Fortinet FortiWeb User Manual

WEB APPLICATION FIREWALL
FortiWeb™ 5.0 Patch 6
Administration Guide
Courtney Schwartz
Contributors:
George Csaba
Martijn Duijm
Patricia Siertsema
Idan Soen
Shiji Li
Qin Lu
Atsunobu Shiiya
Hao Xu
Shiqiang Xu
Forrest Zhang
FortiWeb 5.0 Patch 6 Administration Guide
February 19, 2014
2nd Edition
Copyright© 2014 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, and FortiGuard® are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance metrics contained herein were attained in internal lab tests under ideal conditions, and performance may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to the performance metrics herein. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any guarantees. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.
Technical Documentation |
http://help.fortinet.com |
Knowledge Base |
http://kb.fortinet.com |
Forums |
https://support.fortinet.com/forum |
Customer Service & Support |
https://support.fortinet.com |
Training |
http://training.fortinet.com |
FortiGuard Threat Research & Response |
http://www.fortiguard.com |
License |
http://www.fortinet.com/doc/legal/EULA.pdf |
Document Feedback |
Email: techdocs@fortinet.com |
Table of contents
Introduction..................................................................................................... |
13 |
Benefits.................................................................................................................. |
13 |
Architecture ........................................................................................................... |
14 |
Scope..................................................................................................................... |
14 |
What’s new...................................................................................................... |
16 |
Documentation enhancements.............................................................................. |
21 |
Key concepts .................................................................................................. |
22 |
Workflow................................................................................................................ |
22 |
Sequence of scans ................................................................................................ |
23 |
Solutions for specific web attacks......................................................................... |
27 |
HTTP/HTTPS threats ....................................................................................... |
27 |
DoS attacks ..................................................................................................... |
32 |
HTTP sessions & security ...................................................................................... |
34 |
FortiWeb sessions vs. web application sessions ............................................ |
37 |
Sessions & FortiWeb HA.................................................................................. |
39 |
Example: Magento & FortiWeb sessions during failover ........................... |
39 |
HA heartbeat & synchronization ............................................................................ |
40 |
Data that is not synchronized by HA ............................................................... |
41 |
Configuration settings that are not synchronized by HA ................................. |
42 |
How HA chooses the active appliance ............................................................ |
44 |
How to use the web UI .......................................................................................... |
45 |
System requirements ....................................................................................... |
45 |
URL for access ................................................................................................ |
45 |
Workflow .......................................................................................................... |
46 |
Permissions...................................................................................................... |
47 |
Trusted hosts ............................................................................................. |
51 |
Maximum concurrent administrator sessions.................................................. |
51 |
Global web UI & CLI settings........................................................................... |
51 |
Buttons, menus, & the displays ....................................................................... |
55 |
Deleting entries .......................................................................................... |
57 |
Renaming entries ....................................................................................... |
58 |
Shutdown............................................................................................................... |
58 |
How to set up your FortiWeb......................................................................... |
60 |
Appliance vs. VMware ........................................................................................... |
60 |
Registering your FortiWeb ..................................................................................... |
60 |
Fortinet |
3 |
FortiWeb 5.0 Patch 6 Administration Guide |
Planning the network topology .............................................................................. |
61 |
How to choose the operation mode ................................................................ |
61 |
Supported features in each operation mode ............................................. |
62 |
Matching topology with operation mode & HA mode................................ |
63 |
Topology for reverse proxy mode.................................................................... |
63 |
Topology for either of the transparent modes ................................................. |
65 |
Topology for offline protection mode .............................................................. |
67 |
Topologies for high availability (HA) clustering ................................................ |
68 |
Connecting to the web UI or CLI ........................................................................... |
71 |
Connecting to the web UI ................................................................................ |
72 |
Connecting to the CLI...................................................................................... |
74 |
Updating the firmware ........................................................................................... |
77 |
Testing new firmware before installing it ......................................................... |
77 |
Installing firmware ............................................................................................ |
79 |
Updating firmware on an HA pair............................................................... |
83 |
Installing alternate firmware ............................................................................. |
84 |
Booting from the alternate partition ........................................................... |
87 |
Changing the “admin” account password............................................................. |
90 |
Setting the system time & date.............................................................................. |
91 |
Setting the operation mode ................................................................................... |
94 |
Configuring a high availability (HA) FortiWeb cluster............................................. |
97 |
Replicating the configuration without FortiWeb HA (external HA) ................. |
107 |
Configuring the network settings......................................................................... |
111 |
Network interface or bridge? ......................................................................... |
111 |
Configuring the network interfaces.......................................................... |
113 |
Adding VLAN subinterfaces ............................................................... |
117 |
Link aggregation ...................................................................................... |
120 |
Configuring a bridge (V-zone) .................................................................. |
122 |
Adding a gateway .......................................................................................... |
125 |
Configuring DNS settings .............................................................................. |
130 |
Connecting to FortiGuard services...................................................................... |
134 |
Choosing the virus signature database & decompression buffer.................. |
138 |
Accessing FortiGuard via a web proxy .......................................................... |
140 |
How often does Fortinet provide FortiGuard updates for FortiWeb? ............ |
140 |
Scheduling automatic signature updates ...................................................... |
141 |
Manually initiating update requests ............................................................... |
144 |
Uploading signature & geography-to-IP updates .......................................... |
146 |
Configuring basic policies ................................................................................... |
148 |
Example 1: Configuring a policy for HTTP via auto-learning......................... |
148 |
Example 2: Configuring a policy for HTTPS .................................................. |
149 |
Example 3: Configuring a policy for load balancing ...................................... |
150 |
Fortinet |
4 |
FortiWeb 5.0 Patch 6 Administration Guide |
Auto-learning ....................................................................................................... |
151 |
How to adapt auto-learning to dynamic URLs & unusual parameters .......... |
151 |
Configuring URL interpreters ................................................................... |
152 |
Example: URL interpreter for a JSP application ................................ |
156 |
Example: URL interpreter for Microsoft Outlook Web App 2007....... |
156 |
Example: URL interpreter for WordPress........................................... |
160 |
Grouping URL interpreters....................................................................... |
165 |
Recognizing data types ................................................................................. |
166 |
Predefined data types.............................................................................. |
166 |
Grouping predefined data types .............................................................. |
170 |
Recognizing suspicious requests .................................................................. |
171 |
Predefined suspicious request URLs....................................................... |
172 |
Configuring custom suspicious request URLs ........................................ |
173 |
Grouping custom suspicious request URLs ............................................ |
174 |
Grouping all suspicious request URLs..................................................... |
175 |
Configuring an auto-learning profile .............................................................. |
177 |
Running auto-learning.................................................................................... |
180 |
Pausing auto-learning for a URL.................................................................... |
181 |
Viewing auto-learning reports........................................................................ |
182 |
Using the report navigation pane............................................................. |
183 |
Using the report display pane.................................................................. |
186 |
Overview tab ...................................................................................... |
186 |
Attacks tab ......................................................................................... |
188 |
About the attack count....................................................................... |
191 |
Visits tab............................................................................................. |
191 |
Parameters tab................................................................................... |
194 |
Cookies tab ........................................................................................ |
195 |
Generating a profile from auto-learning data................................................. |
196 |
Transitioning out of the auto-learning phase ................................................. |
199 |
Removing old auto-learning data................................................................... |
200 |
Testing your installation ....................................................................................... |
201 |
Reducing false positives ................................................................................ |
202 |
Testing for vulnerabilities & exposure ............................................................ |
203 |
Expanding the initial configuration................................................................. |
203 |
Switching out of offline protection mode............................................................. |
205 |
Backups......................................................................................................... |
206 |
Restoring a previous configuration...................................................................... |
210 |
Administrators .............................................................................................. |
212 |
Configuring access profiles ................................................................................. |
216 |
Grouping remote authentication queries for administrators................................ |
218 |
Changing an administrator’s password............................................................... |
219 |
Fortinet |
5 |
FortiWeb 5.0 Patch 6 Administration Guide |
Users.............................................................................................................. |
221 |
Authentication styles............................................................................................ |
221 |
Via the “Authorization:” header in the HTTP/HTTPS protocol....................... |
221 |
Via forms embedded in the HTML ................................................................. |
222 |
Via a personal certificate................................................................................ |
224 |
Offloading HTTP authentication & authorization ................................................. |
225 |
Configuring local end-user accounts............................................................. |
227 |
