Chapter 18 Product Specifications
Table 69 Voice Features
Firmware update
enable / disable
Call waiting This feature allows you to hear an alert when you are already using
Call forwarding With this feature, you can set the WiMAX Modem to forward calls to a
Caller ID The WiMAX Modem supports caller ID, which allows you to see the
REN A Ringer Equivalence Number (REN) is used to determine the number
QoS (Quality of
Service)
SIP ALG Your device is a SIP Application Layer Gateway (ALG). It allows VoIP
Other Voice
Features
If your service provider uses this feature, you hear a recorded
message when you pick up the phone when new firmware is available
for your W iMAX Modem. Enter *99# in your phone’s keypad to have
the WiMAX Modem upgrade the firmware, or enter #99# to not
upgrade. If your service provider gave you different numbers to use,
enter them instead. If you enter the code to not upgrade, you can
make a call as normal. You will hear the recording again each time
you pick up the phone, until you upgrade.
the phone and another person calls you. You can then either reject
the new incoming call, put your current call on hold and receive the
new incoming call, or end the current call and receive the new
incoming call.
specified number, either unconditionally (alw ays), when your number
is busy, or when you do not answer. You can also forward incoming
calls from one specified number to another.
originating number of an incoming call (on a phone with a suitable
display).
of devices (like telephones or fax machines) that may be connected
to the telephone line. Your device has a REN of three, so it can
support three devices per telephone port.
Quality of Service (QoS) mechanisms help to provide better service
on a per-flow basis. Your device supports Type of Service (ToS)
tagging and Differentiated Services (DiffServ) tagging. This allows
the device to tag voice frames so they can be prioritized over the
network.
calls to pass through NAT for devices behind it (such as a SIP-based
VoIP software application on a computer).
SIP version 2 (Session Initiating Protocol RFC 3261)
SDP (Session Description Protocol RFC 2327)
182
RTP (RFC 1889)
RTCP (RFC 1890)
Voice codecs (coder/decoders) G.711, G.726, G.729
Fax and data modem discrimination
DTMF Detection and Generation
DTMF: In-band and Out-band traffic (RFC 2833),(PCM), (SIP INFO)
Point-to-point call establishment between two IADs
Quick dialing through predefined phone book, which maps the phone
dialing number and destination URL.
Flexible Dial Plan (RFC3525 section 7.1.14)
User’s Guide
Chapter 18 Product Specifications
Table 70 Star (*) and Pound (#) Code Support
*0 Wireless Operator Services
*2 Customer Care Access
*66 Repeat Dialing
*67 Plus the 10 digit phone number to block Caller ID on a single call
basis
*69 Return last call received
*70 Followed by the 10 digit phone number to cancel Call Waiting on a
single call basis
*72 Activate Call Forwarding (*72 followed by the 10 digit phone number
that is requesting call forwarding service)
*720 Activate Call Forwarding (*720 followed by the 10 digit phone number
that is requesting deactivation of call forwarding service)
*73 Plus the forward to phone number to activate Call Forwarding No
Answer (no VM service plan)
*730 Deactivate Call Forwarding No Answer
*740 Plus the forward to phone number to activate Call Forwarding Busy
(no VM service plan)
*911/911 Emergency phone number (same as dialing 911)
*411/411 Wireless Information Services
Note: To take full advantage of the supplementary phone services available through
the WiMAX Modem's phone port, you may need to subscribe to the services
from your voice account service provider.
Not all features are supported by all service providers. Consult your service
provider for more information.
User’s Guide
183

Chapter 18 Product Specifications
184
User’s Guide
PART VII
Appendices and
Index
WiMAX Security (187)
Setting Up Your Computer’s IP Address
(191)
Pop-up Windows, JavaScripts and Java
Permissions (219)
IP Addresses and Subnetting (229)
Importing Certificates (241)
SIP Passthrough (273)
Common Services (275)
Legal Information (279)
Customer Support (313)
185

186

APPENDIX A
WiMAX Security
Wireless security is vital to protect your wireless communications. Without it,
information transmitted over the wireless network would be accessible to any
networking device within range.
