Page 1

User Manual
Product Model:
Layer 2 Managed Ethernet Switch
Release 1.1
DES-3200-10/18/28/28F
®
Page 2

_________________________________________________________________________________
Information in this document is subject to change without notice.
© 2009 D-Link Corporation. All rights reserved.
Reproduction in any manner whatsoever without the written permission of D-Link Corporation is strictly forbidden.
Trademarks used in this text: D-Link and the D-LINK logo are trademarks of D-Link Corporation; Microsoft and Windows are registered trademarks
of Microsoft Corporation.
Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products.
D-Link Corporation disclaims any proprietary interest in trademarks and trade names other than its own.
August 2009 P/N
651S3200.015G
.
Page 3

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Table of Contents
Intended Readers ....................................................................................................................................................... viii
Typographical Conventions...................................................................................................................................................... viii
Notes, Notices, and Cautions ..................................................................................................................................... viii
Web-based Switch Configuration ................................................................................................. 9
Introduction ................................................................................................................................................................... 9
Login to Web Manager ............................................................................................................................................................... 9
Web-based User Interface ....................................................................................................................................................... 10
Web Pages .............................................................................................................................................................................. 11
Configuration ............................................................................................................................... 12
Device Information ...................................................................................................................................................... 13
System Information ..................................................................................................................................................... 13
Serial Port Settings ..................................................................................................................................................... 14
IP Address Settings .................................................................................................................................................... 14
IPv6 Address Settings ................................................................................................................................................ 16
IPv6 Route Settings .................................................................................................................................................... 17
IPv6 Neighbor Settings ............................................................................................................................................... 17
Port Configuration ....................................................................................................................................................... 18
Port Settings ............................................................................................................................................................................ 18
Port Description Settings ......................................................................................................................................................... 20
Port Error Disabled .................................................................................................................................................................. 20
Static ARP Settings .................................................................................................................................................... 21
User Accounts ............................................................................................................................................................ 22
System Log Configuration .......................................................................................................................................... 23
System Log Settings ................................................................................................................................................................ 23
System Log Server .................................................................................................................................................................. 23
DHCP Relay ............................................................................................................................................................... 25
DHCP Relay Global Settings ................................................................................................................................................... 25
DHCP Relay Interface Settings ................................................................................................................................................ 28
DHCP Local Relay Settings ..................................................................................................................................................... 28
DHCP Auto Configuration Settings ............................................................................................................................. 29
MAC Address Aging Time .......................................................................................................................................... 29
Web Settings .............................................................................................................................................................. 29
Telnet Settings ............................................................................................................................................................ 30
Password Encryption .................................................................................................................................................. 30
CLI Paging Settings .................................................................................................................................................... 30
Firmware Information .................................................................................................................................................. 31
SNTP Settings ............................................................................................................................................................ 32
Time Settings ........................................................................................................................................................................... 32
Time Zone Settings .................................................................................................................................................................. 33
ii
Page 4

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
SMTP Settings ............................................................................................................................................................ 35
SMTP Service Settings ............................................................................................................................................................ 35
SMTP Service .......................................................................................................................................................................... 36
MAC Notification Settings ........................................................................................................................................... 36
MAC Notification Global Settings ............................................................................................................................................. 36
MAC Notification Port Settings ................................................................................................................................................. 36
SNMP Settings ........................................................................................................................................................... 37
SNMP View Table .................................................................................................................................................................... 38
SNMP Group Table .................................................................................................................................................................. 39
SNMP User Table .................................................................................................................................................................... 40
SNMP Community Table.......................................................................................................................................................... 41
SNMP Host Table .................................................................................................................................................................... 42
SNMP Engine ID ...................................................................................................................................................................... 42
SNMP Trap Configuration ........................................................................................................................................................ 43
RMON ...................................................................................................................................................................................... 43
Time Range Settings .................................................................................................................................................. 44
Single IP Management ............................................................................................................................................... 44
Single IP Settings ..................................................................................................................................................................... 46
Topology .................................................................................................................................................................................. 47
Tool Tips .................................................................................................................................................................................. 49
Right-Click ................................................................................................................................................................................ 50
Menu Bar ................................................................................................................................................................................. 52
Firmware Upgrade ................................................................................................................................................................... 53
Configuration File Backup/Restore .......................................................................................................................................... 53
Upload Log File ........................................................................................................................................................................ 54
Gratuitous ARP ........................................................................................................................................................... 54
Gratuitous ARP Global Settings ............................................................................................................................................... 54
Gratuitous ARP Settings .......................................................................................................................................................... 55
ARP Spoofing Prevention Settings ............................................................................................................................. 56
L2 Features ................................................................................................................................... 57
Jumbo Frame .............................................................................................................................................................. 57
VLANs ......................................................................................................................................................................... 58
Understanding IEEE 802.1p Priority ........................................................................................................................................ 58
VLAN Description ..................................................................................................................................................................... 58
IEEE 802.1Q VLANs ................................................................................................................................................................ 59
Q-in-Q VLANs .......................................................................................................................................................................... 62
802.1Q Static VLAN ................................................................................................................................................................. 64
Q-in-Q ......................................................................................................................................................................... 67
Q-in-Q Settings ........................................................................................................................................................................ 68
VLAN Translation Settings ....................................................................................................................................................... 69
802.1v Protocol VLAN ................................................................................................................................................ 69
802.1v Protocol Group Settings ............................................................................................................................................... 69
802.1v Protocol VLAN Settings ................................................................................................................................................ 70
iii
Page 5

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
VLAN Trunk Settings .................................................................................................................................................. 71
GVRP Settings ............................................................................................................................................................ 72
Asymmetric VLAN Settings ......................................................................................................................................... 73
MAC-based VLAN Settings ........................................................................................................................................ 73
PVID Auto Assign Settings ......................................................................................................................................... 74
Port Trunking .............................................................................................................................................................. 74
LACP Port Settings ..................................................................................................................................................... 76
Traffic Segmentation ................................................................................................................................................... 77
BPDU Tunneling Settings ........................................................................................................................................... 78
IGMP Snooping .......................................................................................................................................................... 78
IGMP Snooping Settings .......................................................................................................................................................... 78
IGMP Access Control Settings ................................................................................................................................................. 80
IGMP Snooping Multicast VLAN Settings ................................................................................................................................ 81
IP Multicast Profile Settings ..................................................................................................................................................... 82
Limited Multicast Range Settings ............................................................................................................................................. 84
Max Multicast Group Settings .................................................................................................................................................. 84
MLD Snooping Settings .............................................................................................................................................. 85
Port Mirror ................................................................................................................................................................... 88
Loopback Detection Settings ...................................................................................................................................... 89
Spanning Tree ............................................................................................................................................................ 90
STP Bridge Global Settings ..................................................................................................................................................... 92
STP Port Settings .................................................................................................................................................................... 93
MST Configuration Identification .............................................................................................................................................. 95
STP Instance Settings ............................................................................................................................................................. 96
MSTP Port Information ............................................................................................................................................................ 97
Forwarding & Filtering ................................................................................................................................................. 97
Unicast Forwarding Settings .................................................................................................................................................... 97
Multicast Forwarding Settings .................................................................................................................................................. 98
Multicast Filtering Mode ........................................................................................................................................................... 99
LLDP ........................................................................................................................................................................... 99
LLDP Global Settings ............................................................................................................................................................. 100
LLDP Port Settings ................................................................................................................................................................ 101
LLDP Basic TLVs Settings ..................................................................................................................................................... 102
LLDP Dot1 TLVs Settings ...................................................................................................................................................... 103
LLDP Dot3 TLVs Settings ...................................................................................................................................................... 104
QoS ............................................................................................................................................. 105
Advantages of QoS ................................................................................................................................................................ 105
Understanding QoS ............................................................................................................................................................... 106
Bandwidth Control .................................................................................................................................................... 107
Traffic Control ........................................................................................................................................................... 107
802.1p Default Priority .............................................................................................................................................. 110
802.1p User Priority .................................................................................................................................................. 110
QoS Scheduling Settings .......................................................................................................................................... 111
iv
Page 6

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Priority Mapping ........................................................................................................................................................ 112
TOS Mapping ............................................................................................................................................................ 113
DSCP Mapping ......................................................................................................................................................... 114
Security ....................................................................................................................................... 115
Safeguard Engine ..................................................................................................................................................... 115
Trusted Host ............................................................................................................................................................. 117
IP-MAC-Port Binding ................................................................................................................................................ 117
IMP Binding Global Settings .................................................................................................................................................. 117
IMP Binding Port Settings ...................................................................................................................................................... 118
IMP Binding Entry Settings .................................................................................................................................................... 119
DHCP Snooping Entries ........................................................................................................................................................ 120
MAC Block List ....................................................................................................................................................................... 120
Port Security ............................................................................................................................................................. 120
Port Security Port Settings ..................................................................................................................................................... 120
Port Security FDB Entries ...................................................................................................................................................... 122
802.1X ....................................................................................................................................................................... 122
Understanding 802.1X Port-based and MAC-based Network Access Control ....................................................................... 125
Port-Based Network Access Control ...................................................................................................................................... 125
MAC-Based Network Access Control .................................................................................................................................... 126
802.1X Settings ...................................................................................................................................................................... 127
802.1X User ........................................................................................................................................................................... 128
Authentication RADIUS Server .............................................................................................................................................. 129
Guest VLAN Configuration ..................................................................................................................................................... 130
Guest VLAN ........................................................................................................................................................................... 131
Initialize Port(s) ...................................................................................................................................................................... 131
Reauthenticate Port(s) ........................................................................................................................................................... 132
SSL Settings ............................................................................................................................................................. 133
Download Certificate .............................................................................................................................................................. 134
Ciphersuite ............................................................................................................................................................................. 134
SSH ........................................................................................................................................................................... 135
SSH Settings .......................................................................................................................................................................... 136
SSH Authmode and Algorithm Settings ................................................................................................................................. 136
SSH User Authentication Lists ............................................................................................................................................... 138
Access Authentication Control .................................................................................................................................. 139
Authentication Policy Settings ................................................................................................................................................ 140
Application Authentication Settings ........................................................................................................................................ 140
Authentication Server Group .................................................................................................................................................. 141
Authentication Server ............................................................................................................................................................. 142
Login Method Lists ................................................................................................................................................................. 143
Enable Method Lists .............................................................................................................................................................. 144
Local Enable Password Settings ............................................................................................................................................ 145
MAC-based Access Control ...................................................................................................................................... 146
MAC-based Access Control Settings ..................................................................................................................................... 146
v
Page 7

®
xStack
MAC-based Access Control Local Settings ........................................................................................................................... 148
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
DoS Prevention Settings ........................................................................................................................................... 149
ACL ............................................................................................................................................. 150
ACL Configuration Wizard ........................................................................................................................................ 150
Access Profile List .................................................................................................................................................... 151
CPU Interface Filtering ............................................................................................................................................. 168
CPU Access Profile List ............................................................................................................................................ 168
ACL Finder ................................................................................................................................................................ 182
ACL Flow Meter ........................................................................................................................................................ 182
Monitoring .................................................................................................................................. 184
Cable Diagnostic ....................................................................................................................................................... 184
CPU Utilization .......................................................................................................................................................... 184
Port Utilization ........................................................................................................................................................... 185
Packet Size ............................................................................................................................................................... 186
Memory Utilization .................................................................................................................................................... 188
Packets ..................................................................................................................................................................... 188
Received (Rx) ........................................................................................................................................................................ 188
UMB_cast (Rx) ....................................................................................................................................................................... 190
Transmitted (Tx) ..................................................................................................................................................................... 191
Errors ........................................................................................................................................................................ 193
Received (RX) ........................................................................................................................................................................ 193
Transmitted (TX) .................................................................................................................................................................... 195
Port Access Control .................................................................................................................................................. 196
RADIUS Authentication .......................................................................................................................................................... 197
RADIUS Account Client ......................................................................................................................................................... 198
Authenticator State ................................................................................................................................................................ 200
Authenticator Statistics .......................................................................................................................................................... 201
Authenticator Session Statistics ............................................................................................................................................. 202
Authenticator Diagnostics ...................................................................................................................................................... 204
Browse ARP Table ................................................................................................................................................... 206
Browse VLAN ........................................................................................................................................................... 206
IGMP Snooping ........................................................................................................................................................ 206
Browse IGMP Router Port...................................................................................................................................................... 206
IGMP Snooping Group ........................................................................................................................................................... 207
IGMP Snooping Host ............................................................................................................................................................. 208
MLD Snooping .......................................................................................................................................................... 208
Browse MLD Router Port ....................................................................................................................................................... 208
MLD Snooping Group ............................................................................................................................................................ 209
LLDP ......................................................................................................................................................................... 209
LLDP Statistics System .......................................................................................................................................................... 209
LLDP Local Port Information .................................................................................................................................................. 210
LLDP Remote Port Information .............................................................................................................................................. 210
MBA Authentication State ......................................................................................................................................... 211
vi
Page 8

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Browse Session Table .............................................................................................................................................. 211
MAC Address Table .................................................................................................................................................. 211
System Log ............................................................................................................................................................... 212
Save and Tools ........................................................................................................................... 213
Save Configuration ................................................................................................................................................... 213
Save Log ................................................................................................................................................................... 214
Save All ..................................................................................................................................................................... 214
Configuration File Upload & Download ..................................................................................................................... 214
Upload Log File ......................................................................................................................................................... 215
Reset ......................................................................................................................................................................... 215
Ping Test ................................................................................................................................................................... 216
Download Firmware .................................................................................................................................................. 217
Reboot System ......................................................................................................................................................... 217
Mitigating ARP Spoofing Attacks Using Packet Content ACL ............................................... 218
System Log Entries ................................................................................................................... 226
Glossary...................................................................................................................................... 237
vii
Page 9
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Intended Readers
The DES-3200-10/18/28/28F User Manual contains information for setup and management of the Switch. This
manual is intended for network managers familiar with network management concepts and terminology.
Typographical Conventions
Convention Description
[ ] In a command line, square brackets indicate an optional entry. For example: [copy
filename] means that optionally you can type copy followed by the name of the file. Do not
type the brackets.
Bold font
Boldface Typewriter
Font
Initial capital letter Indicates a window name. Names of keys on the keyboard have initial capitals. For
Italics Indicates a window name or a field. Also can indicate a variables or parameter that is
Menu Name > Menu
Option
Indicates a button, a toolbar icon, menu, or menu item. For example: Open the File menu
and choose Cancel. Used for emphasis. May also indicate system messages or prompts
appearing on your screen. For example: You have mail. Bold font is also used to
represent filenames, program names and commands. For example: use the copy
command.
Indicates commands and responses to prompts that must be typed exactly as printed in
the manual.
example: Click Enter.
replaced with an appropriate word or string. For example: type filename means that you
should type the actual filename instead of the word shown in italic.
Menu Name > Menu Option Indicates the menu structure. Device > Port > Port
Properties means the Port Properties menu option under the Port menu option that is
located under the Device menu.
Notes, Notices, and Cautions
A NOTE indicates important information that helps you make better use of your device.
A NOTICE indicates either potential damage to hardware or loss of data and tells you
how to avoid the problem.
A CAUTION indicates a potential for property damage, personal injury, or death.
viii
Page 10
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Section 1
Web-based Switch Configuration
Introduction
Login to Web Manager
Web-based User Interface
Web Pages
Introduction
All software functions of the Switch can be managed, configured and monitored via the embedded web-based (HTML)
interface. The Switch can be managed from remote stations anywhere on the network through a standard browser
such as Firefox, Microsoft Internet Explorer, Mozilla, or Netscape. The browser acts as a universal access tool and
can communicate directly with the Switch using the HTTP protocol.
The Web-based management module and the Console program (and Telnet) are different ways to access the same
internal switching software and configure it. Thus, all settings encountered in Web-based management are the same
as those found in the console program.
Login to Web Manager
To begin managing the Switch, simply run the browser you have installed on your computer and point it to the IP
address you have defined for the device. The URL in the address bar should read something like:
http://123.123.123.123, where the numbers 123 represent the IP address of the Switch.
NOTE: The Factory default IP address for the Switch is 10.90.90.90.
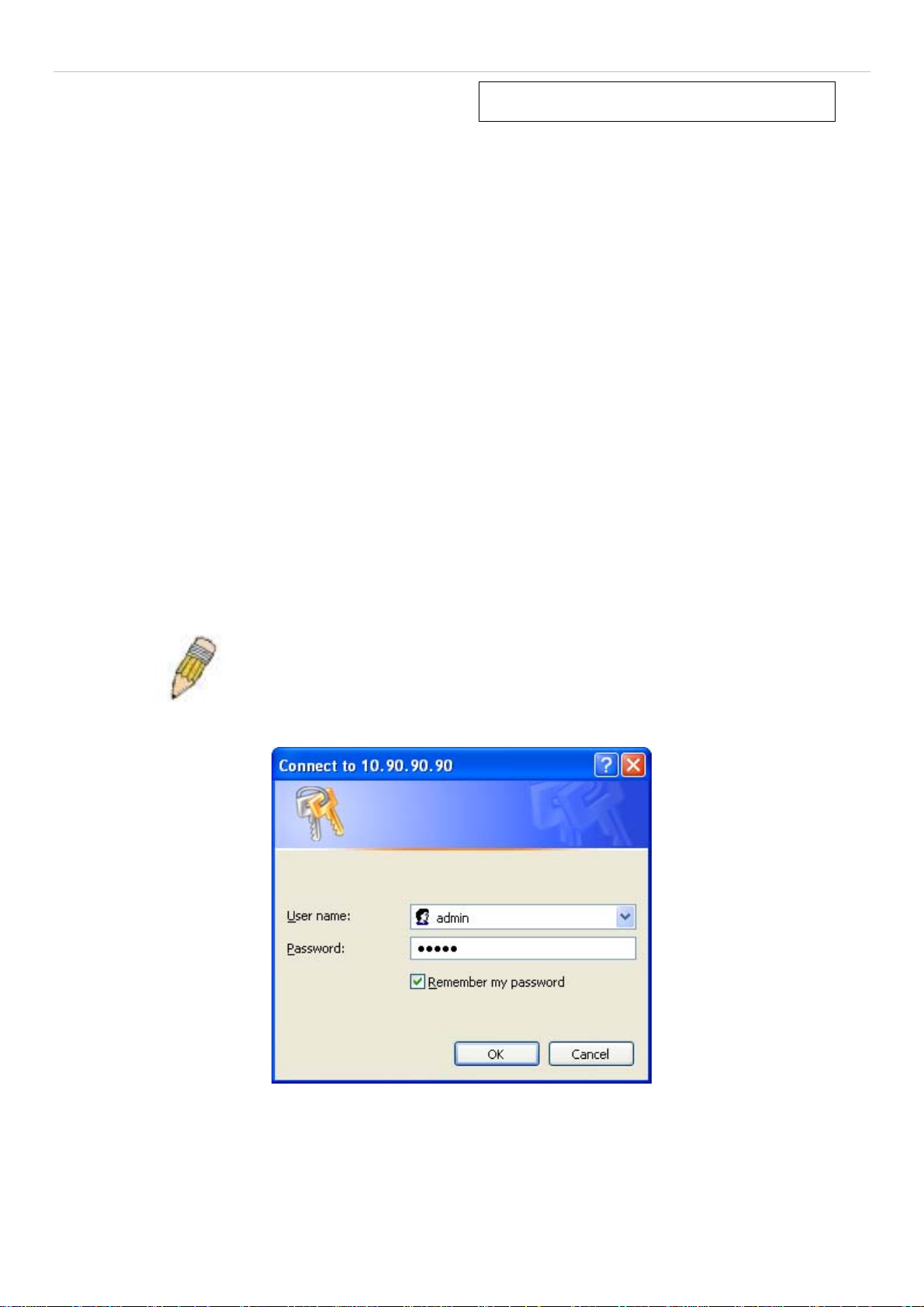
This opens the management module's user authentication window, as seen below.
Figure 1 - 1 Enter Network Password dialog
Enter “admin” in both the User Name and Password fields and click OK. This will open the Web-based user interface.
The Switch management features available in the web-based manager are explained below.
9
Page 11
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Web-based User Interface
The user interface provides access to various Switch configuration and management windows, allows you to view
performance statistics, and permits you to graphically monitor the system status.
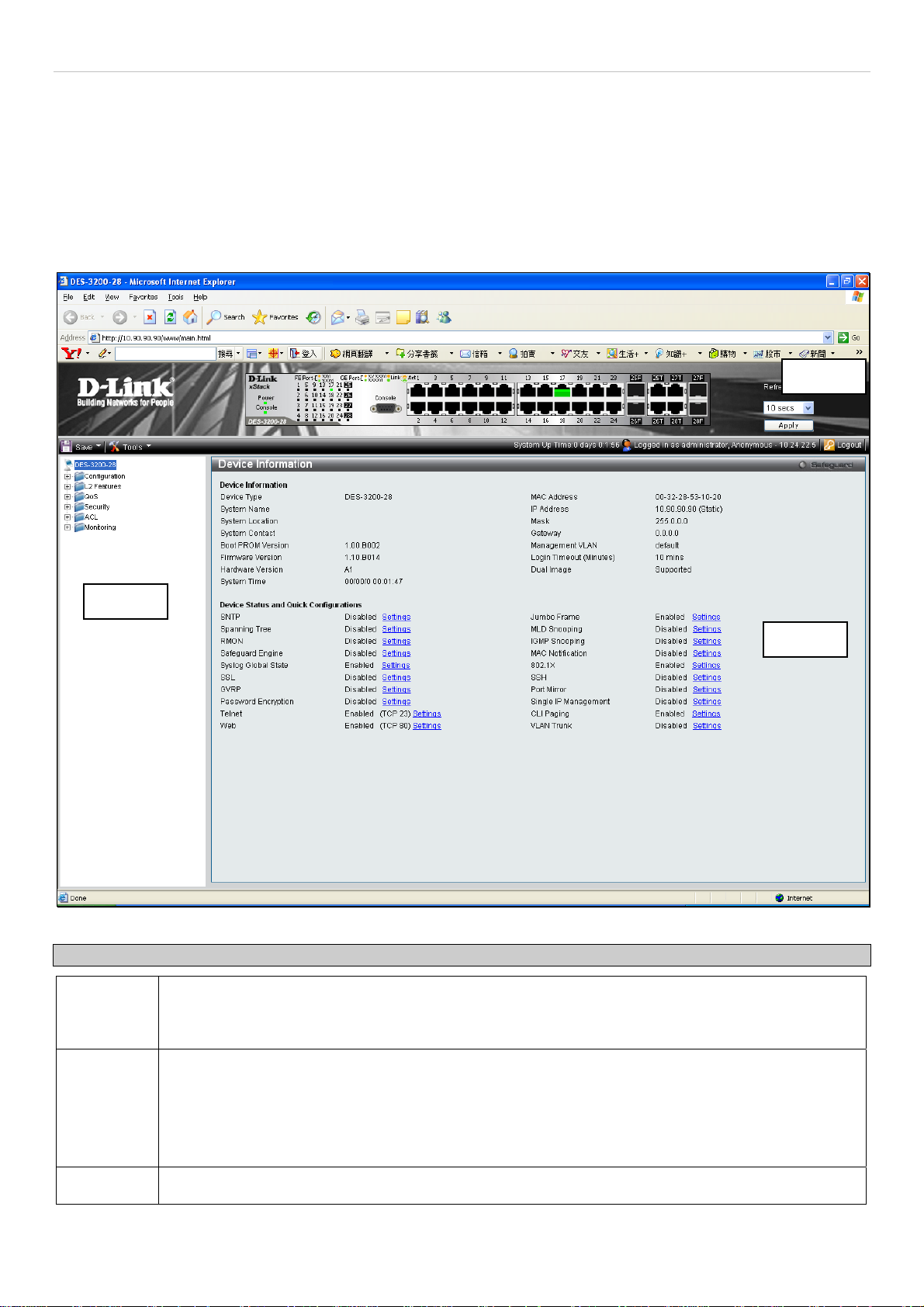
Areas of the User Interface
The figure below shows the user interface. The user interface is divided into three distinct areas as described in the
table.
Area 2
Area 1
Area Function
Area 1
Select the folder or window to be displayed. The folder icons can be opened to display the
hyperlinked window buttons and subfolders contained within them. Click the D-Link logo to go to the
D-Link website.
Area
Figure 1 - 2 Main Web-Manager page
Area 2
Area 3
Presents a graphical near real-time image of the front panel of the Switch. This area displays the
Switch's ports and expansion modules, showing port activity, duplex mode, or flow control,
depending on the specified mode.
Various areas of the graphic can be selected for performing management functions, including port
configuration.
Presents switch information based on your selection and the entry of configuration data.
10
Page 12

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
NOTICE: Any changes made to the Switch configuration during the current
session must be saved in the Save Configuration window (Save > Save
Configuration) or use the command line interface (CLI) command save
config.
Web Pages
When you connect to the management mode of the Switch with a Web browser, a login window is displayed. Enter a
user name and password to access the Switch's management mode.
Below is a list and description of the main folders available in the Web interface:
Configuration – Contains main windows concerning Device Information, System Information, Serial Port Settings, IP
Address, IPv6 Interface Settings, IPv6 Route Settings, IPv6 Neighbor Settings, Port Configuration, Static ARP
Settings, User Accounts, System Log Configuration, DHCP Relay, DHCP Auto Configuration Settings, MAC Address
Aging Time, Web Settings, Telnet Settings, Password Encryption, CLI Paging Settings, Firmware Information, SNTP
Settings, SMTP Settings, MAC Notification Settings, SNMP Settings, Time Range Settings, Single IP Management,
Gratuitous ARP, and ARP Spoofing Prevention Settings.
L2 Features – Contains main windows concerning Jumbo Frame, 802.1Q Static VLAN, Q-in-Q, 802.1v Protocol VLAN,
VLAN Trunk Settings, GVRP Settings, Asymmetric VLAN Settings, MAC-based VLAN Settings, PVID Auto Assign
Settings, Port Trunking, LACP Port Settings, Traffic Segmentation, BPDU Tunneling Settings, IGMP Snooping, MLD
Snooping Settings, Port Mirror, Loopback Detection Settings, Spanning Tree, Forwarding & Filtering, and LLDP.
QoS – Contains main windows concerning Bandwidth Control, Traffic Control, 802.1P Default Priority, 802.1P User
Priority, QoS Scheduling Settings, Priority Mapping, TOS Mapping, and DSCP Mapping.
Security – Contains main windows concerning Safeguard Engine, Trusted Host, IP-MAC-Port Binding, Port Security,
802.1X, SSL Settings, SSH, Access Authentication Control, MAC-based Access Control, and DoS Prevention Settings.
ACL – Contains main windows concerning ACL Configuration Wizard, Access Profile List, CPU Access Profile List,
ACL Finder, and ACL Flow Meter.
Monitoring – Contains main windows concerning Cable Diagnostic, CPU Utilization, Port Utilization, Packet Size,
Memory Utilization, Packets, Errors, Port Access Control, Browse ARP Table, Browse VLAN, IGMP Snooping, MLD
Snooping, LLDP, MBA Authentication State, Browse Session Table, MAC Address Table, and System Log.
Save & Tools – Contains main windows concerning Save Configuration, Save Log, Save All, Configuration File
Upload & Download, Upload Log File, Reset, Ping Test, Download Firmware, and Reboot System.
NOTE: Be sure to configure the user name and password in the User
Accounts window (Configuration > User Accounts) before connecting
the Switch to the greater network.
11
Page 13

