Page 1
ACCESSBUILDER SECURITY
PACKAGE -- NETWARE/WORKGROUP
USER GUIDE
Software Version 1.2
Part No. 09-0704-001
Published May 1995
Page 2

3Com Corporation ■ 5400 Bayfront Plaza ■ Santa Clara, California ■ 95052-8145
3Com Corporation, 1994. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make
any derivative work (such as translation, transformation, or adaptation) without permission from 3Com Corporation.
3Com Corporation reserves the right to revise this documentation and to make changes in content from time to time without obligation on the
part of 3Com Corporation to provide notification of such revision or change.
3Com Corporation provides this documentation without warranty of any kind, either implied or expressed, including, but not limited to, the
implied warranties of merchantability and fitness for a particular purpose. 3Com may make improvements or changes in the product(s) and/or
the program(s) described in this documentation at any time.
UNITED STATES GOVERNMENT LEGENDS:
If you are a United States government agency, then this documentation and the software described herein are provided to you subject to the
following restricted rights:
For units of the Department of Defense:
Restricted Rights Legend: Use, duplication or disclosure by the Government is subject to restrictions as set forth in subparagraph (c) (1) (ii) for
restricted Rights in Technical Data and Computer Software clause at 48 C.F.R. 52.227-7013. 3Com Corporation, 5400 Bayfront Plaza, Santa Clara,
California 95052-8145.
For civilian agencies:
Restricted Rights Legend: Use, reproduction or disclosure is subject to restrictions set forth in subparagraph (a) through (d) of the Commercial
Computer Software - Restricted Rights Clause at 48 C.F.R. 52.227-19 and the limitations set forth in 3Com;s standard commercial agreement for
the software. Unpublished rights reserved under the copyright laws of the United States.
3ComFacts, Ask3Com, CardFacts, NetFacts, and CardBoard are service marks of 3Com Corporation.
3Com, AccessBuilder, LanScanner, LinkBuilder, NETBuilder, NETBuilder II, ViewBuilder, EtherDisk, EtherLink, EtherLink Plus, EtherLink II, TokenLink,
TokenLink Plus, and TokenDisk are registered trademarks of 3Com Corporation. 3Com Laser Library, 3TECH, Boundary Routing, CacheCard,
FDDILink,NetProbe, Parallel Tasking, SmartAgent, Star-Tek, and Transcend are also trademarks of 3Com Corporation.
CompuServe is a registered trademark of CompuServe, Inc.
Other brand and product names may be registered trademarks or trademarks of their respective holders.
Guide written and produced by Gary Halverson.
Page 3

