Page 1

Wireless 11n ADSL Firewall Router
User Guide
WL-603
3CRWDR300A-73
3CRWDR300B-73
http://www.3Com.com/
Part No. 10016794 Rev AA
Published July 2008
Page 2

3Com Corporation
350 Campus Drive,
Marlborough, MA
USA 01752-3064
Copyright © 2004, 2005, 2006, 2007, 2008, 3Com Corporation. All rights reserved. No part of this
documentation may be reproduced in any form or by any means or used to make any derivative work (such as
translation, transformation, or adaptation) without written permission from 3Com Corporation.
3Com Corporation reserves the right to revise this documentation and to make changes in content from time
to time without obligation on the part of 3Com Corporation to provide notification of such revision or change.
3Com Corporation provides this documentation without warranty, term, or condition of any kind, either
implied or expressed, including, but not limited to, the implied warranties, terms or conditions of
merchantability, satisfactory quality, and fitness for a particular purpose. 3Com may make improvements or
changes in the product(s) and/or the program(s) described in this documentation at any time.
If there is any software on removable media described in this documentation, it is furnished under a license
agreement included with the product as a separate document, in the hard copy documentation, or on the
removable media in a directory file named LICENSE.TXT or !LICENSE.TXT. If you are unable to locate a copy,
please contact 3Com and a copy will be provided to you.
UNITED STATES GOVERNMENT LEGEND
If you are a United States government agency, then this documentation and the software described herein are
provided to you subject to the following:
All technical data and computer software are commercial in nature and developed solely at private expense.
Software is delivered as “Commercial Computer Software” as defined in DFARS 252.227-7014 (June 1995) or
as a “commercial item” as defined in FAR 2.101(a) and as such is provided with only such rights as are
provided in 3Com’s standard commercial license for the Software. Technical data is provided with limited rights
only as provided in DFAR 252.227-7015 (Nov 1995) or FAR 52.227-14 (June 1987), whichever is applicable.
You agree not to remove or deface any portion of any legend provided on any licensed program or
documentation contained in, or delivered to you in conjunction with, this User Guide.
Unless otherwise indicated, 3Com registered trademarks are registered in the United States and may or may not
be registered in other countries.
3Com, and the 3Com logo are registered trademarks of 3Com Corporation.
Intel and Pentium are registered trademarks of Intel Corporation. Microsoft, MS-DOS, Windows, and Windows
NT are registered trademarks of Microsoft Corporation. Novell and NetWare are registered trademarks of
Novell, Inc. UNIX is a registered trademark in the United States and other countries, licensed exclusively
through X/Open Company, Ltd.
Netscape Navigator is a registered trademark of Netscape Communications.
JavaScript is a trademark of Sun Microsystems
Wi-Fi and the Wi-Fi logo are registered trademarks of the WI-Fi Alliance.
IEEE and 802 are trademarks of the Institute of Electrical and Electronics Engineers, Inc.
All other company and product names may be trademarks of the respective companies with which they are
associated.
ENVIRONMENTAL STATEMENT
It is the policy of 3Com Corporation to be environmentally-friendly in all operations. To uphold our policy, we
are committed to:
Establishing environmental performance standards that comply with national legislation and regulations.
Conserving energy, materials and natural resources in all operations.
Reducing the waste generated by all operations. Ensuring that all waste conforms to recognized environmental
standards. Maximizing the recyclable and reusable content of all products.
Ensuring that all products can be recycled, reused and disposed of safely.
Ensuring that all products are labelled according to recognized environmental standards.
Improving our environmental record on a continual basis.
End of Life Statement
3Com processes allow for the recovery, reclamation and safe disposal of all end-of-life electronic components.
Regulated Materials Statement
3Com products do not contain any hazardous or ozone-depleting material.
Environmental Statement about the Documentation
The documentation for this product is printed on paper that comes from sustainable, managed forests; it is
fully biodegradable and recyclable, and is completely chlorine-free. The varnish is environmentally-friendly, and
the inks are vegetable-based with a low heavy-metal content.
Page 3

CONTENTS
ABOUT THIS GUIDE
Naming Convention 7
Conventions 8
Feedback About This User Guide 9
Related Documentation 9
INTRODUCING THE ROUTER
Wireless 11n ADSL Firewall Router 11
Router Advantages 14
Package Contents 14
Minimum System and Component Requirements 15
Physical Features 15
INSTALLING THE ROUTER
Introduction 21
Safety Information 21
Positioning the Router 21
Using the Rubber Feet 22
Wall Mounting 22
Mounting Instructions for Cement Walls 22
Mounting Instructions for
Wood Walls 23
Powering Up the Router 23
Connecting the Router 23
SETTING UP YOUR COMPUTERS
Obtaining an IP Address Automatically 27
Windows 2000 27
Page 4

Windows Vista 29
Windows XP 30
Macintosh 30
Disabling PPPoE and PPTP Client Software 31
Disabling Web Proxy 31
RUNNING THE SETUP WIZARD
Accessing the Router using the 3Com Detect Application 33
Running the 3Com Detect Application 33
Accessing the Setup Wizard 35
Wizard - Change Password 38
Wizard - Time and Time Zone 39
Wizard - Connection Type 40
Wizard - LAN Settings 46
Wizard - Wireless Setting 47
Wizard - Configuration Summary 52
CONFIGURING THE ROUTER
Navigating through the Router Configuration Screens 53
Main Menu 53
Welcome Screen 53
Status 53
LAN Settings 54
LAN Settings Unit Configuration 54
DHCP Clients List 55
Wireless Settings 57
Configuration 58
Encryption 60
WPS 65
Connection Control 67
Client List 68
WMM 68
WDS 71
Advanced 74
Internet Settings 76
ATM P V C 76
Page 5

DNS 88
Clone MAC address 89
Firewall 90
SPI 90
Special Applications 94
Virtual Servers 95
DMZ 96
PC Privileges 97
Schedule Rule 99
URL Filter 100
Advanced 101
Security 101
VLAN 104
Static Routes 106
RIP 108
DDNS 110
SNMP 111
Syslog 112
Proxy ARP 113
QoS Settings 114
Traff ic M a ppi ng 115
VPN 117
System Tools 124
Restart Router 124
Configuration 124
Upgrade 125
Time Zone 126
Ping 127
Traceroute 128
DNS Lookup 129
Diagnostic 129
Status and Logs 130
Status 130
ADSL Status 131
ATM PVC Status 131
Routing Table 132
Logs 132
Traffic Statistics 133
Page 6

Support/Feedback 134
Support 134
Feedback 134
TROUBLESHOOTING
Basic Connection Checks 135
Browsing to the Router Configuration Screens 136
Connecting to the Internet 136
Forgotten Password and Reset to Factory Defaults 138
Wireless Networking 139
Recovering from Corrupted Software 140
Power Adapter 141
Frequently Asked Questions 143
IP ADDRESSING
The Internet Protocol Suite 145
Managing the Router over the Network 145
IP Addresses and Subnet Masks 145
How does a Device Obtain an IP Address and Subnet Mask? 147
DHCP Addressing 147
Static Addressing 147
Auto-IP Addressing 148
TECHNICAL SPECIFICATIONS
3Com Wireless 11n Cable/DSL Firewall Router 149
Standards 151
Page 7

SAFETY INFORMATION
END USER SOFTWARE LICENSE AGREEMENT
OBTAINING SUPPORT FOR YOUR 3COM PRODUCTS
Register Your Product to Gain Service Benefits 160
Solve Problems Online 160
Purchase Extended Warranty and Professional Services 160
Access Software Downloads 161
Contact Us 161
Telephone Technical Support and Repair 161
GLOSSARY
REGULATORY NOTICES
INDEX
Page 8

Page 9

ABOUT THIS GUIDE
This guide describes how to install and configure the 3Com Wireless 11n
ADSL Firewall Router (3CRWDR300A-73, 3CRWDR300B-73).
This guide is intended for use by those responsible for installing and
setting up network equipment; consequently, it assumes a basic working
knowledge of LANs (Local Area Networks) and Internet Routers.
This manual covers both Annex A (ADSL over POTS) and Annex B (ADSL
over ISDN) Routers. The only difference is they style of ADSL connector
and type of cable supplied with your Router for connection to your
telephone line.
If a release note is shipped with the 3Com Wireless 11n ADSL Firewall
Router and contains information that differs from the information in this
guide, follow the information in the release note.
Most user guides and release notes are available in Adobe Acrobat
Reader Portable Document Format (PDF) on the 3Com World Wide Web
site:
http://www.3Com.com
Naming Convention Throughout this guide, the 3Com Wireless 11n ADSL Firewall Router is
referred to as the “Router”.
Category 5 Twisted Pair Cables are referred to as Twisted Pair Cables
throughout this guide.
Page 10
8 ABOUT THIS GUIDE
Conventions Table 1 and Table 2 list conventions that are used throughout this guide.
Tab le 1 Notice Icons
Icon Notice Type Description
Information note Information that describes important features or
instructions.
Caution Information that alerts you to potential loss of data or
potential damage to an application, system, or device.
Warning Information that alerts you to potential personal
injury.
Tab le 2 Text Conventions
Convention Description
The words “enter”
and “type”
When you see the word “enter” in this guide, you must type
something, and then press Return or Enter. Do not press
Return or Enter when an instruction simply says “type.”
Keyboard key names If you must press two or more keys simultaneously, the key
names are linked with a plus sign (+). Example:
Press Ctrl+Alt+Del
Words in italics Italics are used to:
■ Emphasize a point.
■ Denote a new term at the place where it is defined in the
text.
■ Identify menu names, menu commands, and software
button names. Examples:
From the Help menu, select Contents.
Click OK.
Page 11
Feedback About This User Guide 9
Feedback About This User Guide
Related Documentation
Your suggestions are very important to us. They will help make our
documentation more useful to you. Please e-mail comments about this
document to 3Com at:
pddtechpubs_comments@3com.com
Please include the following information when commenting:
■ Document title
■ Document part number (on the title page)
■ Page number (if appropriate)
Example:
■ 3Com Wireless 11n ADSL Firewall Router User Guide
■ Part Number 10016794 Rev. AA
■ Page 24
Do not use this e-mail address for technical support questions. For
information about contacting Technical Support, please refer to
Appendix E.
In addition to this guide, each Router document set includes one
Installation Guide. This guide contains the instructions you need to install
and configure your Router.
Page 12

10 ABOUT THIS GUIDE
Page 13

1
INTRODUCING THE ROUTER
Welcome to the world of networking with 3Com®. In the modern
business environment, communication and sharing information is crucial.
Computer networks have proved to be one of the fastest modes of
communication but, until recently, only large businesses could afford the
networking advantage.
Wireless 11n ADSL Firewall Router
The 3Com Wireless 11n ADSL Firewall Router is designed to provide a
cost-effective means of sharing a single broadband Internet connection
amongst several wired and wireless computers. The Router also provides
protection in the form of an electronic “firewall” preventing anyone
outside of your network from seeing your files or damaging your
computers. The Router can also prevent your users from accessing Web
sites which you find unsuitable.
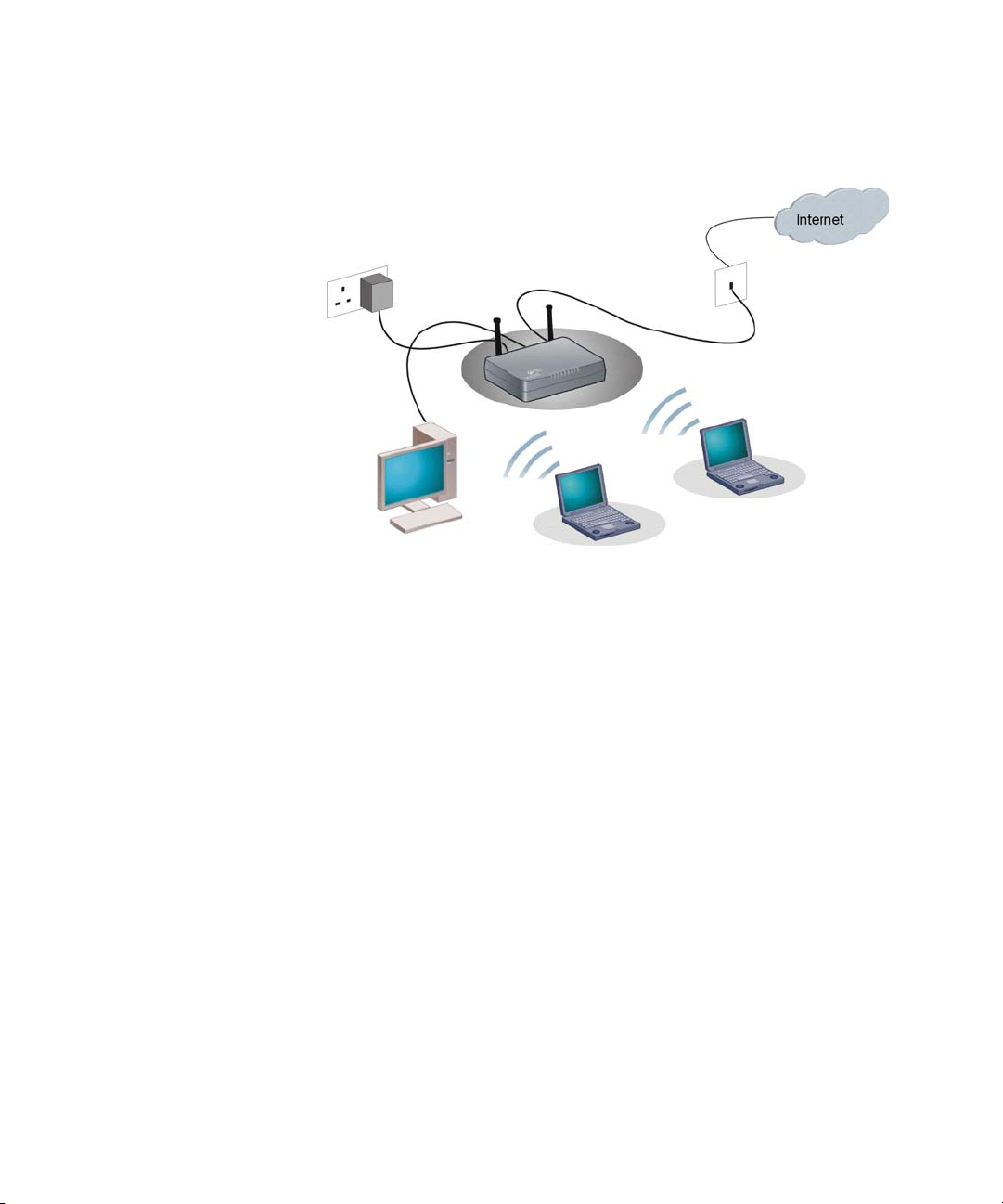
Figure 1 shows an example network without a Router. In this network,
only one computer is connected to the Internet. This computer must
always be powered on for the other computers on the network to access
the Internet.
Page 14

