
D-Link DFL-1100
Network Security Firewall
Manual
October 7, 2004
Building Networks for People

Contents
Introduction....................................................................................6
Features and Benefits..........................................................................6
Introduction to Firewalls .......................................................................6
Introduction to Local Area Networking..................................................7
LEDs & Hardware Connections............................................................8
Package Contents................................................................................9
System Requirements..........................................................................9
Managing D-Link NETDEFEND DFL-1100......................................10
Administration Settings...............................................................11
Administrative Access........................................................................ 11
Add ping access to an interface..................................................................12
Add Admin access to an interface ..............................................................12
Add Read-only access to an interface........................................................13
Enable SNMP access to an interface.........................................................13
System..........................................................................................14
Interfaces...........................................................................................14
WAN Interface Settings – Using Static IP...................................................15
WAN Interface Settings – Using DHCP......................................................15
WAN Interface Settings – Using PPPoE.....................................................16
WAN Interface Settings – Using PPTP.......................................................17
WAN Interface Settings – Using BigPond...................................................18
Traffic Shaping............................................................................................18
MTU Configuration......................................................................................19
VLAN .................................................................................................20
Add a new VLAN.........................................................................................20
Remove a VLAN.........................................................................................20
Routing ..............................................................................................21
Add a new Static Route...............................................................................22
Remove a Static Route...............................................................................22
High Availability..................................................................................23
What High Availability will do for you ..........................................................23
What High Availability will NOT do for you..................................................23
IP Addresses explained ..............................................................................24
The shared IP address and the failover mechanism ..................................24
2

Cluster heartbeats.......................................................................................25
The synchronization interface.....................................................................25
Setting up a High Availability cluster...........................................................26
Interface Monitoring ....................................................................................27
Logging..............................................................................................28
Enable Logging...........................................................................................29
Enable Audit Logging..................................................................................29
Enable E-mail alerting for ISD/IDP events..................................................29
Time...................................................................................................30
Changing the time zone..............................................................................31
Using NTP to sync time ..............................................................................31
Setting time and date manually...................................................................31
Firewall..........................................................................................32
Policy.................................................................................................32
Policy modes...............................................................................................32
Action Types................................................................................................32
Source and Destination Filter......................................................................32
Service Filter...............................................................................................33
Schedule.....................................................................................................33
Intrusion Detection / Prevention..................................................................33
Traffic Shaping............................................................................................34
Policy Routing.............................................................................................34
Add a new policy.........................................................................................35
Change order of policy................................................................................36
Delete policy................................................................................................36
Configure Intrusion Detection .....................................................................36
Configure Intrusion Prevention ...................................................................37
Port mapping / Virtual Servers............................................................38
Add a new mapping....................................................................................38
Delete mapping...........................................................................................39
Administrative users...........................................................................40
Add Administrative User..............................................................................40
Change Administrative User Access level ..................................................41
Change Administrative User Password ......................................................41
Delete Administrative User..........................................................................42
Users .................................................................................................43
The DFL-1100 RADIUS Support.................................................................43
Enable User Authentication via HTTP / HTTPS..........................................44
Enable RADIUS Support.............................................................................44
Add User.....................................................................................................45
Change User Password..............................................................................45
Delete User.................................................................................................46
Schedules..........................................................................................47
Add new recurring schedule .......................................................................47
Add new one-time schedule........................................................................48

Services.............................................................................................49
Adding TCP, UDP or TCP/UDP Service......................................................49
Adding IP Protocol ......................................................................................50
Grouping Services ......................................................................................50
Protocol-independent settings ....................................................................51
VPN ...................................................................................................52
IPSec VPN between two networks.............................................................53
Creating a LAN-to-LAN VPN Tunnel...........................................................53
IPSec VPN between client and an internal network ...................................54
Creating a Roaming Users Tunnel..............................................................54
VPN – Advanced Settings..................................................................55
Limit MTU....................................................................................................55
IKE Mode ....................................................................................................55
IKE DH Group.............................................................................................55
PFS – Perfect Forward Secrecy.................................................................55
NAT Traversal .............................................................................................55
Keepalives...................................................................................................55
Proposal Lists..............................................................................................56
IKE Proposal List ........................................................................................56
IPSec Proposal List.....................................................................................56
Certificates.........................................................................................57
Trusting Certificates....................................................................................57
Local identities ............................................................................................57
Certificates of remote peers........................................................................57
Certificate Authorities (CA)..........................................................................57
Identities......................................................................................................58
Content Filtering.................................................................................59
Edit the URL Global Whitelist......................................................................59
Edit the URL Global Blacklist......................................................................60
Active content handling...............................................................................61
Servers..........................................................................................62
DHCP Server Settings........................................................................62
Enable DHCP Server..................................................................................63
Enable DHCP Relay....................................................................................63
Disable DHCP Server/Relayer....................................................................63
DNS Relayer Settings........................................................................64
Enable DNS Relayer...................................................................................64
Disable DNS Relayer..................................................................................65
Tools..............................................................................................66
Ping ...................................................................................................66
Ping Example..............................................................................................66
Dynamic DNS ....................................................................................67
Add Dynamic DNS Settings........................................................................67
4

Backup...............................................................................................68
Exporting the DFL-1100’s Configuration.....................................................68
Restoring the DFL-1100’s Configuration.....................................................68
Restart/Reset.....................................................................................69
Restarting the DFL-1100.............................................................................69
Restoring system settings to factory defaults .............................................69
Upgrade.............................................................................................71
Upgrade Firmware......................................................................................71
Upgrade IDS Signature-database...............................................................71
Status............................................................................................72
System...............................................................................................72
Interfaces...........................................................................................73
HA......................................................................................................74
VLAN .................................................................................................75
VPN ...................................................................................................76
Connections.......................................................................................77
DHCP Server .....................................................................................78
How to read the logs....................................................................79
USAGE events...................................................................................79
DROP events.....................................................................................79
CONN events.....................................................................................79
Appendixes...................................................................................81
Appendix A: ICMP Types and Codes..................................................81
Appendix B: Common IP Protocol Numbers.......................................83
Limited Warranty..........................................................................84

