Page 1
Default Login Details
LAN IP Address
http://192.168.1.254
User Name
admin
Password
see wireless key on the
back label
eircom D1000 modem
Wireless N ADSL2+ 4-port Gateway
Version 3.00
Edition 2, 9/2014
User’s Guide
Page 2

Copyright © 2013 ZyXEL Communications Corporation
Page 3

Page 4

2
DSL-100HNU-T1 v3 User’s Guide
IMPORTANT!
READ CAREFULLY BEFORE USE.
KEEP THIS GUIDE FOR FUTURE REFERENCE.
Screenshots and graphics in this book may differ slightly from your product due to differences in
your product firmware or your computer operating system. Every effort has been made to ensure
that the information in this manual is accurate.
Page 5

3
eircom D1000 modem User’s Guide
Table of Contents
Part I: User’s
Introduction
1.1 Overview ...........................................................................................................................................13
1.2 Ways to Manage the Device .............................................................................................................13
1.3 Good Habits for Managing the Device ..............................................................................................13
1.4 Applications for the Device ................................................................................................................13
1.4.1 Internet Access ........................................................................................................................14
1.4.2 Wireless Access ......................................................................................................................14
1.4.3 Using the WPS/WLAN Button .................................................................................................15
1.5 The RESET Button ............................................................................................................................15
1.5.1 Using the Reset Button ............................................................................................................15
Introducing the Web Configurator .................................................................................................... 17
2.1 Overview ...........................................................................................................................................17
2.1.1 Accessing the Web Configurator .............................................................................................17
2.2 The Web Configurator Layout ...........................................................................................................20
2.2.1 Title Bar ...................................................................................................................................20
2.2.2 Main Window ...........................................................................................................................20
2.2.3 Navigation Panel .....................................................................................................................21
Part II: Technical
The System Info
3.1 Overview ...........................................................................................................................................27
3.2 The System Info Screen ....................................................................................................................27
3.3 The LAN Device Screen ....................................................................................................................29
Broadband
........................................................................................................................................... 31
4.1 Overview ...........................................................................................................................................31
4.1.1 What You Can Do in the WAN Screens ...................................................................................31
4.1.2 What You Need to Know About WAN ......................................................................................31
4.1.3 Before You Begin .....................................................................................................................32
4.2 The Internet Connection Screen .......................................................................................................32
4.3 The More Connections Screen .........................................................................................................36
4.3.1 More Connections Edit ............................................................................................................37
4.4 The 3G Backup Screen .....................................................................................................................40
Guide ....................................................................................................
......................................................................................................................................... 13
Reference .....................................................................................
Screen
..................................................................................................................... 27
25
11
Page 6

4
eircom D1000 modem User’s Guide
Wireless
Home
4.5 WAN Technical Reference ................................................................................................................42
4.5.1 Encapsulation ..........................................................................................................................42
4.5.2 Multiplexing ..............................................................................................................................43
4.5.3 VPI and VCI .............................................................................................................................44
4.5.4 IP Address Assignment ...........................................................................................................44
4.5.5 Nailed-Up Connection (PPP) ...................................................................................................44
4.5.6 NAT ..........................................................................................................................................45
4.6 Traffic Shaping ..................................................................................................................................45
4.6.1 ATM Traffic Classes .................................................................................................................45
LAN
....................................................................................................................................... 47
5.1 Overview ...........................................................................................................................................47
5.1.1 What You Can Do in the Wireless LAN Screens .....................................................................47
5.1.2 What You Need to Know About Wireless ................................................................................48
5.1.3 Before You Start .......................................................................................................................48
5.2 The General Screen ..........................................................................................................................48
5.2.1 No Security ..............................................................................................................................50
5.2.2 Basic (WEP Encryption) ..........................................................................................................50
5.2.3 More Secure (WPA(2)-PSK) ....................................................................................................51
5.2.4 WPA(2) Authentication .............................................................................................................52
5.3 The More AP Screen .........................................................................................................................54
5.3.1 More AP Edit ...........................................................................................................................54
5.4 The MAC Authentication Screen .......................................................................................................56
5.5 The WPS Screen ..............................................................................................................................57
5.6 The WDS Screen ..............................................................................................................................59
5.7 The WMM Screen .............................................................................................................................60
5.8 The Scheduling Screen .....................................................................................................................60
5.9 The Advanced Screen .......................................................................................................................61
5.10 Wireless LAN Technical Reference .................................................................................................63
5.10.1 Wireless Network Overview ...................................................................................................63
5.10.2 Additional Wireless Terms .....................................................................................................64
5.10.3 Wireless Security Overview ...................................................................................................64
5.10.4 Signal Problems ....................................................................................................................67
5.10.5 BSS .......................................................................................................................................67
5.10.6 MBSSID .................................................................................................................................68
5.10.7 Wireless Distribution System (WDS) .....................................................................................68
5.10.8 WiFi Protected Setup (WPS) .................................................................................................68
Networking ...............................................................................................................................
6.1 Overview ...........................................................................................................................................77
6.1.1 What You Can Do in the LAN Screens ....................................................................................77
6.1.2 What You Need To Know .........................................................................................................78
6.1.3 Before You Begin .....................................................................................................................79
6.2 The LAN Setup Screen .....................................................................................................................79
77
Page 7

5
eircom D1000 modem User’s Guide
6.3 The Static DHCP Screen ...................................................................................................................81
6.4 The IP Alias Screen ..........................................................................................................................83
6.4.1 Configuring the LAN IP Alias Screen .......................................................................................83
6.5 The UPnP Screen .............................................................................................................................83
6.6 The IPv6 LAN Setup Screen .............................................................................................................84
6.7 The File Sharing Screen ..................................................................................................................88
6.7.1 What You Need to Know ..........................................................................................................88
6.7.2 Before You Begin .....................................................................................................................89
6.7.3 The File Sharing Screen ..........................................................................................................89
6.7.4 User Edit .................................................................................................................................91
6.8 Print Server .......................................................................................................................................91
6.8.1 What You Need to Know ..........................................................................................................92
6.8.2 Before You Begin .....................................................................................................................92
6.8.3 The Print Server Screen ..........................................................................................................93
6.9 Add a New Printer Using Windows ...................................................................................................93
6.10 Add a New Printer Using Macintosh OS X ......................................................................................97
6.10.1 Mac OS 10.3 and 10.4 ...........................................................................................................97
6.10.2 Mac OS 10.5 and 10.6 .........................................................................................................100
6.11 Home Networking Technical Reference ........................................................................................103
6.11.1 LANs, WANs and the Device ...............................................................................................104
6.11.2 DHCP Setup ........................................................................................................................104
6.11.3 DNS Server Addresses ........................................................................................................104
6.11.4 LAN TCP/IP .........................................................................................................................105
6.11.5 RIP Setup .............................................................................................................................106
6.11.6 Multicast ...............................................................................................................................106
Static
Route
....................................................................................................................................... 109
7.1 Overview ........................................................................................................................................109
7.1.1 What You Can Do in the Static Route Screens ......................................................................109
7.2 The Static Route Screen
7.2.1 Static Route Add/Edit
7.3 IPv6 Static Route
7.3.1 IPv6 Static Route Edit
Quality of Service
8.1 Overview
8.1.1 What You Can Do in the QoS Screens
8.1.2 What You Need to Know About QoS
8.2 The Quality of Service General Screen
8.3 The Queue Setup Screen
8.3.1 Adding a QoS Queue
8.4 The Class Setup Screen
8.4.1 Class Setup Add/Edit
8.5 The QoS Game List Screen ...........................................................................................................121
.................................................................................................................
...........................................................................................................
.............................................................................................................................
..........................................................................................................
(QoS)...................................................................................................................
.........................................................................................................................................
..................................................................................
.....................................................................................
...........................................................................................
...............................................................................................................
...........................................................................................................
................................................................................................................
.............................................................................................................
110
110
111
112
113
113
113
114
114
115
116
117
117
Page 8

6
eircom D1000 modem User’s Guide
8.6 QoS Technical Reference ...............................................................................................................122
8.6.1 IEEE 802.1p ..........................................................................................................................122
8.6.2 IP Precedence .......................................................................................................................122
8.6.3 Automatic Priority Queue Assignment ...................................................................................123
Network Address Translation
(NAT)................................................................................................
9.1 Overview .........................................................................................................................................125
9.1.1 What You Can Do in the NAT Screens ..................................................................................125
9.1.2 What You Need To Know About NAT ....................................................................................125
9.2 The NAT General Screen ................................................................................................................126
9.3 The Port Forwarding Screen ...........................................................................................................127
9.3.1 Configuring the Port Forwarding Screen ...............................................................................127
9.3.2 Port Forwarding Rule Add/Edit ..............................................................................................128
9.4 The DMZ Screen .............................................................................................................................129
9.5 The ALG Screen .............................................................................................................................130
9.6 NAT Technical Reference ................................................................................................................130
9.6.1 NAT Definitions ......................................................................................................................131
9.6.2 What NAT Does .....................................................................................................................131
9.6.3 How NAT Works ....................................................................................................................131
9.6.4 NAT Application .....................................................................................................................132
9.6.5 NAT Mapping Types ..............................................................................................................132
Port
Isolation
..................................................................................................................................... 135
10.1 Overview .......................................................................................................................................135
10.1.1 What You Can Do in the Port Isolation Screens ..................................................................136
10.2 The Port Isolation General Screen ................................................................................................136
10.3 The Port Isolation Screen ..............................................................................................................136
10.3.1 Port Isolation Summary Screen ...........................................................................................137
Dynamic DNS Setup ......................................................................................................................... 139
11.1 Overview .......................................................................................................................................139
11.1.1 What You Can Do in the DDNS Screen ...............................................................................139
11.1.2 What You Need To Know About DDNS ...............................................................................139
11.2 The Dynamic DNS Screen ............................................................................................................139
Fil
ter
................................................................................................................................................... 141
12.1 Overview ......................................................................................................................................141
12.1.1 What You Can Do in the Filter Screens ...............................................................................141
12.1.2 What You Need to Know About Filtering .............................................................................141
12.2 The IP/MAC Filter Screen .............................................................................................................141
12.3 IPv6/MAC Filter .............................................................................................................................143
Firewall .............................................................................................................................................. 147
13.1 Overview .......................................................................................................................................147
13.1.1 What You Can Do in the Firewall Screens ...........................................................................147
125
Page 9

7
eircom D1000 modem User’s Guide
13.1.2 What You Need to Know About Firewall ..............................................................................148
13.2 The Firewall General Screen ........................................................................................................149
13.3 The Default Action Screen ............................................................................................................150
13.4 The Rules Screen .........................................................................................................................151
13.4.1 The Rules Add Screen ........................................................................................................152
13.4.2 Customized Services ..........................................................................................................154
13.4.3 Customized Service Add/Edit .............................................................................................155
13.5 The DoS Screen ............................................................................................................................156
13.5.1 The DoS Advanced Screen .................................................................................................156
13.5.2 Configuring Firewall Thresholds ..........................................................................................157
13.6 Firewall Technical Reference ........................................................................................................158
13.6.1 Firewall Rules Overview ......................................................................................................158
13.6.2 Guidelines For Enhancing Security With Your Firewall .......................................................159
13.6.3 Security Considerations .......................................................................................................160
13.6.4 Triangle Route .....................................................................................................................160
Parental
Control
................................................................................................................................ 163
14.1 Overview .......................................................................................................................................163
14.2 The Parental Control Screen .........................................................................................................163
14.2.1 Add/Edit Parental Control Rule ............................................................................................164
Certificates ........................................................................................................................................
167
15.1 Overview .......................................................................................................................................167
15.1.1 What You Can Do in this Chapter ........................................................................................167
15.2 What You Need to Know ...............................................................................................................167
15.3 Local Certificates ...........................................................................................................................167
15.4 The Trusted CA Screen ................................................................................................................169
15.5 Trusted CA Import .......................................................................................................................169
15.6 View Certificate .............................................................................................................................170
Log .................................................................................................................................................... 173
16.1 Overview ......................................................................................................................................173
16.1.1 What You Can Do in this Chapter ........................................................................................173
16.1.2 What You Need To Know .....................................................................................................173
16.2 The System Log Screen ................................................................................................................174
Traffic
Status .....................................................................................................................................
175
17.1 Overview .......................................................................................................................................175
17.1.1 What You Can Do in this Chapter ........................................................................................175
17.2 The WAN Status Screen ...............................................................................................................175
17.3 The LAN Status Screen .................................................................................................................176
17.4 The NAT Screen ............................................................................................................................177
User Account .................................................................................................................................... 179
18.1 Overview .......................................................................................................................................179
Page 10

8
eircom D1000 modem User’s Guide
18.2 The User Account Screen .............................................................................................................179
System
Setting
.................................................................................................................................. 181
19.1 Overview .......................................................................................................................................181
19.2 The System Screen .......................................................................................................................181
Time Setting ...................................................................................................................................... 183
20.1 Overview .......................................................................................................................................183
20.2 The Time Setting Screen .............................................................................................................183
Log
Setting
........................................................................................................................................ 187
21.1 Overview ......................................................................................................................................187
21.2 The Log Setting Screen ................................................................................................................187
Firmware
Upgrade ............................................................................................................................
22.1 Overview .......................................................................................................................................189
22.2 The Firmware Screen ....................................................................................................................189
Backup/Restore ................................................................................................................................ 191
23.1 Overview .......................................................................................................................................191
23.2 The Backup/Restore Screen .........................................................................................................191
23.3 The Reboot Screen .......................................................................................................................193
Remote
Management........................................................................................................................
24.1 Overview .......................................................................................................................................195
24.1.1 What You Can Do in the Remote Management Screens ....................................................195
24.1.2 What You Need to Know About Remote Management ........................................................196
24.2 The WWW Screen ........................................................................................................................196
24.2.1 Configuring the WWW Screen .............................................................................................196
24.3 The Telnet Screen .........................................................................................................................198
24.4 The FTP Screen ............................................................................................................................199
24.5 The SNMP Screen ........................................................................................................................199
24.5.1 Configuring SNMP ...............................................................................................................200
24.6 The DNS Screen ..........................................................................................................................201
24.7 The ICMP Screen ..........................................................................................................................202
24.8 The SSH Screen ...........................................................................................................................203
Diagnostic ......................................................................................................................................... 205
25.1 Overview .......................................................................................................................................205
25.1.1 What You Can Do in the Diagnostic Screens ......................................................................205
25.2 The General Screen ......................................................................................................................205
25.3 The DSL Line Screen ....................................................................................................................206
Troubleshooting
................................................................................................................................ 209
26.1 Power, Hardware Connections, and LEDs ....................................................................................209
26.2 Device Access and Login ..............................................................................................................210
189
195
Page 11

9
eircom D1000 modem User’s Guide
LED
Descriptions
26.3 Internet Access
.............................................................................................................................. 213
.............................................................................................................................
211
27.1 LED Descriptions ..........................................................................................................................213
Appendix A Legal
Information..........................................................................................................
215
Index .................................................................................................................................................. 219
Page 12

10
eircom D1000 modem User’s Guide
Page 13

PART I
User’s Guide
11
Page 14

12
Page 15

13
eircom D1000 modem User’s Guide
1
1.1 Overview
The eircom D1000 modem is an ADSL2+ router that integrates DSL and NAT, and provides ease of
installation and high-speed, shared Internet access. The Device is also a complete security solution
with a robust firewall and content filtering.
Only use firmware for your Device’s specific model. Refer to the label on
the bottom of your Device.
1.2 Ways to Manage the Device
Use any of the following methods to manage the Device.
• Web Configurator. This is recommended for everyday management of the Device using a
(supported) web browser.
• Command Line Interface. Line commands are mostly used for troubleshooting by service
engineers.
• TR-069. This is an auto-configuration server used to remotely configure your device.
Introduction
1.3 Good Habits for Managing the Device
Do the following things regularly to make the Device more secure and to manage the Device more
effectively.
• Change the password. Use a password that’s not easy to guess and that consists of different
types of characters, such as numbers and letters.
• Write down the password and put it in a safe place.
• Back up the configuration (and make sure you know how to restore it). Restoring an earlier
working configuration may be useful if the device becomes unstable or even crashes. If you
forget your password, you will have to reset the Device to its factory default settings. If you
backed up an earlier configuration file, you would not have to totally re-configure the Device. You
could simply restore your last configuration.
1.4 Applications for the Device
Here are some example uses for which the Device is well suited.
Page 16
14
eircom D1000 modem User’s Guide
Chapter 1 Introduction
1.4.1 Internet Access
Your Device provides shared Internet access by connecting the DSL port to the DSL or MODEM
jack on a splitter or your telephone jack. Computers can connect to the Device’s Ethernet ports (or
wirelessly).
Figure 1 Device’s Router Features
You can also configure firewall and filtering feature on the Device for secure Internet access. When
the firewall is on, all incoming traffic from the Internet to your network is blocked unless it is
initiated from your network. This means that probes from the outside to your network are not
allowed, but you can safely browse the Internet and download files.
Use the filtering feature to block access to specific web sites or Internet applications such as MSN or
Yahoo Messenger. You can also configure IP/MAC filtering rules for incoming or outgoing traffic.
Use QoS to efficiently manage traffic on your network by giving priority to certain types of traffic
and/or to particular computers. For example, you could make sure that the Device gives voice over
Internet calls high priority, and/or limit bandwidth devoted to the boss’s excessive file downloading.
1.4.2 Wireless Access
The Device is a wireless Access Point (AP) for IEEE 802.11b/g/n compliant clients, such as notebook
computers or PDAs and iPads. It allows them to connect to the Internet without having to rely on
inconvenient Ethernet cables. You can set up a wireless network with WPS (WiFi Protected Setup)
or manually add a client to your wireless network.
Figure 2 Wireless Access Example
LAN WAN
DSL
Page 17