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Configuration
Device Information
System Information
Serial Port Settings
IP Address Settings
IPv6 Interface Settings
IPv6 Route Settings
IPv6 Neighbor Settings
Port Configuration
Static ARP Settings
User Accounts
System Log Configuration
Section 2
DHCP Relay
DHCP Auto Configuration Settings
MAC Address Aging Time
Web Settings
Telnet Settings
Password Encryption
CLI Paging Settings
Firmware Information
SNTP Settings
SMTP Settings
MAC Notification Settings
SNMP Settings
Time Range Settings
Single IP Management
Gratuitous ARP
ARP Spoofing Prevention Settings
12
Page 14
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
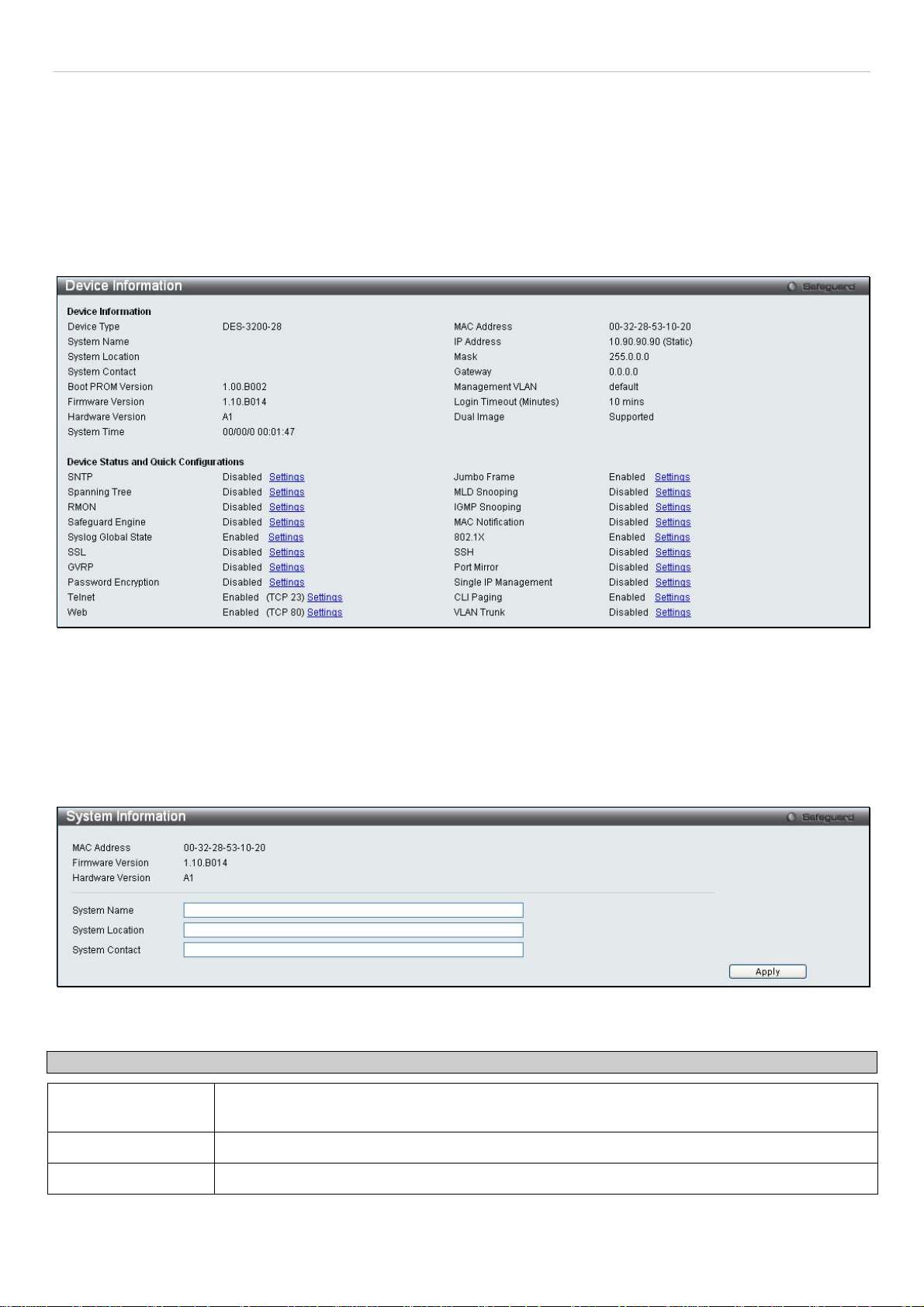
Device Information
This window contains the main settings for all major functions on the Switch and appears automatically when you log
on. To return to the Device Information window, click the DES-3200-10/18/28/28F folder. The Device Information
window shows the Switch’s MAC Address (assigned by the factory and unchangeable), the Boot PROM Version,
Firmware Version, the Hardware Version, and other information about different settings on the Switch. This
information is helpful to keep track of PROM and firmware updates and to obtain the Switch's MAC address for entry
into another network device's address table, if necessary. In addition, this window displays the status of functions on
the Switch to quickly assess their current global status. Some functions are hyper-linked to their configuration window
for easy access from the Device Information window.
Figure 2 - 1. Device Information window
System Information
This window contains the System Information details. The user may enter a System Name, System Location and
System Contact to aid in defining the Switch, to the user's preference. This window displays the MAC Address,
Firmware Version and Hardware Version.
Click Configuration > System Information to display the following window:
Figure 2 - 2. System Information window
The fields that can be configured are described below:
Parameter Description
System Name Enter a system name for the Switch, if so desired. This name will identify it in the Switch
network.
System Location
System Contact
Click Apply to implement changes made.
Enter the location of the Switch, if so desired.
Enter a contact name for the Switch, if so desired.
13
Page 15
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
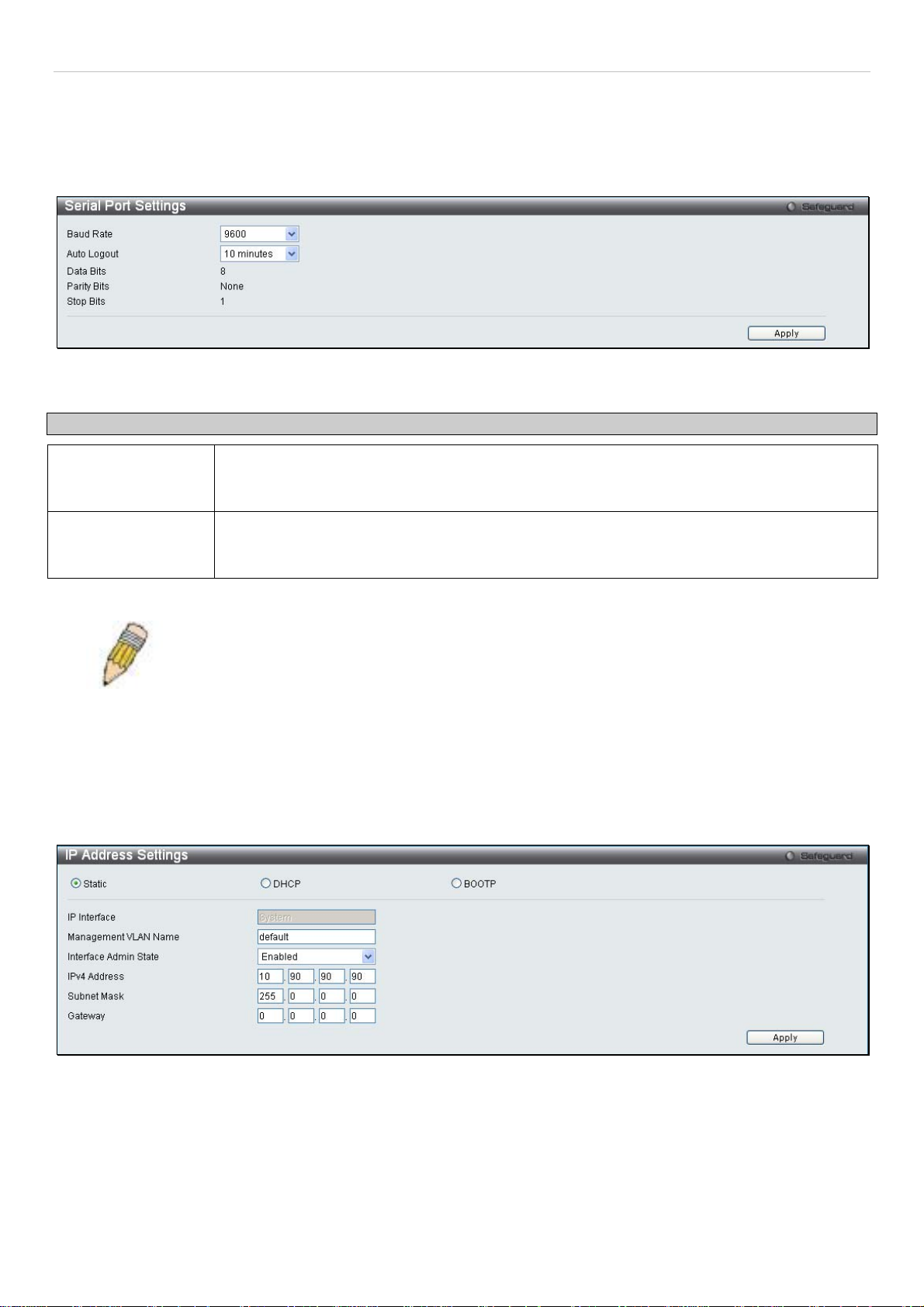
Serial Port Settings
The following window allows the Baud Rate and the Auto Logout to be changed as well as containing information
about the Serial Port Settings.
Click Configuration > Serial Port Settings to display this window:
Figure 2 - 3. Serial Port Settings window
Parameter Description
Baud Rate This field specifies the baud rate for the serial port on the Switch. There are four possible
baud rates to choose from, 9600, 19200, 38400 and 115200. For a connection to the Switch
using the CLI interface, the baud rate must be set to 9600, which is the default setting.
Auto Logout Select the logout time used for the console interface. This automatically logs the user out after
an idle period of time, as defined. Choose from the following options: 2 Minutes, 5 Minutes, 10
Minutes, 15 Minutes or Never. The default setting is 10 minutes.
Click Apply to implement changes made.
NOTE: If a user configures the serial port’s baud rate, the baud rate will take effect and save
immediately.
IP Address Settings
The IP address may initially be set using the console interface prior to connecting to it through the Ethernet. If the
Switch IP address has not yet been changed, read the introduction of the DES-3200-10/18/28/28F CLI Reference
Manual for more information.
Click Configuration > IP Address Settings to display the following window:
Figure 2 - 4. IP Address Settings window
To manually assign the Switch's IP address, subnet mask, and default gateway address:
1. Click Static at the top of the window.
2. Enter the appropriate IPv4 Address and Subnet Mask.
3. To access the Switch from a different subnet from the one it is installed on, enter the IP address of the
Gateway. If the Switch will be managed from the subnet on which it is installed, leave the default address
(0.0.0.0) in this field.
14
Page 16
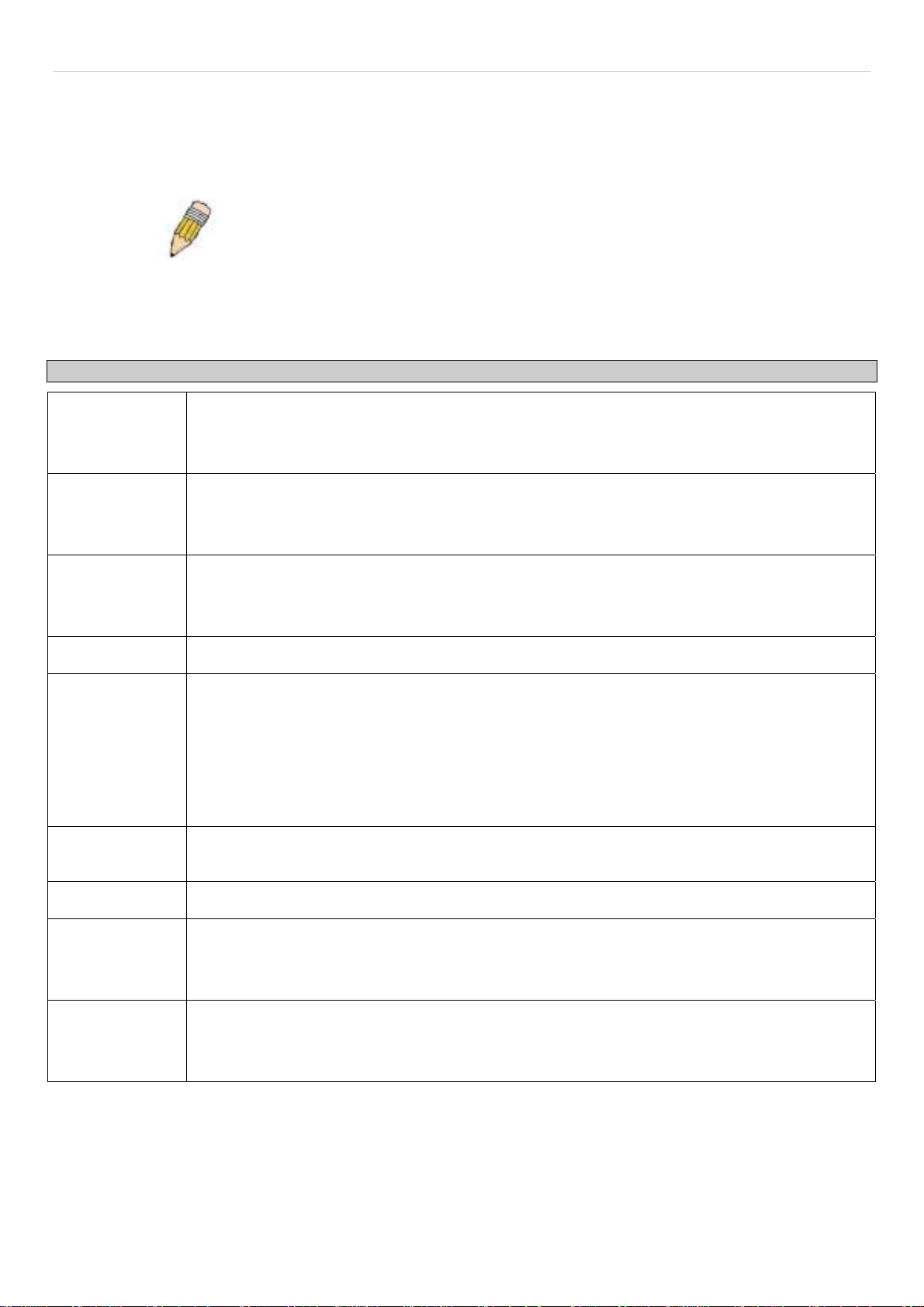
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
4. If no VLANs have been previously configured on the Switch, you can use the default Management VLAN
Name. The default VLAN contains all of the Switch ports as members. If VLANs have been previously
configured on the Switch, the Management VLAN Name of the VLAN that contains the port connected to the
management station will have to be entered to access the Switch.
5. Use the drop-down Interface Admin State menu to select Enabled if it has not already been done.
NOTE: The Switch's factory default IP address is 10.90.90.90 with a
subnet mask of 255.0.0.0 and a default gateway of 0.0.0.0.
To use the BOOTP or DHCP protocols to assign the Switch an IP address, subnet mask, and default gateway address,
select either BOOTP or DHCP.
The IP Address Settings options are:
Parameter Description
Static
DHCP
BOOTP
IP Interface
Management
VLAN Name
Interface Admin
State
Allows the entry of an IPv4 address, Subnet Mask, and a Default Gateway for the Switch. These
fields should be of the form xxx.xxx.xxx.xxx, where each xxx is a number (represented in decimal
form) between 0 and 255. This address should be a unique address on the network assigned for
use by the network administrator.
The Switch will send out a DHCP broadcast request when it is powered up. The DHCP protocol
allows IP addresses, network masks, and default gateways to be assigned by a DHCP server. If
this option is set, the Switch will first look for a DHCP server to provide it with this information
before using the default or previously entered settings.
The Switch will send out a BOOTP broadcast request when it is powered up. The BOOTP
protocol allows IP addresses, network masks, and default gateways to be assigned by a central
BOOTP server. If this option is set, the Switch will first look for a BOOTP server to provide it with
this information before using the default or previously entered settings.
The current IP Interface being assigned an IP address on this window.
This allows the entry of a VLAN Name from which a management station will be allowed to
manage the Switch using TCP/IP (in-band via web manager or Telnet). Management stations that
are on VLANs other than the one entered here will not be able to manage the Switch in-band
unless their IP addresses are entered in the Security IP Management window. If VLANs have
not yet been configured for the Switch, the default VLAN contains all of the Switch's ports. There
are no entries in the Security IP Management table, by default, so any management station that
can connect to the Switch can access the Switch until a management VLAN is specified or
Management Station IP Addresses are assigned.
Toggle between Enabled and Disabled. This must be set to Enabled when setting an IP address
on this window.
IPv4 Address
Subnet Mask
Enter the desired IPv4 address to be set. The default address is 10.90.90.90.
A Bitmask that determines the extent of the subnet that the Switch is on. Should be of the form
xxx.xxx.xxx.xxx, where each xxx is a number (represented in decimal) between 0 and 255. The
value should be 255.0.0.0 for a Class A network, 255.255.0.0 for a Class B network, and
255.255.255.0 for a Class C network, but custom subnet masks are allowed.
Gateway
IP address that determines where packets with a destination address outside the current subnet
should be sent. This is usually the address of a router or a host acting as an IP gateway. If your
network is not part of an intranet, or you do not want the Switch to be accessible outside your
local network, you can leave this field unchanged.
Click Apply to allow changes to take effect.
15
Page 17
xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
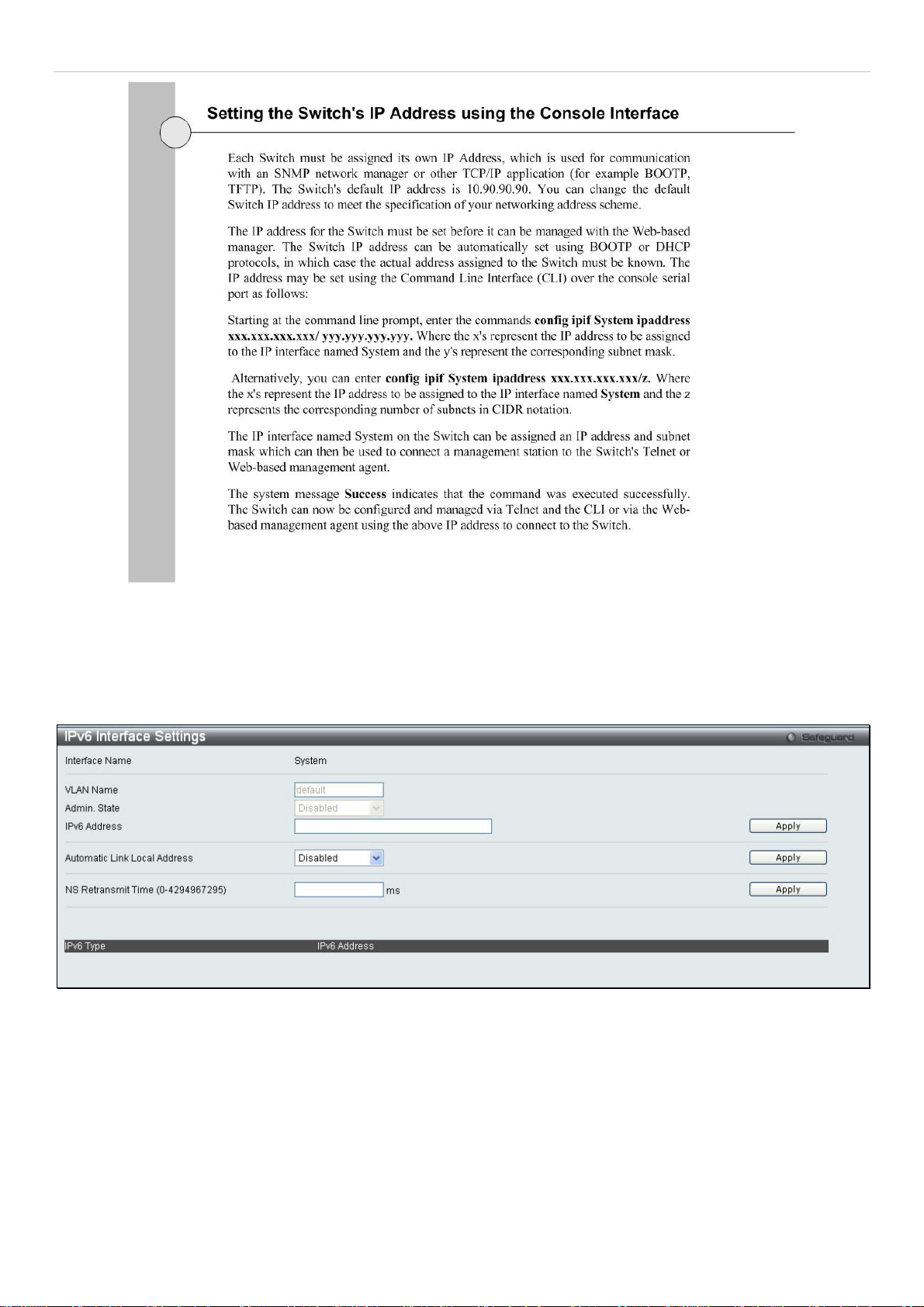
IPv6 Address Settings
Users can display the Switch’s current IPv6 interface settings.
To view the following window, click Configuration > IPv6 Interface Settings:
Figure 2 - 5. IPv6 Interface Settings window
To configure IPv6 interface settings, enter an IPv6 Address and click
the bottom of the window.
After making the desired changes, click the
The following parameters may be configured or viewed:
Apply
button.
16
. The new entry will appear in the table at
Apply
Page 18
®
xStack
Parameter Description
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Interface Name
VLAN Name
Admin. State
IPv6 Address
Automatic Link
Local Address
NS Retransmit
Time (0-
4294967295)
The name of the IPv6 interface being displayed or modified.
Display the VLAN name of the IPv6 interface.
Display the current administrator state.
Enter the IPv6 address of the interface to be modified.
Toggle between Enabled and Disabled. Enabling this is helpful when no external source of network
addressing information is available.
Enter a value between 0 and 4294967295. This is the neighbor solicitation’s retransmit timer in
milliseconds. The default is zero.
IPv6 Route Settings
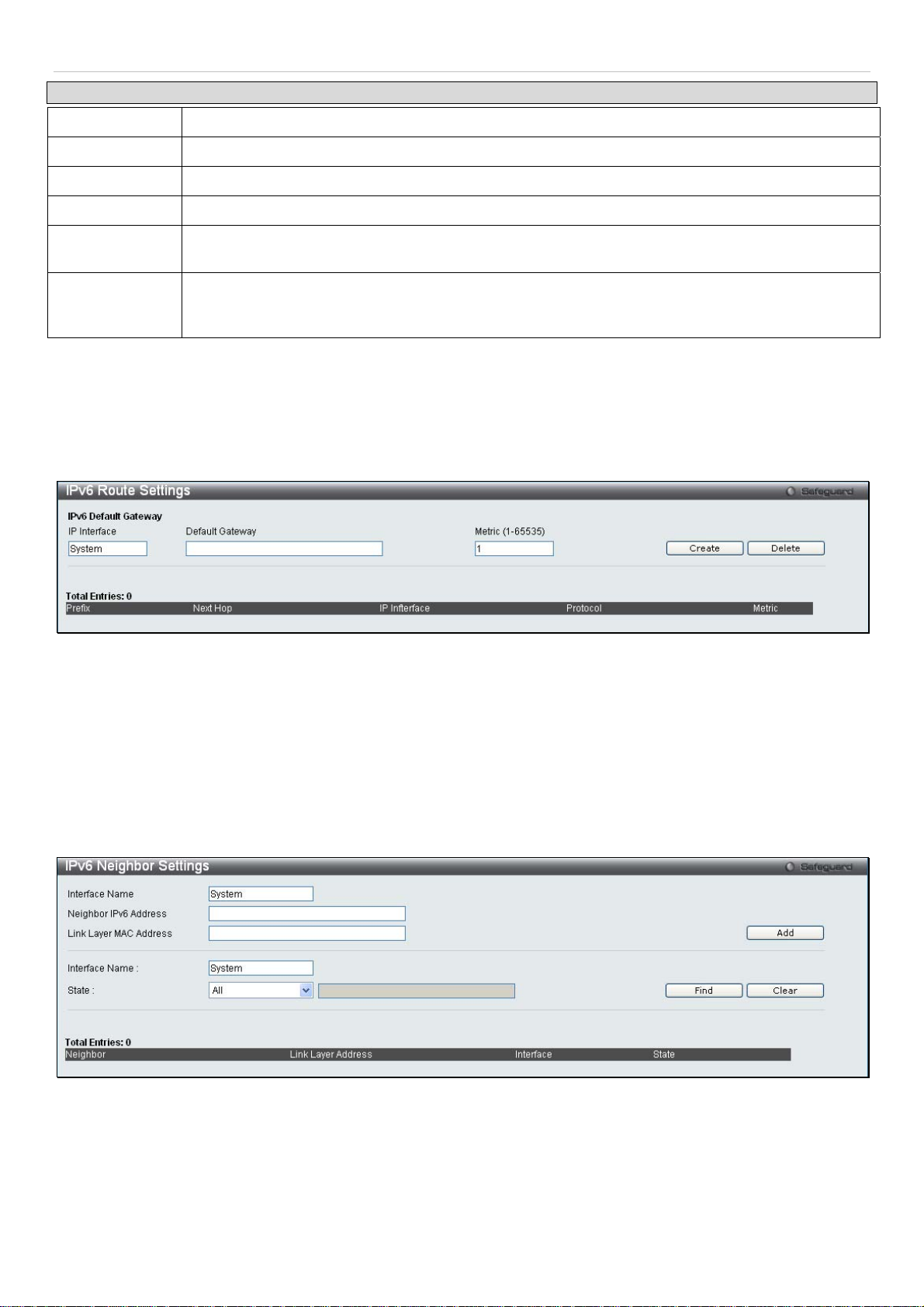
The user can configure the Switch’s IPv6 Route Table.
To view the following window, click Configuration > IPv6 Route Settings:
Figure 2 - 6. IPv6 Route Settings window
Enter an IP Interface, an IPv6 address in the Default Gateway field and then click the Create button. In addition, the
Metric can be entered between 1 and 65535. The new IPv6 route will be displayed in the table at the bottom of the
window.
IPv6 Neighbor Settings
The user can configure the Switch’s IPv6 neighbor settings. The Switch’s current IPv6 neighbor settings will be
displayed in the table at the bottom of this window.
To view the following window, click Configuration > IPv6 Neighbor Settings:
Figure 2 - 7. IPv6 Neighbor Settings window
Enter the Interface Name, Neighbor IPv6 Address, and the Link Layer MAC Address and then click the
To look for an IPv6 Neighbor Settings table entry, enter the Interface Name, select the desired State (All, Address, Static, or
Dynamic) in the middle section of this window, and then click the
To delete all the entries being displayed on the table at the bottom of this window, click the
The following parameters may be configured or viewed:
17
Find
button.
Clear
button.
Add
button.
Page 19
®
xStack
Parameter Description
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Interface Name
Neighbor IPv6
Address
Link Layer MAC
Address
State
Enter the name of the IPv6 neighbor. To search for all the current interfaces on the Switch, go to
the second Interface Name field in the middle part of the window, tick the All check box, and then
click the Find button.
Enter the neighbor IPv6 address.
Enter the link layer MAC address.
Use the drop-down menu to select All, Address, Static, or Dynamic.
Port Configuration
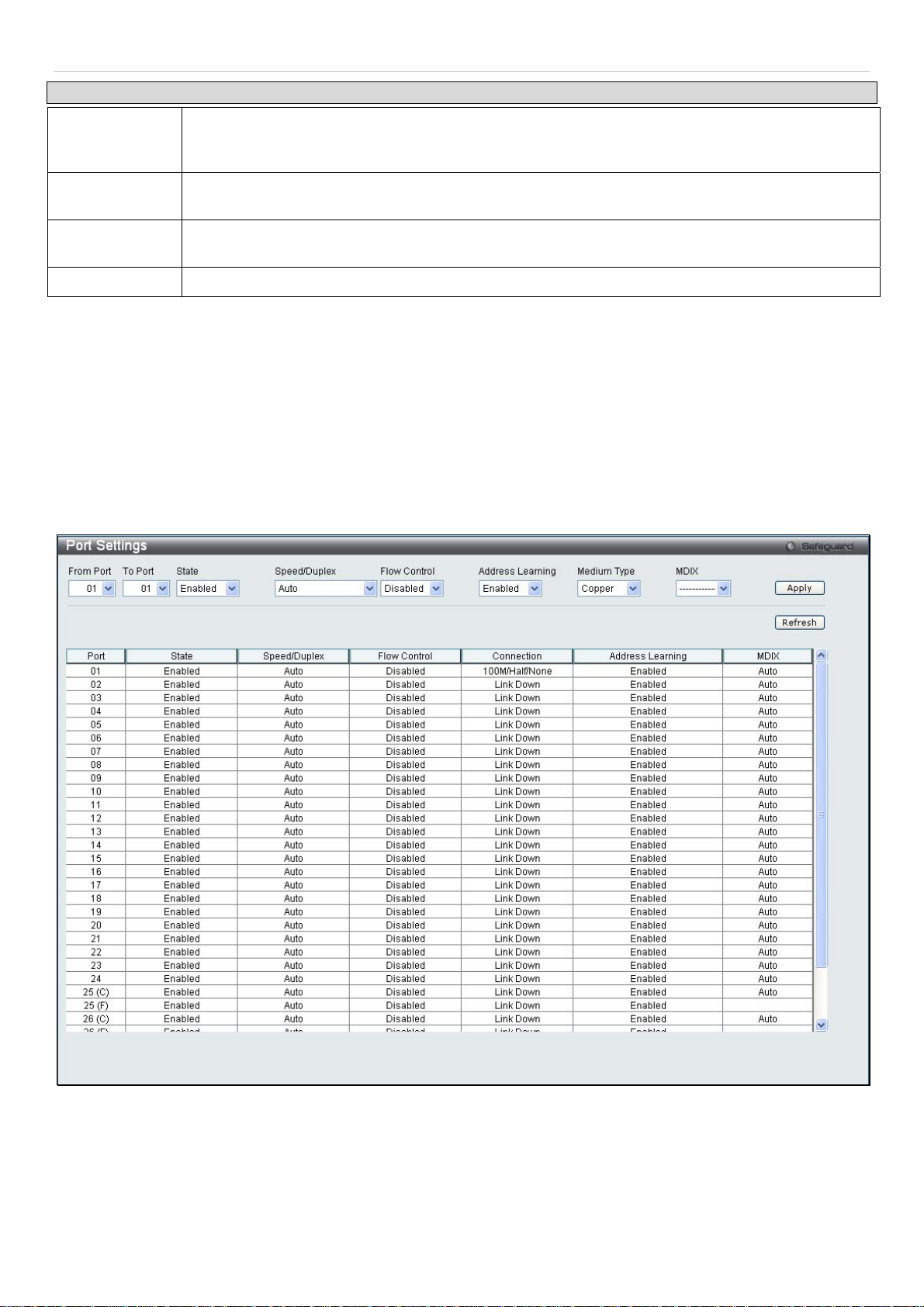
This section contains information for configuring various attributes and properties for individual physical ports,
including port speed and flow control.
Port Settings
Various port settings, including State, Speed/Duplex, Flow Control, Address Learnng, Medium Type, and MDIX can be
configured on the Switch.
To view the following window, click Configuration > Port Configuration > Port Settings:
Figure 2 - 8. Port Settings window
To configure switch ports, choose the port or sequential range of ports using the From Port and To Port pull-down
menus. Use the remaining pull-down menus to configure the parameters described below:
18
Page 20
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Parameter Description
From Port/To
Use the pull-down menus to select the port or range of ports to be configured.
Port
State
Speed/Duplex
Flow Control
Toggle this field to either enable or disable a given port or group of ports.
Toggle the Speed/Duplex field to either select the speed and duplex/half-duplex state of the port.
Auto denotes auto-negotiation between 10 and 100 Mbps devices, in full- or half-duplex. The
Auto setting allows the port to automatically determine the fastest settings the device the port is
connected to can handle, and then to use those settings. The other options are Auto, 10M Half,
10M Full, 100M Half and 100M Full, 1000M Full_Master, 1000M Full_Slave and 1000M Full.
There is no automatic adjustment of port settings with any option other than Auto.
The Switch allows the user to configure two types of gigabit connections; 1000M/Full_M and
1000M/Full_S. Gigabit connections only support full duplex connections and take on certain
characteristics that are different from the other choices listed.
The 1000M Full_Master and 1000M Full_Slave parameters refer to connections running a
1000BASE-T cable for connection between the Switch port and other device capable of a gigabit
connection. The master setting (1000M Full_Master) will allow the port to advertise capabilities
related to duplex, speed and physical layer type. The master setting will also determine the
master and slave relationship between the two connected physical layers. This relationship is
necessary for establishing the timing control between the two physical layers. The timing control
is set on a master physical layer by a local source. The slave setting (1000M Full_Slave) uses
loop timing, where the timing comes from a data stream received from the master. If one
connection is set for 1000M Full_Master, the other side of the connection must be set for 1000M
Full_Slave. Any other configuration will result in a link down status for both ports.
Displays the flow control scheme used for the various port configurations. Ports configured for
full-duplex use 802.3x flow control, half-duplex ports use backpressure flow control, and Auto
ports use an automatic selection of the two. The default is Disabled.
Address
Learning
Medium Type
When Enabled, destination and source MAC addresses are automatically listed in the forwarding
table. The default setting is Enabled.
This applies only to the Combo ports. If configuring the Combo ports this defines the type of
transport medium used. SFP ports should be set at Fiber and the Combo 1000BASE-T ports
should be set at Copper.
MDIX
This can be specified as Auto, Normal, or Cross. In Normal state, the port is in MDIX mode and
can be connected to a PC NIC using a straight cable. If it is in Cross state, the port is in MDI
mode, and can be connected to a port (in MDIX mode) on another switch through a straight
cable.
Click Apply to implement the new settings on the Switch.
19
Page 21
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
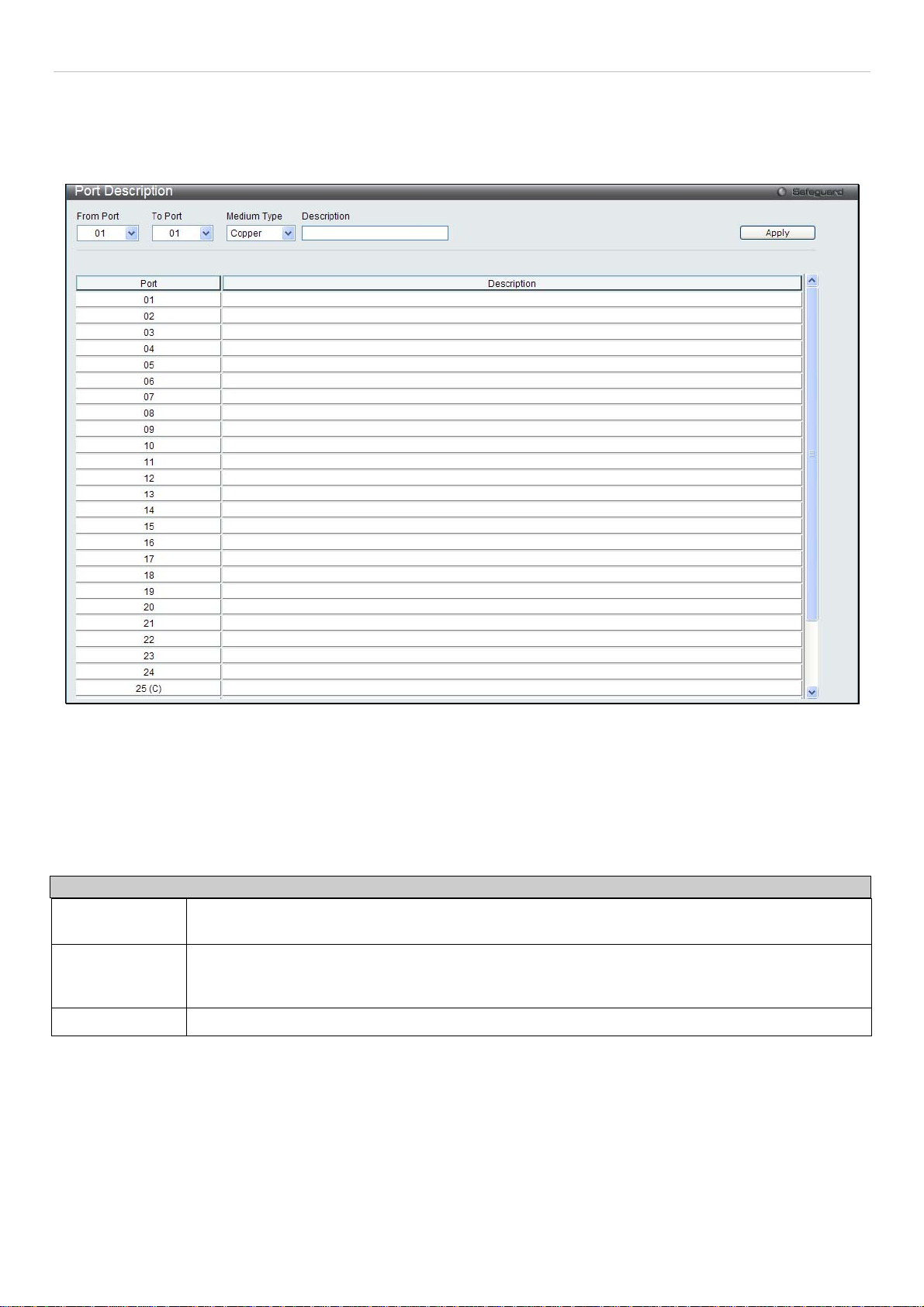
Port Description Settings
The Switch supports a port description feature where the user may name various ports on the Switch.
To view the following window, click Configuration > Port Configuration > Port Description Settings:
Figure 2 - 9. Port Description Settings window
Use the From Port and To Port pull-down menus to choose a port or range of ports to describe, and then enter a
description of the port(s).
The Medium Type applies only to the Combo ports. If configuring the Combo ports this defines the type of transport
medium used. SFP ports should be nominated Fiber and the Combo 1000BASE-T ports should be nominated Copper.
The result will be displayed in the appropriate switch port number slot (C for copper ports and F for fiber ports).
The following parameters can be configured:
Parameter Description
From Port/To
Port
Medium Type
Description
Click Apply to implement the new settings on the Switch.
Use the pull-down menus to select the port or range of ports to be configured.
This only applies to the Combo ports. If configuring the Combo ports, this defines the type of
transport medium used. SFP ports should be set at Fiber and the Combo 1000BASE-T ports
should be set at Copper.
The description of the the ports.
Port Error Disabled
The following window will display information about ports that have had their connection status disabled for reasons
such as STP loopback detection or link down status.
To view this window, click Configuration > Port Configuration > Port Error Disabled:
20
Page 22
®
xStack
The following parameters are displayed:
Parameter Description
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Figure 2 - 10. Port Error Disabled window
Port
Port State
Connection Status
Reason
Displays the port that has been error disabled.
Describes the current running state of the port, whether Enabled or Disabled.
This field will read the uplink status of the individual ports, whether Enabled or Disabled.
Describes the reason why the port has been error-disabled, such as a STP loopback
occurrence.
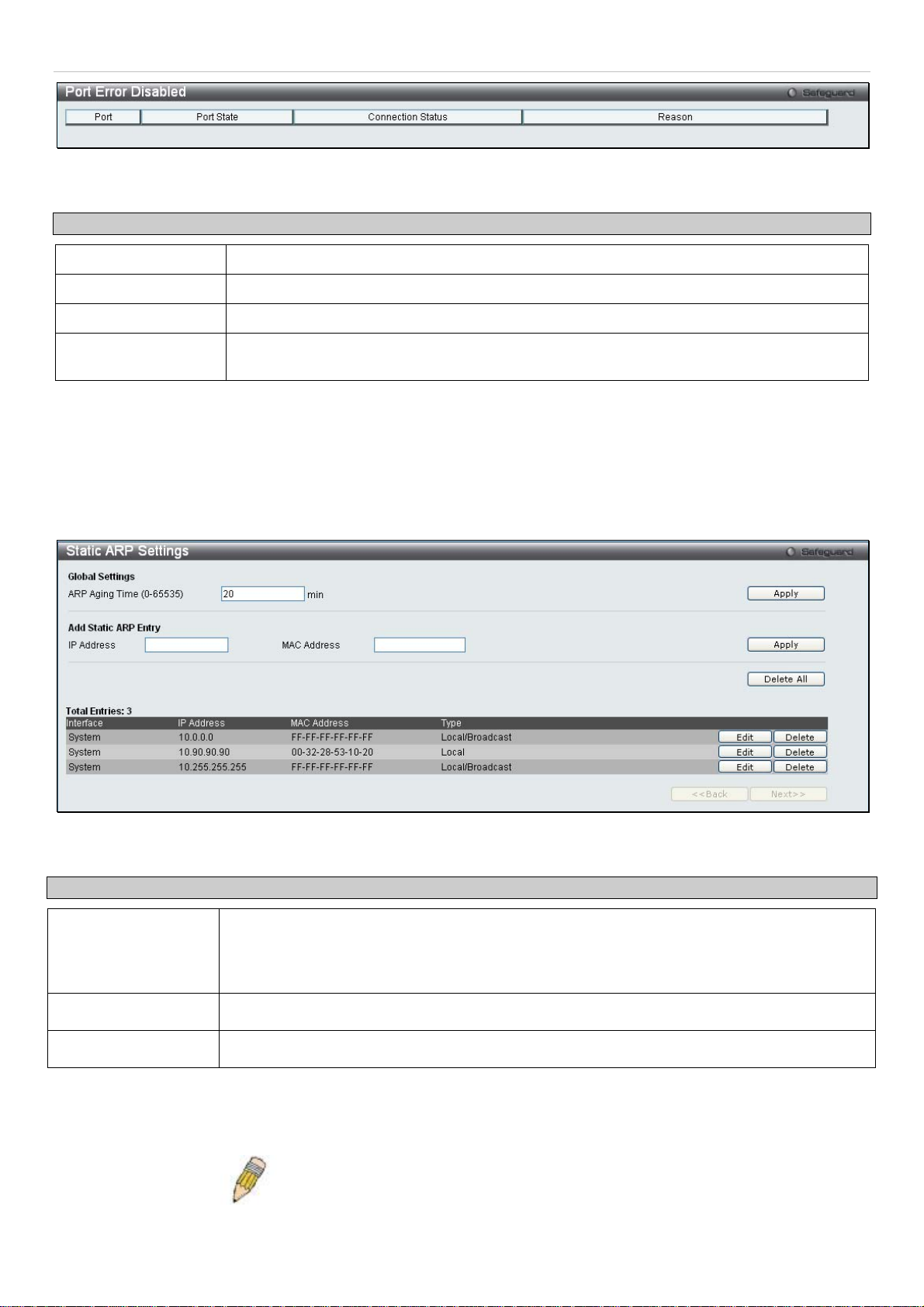
Static ARP Settings
The Address Resolution Protocol (ARP) is a TCP/IP protocol that converts IP addresses into physical addresses. This
table allows network managers to view, define, modify and delete ARP information for specific devices. Static entries
can be defined in the ARP Table. When static entries are defined, a permanent entry is entered and is used to
translate IP address to MAC addresses.
To view this window, click Configuration > Static ARP Settings
Figure 2 - 11. Static ARP Settings window
The following fields can be set:
Parameter Description
ARP Aging Time
(0-65535)
IP Address
MAC Address
After entering the IP Address and MAC Address of the Static ARP entry, click Apply to implement the new entry. To
completely clear the Static ARP Settings, click the Delete All button. To modify a static ARP entry, click the
corresponding Edit button in the table. To delete a static ARP entry, click the corresponding Delete button in the table.
The user may globally set the maximum amount of time, in seconds, that an Address
Resolution Protocol (ARP) entry can remain in the Switch’s ARP table, without being
accessed, before it is dropped from the table. The value may be set in the range of 0 to
65535 seconds, with a default setting of 20 seconds.
The IP address of the ARP entry.
The MAC address of the ARP entry.
NOTE: The Switch supports up to 255 static ARP entries.
21
Page 23
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
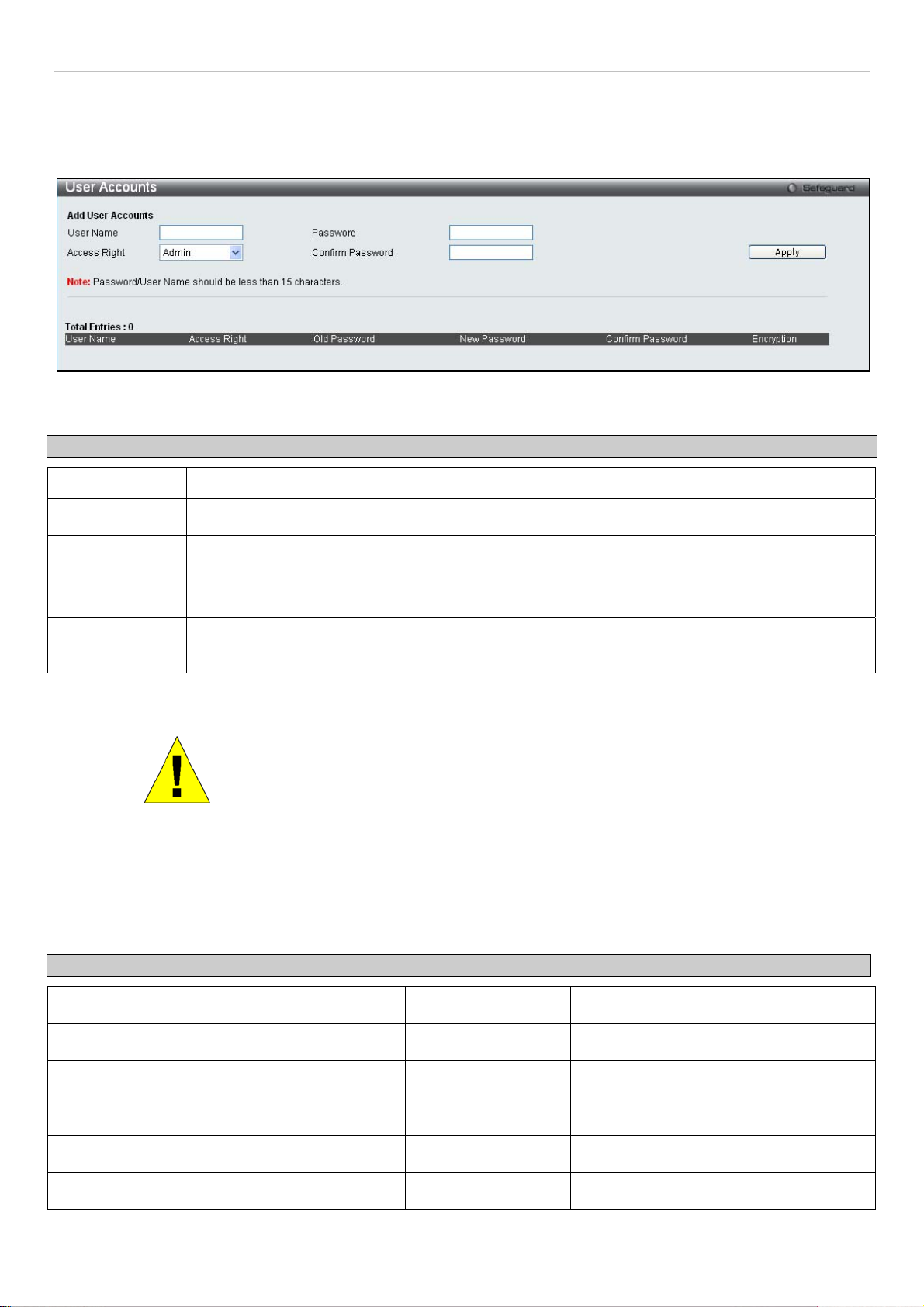
User Accounts
Use this window to control user privileges, create new users, and view existing User Accounts.
To view this window, click Configuration > User Accounts:
Figure 2 - 12. User Accounts window
The following fields can be set:
Parameter Description
User Name
Password
Access Right
Confirm
Password
To add a new user, enter the appropriate information and click Apply. To modify or delete an existing user, click on
the Edit button for that user.
The name of the user, an alphanumeric string of up to 15 characters.
Enter a password for the new user.
There are two levels of user privileges, Admin and User. Some features and selections available
to users with Admin privileges may not be available to those with User level privileges.
(Table 2 - 1 below summarizes Admin and User level privileges)
Retype the new password.
NOTICE: In case of lost passwords or password corruption, please refer to the
“Password Recovery Procedure” Appendix in the DES-3200-10/18/28/28F CLI
Reference Manual which will guide you through the steps necessary to resolve
this issue.
Admin and User Privileges
There are two levels of user privileges, Admin and User. Some menu selections available to users with Admin
privileges may not be available to those with User privileges.
The following table summarizes the Admin and User privileges:
Management Admin User
Configuration Yes Read-only
Network Monitoring Yes Read-only
Community Strings and Trap Stations Yes Read-only
Update Firmware and Configuration Files Yes No
System Utilities Yes No
Factory Reset Yes No
22
Page 24
®
xStack
User Account Management
Add/Update/Delete User Accounts Yes No
View User Accounts Yes No
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Table 2 - 1. Admin and User Privileges
System Log Configuration
This section contains information for configuring various attributes and properties for System Log Configurations,
including System Log Settings and System Log Host.
System Log Settings
This window allows the user to enable or disable the System Log and specify the System Log Save Mode Settings.
To configure the system log settings, click Configuration > System Log Configuration > System Log Settings
Figure 2 - 13. System Log Settings window
The following parameters can be set:
Parameter Description
System Log
Save Mode
min (1-65535)
To modify the system log settings on this window, enter the appropriate information and click Apply.
Use the radio buttons to either enable or disable the system log feature.
Use this drop-down menu to choose the method that will trigger a log entry. Choose among
On Demand, Time Interval, and Log Trigger.
Enter a time interval, in minutes, for which a log entry is to be made.
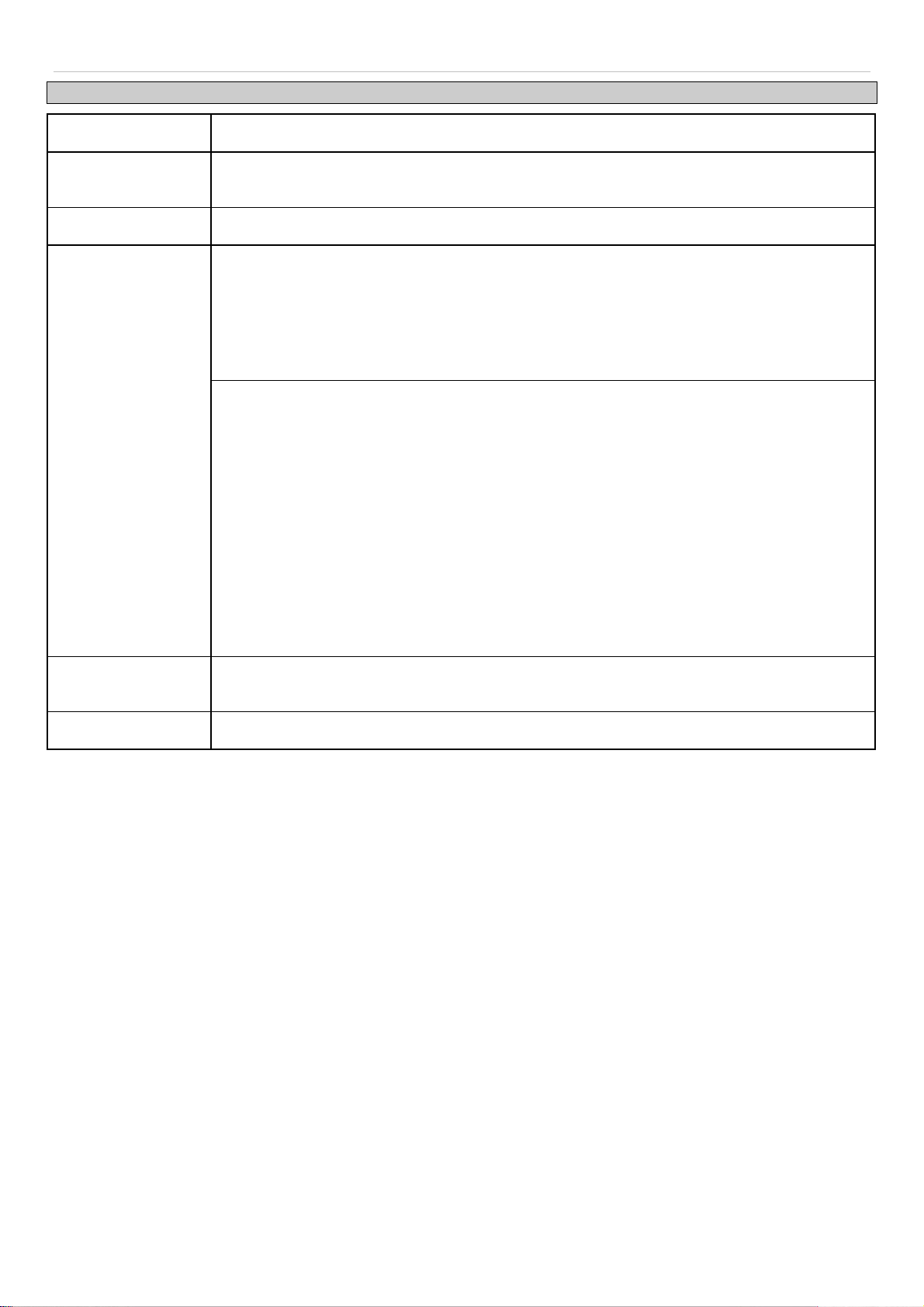
System Log Server
The Switch can send Syslog messages to up to four designated servers using the System Log Server.
To configure the system log settings, click Configuration > System Log Configuration > System Log Server:
The following parameters can be set:
Figure 2 - 14. System Log Server window
23
Page 25
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Parameter Description
Server ID
Severity
Server IP Address
Facility
Syslog server settings index (1-4).
This drop-down menu allows you to select the level of messages that will be sent. The options
are Warning, Informational, and All.
The IP address of the Syslog server.
Some of the operating system daemons and processes have been assigned Facility values.
Processes and daemons that have not been explicitly assigned a Facility may use any of the
"local use" facilities or they may use the "user-level" Facility. Those Facilities that have been
designated are shown in the following: Bold font indicates the facility values that the Switch is
currently employing.
Numerical Facility Code Numerical Facility Code
0
1
2
3
4
5
7
8
9
10
11
kernel messages
user-level messages
mail system
system daemons
security/authorization messages
messages generated internally by
syslog line printer subsystem
network news subsystem
UUCP subsystem
clock daemon
security/authorization messages
FTP daemon
12
13
14
15
16
17
18
19
20
21
22
23
NTP subsystem
log audit
log alert
clock daemon
local use 0 (local0)
local use 1 (local1)
local use 2 (local2)
local use 3 (local3)
local use 4 (local4)
local use 5 (local5)
local use 6 (local6)
local use 7 (local7)
UDP Port
Type the UDP port number used for sending Syslog messages. The default is 514.
(514 or 6000-65535)
Status
Choose Enabled or Disabled to activate or deactivate.
To add a new entry, enter the appropriate information and click Apply.
24
Page 26
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
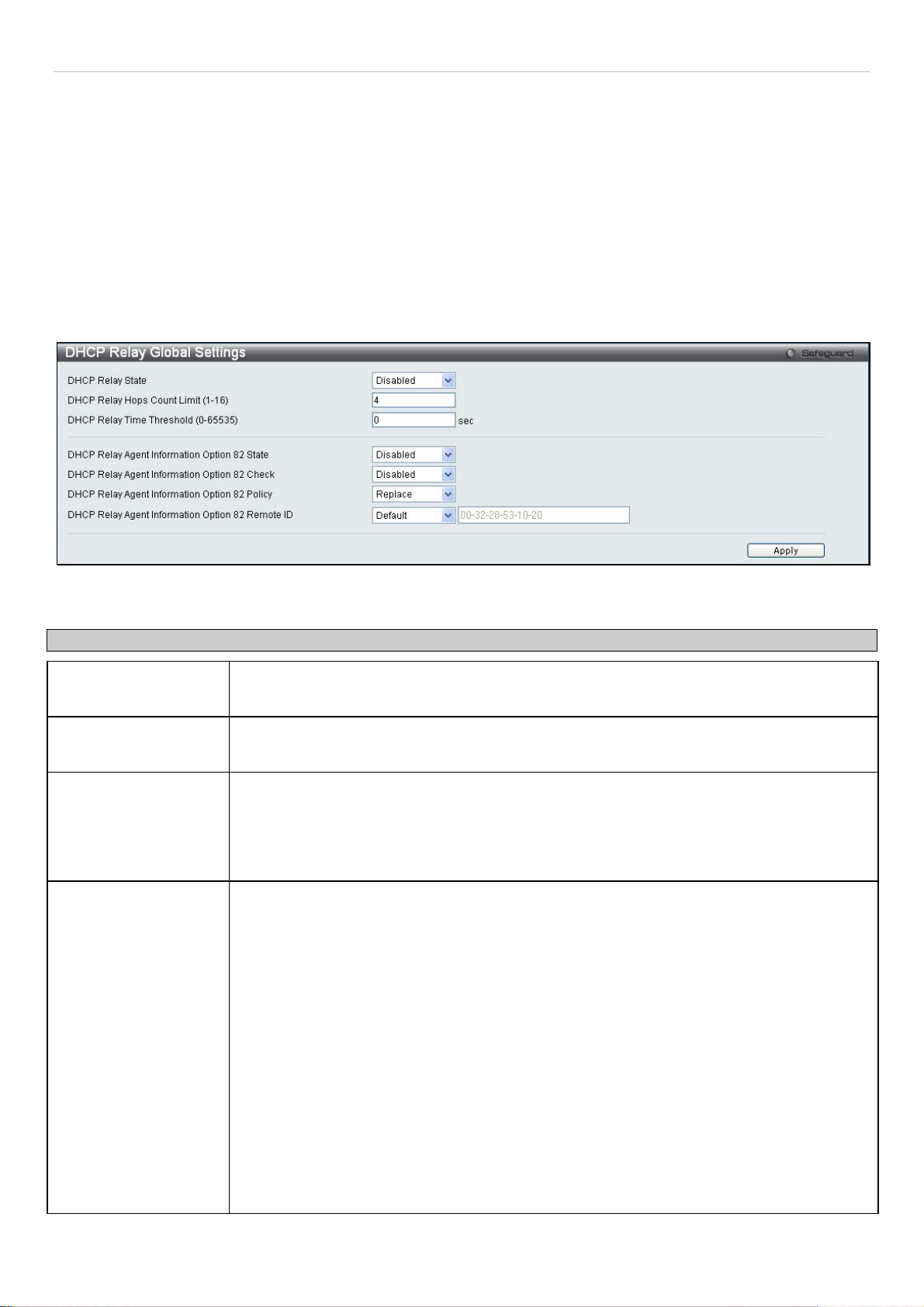
DHCP Relay
The relay hops count limit allows the maximum number of hops (routers) that the DHCP messages can be relayed
through to be set. If a packet’s hop count is equal to or more than the hop count limit, the packet is dropped. The
range is between 1 and 16 hops, with a default value of 4. The relay time threshold sets the minimum time (in seconds)
that the Switch will wait before forwarding a BOOTREQUEST packet. If the value in the seconds field of the packet is
less than the relay time threshold, the packet will be dropped. The range is between 0 and 65,535 seconds, with a
default value of 0 seconds.
DHCP Relay Global Settings
To enable and configure DHCP Relay Global Settings on the Switch, click Configuration > DHCP Relay > DHCP
Relay Global Settings:
Figure 2 - 15. DHCP Relay Global Settings window
The following fields can be set:
Parameter Description
DHCP Relay State
DHCP Relay Hops
Count Limit (1-16)
DHCP Relay Time
Threshold (0-65535)
DHCP Relay Agent
Information Option 82
State
This field can be toggled between Enabled and Disabled using the pull-down menu. It is
used to enable or disable the DHCP Relay service on the Switch. The default is Disabled
This field allows an entry between 1 and 16 to define the maximum number of router hops
DHCP messages can be forwarded across. The default hop count is 4.
Allows an entry between 0 and 65535 seconds, and defines the maximum time limit for
routing a DHCP packet. If a value of 0 is entered, the Switch will not process the value in
the seconds field of the BOOTP or DHCP packet. If a non-zero value is entered, the Switch
will use that value, along with the hop count to determine whether to forward a given
BOOTP or DHCP packet.
This field can be toggled between Enabled and Disabled using the pull-down menu. It is
used to enable or disable the DHCP Agent Information Option 82 on the Switch. The default
is Disabled.
Enabled – When this field is toggled to Enabled the relay agent will insert and remove
DHCP relay information (option 82 field) in messages between DHCP servers and clients.
When the relay agent receives the DHCP request, it adds the option 82 information, and the
IP address of the relay agent (if the relay agent is configured), to the packet. Once the
option 82 information has been added to the packet it is sent on to the DHCP server. When
the DHCP server receives the packet, if the server is capable of option 82, it can implement
policies like restricting the number of IP addresses that can be assigned to a single remote
ID or circuit ID. Then the DHCP server echoes the option 82 field in the DHCP reply. The
DHCP server unicasts the reply to the back to the relay agent if the request was relayed to
the server by the relay agent. The switch verifies that it originally inserted the option 82
data. Finally, the relay agent removes the option 82 field and forwards the packet to the
switch port that connects to the DHCP client that sent the DHCP request.
Disabled - If the field is toggled to Disabled the relay agent will not insert and remove DHCP
relay information (option 82 field) in messages between DHCP servers and clients, and the
25
Page 27
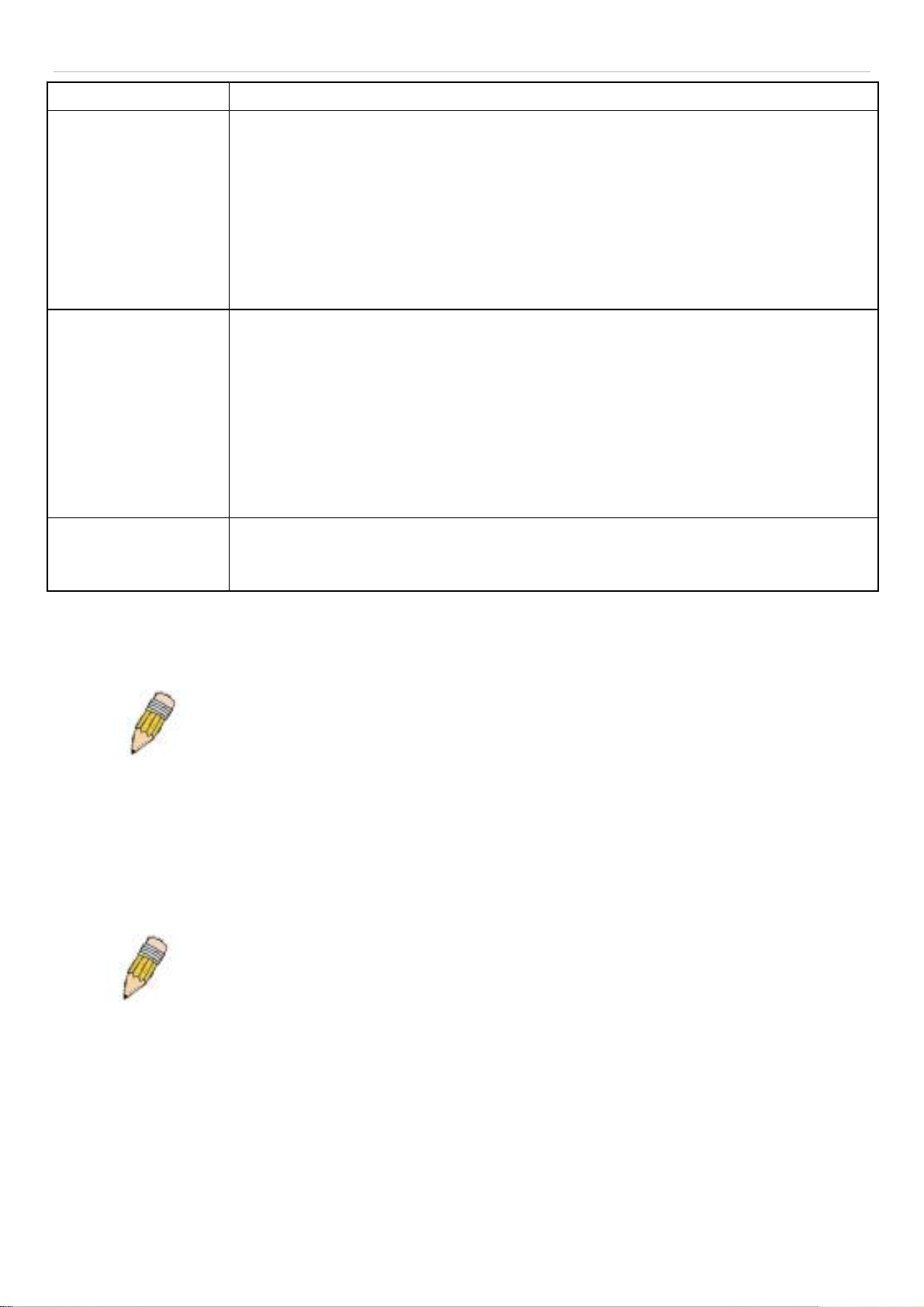
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
check and policy settings will have no effect.
DHCP Relay Agent
Information Option 82
Check
DHCP Relay Agent
Information Option 82
Policy
DHCP Relay Agent
Information Option 82
Remote ID
This field can be toggled between Enabled and Disabled using the pull-down menu. It is
used to enable or disable the Switches ability to check the validity of the packet’s option 82
field.
Enabled – When the field is toggled to Enable, the relay agent will check the validity of the
packet’s option 82 field. If the switch receives a packet that contains the option-82 field from
a DHCP client, the switch drops the packet because it is invalid. In packets received from
DHCP servers, the relay agent will drop invalid messages.
Disabled - When the field is toggled to Disabled, the relay agent will not check the validity of
the packet’s option 82 field.
This field can be toggled between Replace, Drop, and Keep by using the pull-down menu.
It is used to set the Switches policy for handling packets when the DHCP Agent Information
Option 82 Check is set to Disabled. The default is Replace.
Replace - The option 82 field will be replaced if the option 82 field already exists in the
packet received from the DHCP client.
Drop - The packet will be dropped if the option 82 field already exists in the packet received
from the DHCP client.
Keep -The option 82 field will be retained if the option 82 field already exists in the packet
received from the DHCP client.
This field is for you to enter the remote ID. Tick Default to use the Switch’s system MAC
address as the remote ID.
Click Apply to implement any changes that have been made.
NOTE: If the Switch receives a packet that contains the option-82 field from a DHCP
client and the information-checking feature is enabled, the switch drops the packet
because it is invalid. However, in some instances, you might configure a client with the
option-82 field. In this situation, you should disable the information-check feature so
that the switch does not remove the option-82 field from the packet. You can configure
the action that the switch takes when it receives a packet with existing option-82
information by configuring the DHCP Agent Information Option 82 Policy.
The Implementation of DHCP Information Option 82 on the Switch
The config dhcp_relay option_82 command configures the DHCP relay agent information option 82 setting of the
switch. The formats for the circuit ID sub-option and the remote ID sub-option are as follows:
NOTE: For the circuit ID sub-option of a standalone switch, the module field is always
zero.
26
Page 28