Introduction
The NETDEFEND DFL-1100 provides four 10/100MB Ethernet network interface ports:
Internal/LAN, External/WAN, a DMZ port and a port that can be configured as a High
Availability Sync port or as an ETH4 port. It also provides an easily operated Web interface
that allows users to set system parameters or monitor network activities using a Web browser.
Features and Benefits
l Firewall Security
l VPN Server/Client Supported
l Content Filtering
l High Availability
l Bandwidth Management
NETDEFEND DFL-1100 features an extensive Traffic Shaper for
bandwidth management.
l Web Management
Configurable through any networked computer’s Web browser using
Netscape or Internet Explorer.
l Access Control supported
Allows you to assign different access rights for different users such
as Admin or Read-Only User.
Introduction to Firewalls
A firewall is a device that sits between your computer and the Internet and prevents
unauthorized access to or from your network. A firewall can be a computer using firewall
software, or a special piece of hardware built specifically to act as a firewall. In most
circumstances, a firewall is used to prevent unauthorized Internet users from accessing
private networks or corporate LANs and Intranets.
A firewall watches all of the information moving to and from your network and analyzes
each piece of data. Each piece of data is checked against a set of criteria that the
administrator configures. If any data does not meet the criteria, that data is blocked and
discarded. If the data meets the criteria, the data is passed through. This method is called
packet filtering.
A firewall can also run specific security functions based on the type of application or type
of port that is being used. For example, a firewall can be configured to work with an FTP or
Telnet server. Or a firewall can be configured to work with specific UDP or TCP ports to allow
certain applications or games to work properly over the Internet.
6

Introduction to Local Area Networking
Local Area Networking (LAN) is the term used when connecting several computers
together over a small area such as a building or group of buildings. LANs can be connected
over large areas. A collection of LANs connected over a large area is called a Wide Area
Network (WAN).
A LAN consists of multiple computers connected to each other. There are many types of
media that can connect computers together. The most common media is CAT5 cable (UTP or
STP twisted pair wire.) On the other hand, wireless networks do not use wires; instead they
communicate over radio waves. Each computer must have a Network Interface Card (NIC),
which communicates the data between computers. A NIC is usually a 10Mbps network card, a
10/100Mbps network card, or a wireless network card.
Most networks use hardware devices such as hubs or switches that each cable can be
connected to in order to continue the connection between computers. A hub simply takes any
data arriving through each port and forwards the data to all other ports. A switch is more
sophisticated, in that a switch can determine the destination port for a specific piece of data.
A switch minimizes network traffic overhead and speeds up the communication over a
network.
Networks take some time to plan and implement correctly. There are many ways to
configure your network. You may want to take some time to determine the best network setup
for your needs.

LEDs & Hardware Connections
WAN, LAN, DMZ & ETH4/Sync: Ethernet Link port indicators, Green. The Act LED
flickers when the ports are sending or receiving data.
Power: A solid light indicates a proper connection to the power supply.
Status: System status indicators, flashes to indicate an active system. If the LED has a
solid light please contact technical support.
Console: Serial access to the firewall software, 9600, 8bit, None Parity, 1Stop bit.
External Port (WAN): Use this port to connect to the external router, DSL modem, or
cable modem.
Internal Ports (LAN): Use this port to connect to the internal network of the office.
DMZ Port: Use this port to connect to the company’s server(s), which needs direct
connection to the Internet (FTP, SNMP, HTTP and DNS).
ETH4/Sync Port: Use this port as an extra LAN or DMZ port, or when using High
Availability as the Sync interface.
8

