
Chapter 11Certificates
Table 52 SECURITY > CERTIFICATES > My Certificates > Details (continued)
LABEL DESCRIPTION
Serial NumberThis field displays the certificate s identification number given by the certification
SubjectThis field displays information that identifies the owner of the certificate, such as
IssuerThis field displays identifying information about the certificate s issuing
Signature AlgorithmThis field displays the type of algorithm that was used to sign the certificate. The
Valid FromThis field displays the date that the certificate becomes applicable. The text
Valid ToThis field displays the date that the certificate expires. The text displays in red
Key AlgorithmThis field displays the type of algorithm that was used to generate the
Subject Alternative
Name
Key UsageThis field displays for what functions the certificate s key can be used. For
Basic ConstraintThis field displays general information about the certificate. For example,
MD5 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
SHA1 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
Certificate in PEM
(Base-64) Encoded
Format
ApplyClick Apply to save your changes back to the ZyXEL Device. You can only
CancelClick Cancel to quit and return to the My Certificates screen.
authority or generated by the ZyXEL Device.
Common Name (CN), Organizational Unit (OU), Organization (O) and Country
(C).
certification authority, such as Common Name, Organizational Unit,
Organization and Country.
With self-signed certificates, this is the same as the Subject Name field.
ZyXEL Device uses rsa-pkcs1-sha1 (RSA public-private key encryption
algorithm and the SHA1 hash algorithm). Some certification authorities may use
rsa-pkcs1-md5 (RSA public-private key encryption algorithm and the MD5 hash
algorithm).
displays in red and includes a Not Yet Valid! message if the certificate has not
yet become applicable.
and includes an Expiring! or Expired! message if the certificate is about to expire
or has already expired.
certificate s key pair (the ZyXEL Device uses RSA encryption) and the length of
the key set in bits (1024 bits for example).
This field displays the certificate owner%s IP address (IP), domain name (DNS)
or e-mail address (EMAIL).
example, "DigitalSignature# means that the key can be used to sign certificates
and "KeyEncipherment# means that the key can be used to encrypt text.
Subject Type=CA means that this is a certification authority s certificate and
"Path Length Constraint=1# means that there can only be one certification
authority in the certificate s path.
the MD5 algorithm.
the SHA1 algorithm.
This read-only text box displays the certificate or certification request in Privacy
Enhanced Mail (PEM) format. PEM uses 64 ASCII characters to convert the
binary certificate into a printable form.
You can copy and paste a certification request into a certification authority s web
page, an e-mail that you send to the certification authority or a text editor and
save the file on a management computer for later manual enrollment.
You can copy and paste a certificate into an e-mail to send to friends or
colleagues or you can copy and paste a certificate into a text editor and save the
file on a management computer for later distribution (via floppy disk for
example).
change the name, except in the case of a self-signed certificate, which you can
also set to be the default self-signed certificate that signs the imported trusted
remote host certificates.
NBG410W3G Series User s Guide
201

Chapter 11Certificates
11.7 My Certificate Export
Click SECURITY > CERTIFICATES > My Certificates and then a certificate!s export icon
to open the My Certificate Export screen. Follow the instructions in this screen to choose the
file format to use for saving the certificate from the ZyXEL Device to a computer.
11.7.1 Certificate File Export Formats
You can export a certificate in one of these file formats:
Binary X.509: This is an ITU-T recommendation that defines the formats for X.509
certificates.
Binary PKCS#12: This is a format for transferring public key and private key certificates.
The private key in a PKCS #12 file is within a password-encrypted envelope. The file!s
password is not connected to your certificate!s public or private passwords. Exporting a
PKCS #12 file creates this and you must provide it to decrypt the contents when you
import the file into the ZyXEL Device.
Figure 123 SECURITY > CERTIFICATES > My Certificates > Export
202
The following table describes the labels in this screen.
Table 53 SECURITY > CERTIFICATES > My Certificates > Export
LABEL DESCRIPTION
Export the certificate in
binary X.509 format.
Export the certificate
along with the
corresponding private
key in PKCS#12 format.
PasswordType the file s password to use for encrypting the private key. The password
Retype to confirmType the password to make sure that you have entered it correctly.
ApplyClick Apply and then Save in the File Download screen. The Save As
CancelClick Cancel to quit and return to the My Certificates screen.
Binary X.509 is an ITU-T recommendation that defines the formats for X.509
certificates.
PKCS#12 is a format for transferring public key and private key certificates.
You can also password-encrypt the private key in the PKCS #12 file. The
file s password is not connected to your certificate s public or private
passwords.
is optional, although you must specify one if you want to be able to import
the PKCS#12 format certificate into Netscape version 7.2.
screen opens, browse to the location that you want to use and click Save.
NBG410W3G Series User s Guide
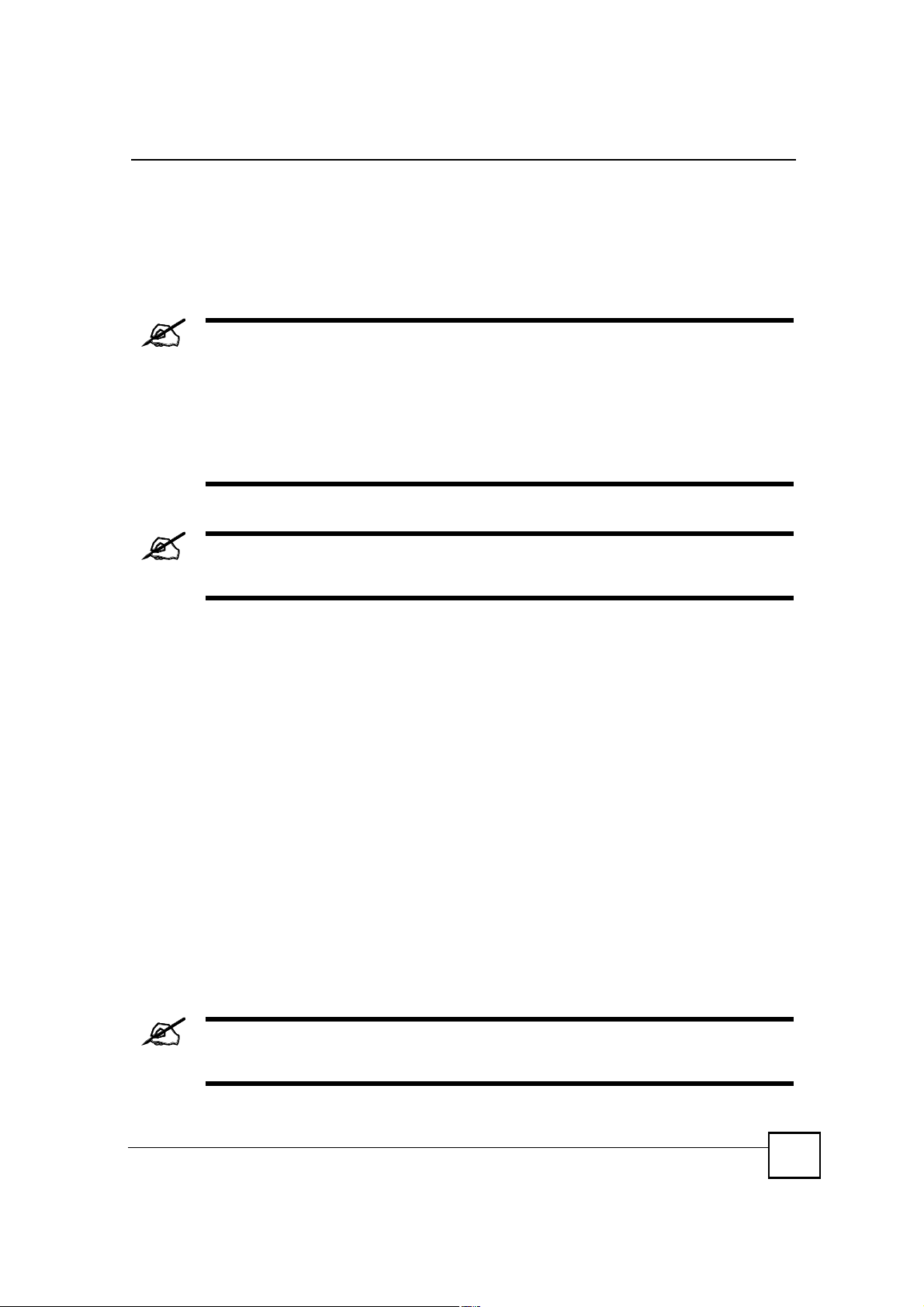
11.8 My Certificate Import
Click SECURITY > CERTIFICATES > My Certificates and then Import to open the My
Certificate Import screen. Follow the instructions in this screen to save an existing certificate
from a computer to the ZyXEL Device.
You can only import a certificate that matches a corresponding certification
request that was generated by the ZyXEL Device (the certification request
contains the private key). The certificate you import replaces the
corresponding request in the My Certificates screen.
One exception is that you can import a PKCS#12 format certificate without a
corresponding certification request since the certificate includes the private
key.
You must remove any spaces from the certificate s filename before you can
import it.
Chapter 11Certificates
11.8.1 Certificate File Formats
The certification authority certificate that you want to import has to be in one of these file
formats:
Binary X.509: This is an ITU-T recommendation that defines the formats for X.509
certificates.
PEM (Base-64) encoded X.509: This Privacy Enhanced Mail format uses 64 ASCII
characters to convert a binary X.509 certificate into a printable form.
Binary PKCS#7: This is a standard that defines the general syntax for data (including
digital signatures) that may be encrypted. The ZyXEL Device currently allows the
importation of a PKS#7 file that contains a single certificate.