12 CHAPTER 1: INTRODUCING THE ROUTER
Figure 1 Example Network Without a Router
When you use the Router in your network (Figure 2 and Figure 3), it
becomes your connection to the Internet. Connections can be made
directly to the Router, or to an OfficeConnect Switch or Hub, expanding
the number of computers you can have in your network.
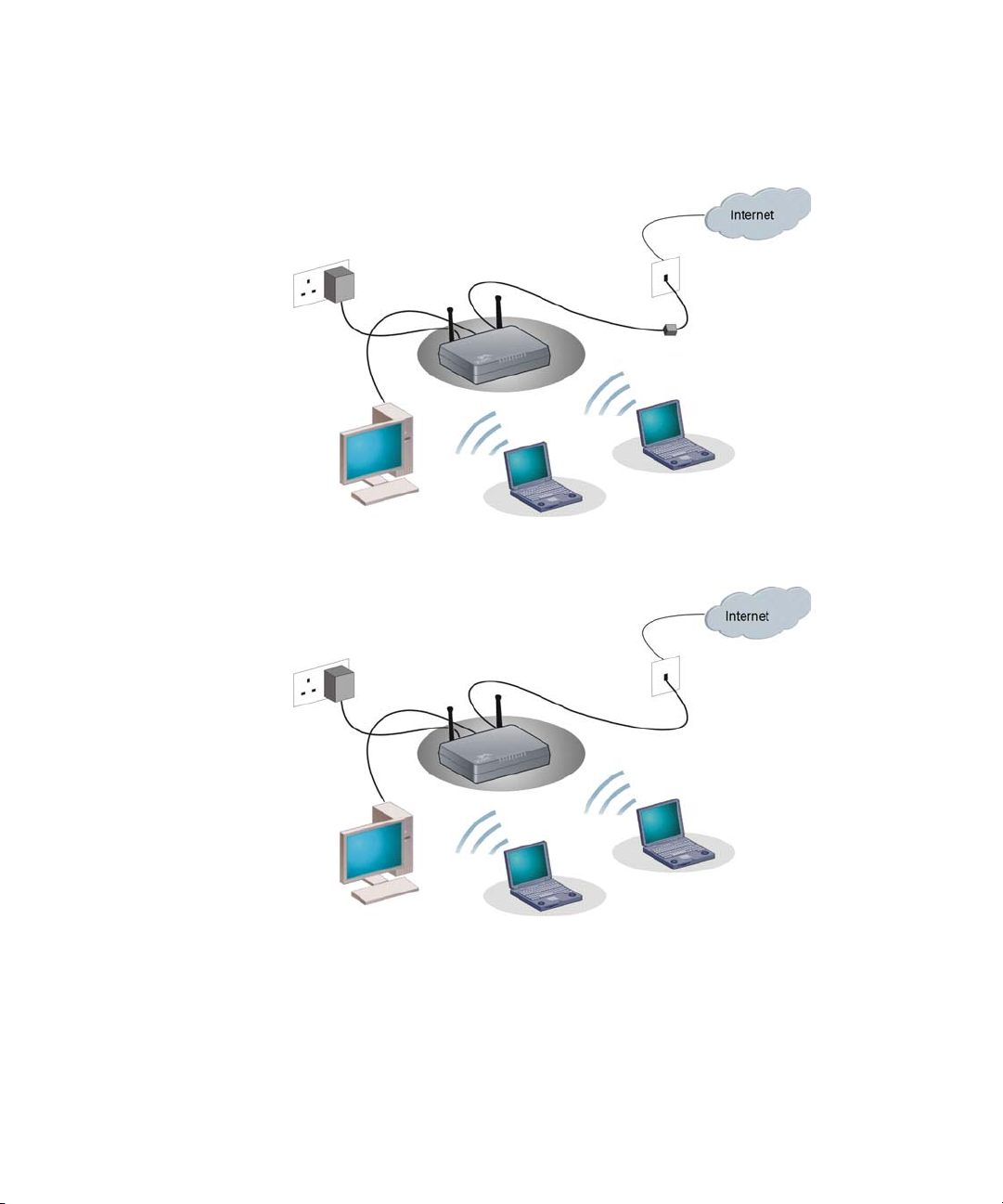
Figure 2 Example Network Using a Firewall Router (with splitter)
Page 15
Wireless 11n ADSL Firewall Router 13
Figure 3 Example Network Using a Firewall Router (without splitter)
Page 16

14 CHAPTER 1: INTRODUCING THE ROUTER
Router Advantages The advantages of the Router include:
■ Shared Internet connection for both wired and wireless computers
■ High speed 802.11n wireless networking
■ No need for a dedicated, “always on” computer serving as your
Internet connection
■ Cross-platform operation for compatibility with Windows, Unix and
Macintosh computers
■ Easy-to-use, Web-based setup and configuration
■ Provides centralization of all network address settings (DHCP)
■ Acts as a Virtual server to enable remote access to Web, FTP, and other
services on your network
■ Security — Firewall protection against Internet hacker attacks and
encryption to protect wireless network traffic
Package Contents The Router kit includes the following items:
■ One 3Com Wireless 11n ADSL Firewall Router
■ One power adapter for use with the Router
■ Four rubber feet
■ One telephone cable (only for 3CRWDR300A-73 version)
■ One Ethernet cable (Two Ethernet cables in 3CRWDR300B-73 version)
■ One CD-ROM containing this user guide, copies of the quick install
guide in various languages and the 3Com Detect application.
■ Installation guide
■ Support and Safety sheet
■ Warranty sheet
If any of these items are missing or damaged, please contact your retailer.
Page 17

Minimum System and Component Requirements 15
1
2
3
4
5
6
7
Minimum System and Component Requirements
Your Router requires that the computer(s) and components in your
network be configured with the following:
■ A computer with an operating system that supports TCP/IP
networking protocols (for example Windows 2000/XP,/Vista, Unix,
Mac OS 8.5 or higher).
■ An Ethernet 10 Mbps or 10/100 Mbps or 10/100/1000 Mbps NIC for
each computer to be connected to the LAN port on your Router.
■ An 802.11b, 802.11g or 802.11n draft2.0 compliant wireless NIC.
■ An active ADSL subscription and connection.
■ A Web browser that supports JavaScript, such as Netscape 4.7 or
higher, Internet Explorer 6.0 or higher, or Mozilla 1.2.1 or higher, or
Apple’s Safari.
Physical Features The front panel of the Router contains a series of indicator lights (LEDs)
that help describe the state of various networking and connection
operations.
Figure 4 Router - Front Panel
Page 18
16 CHAPTER 1: INTRODUCING THE ROUTER
1 Power LED (Illuminated Logo)
White
The 3Com logo serves as power OK indicator. This LED will light if the
router is receiving power from the power adapter. If it is not lit check the
power adapter connections. Refer to Chapter 6 Troubleshooting
2 Alert LED
Amber
Fast flash during self test. If self test fails the LED will remain on.
Fast flash during software upgrade.
Fast flash for software reset to the factory defaults.
Fast flash for hardware reset to the factory defaults.
The LED is on for 2 seconds when the firewall detects a hacker attack.
3ADSL Sync
Blue
LED on indicates the Internet connection is on. This LED flashes during
configuration at power up.
.
4ADSL Data
Blue
Fast flash means transmitting/receiving data.
Slow flash means ADSL connection is down.
5 Wireless LAN (WLAN) Status LED
Blue
If the LED is on it indicates that wireless networking is enabled. If the LED
is flashing, the link is OK and data is being transmitted or received. If the
LED is off, the Wireless LAN has been disabled in the Router, or there is a
problem. Refer to Chapter 6 Troubleshooting
.
6 LAN Status LEDs (4 indicators)
Blue
If the LED is on, the link between the port and the next piece of network
equipment is OK. If the LED is flashing, the link is OK and data is being
transmitted or received. If the LED is off, nothing is connected, or the
connected device is switched off, or there is a problem with the
connection (refer to Chapter 6 Troubleshooting
). The port will
automatically adjust to the correct speed and duplex.
Page 19

Physical Features 17
7 WPS LED
Blue
WiFi Protected Setup (WPS) is a standard for easy and secure
establishment of a wireless network, allowing wireless clients to connect
securely to routers and access points. The WPS LED shows the status of
the WPS function. It has a number of modes to help monitor the status of
clients connecting to the Router using the WPS protocol. The status is
shown by three different flashing rates: slow, medium and quick and
when light constantly.
Note: The WPS function will be enabled for 2 minutes once WPS is
enabled either by pressing the button or by starting the PIN mode via the
web interface. This time will end before 2 minutes if a client has
successfully connected. Only one client should be connected to the
Router using WPS at any one time. Attempting to connect two or more
clients at once may result in connection failures.
When the WPS button is pressed, or WPS is initiated using the PIN
method in the web interface, the WPS LED will flash at a medium rate for
up to 2 minutes to indicate that a WPS connection can be made. When a
connection attempt is underway, the LED will flash slowly.
If the connection has been successful, the WPS LED will remain
illuminated for 5 minutes. If the connection attempt has failed, the WPS
LED will flash rapidly for 5 minutes. You can re-try the connection by
pressing the WPS button, when the connection process will re-start.
If you want to add a further client to the Router, you do not need to wait
for the 5 minute period to end. You can press the WPS button (or use the
PIN method via the web interface) as soon as the first client is successfully
connected.
Page 20
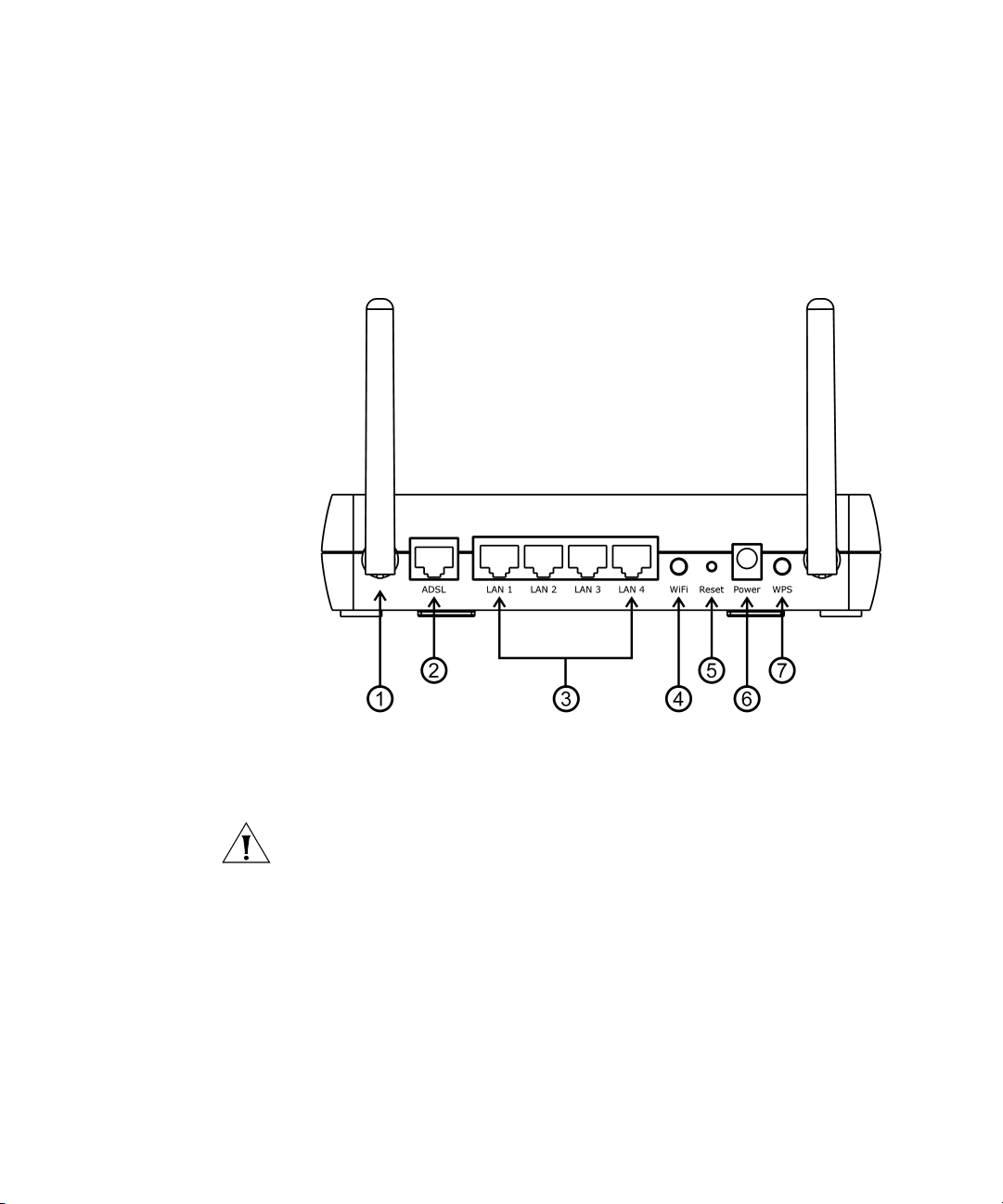
18 CHAPTER 1: INTRODUCING THE ROUTER
The rear panel (Figure 5) of the Router contains one ADSL port, four LAN
ports, one WiFi on/off button, a reset button, one power adapter socket,
and one WPS button.
Figure 5 Router - Rear Panel
1 Wireless Antennae
The antennaes should be placed in a ‘V’ position when initially installed.
CAUTION: Do not force the antennae beyond their mechanical stops.
Rotating the antennae further may cause damage.
2ADSL Port
RJ-11 port (3CRWDR300A-73)/ RJ-45 port (3CRWDR300B-73), connect
this port with the telephone socket.
3 Ethernet Ports (4 ports)
Using suitable RJ-45 cables, you can connect your Router to a computer,
or to any other piece of equipment that has an Ethernet connection (for
example, a hub or a switch). These ports have an automatic MDI/MDIX
feature, which means either straight-through or a crossover cable can be
used.
Page 21