Package Contents
Contents of Package:
• D-Link NETDEFEND DFL-1100 Firewall
• Manual and CD
• Power cord
• Installation Guide – Mini Manual
• CAT5 - Straight-through
• CAT5 - Crossover
If any of the above items are missing, please contact your reseller.
System Requirements
• Computer with a Windows, Macintosh, or Unix based operating system with an
installed Ethernet adapter
• Internet Explorer or Netscape Navigator, version 6.0 or above, with JavaScript
enabled.
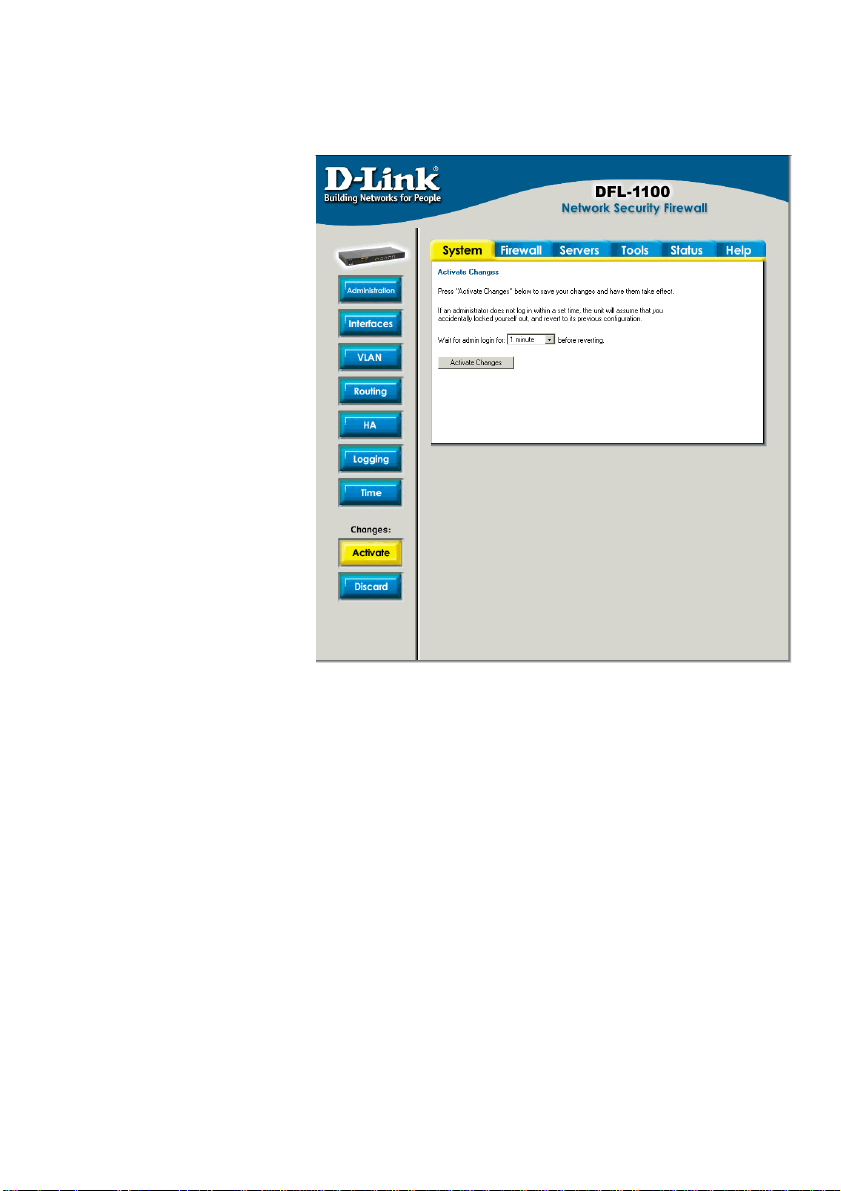
Important Note about Managing the D-Link NETDEFEND DFL-1100
When a change is made to
the configuration, a new icon
named Activate Changes
will appear. When all changes
have been made, click Activate
Changes on the Activate
Configuration Changes page.
The DFL-1100 will save the
configuration, reload it, and the
new changes will take effect.
For the change to become
permanent, the admin needs to
login again. This needs to be
done before the configurable
timeout has been reached; this
can be set on the Activate
Configuration Changes page,
by choosing the time from the
dropdown menu.
10
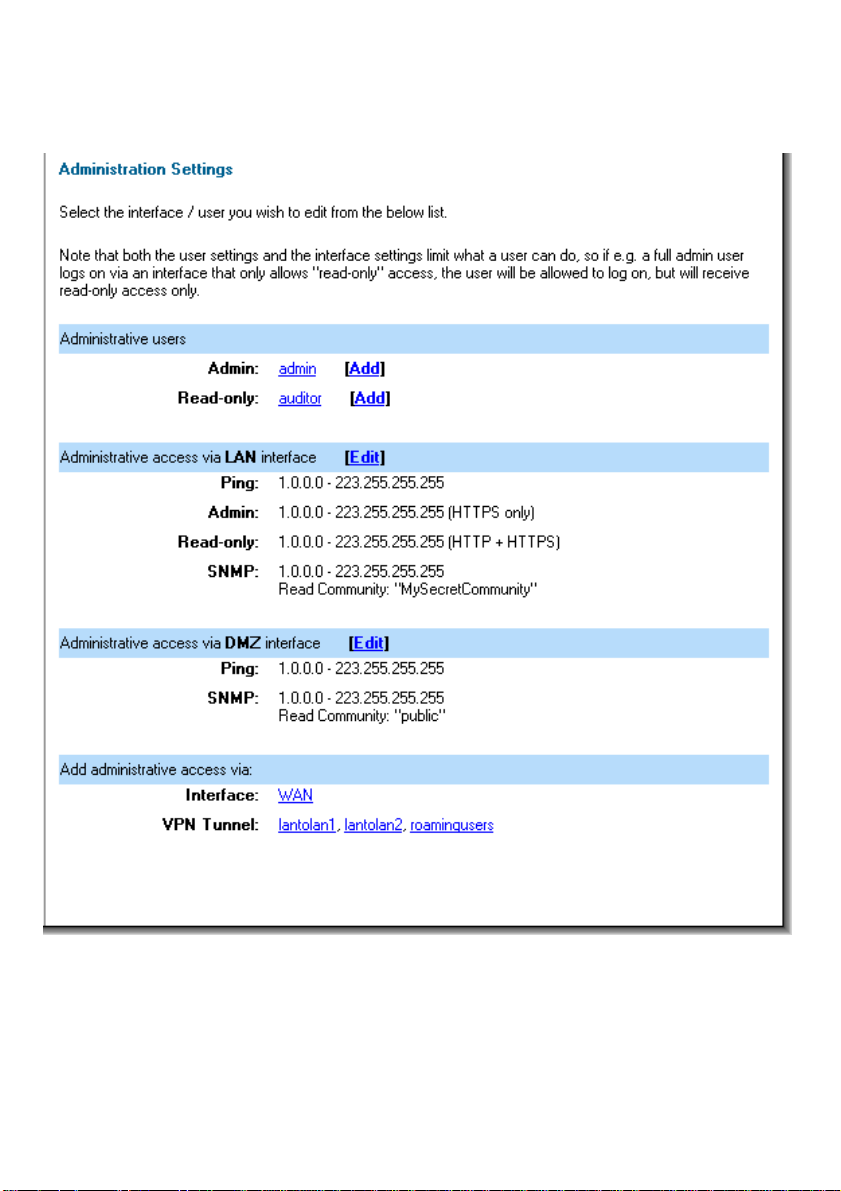
Administration Settings
Administrative Access
Ping – If enabled, specifies who can ping the interface IP of the NETDEFEND DFL-1100.
The default setting allows anyone to ping the interface IP.
Admin – If enabled allows all users with admin access to connect to the DFL-1100 and
change the configuration, which can be HTTPS or HTTP and HTTPS.
Read-Only – If enabled allows all users with read-only access to connect to the DFL-1100
and look at the configuration, which can be HTTPS or HTTP and HTTPS.

