
D-Link DFL-200
TM
Network Security Firewall
Manual
Building Networks for People
(10/28/2004)

Contents
Introduction ........................................................................................6
Features and Benefits........................................................................... 6
Introduction to Firewalls........................................................................ 6
Introduction to Local Area Networking .................................................. 7
LEDs ..................................................................................................... 8
Physical Connections............................................................................ 8
Package Contents................................................................................. 9
System Requirements........................................................................... 9
Managing D-Link DFL-200 ...............................................................10
Resetting the DFL-200................................................................................10
Administration Settings...................................................................11
Administrative Access..........................................................................11
Add ping access to an interface..................................................................12
Add Admin access to an interface...............................................................12
Add Read-only access to an interface........................................................13
Enable SNMP access to an interface.........................................................13
System ..............................................................................................14
Interfaces ............................................................................................ 14
Change IP of the LAN or DMZ interface.....................................................14
WAN Interface Settings – Using Static IP...................................................15
WAN Interface Settings – Using DHCP......................................................15
WAN Interface Settings – Using PPPoE.....................................................16
WAN Interface Settings – Using PPTP.......................................................17
WAN Interface Settings – Using BigPond...................................................18
MTU Configuration......................................................................................18
Routing................................................................................................ 19
Add a new Static Route...............................................................................20
Remove a Static Route...............................................................................20
Logging ............................................................................................... 21
Enable Logging...........................................................................................22
Enable Audit Logging..................................................................................22
Enable E-mail alerting for IDS/IDP events..................................................22
Time .................................................................................................... 23
Changing time zone....................................................................................24
Using NTP to sync time...............................................................................24
Setting time and date manually...................................................................24
2

Firewall..............................................................................................25
Policy................................................................................................... 25
Policy modes...............................................................................................25
Action Types................................................................................................25
Source and Destination Filter......................................................................25
Service Filter...............................................................................................26
Schedule.....................................................................................................26
Intrusion Detection / Prevention..................................................................26
Add a new policy.........................................................................................28
Change order of policy................................................................................29
Delete policy................................................................................................29
Configure Intrusion Detection .....................................................................29
Configure Intrusion Prevention...................................................................30
Port mapping / Virtual Servers............................................................ 31
Add a new mapping....................................................................................31
Delete mapping...........................................................................................32
Administrative user.............................................................................. 33
Change Administrative User Password.......................................................33
Users................................................................................................... 34
The DFL-200 RADIUS Support...................................................................34
Enable User Authentication via HTTP / HTTPS..........................................35
Enable RADIUS Support.............................................................................35
Add User.....................................................................................................36
Change User Password..............................................................................36
Delete User.................................................................................................37
Schedules ........................................................................................... 38
Add new recurring schedule.......................................................................38
Add new one-time schedule........................................................................39
Services .............................................................................................. 40
Adding TCP, UDP or TCP/UDP Service......................................................40
Adding IP Protocol......................................................................................41
Grouping Services ......................................................................................41
Protocol-independent settings....................................................................42
VPN..................................................................................................... 43
IPSec VPN between two networks .............................................................44
Creating a LAN-to-LAN VPN Tunnel...........................................................44
IPSec VPN between client and an internal network...................................45
Creating a Roaming Users Tunnel..............................................................45
VPN – Advanced Settings................................................................... 46
Limit MTU....................................................................................................46
IKE Mode ....................................................................................................46
IKE DH Group.............................................................................................46
PFS – Perfect Forward Secrecy .................................................................46
NA T Traversal .............................................................................................46
Keepalives...................................................................................................46
Proposal Lists..............................................................................................47

IKE Proposal List.........................................................................................47
IPSec Proposal List.....................................................................................47
Certificates.......................................................................................... 48
Trusting Certificates....................................................................................48
Local identities ............................................................................................48
Certificates of remote peers........................................................................48
Certificate Authorities..................................................................................49
Identities......................................................................................................49
Content Filtering.................................................................................. 50
Edit the URL Global Whitelist......................................................................50
Edit the URL Global Blacklist......................................................................51
Active content handling...............................................................................52
Servers..............................................................................................53
DHCP Server Settings......................................................................... 53
Enable DHCP Server..................................................................................54
Enable DHCP Relay....................................................................................54
Disable DHCP Server/Relayer....................................................................54
DNS Relayer Settings......................................................................... 55
Enable DNS Relayer...................................................................................55
Disable DNS Relayer..................................................................................56
Tools..................................................................................................57
Ping..................................................................................................... 57
Ping Example..............................................................................................57
Dynamic DNS...................................................................................... 58
Add Dynamic DNS Settings........................................................................58
Backup................................................................................................ 59
Exporting the DFL-200’s Configuration.......................................................59
Restoring the DFL-200’s Configuration.......................................................59
Restart/Reset...................................................................................... 60
Restoring system settings to factory defaults.............................................60
Upgrade .............................................................................................. 62
Upgrade Firmware......................................................................................62
Upgrade IDS Signature-database...............................................................62
Status ................................................................................................63
System................................................................................................ 63
Interfaces ............................................................................................ 64
VPN..................................................................................................... 65
Connections........................................................................................ 66
DHCP Server ...................................................................................... 67
How to read the logs........................................................................68
4

USAGE events.................................................................................... 68
DROP events...................................................................................... 68
CONN events...................................................................................... 68
Appendixes.......................................................................................70
Appendix A: ICMP Types and Codes..................................................70
Appendix B: Common IP Protocol Numbers....................................... 72
Appendix C: Multiple Public IP addresses........................................... 73
Appendix D: HTTP Content Filtering................................................... 81
Warranty............................................................................................87