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Circuit ID sub-option format:
a. b. c. d. e. f. g.
1 6 0 4 VLAN Module Port
1 byte 1 byte 1 byte 1 byte 2 bytes 1 byte 1 byte
a. Sub-option type
b. Length
c. Circuit ID type
d. Length
e. VLAN: the incoming VLAN ID of DHCP client packet.
f. Module: For a standalone switch, the Module is always 0; For a stackable switch, the Module is the
Unit ID.
g. Port: The incoming port number of DHCP client packet, port number starts from 1.
Remote ID sub-option format: (default)
1. 2. 3. 4. 5.
2 8 0 6 MAC address
1 byte 1 byte 1 byte 1 byte 6 bytes
1. Sub-option type
2. Length
3. Remote ID type
4. Length
5. MAC address: The Switch’s system MAC address.
Remote ID sub-option format:(for user-configured string)
1. 2. 3. 4. 5.
2 N+2 1 N ASCII Remote ID String (up to 127 characters)
1 byte 1 byte 1 byte 1 byte N bytes
1. Sub-option type
2. Length
3. Remote ID type
4. Length
5. User configured Remote-ID
Figure 2 - 16. Circuit ID and Remote ID Sub-option Format
27
Page 29
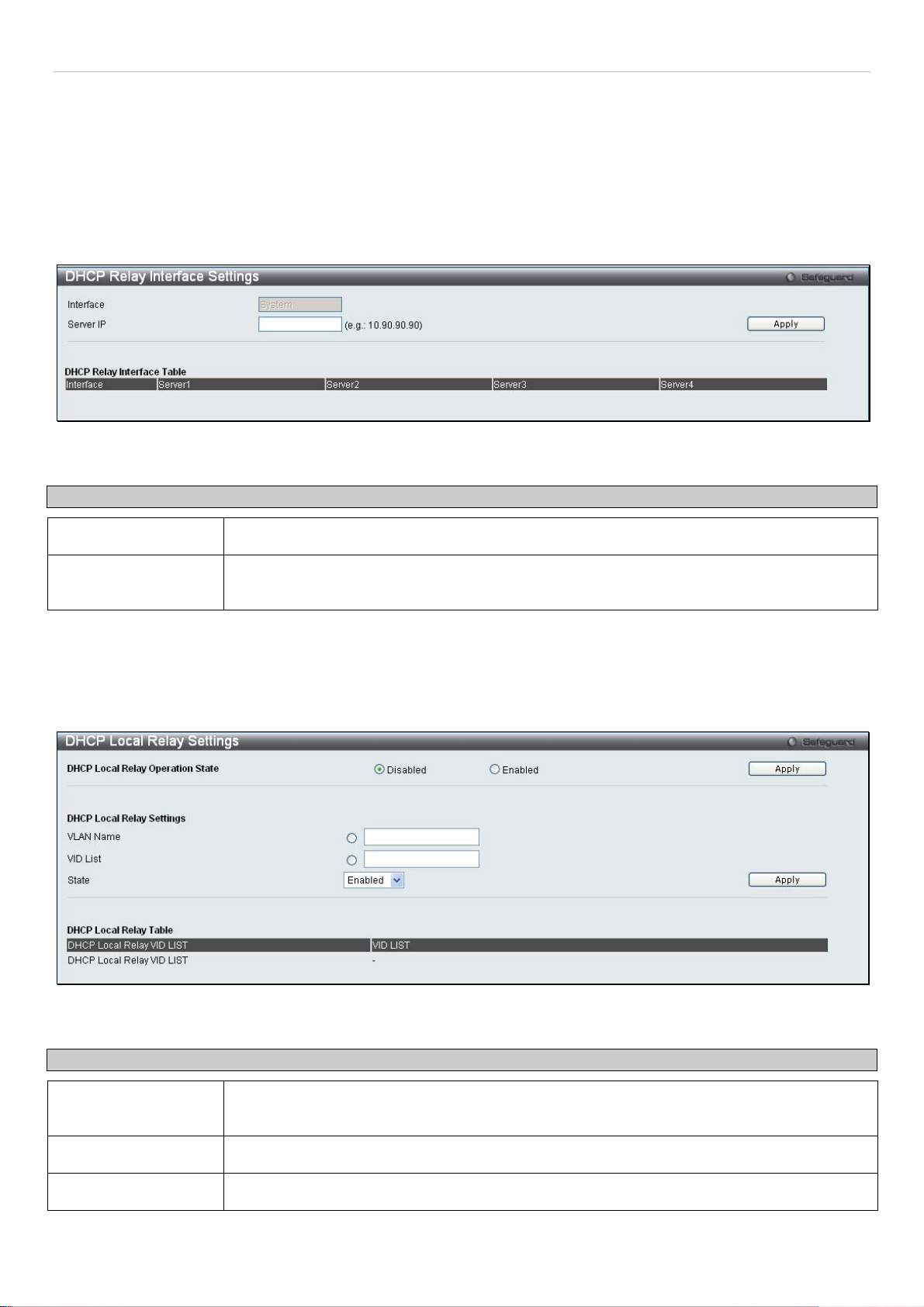
®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
DHCP Relay Interface Settings
This window allows the user to set up a server, by IP address, for relaying DHCP/ BOOTP information to the Switch.
The user may enter a previously configured IP interface on the Switch that will be connected directly to the DHCP
server using the following window. Properly configured settings will be displayed in the DHCP Relay Interface Table at
the bottom of the following window. The user may add up to four server IP’s per IP interface on the Switch.
To enable and configure DHCP Relay Global Settings on the Switch, click Configuration > DHCP Relay > DHCP
Relay Interface Settings:
Figure 2 - 17. DHCP Relay Interface Settings window
The following parameters may be configured or viewed.
Parameter Description
Interface
Server IP
The IP interface on the Switch that will be connected directly to the Server.
Enter the IP address of the DHCP server. Up to four server IPs can be configured per IP
Interface
DHCP Local Relay Settings
This function on the Switch allows configuration of the DHCP local relay for VLAN.
To view this window, click Configuration > DHCP Local Relay> DHCP Local Relay Settings:
Figure 2 - 18. DHCP Local Relay Settings window
The following parameters may be configured.
Parameter Description
DHCP Local Relay
Operation State
VLAN Name
VID List
This is used to enable or disable DHCP Local Relay service on the Switch. The default is
Disabled.
Enter a name of the VLAN to be enabled by DHCP local relay.
Enter a VLAN ID to be enabled by DHCP local relay.
28
Page 30
xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
State
This is used to enable or disable the DHCP local relay for the specified VLAN.
DHCP Auto Configuration Settings
The DHCP automatic configuration function on the Switch will load a previously saved configuration file for current use.
When DHCP auto configuration is Enabled on the Switch, the DHCP reply will contain a configuration file and path
name. It will then request the file from the TFTP server specified in the reply.
To view this window, click Configuration > DHCP Auto Configuration Settings:
Figure 2 - 19. DHCP Auto Configuration Settings window
When DHCP automatic configuration is Enabled, the Switch becomes a DHCP client automatically after rebooting.
The DHCP server must have the TFTP server IP address and configuration file name, and be configured to deliver
this information in the data field of the DHCP reply packet. The TFTP server must be running and have the requested
configuration file in its base directory when the request is received from the Switch. Consult the DHCP server and
TFTP server software instructions for information on loading a configuration file.
If the Switch is unable to complete the automatic configuration process, the previously saved local configuration file
present in Switch memory will be loaded.
MAC Address Aging Time
This table specifies the length of time a learned MAC Address will remain in the forwarding table without being
accessed (that is, how long a learned MAC Address is allowed to remain idle). To change this, enter a value
representing the MAC address age-out time in seconds. The MAC Address Aging Time can be set to any value
between 10 and 1,000,000 seconds. The default setting is 300 seconds.
To access this window, click Configuration > MAC Address Aging Time:
Figure 2 - 20. MAC Address Aging Time window
Web Settings
Web-based management is Enabled by default. If you choose to disable this by selecting Disabled, you will lose the
ability to configure the system through the Web interface as soon as these settings are applied. The TCP ports are
numbered between 1 and 65535. The "well-known" TCP port for the Web protocol is 80.
To access this window, click Configuration > Web Settings:
Figure 2 - 21. Web Settings window
29
Page 31