SNMP – Specifies if SNMP should be allowed or not on the interface, the DFL-1100
supports read-only access.
Add ping access to an interface
Follow these steps to add ping access to an interface.
Step 1. Click on the interface to which you would like to add ping access.
Step 2. Enable the Ping checkbox.
Step 3. Specify what networks are allowed to ping the interface, for example
192.168.1.0/24 for a whole network or 172.16.0.1 – 172.16.0.10 for a range.
Click Apply to apply the setting, or click Cancel to discard the changes.
Example:
Add Admin access to an interface
To add admin access to an interface, click on that interface. Only users with administrator
rights can login on interfaces where admin access only is enabled.
Follow these steps to add admin access to an interface.
Step 1. Click on the interface to which you would like to add admin access.
Step 2. Enable the Admin checkbox.
Step 3. Specify what networks are allowed to access the interface, for example
192.168.1.0/24 for a whole network or 172.16.0.1 – 172.16.0.10 for a range.
Step 4. Specify the protocol used to access the DFL-1100 from the dropdown menu,
either HTTP and HTTPS (Secure HTTP) or only HTTPS.
Click Apply to apply the setting or click Cancel to discard the changes.
Example:
12

Add Read-only access to an interface
Note that if you have read-only access enabled on an interface, all users will get read-only
access, even if they are administrators.
Follow these steps to add read-only access to an interface.
Step 1. Click on the interface.
Step 2. Enable the Read-only checkbox.
Step 3. Specify which networks are allowed to access the interface, for example
192.168.1.0/24 for a whole network, or 172.16.0.1 – 172.16.0.10 for a range.
Step 4. Specify the protocol used to access the DFL-1100 from the dropdown menu, both
HTTP and HTTPS (Secure HTTP), or only HTTPS.
Click the Apply button to apply the setting, or click Cancel to discard the changes.
Example:
Enable SNMP access to an interface
Follow these steps to add read-only SNMP access to an interface.
Step 1. Click on the interface to which you would like to add it.
Step 2. Enable the Read-only checkbox.
Step 3. Specify what network addresses are allowed to receive SNMP Traps, for example
192.168.1.0/24 for a whole network or 172.16.0.1 – 172.16.0.10 for a range.
Step 4. Specify the community string used to authenticate against the DFL-1100.
Click the Apply button to apply the setting, or click Cancel to discard the changes.
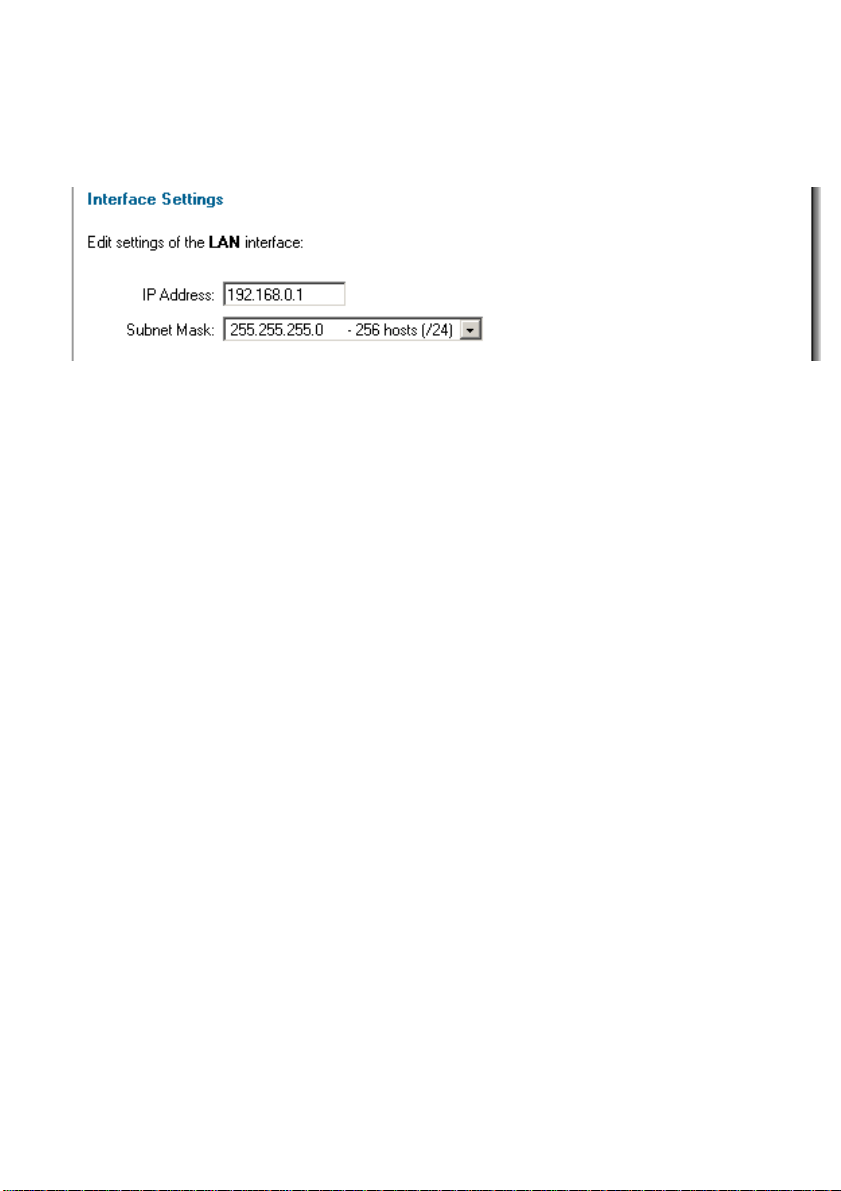
System
Interfaces
Click on System in the menu bar, and then click interfaces below it.
Change the IP of the LAN, DMZ or ETH4 interface
Follow these steps to change the IP of the LAN or DMZ interface.
Step 1. Choose which interface to view or change under the Available interfaces list.
Step 2. Fill in the IP address of the LAN, DMZ or ETH4 interface. These are the
addresses that will be used to ping the firewall, remotely control it, use as a gateway for
the internal hosts or DMZ hosts.
Step 3. Choose the correct subnet mask of this interface from the dropdown menu.
Click Apply to apply the setting, or click Cancel to discard the changes.
14