ACCESSBUILDER SECURITY
PACKAGE -- NETWARE/WORKGROUP
USER GUIDE
(Software Version 1.2)
CONTENTS
1 INTRODUCTION
General Information 1–1
1.1. Three Security Client Types 1–1
NetWare Applications 1–2
Workgroup Applications 1–2
1.2. Compatibility 1–2
1.3. Limitations 1–3
2 NOVELL NETWARE
BINDERY/NDS SECURITY CLIENTS
2.1 Overview 2–1
2.2. Installation 2–1
SNDS Usage 2–5
2.3. De-installation 2–5
2.4. AccessBuilder Configuration 2–6
2.5. Usage 2–6
Client 2–6
Page 4
3 ACCESSBUILDER NAME SERVER
3.1. Overview 3–1
3.2. Installation Steps 3–2
SUN OS 4.1x Installation 3–2
DOS Installation 3–3
Launching the Name Server 3–3
3.3. Command Options 3–4
3.4. Database Conversion 3–4
3.5. AccessBuilder Configuration 3–5
4 NAME SERVER DATABASE UTILITIES
4.1. General Information 4–1
4.2. User Record Contents 4–1
4.3. The Database Utilities User Interface 4–2
4.4. The Main Menu 4–2
Add a User Record 4–2
Modify User Record 4–3
Delete User Record 4–3
Display User Records 4–3
Save User Records into ASCII Files 4–4
Backup Database 4–5
Restore Database 4–5
Change Database Password 4–6
4.5. PATH 4–6
A DATABASE UTILITIES ERROR MESSAGES
B NAME SERVER ERROR MESSAGES
C TECHNICAL SUPPORT
LIMITED WARRANTY
Page 5
1
INTRODUCTION
General
Information
The AccessBuilder Security Package is a model for flexible multi-vendor
security interoperation that is consistent with preliminary IETF (Internet
Engineering Task Force) work. The AccessBuilder Security Package software
provides the network administrator with the means to control network
access by remote users through an existing network security mechanism.
The AccessBuilder Security Package model allows integration of Novell
NetWare security solutions while keeping the AccessBuilder open to future
security options. The AccessBuilder Security Client is thus designed for
maximum flexibility and investment protection for 3Com AccessBuilder
customers.
This document provides an overview of the Novell NetWare Bindery/NDS
Security, a description of the installation procedures, and a summary of
limitations.
Also provided is documentation and installation procedures for
AccessBuilder Name Server, a self-contained security database operating on
a Sun workstation. The AccessBuilder Name Server has application in a
wide variety of workgroup environments.
1.1. Three Security Client Types
The AccessBuilder Security Package - NetWare/Workgroup Version 1.2
software provides compatibility with two major types of Novell
network-based user authentication environments and one self-contained
security database package:
■ AccessBuilder Security Client for Novell NetWare Bindery Services
■ AccessBuilder Security Client for Novell NetWare Directory Services
■ AccessBuilder Name Server for networks running SunOS 4.1.x
Page 6
1-2 CHAPTER 1: INTRODUCTION
The AccessBuilder Security Package - NetWare/Workgroup software
modules are designed to reside on their respective server or client
workstations where they provide the appropriate agent software to
interface between the AccessBuilder and the respective security server or
database.
NetWare
Applications
Workgroup
Applications
The AccessBuilder Security Client for Novell NetWare Bindery/NDS Security
Clients work with the AccessBuilder server software Version 5.0 (or later) to
enable remote user access authentication to be handled automatically from
an existing Novell security database. The AccessBuilder login/password
information is validated directly against the selected Novell security service.
Each version is furnished on a single diskette.
The AccessBuilder Security Client for Novell NetWare bindery/NDS uses a
designated user database maintained by Novell NetWare Bindery or
NetWare Directory Services. It is designed to perform the authentication
process using these services.
The “AccessBuilder Name Server” module executes on a Sun Sparc station
running SunOS 4.1.x to provide integrated LAN-based security through its
own user database. The security database can then be used for automatic
validation of remote users logging into one or more AccessBuilder. This
software module is intended to reside on a network node where the
AccessBuilder can query the security database through the AccessBuilder
UDP/IP-based protocol. Also, a set of tools for managing the security
database is provided to facilitate database administration.
1.2. Compatibility
The AccessBuilder Security Client for Novell NetWare works with
AccessBuilder server software version 5.0 or later and Remote Client
software version 5.0 or later.
Page 7
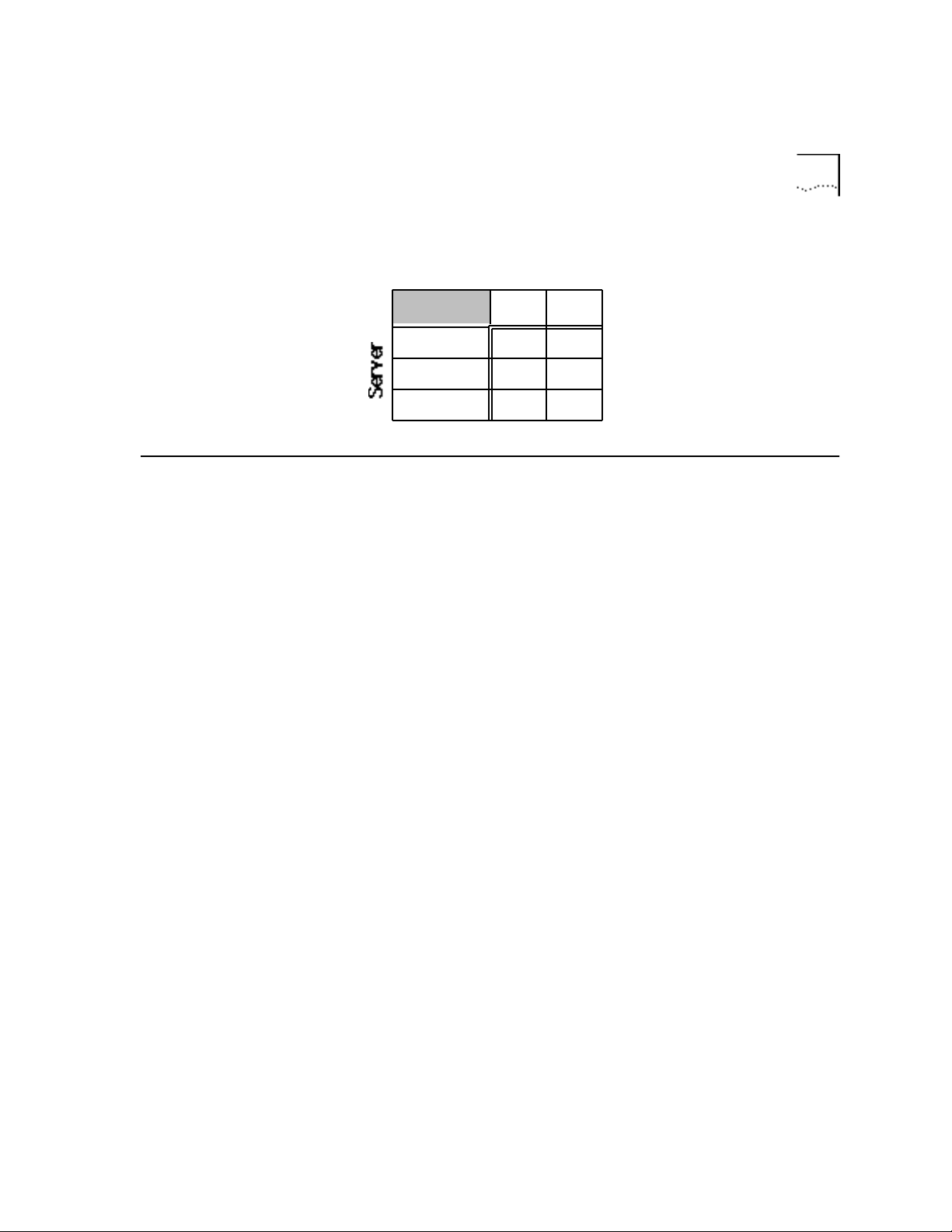
1.3. Limitations 1-3
Table 1-1 AccessBuilder Server and Security Client Version Compatibility Matrix
Security Clients
1.0 1.2
4.0
4.1 ●
5.0 ● ●
1.3. Limitations Novell NetWare Security Client related limitations include:
■ ARA and PPP clients using CHAP authentication are not supported
Limitations applying to both NetWare Security Client and Name Server
include:
■ No space characters are allowed in the user ID and password fields
■ When the AccessBuilder (Version 5.0) Security Access feature is enabled,
the user id and password fields are case sensitive. Also, when the remote
client is using the AccessBuilder Remote Client software, version 5.0 or
later must be used.
Page 8