Physical Features 19
4 WiFi On/Off button
Use this button to turn on/turn off the wireless function. Press the button
for 3 seconds.
5 Reset Button
If you want to reset your Router to factory default settings, or cannot
access the web management interface (for example, due to a lost
password), then you may use this button. Refer to Forgotten Password
and Reset to Factory Defaults on page 138 for further details.
6 Power Adapter Socket
Only use the power adapter that is supplied with this Router. Do not use
any other adapter.
7 WPS button
Press this button for 3 seconds when making WPS setup. Pushing the
WPS button will automatically enable WPS. Then initiate the WPS
procedure on the wireless NIC within two minutes. Refer to your wireless
NIC's documentation on this procedure. The wireless NIC will then be
securely added to your wireless network.
Page 22

20 CHAPTER 1: INTRODUCING THE ROUTER
Page 23
INSTALLING THE ROUTER
2
Introduction This chapter will guide you through a basic installation of the Router,
including:
■ Connecting the Router to the Internet.
■ Connecting the Router to your network.
■ Setting up your computers for networking with the Router.
Safety Information Please note the following:
Positioning the Router
WARNING: Please read the Safety Information
before you start.
VORSICHT: Bitte lesen Sie den Abschnitt Wichtige Sicherheitshinweise
sorgfältig durch, bevor Sie das Gerät einschalten.
AVERTISSEMENT: Veuillez lire attentivement la section Consignes
importantes de sécurité avant de mettre en route.
You should place the Router in a location that:
■ is conveniently located for connection to the telephone socket.
■ is centrally located to the wireless computers that will connect to the
Router. A suitable location might be on top of a high shelf or similar
furniture to optimize wireless connections to computers in both
horizontal and vertical directions, allowing wider coverage.
■ allows convenient connection to the computers that will be connected
to the four LAN ports on the rear panel, if desired.
■ allows easy viewing of the LED indicator lights, and access to the rear
panel connectors, if necessary.
section in Appendix C
Page 24
22 CHAPTER 2: INSTALLING THE ROUTER
When positioning your Router, ensure:
■ It is out of direct sunlight and away from sources of heat.
■ Cabling is away from power lines, fluorescent lighting fixtures, and
sources of electrical noise such as radios, transmitters and broadband
amplifiers.
■ Water or moisture cannot enter the case of the unit.
■ Air flow around the unit and through the vents in the side of the case
is not restricted. 3Com recommends you provide a minimum of
25 mm (1 in.) clearance.
Using the Rubber
Feet
Use the four self-adhesive rubber feet to prevent your Router from
moving around on your desk or when stacking with flat top units. Only
stick the feet to the marked areas at each corner of the underside of your
Router.
Please be careful when you put 3Com 11n ADSL Router on top of
another unit, if the unit underneath is hot, this may impact the reliability
of 3Com 11n ADSL Router.
Wall Mounting There are two slots on the underside of the Router that can be used for
wall mounting. The Router must be mounted with the LEDs facing
upwards.
When wall mounting the unit, ensure it is within reach of the power
outlet. When wall mounting the unit, ensure that the rubber feet are not
fixed.
Mounting
Instructions for
Cement Walls
To wall mount the unit:
1 Make two holes 98 mm (3.9 in.) apart and insert two nylon or similar
screw anchors that are suitable for the wall construction.
2 Fix two suitable screws into the anchors, leaving their heads 3 mm (0.12
in.) clear of the wall surface. The screws should be at least 30 mm (1.2
in.) long.
3 Remove any connections in the Router and locate it over the screw heads.
When in line, gently push the Router on to the wall and move it
downwards to secure.
Page 25
Powering Up the Router 23
Mounting
Instructions for
Wood Walls
Powering Up the Router
To wall mount the unit:
1 Make two holes 98 mm (3.9 in.) apart.
2 Fix two suitable screws directly into the wall, leaving their heads 3 mm
(0.12 in.) clear of the wall surface. The screws should be at least 20 mm
(0.75 in.) long.
3 Remove any connections in the Router and locate it over the screw heads.
When in line, gently push the Router on to the wall and move it
downwards to secure.
CAUTION: When making connections, be careful not to push the unit up
and off the wall.
To power up the Router:
1 Plug the power adapter into the power adapter socket located on the
back panel of the Router.
2 Plug the power adapter into a standard electrical wall socket.
Connecting the Router
The first step for installing your Router is to physically connect it to the
telephone socket and then connect it to a computer in order to be able to
access the Internet. See Figure 6 and Figure 7:
Page 26
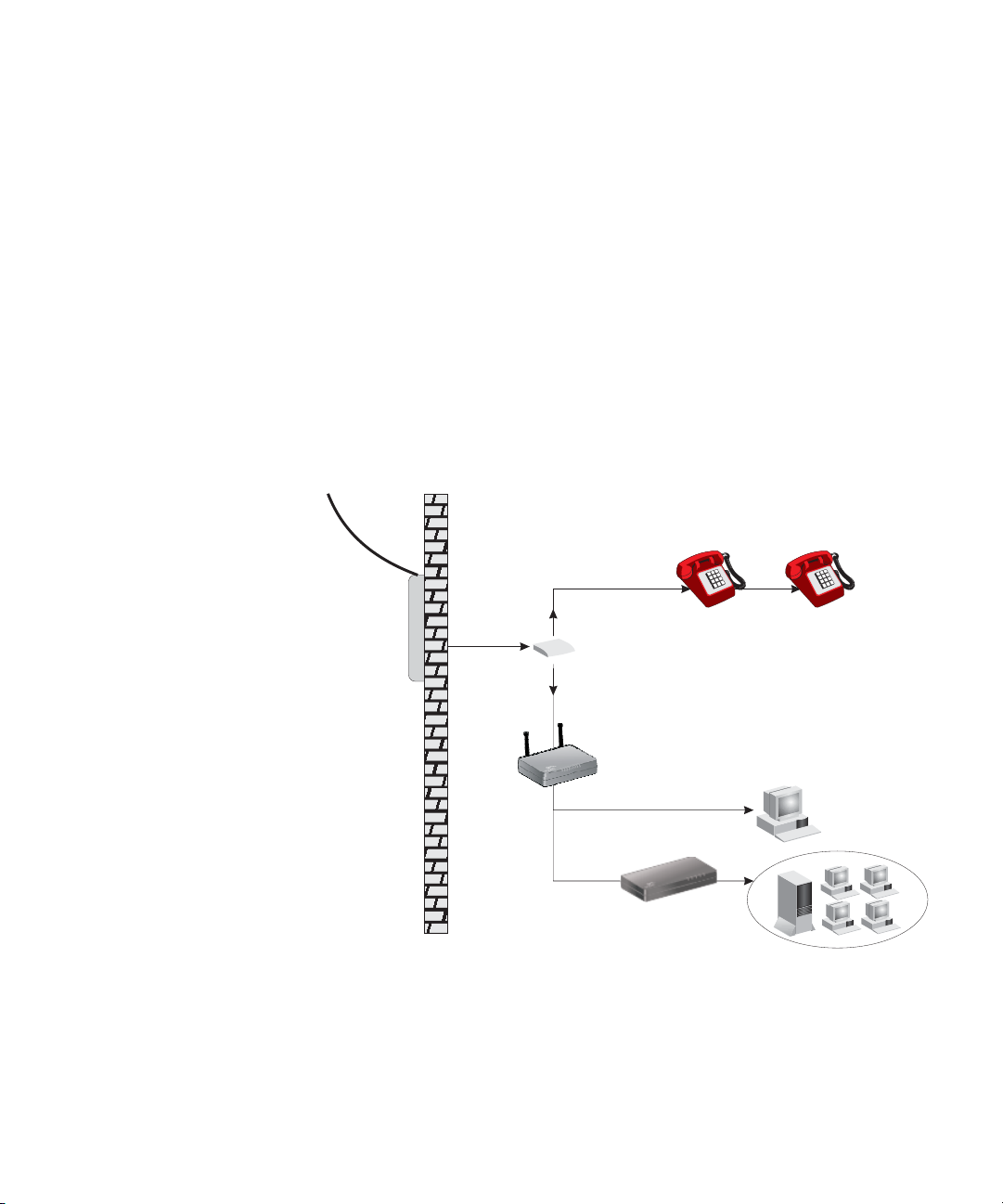
24 CHAPTER 2: INSTALLING THE ROUTER
Figure 6 Connecting the Router (with splitter)
Figure 7 Connecting the Router (without splitter)
1 Run the provided telephone cable from the wall jack providing ADSL
service to the ADSL port on your Router. When inserting an ADSL
RJ-11(Annex A) or RJ-45 (Annex B) plug, be sure the tab on the plug
clicks into position to ensure that it is properly seated. If you are using
splitterless ADSL service, add low-pass filters between the ADSL wall jack
and your telephones. (These filters pass voice signals through but filter
data signals out.)
Page 27
Connecting the Router 25
Voice
Data
Residential
Connection
Point (NID)
Plain Old
Telephone
System (POTS)
or
Ethernet
switch
Splitter
ADSL Router
2 Then:
■ If you are using a full-rate (G.dmt) connection, your service provider
will attach the outside ADSL line to a data/voice splitter. In this case
you can connect your phones and computer directly to the splitter as
shown below (Figure 8):
or
■ If you are using a splitterless (G.lite) connection, then your service
provider will attach the outside ADSL line directly to your phone
system. In this case you can connect your phones and computer
directly to the incoming ADSL line, but you will have to add low-pass
filters to your phones as shown below (Figure 9)
Figure 8 Installing with a splitter
Page 28
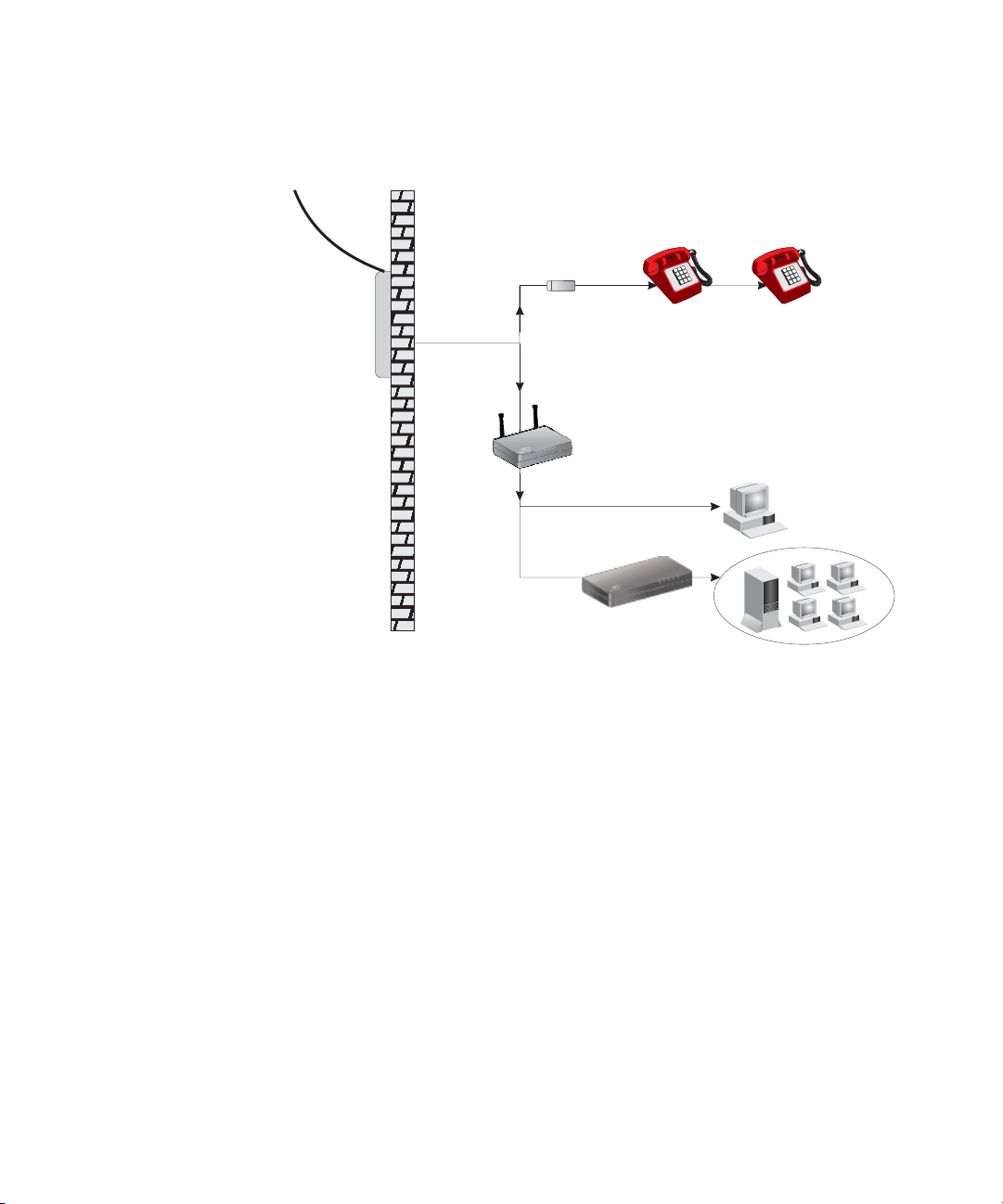
26 CHAPTER 2: INSTALLING THE ROUTER
Plain Old
Telephone
System (POTS)
Filter
or
Voice
& Data
Voice
& Data
Data
Voice
ADSL Router
Residential
Connection
Point [Network
Interface
Device (NID)]
Ethernet
switch
Figure 9 Installing without a splitter
You have now completed the hardware installation of your Router. Next
you need to set up your computers so that they can make use of the
Router to communicate with the Internet.
3Com recommends that you perform the initial Router configuration
from a computer that is directly connected to one of the LAN ports.
If you configure the Router from a wireless computer, note that you may
lose contact with the Router if you change the wireless configuration.
To communicate wirelessly with your Router, your wireless NIC should be
set as follows:
■ Encryption — none
■ SSID — 3Com
■ Channel — 11
Page 29