Introduction
The DFL-200 provides six 10/100Mbps Auto MDI/MDIX Ethernet network interface ports,
which are (4) Internal/LAN, (1) External/WAN, and (1) DMZ port. In addition the DFL-200 also
provides a user-friendly Web UI that allows users to set system parameters or monitor
network activities using a Web browser supporting Java.
Features and Benefits
Firewall Security
VPN Server/Client Supported
Supports IPSec LAN-to-LAN or Roaming user tunnels with AES
encryption
Content Filtering
Strip ActiveX objects, Java Applets, JavaScript, and VBScript from
HTTP traffic
Web Management
Configurable through any networked computer’s Web browser using
Netscape or Internet Explorer.
Access Control supported
Allows assignment of different access rights for different users, such
as Admin or Read-Only User.
Introduction to Firewalls
A firewall is a device that sits between your computer and the Internet that prevents
unauthorized access to or from your network. A firewall can be a computer using firewall
software or a special piece of hardware built specifically to act as a firewall. In most
circumstances, a firewall is used to prevent unauthorized Internet users from accessing
private networks or corporate LAN’s and Intranets. Firewalls are also deployed to prevent
sensitive information about your network from leaking out of your network.
A firewall monitors all of the information moving to and from your network and analyzes each
piece of data. Each piece of data is then checked against a set of criter ia configured by the
administrator. If any data does not meet the criteria, that data is blocked and discarded. If the
data meets the criteria, the data is passed through. This method is called packet filtering.
A firewall can also run specific security functions based on the type of application or type of
port that is being used. For example, a firewall can be configured to work with an FTP or
Telnet server. Or a firewall can be configured to work with specific UDP or TCP ports to allow
certain applications or games to work properly over the Internet.
6

Introduction to Local Area Networking
Local Area Networking (LAN) is the term used when connecting several computers together
over a small area such as a building or group of buildings. LANs can be connected over large
areas. A collection of LANs connected over a large area is called a Wide Area Network
(WAN).
A LAN consists of multiple computers connected to each other. There are many types of
media that can connect computers together. The most common media is CAT5 cable (UTP or
STP twisted pair wire.) On the other hand, wireless networks do not use wires; instead they
communicate over radio waves. Each computer must have a Network Interface Card (NIC),
which communicates the data between computers. A NIC is usually a 10Mbps network card,
or 10/100Mbps network card, or a wireless network card.
Most networks use hardware devices such as hubs or switches that each cable can be
connected to in order to continue the connection between computers. A h ub simply takes any
data arriving through each port and forwards the data to all other ports. A switch is more
sophisticated, in that a switch can determine the destination port for a specific piece of data.
A switch minimizes network traffic overhead and speeds up the communication over a
network.
Networks take some time in order to plan and implement correctly. There are many ways to
configure your network. You may want to take some time to determine the best network setup for your needs.

LEDs
Power: A solid light indicates a proper connection to the power supply.
Status: A System status indicator that flashes occasionally to indicate a functional, active
system. Solid illumination of the Status LED indicates a hardware/software critical failure.
WAN, 4 x LAN, & DMZ: Bright Green illumination indicates a valid Eth ernet Link on that
respective port. Each LED will flicker when that respective port is sending or receiving
data.
Physical Connections
-
COM Port: Serial Read-Only access to the firewall software from a PC equipped with a
Serial COM port (9600 baud, 8 data bits, No Parity, 1Stop bit, No Flow Control).
4 x LAN Port: Use these ports to connect PC’s directly or to connect to Fast Ethernet
Switches to service more than 4 client PCs on the internal office network.
DMZ Port: Use this port to service an additional physically segmented Private or
Transparent Network to be occupied by WAN accessible servers (FTP, HTTP, DNS).
WAN Port: Use this port to connect to an external network, such as a WAN or a modem
provided by an ISP.
Reset: Use this switch to reset the DFL-200 to factory default settings. Refer to page 63
for further instructions.
DC Power: Use the included 5VDC 3A switching power supply to connect to an
110/120VAC electrical receptacle. Do not use less than 5VDC 3A t o power the device,
doing so will damage the unit.
8