Configuring queries for remote end-user accounts....................................... |
228 |
Configuring LDAP queries........................................................................ |
228 |
Configuring RADIUS queries.................................................................... |
233 |
Configuring NTLM queries ....................................................................... |
235 |
Grouping users .............................................................................................. |
236 |
Applying user groups to an authorization realm ............................................ |
238 |
Grouping authorization rules.................................................................... |
240 |
Single sign-on (SSO)............................................................................................ |
243 |
Example: Enforcing complex passwords ............................................................ |
247 |
Defining your web servers & load balancers ............................................. |
248 |
Protected web servers vs. protected/allowed host names ................................. |
248 |
Defining your protected/allowed HTTP “Host:” header names ........................... |
249 |
Defining your web servers ................................................................................... |
251 |
Defining your web server by its IP address ................................................... |
251 |
Defining your web server by its DNS domain name ...................................... |
253 |
Configuring server up/down checks.............................................................. |
254 |
Grouping your web servers into server farms................................................ |
256 |
Routing based upon URL or “Host:” name.............................................. |
262 |
Example: Routing according to URL/path ............................................... |
265 |
Example: Routing according to the HTTP “Host:” field ........................... |
265 |
Defining your proxies, clients, & X-headers......................................................... |
266 |
Indicating the original client’s IP to back-end web servers ........................... |
267 |
Indicating to back-end web servers that the client’s request was HTTPS.... |
269 |
Blocking the attacker’s IP, not your load balancer........................................ |
269 |
Configuring virtual servers on your FortiWeb ...................................................... |
272 |
Defining your network services............................................................................ |
274 |
Defining custom services............................................................................... |
274 |
Predefined services ....................................................................................... |
275 |
Enabling or disabling traffic forwarding to your servers ...................................... |
275 |
Secure connections (SSL/TLS) ................................................................... |
277 |
Offloading vs. inspection ..................................................................................... |
277 |
Supported cipher suites & protocol versions ...................................................... |
279 |
Uploading trusted CAs’ certificates..................................................................... |
280 |
Grouping trusted CAs’ certificates ................................................................ |
282 |
Fortinet |
6 |
FortiWeb 5.0 Patch 6 Administration Guide |
How to offload or inspect HTTPS........................................................................ |
283 |
Generating a certificate signing request ........................................................ |
285 |
Uploading a server certificate ........................................................................ |
289 |
Supplementing a server certificate with its signing chain........................ |
291 |
How to apply PKI client authentication (personal certificates) ............................ |
293 |
Example: Generating & downloading a personal certificate from |
|
Microsoft Windows 2003 Server ................................................................. |
297 |
Example: Downloading the CA’s certificate from |
|
Microsoft Windows 2003 Server ................................................................. |
306 |
Example: Importing the personal certificate & private key to a client’s trust store |
|
on Microsoft Windows 7.............................................................................. |
307 |
Uploading the CA’s certificate to FortiWeb’s trusted CA store ..................... |
315 |
Configuring FortiWeb to validate client certificates ....................................... |
316 |
Revoking certificates ........................................................................................... |
318 |
Revoking certificates by OCSP query............................................................ |
319 |
How to export/back up certificates & private keys.............................................. |
320 |
Access control.............................................................................................. |
321 |
Restricting access to specific URLs .................................................................... |
321 |
Grouping access rules per combination of URL & “Host:”............................ |
324 |
Combination access control & rate limiting ......................................................... |
325 |
Blacklisting & whitelisting clients ......................................................................... |
329 |
Blacklisting source IPs with poor reputation ................................................. |
329 |
Blacklisting countries & regions..................................................................... |
331 |
Blacklisting & whitelisting clients individually by source IP ........................... |
335 |
Blacklisting content scrapers, search engines, web crawlers, & other robots ..... |
|
337 |
|
Rate limiting .................................................................................................. |
338 |
DoS prevention .................................................................................................... |
338 |
Configuring application-layer DoS protection ............................................... |
338 |
Limiting the total HTTP request rate from an IP ...................................... |
339 |
Example: HTTP request rate limit per IP............................................ |
344 |
Limiting TCP connections per IP address by session cookie.................. |
344 |
Example: TCP connection per session limit ...................................... |
347 |
Preventing an HTTP request flood........................................................... |
347 |
Example: HTTP request flood prevention .......................................... |
351 |
Configuring network-layer DoS protection .................................................... |
351 |
Limiting TCP connections per IP address ............................................... |
351 |
Example: TCP flood prevention ......................................................... |
354 |
Preventing a TCP SYN flood.................................................................... |
354 |
Grouping DoS protection rules ...................................................................... |
355 |
Preventing automated requests........................................................................... |
357 |
Example: Preventing email directory harvesting............................................ |
360 |
Configuring browser enforcement exceptions............................................... |
361 |
Preventing brute force logins............................................................................... |
362 |
Fortinet |
7 |
FortiWeb 5.0 Patch 6 Administration Guide |
Rewriting & redirecting ................................................................................ |
367 |
Example: HTTP-to-HTTPS redirect ..................................................................... |
373 |
Example: Full host name/URL translation ........................................................... |
376 |
Example: Sanitizing poisoned HTML................................................................... |
380 |
Example: Inserting & deleting body text .............................................................. |
382 |
Example: Rewriting URLs using regular expressions .......................................... |
383 |
Example: Rewriting URLs using variables ........................................................... |
384 |
Grouping rewriting & redirection rules ................................................................. |
385 |
Blocking known attacks & data leaks ........................................................ |
387 |
Configuring action overrides or exceptions to data leak & attack detection signa- |
|
tures................................................................................................................... |
398 |
Finding signatures that are disabled or “Alert Only”...................................... |
401 |
Defining custom data leak & attack signatures ................................................... |
401 |
Example: ASP .Net version & other multiple server detail leaks.................... |
406 |
Example: Zero-day XSS................................................................................. |
407 |
Example: Local file inclusion fingerprinting via Joomla ................................. |
409 |
Enforcing page order that follows application logic ............................................ |
411 |
Specifying URLs allowed to initiate sessions ...................................................... |
415 |
Preventing zero-day attacks ....................................................................... |
421 |
Validating parameters (“input rules”) ................................................................... |
421 |
Bulk changes to input validation rules ........................................................... |
428 |
Defining custom data types ........................................................................... |
429 |
Preventing tampering with hidden inputs ............................................................ |
430 |
Specifying allowed HTTP methods...................................................................... |
436 |
Configuring allowed method exceptions ....................................................... |
438 |
HTTP/HTTPS protocol constraints ...................................................................... |
440 |
Configuring HTTP protocol constraint exceptions ........................................ |
446 |
Limiting file uploads ..................................................................................... |
451 |
Compression & decompression.................................................................. |
456 |
Configuring compression/decompression exemptions....................................... |
456 |
Configuring compression offloading.................................................................... |
457 |
Configuring decompression to enable scanning & rewriting ............................... |
460 |
Policies .......................................................................................................... |
463 |
How operation mode affects server policy behavior ........................................... |
463 |
Configuring the global object white list ............................................................... |
464 |
Uploading a custom error page........................................................................... |
467 |
Configuring a protection profile for inline topologies........................................... |
468 |
Configuring a protection profile for an out-of-band topology or asynchronous mode |
|
of operation ....................................................................................................... |
477 |
Fortinet |
8 |
FortiWeb 5.0 Patch 6 Administration Guide |
Configuring a server policy .................................................................................. |
483 |
Enabling or disabling a policy ........................................................................ |
497 |
Anti-defacement........................................................................................... |
498 |
Reverting a defaced web site .............................................................................. |
503 |
Compliance ................................................................................................... |
504 |
Database security ................................................................................................ |
504 |
Authorization........................................................................................................ |
504 |
Preventing data leaks .......................................................................................... |
504 |
Vulnerability scans ............................................................................................... |
505 |
Preparing for the vulnerability scan ............................................................... |
506 |
Live web sites .......................................................................................... |
506 |
Network accessibility ............................................................................... |
506 |
Traffic load & scheduling.......................................................................... |
506 |
Scheduling web vulnerability scans............................................................... |
507 |
Configuring vulnerability scan settings .......................................................... |
508 |
Running vulnerability scans ........................................................................... |
513 |
Manually starting & stopping a vulnerability scan.......................................... |
515 |
Viewing vulnerability scan reports ................................................................. |
516 |
Scan report contents ............................................................................... |
516 |
Downloading vulnerability scan reports......................................................... |
517 |
Advanced/optional system settings ........................................................... |
519 |
Changing the FortiWeb appliance’s host name................................................... |
519 |
Fail-to-wire for power loss/reboots ..................................................................... |
520 |
Advanced settings ............................................................................................... |
521 |