3
Obtaining an IP Address Automatically
Windows 2000 If you are using a Windows 2000-based computer, use the following
SETTING UP YOUR COMPUTERS
The Router has the ability to dynamically allocate network addresses to
the computers on your network, using DHCP. However, your computers
need to be configured correctly for this to take place. To change the
configuration of your computers to allow this, follow the instructions in
this chapter.
procedure to change your TCP/IP settings:
1 From the Windows Start Menu, select Settings > Control Panel.
2 Double click on Network and Dial-Up Connections.
3 Double click on Local Area Connection.
4 Click on Properties.
5 A screen similar to Figure 10 should be displayed. Select Internet Protocol
TCP/IP and click on Properties.
Page 30
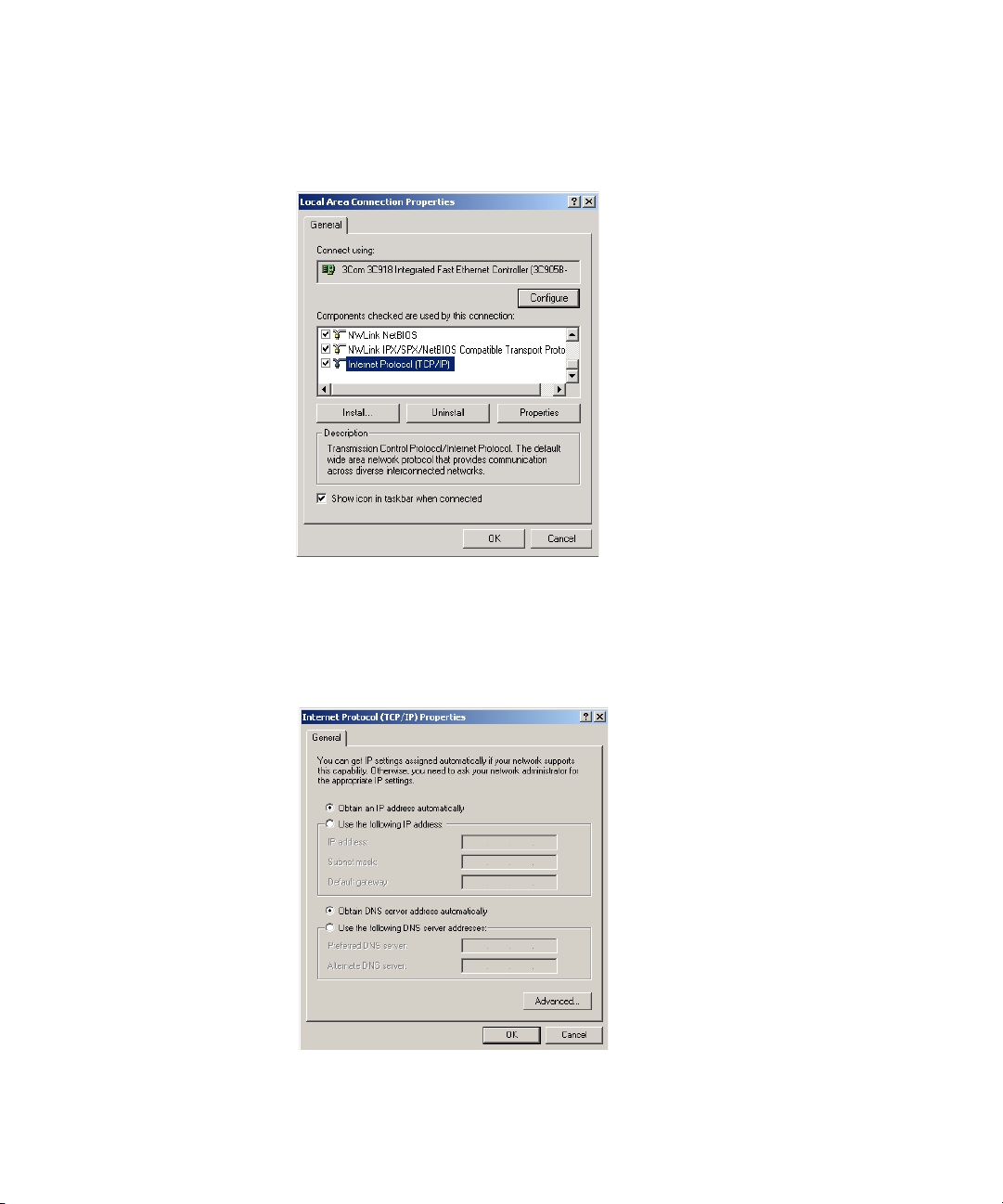
28 CHAPTER 3: SETTING UP YOUR COMPUTERS
Figure 10 Local Area Properties Screen
6 Ensure that the options Obtain an IP address automatically, and Obtain
DNS server address automatically are both selected as shown in
Figure 11. Click OK.
Figure 11 Internet Protocol (TCP/IP) Properties Screen
7 Restart your computer.
Page 31

Windows Vista
Obtaining an IP Address Automatically 29
1 From the Windows Start Menu, select Settings > Network.
2 Click on Organize. Select Properties.
3 Click on Manage network > Connections.
4 Double click Local Area Connection. Select Properties and click continue.
5 A screen similar to Figure 12 should appear. Select Internet Protocol
Version 6,Version 4 (TCP/IPv6,v4) and click on Properties.
Figure 12 Local Area Connection Properties Screen
6 Ensure that the options Obtain an IPv6,v4 address automatically, and
Obtain DNS servers address automatically are both selected as shown in
Figure 13. Click OK.
Figure 13 Internet Protocol Version 6 (TCP/IPv6) Properties Screen
Page 32

30 CHAPTER 3: SETTING UP YOUR COMPUTERS
Windows XP
1 From the Windows Start Menu, select Control Panel.
2 Click on Network and Internet Connections.
3 Click on the Network Connections icon.
4 Double click on LAN or High Speed Connection icon. A screen titled Local
Area Connection Status will appear.
5 Select Internet Protocol TCP/IP and click on Properties.
6 Ensure that the options Obtain an IP address automatically, and Obtain
DNS servers automatically are both selected. Click OK.
7 Restart your computer.
Macintosh If you are using a Macintosh computer, use the following procedure to
change your TCP/IP settings:
1 From the desktop, select Apple Menu, Control Panels, and TCP/IP.
2 In the TCP/IP control panel, set Connect Via: to Ethernet.
3 In the TCP/IP control panel, set Configure: to Using DHCP Server.
4 Close the TCP/IP dialog box, and save your changes.
5 Restart your computer.
Page 33

Disabling PPPoE and PPTP Client Software 31
Disabling PPPoE and PPTP Client Software
If you have PPPoE client software installed on your computer, you will
need to disable it. To do this:
1 From the Windows Start Menu, select Settings > Control Panel.
2 Double click on Internet Options.
3 Select the Connections Tab. A screen similar to Figure 14 should be
displayed.
4 Select the Never dial a connection option.
Figure 14 Internet Properties Screen
Disabling Web Proxy
You may want to remove the PPPoE client software from your computer
to free resources, as it is not required for use with the Router.
Ensure that you do not have a web proxy enabled on your computer.
Go to the Control Panel and click on Internet Options. Select the
Connections tab and click LAN Settings at the bottom. Make sure that
the Use Proxy Server option is unchecked.
Page 34

32 CHAPTER 3: SETTING UP YOUR COMPUTERS
Page 35

4
RUNNING THE SETUP WIZARD
Accessing the Router using the 3Com Detect Application
Running the 3Com Detect Application
The 3Com Detect application works by automatically locating your
Router, establishing what IP address it is using and then launching your
default web browser to connect directly to it.
The application will only locate your Router if it is on the same subnet as
the PC on which the application is running. It will not be able to locate
your Router if there is another router between your PC and the Router.
Note that the 3Com detect application is only designed to run on
Windows operating systems.
The CD-ROM that comes with this Router contains, in addition to the
documentation, the 3Com Detect Application.
To use 3Com Detect to connect to the Web interface of your Router, do
the following:
On the computer that is connected to your Router (either directly or on a
network that is on the same subnet), insert the CD-ROM into its CD drive.
If you have autorun enabled, you will be presented with a menu showing
the contents of the CD-ROM. Select the 3Com Detect Application link to
install the utility. Follow the onscreen instructions.
If the auto-run program does not start, you should browse to your
CD-ROM drive, go to the /3Com detect directory and double click on
setup.exe. Follow the prompts that will take you through the installation
process.
Once installed, the 3Com Detect Application can be accessed from the
Windows Start/Programs list.
When the 3Com Detect application starts, you will see the Welcome
Screen, see Figure 15.
Page 36

34 CHAPTER 4: RUNNING THE SETUP WIZARD
Figure 15 3Com Detect Application
If the computer has multiple network adapters, select the adapter that
connects the computer to the network or the Router, click Next.
You will then be offered the choice of searching the same subnet that
your PC is on for a connected Router (default), or specifying an IP range.
Note that specifying a large range may take some time for the search to
complete (see Figure 16 and Figure 17).
Figure 16 Discovery Screen - search the same subnet
Figure 17 Discovery Screen - search IP range
Once your Router has been located, you will see the list (see Figure 18).
Select the Router to which you want to connect and click Open. Your
default Web browser will launch and connect to the home page of the
Router, see Figure 20.
Page 37

Figure 18 Router List Screen
Accessing the Setup Wizard 35
Accessing the Setup Wizard
The Router setup program is Web-based, which means that it is accessed
through your Web browser (Netscape Navigator 4.7 or higher, Internet
Explorer 6.0 or higher, or Mozilla 1.2.1 or higher, or Apple’s Safari).
To use the Setup Wizard:
1 Ensure that you have at least one computer connected to the Router.
Refer to Chapter 2 for details on how to do this.
2 Launch your Web browser on the computer.
3 Enter the following URL in the location or address field of your browser:
http://192.168.1.1 (Figure 19). The Login screen displays.
Figure 19 Web Browser Location Field (Factory Default)
Page 38

36 CHAPTER 4: RUNNING THE SETUP WIZARD
4 To log in as an administrator, enter the password (the default password is
admin) in the System Password field and click Log in (see Figure 20).
Figure 20 Router Login Screen
5 When you have logged in,
■ if you are logging in for the first time, the Country Selection screen
will appear (see Figure 21). Please select the country form the
drop-down menu, and click Apply.
1. To comply with US FCC regulations, operation for any country is limited
to channels from 1 to 11.
2. Customers outside of the US, Canada or Taiwan can download the
firmware from the 3Com website (www.3com.com) which will enable
operation on channels 12-13. You will be asked to verify your country
before you can download the firmware what will enable the wider
range of channels to be used.
Figure 21 Country Selection Screen
Page 39

Accessing the Setup Wizard 37
The Wizard will then launch automatically (refer to Figure 24). You will be
guided step by step through a basic setup procedure.
■ if the Router has been configured previously, the Welcome screen will
appear (Figure 22). There are three tabs: Notice Board, Password and
Wizard.
Figure 22 Welcome Screen
■ Go to the Notice Board tab to see the current software information. To
view the Web help, click the Help button.
■ Go to the Password tab to change the password (Figure 23).
■ Go to the Wizard tab to do a quick setup of the Router (Figure 24).
The password screen allows you to change the current password and set
the login time limit to the Router’s management interface.
Page 40

38 CHAPTER 4: RUNNING THE SETUP WIZARD
Figure 23 Password Screen
1 To change the current password, enter the password in the Current
Password field.
2 Enter the new password in the New Password field, and enter it again in
the Confirm New Password field.
3 Enter the time period in Login Timeout to set a maximum period of time
for which the login session is maintained during inactivity
(default: 10 minutes). Then click Apply.
Wizard - Change
Password
To ensure the security of your Router, it is recommended that you choose
a new password - this should be a mix of letters and numbers, and not
easily guessed by others. To leave the current password unchanged, leave
the fields blank and click Next.
Figure 24 Change Password Screen
Page 41

Accessing the Setup Wizard 39
Wizard - Time and
Time Zone
The Time and Time Zone screen allows you to set up the time for the
Router.
Figure 25 Time and Time Zone Screen
1 Select the correct base date and time.
2 If you want to automatically synchronize the Router with a public time
server, check the Enable box in the Using Time Server (NTP) field.
3 Select the time zone in the Set Time Zone drop-down menu.
4 Enter the time in the Synchronization Interval field.
5 Select the desired servers from the Time Server drop-down menu.
6 Check the Enable box in the Daylight Savings field, if daylight savings
applies to your area.
7 Click Next.
Page 42

40 CHAPTER 4: RUNNING THE SETUP WIZARD
Wizard - Connection
Ty pe
The Connection Type screen allows you to set up the Router for the type
of Internet connection you have. Before setting up your connection type,
have your account information from your ISP ready.
Figure 26 Connection Type Screen
Select a mode from the following options, and click Next:
■ PPPoE — PPP over Ethernet, providing routing for multiple PCs,
see page 41
■ PPPoA — PPP over ATM, providing routing for multiple PCs,
see page 42
■ Bridge Mode (for a single PC) — RFC1483 Bridged Mode, see page 43
■ Routing Mode over ATM — RFC1483 Routed Mode, for multiple PCs,
see page 44
■ Dynamic/Fixed IP in 1483 Bridge Mode (For Multiple PCs) — see
page 45
For further information on selecting a mode see Internet Settings on
page 76.
Page 43