Package Contents
Contents of Package:
• D-Link DFL-200 Firewall
• Manual and CD
• Quick Installation Guide
• 5V/3A AC Power adapter
• Straight-through CAT-5 cable
Note: Using a power supply with a different voltage rating than the one included
with the DFL-200 will cause irreparable electrical damage and void the warranty
for this product.
If any of the above items are missing, please contact your reseller.
System Requirements
• Computer running Microsoft Windows, Macintosh OS, or a UNIX based operating
system with an installed Ethernet adapter configured to communicate using TCP/IP.
• Internet Explorer or Netscape Navigator, version 6.0 or above, with JavaScript
enabled.
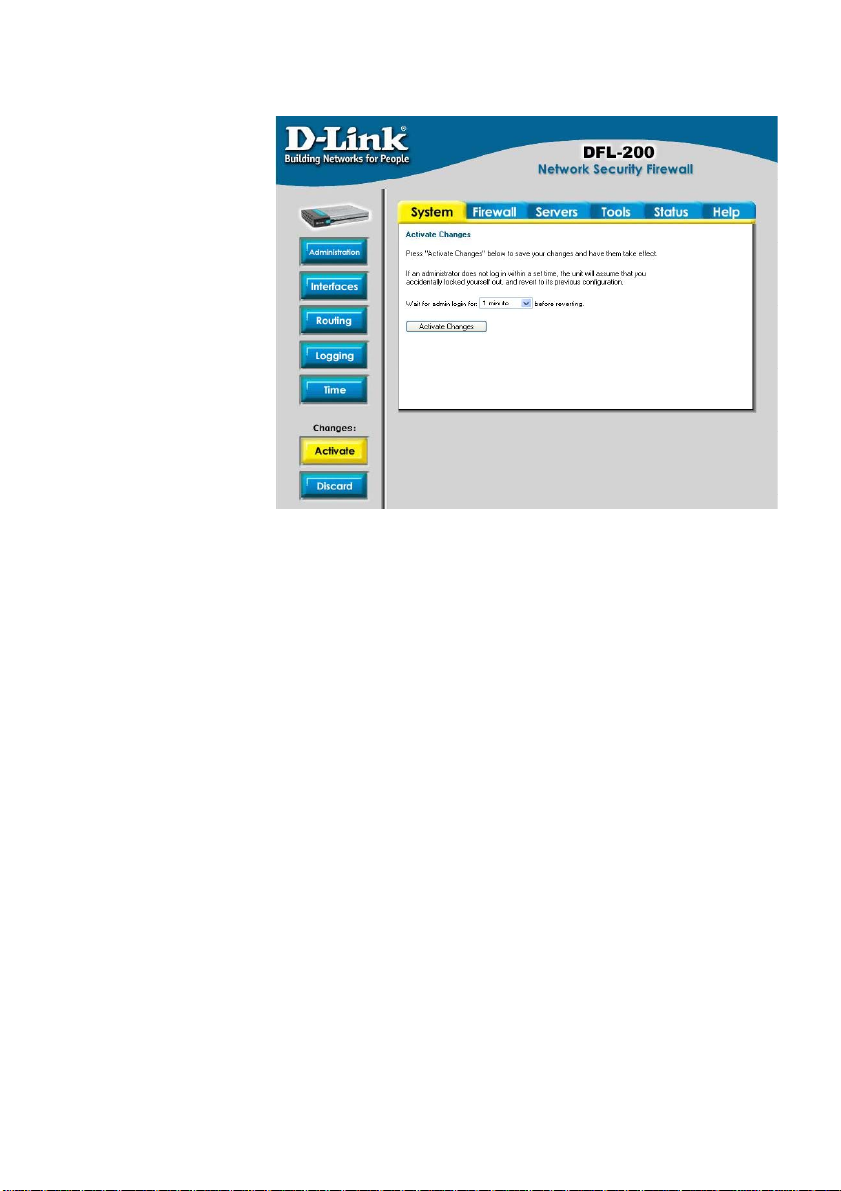
Managing D-Link DFL-200
When a change is made
to the configuration, a new
icon named Activate
Changes will appear.
When all changes made
by the administrator are
complete, those changes
need to be saved and
activated to take effect by
clicking on the Activate
Changes button on the
Activate Configuration
Changes page. The
firewall will save the
configuration and reload it,
making the new changes
take effect. In order to
make the changes
permanent, the
administrator must login
again. This has to be done before a configurable timeout has be en reached, otherwise the
DFL-200 will revert to the previous configuration. The timeout can be set on the Activate
Configuration Changes page, by choosing the time from the dropdown menu.
Resetting the DFL-200
To reset the DFL-200 to factory default settings you must power down the firewall. Press and
hold the reset button down while powering up the DFL-200. Continue to hold for at least 15
seconds after powering on the unit. You will first hear one beep, which will indicate that the
firmware is being restored. Keep the button pressed in until you hear two short consec utive
beeps. After this you can release the reset button and the DFL-200 will continue to load and
startup in default mode, i.e. with 192.168.1.1 on the LAN interface.
For more information on the reset procedure, refer to page 60.
10
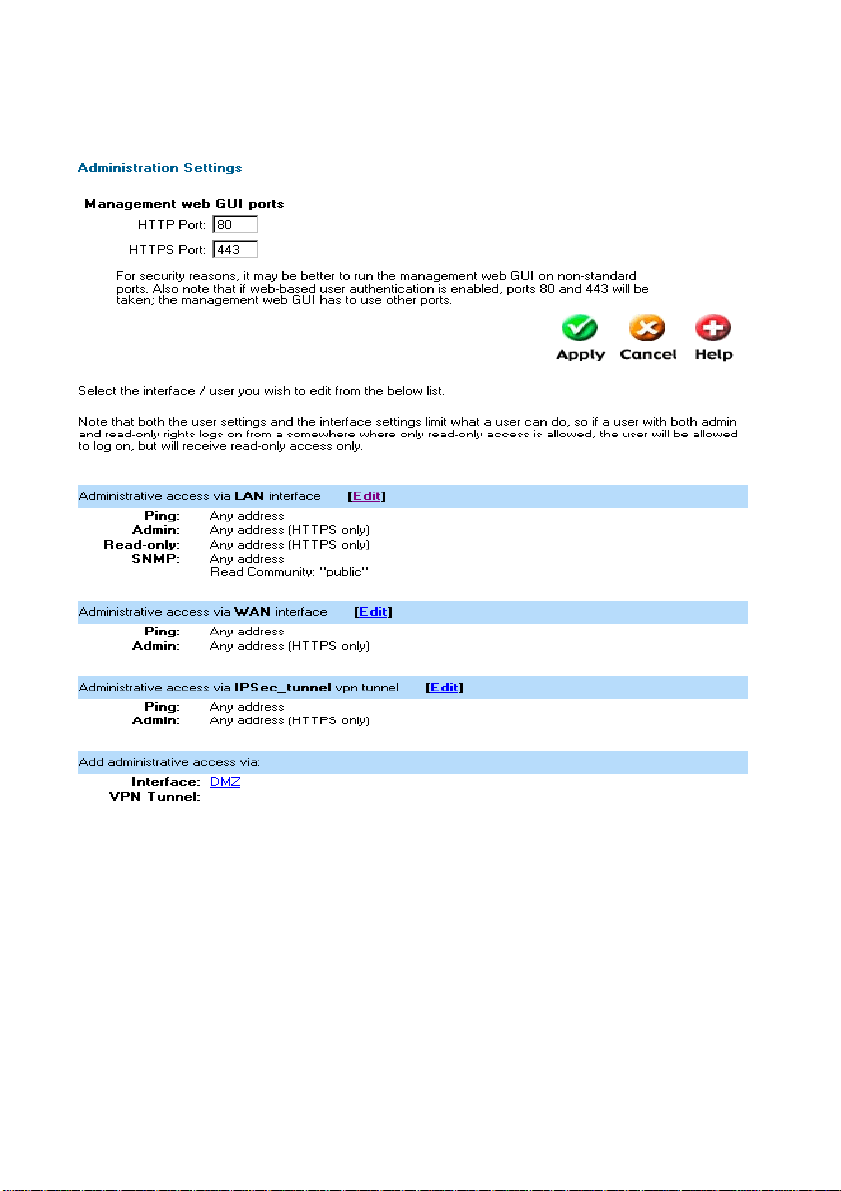
Administration Settings
Administrative Access
Management UI Ports – The ports for the DFL-200’s Web Server Management UI (HTTP
and HTTPS) can be customized if so desired. These values must change if User
Authentication is enabled (User Authentication uses 80 and 443 to accomplish user login).
Ping – If enabled, it specifies who can ping the IP interface of the DFL-200. Enabling
Default allows anyone to ping the interface IP.
Admin – If enable d, it allows all users with admin access to connect to the DFL-200 and
change configuration; this can be HTTPS or HTTP and HTTPS.
Read-Only – If enabled, it allows all users with read-only access to connect to the DFL200 and look at the configuration; this can be HTTPS or HTTP and HTTPS. In the case
where Read-Only access is the only type allowed on a specific interface, all users that log
in to that interface will be in Read-Only mode.
SNMP – Specifies if SNMP should or should not be allowed on the interface. The DFL-200
only supports read-only access.