PEM (Base-64) encoded PKCS#7: This Privacy Enhanced Mail (PEM) format uses 64
ASCII characters to convert a binary PKCS#7 certificate into a printable form.
Binary PKCS#12: This is a format for transferring public key and private key certificates.
The private key in a PKCS #12 file is within a password-encrypted envelope. The file!s
password is not connected to your certificate!s public or private passwords. Exporting a
PKCS #12 file creates this and you must provide it to decrypt the contents when you
import the file into the ZyXEL Device.
Be careful to not convert a binary file to text during the transfer process. It is
easy for this to occur since many programs use text files by default.
NBG410W3G Series User s Guide
203

Chapter 11Certificates
Figure 124 SECURITY > CERTIFICATES > My Certificates > Import
The following table describes the labels in this screen.
Table 54 SECURITY > CERTIFICATES > My Certificates > Import
LABEL DESCRIPTION
File Path Type in the location of the file you want to upload in this field or click Browse to find it.
Browse Click Browse to find the certificate file you want to upload.
ApplyClick Apply to save the certificate on the ZyXEL Device.
CancelClick Cancel to quit and return to the My Certificates screen.
When you import a binary PKCS#12 format certificate, another screen displays for you to
enter the password.
Figure 125 SECURITY > CERTIFICATES > My Certificates > Import: PKCS#12
The following table describes the labels in this screen.
Table 55 SECURITY > CERTIFICATES > My Certificates > Import: PKCS#12
LABEL DESCRIPTION
PasswordType the file s password that was created when the PKCS #12 file was exported.
ApplyClick Apply to save the certificate on the ZyXEL Device.
CancelClick Cancel to quit and return to the My Certificates screen.
204
NBG410W3G Series User s Guide

11.9 My Certificate Create
Click SECURITY > CERTIFICATES > My Certificates > Create to open the My
Certificate Create screen. Use this screen to have the ZyXEL Device create a self-signed
certificate, enroll a certificate with a certification authority or generate a certification request.
Figure 126 SECURITY > CERTIFICATES > My Certificates > Create (Basic)
Chapter 11Certificates
NBG410W3G Series User s Guide
205
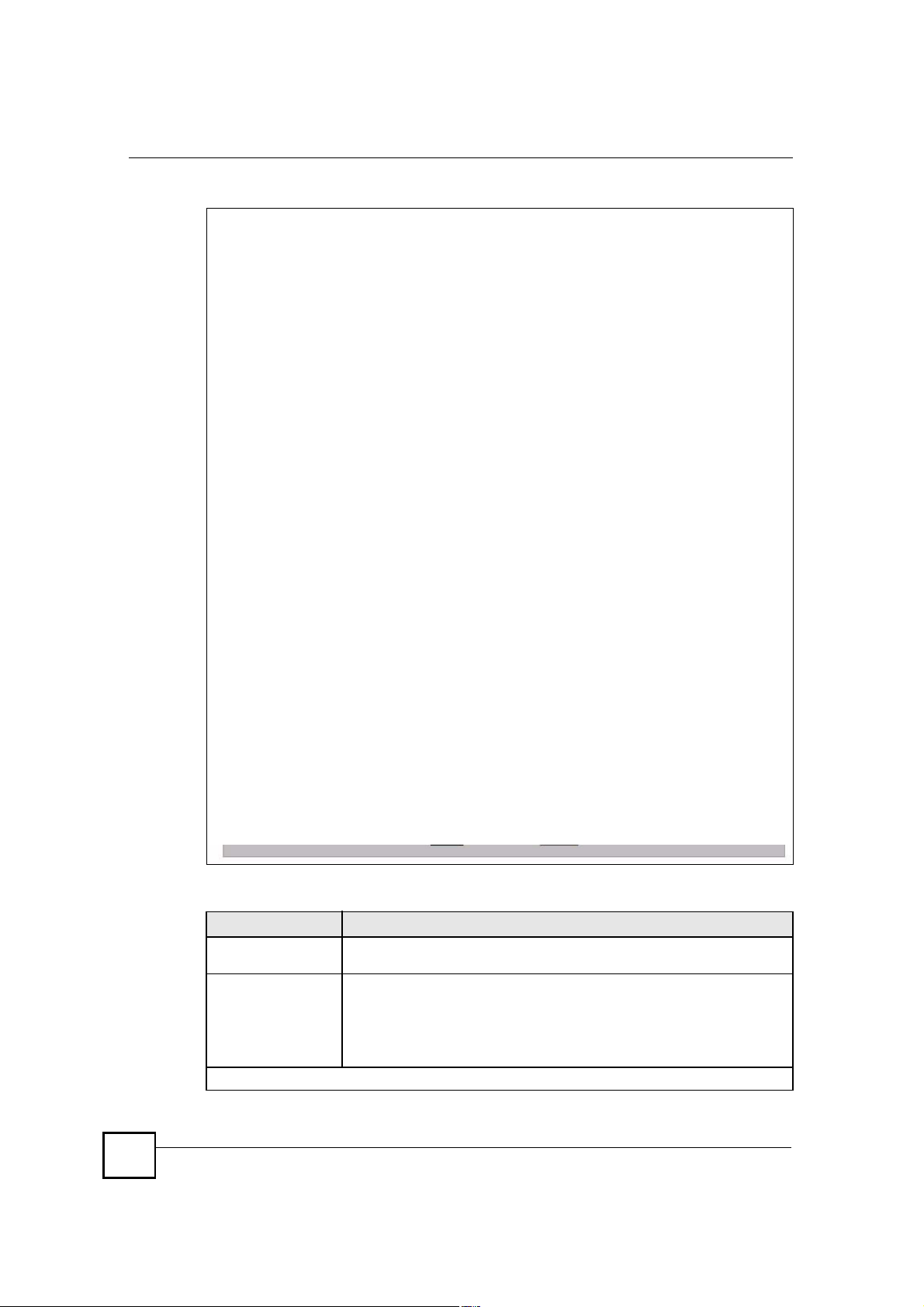
Chapter 11Certificates
Figure 127 SECURITY > CERTIFICATES > My Certificates > Create (Advanced)
206
The following table describes the labels in this screen.
Table 56 SECURITY > CERTIFICATES > My Certificates > Create
LABEL DESCRIPTION
Certificate NameType up to 31 ASCII characters (not including spaces) to identify this
certificate.
Subject InformationUse these fields to record information that identifies the owner of the
certificate. You do not have to fill in every field, but the Common Name is
mandatory if you click << Basic. The certification authority may add fields
(such as a serial number) to the subject information when it issues a
certificate. It is recommended that each certificate have unique subject
information.
The fields below display when you click << Basic.
NBG410W3G Series User s Guide
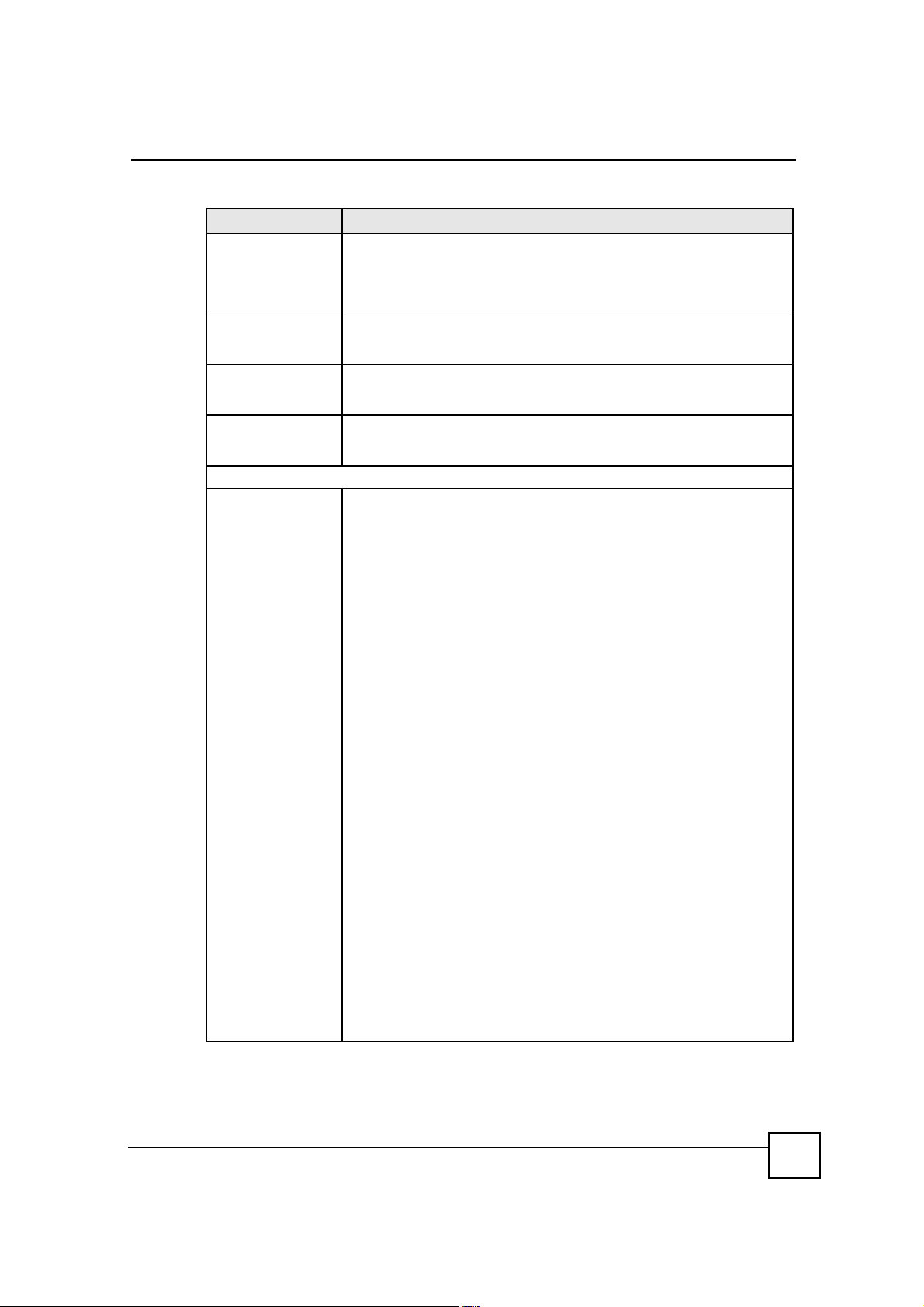
Chapter 11Certificates
Table 56 SECURITY > CERTIFICATES > My Certificates > Create (continued)
LABEL DESCRIPTION
Common Name Select a radio button to identify the certificate s owner by IP address, domain
Organizational UnitType up to 63 characters to identify the organizational unit or department to
OrganizationType up to 63 characters to identify the company or group to which the
CountryType up to 63 characters to identify the nation where the certificate owner is
The fields below display when you click Advanced >>.
