Page 1
DES-3326
24-Port Fast Ethernet
Plus 2-Port Gigabit Module
Layer 3 Switch
Second Edition (July 2002)
651ES3326025
Printed In Taiwan
RECYCLABLE
User’s Guide
Page 2

Wichtige Sicherheitshinweise
1. Bitte lesen Sie sich diese Hinweise sorgfältig durch.
2. Heben Sie diese Anleitung für den spätern Gebrauch auf.
3. Vor jedem Reinigen ist das Gerät vom Stromnetz zu trennen. Vervenden Sie keine Flüssig- oder Aerosolreiniger. Am besten dient ein
angefeuchtetes Tuch zur Reinigung.
4. Um eine Beschädigung des Gerätes zu vermeiden sollten Sie nur Zubehörteile verwenden, die vom Hersteller zugelassen sind.
5. Das Gerät is vor Feuchtigkeit zu schützen.
6. Bei der Aufstellung des Gerätes ist auf sichern Stand zu achten. Ein Kippen oder Fallen könnte Verletzungen hervorrufen. Verwenden Sie nur
sichere Standorte und beachten Sie die Aufstellhinweise des Herstellers.
7. Die Belüftungsöffnungen dienen zur Luftzirkulation die das Gerät vor Überhitzung schützt. Sorgen Sie dafür, daß diese Öffnungen nicht
abgedeckt werden.
8. Beachten Sie beim Anschluß an das Stromnetz die Anschlußwerte.
9. Die Netzanschlußsteckdose muß aus Gründen der elektrischen Sicherheit einen Schutzleiterkontakt haben.
10. Verlegen Sie die Netzanschlußleitung so, daß niemand darüber fallen kann. Es sollete auch nichts auf der Leitung abgestellt werden.
11. Alle Hinweise und Warnungen die sich am Geräten befinden sind zu beachten.
12. Wird das Gerät über einen längeren Zeitraum nicht benutzt, sollten Sie es vom Stromnetz trennen. Somit wird im Falle einer Überspannung
eine Beschädigung vermieden.
13. Durch die Lüftungsöffnungen dürfen niemals Gegenstände oder Flüssigkeiten in das Gerät gelangen. Dies könnte einen Brand bzw.
Elektrischen Schlag auslösen.
14. Öffnen Sie niemals das Gerät. Das Gerät darf aus Gründen der elektrischen Sicherheit nur von authorisiertem Servicepersonal geöffnet
werden.
15. Wenn folgende Situationen auftreten ist das Gerät vom Stromnetz zu trennen und von einer qualifizierten Servicestelle zu überprüfen:
a – Netzkabel oder Netzstecker sint beschädigt.
b – Flüssigkeit ist in das Gerät eingedrungen.
c – Das Gerät war Feuchtigkeit ausgesetzt.
d – Wenn das Gerät nicht der Bedienungsanleitung ensprechend funktioniert oder Sie mit Hilfe dieser Anleitung keine Verbesserung erzielen.
e – Das Gerät ist gefallen und/oder das Gehäuse ist beschädigt.
f – Wenn das Gerät deutliche Anzeichen eines Defektes aufweist.
16. Bei Reparaturen dürfen nur Orginalersatzteile bzw. den Orginalteilen entsprechende Teile verwendet werden. Der Einsatz von ungeeigneten
Ersatzteilen kann eine weitere Beschädigung hervorrufen.
17. Wenden Sie sich mit allen Fragen die Service und Repartur betreffen an Ihren Servicepartner. Somit stellen Sie die Betriebssicherheit des
Gerätes sicher.
18. Zum Netzanschluß dieses Gerätes ist eine geprüfte Leitung zu verwenden, Für einen Nennstrom bis 6A und einem Gerätegewicht grőßer 3kg ist
eine Leitung nicht leichter als H05VV-F, 3G, 0.75mm2 einzusetzen.
ii
Page 3

WARRANTIES EXCLUSIVE
IF THE D-LINK PRODUCT DOES NOT OPERATE AS WARRANTED ABOVE, THE CUSTOMER'S SOLE REMEDY SHALL BE, AT D-LINK'S OPTION,
REPAIR OR REPLACEMENT. THE FOREGOING WARRANTIES AND REMEDIES ARE EXCLUSIVE AND ARE IN LIEU OF ALL OTHER WARRANTIES,
EXPRESSED OR IMPLIED, EITHER IN FACT OR BY OPERATION OF LAW, STATUTORY OR OTHERWISE, INCLUDING WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. D-LINK NEITHER ASSUMES NOR AUTHORIZES ANY OTHER PERSON TO
ASSUME FOR IT ANY OTHER LIABILITY IN CONNECTION WITH THE SALE, INSTALLATION MAINTENANCE OR USE OF D-LINK'S PRODUCTS
D-LINK SHALL NOT BE LIABLE UNDER THIS WARRANTY IF ITS TESTING AND EXAMINATION DISCLOSE THAT THE ALLEGED DEFECT IN THE
PRODUCT DOES NOT EXIST OR WAS CAUSED BY THE CUSTOMER'S OR ANY THIRD PERSON'S MISUSE, NEGLECT, IMPROPER INSTALLATION
OR TESTING, UNAUTHORIZED ATTEMPTS TO REPAIR, OR ANY OTHER CAUSE BEYOND THE RANGE OF THE INTENDED USE, OR BY
ACCIDENT, FIRE, LIGHTNING OR OTHER HAZARD.
LIMITATION OF LIABILITY
IN NO EVENT WILL D-LINK BE LIABLE FOR ANY DAMAGES, INCLUDING LOSS OF DATA, LOSS OF PROFITS, COST OF COVER OR OTHER
INCIDENTAL, CONSEQUENTIAL OR INDIRECT DAMAGES ARISING OUT THE INSTALLATION, MAINTENANCE, USE, PERFORMANCE, FAILURE
OR INTERRUPTION OF A D- LINK PRODUCT, HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY. THIS LIMITATION WILL APPLY EVEN IF
D-LINK HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
IF YOU PURCHASED A D-LINK PRODUCT IN THE UNITED STATES, SOME STATES DO NOT ALLOW THE LIMITATION OR EXCLUSION OF
LIABILITY FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES, SO THE ABOVE LIMITATION MAY NOT APPLY TO YOU.
Limited Warranty
Hardware:
D-Link warrants each of its hardware products to be free from defects in workmanship and materials under normal use and service for a period
commencing on the date of purchase from D-Link or its Authorized Reseller and extending for the length of time stipulated by the Authorized
Reseller or D-Link Branch Office nearest to the place of purchase.
This Warranty applies on the condition that the product Registration Card is filled out and returned to a D-Link office within ninety (90) days of
purchase. A list of D-Link offices is provided at the back of this manual, together with a copy of the Registration Card.
If the product proves defective within the applicable warranty period, D-Link will provide repair or replacement of the product. D-Link shall have
the sole discretion whether to repair or replace, and replacement product may be new or reconditioned. Replacement product shall be of equivalent
or better specifications, relative to the defective product, but need not be identical. Any product or part repaired by D-Link pursuant to this
warranty shall have a warranty period of not less than 90 days, from date of such repair, irrespective of any earlier expiration of original warranty
period. When D-Link provides replacement, then the defective product becomes the property of D-Link.
Warranty service may be obtained by contacting a D-Link office within the applicable warranty period, and requesting a Return Material
Authorization (RMA) number. If a Registration Card for the product in question has not been returned to D-Link, then a proof of purchase (such as
a copy of the dated purchase invoice) must be provided. If Purchaser's circumstances require special handling of warranty correction, then at the
time of requesting RMA number, Purchaser may also propose special procedure as may be suitable to the case.
After an RMA number is issued, the defective product must be packaged securely in the original or other suitable shipping package to ensure that it
will not be damaged in transit, and the RMA number must be prominently marked on the outside of the package. The package must be mailed or
otherwise shipped to D-Link with all costs of mailing/shipping/insurance prepaid. D-Link shall never be responsible for any software, firmware,
information, or memory data of Purchaser contained in, stored on, or integrated with any product returned to D-Link pursuant to this warranty.
Any package returned to D-Link without an RMA number will be rejected and shipped back to Purchaser at Purchaser's expense, and D-Link
reserves the right in such a case to levy a reasonable handling charge in addition mailing or shipping costs.
Software:
Warranty service for software products may be obtained by contacting a D-Link office within the applicable warranty period. A list of D-Link offices
is provided at the back of this manual, together with a copy of the Registration Card. If a Registration Card for the product in question has not been
returned to a D-Link office, then a proof of purchase (such as a copy of the dated purchase invoice) must be provided when requesting warranty
service. The term "purchase" in this software warranty refers to the purchase transaction and resulting license to use such software.
D-Link warrants that its software products will perform in substantial conformance with the applicable product documentation provided by D-Link
with such software product, for a period of ninety (90) days from the date of purchase from D-Link or its Authorized Reseller. D-Link warrants the
magnetic media, on which D-Link provides its software product, against failure during the same warranty period. This warranty applies to
purchased software, and to replacement software provided by D-Link pursuant to this warranty, but shall not apply to any update or replacement
which may be provided for download via the Internet, or to any update which may otherwise be provided free of charge.
D-Link's sole obligation under this software warranty shall be to replace any defective software product with product which substantially conforms
to D-Link's applicable product documentation. Purchaser assumes responsibility for the selection of appropriate application and system/platform
software and associated reference materials. D-Link makes no warranty that its software products will work in combination with any hardware, or
any application or system/platform software product provided by any third party, excepting only such products as are expressly represented, in
D-Link's applicable product documentation as being compatible. D-Link's obligation under this warranty shall be a reasonable effort to provide
compatibility, but D-Link shall have no obligation to provide compatibility when there is fault in the third-party hardware or software. D-Link
makes no warranty that operation of its software products will be uninterrupted or absolutely error-free, and no warranty that all defects in the
software product, within or without the scope of D-Link's applicable product documentation, will be corrected.
Page 4

D-Link Offices for Registration and Warranty Service
The product's Registration Card, provided at the back of this manual, must be sent to a D-Link office. To obtain an RMA number for warranty
service as to a hardware product, or to obtain warranty service as to a software product, contact the D-Link office nearest you. An
address/telephone/fax/e-mail/Web site list of D-Link offices is provided in the back of this manual.
Trademarks
Copyright 2002 D-Link Corporation.
Contents subject to change without prior notice.
D-Link is a registered trademark of D-Link Corporation/D-Link Systems, Inc. All other trademarks belong to their
respective proprietors.
Copyright Statement
No part of this publication may be reproduced in any form or by any means or used to make any derivative such as
translation, transformation, or adaptation without permission from D-Link Corporation/D-Link Systems Inc., as
stipulated by the United States Copyright Act of 1976.
iv
Page 5

FCC Warning
This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to Part
15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when
the equipment is operated in a commercial environment. This equipment generates, uses, and can radiate radio
frequency energy and, if not installed and used in accordance with this user’s guide, may cause harmful
interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful
interference in which case the user will be required to correct the interference at his own expense.
CE Mark Warning
This is a Class A product. In a domestic environment, this product may cause radio interference in which case the
user may be required to take adequate measures.
VCCI Warning
BSMI Warning
Page 6

Page 7

Table of Contents
Introduction .......................................................................................................................................10
Layer 3 Switching ............................................................................................................................10
The Functions of a Layer 3 Switch.................................................................................................11
Features ..........................................................................................................................................11
Ports .............................................................................................................................................11
Performance Features......................................................................................................................11
Layer 2 Features ...........................................................................................................................11
Layer 3 Switch Features................................................................................................................12
Traffic Classification and Prioritization ..........................................................................................13
Management .................................................................................................................................13
Optional Redundant Power Supply................................................................................................14
Fast Ethernet Technology ................................................................................................................14
Gigabit Ethernet Technology............................................................................................................14
Unpacking and Setup.........................................................................................................................15
Unpacking .......................................................................................................................................15
Installation ......................................................................................................................................15
Desktop or Shelf Installation .........................................................................................................15
Rack Installation...........................................................................................................................16
Power on..........................................................................................................................................17
Power Failure ................................................................................................................................17
Identifying External Components .......................................................................................................18
Front Panel......................................................................................................................................18
Rear Panel .......................................................................................................................................18
Side Panels ......................................................................................................................................19
Optional Plug-in Modules ................................................................................................................19
1000BASE-T Module.....................................................................................................................19
1000BASE-SX Fiber Module .........................................................................................................20
1000BASE-LX Fiber Module..........................................................................................................20
GBIC Two-Port Module..................................................................................................................21
LED Indicators ................................................................................................................................21
Connecting The Switch.......................................................................................................................22
Switch to End Node .........................................................................................................................22
Switch to Hub or Switch ..................................................................................................................22
10BASE-T Device ..........................................................................................................................23
100BASE-TX Device......................................................................................................................23
Switch Management and Operating Concepts ....................................................................................24
Local Console Management .............................................................................................................24
Diagnostic (console) port (RS-232 DCE).........................................................................................24
IP Addresses and SNMP Community Names ....................................................................................25
Traps...............................................................................................................................................26
SNMP ..............................................................................................................................................27
MIBs................................................................................................................................................28
Packet Forwarding ...........................................................................................................................28
Filtering...........................................................................................................................................29
Spanning Tree .................................................................................................................................30
Link Aggregation..............................................................................................................................35
VLANs .............................................................................................................................................37
IP Addresses ....................................................................................................................................41
vii
Page 8

Internet Protocols ............................................................................................................................46
Packet Headers................................................................................................................................50
The Domain Name System ...............................................................................................................54
DHCP Servers ..................................................................................................................................55
IP Routing .......................................................................................................................................55
ARP .................................................................................................................................................57
Multicasting ....................................................................................................................................57
Multicast Routing Protocols .............................................................................................................62
Routing Protocols ............................................................................................................................62
Configuring the Switch Using the Console Interface ...........................................................................87
Saving Changes..................................................................................................................................93
Advanced Setup.............................................................................................................................112
Layer 3 IP Networking....................................................................................................................121
Multicasting ..................................................................................................................................133
Port Mirroring................................................................................................................................142
Priority ..........................................................................................................................................144
Filtering.........................................................................................................................................146
Forwarding ....................................................................................................................................148
Spanning Tree ...............................................................................................................................151
Link Aggregation............................................................................................................................154
Spanning Tree ...............................................................................................................................156
Utilities..........................................................................................................................................159
Network Monitoring .......................................................................................................................167
Load Factory Defaults....................................................................................................................182
Web-Based Network Management ....................................................................................................185
Introduction ..................................................................................................................................185
Before You Start ............................................................................................................................185
General Deployment Strategy......................................................................................................185
VLAN Layout ...............................................................................................................................186
Assigning IP Network Addresses and Subnet Masks to VLANs.....................................................186
Defining Static Routes.................................................................................................................187
Getting Started ..............................................................................................................................187
Management..................................................................................................................................187
Configuring the Switch ..................................................................................................................187
User Accounts Management........................................................................................................187
Saving Changes .............................................................................................................................189
Reboot and Load Factory Defaults .................................................................................................189
USING WEB-BASED MANAGEMENT .............................................................................................190
CONFIGURING AND MONITORING................................................................................................193
Advanced Setup.............................................................................................................................208
Layer 3 IP Networking....................................................................................................................215
Multicasting ..................................................................................................................................223
Port Mirroring................................................................................................................................231
Priority ..........................................................................................................................................233
Filtering.........................................................................................................................................234
Spanning Tree ...............................................................................................................................238
Link Aggregation............................................................................................................................241
Utilities..........................................................................................................................................242
Network Monitoring .......................................................................................................................247
Technical Specifications ...................................................................................................................262
Sample Configuration File ................................................................................................................264
viii
Page 9

Runtime Switching Software Default Settings...................................................................................266
Understanding and Troubleshooting the Spanning Tree Protocol......................................................267
Blocking State.............................................................................................................................267
Listening State ............................................................................................................................268
Learning State.............................................................................................................................269
Forwarding State.........................................................................................................................270
Disabled State.............................................................................................................................271
Troubleshooting STP......................................................................................................................272
Spanning Tree Protocol Failure ...................................................................................................272
Full/Half Duplex Mismatch.........................................................................................................273
Unidirectional Link .....................................................................................................................274
Packet Corruption .......................................................................................................................275
Resource Errors ..........................................................................................................................275
Identifying a Data Loop ...............................................................................................................275
Avoiding Trouble .........................................................................................................................275
Brief Review of Bitwise Logical Operations........................................................................................279
Index................................................................................................................................................280
ix
Page 10

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
1
INTRODUCTION
This section describes the Layer 3 functionality and Layer 2 and Layer 3 features of the DES-3326.
Some background information about Ethernet/Fast Ethernet, Gigabit Ethernet, and switching
technology is presented. This is intended for readers who may not be familiar with the concepts of
layered switching and routing but is not intended to be a complete or in-depth discussion.
Layer 3 Switching
Layer 3 switching is the integration of two proven technologies: switching and routing. In fact, Layer 3
switches are running the same routing routines and protocols as traditional routers. The main
difference between traditional routing and Layer 3 switching is the addition of a group of Layer 2
switching domains and the execution of routing routines for most packets via an ASIC – in hardware
instead of software.
Where a traditional router would have one, or at best a few, Fast Ethernet ports, the DES-3326 Layer 3
switch has 24 Fast Ethernet ports and optionally, 2 Gigabit Ethernet ports. Where a traditional router
would have one or two high-speed serial WAN connections, the DES-3326 relies upon a Fast Ethernet
port to connect to a separate device, which in turn, connects the network to a WAN or the Internet.
The DES-3326 can be thought of as 24 Fast Ethernet Layer 2 switching domains with a wire-speed
router between each domain. It can be deployed in a network between a traditional router and the
intranetwork. The traditional router and its associated WAN interface would then handle routing
between the intranetwork and the WAN (the Internet, for example) while the Layer 3 switch would
handle routing within the LAN (between the Fast Ethernet Layer 2 domains). Any installed Layer 2
switches, and indeed the entire subnetting scheme, would remain in place.
The DES-3326 can also replace key traditional routers for data centers and server farms, routing
between these locations and the rest of the network, and providing 24 ports of Layer 2 switching
performance combined with wire-speed routing.
Backbone routers can also be replaced with DES-3326 and a series of DES-3326 could be linked via
the optional Gigabit Ethernet ports. Routers that service WAN connections would remain in place, but
would now be removed from the backbone and connected to the DES-3326 via an Ethernet/Fast
Ethernet port. The backbone itself could be migrated to Gigabit Ethernet, or faster technologies as they
become available.
The DES-3326 accomplishes two objectives. First as a tool to provide high-performance access to
enterprise data servers and infrastructure, and second, to enhance the performance of network
equipment already installed. Many network segments display poor performance, but the Ethernet wire
is only carrying a fraction of its total traffic capacity. The problem is not the network, but the ability of
the connected devices utilize the full capacity of the network. The DES-3326 can eliminate network
bottlenecks to high-traffic areas, and improve the utilization of the network’s installed bandwidth.
10
Page 11
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
The Functions of a Layer 3 Switch
Traditional routers, once the core components of large networks, became an obstacle to the migration
toward next-generation networks. Attempts to make software-based routers forward packets more
quickly were inadequate.
A layer 3 switch does everything to a packet that a traditional router does:
• Determines forwarding path based on Layer 3 information
• Validates the integrity of the Layer 3 header via checksum
• Verifies packet expiration and updates accordingly
• Processes and responds to any optional information
• Updates forwarding statistics in the Management Information Base
A Layer 3 switch can be placed anywhere within a network core or backbone, easily and cost-effectively
replacing the traditional collapsed backbone router. The DES-3326 Layer 3 switch communicates with
a WAN router using a standard Ethernet/Fast Ethernet port. Multiple DES-3326 switches can be
linked via the optional, 2-port Gigabit Ethernet module.
Features
The DES-3326 Switch was designed for easy installation and high performance in an environment
where traffic on the network and the number of users increase continuously.
Switch features include:
Ports
• 24 high-performance NWay ports all operating at 10/100 Mbps for connecting to end stations,
servers and hubs (23 MDI-X 10/100 Ethernet UTP ports and one MDI-II/MDI-X port. The MDIII/MDI-X port can be switched between the two modes from the front panel.)
• All ports can auto-negotiate (NWay) between 10Mbps/ 100Mbps, half-duplex or full duplex and
flow control for half-duplex ports.
• One front panel slide-in module interface for a 2-port 1000BASE-SX, 1000BASE-LX, 1000BASET, or GBIC Gigabit Ethernet module.
• RS-232 DCE Diagnostic port (console port) for setting up and managing the Switch via a
connection to a console terminal or PC using a terminal emulation program.
Performance Features
Layer 2 Features
• 8.8 Gbps switching fabric capacity
11
Page 12

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
• Store and forward switching scheme.
• Full and half-duplex for both 10Mbps and 100Mbps connections. The front-port Gigabit Ethernet
module operates at full duplex only. Full duplex allows the switch port to simultaneously
transmit and receive data, and only works with connections to full-duplex capable end stations
and switches. Connections to hubs must take place at half-duplex.
• Supports IEEE 802.3x flow control for full-duplex mode ports.
• Supports Back-pressure flow control for half-duplex mode ports.
• Auto-polarity detection and correction of incorrect polarity on the transmit and receive twisted-
pair at each port.
• IEEE 802.3z compliant for all Gigabit ports (optional module).
• IEEE 802.3x compliant Flow Control support for all Gigabit ports (optional module).
• IEEE 802.3ab compliant for 1000BASE-T (Copper) Gigabit ports (optional module).
• Data forwarding rate 14,880 pps per port at 100% of wire-speed for 10Mbps speed.
• Data forwarding rate 148,800 pps per port at 100% of wire-speed for 100Mbps speed.
• Data filtering rate eliminates all error packets, runts, etc. at 14,880 pps per port at 100% of wire-
speed for 10Mbps speed.
• Data filtering rate eliminates all error packets, runts, etc. at 148,800 pps per port at 100% of
wire-speed for 100Mbps speed.
• 8K active MAC address entry table per device with automatic learning and aging (10 to 9999
seconds).
• 16 MB packet buffer per device.
• Broadcast and Multicast storm filtering.
• Supports Port Mirroring.
• Supports Port Trunking – up to six trunk groups (each consisting of up to eight ports) may be set
up.
• 802.1D Spanning Tree support.
• 802.1Q Tagged VLAN support – up to 63 User-defined VLANs per device (one VLAN is reserved
for internal use).
• GVRP – (GARP VLAN Registration Protocol) support for dynamic VLAN registration.
• 802.1p Priority support with 4 priority queues.
• IGMP Snooping support.
• Layer 2 Multicast support – GMRP (GARP Multicast Registration Protocol).
Layer 3 Switch Features
• Wire speed IP forwarding.
12
Page 13