User Authentication and Data Encryption
The WiMAX (IEEE 802.16) standard employs user authentication and encryption to
ensure secured communication at all times.
User authentication is the process of confirming a user’s identity and level of
authorization. Data encryption is the process of encoding information so that it
cannot be read by anyone who does not know the code.
PKMv2
WiMAX uses PKMv2 (Privacy Key Management version 2) for authentication, and
CCMP (Counter Mode with Cipher Block Chaining Message Authentication Protocol)
for data encryption.
WiMAX supports EAP (Extensible Authentication Protocol, RFC 2486) which allows
additional authentication methods to be deployed with no changes to the base
station or the mobile or subscriber stations.
PKMv2 is a procedure that allows authentication of a mobile or subscriber station
and negotiation of a public key to encryp t tr affic between t he MS/SS and the base
station. PKMv2 uses standard EAP methods such as Transport Layer Security
(EAP-TLS) or Tunneled TLS (EAP-TTLS) for secure communication.
In cryptography, a ‘key’ is a piece of information, typically a string of random
numbers and letters, that can be used to ‘lock’ (encrypt) or ‘unlock’ (decrypt) a
message. Public key encryption uses key pairs, which consist of a public (freely
available) key and a priv ate (secret) key. The public key is used for encryption and
the private key is used for decryption. Y ou can decrypt a message only if you have
the private key. Public key certificates (or ‘digital IDs’) allow users to verify each
other’s identity.
User’s Guide
187

Appendix A WiMAX Security
RADIUS
RADIUS is based on a client-server model that supports authentication,
authorization and accounting. The base station is the client and the server is the
RADIUS server. The RADIUS server handles the following tasks:
• Authentication
Determines the identity of the users.
• Authorization
Determines the network services available to authenticated users once they are
connected to the network.
•Accounting
Keeps track of the client’s network activity.
RADIUS is a simple package exchange in which your base station acts as a
message relay between the MS/SS and the network RADIUS server.
Types of RADIUS Messages
The following types of RADIUS messages are exchanged between the base station
and the RADIUS server for user authentication:
• Access-Request
Sent by an base station requesting authentication.
• Access-Reject
Sent by a RADIUS server rejecting access.
• Access-Accept
Sent by a RADIUS server allowing access.
• Access-Challenge
Sent by a RADIUS server requesting more information in order to allow access.
The base station sends a proper response from the user and then sends another
Access-Request message.
The following types of RADIUS messages are exchanged between the base station
and the RADIUS server for user accounting:
•Accounting-Request
188
Sent by the base station requesting accounting.
• Accounting-Response
Sent by the RADIUS server to indicate that it has started or stopped accounting.
In order to ensure network security , the access point and the RA DIUS server use a
shared secret key, which is a password they both know. The key is not sent over
User’s Guide

the network. In addition to the shared key, password information exchanged is
also encrypted to protect the network from unauthorized access.
Diameter
Diameter (RFC 3588) is a type of AAA server that provides several improvements
over RADIUS in efficiency, security, and support for roaming.
Security Association
The set of information about user authentication and data encryption between two
computers is known as a security association (SA). In a WiMAX network, the
process of security association has three stages.
• Authorization request and reply
The MS/SS presents its public certificate to the base station. The base station
verifies the certificate and sends an authentication key (AK) to the MS/SS.
Appendix A WiMAX Security
CCMP
• Key request and reply
The MS/SS requests a transport encryption key (TEK) which the base station
generates and encrypts using the authentication key.
• Encrypted traffic
The MS/SS decrypts the TEK (using the authentication key). Both stations can
now securely encrypt and decrypt the data flow.
All traffic in a WiMAX network is encrypted using CCMP (Counter Mode with Cipher
Block Chaining Message Authentication Protocol). CCMP is based on the 128-bit
Advanced Encryption Standard (AES) algorithm.