Subject NameYou must configure at least one of these fields.
name or e-mail address. Type the IP address (in dotted decimal notation),
domain name or e-mail address in the field provided. The domain name or email address can be up to 31 ASCII characters. The domain name or e-mail
address is for identification purposes only and can be any string.
which the certificate owner belongs. You may use any character, including
spaces, but the ZyXEL Device drops trailing spaces.
certificate owner belongs. You may use any character, including spaces, but
the ZyXEL Device drops trailing spaces.
located. You may use any character, including spaces, but the ZyXEL Device
drops trailing spaces.
Select an item from the drop-down list box and enter the corresponding
information in the field to the right.
SN (serial number) - select this and enter the certificate s identification
number, such as the ZyXEL Device s MAC address. You can use up to 63
characters.
CN (common name) - select this and enter a name to identify the owner of the
certificate. You can use up to 63 characters.
OU (organizational unit) - select this and enter a unit within the organization
to identify the owner of the certificate. You can use up to 63 characters.
O (organization) - select this and enter an organization to identify the owner
of the certificate. You can use up to 63 characters.
DC (domain component) - select this and enter the domain component of a
domain to identify the owner of the certificate. For example, if the domain is
zyxel.com, the domain component is "zyxel# or "com#. You can use up to 63
characters.
L (locality name) - select this and enter the place where the owner of the
certificate resides, such as a city or county. You can use up to 63 characters.
ST (state or province name) - select this and enter the state or province in
which the owner of the certificate resides. You can use up to 63 characters.
C (country) - select this and enter the name of the country at which the owner
of the certificate resides. You can use up to 63 characters.
unstructuredName (PKCS 9 unname) - select this and enter the name of the
owner of the certificate as an unstructured ASCII string. You can use up to 63
characters. Check with the certificate s issuing certification authority for their
interpretation in this field if you select to apply to a certification authority for a
certificate.
unstructuredAddress (PKCS 9 unaddr) - select this and enter the address
of the owner of the certificate as an unstructured ASCII string. You can use up
to 63 characters. Check with the certificate s issuing certification authority for
their interpretation in this field if you select to apply to a certification authority
for a certificate.
MAILTO (PKCS 9 email address) - select this and enter the email address of
the owner of the certificate. You can use up to 63 characters. Check with the
certificate s issuing certification authority for their interpretation in this field if
you select to apply to a certification authority for a certificate.
NBG410W3G Series User s Guide
207

Chapter 11Certificates
Table 56 SECURITY > CERTIFICATES > My Certificates > Create (continued)
LABEL DESCRIPTION
Subject Alternative
Name
Key LengthSelect a number from the drop-down list box to determine how many bits the
<< Basic/Advanced >>Click << Basic to configure basic subject information. Click Advanced >> to
Enrollment OptionsThese radio buttons deal with how and when the certificate is to be generated.
Create a self-signed
certificate
Create a certification
request and save it
locally for later
manual enrollment
Create a certification
request and enroll for
a certificate
immediately online
Enrollment ProtocolSelect the certification authority s enrollment protocol from the drop-down list
CA Server Address Enter the IP address (or URL) of the certification authority server.
CA CertificateSelect the certification authority s certificate from the CA Certificate drop-
Enrollment via an RA If you select Create a certification request and enroll for a certificate
Select a radio button to identify the certificate s owner by IP address, domain
name or e-mail address. Type the IP address (in dotted decimal notation),
domain name or e-mail address in the field provided. The domain name or email address can be up to 31 ASCII characters. The domain name or e-mail
address is for identification purposes only and can be any string.
key should use (512 to 2048). The longer the key, the more secure it is. A
longer key also uses more PKI storage space.
configure more subject information for a certificate.
Select Create a self-signed certificate to have the ZyXEL Device generate
the certificate and act as the Certification Authority (CA) itself. This way you do
not need to apply to a certification authority for certificates.
Select Create a certification request and save it locally for later manual
enrollment to have the ZyXEL Device generate and store a request for a
certificate. Use the My Certificate Details screen to view the certification
request and copy it to send to the certification authority.
Copy the certification request from the My Certificate Details screen (see
Section 11.6 on page 200) and then send it to the certification authority.
Select Create a certification request and enroll for a certificate
immediately online to have the ZyXEL Device generate a request for a
certificate and apply to a certification authority for a certificate.
You must have the certification authority s certificate already imported in the
Trusted CAs screen.
When you select this option, you must select the certification authority s
enrollment protocol and the certification authority s certificate from the dropdown list boxes and enter the certification authority s server address. You also
need to fill in the Reference Number and Key if the certification authority
requires them.
box.
Simple Certificate Enrollment Protocol (SCEP) is a TCP-based enrollment
protocol that was developed by VeriSign and Cisco.
Certificate Management Protocol (CMP) is a TCP-based enrollment protocol
that was developed by the Public Key Infrastructure X.509 working group of
the Internet Engineering Task Force (IETF) and is specified in RFC 2510.
down list box.
You must have the certification authority s certificate already imported in the
Trusted CAs screen. Click Trusted CAs to go to the Trusted CAs screen
where you can view (and manage) the ZyXEL Device's list of certificates of
trusted certification authorities.
immediately online, you can select this option to apply for a certificate
through a RA (Registration Authority). The RA is an intermediary authorized by
a CA to verify each subscriber s identity and forward the requests to the CA.
After the CA signs and issues the certificates, the RA distributes the
certificates to the subscribers.
208
NBG410W3G Series User s Guide
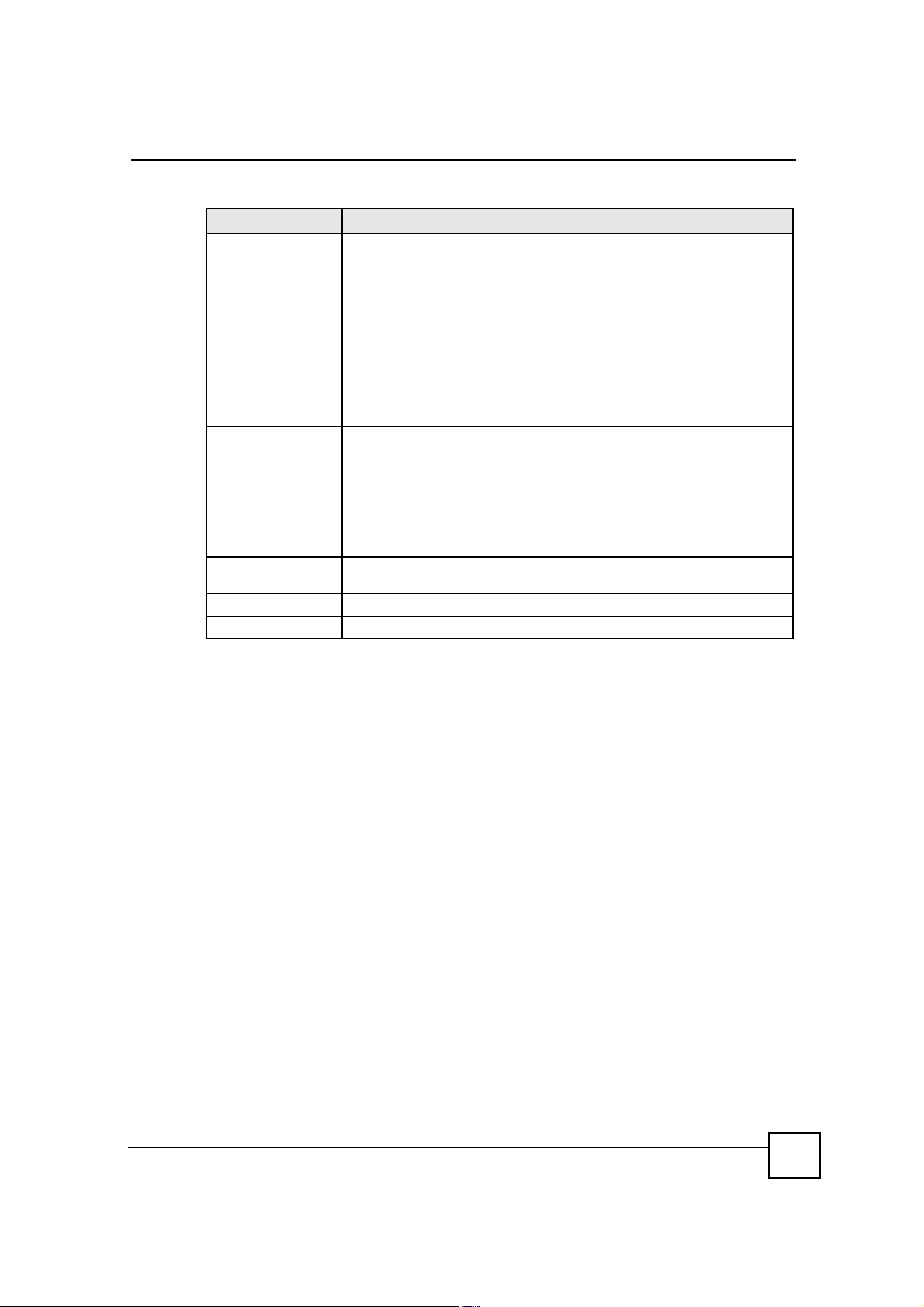
Chapter 11Certificates
Table 56 SECURITY > CERTIFICATES > My Certificates > Create (continued)
LABEL DESCRIPTION
RA Signing CertificateIf you select Enrollment via an RA, select the CA s RA signing certificate from
RA Encryption
Certificate
Request
Authentication
Reference NumberEnter the reference number that the certification authority gave you. You can
KeyType the key that the certification authority gave you. You can use up to 31
ApplyClick Apply to begin certificate or certification request generation.