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Telnet Settings
Telnet configuration is Enabled by default. If you do not want to allow configuration of the system through Telnet
choose Disabled. The TCP ports are numbered between 1 and 65535. The "well-known" TCP port for the Telnet
protocol is 23.
To access this window, click Configuration > Telnet Settings:
Figure 2 - 22. Telnet Settings window
Password Encryption
Password Encryption can be Enabled or Disabled in this window. It is Disabled by default. Password encryption allows
the user to encrypt a password for additional security. Select Enabled to change the password into encrypted form.
When password encryption is Disabled, the password will be in plain text form. However, if the user specifies the
password in encrypted form, or if the password has been converted to encrypted form by the last enable password
encryption command, the password will still be in encrypted form and cannot be reverted back to plain text form.
To access this window, click Configuration > Password Encryption:
Figure 2 - 23. Password Encryption window
CLI Paging Settings
CLI paging can be Enabled or Disabled in this window. It is Enabled by default. CLI paging settings are used when
issuing a command which causes the console screen to rapidly scroll through several pages. This command will cause
the console to pause at the end of each page.
To access this window, click Configuration > CLI Paging Settings:
Figure 2 - 24. CLI Paging Settings window
30
Page 32

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Firmware Information
Information about current firmware images stored on the Switch can be viewed.
To access this window, click Configuration > Firmware Information:
Figure 2 - 25. Firmware Information window
This window holds the following information:
Parameter Description
ID
Version
Size (Bytes)
Update Time
From
User
States the image ID number of the firmware in the Switch’s memory. The Switch can store two
firmware images for use. Image ID 1 will be the default boot up firmware for the Switch unless
otherwise configured by the user.
States the firmware version.
States the size of the corresponding firmware, in bytes.
States the specific time the firmware version was downloaded to the Switch.
States the IP address of the origin of the firmware.
States the user who downloaded the firmware. This field may read “Anonymous” or “Unknown”
for users that are unidentified.
31
Page 33

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
SNTP Settings
The SNTP Settings folder offers two windows: Time Settings and Time Zone Settings.
Time Settings
To configure the time settings for the Switch, click Configuration > SNTP Settings > Time Settings:
Figure 2 - 26. Time Settings window
The following parameters can be set or are displayed:
Parameter Description
SNTP State
Current Time
Time Source
SNTP First Server
SNTP Second Server
SNTP Poll Interval in
Seconds (30-99999)
Date (DD/MM/YYYY)
Time (HH:MM:SS)
Click Apply to implement changes made.
Use the radio button to select an Enabled or Disabled SNTP state.
Displays the Current Time set on the Switch.
Displays the time source for the system.
SNTP Settings
This is the IP address of the primary server the SNTP information will be taken from.
This is the IP address of the secondary server the SNTP information will be taken from.
This is the interval, in seconds, between requests for updated SNTP information.
Set Current Time
Enter the current date in day, month and year to update the system clock.
Enter the current time in hours, minutes, and seconds.
Status
32
Page 34