‘Counter mode’ refers to the encryption of each block of plain text with an
arbitrary number, known as the counter. This number changes each time a block
of plain text is encrypted. Counter mode avoids the security weakness of repeated
identical blocks of encrypted text that makes encrypted data vulnerable to
pattern-spotting.
‘Cipher Block Chaining Message Authentication’ (also known as CBC -MAC) ensures
message integrity by encrypting each block of plain text in such a way that its
encryption is dependent on the block before it. This series of ‘chained’ blocks
creates a message authentication code (MAC or CMAC) that ensures the encrypted
data has not been tampered with.
User’s Guide
189

Appendix A WiMAX Security
Authentication
The WiMAX Modem supports EAP-TTLS authentication.
EAP-TTLS (Tunneled Transport Layer Service)
EAP-TTLS is an extension of the EAP-TLS authentication that uses certificates for
only the server-side authentications to establish a secure connection (with EAPTLS digital certifications are needed by both the server and the wireless clients for
mutual authentication). Client authentication is then done by sending username
and password through the secure connection, thus client identity is protected. For
client authentication, EAP-TTLS supports EAP methods and legacy authentication
methods such as PAP, CHAP, MS-CHAP and MS-CHAP v2.
190
User’s Guide

APPENDIX B
Setting Up Your Computer’s IP
Address
