seagate BLACKARMOR BACKUP user guide


Copyright (c) 2000-2009 Acronis. All rights reserved. Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved.
“Acronis”, "Acronis Compute with Confidence" and the Acronis logo are trademarks of Acronis, Inc. Linux is a registered trademark of Linus Torvalds.
Windows and MS-DOS are registered trademarks of Microsoft Corporation.
All other trademarks and copyrights referred to are the property of their respective owners.
Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder.
Distribution of this work or derivative work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained from the copyright holder.
DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID.
2 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

Table of Contents
Chapter 1. Introduction........................................................................................... |
7 |
||
1.1 |
What is Seagate BlackArmor® Backup? ............................................................................... |
7 |
|
1.2 |
Advantages ...................................................................................................................... |
7 |
|
1.3 |
System requirements and supported media ......................................................................... |
8 |
|
1.3.1 |
Minimum system requirements .................................................................................... |
8 |
|
1.3.2 Supported storage media ............................................................................................. |
9 |
||
1.3.3 |
Supported operating systems....................................................................................... |
9 |
|
1.3.4 |
Supported file systems ................................................................................................ |
9 |
|
1.4 |
License policy ................................................................................................................... |
9 |
|
1.5 |
Technical support............................................................................................................ |
10 |
|
Chapter 2. Seagate BlackArmor Backup installation and startup......................... |
12 |
|
2.1 |
Installing Seagate BlackArmor Backup............................................................................... |
12 |
2.1.1 Installing Seagate BlackArmor Backup ........................................................................ |
12 |
|
2.2 |
Extracting Seagate BlackArmor Backup ............................................................................. |
13 |
2.3 |
Running Seagate BlackArmor Backup................................................................................ |
13 |
2.4 |
Removing Seagate BlackArmor Backup ............................................................................. |
13 |
Chapter 3. General information............................................................................. |
14 |
|
3.1 |
The difference between file archives and disk/partition images ........................................... |
14 |
3.2 |
Full, incremental and differential backups.......................................................................... |
14 |
3.3 |
BlackArmor Backup Secure Zone ...................................................................................... |
15 |
3.4 |
Viewing disk and partition information .............................................................................. |
15 |
3.5 |
Try&Decide .................................................................................................................... |
16 |
3.6 |
BlackArmor DriveCleanser, File Shredder, and System Clean-up .......................................... |
16 |
3.7 |
Support for Zip format..................................................................................................... |
16 |
Chapter 4. Getting to know Seagate BlackArmor Backup |
....................................18 |
||
4.1 |
BlackArmor One-Click Protection....................................................................................... |
18 |
|
4.2 |
Program workspace......................................................................................................... |
20 |
|
Chapter 5. Creating backup archives .................................................................... |
24 |
||
5.1 |
Selecting what data to back up ........................................................................................ |
24 |
|
5.2 |
Performing backup .......................................................................................................... |
25 |
|
5.2.1 |
Selecting data for backup .......................................................................................... |
25 |
|
5.2.2 |
Selecting the target archive location ........................................................................... |
27 |
|
5.2.3 |
Scheduling ............................................................................................................... |
28 |
|
5.2.4 |
Backup method ........................................................................................................ |
29 |
|
5.2.5 |
Source files exclusion ................................................................................................ |
30 |
|
5.2.6 |
Selecting the backup options ..................................................................................... |
31 |
|
5.2.7 |
Setting automatic consolidation.................................................................................. |
32 |
|
5.2.8 |
Providing a comment ................................................................................................ |
33 |
|
5.2.9 |
The operation summary and the backup process ......................................................... |
33 |
|
5.3 |
Fine-tuning your backups................................................................................................. |
33 |
|
5.3.1 |
Archive protection..................................................................................................... |
33 |
|
5.3.2 |
Source files exclusion ................................................................................................ |
34 |
|
5.3.3 |
Pre/post commands .................................................................................................. |
34 |
|
5.3.4 |
Compression level..................................................................................................... |
34 |
|
5.3.5 |
Backup performance ................................................................................................. |
35 |
|
5.3.6 |
Archive splitting........................................................................................................ |
36 |
|
|
|
||
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
||
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
3 |
||

5.3.7 |
File-level security settings.......................................................................................... |
36 |
5.3.8 |
Error handling .......................................................................................................... |
36 |
5.3.9 |
Additional settings .................................................................................................... |
37 |
5.3.10 |
Backup reserve copy settings ................................................................................... |
37 |
5.3.11 |
Creating a custom data category for backups ............................................................ |
38 |
5.4 Making reserve copies of your backups ............................................................................. |
39 |
|
Chapter 6. Restoring backup data......................................................................... |
40 |
||
6.1 |
Restore under Windows or boot from CD?......................................................................... |
40 |
|
6.1.1 |
Network settings in rescue mode ............................................................................... |
40 |
|
6.2 |
Restoring files and folders from file archives...................................................................... |
40 |
|
6.3 |
Restoring disks/partitions or files from images ................................................................... |
44 |
|
6.3.1 |
Starting the Restore Wizard ....................................................................................... |
44 |
|
6.3.2 |
Archive selection....................................................................................................... |
44 |
|
6.3.3 |
Restoration method selection..................................................................................... |
45 |
|
6.3.4 |
Selecting a disk/partition to restore ............................................................................ |
46 |
|
6.3.5 |
Selecting a target disk/partition.................................................................................. |
47 |
|
6.3.6 |
Changing the restored partition type .......................................................................... |
47 |
|
6.3.7 |
Changing the restored partition size and location......................................................... |
48 |
|
6.3.8 |
Assigning a letter to the restored partition .................................................................. |
48 |
|
6.3.9 |
Setting restore options .............................................................................................. |
48 |
|
6.3.10 |
Restoration summary and executing restoration ........................................................ |
49 |
|
6.4 |
Setting restore options .................................................................................................... |
49 |
|
6.4.1 |
Files to preserve during restoration ............................................................................ |
49 |
|
6.4.2 |
Pre/post commands .................................................................................................. |
49 |
|
6.4.3 |
Restoration priority ................................................................................................... |
50 |
|
6.4.4 |
File-level security settings.......................................................................................... |
50 |
|
6.4.5 |
Additional settings .................................................................................................... |
50 |
|
Chapter 7. Try&Decide .......................................................................................... |
51 |
|
7.1 |
Using Try&Decide............................................................................................................. |
54 |
7.1.2. Try&Decide options.................................................................................................. |
54 |
|
7.2 |
Try&Decide usage examples ............................................................................................. |
54 |
Chapter 8. Scheduling tasks.................................................................................. |
57 |
|
8.1 Creating scheduled tasks ................................................................................................. |
57 |
|
8.1.1 |
Setting up once only execution .................................................................................. |
58 |
8.1.2 |
Setting up upon event execution................................................................................ |
58 |
8.1.3 |
Setting up daily execution ......................................................................................... |
59 |
8.1.4 |
Setting up weekly execution ...................................................................................... |
60 |
8.1.5 |
Setting up monthly execution..................................................................................... |
60 |
8.2 Managing scheduled tasks ............................................................................................... |
61 |
|
Chapter 9. Managing BlackArmor Backup Secure Zone........................................ |
62 |
|
9.1 |
Creating BlackArmor Backup Secure Zone ......................................................................... |
62 |
9.2 |
Resizing BlackArmor Backup Secure Zone.......................................................................... |
64 |
9.3 |
Changing password for BlackArmor Backup Secure Zone .................................................... |
65 |
9.4 |
Deleting BlackArmor Backup Secure Zone.......................................................................... |
66 |
Chapter 10. Creating bootable media ................................................................... |
67 |
|
Chapter 11. Other operations................................................................................ |
70 |
|
11.1 |
Validating backup archives ............................................................................................. |
70 |
11.2 |
Operation results notification.......................................................................................... |
72 |
11.2.1 Email notification .................................................................................................... |
72 |
|
|
|
|
4 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
|