Accessing the Setup Wizard 41
PPPoE
PPPoE is often used for DSL connection. To set up the Router for use with
a PPPoE (PPP over Ethernet) connection, use the following procedure:
Figure 27 PPPoE Screen
1 Enter your user name in the Username field.
2 Enter your password in the Password field.
3 Re-type your password in the Retype Password field.
4 Enter your VPI and VCI information in the VPI/VCI fields.
5 Select the encapsulation type (LLC or VC MUX) in the Encapsulation
drop-down menu. This information should be provided to you by your ISP.
Check all of your settings, and then click Next.
The LAN Settings screen will then be displayed (refer to Figure 32).
Page 44

42 CHAPTER 4: RUNNING THE SETUP WIZARD
PPPoA
To set up the Router for use with a PPP over ATM (PPPoA) connection, use
the following procedure:
Figure 28 PPPoA Screen
1 Enter your user name in the Username field.
2 Enter your password in the Password field.
3 Re-type your password in the Retype Password field.
4 Enter your VPI and VCI information in the VPI/VCI fields.
5 Select the encapsulation type (LLC or VC MUX) in the Encapsulation
drop-down menu. This information should be provided to you by your ISP.
Check all of your settings, and then click Next.
The LAN Settings screen will then be displayed (refer to Figure 32).
Page 45

Accessing the Setup Wizard 43
Bridge Mode (for a single PC)
Selecting the Bridge mode sets the device into 1483 bridging mode in
which the device connects LANs and WAN together. It operates as a Data
Link Layer device that acts to limit the traffic between two network
segments by filtering the data between them based on the hardware
address.
To set up the Router for use with an RFC1483 bridged connection, use
the following procedure:
Figure 29 Bridged Mode Screen
1 Enter your VPI and VCI information in the VPI/VCI fields.
2 Select the encapsulation type (LLC or VC MUX) in the Encapsulation
drop-down menu. This information should be provided to you by your ISP.
Check all of your settings, and then click Next.
The LAN Settings screen will then be displayed (refer to Figure 32).
Page 46

44 CHAPTER 4: RUNNING THE SETUP WIZARD
Routing Mode over ATM
The Routing Mode over ATM uses fixed/static IP addresses, which are
provided by your ISP, to connect to the Internet. Obtain the information
on this screen from your ISP.
Figure 30 Routing mode over ATM Screen
1 Enter your Internet IP address in the WAN IP field.
2 Enter the subnet mask in the Subnet Mask field.
3 Enter the default gateway IP address in the Default Gateway field.
4 Enter the DNS address in the DNS field.
5 Enter your VPI and VCI information in the VPI/VCI fields.
6 Select the encapsulation type (LLC or VC MUX) in the Encapsulation
drop-down menu. This information should be provided to you by your ISP.
Check all of your settings, and then click Next.
The LAN Settings screen will then be displayed (refer to Figure 32).
Page 47

Accessing the Setup Wizard 45
Dynamic/Fixed IP in 1483 Bridge Mode (For Multiple PCs)
For bridge mode to work, you need to assign an IP address to the Router.
You can either configure the Router to obtain an IP address automatically
from a DHCP server or assign a fixed or static IP address to it.
Figure 31 Dynamic/Fixed IP for Bridge Mode Screen
■ To obtain an IP address automatically from a DHCP server: check the
Get WAN IP By DCHP checkbox, and then click Next.
■ To assign a fixed IP address:
1 Enter your IP address in the WAN IP field.
2 Enter the subnet mask in the Subnet Mask field.
3 Enter the default gateway IP address in the Default Gateway field.
4 Enter the DNS address in the DNS field.
5 Enter your VPI and VCI information in the VPI/VCI fields.
6 Select the encapsulation type (LLC or VC MUX) in the Encapsulation
drop-down menu. This information should be provided to you by your ISP.
Check all of your settings, and then click Next.
The LAN Settings screen will then be displayed (refer to Figure 32).
Page 48

46 CHAPTER 4: RUNNING THE SETUP WIZARD
Wizard - LAN Settings The LAN Settings screen allows you to set the default IP address and
DHCP client IP range for the Router.
Figure 32 The LAN Settings Screen
1 To change the Router’s default IP address, enter the new IP address in the
IP Address field, and then enter the subnet mask in the Subnet Mask
field.
2 Check the Enable DHCP Server box to enable the DHCP function.
3 Enter the client IP address range in the IP Pool Start Address and IP Pool
End Address fields. You can also click Auto IP Range to automatically set
the starting and ending IP address: 192.168.1.2 ~ 192.168.1.254.
4 Click Next. The Wireless Settings screen will appear (refer to Figure 33).
Page 49

Accessing the Setup Wizard 47
Wizard - Wireless
Setting
The Wireless Settings screen allows you to set up the SSID and radio
channel used for the wireless connection.
Figure 33 Wireless Setting Screen
1 Select the channel you want to use from the Channel drop-down menu.
2 Specify the SSID to be used by your wireless network in the SSID field. If
there are other wireless networks in your area, you should give your
wireless network an unique name.
For advanced settings, please click Wireless Settings on the left menu bar
after completing this Setup Wizard setting.
3 Click Next. The security mode screen appears.
Security Mode
Select the Security Mode, five options available:
■ Disabled: in this mode, wireless transmissions will not be
encrypted, and will be visible to everyone. However, when setting
up or debugging wireless networks, it is often useful to use this
security mode.
■ 64-bit WEP, see page 48
■ 128-bit WEP, see page 49
■ WPA-PSK (no server), this mode includes WPA and WPA2,
see page 50
■ WPA (with Radius Server), this mode includes WPA and WPA2,
see page 51
Page 50

48 CHAPTER 4: RUNNING THE SETUP WIZARD
Figure 34 Security Mode Screen
64-bit WEP
WEP is the basic mechanism to transmit your data securely over the
wireless network. Matching encryption keys must be setup on your
Router and wireless client devices to use WEP.
Figure 35 64-bit WEP Screen
To enable 64-bit WEP:
1 You can enter the 64-bit WEP key manually. Enter the WEP key as 5 pairs
of hex digits (0-9, A-F). Or you can generate the 64-bit WEP key
automatically. Enter a memorable passphrase in the Passphrase box, and
then click Generate to generate the hex keys from the passphrase.
For 64-bit WEP, you can enter up to four keys, in the fields Key 1 to Key 4.
The radio button on the left hand side selects the key that is used in
transmitting data.
Page 51

Accessing the Setup Wizard 49
2 Click Next.
Note that all four WEP keys on each device of the same wireless network
must be identical.
128-bit WEP
WEP is the basic mechanism to transmit your data securely over the
wireless network. Matching encryption keys must be set up on your
Router and wireless client devices to use WEP.
Figure 36 128-bit WEP
To enable 128-bit WEP:
1 You can enter the 128-bit WEP key manually, enter your WEP key as 13
pairs of hex digits (0-9, A-F). Or you can generate the 128-bit WEP key
automatically, enter a memorable passphrase in the Passphrase box, and
then click Generate to generate the hex keys from the passphrase.
2 Click Next.
Note that the WEP keys on each device of the same wireless network
must be identical. And In 128-bit WEP mode, only one WEP key can be
specified.
Page 52

50 CHAPTER 4: RUNNING THE SETUP WIZARD
WPA-PSK (no server)
WPA (Wi-Fi Protected Access) provides dynamic key changes and
constitutes the best security solution. If your network does not have a
RADIUS server. Select the no server option. Note that in home and very
small office deployments, PSK is typically used.
Figure 37 WPA-PSK no server Screen
1 Select WPA-PSK (no server) from the WPA drop-down menu.
2 Select WPA mode from the drop-down menu, three modes are
supported: WPA, WPA2, and Mixed mode.
3 Select Encryption technique from the drop-down menu, four options are
available: TKIP, AES, Auto for WPA AES for WPA2, and AES for both WPA
and WPA2.
WPA supports TKIP and AES Encryption technique, for some old module
of wireless client cards, they may only support TKIP. In this case, we
suggest you to select “AUTO for WPA, AES for WPA2”. If your wireless
client cards can support AES over WPA, we suggest you directly select
“AES for both WPA and WPA2”.
4 Enter the pre-shared key in the Pre-shared Key (PSK) field. The pre-shared
key is a password, in the form of a word, phrase or series of letters and
numbers. The key must be between 8 and 63 characters long and can
include spaces and symbols. Each client that connects to the network
must use the same key.
5 If you want the key that you enter to be shown on the screen as a series
of asterisks (*), then check the Hide PSK checkbox.
6 Click Next.
Page 53

Accessing the Setup Wizard 51
WPA with Radius Server
WPA (Wi-Fi Protected Access) provides dynamic key changes and
constitutes the best security solution. This function requires that a
RADIUS server is running on the network.
Figure 38 WPA with Radius Server Screen
1 Select WPA with RADIUS server from the Security Mode drop-down
menu.
2 Select WPA mode from the drop-down menu, three modes are
supported: WPA, WPA2, and Mixed mode.
3 Select Encryption technique from the drop-down menu, four options are
available: TKIP, AES, Auto for WPA AES for WPA2, and AES for both WPA
and WPA2.
WPA supports TKIP and AES Encryption technique, for some old module
of wireless client cards, they may only support TKIP. In this case, we
suggest you to select “AUTO for WPA, AES for WPA2”. If your wireless
client cards can support AES over WPA, we suggest you directly select
“AES for both WPA and WPA2”.
4 Enter the IP address of the RADIUS server on your network into the
RADIUS Server field.
5 Enter the Radius Port number that the RADIUS server is operating on.
6 Enter the key for the RADIUS server in the Radius Key field.
7 By default, the WPA keys are changed every hour, but if you want to
change this setting, you can do so by specifying the rotation time in the
Re-key Interval field.
8 Click Next.
Page 54

52 CHAPTER 4: RUNNING THE SETUP WIZARD
Wizard -
Configuration
Summary
When you have completed the Setup Wizard, a configuration summary
will appear. Verify the configuration information of the Router and then
click Apply to save your settings. 3Com recommends that you print out
this page for your records.
Figure 39 Configuration Summary Screen
Your Router is now configured and ready for use.
See Chapter 5 for a further detailed description of the Router
configuration.
Page 55

5
CONFIGURING THE ROUTER
Navigating through the Router Configuration Screens
Main Menu The main menu is located on the left side, as shown in Figure 40. When
Welcome Screen The Welcome screen shows the current software information.
Status
This chapter describes all the screens available through the Router
configuration screens, and is provided as a reference. To get to the
configuration screens, enter the Router’s default IP in the location bar of
your browser. The default IP is http://192.168.1.1.
However, if you changed the Router LAN IP address during initial
configuration, use the new IP address instead. Enter your password to
login to the management interface. (The default password is admin).
you click on an item from the main menu, the corresponding screen will
then appear in the center.
Figure 40 Welcome Screen
Page 56

54 CHAPTER 5: CONFIGURING THE ROUTER
LAN Settings Your Router is equipped with a DHCP server that will automatically assign
IP addresses to each computer on your network. The factory default
settings for the DHCP server will work with most applications. If you need
to make changes to the settings, you can do so.
The LAN settings screen allows you to:
■ Change the default IP address of the Router. The default IP is
192.168.1.1
■ Change the Subnet Mask. The default setting is 255.255.255.0
■ Enable/Disable the DHCP Server Function. The default is: Enable.
■ Specify the Starting and Ending IP Pool address. The default is
Starting: 2 / Ending: 254.
■ Specify the IP address Lease Time. The default is One day.
■ Specify a local Domain Name. This field is optional.
■ Specify the IP address of 3Com NBX call processor.
The Router will also provide a list of all client computers connected to the
Router.
LAN Settings Unit
Configuration
The LAN Settings unit configuration screen is used to specify the LAN IP
address of your Router, and to configure the DHCP server.
Figure 41 LAN Settings Unit Configuration Screen
Page 57

LAN Settings 55
1 Enter the Router’s IP Address and Subnet Mask in the appropriate fields.
The default IP address is 192.168.1.1.
2 If you want to use the Router as a DHCP Server, check Enable in the DHCP
Server field.
3 Enter the IP address range in the IP Pool Start Address and IP Pool End
Address fields.
4 Specify the DHCP Lease time by selecting the required value from the
Lease Time drop-down menu. The lease time is the length of time the
DHCP server will reserve the IP address for each computer.
5 Specify the Local Domain Name for your network (this step is optional).
6 Enter the IP address of the NBX Call Processor in the 3Com NBX Call
Processor field (this step is optional).
7 Check all of your settings, and then click Apply.
DHCP Clients List The DHCP Clients List provides details on the devices that have received IP
addresses from the Router. The list is only created when the Router is set
up as a DHCP server. A maximum of 253 clients can be connected to the
Router.
Figure 42 DHCP Clients List Screen
For each device that is connected to the LAN, the following information is
displayed:
■ IP address — The Internet Protocol (IP) address issued to the client
machine.
Page 58

56 CHAPTER 5: CONFIGURING THE ROUTER
■ Host Name — The client machine’s host name, if configured.
■ MAC Address — The Media Access Control (MAC) address of the
client’s network card.
■ Client Type — Whether the client is connected to the Router by wired
or wireless connection.
■ Check the Fix checkbox to permanently fix the IP address.
■ Click Release to release the displayed IP address.
■ Click Add to allocate an IP address to a MAC address. Enter the
required details and click Apply to save your settings.
The DHCP server will give out addresses to both wired and wireless
clients.
Page 59

Wireless Settings 57
Wireless Settings The Wireless Settings screens allow you to configure the settings for the
wireless connections.
You can enable or disable the wireless connection for your LAN. When
disabled, no wireless PCs can gain access to either the Internet or other
PCs on your wired or wireless LAN through this Router.
Figure 43 Wireless Settings Screen
There are 8 tabs available:
■ Configuration
■ Encryption
■ WPS
■ Connection Control
■ Client List
■ WMM
■ WDS
■ Advanced
Page 60

