth MGMT > Advanced: Rule Configuration ................................... 157
20
NBG-318S User’s Guide
Page 21

List of Figures
Figure 82 Management > Bandwidth MGMT > Advanced: User-defined Service Rule Configuration 158
Figure 83 Management > Bandwidth MGMT > Monitor ...................................................................... 159
Figure 84 Management > Remote MGMT > WWW ............................................................................ 162
Figure 85 Telnet Configuration on a TCP/IP Network ........................................................................... 163
Figure 86 Management > Remote MGMT > Telnet ............................................................................. 163
Figure 87 Management > Remote MGMT > FTP ................................................................................ 164
Figure 88 Management > Remote MGMT > DNS ............................................................................... 165
Figure 89 Management > UPnP > General .........................................................................................168
Figure 90 Add/Remove Programs: Windows Setup: Communication .................................................. 169
Figure 91 Add/Remove Programs: Windows Setup: Communication: Components ............................ 170
Figure 92 Network Connections ........................................................................................................... 170
Figure 93 Windows Optional Networking Components Wizard ............................................................ 171
Figure 94 Networking Services ............................................................................................................. 171
Figure 95 Network Connections ........................................................................................................... 172
Figure 96 Internet Connection Properties ............................................................................................ 173
Figure 97 Internet Connection Properties: Advanced Settings ............................................................. 174
Figure 98 Internet Connection Properties: Advanced Settings: Add .................................................... 174
Figure 99 System Tray Icon .................................................................................................................. 175
Figure 100 Internet Connection Status ................................................................................................. 175
Figure 101 Network Connections ......................................................................................................... 176
Figure 102 Network Connections: My Network Places ........................................................................ 177
Figure 103 Network Connections: My Network Places: Properties: Example ...................................... 177
Figure 104 Maintenance > System > General .....................................................................................181
Figure 105 Maintenance > System > Time Setting .............................................................................. 182
Figure 106 Maintenance > Logs > View Log ....................................................................................... 185
Figure 107 Maintenance > Logs > Log Settings ..................................................................................187
Figure 108 Maintenance > Tools > Firmware ...................................................................................... 199
Figure 109 Upload Warning .................................................................................................................. 200
Figure 110 Network Temporarily Disconnected ....................................................................................200
Figure 111 Upload Error Message ........................................................................................................ 200
Figure 112 Maintenance > Tools > Configuration ................................................................................201
Figure 113 Configuration Restore Successful ...................................................................................... 202
Figure 114 Temporarily Disconnected .................................................................................................. 202
Figure 115 Configuration Restore Error ................................................................................................ 202
Figure 116 Maintenance > Tools > Restart .......................................................................................... 203
Figure 117 Maintenance > Config Mode > General ............................................................................. 205
Figure 118 Maintenance > Sys OP Mode > General ........................................................................... 207
Figure 119 System Operation Mode: Ethernet WAN ........................................................................... 207
Figure 120 System Operation Mode: HomePlug WAN ........................................................................ 208
Figure 121 Wall-mounting Example ...................................................................................................... 223
Figure 122 Masonry Plug and M4 Tap Screw .......................................................................................223
Figure 123 Pop-up Blocker ................................................................................................................... 225
Figure 124 Internet Options: Privacy .................................................................................................... 226
NBG-318S User’s Guide
21
Page 22

List of Figures
Figure 125 Internet Options: Privacy .................................................................................................... 227
Figure 126 Pop-up Blocker Settings ..................................................................................................... 227
Figure 127 Internet Options: Security ................................................................................................... 228
Figure 128 Security Settings - Java Scripting ....................................................................................... 229
Figure 129 Security Settings - Java ...................................................................................................... 229
Figure 130 Java (Sun) .......................................................................................................................... 230
Figure 131 Network Number and Host ID ............................................................................................ 232
Figure 132 Subnetting Example: Before Subnetting ............................................................................ 234
Figure 133 Subnetting Example: After Subnetting ............................................................................... 235
Figure 134 WIndows 95/98/Me: Network: Configuration ...................................................................... 240
Figure 135 Windows 95/98/Me: TCP/IP Properties: IP Address .......................................................... 241
Figure 136 Windows 95/98/Me: TCP/IP Properties: DNS Configuration .............................................. 242
Figure 137 Windows XP: Start Menu .................................................................................................... 243
Figure 138 Windows XP: Control Panel ............................................................................................... 243
Figure 139 Windows XP: Control Panel: Network Connections: Properties ......................................... 244
Figure 140 Windows XP: Local Area Connection Properties ............................................................... 244
Figure 141 Windows XP: Internet Protocol (TCP/IP) Properties .......................................................... 245
Figure 142 Windows XP: Advanced TCP/IP Properties ....................................................................... 246
Figure 143 Windows XP: Internet Protocol (TCP/IP) Properties .......................................................... 247
Figure 144 Macintosh OS 8/9: Apple Menu .......................................................................................... 248
Figure 145 Macintosh OS 8/9: TCP/IP ................................................................................................. 248
Figure 146 Macintosh OS X: Apple Menu ............................................................................................ 249
Figure 147 Macintosh OS X: Network .................................................................................................. 250
Figure 148 Red Hat 9.0: KDE: Network Configuration: Devices ......................................................... 251
Figure 149 Red Hat 9.0: KDE: Ethernet Device: General ................................................................... 252
Figure 150 Red Hat 9.0: KDE: Network Configuration: DNS ............................................................... 252
Figure 151 Red Hat 9.0: KDE: Network Configuration: Activate ......................................................... 253
Figure 152 Red Hat 9.0: Dynamic IP Address Setting in ifconfig-eth0 ................................................ 253
Figure 153 Red Hat 9.0: Static IP Address Setting in ifconfig-eth0 ................................................... 253
Figure 154 Red Hat 9.0: DNS Settings in resolv.conf ........................................................................ 254
Figure 155 Red Hat 9.0: Restart Ethernet Card .................................................................................. 254
Figure 156 Red Hat 9.0: Checking TCP/IP Properties ........................................................................ 254
Figure 157 Peer-to-Peer Communication in an Ad-hoc Network ......................................................... 255
Figure 158 Basic Service Set ............................................................................................................... 256
Figure 159 Infrastructure WLAN ........................................................................................................... 257
Figure 160 RTS/CTS ........................................................................................................................... 258
Figure 161 WPA(2)-PSK Authentication ............................................................................................... 264
22
NBG-318S User’s Guide
Page 23

List of Tables
List of Tables
Table 1 Front Panel LEDs ...................................................................................................................... 31
Table 2 Status Screen Icon Key ............................................................................................................. 36
Table 3 Web Configurator Status Screen ........................................................................................... 37
Table 4 Screens Summary .................................................................................................................... 38
Table 5 Summary: DHCP Table ............................................................................................................. 41
Table 6 Summary: Packet Statistics ...................................................................................................... 42
Table 7 Summary: Wireless Association List ......................................................................................... 43
Table 8 Summary: My Homeplug Network ............................................................................................ 44
Table 9 Wizard Step 1: System Information ........................................................................................... 47
Table 10 Wizard Step 2: Wireless LAN .................................................................................................. 48
Table 11 Wizard Step 2: Basic (WEP) Security ..................................................................................... 49
Table 12 Wizard Step 2: Extend (WPA-PSK or WPA2-PSK) Security ................................................... 50
Table 13 Wizard Step 3: ISP Parameters .............................................................................................. 51
Table 14 Wizard Step 3: PPPoE Connection ......................................................................................... 52
Table 15 Wizard Step 3: PPTP Connection ........................................................................................... 53
Table 16 Wizard Step 3: Your IP Address .............................................................................................. 54
Table 17 Private IP Address Ranges ..................................................................................................... 54
Table 18 Wizard Step 3: WAN IP and DNS Server Addresses .............................................................. 56
Table 19 Example of Network Properties for LAN Servers with Fixed IP Addresses ............................ 57
Table 20 Wizard Step 3: WAN MAC Address ........................................................................................ 57
Table 21 Wizard Step 4: Bandwidth Management ................................................................................. 58
Table 22 Types of Encryption for Each Type of Authentication ............................................................. 72
Table 23 WMM QoS Priorities ............................................................................................................... 75
Table 24 Network > Wireless LAN > General ........................................................................................ 76
Table 25 Wireless No Security ............................................................................................................... 77
Table 26 Network > Wireless LAN > General: Static WEP .................................................................... 78
Table 27 Network > Wireless LAN > General: WPA-PSK/WPA2-PSK .................................................. 79
Table 28 Network > Wireless LAN > General: WPA/WPA2 ................................................................... 81
Table 29 Network > Wireless LAN > MAC Filter .................................................................................... 82
Table 30 Network > Wireless LAN > Advanced ..................................................................................... 83
Table 31 Network > Wireless LAN > QoS .............................................................................................. 85
Table 32 Network > Wireless LAN > QoS: Application Priority Configuration ....................................... 86
Table 33 Network > WAN > Internet Connection: Ethernet Encapsulation ............................................ 91
Table 34 Network > WAN > Internet Connection: PPPoE Encapsulation .............................................. 93
Table 35 Network > WAN > Internet Connection: PPTP Encapsulation ................................................ 96
Table 36 WAN > Advanced .................................................................................................................... 98
Table 37 Network > LAN > IP .............................................................................................................. 102
Table 38 Network > LAN > IP Alias ..................................................................................................... 103
NBG-318S User’s Guide
23
Page 24

List of Tables
Table 39 Network > LAN > Advanced .................................................................................................. 104
Table 40 Network > HomePlug > Network Settings ............................................................................ 109
Table 41 Network > HomePlug > Edit ..................................................................................................110
Table 42 Network > DHCP Server > General ....................................................................................... 111
Table 43 Network > DHCP Server > Advanced ....................................................................................112
Table 44 Network > DHCP Server > Client List ....................................................................................114
Table 45 Network > NAT > General ......................................................................................................117
Table 46 NAT Application .....................................................................................................................118
Table 47 Network > NAT > Advanced .................................................................................................. 122
Table 48 Dynamic DNS ....................................................................................................................... 126
Table 49 Security > Firewall > General ................................................................................................ 133
Table 50 Security > Firewall > Services ............................................................................................... 135
Table 51 Security > Content Filter > Filter ........................................................................................... 138
Table 52 Security > Content Filter > Schedule .................................................................................... 139
Table 53 Management > Static Route > IP Static Route ...................................................................... 146
Table 54 Management > Static Route > IP Static Route: Static Route Setup ...................................... 147
Table 55 Application and Subnet-based Bandwidth Management Example ....................................... 150
Table 56 Bandwidth Management Priorities ........................................................................................ 150
Table 57 Media Bandwidth Management Setup: Services .................................................................. 151
Table 58 Commonly Used Services ..................................................................................................... 152
Table 59 Bandwidth Management Priority with Default Classes ......................................................... 154
Table 60 Management > Bandwidth MGMT > General ....................................................................... 155
Table 61 Management > Bandwidth MGMT > Advanced .................................................................... 156
Table 62 Management > Bandwidth MGMT > Advanced: Application Rule Configuration .................. 157
Table 63 Management > Bandwidth MGMT > Advanced: User-defined Service Rule Configuration . 158
Table 64 Management > Remote MGMT > WWW .............................................................................. 162
Table 65 Management > Remote MGMT > Telnet ............................................................................... 163
Table 66 Management > Remote MGMT > FTP ................................................................................. 164
Table 67 Management > Remote MGMT > DNS ................................................................................. 165
Table 68 Management > UPnP > General ........................................................................................... 168
Table 69 Maintenance > System > General ........................................................................................ 181
Table 70 Maintenance > System > Time Setting ................................................................................. 183
Table 71 Maintenance > Logs > View Log ........................................................................................... 186
Table 72 Maintenance > Logs > Log Settings ..................................................................................... 187
Table 73 System Maintenance Logs .................................................................................................... 189
Table 74 System Error Logs ................................................................................................................ 190
Table 75 Access Control Logs ............................................................................................................. 190
Table 76 TCP Reset Logs .................................................................................................................... 190
Table 77 Packet Filter Logs ................................................................................................................. 191
Table 78 ICMP Logs ............................................................................................................................ 191
Table 79 CDR Logs ............................................................................................................................. 192
Table 80 PPP Logs .............................................................................................................................. 192
Table 81 UPnP Logs ............................................................................................................................ 192
24
NBG-318S User’s Guide
Page 25

List of Tables
Table 82 Content Filtering Logs ........................................................................................................... 192
Table 83 Attack Logs ........................................................................................................................... 193
Table 84 PKI Logs ............................................................................................................................... 194
Table 85 802.1X Logs .......................................................................................................................... 195
Table 86 ACL Setting Notes ................................................................................................................ 196
Table 87 ICMP Notes ........................................................................................................................... 196
Table 88 Syslog Logs .......................................................................................................................... 197
Table 89 RFC-2408 ISAKMP Payload Types ...................................................................................... 197
Table 90 Maintenance > Tools > Firmware .......................................................................................... 199
Table 91 Maintenance Restore Configuration ..................................................................................... 201
Table 92 Maintenance > Config Mode > General ............................................................................... 205
Table 93 Advanced Configuration Options ......................................................................................... 206
Table 94 Maintenance > Sys OP Mode > General ............................................................................. 208
Table 95 Hardware Features ............................................................................................................... 219
Table 96 Firmware Features ................................................................................................................ 220
Table 97 Standards Supported ............................................................................................................ 221
Table 98 Subnet Mask - Identifying Network Number ......................................................................... 232
Table 99 Subnet Masks ....................................................................................................................... 233
Table 100 Maximum Host Numbers .................................................................................................... 233
Table 101 Alternative Subnet Mask Notation ....................................................................................... 233
Table 102 Subnet 1 .............................................................................................................................. 235
Table 103 Subnet 2 .............................................................................................................................. 236
Table 104 Subnet 3 .............................................................................................................................. 236
Table 105 Subnet 4 .............................................................................................................................. 236
Table 106 Eight Subnets ...................................................................................................................... 236
Table 107 24-bit Network Number Subnet Planning ............................................................................ 237
Table 108 16-bit Network Number Subnet Planning ............................................................................ 237
Table 109 IEEE 802.11g ...................................................................................................................... 259
Table 110 Comparison of EAP Authentication Types .......................................................................... 262
Table 111 Wireless Security Relational Matrix ..................................................................................... 265
Table 112 Examples of Services .......................................................................................................... 267
NBG-318S User’s Guide
25
Page 26

List of Tables
26
NBG-318S User’s Guide
Page 27

PART I
Introduction
Getting to Know Your NBG-318S (29)
Wireless Tutorial (61)
Introducing the Web Configurator (33)
Connection Wizard (45)
27
Page 28