Add ping access to an interface
To add ping access click on the interface you would like to add it to.
Follow these steps to add ping access to an interface.
Step 1. Click on the interface you would like to add it to.
Step 2. Enable the Ping checkbox.
Step 3. Specify which network addresses should be allowed to ping the interface, for
example 192.168.1.0/24 for a whole class C network or 172.16.0.1 – 172.16.0.10 for a
range of IP addresses.
Click the Apply button below to apply the settings or click Cancel to discard changes.
Example:
Add Admin access to an interface
To add admin access, click on the interface you would like to add it to. Only users with
administrative rights can login on interfaces where there is only admin access enabled.
Follow these steps to add admin access to an interface.
Step 1. Click on the interface you would like to add it to.
Step 2. Enable the Admin checkbox.
Step 3. Specify which network addresses shoul d be allowed to access the administrative
interface, for example 192.168.1.0/24 for a whole class C network or 172.16.0.1 –
172.16.0.10 for a range of IP addresses.
Step 4. Specify protocol to be used to access the DFL-200 via the dropdown menu.
Select HTTP and HTTPS (Secure HTTP) or HTTPS only.
Click the Apply button below to apply the settings or click Cancel to discard changes.
Example:
12

Add Read-only access to an interface
To add read-only access, click on the interface you would like to add it to. Note that if you only
have read-only access enabled on an interface, all users will only have read-only access,
even if they are administrators.
Follow these steps to add read-only access to an interface.
Step 1. Click on the interface you would like to add it to.
Step 2. Enable the Read-only checkbox.
Step 3. Specify which network addresses should be allowed read-only access to the
interface, for example 192.168.1.0/24 for a whole class C network or 172.16.0.1 –
172.16.0.10 for a range of IP addresses.
Step 4. Specify protocol to be used to access the DFL-200 via the dropdown menu.
Select HTTP and HTTPS (Secure HTTP) or HTTPS only.
Click the Apply button below to apply the settings or click Cancel to discard changes.
Example:
Enable SNMP access to an interface
Follow these steps to add read-only SNMP access to an interface.
Step 1. Click on the interface you would like to add it to.
Step 2. Enable the Read-only checkbox.
Step 3. Specify which network addresses should be allowed to receive SNMP traps, for
example 192.168.1.0/24 for a whole class C network or 172.16.0.1 – 172.16.0.1 0 for a
range of IP addresses.
Step 4. Specify the community string used to authenticate the DFL-200.
Click the Apply button below to apply the settings or click Cancel to discard changes.
Example:

System
Interfaces
Click on System in the menu bar, and then click interfaces below it.
Change IP of the LAN or DMZ interface
Follow these steps to change the IP of the LAN or DMZ interface.
Step 1. Choose which interface to view or change under the Available interfaces list.
Step 2. Fill in the IP address of the LAN or DMZ interface. These are the addresses that
will be used to ping the firewall, remotely control it, and used as the gateway for the
internal hosts or DMZ hosts.
Step 3. Choose the correct Subnet mask of this interface from the drop down menu. This
configuration will determine the IP addresses that can communicate with this interface.
Click the Apply button below to apply the settings or click Cancel to discard changes.
14

WAN Interface Settings – Using Static IP
If you are using Static IP, you have to fill
in the IP address information provided to
you by your ISP. All fields are required
except the Secondary DNS Server. Note:
Do not use the numbers displayed in
these fields, they are only used as an
example.
• IP Address – The IP
address of the WAN
interface. This is the
address that may be used
to ping the firewall, remotely control it, and be used as the source address for
dynamically translated connections.
• Subnet Mask – Size of the external network.
• Gateway IP – Specifies the IP address of the default gateway used to access the
Internet.
• Primary and Secondary DNS Server – The IP addresses of your DNS servers;
only the Primary DNS is required.
WAN Interface Settings – Using DHCP
If you are using DHCP, there is no
need to complete any fields.