58 CHAPTER 5: CONFIGURING THE ROUTER
Configuration The Wireless Configuration Screen allows you to turn on/ turn off the
wireless function, and set up basic wireless settings. You can also
enable/disable the Wireless function using the WiFi on/off button at the
back of the Router.
Figure 44 Wireless Configuration Screen
To enable the wireless function:
1 Check Enable Wireless Networking checkbox.
2 Select the wireless channel you want to use from the Channel drop-down
menu.
3 Select the Extension Channel.
4 Specify the SSID to be used by your wireless network in the SSID field. If
there are other wireless networks in your area, you should give your
wireless network an unique name.
5 Enable or disable SSID Broadcast.
A feature of many wireless network adapters is that a computer's SSID
can be set to ANY, which means it looks randomly for any existing
wireless network. The available networks are then displayed in a site
survey, and your computer can select a network. If you disable this SSID
broadcast function, you can block this random search, and set the
computer's SSID to a specific network (for example, WLAN). This
increases network security. If you decide to disable SSID Broadcast, ensure
that you know the name of your network first.
Page 61

Wireless Settings 59
6 Select whether your Router will operate in 11b mode only, 11g mode
only, 11n mode only, or mixed mode from the Wireless Mode drop-down
menu. If your network contains 11b, 11g, and 11n clients, select the
mixed mode. If your network contains just one type of clients only, select
11b only, or 11g only, or 11n only, depending on your wireless network
environment. Note that selecting one type of wireless network only will
improve the performance, however, this will prevent clients of other type
from connecting to the Router.
7 Bandwidth: select the bandwidth to use. Select 20/40 MHz when your
wireless mode is 802.11n or 11n with 11b, 11 g mixed mode. If your
wireless network is purely 11b only or 11g only, or 11b and 11g mixed,
select 20 MHz.
8 Select to turn on/off the Protected Mode function. As part of the
802.11g & 802.11n specification, Protected mode ensures proper
operation of 802.11g & 802.11n clients and access points when there is
heavy 802.11b traffic in the operating environment. When protected
mode is ON, 802.11g & 802.11n scans for other wireless network traffic
before it transmits data. Therefore, using this mode in environments with
HEAVY 802.11b traffic or interference achieves best performance results.
If you are in an environment with very little, or no other wireless network
traffic, your best performance will be achieved with Protected mode OFF.
9 Click Apply.
Page 62

60 CHAPTER 5: CONFIGURING THE ROUTER
Encryption This feature prevents any non-authorized party from reading or changing
your data over the wireless network.
Figure 45 Encryption Screen
Select the wireless security mode that you want to use from the
drop-down menu, and click Apply. There are five selections:
■ Disabled
■ 64-bit WEP (see page 61)
■ 128-bit WEP (see page 62)
■ WPA-PSK (no server): this option includes both WPA and WPA2
(see page 63)
■ WPA (with RADIUS Server): this option includes both WPA and WPA2
(see page 64)
Disabled
In this mode, wireless transmissions will not be encrypted, and will be
visible to everyone. However, when setting up or debugging wireless
networks, it is often useful to use this security mode.
Page 63

Wireless Settings 61
64-bit WEP
WEP is the basic mechanism to transmit your data securely over the
wireless network. Matching encryption keys must be setup on your
Router and wireless client devices to use WEP. Note that 3Com
recommends using WPA/WPA2 to secure your wireless connection.
Figure 46 64-bit WEP Screen
To setup 64-bit WEP:
1 You can enter the 64-bit WEP key manually:
■ enter the WEP key as 5 pairs of hex digits (0-9, A-F).
Or you can generate the 64-bit WEP key automatically:
■ enter a memorable passphrase in the Passphrase field, and then
click Generate to generate the hex keys from the passphrase.
For 64-bit WEP, you can enter up to four keys, in the fields Key 1 to Key 4.
The radio button on the left hand side selects the key that is used in
transmitting data.
Note that all four WEP keys on each device in the wireless network must
be identical.
2 Click Apply.
Page 64

62 CHAPTER 5: CONFIGURING THE ROUTER
128-bit WEP
WEP is the basic mechanism to transmit your data securely over the
wireless network. Matching encryption keys must be set up on your
Router and wireless client devices to use WEP. Note that 3Com
recommends using WPA/WPA2 to secure your wireless connection.
Figure 47 128-bit WEP Screen
To setup 128-bit WEP:
1 You can enter the 128-bit WEP key manually:
■ enter your WEP key as 13 pairs of hex digits (0-9, A-F).
Or you can generate the 128-bit WEP key automatically:
■ enter a memorable passphrase in the Passphrase field, and then
click Generate to generate the hex keys from the passphrase.
The WEP keys on each device on the wireless network must be identical.
In 128-bit WEP mode, only one WEP key can be specified.
2 Click Apply.
Page 65

Wireless Settings 63
WPA-PSK (no server)
WPA (Wi-Fi Protected Access) provides dynamic key changes and
constitutes the best security solution. If your network does not have a
RADIUS server. Select the no server option. For home network or very
small business networking environment, PSK is typically used.
Figure 48 WPA-PSK (no server) Screen
1 Select WPA-PSK (no server) from the WPA drop-down menu.
2 Select WPA mode from the drop-down menu, three modes are
supported: WPA, WPA2, and Mixed mode.
3 Select Encryption technique from the drop-down menu, four options are
available: TKIP, AES, Auto for WPA AES for WPA2, and AES for both WPA
and WPA2.
WPA supports TKIP and AES Encryption technique, for some old module
of wireless client cards, they may only support TKIP. In this case, we
suggest you to select “AUTO for WPA, AES for WPA2”. If your wireless
client cards can support AES over WPA, we suggest you directly select
“AES for both WPA and WPA2”.
4 Enter the pre-shared key in the Pre-shared Key (PSK) field. The pre-shared
key is a password, in the form of a word, phrase or series of letters and
numbers. The key must be between 8 and 63 characters long and can
include spaces and symbols. Each client that connects to the network
must use the same key.
5 If you want the key that you enter to be shown on the screen as a series
of asterisks (*), then check the Hide PSK checkbox.
6 Click Apply.
Page 66

64 CHAPTER 5: CONFIGURING THE ROUTER
WPA (with RADIUS Server)
WPA (Wi-Fi Protected Access) provides dynamic key changes and
constitutes the best security solution. This function requires that a
RADIUS server is running on the network.
Figure 49 WPA (with RADIUS Server) Screen
1 Select WPA with RADIUS server from the Security Mode drop-down
menu.
2 Select WPA mode from the drop-down menu, three modes are
supported: WPA, WPA2, and Mixed mode.
3 Select Encryption technique from the drop-down menu, four options are
available: TKIP, AES, Auto for WPA AES for WPA2, and AES for both WPA
and WPA2.
WPA supports TKIP and AES Encryption technique, for some old module
of wireless client cards, they may only support TKIP. In this case, we
suggest you to select “AUTO for WPA, AES for WPA2”. If your wireless
client cards can support AES over WPA, we suggest you directly select
“AES for both WPA and WPA2”.
4 Enter the IP address of the RADIUS server on your network into the
RADIUS Server field.
5 Enter the port number that the RADIUS server is operating on in the
RADIUS Port field.
6 Enter the key for the RADIUS server in the RADIUS Key field.
7 By default, the WPA keys are changed every hour, but if you want to
change this setting, you can do so by specifying the required time in the
Re-key Interval field.
8 Click Apply.
Page 67

Wireless Settings 65
WPS Wi-Fi Protected Setup (WPS) integrates the new WLAN clients into your
wireless network easily. You can enable this function by entering the PIN
code via the web UI page or by pressing the WPS button on the rear side
of the device.
Figure 50 WPS Screen
Two methods to setup the WPS, you can choose either one of the
following method. Note that if you choose to use the PBC mode, then it
would be no need to enter the PIN code of the wireless NIC on this
screen.
■ PIN
1 Check the Enable WPS Function box. The WPS-PIN field will appear.
2 Enter the PIN code in the WPS-PIN field. And then click Apply.
Please note that the PIN code is generated this way: on the client side,
run the WPS utility which is provided by the vendor of your Wi-Fi card
and select the PIN method. You should get an 8-digit PIN number from
the WPS utility.
Enter that 8-digit PIN number on this screen and click Apply to activate
this PIN method. Then the Router starts to negotiate the security with the
WLAN clients and WPS LED will start flashing. After the connection has
been established successfully, the WPS LED will then be off.
Page 68

66 CHAPTER 5: CONFIGURING THE ROUTER
■ WPS-PBC
1 Press the WPS button located on the rear of the Router. Note that this
setup process will only be active for 2 minutes. Follow the instruction of
your WLAN NIC to set up the WPS.
The WPS LED shows the status of the WPS function. It has a number of
modes to help monitor the status of clients connecting to the Router
using the WPS protocol. The status is shown by three different flashing
rates: slow, medium and quick and when light constantly.
When the WPS button is pressed, or WPS is initiated using the PIN
method in the web interface, the WPS LED will flash at a medium rate for
up to 2 minutes to indicate that a WPS connection can be made. When a
connection attempt is underway, the LED will flash slowly.
If the connection has been successful, the WPS LED will remain
illuminated for 5 minutes. If the connection attempt has failed, the WPS
LED will flash rapidly for 5 minutes. You can re-try the connection by
pressing the WPS button, when the connection process will re-start.
If you want to add a further client to the Router, you do not need to wait
for the 5 minute period to end. You can press the WPS button (or use the
PIN method via the web interface) as soon as the first client is successfully
connected.
Note: The WPS function will be enabled for 2 minutes once WPS is
enabled either by pressing the button or by starting the PIN mode via the
web interface. This time will end before 2 minutes if a client has
successfully connected. Only one client should be connected to the
Router using WPS at any one time. Attempting to connect two or more
clients at once may result in connection failures.
Page 69

Wireless Settings 67
Connection Control This feature is used to filter the clients based on their MAC addresses.
Using this function, you can limit the access right of the wireless clients to
this Router.
Check the Enable MAC Address Filtering checkbox, the Connection
Control screen will appear.
Figure 51 Connection Control Screen
There are two options available in the Access rule for registered MAC
address field:
■ if you click Allow, this means only the MAC addresses registered here
in the list will be allowed to access the Router via wireless link.
■ if you click Deny, this means the registered MAC addresses will not be
able to access the Router via wireless link.
Use the MAC Address Filtering List to quickly copy the MAC addresses of
the current wireless clients into the list table. You can define up to 32
MAC addresses to the list.
You can click Clear to delete the current entry in the list.
Page 70

68 CHAPTER 5: CONFIGURING THE ROUTER
Client List You can view the list of all wireless clients that are connected to the
Router.
Figure 52 Client List Screen
Click Refresh to update the list.
WMM Wireless Multimedia (WMM) mode, which supports devices that meet the
802.11E QBSS standard. WMM uses traffic priority based on the four
ACs; Voice, Video, Best Effort, and Background. The higher the AC
priority, the higher the probability that data is transmitted.
Check the Enable WMM Function box, the WMM parameters table
appears.
Figure 53 WMM Screen
Page 71

Wireless Settings 69
Access Categories – WMM defines four access categories (ACs): voice,
video, best effort, and background. These categories correspond to traffic
priority levels and are mapped to IEEE 802.1D priority tags. The direct
mapping of the four ACs to 802.1D priorities is specifically intended to
facilitate inter operability with other wired network QoS policies. While
the four ACs are specified for specific types of traffic, WMM allows the
priority levels to be configured to match any network-wide QoS policy.
WMM also specifies a protocol that access points can use to
communicate the configured traffic priority levels to QoS-enabled
wireless clients.
The following table explains the four access categories:
802.1D
Access Category WMM
Designation
AC_BE (AC0) Best Effort Normal priority, medium
AC_BK (AC1) Background Lowest priority. Data with no
AC_VI (AC2) Video High priority, minimum
AC_VO (AC3) Voice Highest priority, minimum
Description
delay and throughput. Data
only affected by long delays.
Data from applications or
devices that lack QoS
capabilities.
delay or throughput
requirements, such as bulk
data transfers.
delay. Time-sensitive data
such as streaming video.
delay. Time-sensitive data
such as VoIP (Voice over IP)
calls.
Tags
0, 3
2, 1
5, 4
7, 6
AIFS (Arbitration Inter-Frame Space) – The minimum amount of wait time
before the next data transmission attempt. Specify the AIFS value in the
range 0-15 microseconds.
CWMax (Maximum Contention Window) – The maximum upper limit of
the random backoff wait time before wireless medium access can be
attempted. The contention window is doubled after each detected
collision up to the CWMax value. Specify the CWMax value in the range
0-15 microseconds. Note that the CWMax value must be greater or equal
to the CWMin value.
Page 72

70 CHAPTER 5: CONFIGURING THE ROUTER
CWMin (Minimum Contention Window) – The initial upper limit of the
random backoff wait time before wireless medium access can be
attempted. The initial wait time is a random value between zero and the
CWMin value. Specify the CWMin value in the range 0-15 microseconds.
Note that the CWMin value must be equal or less than the CWMax value.
TXOP Limit (Transmit Opportunity Limit) – The maximum time an AC
transmit queue has access to the wireless medium. When an AC queue is
granted a transmit opportunity, it can transmit data for a time up to the
TxOp Limit. This data bursting greatly improves the efficiency for high
data-rate traffic. Specify a value in the range 0-65535 microseconds.
ACM – Admission Control Mode, for the access category. When enabled,
clients are blocked from using the access category. (Default: Disabled)
Ack Policy (WMM Acknowledge Policy) – By default, all wireless data
transmissions require the sender to wait for an acknowledgement from
the receiver. WMM allows the acknowledgement wait time to be turned
off for each Access Category (AC). Although this increases data
throughput, it can also result in a high number of errors when traffic
levels are heavy. (Default: Acknowledge)
Page 73