11.2.2 WinPopup notification.............................................................................................. |
73 |
|
11.3 |
Viewing Tasks and Logs................................................................................................. |
74 |
11.4 |
Consolidating backups ................................................................................................... |
76 |
11.5 |
Removing backup archives ............................................................................................. |
79 |
Chapter 12. Exploring archives and mounting images ......................................... |
81 |
|
12.1 |
Searching ..................................................................................................................... |
81 |
12.2 |
Google Desktop and Windows Search integration ............................................................. |
83 |
12.3 |
Mounting an image........................................................................................................ |
90 |
12.4 |
Unmounting an image ................................................................................................... |
92 |
Chapter 13. Transferring the system to a new disk |
..............................................94 |
||
13.1 |
General information....................................................................................................... |
94 |
|
13.2 |
Security........................................................................................................................ |
95 |
|
13.3 |
Executing transfers........................................................................................................ |
95 |
|
13.3.1 |
Selecting Clone mode.............................................................................................. |
95 |
|
13.3.2 |
Selecting source disk............................................................................................... |
95 |
|
13.3.3 |
Selecting destination disk ........................................................................................ |
96 |
|
13.3.4 |
Partitioned destination disk ...................................................................................... |
97 |
|
13.3.5 |
Selecting partition transfer method........................................................................... |
97 |
|
13.3.6 |
Cloning with manual partitioning .............................................................................. |
98 |
|
13.3.7 |
Cloning summary .................................................................................................. |
100 |
|
Chapter 14. Adding a new hard disk |
...................................................................101 |
|
14.1 |
Selecting a hard disk ................................................................................................... |
101 |
14.2 |
Creating new partitions................................................................................................ |
101 |
14.3 |
Disk add summary....................................................................................................... |
102 |
Chapter 15. Security and Privacy Tools............................................................... |
104 |
||
15.1 |
Using File Shredder ..................................................................................................... |
104 |
|
15.2 |
BlackArmor DriveCleanser ............................................................................................ |
105 |
|
15.3 |
Creating custom algorithms of data destruction.............................................................. |
108 |
|
15.4 |
System Clean-up ......................................................................................................... |
109 |
|
15.5 |
System Clean-up Wizard settings .................................................................................. |
110 |
|
15.5.1 |
"Data Destruction Method" setting.......................................................................... |
110 |
|
15.5.2 |
"Files" setting ....................................................................................................... |
110 |
|
15.5.3 |
"Computers" setting .............................................................................................. |
111 |
|
15.5.4 |
"Drive Free Space" setting ..................................................................................... |
112 |
|
15.5.5 |
"Commands" setting.............................................................................................. |
112 |
|
15.5.6 |
"Network Places Filter" setting ............................................................................... |
113 |
|
15.6 |
Cleaning up separate system components ..................................................................... |
113 |
|
Appendix A. Partitions and file systems |
..............................................................114 |
||
A.1 |
Hard disk partitions...................................................................................................... |
114 |
|
A.2 |
File systems ................................................................................................................ |
114 |
|
A.2.1 |
FAT16.................................................................................................................. |
114 |
|
A.2.2 |
FAT32.................................................................................................................. |
115 |
|
A.2.3 |
NTFS ................................................................................................................... |
115 |
|
A.2.4 |
Linux Ext2............................................................................................................ |
115 |
|
A.2.5 |
Linux Ext3............................................................................................................ |
115 |
|
A.2.6 |
Linux ReiserFS...................................................................................................... |
116 |
|
Appendix B. Hard disks and BIOS setup ............................................................. |
117 |
B.1 Installing hard disks in computers ................................................................................. |
117 |
B.1.1 Installing a hard disk, general scheme .................................................................... |
117 |
B.1.2 Motherboard sockets, IDE cable, power cable.......................................................... |
118 |
|
|
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
5 |

B.1.3 Configuring hard disk drives, jumpers..................................................................... |
118 |
|
B.2 |
BIOS .......................................................................................................................... |
119 |
B.2.1 Setup utility.......................................................................................................... |
119 |
|
B.2.2 Standard CMOS setup menu .................................................................................. |
120 |
|
B.2.3 Arranging boot sequence, advanced CMOS setup menu ........................................... |
121 |
|
B.2.4 Hard disk initialization errors.................................................................................. |
122 |
|
B.3 |
Installing a SATA hard drive ......................................................................................... |
123 |
B.3.1 Steps for installing a new internal SATA drive.......................................................... |
123 |
|
Appendix C. Hard Disk Wiping methods.............................................................. |
125 |
|
C.1 |
Information wiping methods’ functioning principles......................................................... |
125 |
C.2 |
Information wiping methods used by Seagate BlackArmor Backup ................................... |
126 |
Appendix D. Startup Parameters......................................................................... |
127 |
|
6 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

Chapter 1. Introduction
1.1 What is Seagate BlackArmor® Backup?
Seagate BlackArmor® Backup is an integrated software suite that ensures security of all information on your PC. It can back up the operating system, applications, settings and all of your data, while also securely destroying any confidential data you no longer need. With this software, you can back up selected files and folders, Windows applications’ settings, settings and messages of Microsoft e-mail clients — or even the entire disk drive or selected partitions. Should your disk drive become damaged or your system attacked by a virus or malware, you can restore the back-up data quickly and easily, eliminating hours or days of work trying to rebuild your disk drive’s data and applications from scratch.
Seagate BlackArmor Backup provides you with all the essential tools you need to recover your computer system should a disaster occur, such as losing data, accidentally deleting critical files or folders, or a complete hard disk crash. If failures occur that block access to information or affect system operation, you will be able to restore the system and the lost data easily.
The unique technology implemented in Seagate BlackArmor Backup allows you to perform exact, sector-by-sector disk backups, including all operating systems, applications and configuration files, personal settings, and data.
Seagate BlackArmor Backup helps you protect your identity as well. Simply deleting old data will not remove it permanently from your computer. Seagate BlackArmor Backup now includes BlackArmor DriveCleanser that permanently destroys files and wipes personal information from partitions and/or entire disks, as well as a wizard that cleans up your Windows system of all traces of user activity.
You can store backups on Seagate BlackArmor Network Attached Storage (NAS) and Direct Attached Storage (DAS) devices, also on Maxtor DAS.
When performing scheduled backup tasks, Seagate BlackArmor Backup automatically selects a backup mode (full, incremental, differential) in accordance with the backup policy set by the user.
If you are going to install a new hard disk drive, Seagate BlackArmor Backup will help you to transfer information from the old one in minutes, including operating systems, applications, documents, and personal settings. After migrating to the new hard disk you can destroy all confidential information on the old one securely. This is the recommended procedure if you intend to donate, throw away, or sell the old hard disk drive.
Wizards and a Windows Vista-style interface will make your work easier. Just perform a few simple steps and let Seagate BlackArmor Backup take care of everything else! When a system problem occurs, the software will get you up and running in no time.
1.2 Advantages
One-Click Protection – During the first start of Seagate BlackArmor Backup after installation, the program will take stock of your computer storage devices and if you have enough free space on Seagate BlackArmor drives (DAS or NAS, depending on which licensing you have selected); it will offer to immediately protect your system by backing up your system volume and Master Boot Record to the storage location of its choice. In addition, Seagate BlackArmor Backup will offer you to refresh such backups regularly (by default, once
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
7 |

every seven days). So you simply need to click Protect and your system will be protected from a disaster.
•File search using Google Desktop and Windows Search – If you use one of these search engines, you will be able to search for files through multiple archives by name or by a part of the name and then restore individual files easily and quickly. In addition, they provide Seagate BlackArmor Backup with the ability to perform full-text indexing of the files in *.tib archives, so you will be able to perform searches of the files content.
•Support for Zip format – Now you can create file-level backup archives as zip files. Zip is one of the most widely used and popular archiving formats. In addition, Microsoft Windows has built-in support of this file format making it possible to extract files from backups created by Seagate BlackArmor Backup without using the program itself.
•Consolidation of backup files – you can create a consistent copy of an archive while deleting selected backups. This allows deleting the backups you do not need anymore from any archive without harming that archive.
•Automatic consolidation - you can set limitations for backup archives, namely maximum archive size, maximum number of backups, and maximum storage period for the archive files. In case any of the preset limits are exceeded, Seagate BlackArmor Backup will combine the first full backup with the next incremental one into one full backup which will be dated the later backup date. Then, if necessary, this backup will be combined with the next, until the occupied storage space (or number of backups) decreases to the preset limit. Thus, the archive integrity will not be affected, in spite of the fact that the oldest backups will be deleted. This procedure is called automatic consolidation.
•Automatic computer shutdown after backup or restoration finishes – you can now perform a backup at night and go to sleep without bothering about turning off the computer – the program will do this on its own.
•More user-friendly – Completely redesigned user interface and usability enhancements make Seagate BlackArmor Backup easier to use than ever before.
1.3System requirements and supported media
1.3.1 Minimum system requirements
Seagate BlackArmor Backup requires the following hardware:
•Pentium processor or higher
•128 MB RAM
•CD-RW/DVD-RW drive for bootable media creation
•Mouse or other pointing device (recommended)
•Seagate BlackArmor external drives
We recommend you to connect Seagate BlackArmor drives via USB cables.
8 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