WAN Interface Settings – Using Static IP
If you are using Static IP you must fill in the IP address information provided to you by your
ISP. All fields are required except the Secondary DNS Server. The numbers displayed in
these fields are used only as examples.
• IP Address – The IP address of the WAN interface. This is the address that may
be used to ping the firewall, remotely control it, and as a source address for
dynamically translated connections.
• Subnet Mask – Network and subnet identifier.
• Gateway IP – Specifies the IP address of the default gateway used to reach for
the Internet.
• Primary and Secondary DNS Server – The IP addresses of your DNS servers,
only the Primary DNS is required.
WAN Interface Settings – Using DHCP
If you are using DHCP, there is no need to enter any values in any of the fields.

WAN Interface Settings – Using PPPoE
Use the following procedure to configure the NETDEFEND DFL-1100 external interface to use
PPPoE (Point-to-Point Protocol over Ethernet). This configuration is required if your ISP uses
PPPoE to assign the IP address of the external interface. Please enter the username and
password provided to you by your ISP.
• Username – The login or username supplied to you by your ISP.
• Password –The password supplied to you by your ISP.
• Service Name – When using PPPoE, some ISPs require you to fill in a Service
Name.
• Primary and Secondary DNS Server – The IP addresses of your DNS servers,
these are optional and are often provided by the PPPoE service.
16

WAN Interface Settings – Using PPTP
PPTP over Ethernet connections are used in some DSL and cable modem networks.
You will need your account details, and you may also need the IP configuration parameters of
the actual physical interface of the PPTP tunnel. Your ISP will supply you with this information.
• Username – The login or username supplied to you by your ISP.
• Password – The password supplied to you by your ISP.
• PPTP Server IP – The IP address of the PPTP server that connects to the
NETDEFEND DFL-1100.
Before PPTP can be used to connect to your ISP, the physical (WAN) interface parameters
need to be supplied. It’s possible to use either DHCP or Static IP depending on the type of
ISP used. This information will be supplied by your ISP.
If you are using static IP, please enter the following information.
• IP Address – The IP address of the WAN interface. This IP is used to connect to
the PPTP server.
• Subnet Mask – Size of the external network.
• Gateway IP – Specifies the IP address of the default gateway used to access the
Internet.

WAN Interface Settings – Using BigPond
The ISP Telstra BigPond uses BigPond for authentication; the IP is assigned with DHCP.
• Username – The login or username supplied to you by your ISP.
• Password – The password supplied to you by your ISP.
Traffic Shaping
When Traffic Shaping is enabled, and the correct maximum up and downstream bandwidth
is specified, it’s possible to control which policies have the highest priority when large
amounts of data are moving through the NETDEFEND DFL-1100. For example, the policy for
the web server might be given higher priority than the policies for most employees' computers.
You can use traffic shaping to guarantee the amount of bandwidth available through the
firewall for a policy; this will ensure that there is enough bandwidth available for a high-priority
service. You can also use traffic shaping to limit the amount of bandwidth available through
the firewall for a policy; in this way, you can keep less important services from using
bandwidth needed for more important services.
Note: If the limit is set too high, i.e. higher then your Internet connection, the traffic shaping
will not work at all.
18