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
• Hardware-based Layer 3 IP switching.
• IP packet forwarding rate of 6.6 Mpps.
• 2K active IP address entry table per device.
• Supports RIP – (Routing Information Protocol) version I and II.
• Supports OSPF − (Open Shortest Path First)
• Supports MD5 and Password OSPF Packet Authentication
• Supports IP version 4.
• IGMP version 1 and 2 support (RFC 1112 and RFC 2236).
• Supports PIM Dense Mode.
• Supports DVMRP.
• Supports IP multi-netting.
• Supports IP packet de-fragmentation.
• Supports Path MTU discovery.
• Supports 802.1D frame support.
Traffic Classification and Prioritization
• Based on 802.1p priority bits
• 4 priority queues
Management
• RS-232 console port for out-of-band network management via a console terminal or PC.
• Spanning Tree Algorithm Protocol for creation of alternative backup paths and prevention of
network loops.
• SNMP v.1 Agent.
• Fully configurable either in-band or out-of-band control via SNMP based software.
• Flash memory for software upgrades. This can be done in-band via TFTP or out-of-band via the
console.
• Built-in SNMP management:
Bridge MIB (RFC 1493)
MIB-II (RFC 1213)
Mini-RMON MIB (RFC 1757) – 4 groups
CIDR MIB (RFC 2096), except IP Forwarding Table.
13
Page 14
802.1p MIB (RFC 2674).
RIP MIB v2 (RFC 1724).
• Supports Web-based management.
• TFTP support.
• BOOTP support.
• BOOTP Relay Agent.
• IP filtering on the management interface.
• DHCP Client support.
• DHCP Relay Agent.
• DNS Relay Agent.
• Password enabled.
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Optional Redundant Power Supply
The DES-3326 24+2 Fast Ethernet Layer 3 Switch supports the optional DPS-1000 (Redundant Power
Supply) to provide automatic power supply monitoring and switchover to a redundant power supply
(located in the chassis of the DPS-1000) in case of a failure in the DES-3326’s internal power supply.
Fast Ethernet Technology
100Mbps Fast Ethernet (or 100BASE-T) is a standard specified by the IEEE 802.3 LAN committee. It is
an extension of the 10Mbps Ethernet standard with the ability to transmit and receive data at
100Mbps, while maintaining the Carrier Sense Multiple Access with Collision Detection (CSMA/CD)
Ethernet protocol.
Gigabit Ethernet Technology
Gigabit Ethernet is an extension of IEEE 802.3 Ethernet utilizing the same packet structure, format,
and support for CSMA/CD protocol, full duplex, flow control, and management objects, but with a
tenfold increase in theoretical throughput over 100Mbps Fast Ethernet and a one hundred-fold
increase over 10Mbps Ethernet. Since it is compatible with all 10Mbps and 100Mbps Ethernet
environments, Gigabit Ethernet provides a straightforward upgrade without wasting a company’s
existing investment in hardware, software, and trained personnel.
Gigabit Ethernet enables fast optical fiber connections and Unshielded Twisted Pair connections to
support video conferencing, complex imaging, and similar data-intensive applications. Likewise, since
data transfers occur 10 times faster than Fast Ethernet, servers outfitted with Gigabit Ethernet NIC’s
are able to perform 10 times the number of operations in the same amount of time.
14
Page 15

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
2
UNPACKING AND SETUP
This chapter provides unpacking and setup information for the Switch.
Unpacking
Open the shipping carton of the Switch and carefully unpack its contents. The carton should contain
the following items:
♦ One DES-3326 24-port Fast Ethernet Layer 3 Switch
♦ Mounting kit: 2 mounting brackets and screws
♦ Four rubber feet with adhesive backing
♦ One AC power cord
♦ This User’s Guide with Registration Card
If any item is found missing or damaged, please contact your local D-Link reseller for replacement.
Installation
Use the following guidelines when choosing a place to install the Switch:
♦ The surface must support at least 3 kg.
♦ The power outlet should be within 1.82 meters (6 feet) of the device.
♦ Visually inspect the power cord and see that it is secured to the AC power connector.
♦ Make sure that there is proper heat dissipation from and adequate ventilation around the switch.
Do not place heavy objects on the switch.
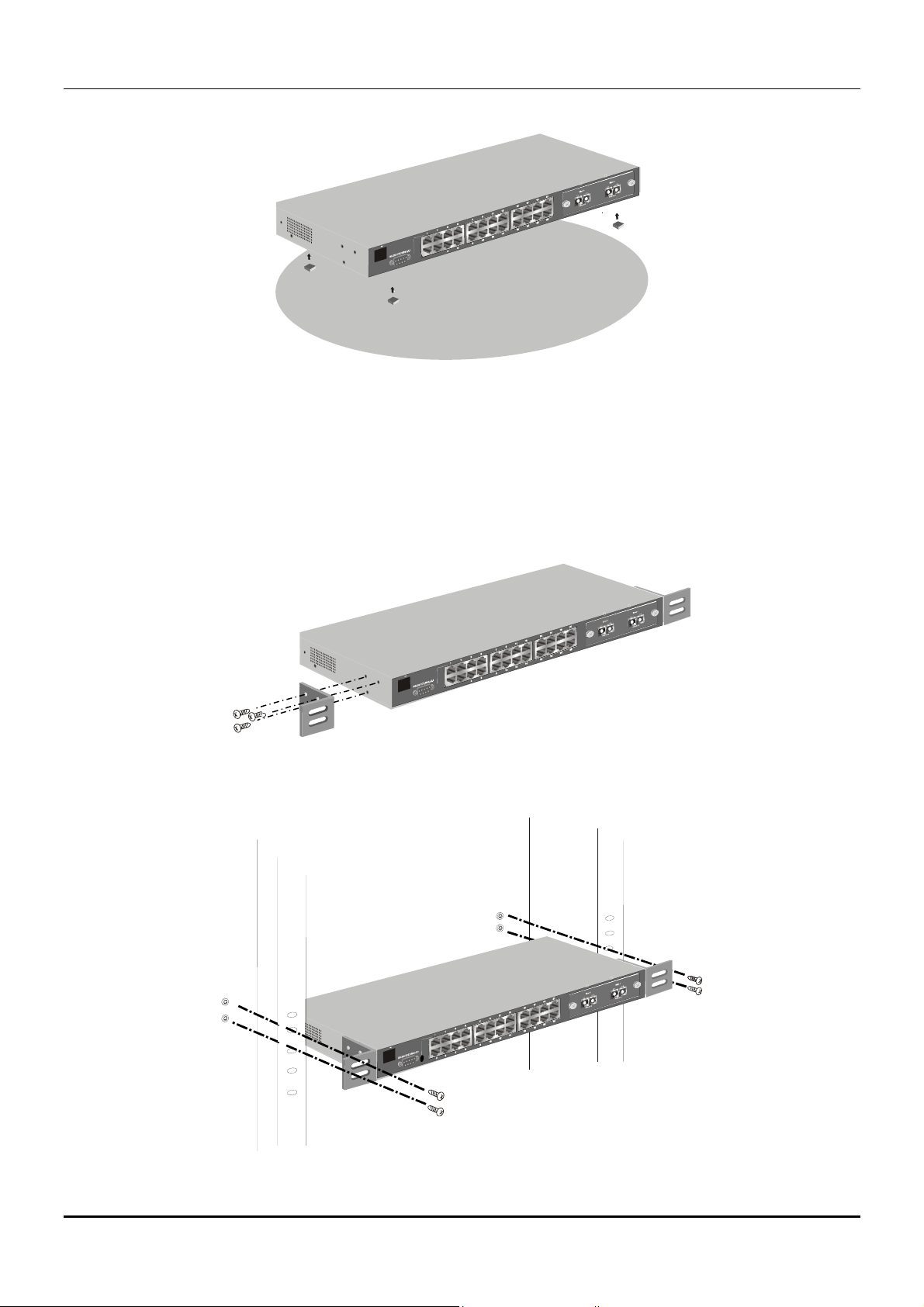
Desktop or Shelf Installation
When installing the Switch on a desktop or shelf, the rubber feet included with the device should first
be attached. Attach these cushioning feet on the bottom at each corner of the device. Allow adequate
space for ventilation between the device and the objects around it.
15
Page 16
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 2-1. Installing rubber feet for desktop installation
Rack Installation
The DES-3326 can be mounted in an EIA standard-sized, 19-inch rack, which can be placed in a wiring
closet with other equipment. To install, attach the mounting brackets on the switch’s side panels (one
on each side) and secure them with the screws provided.
Figure 2- 2A. Attaching the mounting brackets to the switch
Then, use the screws provided with the equipment rack to mount the switch on the rack.
Figure 2-2B. Installing the switch on an equipment rack
16
Page 17

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Power on
The DES-3326 switch can be used with AC power supply 100-240 VAC, 50 - 60 Hz. The power switch is
located at the rear of the unit adjacent to the AC power connector and the system fan. The switch’s
power supply will adjust to the local power source automatically and may be turned on without having
any or all LAN segment cables connected.
After the power switch is turned on, the LED indicators should respond as follows:
♦ All LED indicators will momentarily blink. This blinking of the LED indicators represents a reset
of the system.
♦ The power LED indicator will blink while the Switch loads onboard software and performs a self-
test. After approximately 20 seconds, the LED will light again to indicate the switch is in a ready
state.
♦ The console LED indicator will remain ON if there is a connection at the RS-232 port, otherwise
this LED indicator is OFF.
♦ The 100M LED indicator may remain ON or OFF depending on the transmission speed.
Power Failure
As a precaution in the event of a power failure, unplug the switch. When power is resumed, plug the
switch back in.
17
Page 18
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
3
IDENTIFYING EXTERNAL COMPONENTS
This chapter describes the front panel, rear panel, optional plug-in modules, and LED indicators of the
DES-3326.
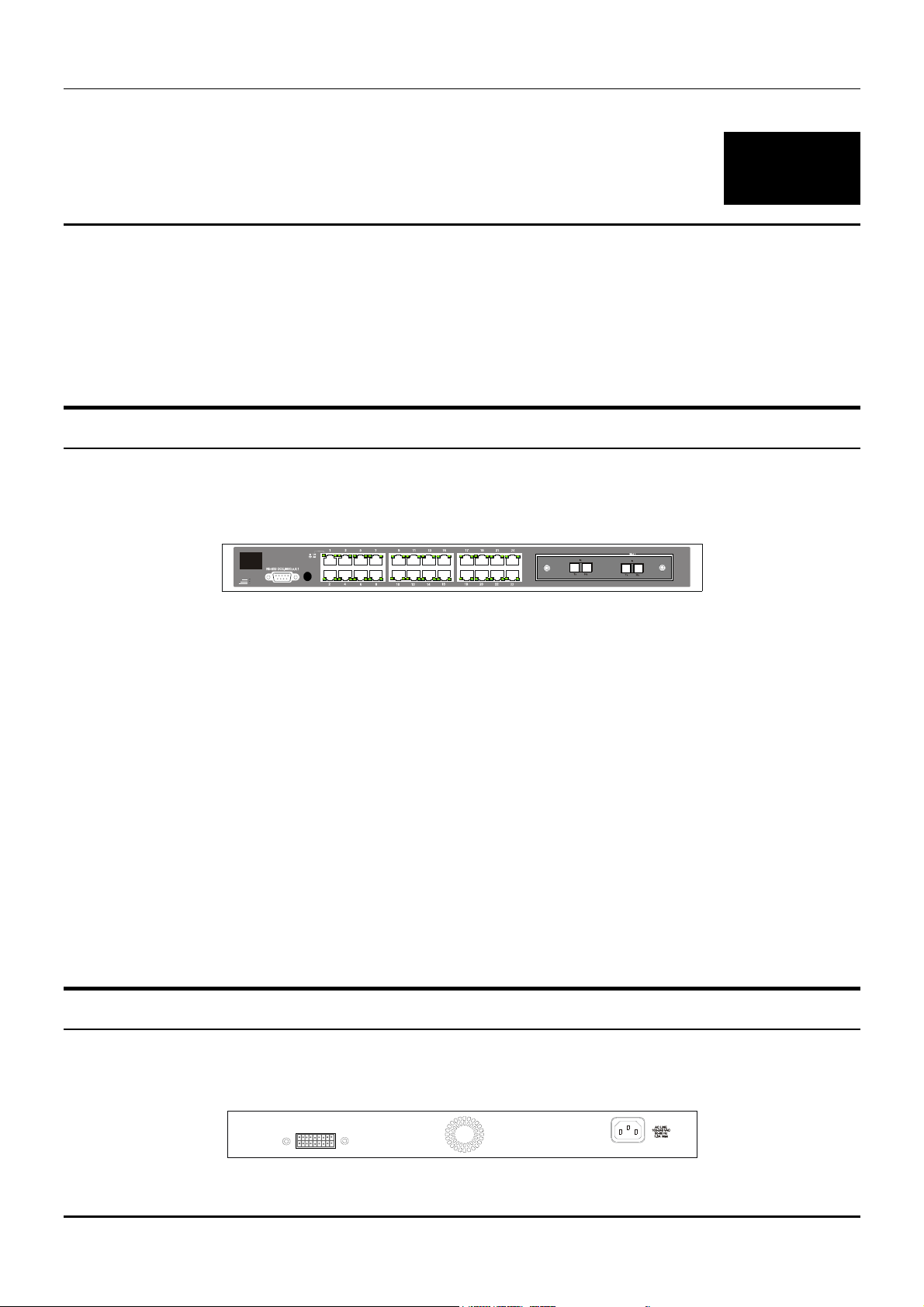
Front Panel
The front panel of the Switch consists of LED indicators, an RS-232 communication port, a slide-in
module slot, one switched MDI-X/MDI-II uplink port, and 23 (10/100 Mbps) Ethernet/Fast Ethernet
ports.
Figure 3-1. Front panel view of the Switch
♦ Comprehensive LED indicators display the status of the switch and the network (see the LED
Indicators section below).
♦ An RS-232 DCE console port for setting up and managing the switch via a connection to a
console terminal or PC using a terminal emulation program.
♦ A front-panel slide-in module slot for Gigabit Ethernet ports can accommodate a 2-port
1000BASE-T Gigabit Ethernet module, a 2-port 1000BASE-SX Gigabit Ethernet module, a 2-port
1000BASE-LX Gigabit Ethernet module, or a 2-port GBIC-based Gigabit Ethernet module.
♦ One switched MDI-X/MDI-II Uplink port that can be used to connect a straight-through cable or a
crossed cable to a normal (non-Uplink) port on a switch or hub. This port is identical to the other
23 ports except for the ability to use a crossed or a straight-through cable.
♦ Twenty-three high-performance, NWay Ethernet ports all of which operate at 10/100 Mbps for
connections to end stations, servers and hubs. All ports can auto-negotiate between 10Mbps or
100Mbps, full or half duplex, and flow control.
Rear Panel
The rear panel of the switch consists of a slot for the optional DPS-1000 (Redundant Power Supply) and
an AC power connector.
Figure 3-2. Rear panel view of the Switch
18
Page 19
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
♦ The AC power connector is a standard three-pronged connector that supports the power cord.
Plug-in the female connector of the provided power cord into this socket, and the male side of the
cord into a power outlet. Supported input voltages range from 100 ~ 240 VAC at 50 ~ 60 Hz.
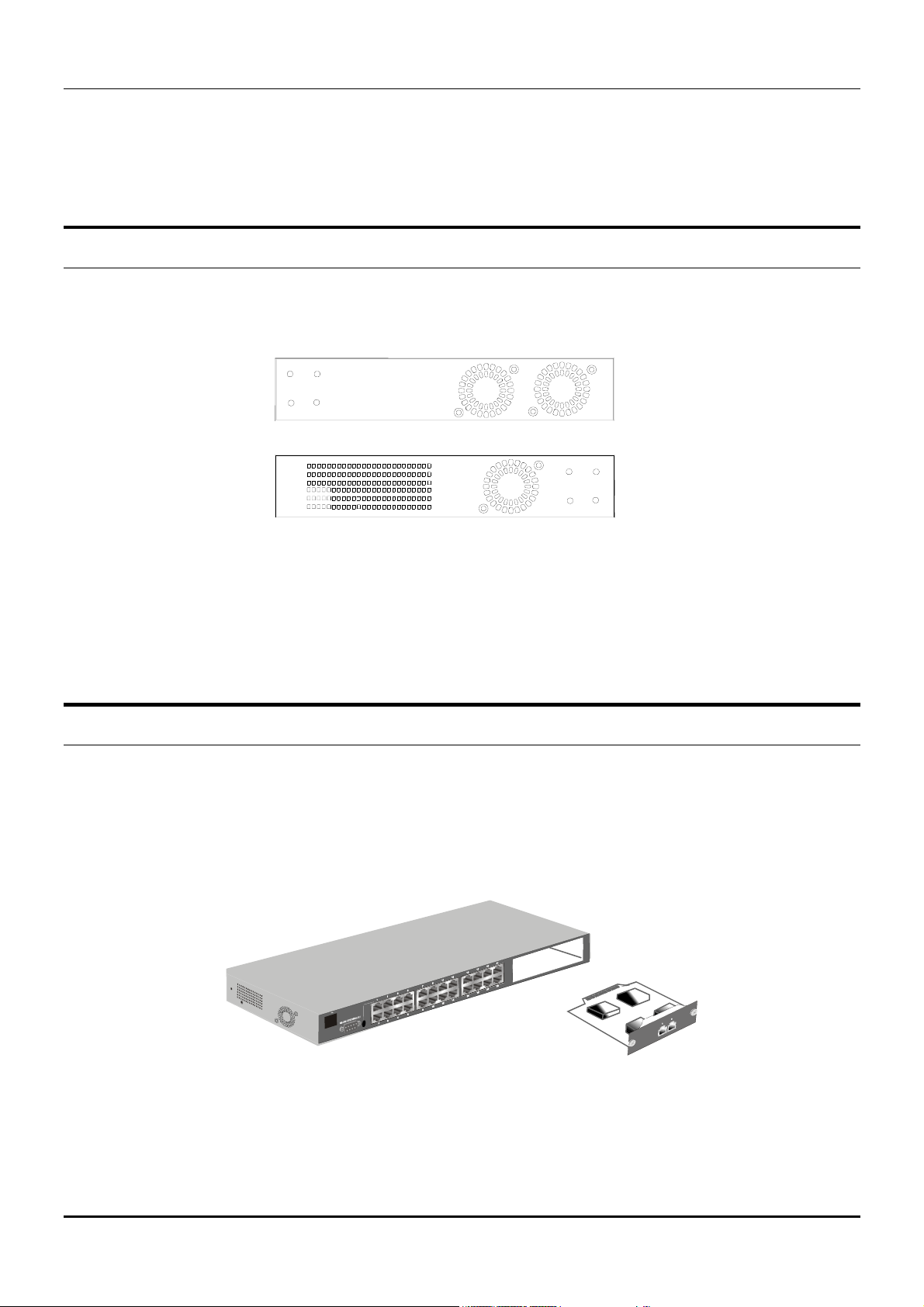
Side Panels
The right side panel of the Switch contains two system fans (see the top part of the diagram below). The
left side panel contains heat vents.
Figure 3-4. Side panel views of the Switch
♦ The system fans are used to dissipate heat. The sides of the system also provide heat vents to
serve the same purpose. Do not block these openings, and leave at least 6 inches of space at the
rear and sides of the switch for proper ventilation. Be reminded that without proper heat
dissipation and air circulation, system components might overheat, which could lead to system
failure.
Optional Plug-in Modules
The DES 3326 24-port Fast Ethernet Layer 3 Switch is able to accommodate a range of optional plug-in
modules in order to increase functionality and performance. These modules must be purchased
separately.
1000BASE-T Module
Figure 3-5. 1000BASE-TX two-port module
♦ Front-panel module.
♦ Connects to 1000BASE-T devices.
♦ Supports Category 5e UTP or STP cable connections of up to 100 meters.
19
Page 20
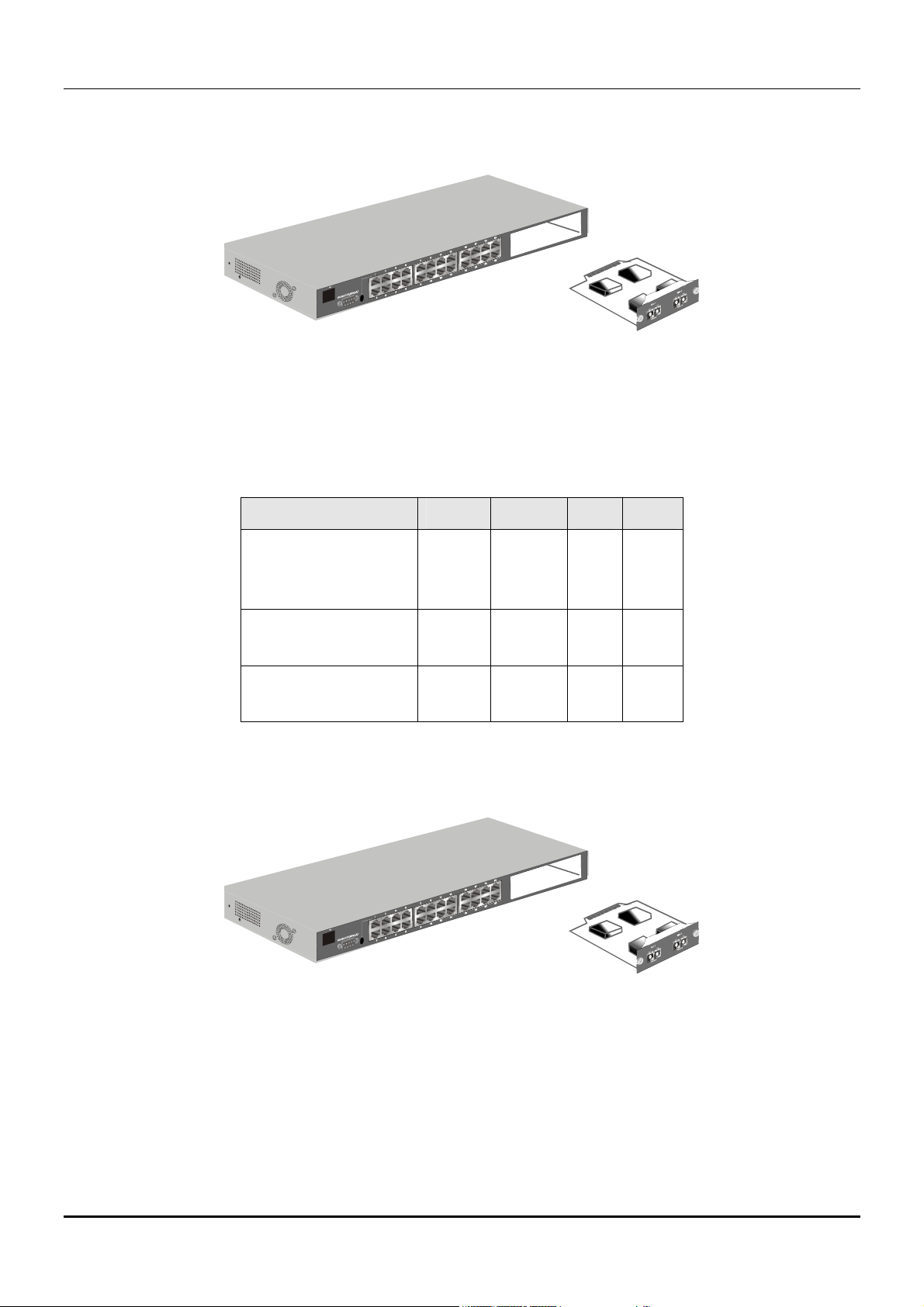
1000BASE-SX Fiber Module
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 3-6. 1000BASE-SX two-port module
♦ Front-panel module.
♦ Connects to 1000BASE-SX devices at full duplex.
♦ Allows connections using multi-mode fiber optic cable in the following configurations:
Modal bandwidth
(min. overfilled launch)
Unit: MHz*km
Operating distance
Unit: meters
Channel insertion loss
Unit: dB
62.5µm 62.5µm 50µm 50µm
160 200 400 500
220 275 500 550
2.33 2.53 3.25 3.43
1000BASE-LX Fiber Module
Figure 3-7. 1000BASE-LX two-port module
♦ Front-panel module.
♦ Connects to 1000BASE-LX devices at full duplex.
♦ Supports multi-mode fiber-optic cable connections of up to 550 meters or 5 km single-mode fiber-
optic cable connections.
20
Page 21

