Page 1

53-1003087-04
30 July 2014
FastIron Ethernet Switch
Layer 3 Routing
Configuration Guide
Supporting FastIron Software Release 08.0.10d
Page 2

©
2014, Brocade Communications Systems, Inc. All Rights Reserved.
Brocade, the B-wing symbol, Brocade Assurance, ADX, AnyIO, DCX, Fabric OS, FastIron, HyperEdge, ICX, MLX, MyBrocade, NetIron,
OpenScript, VCS, VDX, and Vyatta are registered trademarks, and The Effortless Network and the On-Demand Data Center are trademarks
of Brocade Communications Systems, Inc., in the United States and in other countries. Other brands and product names mentioned may be
trademarks of others.
Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any
equipment, equipment feature, or service offered or to be offered by Brocade. Brocade reserves the right to make changes to this document
at any time, without notice, and assumes no responsibility for its use. This informational document describes features that may not be
currently available. Contact a Brocade sales office for information on feature and product availability. Export of technical data contained in
this document may require an export license from the United States government.
The authors and Brocade Communications Systems, Inc. assume no liability or responsibility to any person or entity with respect to the
accuracy of this document or any loss, cost, liability, or damages arising from the information contained herein or the computer programs that
accompany it.
The product described by this document may contain open source software covered by the GNU General Public License or other open
source license agreements. To find out which open source software is included in Brocade products, view the licensing terms applicable to
the open source software, and obtain a copy of the programming source code, please visit http://www.brocade.com/support/oscd.
Page 3

Contents
Preface...................................................................................................................................15
Document conventions....................................................................................15
Text formatting conventions................................................................ 15
Command syntax conventions............................................................ 15
Notes, cautions, and warnings............................................................ 16
Brocade resources.......................................................................................... 17
Contacting Brocade Technical Support...........................................................17
Document feedback........................................................................................ 18
About This Document.............................................................................................................. 19
Supported Hardware....................................................................................... 19
What’s new in this document.......................................................................... 19
How command information is presented in this guide.....................................20
IP Configuration......................................................................................................................21
Supported IP features..................................................................................... 21
Basic IP configuration..................................................................................... 22
IP configuration overview................................................................................ 23
Full Layer 3 support............................................................................ 23
IP interfaces........................................................................................ 23
IP packet flow through a Layer 3 switch..............................................25
IP route exchange protocols............................................................... 28
IP multicast protocols.......................................................................... 29
IP interface redundancy protocols.......................................................29
ACLs and IP access policies...............................................................29
Basic IP parameters and defaults - Layer 3 Switches.....................................30
When parameter changes take effect................................................. 30
IP global parameters - Layer 3 Switches............................................ 30
IP interface parameters - Layer 3 Switches........................................ 34
Basic IP parameters and defaults - Layer 2 Switches.....................................35
IP global parameters - Layer 2 switches............................................. 36
Interface IP parameters - Layer 2 switches.........................................37
Configuring IP parameters - Layer 3 switches................................................ 38
Configuring IP addresses....................................................................38
Configuring 31-bit subnet masks on point-to-point networks.............. 41
Configuring DNS resolver................................................................... 43
Configuring packet parameters........................................................... 45
Changing the router ID........................................................................48
Specifying a single source interface for specified packet types.......... 49
ARP parameter configuration..............................................................53
Configuring forwarding parameters.....................................................59
Disabling ICMP messages.................................................................. 62
Enabling ICMP Redirect Messages.................................................... 63
Static routes configuration...................................................................64
Configuring a default network route.................................................... 72
Configuring IP load sharing.................................................................74
ICMP Router Discovery Protocol configuration...................................77
IRDP parameters................................................................................ 77
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
3
Page 4

Reverse Address Resolution Protocol configuration.........................79
Configuring UDP broadcast and IP helper parameters.....................81
BootP and DHCP relay parameter configuration.............................. 83
DHCP Server.................................................................................... 85
Displaying DHCP Server information................................................94
DHCP Client-Based Auto-Configuration and Flash image update....98
Configuring IP parameters - Layer 2 Switches........................................... 105
Configuring the management IP address and specifying the
default gateway......................................................................... 105
Configuring Domain Name Server (DNS) resolver......................... 106
Changing the TTL threshold............................................................107
DHCP Assist configuration..............................................................108
IPv4 point-to-point GRE tunnels ................................................................ 111
IPv4 GRE tunnel overview.............................................................. 112
GRE packet structure and header format....................................... 112
Path MTU Discovery (PMTUD) support..........................................113
Configuration considerations for PMTUD support ......................... 113
Tunnel loopback ports for GRE tunnels.......................................... 114
Support for IPv4 multicast routing over GRE tunnels..................... 115
GRE support with other features ....................................................115
Configuration considerations for GRE IP tunnels........................... 116
Configuration tasks for GRE tunnels...............................................117
Example point-to-point GRE tunnel configuration...........................126
Displaying GRE tunneling information............................................ 127
Clearing GRE statistics................................................................... 131
Displaying IP configuration information and statistics.................................132
Changing the network mask display to prefix format...................... 132
Displaying IP information - Layer 3 Switches..................................132
Displaying IP information - Layer 2 Switches..................................146
Disabling IP checksum check..................................................................... 151
Layer 3 Routing Protocols................................................................................................... 153
Supported Layer 3 routing protocols features.............................................153
Adding a static IP route...............................................................................154
Configuring a "null" route................................................................ 155
Static route next hop resolution...................................................... 156
Static route recursive lookup...........................................................156
Static route resolve by default route............................................... 156
Adding a static ARP entry........................................................................... 157
Modifying and displaying Layer 3 system parameter limits.........................157
Layer 3 configuration notes.............................................................158
FastIron second generation modules..............................................158
FastIron third generation modules.................................................. 158
Displaying Layer 3 system parameter limits....................................158
Enabling or disabling routing protocols....................................................... 159
Enabling or disabling Layer 2 switching......................................................159
Configuration notes and feature limitations for Layer 2 switching...160
Command syntax for Layer 2 switching.......................................... 160
Configuring a Layer 3 Link Aggregration Group (LAG)...............................160
IPv6 Configuration on FastIron X Series, FCX, and ICX Series Switches................................. 163
Supported IPv6 features on FastIron X Series, FCX, and ICX devices...... 163
Full Layer 3 IPv6 feature support................................................................165
IPv6 addressing overview........................................................................... 165
IPv6 address types..........................................................................166
IPv6 stateless auto-configuration....................................................168
4
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 5

IPv6 CLI command support ..........................................................................168
IPv6 host address on a Layer 2 switch......................................................... 171
Configuring a global or site-local IPv6 address with a manually
configured interface ID................................................................ 171
Configuring a link-local IPv6 address as a system-wide address
for a switch.................................................................................. 171
Configuring the management port for an IPv6 automatic address
configuration............................................................................................ 172
Configuring basic IPv6 connectivity on a Layer 3 switch.............................. 172
Enabling IPv6 routing........................................................................ 172
IPv6 configuration on each router interface...................................... 173
Configuring IPv4 and IPv6 protocol stacks....................................... 175
IPv6 management (IPv6 host support)..........................................................176
Configuring IPv6 management ACLs................................................176
Restricting SNMP access to an IPv6 node....................................... 177
Specifying an IPv6 SNMP trap receiver............................................ 177
Configuring SNMP V3 over IPv6.......................................................177
Secure Shell, SCP, and IPv6............................................................ 177
IPv6 Telnet........................................................................................ 177
IPv6 traceroute..................................................................................178
Configuring name-to-IPv6 address resolution using IPv6 DNS
resolver........................................................................................178
Defining an IPv6 DNS entry.............................................................. 179
Pinging an IPv6 address................................................................... 179
Configuring an IPv6 Syslog server....................................................180
Viewing IPv6 SNMP server addresses............................................. 180
Disabling router advertisement and solicitation messages............... 181
Disabling IPv6 on a Layer 2 switch................................................... 181
IPv6 ICMP feature configuration................................................................... 182
Configuring ICMP rate limiting.......................................................... 182
Enabling IPv6 ICMP redirect messages............................................183
IPv6 neighbor discovery configuration.......................................................... 183
IPv6 neighbor discovery configuration notes.................................... 184
Neighbor solicitation and advertisement messages..........................184
Router advertisement and solicitation messages..............................184
Neighbor redirect messages............................................................. 185
Setting neighbor solicitation parameters for duplicate address
detection...................................................................................... 185
Setting IPv6 router advertisement parameters..................................186
Prefixes advertised in IPv6 router advertisement messages............ 187
Setting flags in IPv6 router advertisement messages....................... 188
Enabling and disabling IPv6 router advertisements.......................... 189
IPv6 router advertisement preference support..................................189
Configuring reachable time for remote IPv6 nodes...........................189
IPv6 MTU...................................................................................................... 190
Configuration notes and feature limitations for IPv6 MTU.................190
Changing the IPv6 MTU....................................................................190
Static neighbor entries configuration.............................................................191
Limiting the number of hops an IPv6 packet can traverse............................ 192
IPv6 source routing security enhancements................................................. 192
TCAM space on FCX device configuration................................................... 192
Allocating TCAM space for IPv4 routing information.........................193
Allocating TCAM space for GRE tunnel information......................... 193
Clearing global IPv6 information................................................................... 193
Clearing the IPv6 cache.................................................................... 194
Clearing IPv6 neighbor information...................................................194
Clearing IPv6 routes from the IPv6 route table................................. 195
Clearing IPv6 traffic statistics............................................................ 195
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
5
Page 6