1.3.2 Supported storage media
•Seagate BlackArmor external drives
•Seagate BlackArmor NAS
•Other Seagate BlackArmor DAS drives
•Maxtor DAS drives
1.3.3 Supported operating systems
Seagate BlackArmor Backup has been tested on the following operating systems:
•Windows XP SP 3
•Windows XP Professional x64 Edition SP2
•Windows Vista SP 1 (all editions)
Seagate BlackArmor Backup also enables the creation of a bootable CD-R/DVD-R that can back up and restore a disk/partition on a computer running any Intelor AMDbased PC operating system, including Linux®. The only exception is the Intel-based Apple Macintosh, which is not supported in native mode at this time.
1.3.4 Supported file systems
•FAT16/32
•NTFS
•Ext2/Ext3
•ReiserFS
•Linux SWAP
If a file system is not supported or is corrupted, Seagate BlackArmor Backup can copy data using a sector-by-sector approach.
The Ext2/Ext3, ReiserFS, and Linux SWAP file systems are supported only for disk or partition backup/restore operations. You cannot use Seagate BlackArmor Backup for filelevel operations with these file systems (file backup, restore, search, as well as image mounting and file restoring from image), as well as for backups to disks or partitions with these file systems.
1.4 License policy
By default, Seagate BlackArmor Backup supports one license for Seagate BlackArmor DAS devices (i.e., one Seagate BlackArmor drive license to use Seagate BlackArmor Backup only on one computer), and 5 or 10 licenses for Seagate BlackArmor NAS devices (depending on the model). If the drive is detected, Seagate BlackArmor Backup uses licenses from the external drive; otherwise a dialog requesting to attach a Seagate BlackArmor drive or select a Seagate BlackArmor NAS with available backup client licenses, and then the program starts.
Hereafter, if Seagate DAS is attached, One-Click Protection will be set up to back up to MyOneClickBackup folder of directly attached storage and the first discovered Seagate DAS will be used as the default backup location (the root of the DAS as well). If Seagate BlackArmor NAS is detected, its available licenses will be used and the backup location for One-Click Protection will be \\BlackArmorNAS_name\Public\Backups\computer_name.tib; for
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
9 |
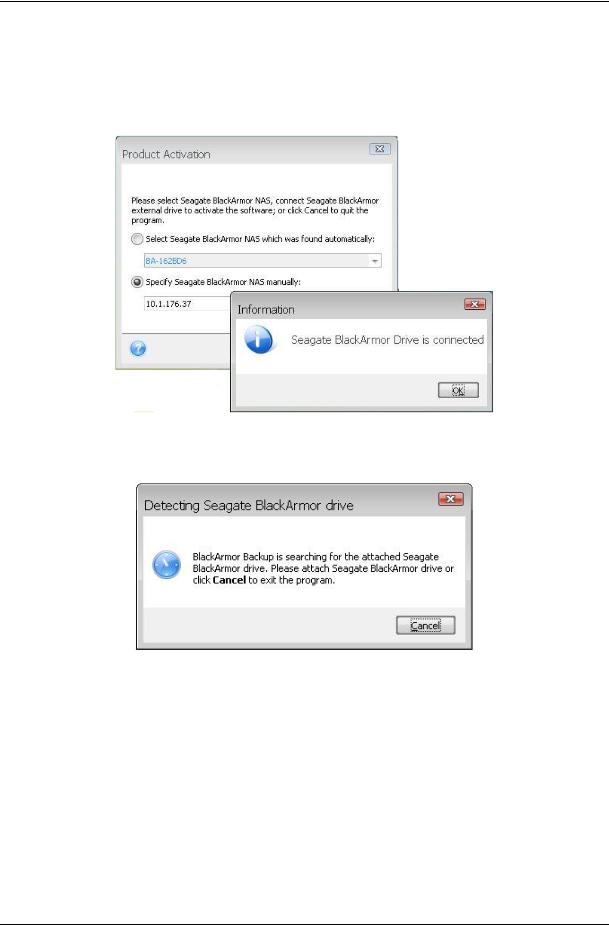
backing up the program will use the Seagate BlackArmor NAS by default. Also you can select the required Seagate BlackArmor NAS manually by IP address or select it from the list. In case a Seagate BlackArmor NAS is selected, on the first run of the One-Click Protection wizard a folder Backups will be created on the Seagate BlackArmor NAS share Public, and then it will be used as a default location.
If during the first launch of the program a Seagate BlackArmor DAS was attached, but then for any reason was disconnected, Seagate BlackArmor Backup will show a message asking to connect it again.
If you need more Seagate BlackArmor NAS licenses, please visit http://www.seagate.com/backupsoftwareoffers/.
Note in case Seagate BlackArmor Backup uses Seagate BlackArmor DAS licensing, the bootable media will ask to connect a Seagate BlackArmor DAS drive while loading. And if a type of the licensing still is not selected and the Media Builder wizard was run right after installing Seagate BlackArmor Backup, then the bootable media, created before the product activation, will not load.
1.5 Technical support
Users of legally purchased and registered copies of Seagate BlackArmor Backup are entitled to free technical support. If you experience problems installing or using Seagate products that you can’t solve yourself by using this guide, then please contact Seagate Technical Support.
10 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

More information about contacting Seagate Technical Support is available at the following link: http://www.seagate.com/www/en-us/support.
In order to open a support trouble ticket, please fill out the Web form on the Seagate site; support will only open a trouble ticket if it is initiated from this form.
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
11 |

Chapter 2. Seagate BlackArmor Backup installation and startup
2.1 Installing Seagate BlackArmor Backup
2.1.1 Installing Seagate BlackArmor Backup
To install Seagate BlackArmor Backup:
•Run the Seagate BlackArmor Backup setup file.
•In the Install Menu, select the program to install: Seagate BlackArmor Backup.
•Select the preferable language of the License Agreement.
•Follow the install wizard instructions on the screen.
Typical, Custom and Complete installation is available. Having pressed Custom, you can choose not to install Rescue Media Builder.
With Rescue Media Builder you can create bootable rescue disks (see details in Chapter 10. Creating bootable media). Installing the Bootable Rescue Media Builder will allow you to create bootable media or its ISO image at any time from the main program window or running Bootable Rescue Media Builder on its own.
When installed, Seagate BlackArmor Backup creates a new device in the Device Manager list (Control Panel -> System -> Hardware -> Device Manager -> Seagate Devices -> BlackArmor Backup Archive Explorer). Do not disable or uninstall this device, as it is necessary for connecting image archives as virtual disks (see Chapter 12. Exploring archives and mounting images).
12 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

2.2 Extracting Seagate BlackArmor Backup
When installing Seagate BlackArmor Backup, you can save the setup (.msi) file on a local or network drive. This will help when modifying or recovering the existing component installation.
To save the setup file:
•Run the Seagate BlackArmor Backup setup file.
•In the Install Menu, right-click on the program name and select Extract.
•Select a location for the setup file and click Save.
Recovering or updating the existing Seagate BlackArmor Backup installation with use of the
.msi file must be done from the command line as follows:
1.Choose Start -> Run
2.Type cmd.
3.When the command-line interpreter window opens, type the following command: msiexec /i path_to_msi_file\msi_file_name.msi REINSTALL=ALL REINSTALLMODE=vomus
4.After the install wizard window opens, choose Typical, Custom or Complete installation for repairing or changing the program's components.
2.3 Running Seagate BlackArmor Backup
You can run Seagate BlackArmor Backup in Windows by selecting Start -> Programs -> Seagate -> BlackArmor Backup-> BlackArmor Backup or by clicking on the appropriate shortcut on the desktop.
If your disk data is totally corrupted and the operating system cannot boot, load the standalone Seagate BlackArmor Backup version from the bootable media, supplied with the retail box or created by you using Rescue Media Builder. This boot disk will allow you to restore your disk from a previously created image.
2.4 Removing Seagate BlackArmor Backup
Select Start -> Settings -> Control panel -> Add or remove programs -> <BlackArmor Backup > -> Remove. Then follow the instructions on the screen. You may have to reboot your computer afterwards to complete the task.
If you use Windows Vista, select Start -> Control panel -> Programs and Features -> < BlackArmor Backup > -> Remove. Then follow the instructions on the screen. You may have to reboot your computer afterwards to complete the task.
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
13 |