Example: Setting a separate rate limit for shared Internet connections........ |
523 |
Monitoring your system ............................................................................... |
525 |
The dashboard..................................................................................................... |
525 |
System Information widget ............................................................................ |
528 |
FortiGuard Information widget....................................................................... |
530 |
CLI Console widget........................................................................................ |
534 |
System Resources widget ............................................................................. |
536 |
Attack Log Console widget............................................................................ |
536 |
Real Time Monitor widget .............................................................................. |
537 |
Event Log Console widget............................................................................. |
538 |
Server Status widget...................................................................................... |
538 |
Policy Sessions widget .................................................................................. |
540 |
Operation widget ........................................................................................... |
540 |
RAID level & disk statuses ................................................................................... |
541 |
Fortinet |
9 |
FortiWeb 5.0 Patch 6 Administration Guide |
Logging ................................................................................................................ |
542 |
About logs & logging...................................................................................... |
543 |
Log types ................................................................................................. |
543 |
Log severity levels.................................................................................... |
544 |
Log rate limits .......................................................................................... |
544 |
Configuring logging........................................................................................ |
545 |
Enabling log types, packet payload retention, & resource shortage alerts .... |
|
546 |
|
Configuring log destinations .................................................................... |
549 |
Obscuring sensitive data in the logs........................................................ |
552 |
Configuring Syslog settings ..................................................................... |
554 |
Configuring FortiAnalyzer policies ........................................................... |
555 |
Configuring triggers ................................................................................. |
557 |
Viewing log messages ................................................................................... |
557 |
Viewing a single log message as a table ................................................. |
562 |
Viewing packet payloads ......................................................................... |
563 |
Switching between Raw & Formatted log views...................................... |
564 |
Displaying & arranging log columns......................................................... |
566 |
Filtering log messages ............................................................................. |
567 |
Downloading log messages..................................................................... |
569 |
Deleting log files....................................................................................... |
571 |
Coalescing similar attack log messages.................................................. |
572 |
Searching attack logs .............................................................................. |
573 |
Alert email ............................................................................................................ |
576 |
Configuring email settings ............................................................................. |
576 |
Configuring alert email for event logs ............................................................ |
578 |
SNMP traps & queries ......................................................................................... |
580 |
Configuring an SNMP community ................................................................. |
581 |
MIB support ................................................................................................... |
586 |
Reports ................................................................................................................ |
586 |
Customizing the report’s headers, footers, & logo ........................................ |
589 |
Restricting the report’s scope ....................................................................... |
590 |
Choosing the type & format of a report profile .............................................. |
592 |
Scheduling reports......................................................................................... |
595 |
Selecting the report’s file type & email delivery............................................. |
595 |
Viewing & downloading generated reports.................................................... |
597 |
Data analytics ................................................................................................ |
598 |
Configuring policies to gather data.......................................................... |
598 |
Updating data analytics definitions.......................................................... |
598 |
Viewing web site statistics ....................................................................... |
599 |
Filtering the data analytics report....................................................... |
603 |
Bot analysis.................................................................................................... |
605 |
Monitoring currently blocked IPs......................................................................... |
606 |
FortiGuard updates.............................................................................................. |
606 |
Vulnerability scans ............................................................................................... |
607 |
Fortinet |
10 |
FortiWeb 5.0 Patch 6 Administration Guide |
Fine-tuning & best practices ....................................................................... |
608 |
Hardening security............................................................................................... |
608 |
Topology ........................................................................................................ |
608 |
Administrator access ..................................................................................... |
609 |
User access ................................................................................................... |
611 |
Signatures & patches..................................................................................... |
612 |
Buffer hardening ............................................................................................ |
612 |
Enforcing valid, applicable HTTP................................................................... |
614 |
Sanitizing HTML application inputs ............................................................... |
614 |
Improving performance ....................................................................................... |
614 |
System performance...................................................................................... |
614 |
Antivirus performance.................................................................................... |
615 |
Regular expression performance tips............................................................ |
615 |
Logging performance..................................................................................... |
617 |
Report performance....................................................................................... |
618 |
Auto-learning performance ............................................................................ |
619 |
Vulnerability scan performance ..................................................................... |
623 |
Packet capture performance ......................................................................... |
623 |
Improving fault tolerance ..................................................................................... |
623 |
Alerting the SNMP manager when HA switches the primary appliance........ |
624 |
Reducing false positives...................................................................................... |
624 |
Regular backups.................................................................................................. |
628 |
Downloading logs in RAM before shutdown or reboot ....................................... |
629 |
Troubleshooting ........................................................................................... |
630 |
Tools .................................................................................................................... |
630 |
Ping & traceroute ........................................................................................... |
630 |
Log messages................................................................................................ |
631 |
Diff.................................................................................................................. |
632 |
Packet capture............................................................................................... |
633 |
Diagnostic commands in the CLI................................................................... |
638 |
How to troubleshoot ............................................................................................ |
638 |
Establishing a system baseline...................................................................... |
638 |
Determining the source of the problem ......................................................... |
639 |
Planning & access privileges ......................................................................... |
640 |
Fortinet |
11 |
FortiWeb 5.0 Patch 6 Administration Guide |
Solutions by issue type........................................................................................ |
640 |
Connectivity issues ........................................................................................ |
641 |
Checking hardware connections ............................................................. |
641 |
Examining the ARP table ......................................................................... |
642 |
Checking routing...................................................................................... |
642 |
Testing for connectivity with ping ...................................................... |
644 |
Testing routes & latency with traceroute ........................................... |
648 |
Examining the routing table ..................................................................... |
651 |
Checking port assignments ..................................................................... |
652 |
Performing a packet trace........................................................................ |
652 |
Debugging the packet processing flow ................................................... |
653 |
Checking the SSL/TLS handshake & encryption..................................... |
653 |
Resource issues............................................................................................. |
654 |
Killing system-intensive processes.......................................................... |
654 |
Monitoring traffic load.............................................................................. |
654 |
Preparing for attacks................................................................................ |
655 |
Login issues ................................................................................................... |
655 |
Checking user authentication policies ..................................................... |
655 |
When an administrator account cannot log in from a specific IP ............ |
656 |
Remote authentication query failures ...................................................... |
656 |
Resetting passwords ............................................................................... |
656 |
Data storage issues ....................................................................................... |
657 |
Bootup issues ................................................................................................ |
658 |
Hard disk corruption or failure ................................................................. |
658 |
Power supply failure................................................................................. |
660 |
Resetting the configuration.................................................................................. |
662 |
Restoring firmware (“clean install”)...................................................................... |
663 |
Appendix A: Port numbers........................................................................... |
666 |
Appendix B: Maximum configuration values ............................................. |
669 |
Maximum values on FortiWeb-VM ...................................................................... |
669 |
Appendix C: Supported RFCs, W3C, & IEEE standards............................ |
671 |
RFCs .................................................................................................................... |
671 |
W3C standards .................................................................................................... |
671 |
IEEE standards .................................................................................................... |
672 |
Appendix D: Regular expressions............................................................... |
673 |
Regular expression syntax................................................................................... |
673 |
What are back-references? ........................................................................... |
678 |
Cookbook regular expressions............................................................................ |
680 |
Language support................................................................................................ |
682 |
Index .............................................................................................................. |
684 |
Fortinet |
12 |
FortiWeb 5.0 Patch 6 Administration Guide |
Introduction
Welcome, and thank you for selecting Fortinet products for your network.
