Brocade FICON User Manual

53-1003144-01
27 June 2014
FICON
Administrator's Guide
Supporting Fabric OS v7.3.0

©
2014, Brocade Communications Systems, Inc. All Rights Reserved.
Brocade, the B-wing symbol, Brocade Assurance, ADX, AnyIO, DCX, Fabric OS, FastIron, HyperEdge, ICX, MLX, MyBrocade, NetIron,
OpenScript, VCS, VDX, and Vyatta are registered trademarks, and The Effortless Network and the On-Demand Data Center are trademarks
of Brocade Communications Systems, Inc., in the United States and in other countries. Other brands and product names mentioned may be
trademarks of others.
Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any
equipment, equipment feature, or service offered or to be offered by Brocade. Brocade reserves the right to make changes to this document
at any time, without notice, and assumes no responsibility for its use. This informational document describes features that may not be
currently available. Contact a Brocade sales office for information on feature and product availability. Export of technical data contained in
this document may require an export license from the United States government.
The authors and Brocade Communications Systems, Inc. assume no liability or responsibility to any person or entity with respect to the
accuracy of this document or any loss, cost, liability, or damages arising from the information contained herein or the computer programs that
accompany it.
The product described by this document may contain open source software covered by the GNU General Public License or other open
source license agreements. To find out which open source software is included in Brocade products, view the licensing terms applicable to
the open source software, and obtain a copy of the programming source code, please visit http://www.brocade.com/support/oscd.

Contents
Preface.....................................................................................................................................5
Document conventions......................................................................................5
Text formatting conventions.................................................................. 5
Command syntax conventions.............................................................. 5
Notes, cautions, and warnings.............................................................. 6
Brocade resources............................................................................................ 7
Contacting Brocade Technical Support.............................................................7
Document feedback.......................................................................................... 8
About This Document................................................................................................................ 9
Supported hardware and software.................................................................... 9
Additional FICON resources............................................................................. 9
What’s new in this document............................................................................ 9
Introducing FICON...................................................................................................................11
FICON overview..............................................................................................11
Fabric OS support for FICON..............................................................11
Latency guideline................................................................................ 12
FICON concepts..............................................................................................13
FICON configurations......................................................................................14
Switched point-to-point........................................................................15
Cascaded FICON................................................................................15
Access control in FICON.................................................................................23
Cascaded zoning................................................................................ 24
Error reporting..................................................................................... 26
Secure access control.........................................................................26
FICON commands.......................................................................................... 28
Link and FC addressing.................................................................................. 30
Domain ID........................................................................................... 31
Port area............................................................................................. 31
ALPA................................................................................................... 31
Administering FICON Fabrics...................................................................................................33
User security considerations........................................................................... 33
Meeting high-integrity fabric requirements...................................................... 33
Enabling the insistent domain ID.........................................................34
Creating and activating the SCC policy...............................................34
Enabling the fabric-wide consistency policy........................................35
Enabling High-Integrity Fabric mode...................................................35
Using other security commands..........................................................36
Preparing a switch for FICON......................................................................... 36
Cascaded FICON and two-byte addressing considerations............... 37
Configuring switched point-to-point FICON.....................................................37
Configuring cascaded FICON......................................................................... 41
FCR and FICON cascading............................................................................ 42
FICON and FICON CUP in Virtual Fabrics..................................................... 43
Addressing modes.......................................................................................... 44
FICON Administrator's Guide
1
53-1003144-01

Mode 0 (10-bit addressing)............................................................... 44
Mode 1 (zero-based addressing)...................................................... 45
Mode 2 (port-based addressing).......................................................45
Changing the addressing mode........................................................ 45
FICON and blade support for addressing modes............................. 46
Port swap limitations......................................................................... 46
Disabling and enabling ports - persistent states........................................... 46
Clearing the FICON management database.................................................47
Automating CS_CTL mapping...................................................................... 47
FICON best practices....................................................................................49
Latency guideline.......................................................................................... 50
Configuring FICON CUP.........................................................................................................51
Control Unit Port overview............................................................................ 51
FICON CUP restrictions....................................................................52
CUP configuration recommendations............................................... 53
FICON CUP zoning and PDCM considerations................................54
Port and switch naming standards for FMS mode........................................ 54
FICON CUP Fabric OS commands...................................................54
Configuring FICON CUP...............................................................................55
Disabling ports 0xFE and 0xFF.........................................................55
Configuring FICON CUP in Virtual Fabrics....................................... 56
Determining physical port assignment ......................................................... 56
FMS mode and FICON CUP.........................................................................56
Fabric OS command limitations and considerations.........................57
Displaying FMS mode.......................................................................58
Enabling FMS mode..........................................................................58
Disabling FMS mode.........................................................................58
Resetting FMS mode........................................................................ 58
FMS mode and FICON OxFE or OxFF ports....................................58
Upgrade considerations.................................................................... 59
Port swap limitations......................................................................... 60
Mode register bit settings..............................................................................60
FICON file access facility.................................................................. 61
Considerations for setting mode register bits....................................63
Setting the mode register bits........................................................... 63
Setting the MIHPTO value............................................................................ 63
Persistently enabling and disabling ports for CUP........................................64
Administering FICON Extension Services................................................................................65
Platforms supporting FICON extension over IP............................................ 65
FICON emulation overview........................................................................... 65
IBM z/OS Global Mirror emulation.................................................... 66
Tape emulation................................................................................. 67
Printer emulation...............................................................................69
Teradata emulation........................................................................... 70
FCIP configuration requirements for FICON extension................................ 70
Configuration requirements for switches and backbones............................. 70
High-integrity fabric requirements for cascaded configurations........ 71
FICON emulation requirement for a determinate path......................71
Configuring FICON emulation.......................................................................72
Configuration examples.................................................................... 72
Displaying FICON emulation configuration values............................73
Modifying FICON emulation..........................................................................73
Displaying FICON emulation performance statistics.....................................73
FICON emulation monitoring.............................................................74
2
FICON Administrator's Guide
53-1003144-01

Options for displaying statistics...........................................................75
Maintaining and Troubleshooting FICON..................................................................................77
Firmware management in a FICON environment........................................... 77
Upgrade and downgrade considerations............................................ 77
Firmware download disruption............................................................ 77
Non-disruptive firmware upload and download................................... 78
Configuration restoration in a FICON environment......................................... 78
Traffic Isolation Zoning....................................................................................79
Determining ports for the TI Zone....................................................... 80
Enhanced TI Zoning............................................................................80
Monitoring and Alerting Policy Suite............................................................... 87
Port fencing..................................................................................................... 87
Defining port fencing........................................................................... 87
Settings for FICON environments....................................................... 88
FICON information.......................................................................................... 88
Link incidents...................................................................................... 88
Registered listeners............................................................................ 89
Node identification data.......................................................................89
FRU error reporting............................................................................. 89
Swapping port area IDs...................................................................................91
Important notes................................................................................... 91
Blade swapping...............................................................................................91
Common FICON issues.................................................................................. 92
Troubleshooting FICON.................................................................................. 95
General information to gather for all cases......................................... 95
Switched point-to-point topology checklist.......................................... 96
Cascaded topology checklist...............................................................97
Gathering additional information......................................................... 97
CUP diagnostics..................................................................................97
Troubleshooting FICON CUP..........................................................................97
Troubleshooting NPIV..................................................................................... 98
Platforms Supporting FICON....................................................................................................99
Introduction..................................................................................................... 99
Supported platforms with end-of-support announcements............................. 99
Currently supported platforms.......................................................................100
Supported Brocade blades............................................................................101
Unsupported blades.......................................................................... 102
Basic Switch Configuration................................................................................................... 103
Address Binding Examples....................................................................................................107
Sequential address binding...........................................................................107
Example scripts for binding ports...................................................... 108
Port-based address binding.......................................................................... 112
Example scripts for binding ports...................................................... 112
Unbinding multiple ports................................................................................116
Configuration Information Record......................................................................................... 117
FICON Administrator's Guide
3
53-1003144-01

EBCDIC Code Page............................................................................................................. 119
Index..................................................................................................................................121
4 FICON Administrator's Guide
53-1003144-01

Preface
● Document conventions......................................................................................................5
● Brocade resources............................................................................................................ 7
● Contacting Brocade Technical Support.............................................................................7
● Document feedback.......................................................................................................... 8
Document conventions
The document conventions describe text formatting conventions, command syntax conventions, and
important notice formats used in Brocade technical documentation.
Text formatting conventions
Text formatting conventions such as boldface, italic, or Courier font may be used in the flow of the text
to highlight specific words or phrases.
Format
Description
bold text
Identifies command names
Identifies keywords and operands
Identifies the names of user-manipulated GUI elements
Identifies text to enter at the GUI
italic text
Identifies emphasis
Identifies variables and modifiers
Identifies paths and Internet addresses
Identifies document titles
Courier font
Identifies CLI output
Identifies command syntax examples
Command syntax conventions
Bold and italic text identify command syntax components. Delimiters and operators define groupings of
parameters and their logical relationships.
Convention
Description
bold text Identifies command names, keywords, and command options.
italic text Identifies a variable.
FICON Administrator's Guide 5
53-1003144-01
Convention Description
value In Fibre Channel products, a fixed value provided as input to a command
option is printed in plain text, for example, --show WWN.
[ ]
Syntax components displayed within square brackets are optional.
Default responses to system prompts are enclosed in square brackets.
{ x | y | z }
A choice of required parameters is enclosed in curly brackets separated by
vertical bars. You must select one of the options.
In Fibre Channel products, square brackets may be used instead for this
purpose.
x | y
A vertical bar separates mutually exclusive elements.
< >
Nonprinting characters, for example, passwords, are enclosed in angle
brackets.
...
Repeat the previous element, for example, member[member...].
\
Indicates a “soft” line break in command examples. If a backslash separates
two lines of a command input, enter the entire command at the prompt without
the backslash.
Notes, cautions, and warnings
Notes, cautions, and warning statements may be used in this document. They are listed in the order of
increasing severity of potential hazards.
NOTE
A Note provides a tip, guidance, or advice, emphasizes important information, or provides a reference
to related information.
ATTENTION
An Attention statement indicates a stronger note, for example, to alert you when traffic might be
interrupted or the device might reboot.
CAUTION
A Caution statement alerts you to situations that can be potentially hazardous to you or cause
damage to hardware, firmware, software, or data.
DANGER
A Danger statement indicates conditions or situations that can be potentially lethal or
extremely hazardous to you. Safety labels are also attached directly to products to warn of
these conditions or situations.
Notes, cautions, and warnings
6 FICON Administrator's Guide
53-1003144-01
Brocade resources
Visit the Brocade website to locate related documentation for your product and additional Brocade
resources.
You can download additional publications supporting your product at www.brocade.com. Select the
Brocade Products tab to locate your product, then click the Brocade product name or image to open the
individual product page. The user manuals are available in the resources module at the bottom of the
page under the Documentation category.
To get up-to-the-minute information on Brocade products and resources, go to MyBrocade. You can
register at no cost to obtain a user ID and password.
Release notes are available on MyBrocade under Product Downloads.
White papers, online demonstrations, and data sheets are available through the Brocade website.
Contacting Brocade Technical Support
As a Brocade customer, you can contact Brocade Technical Support 24x7 online, by telephone, or by e-
mail. Brocade OEM customers contact their OEM/Solutions provider.
Brocade customers
For product support information and the latest information on contacting the Technical Assistance
Center, go to http://www.brocade.com/services-support/index.html.
If you have purchased Brocade product support directly from Brocade, use one of the following methods
to contact the Brocade Technical Assistance Center 24x7.
Online Telephone E-mail
Preferred method of contact for non-
urgent issues:
• My Cases through MyBrocade
• Software downloads and
licensing tools
• Knowledge Base
Required for Sev 1-Critical and Sev
2-High issues:
• Continental US:
1-800-752-8061
• Europe, Middle East, Africa,
and Asia Pacific: +800-AT
FIBREE (+800 28 34 27 33)
• For areas unable to access toll
free number: +1-408-333-6061
• Toll-free numbers are available
in many countries.
support@brocade.com
Please include:
• Problem summary
• Serial number
• Installation details
• Environment description
Brocade OEM customers
If you have purchased Brocade product support from a Brocade OEM/Solution Provider, contact your
OEM/Solution Provider for all of your product support needs.
Brocade resources
FICON Administrator's Guide 7
53-1003144-01