Chapter 3. General information
3.1 The difference between file archives and disk/partition images
A backup archive is a file or a group of files (also called “backups” in this guide), that contains a copy of selected file/folder data or a copy of all information stored on selected Seagate BlackArmor NAS or Seagate\Maxtor DAS.
When you back up files and folders, only the data, along with the folder tree, is compressed and stored.
Backing up disks and partitions is performed in a different way: Seagate BlackArmor Backup stores a sector-by-sector snapshot of the disk, which includes the operating system, registry, drivers, software applications and data files, as well as system areas hidden from the user. This procedure is called “creating a disk image,” and the resulting backup archive is often called a disk/partition image.
By default, Seagate BlackArmor Backup stores only those hard disk parts that contain data (for supported file systems). Further, it does not back up swap file information (pagefile.sys under Windows XP/Vista) and hiberfil.sys (a file that keeps RAM contents when the computer goes into hibernation). This reduces image size and speeds up image creation and restoration. However, you might use the Create an image using the sector-by-sector approach option that lets you include all of the sectors of a hard disk in an image.
A partition image includes all files and folders. This includes all attributes (including hidden and system files), boot record, and FAT (file allocation table); as well as files in the root directory and the zero track of the hard disk with master boot record (MBR).
A disk image includes images of all disk partitions as well as the zero track with master boot record (MBR).
By default, files in all Seagate BlackArmor Backup archives have a “.tib” extension. Do not change this file extension.
It is important to note that you can restore files and folders not only from file archives, but from disk/partition images too. To do so, mount the image as a virtual disk (see Chapter 12. Exploring archives and mounting images) or start the image restoration and select Restore specified files or folders.
3.2 Full, incremental and differential backups
Seagate BlackArmor Backup can create full, incremental and differential backups.
A full backup contains all data at the moment of backup creation. It forms a base for further incremental or differential backup or is used as a standalone archive. A full backup has the shortest restore time compared to incremental or differential ones.
An incremental backup file only contains data changed since the last backup of any type (full, incremental, or differential one). Therefore, it is smaller and takes less time to create, but as it doesn’t contain all data; all the previous backups and the initial full backup are required for restoration.
Unlike an incremental backup, when every backup procedure creates the next file in a “chain”, a differential backup creates an independent file, containing all changes since the
14 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

last full backup. Generally, a differential backup will be restored faster than an incremental one, as it does not have to process through a long chain of previous backups.
A standalone full backup might be an optimal solution if you often roll back the system to its initial state or if you do not like to manage multiple files. If you are interested in saving only the last data state to be able to restore it in case of system failure, consider the differential backup. It is particularly effective if your data changes tend to be few compared to the full data volume.
The same is true for incremental backup. These are most useful when you need frequent backups and the ability to roll back to a specific point in time. Having created a full backup once, if you then create an incremental backup each day of a month, you will get the same result as if you created full backups every day. Incremental images are considerably smaller than full or differential images.
Incremental or Differential?
The difference is typically that in an incremental backup, only the files changed or added since the last time the backup ran are added to the archive. With a differential backup, all the files changed or added since the initial full backup, are added to the archive. Thus, differential backups take longer to run than incremental backups. When restoring from an incremental backup, the program must copy the entire initial backup and then step through each of the previous backups to retrieve all the updated files. A differential backup, on the other hand, can be restored more quickly because the software must copy only the original backup and the most recent one.
An incremental or differential backup created after a disk is defragmented might be considerably larger than usual. This is because the defragmentation program changes file locations on the disk and the backups reflect these changes. Therefore, it is recommended that you re-create a full backup after disk defragmentation.
3.3 BlackArmor Backup Secure Zone
The BlackArmor Backup Secure Zone is a special, hidden partition on the computer system. Ordinary applications cannot access it.
The BlackArmor Backup Secure Zone is available only for the Try&Decide feature.
For information on how to create, resize or delete BlackArmor Backup Secure Zone using this wizard, see Chapter 9. Managing BlackArmor Backup Secure Zone.
3.4 Viewing disk and partition information
You can change the way data is represented in all schemes you see in various wizards.
To the right are three icons: Arrange Icons by, Choose Details and i (Display the properties of the selected item), the latter duplicated in the context menu opened by right-clicking objects.
To sort messages by a particular column, click the header (another click will switch the messages to the opposite order) or the Arrange Icons by button and select the column.
To select columns to view, right-click the headers line or left-click the Choose Columns button. Then flag the columns you want to display. When left-clicking the Choose Columns button, you can also change the display order of columns using the Move Up and Move Down buttons.
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
15 |

If you click the i (Display the properties of the selected item) button, you will see the selected partition or disk properties window.
This window contains two panels. The left panel contains the properties tree and the right describes the selected property in detail. The disk information includes its physical parameters (connection type, device type, size, etc.); partition information includes both physical (sectors, location, etc.), and logical (file system, free space, assigned letter, etc.) parameters.
You can change the width of a column by dragging its borders with the mouse.
3.5 Try&Decide
The Seagate BlackArmor Backup Try&Decide feature allows you to perform potentially dangerous operations such as software installation or opening e-mail attachments without putting your PC at risk. It does this by creating essentially a controlled, secure, temporary workspace that is insulated from the rest of your computer. If the system crashes or your computer stops responding during these operations, you should revert the system to the previous state by discarding changes made in the Try&Decide mode. If operations are successful, you have a choice of applying the changes to the real system. (For more details see Chapter 7. Try&Decide.)
3.6 BlackArmor DriveCleanser, File Shredder, and System Clean-up
Seagate BlackArmor Backup contains utilities for secure destruction of data on an entire hard disk drive, individual partitions, as well as for erasing individual files and eliminating user system activity traces. When replacing your old hard drive with a new, higher-capacity one, you may unwittingly leave on the old disk lots of personal and confidential information that can be recovered, even if you have reformatted it. The BlackArmor DriveCleanser provides for the destruction of confidential information on hard disk drives and/or partitions with the help of techniques that meet or exceed most national and state standards. You can select an appropriate data destruction method depending on the importance of your confidential information. The File Shredder provides the same capabilities for individual files and folders. Finally, the System Clean-up wizard ensures elimination of all your activity traces; while working with a PC, you leave thousands of bytes of evidence showing your actions (records in various system files) that you don’t even know about. This could include user names and passwords, as well as other personal information that could be used to steal your identity if it fell into the wrong hands. This utility wipes them completely from the disk drive.
3.7 Support for Zip format
Now you will be able to retrieve files from backups anywhere without using Seagate BlackArmor Backup, if you choose the zip format instead of the tib format.
Please, be aware that built-in support of zip files in Windows does not cover operations with multivolume zip archives, and zip archives exceeding 4GB in size or which contain files of more than 4GB each.
The Zip format is available when backing up files and/or folders as well as when making reserve copies of your backups. Seagate BlackArmor Backup provides for the zip format most of the functionality available for the tib format, except password protection and encryption –
16 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