WAN Interface Settings – Using PPPoE
Use the following procedure to
configure the DFL-200 external
interface to use PPPoE (Point-to-Point
Protocol over Ethernet). This
configuration is required if your ISP
uses PPPoE to assign the IP address
of the external interface. You will have
to fill in the username and password
provided to you by your ISP.
• Username – The login or
username supplied to you
by your ISP.
• Password – The
password supplied to you by your ISP.
• Service Name – When using PPPoE some ISPs require you to fill in a Service
Name.
• Primary and Secondary DNS Server – The IP addresses of your DNS servers;
these are optional and are often provided by the PPPoE service.
16
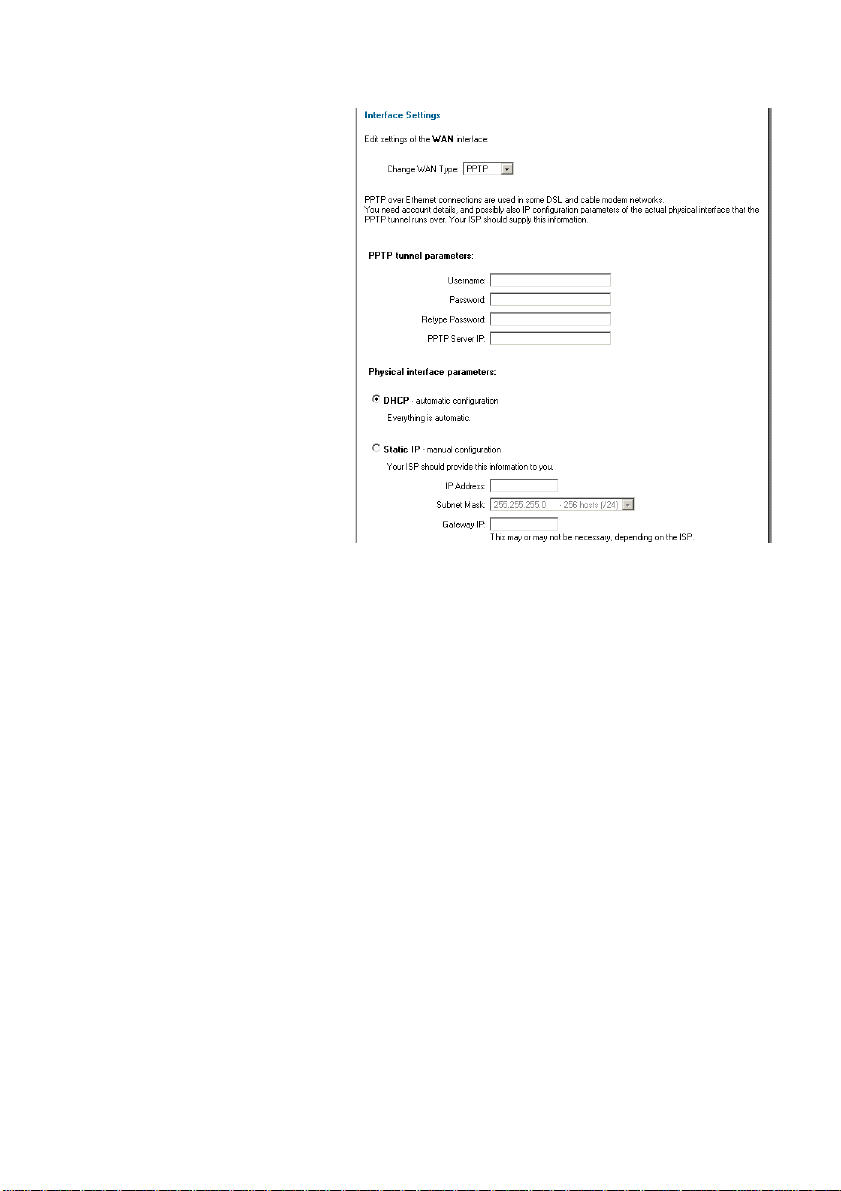
WAN Interface Settings – Using PPTP
PPTP over Ethernet connections are
used in some DSL and cable
modem networks.
You need to enter your account
details, and possibly also IP
configuration parameters of the
actual physical interface that the
PPTP tunnel runs over. Your ISP
should supply this information.
Username – The login
•
or username supplied
to you by your ISP.
• Password – The
password supplied to
you by your ISP.
• PPTP Server IP – The
IP of the PPTP server
that the DFL-200 will
connect to.
Before PPTP can be used to connect to your ISP, the physical (WAN) interface parameters
must be input. You can use either DHCP or Static IP, depending on the type of ISP used.
Your ISP should supply this information.
If using static IP, this information needs to be filled in.
• IP Address – The IP address of the WAN interface. This IP is used to connect to
the PPTP server.
• Subnet Mask – Size of the external network.
• Gateway IP – Specifies the IP address of the default gateway used to access the
Internet.