CancelClick Cancel to quit and return to the My Certificates screen.
the drop-down list box. You must have the certificate already imported in the
Trusted CAs screen.
Click Trusted CAs to go to the Trusted CAs screen where you can view (and
manage) the ZyXEL Device's list of certificates of trusted certification
authorities.
If you select Enrollment via an RA, select the CA s RA encryption certificate
from the drop-down list box. You must have the certificate already imported in
the Trusted CAs screen.
Click Trusted CAs to go to the Trusted CAs screen where you can view (and
manage) the ZyXEL Device's list of certificates of trusted certification
authorities.
When you select Create a certification request and enroll for a certificate
immediately online, the certification authority may want you to include a
reference number and key to identify you when you send a certification
request. Fill in both the Reference Number and the Key fields if your
certification authority uses CMP enrollment protocol. Just fill in the Key field if
your certification authority uses the SCEP enrollment protocol.
use up to 31 ASCII printable characters. Spaces are allowed.
ASCII printable characters. Spaces are allowed.
After you click Apply in the My Certificate Create screen, you see a screen that tells you the
ZyXEL Device is generating the self-signed certificate or certification request.
After the ZyXEL Device successfully enrolls a certificate or generates a certification request
or a self-signed certificate, you see a screen with a Return button that takes you back to the
My Certificates screen.
If you configured the My Certificate Create screen to have the ZyXEL Device enroll a
certificate and the certificate enrollment is not successful, you see a screen with a Return
button that takes you back to the My Certificate Create screen. Click Return and check your
information in the My Certificate Create screen. Make sure that the certification authority
information is correct and that your Internet connection is working properly if you want the
ZyXEL Device to enroll a certificate online.
11.10 Trusted CAs
Click SECURITY > CERTIFICATES > Trusted CAs to open the Trusted CAs screen. This
screen displays a summary list of certificates of the certification authorities that you have set
the ZyXEL Device to accept as trusted. The ZyXEL Device accepts any valid certificate
signed by a certification authority on this list as being trustworthy; thus you do not need to
import any certificate that is signed by one of these certification authorities.
NBG410W3G Series User s Guide
209

Chapter 11Certificates
Figure 128 SECURITY > CERTIFICATES > Trusted CAs
The following table describes the labels in this screen.
Table 57 SECURITY > CERTIFICATES > Trusted CAs
LABEL DESCRIPTION
PKI Storage
Space in Use
#This field displays the certificate index number. The certificates are listed in
NameThis field displays the name used to identify this certificate.
SubjectThis field displays identifying information about the certificate s owner, such as CN
IssuerThis field displays identifying information about the certificate s issuing certification
Valid FromThis field displays the date that the certificate becomes applicable. The text
Valid ToThis field displays the date that the certificate expires. The text displays in red and
CRL IssuerThis field displays Yes if the certification authority issues CRL (Certificate
This bar displays the percentage of the ZyXEL Device s PKI storage space that is
currently in use. When the storage space is almost full, you should consider
deleting expired or unnecessary certificates before adding more certificates.
alphabetical order.
(Common Name), OU (Organizational Unit or department), O (Organization or
company) and C (Country). It is recommended that each certificate have unique
subject information.
authority, such as a common name, organizational unit or department,
organization or company and country. With self-signed certificates, this is the
same information as in the Subject field.
displays in red and includes a Not Yet Valid! message if the certificate has not yet
become applicable.
includes an Expiring! or Expired! message if the certificate is about to expire or
has already expired.
Revocation Lists) for the certificates that it has issued and you have selected the
Check incoming certificates issued by this CA against a CRL check box in the
certificate s details screen to have the ZyXEL Device check the CRL before
trusting any certificates issued by the certification authority. Otherwise the field
displays No.
210
NBG410W3G Series User s Guide

Table 57 SECURITY > CERTIFICATES > Trusted CAs (continued)
LABEL DESCRIPTION
ModifyClick the details icon to open a screen with an in-depth list of information about the
certificate.
Use the export icon to save the certificate to a computer. Click the icon and then
Save in the File Download screen. The Save As screen opens, browse to the
location that you want to use and click Save.
Click the delete icon to remove the certificate. A window displays asking you to
confirm that you want to delete the certificates. Note that subsequent certificates
move up by one when you take this action.
ImportClick Import to open a screen where you can save the certificate of a certification
authority that you trust, from your computer to the ZyXEL Device.
RefreshClick this button to display the current validity status of the certificates.
11.11 Trusted CA Details
Click SECURITY > CERTIFICATES > Trusted CAs to open the Trusted CAs screen.
Click the details icon to open the Trusted CA Details screen. Use this screen to view in-depth
information about the certification authority!s certificate, change the certificate!s name and set
whether or not you want the ZyXEL Device to check a certification authority!s list of revoked
certificates before trusting a certificate issued by the certification authority.
Chapter 11Certificates
NBG410W3G Series User s Guide
211

Chapter 11Certificates
Figure 129 SECURITY > CERTIFICATES > Trusted CAs > Details
212
The following table describes the labels in this screen.
Table 58 SECURITY > CERTIFICATES > Trusted CAs > Details
LABEL DESCRIPTION
NameThis field displays the identifying name of this certificate. If you want to change
Property
Check incoming
certificates issued
by this CA against a
CRL
the name, type up to 31 characters to identify this key certificate. You may use
any character (not including spaces).
Select this check box to have the ZyXEL Device check incoming certificates that
are issued by this certification authority against a Certificate Revocation List
(CRL).
Clear this check box to have the ZyXEL Device not check incoming certificates
that are issued by this certification authority against a Certificate Revocation List
(CRL).
NBG410W3G Series User s Guide

Chapter 11Certificates
Table 58 SECURITY > CERTIFICATES > Trusted CAs > Details (continued)
LABEL DESCRIPTION
Certification PathClick the Refresh button to have this read-only text box display the end entity s
RefreshClick Refresh to display the certification path.
Certificate
Information
TypeThis field displays general information about the certificate. CA-signed means
VersionThis field displays the X.509 version number.
Serial NumberThis field displays the certificate s identification number given by the certification
SubjectThis field displays information that identifies the owner of the certificate, such as
IssuerThis field displays identifying information about the certificate s issuing
Signature AlgorithmThis field displays the type of algorithm that was used to sign the certificate.
Valid FromThis field displays the date that the certificate becomes applicable. The text
Valid ToThis field displays the date that the certificate expires. The text displays in red
Key AlgorithmThis field displays the type of algorithm that was used to generate the
Subject Alternative
Name
Key UsageThis field displays for what functions the certificate s key can be used. For
Basic ConstraintThis field displays general information about the certificate. For example,
certificate and a list of certification authority certificates that shows the hierarchy
of certification authorities that validate the end entity s certificate. If the issuing
certification authority is one that you have imported as a trusted certification
authority, it may be the only certification authority in the list (along with the end
entity s own certificate). The ZyXEL Device does not trust the end entity s
certificate and displays "Not trusted# in this field if any certificate on the path has
expired or been revoked.
These read-only fields display detailed information about the certificate.
that a Certification Authority signed the certificate. Self-signed means that the
certificate s owner signed the certificate (not a certification authority). X.509
means that this certificate was created and signed according to the ITU-T X.509
recommendation that defines the formats for public-key certificates.
authority.
Common Name (CN), Organizational Unit (OU), Organization (O) and Country
(C).
certification authority, such as Common Name, Organizational Unit,
Organization and Country.
With self-signed certificates, this is the same information as in the Subject
Name field.
Some certification authorities use rsa-pkcs1-sha1 (RSA public-private key
encryption algorithm and the SHA1 hash algorithm). Other certification
authorities may use rsa-pkcs1-md5 (RSA public-private key encryption
algorithm and the MD5 hash algorithm).
displays in red and includes a Not Yet Valid! message if the certificate has not
yet become applicable.
and includes an Expiring! or Expired! message if the certificate is about to expire
or has already expired.
certificate s key pair (the ZyXEL Device uses RSA encryption) and the length of
the key set in bits (1024 bits for example).