you can schedule backups, validate zip backup archives, restore files and folders from zip archives, make incremental and differential backups, and so on.
Seagate BlackArmor Backup can restore and validate only its own zip archives. If a zip archive was created by a file archiver program, it cannot be restored and validated by Seagate BlackArmor Backup.
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
17 |
Chapter 4. Getting to know Seagate BlackArmor Backup
4.1 BlackArmor One-Click Protection
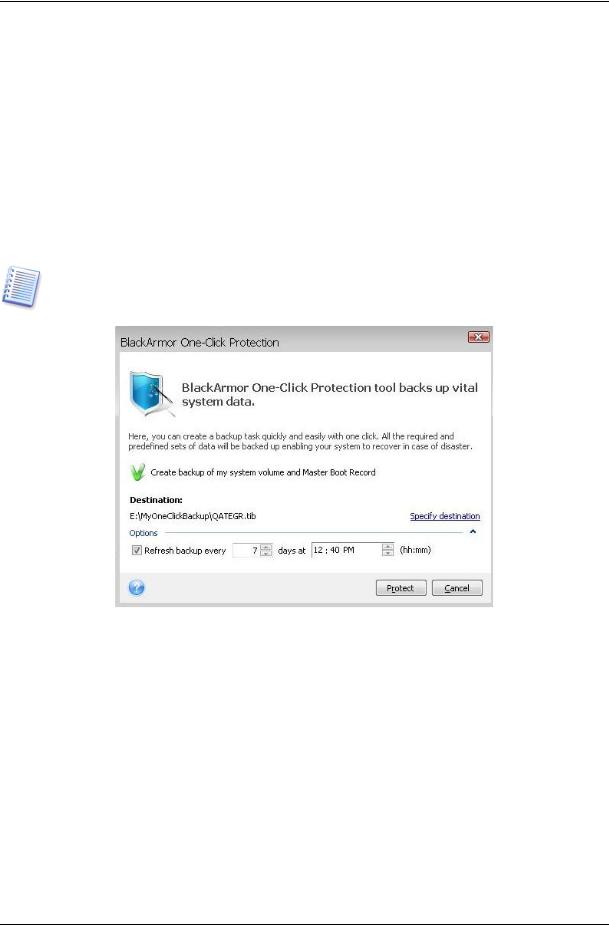
BlackArmor One-Click Protection tool allows you to begin protecting your computer as soon as you install Seagate BlackArmor Backup. During the first start of the just installed Seagate BlackArmor Backup, the program will offer you to protect your computer by immediately backing up its system volume and Master Boot Record (MBR) as well as scheduling subsequent full backups.
The BlackArmor One-Click Protection tool performs only full backups of the system volume; scheduling an incremental or differential backup is not possible. In addition, it does not support backup of drives protected by BitLocker Drive Encryption in Windows Vista.
If Seagate BlackArmor DAS is attached, One-Click Protection will be set up to back up to MyOneClickBackup folder of directly attached storage and the first discovered Seagate DAS will be used as the default backup location (the root of the DAS as well). If Seagate BlackArmor NAS is detected, its available licenses will be used and the backup location for One-Click Protection will be \\BlackArmorNAS_name\Public\Backups\computer_name.tib; for backing up the program will use the Seagate BlackArmor NAS by default.
Seagate BlackArmor Backup will take stock of your computer's configuration and then offer the optimum destination for backups.
For this purpose the program will use the following algorithm:
1) First of all the program estimates the space on the Seagate BlackArmor NAS or Seagate BlackArmor DAS drive required for operation of the One-Click Protection tool. As the average compression ratio when backing up data into tib files is 2:1, you can use this value as a guide. Let’s say your system partition has 20GB of programs and data. Under normal conditions, that will compress down to approximately 10GB and the disk space required for
18 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
operation of the One-Click Protection tool might amount to 10GB plus 250 MB for temporary files.
After applying this algorithm to your computer configuration, Seagate BlackArmor Backup will offer the optimum place for storing your backups. If you would prefer another storage location, click the Specify destination link and select the storage location most suitable for you.
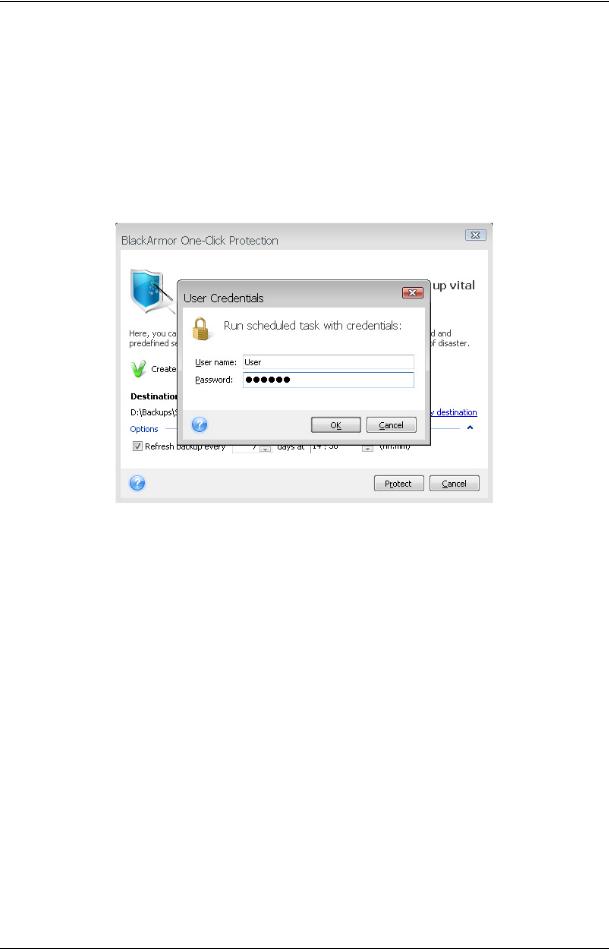
Clicking Protect will start the backup task. But before proceeding with the backup, the program will ask you under whose user credentials the subsequent scheduled backups will run.
Clicking Cancel will cancel One-Click Protection. If you decide to Home on the sidebar and then choose One-Click Protection Welcome screen.
use this feature later, click on the right pane of the
The system will always keep the last backup archive. When a task for another backup begins, the older backup is deleted – freeing space for the backup in progress.
If there is not enough free space on your Seagate BlackArmor NAS or DAS device (depending on which licenses you are using), the program will notify you that it cannot back up the system volume and will suggest that you specify a destination for backup yourself.
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
19 |
4.2 Program workspace
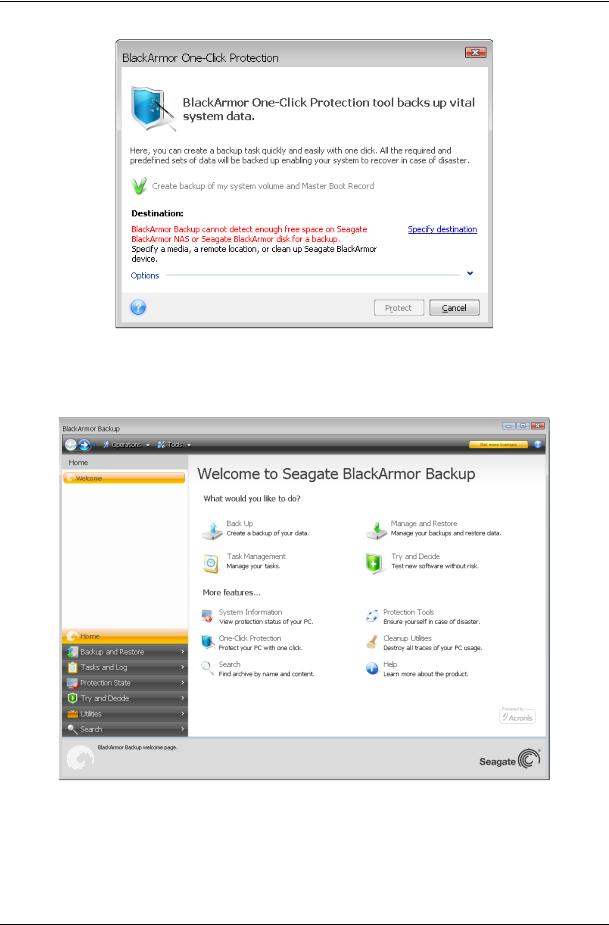
Starting Seagate BlackArmor Backup takes you to the Welcome screen. This screen provides quick access to practically all the program's functionality.
Clicking the items in the right pane takes you to the corresponding wizard or screen where you can either start the selected task or function right away or make further selections.
All the features listed in the right pane are duplicated on the left side of the screen occupied by the so called sidebar. The sidebar also provides easy access to all functionality of Seagate BlackArmor Backup. The main functions are listed in the lower part of the sidebar. If you choose an item in the lower part, the upper part of the sidebar displays subitems related to
20 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