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
GBIC Two-Port Module
Figure 3-8. GBIC two-port module
♦ Front-panel module.
♦ Connects to GBIC devices at full duplex only.
♦ Allows multi-mode fiber optic connections of up to 550 m (SX and LX) and single-mode fiber optic
connections of up to 5 km (LX only). GBIC modules are available in –SX and –LX fiber optic media.
LED Indicators
The LED indicators of the Switch include Power, Console, and Link/Act. The following shows the LED
indicators for the Switch along with an explanation of each indicator.
Figure 3-9. The LED indicators
♦ Power This indicator on the front panel should be lit during the Power-On Self Test (POST). It will
light green approximately 2 seconds after the switch is powered on to indicate the ready state of
the device.
♦ Console This indicator is lit green when the switch is being managed via out-of-band/local
console management through the RS-232 console port using a straight-through serial cable.
♦ Link/Act These indicators are located to the left and right of each port. They are lit when there is
a secure connection (or link) to a device at any of the ports. The LEDs blink whenever there is
reception or transmission (i.e. Activity--Act) of data occurring at a port.
21
Page 22
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
4
CONNECTING THE SWITCH
This chapter describes how to connect the DES 3326 to your Fast Ethernet network.
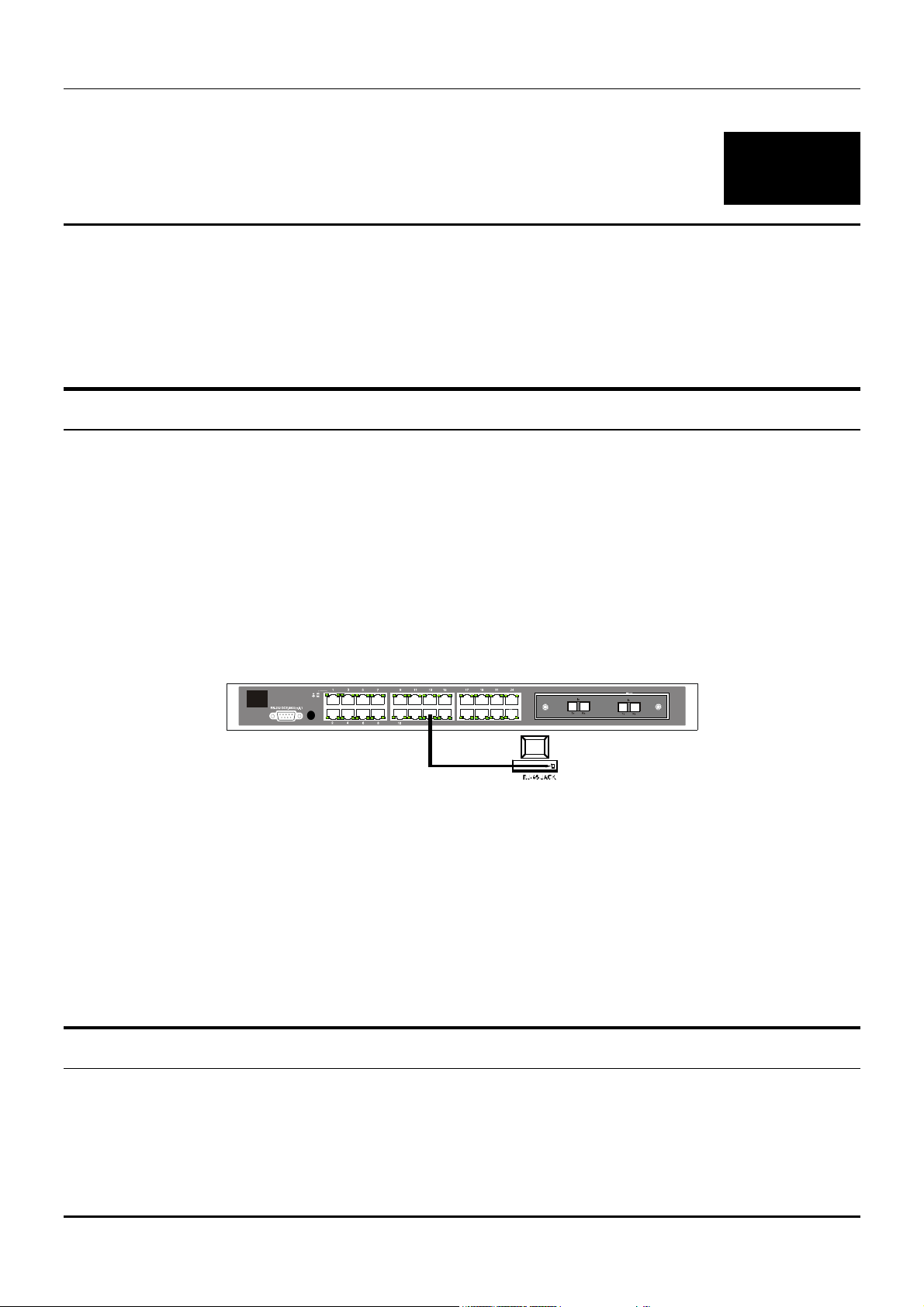
Switch to End Node
End nodes include PCs outfitted with a 10, 100 or 10/100 Mbps RJ-45 Ethernet/Fast Ethernet
Network Interface Card (NIC) and most routers. The RJ-45 UTP ports on NICs and most routers are
MDI-II. When using a normal straight-through cable, an MDI-II port must connect to an MDI-X port.
An end node can be connected to the Switch via a two-pair Category 3, 4, 5 UTP/STP straight cable (be
sure to use Category 5e UTP or STP cabling for 100 Mbps Fast Ethernet connections). The end node
should be connected to any of the twenty-three ports (2x - 24x) of the DES-3326 or to either of the two
100BASE-TX ports on the front-panel module that came preinstalled on the switch. Port 1x can be
used as an uplink port to connect to another switch using either a crossed or a straight-through cable.
This port is switched between MDI-X and MDI-II to accommodate either type of cable.
Figure 4-1. Switch connected to an End Node
The LED indicators for the port the end node is connected to are lit according to the capabilities of the
NIC. If LED indicators are not illuminated after making a proper connection, check the PC’s LAN card,
the cable, switch conditions, and connections.
The following LED indicator states are possible for an end node to switch connection:
1. The 100 LED indicator comes ON for a 100 Mbps and stays OFF for 10 Mbps.
2. The Link/Act LED indicator lights up upon hooking up a PC that is powered on.
Switch to Hub or Switch
These connections can be accomplished in a number of ways. The most important consideration is that
when using a normal, straight-through cable, the connection should be made between a normal
crossed port (Port 2x, 3x, etc.) and an Uplink (MDI-II) port. If you are using a crossover cable, the
connection must be made from Uplink to Uplink (port 1x on the DES-3326), or from a crossed port to
another crossed port.
22
Page 23

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
♦ A 10BASE-T hub or switch can be connected to the Switch via a two-pair Category 3, 4 or 5
UTP/STP straight cable.
♦ A 100BASE-TX hub or switch can be connected to the Switch via a two-pair Category 5e UTP/STP
straight cable.
If the other switch or hub contains an unused Uplink port, we suggest connecting the other device’s
Uplink (MDI-II) port to any of the switch’s (MDI-X) ports (1x - 22x, or one of the optional Gigabit module
ports) using a normal straight-through cable, as shown below.
If the other device does not have an unused Uplink port, make the connection with a normal straightthrough cable from the Uplink port on the switch to any normal crossed port on the hub. Alternatively,
if you have a crossover cable you can save the Uplink ports for other connections and make this one
from a crossed port to another crossed port.
Figure 4-2. Switch connected to a normal (non-Uplink) port on a hub or switch using a straight or crossover
cable
10BASE-T Device
For a 10BASE-T device, the Switch’s LED indicators should display the following:
♦ 100 LED speed indicator is OFF.
♦ Link/Act indicator is ON.
100BASE-TX Device
For a 100BASE-TX device, the Switch’s LED indicators should display the following:
♦ 100 LED speed indicator is ON.
♦ Link/Act is ON.
23
Page 24

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
5
SWITCH MANAGEMENT AND OPERATING
CONCEPTS
This chapter discusses many of the concepts and features used to manage the switch, as well as the
concepts necessary for the user to understand the functioning of the switch. Further, this chapter
explains many important points regarding these features.
Configuring the switch to implement these concepts and make use of its many features is discussed in
detail in the next chapters.
Local Console Management
A local console is a terminal or a workstation running a terminal emulation program that is connected
directly to the switch via the RS-232 console port on the front of the switch. A console connection is
referred to as an ‘Out-of-Band’ connection, meaning that console is connected to the switch using a
different circuit than that used for normal network communications. So, the console can be used to set
up and manage the switch even if the network is down.
Local console management uses the terminal connection to operate the console program built-in to the
switch (see Chapter 6, “Using the Console Interface”). A network administrator can manage, control and
monitor the switch from the console program.
The DES-3326 contains a CPU, memory for data storage, flash memory for configuration data,
operational programs, and SNMP agent firmware. These components allow the switch to be actively
managed and monitored from either the console port or the network itself (out-of-band, or in-band).
Diagnostic (console) port (RS-232 DCE)
Out-of-band management requires connecting a terminal, such as a VT-100 or a PC running a terminal
emulation program (such as HyperTerminal, which is automatically installed with Microsoft Windows) a
to the RS-232 DCE console port of the Switch. Switch management using the RS-232 DCE console port
is called Local Console Management to differentiate it from management performed via management
platforms, such as D-View, HP OpenView, etc. Web-based Management describes management of the
switch performed over the network (in-band) using the switch’s built-in Web-based management
program (see Chapter 7, “Web-based Network Management”). The operations to be performed and the
facilities provided by these two built-in programs are identical.
The console port is set at the factory for the following configuration:
• Baud rate: 9,600
• Data width: 8 bits
• Parity: none
• Stop bits: 1
24
Page 25

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
• Flow Control None
Make sure the terminal or PC you are using to make this connection is configured to match these
settings.
If you are having problems making this connection on a PC, make sure the emulation is set to VT-
100. If you still don’t see anything, try hitting <Ctrl> + r to refresh the screen.
IP Addresses and SNMP Community Names
Each Switch must be assigned its own IP Address, which is used for communication with an SNMP
network manager or other TCP/IP application (for example BOOTP, TFTP). The switch’s default IP
address is 10.90.90.90. You can change the default Switch IP Address to meet the specification of your
networking address scheme.
The switch is also assigned a unique MAC address by the factory. This MAC address cannot be
changed, and can be found from the initial boot console screen – shown below.
Figure 5-1. Boot screen
The switch’s MAC address can also be found from the console program under the Switch Information
menu item, as shown below.
Figure 5-2. Switch Information screen
25
Page 26

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
In addition, you can also set an IP Address for a gateway router. This becomes necessary when the
network management station is located on a different IP network from the Switch, making it necessary
for management packets to go through a router to reach the network manager, and vice-versa.
For security, you can set in the Switch a list of IP Addresses of the network managers that you allow to
manage the Switch. You can also change the default SNMP Community Strings in the Switch and set
the access rights of these Community Strings. In addition, a VLAN may be designated as a
Management VLAN.
Traps
Traps are messages that alert you of events that occur on the Switch. The events can be as serious as a
reboot (someone accidentally turned OFF the Switch), or less serious like a port status change. The
Switch generates traps and sends them to the network manager (trap recipient).
Trap recipients are special users of the network who are given certain rights and access in overseeing
the maintenance of the network. Trap recipients will receive traps sent from the Switch; they must
immediately take certain actions to avoid future failure or breakdown of the network.
You can also specify which network managers may receive traps from the Switch by entering a list of
the IP addresses of authorized network managers. Up to four trap recipient IP addresses, and four
corresponding SNMP community strings can be entered.
SNMP community strings function like passwords in that the community string entered for a given IP
address must be used in the management station software, or a trap will be sent.
The following are trap types the switch can send to a trap recipient:
• Cold Start This trap signifies that the Switch has been powered up and initialized such that
software settings are reconfigured and hardware systems are rebooted. A cold start is
different from a factory reset in that configuration settings saved to non-volatile RAM used to
reconfigure the switch.
• Warm Start This trap signifies that the Switch has been rebooted, however the POST (Power
On Self-Test) is skipped.
• Authentication Failure This trap signifies that someone has tried to logon to the switch
using an invalid SNMP community string. The switch automatically stores the source IP
address of the unauthorized user.
• New Root This trap indicates that the Switch has become the new root of the Spanning Tree,
the trap is sent by the switch soon after its election as the new root. This implies that upon
expiration of the Topology Change Timer the new root trap is sent out immediately after the
Switch’s election as the new root.
• Topology Change (STP) A Topology Change trap is sent by the Switch when any of its
configured ports transitions from the Learning state to the Forwarding state, or from the
Forwarding state to the Blocking state. The trap is not sent if a new root trap is sent for the
same transition.
• Link Up This trap is sent whenever the link of a port changes from link down to link up.
• Link Down This trap is sent whenever the link of a port changes from link up to link down.
26
Page 27

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
SNMP
The Simple Network Management Protocol (SNMP) is an OSI layer 7 (the application layer) protocol for
remotely monitoring and configuring network devices. SNMP enables network management stations to
read and modify the settings of gateways, routers, switches, and other network devices. SNMP can be
used to perform many of the same functions as a directly connected console, or can be used within an
integrated network management software package such as DView or NetView.
SNMP performs the following functions:
• Sending and receiving SNMP packets through the IP protocol.
• Collecting information about the status and current configuration of network devices.
• Modifying the configuration of network devices.
The DES-3326 has a software program called an ‘agent’ that processes SNMP requests, but the user
program that makes the requests and collects the responses runs on a management station (a
designated computer on the network). The SNMP agent and the user program both use the UDP/IP
protocol to exchange packets.
Authentication
The authentication protocol ensures that both the router SNMP agent and the remote user SNMP
application program discard packets from unauthorized users. Authentication is accomplished using
‘community strings’, which function like passwords. The remote user SNMP application and the router
SNMP must use the same community string. SNMP community strings of up to 20 characters may be
entered under the Remote Management Setup menu of the console program.
Traps
Traps are messages that alert network personnel of events that occur on the Switch. The events can be
as serious as a reboot (someone accidentally turned OFF the Switch), or less serious like a port status
change. The Switch generates traps and sends them to the trap recipient (or network manager).
Trap recipients are special users of the network who are given certain rights and access in overseeing
the maintenance of the network. Trap recipients will receive traps sent from the Switch; they must
immediately take certain actions to avoid future failure or breakdown of the network.
You can also specify which network managers may receive traps from the Switch by entering a list of
the IP addresses of authorized network managers. Up to four trap recipient IP addresses, and four
corresponding SNMP community strings can be entered.
SNMP community strings function like passwords in that the community string entered for a given IP
address must be used in the management station software, or a trap will be sent.
The following are trap types the switch can send to a trap recipient:
• Cold Start This trap signifies that the Switch has been powered up and initialized
such that software settings are reconfigured and hardware systems are rebooted. A
cold start is different from a factory reset in that configuration settings saved to nonvolatile RAM used to reconfigure the switch.
• Warm Start This trap signifies that the Switch has been rebooted, however the POST
(Power On Self-Test) is skipped.
27
Page 28

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
• Authentication Failure This trap signifies that someone has tried to logon to the
switch using an invalid SNMP community string. The switch automatically stores the
source IP address of the unauthorized user.
• Topology Change A Topology Change trap is sent by the Switch when any of its
configured ports transitions from the Learning state to the Forwarding state, or from
the Forwarding state to the Blocking state. The trap is not sent if a new root trap is
sent for the same transition.
• Link Change Event This trap is sent whenever the link of a port changes from link
up to link down or from link down to link up.
• Port Partition This trap is sent whenever the port state enters the partition mode (or
automatic partitioning, port disable) when more than thirty-two collisions occur while
transmitting at 10Mbps or more than sixty-four collisions occur while transmitting at
100Mbps.
• Broadcast\Multicast Storm This trap is sent whenever the port reaches the
threshold (in packets per second) set globally for the switch. Counters are maintained
for each port, and separate counters are maintained for broadcast and multicast
packets. The switch’s default setting is 128 kpps for both broadcast and multicast
packets.
MIBs
Management and counter information are stored in the Switch in the Management Information Base
(MIB). The Switch uses the standard MIB-II Management Information Base module. Consequently,
values for MIB objects can be retrieved from any SNMP-based network management software. In
addition to the standard MIB-II, the Switch also supports its own proprietary enterprise MIB as an
extended Management Information Base. These MIBs may also be retrieved by specifying the MIB’s
Object-Identity (OID) at the network manager. MIB values can be either read-only or read-write.
Read-only MIBs variables can be either constants that are programmed into the Switch, or variables
that change while the Switch is in operation. Examples of read-only constants are the number of port
and type of ports. Examples of read-only variables are the statistics counters such as the number of
errors that have occurred, or how many kilobytes of data have been received and forwarded through a
port.
Read-write MIBs are variables usually related to user-customized configurations. Examples of these are
the Switch’s IP Address, Spanning Tree Algorithm parameters, and port status.
If you use a third-party vendors’ SNMP software to manage the Switch, a diskette listing the Switch’s
propriety enterprise MIBs can be obtained by request. If your software provides functions to browse or
modify MIBs, you can also get the MIB values and change them (if the MIBs’ attributes permit the write
operation). This process however can be quite involved, since you must know the MIB OIDs and retrieve
them one by one.
Packet Forwarding
The Switch enters the relationship between destination MAC or IP addresses and the Ethernet port or
gateway router the destination resides on into its forwarding table. This information is then used to
forward packets. This reduces the traffic congestion on the network, because packets, instead of being
28
Page 29
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
transmitted to all ports, are transmitted to the destination port only. Example: if Port 1 receives a
packet destined for a station on Port 2, the Switch transmits that packet through Port 2 only, and
transmits nothing through the other ports. This process is referred to as ‘learning’ the network
topology.
MAC Address Aging Time
The Aging Time affects the learning process of the Switch. Dynamic forwarding table entries, which are
made up of the source MAC addresses and their associated port numbers, are deleted from the table if
they are not accessed within the aging time.
The aging time can be from 10 to 1,000,000 seconds with a default value of 300 seconds. A very long
aging time can result in dynamic forwarding table entries that are out-of-date or no longer exist. This
may cause incorrect packet forwarding decisions by the switch.
If the Aging Time is too short however, many entries may be aged out too soon. This will result in a high
percentage of received packets whose source addresses cannot be found in the forwarding table, in
which case the switch will broadcast the packet to all ports, negating many of the benefits of having a
switch.
Static forwarding entries are not affected by the aging time.
Filtering
The switch uses a filtering database to segment the network and control communication between
segments. It can also filter packets off the network for intrusion control. Static filtering entries can be
made by either MAC address or IP address filtering.
Each port on the switch is a unique collision domain and the switch filters (discards) packets whose
destination lies on the same port as where it originated. This keeps local packets from disrupting
communications on other parts of the network.
For intrusion control, whenever a switch encounters a packet originating from or destined to a MAC
address or an IP Address entered into the filter table, the switch will discard the packet.
Some filtering is done automatically by the switch:
• Dynamic filtering – automatic learning and aging of MAC addresses and their location on the
network. Filtering occurs to keep local traffic confined to its segment.
• Filtering done by the Spanning Tree Protocol, which can filter packets based on topology,
making sure that signal loops don’t occur.
• Filtering done for VLAN integrity. Packets from a member of a VLAN (VLAN 2, for example)
destined for a device on another VLAN (VLAN 3) will be filtered.
Some filtering requires the manual entry of information into a filtering table:
• MAC address filtering – the manual entry of specific MAC addresses to be filtered from the
network. Packets sent from one manually entered MAC address can be filtered from the
network. The entry may be specified as a source, a destination, or both.
• IP address filtering – the manual entry of specific IP addresses to be filtered from the network
(switch must be in IP Routing mode). Packets sent from one manually entered IP address to
29
Page 30

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
g
another can be filtered from the network. The entry may specified as a source, a destination,
or both (switch must be in IP Routing mode).
Spanning Tree
The IEEE 802.1D Spanning Tree Protocol allows for the blocking of links between switches that form
loops within the network. When multiple links between switches are detected, a primary link is
established. Duplicated links are blocked from use and become standby links. The protocol allows for
the duplicate links to be used in the event of a failure of the primary link. Once the Spanning Tree
Protocol is configured and enabled, primary links are established and duplicated links are blocked
automatically. The reactivation of the blocked links (at the time of a primary link failure) is also
accomplished automatically – without operator intervention.
The DES-3326 STP allows two levels of spanning trees to be configured. The first level constructs a
spanning tree on the links between switches. This is referred to as the Switch or Global level. The
second level is on a port group basis. Groups of ports are configured as being members of a spanning
tree and the algorithm and protocol are applied to the group of ports. This is referred to as the Port or
VLAN level.
On the switch level, STP calculates the Bridge Identifier for each switch and then sets the Root Bridge
and the Designated Bridges.
On the port level, STP sets the Root Port and the Designated Ports.
The following are the user-configurable STP parameters for the switch level:
meter Description Default
Value
Bridge Identifier
(Not userconfigurable
except by setting
priority below)
Priority A relative priority for each
Hello Time The length of time between
A combination of the Userset priority and the switch’s
MAC address. The Bridge
Identifier consists of two
parts: a 16-bit priority and
a 48-bit Ethernet MAC
address
switch – lower numbers give
a higher priority and a
greater chance of a given
switch being elected as the
root bridge
broadcasts of the hello
message by the switch
32768 + MAC
32768
2 seconds
Maximum Age
Timer
Forward Delay
Timer
Measures the age of a
received BPDU for a port
and ensures that the BPDU
is discarded when its age
exceeds the value of the
maximum age timer.
The amount time spent by a
port in the learning and
listenin
states waiting for a
20 seconds
15 seconds
30
Page 31