This field displays the certificate s owner%s IP address (IP), domain name (DNS)
or e-mail address (EMAIL).
example, "DigitalSignature# means that the key can be used to sign certificates
and "KeyEncipherment# means that the key can be used to encrypt text.
Subject Type=CA means that this is a certification authority s certificate and
"Path Length Constraint=1# means that there can only be one certification
authority in the certificate s path.
NBG410W3G Series User s Guide
213

Chapter 11Certificates
Table 58 SECURITY > CERTIFICATES > Trusted CAs > Details (continued)
LABEL DESCRIPTION
CRL Distribution
Points
MD5 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
SHA1 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
Certificate in PEM
(Base-64) Encoded
Format
ApplyClick Apply to save your changes back to the ZyXEL Device. You can only
CancelClick Cancel to quit and return to the Trusted CAs screen.
This field displays how many directory servers with Lists of revoked certificates
the issuing certification authority of this certificate makes available. This field
also displays the domain names or IP addresses of the servers.
the MD5 algorithm. You can use this value to verify with the certification
authority (over the phone for example) that this is actually their certificate.
the SHA1 algorithm. You can use this value to verify with the certification
authority (over the phone for example) that this is actually their certificate.
This read-only text box displays the certificate or certification request in Privacy
Enhanced Mail (PEM) format. PEM uses 64 ASCII characters to convert the
binary certificate into a printable form.
You can copy and paste the certificate into an e-mail to send to friends or
colleagues or you can copy and paste the certificate into a text editor and save
the file on a management computer for later distribution (via floppy disk for
example).
change the name and/or set whether or not you want the ZyXEL Device to
check the CRL that the certification authority issues before trusting a certificate
issued by the certification authority.
11.12 Trusted CA Import
Click SECURITY > CERTIFICATES > Trusted CAs to open the Trusted CAs screen and
then click Import to open the Trusted CA Import screen. Follow the instructions in this
screen to save a trusted certification authority!s certificate from a computer to the ZyXEL
Device. The ZyXEL Device trusts any valid certificate signed by any of the imported trusted
CA certificates.
You must remove any spaces from the certificate s filename before you can
import the certificate.
214
NBG410W3G Series User s Guide

Chapter 11Certificates
Figure 130 SECURITY > CERTIFICATES > Trusted CAs > Import
The following table describes the labels in this screen.
Table 59 SECURITY > CERTIFICATES > Trusted CAs Import
LABEL DESCRIPTION
File Path Type in the location of the file you want to upload in this field or click Browse to find it.
Browse Click Browse to find the certificate file you want to upload.
ApplyClick Apply to save the certificate on the ZyXEL Device.
CancelClick Cancel to quit and return to the Trusted CAs screen.
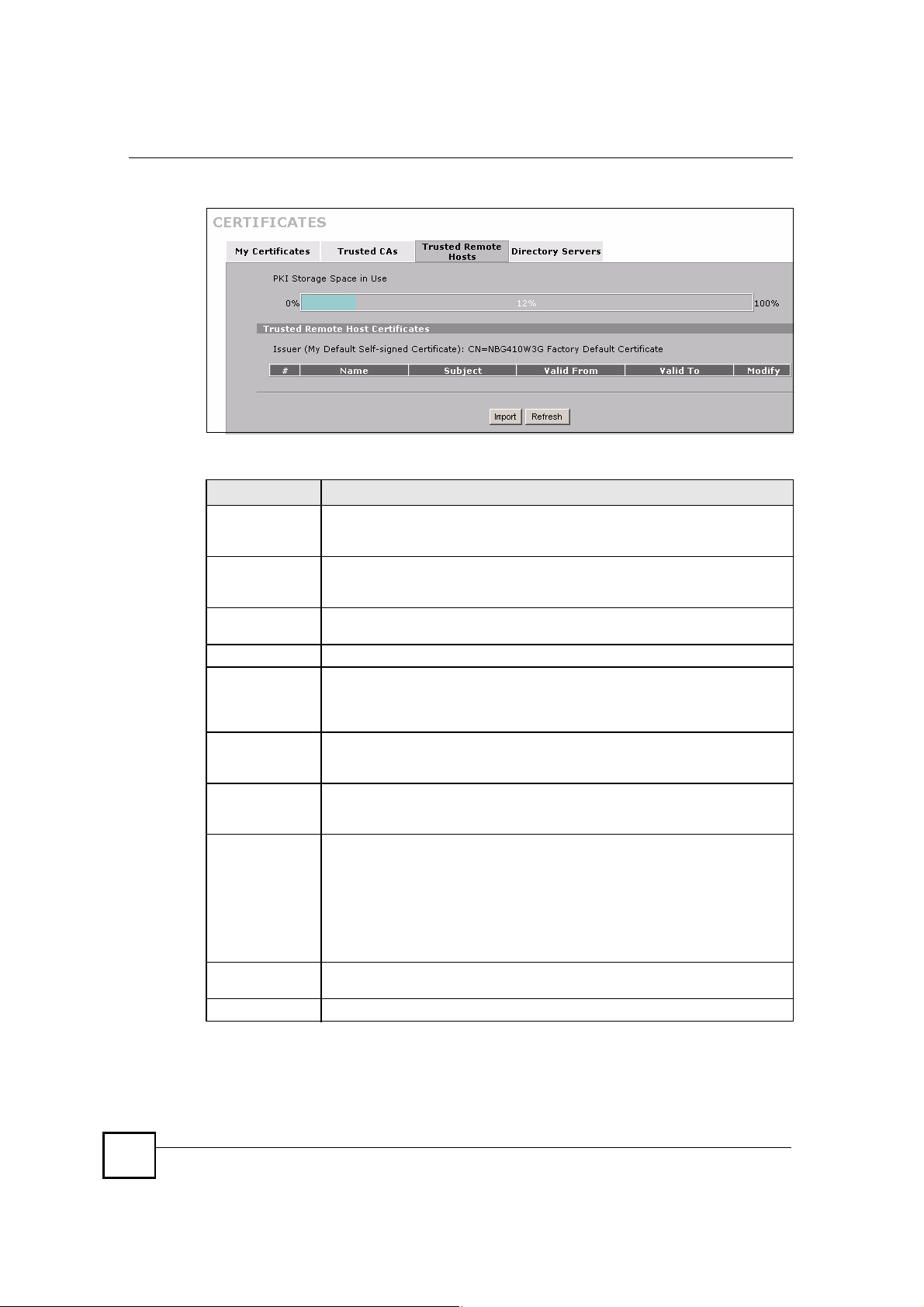
11.13 Trusted Remote Hosts
Click SECURITY > CERTIFICATES > Trusted Remote Hosts to open the Trusted
Remote Hosts screen. This screen displays a list of the certificates of peers that you trust but
which are not signed by one of the certification authorities on the Trusted CAs screen.
You do not need to add any certificate that is signed by one of the certification authorities on
the Trusted CAs screen since the ZyXEL Device automatically accepts any valid certificate
signed by a trusted certification authority as being trustworthy.
NBG410W3G Series User s Guide
215
Chapter 11Certificates
Figure 131 SECURITY > CERTIFICATES > Trusted Remote Hosts
The following table describes the labels in this screen.
Table 60 SECURITY > CERTIFICATES > Trusted Remote Hosts
LABEL DESCRIPTION
PKI Storage
Space in Use
Issuer (My Default
Self-signed
Certificate)
#This field displays the certificate index number. The certificates are listed in
NameThis field displays the name used to identify this certificate.
SubjectThis field displays identifying information about the certificate s owner, such as CN
Valid FromThis field displays the date that the certificate becomes applicable. The text
Valid ToThis field displays the date that the certificate expires. The text displays in red and
ModifyClick the details icon to open a screen with an in-depth list of information about the
ImportClick Import to open a screen where you can save the certificate of a remote host
RefreshClick this button to display the current validity status of the certificates.
This bar displays the percentage of the ZyXEL Device s PKI storage space that is
currently in use. When the storage space is almost full, you should consider
deleting expired or unnecessary certificates before adding more certificates.
This field displays identifying information about the default self-signed certificate
on the ZyXEL Device that the ZyXEL Device uses to sign the trusted remote host
certificates.
alphabetical order.
(Common Name), OU (Organizational Unit or department), O (Organization or
company) and C (Country). It is recommended that each certificate have unique
subject information.
displays in red and includes a Not Yet Valid! message if the certificate has not yet
become applicable.
includes an Expiring! or Expired! message if the certificate is about to expire or
has already expired.
certificate.
Use the export icon to save the certificate to a computer. Click the icon and then
Save in the File Download screen. The Save As screen opens, browse to the
location that you want to use and click Save.
Click the delete icon to remove the certificate. A window displays asking you to
confirm that you want to delete the certificate. Note that subsequent certificates
move up by one when you take this action.
(which you trust) from your computer to the ZyXEL Device.
216
NBG410W3G Series User s Guide
11.14 Trusted Remote Hosts Import
Click SECURITY > CERTIFICATES > Trusted Remote Hosts to open the Trusted
Remote Hosts screen and then click Import to open the Trusted Remote Host Import
screen.
You may have peers with certificates that you want to trust, but the certificates were not signed
by one of the certification authorities on the Trusted CAs screen. Follow the instructions in
this screen to save a peer!s certificates from a computer to the ZyXEL Device.
You do not need to add any certificate that is signed by one of the certification authorities on
the Trusted CAs screen since the ZyXEL Device automatically accepts any valid certificate
signed by a trusted certification authority as being trustworthy.
The trusted remote host certificate must be a self-signed certificate; and you
must remove any spaces from its filename before you can import it.
Figure 132 SECURITY > CERTIFICATES > Trusted Remote Hosts > Import
Chapter 11Certificates
The following table describes the labels in this screen.