MTU Configuration
To improve the performance of your Internet connection, you can adjust the maximum
transmission unit (MTU) of the packets that the NETDEFEND DFL-1100 transmits from its
external interface. Ideally, you want this MTU to be the same as the smallest MTU of all the
networks between the DFL-1100 and the Internet. If the packets the DFL-1100 sends are
larger, they get broken up or fragmented, which could slow down transmission speeds.
Trial and error is the only sure way of finding the optimal MTU, but there are some guidelines
that can help. For example, the MTU of many PPPoE connections is 1480, so if you connect
to the Internet via PPPoE, you might want to set the MTU size between 1400 and 1480. DSL
modems may also have small MTU sizes. Most Ethernet networks have an MTU of 1500.
Note: If you connect to your ISP using DHCP to obtain an IP address for the external
interface, you cannot set the MTU below 576 bytes due to DHCP communication
standards.
Click Apply to apply the setting, or click Cancel to discard the changes.
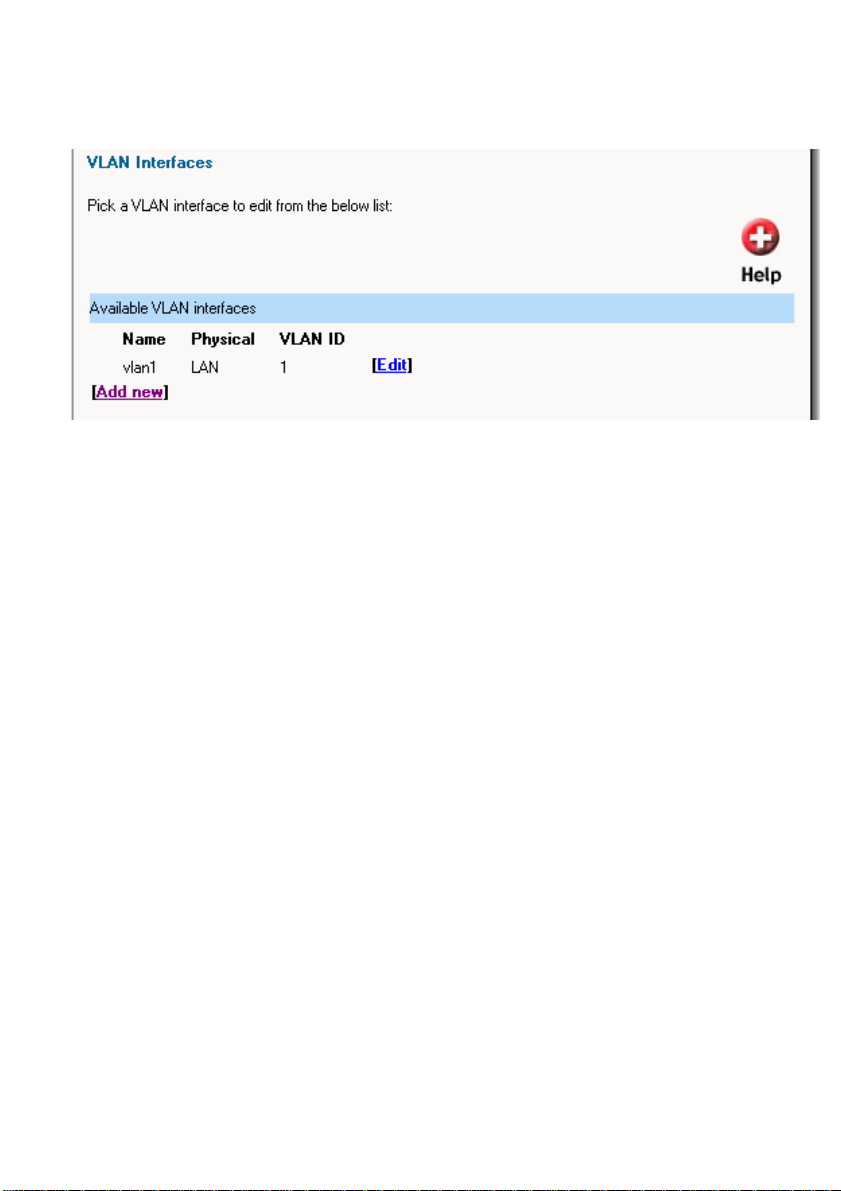
VLAN
Click on System in the menu bar, and then click VLAN below it, this will give a list of all
configured VLANs, it will look something like this:
Add a new VLAN
Follow these steps to add a new VLAN.
Step 1. Go to System and VLAN.
Step 2. Click on Add new in the bottom of the routing table.
Step 3. Choose the interface for the VLAN from the dropdown menu.
Step 4. Specify the 801.2Q VLAN ID.
Step 5. Fill in the IP address of the VLAN interface. This is the address that will be used to
ping the firewall, remotely control it and be used as a gateway for hosts on the VLAN.
Step 6. Choose the correct subnet mask of this interface from the dropdown menu.
Click Apply to apply the setting, or click Cancel to discard the changes.
Remove a VLAN
Follow these steps to add or remove a VLAN.
Step 1. Go to System and VLAN.
Step 2. Click Edit next to the VLAN you would like to remove.
Step 3. Select Delete this VLAN.
Click Apply to apply the setting, or click Cancel to discard the changes.
20
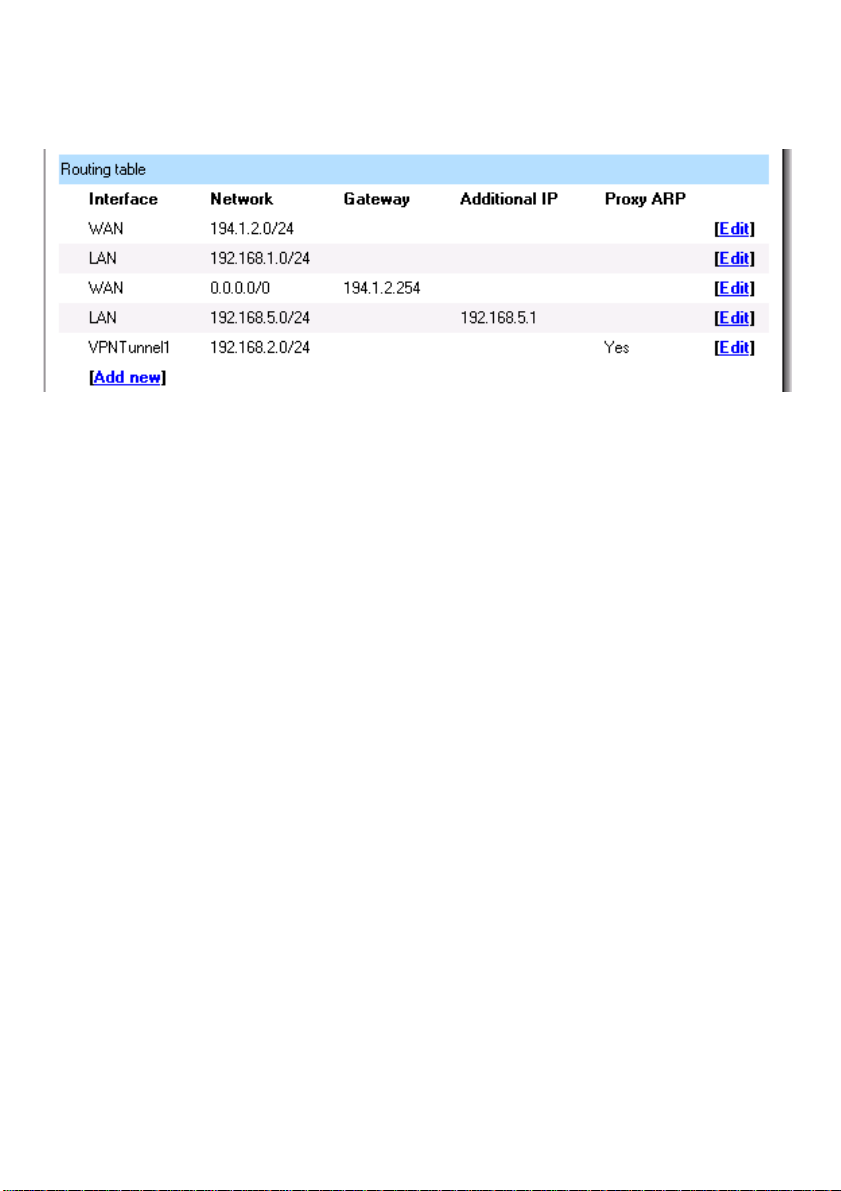
Routing
Click on System in the menu bar, and then click Routing, this will give a list of all configured
routes, it will look something like this:
The Routing configuration section shows the firewall’s routing table. DFL-1100 has an easy to
use interface.
Interface – Specifies the interface through which packets will be sent.
Network – Specifies the network address for this route.
Gateway – Specifies the IP address of the next router hop used to reach the destination
network. If the network is directly connected to the firewall interface, no gateway address
is specified.
Local IP Address – The IP address specified here will be automatically published on the
corresponding interface. This address will also be used as the sender address in ARP
queries. If no address is specified, the firewalls own interface IP address will be used.
Proxy ARP – Specifies that the firewall shall publish this route via Proxy ARP.
One advantage with this form of notation is that you can specify a gateway for a particular
route, without having a route that covers the gateway’s IP address or despite the fact that
the route that covers the gateway’s IP address is normally routed via another interface.
The difference between this form of notation and that most commonly used is that you do
not specify the interface name in a separate column. Instead, you specify the IP address
of each interface as a gateway.
Note: The firewall does not create Proxy ARP routes on VPN interfaces.