1-4 CHAPTER 1: INTRODUCTION
Page 9
NOVELL NETWARE
2
2.1 Overview
BINDERY/NDS SECURITY
CLIENTS
If you are not using the Novell NetWare Bindery/NDS Security Client, you
may skip this section.
The NDS (Netware Directory Services) Security Client is a Novell NLM that
runs on Novell Netware Server 4.X.
The Bindery Security Client is a Novell NLM runs on Novell NetWare Server
3.11 or 4.X.
When a remote user dials into an AccessBuilder and provides the login
information, the AccessBuilder server generates a validation request to the
Bindery/NDS Security Client. The Bindery/NDS Security Client then initiates
an authentication session with the Novell Netware server Bindery/NDS
services. Based on the result of the authentication session, the Bindery/NDS
security Client sends a validation response back to the AccessBuilder server
and indicates to the user that the authentication has failed or passed.
2.2. Installation To install the Bindery/NDS Security Client on a NetWare server, perform the
following steps (on the object server):
1 Verify that TCPIP NLM is running (by verifying the autoexec.ncf file).
If not, verify that Ethernet_II frame type is used. Bind IP to Ethernet_II frame
type. Following this, at the server prompt load TCPIP NLM.
The following are examples of an autoexec.ncf file which loads NetWare
Bindery Services, and NetWare Directory Services security clients:
Page 10
2-2 CHAPTER 2: NOVELL NETWARE BINDERY/NDS SECURITY CLIENTS
(NetWare Bindery example)
set Time Zone = PST8PDT
set Daylight Savings Time Offset = 1:00:00
set Start Of Daylight Savings Time = (APRIL SUNDAY FIRST 2:00:00 AM)
set End Of Daylight Savings Time = (OCTOBER SUNDAY LAST 2:00:00 AM)
set Default Time Server Type = SINGLE
set Bindery Context = O=b010
file server name SATURN
ipx internal net af0bfed9
load clib
load tcpip
load conlog
load 3C5X9 slot=5 frame=ETHERNET_802.2 NAME=3C5X9_1
bind IPX to 3C5X9_1 net=AA440000
load 3c5x9 slot=5 frame=ETHERNET_II name=3c5x9_2
bind ipx to 3c5x9_2 net=cc100001
load 3C5X9 slot=5 frame=ETHERNET_802.3 NAME=3C5X9_3
bind IPX to 3C5X9_3 net=AA330000
load 3c5x9 slot=5 frame=ETHERNET_SNAP name=3c5x9_4
bind ipx to 3c5x9_4 net=AA550000
bind IP to 3c5x9_2 addr=192.147.72.3 mask=255.255.255.0
set maximum concurrent directory cache writes = 50
set maximum directory cache buffers = 4000
load cpqhlth
load cdrom
cpqsnmp
mount all
unload conlog
load monitor
#######################################################################
# AccessBuilder NetWare Security Client Software
#######################################################################
load sbindery 3com
Page 11
2.2. Installation 2-3
(NetWare Directory example)
set Time Zone = PST8PDT
set Daylight Savings Time Offset = 1:00:00
set Start Of Daylight Savings Time = (APRIL SUNDAY FIRST 2:00:00 AM)
set End Of Daylight Savings Time = (OCTOBER SUNDAY LAST 2:00:00 AM)
set Default Time Server Type = SINGLE
set Bindery Context = O=b010
file server name SATURN
ipx internal net af0bfed9
load clib
load tcpip
load conlog
load 3C5X9 slot=5 frame=ETHERNET_802.2 NAME=3C5X9_1
bind IPX to 3C5X9_1 net=AA440000
load 3c5x9 slot=5 frame=ETHERNET_II name=3c5x9_2
bind ipx to 3c5x9_2 net=cc100001
load 3C5X9 slot=5 frame=ETHERNET_802.3 NAME=3C5X9_3
bind IPX to 3C5X9_3 net=AA330000
load 3c5x9 slot=5 frame=ETHERNET_SNAP name=3c5x9_4
bind ipx to 3c5x9_4 net=AA550000
bind IP to 3c5x9_2 addr=192.147.72.3 mask=255.255.255.0
set maximum concurrent directory cache writes = 50
set maximum directory cache buffers = 4000
load cpqhlth
load cdrom
cpqsnmp
mount all
unload conlog
load monitor
load dsapi
#######################################################################
# AccessBuilder NetWare Security Client Software
#######################################################################
load snds 3com
2 For NetWare Directory Services, be sure the line load dsapi.nlm occurs
before load snds.nlm (AccessBuilder Security Client).
3 Add a UDP port for the Bindery/NDS Security Client into \etc\services with
the service name "crsecacc", 888 is the default port number in the
AccessBuilder server.
ex. add "crsecacc 888/udp" at the bottom of \etc\services as shown in the
following example:
Page 12
2-4 CHAPTER 2: NOVELL NETWARE BINDERY/NDS SECURITY CLIENTS
(\etc\services example)
# SYS:ETC\SERVICES
#
# Network service mappings. Maps service names to transport
# protocol and transport protocol ports.
#
echo 7/tcp
discard 9/tcp sink null
systat 11/tcp
daytime 13/tcp
netstat 15/tcp
ftp-data 20/tcp
ftp 21/tcp
telnet 23/tcp
smtp 25/tcp mail
time 37/udp timserver
name 42/udp nameserver
whois 43/tcp nicname # usually to sri-nic
domain 53/tcp
hostnames 101/tcp hostname # usually to sri-nic
sunrpc 111/udp
#
# Host specific functions
#
tftp 69/udp
finger 79/tcp
link 87/tcp ttylink
x400 103/tcp # ISO Mail
x400-snd 104/tcp
csnet-ns 105/tcp
pop-2 109/tcp # Post Office
uucp-path 117/tcp
nntp 119/tcp usenet # Network News Transfer
ntp 123/tcp # Network Time Protocol
NeWS 144/tcp news # Window System
#
# UNIX specific services
#
# these are NOT officially assigned
#
exec 512/tcp
login 513/tcp
shell 514/tcp cmd # no passwords used
printer 515/tcp spooler # experimental
courier 530/tcp rpc # experimental
biff 512/udp comsat
who 513/udp whod
syslog 514/udp
talk 517/udp
route 520/udp router routed
new-rwho 550/udp new-who # experimental
rmonitor 560/udp rmonitord # experimental
monitor 561/udp # experimental
ingreslock 1524/tcp
snmp 161/udp # Simple Network Mgmt Protocol
snmp-trap 162/udp snmptrap # SNMP trap (event) messages
crsecacc 888/udp
?
Page 13

2.3. De- installation 2-5
You may need to unload, then reload NetWare server to make the changes
take effect.
4 Insert the distribution diskette into the floppy drive and load the
AccessBuilder Security Client for Bindery (sbindery.nlm) or for NDS
(snds.nlm) -- (depending upon your NetWare Server's version and which
service is used).
:load sbindery 3com
where sbindery is NLM name for AccessBuilder Security Client for Novell
NetWare Bindery. 3com is the default password for AccessBuilder Security
Client.
:load snds 3com
where snds is NLM name for AccessBuilder Security Client for Novell
NetWare Directory Services. 3com is the default password for the
AccessBuilder Security Client.
SNDS Usage Optionally, SNDS may also take context_name as a parameter for remote
access authorization control. For example:
2.3. Deinstallation
load snds security_password(key) /C:context_name [generic form]
load snds 3com /C:HQ.MyCompany [example]
SNDS will authenticate the remote user against the HQ.MyCompany context
so only user names assigned to that context will be successfully
authenticated. Other users will be denied.
If the context name is not specified in the loading command, SNDS will
authenticate the remote user against the default bindery context.
To remove the AccessBuilder Security Client function from the NetWare
Server, enter:
:unload sbindery
or
:unload snds
Page 14