FortiWeb hardware and FortiWeb-VM virtual appliance models are available that are suitable for medium and large enterprises, as well as service providers.
Benefits
FortiWeb is designed specifically to protect web servers.
FortiWeb web application firewalls (WAF) provide specialized application layer threat detection and protection for HTTP or HTTPS services such as:
•Apache Tomcat
•nginx
•Microsoft IIS
•JBoss
•IBM Lotus Domino
•Microsoft SharePoint
•Microsoft Outlook Web App (OWA)
•RPC and ActiveSync for Microsoft Exchange Server
•Joomla
•WordPress
•and many others
FortiWeb’s integrated web-specific vulnerability scanner can drastically reduces challenges associated with protecting regulated and confidential data by detecting your exposure to the latest threats, especially the OWASP Top 10.
In addition, FortiWeb’s HTTP firewall and denial-of-service (DoS) attack-prevention protect your Internet-facing web-based applications from attack and data theft. Using advanced techniques to provide bidirectional protection against sophisticated threats like SQL injection and cross-site scripting (XSS), FortiWeb helps you prevent identity theft, financial fraud, and corporate espionage. FortiWeb delivers the technology you need to monitor and enforce government regulations, industry best practices, and internal security policies, including firewalling and patching requirements from PCI DSS.
FortiWeb’s application-aware firewalling and load balancing engine can:
•Secure HTTP applications that are often gateways into valuable databases
•Prevent and reverse defacement
•Improve application stability
•Monitor servers for downtime & connection load
•Reduces response times
•Accelerate SSL/TLS *
•Accelerate compression/decompression
•Rewrite content on the fly
Fortinet |
13 |
FortiWeb 5.0 Patch 6 Administration Guide |
* On VM models, acceleration is due to offloading the cryptography burden from the back-end server. On hardware models, cryptography is also hardware-accelerated via ASIC chips.
FortiWeb significantly reduces deployment costs by consolidating WAF, hardware acceleration, load balancing, and vulnerability scanning into a single device with no per-user pricing. Those features drastically reduce the time required to protect your regulated, Internet-facing data and eases the challenges associated with policy enforcement and regulatory compliance.
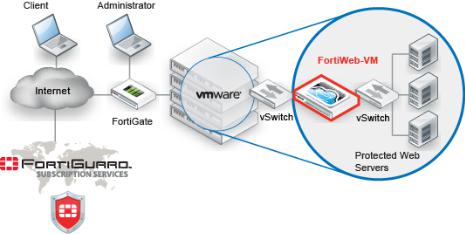
Architecture
Figure 1: Basic topology
FortiWeb can be deployed in a one-arm topology, but is more commonly positioned inline to intercept all incoming clients’ connections and redistribute them to your servers. FortiWeb has TCPand HTTP-specific firewalling capability. Because it is not designed to provide security to non-HTTP applications, it should be deployed behind a firewall such as FortiGate that focuses on security for other protocols that may be forwarded to your back-end servers, such as FTP and SSH.
Once the appliance is deployed, you can configure FortiWeb via its web UI and CLI, from a web browser and terminal emulator on your management computer.
Scope
This document describes how to set up your FortiWeb appliance. For both the hardware and virtual appliance versions of FortiWeb, it describes how to complete first-time system deployment, including planning the network topology.
It also describes how to use the web user interface (web UI), and contains lists of default utilized port numbers, configuration limits, and supported standards.
This document assumes, if you have installed the virtual appliance version (FortiWeb-VM), that you have already followed the instructions in the FortiWeb-VM Install Guide.
Fortinet |
14 |
FortiWeb 5.0 Patch 6 Administration Guide |
After completing “How to set up your FortiWeb” on page 60:
•You will have administrative access to the web UI and/or CLI.
•You will have completed firmware updates, if any.
•The system time, DNS settings, administrator password, and network interfaces will be configured.
•You will have set the operation mode.
•You will have configured basic logging.
•You will have created at least one server policy.
•You may have completed at least one phase of auto-learning to jump-start your configuration.
Once that basic installation is complete, you can use the rest of this document to use the web UI to:
•Update the FortiWeb appliance.
•Reconfigure features.
•Use advanced features, such as anti-defacement.
•Diagnose problems.
This document does not provide a reference for the command line interface (CLI). For that information, see the FortiWeb CLI Reference.
This document is intended for administrators, not end users. If you are accessing a web site protected by FortiWeb, please contact your system administrator.
Fortinet |
15 |
FortiWeb 5.0 Patch 6 Administration Guide |
What’s new
The list below contains features new or changed since FortiWeb 5.0. For upgrade information, see the Release Notes available with the firmware and “Updating the firmware” on page 77.
FortiWeb 5.0 Patch 6
• No new features. Bug fixes only.
FortiWeb 5.0 Patch 5
•RADIUS vendor-specific attributes for access profiles — If your administrator accounts authenticate via a RADIUS query, you can assign their access profile using RFC 2548 Microsoft Vendor-specific RADIUS Attributes. See Access Profile in “Administrators” on page 212 and “Configuring RADIUS queries” on page 233.
FortiWeb 5.0 Patch 4
•Bulk edits for parameter validation rules — Rather than individually editing each rule, you can now replace the Action, Trigger Policy, and/or Severity of multiple rules simultaneously. See “Bulk changes to input validation rules” on page 428.
•Namibian time zone support — System time and date settings now support the Namibian time zone. See “Setting the system time & date” on page 91.
FortiWeb 5.0 Patch 3
• No new features. Bug fixes only.
FortiWeb 5.0 Patch 2
•Hidden fields protection for HTTPS — You can now use the Fetch URL dialog in the GUI to help you tamper-proof hidden inputs in HTTPS requests. See “Preventing tampering with hidden inputs” on page 430.
•Indicating original service to back-end servers— When offloading SSL/TLS, you can now use an HTTP X-header to indicate to back-end web servers that the original client’s request was, in fact, encrypted. See “Indicating to back-end web servers that the client’s request was HTTPS” on page 269.
•More Microsoft file types for file upload restrictions — There are now signatures specifically for Microsoft Office Open XML file types such as .docx. See “Limiting file uploads” on page 451.
•Per CPU SNMP queries— You can now monitor the usage of each CPU in multi-CPU appliances. See “MIB support” on page 586.