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
BPDU that may return the
port to the blocking state.
Table 5-1. STP Parameters – Switch Level
The following are the user-configurable STP parameters for the port or port group level:
Variable Description Default
Value
Port Priority A relative priority for each
port – lower numbers give a
higher priority and a greater
chance of a given port being
elected as the root port
Port Cost A value used by STP to
evaluate paths – STP
calculates path costs and
selects the path with the
minimum cost as the active
path.
128
19 – 100Mbps
Fast Ethernet
ports
10 –
1000Mbps
Gigabit
Ethernet
ports
Table 5-2. STP Parameters – Port Group Level
Bridge Protocol Data Units
For STP to arrive at a stable network topology, the following information is used:
• The unique switch identifier
• The path cost to the root associated with each switch port
• The port identifier
STP communicates between switches on the network using Bridge Protocol Data Units (BPDUs). Each
BPDU contains the following information:
• The unique identifier of the switch that the transmitting switch currently believes is the root
switch
• The path cost to the root from the transmitting port
• The port identifier of the transmitting port
The switch sends BPDUs to communicate and construct the spanning-tree topology. All switches
connected to the LAN on which the packet is transmitted will receive the BPDU. BPDUs are not directly
forwarded by the switch, rather the receiving switch uses the information in the frame to calculate a
BPDU, and, if the topology changes, initiates a BPDU transmission.
The communication between switches via BPDUs results in the following:
• One switch is elected as the root switch
• The shortest distance to the root switch is calculated for each switch
31
Page 32

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
• A designated switch is selected. This is the switch closest to the root switch through which
packets will be forwarded to the root.
• A port for each switch is selected. This is the port providing the best path from the switch to the
root switch.
• Ports included in the STP are selected.
Creating a Stable STP Topology
If all switches have STP enabled with default settings, the switch with the lowest MAC address in the
network will become the root switch. By increasing the priority (lowering the priority number) of the
best switch, STP can be forced to select the best switch as the root switch.
When STP is enabled using the default parameters, the path between source and destination stations
in a switched network might not be ideal. For instance, connecting higher-speed links to a port that has
a higher number than the current root port can cause a root-port change. The goal is to make the
fastest link the root port.
STP Port States
The BPDUs take some time to pass through a network. This propagation delay can result in topology
changes where a port that transitioned directly from a Blocking state to a Forwarding state could create
temporary data loops. Ports must wait for new network topology information to propagate throughout
the network before starting to forward packets. They must also wait for the packet lifetime to expire for
BPDU packets that were forwarded based on the old topology. The forward delay timer is used to allow
the network topology to stabilize after a topology change.
In addition, STP specifies a series of states a port must transition through to further ensure that a
stable network topology is created after a topology change.
Each port on a switch using STP exists is in one of the following five states:
• Blocking – the port is blocked from forwarding or receiving packets
• Listening – the port is waiting to receive BPDU packets that may tell the port to go back to the
blocking state
• Learning – the port is adding addresses to its forwarding database, but not yet forwarding
packets
• Forwarding – the port is forwarding packets
• Disabled – the port only responds to network management messages and must return to the
blocking state first
A port transitions from one state to another as follows:
• From initialization (switch boot) to blocking
• From blocking to listening or to disabled
• From listening to learning or to disabled
• From learning to forwarding or to disabled
32
Page 33

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
• From forwarding to disabled
• From disabled to blocking
Figure 5-3. STP Port State Transitions
When STP is enabled, every port on every switch in the network goes through the blocking state and
then transitions through the states of listening and learning at power up. If properly configured, each
port stabilizes to the forwarding or blocking state.
No packets (except BPDUs) are forwarded from, or received by, STP enabled ports until the forwarding
state is enabled for that port.
Default Spanning-Tree Configuration
Feature Default Value
Enable state STP enabled for all ports
Port priority 128
Port cost 19
Bridge Priority 32,768
Table 5-3. Default STP Parameters
33
Page 34

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
User-Changeable STA Parameters
The factory default setting should cover the majority of installations. However, it is advisable to keep
the default settings as set at the factory; unless, it is absolutely necessary. The user changeable
parameters in the Switch are as follows:
• Priority A Priority for the switch can be set from 0 to 65535. 0 is equal to the highest
Priority.
• Hello Time The Hello Time can be from 1 to 10 seconds. This is the interval between two
transmissions of BPDU packets sent by the Root Bridge to tell all other Switches that it is
indeed the Root Bridge. If you set a Hello Time for your Switch, and it is not the Root Bridge,
the set Hello Time will be used if and when your Switch becomes the Root Bridge.
Note: The Hello Time cannot be longer than the Max. Age. Otherwise, a configuration error will occur.
• Max. Age The Max. Age can be from 6 to 40 seconds. At the end of the Max. Age, if a BPDU
has still not been received from the Root Bridge, your Switch will start sending its own BPDU
to all other Switches for permission to become the Root Bridge. If it turns out that your
Switch has the lowest Bridge Identifier, it will become the Root Bridge.
• Forward Delay Timer The Forward Delay can be from 4 to 30 seconds. This is the time any
port on the Switch spends in the listening state while moving from the blocking state to the
forwarding state.
Note: Observe the following formulas when setting the above parameters:
Max. Age ≤ 2 x (Forward Delay - 1 second)
Max. Age ≥ 2 x (Hello Time + 1 second)
• Port Priority A Port Priority can be from 0 to 255. The lower the number, the greater the
probability the port will be chosen as the Root Port.
• Port Cost A Port Cost can be set from 1 to 65535. The lower the number, the greater the
probability the port will be chosen to forward packets.
Illustration of STP
A simple illustration of three Bridges (or three switches) connected in a loop is depicted below. In this
example, you can anticipate some major network problems if the STP assistance is not applied. If
Bridge A broadcasts a packet to Bridge B, Bridge B will broadcast it to Bridge C, and Bridge C will
broadcast it to back to Bridge A ... and so on. The broadcast packet will be passed indefinitely in a loop,
potentially causing a network failure.
STP can be applied as shown in Figure 2-4. In this example, STP breaks the loop by blocking the
connection between Bridge B and C. The decision to block a particular connection is based on the STP
calculation of the most current Bridge and Port settings. Now, if Bridge A broadcasts a packet to Bridge
C, then Bridge C will drop the packet at port 2 and the broadcast will end there.
Setting-up STP using values other than the defaults, can be complex. Therefore, you are advised to
keep the default factory settings and STP will automatically assign root bridges/ports and block loop
connections. Influencing STP to choose a particular switch as the root bridge using the Priority setting,
or influencing STP to choose a particular port to block using the Port Priority and Port Cost settings
is, however, relatively straight forward.
34
Page 35

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 5-4. Before Applying the STA Rules
In this example, only the default STP values are used.
Figure 5-6. After Applying the STA Rules
The switch with the lowest Bridge ID (switch C) was elected the root bridge, and the ports were selected
to give a high port cost between switches B and C. The two (optional) Gigabit ports (default port cost =
10) on switch A are connected to one (optional) Gigabit port on both switch B and C. The redundant
link between switch B and C is deliberately chosen as a 100 Mbps Fast Ethernet link (default port cost
= 19). Gigabit ports could be used, but the port cost should be increased from the default to ensure
that the link between switch B and switch C is the blocked link.
Link Aggregation
Link aggregation is used to combine a number of ports together to make a single high-bandwidth data
pipeline. The participating parts are called members of a link aggregation group, with one port
35
Page 36

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
designated as the master port of the group. Since all members of the link aggregation group must be
configured to operate in the same manner, the configuration of the master port is applied to all
members of the link aggregation group. Thus, when configuring the ports in a link aggregation group,
you only need to configure the master port.
The DES-3326 supports link aggregation groups, which may include from 2 to 8 switch ports each,
except for a Gigabit link aggregation group which consists of the 2 (optional) Gigabit Ethernet ports of
the front panel. These ports are the two 1000BASE-SX, -LX –TX or GBIC ports contained in a frontpanel mounted module.
24
23
24
23
Figure 5-7. Link Aggregation Group
Data transmitted to a specific host (destination address) will always be transmitted over the same port
in a link aggregation group. This allows packets in a data stream to arrive in the same order they were
sent. A aggregated link connection can be made with any other switch that maintains host-to-host data
streams over a single link aggregate port. Switches that use a load-balancing scheme that sends the
packets of a host-to-host data stream over multiple link aggregation ports cannot have a aggregated
connection with the DES-3326 switch.
36
Page 37

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
VLANs
A VLAN is a collection of end nodes grouped by logic rather than physical location. End nodes that
frequently communicate with each other are assigned to the same VLAN, regardless of where they are
located physically on the network. Logically, a VLAN can be equated to a broadcast domain, because
broadcast packets are forwarded only to members of the VLAN on which the broadcast was initiated.
Notes About VLANs on the DES-3326
1. The DES-3326 supports IEEE 802.1Q VLANs. The port untagging function can be used
to remove the 802.1Q tag from packet headers to maintain compatibility with devices
that are tag-unaware (that is, network devices that do not support IEEE 802.1Q VLANs
or tagging).
2. The switch’s default - in both Layer 2 Only mode and IP Routing mode - is to assign all
ports to a single 802.1Q VLAN named DEFAULT_VLAN.
3. The switch allows the assignment of an IP interface to each VLAN, in IP Routing mode.
The VLANs must be configured before setting up the IP interfaces
4. A VLAN that is not assigned an IP interface will behave as a layer 2 VLAN – and IP
routing, by the switch, will not be possible to this VLAN regardless of the switch’s
operating mode.
IEEE 802.1Q VLANs
Some relevant terms:
Tagging - The act of putting 802.1Q VLAN information into the header of a packet.
Untagging - The act of stripping 802.1Q VLAN information out of the packet header.
Ingress port - A port on a switch where packets are flowing into the switch and VLAN decisions must
be made.
Egress port - A port on a switch where packets are flowing out of the switch, either to another switch
or to an end station, and tagging decisions must be made.
IEEE 802.1Q (tagged) VLANs are implemented on the DES-3326 Layer 3 switch. 802.1Q VLANs require
tagging, which enables the VLANs to span an entire network (assuming all switches on the network are
IEEE 802.1Q-compliant).
Any port can be configured as either tagging or untagging. The untagging feature of IEEE 802.1Q VLANs
allow VLANs to work with legacy switches that don’t recognize VLAN tags in packet headers. The
tagging feature allows VLANs to span multiple 802.1Q-compliant switches through a single physical
connection and allows Spanning Tree to be enabled on all ports and work normally.
802.1Q VLAN Packet Forwarding
Packet forwarding decisions are made based upon the following three types of rules:
• Ingress rules – rules relevant to the classification of received frames belonging to a VLAN.
• Forwarding rules between ports – decides filter or forward the packet
37
Page 38

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
• Egress rules – determines if the packet must be sent tagged or untagged.
Figure 5-8. IEEE 802.1Q Packet Forwarding
802.1Q VLAN Tags
The figure below shows the 802.1Q VLAN tag. There are four additional octets inserted after the source
MAC address. Their presence is indicated by a value of 0x8100 in the EtherType field. When a packet’s
EtherType field is equal to 0x8100, the packet carries the IEEE 802.1Q/802.1p tag. The tag is
contained in the following two octets and consists of 3 bits or user priority, 1 bit of Canonical Format
Identifier (CFI – used for encapsulating Token Ring packets so they can be carried across Ethernet
backbones) and 12 bits of VLAN ID (VID). The 3 bits of user priority are used by 802.1p. The VID is the
VLAN identifier and is used by the 802.1Q standard. Because the VID is 12 bits long, 4094 unique
VLANs can be identified.
The tag is inserted into the packet header making the entire packet longer by 4 octets. All of the
information contained in the packet originally is retained.
Figure 5-9. IEEE 802.1Q Tag
38
Page 39

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
The EtherType and VLAN ID are inserted after the MAC source address, but before the original
EtherType/Length or Logical Link Control. Because the packet is now a bit longer than it was originally,
the Cyclic Redundancy Check (CRC) must be recalculated.
Figure 5-10. Adding an IEEE 802.1Q Tag
Port VLAN ID
Packets that are tagged (are carrying the 802.1Q VID information) can be transmitted from one 802.1Q
compliant network device to another with the VLAN information intact. This allows 802.1Q VLANs to
span network devices (and indeed, the entire network – if all network devices are 802.1Q compliant).
Unfortunately, not all network devices are 802.1Q compliant. These devices are referred to as tag-
unaware. 802.1Q devices are referred to as tag-aware.
Prior to the adoption 802.1Q VLANs, port-based and MAC-based VLANs were in common use. These
VLANs relied upon a Port VLAN ID (PVID) to forward packets. A packet received on a given port would
be assigned that port’s PVID and then be forwarded to the port that corresponded to the packet’s
destination address (found in the switch’s forwarding table). If the PVID of the port that received the
packet is different from the PVID of the port that is to transmit the packet, the switch will drop the
packet.
Within the switch, different PVIDs mean different VLANs (remember that two VLANs cannot
communicate without an external router). So, VLAN identification based upon the PVIDs cannot create
VLANs that extend outside a given switch (or switch stack).
Every physical port on a switch has a PVID. 802.1Q ports are also assigned a PVID, for use within the
switch. If no VLANs are defined on the switch, all ports are then assigned to a default VLAN with a PVID
equal to 1. Untagged packets are assigned the PVID of the port on which they were received.
Forwarding decisions are based upon this PVID, in so far as VLANs are concerned. Tagged packets are
forwarded according to the VID contained within the tag. Tagged packets are also assigned a PVID, but
the PVID is not used to make packet forwarding decisions, the VID is.
Tag-aware switches must keep a table to relate PVIDs within the switch to VIDs on the network. The
switch will compare the VID of a packet to be transmitted to the VID of the port that is to transmit the
packet. If the two VIDs are different, the switch will drop the packet. Because of the existence of the
PVID for untagged packets and the VID for tagged packets, tag-aware and tag-unaware network devices
can coexist on the same network.
A switch port can have only one PVID, but can have as many VIDs as the switch has memory in its
VLAN table to store them.
Because some devices on a network may be tag-unaware, a decision must be made at each port on a
tag-aware device before packets are transmitted – should the packet to be transmitted have a tag or
39
Page 40

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
not? If the transmitting port is connected to a tag-unaware device, the packet should be untagged. If
the transmitting port is connected to a tag-aware device, the packet should be tagged.
Tagging and Untagging
Every port on an 802.1Q compliant switch can be configured as tagging or untagging.
Ports with tagging enabled will put the VID number, priority and other VLAN information into the
header of all packets that flow into and out of it. If a packet has previously been tagged, the port will
not alter the packet, thus keeping the VLAN information intact. The VLAN information in the tag can
then be used by other 802.1Q compliant devices on the network to make packet forwarding decisions.
Ports with untagging enabled will strip the 802.1Q tag from all packets that flow into and out of those
ports. If the packet doesn’t have an 802.1Q VLAN tag, the port will not alter the packet. Thus, all
packets received by and forwarded by an untagging port will have no 802.1Q VLAN information.
(Remember that the PVID is only used internally within the switch). Untagging is used to send packets
from an 802.1Q-compliant network device to a non-compliant network device.
Ingress Filtering
A port on a switch where packets are flowing into the switch and VLAN decisions must be made is
referred to as an ingress port. If ingress filtering is enabled for a port, the switch will examine the VLAN
information in the packet header (if present) and decide whether or not to forward the packet.
If the packet is tagged with VLAN information, the ingress port will first determine if the ingress port
itself is a member of the tagged VLAN. If it is not, the packet will be dropped. If the ingress port is a
member of the 802.1Q VLAN, the switch then determines if the destination port is a member of the
802.1Q VLAN. If it is not, the packet is dropped. If the destination port is a member of the 802.1Q
VLAN, the packet is forwarded and the destination port transmits it to its attached network segment.
If the packet is not tagged with VLAN information, the ingress port will tag the packet with its own PVID
as a VID (if the port is a tagging port). The switch then determines if the destination port is a member of
the same VLAN (has the same VID) as the ingress port. If it does not, the packet is dropped. If it has the
same VID, the packet is forwarded and the destination port transmits it on its attached network
segment.
This process is referred to as ingress filtering and is used to conserve bandwidth within the switch by
dropping packets that are not on the same VLAN as the ingress port at the point of reception. This
eliminates the subsequent processing of packets that will just be dropped by the destination port.
VLANs in Layer 2 Only Mode
The switch initially configures one VLAN, VID = 1, called the DEFAULT_VLAN. The factory default
setting assigns all ports on the switch to the DEFAULT_VLAN.
Packets cannot cross VLANs if the switch is in Layer 2 Only mode. If a member of one VLAN wants to
connect to another VLAN, the link must be through an external router.
When the switch is in Layer 2 Only mode, 802.1Q VLANs are supported.
If no VLANs are configured on the switch and the switch is in Layer 2 Only mode, then all packets will
be forwarded to any destination port. Packets with unknown source addresses will be flooded to all
ports. Broadcast and multicast packets will also be flooded to all ports.
A VLAN that does not have a corresponding IP interface defined for it, will function as a Layer 2 Only
VLAN – regardless of the Switch Operation mode.
40
Page 41

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Layer 3-Based VLANs
Layer 3-based VLANs use network-layer addresses (subnet address for TCP/IP) to determine VLAN
membership. These VLANs are based on layer 3 information, but this does not constitute a ‘routing’
function.
The DES-3326 allows an IP subnet to be configured for each 802.1Q VLAN that exists on the switch.
Even though a switch inspects a packet’s IP address to determine VLAN membership, no route
calculation is performed, the RIP protocol is not employed, and packets traversing the switch are
bridged using the Spanning Tree algorithm.
A switch that implements layer 3 (or ‘subnet’) VLANs without performing any routing function between
these VLANs is referred to as performing ‘IP Switching’.
IP Addressing and Subnetting
This section gives basic information needed to configure your Layer 3 switch for IP routing. The
information includes how IP addresses are broken down and how subnetting works. You will learn how
to assign each interface on the router an IP address with a unique subnet.
Definitions
• IP Address – the unique number ID assigned to each host or interface on a network. IP
addresses have the form xxx.xxx.xxx.xxx.
• Subnet – a portion of a network sharing a particular network address.
• Subnet mask – a 32-bit number used to describe which portion of a Network Address refers to
the subnet and which portion refers to the host. Subnet masks have the form xxx.xxx.xxx.xxx.
• Interface – a network connection
• IP Interface – another name for subnet.
• Network Address – the resulting 32-bit number from a bitwise logical AND operation performed
between an IP address and a subnet mask.
• Subnet Address – another name for network address.
IP Addresses
The Internet Protocol (IP) was designed for routing data between network sites. Later, it was adapted for
routing between networks (referred to as “subnets”) within a site. The IP defines a way of generating a
unique number that can be assigned each network in the internet and each of the computers on each
of those networks. This number is called the IP address.
IP addresses use a “dotted decimal” notation. Here are some examples of IP addresses written in this
format:
1. 210.202.204.205
2. 189.21.241.56
3. 125.87.0.1
This allows IP address to be written in a string of 4 decimal (base 10) numbers. Computers can only
understand binary (base 2) numbers, and these binary numbers are usually grouped together in bytes,
or eight bits. (A bit is a binary digit – either a “1” or a “0”). The dots (periods) simply make the IP
41
Page 42

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
address easier to read. A computer sees an IP address not as four decimal numbers, but as a long
string of binary digits (32 binary digits or 32 bits, IP addresses are 32-bit addresses).
The three IP addresses in the example above, written in binary form are:
1. 11010010.11001010.11001100.11001101
2. 10111101.00010101.11110001.00111000
3. 01111101.01010111.00000000.00000001
The dots are included to make the numbers easier to read.
Eight binary bits are called a ‘byte’ or an ‘octet’. An octet can represent any decimal value between ‘0’
(00000000) and ‘255’ (11111111). IP addresses, represented in decimal form, are four numbers whose
value is between ‘0’ to ‘255’. The total range of IP addresses are then:
Lowest possible IP address - 0.0.0.0
Highest possible IP address - 255.255.255.255
To convert decimal numbers to 8-bit binary numbers (and vice-versa), you can use the following chart:
7
Binary Octet Digit 2
26 25 24 23 22 21 2
0
Decimal Equivalent 128 64 32 16 8 4 2 1
Binary Number
1 1 1 1 1 1 1 1
128+64+32+16+8+4+2+1=
255
Table 5-4. Binary to Decimal Conversion
Each digit in an 8-bit binary number (an octet) represents a power of two. The left-most digit represents
2 raised to the 7
th
power (2x2x2x2x2x2x2=128) while the right-most digit represents 2 raised to the 0th
power (any number raised to the 0th power is equal to one, by definition).
IP addresses actually consist of two parts, one identifying the network and one identifying the
destination (node) within the network.
The IP address discussed above is one part and a second number called the Subnet mask is the other
part. To make this a bit more confusing, the subnet mask has the same numerical form as an IP
address.
Address Classes
Address classes refer to the range of numbers in the subnet mask. Grouping the subnet masks into
classes makes the task of dividing a network into subnets a bit easier.
There are 5 address classes. The first 4 bits in the IP address determine which class the IP address falls
in.
• Class A addresses begin with 0xxx, or 1 to 126 decimal.
• Class B addresses begin with 10xx, or 128 to 191 decimal.
• Class C addresses begin with 110x, or 192 to 223 decimal.
• Class D addresses begin with 1110, or 224 to 239 decimal.
• Class E addresses begin with 1111, or 240 to 254 decimal.
Addresses beginning with 01111111, or 127 decimal, are reserved. They are used for internal testing on
a local machine (called loopback). The address 127.0.0.1 can always be pinged from a local node
because it forms a loopback and points back to the same node.
42
Page 43