2-6 CHAPTER 2: NOVELL NETWARE BINDERY/NDS SECURITY CLIENTS
2.4.
AccessBuilder
Configuration
2.5. Usage
Before running the Bindery/NDS Security Client, you will need to configure
the following parameters in the AccessBuilder server:
1) SecurityServerType,
2) SecurityPasswd,
3) ScrtyClIpAddr,
4) ScrtyClUdpPort if necessary, and
5) Time Zone.
Be sure to enter the correct Security Client password which is shared by
AccessBuilder server and AccessBuilder Security Client. The Security
password for the AccessBuilder server should match the password used at
the client security server (3Com is the default value).
The Bindery/NDS Security Client logs the user login records in the
absecure.log file under the NetWare server root directory.
Client At the AccessBuilder client site, the Novell NetWare login convention may
be used. For example:
login: ServerName/UserName
password: ********
can be used to do authentication with Bindery Security Client for the
specified Novell NetWare server with Bindery service. For NDS Security
Client, users log into a network instead of a specified server. For
authentication purposes, the UserName is adequate. For example:
login: UserName
password: ********
Page 15

ACCESSBUILDER NAME SERVER
3
3.1. Overview The AccessBuilder “Name Server” software module is intended to reside on
a network node (Sun SPARCstation) and includes a security database
management program and a security name server program that interface
with AccessBuilders.
If you are not using the 3Com provided Name Server on a Sun SPARCstation,
you may skip this section.
Figure 3-1 illustrates the data flow during the authentication process
initiated by a remote client:
1 When a remote user dials into the AccessBuilder and provides the
appropriate login information.
2 The AccessBuilder generates a Validation Request to the Database Name
Server.
3 The AccessBuilder Name Server then initiates a database lookup request.
4 User database has retrieved the user record and delivered it to the
AccessBuilder Name Server.
5 The AccessBuilder Name Server then sends a validation response and user
data back to the AccessBuilder.
6 The AccessBuilder then receives the Validation Response and performs a
final check before allowing the remote client to access the network.
Page 16

3-2 CHAPTER 3: ACCESSBUILDER NAME SERVER
3.2. Installation Steps
SUN OS 4.1x
Installation
Figure 3-1 Security Access Data Flow and Steps
The AccessBuilder Name Server is distributed on two floppy diskettes; one
for SUN OS 4.1x tar file format, and the other in standard DOS file format.
Refer to the following installation section for your environment.
1 Install the files on the AccessBuilder Name Server distribution diskette (this
diskette contains three files, aceclnt, dbutil, and dbcnvt):
a On your Sun workstation, call up the target directory:
cd (target directory)
b Insert the distribution diskette into the floppy drive and copy the files on
the diskette to your target directory:
tar xvf /dev/rfd0
2 Change the access right to the distribution files to 7555:
Page 17

3.2. Installation Steps 3-3
chmod 7555 files
3 Change the ownership of the distribution files to root:
chown root files
4 Assign a UDP port for AccessBuilder Name Server:
Edit the /etc/services file to add the following entry:
crsecacc 888/udp #AccessBuilder security access
If the UDP port 888 is used by other application, you may assign an unused
UDP port number. Make sure the UdpPort parameter in AccessBuilder is set
to the same number.
5 Run the dbutil program to build the user database. Refer to Section 3 for
further information.
DOS Installation To install from the DOS format diskette, perform the following:
1 Insert the DOS diskette into the floppy drive on your PC.
Launching the
Name Server
2 Run ftp to transfer the three distribution files from the diskette to the target
directory on a Sun workstation.
3 Perform steps 4 and 5 as described above.
1 Invoke the AccessBuilder Name Server program.
a Add the directory where the dbserver resides to the path.
Start the AccessBuilder Name Server program:
# dbserver
The AccessBuilder Name Server logs the user login records in the
dbserver.log file which can be used to monitor the transaction status.
A list of error messages may be found in Appendix B.
Page 18

3-4 CHAPTER 3: ACCESSBUILDER NAME SERVER
3.3. Command Options
3.4. Database Conversion
With Name Server Release 1.2, the ‘dbserver’ can run from ‘/etc/rc’ file
without user interactions. This makes it possible for the ‘dbserver’ to run
automatically when UNIX boots up.
The command options for dbserver are:
dbserver [-d] [-p password] [-n/-y]
where:
-d -- The -d option enables the Name Server to print out trace
information on the standard output and to save trace information into
the log file ‘dbserver.log’.
-p password -- is used as the encryption key by the Name Server to
encrypt messages between Name Server and AccessBuilder. This
password has to be the same as the ‘Security Parameter’ of the
AccessBuilder. The default password is ‘3com’.
-y/-n -- The -y option allows the user to change the user password, while
the -n option disables changing the user password. The default is ‘-y’.
The following information applies only to users having an existing Name
Server 1.0 database. If you do not have an existing version 1.0 database, skip
this section.
Because Name Server release 1.2 produces the ‘password.db’ file in a
different format from the previous release, it is necessary to convert your
existing version 1.0 ‘password.db’ file into the new file format. The command
‘dbcnvt’ is provided for this purpose.
Before running the dbcnvt command, make sure that the dbcnvt command
resides in the same directory as the ‘password.db’ file, or the environment
variable DBPATH is set to the name of the directory where the ‘password.db’
file is located. To run dbcnvt, enter the command name the UNIX SHELL
prompt and follow the prompt to enter the database password.
Page 19