•NMI and COMlog support — FortiWeb 3000D, 3000DFsx, and 4000D models that have NMI buttons now have firmware support. This can be useful for carriers that require extensive debugging capabilities. See your model’s QuickStart Guide and the FortiWeb NMI & COMlog Technical Note.
•RAM-only traffic log support — To reduce wear and tear on your hard disks when you require traffic logs, you can now disable hard disk storage of traffic logs and use RAM only. See the FortiWeb CLI Reference.
Fortinet |
16 |
FortiWeb 5.0 Patch 6 Administration Guide |

FortiWeb 5.0 Patch 1
•Site publishing— You can now easily publish Microsoft Outlook Web Access (OWA), SharePoint, Lync and other web applications. FortiWeb streamlines access to the applications by providing offloaded authentication with optional single sign-on (SSO) functionality. See Site Publish and “Single sign-on (SSO)” on page 243.
•“Alert Only” action for individual signatures — To provide better flexibility, you can now choose an Alert Only action for individual attack signatures. When configuring a protection profile, save it, then return to it and click the Advanced Mode button. Select a signature category from the menu. When individual signatures appear in the pane on the right, click the signature’s row to select it, then mark the Alert Only check box in the Signature tab. See “Configuring action overrides or exceptions to data leak & attack detection signatures” on page 398.
•Attack signature filters — In the Advanced mode while configuring attack signatures, in the bottom of the navigation tree on the left, new categories have been added that display individual signatures that have been disabled, or whose Alert Only check box is marked. Previously, the Search item in the tree only enabled you to search for signature IDs. See “Finding signatures that are disabled or “Alert Only”” on page 401.
•Custom global white list objects— You can now add your own URLs, parameters, and cookies that you don’t want FortiWeb to inspect. Previously, you could only white list predefined objects. See “Configuring the global object white list” on page 464.
•Advanced/combination access control rule enhancement— When configuring HTTP header conditions for combination access control rules, regular expressions are now supported. See “Combination access control & rate limiting” on page 325.
•Performance enhancements— Memory utilization and other performance enhancements have been made. For example, the antivirus database now loads into memory only while antivirus is enabled in a policy.
•New geo-to-IP database format supported
FortiWeb 5.0
Back up all parts of the configuration and data before updating the firmware to FortiWeb 5.0. Some backup types do not include the full configuration. For full backup instructions, see “Backups” on page 206.
FortiWeb 5.0 configuration files are not compatible with previous firmware versions. Many fundamental changes have been made to its configuration file structure. If you later decide to downgrade to FortiWeb 4.4.7 or earlier, your FortiWeb appliance will lose its configuration. To restore the configuration, you will need a backup that is compatible with the older firmware.
•FortiWeb 3000D, 3000DFsx, and 4000D support — All three models support SSL/TLS acceleration with CP8 ASIC chips and have bypass/fail-to-wire port pairs. For hardware details, see your model’s QuickStart Guide and “Fail-to-wire for power loss/reboots” on page 520. For specifications of maximum supported objects, see “Appendix B: Maximum configuration values” on page 669.
•Password recovery — If you have forgotten the password, but have physical access to your FortiWeb, you can now reset the password for the admin administrator account. See “Resetting passwords” on page 656.
Fortinet |
17 |
FortiWeb 5.0 Patch 6 Administration Guide |

•IPv6 support— If FortiWeb is operating in reverse proxy mode, the following features now support IPv6-to-IPv6 forwarding, as well as NAT64, to support environments where legacy back-end equipment only supports IPv4.
•IP/Netmask for all types of network interfaces, DNS settings, and Gateway and Destination IP/Mask for IP-layer static routes
•Virtual Server/V-zone
•Physical Server/Domain Server/Server Farm
•Server Health Check
•Protected Servers
•Session Management
•Cookie Poisoning Detection
•Signatures
•Custom Access
•Parameter Validation
•Hidden Fields Protection
•File Upload Restriction
•HTTP Protocol Constraints
•Brute Force Login
•URL Access
•Page Access (page order)
•Start Pages
•Allow Method
•IP List (manual, individual IP blacklisting/whitelisting)
•File Compress/File Uncompress
•Auto-learning
•Vulnerability scans
•Global white list objects
•Chunk decoding
•FortiGuard server IP overrides
These are not yet supported:
If a policy has any virtual servers, server farms, physical servers, or domain servers with IPv6 addresses, it will not apply these features, even if they are selected.
Fortinet |
18 |
FortiWeb 5.0 Patch 6 Administration Guide |
•X-Forwarded-For
•Shared IP
•Policy bypasses for known search engines
•Geo IP
•DoS Protection
•IP Reputation
•URL Rewriting (also redirection)
•HTTP Authentication and LDAP, RADIUS, and NTLM profiles
•Data Analytics
•Log-based reports
•Alert email
•Syslog and FortiAnalyzer IP addresses
•NTP
•FTP immediate/scheduled
•OCSP/SCEP
•Anti-defacement
•HA/Configuration sync
•exec restore
•exec backup
•exec traceroute
•exec telnet
•Challenge action for application-level anti-DoS — Rather than simply blocking all clients that exceed your rate limit or trigger other DoS sensors, you can now choose to test the client first — to return a web page that uses a script to assess whether the client is a web browser or an automated tool favored by attackers. In this way, you can allow higher rate limits for people than automated tools. See “Limiting the total HTTP request rate from an IP” on page 339 and “Preventing an HTTP request flood” on page 347.
•Search engine access improved — You can now allow known search engines such as Google, Yahoo!, Baidu and Bing to be exempt from DoS sensors, brute force login sensors, HTTP protocol constraints, and combination rate & access control (called “advanced protection” and “custom policies” in the web UI). See Allow Known Search Engines in “Configuring a protection profile for inline topologies” on page 468 or “Configuring a protection profile for an out-of-band topology or asynchronous mode of operation” on page 477.
•Robot control simplified — Control of known malicious automated tools has been simplified, and custom robot definitions removed. See Bad Robot in “Blocking known attacks & data leaks” on page 387.
•Robot monitoring report — To monitor search engines that may be abusing access, you can monitor throughput and transactions per second for each crawler from your GUI’s reports area. See “Bot analysis” on page 605.
•Dynamic rate threshold in Real Time Monitor widget — The Policy Summary widget has been renamed, and now scales its graph dynamically to best show you differences based upon your normal levels of traffic. See “Real Time Monitor widget” on page 537.
•HTTP status code customization — To prevent WAF fingerprinting that can be a precursor for evasive APT attackers, you can now modify the return codes such as 200 OK that
Fortinet |
19 |
FortiWeb 5.0 Patch 6 Administration Guide |

FortiWeb returns to clients when blocking violation traffic. See Error Page Return Code in “Configuring a server policy” on page 483.
•Seamless FortiWeb-VM vCPU license upgrades— Now you can increase the capacity of FortiWeb-VM to 2, 4, or 8 vCPUs without first invalidating the license. Previously, a new license could be uploaded only while the current license was invalid, thereby temporarily interrupting service. See the FortiWeb-VM Install Guide.
•Maximum physical servers increased — FortiWeb now supports up to 255 physical servers. Previously only 128 were possible. See “Defining your web server by its IP address” on page 251.
•Maximum input validation rules increased — FortiWeb now supports up to 1,024 parameters in the URL validation rule. See “Validating parameters (“input rules”)” on page 421.
•Erasure without alerts — A very high volume of attack logs, alert email, and that can be generated while blocking information disclosure when many protected web servers are misconfigured. To prevent this and allow you to focus on severe attacks, you can now choose to erase server information such as X-Powered-By: without generating any log messages. See Action in “Blocking known attacks & data leaks” on page 387.