• OEM/Solution Providers are trained and certified by Brocade to support Brocade
®
products.
• Brocade provides backline support for issues that cannot be resolved by the OEM/Solution
Provider.
• Brocade Supplemental Support augments your existing OEM support contract, providing direct
access to Brocade expertise. For more information, contact Brocade or your OEM.
• For questions regarding service levels and response times, contact your OEM/Solution Provider.
Document feedback
To send feedback and report errors in the documentation you can use the feedback form posted with
the document or you can e-mail the documentation team.
Quality is our first concern at Brocade and we have made every effort to ensure the accuracy and
completeness of this document. However, if you find an error or an omission, or you think that a topic
needs further development, we want to hear from you. You can provide feedback in two ways:
• Through the online feedback form in the HTML documents posted on www.brocade.com.
• By sending your feedback to documentation@brocade.com.
Provide the publication title, part number, and as much detail as possible, including the topic heading
and page number if applicable, as well as your suggestions for improvement.
Document feedback
8 FICON Administrator's Guide
53-1003144-01

About This Document
● Supported hardware and software.................................................................................... 9
● Additional FICON resources............................................................................................. 9
● What’s new in this document............................................................................................ 9
Supported hardware and software
Although many different software and hardware configurations are tested and supported by Brocade
Communications Systems, Inc. for Fabric OS v7.3.0 documenting all possible configurations and
scenarios is beyond the scope of this document.
For a complete list of platforms supported by FICON and Fabric OS v7.3.0, refer to Platforms
supporting FICON on page 99 Platforms supporting FICON.
In cases where procedures or parts of procedures do not apply to all Brocade hardware platforms, this
guide identifies which platforms are supported.
Additional FICON resources
In addition to Brocade product resources listed under "Brocade Resources" in this Preface, a dedicated
page for mainframe resources is located at Mainframe and FICON Solutions.
What’s new in this document
The following information was added or changed in this document:
• Added information on Brocade 7840 extension switch to various parts of Administering FICON
Extension Services and information on the FC16-64 blade to Supported Brocade blades on page
101.
• Created FCR and FICON cascading on page 42 in Administering FICON Fabrics.
• Created Disabling and enabling ports - persistent states on page 46 in Administering FICON
Fabrics.
• Created Meeting high-integrity fabric requirements on page 33 in Administering FICON Fabrics.
• Created Extended fabric configurations on page 17 in Introducing FICON.
• Added step to configure High-Integrity Fabric Mode in Configuring cascaded FICON on page 41.
• Added Resetting FMS mode on page 58.
• Added notes in various locations, such as in Configuring FICON CUP on page 55 and FMS mode
and FICON CUP on page 56, that High-Integrity Fabric mode must be configured to enable FMS
mode.
• Added definition of IPL file in FICON concepts on page 13.
FICON Administrator's Guide
9
53-1003144-01

• Added notes wherever configupload command mentioned that it backs up Fabric OS feature and
switch configuration, but not FMS and FICON-specific configuration.
• Added notes wherever enabling FMS mode is described that all high-integrity fabric attributes
must be configured and HIF mode enabled to enable FMS mode.
• Changed Moving ports to a logical switch section to Disabling and enabling ports - persistent
states on page 46 and added details comparing port persistent enable and disable states with
interactions of ASM Mode setting, IPL state, and use of portdisable and portenable commands.
• Added note in Upgrade considerations on page 59 that upgrading the Fabric OS v7.3.0 and
later from v7.2.1 and earlier requires high-integrity fabric attributes configured and HIF mode
enabled.
• Added note under "Routing policies" bullet in Fabric OS support for FICON on page 11 that
System z FICON does not support exchange-based routing.
• Added note under "Insistent Domain ID (IDID)" bullet that IDID is the recommended best practice
for single-byte addressing.
• Added Extended fabric configurations on page 17.
• Added sentence to Firmware download disruption on page 77 about FCIP Hot Code Load
feature on Brocade 7840 switch.
• Added Monitoring and Alerting Policy Suite on page 87.
• In Basic Switch Configuration, changed step to enable port-based routing policy to device-based
routing policy.
About This Document
10 FICON Administrator's Guide
53-1003144-01