3.5. AccessBuilder Configuration 3-5
3.5.
AccessBuilder
Configuration
In order for the AccessBuilder to work with the Name Server client, the
following parameters in the AccessBuilder (under the admin directory) must
be set to work properly:
1 SecurityServerType
Set this parameter to AB (AccessBuilder Name Server).
2 SecurityPasswd
This parameter has to be the same as the ‘-p password’ command option to
’dbserver’. The default value is 3com.
3 ScrtyClntIpAddr
This parameter is set to the IP address of the UNIX workstation which runs
the Name Server.
4 ScrtyClntUdpPort
This parameter has to be set to the same UDP port number as the ‘crsecacc’
entry of the /etc/services file. The default value is 888.
5 Date
This parameter is set to the current date.
6 Time
This parameter is set to the current time.
These steps may be performed using the Security Clients Parameters dialog
box in Transcend AccessBuilder Manager.
Page 20

3-6 CHAPTER 3: ACCESSBUILDER NAME SERVER
Page 21

NAME SERVER DATABASE
4
4.1. General Information
4.2. User Record Contents
UTILITIES
The AccessBuilder Name Server Database Utilities (dbutil) are a collection of
tools that enable management of a user database on a Sun Workstation
under SUN OS 4.1.x. Keeping the user database on SUN workstation has two
advantages:
a The system administrator can better manage the user database because
there is only one copy of database to deal with as opposed to one
database per AccessBuilder Server.
b The database can store hundreds of thousands of user records in order
to satisfy the needs of an enterprise network, where there are a large
number of remote users.
The User database contains a set of user records. Each user record contains
information on a remote user who accesses AccessBuilder Server. A user
record is composed of four elements of information:
1 The user's name,
2 login password,
3 privilege and
4 callback number.
The user's name is the key of a user record, and therefore must be unique.
All information except the callback number are mandatory, which means
this information must be supplied when adding a user record to the
database.
Page 22

4-2 CHAPTER 4: NAME SERVER DATABASE UTILITIES
There is a limited length of information that can input for each piece of
information. The user name can contain up to 64 characters. The password
can have up to 32 characters. The callback number can have up to 16
characters.
4.3. The
Database
Utilities User
The Database Utilities provide a character based, menu driven user
interface. Users interact with menu commands to perform database
operations such as query, add, update, delete, backup and restore.
Interface
4.4. The Main
When the Database Utilities start up, the Main menu is displayed as shown:
Menu
***** Main Menu *****
1) Add User Record
2) Modify User Record
3) Delete User Record
4) Display User Records
5) Save User Records into ASCII File
6) Backup Database
7) Restore Database
8) Change Database Password
9) Exit
Please enter your choice:
Add a User Record You can add a user record to the database by selecting '1' from the main
menu. You will be prompted to enter information on the user's name,
password, privilege and callback number. All information except the
callback number are mandatory.
Please enter your choice: 1
User Name: demouser
User Password:
Privilege, (1) for User, (2) for Administrator: 1
Callback #:
Page 23

4.4. The Main Menu 4-3
Modify User Record You can modify a user record in the database by selecting 2 from the Main
menu. You are then prompted to enter the user's name. If the user's name is
in the database, the Utilities display the current information and prompt
you to make modifications. You may elect to skip changes by pressing the
Enter key at the prompt.
Please enter your choice: 2
User Name: demouser
Please enter new password or press enter to skip changes:
The user privilege is: user,
please enter privilege or press enter to skip changes.
(1) for User, (2) for Administrator: 2
The user callback # is: 150,
please enter callback # or press enter to skip changes: 8941800
Delete User Record You can delete a user record from the database by selecting 3 from the
Main menu. You are then prompted to enter the user's name. If the user's
name is in the database, the Utilities will prompt you to confirm the
deletion of the user record.
Please enter your choice: 3
User Name: demouser
Do you really want to delete the user "demouser" from the database? (y/n) y
Display User
By selecting item 4 from the Main menu, you are offered four options:
Records
1 Display user records display a particular user,
2 Display users having a 'user' privilege,
3 Display users having 'admin' privilege,
4 Display all users.
Page 24

4-4 CHAPTER 4: NAME SERVER DATABASE UTILITIES
The following screen shows the Display User Records option and all user
records with ‘user’ privilege.
***** Display User Record Menu *****
1) Display A User Record
2) Display User Records with User Privilege
3) Display User Records with Admin Privilege
4) Display All User Records
5) Return to Main Menu
Please enter your choice: 2
User Name Privilege Callback #
-------------------------------------------------------------------- joe (user) 8941801
john (user) 8941812
Total 2 records found
Save User Records
into ASCII Files
You can save the database information into ASCII files, which can then be
viewed from a text editor or printed. By selecting item '5' from the Main
menu, you have three options to save user records:
1 Save user records with the 'user' privilege,
2 Save user records with the 'admin' privilege,
3 Save all user records.
Page 25

4.4. The Main Menu 4-5
The following screen shows the Save User Records menu command and the
contents of the ASCII file containing all the user records.
***** Save User Record Menu *****
1) Save User Records with User Privilege
2) Save User Records with Admin Privilege
3) Save All User Records
4) Return to Main Menu
Please enter your choice: 3
The contents of ASCII file:
User Name Privilege Callback #
-------------------------------------------------------------------- joe (user) 8941801
john (user) 8941812
Total 2 records found
Backup Database This menu command allows you to backup database into a specified
database name. Since the database includes three related files, this
command eliminates the need to back up three individual files.
Please enter your choice: 6
Please enter database name for backup: all
Backup database...
Restore Database This menu command allows the you to restore the database from a backup
database. Precaution should be taken with this command, because restore
will overwrite the existing database with the backup database.
Please enter your choice: 7
Please enter database name for restore: all
Restoring database will overwrite existing database.
Do you wish to continue? y/n y
Restore database...
Page 26

4-6 CHAPTER 4: NAME SERVER DATABASE UTILITIES
Change Database
Password
This menu command enables you to change database password. Since
every user's password in the database is encrypted with database password,
precaution should be taken with this command, especially when the
dbserver daemon is running.
After changing the database password, terminate and restart the dbserver
daemon so that the user login request can be properly authenticated.
Please enter your choice: 8
Please note that if dbserver is currently running, after changing
database password, dbserver will not be able to authenticate user login
properly.
Please terminate and restart dbserver after database password has
changed.
Do you wish to continue? (y/n) y
Old database password:
New database password:
Confirm database password:
Updating database...
4.5. PATH When dbutil starts, it checks for the setting of environment variable
"DBPATH" to determine the directory to create or to open database files. If
the variable is set, it assumes that the database is under the DBPATH
directory. Otherwise, it assumes that the database files are under the
directory where dbutil starts.
A list of dbutil error messages may be found in Appendix A.
Page 27