15
eircom D1000 modem User’s Guide
1.4.3 Using the WPS/WLAN Button
By default, the wireless network on the Device is turned on. To turn it off, simply press the WPS/
WLAN button on top of the device for over 5 seconds. When the WPS/WLAN LED is green, the
wireless network is active.
You can also use the WPS/WLAN button to quickly set up a secure wireless connection between
the Device and a WPS-compatible client by adding one device at a time.
To activate WPS:
1 Make sure the POWER LED is on and not blinking.
2 Press the WPS/WLAN button for 1-5 seconds and release it.
3 Press the WPS button on another WPS-enabled device within range of the Device. The WPS/WLAN
LED should flash while the Device sets up a WPS connection with the other wireless device.
4 Once the connection is successfully made, the WPS/WLAN LED shines green.
Chapter 1 Introduction
1.5 The RESET Button
If you forget your password or cannot access the web configurator, you will need to use the RESET
button at the side panel of the device to reload the factory-default configuration file. This means
that you will lose all configurations that you had previously and the user name and password will be
1.5.1 Using the Reset Button
reset to the default.
1 Make sure the POWER LED is on (not blinking).
2 To set the device back to the factory default settings, press the RESET button for ten seconds or
until the POWER LED begins to blink and then release it. When the POWER LED begins to blink,
the defaults have been restored and the device restarts.
Page 18

16
eircom D1000 modem User’s Guide
Page 19

17
eircom D1000 modem User’s Guide
2
Introducing the Web Configurator
2.1 Overview
The web configurator is an HTML-based management interface that allows easy device setup and
management via Internet browser. Use Internet Explorer 6.0 and later versions, Mozilla Firefox 3
and later versions, or Safari 2.0 and later versions. The recommended screen resolution is 1024 by
768 pixels.
In order to use the web configurator, you need to allow:
• Web browser pop-up windows from your device. Web pop-up blocking is enabled by default in
2.1.1 Accessing the Web Configurator
Windows XP SP (Service Pack) 2.
• JavaScript (enabled by default).
• Java permissions (enabled by default).
1 Make sure your Device hardware is properly connected.
2 Launch your web browser.
3 Type "192.168.1.254" as the URL.
4 A password screen displays. Type “admin” (default) as the username and enter the default
password (which is the same as the wireless key on the Device’s back label), then click Login. If
you have changed the password, enter your new password and click Login.
Figure 3 Password Screen
Note: For security reasons, the Device automatically logs you out if you do not use the
web configurator for 900 seconds (default). If this happens, log in again.
Page 20

Chapter 2 Introducing the Web Configurator
18
eircom D1000 modem User’s Guide
5 If you enter the wrong username and/or password three times, the Device lockes you out of the
login screen for ten minutes and the following screen displays.
Figure 4 Lockout Screen
6 The following screen displays if you have not yet changed your password. It is strongly
recommended you change the default password. Enter a new password, retype it to confirm and
click Apply; alternatively click Skip to proceed to the next screen if you do not want to change the
password now.
Figure 5 Change Password Screen
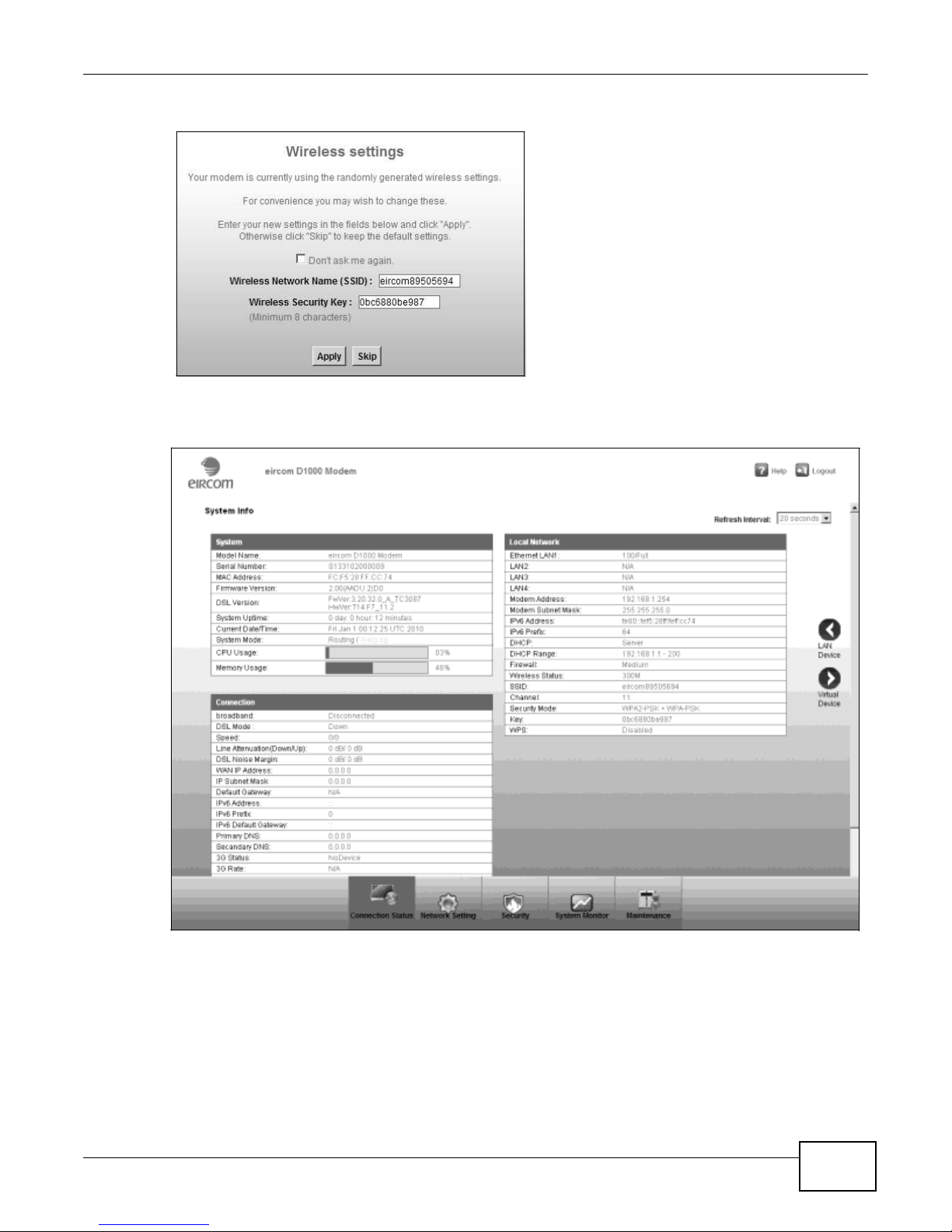
The following screen displays and asks if you want to change your wireless settings, including SSID
and wireless security key. If you have changed the settings, click Apply. If not, click Skip to
proceed to the Connection Status screen if you do not want to change them now.
Page 21
Chapter 2 Introducing the Web Configurator
19
eircom D1000 modem User’s Guide
Figure 6 Change Wireless Settings Screen
7 The Connection Status screen appears.
Figure 7 Connection Status
8 The System Info screen shows. You can view the Device’s interface and system information.
Page 22
Chapter 2 Introducing the Web Configurator
20
eircom D1000 modem User’s Guide
2.2 The Web Configurator Layout
Figure 8 Web Configurator Layout Screen
B
A
As illustrated above, the main screen is divided into these parts:
• A - title bar
• B - main window
• C - navigation panel
2.2.1 Title Bar
The title bar shows the following icon in the upper right corner.
Click this icon to log out of the web configurator.
Click the Help icon to go to eircom’s support website. Click the Logout icon to log out of the web
configurator.
2.2.2 Main Window
The main window displays information and configuration fields. It is discussed in the rest of this
document.
C
Page 23

Chapter 2 Introducing the Web Configurator
21
eircom D1000 modem User’s Guide
LINK
TAB
FUNCTION
Connection Status
This screen shows the Device’s interface and system information.
Network Setting
Broadband
Internet
Connection
Use this screen to configure ISP parameters, WAN IP address
assignment, DNS servers and other advanced properties.
More Connections
Use this screen to configure additional WAN connections.
3G Backup
Use this screen to configure your 3G backup Internet connection
settings.
If you click LAN Device on the System Info screen, the Connection Status screen appears. See
Chapter 3 on page 27 for more information about the Connection Status screen.
If you click Virtual Device on the System Info screen, a visual graphic appears, showing the
connection status of the Device’s ports.
Figure 9 Virtual Device
2.2.3 Navigation Panel
Use the menu items on the navigation panel to open screens to configure Device features. The
following table describes each menu item.
Table 1 Navigation Panel Summary
Page 24
Chapter 2 Introducing the Web Configurator
22
eircom D1000 modem User’s Guide
LINK
TAB
FUNCTION
Wireless
General
Use this screen to turn the wireless connection on or off, specify
the SSID(s) and configure the wireless LAN settings and WLAN
authentication/security settings.
More AP
Use this screen to configure multiple BSSs on the Device.
MAC
Authentication
Use this screen to block or allow wireless traffic from wireless
devices of certain SSIDs and MAC addresses to the Device.
WPS
Use this screen to use WPS (Wi-Fi Protected Setup) to establish a
wireless connection.
WDS
Use this screen to set up Wireless Distribution System (WDS) links
to other access points.
WMM
Use this screen to enable or disable Wi-Fi MultiMedia (WMM).
Scheduling
Use this screen to configure when the Device enables or disables
the wireless LAN.
Advanced
Use this screen to configure advanced wireless settings such as
output power.
Home
Networking
LAN Setup
Use this screen to configure LAN TCP/IP settings, and other
advanced properties.
Static DHCP
Use this screen to assign specific IP addresses to individual MAC
addresses.
IP Alias
Use this screen to partition your LAN interface into dfferent logical
networks.
UPnP
Use this screen to enable the UPnP function.
IPv6 LAN Setup
Use this screen to configure the IPv6 settings on the Device’s LAN
interface.
File Sharing
Use this screen to set up file sharing.
Print Server
The print server screen is used to enable the print server function.
Static Route
Static Route
Use this screen to view and set up static routes on the Device.
IPv6 Static Route
Use this screen to configure IPv6 static routes.
QoS
General
Use this screen to enable QoS and decide allowable bandwidth
using QoS.
Queue
Use this screen to configure QoS queue assignment.
Class Setup
Use this screen to set up classifiers to sort traffic into different
flows and assign priority and define actions to be performed for a
classified traffic flow.
Game List
Use this screen to give priority to traffic for specific games.
NAT
General
Use this screen to activate/deactivate NAT.
Port Forwarding
Use this screen to make your local servers visible to the outside
world.
DMZ
Use this screen to configure a default server which receives
packets from ports that are not specified in the Port Forwarding
screen.
ALG
Use this screen to activate/deactivate the SIP ALG feature.
Port Isolation
General
Use this screen to activate/deactivate port isolation.
Port Isolation
Use this screen to configure and view port binding groups.
Dynamic DNS
Dynamic DNS
Use this screen to allow a static hostname alias for a dynamic IP
address.
Security
Table 1 Navigation Panel Summary (continued)
Page 25
Chapter 2 Introducing the Web Configurator
23
eircom D1000 modem User’s Guide
LINK
TAB
FUNCTION
Filter
IP/MAC Filter
Use this screen to configure IPv4/MAC filtering rules for incoming
or outgoing traffic.
IPv6/MAC Filter
Use this screen to configure IPv6/MAC filtering rules for incoming
or outgoing traffic.
Firewall
General
Use this screen to activate/deactivate the firewall.
Default Action
Use this screen to set the default action that the firewall takes on
packets that do not match any of the firewall rules.
Rules
Use this screen to view the configured firewall rules and add, edit
or remove a firewall rule.
DoS
Use this screen to set the thresholds that the Device uses to
determine when to start dropping sessions that are not fully
established (half-open sessions).
Parental Control
Parental Control
Use this screen to define time periods and days during which the
Device performs parental control and/or block web sites with the
specific URL.
Certificates
Local Certificates
Use this screen to export self-signed certificates or certification
requests and import the Device’s CA-signed certificates.
Trusted CA
Use this screen to save CA certificates to the Device.
System Monitor
Log
Log
Use this screen to view the logs for the level that you selected.
You can export or e-mail the logs.
Traffic Status
WAN
Use this screen to view the status of all network traffic going
through the WAN port of the Device.
LAN
Use this screen to view the status of all network traffic going
through the LAN ports of the Device.
NAT
Use this screen to view the status of NAT sessions on the Device.
Maintenance
Users Account
Users Account
Use this screen to configure the passwords your user accounts.
System
System
Use this screen to configure management inactivity time-out
setting.
Time Setting
Time Setting
Use this screen to change your Device’s time and date.
Log Setting
Log Setting
Use this screen to configure the Device’s log settings and which
logs and/or immediate alerts the Device is to record.
Firmware
Upgrade
Firmware Upgrade
Use this screen to upload firmware to your Device.
Backup/Restore
Backup/Restore
Use this screen to backup and restore your device’s configuration
(settings) or reset the factory default settings.
Reboot
Reboot
Use this screen to reboot the Device without turning the power
off.
Remote MGMT
WWW, Telnet, FTP,
SNMP, DNS, ICMP,
SSH
Use this screen to enable specific traffic directions for specific
network service.
Diagnostic
Ping
Use this screen to test the connections to other devices.
DSL Line
Use this screen to identify problems with the DSL connection.
Table 1 Navigation Panel Summary (continued)
Page 26

Chapter 2 Introducing the Web Configurator
24
eircom D1000 modem User’s Guide
Page 27

PART II
Technical Reference
25
Page 28

26
Page 29
27
eircom D1000 modem User’s Guide
3
3.1 Overview
After you log into the web configurator, the System Info screen shows. Use this screen to view the
status of the Device.
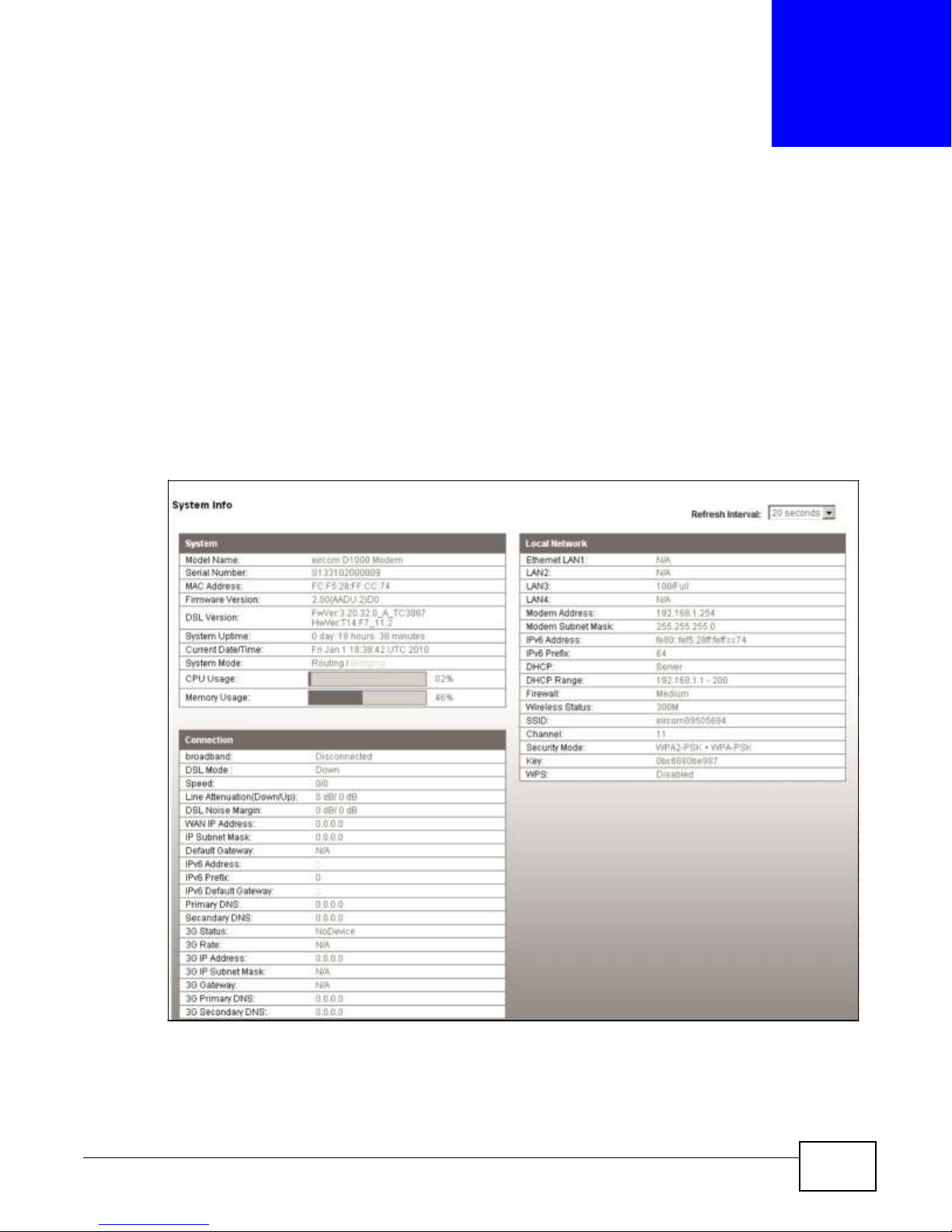
3.2 The System Info Screen
Figure 10 System Info Screen
The System Info Screen
Page 30