Wireless Settings 71
WDS The Router supports WDS (Wireless Distribution System). WDS enables
one or more Access Points to rebroadcast received signals to extend
range and reach, though this can affect the overall throughput of data.
Note that WDS implementation can vary from product to product. Hence
there is no guarantee that different products will interoperate. In
addition, the security settings for WDS links should be the same as the
one set up for your wireless clients.
Figure 54 Wireless WDS Settings Screen
1 Check the Enable WDS Function checkbox.
2 To refresh the list of available access points, click Rescan Wireless
Networking. If the MAC address of the desired APs is in the list of
scanned APs, you can simply check those APs to add them to the WDS.
3 Click Add to add the MAC address of the AP to the list, (up to 4 APs can
be added), the add WDS screen will appear (refer to Figure 55).
Page 74

72 CHAPTER 5: CONFIGURING THE ROUTER
Figure 55 Add WDS screen
On the add WDS screen, enter the MAC address of the access point, up
to 4 APs can be added to the AP MAC Address table, and click Apply.
Here is an example of how to setup two units of 3Com Router over WDS.
Note that when setting up two units of 3Com Router, you should disable
the DHCP function on one of the units.
Setting of the first Router:
■ Set the LAN IP setting, make sure the DHCP function is enabled on this
Router.
■ Set the wireless settings, including SSID, channel, and wireless mode.
■ Set the wireless security setting, and enable wireless WDS function.
Setting of the second Router:
■ Set the LAN IP setting, use a different IP address from the IP address of
the first Router. Disable the DHCP function, this would allow the first
Router to allocate IP address for wireless clients.
■ Set the wireless channel, and security same as the first Router, but use
a different SSID. Make sure that WDS function is enabled.
Access the Web UI of the first Router, use wireless WDS settings screen,
make sure that WDS is enabled. Click Rescan Wireless Networking to
scan the available APs in your area, you should see the SSID of the second
Router. Check and add the second Router to the WDS table
(see Figure 56).
Page 75

Wireless Settings 73
Figure 56 First Router Add WDS Screen
Access the Web UI of the second Router, repeat the above steps to add
the first Router to the WDS table (see Figure 57).
Figure 57 Second Router Add WDS Screen
Page 76

74 CHAPTER 5: CONFIGURING THE ROUTER
Advanced The Advanced screen allows you to configure detailed settings for your
wireless connection. Please note that you should not change this settings
unless you are an expert user. There are six parameters that you can
configure:
Figure 58 Wireless Advanced Setting Screen
■ Beacon Interval: this represents the amount of time between beacon
transmissions.
■ DTIM Interval: A DTIM (Delivery Traffic Indication Message) is a
countdown mechanism used to inform your wireless clients of the
next window for listening to broadcast and multicast messages.
■ Fragmentation Threshold: this is the maximum size for directed data
packets transmitted. The use of fragmentation can increase the
reliability of frame transmissions. Because of sending smaller frames,
collisions are much less likely to occur.
■ RTS Threshold: RTS stands for Request to Send, this parameter
controls what size data packet the low level RF protocol issues to an
RTS packet.
■ CTS Protection Mode: CTS stands for Clear to Send. CTS Protection
Mode boosts the Router’s ability to intercept 802.11b/ 802.11g
transmissions. Conversely, CTS Protection Mode decreases
performance. Leave this feature disabled unless you encounter severe
communication difficulties between the Router and your wireless
clients.
Page 77

Wireless Settings 75
■ AP Isolation Mode: AP Isolation is a function to prevent wireless clients
connected with the device from communicating with one another.
When enabled, this creates a separate virtual network for your
wireless network, each of your wireless client will be in its own virtual
network and will not be able to communicate with each other. You
may want to utilize this feature if you have many guests that
frequently connect to your wireless network.
Page 78

76 CHAPTER 5: CONFIGURING THE ROUTER
Internet Settings You can configure the settings for your WAN port connection.
ATM PVC This feature is used to configure the parameters for your Internet
connection. The information necessary to complete these screens should
be obtained from your ISP. Check with your ISP first to find out what type
of connection you should choose.
Figure 59 ATM PVC Screen
You should see the first entry already contains information that’s been
configured using the Wizard in the initial setup. If you want to change
that information or set up other connection, click Edit.
There are six options available for the connection mode:
■ Disable — To disable the Internet connection function (see page 77)
■ PPPoE — PPP over Ethernet, providing routing for multiple PCs
(see page 77)
■ PPPoA — PPP over ATM, providing routing for multiple PCs
(see page 80)
■ Bridge Mode — RFC1483 Bridged Mode, (see page 82)
■ Routing Mode over ATM — RFC1483/2684 routing mode over ATM
(see page 84)
■ Dynamic/Fixed IP in 1483 Bridge Mode — Using Dynamic/fixed IP for
WAN connection (see page 86)
Page 79

Internet Settings 77
Disable
Selecting this option means that you do not want your Router to connect
to the Internet.
Figure 60 Disable Internet Connection Screen
PPPoE
PPP over Ethernet, provides routing for multiple PCs, this mode is often
used for the DSL connection. To configure this function correctly, you
should obtain the information from your ISP.
Figure 61 PPPoE Settings Screen
Page 80

78 CHAPTER 5: CONFIGURING THE ROUTER
1 Select PPPoE from the protocol drop-down menu.
2 Enter the IP address and Subnet mask information.
3 Enter the user name assigned to you by your ISP in the Username field.
And enter the password assigned to you by your ISP in the Password field.
Re-enter your password in the Confirm Password field.
4 Select always connected, auto, or manual from the Connect type
drop-down menu. If you have a flat rate service charge for Internet
connection, select always connected. If your ISP charges you by the
minute, do not select this mode.
5 If you want your Router to automatically disconnect from the Internet
after a period of inactivity, specify a time in the Idle Time field. (Enter a
value of 0 to disable this timeout).
6 Enter the MTU value in the MTU field. Do not make changes to this
setting, unless your ISP specifically requires a different setting other than
1454.
7 IPCP is used by PPP protocol to get one IP address from the PPP server.
IPCP subnet function allows you to obtain a subnet (IP address and
netmask), rather than an IP address. Check this box to enable the
function.
8 IPCP Subnet Populate DHCP Server: enable this function to allow the
Router to automatically apply the subnet from IPCP subnet to DHCP
server. Then LAN clients can get the public IP address assigned by ISP,
rather than a private IP address of the local LAN.
9 Check the Add Default Route checkbox to set this PVC as the default
route, this is used when you configure more than one PVC for the Router.
10 Enter the VPI/VCI values. Or click Auto Search to find out the values. VPI
(Virtual Path Identifier) and VCI (Virtual Circuit Identifier) numbers should
be provided by your ISP.
11 Select the Encapsulation, VC MUX or LLC. This information should be
provided by your ISP.
Page 81

12 QoS Class: select CBR, UBR or VBR.
■ CBR (constant bit rate): the CBR service class is intended for
real-time applications, for example, those requiring tightly
constrained delay and delay variation, such as voice and video
applications. The consistent availability of a fixed quantity of
bandwidth is considered appropriate for CBR service.
■ VBR (variable bit rate): QoS class defined by the ATM Forum for
ATM networks. VBR is subdivided into a real time (RT) class and
non-real time (NRT) class. VBR (RT) is used for connections in which
there is a fixed timing relationship between samples. VBR (NRT) is
used for connections in which there is no fixed timing relationship
between samples, but that still need a guaranteed QoS. Compare
with ABR, CBR, and UBR.
■ UBR (unspecified bit rate): the UBR service class is intended for
delay-tolerant or non-real-time applications, for example, those
which do not require tightly constrained delay and delay variation,
such as traditional computer communications applications. The
UBR service may be considered as “best effort service”.
Internet Settings 79
13 PCR/SCR/MBS: PCR (Peak Cell Rate), SCR (Sustainable Cell Rate) and MBS
(Maximum Burst Size) are configurable.
14 Click Apply.
Page 82

80 CHAPTER 5: CONFIGURING THE ROUTER
PPPoA
PPP over ATM, this is a popular choice among European DSL providers. To
configure this function correctly, you should obtain the information from
your ISP.
Figure 62 PPPoA Settings Screen
1 Select PPPoA from the protocol drop-down menu.
2 IP assigned by ISP, if select Yes, then no need to enter the IP address and
Subnet mask information. If select No, then enter the IP address and
Subnet mask information.
3 Enter the user name assigned to you by your ISP in the Username field.
And enter the password assigned to you by your ISP in the Password field.
Re-enter your password in the Confirm Password field.
4 Select always connected, auto, or manual from the Connect type
drop-down menu. If you have a flat rate service charge for Internet
connection, select always connected. If your ISP charges you by the
minute, do not select this mode.
5 If you want your Router to automatically disconnect from the Internet
after a period of inactivity, specify a time in the Idle Time field. (Enter a
value of 0 to disable this timeout).
6 Enter the MTU value in the MTU field. Do not make changes to this
setting, unless your ISP specifically requires a different setting other than
1454.
Page 83

Internet Settings 81
7 IPCP is used by PPP protocol to get one IP address from the PPP server.
IPCP subnet function allows you to obtain a subnet (IP address and
netmask), rather than an IP address. Check this box to enable the
function.
8 IPCP Subnet Populate DHCP Server: enable this function to allow the
Router to automatically apply the subnet from IPCP subnet to DHCP
server. Then LAN clients can get the public IP address assigned by ISP,
rather than a private IP address of the local LAN.
9 Check the Add Default Route checkbox to set this PVC as the default
route, this is used when you configure more than one PVC for the Router.
10 Enter the VPI/VCI values. Or click Auto Search to find out the values. VPI
(Virtual Path Identifier) and VCI (Virtual Circuit Identifier) numbers should
be provided by your ISP.
11 Select the Encapsulation, VC MUX or LLC. This information should be
provided by your ISP.
12 QoS Class: select CBR, UBR or VBR.
■ CBR (constant bit rate): the CBR service class is intended for
real-time applications, for example, those requiring tightly
constrained delay and delay variation, such as voice and video
applications. The consistent availability of a fixed quantity of
bandwidth is considered appropriate for CBR service.
■ VBR (variable bit rate): QoS class defined by the ATM Forum for
ATM networks. VBR is subdivided into a real time (RT) class and
non-real time (NRT) class. VBR (RT) is used for connections in which
there is a fixed timing relationship between samples. VBR (NRT) is
used for connections in which there is no fixed timing relationship
between samples, but that still need a guaranteed QoS. Compare
with ABR, CBR, and UBR.
■ UBR (unspecified bit rate): the UBR service class is intended for
delay-tolerant or non-real-time applications, for example, those
which do not require tightly constrained delay and delay variation,
such as traditional computer communications applications. The
UBR service may be considered as “best effort service”.
13 PCR/SCR/MBS: PCR (Peak Cell Rate), SCR (Sustainable Cell Rate) and MBS
(Maximum Burst Size) are configurable.
14 Click Apply.
Page 84

82 CHAPTER 5: CONFIGURING THE ROUTER
Bridge Mode
If your ISP limits access to the Internet to specific computers, this means
that traffic to/from these computers only will be forwarded. In this case,
Bridge Mode is used to connect to the ISP. The ISP will generally give one
Internet account and limit only one computer to access the Internet.
Check with your ISP to determine if this mode is used for your Internet
connection.
Figure 63 Bridge Mode Screen
1 Select Bridge Mode from the Protocol drop-down menu.
2 Select VLAN.
3 Enter the VPI/VCI values. Or click Auto Search to find out the values. VPI
(Virtual Path Identifier) and VCI (Virtual Circuit Identifier) numbers should
be provided by your ISP.
4 Select the Encapsulation, VC MUX or LLC. This information should be
provided by your ISP.
5 QoS Class: select CBR, UBR or VBR.
■ CBR (constant bit rate): the CBR service class is intended for
real-time applications, for example, those requiring tightly
constrained delay and delay variation, such as voice and video
applications. The consistent availability of a fixed quantity of
bandwidth is considered appropriate for CBR service.
Page 85

Internet Settings 83
■ VBR (variable bit rate): QoS class defined by the ATM Forum for
ATM networks. VBR is subdivided into a real time (RT) class and
non-real time (NRT) class. VBR (RT) is used for connections in which
there is a fixed timing relationship between samples. VBR (NRT) is
used for connections in which there is no fixed timing relationship
between samples, but that still need a guaranteed QoS. Compare
with ABR, CBR, and UBR.
■ UBR (unspecified bit rate): the UBR service class is intended for
delay-tolerant or non-real-time applications, for example, those
which do not require tightly constrained delay and delay variation,
such as traditional computer communications applications. The
UBR service may be considered as “best effort service”.
6 PCR/SCR/MBS: PCR (Peak Cell Rate), SCR (Sustainable Cell Rate) and MBS
(Maximum Burst Size) are configurable.
7 Click Apply.
Page 86

84 CHAPTER 5: CONFIGURING THE ROUTER
Routing Mode over ATM
RFC1483/2684 routed encapsulation in routing mode, it carries IP
datagrams directly over ATM. DHCP client function can also be enabled
to obtain an IP address dynamically.
Figure 64 Routing Mode over ATM Screen
1 Select Routing mode over ATM from the protocol drop-down menu.
2 Enter IP address, Subnet mask, and Default gateway information.
3 If your ISP provides DNS information, check the DNS Automatic from ISP
box.
4 If the ISP requires you to input a Host Name, enter it in the Host Name
field.
5 If your ISP uses DHCP to automatically assign IP addresses, check the
DHCP Client checkbox.
6 Check the Add Default Route checkbox to set this PVC as the default
route, this is used when you configure more than one PVC for the Router.
7 Enter the VPI/VCI values. Or click Auto Search to find out the values.
8 Select the Encapsulation, VC MUX or LLC. This information should be
provided by your ISP.
Page 87