DATABASE UTILITIES ERROR
A
Message
Number dbutil Error Messages
1 DES initialization failed.
Cause: Software internal error.
Solution: Call tech support.
2 Database initialization failed.
Cause: File access permission errors.
Solution: Make sure that the user has permission to access all three files:
'helperdb.nx', 'helperdb.dt' and 'password.db' under $DBPATH directory or under
current directory if DBPATH environment variable is not set.
MESSAGES
The following table defines the error messages displayed by the Name
Server Database Utilities(dbutil) when exception conditions arise. Each error
message is accompanied with the possible causes of the error and solutions
to the problem.
3 The user record already exists.
Cause: In adding a user record, entry of a user name which already exists in the
database has been attempted.
Solution: Make sure to enter a unique user name or to choose "Modify User
Record" to modify existing information.
4 The user record doesn't exist.
Cause: In updating or deleting a user record, entry of a user name which
doesnot exist in the database has been attempted.
Solution: Enter a user name which already in the database.
5 Failed to update user record.
Cause: dbutil was not able to update a user record due to internal errors.
Solution: Call tech support.
Page 28

A-2 APPENDIX A: DATABASE UTILITIES ERROR MESSAGES
Message
Number dbutil Error Messages
6 Failed to delete user record.
Cause: dbutil was not able to delete a user record due to internal errors.
Solution: Call tech support.
7 The database password file does not exist.
Cause: dbutil was not able to locate the password file, however, user record files
do exist.
Solution: Make sure DBPATH is set properly or starts dbutil from where the
password file is located.
8 Unable to create password file.
Cause: dbutil was not able to create password file most likely due to a
permission problem.
Solution: Make sure that the user has permission to write to the file
'password.db'.
9 Incorrect password, exit dbutil.
Cause: The user has entered password incorrectly three times.
Solution: Enter the correct password.
10 Unable to create user record file.
Cause: dbutil was not able to create user record file most likely due to
permission problem.
Solution: Make sure that the user has permission to write to the files 'helperdb.nx'
and 'helperdb.dt'.
11 Unable to open user record file.
Cause: dbutil was not able to open user record file most likely due to
permission problem.
Solution: Make sure that the user has permission to open the files 'helperdb.nx'
and 'helperdb.dt'.
12 Unable to create xxx file.
Cause: In saving database into ASCII file, dbutil was not able to create user
specified file 'xxx' file most likely due to permission problem.
Solution: Make sure that the user has permission to write to the files 'xxx'.
Page 29

NAME SERVER ERROR MESSAGES
B
Messages shown in the log file:
Message
Number Name Server Log File Error Message
1 Abnormal exit\n
Recommended Action: Call 3COM Technical Support.
2 Out of memory when allocating request data.
Recommended Action: Call 3COM Technical Support.
3 Protocol Error (<error code>).
Recommended Action: Call 3COM Technical Support.
4 Version number Error (<error code>).
Recommended Action: Call 3COM Technical Support.
5 Command Error (<error code>).
Recommended Action: Call 3COM Technical Support.
6 Data length Error (<error code>).
Recommended Action: Call 3COM Technical Support.
7 Auth Type length Error (<error code>).
Recommended Action: Call 3COM Technical Support.
8 Auth Type data Error (<error code>).
Recommended Action: Call 3COM Technical Support.
9 User Id length Error (<error code>).
Recommended Action: Call 3COM Technical Support.
10 Challenge length Error ().
Recommended Action: Call 3COM Technical Support.
11 Wrong option type (<error code>).
Recommended Action: Call 3COM Technical Support.
Page 30

B-2 APPENDIX B: NAME SERVER ERROR MESSAGES
Message
Number Name Server Log File Error Message
12 Total length error (<error code>).
Recommended Action: Call 3COM Technical Support.
13 Current Time length Error (<error code>).
Recommended Action: Call 3COM Technical Support.
14 Incorrect option fields in the packet(<error code>).
Recommended Action: Call 3COM Technical Support.
15 Incorrect option fields not in the packet(<error code>).
Recommended Action: Call 3COM Technical Support.
16 DES decode input length error (<error code>).
Recommended Action: Call 3COM Technical Support.
17 Recoverable software error.
Recommended Action: Call 3COM Technical Support.
18 DES decode input length error (<error code>).
Recommended Action: Call 3COM Technical Support.
19 Wrong Encrypted Key from user <user id>.
Recommended Action: Verify the Name Server has the same password shared by the
AccessBuilder.
20 Inconsistant time stamp (may be a replay request or misconfigured password).
Recommended Action: Verify the Name Server has the same password shared by the
AccessBuilder.
21 Wrong Encrypted New Key from user <user id>.
Recommended Action: None. User has entered an invalid password.
22 Encrypt New Key appeared for Validation Request Packet.
Recommended Action: None. User has requested changing his/her password.
23 Check password configuration.
Recommended Action: Name Server is set to not allow the user to change his/her
own password, and a user has attempted to change his/her password.
24 Time skew in the incoming packet is too large.
Recommended Action: Verify the time setting on AccessBuilders and Name Server
machine is set up correctly.
Page 31

Message
Number Name Server Log File Error Message
25 UTC time not available.
Recommended Action: Verify the time setting on the Name Server machine is set up
correctly.
26 Duplicate time stamp used from user <user id> (could be a replay packet).
Recommended Action: This may be a replay packet. Check if any user is injecting
traffic to the network.
27 Duplicate sequence number used from user <user id> (could be a replay packet).
Recommended Action: This may be a replay packet. Check if any user is injecting
traffic to the network.
28 Authtication failed from user <user id>.
Recommended Action: None. For information only.
29 Authtication passed from user <user id>.
Recommended Action: None. For information only.
30 Authtication request from user <user id>.
Recommended Action: None. For information only.
B-3
31 Authtication request failed from an invalid user <user id>.
Recommended Action: None. For information only.
32 Change password failed from user <user id>.
Recommended Action: None. For information only.
33 Change password passed from user <user id>
Recommended Action: None. For information only.
34 Out of memory when allocating request data.
Recommended Action: Make sure the system has at least 1MByte memory available.
35 No such service: crsecacc/udp. Check /etc/services file.
Recommended Action: Make sure the /etc/services file has crsecacc entry. Also make
sure no other Name Server is running on the same machine.
36 Cannot get UDP socket.
Recommended Action: Make sure the /etc/services file has crsecacc entry. Also make
sure no other Name Server is running on the same machine.
37 Cannot bind UDP socket.
Recommended Action: Make sure the /etc/services file has crsecacc entry. Also make
sure no other Name Server is running on the same machine.
Page 32