28
eircom D1000 modem User’s Guide
Chapter 3 The System Info Screen
LABEL
DESCRIPTION
Refresh Interval
Select how often you want the Device to update this screen from the drop-down list
box.
System
Model Name
This is the model name of your device.
Serial Number
This field displays the certificate’s identification number given by the certification
authority.
MAC Address
This is the MAC (Media Access Control) or Ethernet address unique to your Device.
Firmware
Version
This field displays the current version of the firmware inside the device. It also shows
the date the firmware version was created.
DSL Version
This is the current version of the Device’s DSL modem code.
System UpTime
This field displays how long the Device has been running since it last started up. The
Device starts up when you plug it in, when you restart it (Maintenance > Reboot), or
when you reset it (see Chapter 1 on page 15).
Current Date/
Time
This field displays the current date and time in the Device. You can change this in
Maintenance > Time Setting.
System Mode
This displays whether the Device is functioning as a router or a bridge.
CPU Usage
This field displays what percentage of the Device’s processing ability is currently used.
When this percentage is close to 100%, the Device is running at full load, and the
throughput is not going to improve anymore. If you want some applications to have
more throughput, you should turn off other applications.
Memory Usage
This field displays what percentage of the Device’s memory is currently used. Usually,
this percentage should not increase much. If memory usage does get close to 100%
and remains like that for a high period of time, the Device may become unstable and
you should restart it. See Section 23.3 on page 193, or turn off the device (unplug the
power) for a few seconds.
Connection
Broadband
This is the current status of your broadband.
DSL Mode
This is the DSL standard that your Device is using.
Speed
This shows the speed of your DSL connection.
Line
Attenuation
(Down/Up)
This indicates the line attenuation status for each upstream and downstream band.
DSL Noise
Margin
This is the signal to noise ratio for the downstream part of the connection (coming into
the Device from the ISP). It is measured in decibels. The higher the number the more
signal and less noise there is.
WAN IP Address
This field displays the current IP address of the Device in the WAN.
IP Subnet Mask
This field displays the current subnet mask in the WAN.
Default
Gateway
This is the IP address of the default gateway, if applicable.
IPv6 Address
This is the current IPv6 address of the Device in the WAN. Click this to go to the screen
where you can change it.
IPv6 Prefix
This is the current IPv6 prefix length in the WAN.
IPv6 Default
Gateway
This is the IPv6 address of the default gateway, if applicable.
Primary/
Secondary DNS
This is the primary/secondary DNS server IP address assigned to the Device.
3G Status
This shows the current status of your 3G connection. NoDevice is shown when no 3G
card is inserted.
Each field is described in the following table.
Table 2 System Info Screen
Page 31

29
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
3G Rate
This shows the rate of the 3G connection if it is available.
3G IP Address
This shows the IP address for the 3G connection.
3G IP Subnet
Mask
This shows the current subnet mask for the 3G connection.
3G Gateway
This shows the IP address of the 3G connection’s default gateway.
3G Primary/
Secondary DNS
This shows the first and second DNS server address assigned by the ISP.
Local Network
LAN1
LAN2
LAN3
LAN4
This displays the link speed and duplex mode of the LAN port(s) in use.
(LAN1 is reserved for Ethernet WAN.)
Modem Address
This field displays the current IP address of the Device in the LAN.
Modem Subnet
Mask
This field displays the current subnet mask in the LAN.
IPv6 Address
This is the current IPv6 address of the Device in the LAN. Click this to go to the screen
where you can change it.
IPv6 Prefix
This is the current IPv6 prefix length in the LAN.
IPv6 Prefix
This is the current IPv6 prefix in the LAN.
DHCP
This field displays what DHCP services the Device is providing to the LAN. Choices are:
Server - The Device is a DHCP server in the LAN. It assigns IP addresses to other
computers in the LAN.
Relay - The Device acts as a surrogate DHCP server and relays DHCP requests and
responses between the remote server and the clients.
None - The Device is not providing any DHCP services to the LAN.
DHCP Range
This is the IP address range that the Device is assigning to other computers in the LAN
when it acts as a DHCP server.
Firewall
This shows the security level setting of the Device’s firewall.
Wireless Status
This displays whether wireless LAN is turned on or off.
SSID
This is the descriptive name used to identify the Device in the wireless LAN.
Channel
This is the channel number used by the Device now.
Security Mode
This displays the type of security the Device is using in the wireless LAN.
Key
This displays the wireless key of the Device.
WPS
Configured displays when the WPS security settings have been configured and wireless
clients can connect with the device through WPS. Unconfigured displays when the
device has not been configured and wireless clients can’t establish a link with the device
through WPS.
Chapter 3 The System Info Screen
Table 2 System Info Screen (continued)
3.3 The LAN Device Screen
Click LAN Device in the System Info screen to view the information of the client(s) connected to
the Device. In this screen, you can configure how often you want the Device to update this screen
in Refresh Interval.
Page 32

Chapter 3 The System Info Screen
30
eircom D1000 modem User’s Guide
Figure 11 LAN Device: List View
If you want to view the connection status of the Device and its client(s), click Icon View in the
Viewing mode selection box.
Figure 12 LAN Device: Icon View
Click on a client’s name to show an Info button.
• Click it to view information about the client. Click OK to close the screen.
Page 33

31
eircom D1000 modem User’s Guide
4
4.1 Overview
This chapter describes the Device’s Broadband screens. Use these screens to configure your
Device for Internet access.
A WAN (Wide Area Network) connection is an outside connection to another network or the
Internet. It connects your private networks (such as a LAN (Local Area Network) and other
networks, so that a computer in one location can communicate with computers in other locations.
Figure 13 LAN and WAN
LAN
4.1.1 What You Can Do in the WAN Screens
• Use the Internet Connection screen (Section 4.2 on page 32) to configure the WAN settings on
the Device for Internet access.
• Use the More Connections screen (Section 4.3 on page 36) to set up additional Internet access
connections.
• Use the 3G Backup screen (Section 4.4 on page 40) to configure your 3G backup Internet
connection settings.
4.1.2 What You Need to Know About WAN
Encapsulation Method
Encapsulation is used to include data from an upper layer protocol into a lower layer protocol. To set
up a WAN connection to the Internet, you need to use the same encapsulation method used by your
ISP (Internet Service Provider). If your ISP offers a dial-up Internet connection using PPPoE (PPP
over Ethernet) or PPPoA, they should also provide a username and password (and service name)
for user authentication.
WAN
Broadband
Page 34

Chapter 4 Broadband
32
eircom D1000 modem User’s Guide
WAN IP Address
The WAN IP address is an IP address for the Device, which makes it accessible from an outside
network. It is used by the Device to communicate with other devices in other networks. It can be
static (fixed) or dynamically assigned by the ISP each time the Device tries to access the Internet.
If your ISP assigns you a static WAN IP address, they should also assign you the subnet mask and
DNS server IP address(es) (and a gateway IP address if you use the Ethernet or ENET ENCAP
encapsulation method).
Multicast
Traditionally, IP packets are transmitted in one of either two ways - Unicast (1 sender - 1 recipient)
or Broadcast (1 sender - everybody on the network). Multicast delivers IP packets to a group of
hosts on the network - not everybody and not just one.
IGMP
IGMP (Internet Group Multicast Protocol) is a network-layer protocol used to establish membership
in a Multicast group - it is not used to carry user data. There are three versions of IGMP. IGMP
version 2 and 3 are improvements over version 1, but IGMP version 1 is still in wide use.
IPv6
IPv6 (Internet Protocol version 6), is designed to increase IP address space and enhance features.
The Device supports IPv4/IPv6 dual stack and can connect to IPv4 and IPv6 networks.
Finding Out More
See Section 4.5 on page 42 for technical background information on WAN.
4.1.3 Before You Begin
You need to know your Internet access settings such as encapsulation and WAN IP address. Get this
information from your ISP.
4.2 The Internet Connection Screen
Use this screen to change your Device’s WAN settings. Click Network Setting > Broadband >
Internet Connection. The screen differs by the WAN type and encapsulation you select.
Page 35

Chapter 4 Broadband
33
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
Line
Type
Select the mode supported by your ISP.
Use Auto Sync-Up if you are not sure which mode to choose from. The Device
dynamically diagnoses the mode supported by the ISP and selects the best
compatible one for your connection.
Other options are Ethernet(ETH1), ADSL2+, ADSL2, G.DMT, T1.413 and G.lite.
General
Mode
Select Router (default) from the drop-down list box if your ISP gives you one IP
address only and you want multiple computers to share an Internet account. Select
Bridge when your ISP provides you more than one IP address and you want the
connected computers to get individual IP address from ISP’s DHCP server directly. If
you select Bridge, you cannot use Firewall, DHCP server and NAT on the Device.
Encapsulation
Select the method of encapsulation used by your ISP from the drop-down list box.
Choices vary depending on the mode you select in the Mode field.
If you select Router in the Mode field, select IPoE, RFC 1483, PPPoE, or PPPoA.
If you select Bridge in the Mode field, method of encapsulation is not available.
User Name
(PPPoA and PPPoE encapsulation only) Enter the user name exactly as your ISP
assigned. If assigned a name in the form user@domain where domain identifies a
service name, then enter both components exactly as given.
Password
(PPPoA and PPPoE encapsulation only) Enter the password associated with the user
name above.
Service Name
(PPPoE only) Type the name of your PPPoE service here.
Figure 14 Network Setting > Broadband > Internet Connection
The following table describes the labels in this screen.
Table 3 Network Setting > Broadband > Internet Connection
Page 36

Chapter 4 Broadband
34
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
Multiplex
Select the method of multiplexing used by your ISP from the drop-down list. Choices
are VC-Mux or LLC.
IPv6/IPv4 Dual Stack
If you select IPv4/IPv6, the Device can connect to both IPv4 and IPv6 networks and
choose the protocol for applications according to the address type. If you select IPv4
or IPv6 the Device will operate in IPv4 or IPv6 mode.
PPP Authentication
The Device supports PAP (Password Authentication Protocol) and CHAP (Challenge
Handshake Authentication Protocol). CHAP is more secure than PAP; however, PAP is
readily available on more platforms.
Use the drop-down list box to select an authentication protocol for outgoing calls.
Options are:
AUTO - Your Device accepts either CHAP or PAP when requested by this remote node.
CHAP - Your Device accepts CHAP only.
PAP - Your Device accepts PAP only.
Virtual Circuit ID
VPI (Virtual Path Identifier) and VCI (Virtual Channel Identifier) define a virtual
circuit. Refer to the appendix for more information.
VPI
The valid range for the VPI is 0 to 255. Enter the VPI assigned to you.
VCI
The valid range for the VCI is 32 to 65535 (0 to 31 is reserved for local management
of ATM traffic). Enter the VCI assigned to you.
IP Address
This option is available if you select Router in the Mode field.
A static IP address is a fixed IP that your ISP gives you. A dynamic IP address is not
fixed; the ISP assigns you a different one each time you connect to the Internet.
Select Obtain an IP Address Automatically if you have a dynamic IP address;
otherwise select Static IP Address and type your ISP assigned IP address in the IP
Address and Gateway IP Address fields (supplied by your ISP) below.
IPv6 Rapid
Deployment
This is available only when you select IPv4 in the IPv6/IPv4 Dual Stack field. By
enabling the IPv6 Rapid Deployment function, the Device uses an ISP’s IPv6 address
prefix instead of the 2002::/48 prefix. The operational domain of 6RD is limited to
and controlled by the ISP’s network. 6RD hosts are ensured to be reachable from all
native IPv6 addresses as 6RD only uses relay servers within control of the ISP.
Enable
Select this option to enable IPv6 Rapid Deployment.
Mode
Select Auto or Manual mode. If you select Manual, enter the tunneling relay
server's IPv4 address in the field below.
Relay Server
Enter the tunneling relay server's IPv4 address in this field.
DNS Server - This section is not available when you select Bridge in the Mode field.
Primary DNS
Server
Enter the first DNS server address assigned by the ISP.
Secondary DNS
Server
Enter the second DNS server address assigned by the ISP.
IPv6 Address (The following fields are available only when you select IPv6 in the IPv6/IPv4 Dual Stack
field.)
Obtain an IP Address
Automatically
Select this option if you want to have the Device use the IPv6 prefix from the
connected router’s Router Advertisement (RA) to generate an IPv6 address.
Table 3 Network Setting > Broadband > Internet Connection (continued)
Page 37

Chapter 4 Broadband
35
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
DHCP IPv6
Select DHCP if you want to obtain an IPv6 address from a DHCPv6 server.
The IP address assigned by a DHCPv6 server has priority over the IP address
automatically generated by the Device using the IPv6 prefix from an RA.
Select SLAAC (Stateless address autoconfiguration) to have the Device use the prefix
to automatically generate a unique IP address that does not need to be maintained by
a DHCP server.
Selelct Auto to have the Device indicate to hosts for IPv6 address generation
depending on the M/O (Managed/Other) flag values in the router advertisements
sending to hosts.
• If M flag is 1, the Device will indicate to hosts to obtain network settings (such as
WAN IP, LAN prefix and DNS settings) through DHCPv6.
• If M flag is 0, the Device will check O flag.
• If O flag is 1, the Device will indicate to hosts to obtain DNS information and LAN
prefix through DHCPv6.
• If O flag is 0, the Device will not get information through DHCPv6.
DHCP PD
Select Enable to use DHCP PD (Prefix Delegation) to allow the Device to pass the
IPv6 prefix information to its LAN hosts. The hosts can then use the prefix to generate
their IPv6 addresses.
WAN Identifier Type
Select Manual to manually enter a WAN Identifier as the interface ID to identify the
WAN interface. The WAN Identifier is appended to the IPv6 address prefix to create
the routable global IPv6 address. Select EUI64 to use the EUI-64 format to generate
an interface ID from the MAC address of the WAN interface.
WAN Identifier
If you selected Manual, enter the WAN Identifier in this field. The WAN identifier
should be unique and 64 bits in hexadecimal form. Every 16 bit block should be
separated by a colon as in XXXX:XXXX:XXXX:XXXX where X is a hexadecimal
character. Blocks of zeros can be represented with double colons as in
XXXX:XXXX::XXXX.
Connection (PPPoA and PPPoE encapsulation only)
Always On
Select Always On when you want your connection up all the time. The Device will try
to bring up the connection automatically if it is disconnected.
Instant On
Select Instant On when you don't want the connection up all the time and specify an
idle time-out in the Max Idle Timeout field.
Advanced Setup
Click this to display the Advanced WAN Setup screen and edit more details of your
WAN setup. Click this button again to display less fields in this screen.
RIP & Multicast Setup
RIP Direction
RIP (Routing Information Protocol) allows a router to exchange routing information
with other routers. Use this field to control how much routing information the Device
sends and receives on the subnet.
Select the RIP direction from None, Both, In Only and Out Only.
RIP Version
This field is not configurable if you select None in the RIP Direction field.
Select the RIP version from RIP-1, RIP2-B/RIP2-M.
Multicast
Multicast packets are sent to a group of computers on the LAN and are an alternative
to unicast packets (packets sent to one computer) and broadcast packets (packets
sent to every computer).
Internet Group Multicast Protocol (IGMP) is a network-layer protocol used to establish
membership in a multicast group. The Device supports IGMP-v1/IGMP-v2/IGMP-
v3. Select None to disable it.
Table 3 Network Setting > Broadband > Internet Connection (continued)
Page 38

Chapter 4 Broadband
36
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
MLD Proxy
Select the version of MLD proxy (MLDv1 or MLDv2) to have the Device act as for this
connection. This allows the Device to get subscription information and maintain a
joined member list for each multicast group. It can reduce multicast traffic
significantly. Select None to turn off MLD proxy.
ATM QoS
ATM QoS Type
Select CBR (Continuous Bit Rate) to specify fixed (always-on) bandwidth for voice or
data traffic. Select UBR With PCR (Unspecified Bit Rate) for applications that are
non-time sensitive, such as e-mail. Select Realtime VBR (real-time Variable Bit
Rate) type for applications with bursty connections that require closely controlled
delay and delay variation. Select Non Realtime VBR (non real-time Variable Bit
Rate) type for connections that do not require closely controlled delay and delay
variation.
Peak Cell Rate
Divide the DSL line rate (bps) by 424 (the size of an ATM cell) to find the Peak Cell
Rate (PCR). This is the maximum rate at which the sender can send cells. Type the
PCR here.
Sustain Cell Rate
The Sustain Cell Rate (SCR) sets the average cell rate (long-term) that can be
transmitted. Type the SCR, which must be less than the PCR. Note that system
default is 0 cells/sec.
Maximum Burst
Size
Maximum Burst Size (MBS) refers to the maximum number of cells that can be sent
at the peak rate. Type the MBS, which is less than 65535.
PPPoE Passthrough
If encapsulation type is PPPoE, select Yes to enable PPPoE Passthrough. In addition to
the Device’s built-in PPPoE client, you can select this to allow hosts on the LAN to use
PPPoE client software on their computers to connect to the ISP via the device. Each
host can have a separate account and a public WAN IP address.
MTU
MTU
The Maximum Transmission Unit (MTU) defines the size of the largest packet allowed
on an interface or connection. Enter the MTU in this field.
For ENET ENCAP, the MTU value is 1500.
For PPPoE, the MTU value is 1492.
For PPPoA and RFC 1483, the MTU is 65535.
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
Table 3 Network Setting > Broadband > Internet Connection (continued)
4.3 The More Connections Screen
The Device allows you to configure more than one Internet access connection. To configure
additional Internet access connections click Network Setting > Broadband > More
Connections. The screen differs by the encapsulation you select. When you use the Broadband >
Internet Connection screen to set up Internet access, you are configuring the first WAN
connection.
Page 39