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Time Zone Settings
The following window is used to configure time zones and Daylight Savings Time settings for SNTP.
To configure the time zone settings for the Switch, click Configura tion > SNTP Settings > Time Zone Settings:
Figure 2 - 27. Time Zone Settings window
The following parameters can be set:
Parameter Description
Time Zone and DST
Daylight Saving
Time State
Daylight Saving
Time Offset in
Minutes
Time Zone Offset
from GMT in +/HH:MM
Using repeating mode will enable DST seasonal time adjustment. Repeating mode requires that the DST beginning
and ending date be specified using a formula. For example, specify to begin DST on Saturday during the second
week of April and end DST on Sunday during the last week of October.
Use this pull-down menu to enable or disable the DST Settings.
Use this pull-down menu to specify the amount of time that will constitute your local DST offset
30, 60, 90, or 120 minutes.
Use these pull-down menus to specify your local time zone's offset from Greenwich Mean
Time (GMT.)
DST Repeating Settings
From: Which Week
of the Month
Enter the week of the month that DST will start on.
33
Page 35

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
From: Day of the
Enter the day of the week that DST will start on.
Week
From: Month
From: Time in
Enter the month DST will start on.
Enter the time of day that DST will start on.
HH:MM
To: Which Week of
Enter the week of the month the DST will end.
the Month
To: Day of the
Enter the day of the week that DST will end.
Week
To: Month
To:Time in HH:MM
Enter the month that DST will end.
Enter the time DST will end.
DST Annual Settings
Using annual mode will enable DST seasonal time adjustment. Annual mode requires that the DST beginning and
ending date be specified concisely. For example, specify to begin DST on April 3 and end DST on October 14.
From: Month
Enter the month DST will start on, each year.
From: Day
From: Time in
Enter the day of the week DST will start on, each year.
Enter the time of day DST will start on, each year.
HH:MM
To: Month
To: Day
To: Time in HH:MM
Enter the month DST will end, each year.
Enter the date DST will end, each year.
Enter the time of day that DST will end, each year.
Click Apply to implement changes made in this window.
34
Page 36

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
SMTP Settings
SMTP or Simple Mail Transfer Protocol is a function of the Switch that will send switch events to mail recipients based
on e-mail addresses entered in the window below. The Switch is to be configured as a client of SMTP while the server
is a remote device that will receive messages from the Switch, place the appropriate information into an e-mail and
deliver it to recipients configured on the Switch. This can benefit the Switch administrator by simplifying the
management of small workgroups or wiring closets, increasing the speed of handling emergency Switch events, and
enhancing security by recording questionable events occurring on the Switch.
Users can set up the SMTP server for the Switch, along with setting e-mail addresses to which switch log files can be
sent when a problem arises on the Switch.
SMTP Service Settings
To view the following window, click Configuration > SMTP Service Settings:
Figure 2 - 28. SMTP Service Settings window
The following parameters may be configured or viewed:
Parameter Description
SMTP State
SMTP Server
Address
SMTP Server Port
(1-65535)
Self Mail Address
Add A Mail
Receiver
Use the radio button to enable or disable the SMTP service on this device.
Enter the IP address of the SMTP server on a remote device. This will be the device that sends
out the mail for you.
Enter the virtual port number that the Switch will connect with on the SMTP server. The common
port number for SMTP is 25, yet a value between 1 and 65535 can be chosen.
Enter the e-mail address from which mail messages will be sent. This address will be the “from”
address on the e-mail message sent to a recipient. Only one self-mail address can be configured
for this Switch. This string can be no more that 64 alphanumeric characters.
Enter an e-mail address and click the Add button. Up to eight e-mail addresses can be added
per Switch. To delete these addresses from the Switch, click the corresponding Delete button in
the SMTP Mail Receiver Address table at the bottom of the window.
35
Page 37

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
SMTP Service
This window is used to test the SMTP Service Settings configured in the previous window.
To view the following window, click Configuration > SMTP Service:
Figure 2 - 29. SMTP Service window
To test to see if the SMTP settings are working properly, enter a Subject, Content, and then click the Send button.
MAC Notification Settings
MAC Notification is used to monitor MAC addresses learned and entered into the forwarding database. To globally set
MAC notification on the Switch, open the following window by opening the MAC Notification Settings in the
Configuration folder.
MAC Notification Global Settings
To configure the MAC Notification Global Settings for the Switch, click Configuration > MAC Notification Settings >
MAC Notification Global Settings
Figure 2 - 30. MAC Notification Global Settings window
The following parameters may be viewed and modified:
Parameter Description
State
Interval
(1-2147483647 sec)
History Size
(1-500)
Enable or disable MAC notification globally on the Switch.
The time in seconds between notifications.
The maximum number of entries listed in the history log used for notification. Up to 500
entries can be specified.
Click Apply to implement changes.
MAC Notification Port Settings
To configure the MAC Notification Port Settings for the Switch, click Configuration > MAC Notification Settings >
MAC Notification Port Settings:
36
Page 38

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Figure 2 - 31. MAC Notification Port Settings window
The following parameters may be modified:
Parameter Description
From Port/To
Port
State
Click Apply to implement changes.
Select a port or group of ports to enable for MAC notification using the pull-down menus.
Enable MAC Notification for the ports selected using the pull-down menu.
SNMP Settings
Simple Network Management Protocol (SNMP) is an OSI Layer 7 (Application Layer) designed specifically for
managing and monitoring network devices. SNMP enables network management stations to read and modify the
settings of gateways, routers, switches, and other network devices. Use SNMP to configure system features for proper
operation, monitor performance and detect potential problems in the Switch, switch group or network.
Managed devices that support SNMP include software (referred to as an agent), which runs locally on the device. A
defined set of variables (managed objects) is maintained by the SNMP agent and used to manage the device. These
objects are defined in a Management Information Base (MIB), which provides a standard presentation of the
information controlled by the on-board SNMP agent. SNMP defines both the format of the MIB specifications and the
protocol used to access this information over the network.
The Switch supports the SNMP versions 1, 2c, and 3. Choose which version to monitor and control the Switch. The
three versions of SNMP vary in the level of security provided between the management station and the network
device.
In SNMP v.1 and v.2, user authentication is accomplished using 'community strings', which function like passwords.
The remote user SNMP application and the Switch SNMP must use the same community string. SNMP packets from
any station that has not been authenticated are ignored (dropped).
The default community strings for the Switch used for SNMP v.1 and v.2 management access are:
• public - Allows authorized management stations to retrieve MIB objects.
• private - Allows authorized management stations to retrieve and modify MIB objects.
37
Page 39

®
xStack
SNMPv3 uses a more sophisticated authentication process that is separated into two parts. The first part is to
maintain a list of users and their attributes that are allowed to act as SNMP managers. The second part describes
what each user on that list can do as an SNMP manager.
The Switch allows groups of users to be listed and configured with a shared set of privileges. The SNMP version may
also be set for a listed group of SNMP managers. Thus, you may create a group of SNMP managers that are allowed
to view read-only information or receive traps using SNMPv1 while assigning a higher level of security to another
group, granting read/write privileges using SNMPv3.
Using SNMPv3 individual users or groups of SNMP managers can be allowed to perform or be restricted from
performing specific SNMP management functions. The functions allowed or restricted are defined using the Object
Identifier (OID) associated with a specific MIB. An additional layer of security is available for SNMPv3 in that SNMP
messages may be encrypted. To read more about how to configure SNMPv3 settings for the Switch read the next
section.
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Traps
Traps are messages that alert network personnel of events that occur on the Switch. The events can be as serious as
a reboot (someone accidentally turned OFF the Switch), or less serious like a port status change. The Switch
generates traps and sends them to the trap recipient (or network manager). Typical traps include trap messages for
Authentication Failure, Topology Change and Broadcast\Multicast Storm.
MIBs
The Switch in the Management Information Base (MIB) stores management and counter information. The Switch uses
the standard MIB-II Management Information Base module. Consequently, values for MIB objects can be retrieved
from any SNMP-based network management software. In addition to the standard MIB-II, the Switch also supports its
own proprietary enterprise MIB as an extended Management Information Base. Specifying the MIB Object Identifier
may also retrieve the proprietary MIB. MIB values can be either read-only or read-write.
The Switch incorporates a flexible SNMP management for the switching environment. SNMP management can be
customized to suit the needs of the networks and the preferences of the network administrator.
The Switch supports the Simple Network Management Protocol (SNMP) versions 1, 2c, and 3. The administrator can
specify the SNMP version used to monitor and control the Switch. The three versions of SNMP vary in the level of
security provided between the management station and the network device.
SNMP View Table
This window is used to assign views to community strings or SNMP groups that define which MIB objects can be
accessed by a remote SNMP manager.
To configure SNMP View Settings for the Switch, click Configuration > SNMP Settings > SNMP View Table:
The following parameters can be set:
Figure 2 - 32. SNMP View Table window
38
Page 40

®
xStack
Parameter Description
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
View Name
Subtree OID
View Type
To implement your new settings, click Apply. To delete an entry click the corresponding Delete button.
Type an alphanumeric string of up to 32 characters. This is used to identify the new SNMP
view being created.
Type the Object Identifier (OID) Subtree for the view. The OID identifies an object tree (MIB
tree) that will be included or excluded from access by an SNMP manager.
Select Included to include this object in the list of objects that an SNMP manager can
access. Select Excluded to exclude this object from the list of objects that an SNMP
manager can access.
SNMP Group Table
An SNMP Group created with this table maps SNMP users (identified in the SNMP User Table window) or community
strings to the views created in the previous window.
To view this window, click Configuration > SNMP Settings > SNMP Group Table:
Figure 2 - 33. SNMP Group Table window
To delete an existing SNMP Group Table entry, click the corresponding Delete button.
The following parameters can be set:
Parameter Description
Group Name Type an alphanumeric string of up to 32 characters. This is used to identify the new SNMP
group of SNMP users.
Read View Name Specify an SNMP group name for users that are allowed SNMP read privileges to the Switch’s
SNMP agent.
Write View Name Specify an SNMP group name for users that are allowed SNMP write privileges to the
Switch's SNMP agent.
Notify View Name Specify an SNMP group name for users that can receive SNMP trap messages generated by
the Switch's SNMP agent.
User-based
Security Model
SNMPv1 - Specifies that SNMP version 1 will be used.
SNMPv2 - Specifies that SNMP version 2c will be used. The SNMPv2 supports both
39
Page 41

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
centralized and distributed network management strategies. It includes improvements in the
Structure of Management Information (SMI) and adds some security features.
SNMPv3 - Specifies that the SNMP version 3 will be used. SNMPv3 provides secure access
to devices through a combination of authentication and encrypting packets over the network.
Security Level
To implement the new settings, click Apply.
The Security Level settings only apply to SNMPv3.
NoAuthNoPriv - Specifies that there will be no authorization and no encryption of packets sent
between the Switch and a remote SNMP manager.
AuthNoPriv - Specifies that authorization will be required, but there will be no encryption of
packets sent between the Switch and a remote SNMP manager.
AuthPriv - Specifies that authorization will be required, and that packets sent between the
Switch and a remote SNMP manger will be encrypted.
SNMP User Table
This window displays all of the SNMP User's currently configured on the Switch and also allows you to add new users.
To view this window, click Configuration > SNMP Settings > SNMP User Table:
Figure 2 - 34. SNMP User Table window
To delete an existing SNMP User Table entry, click the corresponding Delete button.
The following parameters may be set:
Parameter Description
User Name
Group Name
SNMP Version
SNMP V3 Encryption
Auth-Protocol by
Password
An alphanumeric string of up to 32 characters. This is used to identify the SNMP users.
This name is used to specify the SNMP group created can request SNMP messages.
V1 - Indicates that SNMP version 1 is in use.
V2 - Indicates that SNMP version 2 is in use.
V3 - Indicates that SNMP version 3 is in use.
None – Indicates that there is no SNMP V3 Encryption
Password – Indicates that there is SNMP V3 Encryption through a password
Key – Indicates that there is SNMP V3 Encryption through a key.
MD5 - Indicates that the HMAC-MD5-96 authentication level will be used.
SHA - Indicates that the HMAC-SHA authentication protocol will be used.
40
Page 42

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Priv-Protocol by
Password
Auth-Protocol by Key
Priv-Protocol by Key
Password
Key
To implement changes m
None - Indicates that no authorization protocol is in use.
DES - Indicates that DES 56-bit encryption is in use
standard.
cates that the HMAC-MD5-96 authentication level will be used. MD5 - Indi
SHA - Indicates that the HMAC-SHA authentication protocol will be used.
None - Indicates that no authorization protocol is in use.
DES - Indicates that DES 56-bit encryption is in use
standard.
ssword when SNMP V3 Encryption is enabled for Password mode. Enter a Pa
Enter a Key when SNMP V3 Encryption is enabled for Key mode.
ade, click Apply.
based on the CBC-DES (DES-56)
based on the CBC-DES (DES-56)
SNMP Community Table
Use this table to view existing SNMP Com
define the relationship between the SNMP manager and an agent. The community string acts like a password to
permit access to the agent on the Switch. One or more of the following characteristics can be associated with the
community string:
munity Table configurations and to create a SNMP community string to
Any MIB view that d
Read/write or read-only level permission for the MIB objects accessible to the SNMP community.
To configure SNMP Community entries, click Configuration > SNMP Settings > SNMP Commun
The following parameters can set:
Parameter Description
Community Name
View Name
efines the subset of all MIB objects will be accessible to the SNMP community.
Figure 2 - 35. SNMP Community Table window
Type an alphanumeric string of up to 32 characters that is used to identify members of an
SNMP community. This string is used like a password to give remote SNMP managers
access to MIB objects in the Switch's SNMP agent.
o identify the group of MIB Type an alphanumeric string of up to 32 characters that is used t
objects that a remote SNMP manager is allowed to access on the Switch. The view name
must exist in the SNMP View Table.
ity Table:
41
mmunity members using the community string created Read Only - Specifies that SNMP co
Access Right
can only read the contents of the MIBs on the Switch.
Read Write - Specifies that SNMP community members using the community string created
can read from, and write to the contents of the MIBs on the Switch.
To implement the new unity Table, click the settings, click Apply. To delete an entry from the SNMP Comm
corresponding Delete button.
Page 43

®
xStack
SNMP Host Table
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Use the SNMP Host Table w
Configuration > SNMP Settings > SNMP Host Table
The following parameters can set:
Parameter Description
Host IP Address
User-based Security
Model
indow to set up SNMP trap recipients. To configure SNMP Host Table entries, click
Figure 2 - 36. SNMP Host Table window
Type the IP address of the remote management station that will serve as the SNMP host
for the Switch.
SNMPv1 - Specifies that SNMP version 1 will be used.
SNMPV2c - Specifies that SNMP
SNMPV3 - To specify that the SNMP version 3 will be use
version 2 will be used.
d.
Security Level
Community String/
SNMPv3 User Name
To implement your new sett Apply
NMP Engine ID
S
The Engine ID is a unique i
identify the SNMP engine on t
To display the Switch's SNMP Engine ID, click Configuration > SNMP Settings > SNMP Engine ID:
To change the Engine ID, enter the ne k the Apply button. w Engine ID in the space provided and clic
NoAuthNoPriv – To specify a NoAuthNoPriv security level.
- To specify an AuthNoPriv security level. AuthNoPriv
AuthPriv - To specify an AuthPriv security level.
propriate. Type in the community string or SNMPv3 user name as ap
ings, click .
dentifier used for SNMP V3 implementations. This is an alphanumeric string used to
he Switch.
Figure 2 - 37. SNMP Engine ID window
42
Page 44

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
SNMP Trap Configuration
The following window is used to enable and disable trap settings for the SNMP function on the Switch.
To view this window for configuration, click Configuration > SNMP Settings > SNMP Trap Configuration:
Figure 2 - 38. SNMP Trap Configuration window
To enable or disable the SNMP Trap State, SNMP Authentication Traps, SNMP Link Change Traps, and configure
SNMP Link Change Trap Port Settings, use the corresponding pull-down menus. Click Apply to let the changes take
effect.
RMON
Users can enable and disable remote monitoring (RMON) status for the SNMP function on the Switch.
To view this window for configuration, click Configuration > SNMP Settings > RMO N:
Figure 2 - 39. RMON window
To enable or disable RMON for SNMP, use the radio button. Click Apply when finished.
43
Page 45

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Time Range Settings
This window is used in conjunction with the Access Profile feature to determine a starting point and an ending point,
based on days of the week, when an Access Profile configuration will be enabled on the Switch. Once configured here,
the time range settings are to be applied to an access profile rule using the Access Profile table. The user may enter
up to 64 time range entries on the Switch.
To open this window, click Configuration > Time Range Settings:
Figure 2 - 40. Time Range Settings window
Single IP Management
Simply put, D-Link Single IP Management is a concept that will stack switches together over Ethernet instead of using
stacking ports or modules. There are some advantages in implementing the "Single IP Management" feature:
1. SIM can simplify management of small workgroups or wiring closets while scaling the network to handle
increased bandwidth demand.
2. SIM can reduce the number of IP address needed in your network.
3. SIM can eliminate any specialized cables for stacking connectivity and remove the distance barriers that
typically limit your topology options when using other stacking technology.
Switches using D-Link Single IP Management (labeled here as SIM) must conform to the following rules:
SIM is an optional feature on the Switch and can easily be enabled or disabled through the Command Line Interface
or Web Interface. SIM grouping has no effect on the normal operation of the Switch in the user's network.
There are three classifications for SIM. The Commander Switch (CS), which is the master switch of the group,
Member Switch (MS), which is a switch that is recognized by the CS a member of a SIM group, and a Candidate
Switch (CaS), which is a Switch that has a physical link to the SIM group but has not been recognized by the CS as a
member of the SIM group.
A SIM group can only have one Commander Switch (CS).
All switches in a particular SIM group must be in the same IP subnet (broadcast domain). Members of a SIM group
cannot cross a router.
A SIM group accepts up to 33 switches (numbered 0-32), including the Commander Switch (numbered 0).
There is no limit to the number of SIM groups in the same IP subnet (broadcast domain), however a single switch can
only belong to one group.
If multiple VLANs are configured, the SIM group will only utilize the system VLAN on any switch.
SIM allows intermediate devices that do not support SIM. This enables the user to manage switches that are more
than one hop away from the CS.
The SIM group is a group of switches that are managed as a single entity. SIM switches may take on three different
roles:
1. Commander Switch (CS) - This is a switch that has been manually configured as the controlling device for a
group, and takes on the following characteristics:
It has an IP Address.
It is not a commander switch or member switch of another Single IP group.
It is connected to the member switches through its management VLAN.
2. Member Switch (MS) - This is a switch that has joined a single IP group and is accessible from the CS, and it
takes on the following characteristics:
It is not a CS or MS of another Single IP group.
44
Page 46

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
It is connected to the CS through the CS management VLAN.
3. Candidate Switch (CaS) - This is a switch that is ready to join a SIM group but is not yet a member of the
SIM group. The Candidate Switch may join the SIM group of a switch by manually configuring it to be a MS of
a SIM group. A switch configured as a CaS is not a member of a SIM group and will take on the following
characteristics:
It is not a CS or MS of another Single IP group.
It is connected to the CS through the CS management VLAN
After configuring one switch to operate as the CS of a SIM group, additional switches may join the group through a
direct connection to the Commander switch. Only the Commander switch will allow entry to the candidate switch
enabled for SIM. The CS will then serve as the in band entry point for access to the MS. The CS's IP address will
become the path to all MS's of the group and the CS's Administrator's password, and/or authentication will control
access to all MS's of the SIM group.
With SIM enabled, the applications in the CS will redirect the packet instead of executing the packets. The
applications will decode the packet from the administrator, modify some data, then send it to the MS. After execution,
the CS may receive a response packet from the MS, which it will encode and send it back to the administrator.
When a CaS becomes a MS, it automatically becomes a member of the first SNMP community (include read/write and
read only) to which the CS belongs. However, if a MS has its own IP address, it can belong to SNMP communities to
which other switches in the group, including the CS, do not belong.
The Upgrade to v1.6
To better improve SIM management, the Switch has been upgraded to version 1.6 in this release. Many
improvements have been made, including:
1. The Commander Switch (CS) now has the capability to automatically rediscover member switches that have left
the SIM group, either through a reboot or web malfunction. This feature is accomplished through the use of Discover
packets and Maintain packets that previously set SIM members will emit after a reboot. Once a MS has had its MAC
address and password saved to the CS’s database, if a reboot occurs in the MS, the CS will keep this MS information
in its database and when a MS has been rediscovered, it will add the MS back into the SIM tree automatically. No
configuration will be necessary to rediscover these switches.
There are some instances where pre-saved MS switches cannot be rediscovered. For example, if the Switch is still
powered down, if it has become the member of another group, or if it has been configured to be a Commander Switch,
the rediscovery process cannot occur.
2. The topology map now includes new features for connections that are a member of a port trunking group. It will
display the speed and number of Ethernet connections creating this port trunk group.
3. This version will support multiple switch upload and downloads for firmware, configuration files and log files, as
follows:
• Firmware – The switch now supports multiple MS firmware downloads from a TFTP server.
• Configuration Files – This switch now supports multiple downloading and uploading of configuration files
both to (for configuration restoration) and from (for configuration backup) MS’s, using a TFTP server..
• Log – The switch now supports uploading multiple MS log files to a TFTP server.
4. The user may zoom in and zoom out when utilizing the topology window to get a better, more defined view of the
configurations.
45
Page 47

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Single IP Settings
All switches are set as Candidate (CaS) switches as their factory default configuration and Single IP Management will
be disabled.
To enable SIM for the Switch using the Web interface, click Configuration > Single IP Managemnet > Single IP
Settings which will reveal the following window:
Figure 2 - 41. Single IP Settings window (disabled)
Use the drop-down menus to change the SIM State to Enabled, the Role State to Commander, and then fill in the
Group Name field. Click Apply to let the changes take effect.
Figure 2 - 42. Single IP Settings window (enabled)
The following parameters can be set:
Parameters Description
SIM State
Role State
Group Name
Discovery
Interval (30-90)
Hold Time Count
(100-255)
Use the pull-down menu to either enable or disable the SIM state on the Switch. Disabled will
render all SIM functions on the Switch inoperable.
Use the pull-down menu to change the SIM role of the Switch. The two choices are:
Candidate - A Candidate Switch (CaS) is not the member of a SIM group but is connected to a
Commander Switch. This is the default setting for the SIM role.
Commander - Choosing this parameter will make the Switch a Commander Switch (CS). The
user may join other switches to this Switch, over Ethernet, to be part of its SIM group. Choosing
this option will also enable the Switch to be configured for SIM.
The user may enter a name for the group.
The user may set the discovery protocol interval, in seconds that the Switch will send out
discovery packets. Returning information to a Commander Switch will include information about
other switches connected to it. (Ex. MS, CaS). The user may set the Discovery Interval from 30
to 90 seconds.
This parameter may be set for the time, in seconds the Switch will hold information sent to it
from other switches, utilizing the Discovery Interval. The user may set the hold time from 100 to
255 seconds.
Click Apply to implement the settings.
46
Page 48

®
xStack
After enabling the Switch to be a Commander Switch (CS), the Single IP Management folder will then contain four
added links to aid the user in configuring SIM through the Web, including Topology, Firmware Upgrade and
Configuration File Backup/Restore and Upload Log File.
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Topology
The Topology window will be used to configure and manage the Switch within the SIM group and requires Java script
to function properly on your computer.
The Java Runtime Environment on your server should initiate and lead you to the Topology window:
Figure 2 - 43. Topology window
The Topology window holds the following information under the Data tab:
Parameter Description
Device Name
Remote Port
Speed
Local Port
MAC Address
This field will display the Device Name of the switches in the SIM group configured by the user. If
no Device Name is configured by the name, it will be given the name default and tagged with the
last six digits of the MAC Address to identify it.
Displays the number of the physical port on the MS or CaS that the CS is connected to. The CS
will have no entry in this field.
Displays the connection speed between the CS and the MS or CaS.
Displays the number of the physical port on the CS that the MS or CaS is connected to. The CS
will have no entry in this field.
Displays the MAC address of the corresponding Switch.
47
Page 49

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Model Name
Displays the full model name of the corresponding Switch.
To view the Topology Map, click the View menu in the toolbar and then Topology, which will produce the following
window. The Topology View will refresh itself periodically (20 seconds by default).
Figure 2 - 44. Topology view
This window will display how the devices within the Single IP Management Group are connected to other groups and
devices. Possible icons in this window are as follows:
Icon Description
Group
Layer 2 commander switch
Layer 3 commander switch
Commander switch of other group
Layer 2 member switch.
Layer 3 member switch
Member switch of other group
Layer 2 candidate switch
Layer 3 candidate switch
Unknown device
48
Page 50

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Non-SIM devices
Tool Tips
In the Topology view window, the mouse plays an important role in configuration and in viewing device information.
Setting the mouse cursor over a specific device in the topology window (tool tip) will display the same information
about a specific device as the Tree view does. See the window below for an example:
Figure 2 - 45. Device Information Utilizing the Tool Tip
Setting the mouse cursor over a line between two devices will display the connection speed between the two devices,
as shown below:
Figure 2 - 46. Port Speed Utilizing the Tool Tip
49
Page 51

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Right-Click
Right-clicking on a device will allow the user to perform various functions, depending on the role of the Switch in the
SIM group and the icon associated with it.
Group Icon
Figure 2 - 47. Right-Clicking a Group Icon
Figure 2 - 48. Property window
This window holds the following information:
Parameter Description
Device Name
Module Name
MAC Address
Local Port No.
Remote Port No.
Port Speed
Click Close to close the Property window.
This field will display the Device Name of the switches in the SIM group configured by the user.
If no Device Name is configured by the name, it will be given the name default and tagged with
the last six digits of the MAC Address to identify it.
Displays the full module name of the switch that was right-clicked.
Displays the MAC Address of the corresponding Switch.
Displays the number of the physical port on the CS that the MS or CaS is connected to. The CS
will have no entry in this field.
Displays the number of the physical port on the MS or CaS that the CS is connected to. The CS
will have no entry in this field.
Displays the connection speed between the CS and the MS or CaS
50
Page 52

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Commander Switch Icon
Figure 2 - 49. Right-Clicking a Commander Icon
The following options may appear for the user to configure:
y Collapse - To collapse the group that will be represented by a single icon.
y Expand - To expand the SIM group, in detail.
y Property - To pop up a window to display the group information.
Member Switch Icon
Figure 2 - 50. Right-Clicking a Member icon
The following options may appear for the user to configure:
y Collapse - To collapse the group that will be represented by a single icon.
y Expand - To expand the SIM group, in detail.
y Remove from group - Remove a member from a group.
y Configure - Launch the web management to configure the Switch.
y Property - To pop up a window to display the device information.
Candidate Switch Icon
Figure 2 - 51. Right-Clicking a Candidate icon
The following options may appear for the user to configure:
y Collapse - To collapse the group that will be represented by a single icon.
y Expand - To expand the SIM group in detail.
51
Page 53