B-4 APPENDIX B: NAME SERVER ERROR MESSAGES
Message
Number Name Server Log File Error Message
38 Send response failed.
Recommended Action: Make sure the network connection is healthy.
39 Receive Error.
Recommended Action: Make sure the network connection is healthy.
Messages displayed on the terminal:
Message
Number
Name Server Terminal Error Message
1 Cannot open log file.
Recommended Action: Make sure you have write access to the right
directory.
2 DES initialization Error!
Recommended Action: Make sure there is at least 1M bytes of memory
available.
3 UDP socket creation/binding Error!
Recommended Action: Make sure the /etc/services file has a crsecacc
entry. Also make sure no other Name Server is running on the same
machine.
Page 33

C
TECHNICAL SUPPORT
3Com provides easy access to technical support information through a
variety of services. This appendix describes these services.
On-line Technical Services
3Com Bulletin
Board Service
3Com offers worldwide product support seven days a week, 24 hours a day,
through the following on-line systems:
■ 3Com Bulletin Board Service (3ComBBS)
■ World Wide Web site
■ Ask3Com
■ 3ComFacts
SM
on CompuServe
SM
automated fax service
3ComBBS contains patches, software, and drivers for all 3Com products, as
well as technical articles. This service is available via modem seven days a
week, 24 hours a day. To reach the service, set your modem to 8 data bits,
no parity, and 1 stop bit. Call the telephone number nearest you:
Country Baud Rate Telephone Number
Australia up to 14400 baud (61) (2) 955 2073
France up to 14400 baud (33) (1) 69 86 69 54
Germany up to 9600 baud
up to 9600 baud
Hong Kong up to 14400 baud (852) 537 5601
Italy (fee required) up to 9600 baud (39) (2) 273 00680
Japan up to 14400 baud (81) (3) 3345 7266
Singapore up to 14400 baud (65) 534 5693
Taiwan up to 14400 baud (886) (2) 377 5838
U.K. up to 14400 baud (44) (144) 227 8278
U.S. up to 14400 baud (1) (408) 980 8204
(49) (89) 627 32 188
(49) (89) 627 32 189
(886) (2) 377 5840
Page 34

C-2 APPENDIX C: TECHNICAL SUPPORT
World Wide Web Site Access the latest networking information on 3Com’s World Wide Web site by
entering our URL into your Internet browser:
http://www.3Com.com/
This service features news and information about 3Com products, customer
service and support, 3Com’s latest news releases, selected articles from
3TECH, 3Com’s award-winning technical journal, and more.
Ask3Com on
CompuServe
3ComFacts
Automated Fax
Service
Ask3Com is a CompuServe-based service containing patches, software,
drivers, and technical articles about all 3Com products, as well as an
interactive forum for technical questions. To use Ask3Com, you need a
CompuServe account.
To use Ask3Com:
1 Log on to CompuServe.
2 Enter go threecom
3 Press [Return] to see the Ask3Com main menu.
3Com Corporation’s interactive fax service, 3ComFacts, provides data sheets,
technical articles, diagrams, and troubleshooting instructions on 3Com
products 24 hours a day, seven days a week. Within this service, you may
choose to access CardFacts for adapter information, or NetFacts for
network system product information.
■ CardFacts provides adapter installation diagrams, configuration drawings,
troubleshooting instruction, and technical articles.
Document 9999 provides you with an index of adapter documents.
■ NetFacts provides data sheets and technical articles on 3Com Corporation’s
hub, bridge, router, terminal server, and software products.
Document 8888 provides you with an index of system product documents.
Call 3ComFacts using your touch-tone telephone. International access
numbers are:
Page 35

Support from Your Network Supplier C-3
Country Fax Number
Hong Kong (852) 537 5610
U.K. (44) (144) 227 8279
U.S. (1) (408) 727 7021
Local access numbers are available within the following countries:
Country Fax Number Country Fax Number
Australia 800 123853 Italy 1678 99085
Denmark 800 17319 Netherlands 06 0228049
Finland 98 001 4444 Norway 800 11062
France 05 90 81 58 Sweden 020 792954
Germany 0130 8180 63 U.K. 0800 626403
Support from Your Network Supplier
If additional assistance is required, contact your network supplier. Many
suppliers are authorized 3Com service partners who are qualified to provide
a variety of services, including network planning, installation, hardware
maintenance, application training, and support services.
When you contact your network supplier for assistance, have the following
information ready:
■ Diagnostic error messages
■ A list of system hardware and software, including revision levels
■ Details about recent configuration changes, if applicable
If you are unable to contact your network supplier, see the following section
on how to contact 3Com.
Page 36

C-4 APPENDIX C: TECHNICAL SUPPORT
Support from 3Com
If you are unable to receive support from your network supplier, technical
support contracts are available from 3Com.
In the U.S. and Canada, call (800) 876-3266 for customer service.
If you are outside the U.S. and Canada, contact your local 3Com sales office
to find your authorized service provider:
Country Telephone Number Country Telephone Number
Australia (Sydney) (61) (2) 959 3020 Mexico (525) 531 0591
(Melbourne) (61) (3) 653 9515 Netherlands (31) (3) 402 55033
Belgium (32) (2) 7164880 Singapore (65) 538 9368
Brazil (55) (11) 241 1571 South Africa (27) (11) 803 7404
Canada (905) 882 9964 Spain (34) (1) 3831700
France (33) (1) 69 86 68 00 Sweden (46) (8) 632 91 00
Germany (49) (89) 6 27 32 0 Taiwan (886) (2) 577 4352
Hong Kong (852) 868 9111 United Arab Emirates (971) (4) 349049
Italy (39) (2) 273 02041 U.K. (44) (1628) 897000
Japan (81) (3) 3345 7251 U.S. (1) (408) 492 1790
Returning Products for Repair
4/4/95
A product sent directly to 3Com for repair must first be assigned a Return
Materials Authorization (RMA) number. A product sent to 3Com without an
RMA number will be returned to the sender unopened, at the sender’s
expense.
To obtain an RMA number, call or fax:
Country Telephone Number Fax Number
U.S. and Canada (800) 876 3266, option 2 (408) 764 7120
Europe (44) (1442) 278000 (44) (1442) 236824
Outside Europe, U.S. and Canada (1) (408) 492 1790 (1) (408) 764 7290
Page 37