28
Page 29
CHAPTER 1
Getting to Know Your NBG-318S
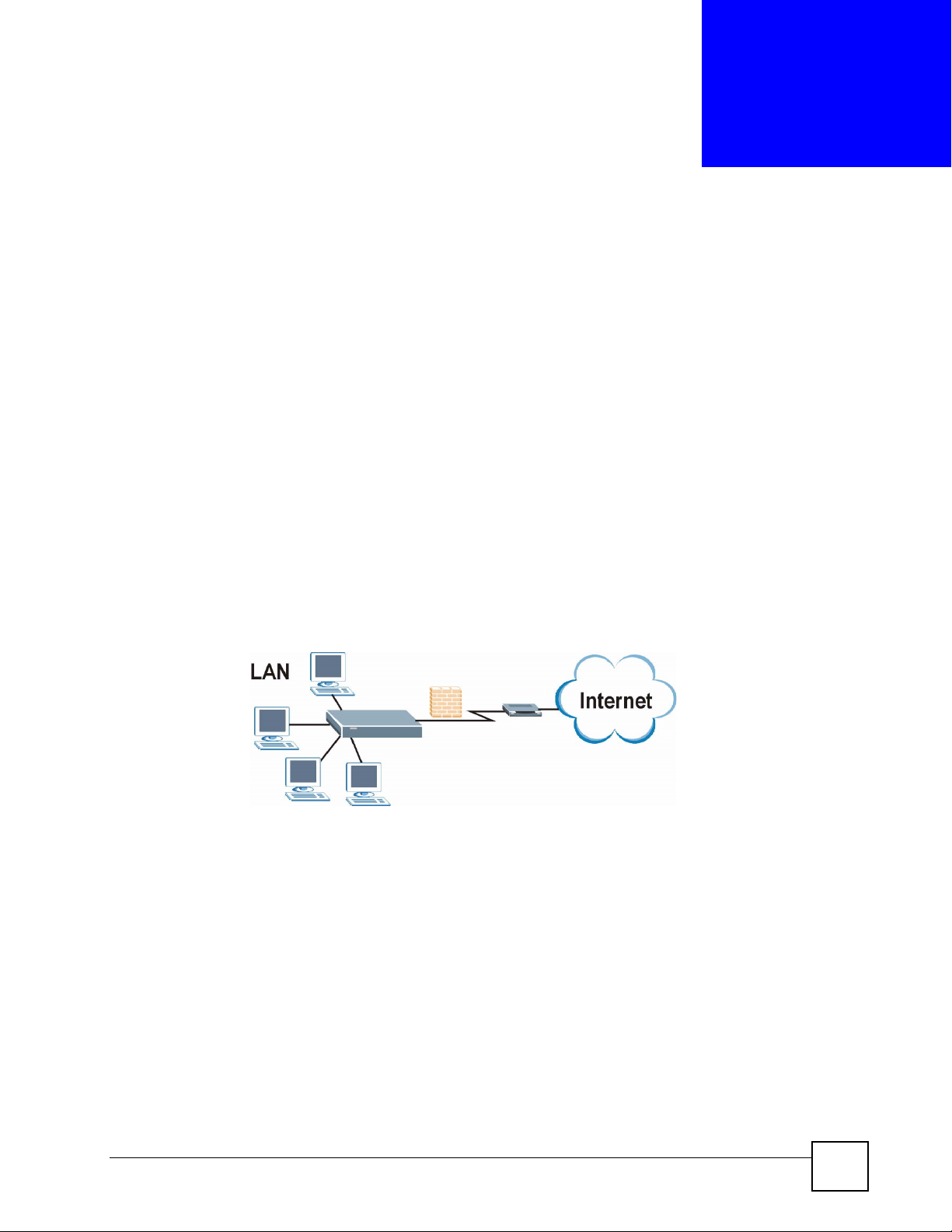
This chapter introduces the main features and applications of the NBG-318S.
1.1 Overview
The NBG-318S is the ideal secure HomePlug AV wireless firewall router for all data passing
between the Internet and your local network.
1.1.1 Secure Broadband Internet Access
Connect a broadband modem to your NBG-318S for shared Internet access protected by
firewall and content filtering. You can also use media bandwidth management to efficiently
manage traffic on your network. The Quality of Service (QoS) features allow you to prioritize
time-sensitive or highly important applications such as Voice over Internet (VoIP).
Figure 1 Secure Internet Access
1.1.2 Wireless LAN Application
The NBG-318S Wireless LAN feature allows IEEE 802.11b or IEEE 802.11g compatible
wireless clients to access the Internet or the local network as well as to communicate with each
other. Wireless stations can move freely anywhere in the coverage area and use resources on
the wired network. The Super G function allows compatible clients to connect to the NBG318S at up to 108 Mbps.
NBG-318S User’s Guide
29
Page 30
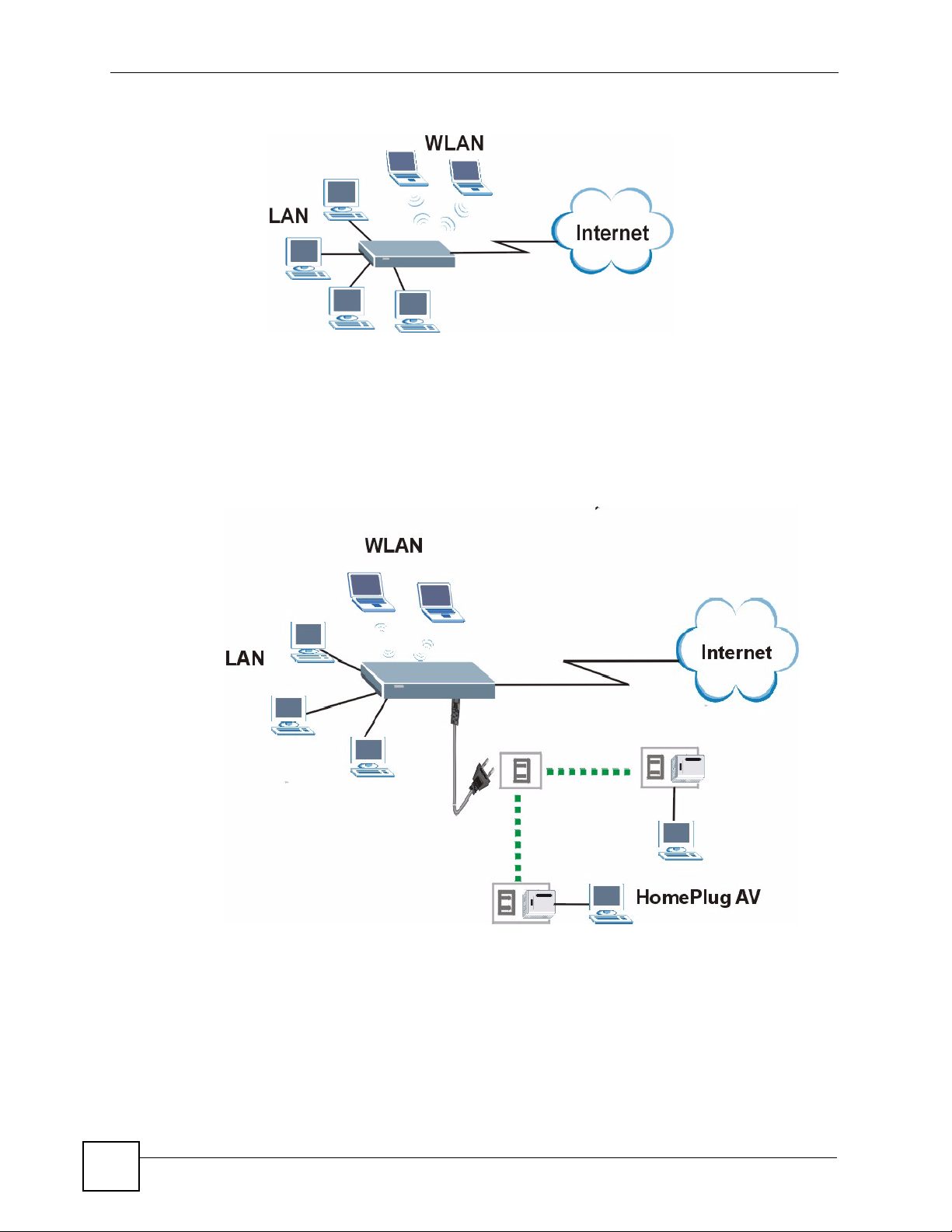
Chapter 1 Getting to Know Your NBG-318S
Figure 2 WLAN Application Example
1.1.3 HomePlug AV
Connect to other HomePlug AV compatible devices through your home electrical wiring. A
HomePlug AV network is capable of up to 200Mbps data transfer without the need for
network cables.
Figure 3 HomePlug AV Internet Connection Example
1.2 Ways to Manage the NBG-318S
Use any of the following methods to manage the NBG-318S.
• Web Configurator. This is recommended for everyday management of the NBG-318S
using a (supported) web browser.
30
NBG-318S User’s Guide
Page 31

Chapter 1 Getting to Know Your NBG-318S
• Command Line Interface. Line commands are mostly used for troubleshooting by service
engineers.
• FTP. Use File Transfer Protocol for firmware upgrades and configuration backup/restore.
1.3 Good Habits for Managing the NBG-318S
Do the following things regularly to make the NBG-318S more secure and to manage the
NBG-318S more effectively.
• Change the password. Use a password that’s not easy to guess and that consists of
different types of characters, such as numbers and letters.
• Write down the password and put it in a safe place.
• Back up the configuration (and make sure you know how to restore it). Restoring an
earlier working configuration may be useful if the device becomes unstable or even
crashes. If you forget your password, you will have to reset the NBG-318S to its factory
default settings. If you backed up an earlier configuration file, you would not have to
totally re-configure the NBG-318S. You could simply restore your last configuration.
1.4 LEDs
Figure 4 Front Panel
The following table describes the LEDs.
Table 1 Front Panel LEDs
LED ICON COLOR STATUS DESCRIPTION
POWER Green On The NBG-318S is receiving power and functioning
properly.
Off The NBG-318S is not receiving power.
HomePlug Green On The NBG-318S has a successful HomePlug AV
connection.
Blinking The NBG-318S is sending/receiving data.
Off The HomePlug AV connection is not ready, or failed.
NBG-318S User’s Guide
31
Page 32

Chapter 1 Getting to Know Your NBG-318S
Table 1 Front Panel LEDs (continued)
LED ICON COLOR STATUS DESCRIPTION
WAN Green On The NBG-318S has a successful 10Mb WAN
connection.
Blinking The NBG-318S is sending/receiving data.
Amber On The NBG-318S has a successful 100Mb Ethernet
connection.
Blinking The NBG-318S is sending/receiving data.
None Off The WAN connection is not ready, or has failed.
LAN 1-3 Green On The NBG-318S has a successful 10Mb Ethernet
connection.
Blinking The NBG-318S is sending/receiving data.
Amber On The NBG-318S has a successful 100Mb Ethernet
connection.
Blinking The NBG-318S is sending/receiving data.
Off The LAN is not connected.
WLAN Green On The NBG-318S is ready, but is not sending/receiving
Blinking The NBG-318S is sending/receiving data through the
None Off The wireless LAN is not ready or has failed.
WPS WPS (WiFi Protected Setup) automatically sets up security on your wireless
network. This function is currently unavailable
data through the wireless LAN.
wireless LAN.
32
NBG-318S User’s Guide
Page 33

CHAPTER 2
Introducing the Web
Configurator
This chapter describes how to access the NBG-318S web configurator and provides an
overview of its screens.
2.1 Web Configurator Overview
The web configurator is an HTML-based management interface that allows easy setup and
management of the NBG-318S via Internet browser. Use Internet Explorer 6.0 and later or
Netscape Navigator 7.0 and later versions. The recommended screen resolution is 1024 by 768
pixels.
In order to use the web configurator you need to allow:
• Web browser pop-up windows from your device. Web pop-up blocking is enabled by
default in Windows XP SP (Service Pack) 2.
• JavaScripts (enabled by default).
• Java permissions (enabled by default).
Refer to the Troubleshooting chapter to see how to make sure these functions are allowed in
Internet Explorer.
2.2 Accessing the Web Configurator
1 Make sure your NBG-318S hardware is properly connected and prepare your computer
or computer network to connect to the NBG-318S (refer to the Quick Start Guide).
2 Launch your web browser.
3 Type "http://192.168.1.1" as the URL.
4 Type "1234" (default) as the password and click Login. In some versions, the default
password appears automatically - if this is the case, click Login.
5 You should see a screen asking you to change your password (highly recommended) as
shown next. Type a new password (and retype it to confirm) and click Apply or click
Ignore.
NBG-318S User’s Guide
33
Page 34

Chapter 2 Introducing the Web Configurator
Figure 5 Change Password Screen
" The management session automatically times out when the time period set in
the Administrator Inactivity Timer field expires (default five minutes). Simply
log back into the NBG-318S if this happens.
6 Select the setup mode you want to use.
• Click Go to Wizard Setup to use the Configuration Wizard for basic Internet and
Wireless setup.
• Click Go to Basic Setup if you want to view and configure basic settings that are not
part of the wizard setup. Not all Web Configurator screens are available in this mode.
• Click Go to Advanced Setup to view and configure all the NBG-318S’s settings.
34
NBG-318S User’s Guide
Page 35

Chapter 2 Introducing the Web Configurator
2.3 Resetting the NBG-318S
If you forget your password or cannot access the web configurator, you will need to use the
RESET button at the back of the NBG-318S to reload the factory-default configuration file.
This means that you will lose all configurations that you had previously saved, and the
password will be reset to “1234”.
2.3.1 Procedure to Use the Reset Button
1 Make sure the PWR LED is on.
2 Press the RESET button for ten seconds or until the PWR LED begins to blink and then
release it. When the PWR LED begins to blink, the defaults have been restored and the
NBG-318S restarts.
2.4 Navigating the Web Configurator
The following summarizes how to navigate the web configurator from the Status screen.
2.4.1 The Status Screen
The following screen displays when you log into the NBG-318S.
" Not all fields are available when you select Basic mode (see Section 2.2 on
page 33). See the Configuration Mode field in the System Status box to
check whether you are in Basic or Advanced mode. Use the Config Mode >
General screen to change between modes.
NBG-318S User’s Guide
35
Page 36

Chapter 2 Introducing the Web Configurator
Figure 6 Web Configurator Status Screen
The following table describes the icons shown in the Status screen.
Table 2 Status Screen Icon Key
ICON DESCRIPTION
Select a language from the drop-down list box to have the web configurator display in
that language.
Click this icon to open the setup wizard.
Click this icon to view copyright and a link for related product information.
Click this icon at any time to exit the web configurator.
Select a number of seconds or None from the drop-down list box to refresh all screen
statistics automatically at the end of every time interval or to not refresh the screen
statistics.
Click this button to refresh the status screen statistics.
36
NBG-318S User’s Guide
Page 37

Chapter 2 Introducing the Web Configurator
The following table describes the labels shown in the Status screen.
Table 3 Web Configurator Status Screen
LABEL DESCRIPTION
Device Information
System Name This is the System Name you enter in the Maintenance > System > General
screen. It is for identification purposes.
Firmware Version This is the ZyNOS firmware version and the date created. ZyNOS is ZyXEL's
proprietary Network Operating System design.
WAN Information
- MAC Address This shows the WAN Ethernet adapter MAC Address of your device.
- IP Address This shows the WAN port’s IP address.
- IP Subnet Mask This shows the WAN port’s subnet mask.
- DHCP This shows the WAN port’s DHCP role - Client or None.
LAN Information
- MAC Address This shows the LAN Ethernet adapter MAC Address of your device.
- IP Address This shows the LAN port’s IP address.
- IP Subnet Mask This shows the LAN port’s subnet mask.
- DHCP This shows the LAN port’s DHCP role - Server or None.
WLAN Information
- MAC Address This shows the wireless adapter MAC Address of your device.
- Name (SSID) This shows a descriptive name used to identify the NBG-318S in the wireless LAN.
- Channel This shows the channel number which you select manually.
- Operating Channel This shows the channel number which the NBG-318S is currently using over the
wireless LAN.
- Security Mode This shows the level of wireless security the NBG-318S is using.
- 802.11 Mode This shows the wireless standard.
- Super G Mode This shows whether SuperG is enabled or not.
HomePlug Information
- MAC Address This shows the MAC Address of your device.
System Status
System Uptime This is the total time the NBG-318S has been on.
Current Date/Time This field displays your NBG-318S’s present date and time.
System Resource
- CPU Usage This displays what percentage of the NBG-318S’s processing ability is currently
used. When this percentage is close to 100%, the NBG-318S is running at full load,
and the throughput is not going to improve anymore. If you want some applications to
have more throughput, you should turn off other applications (for example, using
bandwidth management.
- Memory Usage This shows what percentage of the heap memory the NBG-318S is using. Heap
memory refers to the memory that is not used by ZyNOS (ZyXEL Network Operating
System) and is thus available for running processes like NAT and the firewall.
System Setting
- Firewall This shows whether the firewall is active or not.
- Bandwidth Management This shows whether the bandwidth management is active or not.
NBG-318S User’s Guide
37
Page 38