Displaying global IPv6 information..............................................................195
Displaying IPv6 cache information..................................................195
Displaying IPv6 interface information..............................................196
Displaying IPv6 neighbor information............................................. 198
Displaying the IPv6 route table ...................................................... 199
Displaying local IPv6 routers...........................................................201
Displaying IPv6 TCP information.................................................... 202
Displaying IPv6 traffic statistics.......................................................205
DHCP relay agent for IPv6..........................................................................209
Configuring DHCP for IPv6 relay agent.......................................... 209
Enabling the interface-ID on the DHCPv6 relay agent messages.. 210
Displaying DHCPv6 relay agent information...................................210
Displaying the DHCPv6 Relay configured destinations.................. 210
Displaying the DHCPv6 Relay information for an interface............ 211
DHCPv6 Relay Agent Prefix Delegation Notification...................... 212
Configuring DHCPv6 Relay Agent Prefix Delegation Notification...213
Displaying the DHCPv6 Relay Agent Prefix Delegation
Notification information..............................................................214
RIP.....................................................................................................................................219
RIP feature support.....................................................................................219
RIP Overview.............................................................................................. 219
RIP parameters and defaults...................................................................... 220
RIP global parameters.................................................................... 220
RIP interface parameters................................................................ 222
Configuring RIP parameters........................................................................222
Enabling RIP................................................................................... 222
Configuring metric parameters........................................................223
Changing the administrative distance............................................. 223
Configuring redistribution................................................................ 224
Configuring route learning and advertising parameters.................. 226
Changing the route loop prevention method...................................227
Suppressing RIP route advertisement on a VRRP or VRRPE
backup interface........................................................................ 228
Configuring RIP route filters using prefix-lists and route maps....... 228
Setting RIP timers........................................................................... 229
Displaying RIP Information..........................................................................230
Displaying CPU utilization statistics............................................................ 232
RIPng................................................................................................................................. 233
RIPng feature support.................................................................................233
RIPng Overview.......................................................................................... 233
Configuring RIPng.......................................................................................234
Enabling RIPng............................................................................... 234
Configuring RIPng timers................................................................235
Configuring route learning and advertising parameters.................. 235
Redistributing routes into RIPng..................................................... 237
Controlling distribution of routes through RIPng............................. 237
Configuring poison reverse parameters..........................................238
Clearing RIPng routes from IPv6 route table.............................................. 239
Displaying RIPng information......................................................................239
Displaying RIPng configuration.......................................................239
Displaying RIPng routing table........................................................240
OSPFv2.............................................................................................................................. 243
6
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 7

OSPFv2 feature support............................................................................... 243
OSPF overview............................................................................................. 244
OSPF point-to-point links.............................................................................. 246
Designated routers in multi-access networks................................................247
Designated router election in multi-access networks.................................... 247
OSPF RFC 1583 and 2328 compliance........................................................249
Reduction of equivalent AS external LSAs................................................... 249
Algorithm for AS external LSA reduction...........................................250
Support for OSPF RFC 2328 Appendix E.....................................................251
OSPF graceful restart................................................................................... 252
OSPF stub router advertisement.......................................................252
OSPF Shortest Path First throttling...................................................253
IETF RFC and internet draft support.................................................254
Dynamic OSPF activation and configuration.....................................254
Configuring OSPF......................................................................................... 254
Configuration rules............................................................................ 254
OSPF parameters............................................................................. 255
Enable OSPF on the device..............................................................256
Assign OSPF areas...........................................................................256
Assign a totally stubby area.............................................................. 257
Assigning an area range (optional) .................................................. 260
Assigning an area cost (optional parameter) ................................... 260
Assigning interfaces to an area.........................................................261
Setting all OSPFv2 interfaces to the passive state........................... 262
Modify interface defaults................................................................... 262
Change the timer for OSPF authentication changes.........................264
Block flooding of outbound LSAs on specific OSPF interfaces.........265
Assign virtual links.............................................................................266
Modify virtual link parameters........................................................... 268
Changing the reference bandwidth for the cost on OSPF
interfaces..................................................................................... 269
Define redistribution filters.................................................................271
Modify default metric for redistribution.............................................. 273
Enable route redistribution................................................................ 273
Disable or re-enable load sharing..................................................... 275
Configure external route summarization........................................... 276
Configure default route origination.................................................... 277
Supported match and set conditions.................................................279
OSPF non-stop routing................................................................................. 279
Synchronization of critical OSPF elements................................................... 280
Link state database synchronization................................................. 280
Neighbor router synchronization....................................................... 280
Interface synchronization.................................................................. 281
Standby module operations.......................................................................... 281
Neighbor database............................................................................281
LSA database....................................................................................281
Enabling and disabling NSR......................................................................... 282
Limitations of NSR............................................................................ 282
Disabling configuration..................................................................................282
OSPF distribute list....................................................................................... 283
Configuring an OSPF distribution list using ACLs ............................284
Configuring an OSPF distribution list using route maps ...................285
Modify SPF timers.............................................................................286
Modify redistribution metric type....................................................... 286
Modify administrative distance.......................................................... 287
Configure OSPF group Link State Advertisement (LSA) pacing.......288
Modify OSPF traps generated...........................................................288
Modify exit overflow interval.............................................................. 289
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
7
Page 8

Specify types of OSPF Syslog messages to log.............................289
Configuring an OSPF network type.................................................290
Configuring OSPF Graceful Restart................................................291
Configuring OSPF router advertisement.........................................293
Configuring OSPF shortest path first throttling................................294
Displaying OSPF information......................................................................295
Displaying general OSPF configuration information....................... 296
Displaying OSPF area information..................................................298
Displaying OSPF neighbor information...........................................299
Displaying OSPF interface information........................................... 301
Displaying OSPF interface brief information................................... 303
Displaying OSPF route information.................................................304
Displaying OSPF database information.......................................... 306
Displaying OSPF external link state information.............................307
Displaying OSPF database-summary information.......................... 308
Displaying OSPF database link state information...........................309
Displaying OSPF ABR and ASBR information................................310
Displaying OSPF trap status...........................................................311
Viewing Configured OSPF point-to-point links................................311
Displaying OSPF virtual neighbor and link information...................312
Clearing OSPF neighbors............................................................... 314
Displaying OSPF Graceful Restart information...............................314
Displaying OSPF Router Advertisement information...................... 315
Clearing OSPF information......................................................................... 316
Clearing OSPF neighbors............................................................... 316
Disabling and re-enabling the OSPF process.................................316
Clearing OSPF routes.....................................................................316
OSPFv3.............................................................................................................................. 317
OSPFv3 feature support............................................................................. 317
OSPFv3 overview....................................................................................... 318
Link-state advertisement types for OSPFv3................................................318
Configuring OSPFv3................................................................................... 319
Enabling OSPFv3............................................................................319
Assigning OSPFv3 areas................................................................320
Assigning an area cost for OSPFv3 (optional parameter).............. 324
Specifying a network type............................................................... 325
Configuring virtual links...................................................................326
Changing the reference bandwidth for the cost on OSPFv3
interfaces...................................................................................327
Redistributing routes into OSPFv3..................................................328
Filtering OSPFv3 routes..................................................................332
Configuring default route origination............................................... 335
Modifying Shortest Path First timers............................................... 335
Modifying administrative distance................................................... 336
Configuring the OSPFv3 LSA pacing interval................................. 337
Modifying exit overflow interval....................................................... 338
Modifying external link state database limit.................................... 338
Setting all OSPFv3 interfaces to the passive state......................... 338
Modifying OSPFv3 interface defaults..............................................338
Disabling or re-enabling event logging............................................339
IPsec for OSPFv3........................................................................... 340
Configuring IPsec for OSPFv3........................................................340
Configuring OSPFv3 Graceful Restart Helper mode...................... 347
Configuring OSPFv3 Non-stop routing (NSR).................................347
Displaying OSPFv3 information.................................................................. 348
General OSPFv3 configuration information.................................... 348
8
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 9

Displaying OSPFv3 area information................................................ 348
Displaying OSPFv3 database information........................................ 349
Displaying IPv6 interface information................................................355
Displaying IPv6 OSPFv3 interface information................................. 356
Displaying OSPFv3 memory usage.................................................. 360
Displaying OSPFv3 neighbor information......................................... 361
Displaying routes redistributed into OSPFv3.................................... 365
Displaying OSPFv3 route information............................................... 365
Displaying OSPFv3 SPF information................................................ 367
Displaying OSPFv3 GR Helper mode information ........................... 370
Displaying OSPFv3 NSR information................................................370
Displaying IPv6 OSPF virtual link information...................................371
Displaying OSPFv3 virtual neighbor information...............................371
IPsec examples.................................................................................372
OSPFv3 clear commands ............................................................................ 379
Clearing all OSPFv3 data..................................................................379
Clearing OSPFv3 data in a VRF....................................................... 380
Clearing all OSPFv3 packet counters............................................... 380
Scheduling Shortest Path First (SPF) calculation............................. 380
Clearing all redistributed routes from OSPFv3..................................380
Clearing OSPFv3 neighbors............................................................. 380
Configuring BGP4 (IPv4)....................................................................................................... 383
Supported BGP4 features ............................................................................ 383
BGP4 overview............................................................................................. 385
Relationship between the BGP4 route table and the IP route table..385
How BGP4 selects a path for a route (BGP best path selection
algorithm).....................................................................................386
BGP4 message types....................................................................... 388
Grouping of RIB-out peers................................................................ 389
Implementation of BGP4............................................................................... 390
BGP4 restart................................................................................................. 390
BGP4 Peer notification during a management module switchover... 391
BGP4 neighbor local AS................................................................... 392
Basic configuration and activation for BGP4.................................................393
Disabling BGP4.................................................................................394
BGP4 parameters......................................................................................... 395
Parameter changes that take effect immediately.............................. 396
Parameter changes that take effect after resetting neighbor
sessions.......................................................................................396
Parameter changes that take effect after disabling and re-
enabling redistribution................................................................. 397
Memory considerations................................................................................. 397
Memory configuration options obsoleted by dynamic memory......... 397
Basic configuration tasks required for BGP4................................................ 398
Enabling BGP4 on the device........................................................... 398
Changing the device ID.....................................................................398
Setting the local AS number..............................................................399
Adding a loopback interface..............................................................400
Adding BGP4 neighbors....................................................................400
Adding a BGP4 peer group............................................................... 408
Optional BGP4 configuration tasks............................................................... 411
Changing the Keep Alive Time and Hold Time................................. 411
Changing the BGP4 next-hop update timer...................................... 412
Enabling fast external fallover........................................................... 412
Changing the maximum number of paths for BGP4 Multipath
load sharing................................................................................. 412
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
9
Page 10