Note: Your specific ZyXEL device may not support all of the operating systems
described in this appendix. See the product specifications for more information
about which operating systems are supported.
This appendix shows you how to configure the IP settings on your computer in
order for it to be able to communicate with the other devices on your network.
Windows Vista/XP/2000, Mac OS 9/OS X, and all versions of UNIX/LINUX include
the software components you need to use TCP/IP on your computer.
If you manually assign IP information instead of using a dynamic IP, make sure
that your network’s computers have IP addresses that place them in the same
subnet.
In this appendix, you can set up an IP address for:
• Windows XP/NT/2000 on page 192
• Windows Vista on page 195
• Mac OS X: 10.3 and 10.4 on page 199
• Mac OS X: 10.5 on page 203
• Linux: Ubuntu 8 (GNOME) on page 206
• Linux: openSUSE 10.3 (KDE) on page 212
User’s Guide
191
Appendix B Setting Up Your Computer’s IP Address
Windows XP/NT/2000
The following example uses the default Windows XP display theme but can also
apply to Windows 2000 and Windows NT.
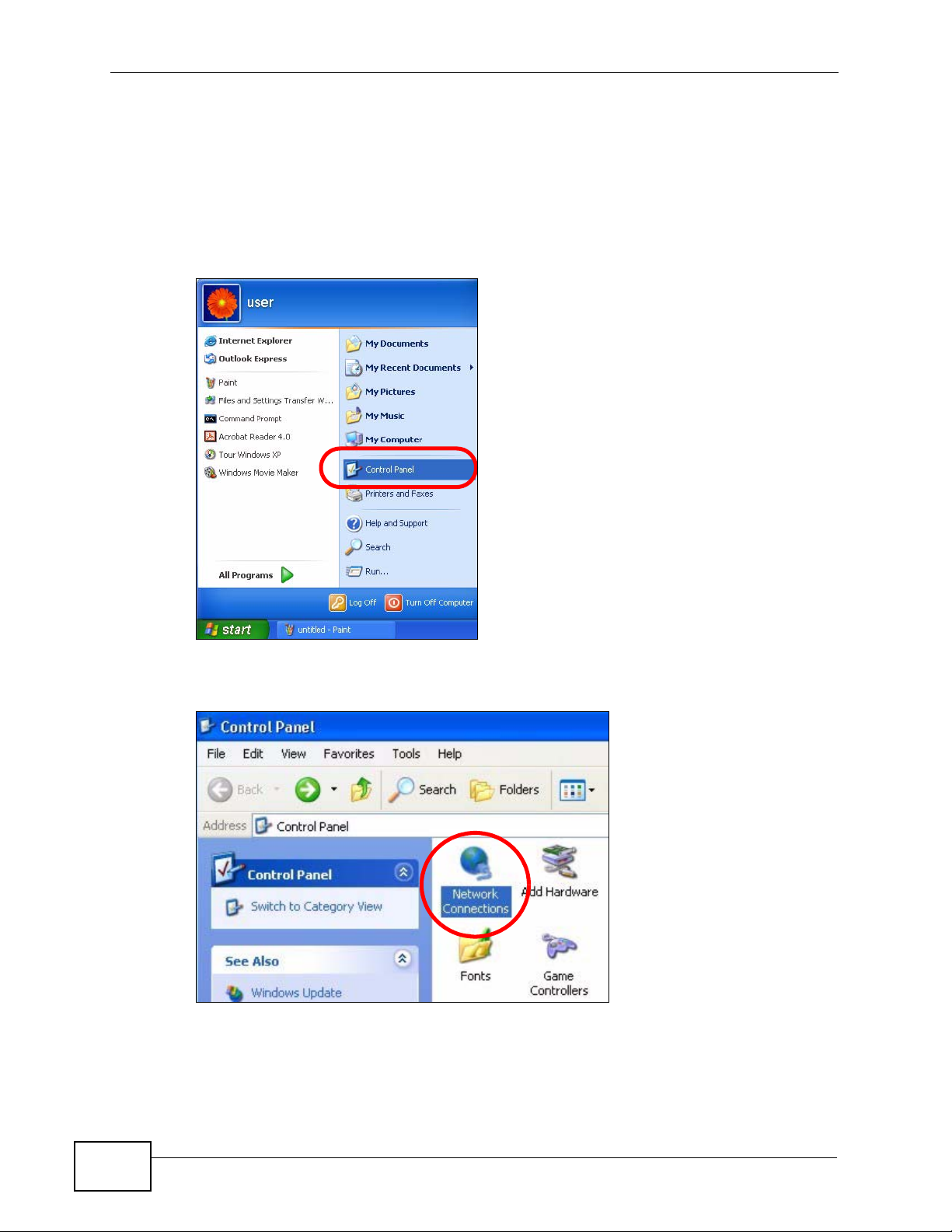
1 Click Start > Control Panel.
Figure 70 Windows XP: Start Menu
2 In the Control Panel, click the Network Connections icon.
Figure 71 Windows XP: Control Panel
192
User’s Guide
Appendix B Setting Up Your Computer’s IP Address
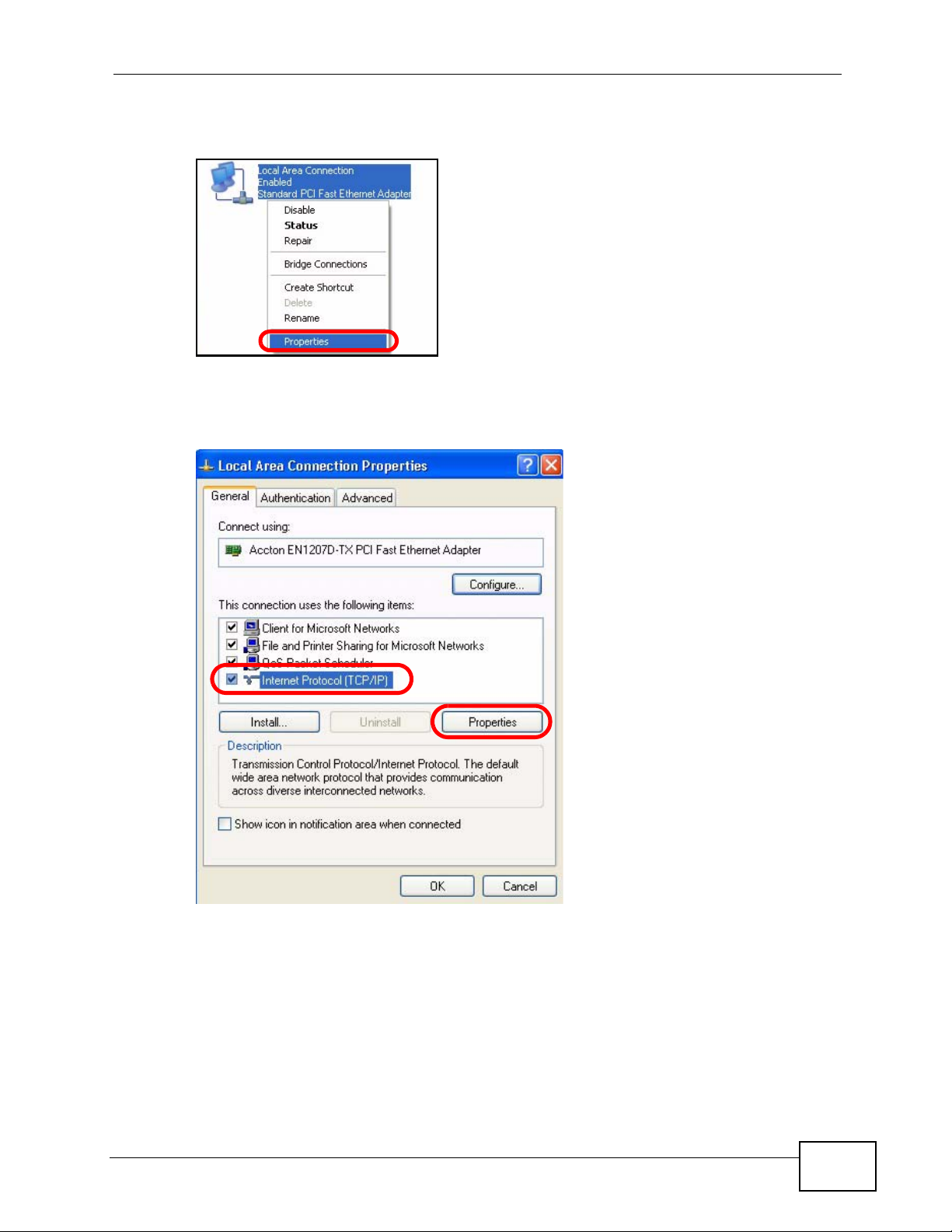