Introducing FICON
● FICON overview..............................................................................................................11
● FICON concepts..............................................................................................................13
● FICON configurations......................................................................................................14
● Access control in FICON.................................................................................................23
● FICON commands.......................................................................................................... 28
● Link and FC addressing.................................................................................................. 30
FICON overview
IBM Fibre Connection (FICON
®
) is an industry-standard, high-speed input/output (I/O) interface for
mainframe connections to storage devices. This guide discusses support offered by Fabric OS in
intermix mode operations, in which FICON and Fibre Channel technology work together.
For specific information about intermix mode and other aspects of FICON, refer to the IBM Redbook,
FICON
®
Implementation Guide (SG24-6497-01), and Implementing an IBM/Brocade SAN with 8 Gbps
Directors and Switches (SG24-6116-08).
NOTE
In this guide, the term switch is used to refer to a Brocade switch, Backbone, or backbone platform
unless otherwise noted.
Fabric OS support for FICON
The following Fabric OS standard features support FICON fabrics:
• Blade swapping
Allows you to swap a blade of the same type so that you can replace a field-replaceable unit (FRU)
with minimal traffic disruption. This feature is available for both FICON and open system
environments. Blade swapping resolves situations in which the hardware has failed and the
channel configurations cannot be changed quickly. In addition, a blade swap minimizes and
eliminates the need to make changes to the I/O sysgen in the hardware configuration definition
(HCD). Blade swapping has minimal or no impact on other switch features.
• Routing policies
System z FICON did not support exchange-based routing as of the publication date of this
document, but does support port-based and device- based routing. For details on these policies,
refer to the "Routing Traffic" chapter in the Fabric OS Administrator's Guide.
• FICON MIB module
Addresses link incident data for FICON hosts and devices connected to a switch. The FICON MIB
module supplements other Management Information Bases (MIBs) used to manage switches and
should be used in conjunction with those other MIBs.
• Insistent Domain ID (IDID)
FICON Administrator's Guide
11
53-1003144-01
Disables the dynamic domain ID feature and only allows the switch to use a pre-set domain ID. All
switches in a fabric must have a unique domain ID. An insistent domain ID is required with 2-byte
addressing. IDID is the recommended best practice for single byte addressing.
• Link incident detection, registration, and reporting
Provides administrative and diagnostic information.
• Swap port area IDs (PIDs) of physical ports
Redirects resources from a failed port to a healthy port without changing the mainframe hardware
configuration definition (HCD) settings. This feature, also called "port swapping," is available for
both FICON and open system environments. Swapping PIDs on ports resolves situations in which
the hardware has failed and the channel configurations cannot be changed quickly. Port swpping
has minimal or no impact on other switch features.
• Switch connection control (SCC) policy
Includes fabric security methods that prevent unauthorized switches from joining a fabric. SCC
policy is required for cascaded FICON configurations and whenever 2-byte addressing is used.
• Traffic Isolation (TI) Zones and Enhanced TI Zones
TI Zones are used to direct traffic across links through a specified path. Enhanced TI Zones allow
you to have ports in more than one TI Zone and to program domain controller routes to
destination domains for F-class traffic, ensuring fabric stability.
NOTE
For more detail on these features and configuration procedures, refer to the Fabric OS Administrator's
Guide.
Brocade management tools provide further support:
• Brocade Network Advisor
Brocade Network Advisor is an optional software program that can be used to manage a fabric
that supports FICON and Fibre Channel Protocol (FCP) devices and traffic. This is the
recommended GUI management tool for FICON environments on B-series enterprise-class
switches. For more information on Brocade Network Advisor, refer to the manual appropriate for
your version requirements:
‐ Brocade Network Advisor SAN + IP User Manual
‐ Brocade Network Advisor SAN User Manual
• Web Tools
Web Tools is an embedded GUI-management tool that can be used to manage a Brocade switch
or backbone that supports FICON and Fibre Channel Protocol (FCP) devices and traffic. For more
information on Web Tools, refer to the Web Tools Administrator's Guide.
Latency guideline
The maximum supported distance for a FICON channel is 300 Km (1.5 msec of delay). Synchronous
mirroring applications are generally limited to 100 Km (0.5 msec of delay). Greater distances require
that the FICON Acceleration feature be used with FCIP. The FICON Acceleration feature emulates
control unit response to the channel to make the devices appear closer to the channel than they
actually are.
Latency guideline
12 FICON Administrator's Guide
53-1003144-01
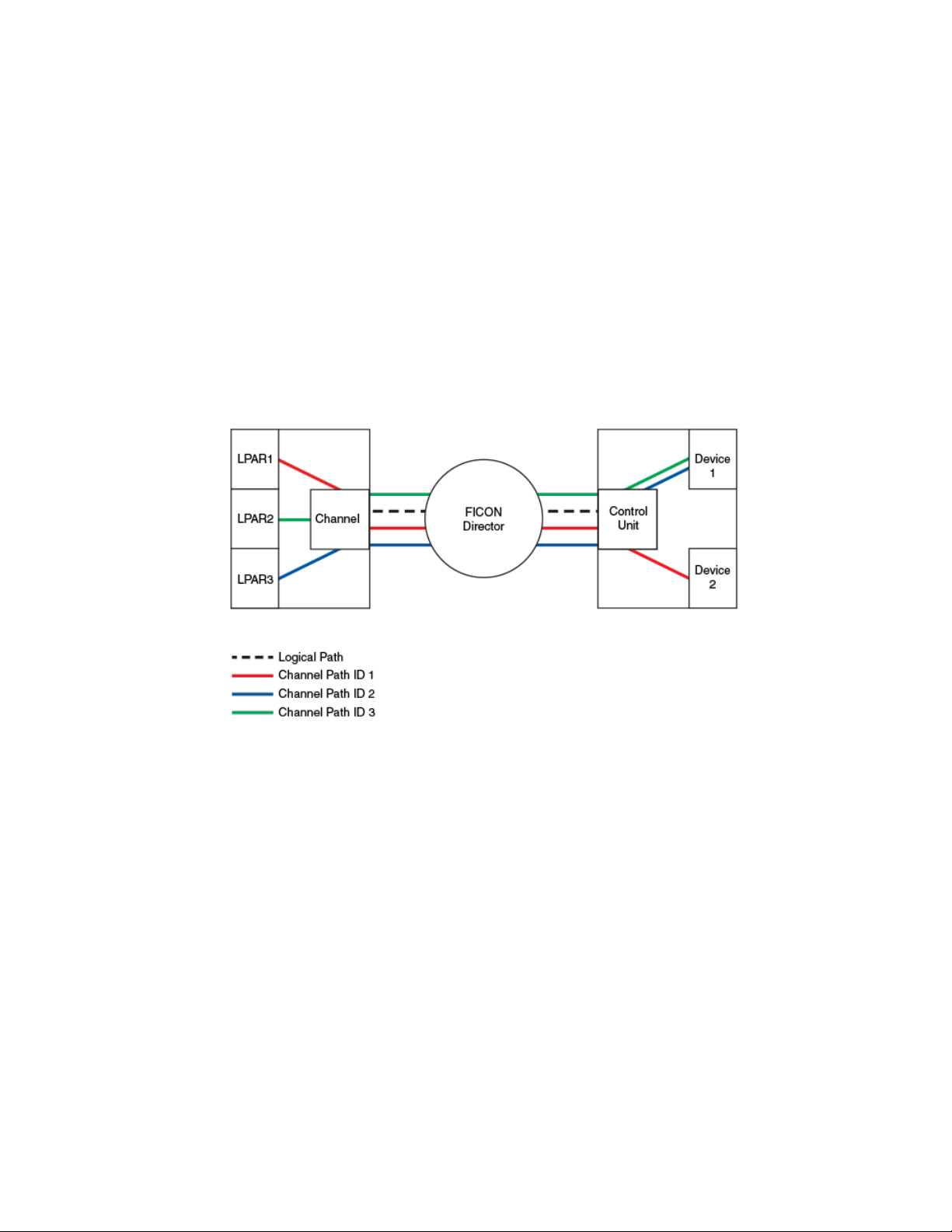
FICON concepts
The following figure shows how the traffic in a switched point-to-point configuration flows in a FICON
environment. The logical path of the traffic is defined as frames moving from the channel to the switch
to the control unit. FICON traffic moves from a logical partition (LPAR) and through the channel, through
a Fibre Channel link to the switch through the control unit, and ends at the device. This is also called a
channel path , which is a single interface between a central processor and one or more control units
along which signals and data can be sent to perform I/O requests. The channel path uses the logical
path to traverse the Fibre Channel fabric. The channel path is defined using an ID, called the channel
path ID (CHPID). This information is stored in the Input/Output Definition File (IODF) and may be
dynamically configured using the mainframe feature, zDAC (Discover and Auto Configuration). The
IODF is typically built using the hardware configuration definition (HCD).
FIGURE 1 FICON traffic
The traffic on the channel path communicates using channel command words (CCWs) that direct the
device to perform device-specific actions, such as seek, read, or rewind. In a FICON environment,
buffer credits are used at the Fibre Channel Protocol (FCP) level for flow control between optically
adjacent ports, while information unit (IU) pacing is the flow control mechanism used by the channel.
There are times when there are no more buffer credits to pass back to the other end of the link and a
frame pacing delay occurs. Frame pacing delay is the number of intervals of 2.5 microseconds that a
frame had to wait to be transmitted due to a lack of available buffer credits. Frame pacing delay
information is reported in the FICON Director Activity Report with the System z RMF feature.
FICON introduces the following concepts:
• FICON Control Unit Port (CUP)
The internal port in a switch that assumes an Fibre Channel (FC) address such that it is the FC
domain ID (DID) used to direct FICON traffic to the FICON Management Server (FMS).
• FICON Manager
Host communication includes control functions such as blocking and unblocking ports, as well as
monitoring and error-reporting functions.
• Hardware configuration definition (HCD)
HCD is an IBM interactive interface application that allows you to define the hardware configuration
for both the processor channel subsystem and the operating system running on the processor.
• Information unit
FICON concepts
FICON Administrator's Guide 13
53-1003144-01