Chapter 2 Introducing the Web Configurator
Table 3 Web Configurator Status Screen (continued)
LABEL DESCRIPTION
- UPnP This shows whether UPnP is active or not.
- Configuration Mode This shows whether the advanced screens of each feature are turned on
Interface Status
Interface This displays the NBG-318S port types. The port types are: WAN , LAN, HomePlug
Status For the LAN and WAN ports, this field displays Down (line is down) or Up (line is up
Rate For the LAN ports, this displays the port speed and duplex setting or N/A when the
Summary
Any IP Table Use this screen to view details of IP addresses assigned to devices not in the same
BW MGMT Monitor Use this screen to view the NBG-318S’s bandwidth usage and allotments.
DHCP Table Use this screen to view current DHCP client information.
Packet Statistics Use this screen to view port status and packet specific statistics.
WLAN Station Status Use this screen to view the wireless stations that are currently associated to the
My HomePlug Network Use this screen to view information on the stations connected to your Home Plug
(Advanced) or not (Basic).
AV and WLAN.
or connected).
For the WLAN, it displays Up when the WLAN is enabled or Down when the WLAN
is disabled.
For the HomePlug AV port it displays Up when the power cord is connected.
line is disconnected.
For the WAN port, it displays the port speed and duplex setting if you’re using
Ethernet encapsulation and Idle (line (ppp) idle), Dial (starting to trigger a call) and
Drop (dropping a call) if you're using PPPoE or PPTP encapsulation. This field
displays N/A when the line is disconnected.
For the WLAN, it displays the maximum transmission rate when the WLAN is
enabled and N/A when the WLAN is disabled.
For the HomePlug AV port it displays the maximum transmission rate when the
HomePlug AV is enabled.
subnet as the NBG-318S.
NBG-318S.
network.
2.4.2 Navigation Panel
After you enter the password, use the sub-menus on the navigation panel to configure NBG318S features.
The following table describes the sub-menus.
Table 4 Screens Summary
LINK TAB FUNCTION
Status This screen shows the NBG-318S’s general device, system and
Network
38
interface status information. Use this screen to access the wizard,
and summary statistics tables.
NBG-318S User’s Guide
Page 39

Chapter 2 Introducing the Web Configurator
Table 4 Screens Summary
LINK TAB FUNCTION
Wireless
LAN
WAN Internet
LAN IP Use this screen to configure LAN IP address and subnet mask.
HomePlug Network
DHCP
Server
NAT General Use this screen to enable NAT.
DDNS General Use this screen to set up dynamic DNS.
Security
Firewall General Use this screen to activate/deactivate the firewall.
Content Filter Filter Use this screen to block certain web features and sites containing
Management
Static Route IP Static
Bandwidth
MGMT
General Use this screen to configure wireless LAN.
MAC Filter Use the MAC filter screen to configure the NBG-318S to block
Advanced This screen allows you to configure advanced wireless settings.
QoS Use this screen to configure Wi-Fi Multimedia Quality of Service
Connection
Advanced Use this screen to configure other advanced properties.
IP Alias Use this screen to partition your LAN interface into subnets.
Advanced Use this screen to enable other advanced properties.
Settings
General Use this screen to enable the NBG-318S’s DHCP server.
Advanced Use this screen to assign IP addresses to specific individual
Client List Use this screen to view current DHCP client information and to
Application Use this screen to configure servers behind the NBG-318S.
Advanced Use this screen to change your NBG-318S’s port triggering
Services This screen shows a summary of the firewall rules, and allows you
Schedule Use this screen to set the days and times for the NBG-318S to
Route
General Use this screen to enable bandwidth management.
Advanced Use this screen to set the upstream bandwidth and edit a
Monitor Use this screen to view the NBG-318S’s bandwidth usage and
access to devices or block the devices from accessing the NBG318S.
(WMM QoS). WMM QoS allows you to prioritize wireless traffic
according to the delivery requirements of individual services.
This screen allows you to configure ISP parameters, WAN IP
address assignment, DNS servers and the WAN MAC address.
Use this screen to configure HomePlug AV devices and set up a
power line network.
computers based on their MAC addresses and to have DNS
servers assigned by the DHCP server.
always assign an IP address to a MAC address (and host name).
settings.
to edit/add a firewall rule.
certain keywords in the URL.
perform content filtering.
Use this screen to configure IP static routes.
bandwidth management rule.
allotments.
NBG-318S User’s Guide
39
Page 40

Chapter 2 Introducing the Web Configurator
Table 4 Screens Summary
LINK TAB FUNCTION
Remote
MGMT
UPnP General Use this screen to enable UPnP on the NBG-318S.
Maintenance
System General Use this screen to view and change administrative settings such as
Logs View Log Use this screen to view the logs for the categories that you
To ols Firmware Use this screen to upload firmware to your NBG-318S.
Config Mode General This screen allows you to display or hide the advanced screens or
Sys OP
Mode
WWW Use this screen to configure through which interface(s) and from
Telnet Use this screen to configure through which interface(s) and from
FTP Use this screen to configure through which interface(s) and from
DNS Use this screen to configure through which interface(s) and from
Time Setting Use this screen to change your NBG-318S’s time and date.
Log Settings Use this screen to change your NBG-318S’s log settings.
Configuration Use this screen to backup and restore the configuration or reset
Restart This screen allows you to reboot the NBG-318S without turning the
General This screen allows you to select either an Ethernet or a HomePlug
which IP address(es) users can use HTTP to manage the NBG318S.
which IP address(es) users can use Telnet to manage the NBG318S.
which IP address(es) users can use FTP to access the NBG-318S.
which IP address(es) users can send DNS queries to the NBG318S.
system and domain names, password and inactivity timer.
selected.
the factory defaults to your NBG-318S.
power off.
features.
AV WAN connection to the Internet.
2.4.3 Summary: Any IP Table
This screen displays the IP address of each computer that is using the NBG-318S via the any
IP feature. Any IP allows computers to access the Internet through the NBG-318S without
changing their network settings when NAT is enabled. To access this screen, open the Status
screen (see
Figure 7 Any IP Table
Section 2.4.1 on page 35), and click (Details...) next to Any IP Table.
40
NBG-318S User’s Guide
Page 41

Chapter 2 Introducing the Web Configurator
2.4.4 Summary: Bandwidth Management Monitor
Select the BW MGMT Monitor (Details...) hyperlink in Status screen. View the bandwidth
usage of the WAN configured bandwidth rules. This is also shown as bandwidth usage over
the bandwidth budget for each rule. The gray section of the bar represents the percentage of
unused bandwidth and the blue color represents the percentage of bandwidth in use.
Figure 8 Summary: BW MGMT Monitor
2.4.5 Summary: DHCP Table
DHCP (Dynamic Host Configuration Protocol, RFC 2131 and RFC 2132) allows individual
clients to obtain TCP/IP configuration at start-up from a server. You can configure the NBG318S as a DHCP server or disable it. When configured as a server, the NBG-318S provides the
TCP/IP configuration for the clients. If DHCP service is disabled, you must have another
DHCP server on your LAN, or else the computer must be manually configured.
Click the DHCP Table (Details...) hyperlink in the Status screen. Read-only information here
relates to your DHCP status. The DHCP table shows current DHCP client information
(including IP Address, Host Name and MAC Address) of all network clients using the
NBG-318S’s DHCP server.
Figure 9 Summary: DHCP Table
The following table describes the labels in this screen.
Table 5 Summary: DHCP Table
LABEL DESCRIPTION
# This is the index number of the host computer.
IP Address This field displays the IP address relative to the # field listed above.
Host Name This field displays the computer host name.
NBG-318S User’s Guide
41
Page 42

Chapter 2 Introducing the Web Configurator
Table 5 Summary: DHCP Table (continued)
LABEL DESCRIPTION
MAC Address This field shows the MAC address of the computer with the name in the Host Name
field.
Every Ethernet device has a unique MAC (Media Access Control) address. The MAC
address is assigned at the factory and consists of six pairs of hexadecimal
characters, for example, 00:A0:C5:00:00:02.
Refresh Click Refresh to renew the screen.
2.4.6 Summary: Packet Statistics
Click the Packet Statistics (Details...) hyperlink in the Status screen. Read-only information
here includes port status and packet specific statistics. Also provided are "system up time" and
"poll interval(s)". The Poll Interval(s) field is configurable.
Figure 10 Summary: Packet Statistics
The following table describes the labels in this screen.
Table 6 Summary: Packet Statistics
LABEL DESCRIPTION
Port This is the NBG-318S’s port type.
Status For the LAN ports, this displays the port speed and duplex setting or Down
TxPkts This is the number of transmitted packets on this port.
RxPkts This is the number of received packets on this port.
Collisions This is the number of collisions on this port.
Tx B/s This displays the transmission speed in bytes per second on this port.
Rx B/s This displays the reception speed in bytes per second on this port.
Up Time This is the total amount of time the line has been up.
System Up Time This is the total time the NBG-318S has been on.
when the line is disconnected.
For the WAN port, it displays the port speed and duplex setting if you’re using
Ethernet encapsulation and Idle (line (ppp) idle), Dial (starting to trigger a call)
and Drop (dropping a call) if you're using PPPoE or PPTP encapsulation. This
field displays Down when the line is disconnected.
For the WLAN, it displays the maximum transmission rate when the WLAN is
enabled and Down when the WLAN is disabled.
42
NBG-318S User’s Guide
Page 43

Chapter 2 Introducing the Web Configurator
Table 6 Summary: Packet Statistics
LABEL DESCRIPTION
Poll Interval(s) Enter the time interval for refreshing statistics in this field.
Set Interval Click this button to apply the new poll interval you entered in the Poll Interval(s)
Stop Click Stop to stop refreshing statistics, click Stop.
field.
2.4.7 Summary: Wireless Station Status
Click the WLAN Station Status (Details...) hyperlink in the Status screen. View the wireless
stations that are currently associated to the NBG-318S in the Association List screen.
Figure 11 Summary: Wireless Association List
The following table describes the labels in this screen.
Table 7 Summary: Wireless Association List
LABEL DESCRIPTION
# This is the index number of an associated wireless station.
MAC Address This field displays the MAC address of an associated wireless station.
Association Time This field displays the time a wireless station first associated with the NBG-
318S.
Refresh Click Refresh to reload the list.
2.4.8 Summary: My HomePlug Network Status
Click the My HomePlug Network (Details...) hyperlink in the Status screen. View the
powerline stations that are currently associated to the NBG-318S in the My Homeplug
Network screen.
Figure 12 Summary: My Homeplug Network.
NBG-318S User’s Guide
43
Page 44

Chapter 2 Introducing the Web Configurator
The following table describes the labels in this screen.
Table 8 Summary: My Homeplug Network
LABEL DESCRIPTION
Site Your NBG-318S is the Local device. All other devices on your network will be
MAC Address This field displays the MAC address of a HomePlug AV device detected by your
Refresh Click Refresh to reload the list.
Remote.
NBG-318S.
44
NBG-318S User’s Guide
Page 45

CHAPTER 3
Connection Wizard
This chapter provides information on the wizard setup screens in the web configurator.
3.1 Wizard Setup
The web configurator’s wizard setup helps you configure your device to access the Internet.
Refer to your ISP (Internet Service Provider) checklist in the Quick Start Guide to know what
to enter in each field. Leave a field blank if you don’t have that information.
1 After you access the NBG-318S web configurator, click the Go to Wizard setup
hyperlink.
You can click the Go to Basic setup or Go to Advanced setup hyperlink to skip this
wizard setup and configure basic or advanced features accordingly.
Figure 13 Select Wizard or Advanced Mode
2 Choose your language from the drop-down list box.
3 Click the Next button to proceed to the next screen.
NBG-318S User’s Guide
45
Page 46
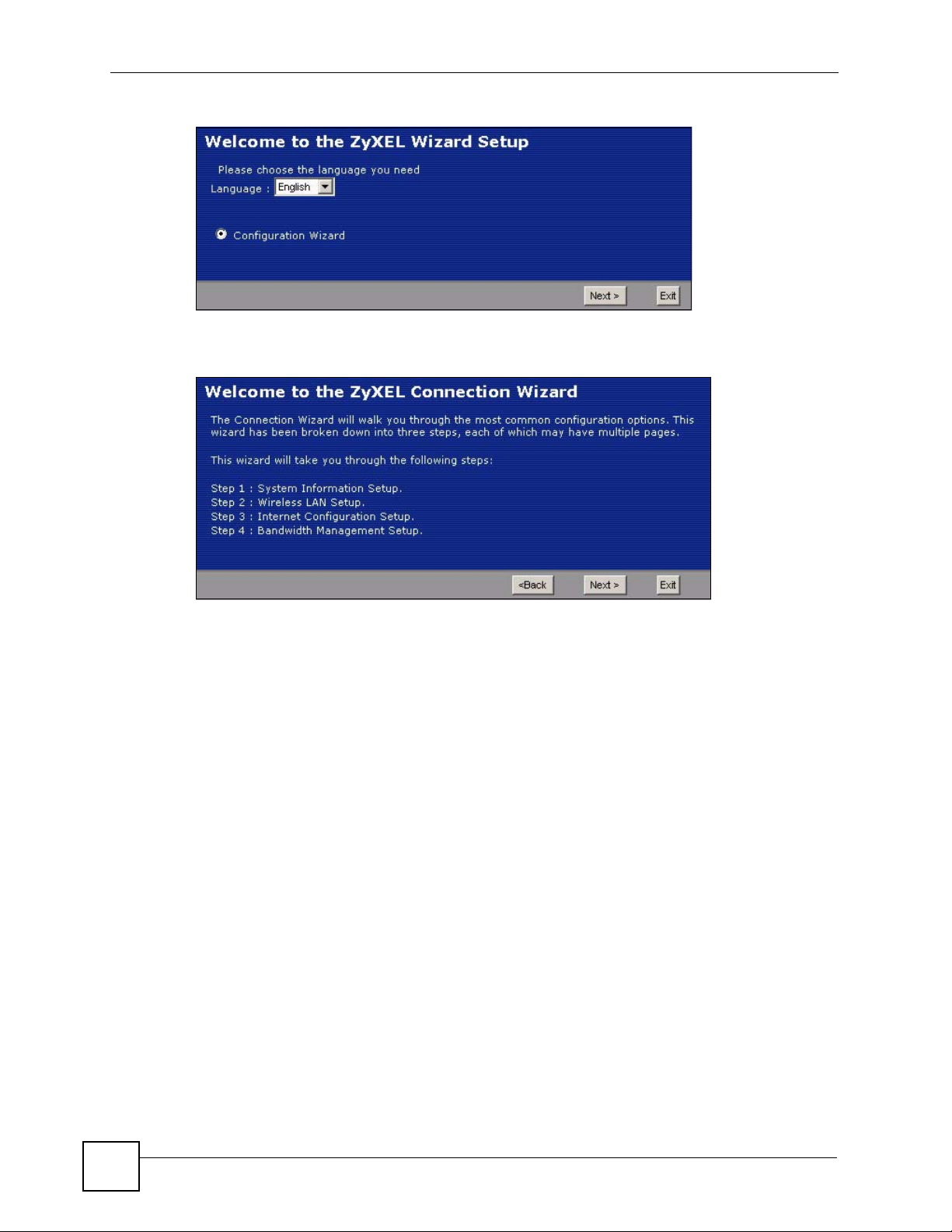
Chapter 3 Connection Wizard
Figure 14 Select a Language
4 Read the on-screen information and click Next.
Figure 15 Welcome to the Connection Wizard
3.2 Connection Wizard: STEP 1: System Information
System Information contains administrative and system-related information.
3.2.1 System Name
System Name is for identification purposes. However, because some ISPs check this name
you should enter your computer's "Computer Name".
• In Windows 95/98 click Start, Settings, Control Panel, Network. Click the
Identification tab, note the entry for the Computer Name field and enter it as the System
Name.
• In Windows 2000, click Start, Settings and Control Panel and then double-click System.
Click the Network Identification tab and then the Properties button. Note the entry for
the Computer name field and enter it as the System Name.
• In Windows XP, click Start, My Computer, View system information and then click
the Computer Name tab. Note the entry in the Full computer name field and enter it as
the NBG-318S System Name.
46
NBG-318S User’s Guide
Page 47