3 Right-click Local Area Connection and then select Properties.
Figure 72 Windows XP: Control Panel > Network Connections > Properties
4 On the General tab, select Internet Protocol (TCP/IP) and then click
Properties.
Figure 73 Windows XP: Local Area Connection Properties
User’s Guide
193

Appendix B Setting Up Your Computer’s IP Address
5 The Internet Protocol TCP/IP Properties window opens.
Figure 74 Windows XP: Internet Protocol (TCP/IP) Properties
6 Select Obtain an IP addr ess automatically if your network administr ator or ISP
assigns your IP address dynamically.
Select Use the following IP Address and fill in the IP address, Subnet mask,
and Default gateway fields if you have a static IP address that was assigned to
you by your network administrator or ISP. You may also have to enter a Preferred
DNS server and an Alternate DNS server, if that information was provided.
7 Click OK to close the Internet Protocol (TCP/IP) Properties window.
Click OK to close the Local Area Connection Properties window.Verifying Settings
1 Click Start > All Programs > Accessories > Command Prompt.
2 In the Command Prompt window, type "ipconfig" and then press [ENTER].
You can also go to Start > Control Panel > Network Connections, right-click a
network connection, click Status and then click the Support tab to view your IP
address and connection information.
194
User’s Guide
Windows Vista
This section shows screens from Windows Vista Professional.