the chosen item (if any) and the right part of the main window shows detailed information for the current subitem or a list of options available for that subitem.
Status bar
At the bottom of the main window, there is a status bar that briefly describes the selected operation or screen. If you select a backup archive, task or log, the status bar will show information on the selected item.
Taskbar notification area icon
During most of the operations, a special indicator icon appears in the Windows taskbar notification area (the right portion of the status bar with the clock). If you mouse over the icon, you will see a tool tip indicating the operation’s progress. Right-clicking on the icon opens a contextual menu where you can change process priority or cancel the operation if necessary. This icon doesn’t depend on the main program window being open. It is present for background execution of scheduled tasks as well.
Seagate BlackArmor Backup uses wizards, which guide you through many operations. Like the main program window, wizards also have the sidebar listing all the steps (both required and optional) needed for completing the operation. For example, see the Backup Wizard screenshot below.
The completed steps are marked with green checkmarks. The green arrow shows the current step. After you complete all the required steps, the Summary button becomes available. If you wish to omit the optional steps, click Summary, read the summary of the operation to be performed (to make sure that the default settings satisfy you) and then click Proceed to start the task. Otherwise proceed to the optional steps where you can change the default settings for the current task.
And now let's get acquainted with some other screens you will use while working with Seagate BlackArmor Backup. One of the most important and informative screens is Protection State. It shows a wealth of information on the protection state of your computer and permits taking measures that will enhance protection of your system (or provide it if the system is as of yet unprotected) – the screen has links for creating a system partition
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
21 |
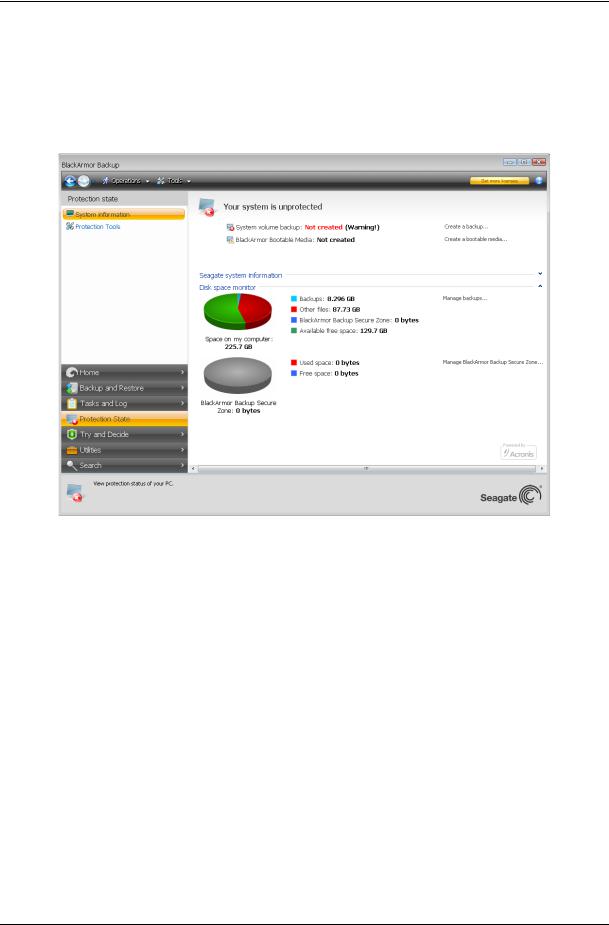
backup, and bootable rescue media. In addition, you will get information on the number of backup archives, as well as the date and time of the last backup, number of scheduled tasks and the last task result, and state of the Try&Decide mode. The screen also shows information on the state of your hard disks (total capacity, free space, space occupied by backup archives from Try&Decide and other files), information on the state of the BlackArmor Backup Secure Zone (free and occupied space).
To go to one more screen of interest, click Backup and Restore -> Manage and restore on the sidebar. This screen gives detailed information on your backup archives and provides for quickly performing operations on these archives – Restore, Validate, Remove, Consolidate, Update, Explore backup archives and Mount image backups by a single click on a button on the toolbar. Clicking the button starts the appropriate wizard or performs the appropriate action. On this screen you can assign ratings to your backups, for instance, you may want to assign a high rating to an important backup. A backup rating is indicated by the number of "stars" in the Rating column (more stars means higher rating). The default rating is three stars, but you can raise or lower it by clicking on the stars in the column. The assigned backup ratings may be helpful, for example, when sometime later you will need to consolidate the backups stored in an archive – it will be easier to choose which backups to keep after consolidation. For more information on manual backup consolidation see 11.4 Consolidating backups. In addition, these ratings might save you a lot of time you will otherwise spend on exploring multiple files in your backup archives trying to guess which of the outdated backups can be deleted without losing important data.
22 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
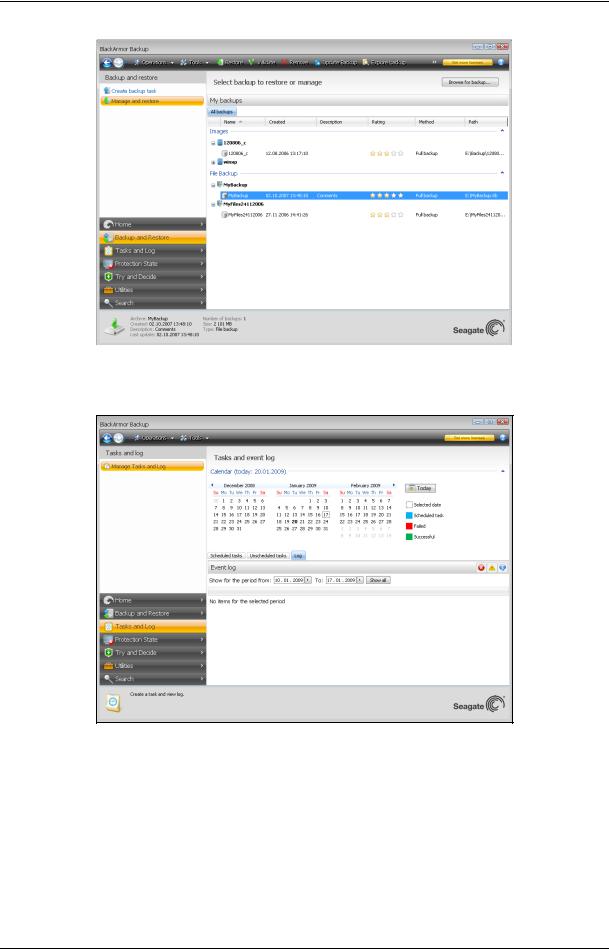
Another useful screen shows logs of program operations and scheduled tasks. A calendar provides quick access to the logs (for past dates) or tasks (for future dates). You just click on a desired date. For more information see 11.3 Viewing Tasks and Logs.
We will not bore you with a description of other screens, because many of them are selfexplanatory and some are described in the appropriate chapters of this guide. In addition, all screens have brief descriptions of the features they allow to access or use and you can always open contextual help by clicking the corresponding button.
By the way, you can also select all the features through the main program menu, which is always at your disposal on the toolbar.
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
23 |

Chapter 5. Creating backup archives
5.1 Selecting what data to back up
As operating systems and application software become ever larger (for example, Windows Vista x64 requires 15GB of free space on a hard disk), usually it will take you several hours to reinstall your operating system and application software from original CDs or DVDs on a new hard disk. Furthermore, the practice of buying application software by downloading from the Internet is becoming more and more popular. If you lose your registration information, for example, the activation key and/or registration number, which are usually sent by software vendors through e-mail, you may have problems with restoring your right to use the application. So making a backup of your entire system disk (making a disk image) will save you a lot of valuable time in case of a disaster, as well as safeguard you against other possible problems.
Backing up the entire system disk (creating a disk image) takes more disk space, but enables you to restore the system in minutes in case of a system crash or hardware failure. Moreover, the imaging procedure is much faster than copying files and could speed up the backup process significantly when it comes to backing up large volumes of data (see details in 3.1 The difference between file archives and disk/partition images).
You might think it would take a while to make a copy of your entire hard disk, but the proprietary technologies used in Seagate BlackArmor Backup ensure that image creation is quite fast. And the program can also back up incrementally or differentially, so after the first time, updating your image to reflect the current state of your hard disk requires only copying the files that are new or changed and will require much less time. Because images can save you a lot of time when you need to recover the operating system, it is recommended that you make them part of your backup strategy. In our opinion creating your system volume image backup is vital for protecting your computer system from a disaster, so now Seagate BlackArmor Backup offers to back up the system volume and Master Boot Record during the first start of the program after installation. For more information see 4.1 BlackArmor OneClick Protection.
Images, however, provide no defense against damaged files. If your hard disk contains damaged files when you are making an image, those problems will appear in the image as well.
For that reason, although we strongly recommend you to create images of your hard disk on a regular basis, that is just part of a reliable backup strategy. You should supplement the images with file archives.
Do you need file-level backups?
Do you have bank records, e-mails, photos, etc. you accumulated on your computer for several years? Hardware and software can be replaced, your personal data cannot.
Though there may be some exceptions, the optimal backup strategy for most users consists of creating both images and file-level backups.
After the initial full backup, file-level backups usually take comparatively little time to run, making it easy to back up your data once (or even several times) each day. This ensures that your most recent backup is never more than a day old. Because they also offer
24 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