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Class D addresses are reserved for multicasting.
Class E Addresses are reserved for future use. They are not used for node addresses.
The part of the IP address that belongs to the network is the part that is ‘hidden’ by the ‘1’s in the
subnet mask. This can be seen below:
• Class A NETWORK.node.node.node
• Class B NETWORK.NETWORK.node.node
• Class C NETWORK.NETWORK.NETWORK.node
For example, the IP address 10.42.73.210 is a Class A address, so the Network part of the address
(called the Network Address) is the first octet (10.x.x.x). The node part of the address is the last three
octets (x.42.73.210).
To specify the network address for a given IP address, the node part is set to all “0”s. In our example,
10.0.0.0 specifies the network address for 10.42.73.210. When the node part is set to all “1”s, the
address specifies a broadcast address. So, 10.255.255.255 is the broadcast address for the network
10.0.0.0.
Subnet Masking
A subnet mask can be applied to an IP address to identify the network and the node parts of the
address. A bitwise logical AND operation between the IP address and the subnet mask results in the
Network Address.
For example:
00001010.00101010.01001001.11010010 10.42.73.210 Class A IP address
11111111.00000000.00000000.00000000 255.0.0.0 Class A Subnet Mask
00001010.00000000.00000000.00000000 10.0.0.0 Network Address
The Default subnet masks are:
• Class A – 11111111.00000000.00000000.00000000 255.0.0.0
• Class B – 11111111.11111111.00000000.00000000 255.255.0.0
• Class C – 1111111.11111111.11111111.00000000 255.255.255.0
Additional bits can be added to the default subnet mask for a given Class to further subnet a network.
When a bitwise logical AND operation is performed between the subnet mask and the IP address, the
result defines the Subnet Address.
Some restrictions apply to subnet addresses. Addresses of all “0”s and all “1”s are reserved for the local
network (when a host does not know it’s network address) and for all hosts on the network (the
broadcast address). This also applies to subnets. A subnet address cannot be all “0”s or all “1”s. A 1bit subnet mask is also not allowed.
Calculating the Number of Subnets and Nodes
To calculate the number of subnets and nodes, use the formula (2n – 2) where n = the number of bits in
either the subnet mask or the node portion of the IP address. Multiplying the number of subnets by the
number of nodes available per subnet gives the total number of nodes for the entire network.
Example
00001010.00101010.01001001.11010010 10.42.73.210 Class A IP address
11111111.11100000.00000000.00000000 255.224.0.0 Subnet Mask
00001010.00100000.00000000.00000000 10.32.0.0 Network Address
00001010.00101010.11111111.11111111 10.32.255.255 Broadcast Address
43
Page 44

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
This example uses an 11-bit subnet mask. (There are 3 additional bits added to the default Class A
subnet mask). So the number of subnets is:
3
2
– 2 = 8 – 2 = 6
Subnets of all “0”s and all “1”s are not allowed, so 2 subnets are subtracted from the total.
The number of bits used in the node part of the address is 24 – 3 = 21 bits, so the total number of
nodes is:
21
2
– 2 = 2,097,152 – 2 = 2,097,150
Multiplying the number of subnets times the number of nodes gives 12,582,900 possible nodes.
Note that this is less than the 16,777,214 possible nodes that an unsubnetted class A network would
have.
Subnetting reduces the number of possible nodes for a given network, but increases the segmentation
of the network.
Classless InterDomain Routing – CIDR
Under CIDR, the subnet mask notation is reduced to a simplified shorthand. Instead of specifying all of
the bits of the subnet mask, it is simply listed as the number of contiguous “1”s (bits) in the network
portion of the address. Look at the subnet mask of the above example in binary -
11111111.11100000.00000000.00000000 – and you can see that there are 11 “1”s or 11 bits used to
mask the network address from the node address. Written in CIDR notation this becomes:
10.32.0.0/11
# of
Subnet Mask CID
Bits
2 255.192.0.0 /10 2 4194302 8388604
3 255.224.0.0 /11 6 2097150 12582900
4 255.240.0.0 /12 14 1048574 14680036
5 255.248.0.0 /13 30 524286 15728580
6 255.252.0.0 /14 62 262142 16252804
7 255.254.0.0 /15 126 131070 16514820
8 255.255.0.0 /16 254 65534 16645636
9 255.255.128.0 /17 510 32766 16710660
10 255.255.192.0 /18 1022 16382 16742404
11 255.255.224.0 /19 2046 8190 16756740
12 255.255.240.0 /20 4094 4094 16760836
13 255.255.248.0 /21 8190 2046 16756740
14 255.255.252.0 /22 16382 1022 16742404
15 255.255.254.0 /23 32766 510 16710660
16 255.255.255.0 /24 65534 254 16645636
17 255.255.255.1
28
18 255.255.255.1
92
19 255.255.255.2
24
20 255.255.255.2
40
21 255.255.255.2
48
22 255.255.255.2
52
# of
R
Subnets
Nota
tion
/25 131070 126 16514820
/26 262142 62 16252804
/27 525286 30 15728580
/28 1048574 14 14680036
/29 2097150 6 12582900
/30 4194302 2 8388604
# of Hosts Total Hosts
Table 5-5. Class A Subnet Masks
44
Page 45

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
# of
Subnet Mask CIDR
Bits
2 255.255.192 /18 2 16382 32764
3 255.255.224.0 /19 6 8190 49140
4 255.255.240.0 /20 14 4094 57316
5 255.255.248.0 /21 30 2046 61380
6 255.255.252.0 /22 62 1022 63364
7 255.255.254.0 /23 126 510 64260
8 255.255.255.0 /24 254 254 64516
9 255.255.255.128 /25 510 126 64260
10 255.255.255.192 /26 1022 62 63364
11 255.255.255.224 /27 2046 30 61380
12 255.255.255.240 /28 4094 14 57316
13 255.255.255.248 /29 8190 6 49140
14 255.255.255.252 /30 16382 2 32764
Table 5-6. Class B Subnet Masks
# of
Subnet Mask CIDR
Bits
2 255.255.255.192 /26 2 62 124
3 255.255.255.224 /27 6 30 180
4 255.255.255.240 /28 14 14 196
5 255.255.255.248 /29 30 6 180
6 255.255.255.252 /30 62 2 124
Table 5-7. Class C Subnet Masks
Notation
Notation
# of
Subnets
# of
Subnets
# of
Hosts
# of
Hosts
Total
Hosts
Total
Hosts
Setting up IP Interfaces
The Layer 3 switch allows ranges of IP addresses (OSI layer 3) to be assigned to VLANs (OSI layer 2).
Each VLAN must be configured prior to setting up the corresponding IP interface. An IP addressing
scheme must then be established, and implemented when the IP interfaces are set up on the switch.
An example is presented below:
VLAN Name VID Switch Ports
System (default) 1 5, 6, 7, 8, 21, 22, 23, 24
Engineering 2 9, 10, 11, 12
Marketing 3 13, 14, 15, 16
Finance 4 17, 18, 19, 20
Sales 5 1, 2, 3, 4
Backbone 6 25, 26
Table 5-8. VLAN Example – Assigned Ports
In this case, 6 IP interfaces are required, so a CIDR notation of 10.32.0.0/11 (or a 11-bit) addressing
scheme will work. This addressing scheme will give a subnet mask of
11111111.11100000.00000000.00000000 (binary) or 255.224.0.0 (decimal).
Using a 10.xxx.xxx.xxx IP address notation, the above example would give 6 network addresses and 6
subnets.
Any IP address from the allowed range of IP addresses for each subnet can be chosen as an IP address
for an IP interface on the switch.
For this example, we have chosen the next IP address above the network address:
45
Page 46

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
VLAN Name VID Network Address IP Address
System (default) 1 10.32.0.0 10.32.0.1
Engineering 2 10.64.0.0 10.64.0.1
Marketing 3 10.96.0.0 10.96.0.1
Finance 4 10.128.0.0 10.128.0.1
Sales 5 10.160.0.0 10.160.0.1
Backbone 6 10.192.0.0 10.192.0.1
Table 5-9. VLAN Example – Assigned IP Addresses
The 6 IP interfaces, each with an IP address (listed in the table above), and a subnet mask of
255.224.0.0 can be entered into the Setup IP Interface menu.
Layer 3-Based VLANs
Layer 3-based VLANs use network-layer addresses (subnet address for TCP/IP) to determine VLAN
membership. These VLANs are based on layer 3 information, but this does not constitute a ‘routing’
function.
The DES-3326 allows an IP subnet to be configured for each 802.1Q VLAN that exists on the switch.
Even though a switch inspects a packet’s IP address to determine VLAN membership, no route
calculation is performed, the RIP protocol is not employed, and packets traversing the switch are
bridged using the Spanning Tree algorithm.
A switch that implements layer 3 (or ‘subnet’) VLANs without performing any routing function between
these VLANs is referred to as performing ‘IP Switching’.
Internet Protocols
This is a brief introduction to the suite of Internet Protocols frequently referred to as TCP/IP. It is
intended to give the reader a reasonable understanding of the available facilities and some familiarity
with terminology. It is not intended to be a complete description.
46
Page 47

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Protocol Layering
The Internet Protocol (IP) divides the tasks necessary to route and forward packets across networks by
using a layered approach. Each layer has clearly defined tasks, protocol, and interfaces for
communicating with adjacent layers, but the exact way these tasks are accomplished is left to
individual software designers. The Open Systems Interconnect (OSI) seven-layer model has been
adopted as the reference for the description of modern networking, including the Internet.
A diagram of the OSI model is shown below (note that this is not a complete listing of the protocols
contained within each layer of the model):
Figure 5-11. OSI Seven Layer Network Model
Each layer is a distinct set of programs executing a distinct set of protocols designed to accomplish
some necessary tasks. They are separated from the other layers within the same system or network,
but must communicate and interoperate. This requires very well-defined and well-known methods for
transferring messages and data. This is accomplished through the protocol stack.
Protocol layering as simply a tool for visualizing the organization of the necessary software and
hardware in a network. In this view, Layer 2 represents switching and Layer 3 represents routing.
Protocol layering is actually a set of guidelines used in writing programs and designing hardware that
delegate network functions and allow the layers to communicate. How these layers communicate within
a stack (for example, within a given computer) is left to the operating system programmers.
47
Page 48

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 5-12. The Protocol Stack
Between two protocol stacks, members of the same layer are known as peers and communicate by wellknown (open and published) protocols. Within a protocol stack, adjacent layers communicate by an
internal interface. This interface is usually not publicly documented and is frequently proprietary. It
has some of the same characteristics of a protocol and two stacks from the same software vendor may
communicate in the same way. Two stacks from different software vendors (or different products from
the same vendor) may communicate in completely different ways. As long as peers can communicate
and interoperate, this has no impact on the functioning of the network.
The communication between layers within a given protocol stack can be both different from a second
stack and proprietary, but communication between peers on the same OSI layer is open and consistent.
A brief description of the most commonly used functional layers is helpful to understand the scope of
how protocol layering works.
Layer 1
This is referred to as the physical layer. It handles the electrical connections and signaling required to
make a physical link from one point in the network to another. It is on this layer that the unique Media
Access Control (MAC) address is defined.
Layer 2
This layer, commonly called the switching layer, allows end station addressing and the establishment of
connections between them.
Layer 2 switching forwards packets based on the unique MAC address of each end station and offers
high-performance, dedicated-bandwidth of Fast or Gigibit Ethernet within the network.
Layer 2 does not ordinarily extend beyond the intranet. To connect to the Internet usually requires a
router and a modem or other device to connect to an Internet Service Provider’s WAN. These are Layer
3 functions.
48
Page 49

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Layer 3
Commonly referred to as the routing layer, this layer provides logical partitioning of networks
(subnetting), scalability, security, and Quality of Service (QoS).
The backbone of the Internet is built using Layer 3 functions. IP is the premier Layer 3 protocol.
IP is itself, only one protocol in the IP protocol suite. More extensive capabilities are found in the other
protocols of the IP suite. For example; the Domain Name System (DNS) associates IP addresses with
text names, the Dynamic Host Configuration Protocol (DHCP) eases the administration of IP addresses,
and routing protocols such as the Routing Information Protocol (RIP), the Open Shortest Path First
(OSPF), and the Border Gateway Protocol (BGP) enable Layer 3 devices to direct data traffic to the
intended destination. IP security allows for authentication and encryption. IP not only allows for userto-user communication, but also for transmission from point-to-multipoint (known as IP multicasting).
Layer 4
This layer, known as the transport layer, establishes the communication path between user
applications and the network infrastructure and defines the method of communicating. TCP and UDP
are well-known protocols in the transport layer. TCP is a “connection-oriented” protocol, and requires
the establishment of parameters for transmission prior to the exchange of data. Web technology is
based on TCP. UDP is “connectionless” and requires no connection setup. This is important for
multicast traffic, which cannot tolerate the overhead and latency of TCP. TCP and UDP also differ in the
amount of error recovery provided and whether or not it is visible to the user application. Both TCP and
UDP are layered on IP, which has minimal error recovery and detection. TCP forces retransmission of
data that was lost by the lower layers, UDP does not.
Layer 7
This layer, known as the application layer, provides access to either the end user application software
such as a database. Users communicate with the application, which in turn delivers data to the
transport layer. Applications do not usually communicate directly with lower layers. They are written to
use a specific communication library, like the popular WinSock library.
Software developers must decide what type of transport mechanism is necessary. For example, Web
access requires reliable, error-free access and would demand TCP. Multimedia, on the other hand,
requires low overhead and latency and commonly uses UDP.
TCP/IP
The TCP/IP protocol suite is a set of protocols that allow computers to share resources across a
network. TCP and IP are only two of the Internet suite of protocols, but they are the best known and it
has become common to refer the entire family of Internet protocols as TCP/IP.
TCP/IP is a layered set of protocols. An example, such as sending e-mail, can illustrate this. There is
first a protocol for sending and receiving e-mail. This protocol defines a set of commands to identify the
sender, the recipient, and the content of the e-mail. The e-mail protocol will not handle the actual
communication between the two computers as this is done by TCP/IP. TCP/IP handles the actual
sending and receiving of the packets that make up the e-mail exchange.
TCP makes sure the e-mail commands and messages are received by the appropriate computers. It
keeps track of what is sent and what is received, and retransmits any packets that are lost or dropped.
TCP also handles the division of large messages into several Ethernet packets, and makes sure these
packets are received and reassembled in the correct order.
49
Page 50

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Because these functions are required by a large number of applications, they are grouped into a single
protocol, rather than being the part of the specifications for just sending e-mail. TCP is then a library of
routines that application software can use when reliable network communications are required.
IP is also a library of routines, but with a more general set of functions. IP handles the routing of
packets from the source to the destination. This may require the packets to traverse many different
networks. IP can route packets through the necessary gateways and provides the functions required for
any user on one network to communicate with any user on another connected network.
The communication interface between TCP and IP is relatively simple. When IP received a packet, it
does not know how this packet is related to others it has sent (or received) or even which connection
the packet is part of. IP only knows the address of the source and the destination of the packet, and it
makes its best effort to deliver the packet to its destination.
The information required for IP to do its job is contained in a series of octets added to the beginning of
the packet called headers. A header contains a few octets of data added to the packet by the protocol in
order to keep track of it.
Other protocols on other network devices can add and extract their own headers to and from packets as
they cross networks. This is analogous to putting data into an envelope and sending the envelope to a
higher-level protocol, and having the higher-level protocol put the entire envelope into it’s own, larger
envelope. This process is referred to as encapsulation.
Many levels of encapsulation are required for a packet to cross the Internet.
Packet Headers
TCP
Most data transmissions are much longer that a single packet. The data must then be divided up
among a series of packets. These packets must be transmitted, received and then reassembled into the
original data. TCP handles these functions.
TCP must know how large a packet the network can process. To do this, the TCP protocols at each end
of a connection state how large a packet they can handle and the smaller of the two is selected.
The TCP header contains at least 20 octets. The source and destination TCP port numbers are the most
important fields. These specify the connection between two TCP protocols on two network devices.
The header also contains a sequence number that is used to ensure the packets are received in the
correct order. The packets are not numbered, but rather the octets the packets contain are. If there are
100 octets of data in each packet, the first packet is numbered 0, the second 100, the third 200, etc.
To insure that the data in a packet is received uncorrupted, TCP adds the binary value of all the octets
in the packet and writes the sum in the checksum field. The receiving TCP recalculates the checksum
and if the numbers are different, the packet is dropped.
50
Page 51

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 5-13. TCP Packet Header
When packets have been successfully received, TCP sends an acknowledgement. This is simply a
packet that has the acknowledgement number field filled in.
An acknowledgement number of 1000 indicates that all of the data up to octet 1000 has been received.
If the transmitting TCP does not receive an acknowledgement in a reasonable amount of time, the data
is resent.
The window field controls the amount of data being sent at any one time. It would require too much
time and overhead to acknowledge each packet received. Each end of the TCP connection declares how
much data it is able to receive at any one time by writing this number of octets in the window field.
The transmitting TCP decrements the number in the window field and when it reaches zero, the
transmitting TCP stops sending data. When the receiving TCP can accept more data, it increases the
number in the window field. In practice, a single packet can acknowledge the receipt of data and give
permission for more data to be sent.
IP
TCP sends its packets to IP with the source and destination IP addresses. IP is only concerned with
these IP addresses. It is not concerned with the contents of the packet or the TCP header.
IP finds a route for the packet to get to the other end of the TCP connection. IP adds its own header to
the packet to accomplish this.
The IP header contains the source and destination addresses, the protocol number, and another
checksum.
The protocol number tells the receiving IP which protocol to give the packet to. Although most IP traffic
uses TCP, other protocols can be used (such as UDP).
The checksum is used by the receiving IP in the same way as the TCP checksum.
51
Page 52

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 5-14. IP Packet Header
The flags and fragment offset are used to keep track of packets that must be divided among several
smaller packets to cross networks for which they are too large.
The Time-to-Live (TTL) is the number of gateways the packet is allowed to cross between the source and
destination. This number is decremented by one when the packet crosses a gateway and when the TTL
reaches zero, the packet is dropped. This helps reduce network traffic if a loop develops.
Ethernet
Every active Ethernet device has its own Ethernet address (commonly called the MAC address) assigned
to it by the manufacturer. Ethernet uses 48 bit addresses.
The Ethernet header is 14 octets that include the source and destination MAC address and a type code.
There is no relationship between the MAC address of a network node and its IP address. There must be
a database of Ethernet addresses and their corresponding IP addresses.
Different protocol families can be in use on the same network. The type code field allows each protocol
family to have its own entry.
A checksum is calculated and when the packet is received, the checksum is recalculated. If the two
checksums are different, the packet is dropped.
Figure 5-15. Ethernet Packet Header
52
Page 53

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
When a packet is received, the headers are removed. The Ethernet Network Interface Card (NIC)
removes the Ethernet header and checks the checksum. It then looks at the type code. If the type code
is for IP, the packet is given to IP. IP then removes the IP header and looks at its protocol field. If the
protocol field is TCP, the packet is sent to TCP. TCP then looks at the sequence number and uses this
number and other data from the headers to reassemble the data into the original file.
TCP and UDP Well-Known Ports
Application protocols run ‘on top of’ TCP/IP. When an application wants to send data or a message, it
gives the data to TCP. Because TCP and IP take care of the networking details, the application can look
at the network connection as a simple data stream.
To transfer a file across a network using the File Transfer Protocol (FTP), a connection must first be
established. The computer requesting the file transfer must connect specifically to the FTP server on
the computer that has the file.
This is accomplished using sockets. A socket is a pair of TCP port numbers used to establish a
connection from one computer to another. TCP uses these port numbers to keep track of connections.
Specific port numbers are assigned to applications that wait for requests. These port numbers are
referred to as ‘well-known’ ports.
TCP will open a connection to the FTP server using some random port number, 1234 for example, on
the local computer. TCP will specify port 21 for the FTP server. Port 21 is the well-known port number
for FTP servers. Note that there are two different FTP programs running in this example – an FTP client
that requests the file to be transferred, and an FTP server that sends the file to the FTP client. The FTP
server accepts commands from the client, so the FTP client must know how to connect to the server
(must know the TCP port number) in order to send commands. The FTP Server can use any TCP port
number to send the file, so long as it is sent as part of the connection setup.
A TCP connection is then described by a set of four numbers – the IP address and TCP port number for
the local computer, and the IP address and TCP port number for the remote computer. The IP address
is in the IP header and the TCP port number is in the TCP header.
No two TCP connection can have the same set of numbers, but only one number needs to be different.
It is possible, for example, for two users to send files to the same destination at the same time. This
could give the following connection numbers:
Internet addresses TCP ports
Connection 1 10.42.73.23, 10.128.12.1 1234, 21
Connection 2 10.42.73.23, 10.128.12.1 1235, 21
The same computers are making the connections, so the IP addresses are the same. Both computers
are using the same well-known TCP port for the FTP server. The local FTP clients are using different
TCP port numbers.
FTP transfers actually involve two different connections. The connection begins by the FTP sending
commands to send a particular file. Once the commands are sent, a second connection is opened for
the actual data transfer. Although it is possible to send data on the same connection, it is very
convenient for the FTP client to be able to continue to send commands (such as ‘stop sending this file’).
UDP and ICMP
There are many applications that do not require long messages that cannot fit into a single packet.
Looking up computer names is an example. Users wanting to make connections to other computers will
usually use a name rather than the computer’s IP or MAC address. The user’s computer must be able
53
Page 54

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
to determine the remote computer’s address before a connection can be made. A designated computer
on the network will contain a database of computer names and their corresponding IP and MAC
addresses. The user’s computer will send a query to the name database computer, and the database
computer will send a response. Both the query and the response are very short. There is no need to
divide the query or response between multiple packets, so the complexity of TCP is not required. If
there is no response to the query after a period of time, the query can simply be resent.
The User Datagram Protocol (UDP) is designed for communications that do not require division among
multiple packets and subsequent reassembly. UDP does not keep track of what is sent.
UDP uses port numbers in a way that is directly analogous to TCP. There are well-known UDP port
numbers for servers that use UDP.
Figure 5-16. Ethernet Packet Header
The UDP header is shorter than a TCP header. UDP also uses a checksum to verify that data is received
uncorrupted.
The Internet Control Message Protocol (ICMP) is also a simplified protocol used for error messages and
messages used by TCP/IP. ICMP, like UDP, processes messages that will fit into a single packet. ICMP
does not, however use ports because its messages are processed by the network software.
The Domain Name System
Computer users usually prefer to use text names for computers they may want to open a connection
with. Computers themselves, require 32 bit IP addresses. Somewhere, a database of network devices’
text names and their corresponding IP addresses must be maintained.
The Domain Name System (DNS) is used to map names to IP addresses throughout the Internet and
has been adapted for use within intranets.
For two DNS servers to communicate across different subnets, the DNS Relay of the DES-3326 must
be used. The DNS servers are identified by IP addresses.
Mapping Domain Names to Addresses
Name-to-address translation is performed by a program called a Name server. The client program is
called a Name resolver. A Name resolver may need to contact several Name servers to translate a name
to an address.
The Domain Name System (DNS) servers are organized in a somewhat hierarchical fashion. A single
server often holds names for a single network, which is connected to a root DNS server – usually
maintained by an ISP.
54
Page 55