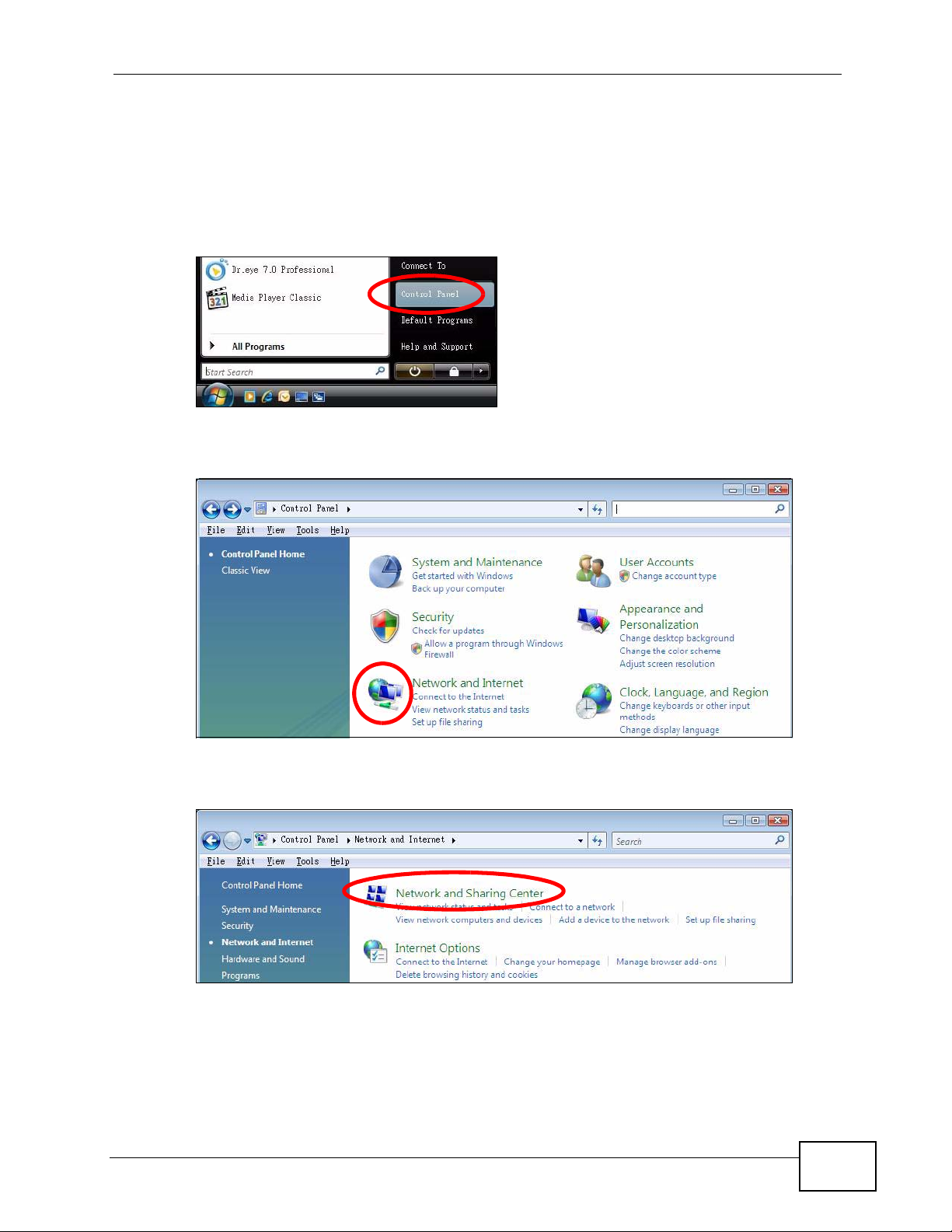
1 Click Start > Control Panel.
Figure 75 Windows Vista: Start Menu
2 In the Control Panel, click the Network and Internet icon.
Figure 76 Windows Vista: Control Panel
Appendix B Setting Up Your Computer’s IP Address
3 Click the Network and Sharing Center icon.
User’s Guide
Figure 77 Windows Vista: Network And Internet
195
Appendix B Setting Up Your Computer’s IP Address