Customizing BGP4 Multipath load sharing..................................... 414
Specifying a list of networks to advertise........................................ 415
Changing the default local preference............................................ 416
Using the IP default route as a valid next-hop for a BGP4 route.... 416
Changing the default MED (Metric) used for route redistribution....417
Enabling next-hop recursion........................................................... 417
Changing administrative distances................................................. 419
Requiring the first AS to be the neighbor AS.................................. 420
Disabling or re-enabling comparison of the AS-Path length........... 421
Enabling or disabling comparison of device IDs............................. 422
Configuring the device to always compare Multi-Exit
Discriminators............................................................................422
Treating missing MEDs as the worst MEDs....................................423
Configuring route reflection parameters..........................................423
Configuring confederations............................................................. 426
Aggregating routes advertised to BGP4 neighbors.........................429
Configuring BGP4 restart............................................................................429
Configuring BGP4 Restart for the global routing instance.............. 429
Configuring BGP4 Restart for a VRF.............................................. 430
Configuring timers for BGP4 Restart (optional)...............................430
BGP4 null0 routing..........................................................................431
Configuring BGP4 null0 routing...................................................... 431
Modifying redistribution parameters............................................................434
Redistributing connected routes..................................................... 435
Redistributing RIP routes................................................................ 435
Redistributing OSPF external routes...............................................435
Redistributing static routes..............................................................436
Redistributing IBGP routes..............................................................436
Filtering....................................................................................................... 437
AS-path filtering...............................................................................437
BGP4 filtering communities.............................................................440
Defining and applying IP prefix lists................................................ 441
Defining neighbor distribute lists..................................................... 442
Defining route maps........................................................................443
Using a table map to set the tag value............................................451
Configuring cooperative BGP4 route filtering..................................451
Four-byte Autonomous System Numbers (AS4).........................................454
Enabling AS4 numbers................................................................... 454
BGP4 AS4 attribute errors.......................................................................... 458
Error logs.........................................................................................458
Configuring route flap dampening...............................................................459
Globally configuring route flap dampening......................................460
Using a route map to configure route flap dampening for a
specific neighbor........................................................................461
Removing route dampening from a route....................................... 462
Displaying and clearing route flap dampening statistics................. 462
Generating traps for BGP4..........................................................................464
Configuring BGP4....................................................................................... 464
Entering and exiting the address family configuration level........................ 466
BGP route reflector..................................................................................... 466
Configuring BGP route reflector......................................................467
Specifying a maximum AS path length....................................................... 469
Setting a global maximum AS path limit..........................................470
Setting a maximum AS path limit for a peer group or neighbor...... 470
BGP4 max-as error messages....................................................................471
Originating the default route........................................................................471
Changing the default metric used for route cost......................................... 472
Configuring a static BGP4 network ............................................................ 472
10
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 11

Setting an administrative distance for a static BGP4 network...........473
Limiting advertisement of a static BGP4 network to selected
neighbors.....................................................................................473
Route-map continue clauses for BGP4 routes..................................473
Specifying route-map continuation clauses.......................................474
Dynamic route filter update............................................................... 475
Generalized TTL Security Mechanism support............................................. 477
Displaying BGP4 information........................................................................ 477
Displaying summary BGP4 information............................................ 478
Displaying the active BGP4 configuration......................................... 481
Displaying summary neighbor information........................................ 481
Displaying BGP4 neighbor information............................................. 483
Displaying peer group information.................................................... 493
Displaying summary route information..............................................493
Displaying VRF instance information................................................ 494
Displaying the BGP4 route table....................................................... 494
Displaying BGP4 route-attribute entries............................................502
Displaying the routes BGP4 has placed in the IP route table........... 503
Displaying route flap dampening statistics........................................ 504
Displaying the active route map configuration.................................. 505
Displaying BGP4 graceful restart neighbor information.................... 505
Displaying AS4 details...................................................................... 506
Displaying route-map continue clauses............................................ 514
Updating route information and resetting a neighbor session...........517
Using soft reconfiguration................................................................. 517
Dynamically requesting a route refresh from a BGP4 neighbor........519
Closing or resetting a neighbor session............................................ 522
Clearing and resetting BGP4 routes in the IP route table................. 522
Clearing traffic counters................................................................................ 523
Clearing diagnostic buffers............................................................................523
Configuring BGP4+...............................................................................................................525
Supported BGP4+ features...........................................................................525
BGP4+ overview........................................................................................... 525
Address family configuration level.................................................................526
Configuring BGP4+....................................................................................... 526
Enabling BGP4+................................................................................527
Configuring BGP4+ neighbors using global or site-local IPv6
addresses.................................................................................... 528
Adding BGP4+ neighbors using link-local addresses....................... 528
Configuring a BGP4+ peer group......................................................530
Advertising the default BGP4+ route.................................................531
Importing routes into BGP4+ ............................................................532
Redistributing prefixes into BGP4+................................................... 532
Aggregating routes advertised to BGP4 neighbors...........................533
Using route maps.............................................................................. 534
Enabling next-hop recursion............................................................. 534
Using the IPv6 default route as a valid next-hop for a BGP4+ route.536
Clearing BGP4+ information......................................................................... 537
Removing route flap dampening....................................................... 537
Clearing route flap dampening statistics........................................... 537
Clearing BGP4+ local route information............................................538
Clearing BGP4+ neighbor information.............................................. 538
Clearing and resetting BGP4+ routes in the IPv6 route table........... 541
Clearing traffic counters for all BGP4+ neighbors.............................541
Displaying BGP4+ information...................................................................... 541
Displaying the BGP4+ route table.....................................................542
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
11
Page 12

Displaying BGP4+ route information...............................................547
Displaying BGP4+ route-attribute entries........................................549
Displaying the BGP4+ running configuration.................................. 551
Displaying dampened BGP4+ paths............................................... 551
Displaying filtered-out BGP4+ routes..............................................552
Displaying route flap dampening statistics......................................556
Displaying BGP4+ neighbor information......................................... 557
Displaying BGP4+ peer group configuration information................ 579
Displaying BGP4+ summary........................................................... 580
Configuring BGP4+ graceful restart............................................................ 582
Configuring BGP4+ graceful restart for the global routing
instance..................................................................................... 582
Configuring timers for BGP4+ graceful restart (optional)................ 582
Displaying BGP4+ graceful restart neighbor information................ 583
VRRP and VRRP-E...............................................................................................................585
VRRP and VRRP-E Feature Table............................................................. 585
Overview..................................................................................................... 586
VRRP and VRRP-E overview..................................................................... 586
VRRP overview...............................................................................586
VRRP-E overview........................................................................... 591
ARP behavior with VRRP-E............................................................593
Comparison of VRRP and VRRP-E............................................................ 594
VRRP.............................................................................................. 594
VRRP-E...........................................................................................594
Architectural differences between VRRP and VRRP-E.................. 594
VRRP and VRRP-E parameters................................................................. 595
Note regarding disabling VRRP or VRRP-E................................... 598
Basic VRRP parameter configuration......................................................... 599
Configuration rules for VRRP..........................................................599
Configuring the Owner for IPv4 VRRP............................................599
Configuring the Owner for IPv6 VRRP............................................600
Configuring a Backup for IPv4 VRRP............................................. 600
Configuring a Backup for IPv6 VRRP............................................. 601
Assigning an auto-generated link-local IPv6 address for a
VRRPv3 cluster......................................................................... 602
Enabling the v2 checksum computation method in IPv4 and
IPv6 VRRPv3.............................................................................602
Enabling accept mode in VRRP non-Owner Master router............ 603
Configuration considerations for IPv6 VRRP v3 and IPv6
VRRP-E v3 support on Brocade devices...................................603
Basic VRRP-E parameter configuration......................................................603
Configuration rules for VRRP-E...................................................... 603
Configuring IPv4 VRRP-E...............................................................604
Configuring IPv6 VRRP-E...............................................................604
Additional VRRP and VRRP-E parameter configuration.............................605
VRRP and VRRP-E authentication types....................................... 606
VRRP router type............................................................................607
Suppression of RIP advertisements................................................609
Hello interval configuration..............................................................609
Dead interval configuration............................................................. 610
Backup Hello message state and interval.......................................610
Track port configuration.................................................................. 611
Track priority configuration..............................................................611
Backup preempt configuration........................................................ 612
Changing the timer scale................................................................ 612
VRRP-E slow start timer................................................................. 613
12
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 13