®
xStack
y Add to group - Add a candidate to a group. Clicking this option will reveal the following dialog for the user
to enter a password for authentication from the Candidate Switch before being added to the SIM group.
Click OK to enter the password or Cancel to exit the window.
y Property - To pop up a window to display the device information.
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Figure 2 - 52. Input password window
Menu Bar
The Single IP Management window contains a menu bar for device configurations, as seen below.
Figure 2 - 53. Menu Bar of the Topology View
The five menus on the menu bar are as follows.
File
y Print Setup - Will set the default printer properties.
y Print Topology - Will print the topology map.
y Preference - Will set display properties, such as polling interval, and the views to open at SIM startup.
Group
y Add to group - Add a candidate to a group. Clicking this option will reveal the following dialog for the user
to enter a password for authentication from the Candidate Switch before being added to the SIM group.
Click OK to enter the password or Cancel to exit the window.
Figure 2 - 54. Input password window
y Remove from Group - Remove an MS from the group.
Device
y Configure - Will open the web manager for the specific device.
View
y Refresh - Update the views with the latest status.
y Topology - Display the Topology view.
52
Page 54

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Help
y About - Will display the SIM information, including the current SIM version.
Figure 2 - 55. About window
Firmware Upgrade
This window is used to upgrade firmware from the Commander Switch to the Member Switch. Member Switches will
be listed in the table and will be specified by ID and Port (port on the CS where the MS resides), MAC Address, Model
Name and Firmware Version. To specify a certain Switch for firmware download, click its corresponding check box
under the Port heading. To update the firmware, enter the Server IP Address where the firmware resides and enter
the Path/Filename of the firmware. Click Download to initiate the file transfer.
To access the following window, click Configuration > Single IP Management > Firmware Upgrade:
Figure 2 - 56. Firmware Upgrade window
Configuration File Backup/Restore
This window is used to upgrade configuration files from the Commander Switch to the Member Switch using a TFTP
server. Member Switches will be listed in the table and will be specified by ID, Port (port on the CS where the MS
resides), MAC Address, Model Name and Firmware Version. To update the configuration file, enter the Server IP
Address where the file resides and enter the Path/Filename of the configuration file. Click Restore to initiate the file
transfer from a TFTP server to the Switch. Click Backup to backup the configuration file to a TFTP server. To access
the following window, click Configuration > Single IP Management > Configuration File Backup/Restore:
Figure 2 - 57. Configuration File Backup/Restore window
53
Page 55

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Upload Log File
The following window is used to upload log files from SIM member switches to a specified PC. To upload a log file,
enter the Server IP address of the SIM member switch and then enter a Path\Filename on your PC where you wish to
save this file. Click Upload to initiate the file transfer. To view this window click Configuration > Single IP
Management > Upload Log File
Figure 2 - 58. Upload Log File window
Gratuitous ARP
An ARP announcement (also known as Gratuitous ARP) is a packet (usually an ARP Request) containing a valid SHA
and SPA for the host which sent it, with TPA equal to SPA. Such a request is not intended to solicit a reply, but merely
updates the ARP caches of other hosts which receive the packet.
This is commonly done by many operating systems on startup, and helps to resolve problems which would otherwise
occur if, for example, a network card had recently been changed (changing the IP address to MAC address mapping)
and other hosts still had the old mapping in their ARP cache.
Gratuitous ARP Global Settings
To view this window, click Configuration > Gratuitous ARP > Gratuitous ARP Global Settings:
Figure 2 - 59. Gratuitous ARP Global Settings window
The following fields can be configured:
Parameter Description
Send On IP
Interface Status Up
Send On Duplicate
IP Detected
This is used to enable or disable the sending of gratuitous ARP request packets while an IP
interface comes up. This is used to automatically announce the interface’s IP address to other
nodes. By default, the state is Enabled.
This is used to enable or disable the sending of gratuitous ARP request packets while a
duplicate IP is detected. By default, the state is Enabled. Duplicate IP detected means that the
system received an ARP request packet that is sent by an IP address that matches the
system’s own IP address.
Gratuitous ARP
Learning
Once you have made the desired gratuitous ARP setting changes, click Apply.
This is used to enable or disable updating ARP cache based on the received gratuitous ARP
packet. If a switch receives a gratuitous ARP packet, it should add or update the ARP entry.
This is Enabled by default.
54
Page 56

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Gratuitous ARP Settings
This window allows you to have more detailed settings for the Gratuitous ARP.
To view this window, click Configuration > Gratuitous ARP > Gratuitous ARP Settings:
Figure 2 - 60. Gratuitous ARP Settings window
The following fields can be set or viewed:
Parameter Description
Trap
Log
IP Interface Name
IP Interface Name
Interval Time (0-
65535)
Click Apply to implement changes made.
The switch can trap IP conflict events to inform the administrator. By default, trap is Disabled.
The switch can log IP conflict events to inform the administrator. By default, Log is Enabled.
Displays the name of the interface that is being edited.
Gratuitous ARP Periodical Send Interval
Displays the name of the interface that is being edited.
This is used to configure the interval for the periodical sending of gratuitous ARP request
packets. By default, the interval is 0.
Gratuitous ARP Trap/Log
55
Page 57

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
ARP Spoofing Prevention Settings
ARP spoofing, also known as ARP poisoning, is a method to attack an Ethernet network which may allow an attacker
to sniff data frames on a LAN, modify the traffic, or stop the traffic altogether (known as a Denial of Service - DoS
attack). The principle of ARP spoofing is to send the fake, or spoofed ARP messages to an Ethernet network.
Generally, the aim is to associate the attacker's or random MAC address with the IP address of another node (such as
the default gateway). Any traffic meant for that IP address would be mistakenly re-directed to the node specified by
the attacker.
To prevent ARP spoofing attack, the switch uses Packet Content ACL to block the invalid ARP packets which contain
faked gateway’s MAC and IP binding.
To view this window, click Configuration > ARP Spoofing Prevention Settings as shown below:
Figure 2 - 61. ARP Spoofing Prevention Settings window
The following fields can be set or viewed:
Parameter Description
Gateway IP Address
Gateway MAC
Address
Ports (e.g.: 1, 7-10)
Enter the IP address of the gateway.
Enter the MAC address of the gateway.
Specify the switch ports for which to configure the ARP Spoofing Prevention settings. Tick
the All Ports check box to configure this entry for all ports on the Switch.
56
Page 58

xStack
L2 Features
Jumbo Frame
802.1Q Static VLAN
Q-in-Q
802.1v Protocol VLAN
VLAN Trunk Settings
GVRP Settings
Asymmetric VLAN Settings
MAC-based VLAN Settings
PVID Auto Assign Settings
Port Trunking
LACP Port Settings
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Section 3
Traffic Segmentation
BPDU Tunneling Settings
IGMP Snooping
MLD Snooping Settings
Port Mirror
Loopback Detection Settings
Spanning Tree
Forwarding & Filtering
LLDP
The following section will aid the user in configuring Layer 2 functions for the Switch. The Switch includes various
functions all discussed in detail in the following section.
Jumbo Frame
This window will enable or disable the Jumbo Frame function on the Switch. The default is Enabled. When Enabled,
jumbo frames (frames larger than the standard Ethernet frame size of 1536 bytes) with a maximum size of 2048 bytes
can be transmitted by the Switch.
To view this window, click L2 Features > Jumbo Frame:
Figure 3 - 1. Jumbo Frame window
Click Apply to implement changes made.
57
Page 59

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
VLANs
Understanding IEEE 802.1p Priority
Priority tagging is a function defined by the IEEE 802.1p standard designed to provide a means of managing traffic on
a network where many different types of data may be transmitted simultaneously. It is intended to alleviate problems
associated with the delivery of time critical data over congested networks. The quality of applications that are
dependent on such time critical data, such as video conferencing, can be severely and adversely affected by even
very small delays in transmission.
Network devices that are in compliance with the IEEE 802.1p standard have the ability to recognize the priority level of
data packets. These devices can also assign a priority label or tag to packets. Compliant devices can also strip priority
tags from packets. This priority tag determines the packet's degree of expeditiousness and determines the queue to
which it will be assigned.
Priority tags are given values from 0 to 7 with 0 being assigned to the lowest priority data and 7 assigned to the
highest. The highest priority tag 7 is generally only used for data associated with video or audio applications, which
are sensitive to even slight delays, or for data from specified end users whose data transmissions warrant special
consideration.
The Switch allows you to further tailor how priority tagged data packets are handled on your network. Using queues to
manage priority tagged data allows you to specify its relative priority to suit the needs of your network. There may be
circumstances where it would be advantageous to group two or more differently tagged packets into the same queue.
Generally, however, it is recommended that the highest priority queue, Queue 7, be reserved for data packets with a
priority value of 7. Packets that have not been given any priority value are placed in Queue 0 and thus given the
lowest priority for delivery.
Strict mode and weighted round robin system are employed on the Switch to determine the rate at which the queues
are emptied of packets. The ratio used for clearing the queues is 4:1. This means that the highest priority queue,
Queue 7, will clear 4 packets for every 1 packet cleared from Queue 0.
Remember, the priority queue settings on the Switch are for all ports, and all devices connected to the Switch will be
affected. This priority queuing system will be especially beneficial if your network employs switches with the capability
of assigning priority tags.
VLAN Description
A Virtual Local Area Network (VLAN) is a network topology configured according to a logical scheme rather than the
physical layout. VLANs can be used to combine any collection of LAN segments into an autonomous user group that
appears as a single LAN. VLANs also logically segment the network into different broadcast domains so that packets
are forwarded only between ports within the VLAN. Typically, a VLAN corresponds to a particular subnet, although not
necessarily.
VLANs can enhance performance by conserving bandwidth, and improve security by limiting traffic to specific domains.
A VLAN is a collection of end nodes grouped by logic instead of physical location. End nodes that frequently
communicate with each other are assigned to the same VLAN, regardless of where they are physically on the network.
Logically, a VLAN can be equated to a broadcast domain, because broadcast packets are forwarded to only members
of the VLAN on which the broadcast was initiated.
Notes About VLANs
No matter what basis is used to uniquely identify end nodes and assign these nodes VLAN membership, packets
cannot cross VLANs without a network device performing a routing function between the VLANs.
The Switch supports IEEE 802.1Q VLANs and Port-Based VLANs. The port untagging function can be used to
remove the 802.1Q tag from packet headers to maintain compatibility with devices that are tag-unaware.
The Switch's default is to assign all ports to a single 802.1Q VLAN named "default."
The "default" VLAN has a VID = 1.
The member ports of Port-based VLANs may overlap, if desired.
58
Page 60

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
IEEE 802.1Q VLANs
Some relevant terms:
y Tagging - The act of putting 802.1Q VLAN information into the header of a packet.
y Untagging - The act of stripping 802.1Q VLAN information out of the packet header.
y Ingress port - A port on a switch where packets are flowing into the Switch and VLAN decisions must be
made.
y Egress port - A port on a switch where packets are flowing out of the Switch, either to another switch or to
an end station, and tagging decisions must be made.
IEEE 802.1Q (tagged) VLANs are implemented on the Switch. 802.1Q VLANs require tagging, which enables them to
span the entire network (assuming all switches on the network are IEEE 802.1Q-compliant).
VLANs allow a network to be segmented in order to reduce the size of broadcast domains. All packets entering a
VLAN will only be forwarded to the stations (over IEEE 802.1Q enabled switches) that are members of that VLAN, and
this includes broadcast, multicast and unicast packets from unknown sources.
VLANs can also provide a level of security to your network. IEEE 802.1Q VLANs will only deliver packets between
stations that are members of the VLAN.
Any port can be configured as either tagging or untagging. The untagging feature of IEEE 802.1Q VLANs allows
VLANs to work with legacy switches that don't recognize VLAN tags in packet headers. The tagging feature allows
VLANs to span multiple 802.1Q-compliant switches through a single physical connection and allows Spanning Tree to
be enabled on all ports and work normally.
The IEEE 802.1Q standard restricts the forwarding of untagged packets to the VLAN of which the receiving port is a
member.
The main characteristics of IEEE 802.1Q are as follows:
y Assigns packets to VLANs by filtering.
y Assumes the presence of a single global
spanning tree.
y Uses an explicit tagging scheme with one-level
tagging.
y 802.1Q VLAN Packet Forwarding
y Packet forwarding decisions are made based
upon the following three types of rules:
y Ingress rules - rules relevant to the classification
of received frames belonging to a VLAN.
y Forwarding rules between ports - decides
whether to filter or forward the packet.
y Egress rules - determines if the packet must be
sent tagged or untagged.
Figure 3 - 2. IEEE 802.1Q Packet Forwarding
802.1Q VLAN Tags
The figure below shows the 802.1Q VLAN tag. There are four additional octets inserted after the source MAC address.
Their presence is indicated by a value of 0x8100 in the EtherType field. When a packet's EtherType field is equal to
0x8100, the packet carries the IEEE 802.1Q/802.1p tag. The tag is contained in the following two octets and consists
of three bits of user priority, one bit of Canonical Format Identifier (CFI - used for encapsulating Token Ring packets
so they can be carried across Ethernet backbones), and twelve bits of VLAN ID (VID). The three bits of user priority
are used by 802.1p. The VID is the VLAN identifier and is used by the 802.1Q standard. Because the VID is twelve
bits long, 4094 unique VLANs can be identified.
The tag is inserted into the packet header making the entire packet longer by four octets. All of the information
originally contained in the packet is retained.
59
Page 61

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Figure 3 - 3. IEEE 802.1Q Tag
The EtherType and VLAN ID are inserted after the MAC source address, but before the original EtherType/Length or
Logical Link Control. Because the packet is now a bit longer than it was originally, the Cyclic Redundancy Check
(CRC) must be recalculated.
Figure 3 - 4. Adding an IEEE 802.1Q Tag
Port VLAN ID
Packets that are tagged (are carrying the 802.1Q VID information) can be transmitted from one 802.1Q compliant
network device to another with the VLAN information intact. This allows 802.1Q VLANs to span network devices (and
indeed, the entire network, if all network devices are 802.1Q compliant).
Unfortunately, not all network devices are 802.1Q compliant. These devices are referred to as tag-unaware. 802.1Q
devices are referred to as tag-aware.
Prior to the adoption of 802.1Q VLANs, port-based and MAC-based VLANs were in common use. These VLANs relied
upon a Port VLAN ID (PVID) to forward packets. A packet received on a given port would be assigned that port's PVID
and then be forwarded to the port that corresponded to the packet's destination address (found in the Switch's
forwarding table). If the PVID of the port that received the packet is different from the PVID of the port that is to
transmit the packet, the Switch will drop the packet.
Within the Switch, different PVIDs mean different VLANs (remember that two VLANs cannot communicate without an
external router). So, VLAN identification based upon the PVIDs cannot create VLANs that extend outside a given
switch (or switch stack).
60
Page 62

®
xStack
Every physical port on a switch has a PVID. 802.1Q ports are also assigned a PVID, for use within the Switch. If no
VLANs are defined on the Switch, all ports are then assigned to a default VLAN with a PVID equal to 1. Untagged
packets are assigned the PVID of the port on which they were received. Forwarding decisions are based upon this
PVID, in so far as VLANs are concerned. Tagged packets are forwarded according to the VID contained within the tag.
Tagged packets are also assigned a PVID, but the PVID is not used to make packet-forwarding decisions, the VID is.
Tag-aware switches must keep a table to relate PVIDs within the Switch to VIDs on the network. The Switch will
compare the VID of a packet to be transmitted to the VID of the port that is to transmit the packet. If the two VIDs are
different, the Switch will drop the packet. Because of the existence of the PVID for untagged packets and the VID for
tagged packets, tag-aware and tag-unaware network devices can coexist on the same network.
A switch port can have only one PVID, but can have as many VIDs as the Switch has memory in its VLAN table to
store them.
Because some devices on a network may be tag-unaware, a decision must be made at each port on a tag-aware
device before packets are transmitted - should the packet to be transmitted have a tag or not? If the transmitting port
is connected to a tag-unaware device, the packet should be untagged. If the transmitting port is connected to a tagaware device, the packet should be tagged.
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Tagging and Untagging
Every port on an 802.1Q compliant switch can be configured as tagging or untagging.
Ports with tagging enabled will put the VID number, priority and other VLAN information into the header of all packets
that flow into and out of it. If a packet has previously been tagged, the port will not alter the packet, thus keeping the
VLAN information intact. Other 802.1Q compliant devices on the network to make packet-forwarding decisions can
then use the VLAN information in the tag.
Ports with untagging enabled will strip the 802.1Q tag from all packets that flow into and out of those ports. If the
packet doesn't have an 802.1Q VLAN tag, the port will not alter the packet. Thus, all packets received by and
forwarded by an untagging port will have no 802.1Q VLAN information. (Remember that the PVID is only used
internally within the Switch). Untagging is used to send packets from an 802.1Q-compliant network device to a noncompliant network device.
Ingress Filtering
A port on a switch where packets are flowing into the Switch and VLAN decisions must be made is referred to as an
ingress port. If ingress filtering is enabled for a port, the Switch will examine the VLAN information in the packet
header (if present) and decide whether or not to forward the packet.
If the packet is tagged with VLAN information, the ingress port will first determine if the ingress port itself is a member
of the tagged VLAN. If it is not, the packet will be dropped. If the ingress port is a member of the 802.1Q VLAN, the
Switch then determines if the destination port is a member of the 802.1Q VLAN. If it is not, the packet is dropped. If
the destination port is a member of the 802.1Q VLAN, the packet is forwarded and the destination port transmits it to
its attached network segment.
If the packet is not tagged with VLAN information, the ingress port will tag the packet with its own PVID as a VID (if the
port is a tagging port). The switch then determines if the destination port is a member of the same VLAN (has the
same VID) as the ingress port. If it does not, the packet is dropped. If it has the same VID, the packet is forwarded and
the destination port transmits it on its attached network segment.
This process is referred to as ingress filtering and is used to conserve bandwidth within the Switch by dropping
packets that are not on the same VLAN as the ingress port at the point of reception. This eliminates the subsequent
processing of packets that will just be dropped by the destination port.
Default VLANs
The Switch initially configures one VLAN, VID = 1, called "default." The factory default setting assigns all ports on the
Switch to the "default." As new VLANs are configured in Port-based mode, their respective member ports are removed
from the "default."
Packets cannot cross VLANs. If a member of one VLAN wants to connect to another VLAN, the link must be through
an external router.
61
Page 63

®
xStack
NOTE: If no VLANs are configured on the Switch, then all packets will be forwarded to any
destination port. Packets with unknown source addresses will be flooded to all ports.
Broadcast and multicast packets will also be flooded to all ports.
An example is presented below:
VLAN Name VID Switch Ports
System (default) 1 5, 6, 7, 8, 21, 22, 23, 24
Engineering 2 9, 10, 11, 12
Marketing 3 13, 14, 15, 16
Finance 4 17, 18, 19, 20
Sales 5 1, 2, 3, 4
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Table 3 - 1. VLAN Example - Assigned Ports
Port-based VLANs
Port-based VLANs limit traffic that flows into and out of switch ports. Thus, all devices connected to a port are
members of the VLAN(s) the port belongs to, whether there is a single computer directly connected to a switch, or an
entire department.
On port-based VLANs, NICs do not need to be able to identify 802.1Q tags in packet headers. NICs send and receive
normal Ethernet packets. If the packet's destination lies on the same segment, communications take place using
normal Ethernet protocols. Even though this is always the case, when the destination for a packet lies on another
switch port, VLAN considerations come into play to decide if the packet gets dropped by the Switch or delivered.
VLAN Segmentation
Take for example a packet that is transmitted by a machine on Port 1 that is a member of VLAN 2. If the destination
lies on another port (found through a normal forwarding table lookup), the Switch then looks to see if the other port
(Port 10) is a member of VLAN 2 (and can therefore receive VLAN 2 packets). If Port 10 is not a member of VLAN 2,
then the packet will be dropped by the Switch and will not reach its destination. If Port 10 is a member of VLAN 2, the
packet will go through. This selective forwarding feature based on VLAN criteria is how VLANs segment networks.
The key point being that Port 1 will only transmit on VLAN 2.
Network resources can be shared across VLANs. This is achieved by setting up overlapping VLANs. That is ports can
belong to more than one VLAN group. For example, by setting VLAN 1 members to ports 1, 2, 3 and 4 and VLAN 2
members to ports 1, 5, 6 and 7, Port 1 will belong to two VLAN groups. Ports 8, 9 and 10 are not configured to any
VLAN group. This means ports 8, 9 and 10 are in the same VLAN group.
VLAN and Trunk Groups
The members of a trunk group have the same VLAN setting. Any VLAN setting on the members of a trunk group will
apply to the other member ports.
NOTE: In order to use VLAN segmentation in conjunction with port trunk groups, you can first
set the port trunk group(s), and then you may configure VLAN settings. If you wish to change
the port trunk grouping with VLANs already in place, you will not need to reconfigure the VLAN
settings after changing the port trunk group settings. VLAN settings will automatically change in
conjunction with the change of the port trunk group settings.
Q-in-Q VLANs
Q-in-Q VLANs (also sometimes referred to as double VLANs) allow network providers to expand their VLAN
configurations to place customer VLANs within a larger inclusive VLAN, which adds a new layer to the VLAN
configuration. This basically lets large ISP's create L2 Virtual Private Networks and also create transparent LANs for
their customers, which will connect two or more customer LAN points without over-complicating configurations on the
client's side. Not only will over-complication be avoided, but also now the administrator has over 4000 VLANs in which
62
Page 64

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
over 4000 VLANs can be placed, therefore greatly expanding the VLAN network and enabling greater support of
customers utilizing multiple VLANs on the network.
Q-in-Q VLANs are basically VLAN tags placed within existing IEEE 802.1Q VLANs which we will call SPVIDs (Service
Provider VLAN IDs). These VLANs are marked by a TPID (Tagged Protocol ID), configured in hex form to be
encapsulated within the VLAN tag of the packet. This identifies the packet as double-tagged and segregates it from
other VLANs on the network, therefore creating a hierarchy of VLANs within a single packet.
Here is an example Q-in-Q VLAN tagged packet:
Destination
Address
Address
Consider the example below:
Source
SPVLAN (TPID +
Service Provider
VLAN Tag)
802.1Q CEVLAN Tag
(TPID + Customer VLAN
Tag)
Ether
Type
Payload
Figure 3 - 5. Q-in-Q VLAN Example
In this example, the Service Provider Access Network switch (Provider edge switch) is the device creating and
configuring Q-in-Q VLANs with different SPVIDs for specific customers (say Customer A and Customer B). Both
CEVLANs (Customer VLANs), CEVLAN 10 are tagged with the SPVID 100 (for Customer A) or SPVID 200 (for
Customer B) on the Service Provider Access Network, thus being a member of two VLANs on the Service Provider’s
network. In this way, the Customer can retain their normal VLAN ID’s and the Service Provider can seperate multiple
Customer VLANs using SPVLANs, thus greatly regulating traffic and routing on the Service Provider switch. This
information is then routed to the Service Provider’s main network and regarded there as one VLAN, with one set of
protocols and one routing behavior.
Regulations for Q-in-Q VLANs
Some rules and regulations apply with the implementation of the Q-in-Q VLAN procedure.
1. All ports must be configured for the SPVID and its corresponding TPID on the Service Provider’s edge switch.
63
Page 65

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
2. All ports must be configured as Access Ports or Uplink ports. Access ports can only be Ethernet ports while
Uplink ports must be Gigabit ports.
3. Provider Edge switches must allow frames of at least 1522 bytes or more, due to the addition of the SPVID
tag.
4. Access Ports must be an un-tagged port of the service provider VLANs. Uplink Ports must be a tagged port of
the service provider VLANs.
5. The switch cannot have both Q-in-Q and normal VLANs co-existing. Once the change of VLAN is made, all
Access Control lists are cleared and must be reconfigured.
6. Before Q-in-Q VLANs are enabled, users need to disable STP and GVRP manually.
7. All packets sent from the CPU to the Access ports must be untagged.
802.1Q Static VLAN
This window lists all previously configured VLANs by VLAN ID and VLAN Name.
To view this window, click L2 Features > 802.1Q Static VLAN:
Figure 3 - 6. 802.1Q Static VLAN window - VLAN List tab
To create a new 802.1Q VLAN entry, click the Add/Edit VLAN tab at the top of the window. A new tab will appear, as
shown in the first figure on the next page, to configure the port settings and to assign a unique name and number to
the new VLAN.
To edit an existing 802.1Q VLAN entry, click the Edit button next to the corresponding VLAN entry above. A new tab
will appear, as shown in the second figure on the next page.
See the table on the next page for a description of the parameters of the 802.1Q Static VLAN window’s Add/Edit
VLAN tab.
NOTE: After all IP interfaces are set for configurations, VLANs on the
Switch can be routed without any additional steps.
64
Page 66

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Figure 3 - 7. 802.1Q Static VLAN window – Add/Edit VLAN tab (Add)
To return to the initial 802.1Q Static VLAN window, click the VLAN List tab at the top of the window. To change an
existing 802.1Q static VLAN entry, click the corresponding Edit button. A new window will appear to configure the port
settings and to assign a unique name and number to the new VLAN. See the table below for a description of the
parameters in the new window.
NOTE: The Switch supports up to 4k static VLAN entries.
Figure 3 - 8. 802.1Q Static VLAN window – Add/Edit VLAN tab (Edit)
The following fields can then be set in the Add/Edit VLAN tab:
Parameter Description
VID (VLAN ID)
Allows the entry of a VLAN ID, or displays the VLAN ID of an existing VLAN in the Edit
window. VLANs can be identified by either the VID or the VLAN name.
VLAN Name
Allows the entry of a name for a new VLAN, or modifying the VLAN name in the Edit window.
65
Page 67

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
VLAN Name should be no more than 32 characters in length.
Advertisement
Enabling this function will allow the Switch to send out GVRP packets to outside sources,
notifying that they may join the existing VLAN.
Port Settings
Tagged
Untagged
Forbidden
Allows an individual port to be specified as member of a VLAN.
Specifies the port as 802.1Q tagged. Checking the box will designate the port as Tagged.
Specifies the port as 802.1Q untagged. Checking the box will designate the port as untagged.
Select this to specify the port as not being a member of the VLAN and that the port is
forbidden from becoming a member of the VLAN dynamically.
Not Member
Allows an individual port to be specified as a non-VLAN member.
Click Apply to implement changes made.
To search for a VLAN, click the Find VLAN tab at the top of the window (see below), enter a VLAN ID, and click Find
to display the settings for a previously configured VLAN.
Figure 3 - 9. 802.1Q Static VLAN window – Find VLAN tab
To create a VLAN Batch entry, click the VLAN Batch Settings tab at the top of the window, which will display the
following window:
66
Page 68