Chapter 4 Broadband
37
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
#
This is an index number indicating the number of the corresponding connection.
Active
This field indicates whether the connection is active or not.
Clear the check box to disable the connection. Select the check box to enable it.
Node Name
This is the name you gave to the Internet connection.
VPI/VCI
This field displays the Virtual Path Identifier (VPI) and Virtual Channel Identifier (VCI)
numbers configured for this WAN connection.
Encapsulation
This field indicates the encapsulation method of the Internet connection.
Modify
The first (ISP) connection is read-only in this screen. Use the Broadband > Internet
Connection screen to edit it.
Click the Edit icon to edit the Internet connection settings. Click this icon on an empty
configuration to add a new Internet access setup.
Click the Remove icon to delete the Internet access setup from your connection list.
Figure 15 Network Setting > Broadband > More Connections
The following table describes the labels in this screen.
Table 4 Network Setting > Broadband > More Connections
4.3.1 More Connections Edit
Use this screen to configure a connection. Click the edit icon in the More Connections screen to
display the following screen.
Page 40

Chapter 4 Broadband
38
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
General
Active
Select the check box to activate or clear the check box to deactivate this connection.
Node Name
Enter a unique, descriptive name of up to 13 ASCII characters for this connection.
Figure 16 Network Setting > Broadband > More Connections: Edit
The following table describes the labels in this screen.
Table 5 Network Setting > Broadband > More Connections: Edit
Page 41

Chapter 4 Broadband
39
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
Mode
Select Router from the drop-down list box if your ISP allows multiple computers to share
an Internet account.
If you select Bridge, the Device will forward any packet that it does not route to this
remote node; otherwise, the packets are discarded.
Encapsulation
Select the method of encapsulation used by your ISP from the drop-down list box.
Choices vary depending on the mode you select in the Mode field.
If you select Router in the Mode field, select PPPoA, RFC 1483, ENET ENCAP or
PPPoE.
If you select Bridge in the Mode field, method of encapsulation is not available.
Multiplex
Select the method of multiplexing used by your ISP from the drop-down list. Choices are
VC or LLC.
By prior agreement, a protocol is assigned a specific virtual circuit, for example, VC1 will
carry IP. If you select VC, specify separate VPI and VCI numbers for each protocol.
For LLC-based multiplexing or PPP encapsulation, one VC carries multiple protocols with
protocol identifying information being contained in each packet header. In this case, only
one set of VPI and VCI numbers need be specified for all protocols.
IPv6/IPv4 Dual
Stack
If you select Enable, the Device can connect to IPv4 and IPv6 networks and choose the
protocol for applications according to the address type. If you select Disable, the Device
will operate in IPv4 mode.
VPI
The valid range for the VPI is 0 to 255. Enter the VPI assigned to you.
VCI
The valid range for the VCI is 32 to 65535 (0 to 31 is reserved for local management of
ATM traffic). Enter the VCI assigned to you.
IP Address
This option is available if you select Router in the Mode field.
A static IP address is a fixed IP that your ISP gives you. A dynamic IP address is not fixed;
the ISP assigns you a different one each time you connect to the Internet.
If you use the encapsulation type except RFC 1483, select Obtain an IP Address
Automatically when you have a dynamic IP address; otherwise select Static IP
Address and type your ISP assigned IP address in the IP Address field below.
If you use RFC 1483, enter the IP address given by your ISP in the IP Address field.
Subnet Mask
Enter a subnet mask in dotted decimal notation.
Gateway IP
Address
Specify a gateway IP address (supplied by your ISP).
Primary DNS
Enter the primary DNS server’s address for the Device.
Secondary
DNS
Enter the secondary DNS server’s address for the Device.
NAT
SUA Only is available only when you select Router in the Mode field.
Select SUA Only if you have one public IP address and want to use NAT. Otherwise, select
None to disable NAT.
Apply
Click this to save your changes.
Cancel
Click this to return to the previous screen without saving.
Advanced Setup
Click this to display more fields in this screen to configure more details of your WAN
settings.
RIP & Multicast Setup
RIP Direction
Select the RIP Direction from None, Both, In Only and Out Only.
RIP Version
This field is not configurable if you select None in the RIP Direction field.
Select the RIP Version from RIP-1, RIP2-B and RIP2-M.
Table 5 Network Setting > Broadband > More Connections: Edit (continued)
Page 42

Chapter 4 Broadband
40
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
Multicast
Internet Group Multicast Protocol (IGMP) is a network-layer protocol used to establish
membership in a multicast group. The Device supports IGMP-v1, IGMP-v2 and IGMP-
v3. Select None to disable it.
ATM QoS
ATM QoS Type
Select CBR (Continuous Bit Rate) to specify fixed (always-on) bandwidth for voice or data
traffic. Select UBR (Unspecified Bit Rate) for applications that are non-time sensitive,
such as e-mail. Select nrtVBR (Variable Bit Rate-non Real Time) or rtVBR (Variable Bit
Rate-Real Time) for bursty traffic and bandwidth sharing with other applications.
Peak Cell Rate
Divide the DSL line rate (bps) by 424 (the size of an ATM cell) to find the Peak Cell Rate
(PCR). This is the maximum rate at which the sender can send cells. Type the PCR here.
Sustain Cell Rate
The Sustain Cell Rate (SCR) sets the average cell rate (long-term) that can be
transmitted. Type the SCR, which must be less than the PCR. Note that system default is
0 cells/sec.
Maximum Burst
Size
Maximum Burst Size (MBS) refers to the maximum number of cells that can be sent at
the peak rate. Type the MBS, which is less than 65535.
MTU
MTU
The Maximum Transmission Unit (MTU) defines the size of the largest packet allowed on
an interface or connection. Enter the MTU in this field.
For ENET ENCAP, the MTU value is 1500.
For PPPoE, the MTU value is 1492.
For PPPoA and RFC, the MTU is 100-1500.
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
Table 5 Network Setting > Broadband > More Connections: Edit (continued)
4.4 The 3G Backup Screen
Use this screen to configure your 3G settings. Click Network Setting > Broadband > 3G
Backup.
Note: The actual data rate you obtain varies depending the 3G card you use, the signal
strength to the service provider’s base station, and so on.
Page 43

Chapter 4 Broadband
41
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
General
3G Backup
Select Enable to have the Device use the 3G connection as your WAN or a backup when the
wired WAN connection fails.
Card
description
This field displays the manufacturer and model name of your 3G card if you inserted one in
the Device. Otherwise, it displays N/A.
Username
Type the user name (of up to 64 ASCII printable characters) given to you by your service
provider.
Password
Type the password (of up to 64 ASCII printable characters) associated with the user name
above.
PIN
A PIN (Personal Identification Number) code is a key to a 3G card. Without the PIN code,
you cannot use the 3G card.
If your ISP enabled PIN code authentication, enter the 4-digit PIN code (0000 for example)
provided by your ISP. If you enter the PIN code incorrectly, the 3G card may be blocked by
your ISP and you cannot use the account to access the Internet.
If your ISP disabled PIN code authentication, leave this field blank.
Dial string
Enter the phone number (dial string) used to dial up a connection to your service provider’s
base station. Your ISP should provide the phone number.
For example, *99# is the dial string to establish a GPRS or 3G connection in Taiwan.
Figure 17 Network Setting > Broadband > 3G Backup
The following table describes the labels in this screen.
Table 6 Network Setting > Broadband > 3G Backup
Page 44

Chapter 4 Broadband
42
eircom D1000 modem User’s Guide
LABEL
DESCRIPTION
APN
Enter the APN (Access Point Name) provided by your service provider. Connections with
different APNs may provide different services (such as Internet access or MMS (Multi-Media
Messaging Service)) and charge method.
You can enter up to 32 ASCII printable characters. Spaces are allowed.
Obtain an IP
Address
Automatically
Select this option If your ISP did not assign you a fixed IP address.
Use the
following static
IP address
Select this option If the ISP assigned a fixed IP address.
IP Address
Enter your WAN IP address in this field if you selected Use the following static IP
address.
Obtain DNS
info
dynamically
Select this to have the Device get the DNS server addresses from the ISP automatically.
Use the
following static
DNS IP address
Select this to have the Device use the DNS server addresses you configure manually.
Primary DNS
server
Enter the first DNS server address assigned by the ISP.
Secondary
DNS
server
Enter the second DNS server address assigned by the ISP.
Connection
Select Keep Alive if you do not want the connection to time out.
Select Connect on Demand if you do not want the connection up all the time and specify
an idle time-out in the Max Idle Timeout field.
Max Idle
Timeout
This value specifies the time in minutes that elapses before the Device automatically
disconnects from the ISP.
Apply
Click Apply to save your changes back to the Device.
Cancel
Click Cancel to return to the previous configuration.
Table 6 Network Setting > Broadband > 3G Backup (continued)
4.5 WAN Technical Reference
This section provides some technical background information about the topics covered in this
4.5.1 Encapsulation
4.5.1.1 ENET ENCAP
chapter.
Be sure to use the encapsulation method required by your ISP. The Device supports the following
methods.
The MAC Encapsulated Routing Link Protocol (ENET ENCAP) is only implemented with the IP
network protocol. IP packets are routed between the Ethernet interface and the WAN interface and
then formatted so that they can be understood in a bridged environment. For instance, it
encapsulates routed Ethernet frames into bridged ATM cells. ENET ENCAP requires that you specify
Page 45

Chapter 4 Broadband
43
eircom D1000 modem User’s Guide
a gateway IP address in the Gateway IP Address field in the wizard or WAN screen. You can get
this information from your ISP.
4.5.1.2 PPP over Ethernet
The Device supports PPPoE (Point-to-Point Protocol over Ethernet). PPPoE is an IETF Draft standard
(RFC 2516) specifying how a personal computer (PC) interacts with a broadband modem (DSL,
cable, wireless, etc.) connection. The PPPoE option is for a dial-up connection using PPPoE.
For the service provider, PPPoE offers an access and authentication method that works with existing
access control systems (for example RADIUS).
One of the benefits of PPPoE is the ability to let you access one of multiple network services, a
function known as dynamic service selection. This enables the service provider to easily create and
offer new IP services for individuals.
Operationally, PPPoE saves significant effort for both you and the ISP or carrier, as it requires no
specific configuration of the broadband modem at the customer site.
By implementing PPPoE directly on the Device (rather than individual computers), the computers on
the LAN do not need PPPoE software installed, since the Device does that part of the task.
Furthermore, with NAT, all of the LANs’ computers will have access.
4.5.1.3 PPPoA
PPPoA stands for Point to Point Protocol over ATM Adaptation Layer 5 (AAL5). A PPPoA connection
functions like a dial-up Internet connection. The Device encapsulates the PPP session based on
RFC1483 and sends it through an ATM PVC (Permanent Virtual Circuit) to the Internet Service
Provider’s (ISP) DSLAM (Digital Subscriber Line (DSL) Access Multiplexer). Please refer to RFC 2364
for more information on PPPoA. Refer to RFC 1661 for more information on PPP.
4.5.1.4 RFC 1483
RFC 1483 describes two methods for Multiprotocol Encapsulation over ATM Adaptation Layer 5
(AAL5). The first method allows multiplexing of multiple protocols over a single ATM virtual circuit
(LLC-based multiplexing) and the second method assumes that each protocol is carried over a
separate ATM virtual circuit (VC-based multiplexing). Please refer to RFC 1483 for more detailed
information.
4.5.2 Multiplexing
There are two conventions to identify what protocols the virtual circuit (VC) is carrying. Be sure to
use the multiplexing method required by your ISP.
VC-based Multiplexing
In this case, by prior mutual agreement, each protocol is assigned to a specific virtual circuit; for
example, VC1 carries IP, etc. VC-based multiplexing may be dominant in environments where
dynamic creation of large numbers of ATM VCs is fast and economical.
Page 46

Chapter 4 Broadband
44
eircom D1000 modem User’s Guide
LLC-based Multiplexing
In this case one VC carries multiple protocols with protocol identifying information being contained
in each packet header. Despite the extra bandwidth and processing overhead, this method may be
advantageous if it is not practical to have a separate VC for each carried protocol, for example, if
charging heavily depends on the number of simultaneous VCs.
4.5.3 VPI and VCI
Be sure to use the correct Virtual Path Identifier (VPI) and Virtual Channel Identifier (VCI) numbers
assigned to you. The valid range for the VPI is 0 to 255 and for the VCI is 32 to 65535 (0 to 31 is
reserved for local management of ATM traffic). Please see the appendix for more information.
4.5.4 IP Address Assignment
A static IP is a fixed IP that your ISP gives you. A dynamic IP is not fixed; the ISP assigns you a
different one each time. The Single User Account feature can be enabled or disabled if you have
either a dynamic or static IP. However the encapsulation method assigned influences your choices
for IP address and ENET ENCAP gateway.
IP Assignment with PPPoA or PPPoE Encapsulation
If you have a dynamic IP, then the IP Address and Gateway IP Address fields are not applicable
(N/A). If you have a Static IP Address assigned by your ISP, then they should also assign you a
Subnet Mask and a Gateway IP Address.
IP Assignment with RFC 1483 Encapsulation
In this case the IP address assignment must be static.
IP Assignment with ENET ENCAP Encapsulation
In this case you can have either a static or dynamic IP. For a static IP you must fill in all the IP
Address and Gateway IP Address fields as supplied by your ISP. However for a dynamic IP, the
Device acts as a DHCP client on the WAN port and so the IP Address and Gateway IP Address
fields are not applicable (N/A) as the DHCP server assigns them to the Device.
4.5.5 Nailed-Up Connection (PPP)
A nailed-up connection is a dial-up line where the connection is always up regardless of traffic
demand. The Device does two things when you specify a nailed-up connection. The first is that idle
timeout is disabled. The second is that the Device will try to bring up the connection when turned
on and whenever the connection is down. A nailed-up connection can be very expensive for obvious
reasons.
Do not specify a nailed-up connection unless your telephone company offers flat-rate service or you
need a constant connection and the cost is of no concern.
Page 47

Chapter 4 Broadband
45
eircom D1000 modem User’s Guide
4.5.6 NAT
NAT (Network Address Translation - NAT, RFC 1631) is the translation of the IP address of a host in
a packet, for example, the source address of an outgoing packet, used within one network to a
different IP address known within another network.
4.6 Traffic Shaping
Traffic Shaping is an agreement between the carrier and the subscriber to regulate the average rate
and fluctuations of data transmission over an ATM network. This agreement helps eliminate
congestion, which is important for transmission of real time data such as audio and video
connections.
Peak Cell Rate (PCR) is the maximum rate at which the sender can send cells. This parameter may
be lower (but not higher) than the maximum line speed. 1 ATM cell is 53 bytes (424 bits), so a
maximum speed of 832Kbps gives a maximum PCR of 1962 cells/sec. This rate is not guaranteed
because it is dependent on the line speed.
Sustained Cell Rate (SCR) is the mean cell rate of each bursty traffic source. It specifies the
maximum average rate at which cells can be sent over the virtual connection. SCR may not be
greater than the PCR.
Maximum Burst Size (MBS) is the maximum number of cells that can be sent at the PCR. After MBS
is reached, cell rates fall below SCR until cell rate averages to the SCR again. At this time, more
cells (up to the MBS) can be sent at the PCR again.
If the PCR, SCR or MBS is set to the default of "0", the system will assign a maximum value that
correlates to your upstream line rate.
The following figure illustrates the relationship between PCR, SCR and MBS.
Figure 18 Example of Traffic Shaping
4.6.1 ATM Traffic Classes
These are the basic ATM traffic classes defined by the ATM Forum Traffic Management 4.0
Specification.
Page 48

Chapter 4 Broadband
46
eircom D1000 modem User’s Guide
Constant Bit Rate (CBR)
Constant Bit Rate (CBR) provides fixed bandwidth that is always available even if no data is being
sent. CBR traffic is generally time-sensitive (doesn't tolerate delay). CBR is used for connections
that continuously require a specific amount of bandwidth. A PCR is specified and if traffic exceeds
this rate, cells may be dropped. Examples of connections that need CBR would be high-resolution
video and voice.
Variable Bit Rate (VBR)
The Variable Bit Rate (VBR) ATM traffic class is used with bursty connections. Connections that use
the Variable Bit Rate (VBR) traffic class can be grouped into real time (VBR-RT) or non-real time
(VBR-nRT) connections.
The VBR-RT (real-time Variable Bit Rate) type is used with bursty connections that require closely
controlled delay and delay variation. It also provides a fixed amount of bandwidth (a PCR is
specified) but is only available when data is being sent. An example of an VBR-RT connection would
be video conferencing. Video conferencing requires real-time data transfers and the bandwidth
requirement varies in proportion to the video image's changing dynamics.
The VBR-nRT (non real-time Variable Bit Rate) type is used with bursty connections that do not
require closely controlled delay and delay variation. It is commonly used for "bursty" traffic typical
on LANs. PCR and MBS define the burst levels, SCR defines the minimum level. An example of an
VBR-nRT connection would be non-time sensitive data file transfers.
Unspecified Bit Rate (UBR)
The Unspecified Bit Rate (UBR) ATM traffic class is for bursty data transfers. However, UBR doesn't
guarantee any bandwidth and only delivers traffic when the network has spare bandwidth. An
example application is background file transfer.
Page 49