VRRP-E Extension for Server Virtualization..................................... 614
Suppressing default interface-level RA messages on an interface
configured with IPv6 VRRP or VRRP-E...................................... 616
Suppression of interface level RA in a IPv6 VRRP/VRRP-E
configured interface..................................................................... 617
Forcing a Master router to abdicate to a Backup router................................617
Displaying VRRP and VRRP-E information.................................................. 618
Displaying summary information....................................................... 619
Displaying detailed information......................................................... 620
Displaying statistics...........................................................................627
Clearing VRRP or VRRP-E statistics................................................ 631
Configuration examples................................................................................ 631
VRRP example..................................................................................632
VRRP-E example.............................................................................. 633
Configuring Multi-VRF...........................................................................................................635
Supported Multi-VRF features ......................................................................635
Supported devices, interface modules, and protocols.................................. 636
Multi-VRF Overview...................................................................................... 637
Configuring Multi-VRF...................................................................................638
Configuring VRF-related system-max values....................................639
Configuring VRF instances............................................................... 642
Configuring a route distinguisher...................................................... 642
Configuring IPv4 and/or IPv6 address families ................................ 642
Configuring routing protocols for new Multi-VRF instance................ 643
Assigning a VRF routing instance to an L3 interface........................ 643
Removing a Multi-VRF instance....................................................................644
Configuring Management VRFs....................................................................645
Source interface and management VRF compatibility...................... 645
Supported management applications................................................646
Configuring a global management VRF........................................................ 648
Configuration notes........................................................................... 649
Displaying the management VRF information...............................................649
Configuring sFlow with Multi-VRFs............................................................... 651
Configuring static-ARP for Multi-VRFs..........................................................652
Configuring static-ARP on default VRFs........................................... 653
Configuring static-ARP on non-default VRFs....................................653
Proxy ARP and Local Proxy ARP..................................................... 653
ARP rate-limiting .............................................................................. 653
Configuring DAI to support a Multi-VRF instance......................................... 654
Configuring DHCP snooping to support a Multi-VRF instance......................654
Configuring IP Source Guard to support a Multi-VRF instance.....................654
Configuring the Neighbor Discovery Protocol............................................... 654
Configuring Static-Neighbor on default VRFs................................... 654
Configuring static-neighbor on non-default VRFs............................. 655
Assigning loopback interfaces.......................................................................655
Configuring load sharing for Multi-VRFs....................................................... 655
Multi-VRF Show commands..........................................................................655
View all configured VRFs in summary mode.................................... 656
View specific VRF in detail mode......................................................656
View all configured VRFs in detail mode...........................................656
View DHCPv6 snooping status and ports ........................................ 657
View DHCPv6 snooping binding database ...................................... 657
Application and routing protocol specific VRF show commands.......657
Multi-VRF basic configuration example ........................................................657
Step 1: System-max configuration.................................................... 658
Step 2: Configuring VRFs................................................................. 660
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
13
Page 14

Step 3: Start OSPF process for each VRF......................................660
Step 4: Assign VRFs to each ve interfaces, and configure IP
address and OSPF ...................................................................660
Show IP OSPF neighbor and show ip route output for each VRF . 661
Layer 3 Routing Commands................................................................................................ 663
arp-internal-priority......................................................................................664
ipv6 nd router-preference............................................................................665
ipv6-address auto-gen-link-local................................................................. 666
use-v2-checksum........................................................................................667
accept-mode............................................................................................... 668
ipv6 nd skip-interface-ra..............................................................................669
hello-interval................................................................................................670
version ........................................................................................................671
ip arp inspection validate............................................................................ 672
14 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 15

Preface
● Document conventions....................................................................................................15
● Brocade resources.......................................................................................................... 17
● Contacting Brocade Technical Support...........................................................................17
● Document feedback........................................................................................................ 18
Document conventions
The document conventions describe text formatting conventions, command syntax conventions, and
important notice formats used in Brocade technical documentation.
Text formatting conventions
Text formatting conventions such as boldface, italic, or Courier font may be used in the flow of the text
to highlight specific words or phrases.
Format
bold text
italic text
Courier font
Description
Identifies command names
Identifies keywords and operands
Identifies the names of user-manipulated GUI elements
Identifies text to enter at the GUI
Identifies emphasis
Identifies variables and modifiers
Identifies paths and Internet addresses
Identifies document titles
Identifies CLI output
Identifies command syntax examples
Command syntax conventions
Bold and italic text identify command syntax components. Delimiters and operators define groupings of
parameters and their logical relationships.
Convention
bold text Identifies command names, keywords, and command options.
italic text Identifies a variable.
Description
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 15
53-1003087-04
Page 16
Notes, cautions, and warnings
Convention Description
value In Fibre Channel products, a fixed value provided as input to a command
[ ] Syntax components displayed within square brackets are optional.
option is printed in plain text, for example, --show WWN.
Default responses to system prompts are enclosed in square brackets.
{ x | y | z } A choice of required parameters is enclosed in curly brackets separated by
x | y A vertical bar separates mutually exclusive elements.
< > Nonprinting characters, for example, passwords, are enclosed in angle
...
\
vertical bars. You must select one of the options.
In Fibre Channel products, square brackets may be used instead for this
purpose.
brackets.
Repeat the previous element, for example, member[member...].
Indicates a “soft” line break in command examples. If a backslash separates
two lines of a command input, enter the entire command at the prompt without
the backslash.
Notes, cautions, and warnings
Notes, cautions, and warning statements may be used in this document. They are listed in the order of
increasing severity of potential hazards.
NOTE
A Note provides a tip, guidance, or advice, emphasizes important information, or provides a reference
to related information.
ATTENTION
An Attention statement indicates a stronger note, for example, to alert you when traffic might be
interrupted or the device might reboot.
CAUTION
A Caution statement alerts you to situations that can be potentially hazardous to you or cause
damage to hardware, firmware, software, or data.
DANGER
A Danger statement indicates conditions or situations that can be potentially lethal or
extremely hazardous to you. Safety labels are also attached directly to products to warn of
these conditions or situations.
16 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 17
Brocade resources
Visit the Brocade website to locate related documentation for your product and additional Brocade
resources.
You can download additional publications supporting your product at www.brocade.com. Select the
Brocade Products tab to locate your product, then click the Brocade product name or image to open the
individual product page. The user manuals are available in the resources module at the bottom of the
page under the Documentation category.
To get up-to-the-minute information on Brocade products and resources, go to MyBrocade. You can
register at no cost to obtain a user ID and password.
Release notes are available on MyBrocade under Product Downloads.
White papers, online demonstrations, and data sheets are available through the Brocade website.
Contacting Brocade Technical Support
Brocade resources
As a Brocade customer, you can contact Brocade Technical Support 24x7 online, by telephone, or by email. Brocade OEM customers contact their OEM/Solutions provider.
Brocade customers
For product support information and the latest information on contacting the Technical Assistance
Center, go to http://www.brocade.com/services-support/index.html.
If you have purchased Brocade product support directly from Brocade, use one of the following methods
to contact the Brocade Technical Assistance Center 24x7.
Online Telephone E-mail
Preferred method of contact for nonurgent issues:
• My Cases through MyBrocade
• Software downloads and licensing
tools
• Knowledge Base
Required for Sev 1-Critical and Sev
2-High issues:
• Continental US: 1-800-752-8061
• Europe, Middle East, Africa, and
Asia Pacific: +800-AT FIBREE
(+800 28 34 27 33)
• For areas unable to access toll
free number: +1-408-333-6061
• Toll-free numbers are available in
many countries.
support@brocade.com
Please include:
• Problem summary
• Serial number
• Installation details
• Environment description
Brocade OEM customers
If you have purchased Brocade product support from a Brocade OEM/Solution Provider, contact your
OEM/Solution Provider for all of your product support needs.
• OEM/Solution Providers are trained and certified by Brocade to support Brocade® products.
• Brocade provides backline support for issues that cannot be resolved by the OEM/Solution Provider.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 17
53-1003087-04
Page 18

Document feedback
• Brocade Supplemental Support augments your existing OEM support contract, providing direct
access to Brocade expertise. For more information, contact Brocade or your OEM.
• For questions regarding service levels and response times, contact your OEM/Solution Provider.
Document feedback
To send feedback and report errors in the documentation you can use the feedback form posted with
the document or you can e-mail the documentation team.
Quality is our first concern at Brocade and we have made every effort to ensure the accuracy and
completeness of this document. However, if you find an error or an omission, or you think that a topic
needs further development, we want to hear from you. You can provide feedback in two ways:
• Through the online feedback form in the HTML documents posted on www.brocade.com.
• By sending your feedback to documentation@brocade.com.
Provide the publication title, part number, and as much detail as possible, including the topic heading
and page number if applicable, as well as your suggestions for improvement.
18 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 19

About This Document
● Supported Hardware....................................................................................................... 19
● What’s new in this document.......................................................................................... 19
● How command information is presented in this guide.....................................................20
Supported Hardware
This guide supports the following product families from Brocade:
• FastIron X Series devices (chassis models):
‐ FastIron SX 800
‐ FastIron SX 1600
• Brocade FCX Series (FCX) Stackable Switch
• Brocade ICX™ 6610 (ICX 6610) Stackable Switch
• Brocade ICX 6430 Series (ICX 6430)
• Brocade ICX 6450 Series (ICX 6450)
• Brocade ICX 6650 Series (ICX 6650)
• Brocade ICX 7750 Series (ICX 7750)
For information about the specific models and modules supported in a product family, refer to the
hardware installation guide for that product family.
NOTE
The Brocade ICX 6430-C switch supports the same feature set as the Brocade ICX 6430 switch unless
otherwise noted.
NOTE
The Brocade ICX 6450-C12-PD switch supports the same feature set as the Brocade ICX 6450 switch
unless otherwise noted.
What’s new in this document
This document includes a description of the new information added to this guide for version 08.0.10d of
the latest FastIron software release.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
19
Page 20