WAN Interface Settings – Using BigPond
The ISP Telstra BigPond uses
BigPond for authentication; the IP is
assigned with DHCP.
• Username – The login
or username supplied to
you by your ISP.
• Password – The
password supplied to
you by your ISP.
MTU Configuration
To improve the performance of your Internet connection, you can adjust the maximum
transmission unit (MTU) of the packets that the DFL-200 transmits from its external interface.
Ideally, you want this MTU to be the same as the smallest MTU of all the networks between
the DFL-200 and the Internet. If the packets the DFL-200 sends are larger, they get broken up
or fragmented, which could slow down transmission speeds.
Trial and error is the only sure way of finding the optimal MTU, but there are some guid elines
that can help. For example, the MTU of many PPP connections is 576, so if you connect to
the Internet via PPPoE, you may want to set the MTU size to this value. DSL modems may
also have small MTU sizes. Most Ethernet networks have an MTU of 1500.
Note: If you connect to your ISP using DHCP to obtain an IP address for the external
interface, you cannot set the MTU below 576 bytes due to DHCP communication
standards.
Click the Apply button below to apply the settings or click Cancel to discard changes.
18
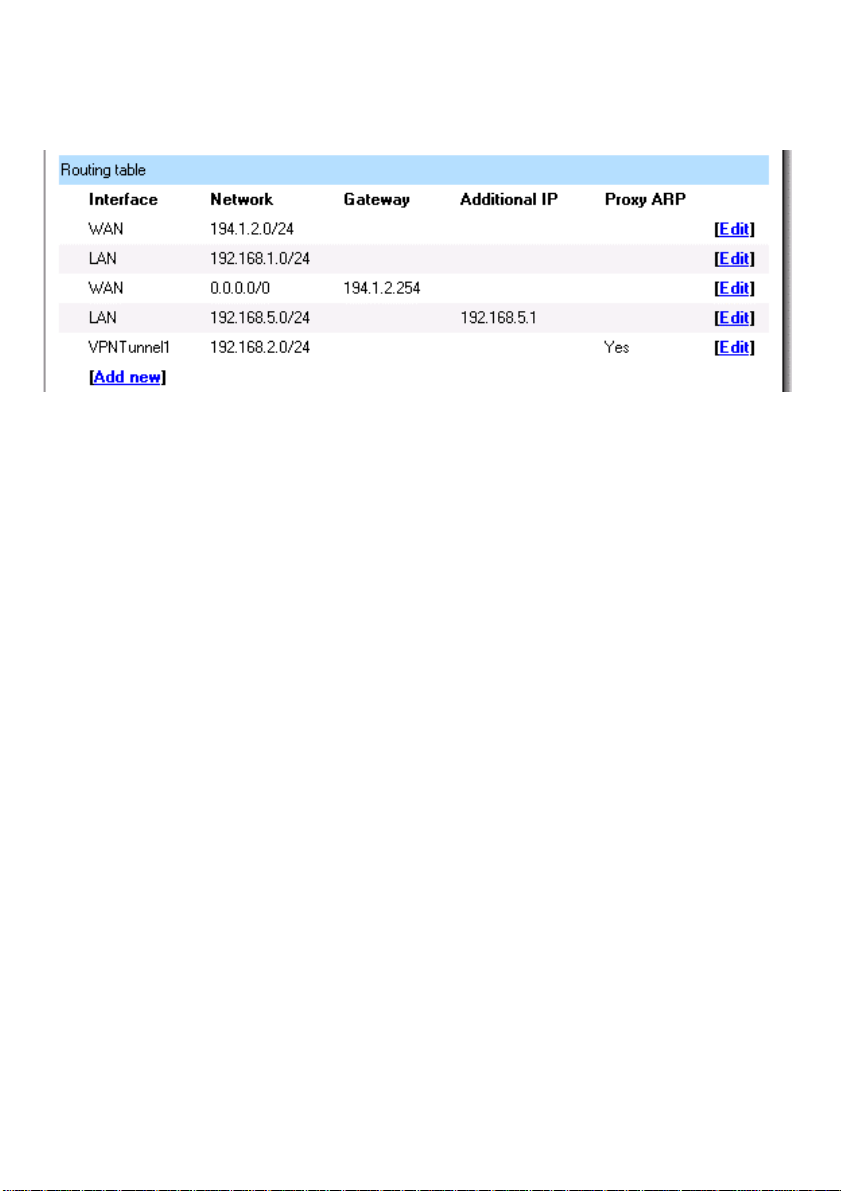
Routing
Click on System in the menu bar, and then click Routing below it; this will provide a list of all
configured routes, and it will look something like this:
The Routes configuration section describes the firewall’s routing table. T he DFL-200 uses a
slightly different method of describing routes compared to most other systems. However, we
believe that this method of describing routes is easier to understand, making it less likely for
users to cause errors or breaches in security.
Interface – Specifies which interface packets destined for this route shall be sent through.
Network – Specifies the network address for this route.
Gateway – Specifies the IP address of the next router hop used to reach the destination
network. If the network is directly connected to the firewall interface, no gateway address is
specified.
Additional IP Address – The IP address specified here will be automatically published on the
corresponding interface. This address will also be used as the send er ad dr ess in ARP q u eries.
If no address is specified, the interface IP address of the firewall will be used.
Proxy ARP – Specifies that the firewall shall publish this route via Proxy ARP.
One advantage with this form of notation is that you can specify a gateway for a particular
route, without having a route that covers the gateway’s IP address or despite the fact that the
route that covers the gateway’s IP address is normally routed via another interface.
The major difference between this form of notation and the f orm most comm only used is there
is no need to specify the interface name in a separate column. Instead, you specify the IP
address of each interface as a gateway.
Note: Proxy ARP will publish the remote network on all int e rfaces (exce pt W AN) if ena bled on
the VPN tunnel.

Add a new Static Route
Follow these steps to add a new route.
Step 1. Go to System and Routing.
Step 2. Click on Add new in the bottom of the routing table.
Step 3. Choose the interface that the route should be sent trough from the dropdown
menu.
Step 4. Specify the Network and Subnet mask.
Step 5. If this network is behind a remote gateway, enable the checkbox Network is
behind remote gateway and specify the IP of that gateway.
Click the Apply button below to apply the settings or click Cancel to discard changes.
Remove a Static Route
Follow these steps to remove a route.
Step 1. Go to System and Routing.
Step 2. Click the Edit corresponding to the route you would like to remove.
Step 3. Check the checkbox named Delete this route.
Click the Apply button below to apply the settings or click Cancel to discard changes.
20
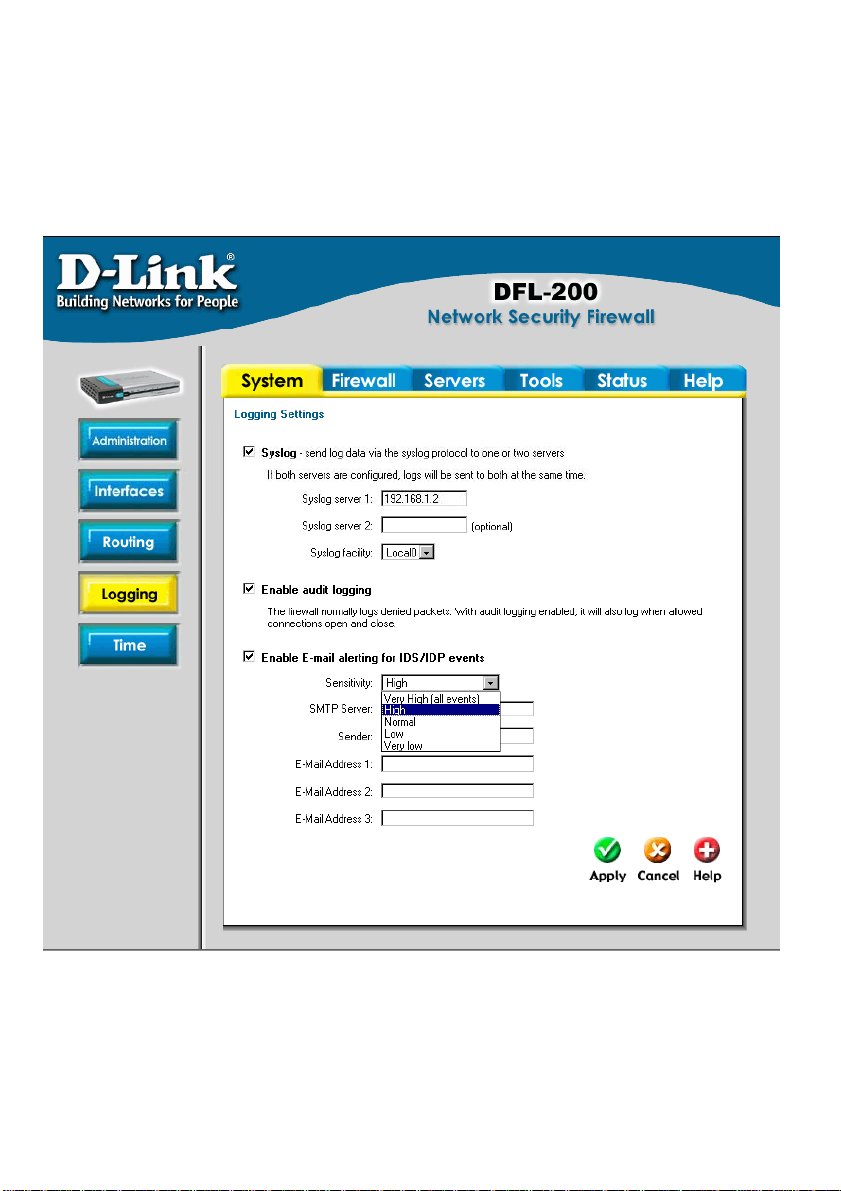
Logging
Click on System in the menu bar, and then click Logging below it.
Logging, the ability to audit decisions made by the firewall, is a vital part in all network security
products. The D-Link DFL-200 provides several options for logging activity. The D-Link DFL200 logs activity by sending the log data to one or two log receivers in the network.
All logging is done to SYSLog recipients. The log format used for SYSLog logging is suitable
for automated processing and searching.
The D-Link DFL-200 specifies a number of events that can be logged. Some of these events,
such as startup and shutdown, are mandatory and will always generate log entries. Other
events, for instance when allowed connections are opened and closed, are configurab le. It is
also possible to have E-mail alerting for IDS/IDP events to up to three email addresses.