3.2.2 Domain Name
The Domain Name entry is what is propagated to the DHCP clients on the LAN. If you leave
this blank, the domain name obtained by DHCP from the ISP is used. While you must enter
the host name (System Name) on each individual computer, the domain name can be assigned
from the NBG-318S via DHCP.
Click Next to configure the NBG-318S for Internet access.
Figure 16 Wizard Step 1: System Information
Chapter 3 Connection Wizard
The following table describes the labels in this screen.
Table 9 Wizard Step 1: System Information
LABEL DESCRIPTION
System Name System Name is a unique name to identify the NBG-318S in an Ethernet network.
Enter a descriptive name. This name can be up to 30 alphanumeric characters long.
Spaces are not allowed, but dashes "-" and underscores "_" are accepted.
Domain Name Type the domain name (if you know it) here. If you leave this field blank, the ISP may
assign a domain name via DHCP. The domain name entered by you is given priority
over the ISP assigned domain name.
Back Click Back to display the previous screen.
Next Click Next to proceed to the next screen.
Exit Click Exit to close the wizard screen without saving.
3.3 Connection Wizard: STEP 2: Wireless LAN
Set up your wireless LAN using the following screen.
NBG-318S User’s Guide
47
Page 48

Chapter 3 Connection Wizard
Figure 17 Wizard Step 2: Wireless LAN
The following table describes the labels in this screen.
Table 10 Wizard Step 2: Wireless LAN
LABEL DESCRIPTION
Name (SSID) Enter a descriptive name (up to 32 printable 7-bit ASCII characters) for the wireless
Security Select a Security level from the drop-down list box.
Channel
Selection
Back Click Back to display the previous screen.
Next Click Next to proceed to the next screen.
Exit Click Exit to close the wizard screen without saving.
LAN.
If you change this field on the NBG-318S, make sure all wireless stations use the
same SSID in order to access the network.
Choose Auto to have the NBG-318S generate a pre-shared key automatically. A
screen pops up displaying the generated pre-shared key after you click Next. Write
down the key for use later when connecting other wireless devices to your network.
Click OK to continue.
Choose None to have no wireless LAN security configured. If you do not enable any
wireless security on your NBG-318S, your network is accessible to any wireless
networking device that is within range. If you choose this option, skip directly to
Section 3.4 on page 50.
Choose Basic (WEP) security if you want to configure WEP Encryption parameters. If
you choose this option, go directly to
Choose Extend (WPA-PSK or WPA2-PSK) security to configure a Pre-Shared Key.
Choose this option only if your wireless clients support WPA-PSK or WPA2-PSK
respectively. If you choose this option, skip directly to
The range of radio frequencies used by IEEE 802.11b/g wireless devices is called a
channel.
Select a channel that is not used by any nearby devices.
Section 3.3.1 on page 49.
Section 3.3.2 on page 50.
" The wireless stations and NBG-318S must use the same SSID, channel ID
and WEP encryption key (if WEP is enabled), WPA-PSK (if WPA-PSK is
enabled) or WPA2-PSK (if WPA2-PSK is enabled) for wireless
communication.
48
NBG-318S User’s Guide
Page 49

3.3.1 Basic (WEP) Security
Choose Basic (WEP) to setup WEP Encryption parameters.
Figure 18 Wizard Step 2: Basic (WEP) Security
Chapter 3 Connection Wizard
The following table describes the labels in this screen.
Tabl e 11 Wizard Step 2: Basic (WEP) Security
LABEL DESCRIPTION
Passphrase Type a Passphrase (up to 32 printable characters) and click Generate. The NBG-
WEP
Encryption
ASCII Select this option in order to enter ASCII characters as the WEP keys.
HEX Select this option to enter hexadecimal characters as the WEP keys.
Key 1 to Key 4 The WEP keys are used to encrypt data. Both the NBG-318S and the wireless
Back Click Back to display the previous screen.
NBG-318S User’s Guide
318S automatically generates a WEP key.
Select 64-bit WEP or 128-bit WEP to allow data encryption.
The preceding “0x” is entered automatically.
stations must use the same WEP key for data transmission.
If you chose 64-bit WEP, then enter any 5 ASCII characters or 10 hexadecimal
characters ("0-9", "A-F").
If you chose 128-bit WEP, then enter 13 ASCII characters or 26 hexadecimal
characters ("0-9", "A-F").
You must configure at least one key, only one key can be activated at any one time.
The default key is key 1.
49
Page 50

Chapter 3 Connection Wizard
Tabl e 11 Wizard Step 2: Basic (WEP) Security
LABEL DESCRIPTION
Next Click Next to proceed to the next screen.
Exit Click Exit to close the wizard screen without saving.
3.3.2 Extend (WPA-PSK or WPA2-PSK) Security
Choose Extend (WPA-PSK) or Extend (WPA2-PSK) security in the Wireless LAN setup
screen to set up a Pre-Shared Key.
Figure 19 Wizard Step 2: Extend (WPA-PSK or WPA2-PSK) Security
The following table describes the labels in this screen.
Table 12 Wizard Step 2: Extend (WPA-PSK or WPA2-PSK) Security
LABEL DESCRIPTION
Pre-Shared
Key
Back Click Back to display the previous screen.
Next Click Next to proceed to the next screen.
Exit Click Exit to close the wizard screen without saving.
Type from 8 to 63 case-sensitive ASCII characters. You can set up the most secure
wireless connection by configuring WPA in the wireless LAN screens. You need to
configure an authentication server to do this.
3.4 Connection Wizard: STEP 3: Internet Configuration
The NBG-318S offers three Internet connection types. They are Ethernet, PPP over
Ethernet or PPTP. The wizard attempts to detect which WAN connection type you are using.
If the wizard does not detect a connection type, you must select one from the drop-down list
box. Check with your ISP to make sure you use the correct type.
This wizard screen varies according to the connection type that you select.
50
NBG-318S User’s Guide
Page 51

Chapter 3 Connection Wizard
Figure 20 Wizard Step 3: ISP Parameters.
The following table describes the labels in this screen,
Table 13 Wizard Step 3: ISP Parameters
CONNECTION TYPE DESCRIPTION
Ethernet Select the Ethernet option when the WAN port is used as a regular Ethernet.
PPPoE Select the PPP over Ethernet option for a dial-up connection. If your ISP
gave you a an IP address and/or subnet mask, then select PPTP.
PPTP Select the PPTP option for a dial-up connection.
3.4.1 Ethernet Connection
Choose Ethernet when the WAN port is used as a regular Ethernet.
Figure 21 Wizard Step 3: Ethernet Connection
3.4.2 PPPoE Connection
Point-to-Point Protocol over Ethernet (PPPoE) functions as a dial-up connection. PPPoE is an
IETF (Internet Engineering Task Force) standard specifying how a host personal computer
interacts with a broadband modem (for example DSL, cable, wireless, etc.) to achieve access
to high-speed data networks.
For the service provider, PPPoE offers an access and authentication method that works with
existing access control systems (for instance, RADIUS).
NBG-318S User’s Guide
51
Page 52

Chapter 3 Connection Wizard
One of the benefits of PPPoE is the ability to let end users access one of multiple network
services, a function known as dynamic service selection. This enables the service provider to
easily create and offer new IP services for specific users.
Operationally, PPPoE saves significant effort for both the subscriber and the ISP/carrier, as it
requires no specific configuration of the broadband modem at the subscriber’s site.
By implementing PPPoE directly on the NBG-318S (rather than individual computers), the
computers on the LAN do not need PPPoE software installed, since the NBG-318S does that
part of the task. Furthermore, with NAT, all of the LAN's computers will have Internet access.
Refer to the appendix for more information on PPPoE.
Figure 22 Wizard Step 3: PPPoE Connection
The following table describes the labels in this screen.
Table 14 Wizard Step 3: PPPoE Connection
LABEL DESCRIPTION
ISP Parameter for Internet Access
Connection Type Select the PPP over Ethernet option for a dial-up connection.
Service Name Type the name of your service provider.
User Name Type the user name given to you by your ISP.
Password Type the password associated with the user name above.
Back Click Back to return to the previous screen.
Next Click Next to continue.
Exit Click Exit to close the wizard screen without saving.
3.4.3 PPTP Connection
Point-to-Point Tunneling Protocol (PPTP) is a network protocol that enables transfers of data
from a remote client to a private server, creating a Virtual Private Network (VPN) using TCP/
IP-based networks.
PPTP supports on-demand, multi-protocol, and virtual private networking over public
networks, such as the Internet.
52
Refer to the appendix for more information on PPTP.
NBG-318S User’s Guide
Page 53

Chapter 3 Connection Wizard
" The NBG-318S supports one PPTP server connection at any given time.
Figure 23 Wizard Step 3: PPTP Connection
The following table describes the fields in this screen
Table 15 Wizard Step 3: PPTP Connection
LABEL DESCRIPTION
ISP Parameters for Internet Access
Connection Type Select PPTP from the drop-down list box. To configure a PPTP client, you must
User Name Type the user name given to you by your ISP.
Password Type the password associated with the User Name above.
PPTP Configuration
Get automatically
from ISP
Use fixed IP
address
My IP Address Type the (static) IP address assigned to you by your ISP.
My IP Subnet
Mask
Server IP Address Type the IP address of the PPTP server.
Connection ID/
Name
Back Click Back to return to the previous screen.
configure the User Name and Password fields for a PPP connection and the
PPTP parameters for a PPTP connection.
Select this radio button if your ISP did not assign you a fixed IP address.
Select this radio button, provided by your ISP to give the NBG-318S a fixed,
unique IP address.
Type the subnet mask assigned to you by your ISP (if given).
Enter the connection ID or connection name in this field. It must follow the "c:id"
and "n:name" format. For example, C:12 or N:My ISP.
This field is optional and depends on the requirements of your ISP.
NBG-318S User’s Guide
53
Page 54

Chapter 3 Connection Wizard
Table 15 Wizard Step 3: PPTP Connection
LABEL DESCRIPTION
Next Click Next to continue.
Exit Click Exit to close the wizard screen without saving.
3.4.4 Your IP Address
The following wizard screen allows you to assign a fixed IP address or give the NBG-318S an
automatically assigned IP address depending on your ISP.
Figure 24 Wizard Step 3: Your IP Address
The following table describes the labels in this screen
Table 16 Wizard Step 3: Your IP Address
LABEL DESCRIPTION
Get automatically from
your ISP
Use fixed IP address
provided by your ISP
Back Click Back to return to the previous screen.
Next Click Next to continue.
Exit Click Exit to close the wizard screen without saving.
Select this option If your ISP did not assign you a fixed IP address. This is
the default selection. If you choose this option, skip directly to section
3.4.9.
Select this option if you were given IP address and/or DNS server settings
by the ISP. The fixed IP address should be in the same subnet as your
broadband modem or router.
3.4.5 WAN IP Address Assignment
Every computer on the Internet must have a unique IP address. If your networks are isolated
from the Internet, for instance, only between your two branch offices, you can assign any IP
addresses to the hosts without problems. However, the Internet Assigned Numbers Authority
(IANA) has reserved the following three blocks of IP addresses specifically for private
networks.
Table 17 Private IP Address Ranges
10.0.0.0 - 10.255.255.255
172.16.0.0 - 172.31.255.255
192.168.0.0 - 192.168.255.255
54
NBG-318S User’s Guide
Page 55

Chapter 3 Connection Wizard
You can obtain your IP address from the IANA, from an ISP or have it assigned by a private
network. If you belong to a small organization and your Internet access is through an ISP, the
ISP can provide you with the Internet addresses for your local networks. On the other hand, if
you are part of a much larger organization, you should consult your network administrator for
the appropriate IP addresses.
" Regardless of your particular situation, do not create an arbitrary IP address;
always follow the guidelines above. For more information on address
assignment, please refer to RFC 1597, Address Allocation for Private Internets
and RFC 1466, Guidelines for Management of IP Address Space.
3.4.6 IP Address and Subnet Mask
Similar to the way houses on a street share a common street name, so too do computers on a
LAN share one common network number.
Where you obtain your network number depends on your particular situation. If the ISP or
your network administrator assigns you a block of registered IP addresses, follow their
instructions in selecting the IP addresses and the subnet mask.
If the ISP did not explicitly give you an IP network number, then most likely you have a single
user account and the ISP will assign you a dynamic IP address when the connection is
established. The Internet Assigned Number Authority (IANA) reserved this block of addresses
specifically for private use; please do not use any other number unless you are told otherwise.
Let's say you select 192.168.1.0 as the network number; which covers 254 individual
addresses, from 192.168.1.1 to 192.168.1.254 (zero and 255 are reserved). In other words, the
first three numbers specify the network number while the last number identifies an individual
computer on that network.
Once you have decided on the network number, pick an IP address that is easy to remember,
for instance, 192.168.1.1, for your NBG-318S, but make sure that no other device on your
network is using that IP address.
The subnet mask specifies the network number portion of an IP address. Your NBG-318S will
compute the subnet mask automatically based on the IP address that you entered. You don't
need to change the subnet mask computed by the NBG-318S unless you are instructed to do
otherwise.
3.4.7 DNS Server Address Assignment
Use DNS (Domain Name System) to map a domain name to its corresponding IP address and
vice versa, for instance, the IP address of www.zyxel.com is 204.217.0.2. The DNS server is
extremely important because without it, you must know the IP address of a computer before
you can access it.
The NBG-318S can get the DNS server addresses in the following ways.
1 The ISP tells you the DNS server addresses, usually in the form of an information sheet,
when you sign up. If your ISP gives you DNS server addresses, enter them in the DNS
Server fields in the Wizard and/or WAN > Internet Connection screen.
NBG-318S User’s Guide
55
Page 56