How command information is presented in this guide
Summary of Enhancements in FastIron release 08.0.10dTABLE 1
Feature Description Location
DHCPv6 Relay Agent Prefix
Delegation Notification
DHCPv6 Relay Agent Prefix
Delegation Notification allows a
DHCPv6 server to dynamically
delegate IPv6 prefixes to a DHCPv6
client using the DHCPv6 Prefix
Delegation (PD) option.
Described in IPv6 Configuration on
FastIron X Series, FCX, and ICX
Series Switches on page 163
How command information is presented in this guide
For all new content, command syntax and parameters are documented in a separate command
reference section at the end of the publication.
In an effort to provide consistent command line interface (CLI) documentation for all products, Brocade
is in the process of preparing standalone Command References for the IP platforms. This process
involves separating command syntax and parameter descriptions from configuration tasks. Until this
process is completed, command information is presented in two ways:
• For all new content included in this guide, the CLI is documented in separate command pages. The
new command pages follow a standard format to present syntax, parameters, usage guidelines,
examples, and command history. Command pages are compiled in alphabetical order in a separate
command reference chapter at the end of the publication.
• Legacy content continues to include command syntax and parameter descriptions in the chapters
where the features are documented.
If you do not find command syntax information embedded in a configuration task, refer to the
command reference section at the end of this publication for information on CLI syntax and usage.
20 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 21

IP Configuration
● Supported IP features..................................................................................................... 21
● Basic IP configuration..................................................................................................... 22
● IP configuration overview................................................................................................ 23
● Basic IP parameters and defaults - Layer 3 Switches.....................................................30
● Basic IP parameters and defaults - Layer 2 Switches.....................................................35
● Configuring IP parameters - Layer 3 switches................................................................ 38
● Configuring IP parameters - Layer 2 Switches..............................................................105
● IPv4 point-to-point GRE tunnels ...................................................................................111
● Displaying IP configuration information and statistics................................................... 132
● Disabling IP checksum check....................................................................................... 151
Supported IP features
Lists IP configuration features supported on FastIron devices.
IP features are supported with the full Layer 3 software image except where explicitly noted.
Feature ICX 6430 ICX 6450 FCX ICX 6610 ICX 6650 FSX 800
FSX 1600
ARP Packet Validation 08.0.10a 08.0.10a 08.0.10a 08.0.10a 08.0.10a 08.0.10a 08.0.10a
BootP/DHCP relay No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Specifying which IP address will be
included in a DHCP/BootP reply packet
DHCP Server 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
DHCP Client-Based Auto-Configuration 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
DHCP Client-Based Flash image Autoupdate
DHCP assist 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Equal Cost Multi-Path (ECMP) load
sharing
IP helper No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Single source address for the following
packet types: Telnet, TFTP, Syslog,
NTP, TACACS TACACS+, RADIUS,
SSH, SNMP
IPv4 point-to-point GRE IP tunnels No 08.0.01
No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
No No No No 08.0.01 08.0.01 08.0.10
1
08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
ICX 7750
1
In a mixed stack only.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 21
53-1003087-04
Page 22

Basic IP configuration
Feature ICX 6430 ICX 6450 FCX ICX 6610 ICX 6650 FSX 800
FSX 1600
GRE tunnel counters enhancement No No 08.0.01 No 08.0.01 No 08.0.10
Routing for directly connected IP
subnets
Virtual Interfaces: Up to 512 virtual
interfaces
31-bit subnet mask on point-to-point
networks
Address Resolution Protocol (ARP) No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Reverse Address Resolution Protocol
(RARP)
IP follow No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Proxy ARP No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Local proxy ARP No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Learning Gratuitous ARP No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Jumbo frames: Up to 10,200 bytes 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
IP MTU (individual port setting) No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Path MTU discovery No No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
No 08.0.01
No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
2
08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
ICX 7750
ICMP Router Discovery Protocol (IRDP) No 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
Domain Name Server (DNS) resolver 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.01 08.0.10
IP checksum check disable No No No No 08.0.01 08.0.01 08.0.10
NOTE
References to chassis-based Layer 3 switches apply to the FSX 800 and FSX 1600.
NOTE
The terms Layer 3 Switch and router are used interchangeably in this chapter and mean the same.
Basic IP configuration
IP is enabled by default. Basic configuration consists of adding IP addresses for Layer 3 switches,
enabling a route exchange protocol, such as the Routing Information Protocol (RIP).
If you are configuring a Layer 3 switch, refer to Configuring IP addresses on page 38 to add IP
addresses, then enable and configure the route exchange protocols, as described in other chapters of
this guide.
2
Up to 255 virtual interfaces.
22 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 23
If you are configuring a Layer 2 switch, refer to Configuring the management IP address and specifying
the default gateway on page 105 to add an IP address for management access through the network
and to specify the default gateway.
The rest of this chapter describes IP and how to configure it in more detail. Use the information in this
chapter if you need to change some of the IP parameters from their default values or you want to view
configuration information or statistics.
IP configuration overview
Brocade Layer 2 switches and Layer 3 switches support Internet Protocol version 4 (IPv4) and IPv6. IP
support on BrocadeLayer 2 switches consists of basic services to support management access and
access to a default gateway.
Full Layer 3 support
IP support on Brocade full Layer 3 switches includes all of the following, in addition to a highly
configurable implementation of basic IP services including Address Resolution Protocol (ARP), ICMP
Router Discovery Protocol (IRDP), and Reverse ARP (RARP):
• Route exchange protocols:
‐ Routing Information Protocol (RIP)
‐ Open Shortest Path First (OSPF)
‐ Border Gateway Protocol version 4 (BGP4)
• Multicast protocols:
‐ Internet Group Membership Protocol (IGMP)
‐ Protocol Independent Multicast Dense (PIM-DM)
‐ Protocol Independent Multicast Sparse (PIM-SM)
• Router redundancy protocols:
‐ Virtual Router Redundancy Protocol Extended (VRRP-E)
‐ Virtual Router Redundancy Protocol (VRRP)
IP configuration overview
IP interfaces
NOTE
This section describes IPv4 addresses. For information about IPv6 addresses on FastIron X Series
devices, refer to "IPv6 addressing overview" section in the FastIron Ethernet Switch Administration
Guide .
Brocade Layer 3 switches and Layer 2 switches allow you to configure IP addresses. On Layer 3
switches, IP addresses are associated with individual interfaces. On Layer 2 switches, a single IP
address serves as the management access address for the entire device.
All Brocade Layer 3 switches and Layer 2 switches support configuration and display of IP addresses in
classical subnet format (for example: 192.168.1.1 255.255.255.0) and Classless Interdomain Routing
(CIDR) format (for example: 192.168.1.1/24). You can use either format when configuring IP address
information. IP addresses are displayed in classical subnet format by default but you can change the
display format to CIDR. Refer to Changing the network mask display to prefix format on page 132.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 23
53-1003087-04
Page 24