Add a new Static Route
Follow these steps to add a new route.
Step 1. Go to System and Routing.
Step 2. Click on Add new in the bottom of the routing table.
Step 3. Choose the interface that the route should be sent through from the dropdown
menu.
Step 4. Specify the network and subnet mask.
Step 5. If this network is behind a remote gateway, select Network is behind remote
gateway and specify the IP of that gateway.
Click Apply to apply the setting, or click Cancel to discard the changes.
Remove a Static Route
Follow these steps to remove a route.
Step 1. Go to System and Routing.
Step 2. Click Edit at the route you would like to remove.
Step 3. Select Delete this route.
Click Apply to apply the setting, or click Cancel to discard the changes.
22

High Availability
D-Link High Availability works by adding a back-up firewall to your existing firewall. The backup firewall has the same configuration as the primary firewall. It will stay inactive, monitoring
the primary firewall, until it deems that the primary firewall is no longer functioning, at which
point it will go active and assume the active role in the cluster. When the other firewall comes
back up, it will assume a passive role, monitoring the now active firewall.
What High Availability will do for you
D-Link High Availability will provide a redundant, state-synchronized firewalling solution. This
means that the state of the active firewall, i.e., the connection table and other vital information,
is continuously copied to the inactive firewall. When the cluster fails over to the inactive
firewall, it knows which connections are active, and communication may continue to flow
uninterrupted.
The failover time is typically about one second; well in the scope for the normal TCP
retransmit timeout, which is normally over one minute. Clients connecting through the firewall
will merely experience the failover procedure as a slight burst of packet loss, and, as TCP
always does in such situations, retransmit the lost packets within a second or two, and go on
communicating.
What High Availability will NOT do for you
Adding redundancy to your firewall setup will eliminate one of the single points of failure in
your communication path. However, it is not a panacea for all possible communication failures.
Typically, your firewall is far from the only single point of failure. Redundancy for your routers,
switches, and your Internet connection are also issues that need to be addressed.
D-Link High Availability clusters will not create a load-sharing cluster. One firewall will be
active, and the other will be inactive.
Multiple back-up firewalls cannot be used in a cluster. Only two firewalls, a "master" and a
"slave", are supported.
As is the case with all other firewalls supporting stateful failover, the D-Link High Availability
will only work between two D-Link DFL-1100 Firewalls. As the internal workings of different
firewalls, and, indeed, different major versions of the same firewall, can be radically different,
there is no way of communicating "state" to something which has a completely different
comprehension of what "state" means.

IP Addresses explained
For each cluster interface, there are three IP addresses:
• Two "real" IP addresses; one for each firewall. These addresses are used to
communicate with the firewalls themselves, i.e., for remote control and
monitoring. They should not be associated in any way with traffic flowing through
the cluster; if either firewall is inoperative, the associated IP address will simply
be unreachable.
• One "virtual" IP address; shared between the firewalls. This is the IP address to
use when configuring default gateways and other routing related matters. It is
also the address used by dynamic address translation, unless the configuration
explicitly specifies another address.
There is not much to say about the real IP addresses; they will act just like firewall interfaces
normally do. You can ping them or remote control the firewalls through them if your
configuration allows it. ARP queries for the respective addresses are answered by the firewall
that owns the IP address, using the normal hardware address, just like normal IP units do.
Note: You must have a static IP address to use HA.
The shared IP address and the failover mechanism
Both firewalls in the cluster know about the shared IP address. ARP queries for the shared IP
address, or any other IP address published via the ARP configuration section or through
Proxy ARP, will be answered by the active firewall.
The hardware address of the shared IP address, and other published addresses for that
matter, is not related to the hardware addresses of the firewall interfaces. Rather, it is
constructed from the cluster ID, on the following form: 10-00-00-C1-4A-nn, where nn is the
Cluster ID configured in the Settings section.
As the shared IP address always has the same hardware address, there will be no latency
time in updating ARP caches of units attached to the same LAN as the cluster when failover
occurs.
When a firewall discovers that its peer is no longer operational, it will broadcast a number of
ARP queries for itself, using the shared hardware address as sender address, on all
interfaces. This causes switches and bridges to re-learn where to send packets destined for
the shared hardware address in a matter of milliseconds.
Hence, the only real delay in the failover mechanism is detecting that a firewall is no longer
operational.
The activation messages (ARP queries) described above are also broadcast periodically to
ensure that switches won't forget where to send packets destined for the shared hardware
address.
24