47
eircom D1000 modem User’s Guide
5
5.1 Overview
This chapter describes how to perform tasks related to setting up and optimizing your wireless
network, including the following.
5.1.1 What You Can Do in the Wireless LAN Screens
• Turning the wireless connection on or off.
• Configuring a name, wireless channel and security for the network.
• Using WiFi Protected Setup (WPS) to configure your wireless network.
• Setting up multiple wireless networks.
• Using a MAC (Media Access Control) address filter to restrict access to the wireless network.
• Performing other performance-related wireless tasks.
This section describes the Device’s Network Setting > Wireless screens. Use these screens to set
up your Device’s wireless connection.
• Use the General screen to enable the Wireless LAN, enter the SSID and select the wireless
security mode (Section 5.2 on page 48).
• Use the More AP screen (see Section 5.3 on page 54) to set up multiple wireless networks on
your Device.
• Use the MAC Authentication screen to allow or deny wireless clients based on their MAC
addresses from connecting to the Device (Section 5.4 on page 56).
• Use the WPS screen (see Section 5.5 on page 57) to enable or disable WPS, generate a security
PIN (Personal Identification Number) and see information about the Device’s WPS status.
• Use the WDS screen (see Section 5.6 on page 59) to set up a Wireless Distribution System, in
which the Device acts as a bridge with other access points.
• Use the WMM screen to enable Wi-Fi MultiMedia (WMM) to ensure quality of service in wireless
networks for multimedia applications (Section 5.7 on page 60).
• Use the Scheduling screen (see Section 5.8 on page 60) to configure the dates/times to enable
or disable the wireless LAN.
• Use the Advanced screen to configure wireless advanced features (Section 5.9 on page 61).
You don’t necessarily need to use all these screens to set up your wireless connection. For example,
you may just want to set up a network name, a wireless radio channel and security in the General
screen.
Wireless LAN
Page 50

48
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
5.1.2 What You Need to Know About Wireless
Wireless Basics
“Wireless” is essentially radio communication. In the same way that walkie-talkie radios send and
receive information over the airwaves, wireless networking devices exchange information with one
another. A wireless networking device is just like a radio that lets your computer exchange
information with radios attached to other computers. Like walkie-talkies, most wireless networking
devices operate at radio frequency bands that are open to the public and do not require a license to
use. However, wireless networking is different from that of most traditional radio communications in
that there a number of wireless networking standards available with different methods of data
encryption.
Finding Out More
See Section 5.10 on page 63 for advanced technical information on wireless networks.
5.1.3 Before You Start
Before you start using these screens, ask yourself the following questions. See Section 5.1.2 on
page 48 if some of the terms used here are not familiar to you.
• What wireless standards do the other wireless devices in your network support (IEEE 802.11g,
for example)? What is the most appropriate standard to use?
• What security options do the other wireless devices in your network support (WPA-PSK, for
example)? What is the strongest security option supported by all the devices in your network?
• Do the other wireless devices in your network support WPS (Wi-Fi Protected Setup)? If so, you
can set up a well-secured network very easily.
Even if some of your devices support WPS and some do not, you can use WPS to set up your
network and then add the non-WPS devices manually, although this is somewhat more
complicated to do.
• What advanced options do you want to configure, if any? If you want to configure advanced
options such as Quality of Service, ensure that you know precisely what you want to do. If you do
not want to configure advanced options, leave them as they are.
5.2 The General Screen
Use this screen to enable the Wireless LAN, enter the SSID and select the wireless security mode.
Note: If you are configuring the Device from a computer connected to the wireless LAN
and you change the Device’s SSID, channel or security settings, you will lose your
wireless connection when you press Apply to confirm. You must then change the
wireless settings of your computer to match the Device’s new settings.
Click Network Setting > Wireless to open the General screen.
Page 51

49
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Wireless Network Setup
Wireless
Select Enable Wireless LAN to activate wireless LAN.
Wireless Network Settings
Wireless
Network Name
(SSID)
The SSID (Service Set IDentity) identifies the service set with which a wireless device is
associated. Wireless devices associating to the access point (AP) must have the same
SSID.
Enter a descriptive name (up to 32 English keyboard characters) for the wireless LAN.
Hide SSID
Select this check box to hide the SSID in the outgoing beacon frame so a station cannot
obtain the SSID through scanning using a site survey tool.
Client Isolation
Select this to keep the wireless clients in this SSID from communicating with each other
through the Device.
MBSSID/LAN
Isolation
Select this to keep the wireless clients in this SSID from communicating with clients in
other SSIDs or wired LAN devices through the Device.
Select both Client Isolation and MBSSID/LAN Isolation to allow this SSID’s wireless
clients to only connect to the Internet through the Device.
Channel
Selection
Set the operating channel manually by selecting a channel from the Channel Selection
list or use Auto to have it automatically determine a channel to use.
Figure 19 Network Setting > Wireless > General
The following table describes the labels in this screen.
Table 7 Network Setting > Wireless > General
Page 52

50
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Operating
Channel
This field displays the channel the Device is currently using.
Security Level
Security Mode
Select Basic (WEP) or More Secure (WPA(2)-PSK, WPA(2)) to add security on this
wireless network. The wireless clients which want to associate to this network must have
same wireless security settings as the Device. When you select to use a security, additional
options appears in this screen.
Or you can select No Security to allow any client to associate this network without any
data encryption or authentication.
See the following sections for more details about this field.
WPS/WiFi
Button
Select the checkbox to enable the WPS/WiFi button.
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
Table 7 Network Setting > Wireless > General (continued)
5.2.1 No Security
Select No Security to allow wireless stations to communicate with the access points without any
data encryption or authentication.
Note: If you do not enable any wireless security on your Device, your network is
accessible to any wireless networking device that is within range.
Figure 20 Wireless > General: No Security
5.2.2 Basic (WEP Encryption)
WEP encryption scrambles the data transmitted between the wireless stations and the access points
(AP) to keep network communications private. Both the wireless stations and the access points
must use the same WEP key.
Note: WEP is extremely insecure. Its encryption can be broken by an attacker, using
widely-available software. It is strongly recommended that you use a more
effective security mechanism. Use the strongest security mechanism that all the
wireless devices in your network support. For example, use WPA-PSK or WPA2-PSK
if all your wireless devices support it, or use WPA or WPA2 if your wireless devices
support it and you have a RADIUS server. If your wireless devices support nothing
stronger than WEP, use the highest encryption level available.
Your Device allows you to configure one 64-bit or 128-bit WEP key.
Page 53

51
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Security Level
Select Basic to enable WEP data encryption.
Generate
password
automatically
Select this option to have the Device automatically generate a password. The password
field will not be configurable when you select this option.
Password
The password (WEP key) are used to encrypt data. Both the Device and the wireless
stations must use the same password (WEP key) for data transmission.
If you chose 64-bit WEP, then enter any 5 ASCII characters or 10 hexadecimal characters
("0-9", "A-F").
If you chose 128-bit WEP, then enter 13 ASCII characters or 26 hexadecimal characters
("0-9", "A-F").
WEP Encryption
Select 64-bits or 128-bits.
This dictates the length of the security key that the network is going to use.
In order to configure and enable WEP encryption, click Network Setting > Wireless to display the
General screen, then select Basic as the security level.
Figure 21 Wireless > General: Basic (WEP)
The following table describes the wireless LAN security labels in this screen.
Table 8 Wireless > General: Basic (WEP)
5.2.3 More Secure (WPA(2)-PSK)
The WPA-PSK security mode provides both improved data encryption and user authentication over
WEP. Using a Pre-Shared Key (PSK), both the Device and the connecting client share a common
password in order to validate the connection. This type of encryption, while robust, is not as strong
as WPA, WPA2 or even WPA2-PSK. The WPA2-PSK security mode is a newer, more robust version of
the WPA encryption standard. It offers slightly better security, although the use of PSK makes it
less robust than it could be.
Click Network Setting > Wireless to display the General screen. Select More Secure as the
security level. Then select WPA-PSK or WPA2-PSK from the Security Mode list.
Page 54

52
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Security Level
Select More Secure to enable WPA(2)-PSK data encryption.
Security Mode
Select WPA-PSK or WPA2-PSK from the drop-down list box.
Pre-Shared Key
The encryption mechanisms used for WPA(2) and WPA(2)-PSK are the same. The only
difference between the two is that WPA(2)-PSK uses a simple common password,
instead of user-specific credentials.
Type a pre-shared key from 8 to 63 case-sensitive keyboard characters.
more.../hide more
Click more... to show more fields in this section. Click hide more to hide them.
WPA-PSK Compatible
This field appears when you choose WPA-PSK2 as the Security Mode.
Select Enable to allow wireless devices using WPA-PSK security mode to connect to
your Device. The Device supports WPA-PSK and WPA2-PSK simultaneously. Otherwise,
select Disable.
Group Key Update
Timer
The Group Key Update Timer is the rate at which the RADIUS server sends a new
group key out to all clients.
Encryption
This field displays the encryption type for data encryption.
If you choose WPA-PSK as the security mode, the Device uses TKIP for data
encryption.
If you choose WPA2-PSK as the security mode and enable WPA-PSK Compatible, the
Device uses either TKIP and AES (TKIPAES MIX) for data encryption.
If you choose WPA2-PSK as the security mode but disable WPA-PSK Compatible, the
Device uses AES for data encryption.
Figure 22 Wireless > General: More Secure: WPA(2)-PSK
The following table describes the wireless LAN security labels in this screen.
Table 9 Wireless > General: More Secure: WPA(2)-PSK
5.2.4 WPA(2) Authentication
The WPA2 security mode is currently the most robust form of encryption for wireless networks. It
requires a RADIUS server to authenticate user credentials and is a full implementation the security
protocol. Use this security option for maximum protection of your network. However, it is the least
backwards compatible with older devices.
Page 55

53
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Security Level
Select More Secure to enable WPA(2) data encryption.
Security Mode
Choose WPA or WPA2 from the drop-down list box.
Authentication Server
IP Address
Enter the IP address of the external authentication server in dotted decimal notation.
Port Number
Enter the port number of the external authentication server.
You need not change this value unless your network administrator instructs you to do
so with additional information.
Shared Secret
Enter a password (up to 31 alphanumeric characters) as the key to be shared between
the external authentication server and the Device.
The key must be the same on the external authentication server and your Device. The
key is not sent over the network.
more.../hide more
Click more... to show more fields in this section. Click hide more to hide them.
ReAuthentication
Timer
Enter how often the external authentication server requires a connected wireless client
to reauthenticate itself to the server again.
Network Re-auth
Interval
Specify how often wireless stations have to resend usernames and passwords in order
to stay connected.
This field is available only when you select WPA2 as security mode. If wireless station
authentication is done using a RADIUS server, the reauthentication timer on the
RADIUS server has priority.
WPA Compatible
This field is only available for WPA2. Select this if you want the Device to support WPA
and WPA2 simultaneously.
The WPA security mode is a security subset of WPA2. It requires the presence of a RADIUS server
on your network in order to validate user credentials. This encryption standard is slightly older than
WPA2 and therefore is more compatible with older devices.
Click Network Setting > Wireless to display the General screen. Select More Secure as the
security level. Then select WPA or WPA2 from the Security Mode list.
Figure 23 Wireless > General: More Secure: WPA(2)
The following table describes the labels in this screen.
Table 10 Wireless > General: More Secure: WPA(2)
Page 56

54
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Group Key Update
Timer
The Group Key Update Timer is the rate at which the RADIUS server sends a new
group key out to all clients.
Encryption
Select the encryption type for data encryption.
If you choose WPA as the security mode, the Device uses TKIP for data encryption.
If you choose WPA2 as the security mode and enable WPA-PSK Compatible, the
Device uses either TKIP and AES (TKIPAES MIX) for data encryption.
If you choose WPA2 as the security mode but disable WPA-PSK Compatible, the
Device uses AES for data encryption.
LABEL
DESCRIPTION
#
This is the index number of each SSID profile.
Active
This field indicates whether this SSID is active. A yellow bulb signifies that this SSID is active. A
gray bulb signifies that this SSID is not active.
SSID
An SSID profile is the set of parameters relating to one of the Device’s BSSs. The SSID (Service
Set IDentifier) identifies the Service Set with which a wireless device is associated.
This field displays the name of the wireless profile on the network. When a wireless client scans for
an AP to associate with, this is the name that is broadcast and seen in the wireless client utility.
Security
This field indicates the security mode of the SSID profile.
Modify
Click the Edit icon to configure the SSID profile.
Table 10 Wireless > General: More Secure: WPA(2) (continued)
5.3 The More AP Screen
This screen allows you to enable and configure multiple Basic Service Sets (BSSs) on the Device.
Click Network Setting > Wireless > More AP. The following screen displays.
Figure 24 Network Seting > Wireless > More AP
The following table describes the labels in this screen.
Table 11 Network Setting > Wireless > More AP
5.3.1 More AP Edit
Use this screen to edit an SSID profile. Click the Edit icon next to an SSID in the More AP screen.
The following screen displays.
Page 57

55
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Wireless Network Setup
Wireless
Select Enable Wireless LAN to activate wireless LAN.
Wireless Network Settings
Wireless Network Name
(SSID)
The SSID (Service Set IDentity) identifies the service set with which a wireless
device is associated. Wireless devices associating to the access point (AP) must
have the same SSID.
Enter a descriptive name (up to 32 English keyboard characters) for the wireless
LAN.
Hide SSID
Select this check box to hide the SSID in the outgoing beacon frame so a station
cannot obtain the SSID through scanning using a site survey tool.
Client Isolation
Select this to keep the wireless clients in this SSID from communicating with each
other through the Device.
MBSSID/LAN Isolation
Select this to keep the wireless clients in this SSID from communicating with clients
in other SSIDs or wired LAN devices through the Device.
Select both Client Isolation and MBSSID/LAN Isolation to allow this SSID’s
wireless clients to only connect to the Internet through the Device.
Security Level
Security Mode
Select Basic (WEP) or More Secure (WPA(2)-PSK, WPA(2)) to add security on
this wireless network. The wireless clients which want to associate to this network
must have same wireless security settings as the Device. After you select to use a
security, additional options appears in this screen.
Or you can select No Security to allow any client to associate this network without
any data encryption or authentication.
Figure 25 More AP: Edit
The following table describes the fields in this screen.
Table 12 More AP: Edit
Page 58

56
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
OK
Click OK to save your changes.
Cancel
Click Cancel to exit this screen without saving.
LABEL
DESCRIPTION
SSID
Select the SSID for which you want to configure MAC filter settings.
MAC Restrict
Mode
Define the filter action for the list of MAC addresses in the MAC Address table.
Select Disable to turn off MAC filtering.
Select Allow to permit access to the Device. MAC addresses not listed will be denied access
to the Device.
Select Deny to block access to the Device. MAC addresses not listed will be allowed to access
the Device.
MAC address List
Add new MAC
address
Click this if you want to add a new MAC address entry to the MAC filter list below.
Enter the MAC addresses of the wireless devices that are allowed or denied access to the
Device in these address fields. Enter the MAC addresses in a valid MAC address format, that
is, six hexadecimal character pairs, for example, 12:34:56:78:9a:bc.
#
This is the index number of the entry.
MAC Address
This is the MAC addresses of the wireless devices that are allowed or denied access to the
Device.
Table 12 More AP: Edit
5.4 The MAC Authentication Screen
This screen allows you to configure the Device to give exclusive access to specific devices (Allow)
or exclude specific devices from accessing the Device (Deny). Every Ethernet device has a unique
MAC (Media Access Control) address. The MAC address is assigned at the factory and consists of six
pairs of hexadecimal characters, for example, 00:A0:C5:00:00:02. You need to know the MAC
addresses of the devices to configure this screen.
Use this screen to view your Device’s MAC filter settings and add new MAC filter rules. Click
Network Setting > Wireless > MAC Authentication. The screen appears as shown.
Figure 26 Network Setting > Wireless > MAC Authentication
The following table describes the labels in this screen.
Table 13 Network Setting > Wireless > MAC Authentication
Page 59

57
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Modify
Click the Delete icon to delete the entry.
Apply
Click Apply to save your changes.
Cancel
Click Cancel to exit this screen without saving.
Table 13 Network Setting > Wireless > MAC Authentication (continued)
5.5 The WPS Screen
Use this screen to configure WiFi Protected Setup (WPS) on your Device.
WPS allows you to quickly set up a wireless network with strong security, without having to
configure security settings manually. Set up each WPS connection between two devices. Both
devices must support WPS. See Section 5.10.8.3 on page 71 for more information about WPS.
Note: The Device applies the security settings configured in the General screen (see
Section 5.2 on page 48). If you want to use the WPS feature, make sure you have
set the security mode to WPA-PSK, WPA2-PSK or No Security.
Click Network Setting > Wireless > WPS. The following screen displays. Select Enable and click
Apply to activate the WPS function. Then you can configure the WPS settings in this screen.
Figure 27 Network Setting > Wireless > WPS
Page 60