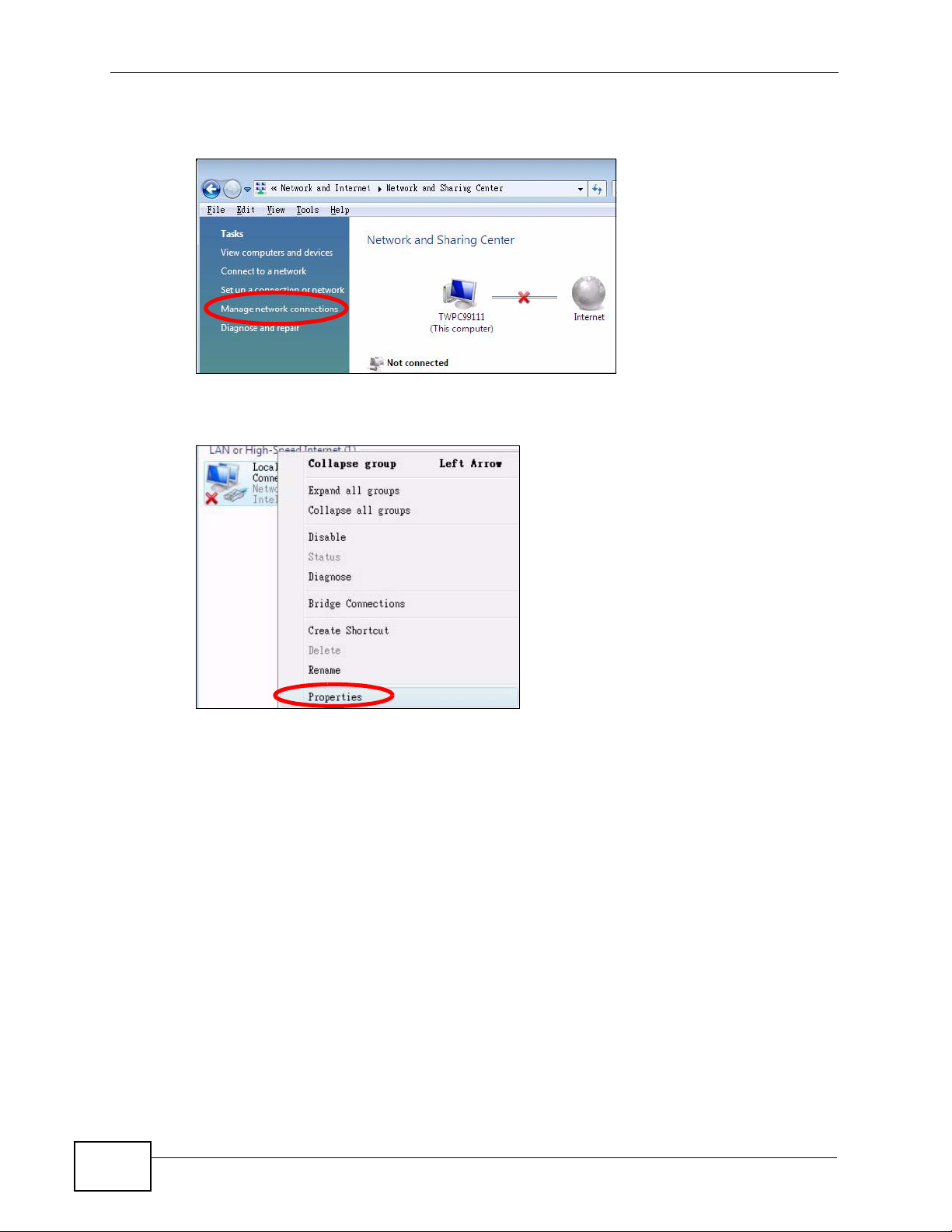
4 Click Manage network connections.
Figure 78 Windows Vista: Network and Sharing Center
5 Right-click Local Area Connection and then select Properties.
Figure 79 Windows Vista: Network and Sharing Center
196
Note: During this procedure, click Continue whenever Windows displays a screen
saying that it needs your permission to continue.
User’s Guide
 Loading...
Loading...