Chapter 3 Connection Wizard
2 If the ISP did not give you DNS server information, leave the DNS Server fields set to
0.0.0.0 in the Wizard screen and/or set to From ISP in the WAN > Internet
Connection screen for the ISP to dynamically assign the DNS server IP addresses.
3.4.8 WAN IP and DNS Server Address Assignment
The following wizard screen allows you to assign a fixed WAN IP address and DNS server
addresses.
Figure 25 Wizard Step 3: WAN IP and DNS Server Addresses
The following table describes the labels in this screen
Table 18 Wizard Step 3: WAN IP and DNS Server Addresses
LABEL DESCRIPTION
WAN IP Address Assignment
My WAN IP Address Enter your WAN IP address in this field. The WAN IP address should be in
the same subnet as your DSL/Cable modem or router.
My WAN IP Subnet Mask Enter the IP subnet mask in this field.
Gateway IP Address Enter the gateway IP address in this field.
System DNS Server Address Assignment (if applicable)
DNS (Domain Name System) is for mapping a domain name to its corresponding IP address and vice
versa. The DNS server is extremely important because without it, you must know the IP address of a
computer before you can access it. The NBG-318S uses a system DNS server (in the order you specify
here) to resolve domain names for DDNS and the time server.
First DNS Server
Second DNS Server
Third DNS Server
Back Click Back to return to the previous screen.
Next Click Next to continue.
Exit Click Exit to close the wizard screen without saving.
Enter the DNS server's IP address in the fields provided.
If you do not configure a system DNS server, you must use IP addresses
when configuring DDNS and the time server.
56
NBG-318S User’s Guide
Page 57

3.4.9 WAN MAC Address
Every Ethernet device has a unique MAC (Media Access Control) address. The MAC address
is assigned at the factory and consists of six pairs of hexadecimal characters, for example,
00:A0:C5:00:00:02.
Table 19 Example of Network Properties for LAN Servers with Fixed IP Addresses
Choose an IP address 192.168.1.2-192.168.1.32; 192.168.1.65-192.168.1.254.
Subnet mask 255.255.255.0
Gateway (or default route) 192.168.1.1(NBG-318S LAN IP)
This screen allows users to configure the WAN port's MAC address by either using the NBG318S’s MAC address, copying the MAC address from a computer on your LAN or manually
entering a MAC address. Once it is successfully configured, the address will be copied to the
"rom" file (ZyNOS configuration file). It will not change unless you change the setting or
upload a different "rom" file. It is advisable to clone the MAC address from a computer on
your LAN even if your ISP does not presently require MAC address authentication.
Figure 26 Wizard Step 3: WAN MAC Address
Chapter 3 Connection Wizard
The following table describes the fields in this screen.
Table 20 Wizard Step 3: WAN MAC Address
LABEL DESCRIPTION
Factory Default Select Factory Default to use the factory assigned default MAC address.
Clone the
computer’s MAC
address
Set WAN MAC
Address
Back Click Back to return to the previous screen.
Next Click Next to continue.
Exit Click Exit to close the wizard screen without saving.
NBG-318S User’s Guide
Select this option and enter the IP address of the computer on the LAN whose
MAC you are cloning. It is advisable to clone the MAC address from a computer
on your LAN even if your ISP does not presently require MAC address
authentication.
Select this option and enter the MAC address you want to use.
57
Page 58

Chapter 3 Connection Wizard
3.5 Connection Wizard: STEP 4: Bandwidth management
Bandwidth management allows you to control the amount of bandwidth going out through the
NBG-318S’s WAN, LAN or WLAN port and prioritize the distribution of the bandwidth
according to the traffic type. This helps keep one service from using all of the available
bandwidth and shutting out other users.
Figure 27 Wizard Step 4: Bandwidth Management
The following fields describe the label in this screen.
Table 21 Wizard Step 4: Bandwidth Management
LABEL DESCRIPTION
Enable BM for all traffic
automatically
Back Click Back to return to the previous screen.
Next Click Next to continue.
Exit Click Exit to close the wizard screen without saving.
Select the check box to have the NBG-318S apply bandwidth management
to traffic going out through the NBG-318S’s WAN, LAN, HomePlug AV or
WLAN port. Bandwidth is allocated according to the traffic type
automatically. Real-time packets, such as VoIP traffic always get higher
priority.
3.6 Connection Wizard Complete
Click Apply to save your configuration.
58
NBG-318S User’s Guide
Page 59

Chapter 3 Connection Wizard
Figure 28 Connection Wizard Save
Follow the on-screen instructions and click Finish to complete the wizard setup.
Figure 29 Connection Wizard Complete
Well done! You have successfully set up your NBG-318S to operate on your network and
access the Internet.
NBG-318S User’s Guide
59
Page 60

Chapter 3 Connection Wizard
60
NBG-318S User’s Guide
Page 61

CHAPTER 4
Wireless Tutorial
This chapter gives you examples of how to set up an access point and wireless client for
wireless communication using the following parameters. The wireless clients can access the
Internet through an AP wirelessly.
4.1 Example Parameters
SSID SSID_Example3
Channel 6
Security WPA-PSK
(Pre-Shared Key: ThisismyWPA-PSKpre-sharedkey)
802.11 mode IEEE 802.11b/g
An access point (AP) or wireless router is referred to as an “AP” and a computer with a
wireless network card or USB/PCI adapter is referred to as a “wireless client” here.
We use the M-302 utility screens as an example for the wireless client. The screens may vary
for different models.
4.2 Configuring the AP
Flow the steps below to configure the wireless settings on your AP.
3 Open the Wireless LAN > General screen in the AP’s web configurator.
NBG-318S User’s Guide
61
Page 62
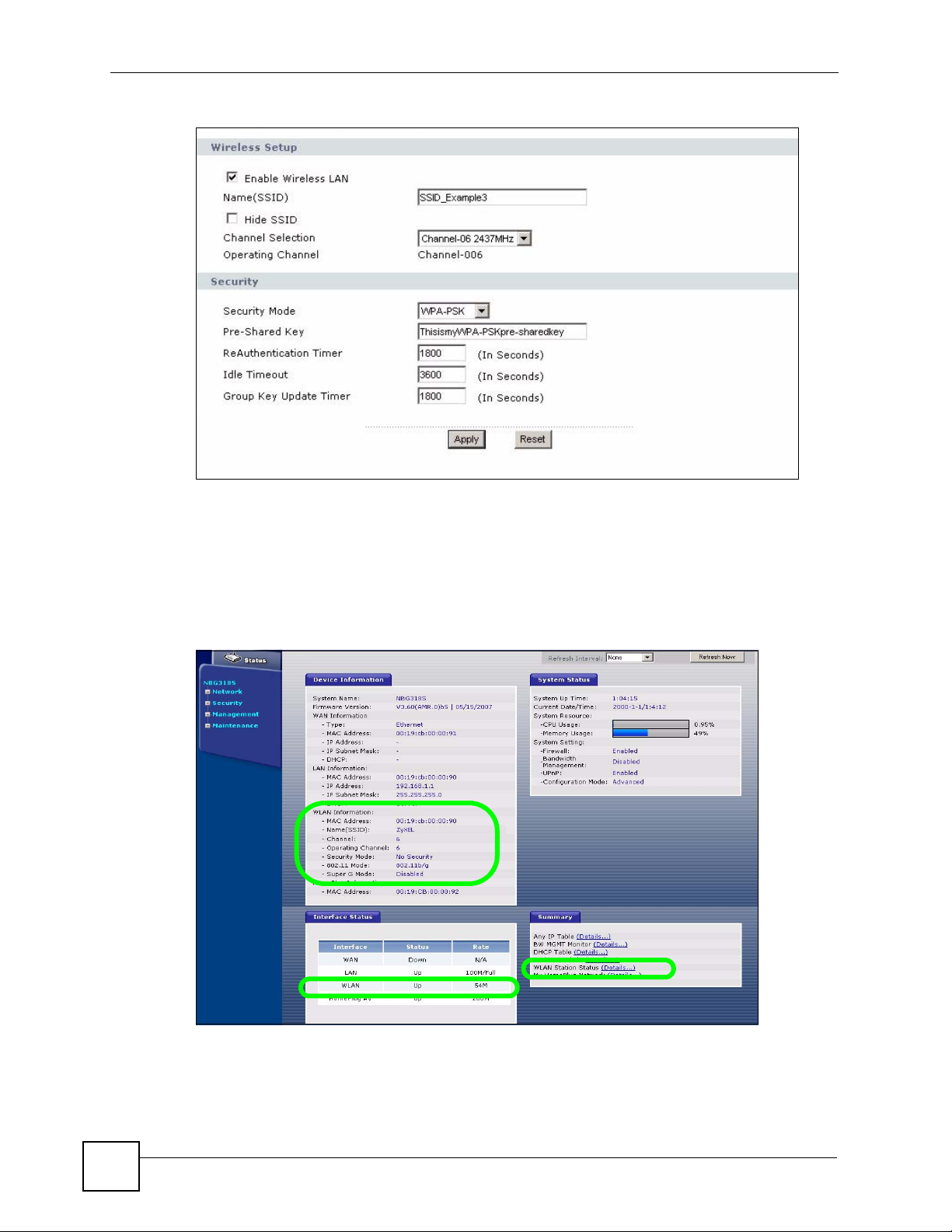
Chapter 4 Wireless Tutorial
Figure 30 Network > Wireless LAN > General
4 Make sure the Enable Wireless LAN check box is selected.
5 Enter SSID_Example3 as the SSID and select a channel.
6 Set security mode to WPA-PSK and enter ThisismyWPA-PSKpre-sharedkey in the
Pre-Shared Key field. Click Apply.
7 Open the Status screen.Verify your wireless and wireless security settings under Device
Information and check if the WLAN connection is up under Interface Status.
Figure 31 Network > Wireless LAN > General
8 Click the WLAN Station Status hyperlink in the AP’s Status screen. You can see if any
wireless client has connected to the AP.
62
NBG-318S User’s Guide
Page 63

Figure 32 AP: Status: WLAN Station Status
4.3 Configuring the Wireless Client
This section describes how to connect the wireless client to a network.
4.3.1 Connecting to a Wireless LAN
The following sections show you how to join a wireless network using the ZyXEL utility, as in
the following diagram. The wireless client is labelled C and the access point is labelled AP.
Chapter 4 Wireless Tutorial
There are three ways to connect the client to an access point.
• Configure nothing and leave the wireless client to automatically scan for and connect to
any available network that has no wireless security configured.
• Manually connect to a network.
• Configure a profile to have the wireless client automatically connect to a specific network
or peer computer.
This example illustrates how to manually connect your wireless client to an access point (AP)
which is configured for WPA-PSK security and connected to the Internet. Before you connect
to the access point, you must know its Service Set IDentity (SSID) and WPA-PSK pre-shared
key. In this example, the SSID is “SSID_Example3” and the pre-shared key is
“ThisismyWPA-PSKpre-sharedkey”.
After you install the ZyXEL utility and then insert the wireless client, follow the steps below
to connect to a network using the Site Survey screen.
NBG-318S User’s Guide
63
Page 64

Chapter 4 Wireless Tutorial
1 Open the ZyXEL utility and click the Site Survey tab to open the screen shown next.
2 The wireless client automatically searches for available wireless networks. Click Scan if
you want to search again. If no entry displays in the Available Network List, that means
there is no wireless network available within range. Make sure the AP or peer computer
is turned on or move the wireless client closer to the AP or peer computer.
3 When you try to connect to an AP with security configured, a window will pop up
prompting you to specify the security settings. Enter the pre-shared key and leave the
encryption type at the default setting.
Use the Next button to move on to the next screen. You can use the Back button at any
time to return to the previous screen, or the Exit button to return to the Site Survey
screen.
Figure 33 ZyXEL Utility: Security Settings
4 The Confirm Save window appears. Check your settings and click Save to continue.
64
NBG-318S User’s Guide
Page 65

Chapter 4 Wireless Tutorial
Figure 34 ZyXEL Utility: Confirm Save
5 The ZyXEL utility returns to the Link Info screen while it connects to the wireless
network using your settings. When the wireless link is established, the ZyXEL utility
icon in the system tray turns green and the Link Info screen displays details of the active
connection. Check the network information in the Link Info screen to verify that you
have successfully connected to the selected network. If the wireless client is not
connected to a network, the fields in this screen remain blank.
Figure 35 ZyXEL Utility: Link Info
6 Open your Internet browser and enter http://www.zyxel.com or the URL of any other
web site in the address bar. If you are able to access the web site, your wireless
connection is successfully configured.
If you cannot access the web site, try changing the encryption type in the Security
Settings screen, check the Troubleshooting section of this User's Guide or contact your
network administrator.
NBG-318S User’s Guide
65
Page 66

Chapter 4 Wireless Tutorial
66
NBG-318S User’s Guide
Page 67

PART II
Network
Wireless LAN (69)
WA N ( 8 9)
LAN (99)
HomePlug AV (105)
DHCP (111)
Network Address Translation (NAT) (115)
Dynamic DNS (125)
67
Page 68

68
Page 69

CHAPTER 5
Wireless LAN
This chapter discusses how to configure the wireless network settings in your NBG-318S. See
the appendices for more detailed information about wireless networks.
5.1 Wireless Network Overview
The following figure provides an example of a wireless network.
Figure 36 Example of a Wireless Network
The wireless network is the part in the blue circle. In this wireless network, devices A and B
are called wireless clients. The wireless clients use the access point (AP) to interact with other
devices (such as the printer) or with the Internet. Your NBG-318S is the AP.
Every wireless network must follow these basic guidelines.
• Every wireless client in the same wireless network must use the same SSID.
The SSID is the name of the wireless network. It stands for Service Set IDentity.
• If two wireless networks overlap, they should use different channels.
Like radio stations or television channels, each wireless network uses a specific channel,
or frequency, to send and receive information.
NBG-318S User’s Guide
69
Page 70

Chapter 5 Wireless LAN
• Every wireless client in the same wireless network must use security compatible with the
AP.
Security stops unauthorized devices from using the wireless network. It can also protect
the information that is sent in the wireless network.
Requirements
To add a wireless LAN to your existing network, make sure you have the following:
1 an access point (AP) or a router with the wireless feature
2 at least one wireless network card/adapter which varies according to your computer.
• If you have a desktop, use either a wireless USB adapter or a wireless PCI adapter.
• If you have a laptop, use either a wireless USB adapter or a wireless CardBus
3 a RADIUS server only if you want to use IEEE802.1x, WPA or WPA2
To have two or more computers communicate with each other wirelessly without an AP or
wireless router, make sure you have the following:
card.
1 two or more wireless network cards/adapters which vary according to your computers.
• If you have a desktop, use either a wireless USB adapter or a wireless PCI adapter.
• If you have a laptop, use either a wireless USB adapter or a wireless CardBus
card.
Setup Information
To set up your wireless network using an AP or wireless router, make sure your AP or wireless
router and wireless network card(s)/adapter(s) use the same following settings:
• SSID:_____________________
• Channel: auto or _________
• Network type of a wireless network card/adapter: Infrastructure
• wireless standard: IEEE 802.11b, g, b/g or a
• Security:
( ) None
( ) WEP (64bit, 128bit or 256bit key) (ASCII or Hex):________________
( ) IEEE 802.1x
70
( ) WPA-PSK (TKIP or AES):_______________
( ) WPA (TKIP or AES)
( ) WPA2-PSK (TKIP or AES):______________
NBG-318S User’s Guide
Page 71