A unit of FICON data consisting of from one to four Fibre Channel frames.
• Link Incident Record Registration (LIRR)
The LIRR Extended Link Service (ELS) requests that the recipient add the requesting port to its
list of ports that are to receive a Registered Link Incident Report (RLIR).
• Node
A node is an endpoint that contains information. It can be a computer (host), a device controller,
or a peripheral device, such as a disk array or tape drive. A node has a unique 64-bit identifier
known as the Node_Name. The Node_Name is typically used for management purposes.
• Prohibit Dynamic Connectivity Mask (PDCM) and connectivity attributes
PDCM controls whether communication between a pair of ports in the switch is prohibited.
Connectivity attributes control whether all the communication is blocked for a port.
• Read Record Set (RRS)
RRS is an IBM Channel-initiated CCW command. The Brocade FCIP FICON Acceleration
License allows the emulation of command chains that include this CCW command. The command
is used in IBM z/OS Global Mirror configurations to read updates from a volume in an active
mirroring session.
• Registered Link Incident Report (RLIR)
RLIR ELS provides a way for a node port to send an incident record to another node port.
• Request Node Identification Data (RNID)
RNID ELS acquires the associated node’s identification data, which provides configuration
discovery and management purpose information.
• Resource Measurement Facility (RMF)
Performance monitoring software that gathers transaction data from the environment and
generates performance reports. All Level II reports, which include port statistics, require the
FICON Control Unit Port (CUP) and FICON Management Server (FMS).
• Systems Operations (SysOps)
SysOps provides the ability to monitor and control all subsystems in a sysplex from any system in
the sysplex. This includes controlled startup, controlled shutdown, and automated recovery of
software resources.
• Sysplex
In IBM mainframe computers, a Systems Complex, commonly called a sysplex, allows multiple
processors to be joined into a single unit, sharing the same sysplex name and Couple Data Sets.
• IPL file
The initial program load (IPL) File, located in nonvolatile storage, contains the current, active
configuration settings for the FICON director. If functions to initialize data on the Director during a
POR event. When the "Active=Saved" FICON CUP mode register bit setting is on, any active
configuration in switch memory is automatically saved to the IPL file.
FICON configurations
There are two types of FICON configurations that are supported using Brocade Fabric OS: switched
point-to-point and cascaded topologies.
FICON configurations
14 FICON Administrator's Guide
53-1003144-01
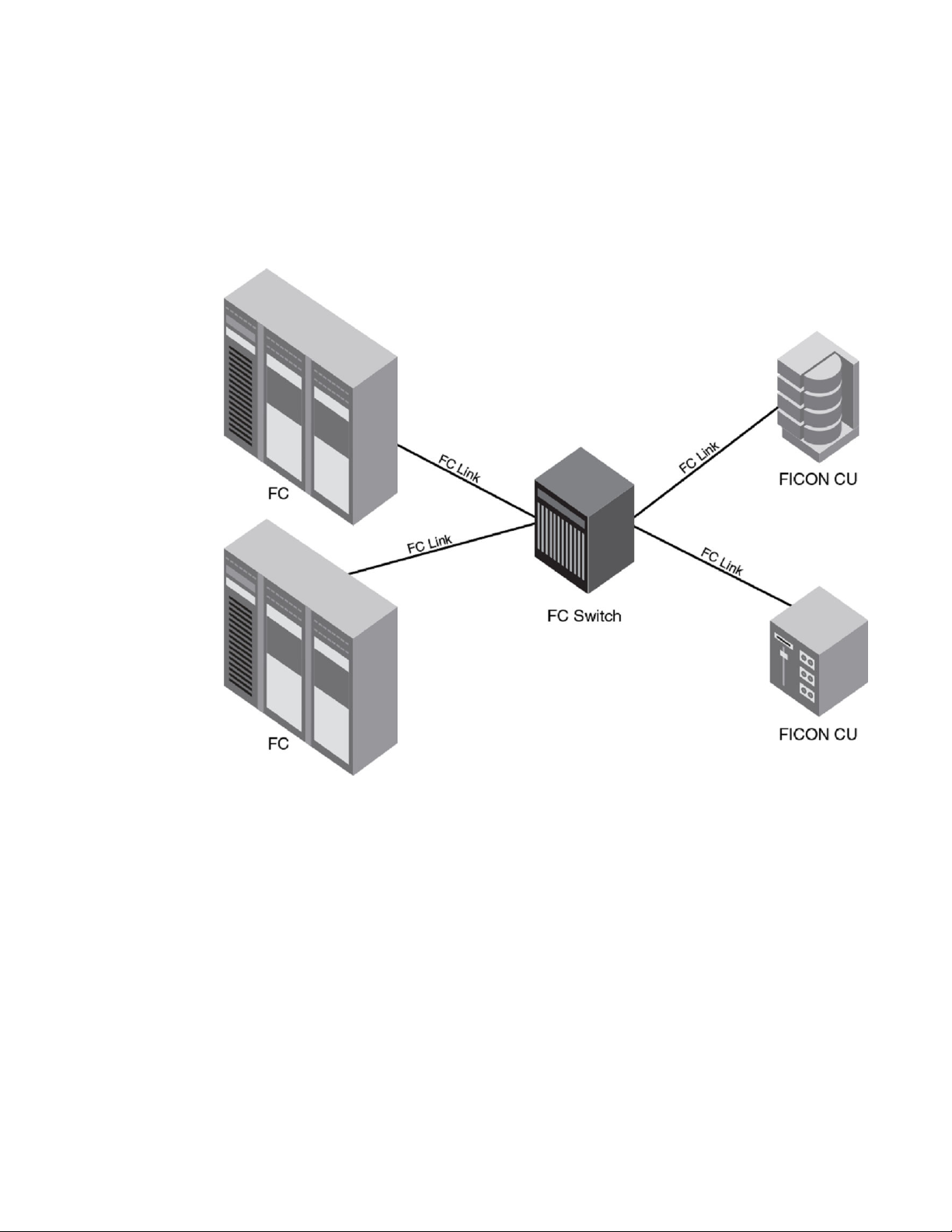
Switched point-to-point
A single-switch configuration is called switched point-to-point allows the channel to use single-byte
addressing.
FIGURE 2 Switched point-to-point FICON
Cascaded FICON
Cascaded FICON refers to an implementation of FICON that uses one or more FICON channel paths in
which the domain ID of the entry switch is different than the domain ID of the switch where the control
unit is attached. Therefore, cascading requires a two-byte link address. Anytime a two-byte link address
is defined on a channel, all link addresses must be two-byte link addresses.
Switches may be interconnected using the following links:
• Traditional Inter-Switch Links (ISLs)
• Inter-Chassis Links (ICLs)
• Fibre Channel over Internet Protocol (FCIP)
The processor interface is connected to one switch (known as the entry switch), while the storage
interface is connected to the other. This configuration is supported for both disk and tape, with multiple
processors, disk subsystems, and tape subsystems sharing the ISLs or ICLs between the switches and
backbones. Multiple ISLs between the switches and backbones are also supported. Cascading between
Switched point-to-point
FICON Administrator's Guide 15
53-1003144-01
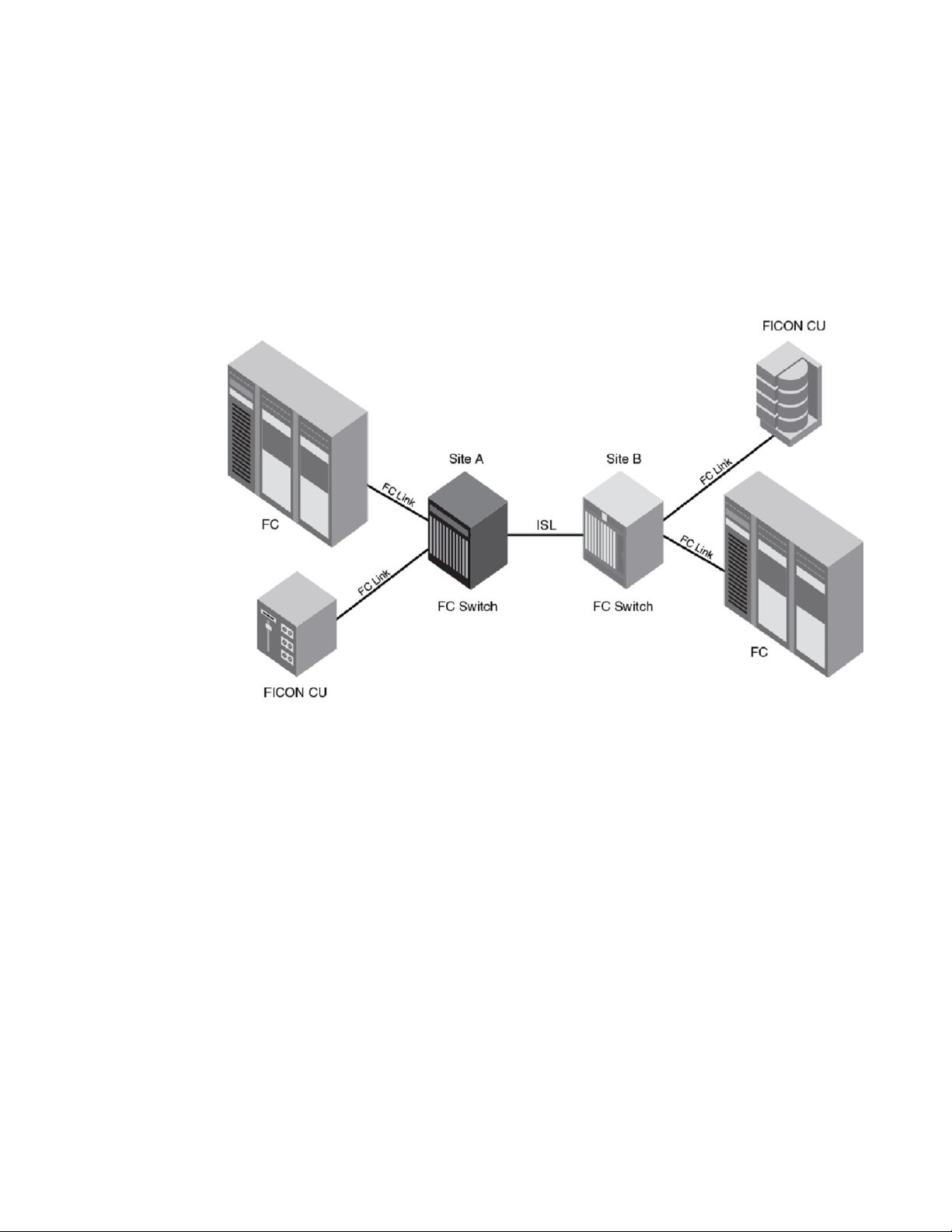
switches and backbones is also supported. An example of this would be a Brocade DCX 8510-8
Backbone connected to a Brocade 6510.
A cascaded configuration (refer to the following figure) requires two-byte addressing. Two byte-
addressing requires a list of authorized switches. This authorization feature, called fabric binding, is
available through the Secure Access Control List feature. The fabric binding policy allows a predefined