LIMITED WARRANTY
HARDWARE: 3Com warrants its hardware products to be free from defects in workmanship and materials, under normal use and service, for the
following lengths of time from the date of purchase from 3Com or its Authorized Reseller:
Internetworking products One year
Network adapters Lifetime
Ethernet stackable hubs and
Unmanaged Ethernet fixed port repeaters Lifetime* (One year if not registered)
*Power supply and fans in these stackable hubs and unmanaged repeatersOne year
Other hardware products One year
Spare parts and spares kits 90 days
If a product does not operate as warranted during the applicable warranty period, 3Com shall, at its option and expense, repair the defective
product or part, deliver to Customer an equivalent product or part to replace the defective item, or refund to Customer the purchase price paid
for the defective product. All products that are replaced will become the property of 3Com. Replacement products may be new or
reconditioned. Any replaced or repaired product or part has a ninety (90) day warranty or the remainder of the initial warranty period,
whichever is longer.
3Com shall not be responsible for any software, firmware, information, or memory data of Customer contained in, stored on, or integrated with
any products returned to 3Com pursuant to any warranty.
SOFTWARE: 3Com warrants that the software programs licensed from it will perform in substantial conformance to the program specifications
therefor for a period of ninety (90) days from the date of purchase from 3Com or its Authorized Reseller. 3Com warrants the magnetic media
containing software against failure during the warranty period. No updates are provided. 3Com's sole obligation hereunder shall be (at 3Com's
discretion) to refund the purchase price paid by Customer for any defective software products, or to replace any defective media with software
which substantially conforms to 3Com's applicable published specifications. Customer assumes responsibility for the selection of the
appropriate applications program and associated reference materials. 3Com makes no warranty that its software products will work in
combination with any hardware or applications software products provided by third parties, that the operation of the software products will be
uninterrupted or error free, or that all defects in the software products will be corrected. For any third party products listed in the 3Com
software product documentation or specifications as being compatible, 3Com will make reasonable efforts to provide compatibility, except
where the non-compatibility is caused by a “bug” or defect in the third party's product.
STANDARD WARRANTY SERVICE: Standard warranty service for hardware products may be obtained by delivering the defective product,
accompanied by a copy of the dated proof of purchase, to 3Com's Corporate Service Center or to an Authorized 3Com Service Center during
the applicable warranty period. Standard warranty service for software products may be obtained by telephoning 3Com's Corporate Service
Center or an Authorized 3Com Service Center, within the warranty period. Products returned to 3Com's Corporate Service Center must be
pre-authorized by 3Com with a Return Material Authorization (RMA) number marked on the outside of the package, and sent prepaid, insured,
and packaged appropriately for safe shipment. The repaired or replaced item will be shipped to Customer, at 3Com's expense, not later than
thirty (30) days after receipt by 3Com.
WARRANTIES EXCLUSIVE: IF A 3COM PRODUCT DOES NOT OPERATE AS WARRANTED ABOVE, CUSTOMER’S SOLE REMEDY SHALL BE REPAIR,
REPLACEMENT, OR REFUND OF THE PURCHASE PRICE PAID, AT 3COM’S OPTION. THE FOREGOING WARRANTIES AND REMEDIES ARE EXCLUSIVE
AND ARE IN LIEU OF ALL OTHER WARRANTIES, EXPRESS OR IMPLIED, EITHER IN FACT OR BY OPERATION OF LAW, STATUTORY OR OTHERWISE,
INCLUDING WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. 3COM NEITHER ASSUMES NOR AUTHORIZES ANY
OTHER PERSON TO ASSUME FOR IT ANY OTHER LIABILITY IN CONNECTION WITH THE SALE, INSTALLATION, MAINTENANCE OR USE OF ITS
PRODUCTS.
3COM SHALL NOT BE LIABLE UNDER THIS WARRANTY IF ITS TESTING AND EXAMINATION DISCLOSE THAT THE ALLEGED DEFECT IN THE
PRODUCT DOES NOT EXIST OR WAS CAUSED BY CUSTOMER'S OR ANY THIRD PERSON'S MISUSE, NEGLECT, IMPROPER INSTALLATION OR
TESTING, UNAUTHORIZED ATTEMPTS TO REPAIR, OR ANY OTHER CAUSE BEYOND THE RANGE OF THE INTENDED USE, OR BY ACCIDENT, FIRE,
LIGHTNING, OR OTHER HAZARD.
LIMITATION OF LIABILITY: IN NO EVENT, WHETHER BASED IN CONTRACT OR TORT (INCLUDING NEGLIGENCE) SHALL 3COM BE LIABLE FOR
INCIDENTAL, CONSEQUENTIAL, INDIRECT, SPECIAL, OR PUNITIVE DAMAGES OF ANY KIND, OR FOR LOSS OF REVENUE, LOSS OF BUSINESS, OR
OTHER FINANCIAL LOSS ARISING OUT OF OR IN CONNECTION WITH THE SALE, INSTALLATION, MAINTENANCE, USE, PERFORMANCE, FAILURE, OR
INTERRUPTION OF ITS PRODUCTS, EVEN IF 3COM OR ITS AUTHORIZED RESELLER HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES
Some states do not allow the exclusion of implied warranties or the limitation of incidental or consequential damages for consumer products,
so the above limitations and exclusions may not apply to you. This warranty gives you specific legal rights which may vary from state to state.
GOVERNING LAW: This Limited Warranty shall be governed by the laws of the state of California.
3Com Corporation
5400 Bayfront Plaza
Santa Clara, CA 95052-8145
(408) 764-5000
1/1/94
 Loading...
Loading...