( ) WPA2 (TKIP or AES)
• Preamble type (if available): auto, short or long
To set up your wireless network without an AP or wireless router, make sure wireless network
cards/adapters use the same following settings:
• Network type: Ad-Hoc
• SSID:_____________________
• Channel: _________________
• wireless standard: IEEE 802.11b, g, b/g or a
• Security:
( ) None
( ) WEP (64bit, 128bit or 256bit key) (ASCII or Hex):________________
5.2 Wireless Security Overview
Chapter 5 Wireless LAN
The following sections introduce different types of wireless security you can set up in the
wireless network.
5.2.1 SSID
Normally, the AP acts like a beacon and regularly broadcasts the SSID in the area. You can
hide the SSID instead, in which case the AP does not broadcast the SSID. In addition, you
should change the default SSID to something that is difficult to guess.
This type of security is fairly weak, however, because there are ways for unauthorized devices
to get the SSID. In addition, unauthorized devices can still see the information that is sent in
the wireless network.
5.2.2 MAC Address Filter
Every wireless client has a unique identification number, called a MAC address.1 A MAC
address is usually written using twelve hexadecimal characters2; for example, 00A0C5000002
or 00:A0:C5:00:00:02. To get the MAC address for each wireless client, see the appropriate
User’s Guide or other documentation.
You can use the MAC address filter to tell the AP which wireless clients are allowed or not
allowed to use the wireless network. If a wireless client is allowed to use the wireless network,
it still has to have the correct settings (SSID, channel, and security). If a wireless client is not
allowed to use the wireless network, it does not matter if it has the correct settings.
This type of security does not protect the information that is sent in the wireless network.
Furthermore, there are ways for unauthorized devices to get the MAC address of an authorized
wireless client. Then, they can use that MAC address to use the wireless network.
1. Some wireless devices, such as scanners, can detect wireless networks but cannot use wireless networks.
These kinds of wireless devices might not have MAC addresses.
2. Hexadecimal characters are 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, and F.
NBG-318S User’s Guide
71
Page 72

Chapter 5 Wireless LAN
5.2.3 User Authentication
You can make every user log in to the wireless network before they can use it. This is called
user authentication. However, every wireless client in the wireless network has to support
IEEE 802.1x to do this.
For wireless networks, there are two typical places to store the user names and passwords for
each user.
• In the AP: this feature is called a local user database or a local database.
• In a RADIUS server: this is a server used in businesses more than in homes.
If your AP does not provide a local user database and if you do not have a RADIUS server,
you cannot set up user names and passwords for your users.
Unauthorized devices can still see the information that is sent in the wireless network, even if
they cannot use the wireless network. Furthermore, there are ways for unauthorized wireless
users to get a valid user name and password. Then, they can use that user name and password
to use the wireless network.
Local user databases also have an additional limitation that is explained in the next section.
5.2.4 Encryption
Wireless networks can use encryption to protect the information that is sent in the wireless
network. Encryption is like a secret code. If you do not know the secret code, you cannot
understand the message.
The types of encryption you can choose depend on the type of user authentication. (See
Section 5.2.3 on page 72 for information about this.)
Table 22 Types of Encryption for Each Type of Authentication
NO AUTHENTICATION RADIUS SERVER
Weakest No Security WPA
Static WEP
WPA-PSK
Strongest WPA2-PSK WPA2
For example, if the wireless network has a RADIUS server, you can choose WPA or WPA2.
If users do not log in to the wireless network, you can choose no encryption, Static WEP,
WPA-PSK, or WPA2-PSK.
Usually, you should set up the strongest encryption that every wireless client in the wireless
network supports. For example, suppose the AP does not have a local user database, and you
do not have a RADIUS server. Therefore, there is no user authentication. Suppose the wireless
network has two wireless clients. Device A only supports WEP, and device B supports WEP
and WPA. Therefore, you should set up Static WEP in the wireless network.
72
NBG-318S User’s Guide
Page 73

Chapter 5 Wireless LAN
" It is recommended that wireless networks use WPA-PSK, WPA, or stronger
encryption. IEEE 802.1x and WEP encryption are better than none at all, but it
is still possible for unauthorized devices to figure out the original information
pretty quickly.
It is not possible to use WPA-PSK, WPA or stronger encryption with a local
user database. In this case, it is better to set up stronger encryption with no
authentication than to set up weaker encryption with the local user database.
When you select WPA2 or WPA2-PSK in your NBG-318S, you can also select an option
(WPA Compatible) to support WPA as well. In this case, if some wireless clients support
WPA and some support WPA2, you should set up WPA2-PSK or WPA2 (depending on the
type of wireless network login) and select the WPA Compatible option in the NBG-318S.
Many types of encryption use a key to protect the information in the wireless network. The
longer the key, the stronger the encryption. Every wireless client in the wireless network must
have the same key.
5.3 Roaming
A wireless station is a device with an IEEE 802.11a/b/g compliant wireless interface. An
access point (AP) acts as a bridge between the wireless and wired networks. An AP creates its
own wireless coverage area. A wireless station can associate with a particular access point
only if it is within the access point’s coverage area.
In a network environment with multiple access points, wireless stations are able to switch from
one access point to another as they move between the coverage areas. This is known as
roaming. As the wireless station moves from place to place, it is responsible for choosing the
most appropriate access point depending on the signal strength, network utilization or other
factors.
The roaming feature on the access points allows the access points to relay information about
the wireless stations to each other. When a wireless station moves from a coverage area to
another, it scans and uses the channel of a new access point, which then informs the other
access points on the LAN about the change. An example is shown in
With roaming, a wireless LAN mobile user enjoys a continuous connection to the wired
network through an access point while moving around the wireless LAN.
Enable roaming to exchange the latest bridge information of all wireless stations between APs
when a wireless station moves between coverage areas. Wireless stations can still associate
with other APs even if you disable roaming. Enabling roaming ensures correct traffic
forwarding (bridge tables are updated) and maximum AP efficiency. The AP deletes records
of wireless stations that associate with other APs (Non-ZyXEL APs may not be able to
perform this). 802.1x authentication information is not exchanged (at the time of writing).
Figure 37 on page 74.
NBG-318S User’s Guide
73
Page 74

Chapter 5 Wireless LAN
Figure 37 Roaming Example
The steps below describe the roaming process.
1 Wireless station Y moves from the coverage area of access point AP 1 to that of access
point AP 2.
2 Wireless station Y scans and detects the signal of access point AP 2.
3 Wireless station Y sends an association request to access point AP 2.
4 Access point AP 2 acknowledges the presence of wireless station Y and relays this
information to access point AP 1 through the wired LAN.
5 Access point AP 1 updates the new position of wireless station Y.
5.3.1 Requirements for Roaming
The following requirements must be met in order for wireless stations to roam between the
coverage areas.
1 All the access points must be on the same subnet and configured with the same ESSID.
2 If IEEE 802.1x user authentication is enabled and to be done locally on the access point,
the new access point must have the user profile for the wireless station.
3 The adjacent access points should use different radio channels when their coverage areas
overlap.
4 All access points must use the same port number to relay roaming information.
5 The access points must be connected to the Ethernet and be able to get IP addresses from
a DHCP server if using dynamic IP address assignment.
5.4 Quality of Service
This section discusses the Quality of Service (QoS) features available on the NBG-318S.
74
NBG-318S User’s Guide
Page 75

5.4.1 WMM QoS
WMM (Wi-Fi MultiMedia) QoS (Quality of Service) ensures quality of service in wireless
networks. It controls WLAN transmission priority on packets to be transmitted over the
wireless network.
WMM QoS prioritizes wireless traffic according to delivery requirements. WMM QoS is a
part of the IEEE 802.11e QoS enhancement to certified Wi-Fi wireless networks.
On APs without WMM QoS, all traffic streams are given the same access priority to the
wireless network. If the introduction of another traffic stream creates a data transmission
demand that exceeds the current network capacity, then the new traffic stream reduces the
throughput of the other traffic streams.
The NBG-318S uses WMM QoS to prioritize traffic streams according to the IEEE 802.1q tag
or DSCP information in each packet’s header. The NBG-318S automatically determines the
priority to use for an individual traffic stream. This prevents reductions in data transmission
for applications that are sensitive to latency (delay) and jitter (variations in delay).
5.4.1.1 WMM QoS Priorities
The following table describes the WMM QoS priority levels that the NBG-318S uses.
Table 23 WMM QoS Priorities
PRIORITY LEVEL DESCRIPTION
voice
(WMM_VOICE)
video
(WMM_VIDEO)
best effort
(WMM_BEST_EFFORT)
background
(WMM_BACKGROUND)
Chapter 5 Wireless LAN
Typically used for traffic that is especially sensitive to jitter. Use this priority
to reduce latency for improved voice quality.
Typically used for traffic which has some tolerance for jitter but needs to be
prioritized over other data traffic.
Typically used for traffic from applications or devices that lack QoS
capabilities. Use best effort priority for traffic that is less sensitive to latency,
but is affected by long delays, such as Internet surfing.
This is typically used for non-critical traffic such as bulk transfers and print
jobs that are allowed but that should not affect other applications and users.
Use background priority for applications that do
throughput requirements.
not have strict latency and
5.5 General Wireless LAN Screen
" If you are configuring the NBG-318S from a computer connected to the
wireless LAN and you change the NBG-318S’s SSID, channel or security
settings, you will lose your wireless connection when you press Apply to
confirm. You must then change the wireless settings of your computer to
match the NBG-318S’s new settings.
Click Network > Wireless LAN to open the General screen.
NBG-318S User’s Guide
75
Page 76

Chapter 5 Wireless LAN
Figure 38 Network > Wireless LAN > General
The following table describes the general wireless LAN labels in this screen.
Table 24 Network > Wireless LAN > General
LABEL DESCRIPTION
Enable
Wireless LAN
Name(SSID) (Service Set IDentity) The SSID identifies the Service Set with which a wireless
Hide SSID Select this check box to hide the SSID in the outgoing beacon frame so a station
Channel
Selection
Operating
Channel
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to reload the previous configuration for this screen.
Click the check box to activate wireless LAN.
station is associated. Wireless stations associating to the access point (AP) must
have the same SSID. Enter a descriptive name (up to 32 printable 7-bit ASCII
characters) for the wireless LAN.
cannot obtain the SSID through scanning using a site survey tool.
Set the operating frequency/channel depending on your particular region.
Select a channel from the drop-down list box. The options vary depending on
whether you are using A or B/G frequency band and the country you are in.
Refer to the Connection Wizard chapter for more information on channels.
This displays the channel the NBG-318S is currently using.
See the rest of this chapter for information on the other labels in this screen.
5.5.1 No Security
Select No Security to allow wireless stations to communicate with the access points without
any data encryption.
" If you do not enable any wireless security on your NBG-318S, your network is
accessible to any wireless networking device that is within range.
76
NBG-318S User’s Guide
Page 77

Chapter 5 Wireless LAN
Figure 39 Network > Wireless LAN > General: No Security
The following table describes the labels in this screen.
Table 25 Wireless No Security
LABEL DESCRIPTION
Security Mode Choose No Security from the drop-down list box.
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to reload the previous configuration for this screen.
5.5.2 WEP Encryption
WEP encryption scrambles the data transmitted between the wireless stations and the access
points to keep network communications private. It encrypts unicast and multicast
communications in a network. Both the wireless stations and the access points must use the
same WEP key.
Your NBG-318S allows you to configure up to four 64-bit or 128-bit WEP keys but only one
key can be enabled at any one time.
In order to configure and enable WEP encryption; click Network > Wireless LAN to display
the General screen. Select Static WEP from the Security Mode list.
NBG-318S User’s Guide
77
Page 78

Chapter 5 Wireless LAN
Figure 40 Network > Wireless LAN > General: Static WEP
The following table describes the wireless LAN security labels in this screen.
Table 26 Network > Wireless LAN > General: Static WEP
LABEL DESCRIPTION
Passphrase Enter a passphrase (password phrase) of up to 32 printable characters and click
Generate. The NBG-318S automatically generates four different WEP keys and
displays them in the Key fields below.
WEP
Encryption
Authentication
Method
ASCII Select this option in order to enter ASCII characters as WEP key.
Hex Select this option in order to enter hexadecimal characters as a WEP key.
Key 1 to Key 4 The WEP keys are used to encrypt data. Both the NBG-318S and the wireless
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to reload the previous configuration for this screen.
Select 64-bit WEP or 128-bit WEP to enable data encryption.
This field is activated when you select 64-bit WEP or 128-bit WEP in the WEP
Encryption field.
Select Auto, Open System or Shared Key from the drop-down list box.
The preceding "0x", that identifies a hexadecimal key, is entered automatically.
stations must use the same WEP key for data transmission.
If you chose 64-bit WEP, then enter any 5 ASCII characters or 10 hexadecimal
characters ("0-9", "A-F").
If you chose 128-bit WEP, then enter 13 ASCII characters or 26 hexadecimal
characters ("0-9", "A-F").
You must configure at least one key, only one key can be activated at any one time.
The default key is key 1.
78
NBG-318S User’s Guide
Page 79

5.5.3 WPA-PSK/WPA2-PSK
Click Network > Wireless LAN to display the General screen. Select WPA-PSK or WPA2-
PSK from the Security Mode list.
Figure 41 Network > Wireless LAN > General: WPA-PSK/WPA2-PSK
Chapter 5 Wireless LAN
The following table describes the labels in this screen.
Table 27 Network > Wireless LAN > General: WPA-PSK/WPA2-PSK
LABEL DESCRIPTION
WPA Compatible This check box is available only when you select WPA2-PSK or WPA2 in the
Security Mode field.
Select the check box to have both WPA2 and WPA wireless clients be able to
communicate with the NBG-318S even when the NBG-318S is using WPA2-PSK
or WPA2.
Pre-Shared Key The encryption mechanisms used for WPA/WPA2 and WPA-PSK/WPA2-PSK
ReAuthentication
Timer (in
seconds)
are the same. The only difference between the two is that WPA-PSK/WPA2-PSK
uses a simple common password, instead of user-specific credentials.
Type a pre-shared key from 8 to 63 case-sensitive ASCII characters (including
spaces and symbols).
Specify how often wireless stations have to resend usernames and passwords in
order to stay connected. Enter a time interval between 10 and 9999 seconds. The
default time interval is 1800 seconds (30 minutes).
Note: If wireless station authentication is done using a RADIUS
server, the reauthentication timer on the RADIUS server has
priority.
Idle Timeout The NBG-318S automatically disconnects a wireless station from the wired
network after a period of inactivity. The wireless station needs to enter the
username and password again before access to the wired network is allowed. The
default time interval is 3600 seconds (or 1 hour).
NBG-318S User’s Guide
79
Page 80

Chapter 5 Wireless LAN
Table 27 Network > Wireless LAN > General: WPA-PSK/WPA2-PSK
LABEL DESCRIPTION
Group Key
Update Timer
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to reload the previous configuration for this screen.
5.5.4 WPA/WPA2
Click Network > Wireless LAN to display the General screen. Select WPA or WPA2 from
the Security Mode list.
Figure 42 Network > Wireless LAN > General: WPA/WPA2
The Group Key Update Timer is the rate at which the AP (if using WPA-PSK/
WPA2-PSK key management) or RADIUS server (if using WPA/WPA2 key
management) sends a new group key out to all clients. The re-keying process is
the WPA/WPA2 equivalent of automatically changing the WEP key for an AP and
all stations in a WLAN on a periodic basis. Setting of the Group Key Update
Timer is also supported in WPA-PSK/WPA2-PSK mode. The default is 1800
seconds (30 minutes).
80
NBG-318S User’s Guide
Page 81