•Support for subnets in URL access rules & manual blacklists/white lists— When specifying which source IP addresses are allowed to access your web apps, you can now specify multiple IP addresses by entering a subnet, rather than creating many individual rules. See “Restricting access to specific URLs” on page 321 and “Blacklisting & whitelisting clients individually by source IP” on page 335.
•RADIUS realm support— RADIUS accounts on servers that require the realm (e.g. admin@example.com or user@example.com) are now supported. No change to the FortiWeb configuration is required for end-user accounts. For administrators, modify the Administrator setting to include the realm name (e.g. @example.com).
•Fail-to-wire during reboot/shutdown— Previously, fail-to-wire only engaged during unexpected power loss, without a graceful shutdown. See “Fail-to-wire for power loss/reboots” on page 520.
•Threshold for shared IPs configurable — Previously, shared IP analysis was not configurable. See “Shared IP” on page 522.
•Reports like FortiGate 5.0 — Reports have been updated, and now reflect the same styles also found in FortiGate 5.0 firewalls. See “Reports” on page 586.
•Debugging commands on HA standby — You can now use the active FortiWeb HA appliance’s CLI to send diagnose debug commands through the HA link to the standby. Previously, you could only connect to standby appliances through the local console, or by triggering a failover so that the standby became active — network connectivity was only possible with the active appliance. See the FortiWeb CLI Reference.
•XML protection profiles removed — For protection against XML-related attacks, customers should now use the Illegal XML Format setting (see “Configuring a protection profile for inline topologies” on page 468 or “Configuring a protection profile for an out-of-band topology or asynchronous mode of operation” on page 477). Legacy configuration data related to XML protection profiles from FortiWeb 4.0 MR4 Patch 6 or previous versions of the firmware will be deleted during upgrade.
If your back-end web servers require extensive protection for a vulnerable XML parser, you should add 3rd-party XML protection to your security architecture. Unlike XML protection profiles in previous versions of FortiWeb, Illegal XML Format does not scan for conformity with the document object model (DOM)/DTD/W3C Schema, recursive payloads, Schema poisoning, or other advanced XML attacks. Failure to provide adequate XML protection could allow attackers to penetrate your network.
Fortinet |
20 |
FortiWeb 5.0 Patch 6 Administration Guide |
•Static routes moved— It is now located under the System > Network menu. See “Adding a gateway” on page 125.
•FortiGuard updates moved— It is now located under the System > Config menu, similar to FortiGate 5.0. Configuration of the antivirus database has also moved. See “Choosing the virus signature database & decompression buffer” on page 138.
•LDAP, RADIUS, NTLM profiles moved— They are now located under the new User > Remote Server menu to make obvious the dichotomy versus local authentication. See “Grouping remote authentication queries for administrators” on page 218 and “Configuring queries for remote end-user accounts” on page 228.
•Anti-defacement moved— It is now located under the Web Protection menu. See “Anti-defacement” on page 498.
Fortinet |
21 |
FortiWeb 5.0 Patch 6 Administration Guide |
Key concepts
This chapter defines basic FortiWeb concepts and terms.
If you are new to FortiWeb, or new to security, this chapter can help you to quickly understand.
See also
• Appliance vs. VMware
Workflow
Begin with “How to set up your FortiWeb” on page 60 for your initial deployment. These instructions will guide you to the point where you have a simple, verifiably working installation.
Ongoing use is located in the chapters after “How to set up your FortiWeb”. Once you have successfully deployed, ongoing use involves:
•Backups
•Updates
•Configuring optional features
•Adjusting policies if:
•New attack signatures become available
•Requirements change
•Fine-tuning performance
•Periodic web vulnerability scans if required by your compliance regime
•Monitoring for defacement or focused, innovative attack attempts from advanced persistent threats (APTs)
•Monitoring for accidentally blacklisted client IPs
•Using data analytics to show traffic patterns
Fortinet |
22 |
FortiWeb 5.0 Patch 6 Administration Guide |
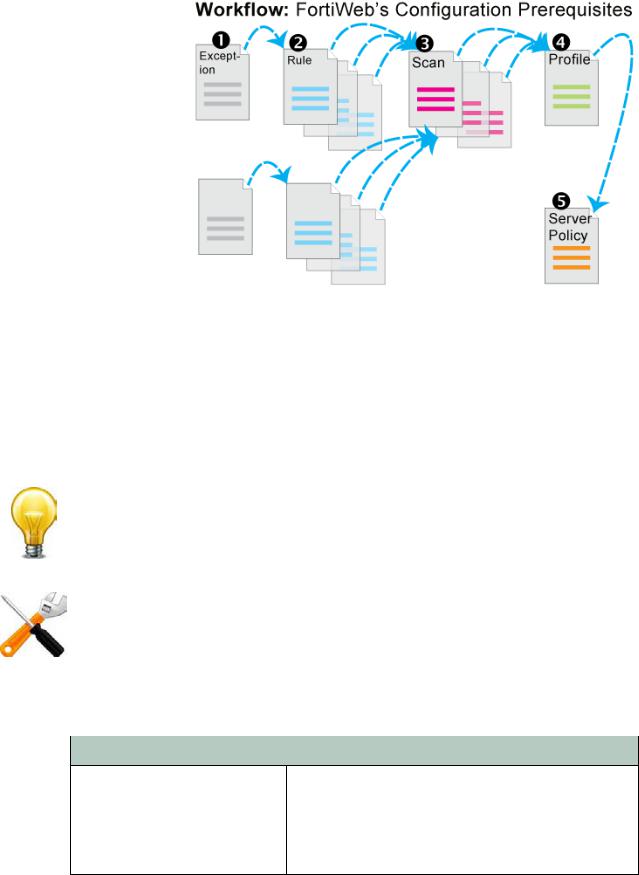
Except for features independent of policies such as anti-defacement, most features are configured before policies. Policies link protection components together and apply them. As such, policies usually should be configured last, not first.
Sequence of scans
FortiWeb appliances apply protection rules and perform protection profile scans in the following order of execution, which varies by whether you have applied a web protection profile. To understand the scan sequence, read from the top of the table (the first scan/action) towards the bottom (the last scan/action). Disabled scans are skipped.
To improve performance, block attackers using the earliest possible technique in the execution sequence and/or the least memory-consuming technique.
The blocking style varies by feature and configuration. For example, when detecting cookie poisoning, instead of resetting the TCP connection or blocking the HTTP request, you could log and remove the offending cookie. For details, see each specific feature.