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Domain Name Resolution
The domain name system can be used by contacting the name servers one at a time, or by asking the
domain name system to do the complete name translation. The client makes a query containing the
name, the type of answer required, and a code specifying whether the domain name system should do
the entire name translation, or simply return the address of the next DNS server if the server receiving
the query cannot resolve the name.
When a DNS server receives a query, it checks to see if the name is in its subdomain. If it is, the server
translates the name and appends the answer to the query, and sends it back to the client. If the DNS
server cannot translate the name, it determines what type of name resolution the client requested. A
complete translation is called recursive resolution and requires the server to contact other DNS servers
until the name is resolved. Iterative resolution specifies that if the DNS server cannot supply an
answer, it returns the address of the next DNS server the client should contact.
Each client must be able to contact at least one DNS server, and each DNS server must be able to
contact at least one root server.
The address of the machine that supplies domain name service is often supplied by a DHCP or BOOTP
server, or can be entered manually and configured into the operating system at startup.
DHCP Servers
The Dynamic Host Configuration Protocol (DHCP) is used to dynamically assign a TCP/IP network
configuration to network devices and computers on the network. It also ensures that IP address
conflicts do not occur.
IP addresses are assigned from a pool of free addresses. Each IP address assigned has a ‘lease’ and a
‘lease expiration period’. The lease must be periodically renewed. If the lease is expires, the IP address
is returned to the pool of available IP addresses.
Usually, it is a network policy to assign the same IP address to a given network device or computer
each time.
If the IP address lease expires, the network device sends a message to the DHCP server requesting a
lease renewal. The DHCP server can send an acknowledgement containing a new lease and updated
configuration information.
If an IP address lease cannot be renewed, the network device or computer sends a request to all local
DHCP servers attempting to renew the lease. If the DHCP returns a negative acknowledgement, the
network device must release its TCP/IP configuration and reinitialize.
When a new TCP/IP configuration is received from a DHCP server, the network device checks for a
possible IP address conflict by sending an Address Resolution Protocol (ARP) request that contains its
new IP address.
For two DHCP servers to communicate across different subnets, the BOOTP/DHCP Relay of the
DES-3326 must be used. The DHCP servers are identified by IP addresses.
IP Routing
IP handles the task of determining how packets will get from their source to their destination. This
process is referred to as routing.
55
Page 56

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
For IP to work, the local system must be attached to a network. It is safe to assume that any system on
this network can send packets to any other system, but when packets must cross other networks to
reach a destination on a remote network, these packets must be handled by gateways (also called
routers).
Gateways connect a network with one or more other networks. Gateways can be a computer with two
network interfaces or a specialized device with multiple network interfaces. The device is designed to
forward packets from one network to another.
IP routing is based on the network address of the destination IP address. Each computer has a table of
network addresses. For each network address, a corresponding gateway is listed. This is the gateway to
use to communicate with that network. The gateway does not have to be directly connected to the
remote network, it simply needs to be the first place to go on the way to the remote network.
Before a local computer sends a packet, it first determines whether the destination address is on the
local network. If it is, the packet can be sent directly to the remote device. If it is not, the local computer
looks for the network address of the destination and the corresponding gateway address. The packet is
then sent to the gateway leading to the remote network. There is often only one gateway on a network.
A single gateway is usually defined as a default gateway, if that gateway connects the local network to a
backbone network or to the Internet. This default gateway is also used whenever no specific route is
found for a packet, or when there are several gateways on a network.
Local computers can use default gateways, but the gateways themselves need a more complete routing
table to be able to forward packets correctly. A protocol is required for the gateways to be able to
communicate between themselves and to keep their routing tables updated.
Packet Fragmentation and Reassembly
TCP/IP can be used with many different types of networks, but not all network types can handle the
same length packets.
When IP is transmitting large files, large packets are much more efficient than small ones. It is
preferable to use the largest possible packet size, but still be able to cross networks that require smaller
packets.
To do this, IP can ‘negotiate’ packet size between the local and remote ends of a connection. When an IP
connection is first made, the IPs at both ends of the connection state the largest packet they can
handle. The smaller of the two is selected.
When an IP connection crosses multiple networks, it is possible that one of the intermediate networks
has a smaller packet size limit than the local or remote network. IP is not able to determine the
maximum packet size across all of the networks that may make up the route for a connection. IP has,
therefore, a method to divide packets into multiple, smaller packets to cross such networks. This
division of large packets into smaller packets is referred to as fragmentation.
A field in the TCP header indicates that a packet has been fragmented, and other information aids in
the reassembly of the packets into the original data.
Gateways that connect networks of different packet size limits split the large packets into smaller ones
and forward the smaller packets on their attached networks.
56
Page 57

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
ARP
The Address Resolution Protocol (ARP) determines the MAC address and IP address correspondence for
a network device.
A local computer will maintain an ARP cache that is a table of MAC addresses and the corresponding IP
addresses. Before a connection with another computer is made, the local computer first checks its ARP
cache to determine whether the remote computer has an entry. If it does, the local computer reads the
remote computer’s MAC address and writes it into the destination field of the packets to be sent.
If the remote computer does not have an ARP cache entry, the local computer must send an ARP
request and wait for a reply.
When the local computer receives the ARP reply packet, the local ARP reads the IP MAC address pair,
and then checks the ARP cache for this entry. If there is an entry, it is updated with the new
information. If there is no entry, a new entry is made.
There are two possible cases when an ARP packet is received by a local computer. First, the local
computer is the target of the request. If it is, the local ARP replies by sending its MAC IP address pair
back to the requesting system. Second, if the local computer is not the target of the request, the packet
is dropped.
Multicasting
Multicasting is a group of protocols and tools that enable a single source point to send packets to
groups of multiple destination points with persistent connections that last for some amount of time.
The main advantage to multicasting is a decrease in the network load compared to broadcasting.
Multicast Groups
Class D IP addresses are assigned to a group of network devices that comprise a multicast group. The
four most significant four bits of a Class D address are set to “1110”. The following 28 bits is referred
to as the ‘multicast group ID’. Some of the range of Class D addresses are registered with the Internet
Assigned Numbers Authority (IANA) for special purposes. For example, the block of multicast addresses
ranging from 224.0.0.1 to 224.0.0.225 is reserved for use by routing protocols and some other low-level
topology discovery and maintenance protocols.
Figure 5-17. Class D Multicast Address
Some of the reserved IP multicast addresses are as follows:
Address Assignment
224.0.0.0
224.0.0.1
Base Address (reserved)
All Systems on this subnet
57
Page 58

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
224.0.0.2
224.0.0.3
224.0.0.4
224.0.0.5
224.0.0.6
224.0.0.7
224.0.0.8
224.0.0.9
224.0.0.10
224.0.0.11
224.0.0.12
224.0.0.13
224.0.0.14
224.0.0.15
All Routers on this subnet
Unassigned
DVMRP Routers
OSPF IGP Routers
OSPF IGP Designated Routers
ST Routers
ST Hosts
All RIP2 Routers
All IGRP Routers
Mobile Agents
DHCP Servers and Relay Agents
All PIM Routers
RSVP Encapsulation
All CBT Routers
224.0.0.16
224.0.0.17
224.0.0.18
224.0.0.19
Designated Sbm
All Sbms
VRRP
Unassigned
through
224.0.0.225
224.0.0.21
DVMRP on MOSPF
Table 5-10. Reserved Multicast Address Assignment
Internet Group Management Protocol (IGMP)
End users that want to receive multicast packets must be able to inform nearby routers that they want
to become a multicast group member of the group these packets are being sent to. The Internet Group
Management Protocol (IGMP) is used by multicast routers to maintain multicast group membership.
IGMP is also used to coordinate between multiple multicast routers that may be present on a network
by electing one of the multicast routers as the ‘querier’. This router then keep track of the membership
of multicast groups that have active members on the network. IGMP is used to determine whether the
router should forward multicast packets it receives to the subnetworks it is attached to or not. A
multicast router that has received a multicast packet will check to determine if there is at least one
member of a multicast group that has requested to receive multicast packets from this source. If there
is one member, the packet is forwarded. If there are no members, the packet is dropped.
58
Page 59

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
IGMP Versions 1 and 2
Users that want to receive multicast packets need to be able to join and leave multicast groups. This is
accomplished using IGMP.
Figure 5-18. IGMP Message Format
The IGMP Type codes are shown below:
Type Meaning
0x11
0x11 Specific Group Membership Query (if Group Address
0x16 Membership Report (version 2)
Membership Query (if Group Address is 0.0.0.0)
is Present)
0x17 Leave a Group (version 2)
0x12 Membership Report (version 1)
Table 5-11. IGMP Type Codes
Multicast routers use IGMP to manage multicast group memberships:
• An IGMP “report” is sent by a user’s computer to join a group
• IGMP version 1 does not have an explicit ‘leave’ message. Group members have an expiration
timer, and if this timer expires before a query response is returned, the member is dropped from
the group.
• IGMP version 2 introduces an explicit “leave” report. When a user wants to leave a group, this
report is sent to the multicast router (for IGMP version 2).
• Multicast routers send IGMP queries (to the all-hosts group address: 224.0.0.1) periodically to
see whether any group members exist on their subnetworks. If there is no response from a
particular group, the router assumes that there are no group members on the network, and
multicast packets are not forwarded.
The TTL field of query messages is set to 1 so that the queries do not get forwarded to other
subnetworks.
IGMP version 2 introduces a few extensions to IGMP version 1 such as, the election of a single
multicast querier for each network, explicit ‘leave’ reports, and queries that are specific to a particular
multicast group.
The router with the lowest IP address is elected as the querier. The explicit group leave message is
added to decrease latency, and routers can ask for membership reports from a particular multicast
group ID.
59
Page 60

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
The transition states a host will go through to join or leave a multicast group are shown in the diagram
below.
Figure 5-19. IGMP State Transitions
Multicast Routing Algorithms
An algorithm is not a program. An algorithm is a statement of how a problem can be solved. A program is
written to implement an algorithm.
Multicast packets are delivered by constructing multicast trees where the multicast router is the trunk,
the branches are the various subnetworks that may be present, and the leaves are end recipients of the
multicast packets. Several algorithms have been developed to construct these trees and to prune
branches that have no active mulitcast group members.
Flooding
The simplest algorithm for the delivery of multicast packets is for the multicast router to forward a
multicast packet to all interfaces. This is referred to as flooding. An equally simple refinement of
flooding is to have the router check to determine if a given multicast packet has been received before (in
a certain amount of time). If it has, then the packet does not need to be forwarded at all and can be
dropped. If the packet is being received for the first time, it should be flooded to all interfaces, except
the interface on which it was received. This will ensure that all routers on the network will receive at
least one copy of the multicast packet.
There are some obvious disadvantages to this simple algorithm. Flooding duplicates a lot of packets
and uses a lot of network bandwidth. A multicast router must also keep a record of the multicast
packets it has received (for a period of time) to determine if a given packet has been previously received.
So flooding uses a lot of router memory.
Multicast Spanning Trees
A multicast delivery tree that spans the entire network with a single active link between routers (or
subnetwork) is called a multicast spanning tree. Links (or branches) are chosen such that there is only
one active path between any two routers. When a router receives a multicast packet, it forwards the
60
Page 61

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
packet on all links except the one on which it was received. This guarantees that all routers in the
network will receive a copy of the packet. The only information the router needs to store is whether a
link is a part of the spanning tree (leads to a router) or not.
Multicast spanning trees do not use group membership information when deciding to forward or drop a
given multicast packet.
Reverse Path Broadcasting (RPB)
The Reverse Path Broadcasting (RPB) algorithm is an enhancement of the multicast spanning tree
algorithm. RPB constructs a spanning tree for each multicast source. When the router receives a
multicast packet, it then checks to determine if the packet was received on the shortest path back from
the router to the source. If the packet was received on the shortest path back to the source, the packet
is forwarded on all links except the link on which the packet was received. If the packet was not
received on the shortest link back to the source, the packet is dropped.
If a link-state routing protocol is in use, RPB on a local router can determine if the path from the
source through the local router to an immediately neighboring router. If it is not, the packet will be
dropped at the next router and the packet should not be forwarded.
If a distance-vector routing protocol is in use, a neighboring router can either advertise its previous hop
for the source as part of its routing update messages. This will ‘poison-reverse’ the route (or have the
local router prune the branch from the multicast source to the neighboring router because the
neighboring router has a better route from the source to the next router or subnetwork).
Since multicast packets are forwarded through the shortest route between source and destination, RPB
is fast. A given router also does not need information about the entire spanning tree, nor does it need a
mechanism to stop the forwarding of packets.
RPB does not use multicast group membership information in its forwarding decisions.
Reverse Path Multicasting (RPM)
Reverse Path Multicasting (RPM) introduces an enhancement to RPB – an explicit method to prune
branches of the spanning tree that have on active multicast group members for the source. RPM
constructs a tree that spans only subnetworks with multicast group member and routers along the
shortest path between the source and the destinations.
When a multicast router receives a multicast packet, it is forwarded using the RPB constructed
spanning tree. Subsequent routers in the tree that have no active path to another router are referred to
as leaf routers. If the multicast packet if forwarded to a leaf router that has no active multicast group
members for the source, the leaf router will send a prune message to the previous router. This will
remove the leaf router’s branch from the spanning tree, and no more multicast packets (from that
source) will be forwarded to it. Prune messages have a TTL equal to one, so they can be sent only one
hop (one router) back toward the source. If the previous router receives prune messages from all of its
branch and leaf routers, the previous router will then send it’s own prune message back one router
toward the multicast source, and the process will repeat. In this way, multicast group membership
information can be used to prune the spanning tree between a given multicast source and the
corresponding multicast group.
Since the membership of any given multicast group can change and the network topology can also
change, RPM periodically removes all of the prune information it has gathered from its memory, and the
entire process repeats. This gives all subsequent routers on the network a chance to receive multicast
packets from all multicast sources on the network. It also gives all users a chance to join a given
multicast group.
61
Page 62

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Multicast Routing Protocols
This section contains an overview of two multicast routing protocols – Distance Vector Multicast
Routing Protocol (DVMRP), and Protocol Independent Multicast-Dense Mode
(PIM-DM). The most commonly used routing protocol (not a multicast routing protocol), the Routing
Information Protocol, is discussed in a later section.
Distance Vector Multicast Routing Protocol (DVMRP)
The Distance Vector Multicast Routing Protocol (DVMRP) was derived from the Routing Information
Protocol (RIP) with the introduction of multicast delivery trees constructed from information about the
‘distance’ from the local router back toward the multicast source. DVMRP uses an RPM algorithm to
construct its multicast delivery trees.
The first multicast packet received by a multicast router using DVMRP is flooded to all interfaces except
the one on which the packet was received. Subsequent prune messages are used to prune branches of
the delivery tree that are either not on the shortest path back to the multicast source, or that have no
active multicast group members. A ‘graft’ message is added that allows a previously pruned branch of
the multicast delivery tree to be reactivated. This allows for lower latency when a leaf router adds a new
member to a multicast membership group. Graft messages are forwarded one hop (one router) back at a
time toward a multicast source until they reach a router that is on an active branch of the multicast
delivery tree.
If there is more than one multicast router on a network, the one that has the shortest path back to the
multicast source is elected to forward multicast packets from that source. All other routers will discard
multicast packets from that source. If two multicast routers on a network have the same distance back
to a multicast source, the router with the lowest IP address is elected.
DVMRP also supports tunnel interfaces, where two multicast routers are connected through a router
that cannot process multicast packets. This allows multicast packets to cross networks with routers
that are not multicast-aware.
Protocol-Independent Multicast – Dense Mode
There are two protocols in Protocol Independent Multicast (PIM), Protocol Independent Multicast-Dense
Mode (PIM-DM) which is used when the multicast destinations are closely spaced, and Protocol
Independent Multicast-Sparse Mode (PIM-SM) which is used when the multicast destinations are
spaced further apart. PIM-DM is most commonly implemented in an intranetwork (LAN) where the
distance between users is minimal.
Routing Protocols
Routing Information Protocol (RIP)
The Routing Information Protocol is a distance-vector routing protocol. There are two types of network
devices running RIP – active and passive. Active devices advertise their routes to others through RIP
messages, while passive devices listen to these messages. Both active and passive routers update their
routing tables based upon RIP messages that active routers exchange. Only routers can run RIP in the
active mode.
62
Page 63

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Every 30 seconds, a router running RIP broadcasts a routing update containing a set of pairs of
network addresses and a distance (represented by the number of hops or routers between the
advertising router and the remote network). So, the vector is the network address and the distance is
measured by the number of routers between the local router and the remote network.
RIP measures distance by an integer count of the number of hops from one network to another. A
router is one hop from a directly connected network, two hops from a network that can be reached
through a router, etc. The more routers between a source and a destination, the greater the RIP
distance (or hop count).
There are a few rules to the routing table update process that help to improve performance and
stability. A router will not replace a route with a newly learned one if the new route has the same hop
count (sometimes referred to as ‘cost’). So learned routes are retained until a new route with a lower
hop count is learned.
When learned routes are entered into the routing table, a timer is started. This timer is restarted every
time this route is advertised. If the route is not advertised for a period of time (usually 180 seconds),
the route is removed from the routing table.
RIP does not have an explicit method to detect routing loops. Many RIP implementations include an
authorization mechanism (a password) to prevent a router from learning erroneous routes from
unauthorized routers.
To maximize stability, the hop count RIP uses to measure distance must have a low maximum value.
Infinity (that is, the network is unreachable) is defined as 16 hops. In other words, if a network is more
than 16 routers from the source, the local router will consider the network unreachable.
RIP can also be slow to converge (to remove inconsistent, unreachable or looped routes from the routing
table) because RIP messages propagate relatively slowly through a network.
Slow convergence can be solved by using split horizon update, where a router does not propagate
information about a route back to the interface on which it was received. This reduces the probability of
forming transient routing loops.
Hold down can be used to force a router to ignore new route updates for a period of time (usually 60
seconds) after a new route update has been received. This allows all routers on the network to receive
the message.
A router can ‘poison reverse’ a route by adding an infinite (16) hop count to a route’s advertisement.
This is usually used in conjunction with triggered updates, which force a router to send an immediate
broadcast when an update of an unreachable network is received.
RIP Version 1 Message Format
There are two types of RIP messages: routing information messages and information requests. The
same format is used by both types.
63
Page 64

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 5-20. RIP v.1 Message Format
64
Page 65

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
The COMMAND field specifies an operation according the following table:
Command Meaning
1
2
3
4
5
9
10
11
Request for partial or full routing information
Response containing network-distance pairs from
sender’s routing table
Turn on trace mode (obsolete)
Turn off trace mode (obsolete)
Reserved for Sun Microsystem’s internal use
Update Request
Update Response
Update Acknowledgement
Table 5-12. RIP Command Codes
The field VERSION contains the protocol version number (1 in this case), and is used by the receiver to
verify which version of RIP the packet was sent from.
RIP 1 Message
RIP is not limited to TCP/IP. Its address format can support up to 14 octets (when using IP, the
remaining 10 octets must be zeros). Other network protocol suites can be specified in the Family of
Source Network field (IP has a value of 2). This will determine how the address field is interpreted.
RIP specifies that the IP address 0.0.0.0 denotes a default route.
The distances, measured in router hops are entered in the Distance to Source Network, and Distance to
Destination Network fields.
RIP 1 Route Interpretation
RIP was designed to be used with classed address schemes, and does not include an explicit subnet
mask. An extension to version 1 does allow routers to exchange subnetted addresses, but only if the
subnet mask used by the network is the same as the subnet mask used by the address. This means the
RIP version 1 cannot be used to propagate classless addresses.
Routers running RIP version 1 must send different update messages for each IP interface to which it is
connected. Interfaces that use the same subnet mask as the router’s network can contain subnetted
routes, other interfaces cannot. The router will then advertise only a single route to the network.
RIP Version 2 Extensions
RIP version 2 includes an explicit subnet mask entry, so RIP version 2 can be used to propagate
variable length subnet addresses or CIDR classless addresses. RIP version 2 also adds an explicit next
hop entry, which speeds convergence and helps prevent the formation of routing loops.
RIP2 Message Format
The message format used with RIP2 is an extension of the RIP1 format:
65
Page 66

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 5-21. RIP Message Format
RIP version 2 also adds a 16-bit route tag that is retained and sent with router updates. It can be used
to identify the origin of the route.
Because the version number in RIP2 occupies the same octet as in RIP1, both versions of the protocols
can be used on a given router simultaneously without interference.
Open Shortest Path First (OSPF)
The Open Shortest Path First (OSPF) routing protocol uses a link-state algorithm to determine routes to
network destinations. A “link” is an interface on a router and the “state” is a description of that
interface and its relationship to neighboring routers. The state contains information such as the IP
address, subnet mask, type of network the interface is attached to, other routers attached to the
network, etc. The collection of link-states is then collected in a link-state database that is maintained
by routers running OSPF.
OSPF specifies how routers will communicate to maintain their link-state database and defines several
concepts about the topology of networks that use OSPF.
To limit the extent of link-state update traffic between routers, OSPF defines the concept of Area. All
routers within an area share the exact same link-state database, and a change to this database on one
router triggers an update to the link-state database of all other routers in that area. Routers that have
interfaces connected to more than one area are called Border Routers and take the responsibility of
distributing routing information between areas.
One area is defined as Area 0 or the Backbone. This area is central to the rest of the network in that all
other areas have a connection (through a router) to the backbone. Only routers have connections to the
backbone and OSPF is structured such that routing information changes in other areas will be
introduced into the backbone, and then propagated to the rest of the network.
When constructing a network to use OSPF, it is generally advisable to begin with the backbone (area 0)
and work outward.
66
Page 67

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
The Link-State Algorithm
An OSPF router uses a link-state algorithm to build a shortest path tree to all destinations known to
the router. The following is a simplified description of the algorithm’s steps:
1. When OSPF is started, or when a change in the routing information changes, the router
generates a link-state advertisement. This advertisement is a specially formatted packet
that contains information about all the link-states on the router.
2. This link-state advertisement is flooded to all router in the area. Each router that
receives the link-state advertisement will store the advertisement and then forward a
copy to other routers.
3. When the link-state database of each router is updated, the individual routers will
calculate a Shortest Path Tree to all destinations − with the individual router as the root.
The IP routing table will then be made up of the destination address, associated cost,
and the address of the next hop to reach each destination.
4. Once the link-state databases are updated, Shortest Path Trees calculated, and the IP
routing tables written − if there are no subsequent changes in the OSPF network (such
as a network link going down) there is very little OSPF traffic.
The Shortest Path Algorithm
The Shortest Path to a destination is calculated using the Dijkstra algorithm. Each router is places at
the root of a tree and then calculates the shortest path to each destination based on the cumulative
cost to reach that destination over multiple possible routes. Each router will then have its own
Shortest Path Tree (from the perspective of its location in the network area) even though every router in
the area will have and use the exact same link-state database.
The following sections describe the information used to build the Shortest Path Tree.
OSPF Cost
Each OSPF interface has an associated cost (also called “metric”) that is representative of the overhead
required to send packets over that interface. This cost is inversely proportional to the bandwidth of the
interface (i.e. a higher bandwidth interface has a lower cost). There is then a higher cost (and longer
time delays) in sending packets over a 56 Kbps dial-up connection than over a 10 Mbps Ethernet
connection. The formula used to calculate the OSPF cost is as follows:
Cost = 100,000,000 / bandwidth in bps
As an example, the cost of a 10 Mbps Ethernet line will be 10 and the cost to cross a 1.544 Mbps T1
line will be 64.
Shortest Path Tree
To build Router A’s shortest path tree for the network diagramed below, Router A is put at the root of
the tree and the smallest cost link to each destination network is calculated.
67
Page 68