Layer 3 switches
Layer 3 switches
Brocade Layer 3 switches allow you to configure IP addresses on the following types of interfaces:
• Ethernet ports
• Virtual routing interfaces (used by VLANs to route among one another)
• Loopback interfaces
• GRE tunnels
Each IP address on a Layer 3 switch must be in a different subnet. You can have only one interface
that is in a given subnet. For example, you can configure IP addresses 192.168.1.1/24 and
192.168.2.1/24 on the same Layer 3 switch, but you cannot configure 192.168.1.1/24 and
192.168.1.2/24 on the same Layer 3 switch.
You can configure multiple IP addresses on the same interface.
The number of IP addresses you can configure on an individual interface depends on the Layer 3
switch model. To display the maximum number of IP addresses and other system parameters you can
configure on a Layer 3 switch, refer to "Displaying and modifying system parameter default settings"
section in the FastIron Ethernet Switch Platform and Layer 2 Switching Configuration Guide .
You can use any of the IP addresses you configure on the Layer 3 switch for Telnet or SNMP access.
Layer 2 switches
You can configure an IP address on a BrocadeLayer 2 switch for management access to the Layer 2
switch. An IP address is required for Telnet access and SNMP access.
You also can specify the default gateway for forwarding traffic to other subnets.
24 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 25
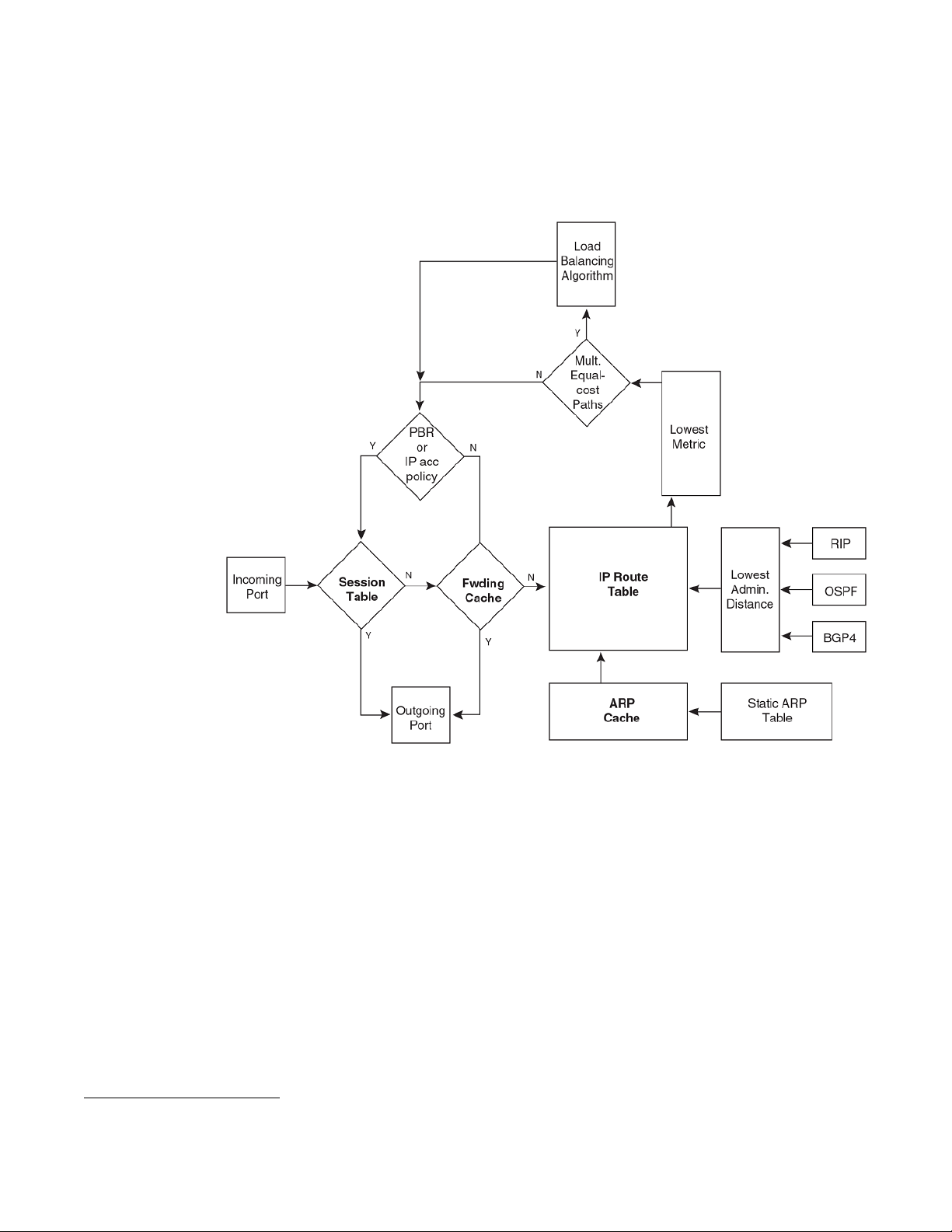
IP packet flow through a Layer 3 switch
FIGURE 1 IP Packet flow through a Brocade Layer 3 switch
IP packet flow through a Layer 3 switch
1. When the Layer 3 switch receives an IP packet, the Layer 3 switch checks for filters on the receiving
interface.3 If a deny filter on the interface denies the packet, the Layer 3 switch discards the packet
and performs no further processing, except generating a Syslog entry and SNMP message, if logging
is enabled for the filter.
2. If the packet is not denied at the incoming interface, the Layer 3 switch looks in the session table for
an entry that has the same source IP address and TCP or UDP port as the packet. If the session
table contains a matching entry, the Layer 3 switch immediately forwards the packet, by addressing it
to the destination IP address and TCP or UDP port listed in the session table entry and sending the
packet to a queue on the outgoing ports listed in the session table. The Layer 3 switch selects the
queue based on the Quality of Service (QoS) level associated with the session table entry.
3. If the session table does not contain an entry that matches the packet source address and TCP or
UDP port, the Layer 3 switch looks in the IP forwarding cache for an entry that matches the packet
destination IP address. If the forwarding cache contains a matching entry, the Layer 3 switch
forwards the packet to the IP address in the entry. The Layer 3 switch sends the packet to a queue
on the outgoing ports listed in the forwarding cache. The Layer 3 switch selects the queue based on
the Quality of Service (QoS) level associated with the forwarding cache entry.
4. If the IP forwarding cache does not have an entry for the packet, the Layer 3 switch checks the IP
route table for a route to the packet destination. If the IP route table has a route, the Layer 3 switch
3
The filter can be an Access Control List (ACL) or an IP access policy.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 25
53-1003087-04
Page 26

ARP cache and static ARP table
makes an entry in the session table or the forwarding cache, and sends the route to a queue on the
outgoing ports:
• ‐ If the running-config contains an IP access policy for the packet, the software makes an
‐ If the running-config does not contain an IP access policy for the packet, the software
The following sections describe the IP tables and caches:
• ARP cache and static ARP table
• IP route table
• IP forwarding cache
• Layer 4 session table
The software enables you to display these tables. You also can change the capacity of the tables
on an individual basis if needed by changing the memory allocation for the table.
ARP cache and static ARP table
entry in the session table. The Layer 3 switch uses the new session table entry to
forward subsequent packets from the same source to the same destination.
creates a new entry in the forwarding cache. The Layer 3 switch uses the new cache
entry to forward subsequent packets to the same destination.
The ARP cache contains entries that map IP addresses to MAC addresses. Generally, the entries are
for devices that are directly attached to the Layer 3 switch.
An exception is an ARP entry for an interface-based static IP route that goes to a destination that is
one or more router hops away. For this type of entry, the MAC address is either the destination device
MAC address or the MAC address of the router interface that answered an ARP request on behalf of
the device, using proxy ARP.
ARP cache
The ARP cache can contain dynamic (learned) entries and static (user-configured) entries. The
software places a dynamic entry in the ARP cache when the Layer 3 switch learns a device MAC
address from an ARP request or ARP reply from the device.
The software can learn an entry when the Layer 2 switch or Layer 3 switch receives an ARP request
from another IP forwarding device or an ARP reply. Here is an example of a dynamic entry:
IP Address MAC Address Type Age Port
1 10.95.6.102 0000.00fc.ea21 Dynamic 0 6
Each entry contains the destination device IP address and MAC address.
Static ARP table
In addition to the ARP cache, Layer 3 switches have a static ARP table. Entries in the static ARP table
are user-configured. You can add entries to the static ARP table regardless of whether or not the
device the entry is for is connected to the Layer 3 switch.
NOTE
Layer 3 switches have a static ARP table. Layer 2 switches do not.
The software places an entry from the static ARP table into the ARP cache when the entry interface
comes up.
26 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 27
IP route table
Here is an example of a static ARP entry.
Index IP Address MAC Address Port
1 10.95.6.111 0000.003b.d210 1/1
Each entry lists the information you specified when you created the entry.
IP route table
The IP route table contains paths to IP destinations.
NOTE
Layer 2 switches do not have an IP route table. A Layer 2 switch sends all packets addressed to
another subnet to the default gateway, which you specify when you configure the basic IP information
on the Layer 2 switch.
The IP route table can receive the paths from the following sources:
• A directly-connected destination, which means there are no router hops to the destination
• A static IP route, which is a user-configured route
• A route learned through RIP
• A route learned through OSPF
• A route learned through BGP4
The IP route table contains the best path to a destination:
• When the software receives paths from more than one of the sources listed above, the software
compares the administrative distance of each path and selects the path with the lowest
administrative distance. The administrative distance is a protocol-independent value from 1 through
255.
• When the software receives two or more best paths from the same source and the paths have the
same metric (cost), the software can load share traffic among the paths based on destination host or
network address (based on the configuration and the Layer 3 switch model).
Here is an example of an entry in the IP route table.
Destination NetMask Gateway Port Cost Type
10.1.0.0 255.255.0.0
10.1.1.2 1/1 2 R
Each IP route table entry contains the destination IP address and subnet mask and the IP address of
the next-hop router interface to the destination. Each entry also indicates the port attached to the
destination or the next-hop to the destination, the route IP metric (cost), and the type. The type indicates
how the IP route table received the route.
To increase the size of the IP route table for learned and static routes, refer to the section "Displaying
and modifying system parameter default settings" in the FastIron Ethernet Switch Platform and Layer 2
Switching Configuration Guide:
• For learned routes, modify theip-route parameter.
• For static routes, modify the ip-static-route parameter.
IP forwarding cache
The IP forwarding cache provides a fast-path mechanism for forwarding IP packets. The cache contains
entries for IP destinations. When a Brocade Layer 3 switch has completed processing and addressing
for a packet and is ready to forward the packet, the device checks the IP forwarding cache for an entry
to the packet destination:
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 27
53-1003087-04
Page 28
Layer 4 session table
• If the cache contains an entry with the destination IP address, the device uses the information in the
entry to forward the packet out the ports listed in the entry. The destination IP address is the
address of the packet final destination. The port numbers are the ports through which the
destination can be reached.
• If the cache does not contain an entry and the traffic does not qualify for an entry in the session
table instead, the software can create an entry in the forwarding cache.
Each entry in the IP forwarding cache has an age timer. If the entry remains unused for ten minutes,
the software removes the entry. The age timer is not configurable.
Here is an example of an entry in the IP forwarding cache.
IP Address Next Hop MAC Type Port Vlan Pri
1 192.168.1.11 DIRECT 0000.0000.0000 PU n/a 0
Each IP forwarding cache entry contains the IP address of the destination, and the IP address and
MAC address of the next-hop router interface to the destination. If the destination is actually an
interface configured on the Layer 3 switch itself, as shown here, then next-hop information indicates
this. The port through which the destination is reached is also listed, as well as the VLAN and Layer 4
QoS priority associated with the destination if applicable.
NOTE
You cannot add static entries to the IP forwarding cache, although you can increase the number of
entries the cache can contain. Refer to the section "Displaying and modifying system parameter
default settings" in the FastIron Ethernet Switch Platform and Layer 2 Switching Configuration Guide .
Layer 4 session table
The Layer 4 session provides a fast path for forwarding packets. A session is an entry that contains
complete Layer 3 and Layer 4 information for a flow of traffic. Layer 3 information includes the source
and destination IP addresses. Layer 4 information includes the source and destination TCP and UDP
ports. For comparison, the IP forwarding cache contains the Layer 3 destination address but does not
contain the other source and destination address information of a Layer 4 session table entry.
The Layer 2 switch or Layer 3 switch selects the session table instead of the IP forwarding table for
fast-path forwarding for the following features:
• Layer 4 Quality-of-Service (QoS) policies
• IP access policies
To increase the size of the session table, refer to the section "Displaying and modifying system
parameter default settings" in the FastIron Ethernet Switch Platform and Layer 2 Switching
Configuration Guide . The ip-qos-session parameter controls the size of the session table.
IP route exchange protocols
Brocade Layer 3 switches support the following IP route exchange protocols:
• Routing Information Protocol (RIP)
• Open Shortest Path First (OSPF)
• Border Gateway Protocol version 4 (BGP4)
All these protocols provide routes to the IP route table. You can use one or more of these protocols, in
any combination. The protocols are disabled by default.
28 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 29