Cluster heartbeats
A firewall detects that its peer is no longer operational when it can no longer hear "cluster
heartbeats" from its peer.
Currently, a firewall will send five cluster heartbeats per second.
When a firewall has "missed" three heartbeats, i.e., after 0.6 seconds, it will be declared
inoperative.
Cluster heartbeats have the following characteristics:
• The source IP is the interface address of the sending firewall
• The destination IP is the shared IP address
• The IP TTL is always 255. If a firewall receives a cluster heartbeat with any other
TTL, it is assumed that the packet has traversed a router, and hence cannot be
trusted at all.
• It is an UDP packet, sent from port 999, to port 999.
• The destination MAC address is the ethernet multicast address corresponding to
the shared hardware address, i.e., 11-00-00-C1-4A-nn. Link-level multicasts were
chosen over normal unicast packets for security reasons. Using unicast packets
would have meant that a local attacker could fool switches to route the
heartbeats somewhere else, causing the peer firewall to never hear the
heartbeats.
The synchronization interface
Both firewalls are connected to each other by a separate synchronization connection; the
fourth port is dedicated solely for this purpose when the firewalls are configured as HA.
The active firewall continuously sends state update messages to its peer, informing it of
connections that are opened, connections that are closed, state and lifetime changes in
connections, etc. The configuration is also transferred between the nodes using the
synchronization connection.
When the active firewall ceases to function, for whatever reason and for even a short time, the
cluster heartbeat mechanism described above will cause the inactive firewall to go active.
Since it already knows about all open connections, communication can continue to flow
uninterrupted.
Setting up a High Availability cluster
First of all, the two DFL-1100s need to be setup so that you can manage them over the we b
interface. In this example the two units are configured as follows, the master DFL-1100 will be
configured with 192.168.1.2 on its internal interface, and the slave DFL-1100 with 192.168.1.3.
Later when the setup of the HA is done, the virtual or shared IP will be 192.168.1.1 on the
LAN, this is the IP that clients on that network will use as gateway.
When both units are configured with the two individual IPs they should be connected with a
crossover cable between the fourth interfaces on each unit, this interface (ETH4) will not be
available to use as an extra DMZ or LAN interface when running HA.
Login to the master firewall and click on System in the menu bar, and then click HA below it;
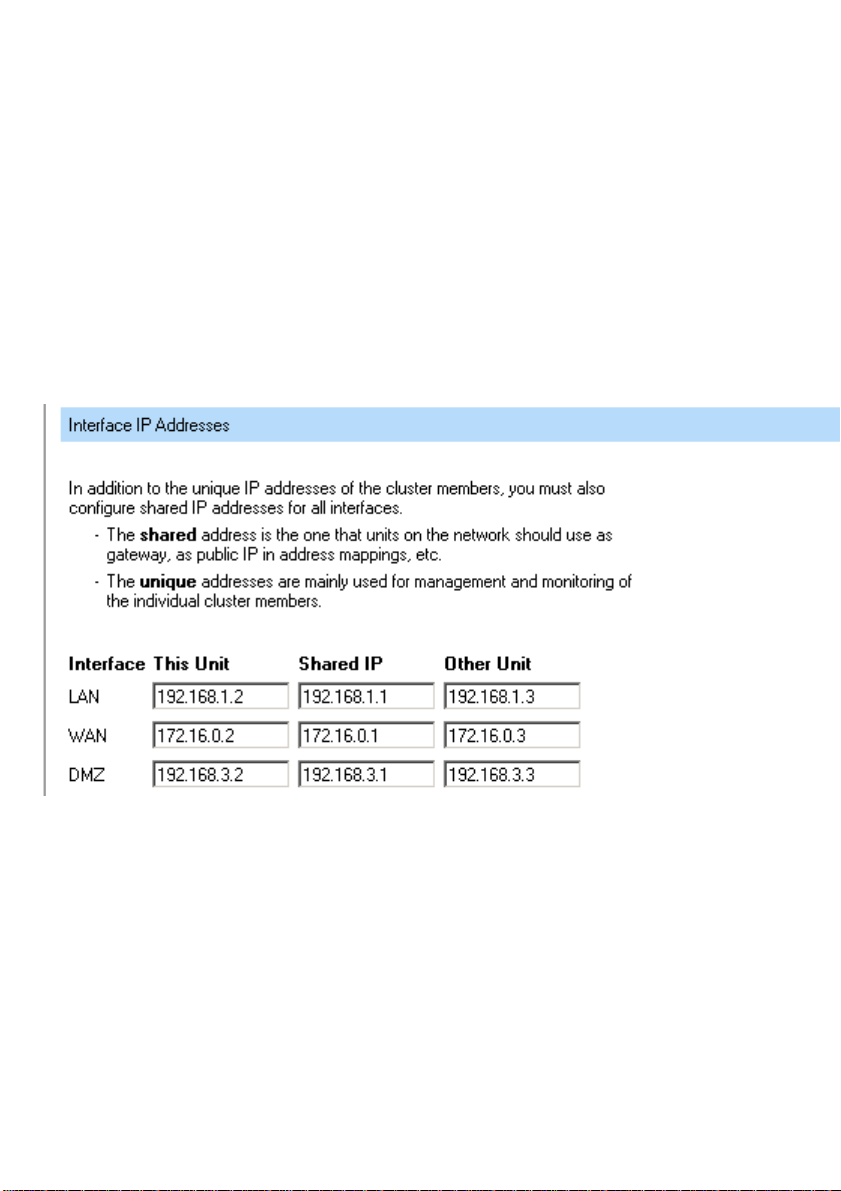
in this screen you will click on Configure additional HA parameters. This will show the
screen below; here you will fill in each Unit’s own IP and the shared IP on each interface. This
Unit means the master firewall, the one you should be configuring at the moment. Other Unit
is the slave firewall, the other DFL-1100.
You also need to configure the Cluster ID of the cluster, this has to be a number between 0
and 63, which must be the same on both firewalls in the cluster. This must be unique to your
LAN, if you are running more then one cluster.
26
 Loading...
Loading...