192.128.11.0
Router C
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Router A
128.213.0.0
Router B
Router D
222.211.10.0
Figure 5-22. Constructing a Shortest Path Tree
Router A
0
128.213.0.0
10
10
Router B
5
5
192.213.11.0
Router D
10
222.211.10.0
Figure 5-23. Constructing a Shortest Path Tree
Router C
10
The diagram above shows the network from the viewpoint of Router A. Router A can reach
192.213.11.0 through Router B with a cost of 10+5=15. Router A can reach 222.211.10.0 through
Router C with a cost of 10+10=20. Router A can also reach 222.211.10.0 through Router B and Router
D with a cost of 10+5+10=25, but the cost is higher than the route through Router C. This higher-cost
route will not be included in the Router A’s shortest path tree. The resulting tree will look like this:
68
Page 69

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
128.213.0.0
Router A
0
10
10
Router B
5
192.213.11.0
Figure 5-24. Constructing a Shortest Path Tree - Completed
Note that this shortest path tree is only from the viewpoint of Router A. The cost of the link from Router
B to Router A, for instance is not important to constructing Router A’s shortest path tree, but is very
important when Router B is constructing its shortest path tree.
Note also that directly connected networks are reached at a cost of 0, while other networks are reached
at the cost calculated in the shortest path tree.
Router A can now build its routing table using the network addresses and costs calculated in building
the above shortest path tree.
Router C
10
222.211.10.0
Areas and Border Routers
OSPF link-state updates are forwarded to other routers by flooding to all routers on the network. OSPF
uses the concept of areas to define where on the network routers that need to receive particular linkstate updates are located. This helps ensure that routing updates are not flooded throughout the entire
network and to reduce the amount of bandwidth consumed by updating the various router’s routing
tables.
Areas establish boundaries beyond which link-state updates do not need to be flooded. So the exchange
of link-state updates and the calculation of the shortest path tree are limited to the area that the router
is connected to.
Routers that have connections to more than one area are called Border Routers (BR). The Border
Routers have the responsibility of distributing necessary routing information and changes between
areas.
Areas are specific to the router interface. A router that has all of its interfaces in the same area is called
an Internal Router. A router that has interfaces in multiple areas is called a Border Router. Routers
that act as gateways to other networks (possibly using other routing protocols) are called Autonomous
System Border Routers (ASBRs).
Link-State Packets
There are different types of link-state packets, four are illustrated below:
• Router Link-State Updates − these describe a router’s links to destinations within an
area.
69
Page 70

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
• Summary Link-State Updates – issued by Border Routers and describe links to networks
outside the area but within the Autonomous System (AS).
• Network Link-State Updates – issued by multi-access areas that have more than one
attached router. One router is elected as the Designated Router (DR) and this router
issues the network link-state updates describing every router on the segment.
• External Link-State Updates – issued by an Autonomous System Border Router and
describes routes to destinations outside the AS or a default route to the outside AS.
The format of these link-state updates is described in more detail below.
Router link-state updates are flooded to all routers in the current area. These updates describe the
destinations reachable through all of the router’s interfaces.
Summary link-state updates are generated by Border Routers to distribute routing information about
other networks within the AS. Normally, all Summary link-state updates are forwarded to the backbone
(area 0) and are then forwarded to all other areas in the network. Border Routers also have the
responsibility of distributing routing information from the Autonomous System Border Router in order
for routers in the network to get and maintain routes to other Autonomous Systems.
Network link-state updates are generated by a router elected as the Designated Router on a multiaccess segment (with more than one attached router). These updates describe all of the routers on the
segment and their network connections.
External link-state updates carry routing information to networks outside the Autonomous System. The
Autonomous System Border Router is responsible for generating and distributing these updates.
OSPF Authentication
OSPF packets can be authenticated as coming from trusted routers by the use of predefined passwords.
The default for routers is to use not authentication.
There are two other authentication methods − simple password authentication (key) and Message
Digest authentication (MD-5).
Simple Password Authentication
A password (or key) can be configured on a per-area basis. Routers in the same area that participate in
the routing domain must be configured with the same key. This method is possibly vulnerable to
passive attacks where a link analyzer is used to obtain the password.
Message Digest Authentication (MD-5)
MD-5 authentication is a cryptographic method. A key and a key-ID are configured on each router. The
router then uses an algorithm to generate a mathematical “message digest” that is derived from the
OSPF packet, the key and the key-ID. This message digest (a number) is then appended to the packet.
The key is not exchanged over the wire and a non-decreasing sequence number is included to prevent
replay attacks.
The Backbone and Area 0
OSPF limits the number of link-state updates required between routers by defining areas within which
a given router operates. When more than one area is configured, one area is designated as area 0 − also
called the backbone.
70
Page 71

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
The backbone is at the center of all other areas − all areas of the network have a physical (or virtual)
connection to the backbone through a router. OSPF allows routing information to be distributed by
forwarding it into area 0, from which the information can be forwarded to all other areas (and all other
routers) on the network.
In situations where an area is required, but is not possible to provide a physical connection to the
backbone, a virtual link can be configured.
Virtual Links
Virtual links accomplish two purposes:
1. Linking an area that does not have a physical connection to the backbone.
2. Patching the backbone in case there is a discontinuity in area 0.
Areas Not Physically Connected to Area 0
All areas of an OSPF network should have a physical connection to the backbone, but is some cases it
is not possible to physically connect a remote area to the backbone. In these cases, a virtual link is
configured to connect the remote area to the backbone. A virtual path is a logical path between two
border routers that have a common area, with one border router connected to the backbone.
Partitioning the Backbone
OSPF also allows virtual links to be configured to connect the parts of the backbone that are
discontinuous. This is the equivalent to linking different area 0s together using a logical path between
each area 0. Virtual links can also be added for redundancy to protect against a router failure. A virtual
link is configured between two border routers that both have a connection to their respective area 0s.
Neighbors
Routers that are connected to the same area or segment become neighbors in that area. Neighbors are
elected via the Hello protocol. IP multicast is used to send out Hello packets to other routers on the
segment. Routers become neighbors when they see themselves listed in a Hello packet sent by another
router on the same segment. In this way, two-way communication is guaranteed to be possible between
any two neighbor routers.
Any two routers must meet the following conditions before the become neighbors:
• Area ID − two routers having a common segment − their interfaces have to belong to the
same area on that segment. Of course, the interfaces should belong to the same subnet
and have the same subnet mask.
• Authentication − OSPF allows for the configuration of a password for a specific area.
Two routers on the same segment and belonging to the same area must also have the
same OSPF password before they can become neighbors.
• Hello and Dead Intervals − The Hello interval specifies the length of time, in seconds,
between the hello packets that a router sends on an OSPF interface. The dead interval is
the number of seconds that a router’s Hello packets have not been seen before its
neighbors declare the OSPF router down. OSPF routers exchange Hello packets on each
segment in order to acknowledge each other’s existence on a segment and to elect a
Designated Router on multi-access segments. OSPF requires these intervals to be exactly
the same between any two neighbors. If any of these intervals are different, these routers
will not become neighbors on a particular segment.
71
Page 72

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
• Stub Area Flag − any two routers also have to have the same stub area flag in their Hello
packets in order to become neighbors.
Adjacencies
Adjacent routers go beyond the simple Hello exchange and participate in the link-state database
exchange process. OSPF elects one router as the Designated Router (DR) and a second router as the
Backup Designated Router (BDR) on each multi-access segment (the BDR is a backup in case of a DR
failure). All other routers on the segment will then contact the DR for link-state database updates and
exchanges. This limits the bandwidth required for link-state database updates.
Designated Router Election
The election of the DR and BDR is accomplished using the Hello protocol. The router with the highest
OSPF priority on a given multi-access segment will be elected the DR for that segment. In case of a tie,
the router with the highest Router ID wins. The default OSPF priority is 1. A priority of zero indicates a
router that cannot be elected as the DR.
Building Adjacency
Two routers undergo a multi-step process in building the adjacency relationship. The following is a
simplified description of the steps required:
• Down − No information has been received from any router on the segment.
• Attempt − On non-broadcast multi-access networks (such as Frame Relay or X.25), this
state indicates that no recent information has been received from the neighbor. An effort
should be made to contact the neighbor by sending Hello packets at the reduced rate set
by the Poll Interval.
• Init − The interface has detected a Hello packet coming from a neighbor but bi-
directional communication has not yet been established.
• Two-way − Bi-directional communication with a neighbor has been established. The
router has seen its address in the Hello packets coming from a neighbor. At the end of
this stage the DR and BDR election would have been done. At the end of the Two-way
stage, routers will decide whether to proceed in building an adjacency or not. The
decision is based on whether one of the routers is a DR or a BDR or the link is a pointto-point or virtual link.
• Exstart − (Exchange Start) Routers establish the initial sequence number that is going to
be used in the information exchange packets. The sequence number insures that routers
always get the most recent information. One router will become the primary and the
other will become secondary. The primary router will poll the secondary for information.
• Exchange − Routers will describe their entire link-state database by sending database
description packets.
• Loading − The routers are finalizing the information exchange. Routers have link-state
request list and a link-state retransmission list. Any information that looks incomplete or
outdated will be put on the request list. Any update that is sent will be put on the
retransmission list until it gets acknowledged.
• Full − The adjacency is now complete. The neighboring routers are fully adjacent.
Adjacent routers will have the same link-state database.
72
Page 73

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Adjacencies on Point-to-Point Interfaces
OSPF Routers that are linked using point-to-point interfaces (such as serial links) will always form
adjacencies. The concepts of DR and BDR are unnecessary.
OSPF Packet Formats
All OSPF packet types begin with a standard 24-byte header and there are five packet types. The
header is described first, and each packet type is described in a subsequent section.
All OSPF packets (except for Hello packets) forward link-state advertisements. Link-State Update
packets, for example, flood advertisements throughout the OSPF routing domain.
• OSPF packet header
• Hello packet
• Database Description packet
• Link-State Request packet
• The Link-State Update packet
• Link-State Acknowledgment packet
The OSPF Packet Header
Every OSPF packet is preceded by a common 24-byte header. This header contains the information
necessary for a receiving router to determine if the packet should be accepted for further processing.
The format of the OSPP packet header is shown below:
OSPF Packet Header
Version No.
Checksum
Type
Router ID
Area ID
Authentication
Auth entication
Figure 5-25. OSPF Packet Header
Packet Length
Authentication Type
73
Page 74

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Field Description
Version No. The OSPF version number
Type The OSPF packet type. The OSPF packet types
are as follows:
Type Description
1 Hello
2 Database Description
3 Link-State Request
4 Link-State Update
5 Link-State Acknowledgment
Packet Length The length of the packet in bytes. This length
includes the 24-byte header.
Router ID The Router ID of the packet’s source.
Area ID A 32-bit number identifying the area that this
packet belongs to. All OSPF packets are
associated with a single area. Packets traversing a
virtual link are assigned the backbone Area ID of
0.0.0.0
Checksum A standard IP checksum that includes all of the
packet’s contents except for the 64-bit
authentication field.
Authentication Type The type of authentication to be used for the
packet.
Authentication A 64-bit field used by the authentication scheme.
Table 5-13. OSPF Packet Header
The Hello Packet
Hello packets are OSPF packet type 1. They are sent periodically on all interfaces, including virtual
links, in order to establish and maintain neighbor relationships. In addition, Hello Packets are
multicast on those physical networks having a multicast or broadcast capability, enabling dynamic
discovery of neighboring routers.
All routers connected to a common network must agree on certain parameters such as the Network
Mask, the Hello Interval, and the Router Dead Interval. These parameters are included in hello packets,
so that differences can inhibit the forming of neighbor relationships. A detailed explanation of the
receive processing for Hello packets, so that differences can inhibit the forming of neighbor
relationships.
74
Page 75

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
The format of the Hello packet is shown below:
Hello Packet
Version No.
Checksum Authentication Type
Hello Interval
1
Router ID
Area ID
Authentication
Authentication
Network Mask
Options Router Priority
Router Dead Interval
Designated Router
Backup Designated Router
Neighbor
Packet Length
Figure 5-26. Hello Packet
Field Description
Network Mask The network mask associated with this interface.
Options The optional capabilities supported by the router.
Hello Interval The number of seconds between this router’s Hello
packets.
Router Priority This router’s Router Priority. The Router Priority is
used in the election of the DR and BDR. If this field
is set to 0, the router is ineligible to become the DR
or the BDR.
Router Dead Interval The number of seconds that must pass before
declaring a silent router as down.
Designated Router The identity of the DR for this network, in the view of
the advertising router. The DR is identified here by
its IP interface address on the network.
Backup Designated Router The identity of the Backup Designated Router (BDR)
for this network. The BDR is identified here by its IP
interface address on the network. This field is set to
0.0.0.0 if there is no BDR.
Neighbor The Router Ids of each router from whom valid Hello
packets have been seen within the Router Dead
Interval on the network.
75
Page 76

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Table 5-14. Hello Packet
The Database Description Packet
Database Description packets are OSPF packet type 2. These packets are exchanged when an
adjacency is being initialized. They describe the contents of the topological database. Multiple packets
may be used to describe the database. For this purpose a poll-response procedure is used. One of the
routers is designated to be master, the other a slave. The master seconds Database Description packets
(polls) that are acknowledged by Database Description packets sent by the slave (responses). The
responses are linked to the polls via the packets’ DD sequence numbers.
Database Description Packet
Version No.
Reserved
Checksum
IM
2 Packet Length
Router ID
Area ID
Authentication
Authentication
MS
Reserved
DD Sequence No.
Link-State Advertisement Header ...
Authentication Type
Figure 5-27. Database Description Packet
Field Description
Options The optional capabilities supported by the router.
I – bit The Initial bit. When set to 1, this packet is the
first in the sequence of Database Description
packets.
M – bit The More bit. When set to 1, this indicates that
more Database Description packets will follow.
Options
MS – bit The Master Slave bit. When set to 1, this indicates
that the router is the master during the Database
Exchange process. A zero indicates the opposite.
DD Sequence Number User to sequence the collection of Database
Description Packets. The initial value (indicated by
the Initial bit being set) should be unique. The DD
sequence number then increments until the
complete database description has been sent.
Table 5-15. Database Description Packet
The rest of the packet consists of a list of the topological database’s pieces. Each link state
advertisement in the database is described by its link state advertisement header.
76
Page 77

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
The Link-State Request Packet
Link-State Request packets are OSPF packet type 3. After exchanging Database Description packets
with a neighboring router, a router may find that parts of its topological database are out of date. The
Link-State Request packet is used to request the pieces of the neighbor’s database that are more up to
date. Multiple Link-State Request packets may need to be used. The sending of Link-State Request
packets is the last step in bringing up an adjacency.
A router that sends a Link-State Request packet has in mind the precise instance of the database
pieces it is requesting, defined by LS sequence number, LS checksum, and LS age, although these
fields are not specified in the Link-State Request packet itself. The router may receive even more recent
instances in response.
The format of the Link-State Request packet is shown below:
Link-State Request Packet
Version No.
3
Router ID
Area ID
Checksum
Authentication
Authentication
Link-State Type
Link-State ID
Advertising Router
Packet Length
Authentication Type
Figure 5-29. Link-State Request Packet
Each advertisement requested is specified by its Link-State Type, Link-State ID, and Advertising
Router. This uniquely identifies the advertisement, but not its instance. Link-State Request packets
are understood to be requests for the most recent instance.
The Link-State Update Packet
Link-State Update packets are OSPF packet type 4. These packets implement the flooding of link-state
advertisements. Each Link-State Update packet carries a collection of link-state advertisements one
hop further from its origin. Several link-state advertisements may be included in a single packet.
Link-State Update packets are multicast on those physical networks that support multicast/broadcast.
In order to make the flooding procedure reliable, flooded advertisements are acknowledged in LinkState Acknowledgment packets. If retransmission of certain advertisements is necessary, the
retransmitted advertisements are always carried by unicast Link-State Update packets.
The format of the Link-State Update packet is shown below:
77
Page 78

Link-State Update Packet
DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Version No.
4
Router ID
Area ID
Checksum
Authentication
Authentication
Number of Advertisements
Link-State Advertisements ...
Packet Length
Authentication Type
Figure 5-30. Link-State Update Packet
The body of the Link-State Update packet consists of a list of link-state advertisements. Each
advertisement begins with a common 20-byte header, the link-state advertisement header. Otherwise,
the format of each of the five types of link-state advertisements is different.
The Link-State Acknowledgment Packet
Link-State Acknowledgment packets are OSPF packet type 5. To make the folding of link-state
advertisements reliable, flooded advertisements are explicitly acknowledged. This acknowledgment is
accomplished through the sending and receiving of Link-State Acknowledgment packets. Multiple linkstate advertisements can be acknowledged in a single Link-State Acknowledgment packet.
Depending on the state of the sending interface and the source of the advertisements being
acknowledged, a Link-State Acknowledgment packet is sent either to the multicast address
AllSPFRouters, to the multicast address AllDRouters, or as a unicast packet.
The format of this packet is similar to that of the Data Description packet. The body of both packets is
simply a list of link-state advertisement headers.
The format of the Link-State Acknowledgment packet is shown below:
Link-State Acknowledgment Packet
Version No.
5
Router ID
Area ID
Checksum
Authentication
Authentication
Link-State Advertisement Header ...
Packet Length
Authentication Type
Figure 5-31. Link-State Acknowledgement Packet
78
Page 79

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Each acknowledged link-state advertisement is described by its link-state advertisement header. It
contains all the information required to uniquely identify both the advertisement and the
advertisement’s current instance.
Link-State Advertisement Formats
There are five distinct types of link-state advertisements. Each link-state advertisement begins with a
standard 20-byte link-state advertisement header. Succeeding sections then diagram the separate linkstate advertisement types.
Each link-state advertisement describes a piece of the OSPF routing domain. Every router originates a
router links advertisement. In addition, whenever the router is elected as the Designated Router, it
originates a network links advertisement. Other types of link-state advertisements may also be
originated. The flooding algorithm is reliable, ensuring that all routers have the same collection of linkstate advertisements. The collection of advertisements is called the link-state (or topological) database.
From the link-state database, each router constructs a shortest path tree with itself as root. This yields
a routing table.
There are four types of link state advertisements, each using a common link state header. These are:
• Router Links Advertisements
• Network Links Advertisements
• Summary Link Advertisements
• Autonomous System Link Advertisements
The Link State Advertisement Header
All link state advertisements begin with a common 20-byte header. This header contains enough
information to uniquely identify the advertisements (Link State Type, Link State ID, and Advertising
Router). Multiple instances of the link state advertisement may exist in the routing domain at the same
time. It is then necessary to determine which instance is more recent. This is accomplished by
examining the link state age, link state sequence number and link state checksum fields that are also
contained in the link state advertisement header.
The format of the Link State Advertisement Header is shown below:
Link-State Advertisement Header
Link-State Age
Link-State ID
Options Link-State Type
Advertising Router
Link-State Sequence Number
Link-State Checksum
Length
Figure 5-32. Link-State Advertisement Header
79
Page 80

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Field Description
Link State Age The time is seconds since the link state advertisement was
originated.
Options The optional capabilities supported by the described portion of
the routing domain.
Link State Type The type of the link state advertisement. Each link state type
has a separate advertisement format. The link state type are as
follows:
Type Description
1 Router Links
2 Network Links
3 Summary Link (IP Network)
4 Summary Link (ASBR)
5 AS External Link
Link State ID This field identifies the portion of the internet environment that
is being described by the advertisement. The contents of this
field depend on the advertisement’s Link State Type.
Advertising Router The Router ID of the router that originated the Link State
Advertisement. For example, in network links advertisements
this field is set to the Router ID of the network’s Designated
Router.
Link State Sequence
Number
Detects old or duplicate link state advertisements. Successive
instances of a link state advertisement are given successive Link
State Sequence numbers.
Link State Checksum The Fletcher checksum of the complete contents of the link
state advertisement, including the link state advertisement
header except for the Link State Age field.
Length The length in bytes of the link state advertisement. This
includes the 20-byte link state advertisement header.
Table 5-16. Link-State Advertisement Header
Router Links Advertisements
Router links advertisements are type 1 link state advertisements. Each router in an area originates a
routers links advertisement. The advertisement describes the state and cost of the router’s links to the
area. All of the router’s links to the area must be described in a single router links advertisement.
The format of the Router Links Advertisement is shown below:
80
Page 81

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Routers Links Advertisements
Link-State Age
Link-State ID
Advertising Router
Link-State Sequence Number
Link-State Checksum
Reserved Reserved Number of Links
VBE
Link ID
Link Data
Type No. Of TOS TOS 0 Metric
TOS
TOS
0
...
0
...
Link ID
Link Data
Options Link-State Type
Length
Metric
Metric
Figure 5-33. Routers Links Advertisement
In router links advertisements, the Link State ID field is set to the router’s OSPF Router ID. The T – bit
is set in the advertisement’s Option field if and only if the router is able to calculate a separate set of
routes for each IP Type of Service (TOS). Router links advertisements are flooded throughout a single
area only.
Field Description
V – bit When set, the router is an endpoint of an active
virtual link that is using the described area as a
Transit area (V is for Virtual link endpoint).
E – bit When set, the router is an Autonomous System
(AS) boundary router (E is for External).
B – bit When set, the router is an area border router (B is
for Border).
Number of Links The number of router links described by this
advertisement. This must be the total collection of
router links to the area.
Table 5-17. Routers Links Advertisement
The following fields are used to describe each router link. Each router link is typed. The Type field
indicates the kind of link being described. It may be a link to a transit network, to another router or to
a stub network. The values of all the other fields describing a router link depend on the link’s Type. For
example, each link has an associated 32-bit data field. For links to stub networks this field specifies the
81
Page 82

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
network’s IP address mask. For other link types the Link Data specifies the router’s associated IP
interface address.
Field Description
Type A quick classification of the router link. One of the following:
Type Description
1 Point-to-point connection to another router.
2 Connection to a transit network.
3 Connection to a stub network.
4 Virtual link.
Link ID Identifies the object that this router link connects to. Value
depends on the link’s Type. When connecting to an object that
also originates a link state advertisement (i.e. another router or
a transit network) the Link ID is equal to the neighboring
advertisement’s Link State ID. This provides the key for
looking up an advertisement in the link state database.
Type Link ID
1 Neighboring router’s Router ID.
2 IP address of Designated Router.
3 IP network/subnet number.
4 Neighboring router’s Router ID
Link Data Contents again depend on the link’s Type field. For connections
to stub networks, it specifies the network’s IP address mask.
For unnumbered point-to-point connection, it specifies the
interface’s MIB-II ifIndex value. For other link types it specifies
the router’s associated IP interface address. This latter piece of
information is needed during the routing table build process,
when calculating the IP address of the next hop.
No. of TOS The number of different Type of Service (TOS) metrics given for
this link, not counting the required metric for TOS 0. If no
additional TOS metrics are given, this field should be set to 0.
TOS 0 Metric The cost of using this router link for TOS 0.
Table 5-18. Routers Links Advertisements − Continued
For each link, separate metrics may be specified for each Type of Service (TOS). The metric for TOS 0
must always be included, and was discussed above. Metrics for non-zero TOS are described below. Note
that the cost for non-zero TOS values that are not specified defaults to the TOS 0 cost. Metrics must be
listed in order of increasing TOS encoding. For example, the metric for TOS 16 must always follow the
metric for TOS 8 when both are specified.
82
Page 83