IP multicast protocols
IP multicast protocols
Brocade Layer 3 switches also support the following Internet Group Membership Protocol (IGMP) based
IP multicast protocols:
• Protocol Independent Multicast - Dense mode (PIM-DM)
• Protocol Independent Multicast - Sparse mode (PIM-SM)
For configuration information, refer to chapter "IP Multicast Protocols" in the FastIron Ethernet Switch IP
Multicast Configuration Guide .
NOTE
Brocade Layer 3 switches support IGMP and can forward IP multicast packets. Refer to the "IP
Multicast Traffic Reduction" chapter in the FastIron Ethernet Switch IP Multicast Configuration Guide .
IP interface redundancy protocols
You can configure a Brocade Layer 3 switch to back up an IP interface configured on another Brocade
Layer 3 switch. If the link for the backed up interface becomes unavailable, the other Layer 3 switch can
continue service for the interface. This feature is especially useful for providing a backup to a network
default gateway.
Brocade Layer 3 switches support the following IP interface redundancy protocols:
• Virtual Router Redundancy Protocol (VRRP) - A standard router redundancy protocol based on RFC
2338. You can use VRRP to configure Brocade Layer 3 switches and third-party routers to back up
IP interfaces on other Brocade Layer 3 switches or third-party routers.
• Virtual Router Redundancy Protocol Extended (VRRP-E) - A Brocade extension to standard VRRP
that adds additional features and overcomes limitations in standard VRRP. You can use VRRP-E
only on Brocade Layer 3 switches.
ACLs and IP access policies
Brocade Layer 3 switches provide two mechanisms for filtering IP traffic:
• Access Control Lists (ACLs)
• IP access policies
Both methods allow you to filter packets based on Layer 3 and Layer 4 source and destination
information.
ACLs also provide great flexibility by providing the input to various other filtering mechanisms such as
route maps, which are used by BGP4.
IP access policies allow you to configure QoS based on sessions (Layer 4 traffic flows).
Only one of these filtering mechanisms can be enabled on a Brocade device at a time. Brocade devices
can store forwarding information for both methods of filtering in the session table.
For configuration information, refer to the chapter "Rule-Based IP ACLs" in the FastIron Ethernet Switch
Security Configuration Guide .
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 29
53-1003087-04
Page 30
Basic IP parameters and defaults - Layer 3 Switches
Basic IP parameters and defaults - Layer 3 Switches
IP is enabled by default. The following IP-based protocols are all disabled by default:
• Routing protocols:
‐ Routing Information Protocol (RIP)
‐ Open Shortest Path First (OSPF)
‐ Border Gateway Protocol version 4 (BGP4)
• Multicast protocols:
‐ Internet Group Membership Protocol (IGMP)
‐ Protocol Independent Multicast Dense (PIM-DM)
‐ Protocol Independent Multicast Sparse (PIM-SM)
• Router redundancy protocols:
‐ Virtual Router Redundancy Protocol Extended (VRRP-E)
‐ Virtual Router Redundancy Protocol (VRRP)
When parameter changes take effect
Most IP parameters described in this chapter are dynamic. They take effect immediately, as soon as
you enter the CLI command. You can verify that a dynamic change has taken effect by displaying the
running-config. To display the running-config, enter the show running-config or write terminal
command at any CLI prompt.
To save a configuration change permanently so that the change remains in effect following a system
reset or software reload, save the change to the startup-config file:
• To save configuration changes to the startup-config file, enter the write memory command from the
Privileged EXEC level of any configuration level of the CLI.
Changes to memory allocation require you to reload the software after you save the changes to the
startup-config file. When reloading the software is required to complete a configuration change
described in this chapter, the procedure that describes the configuration change includes a step for
reloading the software.
IP global parameters - Layer 3 Switches
IP global parameters - Layer 3 Switches TABLE 2
Parameter Description Default
IP state The Internet Protocol, version 4 Enabled
NOTE
You cannot disable IP.
30 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 31

IP global parameters - Layer 3 Switches (Continued)TABLE 2
Parameter Description Default
IP Configuration
IP address and
mask notation
Router ID The value that routers use to identify themselves to other routers
Maximum
Transmission Unit
(MTU)
Format for displaying an IP address and its network mask
information. You can enable one of the following:
• Class-based format; example: 192.168.1.1 255.255.255.0
• Classless Interdomain Routing (CIDR) format; example:
192.168.1.1/24
when exchanging route information. OSPF and BGP4 use router
IDs to identify routers. RIP does not use the router ID.
The maximum length an Ethernet packet can be without being
fragmented.
Class-based
NOTE
Changing this
parameter affects the
display of IP
addresses, but you
can enter addresses in
either format
regardless of the
display setting.
The IP address
configured on the
lowest-numbered
loopback interface.
If no loopback
interface is configured,
then the lowestnumbered IP address
configured on the
device.
1500 bytes for
Ethernet II
encapsulation
1492 bytes for SNAP
encapsulation
Address Resolution
Protocol (ARP)
ARP rate limiting Lets you specify a maximum number of ARP packets the device
ARP age The amount of time the device keeps a MAC address learned
Proxy ARP An IP mechanism a router can use to answer an ARP request on
Static ARP entries An ARP entry you place in the static ARP table. Static entries do
A standard IP mechanism that routers use to learn the Media
Access Control (MAC) address of a device on the network. The
router sends the IP address of a device in the ARP request and
receives the device MAC address in an ARP reply.
will accept each second. If the device receives more ARP packets
than you specify, the device drops additional ARP packets for the
remainder of the one-second interval.
through ARP in the device ARP cache. The device resets the timer
to zero each time the ARP entry is refreshed and removes the
entry if the timer reaches the ARP age.
NOTE
You also can change the ARP age on an individual interface basis.
behalf of a host, by replying with the router own MAC address
instead of the host.
not age out.
Enabled
Disabled
Ten minutes
Disabled
No entries
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 31
53-1003087-04
Page 32

IP Configuration
IP global parameters - Layer 3 Switches (Continued)TABLE 2
Parameter Description Default
Time to Live (TTL) The maximum number of routers (hops) through which a packet
Directed broadcast
forwarding
Directed broadcast
mode
Source-routed
packet forwarding
can pass before being discarded. Each router decreases a packet
TTL by 1 before forwarding the packet. If decreasing the TTL
causes the TTL to be 0, the router drops the packet instead of
forwarding it.
A directed broadcast is a packet containing all ones (or in some
cases, all zeros) in the host portion of the destination IP address.
When a router forwards such a broadcast, it sends a copy of the
packet out each of its enabled IP interfaces.
NOTE
You also can enable or disable this parameter on an individual
interface basis.
The packet format the router treats as a directed broadcast. The
following formats can be directed broadcast:
• All ones in the host portion of the packet destination address.
• All zeroes in the host portion of the packet destination address.
A source-routed packet contains a list of IP addresses through
which the packet must pass to reach its destination.
64 hops
Disabled
All ones
NOTE
If you enable allzeroes directed
broadcasts, all-ones
directed broadcasts
remain enabled.
Enabled
Internet Control
Message Protocol
(ICMP) messages
ICMP Router
Discovery Protocol
(IRDP)
Reverse ARP
(RARP)
The Brocade Layer 3 Switch can send the following types of ICMP
messages:
• Echo messages (ping messages)
• Destination Unreachable messages
An IP protocol a router can use to advertise the IP addresses of its
router interfaces to directly attached hosts. You can enable or
disable the protocol, and change the following protocol
parameters:
• Forwarding method (broadcast or multicast)
• Hold time
• Maximum advertisement interval
• Minimum advertisement interval
• Router preference level
NOTE
You also can enable or disable IRDP and configure the
parameters on an individual interface basis.
An IP mechanism a host can use to request an IP address from a
directly attached router when the host boots.
Enabled
Disabled
Enabled
32 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 33

IP global parameters - Layer 3 Switches (Continued)TABLE 2
Parameter Description Default
IP Configuration
Static RARP entries An IP address you place in the RARP table for RARP requests
Maximum BootP
relay hops
Domain name for
Domain Name
Server (DNS)
resolver
DNS default
gateway addresses
IP load sharing A Brocade feature that enables the router to balance traffic to a
from hosts.
NOTE
You must enter the RARP entries manually. The Layer 3 Switch
does not have a mechanism for learning or dynamically generating
RARP entries.
The maximum number of hops away a BootP server can be
located from a router and still be used by the router clients for
network booting.
A domain name (example: brocade.router.com) you can use in
place of an IP address for certain operations such as IP pings,
trace routes, and Telnet management connections to the router.
A list of gateways attached to the router through which clients
attached to the router can reach DNSs.
specific destination across multiple equal-cost paths.
IP load sharing uses a hashing algorithm based on the source IP
address, destination IP address, protocol field in the IP header,
TCP, and UDP information.
No entries
Four
None configured
None configured
Enabled
NOTE
Load sharing is sometimes called Equal Cost Multi Path (ECMP).
Maximum IP load
sharing paths
Origination of
default routes
Default network
route
Static route An IP route you place in the IP route table. No entries
The maximum number of equal-cost paths across which the Layer
3 Switch is allowed to distribute traffic.
You can enable a router to originate default routes for the following
route exchange protocols, on an individual protocol basis:
• OSPF
• BGP4
The router uses the default network route if the IP route table does
not contain a route to the destination and also does not contain an
explicit default route (0.0.0.0 0.0.0.0 or 0.0.0.0/0).
Four
Disabled
None configured
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 33
53-1003087-04
Page 34