Chapter 5 Wireless LAN
The following table describes the labels in this screen.
Table 28 Network > Wireless LAN > General: WPA/WPA2
LABEL DESCRIPTION
WPA Compatible This check box is available only when you select WPA2-PSK or WPA2 in the
ReAuthentication
Timer (in seconds)
Security Mode field.
Select the check box to have both WPA2 and WPA wireless clients be able to
communicate with the NBG-318S even when the NBG-318S is using WPA2-PSK
or WPA2.
Specify how often wireless stations have to resend usernames and passwords in
order to stay connected. Enter a time interval between 10 and 9999 seconds.
The default time interval is 1800 seconds (30 minutes).
Note: If wireless station authentication is done using a RADIUS
server, the reauthentication timer on the RADIUS server
has priority.
Idle Timeout The NBG-318S automatically disconnects a wireless station from the wired
Group Key Update
Timer
Authentication Server
IP Address Enter the IP address of the external authentication server in dotted decimal
Port Number Enter the port number of the external authentication server. The default port
Shared Secret Enter a password (up to 31 alphanumeric characters) as the key to be shared
Accounting Server
Active Select Yes from the drop down list box to enable user accounting through an
IP Address Enter the IP address of the external accounting server in dotted decimal notation.
Port Number Enter the port number of the external accounting server. The default port number
Shared Secret Enter a password (up to 31 alphanumeric characters) as the key to be shared
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to reload the previous configuration for this screen.
network after a period of inactivity. The wireless station needs to enter the
username and password again before access to the wired network is allowed.
The default time interval is 3600 seconds (or 1 hour).
The Group Key Update Timer is the rate at which the AP (if using WPA-PSK/
WPA2-PSK key management) or RADIUS server (if using WPA/WPA2 key
management) sends a new group key out to all clients. The re-keying process is
the WPA/WPA2 equivalent of automatically changing the WEP key for an AP
and all stations in a WLAN on a periodic basis. Setting of the Group Key Update
Timer is also supported in WPA-PSK/WPA2-PSK mode. The NBG-318S default
is 1800 seconds (30 minutes).
notation.
number is 1812.
You need not change this value unless your network administrator instructs you
to do so with additional information.
between the external authentication server and the NBG-318S.
The key must be the same on the external authentication server and your NBG-
318S. The key is not sent over the network.
external authentication server.
is 1813.
You need not change this value unless your network administrator instructs you
to do so with additional information.
between the external accounting server and the NBG-318S.
The key must be the same on the external accounting server and your NBG-
318S. The key is not sent over the network.
NBG-318S User’s Guide
81
Page 82

Chapter 5 Wireless LAN
5.6 MAC Filter
The MAC filter screen allows you to configure the NBG-318S to give exclusive access to up
to 32 devices (Allow) or exclude up to 32 devices from accessing the NBG-318S (Deny).
Every Ethernet device has a unique MAC (Media Access Control) address. The MAC address
is assigned at the factory and consists of six pairs of hexadecimal characters, for example,
00:A0:C5:00:00:02. You need to know the MAC address of the devices to configure this
screen.
To change your NBG-318S’s MAC filter settings, click Network > Wireless LAN > MAC
Filter. The screen appears as shown.
Figure 43 Network > Wireless LAN > MAC Filter
82
The following table describes the labels in this menu.
Table 29 Network > Wireless LAN > MAC Filter
LABEL DESCRIPTION
Active Select Ye s from the drop down list box to enable MAC address filtering.
Filter Action Define the filter action for the list of MAC addresses in the MAC Address table.
Select Deny to block access to the NBG-318S, MAC addresses not listed will be
allowed to access the NBG-318S
Select Allow to permit access to the NBG-318S, MAC addresses not listed will be
denied access to the NBG-318S.
NBG-318S User’s Guide
Page 83

Table 29 Network > Wireless LAN > MAC Filter
LABEL DESCRIPTION
Set This is the index number of the MAC address.
MAC
Address
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to reload the previous configuration for this screen.
Enter the MAC addresses of the wireless station that are allowed or denied access to
the NBG-318S in these address fields. Enter the MAC addresses in a valid MAC
address format, that is, six hexadecimal character pairs, for example,
12:34:56:78:9a:bc.
5.7 Wireless LAN Advanced Screen
Click Network > Wireless LAN > Advanced. The screen appears as shown.
Figure 44 Network > Wireless LAN > Advanced
Chapter 5 Wireless LAN
The following table describes the labels in this screen.
Table 30 Network > Wireless LAN > Advanced
LABEL DESCRIPTION
Roaming Configuration
Enable
Roaming
Wireless Advanced Setup
RTS/CTS
Threshold
Fragmentation
Threshold
NBG-318S User’s Guide
Select this option if your network environment has multiple APs and you want your
wireless device to be able to access the network as you move between wireless
networks.
Data with its frame size larger than this value will perform the RTS (Request To
Send)/CTS (Clear To Send) handshake.
If the RTS/CTS value is greater than the Fragmentation Threshold value, then the
RTS/CTS handshake will never occur as data frames will be fragmented before they
reach RTS/CTS size.
Enter a value between 0 and 2432.
It is the maximum data fragment size that can be sent. Enter a value between 256
and 2432.
83
Page 84

Chapter 5 Wireless LAN
Table 30 Network > Wireless LAN > Advanced
LABEL DESCRIPTION
Enable IntraBSS Traffic
Output Power Set the output power of the NBG-318S in this field. If there is a high density of APs
802.11 Mode Select 802.11b to allow only IEEE 802.11b compliant WLAN devices to associate
Super G Mode Use this field to enable or disable the Super G function. Super G mode is available
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to reload the previous configuration for this screen.
A Basic Service Set (BSS) exists when all communications between wireless clients
or between a wireless client and a wired network client go through one access point
(AP).
Intra-BSS traffic is traffic between wireless clients in the BSS. When Intra-BSS is
enabled, wireless client A and B can access the wired network and communicate
with each other. When Intra-BSS is disabled, wireless client A and B can still access
the wired network but cannot communicate with each other.
within an area, decrease the output power of the NBG-318S to reduce interference
with other APs.
with the NBG-318S.
Select 802.11g to allow only IEEE 802.11g compliant WLAN devices to associate
with the NBG-318S.
Select 802.11b/g to allow either IEEE802.11b or IEEE802.11g compliant WLAN
devices to associate with the NBG-318S. The transmission rate of your NBG-318S
might be reduced.
only if you select 802.11g or 802.11b/g in the 802.11 Mode field.
Super G provides higher data transmission rates than 802.11g.
Select Disabled if your wireless clients do not support Super G.
Select Super G with Dynamic Turbo if some or all of your wireless clients support
Super G with Dynamic Turbo. Dynamic Turbo uses two channels bonded together to
achieve higher transmission rates than 802.11g or Super G without Dynamic Turbo.
Dynamic turbo is on only when all wireless devices on the network support it. The
wireless channel is automatically fixed at 6 if you select this mode.
Select Super G without Turbo if the wireless clients on your network support Super
G but do not support dynamic turbo.
5.8 Quality of Service (QoS) Screen
The QoS screen allows you to automatically give a service (such as e-mail, VoIP or FTP) a
priority level.
Click Network > Wireless LAN > QoS. The following screen appears.
84
NBG-318S User’s Guide
Page 85

Figure 45 Network > Wireless LAN > QoS
Chapter 5 Wireless LAN
The following table describes the labels in this screen.
Table 31 Network > Wireless LAN > QoS
LABEL DESCRIPTION
Enable WMM QoS Select this to turn on WMM QoS (Wireless MultiMedia Quality of
WMM QoS Policy Select Default to have the NBG-318S automatically give a service
# This is the number of an individual application entry.
Name This field displays a description given to an application entry.
Service This field displays either FTP, WWW, E-mail or a User Defined
Dest Port This field displays the destination port number to which the
Service). The NBG-318S assigns priority to packets based on the
802.1q or DSCP information in their headers. If a packet has no
WMM information in its header, it is assigned the default priority.
a priority level according to the ToS value in the IP header of
packets it sends. WMM QoS (Wifi MultiMedia Quality of Service)
gives high priority to voice and video, which makes them run more
smoothly.
Select Application Priority from the drop-down list box to display a
table of application names, services, ports and priorities to which
you want to apply WMM QoS.
The table appears only if you select Application Priority in WMM
QoS Policy.
service to which you want to apply WMM QoS.
application sends traffic.
NBG-318S User’s Guide
85
Page 86

Chapter 5 Wireless LAN
Table 31 Network > Wireless LAN > QoS (continued)
LABEL DESCRIPTION
Priority This field displays the priority of the application.
Highest - Typically used for voice or video that should be highquality.
High - Typically used for voice or video that can be medium-quality.
Mid - Typically used for applications that do not fit into another
priority. For example, Internet surfing.
Low - Typically used for non-critical “background” applications,
such as large file transfers and print jobs that should not affect
other applications.
Modify Click the Edit icon to open the Application Priority Configuration
Apply Click Apply to save your changes to the NBG-318S.
screen. Modify an existing application entry or create a application
entry in the Application Priority Configuration screen.
Click the Remove icon to delete an application entry.
5.8.1 Application Priority Configuration
Use this screen to edit a WMM QoS application entry. Click the edit icon under Modify. The
following screen displays.
Figure 46 Network > Wireless LAN > QoS: Application Priority Configuration
See Appendix F on page 267 for a list of commonly-used services and destination ports. The
following table describes the fields in this screen.
Table 32 Network > Wireless LAN > QoS: Application Priority Configuration
LABEL DESCRIPTION
Application Priority Configuration
Name Type a description of the application priority.
86
NBG-318S User’s Guide
Page 87

Chapter 5 Wireless LAN
Table 32 Network > Wireless LAN > QoS: Application Priority Configuration (continued)
LABEL DESCRIPTION
Service The following is a description of the applications you can prioritize with WMM
QoS. Select a service from the drop-down list box.
• E-Mail
Electronic mail consists of messages sent through a computer network to
specific groups or individuals. Here are some default ports for e-mail:
POP3 - port 110
IMAP - port 143
SMTP - port 25
HTTP - port 80
•FTP
File Transfer Protocol enables fast transfer of files, including large files that it
may not be possible to send via e-mail. FTP uses port number 21.
•WWW
The World Wide Web is an Internet system to distribute graphical, hyperlinked information, based on Hyper Text Transfer Protocol (HTTP) - a client/
server protocol for the World Wide Web. The Web is not synonymous with the
Internet; rather, it is just one service on the Internet. Other services on the
Internet include Internet Relay Chat and Newsgroups. The Web is accessed
through use of a browser.
•User-Defined
User-defined services are user specific services configured using known ports
and applications.
Dest Port This displays the port the selected service uses. Type a port number in the
field provided if you want to use a different port to the default port.
Priority Select a priority from the drop-down list box.
Apply Click Apply to save your changes back to the NBG-318S.
Cancel Click Cancel to return to the previous screen.
NBG-318S User’s Guide
87
Page 88

Chapter 5 Wireless LAN
88
NBG-318S User’s Guide
Page 89

CHAPTER 6
WAN
This chapter describes how to configure WAN settings.
6.1 WAN Overview
See the chapter about the connection wizard for more information on the fields in the WAN
screens.
6.2 WAN MAC Address
The MAC address screen allows users to configure the WAN port's MAC address by either
using the factory default or cloning the MAC address from a computer on your LAN. Choose
Factory Default to select the factory assigned default MAC Address.
Otherwise, click Clone the computer's MAC address - IP Address and enter the IP address
of the computer on the LAN whose MAC you are cloning. Once it is successfully configured,
the address will be copied to the rom file (ZyNOS configuration file). It will not change unless
you change the setting or upload a different ROM file.
MAC address prior to hooking up the WAN Port.
6.3 Multicast
Traditionally, IP packets are transmitted in one of either two ways - Unicast (1 sender - 1
recipient) or Broadcast (1 sender - everybody on the network). Multicast delivers IP packets to
a group of hosts on the network - not everybody and not just 1.
IGMP (Internet Group Multicast Protocol) is a network-layer protocol used to establish
membership in a Multicast group - it is not used to carry user data. IGMP version 2 (RFC
2236) is an improvement over version 1 (RFC 1112) but IGMP version 1 is still in wide use. If
you would like to read more detailed information about interoperability between IGMP
version 2 and version 1, please see sections 4 and 5 of RFC 2236. The class D IP address is
used to identify host groups and can be in the range 224.0.0.0 to 239.255.255.255. The address
224.0.0.0 is not assigned to any group and is used by IP multicast computers. The address
224.0.0.1 is used for query messages and is assigned to the permanent group of all IP hosts
(including gateways). All hosts must join the 224.0.0.1 group in order to participate in IGMP.
The address 224.0.0.2 is assigned to the multicast routers group.
It is recommended that you clone the
NBG-318S User’s Guide
89
Page 90

Chapter 6 WAN
The NBG-318S supports both IGMP version 1 (IGMP-v1) and IGMP version 2 (IGMP-v2).
At start up, the NBG-318S queries all directly connected networks to gather group
membership. After that, the NBG-318S periodically updates this information. IP multicasting
can be enabled/disabled on the NBG-318S LAN and/or WAN interfaces in the web
configurator (LAN; WA N ). Select None to disable IP multicasting on these interfaces.
6.4 Internet Connection
Use this screen to change your NBG-318S’s Internet access settings. Click Network > WA N.
The screen differs according to the encapsulation you choose.
6.4.1 Ethernet Encapsulation
This screen displays when you select Ethernet encapsulation.
Figure 47 Network > WAN > Internet Connection: Ethernet Encapsulation
90
NBG-318S User’s Guide
Page 91

Chapter 6 WAN
The following table describes the labels in this screen.
Table 33 Network > WAN > Internet Connection: Ethernet Encapsulation
LABEL DESCRIPTION
Encapsulation You must choose the Ethernet option when the WAN port is used as a regular
Service Type Choose from Standard, RR-Telstra (RoadRunner Telstra authentication
User Name Type the user name given to you by your ISP.
Password Type the password associated with the user name above.
Retype to Confirm Type your password again to make sure that you have entered is correctly.
Login Server IP
Address
Login Server
(Telia Login only)
Relogin
Every(min) (Telia
Login only)
WAN IP Address Assignment
Get automatically
from ISP
Use Fixed IP
Address
IP Address Enter your WAN IP address in this field if you selected Use Fixed IP Address.
IP Subnet
Mask
Gateway IP
Address
DNS Servers
First DNS Server
Second DNS
Server
Third DNS Server
WAN MAC
Address
Factory default Select Factory default to use the factory assigned default MAC Address.
Clone the
computer’s MAC
address
Ethernet.
method), RR-Manager (Roadrunner Manager authentication method), RR-
Tosh iba (Roadrunner Toshiba authentication method) or Telia Login.
The following fields do not appear with the Standard service type.
Type the authentication server IP address here if your ISP gave you one.
This field is not available for Telia Login.
Type the domain name of the Telia login server, for example login1.telia.com.
The Telia server logs the NBG-318S out if the NBG-318S does not log in
periodically. Type the number of minutes from 1 to 59 (30 default) for the NBG318S to wait between logins.
Select this option If your ISP did not assign you a fixed IP address. This is the
default selection.
Select this option If the ISP assigned a fixed IP address.
Enter the IP Subnet Mask in this field.
Enter a Gateway IP Address (if your ISP gave you one) in this field.
Select From ISP if your ISP dynamically assigns DNS server information (and the
NBG-318S's WAN IP address). The field to the right displays the (read-only) DNS
server IP address that the ISP assigns.
Select User-Defined if you have the IP address of a DNS server. Enter the DNS
server's IP address in the field to the right. If you chose User-Defined, but leave
the IP address set to 0.0.0.0, User-Defined changes to None after you click
Apply. If you set a second choice to User-Defined, and enter the same IP
address, the second User-Defined changes to None after you click Apply.
Select None if you do not want to configure DNS servers. If you do not configure
a DNS server, you must know the IP address of a computer in order to access it.
The MAC address section allows users to configure the WAN port's MAC address
by either using the NBG-318S’s MAC address, copying the MAC address from a
computer on your LAN or manually entering a MAC address.
Select Clone the computer's MAC address - IP Address and enter the IP
address of the computer on the LAN whose MAC you are cloning. Once it is
successfully configured, the address will be copied to the rom file (ZyNOS
configuration file). It will not change unless you change the setting or upload a
different ROM file.
NBG-318S User’s Guide
91
Page 92