Enable Logging
Follow these steps to enable logging.
Step 1. Enable SYSLog by checking the SYSLog box.
Step 2. Fill in your first SYSLog server as SYSLog server 1. If you have two SYSLog
servers, you have to fill in the second one as SYSLog server 2. You must fill in at least
one SYSLog server for logging to work.
Step 3. Specify what facility to use by selecting the appropriate SYSLog facility. Local0 is
the default facility.
Click the Apply button below to apply the settings or click Cancel to discard changes.
Enable Audit Logging
To start auditing all traffic through the firewall, follow the steps below. This is required when
running third party log analyzers on the l ogs or to see how much traffic specific connections
account for.
Follow these steps to enable auditing.
Step 1. Enable SYSLog by checking the Enable Audit Logging box.
Click the Apply button below to apply the settings or click Cancel to discard changes.
Enable E-mail alerting for IDS/IDP events
Follow these steps to enable E-mail alerting.
Step 1. Enable E-mail alerting by checking the Enable E-mail alerting for IDS/IDP
events checkbox.
Step 2. Choose the sensitivity level.
Step 3. In the SMTP Server field, fill in the SMTP server to which the DFL-200 will send
the e-mail alerts.
Step 4. Specify up to three valid email addresses to receive the e-mail alerts.
Click the Apply button below to apply the settings or click Cancel to discard changes.
22
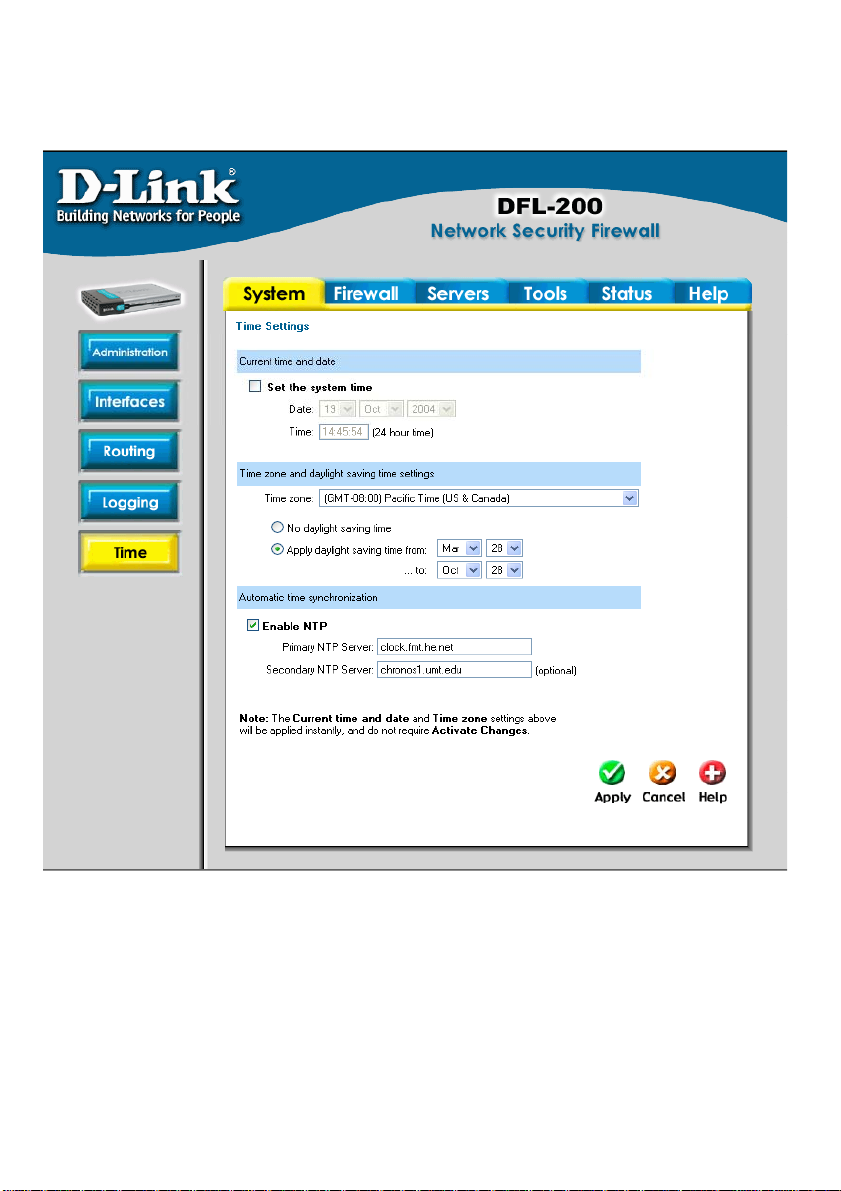
Time
Click on System in the menu bar, and then click Time below it. This will give you the option to
either set the system time by syncing to an Internet Network Time Server (NTP) or by entering
the system time manually.