58
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
General
WPS
Select Enable to activate WPS on the Device. Otherwise, select Disable to deactivate
WPS.
Add a new device with WPS Method
Method 1 PBC
Use this section to set up a WPS wireless network using Push Button Configuration
(PBC).
WPS
Click this button to add another WPS-enabled wireless device (within wireless range of
the Device) to your wireless network. This button may either be a physical button on the
outside of device, or a menu button similar to the WPS button on this screen.
Note: You must press the other wireless device’s WPS button within two minutes of
pressing this button.
Method 2 PIN
Use this section to set up a WPS wireless network by entering the PIN of the client into
the Device.
Register
Enter the PIN of the device that you are setting up a WPS connection with and click
Register to authenticate and add the wireless device to your wireless network.
You can find the PIN either on the outside of the device, or by checking the device’s
settings.
Note: You must also activate WPS on that device within two minutes to have it present its
PIN to the Device.
WPS Configuration Summary
AP PIN
The PIN (Personal Identification Number) of the Device is shown here. Enter this PIN in
the configuration utility of the device you want to connect to using WPS.
The PIN is not necessary when you use WPS push-button method.
Click the Generate New PIN button to have the Device create a new PIN.
Status
This displays Configured when the Device has connected to a wireless network using
WPS or Enable WPS is selected and wireless or wireless security settings have been
changed. The current wireless and wireless security settings also appear in the screen.
This displays Unconfigured if WPS is disabled and there is no wireless or wireless
security changes on the Device or you click Release Configuration to remove the
configured wireless and wireless security settings.
Release
Configuration
The default WPS status is Configured.
Click this button to remove all configured wireless and wireless security settings for WPS
connections on the Device.
802.11 Mode
This field displays the Device’s wireless mode that only allows the compliant WLAN
devices to associate with it.
SSID
This field displays the SSID the Device is currently using.
Security
This field displays the security mode the Device is currently using.
Pre-Shared Key
This field displays the pre-shared key the Device uses when the security mode is set to
WPA(2)-PSK.
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
The following table describes the labels in this screen.
Table 14 Network Setting > Wireless > WPS
Page 61

59
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
WDS Security
Select the type of the key used to encrypt data between APs. All the wireless APs
(including the Device) must use the same pre-shared key for data transmission.
The option is available only when you set the security mode to WPA(2) or WPA(2)-
PSK in the Wireless > General screen.
TKIP
Select this to use TKIP (Temporal Key Integrity Protocol) encryption.
AES
Select this to use AES (Advanced Encryption Standard) encryption.
#
This is the index number of the individual WDS link.
Active
Select this to activate the link between the Device and the peer device to which this
entry refers. When you do not select the check box this link is down.
Remote Bridge
MAC Address
Type the MAC address of the peer device in a valid MAC address format (six hexadecimal
character pairs, for example 12:34:56:78:9a:bc).
PSK
Enter a Pre-Shared Key (PSK) from 8 to 63 case-sensitive ASCII characters (including
spaces and symbols).
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
5.6 The WDS Screen
An AP using the Wireless Distribution System (WDS) can function as a wireless network bridge
allowing you to wirelessly connect wired network segments. The WDS screen allows you to
configure the Device to connect to other APs wirelessly when WDS is enabled.
Use this screen to set up your WDS (Wireless Distribution System) links between the Device and
other wireless APs. You need to know the MAC address of the peer device. Once the security
settings of peer sides match one another, the connection between devices is made.
Note: WDS security is independent of the security settings between the Device and any
wireless clients.
Note: Not all APs support WDS links. Check your other AP’s documentation.
Click Network Setting > Wireless > WDS. The following screen displays.
Figure 28 Network Setting > Wireless > WDS
The following table describes the labels in this screen.
Table 15 Network Setting > Wireless > WDS
Page 62

60
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Enable WMM of
SSID1~4
Determine whether to have the Device automatically give a service a priority level
according to the ToS value in the IP header of packets it sends for a wireless network.
WMM QoS (Wifi MultiMedia Quality of Service) gives high priority to voice and video,
which makes them run more smoothly.
Apply
Click Apply to save your changes.
Cancel
Click Cancel to restore your previously saved settings.
5.7 The WMM Screen
Currently, the Wi-Fi MultiMedia (WMM) feauture of SSID1-4 is enabled and this screen is read-only.
Click Network Setting > Wireless > WMM. The following screen displays.
Figure 29 Network Setting > Wireless > WMM
The following table describes the labels in this screen.
Table 16 Network Setting > Wireless > WMM
5.8 The Scheduling Screen
Use the wireless LAN scheduling to configure the days you want to enable or disable the wireless
LAN. Click Network Setting > Wireless > Scheduling. The following screen displays.
Page 63

61
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Wireless LAN
Scheduling
Select Enable or Disable to activate or deactivate wireless LAN scheduling on your
Device.
State
Select On or Off to enable or disable the wireless LAN.
Day
Check the day(s) you want to turn the wireless LAN on or off.
Time (24-Hour
Format)
Specify a time frame during which the schedule would apply.
For example, if you set the time range from 12:00 to 23:00, the wireless LAN will be
turned on only during this time period.
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
Figure 30 Network Setting > Wireless > Scheduling
The following table describes the labels in this screen.
Table 17 Network Setting > Wireless > Scheduling
5.9 The Advanced Screen
Use this screen to configure advanced wireless settings. Click Network Setting > Wireless >
Advanced, the screen appears as shown.
See Section 5.10.2 on page 64 for detailed definitions of the terms listed in this screen.
Page 64

62
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
LABEL
DESCRIPTION
Fragmentation
Threshold
This is the maximum data fragment size that can be sent. Enter a value between 256 and
2346.
Output Power
Set the output power of the Device. If there is a high density of APs in an area, decrease
the output power to reduce interference with other APs. Select one of the following:
100%, 75%, 50% or 25%.
Preamble
Select a preamble type from the drop-down list menu. Choices are Long or Short.
802.11 Mode
Select 802.11b Only to allow only IEEE 802.11b compliant WLAN devices to associate
with the Device.
Select 802.11g Only to allow only IEEE 802.11g compliant WLAN devices to associate
with the Device.
Select 802.11b+g to allow either IEEE 802.11b or IEEE 802.11g compliant WLAN
devices to associate with the Device. The transmission rate of your Device might be
reduced.
Select 802.11n to allow only IEEE 802.11n compliant WLAN devices to associate with the
Device.
Select 802.11g+n to allow either IEEE 802.11g or IEEE 802.11n compliant WLAN
devices to associate with the Device. The transmission rate of your Device might be
reduced.
Select 802.11b+g+n to allow IEEE 802.11b, IEEE 802.11g or IEEE802.11n compliant
WLAN devices to associate with the Device. The transmission rate of your Device might
be reduced.
Channel Width
Select whether the Device uses a wireless channel width of 20MHz or Auto. If Auto is
selected, the Device will use 40MHz if it is supported.
A standard 20MHz channel offers transfer speeds of up to 150Mbps whereas a 40MHz
channel uses two standard channels and offers speeds of up to 300 Mbps.
40MHz (channel bonding or dual channel) bonds two adjacent radio channels to increase
throughput. The wireless clients must also support 40 MHz. It is often better to use the 20
MHz setting in a location where the environment hinders the wireless signal.
Select 20MHz if you want to lessen radio interference with other wireless devices in your
neighborhood or the wireless clients do not support channel bonding.
This field is available only when you set the 802.11 Mode to 802.11n or 802.11b+g+n
in the Advanced Setup screen.
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
Figure 31 Network Setting > Wireless> Advanced
The following table describes the labels in this screen.
Table 18 Network Setting > Wireless> Advanced
Page 65

63
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
5.10 Wireless LAN Technical Reference
5.10.1 Wireless Network Overview
This section discusses wireless LANs in depth. For more information, see the appendix.
Wireless networks consist of wireless clients, access points and bridges.
• A wireless client is a radio connected to a user’s computer.
• An access point is a radio with a wired connection to a network, which can connect with
numerous wireless clients and let them access the network.
• A bridge is a radio that relays communications between access points and wireless clients,
extending a network’s range.
Traditionally, a wireless network operates in one of two ways.
• An “infrastructure” type of network has one or more access points and one or more wireless
clients. The wireless clients connect to the access points.
• An “ad-hoc” type of network is one in which there is no access point. Wireless clients connect to
one another in order to exchange information.
The following figure provides an example of a wireless network.
Figure 32 Example of a Wireless Network
The wireless network is the part in the blue circle. In this wireless network, devices A and B use the
access point (AP) to interact with the other devices (such as the printer) or with the Internet. Your
Device is the AP.
Page 66

64
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
TERM
DESCRIPTION
Preamble
A preamble affects the timing in your wireless network. There are two preamble
modes: long and short. If a device uses a different preamble mode than the Device
does, it cannot communicate with the Device.
Authentication
The process of verifying whether a wireless device is allowed to use the wireless
network.
Fragmentation
Threshold
A small fragmentation threshold is recommended for busy networks, while a larger
threshold provides faster performance if the network is not very busy.
Every wireless network must follow these basic guidelines.
• Every device in the same wireless network must use the same SSID.
The SSID is the name of the wireless network. It stands for Service Set IDentifier.
• If two wireless networks overlap, they should use a different channel.
Like radio stations or television channels, each wireless network uses a specific channel, or
frequency, to send and receive information.
• Every device in the same wireless network must use security compatible with the AP.
Security stops unauthorized devices from using the wireless network. It can also protect the
information that is sent in the wireless network.
Radio Channels
In the radio spectrum, there are certain frequency bands allocated for unlicensed, civilian use. For
the purposes of wireless networking, these bands are divided into numerous channels. This allows a
variety of networks to exist in the same place without interfering with one another. When you
create a network, you must select a channel to use.
Since the available unlicensed spectrum varies from one country to another, the number of
available channels also varies.
5.10.2 Additional Wireless Terms
The following table describes some wireless network terms and acronyms used in the Device’s Web
Configurator.
Table 19 Additional Wireless Terms
5.10.3 Wireless Security Overview
By their nature, radio communications are simple to intercept. For wireless data networks, this
means that anyone within range of a wireless network without security can not only read the data
passing over the airwaves, but also join the network. Once an unauthorized person has access to
the network, he or she can steal information or introduce malware (malicious software) intended to
compromise the network. For these reasons, a variety of security systems have been developed to
ensure that only authorized people can use a wireless data network, or understand the data carried
on it.
These security standards do two things. First, they authenticate. This means that only people
presenting the right credentials (often a username and password, or a “key” phrase) can access the
network. Second, they encrypt. This means that the information sent over the air is encoded. Only
Page 67

65
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
people with the code key can understand the information, and only people who have been
authenticated are given the code key.
These security standards vary in effectiveness. Some can be broken, such as the old Wired
Equivalent Protocol (WEP). Using WEP is better than using no security at all, but it will not keep a
determined attacker out. Other security standards are secure in themselves but can be broken if a
user does not use them properly. For example, the WPA-PSK security standard is very secure if you
use a long key which is difficult for an attacker’s software to guess - for example, a twenty-letter
long string of apparently random numbers and letters - but it is not very secure if you use a short
key which is very easy to guess - for example, a three-letter word from the dictionary.
Because of the damage that can be done by a malicious attacker, it’s not just people who have
sensitive information on their network who should use security. Everybody who uses any wireless
network should ensure that effective security is in place.
A good way to come up with effective security keys, passwords and so on is to use obscure
information that you personally will easily remember, and to enter it in a way that appears random
and does not include real words. For example, if your mother owns a 1970 Dodge Challenger and
her favorite movie is Vanishing Point (which you know was made in 1971) you could use
“70dodchal71vanpoi” as your security key.
The following sections introduce different types of wireless security you can set up in the wireless
network.
5.10.3.1 SSID
Normally, the Device acts like a beacon and regularly broadcasts the SSID in the area. You can hide
the SSID instead, in which case the Device does not broadcast the SSID. In addition, you should
change the default SSID to something that is difficult to guess.
This type of security is fairly weak, however, because there are ways for unauthorized wireless
devices to get the SSID. In addition, unauthorized wireless devices can still see the information that
is sent in the wireless network.
5.10.3.2 MAC Address Filter
Every device that can use a wireless network has a unique identification number, called a MAC
address.1 A MAC address is usually written using twelve hexadecimal characters2; for example,
00A0C5000002 or 00:A0:C5:00:00:02. To get the MAC address for each device in the wireless
network, see the device’s User’s Guide or other documentation.
You can use the MAC address filter to tell the Device which devices are allowed or not allowed to
use the wireless network. If a device is allowed to use the wireless network, it still has to have the
correct information (SSID, channel, and security). If a device is not allowed to use the wireless
network, it does not matter if it has the correct information.
This type of security does not protect the information that is sent in the wireless network.
Furthermore, there are ways for unauthorized wireless devices to get the MAC address of an
authorized device. Then, they can use that MAC address to use the wireless network.
1. Some wireless devices, such as scanners, can detect wireless networks but cannot use wireless networks. These kinds
of wireless devices might not have MAC addresses.
2. Hexadecimal characters are 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, and F.
Page 68

66
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
No Authentication
RADIUS Server
Weakest
No Security
WPA
Static WEP
WPA-PSK
Strongest
WPA2-PSK
WPA2
5.10.3.3 User Authentication
Authentication is the process of verifying whether a wireless device is allowed to use the wireless
network. You can make every user log in to the wireless network before using it. However, every
device in the wireless network has to support IEEE 802.1x to do this.
For wireless networks, you can store the user names and passwords for each user in a RADIUS
server. This is a server used in businesses more than in homes. If you do not have a RADIUS server,
you cannot set up user names and passwords for your users.
Unauthorized wireless devices can still see the information that is sent in the wireless network,
even if they cannot use the wireless network. Furthermore, there are ways for unauthorized
wireless users to get a valid user name and password. Then, they can use that user name and
password to use the wireless network.
5.10.3.4 Encryption
Wireless networks can use encryption to protect the information that is sent in the wireless
network. Encryption is like a secret code. If you do not know the secret code, you cannot
understand the message.
The types of encryption you can choose depend on the type of authentication. (See Section
5.10.3.3 on page 66 for information about this.)
Table 20 Types of Encryption for Each Type of Authentication
For example, if the wireless network has a RADIUS server, you can choose WPA or WPA2. If users
do not log in to the wireless network, you can choose no encryption, Static WEP, WPA-PSK, or
WPA2-PSK.
Usually, you should set up the strongest encryption that every device in the wireless network
supports. For example, suppose you have a wireless network with the Device and you do not have
a RADIUS server. Therefore, there is no authentication. Suppose the wireless network has two
devices. Device A only supports WEP, and device B supports WEP and WPA-PSK. Therefore, you
should set up Static WEP in the wireless network.
Note: It is recommended that wireless networks use WPA-PSK, WPA, or stronger
encryption. The other types of encryption are better than none at all, but it is still
possible for unauthorized wireless devices to figure out the original information
pretty quickly.
When you select WPA2 or WPA2-PSK in your Device, you can also select an option (WPA
compatible) to support WPA as well. In this case, if some of the devices support WPA and some
support WPA2, you should set up WPA2-PSK or WPA2 (depending on the type of wireless network
login) and select the WPA compatible option in the Device.
Page 69

67
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
Many types of encryption use a key to protect the information in the wireless network. The longer
the key, the stronger the encryption. Every device in the wireless network must have the same key.
5.10.4 Signal Problems
Because wireless networks are radio networks, their signals are subject to limitations of distance,
interference and absorption.
Problems with distance occur when the two radios are too far apart. Problems with interference
occur when other radio waves interrupt the data signal. Interference may come from other radio
transmissions, such as military or air traffic control communications, or from machines that are
coincidental emitters such as electric motors or microwaves. Problems with absorption occur when
physical objects (such as thick walls) are between the two radios, muffling the signal.
5.10.5 BSS
A Basic Service Set (BSS) exists when all communications between wireless stations or between a
wireless station and a wired network client go through one access point (AP).
Intra-BSS traffic is traffic between wireless stations in the BSS. When Intra-BSS traffic blocking is
disabled, wireless station A and B can access the wired network and communicate with each other.
When Intra-BSS traffic blocking is enabled, wireless station A and B can still access the wired
network but cannot communicate with each other.
Figure 33 Basic Service set
Page 70

68
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
5.10.6 MBSSID
Traditionally, you need to use different APs to configure different Basic Service Sets (BSSs). As well
as the cost of buying extra APs, there is also the possibility of channel interference. The Device’s
MBSSID (Multiple Basic Service Set IDentifier) function allows you to use one access point to
provide several BSSs simultaneously. You can then assign varying QoS priorities and/or security
modes to different SSIDs.
Wireless devices can use different BSSIDs to associate with the same AP.
5.10.6.1 Notes on Multiple BSSs
• A maximum of eight BSSs are allowed on one AP simultaneously.
• You must use different keys for different BSSs. If two wireless devices have different BSSIDs
(they are in different BSSs), but have the same keys, they may hear each other’s
communications (but not communicate with each other).
• MBSSID should not replace but rather be used in conjunction with 802.1x security.
5.10.7 Wireless Distribution System (WDS)
The Device can act as a wireless network bridge and establish WDS (Wireless Distribution System)
links with other APs. You need to know the MAC addresses of the APs you want to link to. Once the
security settings of peer sides match one another, the connection between devices is made.
At the time of writing, WDS security is not compatible with all access points. Refer to your other
access point’s documentation for details.
The following figure illustrates how WDS link works between APs. Notebook computer A is a
wireless client connecting to access point AP 1. AP 1 has no wired Internet connection, but it can
establish a WDS link with access point AP 2, which has a wired Internet connection. When AP 1
has a WDS link with AP 2, the notebook computer can access the Internet through AP 2.
Figure 34 WDS Link Example
A
WDS
AP 1
5.10.8 WiFi Protected Setup (WPS)
Your Device supports WiFi Protected Setup (WPS), which is an easy way to set up a secure wireless
network. WPS is an industry standard specification, defined by the WiFi Alliance.
WPS allows you to quickly set up a wireless network with strong security, without having to
configure security settings manually. Each WPS connection works between two devices. Both
devices must support WPS (check each device’s documentation to make sure).
Depending on the devices you have, you can either press a button (on the device itself, or in its
configuration utility) or enter a PIN (a unique Personal Identification Number that allows one device
to authenticate the other) in each of the two devices. When WPS is activated on a device, it has two
AP 2
Page 71