list of switches (domains) to exist in the fabric and prevents other switches from joining the fabric. This
type of configuration is described in User security considerations on page 33.
FIGURE 3 Cascaded FICON
There are hardware and software requirements specific to two-byte addressing:
• Both the FICON switches must be Brocade switches.
• The mainframes must be zSeries machines or System z processors: z196, z114, z800, 890, 900,
990, z9 BC, z9 EC, z10 BC, EC, and zEC12. Cascaded FICON requires 64-bit architecture to
support the two-byte addressing scheme. Cascaded FICON is not supported on 9672 G5/G6
mainframes.
• z/OS version 1.4 or later, or z/OS version 1.3 with required Program Temporary Fixes (PTFs) and
Microcode Loads (MCLs) to support two-byte link addressing (DRV3g and MCL (J11206) or later)
is required.
• Switch configuration requirements:
‐ Make sure that E_D_TOV is the same on all switches in the fabric (typically, this is not
changed from the default)
‐ Make sure that R_A_TOV is the same on all switches in the fabric (typically, this is not
changed from the default)
‐ Configure insistent Domain ID (IDID)
‐ Configure fabric binding (strict SCC policy)
Qualified FICON cascaded configurations
Not all fibre channel fabrics are qualified for FICON. Cascaded FICON configurations are limited to
well-controlled paths. Only the channel paths illustrated in this section are supported for FICON. The
Qualified FICON cascaded configurations
16 FICON Administrator's Guide
53-1003144-01
resulting fabric scenario after ISL failures must not result in an unsupported configuration. When
physical cabling is not practical to enforce these configurations, zoning or Traffic Isolation zoning (TI
zoning) with failover disabled may be used to ensure unsupported fabrics cannot be formed. Note that
these restrictions apply to logical switches and not the chassis.
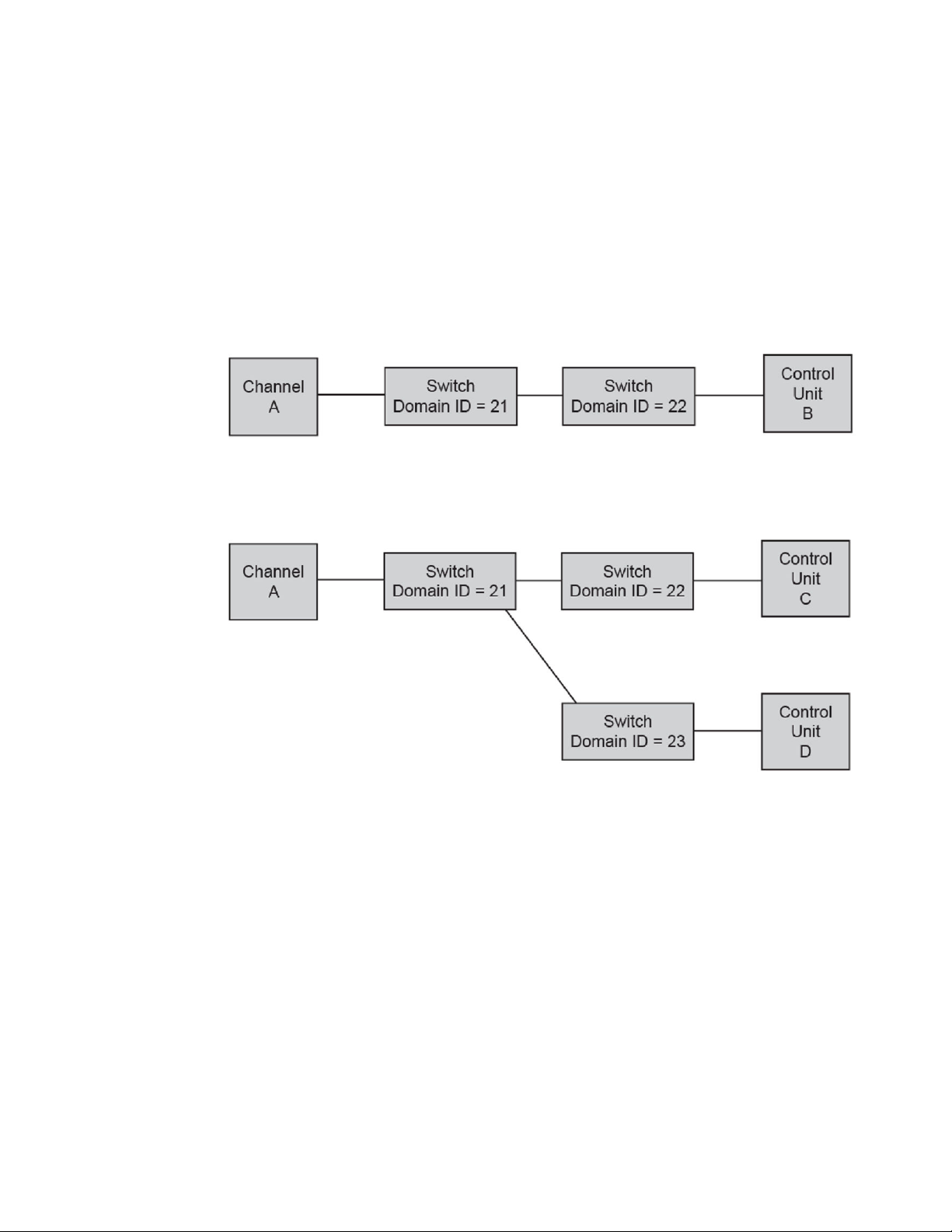
The following figures show two cascaded configurations. These configurations require Channel A to be
configured for two-byte addressing and require IDID and fabric binding. It is recommended that there be
only two domains in a path from a FICON Channel interface to a FICON Control Unit interface. There
are exceptions to the two-domain rule in extended fabric configurations. Refer to Extended fabric
configurations on page 17 for examples.
FIGURE 4 Cascaded configuration, two switches
The following figure illustrates multiple switches cascaded off of switch 21. As long as there is only one
hop from channel to control unit, the configuration is supported.
FIGURE 5 Cascaded configuration, core-edge architecture
Extended fabric configurations
Switches in cascaded configurations may be connected through interchassis links (ICLs), interswitch
links (ICLs), and FCIP. Connection using FCIP is through Fibre Channel extension devices, such as
7800 switches and FX8-24 blades. Following are example configurations.
For more information on long distance and extended fabrics, refer to the Fabric OS Administrator's
Guide. For more information on FCIP and extension products, refer to the Fabric OS FCIP
Administrator's Guide.
Extended fabric configurations
FICON Administrator's Guide 17
53-1003144-01
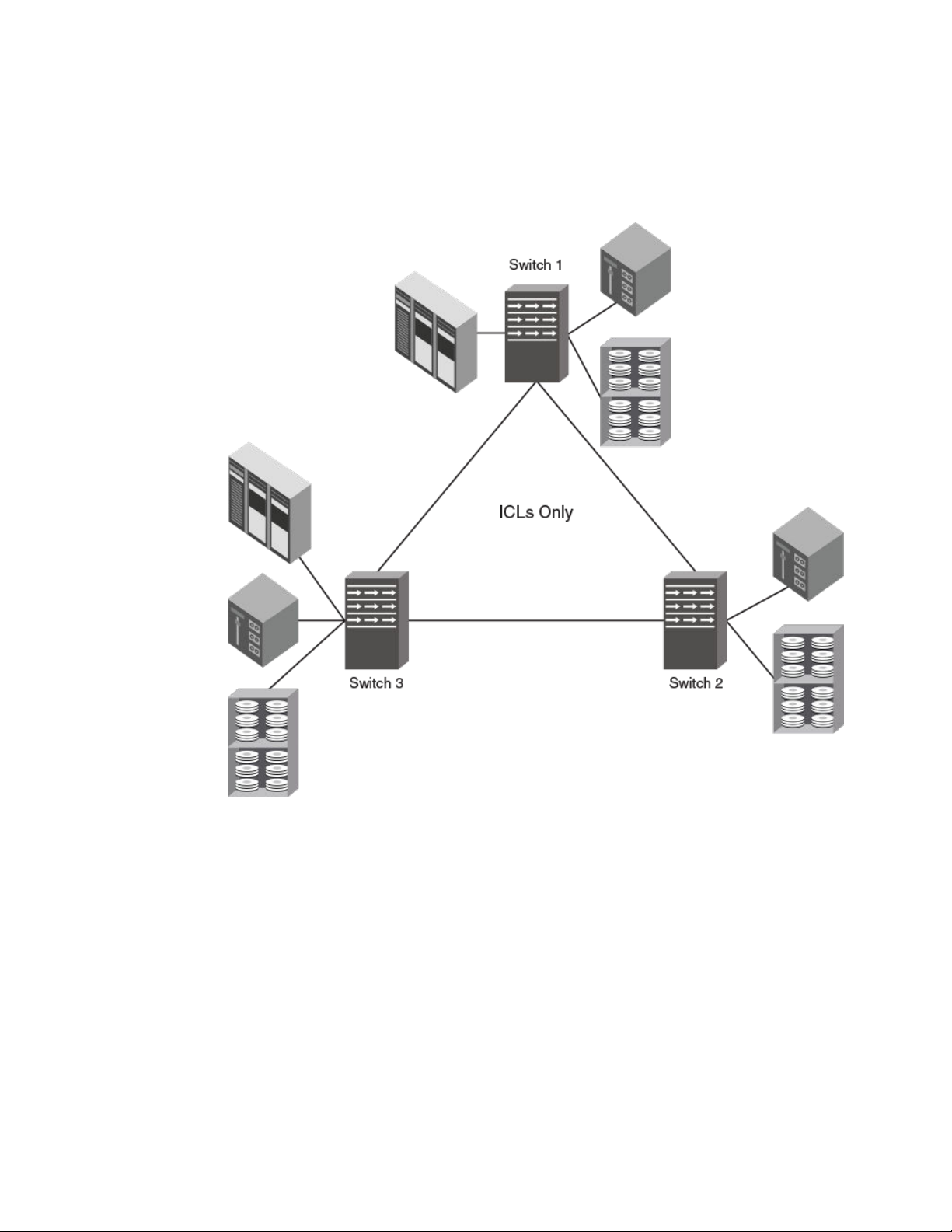
The following figure illustrates a multi-hop ICL triangle configuration that uses ICLs. Note that three
switches are connected through ICLs only.
FIGURE 6 Multi-hop ICL triangle
Introducing FICON
18 FICON Administrator's Guide
53-1003144-01
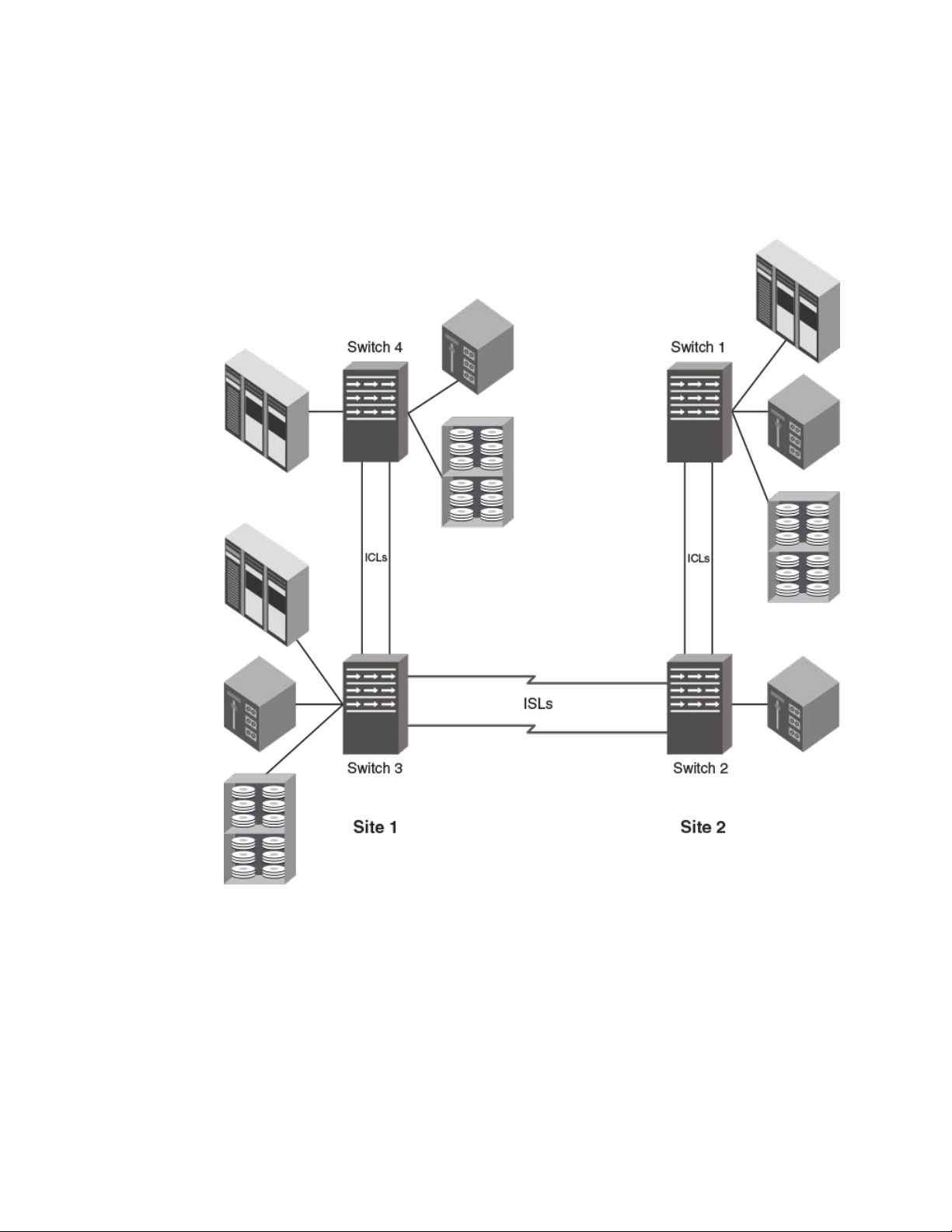
The following figure illustrates a multi-hop configuration that uses ICLs and ISLs. This configuration is
supported with or without switches 4 or 1. All switches must be all generation (Gen) 4 or all Gen 5. You
cannot mix Gen 4 and Gen 4 on ICL connections.
FIGURE 7 Multi-hop configuration with ICLs
The following figure illustrates a multi-hop configuration that uses ICLs and FCIP. The two 7800
switches are for ISL extension only using FCIP. Channel or control unit connections are not permitted.
These switches may be replaced with an FX8-24 blade installed in directors. This configuration can be
Introducing FICON
FICON Administrator's Guide 19
53-1003144-01
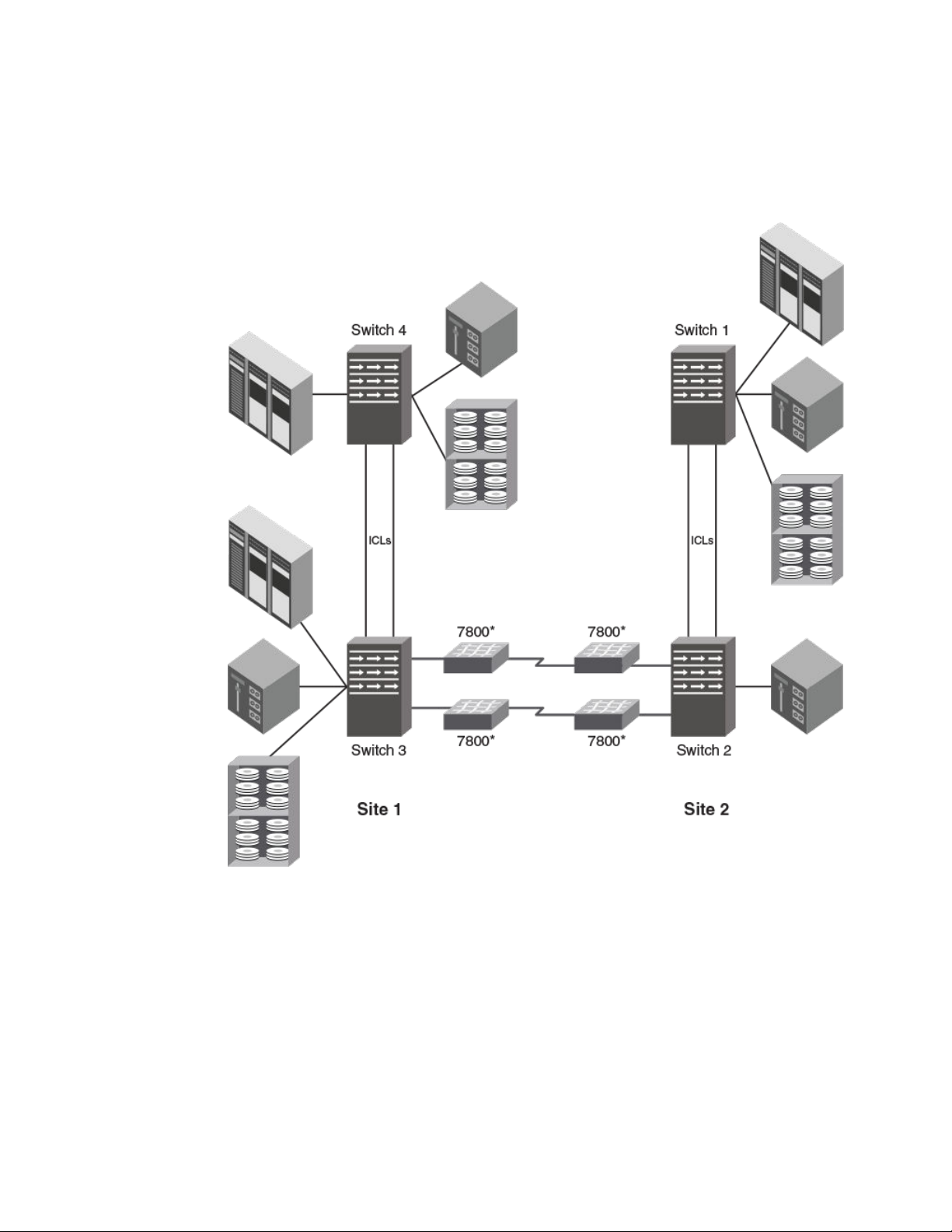
supported with or without switches 4 or 1. All switches must be Gen 4 or Gen 5. You cannot mix Gen 4
and Gen 5 switches with ICLs.
FIGURE 8 Multi-hop with ICLS and FCIP
Introducing FICON
20 FICON Administrator's Guide
53-1003144-01