Chapter 6 WAN
Table 33 Network > WAN > Internet Connection: Ethernet Encapsulation
LABEL DESCRIPTION
Set WAN MAC
Address
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to begin configuring this screen afresh.
Select this option and enter the MAC address you want to use.
6.4.2 PPPoE Encapsulation
The NBG-318S supports PPPoE (Point-to-Point Protocol over Ethernet). PPPoE is an IETF
standard (RFC 2516) specifying how a personal computer (PC) interacts with a broadband
modem (DSL, cable, wireless, etc.) connection. The PPP over Ethernet option is for a dialup connection using PPPoE.
For the service provider, PPPoE offers an access and authentication method that works with
existing access control systems (for example Radius).
One of the benefits of PPPoE is the ability to let you access one of multiple network services,
a function known as dynamic service selection. This enables the service provider to easily
create and offer new IP services for individuals.
Operationally, PPPoE saves significant effort for both you and the ISP or carrier, as it requires
no specific configuration of the broadband modem at the customer site.
By implementing PPPoE directly on the NBG-318S (rather than individual computers), the
computers on the LAN do not need PPPoE software installed, since the NBG-318S does that
part of the task. Furthermore, with NAT, all of the LANs’ computers will have access.
This screen displays when you select PPPoE encapsulation.
92
NBG-318S User’s Guide
Page 93

Figure 48 Network > WAN > Internet Connection: PPPoE Encapsulation
Chapter 6 WAN
The following table describes the labels in this screen.
Table 34 Network > WAN > Internet Connection: PPPoE Encapsulation
LABEL DESCRIPTION
ISP Parameters for Internet Access
Encapsulation The PPP over Ethernet choice is for a dial-up connection using PPPoE. The NBG-
Service Name Type the PPPoE service name provided to you. PPPoE uses a service name to
User Name Type the user name given to you by your ISP.
Password Type the password associated with the user name above.
Retype to
Confirm
NBG-318S User’s Guide
318S supports PPPoE (Point-to-Point Protocol over Ethernet). PPPoE is an IETF
Draft standard (RFC 2516) specifying how a personal computer (PC) interacts with
a broadband modem (i.e. xDSL, cable, wireless, etc.) connection. Operationally,
PPPoE saves significant effort for both the end user and ISP/carrier, as it requires
no specific configuration of the broadband modem at the customer site. By
implementing PPPoE directly on the router rather than individual computers, the
computers on the LAN do not need PPPoE software installed, since the router does
that part of the task. Further, with NAT, all of the LAN's computers will have access.
identify and reach the PPPoE server.
Type your password again to make sure that you have entered is correctly.
93
Page 94

Chapter 6 WAN
Table 34 Network > WAN > Internet Connection: PPPoE Encapsulation
LABEL DESCRIPTION
Nailed-Up
Connection
Idle Timeout This value specifies the time in seconds that elapses before the router
WAN IP Address Assignment
Get automatically
from ISP
Use Fixed IP
Address
DNS Servers
First DNS Server
Second DNS
Server
Third DNS Server
WAN MAC
Address
Factory default Select Factory default to use the factory assigned default MAC Address.
Clone the
computer’s MAC
address
Set WAN MAC
Address
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to begin configuring this screen afresh.
My WAN IP
Address
Remote IP
Address
Remote IP
Subnet Mask
Select Nailed-Up Connection if you do not want the connection to time out.
automatically disconnects from the PPPoE server.
Select this option If your ISP did not assign you a fixed IP address. This is the
default selection.
Select this option If the ISP assigned a fixed IP address.
Enter your WAN IP address in this field if you selected Use Fixed IP Address.
Enter the remote IP address (if your ISP gave you one) in this field.
Enter the remote IP subnet mask in this field.
Select From ISP if your ISP dynamically assigns DNS server information (and the
NBG-318S's WAN IP address). The field to the right displays the (read-only) DNS
server IP address that the ISP assigns.
Select User-Defined if you have the IP address of a DNS server. Enter the DNS
server's IP address in the field to the right. If you chose User-Defined, but leave
the IP address set to 0.0.0.0, User-Defined changes to None after you click
Apply. If you set a second choice to User-Defined, and enter the same IP
address, the second User-Defined changes to None after you click Apply.
Select None if you do not want to configure DNS servers. If you do not configure a
DNS server, you must know the IP address of a computer in order to access it.
The MAC address section allows users to configure the WAN port's MAC address
by using the NBG-318S’s MAC address, copying the MAC address from a
computer on your LAN or manually entering a MAC address.
Select Clone the computer's MAC address - IP Address and enter the IP
address of the computer on the LAN whose MAC you are cloning. Once it is
successfully configured, the address will be copied to the rom file (ZyNOS
configuration file). It will not change unless you change the setting or upload a
different ROM file.
Select this option and enter the MAC address you want to use.
6.4.3 PPTP Encapsulation
Point-to-Point Tunneling Protocol (PPTP) is a network protocol that enables secure transfer of
data from a remote client to a private server, creating a Virtual Private Network (VPN) using
TCP/IP-based networks.
PPTP supports on-demand, multi-protocol and virtual private networking over public
networks, such as the Internet.
This screen displays when you select PPTP encapsulation.
94
NBG-318S User’s Guide
Page 95

Figure 49 Network > WAN > Internet Connection: PPTP Encapsulation
Chapter 6 WAN
NBG-318S User’s Guide
95
Page 96

Chapter 6 WAN
The following table describes the labels in this screen.
Table 35 Network > WAN > Internet Connection: PPTP Encapsulation
LABEL DESCRIPTION
ISP Parameters for Internet Access
Encapsulation Point-to-Point Tunneling Protocol (PPTP) is a network protocol that enables
User Name Type the user name given to you by your ISP.
Password Type the password associated with the User Name above.
Retype to Confirm Type your password again to make sure that you have entered is correctly.
Nailed-up Connection Select Nailed-Up Connection if you do not want the connection to time out.
Idle Timeout This value specifies the time in seconds that elapses before the NBG-318S
PPTP Configuration
Get automatically from
ISP
Use Fixed IP Address Select this option If the ISP assigned a fixed IP address.
WAN IP Address Assignment
Get automatically from
ISP
Use Fixed IP Address Select this option If the ISP assigned a fixed IP address.
DNS Servers
secure transfer of data from a remote client to a private server, creating a
Virtual Private Network (VPN) using TCP/IP-based networks. PPTP supports
on-demand, multi-protocol, and virtual private networking over public
networks, such as the Internet. The NBG-318S supports only one PPTP
server connection at any given time.
To configure a PPTP client, you must configure the User Name and
Password fields for a PPP connection and the PPTP parameters for a PPTP
connection.
automatically disconnects from the PPTP server.
Select this option If your ISP did not assign you a fixed IP address. This is the
default selection.
My IP Address Type the (static) IP address assigned to you by your ISP.
My IP Subnet
Mask
Server IP Address Type the IP address of the PPTP server.
Connection ID/
Name
My WAN IP
Address
Remote IP
Address
Remote IP Subnet
Mask
Your NBG-318S will automatically calculate the subnet mask based on the IP
address that you assign. Unless you are implementing subnetting, use the
subnet mask computed by the NBG-318S.
Type your identification name for the PPTP server.
Select this option If your ISP did not assign you a fixed IP address. This is the
default selection.
Enter your WAN IP address in this field if you selected Use Fixed IP
Address.
Enter the remote IP address (if your ISP gave you one) in this field.
Enter the remote IP subnet mask in this field.
96
NBG-318S User’s Guide
Page 97

Chapter 6 WAN
Table 35 Network > WAN > Internet Connection: PPTP Encapsulation
LABEL DESCRIPTION
First DNS Server
Second DNS Server
Third DNS Server
WAN MAC Address The MAC address section allows users to configure the WAN port's MAC
Factory default Select Factory default to use the factory assigned default MAC Address.
Clone the computer’s
MAC address
Set WAN MAC
Address
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to begin configuring this screen afresh.
Select From ISP if your ISP dynamically assigns DNS server information (and
the NBG-318S's WAN IP address). The field to the right displays the (readonly) DNS server IP address that the ISP assigns.
Select User-Defined if you have the IP address of a DNS server. Enter the
DNS server's IP address in the field to the right. If you chose User-Defined,
but leave the IP address set to 0.0.0.0, User-Defined changes to None after
you click Apply. If you set a second choice to User-Defined, and enter the
same IP address, the second User-Defined changes to None after you click
Apply.
Select None if you do not want to configure DNS servers. If you do not
configure a DNS server, you must know the IP address of a computer in order
to access it.
address by either using the NBG-318S’s MAC address, copying the MAC
address from a computer on your LAN or manually entering a MAC address.
Select Clone the computer's MAC address - IP Address and enter the IP
address of the computer on the LAN whose MAC you are cloning. Once it is
successfully configured, the address will be copied to the rom file (ZyNOS
configuration file). It will not change unless you change the setting or upload a
different ROM file.
Select this option and enter the MAC address you want to use.
6.5 Advanced WAN Screen
To change your NBG-318S’s advanced WAN settings, click Network > WA N > Advanced.
The screen appears as shown.
Figure 50 Network > WAN > Advanced
NBG-318S User’s Guide
97
Page 98

Chapter 6 WAN
The following table describes the labels in this screen.
Table 36 WAN > Advanced
LABEL DESCRIPTION
Multicast Setup
Multicast Select IGMP V-1, IGMP V-2 or None. IGMP (Internet Group Multicast
Windows Networking (NetBIOS over TCP/IP): NetBIOS (Network Basic Input/Output System) are TCP
or UDP broadcast packets that enable a computer to connect to and communicate with a LAN. For
some dial-up services such as PPPoE or PPTP, NetBIOS packets cause unwanted calls. However it
may sometimes be necessary to allow NetBIOS packets to pass through to the WAN in order to find a
computer on the WAN.
Allow between LAN
and WAN
Allow Trigger Dial Select this option to allow NetBIOS packets to initiate calls.
Apply Click Apply to save your changes back to the NBG-318S.
Reset Click Reset to begin configuring this screen afresh.
Protocol) is a network-layer protocol used to establish membership in a
Multicast group - it is not used to carry user data. IGMP version 2 (RFC 2236)
is an improvement over version 1 (RFC 1112) but IGMP version 1 is still in
wide use. If you would like to read more detailed information about
interoperability between IGMP version 2 and version 1, please see sections 4
and 5 of RFC 2236.
Select this check box to forward NetBIOS packets from the LAN to the WAN
and from the WAN to the LAN. If your firewall is enabled with the default
policy set to block WAN to LAN traffic, you also need to enable the default
WAN to LAN firewall rule that forwards NetBIOS traffic.
Clear this check box to block all NetBIOS packets going from the LAN to the
WAN and from the WAN to the LAN.
98
NBG-318S User’s Guide
Page 99

CHAPTER 7
LAN
This chapter describes how to configure LAN settings.
7.1 LAN Overview
A Local Area Network (LAN) is a shared communication system to which many computers
are attached. A LAN is a computer network limited to the immediate area, usually the same
building or floor of a building. The LAN screens can help you configure a LAN DHCP server,
manage IP addresses, and partition your physical network into logical networks.
7.1.1 IP Pool Setup
The NBG-318S is pre-configured with a pool of 32 IP addresses starting from 192.168.1.33 to
192.168.1.64. This configuration leaves 31 IP addresses (excluding the NBG-318S itself) in
the lower range (192.168.1.2 to 192.168.1.32) for other server computers, for instance, servers
for mail, FTP, TFTP, web, etc., that you may have.
7.1.2 System DNS Servers
Refer to the IP address and subnet mask section in the Connection Wizard chapter.
7.2 LAN TCP/IP
The NBG-318S has built-in DHCP server capability that assigns IP addresses and DNS
servers to systems that support DHCP client capability.
7.2.1 Factory LAN Defaults
The LAN parameters of the NBG-318S are preset in the factory with the following values:
• IP address of 192.168.1.1 with subnet mask of 255.255.255.0 (24 bits)
• DHCP server enabled with 32 client IP addresses starting from 192.168.1.33.
These parameters should work for the majority of installations. If your ISP gives you explicit
DNS server address(es), read the embedded web configurator help regarding what fields need
to be configured.
NBG-318S User’s Guide
99
Page 100

Chapter 7 LAN
7.2.2 IP Address and Subnet Mask
Refer to the IP address and subnet mask section in the Connection Wizard chapter for this
information.
7.2.3 Multicast
Traditionally, IP packets are transmitted in one of either two ways - Unicast (1 sender - 1
recipient) or Broadcast (1 sender - everybody on the network). Multicast delivers IP packets to
a group of hosts on the network - not everybody and not just 1.
IGMP (Internet Group Multicast Protocol) is a network-layer protocol used to establish
membership in a Multicast group - it is not used to carry user data. IGMP version 2 (RFC
2236) is an improvement over version 1 (RFC 1112) but IGMP version 1 is still in wide use. If
you would like to read more detailed information about interoperability between IGMP
version 2 and version 1, please see sections 4 and 5 of RFC 2236. The class D IP address is
used to identify host groups and can be in the range 224.0.0.0 to 239.255.255.255. The address
224.0.0.0 is not assigned to any group and is used by IP multicast computers. The address
224.0.0.1 is used for query messages and is assigned to the permanent group of all IP hosts
(including gateways). All hosts must join the 224.0.0.1 group in order to participate in IGMP.
The address 224.0.0.2 is assigned to the multicast routers group.
The NBG-318S supports both IGMP version 1 (IGMP-v1) and IGMP version 2 (IGMP-v2).
At start up, the NBG-318S queries all directly connected networks to gather group
membership. After that, the NBG-318S periodically updates this information. IP multicasting
can be enabled/disabled on the NBG-318S LAN and/or WAN interfaces in the web
configurator (LAN; WA N ). Select None to disable IP multicasting on these interfaces.
7.2.4 Any IP
Traditionally, you must set the IP addresses and the subnet masks of a computer and the NBG318S to be in the same subnet to allow the computer to access the Internet (through the NBG318S). In cases where your computer is required to use a static IP address in another network,
you may need to manually configure the network settings of the computer every time you want
to access the Internet via the NBG-318S.
With the Any IP feature and NAT enabled, the NBG-318S allows a computer to access the
Internet without changing the network settings (such as IP address and subnet mask) of the
computer, when the IP addresses of the computer and the NBG-318S are not in the same
subnet. Whether a computer is set to use a dynamic or static (fixed) IP address, you can simply
connect the computer to the NBG-318S and access the Internet.
The following figure depicts a scenario where a computer is set to use a static private IP
address in the corporate environment. In a residential house where a NBG-318S is installed,
you can still use the computer to access the Internet without changing the network settings,
even when the IP addresses of the computer and the NBG-318S are not in the same subnet.
100
NBG-318S User’s Guide
 Loading...
Loading...