69
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
minutes to find another device that also has WPS activated. Then, the two devices connect and set
up a secure network by themselves.
5.10.8.1 Push Button Configuration
WPS Push Button Configuration (PBC) is initiated by pressing a button on each WPS-enabled
device, and allowing them to connect automatically. You do not need to enter any information.
Not every WPS-enabled device has a physical WPS button. Some may have a WPS PBC button in
their configuration utilities instead of or in addition to the physical button.
Take the following steps to set up WPS using the button.
1 Ensure that the two devices you want to set up are within wireless range of one another.
2 Look for a WPS button on each device. If the device does not have one, log into its configuration
utility and locate the button (see the device’s User’s Guide for how to do this - for the Device, see
Section 5.6 on page 59).
3 Press the button on one of the devices (it doesn’t matter which). For the Device you must press the
WPS button for more than three seconds.
4 Within two minutes, press the button on the other device. The registrar sends the network name
(SSID) and security key through an secure connection to the enrollee.
If you need to make sure that WPS worked, check the list of associated wireless clients in the AP’s
configuration utility. If you see the wireless client in the list, WPS was successful.
5.10.8.2 PIN Configuration
Each WPS-enabled device has its own PIN (Personal Identification Number). This may either be
static (it cannot be changed) or dynamic (in some devices you can generate a new PIN by clicking
on a button in the configuration interface).
Use the PIN method instead of the push-button configuration (PBC) method if you want to ensure
that the connection is established between the devices you specify, not just the first two devices to
activate WPS in range of each other. However, you need to log into the configuration interfaces of
both devices to use the PIN method.
When you use the PIN method, you must enter the PIN from one device (usually the wireless client)
into the second device (usually the Access Point or wireless router). Then, when WPS is activated
on the first device, it presents its PIN to the second device. If the PIN matches, one device sends
the network and security information to the other, allowing it to join the network.
Take the following steps to set up a WPS connection between an access point or wireless router
(referred to here as the AP) and a client device using the PIN method.
1 Ensure WPS is enabled on both devices.
2 Access the WPS section of the AP’s configuration interface. See the device’s User’s Guide for how to
do this.
Page 72

70
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
3 Look for the client’s WPS PIN; it will be displayed either on the device, or in the WPS section of the
client’s configuration interface (see the device’s User’s Guide for how to find the WPS PIN - for the
Device, see Section 5.5 on page 57).
4 Enter the client’s PIN in the AP’s configuration interface.
5 If the client device’s configuration interface has an area for entering another device’s PIN, you can
either enter the client’s PIN in the AP, or enter the AP’s PIN in the client - it does not matter which.
6 Start WPS on both devices within two minutes.
7 Use the configuration utility to activate WPS, not the push-button on the device itself.
8 On a computer connected to the wireless client, try to connect to the Internet. If you can connect,
WPS was successful.
If you cannot connect, check the list of associated wireless clients in the AP’s configuration utility. If
you see the wireless client in the list, WPS was successful.
The following figure shows a WPS-enabled wireless client (installed in a notebook computer)
connecting to the WPS-enabled AP via the PIN method.
Page 73

71
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
Figure 35 Example WPS Process: PIN Method
ENROLLEE
5.10.8.3 How WPS Works
When two WPS-enabled devices connect, each device must assume a specific role. One device acts
as the registrar (the device that supplies network and security settings) and the other device acts
as the enrollee (the device that receives network and security settings. The registrar creates a
secure EAP (Extensible Authentication Protocol) tunnel and sends the network name (SSID) and the
WPA-PSK or WPA2-PSK pre-shared key to the enrollee. Whether WPA-PSK or WPA2-PSK is used
depends on the standards supported by the devices. If the registrar is already part of a network, it
sends the existing information. If not, it generates the SSID and WPA(2)-PSK randomly.
The following figure shows a WPS-enabled client (installed in a notebook computer) connecting to a
WPS-enabled access point.
This
device’s
123456
WPS
PIN
device:
START
WPS PIN:
Enter WPS
from other
WPS
WITHIN 2 MINUTES
SECURE EAP TUNNEL
SSID
WPA(2)-PSK
COMMUNICATION
WPS
START
REGISTRAR
WPS
Page 74

72
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
Figure 36 How WPS works
ACTIVATE
WPS
ENROLLEE
The roles of registrar and enrollee last only as long as the WPS setup process is active (two
minutes). The next time you use WPS, a different device can be the registrar if necessary.
The WPS connection process is like a handshake; only two devices participate in each WPS
transaction. If you want to add more devices you should repeat the process with one of the existing
networked devices and the new device.
Note that the access point (AP) is not always the registrar, and the wireless client is not always the
enrollee. All WPS-certified APs can be a registrar, and so can some WPS-enabled wireless clients.
By default, a WPS devices is “unconfigured”. This means that it is not part of an existing network
and can act as either enrollee or registrar (if it supports both functions). If the registrar is
unconfigured, the security settings it transmits to the enrollee are randomly-generated. Once a
WPS-enabled device has connected to another device using WPS, it becomes “configured”. A
configured wireless client can still act as enrollee or registrar in subsequent WPS connections, but a
configured access point can no longer act as enrollee. It will be the registrar in all subsequent WPS
connections in which it is involved. If you want a configured AP to act as an enrollee, you must reset
it to its factory defaults.
5.10.8.4 Example WPS Network Setup
This section shows how security settings are distributed in an example WPS setup.
The following figure shows an example network. In step 1, both AP1 and Client 1 are
unconfigured. When WPS is activated on both, they perform the handshake. In this example, AP1
is the registrar, and Client 1 is the enrollee. The registrar randomly generates the security
information to set up the network, since it is unconfigured and has no existing information.
WITHIN 2 MINUTES
WPS HANDSHAKE
SECURE TUNNEL
SECURITY INFO
COMMUNICATION
ACTIVATE
WPS
REGISTRAR
Page 75

73
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
Figure 37 WPS: Example Network Step 1
ENROLLEE
REGISTRAR
CLIENT 1
SECURITY INFO
AP1
In step 2, you add another wireless client to the network. You know that Client 1 supports registrar
mode, but it is better to use AP1 for the WPS handshake with the new client since you must
connect to the access point anyway in order to use the network. In this case, AP1 must be the
registrar, since it is configured (it already has security information for the network). AP1 supplies
the existing security information to Client 2.
Figure 38 WPS: Example Network Step 2
EXISTING CONNECTION
REGISTRAR
CLIENT 1
ENROLLEE
AP1
CLIENT 2
In step 3, you add another access point (AP2) to your network. AP2 is out of range of AP1, so you
cannot use AP1 for the WPS handshake with the new access point. However, you know that Client
2 supports the registrar function, so you use it to perform the WPS handshake instead.
Page 76

74
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
Figure 39 WPS: Example Network Step 3
EXISTING CONNECTION
CLIENT 1
REGISTRAR
CLIENT 2
5.10.8.5 Limitations of WPS
WPS has some limitations of which you should be aware.
• WPS works in Infrastructure networks only (where an AP and a wireless client communicate). It
does not work in Ad-Hoc networks (where there is no AP).
• When you use WPS, it works between two devices only. You cannot enroll multiple devices
simultaneously, you must enroll one after the other.
For instance, if you have two enrollees and one registrar you must set up the first enrollee (by
pressing the WPS button on the registrar and the first enrollee, for example), then check that it
successfully enrolled, then set up the second device in the same way.
• WPS works only with other WPS-enabled devices. However, you can still add non-WPS devices to
a network you already set up using WPS.
WPS works by automatically issuing a randomly-generated WPA-PSK or WPA2-PSK pre-shared
key from the registrar device to the enrollee devices. Whether the network uses WPA-PSK or
WPA2-PSK depends on the device. You can check the configuration interface of the registrar
device to discover the key the network is using (if the device supports this feature). Then, you
can enter the key into the non-WPS device and join the network as normal (the non-WPS device
must also support WPA-PSK or WPA2-PSK).
• When you use the PBC method, there is a short period (from the moment you press the button
on one device to the moment you press the button on the other device) when any WPS-enabled
device could join the network. This is because the registrar has no way of identifying the
“correct” enrollee, and cannot differentiate between your enrollee and a rogue device. This is a
possible way for a hacker to gain access to a network.
You can easily check to see if this has happened. WPS works between only two devices
simultaneously, so if another device has enrolled your device will be unable to enroll, and will not
have access to the network. If this happens, open the access point’s configuration interface and
look at the list of associated clients (usually displayed by MAC address). It does not matter if the
AP1
ENROLLEE
AP2
Page 77

75
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
access point is the WPS registrar, the enrollee, or was not involved in the WPS handshake; a
rogue device must still associate with the access point to gain access to the network. Check the
MAC addresses of your wireless clients (usually printed on a label on the bottom of the device). If
there is an unknown MAC address you can remove it or reset the AP.
Page 78

76
eircom D1000 modem User’s Guide
Chapter 5 Wireless LAN
Page 79

77
eircom D1000 modem User’s Guide
6
6.1 Overview
A Local Area Network (LAN) is a shared communication system to which many networking devices
are connected. It is usually located in one immediate area such as a building or floor of a building.
6.1.1 What You Can Do in the LAN
Use the LAN screens to help you configure a LAN DHCP server and manage IP addresses.
LAN
• Use the LAN Setup screen to set the LAN IP address, subnet mask, and DHCP settings of your
Device (Section 6.2 on page 79).
• Use the Static DHCP screen to assign IP addresses on the LAN to specific individual computers
based on their MAC Addresses (Section 6.3 on page 81).
• Use the IP Alias screen (Section 6.6 on page 84) to change your Device’s IP alias settings.
• Use the UPnP screen to enable UPnP and UPnP NAT traversal on the Device (Section 6.5 on page
83).
• Use the IPv6 LAN Setup screen (Section 6.6 on page 84) to configure the IPv6 settings on your
Device’s LAN interface.
• Use the File Sharing screen (Section 6.7 on page 88) to set up file sharing via the Device.
• Use the Print Server screen (Section 6.8 on page 91) to enable the print server function on the
Device.
Screens
Home Networking
DSL
Page 80

78
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
6.1.2 What You Need To Know
6.1.2.1 About LAN
IP Address
IP addresses identify individual devices on a network. Every networking device (including
computers, servers, routers, printers, etc.) needs an IP address to communicate across the
network. These networking devices are also known as hosts.
Subnet Mask
Subnet masks determine the maximum number of possible hosts on a network. You can also use
subnet masks to divide one network into multiple sub-networks.
DHCP
A DHCP (Dynamic Host Configuration Protocol) server can assign your Device an IP address, subnet
mask, DNS and other routing information when it's turned on.
DNS
DNS (Domain Name System) is for mapping a domain name to its corresponding IP address and
vice versa. The DNS server is extremely important because without it, you must know the IP
address of a networking device before you can access it.
6.1.2.2 About UPnP
Identifying UPnP Devices
UPnP hardware is identified as an icon in the Network Connections folder (Windows XP). Each UPnP
compatible device installed on your network will appear as a separate icon. Selecting the icon of a
UPnP device will allow you to access the information and properties of that device.
NAT Traversal
UPnP NAT traversal automates the process of allowing an application to operate through NAT. UPnP
network devices can automatically configure network addressing, announce their presence in the
network to other UPnP devices and enable exchange of simple product and service descriptions.
NAT traversal allows the following:
• Dynamic port mapping
• Learning public IP addresses
• Assigning lease times to mappings
Windows Messenger is an example of an application that supports NAT traversal and UPnP.
Page 81

79
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
Cautions with UPnP
The automated nature of NAT traversal applications in establishing their own services and opening
firewall ports may present network security issues. Network information and configuration may also
be obtained and modified by users in some network environments.
When a UPnP device joins a network, it announces its presence with a multicast message. For
security reasons, the Device allows multicast messages on the LAN only.
All UPnP-enabled devices may communicate freely with each other without additional configuration.
Disable UPnP if this is not your intention.
Finding Out More
See Section 6.11 on page 103 for technical background information on LANs.
6.1.3 Before You Begin
Find out the MAC addresses of your network devices if you intend to add them to the DHCP Client
List screen.
6.2 The LAN Setup Screen
Use this screen to set the Local Area Network IP address, subnet mask and advanced networking
settings such as RIP, multicast of your Device. Click Network Setting > Home Networking to
open the LAN Setup screen.
Page 82

80
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
LAN IP Setup
IP Address
Enter the LAN IP address you want to assign to your Device in dotted decimal
notation, for example, 192.168.1.254 (factory default).
Subnet Mask
Type the subnet mask of your network in dotted decimal notation, for example
255.255.255.0 (factory default). Your Device automatically computes the subnet mask
based on the IP Address you enter, so do not change this field unless you are
instructed to do so.
RIP Version
RIP (Routing Information Protocol) allows a router to exchange routing information
with other routers. Select the RIP version from RIP1 and RIP2-B/RIP2-M.
Direction
Use this field to control how much routing information the VDSL Router sends and
receives on the subnet. Select the RIP Direction from None, Both, IN Only and
OUT Only.
Multicast
IGMP (Internet Group Multicast Protocol) is a network-layer protocol used to establish
membership in a multicast group. The Device supports IGMP v1/IGMP v2/IGMP
v3. Select None to disable it.
IGMP Snooping
Select Enabled to activate IGMP Snooping. This allows the Device to passively learn
memberships in multicast groups. Otherwise, select Disabled to deactivate it.
DHCP Server State
Figure 40 Network Setting > Home Networking > LAN Setup
The following table describes the fields in this screen.
Table 21 Network Setting > Home Networking > LAN Setup
Page 83

81
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
DHCP
If set to Enable, your Device can assign IP addresses, an IP default gateway and DNS
servers to Windows 95, Windows NT and other systems that support the DHCP client.
If set to Disable, the DHCP server will be disabled.
If set to DHCP Relay, the Device acts as a surrogate DHCP server and relays DHCP
requests and responses between the remote server and the clients. Enter the IP
address of the actual, remote DHCP server in the Remote DHCP Server field in this
case.
When DHCP is used, the following items need to be set:
IP Addressing Values
IP Pool Starting
Address
This field specifies the first of the contiguous addresses in the IP address pool.
Pool Size
This field specifies the size, or count of the IP address pool.
DHCP Server Lease Time
Lease Time
This field specifies the lease time in seconds of an IP address assigned by the DHCP
server.
DNS Values
DNS Server 1
DNS Server 2
Select Obtained From ISP if your ISP dynamically assigns DNS server information
(and the Device's WAN IP address).
Select UserDefined if you have the IP address of a DNS server. Enter the DNS
server's IP address in the field to the right. If you chose UserDefined, but leave the
IP address set to 0.0.0.0, UserDefined changes to None after you click Apply. If you
set a second choice to UserDefined, and enter the same IP address, the second
UserDefined changes to None after you click Apply.
Select DNS Relay to have the Device act as a DNS proxy only when the ISP uses IPCP
DNS server extensions. The Device's LAN IP address displays in the field to the right
(read-only). The Device tells the DHCP clients on the LAN that the Device itself is the
DNS server. When a computer on the LAN sends a DNS query to the Device, the
Device forwards the query to the real DNS server learned through IPCP and relays the
response back to the computer. You can only select DNS Relay for one of the three
servers; if you select DNS Relay for a second server, that choice changes to None
after you click Apply.
Select None if you do not want to configure DNS servers. You must have another
DHCP sever on your LAN, or else the computers must have their DNS server addresses
manually configured. If you do not configure a DNS server, you must know the IP
address of a computer in order to access it.
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
Table 21 Network Setting > Home Networking > LAN Setup (continued)
6.3 The Static DHCP Screen
This table allows you to assign IP addresses on the LAN to specific individual computers based on
their MAC Addresses.
Every Ethernet device has a unique MAC (Media Access Control) address. The MAC address is
assigned at the factory and consists of six pairs of hexadecimal characters, for example,
00:A0:C5:00:00:02.
Page 84

82
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
Add new static lease
Click this to add a new static DHCP entry.
#
This is the index number of the entry.
Active
This field displays whether the client is connected to the Device.
MAC Address
The MAC (Media Access Control) or Ethernet address on a LAN (Local Area Network) is
unique to your computer (six pairs of hexadecimal notation).
A network interface card such as an Ethernet adapter has a hardwired address that is
assigned at the factory. This address follows an industry standard that ensures no other
adapter has a similar address.
IP Address
This field displays the IP address relative to the # field listed above.
Modify
Click the Edit icon to have the IP address field editable and change it.
Click the Delete icon to delete a static DHCP entry. A window displays asking you to
confirm that you want to delete the selected entry.
LABEL
DESCRIPTION
MAC Address
If you select Manual Input in the Select Device Info field, enter the MAC address of
a computer on your LAN.
IP Address
If you select Manual Input in the Select Device Info field, enter the IP address that
you want to assign to the computer on your LAN with the MAC address that you will
also specify.
OK
Click OK to save your changes.
Cancel
Click Cancel to exit this screen without saving.
Use this screen to change your Device’s static DHCP settings. Click Network Setting > Home
Networking > Static DHCP to open the following screen.
Figure 41 Network Setting > Home Networking > Static DHCP
The following table describes the labels in this screen.
Table 22 Network Setting > Home Networking > Static DHCP
If you click Add new static lease in the Static DHCP screen or the Edit icon next to a static DHCP
entry, the following screen displays.
Figure 42 Static DHCP: Add/Edit
The following table describes the labels in this screen.
Table 23 Static DHCP: Add/Edit
Page 85