The following figure illustrates a configuration that uses FCIP between 7800 switches that are used as
routers only, for ISL extension. Channel or control unit connections are not permitted. The 7800
switches may be replaced with FX8-24 blades installed in directors.
FIGURE 9 FCIP with 7800 switches as routers only
The following figure illustrates a configuration that uses cascaded FCIP with four 7800 switches. The
7800 switches at site 1 are used for ISL extension only. Channel or control unit connections are not
Introducing FICON
FICON Administrator's Guide 21
53-1003144-01
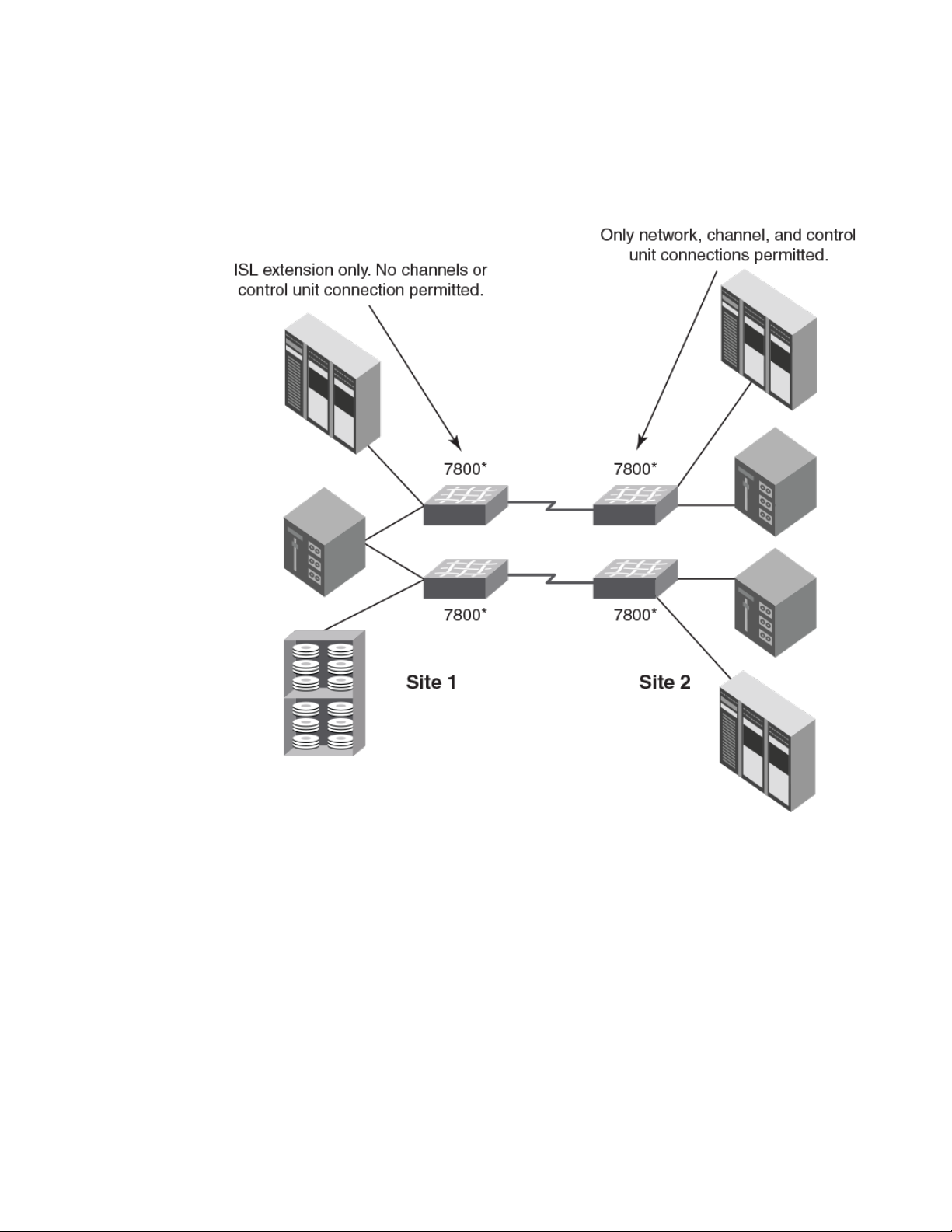
permitted. The 7800 switches at site 2 are only for network, channel, and control unit connections. The
7800 switches on either site may be replaced with the FX8-24 blades installed in directors.
FIGURE 10 Cascaded configuration using FCIP and 7800 switches
The following figure illustrates a cascaded configuration that uses FCIP and 7800 switches as edge
switches. At site 1, the 7800 switches are used for ISL extension only. Channel or control unit
connections are not permitted. At site 2, only channel, and control unit connections are permitted on
Introducing FICON
22 FICON Administrator's Guide
53-1003144-01
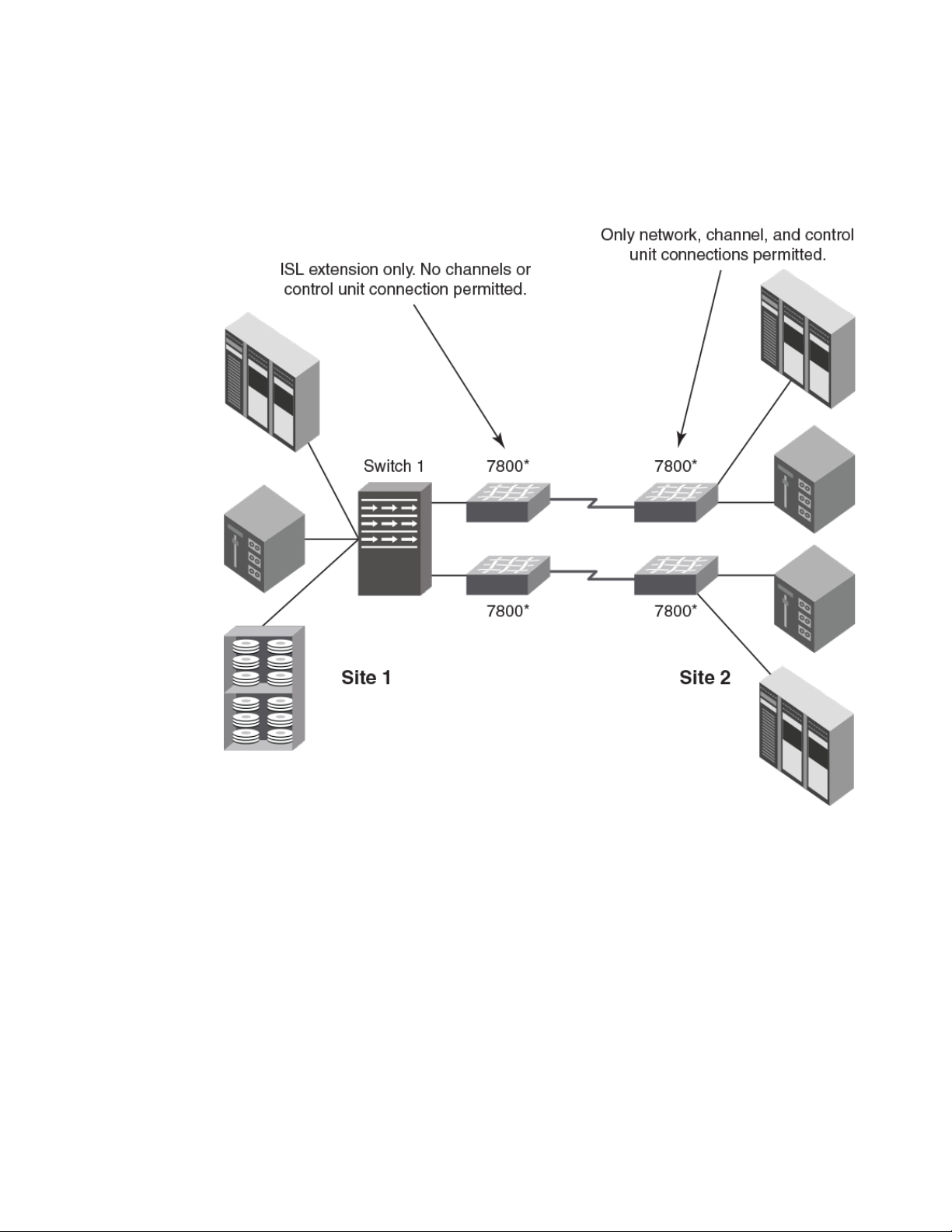
the 7800 switches. The 7800 switches at either site may be replaced with the FX8-24 blades installed in
directors.
FIGURE 11 Cascaded configuration using FCIP and 7800 edge switches
Access control in FICON
Zoning is used to control access in a FICON environment. A zone consists of a group of ports or
WWNs. Connectivity is permitted only between connections to the switch that are in the same zone.
There are three types of zoning: WWN, port, and domain index zoning. A zone configuration includes at
least one zone. In open systems environments and in more complex FICON deployments, the zone
configuration contains multiple zones. Although domain index zoning is supported, WWN zoning for
Quality of Service (QoS) is recommended in environments where N_Port ID Virtualization (NPIV) is
deployed. For more information on how to implement QoS domain index zoning in your fabric, refer to
the "QoS zones" section of the Fabric OS Administrator's Guide for details.
When zoning changes occur, Registered State Change Notification (RSCN) messages are sent out
throughout the zone. RSCNs are part of the low-level Fibre Channel Protocol that alerts channels and
Access control in FICON
FICON Administrator's Guide 23
53-1003144-01
devices to changes in the fabric. Using multiple smaller zones instead of one large zone helps
alleviate the need for channels and device interfaces to process RSCNs that are not relevant.
NOTE
Session-based zoning enforcement is not recommended on a FICON switch. For more information on
session-based zoning enforcement, refer to the Fabric OS Administrator's Guide.
Cascaded zoning
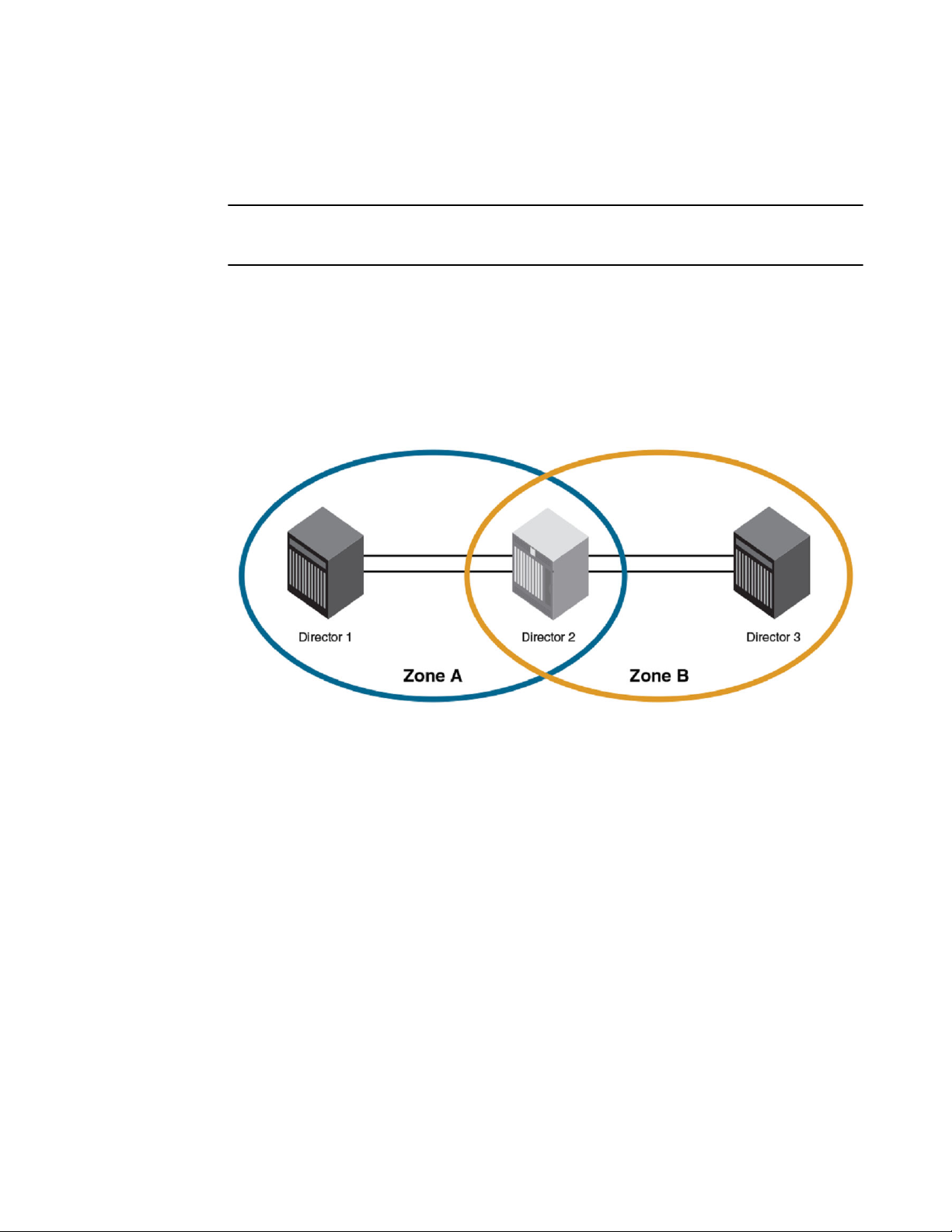
The figure below illustrates multiple sites sharing the same disaster-recovery site. Each switch or
Backbone at a remote site, labeled Director 1 and Director 31, can pass traffic to Director 2, but no
traffic is permitted between Zone A and Zone B.
FIGURE 12 Simple cascaded zoning
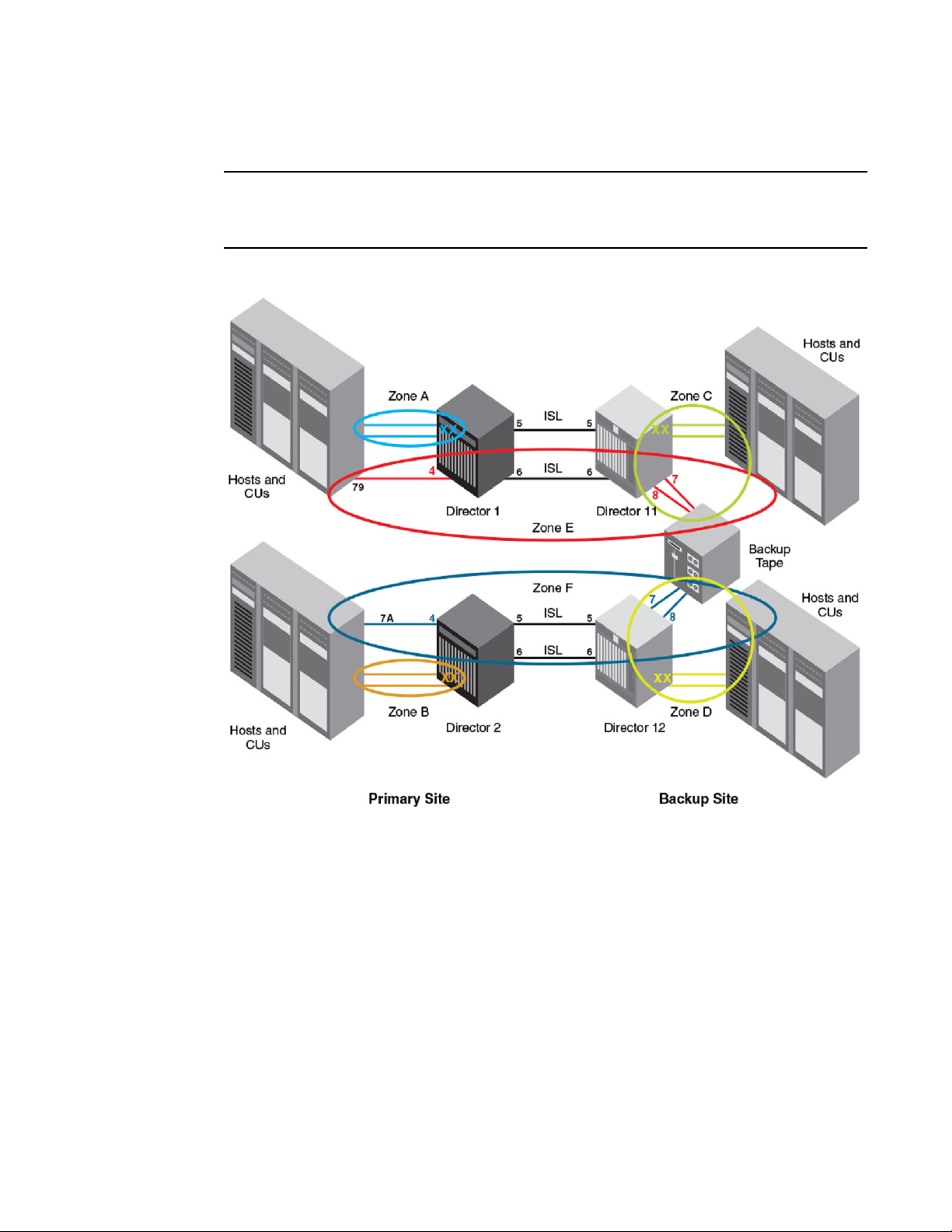
The figure below illustrates the multiple zoning concepts that can be used to restrict traffic. Any host
channel at the Backup Site (connected to Director 11 or Director 12) can connect to the backup tape
contained within the same zone. Notice that no more than a single hop is ever allowed and only
Channel Path Identifiers (CHPIDs) 79 and 7A on the Primary Site can connect to the backup tape.
Furthermore, CHPIDs 79 and 7A can only connect to the backup tape at the Backup Site.
Cascaded zoning
24 FICON Administrator's Guide
53-1003144-01
NOTE
Zoning does not replace the need to set up the connectivity from the host to storage control units in the
HCD or Input/Output Configuration Program (IOCP). For more information on zoning, refer to the Fabric
OS Administrator's Guide.
FIGURE 13 Complex cascaded zoning
Zone A (Blue): Any CHPID connected to Director 1, except CHPID 79, can get to any control unit
connected to Director 1. The zone includes all ports in Director 1 except ports 4, 5, and 6.
Zone B (Orange): Any CHPID connected to Director 2, except CHPID 7A, can get to any control unit
connected to Director 2. The zone includes all ports in Director 2 except ports 4, 5, and 6.
Zone C (Green): Any CHPID connected to Director 11 can get to any control unit connected to Director
11. The zone includes all ports in Director 11 except ports 5 and 6. Adding ports 5 and 6 to the zone, so
that all ports in the switch or Backbone are in the same zone, would not affect permitted connectivity
and may be a more practical alternative.
Zone D (Yellow): Any CHPID connected to Director 12 can get to any control unit connected to Director
12. The zone includes all ports in Director 12 except ports 5 and 6, which are used for ISLs.
Red Zone E: CHPID 79 can talk only to the remote tape connected to ports 7 and 8 on Director 11. The
zone includes port 4 of Director 1 and ports 7 and 8 of Director 11. Either ISL can be used.
Purple Zone F: CHPID 7A can talk only to the remote tape connected to ports 7 and 8 on Director 12.
The zone includes port 4 of Director 2 and ports 7 and 8 of Director 12. Either ISL can be used.
Introducing FICON
FICON Administrator's Guide 25
53-1003144-01