Table 61 SECURITY > CERTIFICATES > Trusted Remote Hosts > Import
LABEL DESCRIPTION
File Path Type in the location of the file you want to upload in this field or click Browse to find it.
Browse Click Browse to find the certificate file you want to upload.
ApplyClick Apply to save the certificate on the ZyXEL Device.
CancelClick Cancel to quit and return to the Trusted Remote Hosts screen.
NBG410W3G Series User s Guide
217

Chapter 11Certificates
11.15 Trusted Remote Host Certificate Details
Click SECURITY > CERTIFICATES > Trusted Remote Hosts to open the Trusted
Remote Hosts screen. Click the details icon to open the Trusted Remote Host Details screen.
You can use this screen to view in-depth information about the trusted remote host!s certificate
and/or change the certificate!s name.
Figure 133 SECURITY > CERTIFICATES > Trusted Remote Hosts > Details
218
NBG410W3G Series User s Guide

Chapter 11Certificates
The following table describes the labels in this screen.
Table 62 SECURITY > CERTIFICATES > Trusted Remote Hosts > Details
LABEL DESCRIPTION
NameThis field displays the identifying name of this certificate. If you want to change
Certification PathClick the Refresh button to have this read-only text box display the end entity s
RefreshClick Refresh to display the certification path.
Certificate
Information
TypeThis field displays general information about the certificate. With trusted
VersionThis field displays the X.509 version number.
Serial NumberThis field displays the certificate s identification number given by the device
SubjectThis field displays information that identifies the owner of the certificate, such
IssuerThis field displays identifying information about the default self-signed
Signature AlgorithmThis field displays the type of algorithm that the ZyXEL Device used to sign the
Valid FromThis field displays the date that the certificate becomes applicable. The text
Valid ToThis field displays the date that the certificate expires. The text displays in red
Key AlgorithmThis field displays the type of algorithm that was used to generate the
Subject Alternative
Name
Key UsageThis field displays for what functions the certificate s key can be used. For
Basic ConstraintThis field displays general information about the certificate. For example,
the name, type up to 31 characters to identify this key certificate. You may use
any character (not including spaces).
own certificate and a list of certification authority certificates in the hierarchy of
certification authorities that validate a certificate s issuing certification authority.
For a trusted host, the list consists of the end entity s own certificate and the
default self-signed certificate that the ZyXEL Device uses to sign remote host
certificates.
These read-only fields display detailed information about the certificate.
remote host certificates, this field always displays CA-signed. The ZyXEL
Device is the Certification Authority that signed the certificate. X.509 means
that this certificate was created and signed according to the ITU-T X.509
recommendation that defines the formats for public-key certificates.
that created the certificate.
as Common Name (CN), Organizational Unit (OU), Organization (O) and
Country (C).
certificate on the ZyXEL Device that the ZyXEL Device uses to sign the trusted
remote host certificates.
certificate, which is rsa-pkcs1-sha1 (RSA public-private key encryption
algorithm and the SHA1 hash algorithm).
displays in red and includes a Not Yet Valid! message if the certificate has not
yet become applicable.
and includes an Expiring! or Expired! message if the certificate is about to
expire or has already expired.
certificate s key pair (the ZyXEL Device uses RSA encryption) and the length
of the key set in bits (1024 bits for example).
This field displays the certificate s owner%s IP address (IP), domain name
(DNS) or e-mail address (EMAIL).
example, "DigitalSignature# means that the key can be used to sign certificates
and "KeyEncipherment# means that the key can be used to encrypt text.
Subject Type=CA means that this is a certification authority s certificate and
"Path Length Constraint=1# means that there can only be one certification
authority in the certificate s path.
NBG410W3G Series User s Guide
219
Chapter 11Certificates
Table 62 SECURITY > CERTIFICATES > Trusted Remote Hosts > Details (continued)
LABEL DESCRIPTION
MD5 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
SHA1 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
Certificate in PEM
(Base-64) Encoded
Format
ApplyClick Apply to save your changes back to the ZyXEL Device. You can only
CancelClick Cancel to quit configuring this screen and return to the Trusted Remote
the MD5 algorithm. The ZyXEL Device uses one of its own self-signed
certificates to sign the imported trusted remote host certificates. This changes
the fingerprint value displayed here (so it does not match the original). See
Section 11.3 on page 196 for how to verify a remote host s certificate before
you import it into the ZyXEL Device.
the SHA1 algorithm. The ZyXEL Device uses one of its own self-signed
certificates to sign the imported trusted remote host certificates. This changes
the fingerprint value displayed here (so it does not match the original). See
Section 11.3 on page 196 for how to verify a remote host s certificate before
you import it into the ZyXEL Device.
This read-only text box displays the certificate or certification request in Privacy
Enhanced Mail (PEM) format. PEM uses 64 ASCII characters to convert the
binary certificate into a printable form.
You can copy and paste the certificate into an e-mail to send to friends or
colleagues or you can copy and paste the certificate into a text editor and save
the file on a management computer for later distribution (via floppy disk for
example).
change the name of the certificate.
Hosts screen.
11.16 Directory Servers
Click SECURITY > CERTIFICATES > Directory Servers to open the Directory Servers
screen. This screen displays a summary list of directory servers (that contain lists of valid and
revoked certificates) that have been saved into the ZyXEL Device. If you decide to have the
ZyXEL Device check incoming certificates against the issuing certification authority!s list of
revoked certificates, the ZyXEL Device first checks the server(s) listed in the CRL
Distribution Points field of the incoming certificate. If the certificate does not list a server or
the listed server is not available, the ZyXEL Device checks the servers listed here.
Figure 134 SECURITY > CERTIFICATES > Directory Servers
220
NBG410W3G Series User s Guide
Chapter 11Certificates
The following table describes the labels in this screen.
Table 63 SECURITY > CERTIFICATES > Directory Servers
LABEL DESCRIPTION
PKI Storage
Space in Use
#The index number of the directory server. The servers are listed in alphabetical
NameThis field displays the name used to identify this directory server.
AddressThis field displays the IP address or domain name of the directory server.
PortThis field displays the port number that the directory server uses.
ProtocolThis field displays the protocol that the directory server uses.
ModifyClick the details icon to open a screen where you can change the information
AddClick Add to open a screen where you can configure information about a directory
This bar displays the percentage of the ZyXEL Device s PKI storage space that is
currently in use. When the storage space is almost full, you should consider
deleting expired or unnecessary certificates before adding more certificates.
order.
about the directory server.
Click the delete icon to remove the directory server entry. A window displays
asking you to confirm that you want to delete the directory server. Note that
subsequent certificates move up by one when you take this action.
server so that the ZyXEL Device can access it.
11.17 Directory Server Add or Edit
Click SECURITY > CERTIFICATES > Directory Servers to open the Directory Servers
screen. Click Add (or the details icon) to open the Directory Server Add screen. Use this
screen to configure information about a directory server that the ZyXEL Device can access.
Figure 135 SECURITY > CERTIFICATES > Directory Server > Add
The following table describes the labels in this screen.
Table 64 SECURITY > CERTIFICATES > Directory Server > Add
LABEL DESCRIPTION
Directory Service
Setting
NameType up to 31 ASCII characters (spaces are not permitted) to identify this
directory server.
NBG410W3G Series User s Guide
221
Chapter 11Certificates
Table 64 SECURITY > CERTIFICATES > Directory Server > Add
LABEL DESCRIPTION
Access ProtocolUse the drop-down list box to select the access protocol used by the directory
Server AddressType the IP address (in dotted decimal notation) or the domain name of the
Server PortThis field displays the default server port number of the protocol that you select in
Login Setting
Login The ZyXEL Device may need to authenticate itself in order to assess the directory
PasswordType the password (up to 31 ASCII characters) from the entity maintaining the
ApplyClick Apply to save your changes back to the ZyXEL Device.
CancelClick Cancel to quit configuring this screen and return to the Directory Servers
A.At the time of writing, LDAP is the only choice of directory server access protocol.
server.
LDAP (Lightweight Directory Access Protocol) is a protocol over TCP that
specifies how clients access directories of certificates and lists of revoked
certificates.
directory server.
the Access Protocol field.
You may change the server port number if needed, however you must use the
same server port number that the directory server uses.
389 is the default server port number for LDAP.
server. Type the login name (up to 31 ASCII characters) from the entity
maintaining the directory server (usually a certification authority).
directory server (usually a certification authority).
screen.
A
222
NBG410W3G Series User s Guide
PART V
Advanced
Network Address Translation (NAT) (225)
Static Route (243)
DNS (247)
Remote Management (259)
UPnP (281)
Custom Application (291)
ALG Screen (293)
223
224
CHAPTER 12
Network Address Translation
(NAT)
This chapter discusses how to configure NAT on the ZyXEL Device.
12.1 NAT Overview
NAT (Network Address Translation - NAT, RFC 1631) is the translation of the IP address of a
host in a packet. For example, the source address of an outgoing packet, used within one
network is changed to a different IP address known within another network.
12.1.1 NAT Definitions
Inside/outside denotes where a host is located relative to the ZyXEL Device. For example, the
computers of your subscribers are the inside hosts, while the web servers on the Internet are
the outside hosts.
Global/local denotes the IP address of a host in a packet as the packet traverses a router. For
example, the local address refers to the IP address of a host when the packet is in the local
network, while the global address refers to the IP address of the host when the same packet is
traveling in the WAN side.
Note that inside/outside refers to the location of a host, while global/local refers to the IP
address of a host used in a packet. Thus, an inside local address (ILA) is the IP address of an
inside host in a packet when the packet is still in the local network, while an inside global
address (IGA) is the IP address of the same inside host when the packet is on the WAN side.