Internet Settings 85
9 QoS Class: select CBR, UBR or VBR.
■ CBR (constant bit rate): the CBR service class is intended for
real-time applications, for example, those requiring tightly
constrained delay and delay variation, such as voice and video
applications. The consistent availability of a fixed quantity of
bandwidth is considered appropriate for CBR service.
■ VBR (variable bit rate): QoS class defined by the ATM Forum for
ATM networks. VBR is subdivided into a real time (RT) class and
non-real time (NRT) class. VBR (RT) is used for connections in which
there is a fixed timing relationship between samples. VBR (NRT) is
used for connections in which there is no fixed timing relationship
between samples, but that still need a guaranteed QoS. Compare
with ABR, CBR, and UBR.
■ UBR (unspecified bit rate): the UBR service class is intended for
delay-tolerant or non-real-time applications, for example, those
which do not require tightly constrained delay and delay variation,
such as traditional computer communications applications. The
UBR service may be considered as “best effort service”.
10 PCR/SCR/MBS: PCR (Peak Cell Rate), SCR (Sustainable Cell Rate) and MBS
(Maximum Burst Size) are configurable.
11 Click Apply.
Page 88

86 CHAPTER 5: CONFIGURING THE ROUTER
Dynamic/Fixed IP in 1483 Bridge Mode
Dynamic/Fixed IP in 1483 Bridge Mode uses the same encapsulation as
1483 Bridging but with bridging function disabled. DHCP client function
can also be enabled to obtain an IP address dynamically.
Figure 65 Dynamic/Fixed IP in 1483 Bridge Mode Screen
1 Select Dynamic/Fixed IP in 1483 Bridge Mode from the protocol drop-down
menu.
2 Enter your IP address, subnet mask, and default gateway information.
3 IPoEoA NAT IP - enter the IP address in this field.
IPoE over AAL5 (IPoEoA) adopts a three-layer architecture, with IP
encapsulation at the uppermost layer, IP over Ethernet (IPoE) in the
middle, and IPoEoA at the bottom. When a device is connected to a
remote access server at high speed to access an external network, PVC
over ATM is used because of the long distance. In this case, it is required
for the ATM port of the server to carry Ethernet packets, which is known
as IPoEoA. In the application of IPoEoA, one virtual Ethernet (VE) interface
can be associated with multiple PVCs. PVCs associated with the same VE
interface are interconnected at layer 2.
4 If your ISP provides DNS information, check the DNS Automatic from ISP
box.
5 If the ISP requires you to input a Host Name, enter it in the Host Name
field.
Page 89

Internet Settings 87
6 If your ISP uses DHCP to automatically assign IP addresses, check the
DHCP Client checkbox.
7 Check the Add Default Route checkbox to set this PVC as the default
route, this is used when you configure more than one PVC for the Router.
8 Enter the VPI/VCI values. Or you can click Auto Search to automatically
find out this information.
9 Select the Encapsulation, VC MUX or LLC. This information should be
provided to you by your ISP.
10 QoS Class: select CBR, UBR or VBR.
■ CBR (constant bit rate): the CBR service class is intended for
real-time applications, for example, those requiring tightly
constrained delay and delay variation, such as voice and video
applications. The consistent availability of a fixed quantity of
bandwidth is considered appropriate for CBR service.
■ VBR (variable bit rate): QoS class defined by the ATM Forum for
ATM networks. VBR is subdivided into a real time (RT) class and
non-real time (NRT) class. VBR (RT) is used for connections in which
there is a fixed timing relationship between samples. VBR (NRT) is
used for connections in which there is no fixed timing relationship
between samples, but that still need a guaranteed QoS. Compare
with ABR, CBR, and UBR.
■ UBR (unspecified bit rate): the UBR service class is intended for
delay-tolerant or non-real-time applications, for example, those
which do not require tightly constrained delay and delay variation,
such as traditional computer communications applications. The
UBR service may be considered as “best effort service”.
11 PCR/SCR/MBS: PCR (Peak Cell Rate), SCR (Sustainable Cell Rate) and MBS
(Maximum Burst Size) are configurable.
12 Click Apply.
Page 90

88 CHAPTER 5: CONFIGURING THE ROUTER
DNS Domain Name Service (or Server) is an Internet service that translates
domain names into IP addresses. Because domain names are alphabetic,
they're easier to remember. The Internet however, is really based on IP
addresses. Every time you use a domain name, a DNS service must
translate the name into the corresponding IP address. For example, the
domain name www.example.com might translate to 198.105.232.14.
Figure 66 DNS Screen
If the DNS information is automatically provided by your ISP every time
you connect to it, check the Automatic from ISP checkbox (this is the
default setting).
If your ISP provided you with specific DNS addresses to use, enter them
into the appropriate fields on the screen and click Apply.
Many ISPs do not require you to enter this information into the Router. If
you are using a static IP connection type, you may need to enter a specific
DNS address and secondary DNS address for your connection to work
properly. If your connection type is dynamic or PPPoE, it is likely that you
do not have to enter a DNS address.
Page 91

Internet Settings 89
Clone MAC address To configure the hostname and Clone MAC Address information for your
Router, select Internet Settings, then go to the Clone MAC address tab.
The Hostname and MAC Address screen displays.
Figure 67 Hostname and Clone MAC Address Screen
1 Some ISPs require a host name. If your ISP has this requirement, enter the
host name in the Host Name field.
2 Three different ways to configure the WAN MAC Address:
■ If your ISP requires an assigned MAC address, enter the values in the
WAN MAC address field.
or
■ If the computer that you are using is the one that was previously
connected directly to the cable modem, click Clone.
or
■ To reset the MAC Address to the default, click Reset MAC.
3 Click Apply to save the settings.
Page 92

90 CHAPTER 5: CONFIGURING THE ROUTER
Firewall This section is for configuration settings of the Router’s firewall function.
Your Router is equipped with a firewall that will protect your network
from a wide array of common hacker attacks including Ping of Death
(PoD) and Denial of Service (DoS) attacks. You can turn the firewall
function off if needed. Turning off the firewall protection will not leave
your network completely vulnerable to hacker attacks, but 3Com
recommends that you leave the firewall enabled whenever possible.
SPI Stateful Packet Inspection (SPI) - The Intrusion Detection Feature of the
Router limits access for incoming traffic at the WAN port.
This feature is called a "stateful" packet inspection, because it examines
the contents of the packet to determine the state of the communications;
i.e., it ensures that the stated destination computer has previously
requested the current communication. This is a way of ensuring that all
communications are initiated by the recipient computer and are taking
place only with sources that are known and trusted from previous
interactions. In addition to being more rigorous in their inspection of
packets, stateful inspection firewalls also close off ports until connection
to the specific port is requested.
Figure 68 Firewall Screen
Page 93

Firewall 91
To enable the firewall function:
1 Select the level of protection (High, Medium, or Low) that you desire from
the Firewall level drop-down menu.
2 Click Apply.
■ For low and medium levels of firewall protection, refer to Figure 69.
For low level of firewall protection, the DoS and SPI functions are both
off. For medium level of firewall protection, DoS is on, but SPI is off.
■ For high level of firewall protection, refer to Figure 70. Both DoS and
SPI are on for this level of firewall protection. The higher the firewall
level is, the safer that your network is.
Figure 69 Low and Medium Level Firewall Protection Screen
When abnormal network activity occurs, an alerting email will be sent out
to you. Enter the following information to receive the email:
■ Your E-mail Address
■ SMTP Server Address
■ User name
■ Password
Page 94

92 CHAPTER 5: CONFIGURING THE ROUTER
Figure 70 High Level Firewall Protection Screen
If you select high level of protection, you would have an option to
configure additional parameters for the firewall.
■ Fragmentation half-open wait - Configures the number of seconds
that a packet state structure remains active. When the timeout value
expires, the Router drops the un-assembled packet, freeing that
structure for use by another packet.
■ TCP SYN wait - Defines how long the software will wait for a TCP
session to synchronize before dropping the session.
■ TCP FIN wait - Specifies how long a TCP session will be maintained
after the firewall detects a FIN packet.
■ TCP connection idle timeout - The length of time for which a TCP
session will be managed if there is no activity.
■ UDP session idle timeout - The length of time for which a UDP session
will be managed if there is no activity.
■ H.323 data channel idle timeout - The length of time for which an
H.323 session will be managed if there is no activity.
Page 95

Firewall 93
■ Total incomplete TCP/UDP sessions HIGH - Defines the rate of new
unestablished sessions that will cause the software to start deleting
half-open sessions.
■ Total incomplete TCP/UDP sessions LOW - Defines the rate of new
unestablished sessions that will cause the software to stop deleting
half-open sessions.
■ Incomplete TCP/UDP sessions (per min) HIGH - Maximum number of
allowed incomplete TCP/UDP sessions per minute.
■ Incomplete TCP/UDP sessions (per min) LOW - Minimum number of
allowed incomplete TCP/UDP sessions per minute.
■ Maximum incomplete TCP/UDP sessions number from same host -
Maximum number of incomplete TCP/UDP sessions from the same
host.
■ Incomplete TCP/UDP sessions detect sensitive time period - Length of
time before an incomplete TCP/UDP session is detected as incomplete.
■ Maximum half-open fragmentation packet number from same host -
Maximum number of half-open fragmentation packets from the same
host.
■ Half-open fragmentation detect sensitive time period - Length of time
before a half-open fragmentation session is detected as half-open.
■ Flooding cracker block time - Length of time from detecting a flood
attack to blocking the attack.
Page 96

94 CHAPTER 5: CONFIGURING THE ROUTER
Special Applications Special Applications (port triggering) let you choose specific ports to be
open for specific applications to work properly with the Network Address
Translation (NAT) feature of the Router.
Figure 71 Special Applications Screen
A list of popular applications has been included to choose from. Select
the application from the Popular Applications drop-down menu. Then
select the row that you want to copy the settings to from the Copy To
drop-down menu, and click Copy To. The settings will be transferred to
the row that you specified. Click Apply to save the setting for that
application.
If your application is not listed, you will need to check with the
application vendor to determine which ports need to be configured. You
can manually enter the port information into the Router. To manually
enter the port information:
1 Specify the trigger port (the one used by the application when it is
initialized) in the Trigger Port column, and specify whether the trigger is
TCP or UDP.
2 Specify the Public Ports used by the application, that will need to be
opened up in the firewall for the application to work properly. Also
specify whether these ports are TCP or UDP. Note that the range of the
trigger port is from 1 to 65535. You can enter the port number as one
single port, or in range, use comma to separate different entries.
3 Check the Enabled checkbox, then click Apply.
Page 97

Firewall 95
Virtual Servers The Virtual servers feature allows you to route external (Internet) calls for
services such as a web server (port 80), FTP server (Port 21), or other
applications through your Router to your internal network. Since your
internal computers are protected by a firewall, machines from the
Internet cannot get to them because they cannot be 'seen'.
If you need to configure the Virtual Server function for a specific
application, you will need to contact the application vendor to find out
which port settings you need.
The maximum number of virtual servers that can be configured is 20.
Figure 72 Virtual Servers Screen
A list of popular servers has been included to choose from. Select the
server from the Popular servers drop-down menu. Then click Add, your
selection will be added to the table.
If the server that you want to use is not listed in the drop-down menu,
you can manually add the virtual server to the table. To manually
configure your virtual servers:
1 Enter the IP address, and the description in the spaces provided for the
internal machine.
2 Select the protocol type (TCP, UDP, or both TCP and UDP) from the
drop-down menu.
Page 98

96 CHAPTER 5: CONFIGURING THE ROUTER
3 Specify the public port that will be seen by clients on the Internet, and the
LAN port which the traffic will be routed to.
4 You can enable or disable each Virtual Server entry by checking or
unchecking the appropriate Enabled checkbox.
5 Click Apply to save the changes for each Virtual Server entry.
DMZ If you have a client PC that cannot run an Internet application properly
from behind the firewall, you can open the client up to unrestricted
two-way Internet access. This may be necessary if the NAT feature is
causing problems with an application such as a game or video
conferencing application.
Figure 73 DMZ Screen
Use this feature on a temporary basis. The computer in the DMZ is not
protected from hacker attacks.
Check the Enable DMZ box, the IP Address of Virtual DMZ Host will
appear.
1 Enter the last digits of the LAN IP address in the Client PC IP Address field.
Enter the IP address (if known) that will be accessing the DMZ PC into the
Public IP Address field, so that only the computer on the Internet at this
address can access the DMZ PC without firewall protection. If the IP
Page 99

Firewall 97
address is not known, or if more than one PC on the Internet will need to
access the DMZ PC, then set the Public IP Address to 0.0.0.0.
In the default setting, (line 1) refer to Figure 73, Public IP address is set to
0.0.0.0 and it is automatically transformed by default WAN IP. We only
allow one DMZ server to be accessed by public IPs (Many to 1 NAT). If you
have more than one DMZ server, you have to set a second WAN IP in line
2 and define which IP address of DMZ server you would like to set in the
Client PC IP address. For this Router, only 1 to 1 NAT function is allowed.
2 Click Apply.
PC Privileges The Router can be configured to restrict access to the Internet, email or
other network services at specific days and times. Restriction can be set
for a single computer, a range of computers, or multiple computers.
You can define the traffic type permitted or not-permitted to the Internet.
Note that this function requires time-scheduling to be applied to access
control, you will need to create schedule rules first and then use PC
Privileges.
Figure 74 PC Privileges Screen
1 Select one option from filtering function:
■ All PCs have access to the Internet: selecting this mode means that all
clients have full access to Internet.
■ PCs access authorised services only: selecting this mode means clients
can only access authorised or limited services.
2 Click Add PC (refer to Figure 75).
Page 100

98 CHAPTER 5: CONFIGURING THE ROUTER
To edit or delete specific existing filtering rules, click on Edit or Delete for
the appropriate filtering rule.
Figure 75 PC Privileges Add PC Screen
1 Enter a description in the Client PC Description field, and the IP address or
IP address range into the Client PC IP Address fields.
2 To bypass the URL Filter, check the corresponding Bypass checkbox. If you
check this option, then the Web sites and keywords defined in this screen
will not be filtered out.
3 Select the services to be blocked. A list of popular services is listed on this
screen, to block a particular service, check the appropriate Blocking
checkbox.
If the service to be restricted is not listed here, you can enter a custom
range of ports at the bottom of the screen, under User Defined Blocked
Ports.
4 If you want the restriction to apply only at certain times, select the
schedule rule to apply from the Schedule Rule drop-down menu.
Note that schedule rules are defined on the Schedule Rules screen
(see page 99).
5 Click Apply to add the settings.
 Loading...
Loading...