Error reporting
Non-implicit link incidents (such as Fabric OS recognized or bit error rate threshold exceeded) and
implicit link incidents (such as FRU failure) are reported to registered listeners on the local switch. The
RMF 74-7 record (FICON Director Activity Report, which is the same RMF record containing the
average frame pacing delay information) reports port errors, which in turn are also reported back to the
mainframe host management consoles.
Secure access control
Binding is a method used to prevent devices from attaching to the switch or backbone. Secure Access
Control Lists (ACLs) provides the following fabric, switch, and port binding features:
• Fabric binding is a security method for restricting switches within a multiple-switch fabric. Brocade
recommends using fabric binding for cascaded FICON. SCC ACLs with strict fabric-wide
consistency are required for FICON fabric binding.
• Switch binding is a security method for restricting devices that connect to a particular switch or
backbone. If the device is another switch, this is handled by the SCC policy. If the device is a host
or storage device, the device connection control (DCC) policy binds those devices to a particular
switch. Policies range from completely restrictive to reasonably flexible, based upon customer
needs. SCC ACLs with strict fabric-wide consistency are necessary for FICON switch binding.
• Port binding is a security method for restricting host or storage devices that connect to particular
switch ports. The DCC policy also binds device ports to switch ports. Policies range from
completely restrictive to reasonably flexible, based on customer needs.
Error reporting
26 FICON Administrator's Guide
53-1003144-01
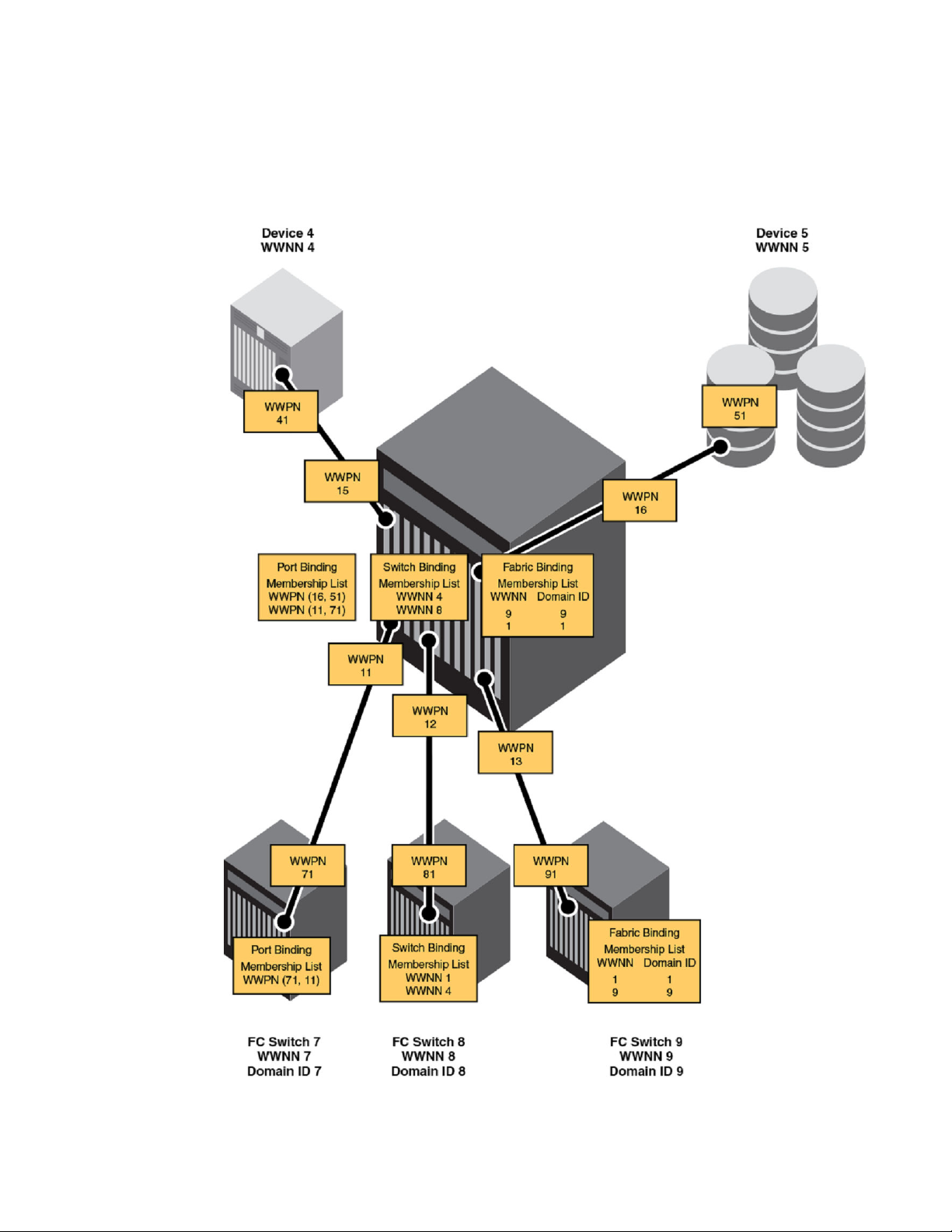
The figure below demonstrates the three types of binding you can use depending on the security
requirements of your fabric.
FIGURE 14 Types of binding for access control
Introducing FICON
FICON Administrator's Guide 27
53-1003144-01