®
xStack
Figure 3 - 10. 802.1Q Static VLAN window – VLAN Batch Settings tab
The following fields can be set in the VLAN Batch Settings tab:
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Parameter Description
VID List (e.g.: 2-5)
Advertisement
Port List (e.g.: 1-5)
Tagged
Untagged
Forbidden
Click Apply to implement changes made.
Enter a VLAN ID List that can be added, deleted or configured.
Enabling this function will allow the Switch to send out GVRP packets to outside sources,
notifying that they may join the existing VLAN.
Allows an individual port list to be added or deleted as a member of the VLAN.
Specifies the port as 802.1Q tagged. Checking the box will designate the port as Tagged.
Specifies the port as 802.1Q untagged. Checking the box will designate the port as untagged.
Select this to specify the port as not being a member of the VLAN and that the port is
forbidden from becoming a member of the VLAN dynamically.
Q-in-Q
This function allows the user to enable or disable the Q-in-Q function. Q-in-Q is designed for service providers to carry
traffic from multiple users across a network.
Q-in-Q is used to maintain customer specific VLAN and Layer 2 protocol configurations even when the same VLAN ID
is being used by different customers. This is achieved by inserting SPVLAN tags into the customer’s frames when
they enter the service provider’s network, and then removing the tags when the frames leave the network.
Customers of a service provider may have different or specific requirements regarding their internal VLAN IDs and the
number of VLANs that can be supported. Therefore customers in the same service provider network may have VLAN
ranges that overlap, which might cause traffic to become mixed up. So assigning a unique range of VLAN IDs to each
customer might cause restrictions on some of their configurations requiring intense processing of VLAN mapping
tables which may exceed the VLAN mapping limit. Q-in-Q uses a single service provider VLAN (SPVLAN) for
customers who have multiple VLANs. Customer’s VLAN IDs are segregated within the service provider’s network
even when they use the same customer specific VLAN ID. Q-in-Q expands the VLAN space available while preserving
the customer’s original tagged packets and adding SPVLAN tags to each new frame.
67
Page 69

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Q-in-Q Settings
To view this window, click L2 Features > Q-in-Q > Q-in-Q Settings:
The following fields can be set:
Parameter Description
Q-in-Q Global
Settings
From Port/To Port
Role
Outer TPID (hex:
0x1 -0xffff)
Trust CVID
Click the radio button to enable or disable the Q-in-Q Global Settings.
A consecutive group of ports that are part of the VLAN configuration starting with the selected
port.
The user can choose between UNI or NNI role.
UNI – To select a user-network interface which specifies that communication between the
specified user and a specified network will occur.
NNI – To select a network-to-network interface specifies that communication between two
specified networks will occur.
The Outer TPID is used for learning and switching packets. The Outer TPID constructs and
inserts the outer tag into the packet based on the VLAN ID and Inner Priority.
Enable or disable the Trust Customer VLAN ID (CVID). If the state is Enabled, use the CVID
from the customer’s packet as the VLAN ID of the SPVLAN tag. The default is Disabled.
Figure 3 - 11. Q-in-Q Settings window
VLAN Translation
Click Apply to implement changes.
Enable or disable VLAN Translation. This translates the VLAN IDs carried in the data packets
received from private networks into those used in the Service Provider’s network. The default
is Disabled. Note: To use this function, Trust CVID must also be enabled.
68
Page 70

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
VLAN Translation Settings
VLAN translation translates the VLAN ID carried in the data packets it receives from private networks into those used
in the Service Providers network.
To view this window click L2 Features > Q-in-Q > VLAN Translation CVID Entry Settings:
Figure 3 - 12. VLAN Translation Settings window
The following fields can be set:
Parameter Description
Action
CVID (1-4094)
SVID(1-4094)
Click Apply to make a new entry and Delete All to remove a VLAN Translation entry.
Specify to Add or Replace Service Provider VLAN ID (SVID) packets.
The customer VLAN ID List to which the tagged packets will be added.
This configures the VLAN to join the Service Providers VLAN as a tagged member.
802.1v Protocol VLAN
The window allows the user to create Protocol VLAN groups and add protocols to that group. The 802.1v Protocol
VLAN Group Settings supports multiple VLANs for each protocol and allows the user to configure the untagged ports
of different protocols on the same physical port. For example it allows the user to configure an 802.1Q and 802.1v
untagged port on the same physical port. The lower half of the window displays any previously created groups.
802.1v Protocol Group Settings
To view this window, click L2 Features > 802.1v Protocol VLAN > 802.1v Protocol Group Settings:
The following fields can be set:
Figure 3 - 13. 802.1v Protocol Group Settings window
69
Page 71

®
xStack
Parameter Description
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Group ID (1-16)
Group Name
Protocol
Protocol Value
(0-FFFF)
Click Add to make a new entry and Delete All to remove an entry.
Select an ID number for the group, between 1 and 16.
This is used to identify the new Protocol VLAN group. Type an alphanumeric string of up to 32
characters.
This function maps packets to protocol-defined VLANs by examining the type octet within the
packet header to discover the type of protocol associated with it. Use the drop-down menu to
toggle between Ethernet II and IEEE802.3 SNAP.
Enter a value for the Group.
802.1v Protocol VLAN Settings
The window allows the user to configure Protocol VLAN settings. The lower half of the window displays any previously
created settings.
To view this window, click L2 Features > 802.1v Protocol VLAN > 802.1v Protocol VLAN Settings:
Figure 3 - 14. 802.1v Protocol VLAN Settings window
The following fields can be set:
Parameter Description
Group ID
Group Name
VID (1-4094)
VLAN Name
802.1p Priority
Click the corresponding radio button to select a previously configured Group ID from the dropdown menu.
Click the corresponding radio button to select a previously configured Group Name from the
drop-down menu.
Click the radio button to enter the VID. This is the VLAN ID that, along with the VLAN Name,
identifies the VLAN the user wishes to create.
Click the radio button to enter a VLAN Name. This is the VLAN Name that, along with the
VLAN ID, identifies the VLAN the user wishes to create.
This parameter is specified to re-write the 802.1p default priority previously set in the Switch,
which is used to determine the CoS queue to which packets are forwarded to. Once this field
is specified, packets accepted by the Switch that match this priority are forwarded to the CoS
queue specified previously by the user.
For more information on priority queues, CoS queues and mapping for 802.1p, see the QoS
section of this manual.
70
Page 72

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Port List (e.g.: 1-6)
Search Port List
Select the specified ports you wish to configure by entering the port number in this field, or tick
the Select All Ports box.
This function allows the user to search all previously configured port list settings and display
them on the lower half of the table. To search for a port list enter the port number you wish to
view and click Find. To display all previously configured port lists on the bottom half of the
window click the Show All button, to clear all previously configured lists click the Delete All
button.
VLAN Trunk Settings
Enable VLAN on a port to allow frames belonging to unknown VLAN groups to pass through that port. This is useful if
you want to set up VLAN groups on end devices without having to configure the same VLAN groups on intermediary
devices.
Refer to the following figure for an illustrated example. Suppose you want to create VLAN groups 1 and 2 (V1 and V2)
on devices A and B. Without a VLAN Trunk, you must first configure VLAN groups 1 and 2 on all intermediary
switches C, D and E; otherwise they will drop frames with unknown VLAN group tags. However, with VLAN Trunk
enabled on a port(s) in each intermediary switch, you only need to create VLAN groups in the end devices (A and B).
C, D and E automatically allow frames with VLAN group tags 1 and 2 (VLAN groups that are unknown to those
switches) to pass through their VLAN trunking port(s).
Users can combine a number of VLAN ports together to create VLAN trunks. To create VLAN Trunk Port settings on
the Switch, select the ports to be configured, change the VLAN Trunk Global State to Enabled, and click Apply, the
new settings will appear in the VLAN Trunk Settings table in the lower part of the window.
To view the following window, click L2 Features > VLAN Trunk Settings:
Figure 3 - 15. VLAN Trunk Settings window
The user-changeable parameters are as follows:
Parameter Description
VLAN Trunk Global
State
Enable or disable the VLAN trunking global state.
Ports
The ports to be configured.
71
Page 73

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
GVRP Settings
This window allows the user to determine whether the Switch will share its VLAN configuration information with other
GARP VLAN Registration Protocol (GVRP) enabled switches. In addition, Ingress Checking can be used to limit traffic
by filtering incoming packets whose PVID do not match the PVID of the port. Results can be seen in the table under
the configuration settings, as seen below.
To view this window, click L2 Features > GVRP Settings:
The following fields can be set:
Parameter Description
GVRP State
Settings
From Port/To Port
PVID (1-4094)
GVRP
Ingress Checking
Click the radio buttons to enable or disable the GVRP global state settings.
These two fields allow you to specify the range of ports that will be included in the Port-based
VLAN that you are creating using the 802.1Q Port Settings window.
Enter a PVID assignment for each port, which may be manually assigned to a VLAN when
created in the 802.1Q Port Settings table. The Switch's default is to assign all ports to the
default VLAN with a VID of 1. The PVID is used by the port to tag outgoing, untagged packets,
and to make filtering decisions about incoming packets. If the port is specified to accept only
tagged frames - as tagging, and an untagged packet is forwarded to the port for transmission,
the port will add an 802.1Q tag using the PVID to write the VID in the tag. When the packet
arrives at its destination, the receiving device will use the PVID to make VLAN forwarding
decisions. If the port receives a packet, and Ingress filtering is enabled, the port will compare
the VID of the incoming packet to its PVID. If the two are unequal, the port will drop the packet.
If the two are equal, the port will receive the packet.
The Group VLAN Registration Protocol (GVRP) enables the port to dynamically become a
member of a VLAN. GVRP is Disabled by default.
This field can be toggled using the space bar between Enabled and Disabled. Enabled enables
Figure 3 - 16. GVRP Settings window
72
Page 74

®
xStack
the port to compare the VID tag of an incoming packet with the PVID number assigned to the
port. If the two are different, the port filters (drops) the packet. Disabled disables ingress filtering. Ingress Checking is Enabled by default.
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Acceptable Frame
Type
Click Apply to implement changes made.
This field denotes the type of frame that will be accepted by the port. The user may choose
between Tagged Only, which means only VLAN tagged frames will be accepted, and All, which
mean both tagged and untagged frames will be accepted. All is enabled by default.
Asymmetric VLAN Settings
Shared VLAN Learning is a primary example of the requirement for Asymmetric VLANs. Under normal circumstances,
a pair of devices communicating in a VLAN environment will both send and receive using the same VLAN; however,
there are some circumstances in which it is convenient to make use of two distinct VLANs, one used for A to transmit
to B and the other used for B to transmit to A in these cases Asymmetric VLANs are needed. An example of when this
type of configuration might be required would be if the client was on a distinct IP subnet, or if there was some
confidentiality-related need to segregate traffic between the clients.
To view this window, click L2 Features > Asymmetric VLAN Settings:
Figure 3 - 17. Asymmetric VLAN Settings window
Click Apply to implement changes.
MAC-based VLAN Settings
This window is used to create MAC-based VLAN entries on the switch. A MAC Address can be mapped to any existing
static VLAN and multiple MAC addresses can be mapped to the same VLAN. When a static MAC-based VLAN entry
is created for a user, the traffic from this user is able to be serviced under the specified VLAN. Therefore each entry
specifies a relationship of a source MAC address with a VLAN.
To view this window, click L2 Features > MAC-based VLAN Settings:
Figure 3 - 18. MAC-based VLAN Settings window
The following fields can be set
Parameter Description
MAC Address
VLAN Name
Click Find, Add or Delete All for changes to take affect.
Specify the MAC address to be mapped.
Enter the VLAN name of a previously configured VLAN.
73
Page 75

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
PVID Auto Assign Settings
This enables or disables PVID Auto Assign on the Switch. PVID is the VLAN that the switch will use for forwarding and
filtering purposes. If PVID Auto-Assign is Enabled, PVID will be possibly changed by previously set PVID or VLAN
configurations. When a user configures a port to VLAN X’s untagged membership, this port’s PVID will be updated
with VLAN X. In the form of a VLAN list command, PVID is updated with the last item on the VLAN list. When a user
removes a port from the untagged membership of the PVID’s VLAN, the port’s PVID will be assigned to a default
VLAN. When PVID Auto Assign is Disabled, PVID can only be changed by PVID configuration (user changes
explicitly). The VLAN configuration will not automatically change the PVID. The default setting is Enabled.
To view this window, click L2 Features > PVID Auto Assign Settings:
Figure 3 - 19. PVID Auto Assign Settings window
Port Trunking
Understanding Port Trunk Groups
Port trunk groups are used to combine a number of ports together to make a single high-bandwidth data pipeline. The
Switch supports up to fourteen port trunk groups with two to eight ports in each group.
Figure 3 - 20 Example of Port Trunk Group
The Switch treats all ports in a trunk group as a single port. Data transmitted to a specific host (destination address)
will always be transmitted over the same port in a trunk group. This allows packets in a data stream to arrive in the
same order they were sent.
74
Page 76

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
NOTE: If any ports within the trunk group become disconnected, packets intended for the
disconnected port will be load shared among the other unlinked ports of the link aggregation
group.
Link aggregation allows several ports to be grouped together and to act as a single link. This gives a bandwidth that is
a multiple of a single link's bandwidth.
Link aggregation is most commonly used to link a bandwidth intensive network device or devices, such as a server, to
the backbone of a network.
The Switch allows the creation of up to fourteen link aggregation groups, each group consisting of two to eight links
(ports). All of the ports in the group must be members of the same VLAN, and their STP status, static multicast, traffic
control; traffic segmentation and 802.1p default priority configurations must be identical. Port locking, port mirroring
and 802.1X must not be enabled on the trunk group. Further, the aggregated links must all be of the same speed and
should be configured as full duplex.
The Master Port of the group is to be configured by the user, and all configuration options, including the VLAN
configuration that can be applied to the Master Port, are applied to the entire link aggregation group.
Load balancing is automatically applied to the ports in the aggregated group, and a link failure within the group causes
the network traffic to be directed to the remaining links in the group.
The Spanning Tree Protocol will treat a link aggregation group as a single link, on the switch level. On the port level,
the STP will use the port parameters of the Master Port in the calculation of port cost and in determining the state of
the link aggregation group. If two redundant link aggregation groups are configured on the Switch, STP will block one
entire group; in the same way STP will block a single port that has a redundant link.
To view this window, click L2 Features > Port Trunking:
Figure 3 - 21. Port Trunking window
The following fields can be set
Parameter Description
Algorithm
The algorithm that the Switch uses to balance the load across the ports that make up the port
trunk group is defined by this definition. Choose MAC Source, MAC Destination, MAC Source
Dest, IP Source , IP Destination or IP Source Dest (See the Link Aggregation section of this
manual).
Group ID (1-14)
Type
Master Port
State
Active Ports
Select an ID number for the group, between 1 and 14.
This pull-down menu allows you to select between Static and LACP (Link Aggregation Control
Protocol). LACP allows for the automatic detection of links in a Port Trunking Group.
Choose the Master Port for the trunk group using the pull-down menu.
Trunk groups can be toggled between Enabled and Disabled. This is used to turn a port
trunking group on or off. This is useful for diagnostics, to quickly isolate a bandwidth intensive
network device or to have an absolute backup aggregation group that is not under automatic
control.
Shows the ports that are currently forwarding packets.
75
Page 77

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
(Member) Ports
Flooding Ports
Click Apply to implement changes made.
Choose the members of a trunked group. Up to eight ports per group can be assigned to a
group.
These ports are designated for flooding broadcast, multicast, and DLF (unicast Destination
Lookup Fail) packets from the CPU in a trunk group. The port is defined by software and
doesn’t actually exist in the hardware.
LACP Port Settings
This window is used to create port trunking groups on the Switch. The user may set which ports will be active and
passive in processing and sending LACP control frames.
To view this window, click L2 Features > LACP Port Settings:
Figure 3 - 22. LACP Port Settings window
The following fields can be set
Parameter Description
From Port/To Port
Activity
Click Apply to implement changes made.
A consecutive group of ports may be configured starting with the selected port.
Active - Active LACP ports are capable of processing and sending LACP control frames. This
allows LACP compliant devices to negotiate the aggregated link so the group may be
changed dynamically as needs require. In order to utilize the ability to change an aggregated
port group, that is, to add or subtract ports from the group, at least one of the participating
devices must designate LACP ports as active. Both devices must support LACP.
Passive - LACP ports that are designated as passive cannot initially send LACP control
frames. In order to allow the linked port group to negotiate adjustments and make changes
dynamically, one end of the connection must have "active" LACP ports (see above).
76
Page 78

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Traffic Segmentation
Traffic segmentation is used to limit traffic flow from a single port to a group of ports on the Switch. This method of
segmenting the flow of traffic is similar to using VLANs to limit traffic, but is more restrictive. It provides a method of
directing traffic that does not increase the overhead of the Switch CPU. This window allows the user to view which
ports on the Switch are allowed to forward packets to other ports on the Switch. To configure new forwarding ports for
a particular port, select a port from the From Port and To Port drop-down menus and click Apply.
To view this window, click L2 Features > Traffic Segmentation:
Figure 3 - 23. Traffic Segmentation window
The following fields can be set
Parameter Description
From Port/To Port
Forward Portlist
Clicking the Apply button will enter the combination of transmitting port and allowed receiving ports into the Switch's
Current Traffic Segmentation Table.
Check the corresponding boxes for the port(s) to transmit packets.
Check the boxes to select which of the ports on the Switch will be able to forward packets.
These ports will be allowed to receive packets from the port specified above.
77
Page 79

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
BPDU Tunneling Settings
To view this window, click L2 Features > BPDU Tunneling Settings:
Figure 3 - 24. BPDU Tunneling Settings window
IGMP Snooping
Internet Group Management Protocol (IGMP) snooping allows the Switch to recognize IGMP queries and reports sent
between network stations or devices and an IGMP host. When enabled for IGMP snooping, the Switch can add or
remove a port to a specific device based on IGMP messages passing through the Switch.
In order to use IGMP Snooping, it must first be enabled for the entire Switch. Then, fine-tune the settings for each
VLAN using the IGMP Snooping windows in the L2 Features folder. When enabled for IGMP snooping, the Switch
can open or close a port to a specific multicast group member based on IGMP messages sent from the device to the
IGMP host or vice versa. The Switch monitors IGMP messages and discontinues forwarding multicast packets when
there are no longer hosts requesting that they continue.
IGMP Snooping Settings
Use this window to enable or disable IGMP snooping on the Switch. The IGMP Snooping State under IGMP Snooping
Global Settings can be enabled or disabled and a Max Learning Entry Value between 1 and 1024 can be entered in
the field under IGMP Data Driven Learning Settings. Click Apply to modify the settings.
To view this window, click L2 Features > IGMP Snooping > IGMP Snooping Settings:
Figure 3 - 25. IGMP Snooping Settings window
Clicking the Edit button will open this window:
78
Page 80

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Figure 3 - 26. IGMP Snooping Settings (Edit) window
The following fields can be set.
Parameter Description
VLAN ID
VLAN Name
Querier Expiry
Time
Querier IP
Max Response
Time (1-25)
Query Interval
(1-65535)
Last Listener
Query Interval
(1-25)
Robustness Value
(1-255)
Querier State
Fast Done
This is the VLAN ID that, along with the VLAN Name, identifies the VLAN for which the user
wishes to modify the IGMP Snooping Settings.
This is the VLAN Name that, along with the VLAN ID, identifies the VLAN for which the user
wishes to modify the IGMP Snooping Settings.
Displays the querier expiry time.
The IP address of the device which acts as the IGMP querier for the network.
This determines the maximum amount of time in seconds to wait for reports from members.
The Max Response Time field allows an entry between 1 and 25 (seconds). The default is 10.
The Query Interval field is used to set the time (in seconds) between transmitting IGMP
queries. Entries between 1 and 65535 seconds are allowed. The default is 125.
This field specifies the maximum amount of time between group-specific query messages,
including those sent in response to leave group messages. The default is 1.
Adjust this variable according to expected packet loss. If packet loss on the VLAN is expected
to be high, the Robustness Variable should be increased to accommodate increased packet
loss. This entry field allows an entry of 1 to 255. The default is 2.
Choose Enabled to enable transmitting IGMP query packets or Disabled to disable the
transmitting of IGMP query packets. The default is Disabled.
This parameter allows the user to enable the Fast Leave function. Enabled, this function will
allow members of a multicast group to leave the group immediately (without the
implementation of the Last Member Query Timer) when an IGMP Leave Report Packet is
received by the Switch. The default is Disabled.
State
Data Driven
Learning Aged Out
Version
Querier Role
Select Enabled to implement IGMP Snooping. This field is Disabled by default.
Allows users to enable or disable aged out of IGMP Snooping data driven learning for the
specified VLAN.
Allows the user to configure the IGMP version used on the Switch. The default value is 3.
This read-only field describes the behavior of the Switch for sending query packets. Querier will
denote that the Switch is sending out IGMP query packets. Non-Querier will denote that the
Switch is not sending out IGMP query packets. This field will only read Querier when the
Querier State and the State fields have been Enabled.
To modify the IGMP Snooping Router Port Settings, click on the Modify Router Port hyperlink, which will show the
following window for the user to configure:
79
Page 81

®
xStack
Select the desired member ports and click Apply. Click <<Back to go back to the IGMP Snooping Settings window.
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Figure 3 - 27. IGMP Snooping Router Ports Settings window
IGMP Access Control Settings
This window is used to configure IGMP Access Control settings on the Switch.
To view this window, click L2 Features > IGMP Snooping > IGMP Access Control Settings:
Figure 3 - 28. IGMP Access Control Settings window
Parameter Description
From Port/To Port
State
Click Apply to implement changes made.
Select a range of ports.
Enable or disable the IGMP Access Control. When Enable is selected and the Switch receives
an IGMP Join request, the Switch will send the access request to the RADIUS server to do the
authentication.
80
Page 82

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
IGMP Snooping Multicast VLAN Settings
This window is used to configure the IGMP Snooping Multicast VLAN settings on the Switch.
To view this window, click L2 Features > IGMP Snooping > IGMP Snooping Multicast VLAN Settings:
Figure 3 - 29. IGMP Snooping Multicast VLAN Settings window
The following fields can be set
Parameter Description
ISM VLAN Global
State
VLAN Name
VID (2-4094)
State
Replace Source IP
Member Port (e.g.:
1-4, 6)
Source Port (e.g.:
1-4, 6)
Tagged Member
Port (e.g.: 1-4, 6)
Untagged Source
Port (e.g.: 1-4, 6)
Remap Priority
(Value 0-7)
Click the Enabled or Disabled radio button to enable or disable multicast VLAN.
This is the VLAN Name that, along with the VLAN ID, identifies the VLAN the user wishes to
add or modify the IGMP Snooping Settings for.
This is the VLAN ID that, along with the VLAN Name, identifies the VLAN the user wishes to
add or modify the IGMP Snooping Settings for.
Enable or disable multicast VLANs for the chosen VLAN.
With the IGMP snooping function, the IGMP report packet sent by the host will be forwarded to
the source port. Before forwarding of the packet, the source IP address in the join packet
needs to be replaced by this IP address. If none is specified, the source IP address will not be
replaced.
A range of member ports to add to the multicast VLAN. They will become the untagged
member ports of the ISM VLAN.
Select the source Port for the multicast VLAN.
Specifies the ports that will be tagged as members of the multicast VLAN.
A range of untagged source ports to add to the multicast VLAN. The reassigned PVID of the
untagged source port will be automatically changed to the multicast VLAN.
The remap priority is associated with the data traffic to be forwarded on the multicast VLAN. If
None is selected, the packet’s original priority will be used.The default setting is None.
Replace Priority
To edit an entry, click the corresponding Edit button. To delete an entry, click the corresponding Delete button.
To add a multicast VLAN to a profile that has been created, click the corresponding hyperlinked Group List
the following window:
Tick this option so that the packet’s priority will be changed based on the remap priority by the
Switch. This option takes effect only when remap priority is set.
to reveal
81
Page 83

®
xStack
Figure 3 - 30. IGMP Snooping Multicast VLAN Group List Settings window
Enter a Multicast Address and click Add. The new information will be displayed in the table at the bottom of the
window. Click Show IGMP Snooping Multicast VLAN Entries
Settings window. Click Delete All to remove all the entries on this window.
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
to return to the IGMP Snooping Multicast VLAN
IP Multicast Profile Settings
This window allows the user to add a profile to which multicast IP address reports are to be received on specified
ports on the Switch. This function will therefore limit the number of reports received and the number of multicast
groups configured on the Switch. The user may set an IP Multicast address or range of IP Multicast addresses to
accept reports (Permit) or deny reports (Deny) coming into the specified switch ports.
To view this window, click L2 Features > IGMP Snooping > IP Multicast Profile Settings:
Figure 3 - 31. IP Multicast Profile Settings window
The following fields can be set
Parameter Description
Profile ID
Profile Name
To edit and entry click the corresponding Edit button and to delete an entry click the corresponding Delete button.
To configure the Group List Settings click the hyperlinked Group List
Use the drop-down menu to choose a Profile ID.
Enter a name for the IP Multicast Profile.
Figure 3 - 32. IP Multicast Profile Settings (Edit) window
. The following window will appear:
82
Page 84

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Figure 3 - 33. Multicast Address Group List Settings window
Enter the Multicast Address List starting with the lowest in the range, and click Add. To return to the IP Multicast
Profile Settings window, click the <<Back button.
83
Page 85

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Limited Multicast Range Settings
This window enables the user to configure the ports on the Switch that will be involved in the Limited IP Multicast
Range. The user can configure the range of ports and associate an IP Multicast Profile to allow or disallow IGMP join
requests to multicast groups defined in the profile.
To configure these settings, click L2 Features > IGMP Snooping > Limited Multicast Range Settings:
Figure 3 - 34. Limited Multicast Range Settings window
To add a new range enter the information and click Add, to delete an entry enter the information and click Delete.
Max Multicast Group Settings
This window allows users to configure the ports on the Switch that will be a part of the maximum number of multicast
groups that can be learned. To add a new Max Multicast Group, enter the information and click Apply.
To view this window, click L2 Features > IGMP Snooping > Max Multicast Group Settings:
84
Page 86

xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Figure 3 - 35. Max Multicast Group Settings window
The following fields can be set:
Parameter Description
From Port/To Port
Max Group (1-1024)
Use the drop-down menus to choose a range of ports.
Enter the maximum number of the multicast groups. The range is from 1 to 1024.
MLD Snooping Settings
Multicast Listener Discovery (MLD) Snooping is an IPv6 function used similarly to IGMP snooping in IPv4. It is used to
discover ports on a VLAN that are requesting multicast data. Instead of flooding all ports on a selected VLAN with
multicast traffic, MLD snooping will only forward multicast data to ports that wish to receive this data through the use
of queries and reports produced by the requesting ports and the source of the multicast traffic.
MLD snooping is accomplished through the examination of the layer 3 part of an MLD control packet transferred
between end nodes and a MLD router. When the Switch discovers that this route is requesting multicast traffic, it adds
the port directly attached to it into the correct IPv6 multicast table, and begins the process of forwarding multicast
traffic to that port. This entry in the multicast routing table records the port, the VLAN ID and the associated multicast
IPv6 multicast group address and then considers this port to be a active listening port. The active listening ports are
the only ones to receive multicast group data.
The Switch supports both MLD Snooping version 1 and MLD version 2.
MLD Control Messages
If implementing MLD snooping version 1, three types of messages are transferred between devices. These three
messages are all defined by three ICMPv6 packet headers, labeled 130, 131, and 132.
1. Multicast Listener Query, Version 1 – Similar to the IGMPv2 Host Membership Query for IPv4, and labeled
as 130 in the ICMPv6 packet header, this message is sent by the router to ask if any link is requesting
multicast data. There are two types of MLD query messages emitted by the router. The General Query is used
to advertise all multicast addresses that are ready to send multicast data to all listening ports, and the
Multicast Specific query, which advertises a specific multicast address that is also ready. These two types of
messages are distinguished by a multicast destination address located in the IPv6 header and a multicast
address in the Multicast Listener Query Message.
85
Page 87