The following table summarizes this information.
Table 65 NAT Definitions
TERM DESCRIPTION
Inside This refers to the host on the LAN.
Outside This refers to the host on the WAN.
Local This refers to the packet address (source or destination) as the packet travels on the LAN.
Global This refers to the packet address (source or destination) as the packet travels on the
WAN.
NBG410W3G Series User s Guide
225

Chapter 12Network Address Translation (NAT)
NAT never changes the IP address (either local or global) of an outside host.
12.1.2 What NAT Does
In the simplest form, NAT changes the source IP address in a packet received from a
subscriber (the inside local address) to another (the inside global address) before forwarding
the packet to the WAN side. When the response comes back, NAT translates the destination
address (the inside global address) back to the inside local address before forwarding it to the
original inside host. Note that the IP address (either local or global) of an outside host is never
changed.
The global IP addresses for the inside hosts can be either static or dynamically assigned by the
ISP. In addition, you can designate servers (for example a web server and a telnet server) on
your local network and make them accessible to the outside world. Although you can make
designated servers on the LAN accessible to the outside world, it is strongly recommended
that you attach those servers to the DMZ port instead. If you do not define any servers (for
Many-to-One and Many-to-Many Overload mapping), NAT offers the additional benefit of
firewall protection. With no servers defined, your ZyXEL Device filters out all incoming
inquiries, thus preventing intruders from probing your network. For more information on IP
address translation, refer to RFC 1631, The IP Network Address Translator (NAT).
12.1.3 How NAT Works
Each packet has two addresses % a source address and a destination address. For outgoing
packets, the ILA (Inside Local Address) is the source address on the LAN, and the IGA (Inside
Global Address) is the source address on the WAN. For incoming packets, the ILA is the
destination address on the LAN, and the IGA is the destination address on the WAN. NAT
maps private (local) IP addresses to globally unique ones required for communication with
hosts on other networks. It replaces the original IP source address (and TCP or UDP source
port numbers for Many-to-One and Many-to-Many Overload NAT mapping) in each packet
and then forwards it to the Internet. The ZyXEL Device keeps track of the original addresses
and port numbers so incoming reply packets can have their original values restored. The
following figure illustrates this.
226
NBG410W3G Series User s Guide

Figure 136 How NAT Works
LAN
192.168.1.13
192.168.1.12
SA
192.168.1.10
Chapter 12Network Address Translation (NAT)
NAT Table
Inside Local
IP Address
192.168.1.10
192.168.1.11
192.168.1.12
192.168.1.13
Inside Global
IP Address
IGA 1
IGA 2
IGA 3
IGA 4
SA
IGA1
WAN
Internet
192.168.1.11
192.168.1.10
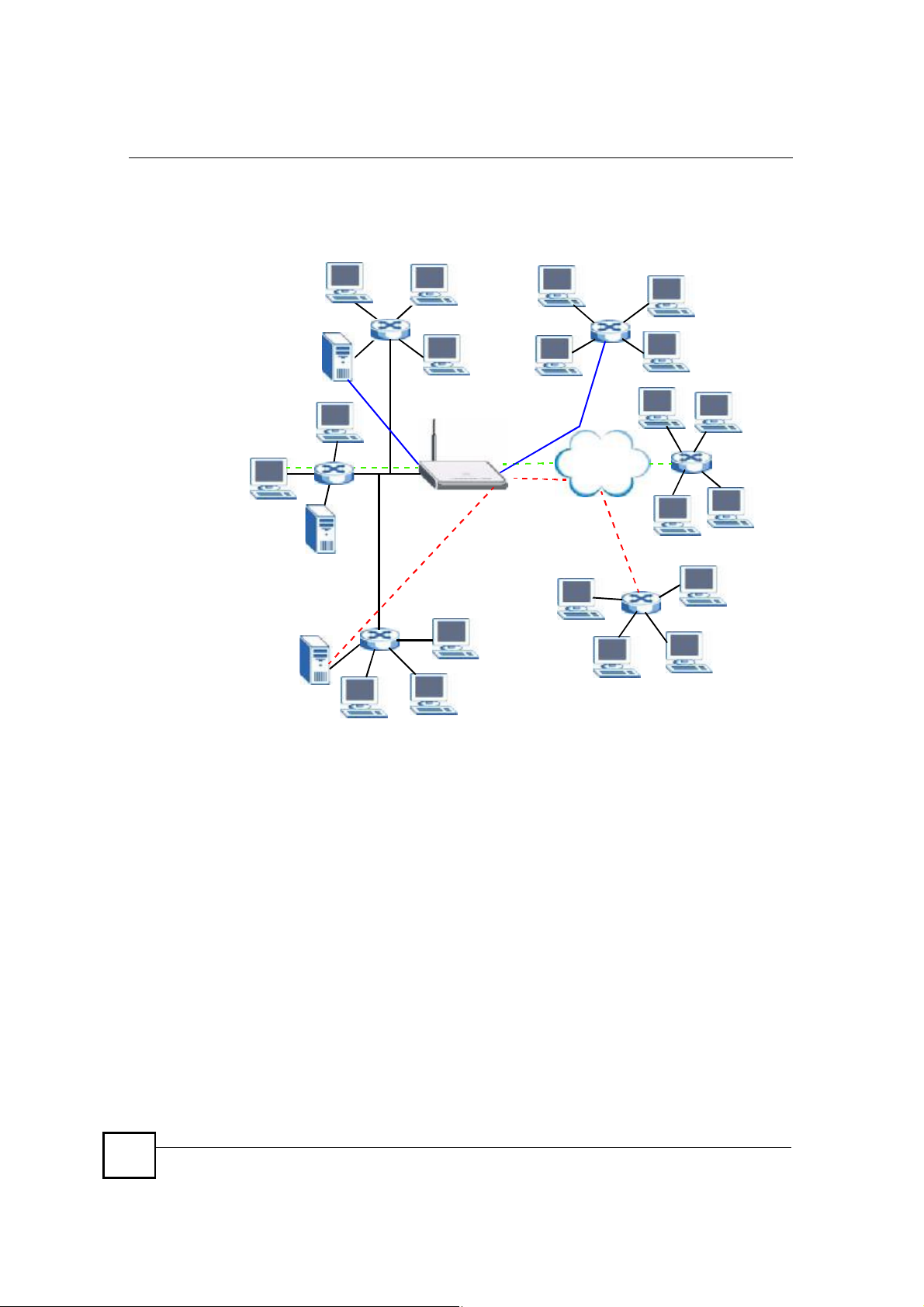
12.1.4 NAT Application
The following figure illustrates a possible NAT application, where three inside LANs (logical
LANs using IP Alias) behind the ZyXEL Device can communicate with three distinct WAN
networks. More examples follow at the end of this chapter.
Inside Local
Address (ILA)
Inside Global
Address (IGA)
NBG410W3G Series User s Guide
227
Chapter 12Network Address Translation (NAT)
Figure 137 NAT Application With IP Alias
Corporation B
LAN2: 192.168.1.X
Network Server
"Admin=192.168.1.1
NAT Server
192.168.1.1
LAN2: 192.168.2.X
Network Server
"Sales#=192.168.2.1
NAT Server
192.168.2.1
LAN3: 192.168.3.X
Network Server
"R&D#=192.168.3.1
Corporation A
Server in
Admin Network
=IP1 (IGA 1)
Internet
Server in
Sales Network
=IP2 (IGA 2)
Server in
R&D Network
=IP3 (IGA 3)
NAT Server
192.168.3.1
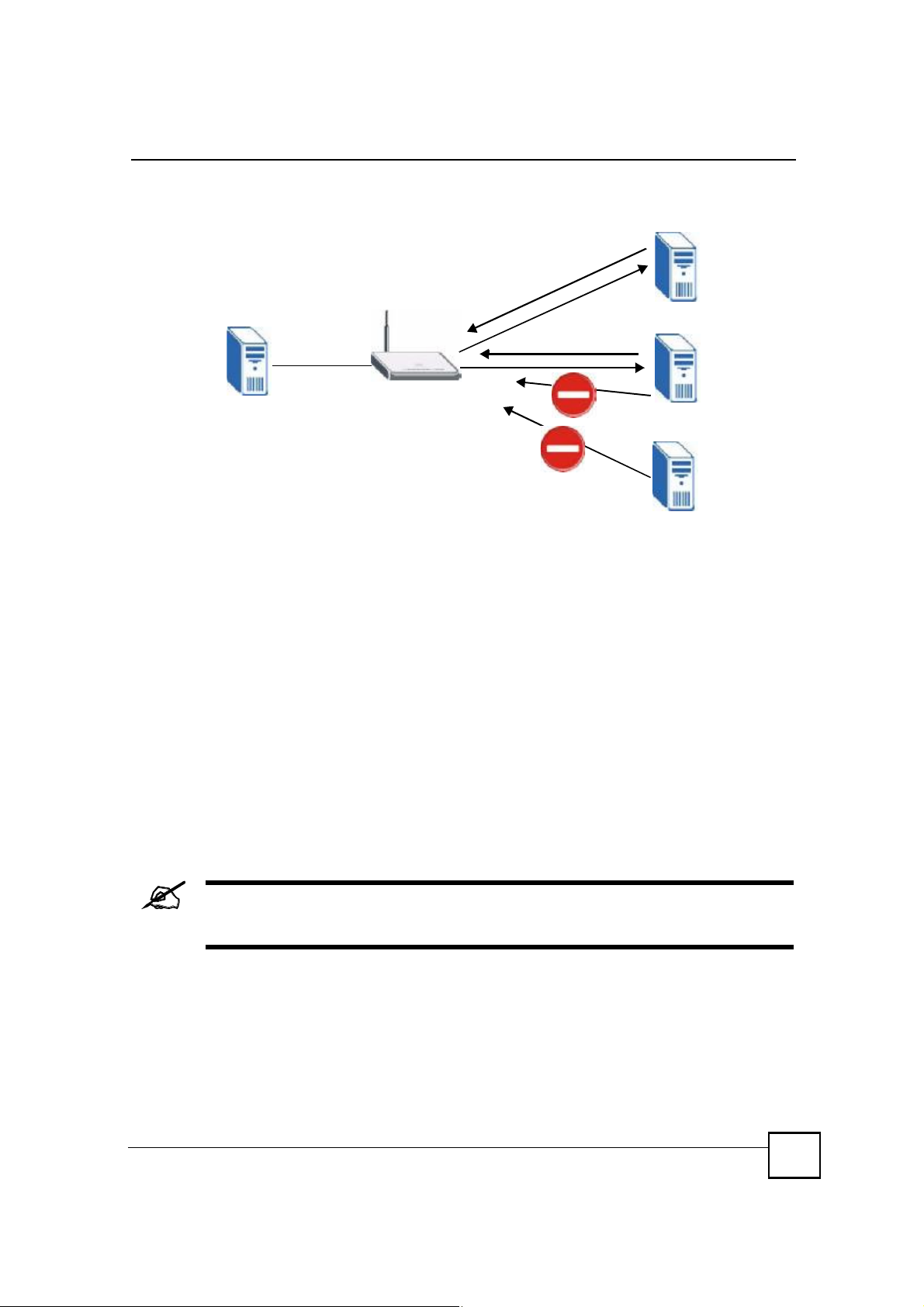
12.1.5 Port Restricted Cone NAT
ZyXEL Device ZyNOS version 4.00 and later uses port restricted cone NAT. Port restricted
cone NAT maps all outgoing packets from an internal IP address and port to a single IP
address and port on the external network. In the following example, the ZyXEL Device maps
the source address of all packets sent from internal IP address 1 and port A to IP address 2 and
port B on the external network. A host on the external network (IP address 3 and Port C for
example) can only send packets to the internal host if the internal host has already sent a
packet to the external host!s IP address and port.