FICON commands
NOTE
The Fabric OS CLI supports only a subset of the Brocade management features for FICON fabrics.
The full set of FICON CUP administrative procedures is available using the Brocade Network Advisor
and Web Tools software features. You can also use an SNMP agent and the FICON Management
Information Base (MIB).
The table below summarizes the Fabric OS CLI commands that can be used for managing FICON
fabrics. For detailed information on these commands, refer to the Fabric OS Command Reference.
Fabric OS commands related to FICON TABLE 1
Command Description
Standard Fabric OS commands
bladeSwap
Swaps the area numbers for matching port pairs of
two blades.
configure
Changes a variety of switch configuration settings,
including setting the domain ID and the insistent
mode.
configUpload
Backs up the current FOS feature and switch
configuration, but does not back up FMS or FICON-
specific configuration such as IPL file, active
configuration, mode register, and host data.
firmwareShow
Displays the current version of the firmware.
licenseAdd
Adds a license to the switch. The license key is case-
sensitive and must be entered exactly.
licenseRemove
Removes a license from the switch. Note that FMS
mode must be disabled before removing the FICON
license.
licenseShow
Displays current license keys, along with a list of
licensed products enabled by these keys.
licenseSlotCfg
Enables and displays slot-based licenses for a switch
chassis. Note that for a switch without blades, such as
the 7800 Extension Switch, slot 0 is used as the slot-
based license target. For blades, slot numbers are
based on the switch chassis numbering scheme. A
license key with the specified capacity must be
installed with the licenseAdd command before you
can enable a feature on a specified slot with this
command.
portAddress
Binds the 16-bit address to the lower two bytes of a
port 24-bit Fibre Channel address. Also unbinds the
currently bound address for the specified port.
FICON commands
28 FICON Administrator's Guide
53-1003144-01
 Loading...
Loading...