Changing time zone
Follow these steps to change the time zone.
Step 1. Choose the correct time zone in the drop down menu.
Step 2. Specify the dates to begin and end daylight saving time or choose no daylight
saving time by checking the correct box.
Click the Apply button below to apply the settings or click Cancel to discard changes.
Using NTP to sync time
Follow these steps to sync to an Internet Time Server.
Step 1. Enable synchronization by checking the Enable NTP box.
Step 2. Enter the Server IP Address or Server name with which you want to synchronize.
Click the Apply button below to apply the settings or click Cancel to discard changes.
Setting time and date manually
Follow these steps to manually set the system time.
Step 1. Check the Set the system time box.
Step 2. Select the correct date.
Step 3. Set the correct time using the 24-hour format.
Click the Apply button below to apply the settings or click Cancel to discard changes.
24

Firewall
Policy
The Firewall Policy configuration section is the "heart" of the firewall. The policies are the
primary filter that is configured to allow or disallo w certain types of network traffic through the
firewall. The policies also regulate how bandwidth management, traffic shaping, is applied to
traffic flowing through the WAN interface of the firewall.
When a new connection is being established through the f irewall, the policies are evaluated,
top to bottom, until a policy that matches the new connection is found. The Action of the rule
is then carried out. If the action is Allow, the connection will be established and a state
representing the connection is added to the firewall's internal state table. If the action is Dr op,
the new connection will be refused. The section below will explain the meanings of the various
action types available.
Policy modes
The first step in configuring security policies is to configure the mode for the firewall. The
firewall can run in NAT or No NAT (Route) mode. Select NAT mode to use DFL-200 network
address translation to protect private networks from public networks. In NAT mode, you can
connect a private network to the internal interface, a DMZ network to the DMZ interface, and a
public network, such as the Internet, to the external interface. Then you c an create NAT mode
policies to accept or deny connections between these networks. NAT mode policies hide the
addresses of the internal and DMZ networks from users on the Internet. In No NAT (Route)
mode you can also create routed policies between interfaces. Route mode policies accept or
deny connections between networks without performing address translation. To use NAT
mode select Hide source addresses (many-to-one NAT) and to use No NAT (Route) mode
choose No NAT.
Action Types
Drop – Packets matching Drop rules will immediately be dropped. Such packets will be
logged if logging has been enabled in the Logging Settings page.
Reject – Reject works basically the same way as Drop. In addition to this, the firewall sends
an ICMP UNREACHABLE message back to the sender or, if the rejected packet was a TCP
packet, a TCP RST message. Such packets will be logged if logging has been enabled in the
Logging Settings page.
Allow – Packets matching Allow rules are passed to the stateful inspection engine, which will
remember that a connection has been opened. Therefore, rules for return traffic will not be
required as traffic belonging to open connections is automatically dealt with before it reaches
the policies. Logging is carried out if audit logging has been enabled in the Logging Settings
page.
Source and Destination Filter
Source Nets – Specifies the sender span of IP addresses to be compared to the received
packet. Leave this blank to match everything.

Source Users/Groups – Specifies if an authenticated username is needed for this policy to
match. Simply make a list of usernames separated by commas (,), specify an entire user
group, or write Any to indicat e all authenticated users to enable authe ntication on this policy.
If it is left blank there is no need for authentication for the policy.
Destination Nets – Specifies the span of IP addresses to be compared to the destination IP
of the received packet. Leave this blank to match everything.
Destination Users/Groups – Specifies if an authenticated username is needed for this policy
to match. Either make a list of usernames, separated by a comma (,) or write Any for any
authenticated user. If it is left blank there is no need for authentication for the policy.
Service Filter
Either choose a predefined service from the dropdown menu or make a custom service.
The following custom services exist:
All – Matches all protocols.
TCP+UDP+ICMP – This service matches all ports on either the TCP or the UDP protocol,
including ICMP.
Custom TCP – This service is based on the TCP protocol.
Custom UDP – This service is based on the UDP protocol.
Custom TCP+UDP – This service uses both the TCP and UDP protocols.
The following is used when making a custom service:
Custom source/destination ports – For many services, a single destination port is sufficient.
The source port used most often are all ports, 0-65535. The http service, for instance, uses
destination port 80. A port range can also be used, meaning that a range 137-139 covers
ports 137, 138, and 139. Multiple ranges or individ ual ports may also be entered, separated
by commas. For instance, a service can be defined as having source ports 1024-65535 and
destination ports 80-82, 90-92, and 95. In this case, a TCP or UDP packet with the destination
port being one of 80, 81, 82, 90, 91, 92 or 95, and the source port b eing in the range 102465535, will match this service.
Schedule
If a schedule should be used for the policy, choose one from the dropdo wn menu. These are
specified on the Schedules page. If the policy should always be active, choose Always from
the dropdown menu.
Intrusion Detection / Prevention
The DFL-200 Intrusion Detection/Prevention System (IDS/IDP) is a real-time intrusion
detection and prevention sensor that identifies and takes action against a wide variety of
suspicious network activity. The IDS uses intrusion signatures, stored in the attack database,
to identify the most common attacks. In response to an attack, the IDS will protect the
networks behind the DFL-200 by dropping the traffic. To notify responsible parties of the
malicious attack, the IDS will send e-mails to the system administrators if e-mail alerting is
26

enabled and configured. D-Link updates the attack database periodically. There are two
modes that can be configured, either Inspection Only or Prevention. Inspection Only will
only inspect the traffic, and if the DFL-200 detects anything it will log, e-mail an alert (if
configured), and pass on the traffic. If Prevention is used the traffic will be dropped and
logged and if configured, an e-mail alert will be sent.
 Loading...
Loading...