83
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
IP Alias
Select Enable to configure a LAN network for the Device.
IP Address
Enter the IP address of your Device in dotted decimal notation.
IP Subnet Mask
Your Device will automatically calculate the subnet mask based on the IP address that
you assign. Unless you are implementing subnetting, use the subnet mask computed by
the Device.
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
6.4 The IP Alias Screen
IP alias allows you to partition a physical network into different logical networks over the same
Ethernet interface. The Device supports multiple logical LAN interfaces via its physical Ethernet
interface with the Device itself as the gateway for the LAN network.
When you use IP alias, you can also configure firewall rules to control access to the LAN's logical
6.4.1 Configuring the LAN IP Alias Screen
network (subnet).
Use this screen to change your Device’s IP alias settings. Click Network Setting > Home
Networking > IP Alias to open the following screen.
Figure 43 Network Setting > Home Networking > IP Alias
The following table describes the labels in this screen.
Table 24 Network Setting > Home Networking > IP Alias
6.5 The UPnP Screen
Universal Plug and Play (UPnP) is a distributed, open networking standard that uses TCP/IP for
simple peer-to-peer network connectivity between devices. A UPnP device can dynamically join a
network, obtain an IP address, convey its capabilities and learn about other devices on the network.
In turn, a device can leave a network smoothly and automatically when it is no longer in use.
See page 78 for more information on UPnP.
Use the following screen to enable or disable the UPnP function on your Device. Click Network
Setting > Home Networking > UPnP to display the screen shown next.
Page 86

84
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
UPnP
Select Enable to activate UPnP. Be aware that anyone could use a UPnP application to
open the web configurator's login screen without entering the Device's IP address
(although you must still enter the password to access the web configurator). Otherwise,
select Disable to deactivate UPnP.
Apply
Click Apply to save your changes.
Cancel
Click Cancel to exit this screen without saving.
Figure 44 Network Setting > Home Networking > UPnP
The following table describes the labels in this screen.
Table 25 Network Setting > Home Networking > UPnP
6.6 The IPv6 LAN Setup Screen
Use this screen to configure the IPv6 settings for your Device’s LAN interface.
Page 87

85
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
Figure 45 Network Setting > Home Networking > IPv6 LAN Setup
Page 88

86
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
IPv6 LAN Setup
Link Local Address
Type
Select Manual to manually enter a link local address. Select EUI64 to use the EUI-64
format to generate a link local address from the Ethernet MAC address.
IPv6 Address
If you selected Manual in the Link Local Address Type field, enter the LAN IPv6
address you want to assign to your Device in hexadecimal notation, for example,
fe80::1 (factory default).
Prefix
Enter the address prefix to specify how many most significant bits in an IPv6 address
compose the network address.
MLD Snooping
Multicast Listener Discovery (MLD) allows an IPv6 switch or router to discover the
presence of MLD hosts who wish to receive multicast packets and the IP addresses of
multicast groups the hosts want to join on its network. Select Enabled to activate
MLD Snooping on the Device. This allows the Device to check MLD packets passing
through it and learn the multicast group membership. It helps reduce multicast traffic.
Lan Global Identifier
Type
Select Manual to manually enter a LAN Identifier as the interface ID to identify the
LAN interface. The LAN Identifier is appended to the IPv6 address prefix to create the
routable global IPv6 address. Select EUI64 to use the EUI-64 format to generate an
interface ID from the Ethernet MAC address.
Lan Identifier
If you selected Manual, enter the LAN Identifier in this field. The LAN identifier should
be unique and 64 bits in hexadecimal form. Every 16 bit block should be separated by
a colon as in XXXX:XXXX:XXXX:XXXX where X is a hexadecimal character. Blocks of
zeros can be represented with double colons as in XXXX:XXXX::XXXX.
LAN IPv6 Address Setting
Delegate prefix from
WAN
Select this option to automatically obtain an IPv6 network prefix from the service
provider or an uplink router.
Static
Select this option to configure a fixed IPv6 address for the Device’s LAN IPv6 address.
Static IPv6 Address
Prefix
If you select static IPv6 address, enter the IPv6 address prefix that the Device uses for
the LAN IPv6 address.
Prefix length
If you select static IPv6 address, enter the IPv6 prefix length that the Device uses to
generate the LAN IPv6 address.
An IPv6 prefix length specifies how many most significant bits (starting from the left)
in the address compose the network address. This field displays the bit number of the
IPv6 subnet mask.
Preferred Lifetime
Enter the preferred lifetime for the prefix.
Valid Lifetime
Enter the valid lifetime for the prefix.
RADVD Setup
Send RA on
Select this to have the Device send router advertisement messages to the LAN hosts.
Router advertisement is a response to a router solicitation or a periodical multicast
advertisement from a router to advertise its presence and other parameters, such as
IPv6 prefix and DNS information.
Router solicitation is a request from a host to locate a router that can act as the
default router and forward packets.
Note: The LAN hosts neither generate global IPv6 addresses nor communicate with
other networks if you disable this feature.
Delegate M/O flag
from WAN
Select this to have the Device obtain the M/O (Managed/Other) flag setting from the
service provider or uplink router.
Manual
Select this to specify the M/O flag setting manually.
The following table describes the labels in this screen.
Table 26 Network Setting > Home Networking > IPv6 LAN Setup
Page 89

87
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
Managed config
flag on
Select this to have the Device indicate to hosts to obtain network settings (such as
prefix and DNS settings) through DHCPv6.
Clear this to have the Device indicate to hosts that DHCPv6 is not available and they
should use the prefix in the router advertisement message.
Other config flag
on
Select this to have the Device indicate to hosts to obtain DNS information through
DHCPv6.
Clear this to have the Device indicate to hosts that DNS information is not available in
this network.
Advertisement
interval option on
Select this to have the Router Advertisement messages the VDSL Router
sends specify the allowed interval between Router Advertisement messages.
Hop limit
Enter the maximum number of network segments that a packet can cross before
reaching the destination. When forwarding an IPv6 packet, IPv6 routers are required
to decrease the Hop Limit by 1 and to discard the IPv6 packet when the Hop Limit is 0.
Possible value for this field are 0-255.
Router Lifetime
Enter the time in seconds that hosts should consider the Device to be the default
router. Possible values for this field are 0-9000.
Router Preference
Select the router preference (Low, Medium or High) for the Device. The Device
sends this preference in the router advertisements to tell hosts what preference they
should use for the Device. This helps hosts to choose their default router especially
when there are multiple IPv6 router in the network.
Note: Make sure the hosts also support router preference to make this function work.
Reachable Time (ms)
Enter the time in milliseconds that can elapse before a neighbor is detected. Possible
values for this field are 0-3600000.
Retrans Timer (ms)
Enter the time in milliseconds between neighbor solicitation packet retransmissions.
Possible values for this field are 1000-4294967295.
RA Interval
Enter the time in seconds between router advertisement messages. Possible values for
this field are 4-1800.
Delegate MTU from
WAN
Select this to have the Device obtain the MTU setting from the service provider or
uplink router.
Manual
Select this to specify the MTU manually.
MTU
The Maximum Transmission Unit. Type the maximum size of each IPv6 data packet, in
bytes, that can move through this interface. If a larger packet arrives, the Device
divides it into smaller fragments.
DAD attempts
Specify the number of DAD (Duplicate Address Detection) attempts before an IPv6
address is assigned to the Device LAN interface. Possible values for this field are 1-7.
DHCPv6
DHCPv6 Server
Use this field to Enable or Disable DHCPv6 server on the Device.
DNSv6 Mode
Select the DNS role (Proxy or Relay) that you want the Device to act in the IPv6 LAN
network. Alternatively, select Manual and specify the DNS servers’ IPv6 address in the
fields below.
Primary DNS
This field is available if you choose Manual as the DNSv6 mode. Enter the first DNS
server IPv6 address the Device passes to the DHCP clients.
Secondary DNS
This field is available if you choose Manual as the DNSv6 mode. Enter the second DNS
server IPv6 address the Device passes to the DHCP clients.
Information refresh
time
Enter the number of seconds a DHCPv6 client should wait before refreshing
information retrieved from DHCPv6.
Apply
Click this to save your changes.
Cancel
Click this to restore your previously saved settings.
Table 26 Network Setting > Home Networking > IPv6 LAN Setup (continued)
Page 90

88
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
6.7 The File Sharing Screen
Share files on a USB memory stick or hard drive connected to your Device with users on your
network. The following figure is an overview of the Device’s file server feature. Computers A and B
can access files on a USB device (C) which is connected to the Device.
6.7.1 What You Need to
Figure 46 File Sharing Overview
B
A
Know
Workgroup name
This is the name given to a set of computers that are connected on a network and share resources
such as a printer or files. Windows automatically assigns the workgroup name when you set up a
network.
Shares
When settings are set to default, each USB device connected to the Device is given a folder, called
a “share”. If a USB hard drive connected to the Device has more than one partition, then each
partition will be allocated a share. You can also configure a “share” to be a sub-folder or file on the
USB device.
File Systems
A file system is a way of storing and organizing files on your hard drive and storage device. Often
different operating systems such as Windows or Linux have different file systems. The file-sharing
feature on your Device supports File Allocation Table (FAT) and FAT32 file systems.
Windows/CIFS
Common Internet File System (CIFS) is a standard protocol supported by most operating systems
in order to share files across the network.
C
Page 91

89
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
CIFS runs over TCP/IP but uses the SMB (Server Message Block) protocol found in Microsoft
Windows for file and printer access; therefore, CIFS will allow all applications, not just Web
browsers, to open and share files across the Internet.
The Device uses Common Internet File System (CIFS) protocol for its file sharing functions. CIFS
compatible computers can access the USB file storage devices connected to the Device. CIFS
protocol is supported on Microsoft Windows, Linux Samba and other operating systems (refer to
your systems specifications for CIFS compatibility).
NFS
Network File System (NFS) is a protocol most commonly used on Unix-like systems in order to
share files across the network.
Samba
SMB is a client-server protocol used by Microsoft Windows systems for sharing files, printers, and
so on.
Samba is a free SMB server that runs on most Unix and Unix-like systems. It provides an
implementation of an SMB client and server for use with non-Microsoft operating systems.
File Transfer Protocol
This is a method of transferring data from one computer to another over a network such as the
6.7.2 Before You
Internet.
Begin
Make sure the Device is connected to your network and turned on.
1 Connect the USB device to one of the Device’s USB ports. Make sure the Device is connected to
your network.
2 The Device detects the USB device and makes its contents available for browsing. If you are
connecting a USB hard drive that comes with an external power supply, make sure it is connected
to an appropriate power source that is on.
Note: If your USB device cannot be detected by the Device, try disconnecting and
reconnecting it.
6.7.3 The File Sharing Screen
Use this screen to set up file sharing via the Device. To access this screen, click Network Setting
> Home Networking > File Sharing.
Page 92

90
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
Server Configuration
Active the File
Sharing Services
Select this to enable file sharing through the Device.
Share Directory
Access Level
Select Public to allow all users on the network to access the shared files.
Select Security to require users to log in to access shared files. Set up user accounts in
the Account Management section.
Account Management
Status
This field displays whether a user account is activated or not. Select the check box to
enable the account. Clear the check box to disable the account.
User Name
This displays the user name that has been configured on the Device for file sharing.
Edit
Click this to go to the screen for editing user account information.
Delete
Click this to remove a user account from the list.
Apply
Click this to save your changes to the Device.
Cancel
Click this to set every field in this screen to its last-saved value.
Figure 47 Network Setting > Home Networking > File Sharing
Each field is described in the following table.
Table 27 Network Setting > Home Networking > File Sharing
Page 93

91
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
Active
Select the check box to enable the account. Clear the check box to disable the account.
User Name
Enter a user name that will be allowed to access shares. You can enter up to 16
characters. Only letters and numbers allowed.
New Password
Enter the password used to access the share. You can enter up to 15 characters. Only
letters and numbers are allowed. The password is case sensitive.
Retype New
Password
Retype the password that you entered above.
Back
Click this to return to the previous screen.
Apply
Click this to save your changes to the Device.
Cancel
Click this to restore your previously saved settings.
6.7.4 User Edit
Click Edit in the File Sharing screen to edit a user’s information on the Device.
Figure 48 Network Setting > Home Networking > File Sharing > Edit
Each field is described in the following table.
Table 28 Network Setting > Home Networking > File Sharing > Edit
6.8 Print Server
The Device allows you to share a USB printer on your LAN. You can do this by connecting a USB
printer to one of the USB ports on the Device and then allowing the computers connected to your
network to communicate with the print server (Device) using the Internet Printing Protocol.
Page 94

92
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
Figure 49 Sharing a USB Printer
6.8.1 What You Need to Know
Print Server
This is a computer or other device which manages one or more printers, and which sends print jobs
to each printer from the computer itself or other devices.
Operating System
An operating system (OS) is the interface which helps you manage a computer. Common examples
are Microsoft Windows, Mac OS or Linux.
Port
A port maps a network service such as http to a process running on your computer, such as a
process run by your web browser. When traffic from the Internet is received on your computer, the
port number is used to identify which process running on your computer it is intended for.
Internet Printing Protocol
The Internet Printing Protocol (IPP) uses TCP and UDP with port 631. It can run locally or over the
Internet on top of HTTP. It allows users to send print jobs to a printer, cancel a previous print job,
and know the status of the printer and print jobs.
Supported OSs
The following OSs support Device’s printer sharing feature.
• Microsoft Windows 2000, Windows XP, Windows 7, Windows Vista or Macintosh OS X and later
versions.
6.8.2 Before You Begin
To configure the print server you need the following:
Page 95

93
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
LABEL
DESCRIPTION
Active Print Server
Select this option to have the Device act as a print server.
Apply
Click Apply to save your changes back to the Device.
Cancel
Click Cancel to return to the previous configuration.
• Your Device must be connected to your computer and any other devices on your network. The
USB printer must be connected to your Device.
• The computers on your network must have the printer software already installed before they can
use the printer. Follow your printer manufacturers instructions on how to install the printer
software on your computer.
Note: Your printer’s installation instructions may ask that you connect the printer to your
computer. Connect your printer to the Device instead.
6.8.3 The Print Server Screen
The print server screen is used to enable the print server function on the Device.
Click Network Setting > Home Networking > Print Server to display the Print Server screen.
Figure 50 Network Setting > Home Networking > Print Server
The following table describes the labels in this screen.
Table 29 Network Setting > Home Networking > Print Server
6.9 Add a New Printer Using Windows
This example shows how to connect a printer behind the Device to your computer using the
Windows XP Professional operating system. Some menu items may look different on your operating
system.
1 Click Start > Control Panel > Printers and Faxes to open the Printers and Faxes screen. Click
Add a Printer.
Page 96

94
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
Figure 51 Printers Folder
2 The Add Printer Wizard screen displays. Click Next.
Figure 52 Add Printer Wizard: Welcome
3 Select A network printer, or a printer attached to another computer and click Next.
Page 97

95
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
Figure 53 Add Printer Wizard: Local or Network Printer
4 Select Connect to a printer on the Internet or on a home or office network: and enter
“http://192.168.1.254:631/printers/USB_PRINTER” as the URL to access the print server (Device).
Click Next.
Note: If you change the Device’s LAN IP address, use the new IP address in the URL to
access the print server.
Figure 54 Add Printer Wizard: Specify a Printer
5 Select the make of the printer that you want to connect to the print server in the Manufacturer list
of printers.
6 Select the printer model from the list of Printers.
7 If your printer is not displayed in the list of Printers, you can insert the printer driver installation
CD/disk or download the driver file to your computer, click Have Disk… and install the new printer
driver.
8 Click Next to continue.
Page 98

96
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
Figure 55 Add Printer Wizard: Printer Model
9 Select Yes and then click the Next button if you want to use this printer as the default printer on
your computer. Otherwise select No and then click Next to continue.
Figure 56 Add Printer Wizard: Default Printer
10 The following screen shows your current printer settings. Select Finish to complete adding a new
printer.
Figure 57 Add Printer Wizard Complete
Page 99

97
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
6.10 Add a New Printer Using Macintosh OS X
6.10.1 Mac OS 10.3 and 10.4
Complete the following steps to set up a print server driver on your Macintosh computer.
This example shows how to connect a printer behind the Device to your computer using Mac OS X
v10.4.11. Some menu items may look different on your operating system.
11 Click the Finder icon on the Dock (a place holding a series of icons/shortcuts at the bottom of the
desktop) or double-click your Mac hard disk icon (Mac OS X in this example) on your desktop to
open the Mac HD window.
Figure 58 Mac OS X HD
12 Open the Applications folder.
Figure 59 Macintosh HD Folder
13 Open the Utilities folder.
Page 100

98
eircom D1000 modem User’s Guide
Chapter 6 Home Networking
Figure 60 Applications Folder
14 Double-click the Printer Setup Utility icon.
Figure 61 Utilities Folder
15 Click the Add icon at the top of the screen.
Figure 62 Printer List: Add
16 Click the IP Printer tab to set up your printer.
• Press the alt key and click More Printers in the Printer Browser screen.
 Loading...
Loading...