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
2. Multicast Listener Report, Version 1 – Comparable to the Host Membership Report in IGMPv2, and labeled
as 131 in the ICMP packet header, this message is sent by the listening port to the Switch stating that it is
interested in receiving multicast data from a multicast address in response to the Multicast Listener Query
message.
3. Multicast Listener Done – Akin to the Leave Group Message in IGMPv2, and labeled as 132 in the ICMPv6
packet header, this message is sent by the multicast listening port stating that it is no longer interested in
receiving multicast data from a specific multicast group address, therefore stating that it is “done” with the
multicast data from this address. Once this message is received by the Switch, it will no longer forward
multicast traffic from a specific multicast group address to this listening port.
If implementing MLD snooping version 2, two types of messages are transferred between devices. The two messages
are defined by two ICMPv6 packet headers, labeled 130 and 143.
1. Multicast Listener Query, Version 2 – Similar to the IGMPv3 Membership Query for IPv4, and labeled as
130 in the ICMPv6 packet header, this message is sent by the router to ask if any link is requesting multicast
data. With MLD snooping version 2, there are three types of MLD query messages emitted by the router, as
described below:
• The router sends a General Query message to learn which multicast addresses have listeners on an
attached link. In a General Query, both the Multicast Address field and the Number of Sources field
are set to zero.
• The router sends a Multicast Address Specific Query message to learn if a particular multicast
address has any listeners on an attached link. In a Multicast Address Specific Query, the Multicast
Address field contains the multicast address that the router is interested in, while the Number of
Sources field is set to zero.
• The router sends a Multicast Address and Source Specific Query to learn if any of the sources from
the specified list for the particular multicast address has any listeners on an attached link or not. In a
Multicast Address and Source Specific Query the Multicast Address field contains the multicast
address that the router is interested in, while the Source Address field(s) contain(s) the source
address(es) that the router is interested in.
2. Multicast Listener Report, Version 2 - Comparable to the Host Membership Report in IGMPv3, and labeled
as 143 in the ICMP packet header, this message is sent by the listening port to the Switch stating that it is
interested in receiving multicast data from a multicast address in response to the Multicast Listener Query
message.
This window is used to enable MLD Snooping on the Switch and to configure the settings for MLD snooping. To
enable the MLD Snooping State, click the Enable radio button under MLD Snooping Global Settings and click Apply.
To view this window, click L2 Features > MLD Snooping Settings:
Figure 3 - 36. MLD Snooping Settings window
To configure the settings for an existing entry click the corresponding Edit button which will display the following
window.
Figure 3 - 37. MLD Snooping Settings (Edit) window
86
Page 88

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
The following parameters may be viewed or modified:
Parameter Description
VLAN ID
VLAN Name
Query Interval
(1-65535)
Max Response
Time (1-25)
Robustness Value
(1-255)
Last Listener
Query Interval
(1-25)
Fast Done
State
Version
Querier Role
This is the VLAN ID that, along with the VLAN Name, identifies the VLAN for which the user
wishes to modify the MLD Snooping Settings.
This is the VLAN Name that, along with the VLAN ID, identifies the VLAN for which the user
wishes to modify the MLD Snooping Settings.
The Query Interval field is used to set the time (in seconds) between transmitting MLD queries.
Entries between 1 and 65535 seconds are allowed. The default is 125.
This determines the maximum amount of time in seconds to wait for reports from members.
The Max Response Time field allows an entry between 1 and 25 (seconds). The default is 10.
Adjust this variable according to expected packet loss. If packet loss on the VLAN is expected
to be high, the Robustness Variable should be increased to accommodate increased packet
loss. This entry field allows an entry of 1 to 255. The default is 2.
This field specifies the maximum amount of time between group-specific query messages,
including those sent in response to leave group messages. The default is 1.
This parameter allows the user to enable the Fast Leave function. Enabled, this function will
allow members of a multicast group to leave the group immediately (without the
implementation of the Last Listener Query Interval) when an MLD Leave Report Packet is
received by the Switch. The default is Disabled.
Select Enabled to implement MLD Snooping. This field is Disabled by default.
The read-only field displays the MLD version used on the Switch, 2.
This read-only field describes the behavior of the Switch for sending query packets. Querier will
denote that the Switch is sending out MLD query packets. Non-Querier will denote that the
Switch is not sending out MLD query packets.
Click Apply to implement any changes made and <<Back to return to the initial MLD Snooping Settings window.
To modify the MLD Snooping Router Port Settings, click on the hyperlinked Modify Router Port
, which will show the
following window for the user to configure:
Figure 3 - 38. MLD Snooping Router Ports Settings window
Select the desired router ports and then click Apply to implement any changes made. To select either all of the static
router ports or all of the forbidden router ports, click the corresponding Select All button. To clear either all of the
selected static router ports or all of the selected forbidden router ports, click the corresponding Clear All button. Click
<<Back to return to the MLD Snooping Settings window.
87
Page 89

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Port Mirror
The Switch allows you to copy frames transmitted and received on a port and redirect the copies to another port. You
can attach a monitoring device to the mirrored port, such as a sniffer or an RMON probe, to view details about the
packets passing through the first port. This is useful for network monitoring and troubleshooting purposes.
To view this window, click Layer 2 Features > Port Mirror:
Figure 3 - 39. Port Mirror window
To configure a mirror port:
1. Change the status to Enabled.
2. Select the Target Port, which receives the copies from the source port.
3. Select the Source Port from where the frames come from.
4. Click Apply to let the changes take effect.
NOTE: You cannot mirror a fast port onto a slower port. For example, if you try to mirror the
traffic from a 100 Mbps port onto a 10 Mbps port, this can cause throughput problems. The port
you are copying frames from should always support an equal or lower speed than the port to
which you are sending the copies. Also, the target port for the mirroring cannot be a member of
a trunk group. Please note a target port and a source port cannot be the same port.
88
Page 90

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Loopback Detection Settings
The Loopback Detection function is used to detect the loop created by a specific port. This feature is used to
temporarily shutdown a port on the Switch when a CTP (Configuration Testing Protocol) packet has been looped back
to the Switch. When the Switch detects CTP packets received from a port, it signifies a loop on the network. The
Switch will automatically block the port and send an alert to the administrator. The Loopback Detection port will restart
(change to discarding state) when the Loopback Detection Recover Time times out. The Loopback Detection function
can be implemented on a range of ports at a time. The user may enable or disable this function using the pull-down
menu.
To view this window, click L2 Features > Loopback Detection Settings:
Figure 3 - 40. Loopback Detection Settings window
Parameter Description
State
Interval (1-32767)
Mode
Recover Time
(0 or 60-1000000)
From Port
To Port
State
Click Apply to implement changes made.
Use the drop-down menu to enable or disable loopback detection. The default is
Disabled.
Set a loop-detect Interval between 1 and 32767 seconds. The default is 10 seconds.
This read-only field displays Port Based.
Time allowed (in seconds) for recovery when a loopback is detected. The Loop-detect
Recover Time can be set at 0 seconds, or 60 to 1000000 seconds. Entering 0 will
disable the Loopdetect Recover Time. The default is 60 seconds.
Use the drop-down menu to select a beginning port number.
Use the drop-down menu to select an ending port number.
Use the drop-down menu to toggle between Enabled and Disabled.
89
Page 91

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Spanning Tree
This Switch supports three versions of the Spanning Tree Protocol: STP, Rapid STP, and MSTP. STP will be familiar
to most networking professionals. However, since RSTP and MSTP have been recently introduced to D-Link managed
Ethernet switches, a brief introduction to the technology is provided below followed by a description of how to set up
STP, RSTP, and MSTP.
802.1Q-2005 MSTP
Multiple Spanning Tree Protocol, or MSTP, is a standard defined by the IEEE community that allows multiple VLANs
to be mapped to a single spanning tree instance, which will provide multiple pathways across the network. Therefore,
these MSTP configurations will balance the traffic load, preventing wide scale disruptions when a single spanning tree
instance fails. This will allow for faster convergences of new topologies for the failed instance. Frames designated for
these VLANs will be processed quickly and completely throughout interconnected bridges utilizing any of the three
spanning tree protocols (STP, RSTP or MSTP).
This protocol will also tag BPDU packets so receiving devices can distinguish spanning tree instances, spanning tree
regions and the VLANs associated with them. An MSTI ID will classify these instances. MSTP will connect multiple
spanning trees with a Common and Internal Spanning Tree (CIST). The CIST will automatically determine each MSTP
region, its maximum possible extent and will appear as one virtual bridge that runs a single spanning tree.
Consequentially, frames assigned to different VLANs will follow different data routes within administratively
established regions on the network, continuing to allow simple and full processing of frames, regardless of administrative errors in defining VLANs and their respective spanning trees.
Each switch utilizing the MSTP on a network will have a single MSTP configuration that will have the following three
attributes:
1. A configuration name defined by an alphanumeric string of up to 32 characters (defined in the MST
Configuration Identification window in the Configuration Name field).
2. A configuration revision number (named here as a Revision Level and found in the MST Configuration
Identification window) and;
3. A 4094-element table (defined here as a VID List in the MST Configuration Identification window), which
will associate each of the possible 4094 VLANs supported by the Switch for a given instance.
To utilize the MSTP function on the Switch, three steps need to be taken:
1. The Switch must be set to the MSTP setting (found in the STP Bridge Global Settings window in the STP
Version field)
2. The correct spanning tree priority for the MSTP instance must be entered (defined here as a Priority in the
MSTI Config Information window when configuring MSTI ID settings).
3. VLANs that will be shared must be added to the MSTP Instance ID (defined here as a VID List in the MST
Configuration Identification window when configuring an MSTI ID settings).
Rapid Spanning Tree
The Switch implements three versions of the Spanning Tree Protocol, the Multiple Spanning Tree Protocol (MSTP) as
defined by the IEEE 802.1Q-2005, the Rapid Spanning Tree Protocol (RSTP) as defined by the IEEE 802.1D-2004
specification and a version compatible with the IEEE 802.1D-1998 STP. RSTP can operate with legacy equipment
implementing IEEE 802.1D-1998, however the advantages of using RSTP will be lost.
The Rapid Spanning Tree Protocol (RSTP) evolved from the STP standard. RSTP was developed in order to
overcome some limitations of STP that impede the function of some recent switching innovations, in particular, certain
Layer 3 functions that are increasingly handled by Ethernet switches. The basic function and much of the terminology
is the same as STP. Most of the settings configured for STP are also used for RSTP. This section introduces some
new Spanning Tree concepts and illustrates the main differences between the two protocols.
90
Page 92

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Port Transition States
An essential difference between the three protocols is in the way ports transition to a forwarding state and in the way
this transition relates to the role of the port (forwarding or not forwarding) in the topology. MSTP and RSTP combine
the transition states disabled, blocking and listening used in STP and creates a single state Discarding. In either case,
ports do not forward packets. In the STP port transition states disabled, blocking or listening or in the RSTP/MSTP
port state discarding, there is no functional difference, the port is not active in the network topology. The table below
compares how the three protocols differ regarding the port state transition.
All three protocols calculate a stable topology in the same way. Every segment will have a single path to the root
bridge. All bridges listen for BPDU packets. However, BPDU packets are sent more frequently - with every Hello
packet. BPDU packets are sent even if a BPDU packet was not received. Therefore, each link between bridges is
sensitive to the status of the link. Ultimately this difference results in faster detection of failed links, and thus faster
topology adjustment. A drawback of STP is this absence of immediate feedback from adjacent bridges.
MSTP RSTP STP Forwarding Learning
Disabled Disabled Disabled No No
Discarding Discarding Blocking
Discarding Discarding Listening
Learning Learning Learning
Forwarding Forwarding Forwarding Yes Yes
Table 3 - 1. Comparing Port States
RSTP is capable of a more rapid transition to a forwarding state - it no longer relies on timer configurations - RSTP
compliant bridges are sensitive to feedback from other RSTP compliant bridge links. Ports do not need to wait for the
topology to stabilize before transitioning to a forwarding state. In order to allow this rapid transition, the protocol
introduces two new variables: the edge port and the point-to-point (P2P) port.
No No
No No
No
Yes
Edge Port
The edge port is a configurable designation used for a port that is directly connected to a segment where a loop
cannot be created. An example would be a port connected directly to a single workstation. Ports that are designated
as edge ports transition to a forwarding state immediately without going through the listening and learning states. An
edge port loses its status if it receives a BPDU packet, immediately becoming a normal spanning tree port.
P2P Port
A P2P port is also capable of rapid transition. P2P ports may be used to connect to other bridges. Under RSTP/MSTP,
all ports operating in full-duplex mode are considered to be P2P ports, unless manually overridden through
configuration.
STP/RSTP/MSTP Compatibility
MSTP or RSTP can interoperate with legacy equipment and is capable of automatically adjusting BPDU packets to
STP format when necessary. However, any segment using STP will not benefit from the rapid transition and rapid
topology change detection of MSTP or RSTP. The protocol also provides for a variable used for migration in the event
that legacy equipment on a segment is updated to use RSTP or MSTP.
The Spanning Tree Protocol (STP) operates on two levels:
1. On the switch level, the settings are globally implemented.
2. On the port level, the settings are implemented on a per user-defined group of ports basis.
91
Page 93

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
STP Bridge Global Settings
To open the following window, click L2 features > Spanning Tree > STP Bridge Global Settings:
Figure 3 - 41. STP Bridge Global Settings window
The following parameters can be set:
Parameter Description
STP State
STP Version
Forwarding BPDU
Bridge Max Age (6-40)
Use the radio buttons to enable or disable the STP Status.
Use the pull-down menu to choose the desired version of STP to be implemented on the
Switch. There are three choices:
STP - Select this parameter to set the Spanning Tree Protocol (STP) globally on the
switch.
RSTP - Select this parameter to set the Rapid Spanning Tree Protocol (RSTP) globally
on the Switch.
MSTP − Select this parameter to set the Multiple Spanning Tree Protocol (MSTP)
globally on the Switch.
This field can be Enabled or Disabled. When Enabled, it allows the forwarding of STP
BPDU packets from other network devices. The default is Enabled.
The Max Age may be set to ensure that old information does not endlessly circulate
through redundant paths in the network, preventing the effective propagation of the new
information. Set by the Root Bridge, this value will aid in determining that the Switch has
spanning tree configuration values consistent with other devices on the bridged LAN. If
the value ages out and a BPDU has still not been received from the Root Bridge, the
Switch will start sending its own BPDU to all other switches for permission to become
the Root Bridge. If it turns out that your switch has the lowest Bridge Identifier, it will
become the Root Bridge. The user may choose a time between 6 and 40 seconds. The
default value is 20.
Bridge Forward Delay
(4-30)
Tx Hold Count (1-10)
Max Hops (6-40)
Click Apply to implement changes made.
The Forward Delay can be from 4 to 30 seconds. Any port on the Switch spends this
time in the listening state while moving from the blocking state to the forwarding state.
Used to set the maximum number of Hello packets transmitted per interval. The count
can be specified from 1 to 10. The default is 6.
Used to set the number of hops between devices in a spanning tree region before the
BPDU (bridge protocol data unit) packet sent by the Switch will be discarded. Each
switch on the hop count will reduce the hop count by one until the value reaches zero.
The Switch will then discard the BPDU packet and the information held for the port will
age out. The user may set a hop count from 6 to 40. The default is 20.
92
Page 94

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
NOTE: The Hello Time cannot be longer than the Max. Age. Otherwise, a
configuration error will occur. Observe the following formulas when setting
the above parameters:
Max. Age ≤ 2 x (Forward Delay - 1 second)
Max. Age ≥ 2 x (Hello Time + 1 second)
STP Port Settings
STP can be set up on a port per port basis.
To view the following window, click L2 Features > Spanning Tree > STP Port Settings:
Figure 3 - 42. STP Port Settings window
In addition to setting Spanning Tree parameters for use on the switch level, the Switch allows for the configuration of
groups of ports, each port-group of which will have its own spanning tree, and will require some of its own
configuration settings. An STP Group will use the switch-level parameters entered above, with the addition of Port
Priority and Port Cost.
An STP Group spanning tree works in the same way as the switch-level spanning tree, but the root bridge concept is
replaced with a root port concept. A root port is a port of the group that is elected based on port priority and port cost,
to be the connection to the network for the group. Redundant links will be blocked, just as redundant links are blocked
on the switch level.
The STP on the switch level blocks redundant links between switches (and similar network devices). The port level
STP will block redundant links within an STP Group.
It is advisable to define an STP Group to correspond to a VLAN group of ports.
93
Page 95

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
The following fields can be set:
Parameter Description
From Port/To Port
External Cost (0=Auto)
Migrate
Edge
A consecutive group of ports may be configured starting with the selected port.
External Cost - This defines a metric that indicates the relative cost of forwarding packets
to the specified port list. Port cost can be set automatically or as a metric value. The
default value is 0 (auto).
0 (auto) - Setting 0 for the external cost will automatically set the speed for forwarding
packets to the specified port(s) in the list for optimal efficiency. Default port cost: 100Mbps
port = 200000. Gigabit port = 20000.
value 1-200000000 - Define a value between 1 and 200000000 to determine the external
cost. The lower the number, the greater the probability the port will be chosen to forward
packets.
Setting this parameter as Yes will set the ports to send out BPDU packets to other
bridges, requesting information on their STP setting If the Switch is configured for RSTP,
the port will be capable to migrate from 802.1D STP to 802.1w RSTP. Migration should be
set as yes on ports connected to network stations or segments that are capable of being
upgraded to 802.1w RSTP on all or some portion of the segment.
Choosing the True parameter designates the port as an edge port. Edge ports cannot
create loops, however an edge port can lose edge port status if a topology change creates
a potential for a loop. An edge port normally should not receive BPDU packets. If a BPDU
packet is received, it automatically loses edge port status. Choosing the Auto parameter
will indicate that the port will be able to automatically enable edge port status if needed.
P2P
Port STP
Restricted Role
Restricted TCN
Forward BPDU
Hello Time (1–2)
Choosing the True parameter indicates a point-to-point (P2P) shared link. P2P ports are
similar to edge ports, however they are restricted in that a P2P port must operate in fullduplex. Like edge ports, P2P ports transition to a forwarding state rapidly thus benefiting
from RSTP. A p2p value of false indicates that the port cannot have p2p status. Auto
allows the port to have p2p status whenever possible and operate as if the p2p status
were true. If the port cannot maintain this status, (for example if the port is forced to half-
duplex operation) the p2p status changes to operate as if the p2p value were False. The
default setting for this parameter is True. The default value True is equivalent to the Auto
value.
Allows STP to be Enabled or Disabled for the ports.
Toggle between True and False to set the restricted role state of the packet. The default
value is False.
Toggle between True and False to set the restricted TCN of the packet. The default value
is False.
This field can be Enabled or Disabled. When Enabled, it allows the forwarding of STP
BPDU packets from other network devices. The default is Enabled.
The Hello Time can be set from 1 to 2 seconds. This is the interval between two
transmissions of BPDU packets sent by the Root Bridge to tell all other switches that it is
indeed the Root Bridge. The default value is 2.
Click Apply to implement changes made.
94
Page 96

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
MST Configuration Identification
The following windows in the MST Configuration Identification section allow the user to configure a MSTI instance on
the Switch. These settings will uniquely identify a multiple spanning tree instance set on the Switch. The Switch
initially possesses one CIST or Common Internal Spanning Tree of which the user may modify the parameters for but
cannot change the MSTI ID for, and cannot be deleted.
To view this window, click L2 Features > Spanning Tree > MST Configuration Identification:
Figure 3 - 43. MST Configuration Identification window
The window above contains the following information:
Parameter Description
Configuration Name A previously configured name set on the Switch to uniquely identify the MSTI (Multiple
Spanning Tree Instance). If a configuration name is not set, this field will show the MAC
address to the device running MSTP. This field can be set in the STP Bridge Global Set-
tings window.
Revision Level
(0-65535)
MSTI ID (1-4) This field shows the MSTI IDs currently set on the Switch. This field will always have the
Type
VID List (1-4094)
Click Apply for changes to take affect.
This value, along with the Configuration Name will identify the MSTP region configured on
the Switch. The user may choose a value between 0 and 65535 with a default setting of 0.
CIST MSTI, which may be configured but not deleted. Clicking the hyperlinked name will
open a new window for configuring parameters associated with that particular MSTI.
This field allows the user to choose a desired method for altering the MSTI settings. The
user has two choices.
Add VID - Select this parameter to add VIDs to the MSTI ID, in conjunction with the VID List
parameter.
Remove VID - Select this parameter to remove VIDs from the MSTI ID, in conjunction with
the VID List parameter.
This field displays the VLAN IDs associated with the specific MSTI.
95
Page 97

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
STP Instance Settings
The following window displays MSTIs currently set on the Switch.
To view the following table, click L2 Features > Spanning Tree > STP Instance Settings:
Figure 3 - 44. STP Instance Settings window
The following information can be set:
Parameter Description
MSTI ID
Priority
To modify an entry, click the Edit button.
To see the STP Instance Operational Status of a previously configured setting, click View. The following window will
be displayed:
Displays the MSTI ID of the instance being modified. An entry of 0 in this field denotes the
CIST (default MSTI).
Enter the new priority in the Priority field. The user may set a priority value between 0 and
61440.
Figure 3 - 45. STP Instance Settings - View window
96
Page 98

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
MSTP Port Information
This window displays the current MSTP Port Information and can be used to update the port configuration for an MSTI
ID. If a loop occurs, the MSTP function will use the port priority to select an interface to put into the forwarding state.
Set a higher priority value for interfaces to be selected for forwarding first. In instances where the priority value is
identical, the MSTP function will implement the lowest MAC address into the forwarding state and other interfaces will
be blocked. Remember that lower priority values mean higher priorities for forwarding packets.
To view the following window, click L2 Features > Spanning Tree > MSTP Port Information:
Figure 3 - 46. MSTP Port Information window
The following parameters can be viewed or set:
Parameter Description
Port
Instance ID
Internal Path Cost
(1-200000000)
Priority
Click Apply to implement changes made.
Use the drop-down menu to select a port.
Displays the MSTI ID of the instance being configured. An entry of 0 in this field denotes the
CIST (default MSTI).
This parameter is set to represent the relative cost of forwarding packets to specified ports
when an interface is selected within a STP instance. A lower Internal cost represents a quicker
transmission.
Select a value between 0 and 240 to set the priority for the port interface. A higher priority will
designate the interface to forward packets first. A lower number denotes a higher priority.
Forwarding & Filtering
This folder contains windows for Unicast Forwarding and Multicast Forwarding.
Unicast Forwarding Settings
To view this window, click L2 Features > Forwarding & Filtering > Unicast For warding Settings:
Figure 3 - 47. Unicast Forwarding Settings window
97
Page 99

®
xStack
To add or edit an entry, define the following parameters and then click Add/Modify:
Parameter Description
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
VLAN ID (1-4094)
MAC Address
Port
VLAN Name
Click Apply to implement the changes made. The new entries will be displayed on the bottom half of the window.
The VLAN ID number of the VLAN on which the above Unicast MAC address resides.
The MAC address to which packets will be statically forwarded. This must be a unicast
MAC address.
Select the port number on which the MAC address entered above resides.
The VLAN Name associated with the subnet.
Multicast Forwarding Settings
To view this window, click L2 Features > Forwarding & Filtering > Multicast Forwarding Settings:
Figure 3 - 48. Multicast Forwarding Settings window
The following parameters can be set:
Parameter Description
VLAN ID (1-4094)
MAC Address
Port Settings
Click Apply to implement the changes made. To delete an entry in the static multicast forwarding table, click the
corresponding Delete button. To modify an entry in the static multicast forwarding table, click the corresponding Edit
button and make the desired changes at the top of the window before clicking the Apply button.
The VLAN ID of the VLAN to which the corresponding MAC address belongs.
The MAC address that will be added to the multicast forwarding table.
Allows the selection of ports that will be members of the static multicast group. The options
are:
None - No restrictions on the port dynamically joining the multicast group. When None is
chosen, the port will not be a member of the static multicast group.
Egress - The port is a static member of the multicast group.
Click All to choose either all of the ports selected as None or all of the ports selected as
Egress. Click Clear All to clear all the settings at the top of this window.
98
Page 100

®
xStack
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Multicast Filtering Mode
Users can configure the multicast filtering mode.
To view this window, click L2 Features > Forwarding & Filtering > Multicast Filtering Mode:
Figure 3 - 49. Multicast Filtering Mode window
The following parameters can be set:
Parameter Description
From Port/To Port
Filtering Mode
Click Apply to implement the changes made.
The range of ports to be configured.
This drop-down menu instructs the Switch what action to take when it receives a multicast
packet that requires forwarding to a port.
Forward Unregistered Groups – This will instruct the Switch to forward a multicast packet
whose destination is an unregistered multicast group residing within the range of ports
specified above.
Filter Unregistered Groups – This will instruct the Switch to filter any multicast packets
whose destination is an unregistered multicast group residing within the range of ports
specified above..
LLDP
The Link Layer Discovery Protocol (LLDP) allows stations attached to an IEEE 802 LAN to advertise, to other stations
attached to the same IEEE 802 LAN. The major capabilities provided by this system is that it incorporates the station,
the management address or addresses of the entity or entities that provide management of those capabilities, and the
identification of the station’s point of attachment to the IEEE 802 LAN required by those management entity or entities.
The information distributed via this protocol is stored by its recipients in a standard Management Information Base
(MIB), making it possible for the information to be accessed by a Network Management System (NMS) through a
management protocol such as the Simple Network Management Protocol (SNMP).
99
 Loading...
Loading...