Table 1: Execution sequence (web protection profile)
Scan/action |
Involves |
|
|
Request from client to server
TCP Connection Number Limit
(TCP Flood Prevention)
Source IP address of the client (depending on your configuration of X-header rules (see “Defining your proxies, clients, & X-headers” on page 266) this could be derived from either the SRC field in the IP header, or an HTTP header such as X-Forwarded-For: or
X-Real-IP:)
Fortinet |
23 |
FortiWeb 5.0 Patch 6 Administration Guide |
Table 1: Execution sequence (web protection profile)
Scan/action |
Involves |
||
|
|
||
Block Period |
Source IP address of the client (depending on your |
||
|
configuration of X-header rules (see “Defining your |
||
|
proxies, clients, & X-headers” on page 266) this could be |
||
|
derived from either the SRC field in the IP header, or an |
||
|
HTTP header such as X-Forwarded-For: or |
||
|
X-Real-IP:) |
||
|
|
||
IP List * |
Source IP address of the client in the IP layer |
||
(individual client IP black list or |
|
|
|
white list) |
|
|
|
|
|
||
Add X-Forwarded-For: |
Source IP address of the client in the HTTP layer |
||
Add X-Real-IP: |
|
|
|
|
|
||
IP Reputation |
Source IP address of the client (depending on your |
||
|
configuration of X-header rules (see “Defining your |
||
|
proxies, clients, & X-headers” on page 266) this could be |
||
|
derived from either the SRC field in the IP header, or an |
||
|
HTTP header such as X-Forwarded-For: or |
||
|
X-Real-IP:) |
||
|
|
||
Allow Known Search Engines |
Source IP address of the client in the IP layer |
||
|
|
||
Geo IP |
Source IP address of the client in the IP layer |
||
|
|
||
Host |
Host: |
||
(allowed/protected host name) |
|
|
|
|
|
|
|
Allow Method |
• |
Host: |
|
|
• URL in HTTP header |
||
|
• Request method in HTTP header |
||
|
|
|
|
HTTP Request Limit/sec |
• |
Cookie: |
|
|
• |
Session state |
|
|
• Responses from the JavaScript browser tests, if any |
||
|
|
|
|
Session Management |
• |
Cookie: |
|
|
• |
Session state |
|
|
|
||
TCP Connection Number Limit |
Source IP address of the client (depending on your |
||
(Malicious IP) |
configuration of X-header rules (see “Defining your |
||
proxies, clients, & X-headers” on page 266) this could be |
|||
|
|||
|
derived from either the SRC field in the IP header, or an |
||
|
HTTP header such as X-Forwarded-For: or |
||
|
X-Real-IP:) |
||
|
|
|
|
HTTP Request Limit/sec |
• |
Cookie: |
|
(HTTP Flood Prevention) |
• |
Session state |
|
|
• URL in the HTTP header |
||
|
|
|
|
Fortinet |
24 |
FortiWeb 5.0 Patch 6 Administration Guide |
Table 1: Execution sequence (web protection profile)
Scan/action |
Involves |
|
|
|
|
HTTP Request Limit/sec |
• |
ID field of the IP header |
(Standalone IP) |
• Source IP address of the client (depending on your |
|
|
||
or |
|
configuration of X-header rules (see “Defining your |
HTTP Request Limit/sec (Shared |
|
proxies, clients, & X-headers” on page 266) this could |
|
be derived from either the SRC field in the IP header, or |
|
IP) |
|
|
|
an HTTP header such as X-Forwarded-For: or |
|
|
|
|
(HTTP Access Limit) |
|
X-Real-IP:) |
|
|
|
HTTP Authentication |
Authorization: |
|
|
|
|
Global White List |
• |
Cookie: cookiesession1 |
|
• URL if /favicon.ico, AJAX URL parameters such as |
|
|
|
__LASTFOCUS, and others as updated by the |
|
|
FortiGuard Security Service |
|
|
|
URL Access |
• |
Host: |
|
• URL in HTTP header |
|
|
• Source IP of the client in the IP header |
|
|
|
|
Brute Force Login |
• |
Source IP address of the client (depending on your |
|
|
configuration of X-header rules (see “Defining your |
|
|
proxies, clients, & X-headers” on page 266) this could |
|
|
be derived from either the SRC field in the IP header, or |
|
|
an HTTP header such as X-Forwarded-For: or |
|
|
X-Real-IP:) |
|
• URL in the HTTP header |
|
|
|
|
HTTP Protocol Constraints |
• |
Content-Length: |
|
• |
Parameter length |
|
• |
Body length |
|
• |
Header length |
|
• |
Header line length |
|
• Count of Range: header lines |
|
|
• |
Count of cookies |
|
|
|
Cookie Poisoning Detection |
Cookie: |
|
|
|
|
Start Pages |
• |
Host: |
|
• URL in HTTP header |
|
|
• |
Session state |
|
|
|
Page Access |
• |
Host: |
(page order) |
• |
URL in HTTP header |
|
• |
Session state |
|
|
|
File Upload Restriction |
• |
Content-Length: |
|
• |
Content-Type: |
|
in PUT and POST requests |
|
|
|
|
Fortinet |
25 |
FortiWeb 5.0 Patch 6 Administration Guide |

Table 1: Execution sequence (web protection profile)
Scan/action |
Involves |
|
|
|
|
Trojans |
HTTP body |
|
|
|
|
Bad Robot |
User-Agent: |
|
|
|
|
Parameter Validation |
• |
Host: |
|
• URL in the HTTP header |
|
|
• Name, data type, and length of <input> tags except |
|
|
|
<input type="hidden"> |
|
|
|
Cross Site Scripting, SQL |
• |
Cookie: |
Injection, Generic Attacks |
• Parameters in the URL in the HTTP header, or in the |
|
|
||
(attack signatures) |
|
HTTP body (depending on the HTTP method) for |
|
|
<input> tags except <input type="hidden"> |
|
• XML content in the HTTP body (if Enable XML Protocol |
|
|
|
Detection is enabled) |
|
|
|
Hidden Fields Protection |
• |
Host: |
|
• URL in the HTTP header |
|
|
• Name, data type, and length of |
|
|
|
<input type="hidden"> |
|
|
|
X-Forwarded-For |
X-Forwarded-For: in HTTP header |
|
|
|
|
URL Rewriting |
• |
Host: |
(rewriting & redirects) |
• |
Referer: |
|
• |
Location: |
|
• URL in HTTP header |
|
|
• |
HTTP body |
|
|
|
Auto-learning |
Any of the other features included by the auto-learning |
|
|
profile |
|
|
|
|
Data Analytics |
• Source IP address of the client |
|
|
• URL in the HTTP header |
|
|
• Results from other scans |
|
|
|
|
Client Certificate Forwarding |
Client’s personal certificate, if any, supplied during the |
|
|
SSL/TLS handshake |
|
|
|
|
Reply from server to client |
|
|
|
|
|
Information Disclosure |
Server-identifying custom HTTP headers such as |
|
|
Server: and X-Powered-By: |
|
|
|
|
Credit Card Detection |
Credit card number in the body, and, if configured, Credit |
|
|
Card Detection Threshold |
|
|
|
|
File Uncompress |
Content-Encoding: |
|
|
|
|
Fortinet |
26 |
FortiWeb 5.0 Patch 6 Administration Guide |

Table 1: Execution sequence (web protection profile)
Scan/action |
Involves |
|
|
|
|
URL Rewriting |
• |
Host: |
(rewriting) |
• |
Referer: |
|
• |
Location: |
|
• URL in HTTP header |
|
|
• |
HTTP body |
|
|
|
File Compress |
Accept-Encoding: |
|
|
|
|
* If a source IP is white listed, subsequent checks will be skipped.
Solutions for specific web attacks
The types of attacks that web servers are vulnerable to are varied, and evolve as attackers try new strategies.
FortiWeb appliances offer numerous configurable features for preventing web-related attacks, including denial-of-service (DoS) assaults, brute-force logins, data theft, and more.
Early in your deployment of FortiWeb, configure and run web vulnerability scans to detect the most common attack vulnerabilities. You can use this to discover attacks that you may be vulnerable to. For more information, see “Vulnerability scans” on page 505.
HTTP/HTTPS threats
Servers are increasingly being targeted by exploits at the application layer or higher. These attacks use HTTP/HTTPS and aim to compromise the target web server, either to steal information, deface it, or to post malicious files on a trusted site to further exploit visitors to the site, using the web server to create botnets.
Among its many threat management features, FortiWeb’s fends off attacks that use cross-site scripting, state-based, and various injection attacks. This helps you comply with protection standards for:
•credit-card data, such as PCI DSS 6.6
•personally identifiable information, such as HIPAA
Table 2 lists several HTTP-related threats and describes how FortiWeb appliances protect servers from them. FortiWeb can also protect against threats at higher layers (HTML, Flash or XML applications).