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Field Description
TOS IP Type of Service that this
metric refers to.
Metric The cost of using this
outbound router link, for
traffic of the specified TOS.
Table 5-19. Routers Links Advertisement − Continued
Network Links Advertisements
Network links advertisements are Type 2 link state advertisements. A network links advertisement is
originated for each transit network in the area. A transit network is a multi-access network that has
more than one attached router. The network links advertisement is originated by the network’s
Designated router. The advertisement describes all routers attached to the network, including the
Designated Router itself. The advertisement’s Link State ID field lists the IP interface address of the
Designated Router.
The distance form the network to all attached routers is zero, for all TOS. This is why the TOS and
metric fields need not be specified in the network links advertisement.
The format of the Network Links Advertisement is shown below:
Network Link Advertisements
Link-State Age
Link-State Sequence Number
Link-State Checksum
Options
Link-State ID
Advertising Router
Length
Network Mask
Attached Router
2
Figure 5-34. Network Link Advertisement
Field Description
Network Mask The IP address mask for the network.
Attached Router The Router Ids of each of the routers attached to the
network. Only those routers that are fully adjacent
to the Designated Router (DR) are listed. The DR
includes itself in this list.
Table 5-20. Network Link Advertisement
83
Page 84

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Summary Link Advertisements
Summary link advertisements are Type 3 and 4 link state advertisements. These advertisements are
originated by Area Border routers. A separate summary link advertisement is made for each destination
known to the router, that belongs to the Autonomous System (AS), yet is outside the area.
Type 3 link state advertisements are used when the destination is an IP network. In this case the
advertisement’s Link State ID field is an IP network number. When the destination is an AS boundary
router, a Type 4 advertisement is used, and the Link State ID field is the AS boundary router’s OSPF
Router ID. Other that the difference in the Link State ID field, the format of Type 3 and 4 link state
advertisements is identical.
Summary Link Advertisements
Link-State Age
Link-State ID
Advertising Router
Link-State Sequence Number
Link-State Checksum
Network Mask
TOS Metric
Options
Length
2
Figure 5-35. Summary Link Advertisement
For stub area, Type 3 summary link advertisements can also be used to describe a default route on a
per-area basis. Default summary routes are used in stub area instead of flooding a complete set of
external routes. When describing a default summary route, the advertisement’s Link State ID is always
set to the Default Destination − 0.0.0.0, and the Network Mask is set to 0.0.0.0.
Separate costs may be advertised for each IP Type of Service. Note that the cost for TOS 0 must be
included, and is always listed first. If the T-bit is reset in the advertisement’s Option field, only a route
for TOS 0 is described by the advertisement. Otherwise, routes for the other TOS values are also
described. If a cost for a certain TOS is not included, its cost defaults to that specified for TOS 0.
Field Description
Network Mask For Type 3 link state
advertisements, this indicates
the destination network’s IP
address mask. For example,
when advertising the location
of a class A network the value
0xff000000
TOS The Type of Service that the
following cost is relevant to.
Metric The cost of this route.
Expressed in the same units
as the interface costs in the
router links advertisements.
84
Page 85

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Table 5-21. Summary Link Advertisement
Autonomous Systems External Link Advertisements
Autonomous Systems (AS) link advertisements are Type 5 link state advertisements. These
advertisements are originated by AS boundary routers. A separate advertisement is made for each
destination known to the router that is external to the AS.
AS external link advertisements usually describe a particular external destination. For these
advertisements the Link State ID field specifies an IP network number. AS external link advertisements
are also used to describe a default route. Default routes are used when no specific route exists to the
destination. When describing a default route, the Link Stat ID is always set the Default Destination
address (0.0.0.0) and the Network Mask is set to 0.0.0.0.
The format of the AS External Link Advertisement is shown below:
AS External Link Advertisements
Link-State Age
Link-State ID
Advertising Router
Link-State Sequence Number
Link-State Checksum
Network Mask
E
TOS Metric
Forwarding Address
External Route Tag
Options
Length
5
Figure 5-36. AS External Link Advertisement
Field Description
Network Mask
e IP address mask for the advertised destination.
E – bit The type of external metric. If the E – bit is set, the metric
specified is a Type 2 external metric. This means the metric is
considered larger than any link state path. If the E – bit is
zero, the specified metric is a Type 1 external metric. This
means that is comparable directly to the link state metric.
Forwarding Address Data traffic for the advertised destination will be forwarded to
this address. If the Forwarding Address is set to 0.0.0.0, data
traffic will be forwarded instead to the advertisement’s
originator.
TOS The Type of Service that the following cost is relevant to.
Metric The cost of this route. The interpretation of this metric
depends on the external type indication (the E – bit above).
85
Page 86

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
External Route Tag A 32-bit field attached to each external route. This is not used
by the OSPF protocol itself.
Table 5-21. AS External System Advertisement
86
Page 87

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
6
CONFIGURING THE SWITCH USING THE
CONSOLE INTERFACE
The DES-3326 supports a console management interface that allows the user to connect to the switch’s
management agent via a serial port and a terminal or a computer running a terminal emulation
program. The console can also be used over the network using the TCP/IP Telnet protocol. The console
program can be used to configure the switch to use an SNMP-based network management software over
the network.
This chapter describes how to use the console interface to access the switch, change its settings, and
monitor its operation.
Switch configuration settings that are saved to non-volatile RAM using Save
Changes from the Main Menu are retained in the switch’s memory, and are
reloaded when the switch is rebooted.
Before You Start
The DES-3326 supports a wide array of functions and gives great flexibility and increased network
performance by eliminating the routing bottleneck between the WAN and the intranet. Its function in a
network can be thought of as a new generation of wire-speed router that performs routing functions in
hardware, rather than in software.
General Deployment Strategy
The DES-3326 has many automatic features to detect the network topology and
adapt to changes in this topology, but it is recommended that a network scheme
be developed and entered statically into the DES-3326.
1. Determine how the network would be best segmented. This is probably done using VLANs in an
existing layer 2 switched network.
2. Develop an IP addressing scheme. This involves allocating a block of IP addresses to each
network segment. Each network subnet is then assigned a network address and a subnet mask.
3. Determine which network resources must be shared by the subnets. Shared resources may be
connected directly to the Layer 3 switch, if need be. Static routes to each of the shared
resources should be determined.
4. Determine how each subnet will communicate with the WAN or Internet. Again, static routes
should be determined and default gateways identified.
5. Develop a security scheme. Some subnets on the network need more security or should be
isolated from the other subnets. IP or MAC filtering can be used. Also, one or more VLANs on
the Layer 3 switch can be configured without an IP subnet – in which case, these VLANs will
87
Page 88

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
function as a layer 2 VLAN and would require an external router to connect to the rest of the
network.
6. Develop a policy scheme. Some subnets will have a greater need for multicasting bandwidth, for
example. A policy is a mechanism to alter the normal packet forwarding in a network device,
and can be used to intelligently allocate bandwidth to time-critical applications such as the
integration of voice, video, and data on the network.
7. Develop a redundancy scheme. Planning redundant links and routes to critical network
resources can save valuable time in the case of a link or device failure. The DES-3326’s
Spanning Tree function can be used to block the redundant link until it is needed.
VLAN Layout
VLANs on the DES-3326 have more functions than on a traditional layer 2 switch, and must therefore
be laid-out and configured with a bit more care. Layer 3 VLANs (VLANs that have an IP interface
assigned to them) can be thought of as network links – not just as a collection of associated end users.
Further, Layer 3 VLANs are assigned an IP interface address and subnet mask to enable IP routing
between them.
IEEE 802.1Q VLANs must be configured on the switch before they can be assigned IP interface
addresses or subnet masks. Further, the static VLAN configuration is specified on a per port basis. On
the DES-3326, a VLAN can consist of end-nodes – just like a traditional layer 2 switch, but a VLAN can
also consist of a subnetwork defined by an IP interface address and a subnet mask.
The IP subnets for the network must be determined first, and the VLANs configured on the switch to
accommodate the IP subnets. Finally, the IP subnets can be assigned to the VLANs.
Assigning IP Interface Addresses and Subnet Masks to VLANs
The DES-3326 allows the assignment of IP subnets to individual VLANs. Any VLAN configured on the
switch that is not assigned an IP subnet, will behave as a layer 2 VLAN and will not be capable of IP
routing – even if the switch is in IP Routing mode.
Developing an IP addressing scheme is a complex subject, but it is sufficient here to mention that the
total number of anticipated end nodes – for each Layer 3 VLAN – must be accommodated with a unique
IP address. It should be noted that the switch regards a VLAN with an IP interface address and
corresponding subnet mask assigned as an IP subnet in IP Routing mode.
Defining Static Routes
Routes between the IP interfaces and a default gateway or other router with a WAN connection should
be determined beforehand and entered into the static/default routing table on the DES-3326.
88
Page 89

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Connecting to the Switch
The console interface is used by connecting the Switch to a VT100-compatible terminal or a computer
running an ordinary terminal emulator program (e.g., the HyperTerminal program included with the
Windows operating system) using an RS-232C serial cable. Your terminal parameters will need to be set
to:
• VT-100/ANSI compatible
• 9,600 baud
• 8 data bits
• No parity
• One stop bit
• No flow control
You can also access the same functions over a Telnet interface. Once you have set an IP address for
your Switch, you can use a Telnet program (in VT-100 compatible terminal mode) to access and control
the Switch. All of the screens are identical, whether accessed from the console port or from a Telnet
interface.
Console Usage Conventions
The console interface makes use of the following conventions:
1. Items in <angle brackets> can be toggled between several choices using the space bar.
2. Items in [square brackets]can be changed by typing in a new value. You can use the backspace
and delete keys to erase characters behind and in front of the cursor.
3. The up and down arrow keys, the left and right arrow keys, the tab key and the backspace key,
can be used to move between selected items.
4. Items in UPPERCASE are commands. Moving the selection to a command and pressing Enter will
execute that command, e.g. APPLY, etc.
The APPLY command makes the configuration active for the current session only. If
the switch is rebooted, the unsaved changes will be lost and the last configuration
saved to Non-volatile RAM will be loaded into the switch. Use Save Changes from
the main menu to enter the current configuration into the switch’s Non-volatile RAM.
First Time Connecting To The Switch
The Switch supports user-based security that can allow you to prevent unauthorized users from
accessing the Switch or changing its settings. This section explains how to log onto the Switch.
The passwords used to access the Switch are case-sensitive; therefore, “S” is not the
same as “s.”
When you first connect to the Switch, you will be presented with the first login screen
(shown below).
Press Ctrl+R to refresh the screen. This command can be used at any
time to force the console program in the switch to refresh the console
screen.
89
Page 90

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 6-1. Initial Console screen
The factory default Username is “admin”, there is no factory default password. Enter
“admin” for the Username and leave the Password field blank to access the console
initially
Enter the factory default username (“admin”) and leave the Password field blank. Press Enter and
Access will be given to the main menu, as shown below:
Figure 6-2. Main Menu
The first user automatically gets Root privileges (See Table 6-1). It is recommended to create at least
one Root-level user for the Switch.
Creating User Accounts
To create a new user account, highlight Setup User Accounts from the Main Menu and press Enter:
90
Page 91

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 6-3. Main Menu
Figure 6-4. Setup User Accounts Menu
User Accounts Management
From the Main Menu, highlight Setup User Accounts and press Enter, then the Setup User Accounts
menu appears.
1. Toggle the Action field to Add using the space bar. This will allow the addition of a new
user. The other options are Delete, this allows the deletion of a user entry, and Update, this
allows for changes to be made to an existing user entry.
2. Enter the new user name, assign an initial password, and then confirm the new password.
Determine whether the new user should have Root, User+, or User privileges. The space bar
toggles between the three options.
3. Highlight APPLY and press enter to make the user addition effective.
4. Press Esc. to return to the previous screen or Ctrl+T to go to the root screen.
5. APPLY makes changes to the switch configuration for the current session only. All
permanent changes must be entered into non-volatile ram using the Save Changes
command on the Main Menu.
91
Page 92

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Root, User+ and Normal User Privileges
There are three levels of user privileges: Root and User+, and User.
Switch
Privilege
Configuration
Management Root User+ User
Configuration Yes Read Only Read Only
Network
Monitoring
Community
Strings and Trap
Stations
Update Firmware
and Configuration
Files
System Utilities Yes Ping only Ping only
Factory Reset Yes No No
Reboot Switch Yes Yes No
Yes Read Only Read Only
Yes Read Only Read Only
Yes No No
User Accounts Management
Add/Update/Delet
e User Accounts
View User
Accounts
Yes No No
Yes No No
Table 6-1. Root, User+, and User Privileges
92
Page 93

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Saving Changes
Selecting APPLY from a console menu makes the configuration effective for the
current session only. The configuration data will be lost if the switch is restarted.
To make the configuration effective after a switch restart, select Save Changes to
enter the configuration into non-volatile (NV-RAM).
The DES-3326 has two levels of memory: normal RAM and non-volatile or NV-RAM. Configuration
changes are made effective by highlighting APPLY and pressing Enter. When this is done, the settings
will be immediately applied to the switching software in RAM, and will immediately take effect.
Some settings, though, require you to restart the switch before they will take effect. Restarting the
switch erases all settings in RAM and reloads the stored settings from the NV-RAM. Thus, it is
necessary to save all setting changes to NV-RAM before rebooting the switch.
Figure 6-5. Main Menu
To retain any configuration changes permanently, highlight Save Changes from the Main Menu. The
following screen will appear to verify that your new settings have been saved to NV-RAM:
Figure 6-6. Save Changes Confirmation screen
Once the switch configuration settings have been saved to NV-RAM, they become the default settings
for the switch. These settings will be used every time the switch is rebooted.
93
Page 94

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Loading Factory Defaults
Loading the factory defaults returns the switch’s configuration to the factory default values. This will
clear all settings and restore them to their initial values listed in the appendix.
Figure 6-7. Main Menu
Highlight Reboot from the Main Menu and press Enter.
Figure 6-8. System Reboot menu
To execute a factory reset, highlight either Reboot & Load Factory Default Configuration or Reboot &
Load Factory Default Configuration Except IP Address and press enter. A confirmation screen will
appear.
Highlight Yes and press Enter to reset the switch’s NV-RAM to the factory default settings. This will erase
any User Accounts (and all other configuration settings) you may have entered and return the switch to the
state it was in when it was purchased.
Logging Onto The Switch Console
To log in once you have created a registered user, from the Login screen:
1. Type in your Username and press Enter.
2. Type in your Password and press Enter.
94
Page 95

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
3. The Main Menu screen will be displayed based on your access level or privilege.
Updating or Deleting User Accounts
To update or delete a user password:
Choose Setup User Accounts from the Main Menu. The following Setup User Accounts menu
appears:
Figure 6-9. Setup User Accounts screen
1. Toggle the Action field using the space bar to choose Add, Update, or Delete.
2. Type in the Username for the user account you wish to change and enter the Old Password
for that user account.
3. You can now modify the password or the privilege level for this user account.
4. If the password is to be changed, type in the New Password you have chosen, and press
Enter. Type in the same new password in the following field to verify that you have not
mistyped it.
5. If the privilege level is to be changed, toggle the Access Level field until the appropriate level
is displayed – Root, User+ or User.
6. Highlight APPLY and press Enter to make the change effective.
7. You must enter the configuration changes into the non-volatile ram (NV-RAM) using Save
Changes from the Main Menu if you want the configuration to be used after a switch
reboot.
Only a user with Root privileges can make changes to user accounts.
Viewing Current User Accounts
Access to the console, whether using the console port or via Telnet, is controlled using a user name and
password. Up to eight user accounts can be created. The console interface will not let you delete the
current logged-in user, to prevent accidentally deleting all of the users with Root privilege.
Only users with the Root privilege can delete users.
To view the current user accounts:
95
Page 96

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Highlight Setup User Accounts from the Main Menu. The current user accounts can be read from
following screen:
Figure 6-10. Setup User Accounts screen
Deleting a User Account
To delete a user account:
Figure 6-11. Setup User Accounts screen
1. Toggle the Action field to Delete.
2. Enter the Username and Old Password for the account you want to delete. You must enter
the password for the account to be able to delete it.
3. Highlight APPLY and press Enter to make the deletion of the selected user take effect.
4. You must enter the configuration changes into the non-volatile ram (NV-RAM) using Save
Changes from the Main Menu if you want the configuration to be used after a switch
reboot.
Only users with Root privileges can delete user accounts.
96
Page 97

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Setting Up The Switch
Basic Setup
This section will help prepare the Switch user by describing the Switch Information, IP Setup,
Remote Management Setup, Configure Ports, Serial Port Settings and Switch Settings menus.
Figure 6-12. Main Menu – Switch Information
Switch Information
Highlight Switch Information from the Main Menu and press Enter:
Figure 6-13. Switch Information screen
The Switch Information shows the operation mode of switch (Layer 3 or Layer 2), which (if any)
external modules are installed, and the switch’s MAC Address (assigned by the factory and
unchangeable). In addition, the Boot PROM and Firmware Version numbers are shown. This
information is helpful to keep track of PROM and Firmware updates and to obtain the switch’s MAC
address for entry into another network device’s address table – if necessary.
You can also enter the name of the System, its location, and the name and telephone number of the
System Administrator. It is recommended that the person responsible for the maintenance of the
network system that this Layer 3 switch is installed on be listed here.
97
Page 98

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Remote Management Setup
Configuring the Switch’s IP Address
The BOOTP and DHCP Server options for assigning the switch an IP address and
subnet mask are only available when the switch is in Layer 2 Only mode. The IP
Routing mode requires a manual entry of the IP address and subnet mask.
The Switch needs to have an IP address assigned to it so that an In-Band network management system
(for example, the DView or Telnet) client can find it on the network. The IP Setup screen allows you to
change the settings for the Ethernet interface used for in-band communication.
The fields listed under the Current Switch IP Settings heading are those that are currently being used
by the switch. Those fields listed under the Restart Settings heading are those which will be used after
the APPLY button is selected.
To set the switch’s IP address:
Highlight Remote Management Setup from the Main Menu and press Enter.
Figure 6-14. Remote Management Setup menu
The switch’s factory default IP address is 10.90.90.90 with a subnet mask of 255.0.0.0
and a default gateway of 0.0.0.0.
To manually assign the switch’s IP address, subnet mask, and default gateway
address:
Highlight the IP Address field and enter the appropriate IP address.
Highlight the Subnet Mask field and enter the appropriate subnet mask.
If you want to access the switch from a different subnet from the one it is installed on, highlight the
Default Gateway field and enter the IP address of the gateway. If you will manage the switch from the
subnet on which it is installed, you can leave the default address in this field.
To use the BOOTP/DHCP protocols to assign the switch an IP address, subnet mask, and default
gateway address:
Toggle the Get IP From field using the space bar to choose from Manual, BOOTP, or DHCP. This selects
how the switch will be assigned an IP address on the next reboot (or startup).
98
Page 99

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
The Get IP From options are:
• BOOTP – The switch will send out a BOOTP broadcast request when it is powered up. The
BOOTP protocol allows IP addresses, network masks, and default gateways to be assigned by
a central BOOTP server. If this option is set, the Switch will first look for a BOOTP server to
provide it with this information before using the default or previously entered settings.
• DHCP – The switch will send out a DHCP broadcast request when it is powered up. The
DHCP protocol allows IP addresses, network masks, and default gateways to be assigned by a
DHCP server. If this option is set, the switch will first look for a DHCP server to provide it
with this information before using the default or previously entered settings.
• Manual – Allows the entry of an IP address, Subnet Mask, and a Default Gateway for the
switch. These fields should be of the form xxx.xxx.xxx.xxx, where each xxx is a number
(represented in decimal form) between 0 and 255. This address should be a unique address
on the network assigned for use by the Network Administrator. The fields which require
entries under this option are as follows:
• Subnet Mask – A Bitmask that determines the extent of the subnet that the Switch is on.
Should be of the form xxx.xxx.xxx.xxx, where each xxx is a number (represented in decimal)
between 0 and 255. The value should be 255.0.0.0 for a Class A network, 255.255.0.0 for a
Class B network, and 255.255.255.0 for a Class C network, but custom subnet masks are
allowed.
• Default Gateway – IP address that determines where packets with a destination address
outside the current subnet should be sent. This is usually the address of a router or a host
acting as an IP gateway. If your network is not part of an intranet, or you do not want the
Switch to be accessible outside your local network, you can leave this field unchanged.
• Management VID – This field allows the entry of a VLAN ID (VID) from which a management
station (a computer) will be allowed to manage the switch using TCP/IP (in-band, or over the
network). Management stations that are on VLANs other than the one entered in the
Management VID field will not be able to manage the switch in-band unless their IP addresses
are entered in the Management Station IP Addresses field. Any VID that has been configured
on the switch can be entered in this field.
SNMP Settings
Some settings must be entered to allow the switch to be managed from an SNMP-based Network
Management System such as SNMP v1 or to be able to access the Switch using the Telnet protocol or
the Web-based Manager. Please see the next chapter for Web-based network management information.
To setup the switch for remote management:
Highlight Remote Management Setup from the Main Menu. The following screen appears:
99
Page 100

DES-3326 Layer 3 Fast Ethernet Switch User’s Guide
Figure 6-15. Remote Management Setup menu
Management stations are computers on the network that will be used to manage the switch. You can
limit the number of possible management stations by entering up to three IP addresses in the
Management Station IP Settings field. If the three IP Address fields contain all zeros (“0”), then any
station with any IP address can access the switch to manage and configure it. If there is one or more IP
addresses entered in the IP Address field, then only stations with the IP addresses entered will be
allowed to access the switch to manage or configure it.
Setting Up Trap Receivers
This allows the switch to send traps (messages about errors, etc.) to management stations on the
network. Highlight Setup Trap Receivers and press Enter. The trap recipients can be setup from the
following screen:
Figure 6-16. Setup Trap Recipients menu
The IP Address field is the IP address of a management station (a computer) that is configured to
receive the SNMP traps from the switch.
The SNMP Community String is similar to a password in that stations that do not know the correct
string cannot receive or request SNMP information from the switch.
The Status field can be toggled between Enabled and Disabled to enable or disable the receipt of SNMP
traps by the listed management stations.
100
 Loading...
Loading...