A server with IP address 1 and port A sends packets to IP address 3, port C and IP address 4,
port D. The ZyXEL Device changes the server!s IP address to 2 and port to B.
Since 1, A has already sent packets to 3, C and 4, D, they can send packets back to 2, B and the
ZyXEL Device will perform NAT on them and send them to the server at IP address 1, port A.
Packets have not been sent from 1, A to 4, E or 5, so they cannot send packets to 1, A.
WAN Addresses: LAN Addresses: (Default IPs)
IGA 1 ---------------> 192.168.1.1
IGA 2 ---------------> 192.168.2.1
IGA 3 ---------------> 192.168.3.1
228
NBG410W3G Series User s Guide
Chapter 12Network Address Translation (NAT)
Figure 138 Port Restricted Cone NAT Example
NAT
3, C
4, D
1, A
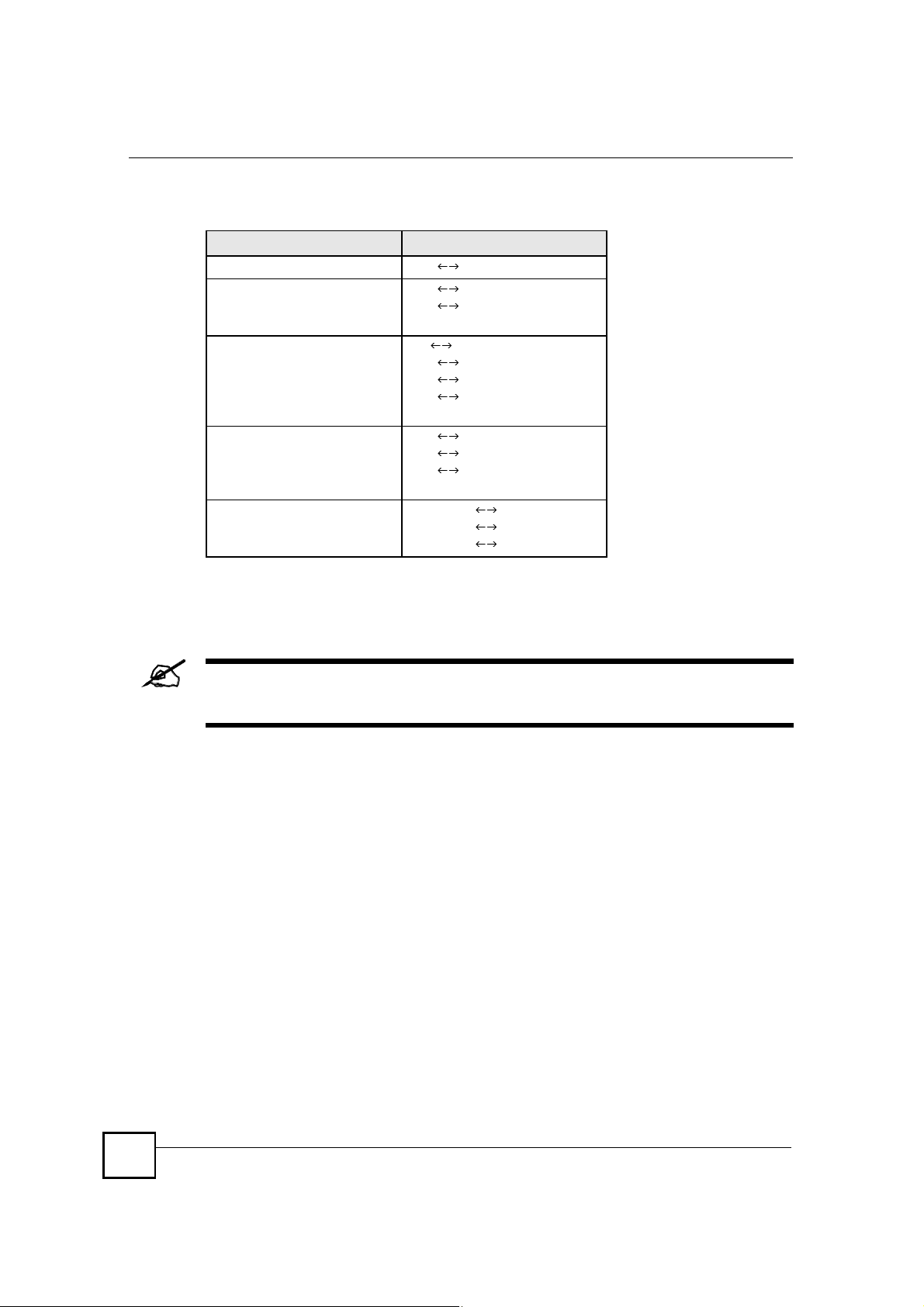
12.1.6 NAT Mapping Types
NAT supports five types of IP/port mapping. They are:
One to One: In One-to-One mode, the ZyXEL Device maps one local IP address to one
global IP address.
Many to One: In Many-to-One mode, the ZyXEL Device maps multiple local IP
addresses to one global IP address. This is equivalent to SUA (i.e., PAT, port address
translation), ZyXEL's Single User Account feature (the SUA option).
Many to Many Overload: In Many-to-Many Overload mode, the ZyXEL Device maps
the multiple local IP addresses to shared global IP addresses.
Many One to One: In Many-One-to-One mode, the ZyXEL Device maps each local IP
address to a unique global IP address.
Server: This type allows you to specify inside servers of different services behind the
NAT to be accessible to the outside world although, it is highly recommended that you use
the DMZ port for these servers instead.
2, B
4, E
5
Port numbers do not change for One-to-One and Many-One-to-One NAT
mapping types.
NBG410W3G Series User s Guide
229
Chapter 12Network Address Translation (NAT)
The following table summarizes the NAT mapping types.
Table 66 NAT Mapping Types
TYPE IP MAPPING
One-to-One ILA1 IGA1
Many-to-One (SUA/PAT) ILA1 IGA1
ILA2 IGA1
&
Many-to-Many Overload ILA IGA1
ILA2 IGA2
ILA3 IGA1
ILA4 IGA2
&
Many-One-to-One ILA1 IGA1
ILA2 IGA2
ILA3 IGA3
&
Server Server 1 IP IGA1
Server 2 IP IGA1
Server 3 IP IGA1
12.2 Using NAT
You must create a firewall rule in addition to setting up SUA/NAT, to allow
traffic from the WAN to be forwarded through the ZyXEL Device.
12.2.1 SUA (Single User Account) Versus NAT
SUA (Single User Account) is a ZyNOS implementation of a subset of NAT that supports two
types of mapping, Many-to-One and Server. The ZyXEL Device also supports Full Feature
NAT to map multiple global IP addresses to multiple private LAN IP addresses of clients or
servers using mapping types. Select either SUA or Full Feature in NAT Overview.
Selecting SUA means (latent) multiple WAN-to-LAN and WAN-to-DMZ address translation.
That means that computers on your DMZ with public IP addresses will still have to undergo
NAT mapping if you!re using SUA NAT mapping. If this is not your intention, then select
Full Feature NAT and don!t configure NAT mapping rules to those computers with public IP
addresses on the DMZ.
12.3 NAT Overview Screen
Click ADVANCED > NAT to open the NAT Overview screen.
230
NBG410W3G Series User s Guide
 Loading...
Loading...