Fortinet |
27 |
FortiWeb 5.0 Patch 6 Administration Guide |
Table 2: Web-related threats
Attack |
Description |
Protection |
FortiWeb Solution |
|
Technique |
|
|
|
|
|
|
|
|
|
Adobe Flash |
Attackers attempt XSS, SQL |
Decode and scan Flash |
Enable AMF3 |
|
binary |
injection or other common |
action message format |
Protocol Detection |
|
(AMF) |
exploits through an Adobe Flash |
(AMF) binary data for |
|
|
protocol |
client. |
matches with attack |
|
|
attacks |
|
signatures. |
|
|
|
|
|
|
|
Botnet |
Utilizes zombies previously |
Decode and scan Flash |
IP Reputation |
|
|
exploited or infected (or willingly |
action message format |
|
|
|
participating), distributed usually |
(AMF) binary data for |
|
|
|
globally, to simultaneously |
matches with attack |
|
|
|
overwhelm the target when |
signatures. |
|
|
|
directed by the command and |
|
|
|
|
control server(s). |
|
|
|
|
|
|
|
|
Browser |
A man-in-the-middle attack |
• Use TLS 1.1 or |
Prioritize RC4 |
|
Exploit |
where an eavesdropper exploits |
greater, or |
Cipher Suite |
|
Against |
reused initialization vectors in |
• Use ciphers that do |
|
|
SSL/TLS |
older TLS 1.0 implementations of |
|
|
|
not involve CBC, |
|
|
||
(BEAST) |
CBC-based encryption ciphers |
|
|
|
such as stream |
|
|
||
|
such as AES and 3DES. |
|
|
|
|
ciphers, or |
|
|
|
|
|
|
|
|
|
|
• Use CBC only with |
|
|
|
|
correct initialization |
|
|
|
|
vector (IV) |
|
|
|
|
implementations |
|
|
|
|
|
|
|
Brute force |
An attacker attempts to gain |
Require strong |
Brute Force Login |
|
login attack |
authorization by repeatedly trying |
passwords for users, |
|
|
|
ID and password combinations |
and throttle login |
|
|
|
until one works. |
attempts. |
|
|
|
|
|
|
|
Clickjacking |
Code such as <IFRAME> HTML |
Scan for illegal inputs to |
• |
Signatures |
|
tags superimposes buttons or |
prevent the initial |
• |
Parameter |
|
other DOM/inputs of the |
injection, then apply |
||
|
|
Validation |
||
|
attacker’s choice over a normal |
rewrites to scrub any |
|
|
|
• |
Hidden Fields |
||
|
form, causing the victim to |
web pages that have |
||
|
|
Protection |
||
|
unwittingly provide data such as |
already been affected. |
|
|
|
|
|
||
|
bank or login credentials to the |
|
• |
URL Rewriting |
|
attacker’s server instead of the |
|
|
|
|
legitimate web server when the |
|
|
|
|
victim clicks to submit the form. |
|
|
|
|
|
|
|
|
Cookie |
Attackers alter cookies originally |
Validate cookies |
Cookie Poisoning |
|
tampering |
established by the server to inject |
returned by the client to |
Detection |
|
|
overflows, shell code, and other |
ensure that they have |
|
|
|
attacks, or to commit identity |
not been altered from |
|
|
|
fraud, hijacking the HTTP |
the previous response |
|
|
|
sessions of other clients. |
from the web server for |
|
|
|
|
that HTTP session. |
|
|
|
|
|
|
|
Fortinet |
28 |
FortiWeb 5.0 Patch 6 Administration Guide |
Table 2: Web-related threats
Attack |
Description |
Protection |
FortiWeb Solution |
Technique |
|
|
|
|
|
|
|
Credit card |
Attackers read users’ credit card |
Detect and sanitize |
Credit Card |
theft |
information in replies from a web |
credit card data leaks. |
Detection |
|
server. |
Helps you comply with |
|
|
|
|
|
|
|
credit card protection |
|
|
|
standards, such as PCI |
|
|
|
DSS 6.6. |
|
|
|
|
|
Cross-site |
A script causes a browser to |
Enforce web application |
Page Access |
request |
access a web site on which the |
business logic to prevent |
|
forgery |
browser has already been |
access to URLs from the |
|
(CSRF) |
authenticated, giving a third party |
same IP but different |
|
|
access to a user’s session on that |
client. |
|
|
site. Classic examples include |
|
|
|
hijacking other peoples’ sessions |
|
|
|
at coffee shops or Internet cafés. |
|
|
|
|
|
|
Cross-site |
Attackers cause a browser to |
Content filtering, cookie |
Cross Site |
scripting |
execute a client-side script, |
security, disable |
Scripting |
(XSS) |
allowing them to bypass security. |
client-side scripts. |
|
|
|
|
|
Denial of |
An attacker uses one or more |
Watch for a multitude of |
DoS Protection |
service |
techniques to flood a host with |
TCP and HTTP requests |
|
(DoS) |
HTTP requests, TCP |
arriving in a short time |
|
|
connections, and/or TCP SYN |
frame, especially from a |
|
|
signals. These use up available |
single source, and close |
|
|
sockets and consume resources |
suspicious connections. |
|
|
on the server, and can lead to a |
Detect increased SYN |
|
|
temporary but complete loss of |
signals, close half-open |
|
|
service for legitimate users. |
connections before |
|
|
|
resources are |
|
|
|
exhausted. |
|
|
|
|
|
HTTP |
Attackers use specially crafted |
Limit the length of HTTP |
HTTP Protocol |
header |
HTTP/HTTPS requests to target |
protocol header fields, |
Constraints |
overflow |
web server vulnerabilities (such |
bodies, and parameters. |
|
|
as a buffer overflow) to execute |
|
|
|
malicious code, escalating to |
|
|
|
administrator privileges. |
|
|
|
|
|
|
Fortinet |
29 |
FortiWeb 5.0 Patch 6 Administration Guide |
Table 2: Web-related threats
Attack |
Description |
Protection |
FortiWeb Solution |
Technique |
|
|
|
|
|
|
|
Local file |
LFI is a type of injection attack. |
Block directory traversal |
Generic Attacks |
inclusion |
However, unlike SQL injection |
commands. |
|
(LFI) |
attacks, a database is not always |
|
|
|
involved. In an LFI, a client |
|
|
|
includes directory traversal |
|
|
|
commands (such as ../../for |
|
|
|
web servers on Linux, Apple Mac |
|
|
|
OS X, or Unix distributions) when |
|
|
|
submitting input. This causes |
|
|
|
vulnerable web servers to use |
|
|
|
one of the computer’s own files |
|
|
|
(or a file previously installed via |
|
|
|
another attack mechanism) to |
|
|
|
either execute it or be included in |
|
|
|
its own web pages. |
|
|
|
This could be used for many |
|
|
|
purposes, including direct |
|
|
|
attacks of other servers, |
|
|
|
installation of malware, and data |
|
|
|
theft of /etc/passwd, display of |
|
|
|
database query caches, creation |
|
|
|
of administrator accounts, and |
|
|
|
use of any other files on the |
|
|
|
server’s file system. |
|
|
|
Many platforms have been |
|
|
|
vulnerable to these types of |
|
|
|
attacks, including Microsoft .NET |
|
|
|
and Joomla. |
|
|
|
|
|
|
Malicious |
Misbehaving web crawlers ignore |
Ban bad robots by |
Real Browser |
robots |
the robots.txt file, and |
source IP or |
Enforcement |
|
consume server resources and |
User-Agent: field, as |
Exception |
|
bandwidth on a site. |
well as rate limiting |
|
|
|
clients that fail a test that |
|
|
|
detects web browsers |
|
|
|
|
|
Fortinet |
30 |
FortiWeb 5.0 Patch 6 Administration Guide |
 Loading...
Loading...