insurance against accidental deletion (or change) and file damage, file-level backups are an essential part of a good backup strategy. But file-level backups alone are not sufficient for two main reasons:
1) If your startup hard drive completely fails, you won’t be able to do any work at all until you’ve replaced it; and 2) Reinstalling an operating system and applications from their original CDs or DVDs is a lengthy and arduous procedure that you could avoid (or speed up greatly) with an image of your hard disk.
You should create images of your primary disk and any other volume you normally use. If you have multiple partitions on a drive, it is advisable to include all of them in the image, because failure of the hard drive in most cases will mean that all the partitions it contains also fail.
Here are some more recommendations you can use to plan your backups. You should also keep your personal data separate from your operating system and applications. Such an arrangement allows speeding up the creation of data disk (or partition) images and reduces the amount of information you will need to restore.
5.2 Performing backup
1.Start Seagate BlackArmor Backup
2.Choose Backup and Restore in the lower area of the sidebar and the Create backup task item will be selected by default.
3.Select what type of data you want to back up.
Seagate BlackArmor Backup offers you the following backup types: My Computer (image backup of any set of disks/partitions)
My Data (file-level backup of any set of files, folders, or an entire file category) System State (file-level backup of system files, drivers, etc.)
My E-mail (file-level backup of Microsoft Outlook, Microsoft Outlook Express, and Windows Mail settings and messages).
My Application Settings (file-level backup of Windows applications settings)
File-level backup operations are supported only for the FAT and NTFS file systems.
Selecting a backup type starts the Backup Wizard, which will guide you through the steps of creating a backup task. You can also start the Backup Wizard by choosing Operations -> Backup in the main menu and then selecting a backup type. Depending on the backup type chosen, the number of steps in the Backup Wizard may change. For example, in case of backing up the System State, the program backs up predefined data and requires the minimum number of settings for configuring a backup task.
5.2.1 Selecting data for backup
When the Backup Wizard screen appears, select the data you wish to back up (in case of choosing the System State, this step will be omitted).
My Computer - select the disks or partitions to back up. You can select a random set of disks and partitions. The wizard's right pane shows the hard drives of your computer.
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
25 |

Selecting a hard drive results in selecting all partitions on that drive. If a hard drive has more than one partition, you may want to select individual partitions for backing up. To do so, click on the Down arrow at the right of the drive's line. Select the desired partition(s) in the displayed partition list. By default the program copies only the hard disk sectors that contain data. However, sometimes it might be useful to make a full sector-by-sector backup. For example, perhaps you deleted some files by mistake and want to make a disk image before trying to undelete them because sometimes un-deleting may create havoc in the file system. To make a sector-by-sector backup, select the Use the sector-by-sector approach box. Please note that this mode increases processing time and usually results in a larger image file because it copies both used and unused hard disk sectors. In addition, when configuring a sector-by-sector backup of a complete hard disk you can include in the backup unallocated space on the hard disk by selecting Back up unallocated space. Thus you will include in the backup all physical sectors on the hard drive.
My Data - select the file category(s) to back up: documents, finance, images, music, and video. Each category represents all files of associated types found on the computer’s hard drives. Furthermore, you can add any number of custom categories containing files and folders. The new categories will be remembered and displayed along with the above. You can change contents of any custom or default file category (edit the category) or delete it. The default file categories cannot be deleted.
For more information on custom categories see 5.3.11 Creating a custom data category for backups. If you do not want to keep custom contents of the current backup by creating a data category, simply select the files/folders from the tree. This set will be effective only for the current backup task. File filtering can be applied to manually added folders in the optional Source files exclusion step.
My Application Settings - back up custom settings of Windows applications. This is a subset of file-level backup that backs up predefined folders and requires minimum user selections. The program displays a list of supported applications that has been found on the computer, sorted by categories. You can select a random set of categories and applications.
It is important to note that the program backs up only your settings, and not the application executable files. If an application seems to malfunction or ceases to run, reinstall it using the last updates and then recover your settings from the backup.
To select all the supported applications found on the computer for backing up, check the Installed Applications box. For instant messenger applications, the program will back up both the settings and history.
The list of supported applications will be expanded gradually. Updates will be available with new program builds or via the Internet.
My E-mail - Seagate BlackArmor Backup offers a straightforward way to back up messages, accounts and settings for Microsoft Outlook 2000, 2002, 2003, 2007, Microsoft Outlook Express, and Windows Mail. E-mail backup is a subset of file-level backups that backs up predefined folders and requires minimum user selections. However, if need be, you can select Microsoft Outlook components and folders individually. The list of supported e-mail clients will be gradually built up. Updates will be available with new program builds or via the Internet.
You can select the following items:
Messages contained in .PST/.DBX Database Files
26 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |

E-mail accounts
For Microsoft Office Outlook 2000, 2002, 2003, 2007
Mail Folders Calendar Contacts Tasks Notes Signatures
News Folders
User Settings
Address Book
For Microsoft Outlook Express
Mail Folders
Address Book (select Windows Address Book).
Seagate BlackArmor Backup provides backup of IMAP (Internet Messages Access Protocol) mail folders for Microsoft Outlook. This means that you can back up folders stored on a mail server. For Microsoft Outlook Express and Windows Mail only local e-mail folders backup is available.
5.2.2 Selecting the target archive location
Select the destination location for the backup and specify the archive name.
If a Seagate BlackArmor DAS is detected during the first start, it will be used as the default backup location (the root of the DAS). Otherwise, a Product Activation dialog will appear during the first launch of Seagate BlackArmor Backup, where you can select Seagate BlackArmor NAS, so it will be used as a backup location by default.
If you are going to create a new archive (i.e. perform a full backup), select Create new backup archive and enter the path to the archive location and new archive file name in the Backup Location: field below or click Browse, select the archive location on the directory tree and enter the new file name in the File name line, or use the file name generator (a button to the right of the line).
When you have chosen the My Data backup type for backing up files and/or folders, you can select the zip archive type. For more information see 3.7 Support for Zip format.
If you want to append an incremental or differential backup file to an existing archive, select Add to existing backup archive and click the Select button to select the existing archive you are going to update. If the archive already has incremental or differential backups, you can select any of the target archive files. It doesn't matter which one you select, as the program recognizes them as a single archive.
If you want to change the location of added backup files, browse for a new backup location after clicking the Browse button, otherwise leave the location the same as that of the existing archive.
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
27 |
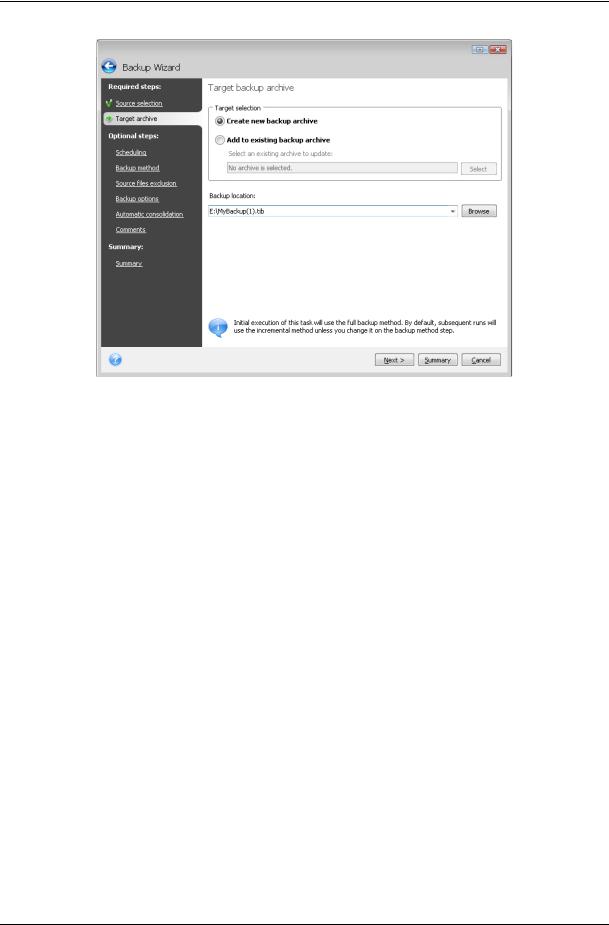
After selecting the archive location and naming the backup archive to be created, you have completed all the required steps for a backup task and this is confirmed by the fact that the Summary button becomes selectable. All the remaining steps are optional and in many cases you may omit them and just click Summary and then Proceed on the Summary page. For example, when you want to proceed with backup right away, you can omit the Scheduling step. If you do not want to exclude any files from the backup, you can omit the Source files exclusion step. When you want to use the default backup options, you can omit the Backup options step, and so on.
Now let's see what optional steps you can set up while configuring a backup task.
5.2.3 Scheduling
By default, the Do not schedule option is chosen so the task will run after completing the wizard and clicking Proceed on the Summary page. However, you may wish to schedule the task being configured by choosing one of the scheduling options.
28 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
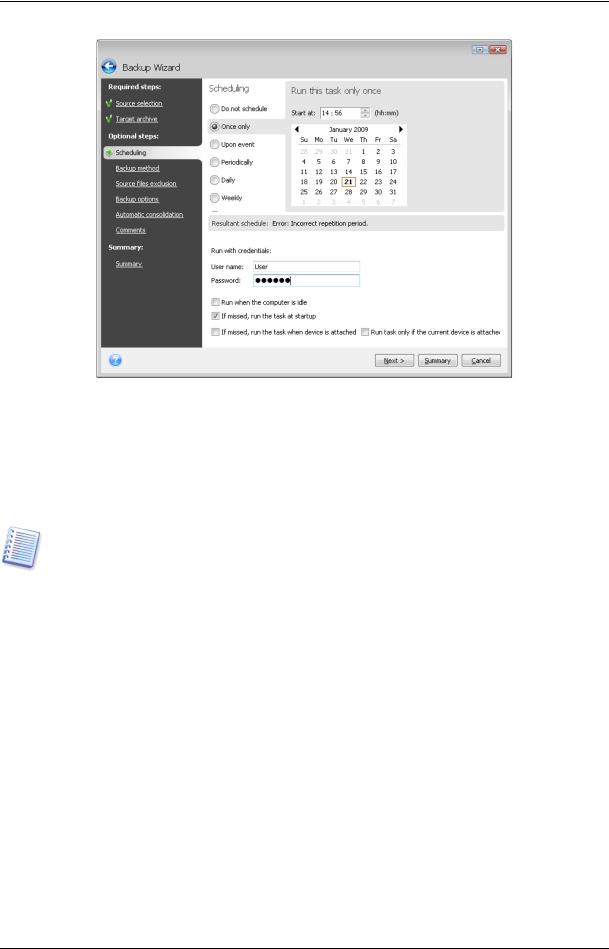
For more information see Chapter 8. Scheduling tasks.
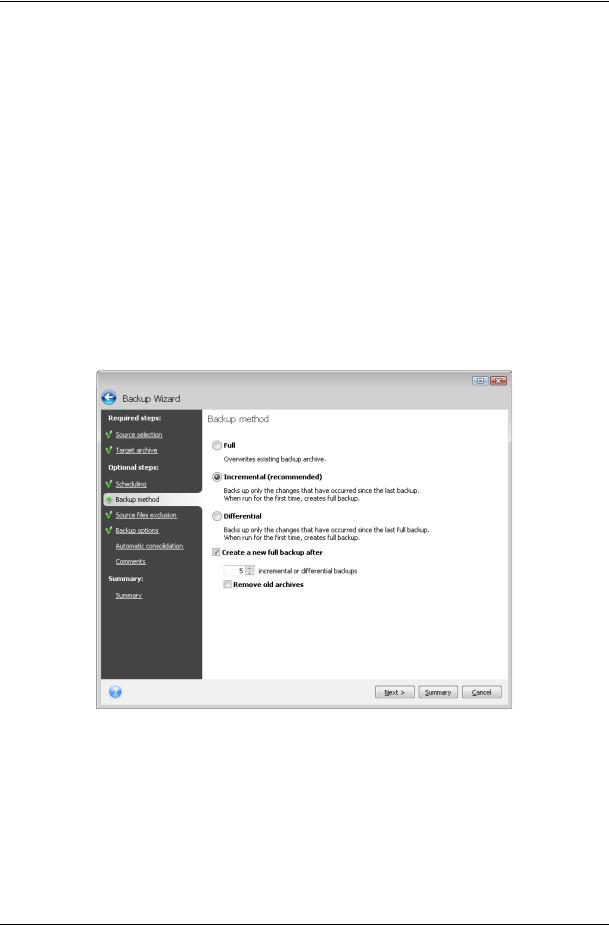
5.2.4 Backup method
Select whether you want to create a full, incremental or differential backup. If you have not backed up the selected data yet, or the full archive is old and you want to create a new master backup file, choose full backup. Otherwise it is recommended that you create an incremental or differential backup (see 3.2 Full, incremental and differential backups).
If you select the Full method, the Automatic consolidation step (see 5.2.7 Setting automatic consolidation) will be disabled. If you are adding a backup to the existing backup archive, the Full method will be unselectable.
You can set a backup policy for the backup task. Seagate BlackArmor Backup offers three types of backup policies:
1)create full backups only
2)create full backups after a specified number of incremental backups
3)create full backups after a specified number of differential backups
When the first backup on a schedule is executed, a full backup will be created. If you choose
(2) or (3) by selecting the Create a new full backup after box, the next backups will be incremental (or differential) until the specified number of incremental (differential) backups is reached. After the selected number of incremental or differential backups is made, the next time a new full backup and a set of subsequent incremental (differential) backups will be created; this process will then continue until you decide to change it.
When the Remove old archives box is selected, creation of a new full backup in accordance with the specified backup policy results in deletion of the complete old backup chain – the old full backup and its subsequent incremental (or differential) backups regardless of the overall limitations you set on the archive at the Automatic consolidation step.
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
29 |
If you decide to keep old backups (by not selecting the Remove old archives box) and creation of a new full backup results in violation(s) of the limits set for automatic consolidation, the program will use the following algorithm:
1)if the actual number of backups exceeds the maximum number of backups, the program automatically consolidates the old full backup with the oldest incremental (differential) one to correct this quota violation;
2)if after correcting the number of backups limit violation there remains other quota violation(s), the program consolidates the oldest backup to correct the storage period of old backups limit violation (if possible - otherwise it deletes the old full backup);
3)if after correcting the storage period of old backups limit violation there remains the archive size limit violation, the program consolidates the old full backup with the oldest incremental (differential) one, then will repeat consolidation (if necessary and possible);
4)if after consolidating all the previous backups the archive size quota violation remains, the old backup archive will be deleted in order to correct the violation;
5)if the new full backup file size exceeds the archive size limit, the program will record a warning into the logs.
5.2.5 Source files exclusion
This step will be present only for the My Computer and My Data backup types. It enables you to exclude unnecessary files from your backup in case when you just want to exclude some file types without creating custom categories. You can exclude hidden or system files and folders, as well as files matching the criteria you specify. You can add your own criteria by clicking Add. While adding criteria, you can use the common Windows wildcard characters and type several criteria in the same line separating them by semicolons. For example, to exclude all files with .gif and .bmp extensions, you may type *.gif;*.bmp. One more thing – if, for example, you want to exclude all the files with the name of test regardless of their extension, you should specify exclusion criteria such as test.*, otherwise
30 |
Copyright (c) 2000-2009 Acronis. All rights reserved. |
|
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. |
 Loading...
Loading...