IP interface parameters - Layer 3 Switches
IP global parameters - Layer 3 Switches (Continued)TABLE 2
Parameter Description Default
Source interface The IP address the router uses as the source address for Telnet,
RADIUS, or TACACS/TACACS+ packets originated by the router.
The router can select the source address based on either of the
following:
• The lowest-numbered IP address on the interface the packet is
sent on.
• The lowest-numbered IP address on a specific interface. The
address is used as the source for all packets of the specified
type regardless of interface the packet is sent on.
The lowest-numbered
IP address on the
interface the packet is
sent on.
IP interface parameters - Layer 3 Switches
IP interface parameters - Layer 3 switches TABLE 3
Parameter Description Default
IP state The Internet Protocol, version 4 Enabled
NOTE
You cannot disable IP.
IP address A Layer 3 network interface address
None configured
4
NOTE
Layer 2 switches have a single IP address used for
management access to the entire device. Layer 3 switches
have separate IP addresses on individual interfaces.
Encapsulation type The format of the packets in which the router encapsulates IP
Maximum
Transmission Unit
(MTU)
ARP age Locally overrides the global setting. Ten minutes
Directed broadcast
forwarding
4
Some devices have a factory default, such as 10.157.22.154, used for troubleshooting during installation. For Layer 3 Switch es, the
address is on module 1 port 1 (or 1/1).
datagrams. The encapsulation format can be one of the
following:
• Ethernet II
• SNAP
The maximum length (number of bytes) of an encapsulated IP
datagram the router can forward.
Locally overrides the global setting. Disabled
Ethernet II
1500 for Ethernet II
encapsulated packets
1492 for SNAP
encapsulated packets
34 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 35

Basic IP parameters and defaults - Layer 2 Switches
IP interface parameters - Layer 3 switches (Continued)TABLE 3
Parameter Description Default
ICMP Router
Discovery Protocol
(IRDP)
DHCP gateway
stamp
DHCP Client-Based
Auto-Configuration
DHCP Server All FastIron devices can be configured to function as DHCP
UDP broadcast
forwarding
Locally overrides the global IRDP settings. Disabled
The router can assist DHCP/BootP Discovery packets from
one subnet to reach DHCP/BootP servers on a different
subnet by placing the IP address of the router interface that
receives the request in the request packet Gateway field.
You can override the default and specify the IP address to use
for the Gateway field in the packets.
NOTE
UDP broadcast forwarding for client DHCP/BootP requests
(bootps) must be enabled (this is enabled by default) and you
must configure an IP helper address (the server IP address or
a directed broadcast to the server subnet) on the port
connected to the client.
Allows the switch to obtain IP addresses from a DHCP host
automatically, for either a specified (leased) or infinite period of
time.
servers.
The router can forward UDP broadcast packets for UDP
applications such as BootP. By forwarding the UDP
broadcasts, the router enables clients on one subnet to find
servers attached to other subnets.
NOTE
To completely enable a client UDP application request to find a
server on another subnet, you must configure an IP helper
address consisting of the server IP address or the directed
broadcast address for the subnet that contains the server. See
the next row.
The lowest-numbered IP
address on the interface
that receives the request
Enabled
Disabled
The router helps forward
broadcasts for the
following UDP
application protocols:
• bootps
• dns
• netbios-dgm
• netbios-ns
• tacacs
• tftp
• time
IP helper address The IP address of a UDP application server (such as a BootP
or DHCP server) or a directed broadcast address. IP helper
addresses allow the router to forward requests for certain UDP
applications from a client on one subnet to a server on another
subnet.
None configured
Basic IP parameters and defaults - Layer 2 Switches
IP is enabled by default. The following tables list the Layer 2 switch IP parameters, their default values,
and where to find configuration information.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 35
53-1003087-04
Page 36

IP global parameters - Layer 2 switches
NOTE
Brocade Layer 2 switches also provide IP multicast forwarding, which is enabled by default. For
information about this feature, refer to chapter "IP Multicast Traffic Reduction" in the FastIron Ethernet
Switch IP Multicast Configuration Guide.
IP global parameters - Layer 2 switches
IP global parameters - Layer 2 switches TABLE 4
Parameter Description Default
IP address and
mask notation
IP address A Layer 3 network interface address
Default gateway The IP address of a locally attached router (or a router attached to
Address Resolution
Protocol (ARP)
Format for displaying an IP address and its network mask
information. You can enable one of the following:
• Class-based format; example: 192.168.1.1 255.255.255.0
• Classless Interdomain Routing (CIDR) format; example:
192.168.1.1/24
NOTE
Layer 2 switches have a single IP address used for management
access to the entire device. Layer 3 switches have separate IP
addresses on individual interfaces.
the Layer 2 switch by bridges or other Layer 2 switches). The
Layer 2 switch and clients attached to it use the default gateway
to communicate with devices on other subnets.
A standard IP mechanism that networking devices use to learn the
Media Access Control (MAC) address of another device on the
network. The Layer 2 switch sends the IP address of a device in
the ARP request and receives the device MAC address in an ARP
reply.
Class-based
NOTE
Changing this
parameter affects the
display of IP addresses,
but you can enter
addresses in either
format regardless of the
display setting.
None configured
None configured
Enabled
NOTE
You cannot disable
ARP.
5
ARP age The amount of time the device keeps a MAC address learned
5
Some devices have a factory default, such as 10.157.22.154, used for troubleshooting during installation. For Layer 3 Switches, the
address is on port 1 (or 1/1).
36 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
through ARP in the device ARP cache. The device resets the
timer to zero each time the ARP entry is refreshed and removes
the entry if the timer reaches the ARP age.
Ten minutes
NOTE
You cannot change the
ARP age on Layer 2
switches.
53-1003087-04
Page 37

Interface IP parameters - Layer 2 switches
IP global parameters - Layer 2 switches (Continued)TABLE 4
Parameter Description Default
Time to Live (TTL) The maximum number of routers (hops) through which a packet
Domain name for
Domain Name
Server (DNS)
resolver
DNS default
gateway addresses
Source interface The IP address the Layer 2 switch uses as the source address for
DHCP gateway
stamp
can pass before being discarded. Each router decreases a packet
TTL by 1 before forwarding the packet. If decreasing the TTL
causes the TTL to be 0, the router drops the packet instead of
forwarding it.
A domain name (example: brocade.router.com) you can use in
place of an IP address for certain operations such as IP pings,
trace routes, and Telnet management connections to the router.
A list of gateways attached to the router through which clients
attached to the router can reach DNSs.
Telnet, RADIUS, or TACACS/TACACS+ packets originated by the
router. The Layer 2 switch uses its management IP address as the
source address for these packets.
The device can assist DHCP/BootP Discovery packets from one
subnet to reach DHCP/BootP servers on a different subnet by
placing the IP address of the router interface that forwards the
packet in the packet Gateway field.
You can specify up to 32 gateway lists. A gateway list contains up
to eight gateway IP addresses. You activate DHCP assistance by
associating a gateway list with a port.
When you configure multiple IP addresses in a gateway list, the
Layer 2 switch inserts the addresses into the DHCP Discovery
packets in a round robin fashion.
64 hops
None configured
None configured
The management IP
address of the Layer 2
switch.
NOTE
This parameter is not
configurable on Layer 2
switches.
None configured
DHCP ClientBased AutoConfiguration
Allows the switch to obtain IP addresses from a DHCP host
automatically, for either a specified (leased) or infinite period of
time.
Enabled
Interface IP parameters - Layer 2 switches
Interface IP parameters - Layer 2 switches TABLE 5
Parameter Description Default
DHCP gateway stamp You can configure a list of DHCP stamp addresses for a port. When the
port receives a DHCP/BootP Discovery packet from a client, the port
places the IP addresses in the gateway list into the packet Gateway field.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 37
53-1003087-04
None configured
Page 38

Configuring IP parameters - Layer 3 switches
Configuring IP parameters - Layer 3 switches
The following sections describe how to configure IP parameters. Some parameters can be configured
globally while others can be configured on individual interfaces. Some parameters can be configured
globally and overridden for individual interfaces.
Configuring IP addresses
You can configure an IP address on the following types of Layer 3 switch interfaces:
• Ethernet port
• Virtual routing interface (also called a Virtual Ethernet or "VE")
• Loopback interface
• GRE tunnels
By default, you can configure up to 24 IP addresses on each interface.
You can increase this amount to up to 128 IP subnet addresses per port by increasing the size of the
ip-subnet-port table.
Refer to the section "Displaying system parameter default values" in the FastIron Ethernet Switch
Platform and Layer 2 Switching Configuration Guide .
NOTE
Once you configure a virtual routing interface on a VLAN, you cannot configure Layer 3 interface
parameters on individual ports. Instead, you must configure the parameters on the virtual routing
interface itself.
Brocade devices support both classical IP network masks (Class A, B, and C subnet masks, and so
on) and Classless Interdomain Routing (CIDR) network prefix masks:
• To enter a classical network mask, enter the mask in IP address format. For example, enter
"10.157.22.99 255.255.255.0" for an IP address with a Class-C subnet mask.
• To enter a prefix network mask, enter a forward slash ( / ) and the number of bits in the mask
immediately after the IP address. For example, enter "10.157.22.99/24" for an IP address that has a
network mask with 24 significant bits (ones).
By default, the CLI displays network masks in classical IP address format (example: 255.255.255.0).
You can change the display to prefix format.
Assigning an IP address to an Ethernet port
To assign an IP address to port 1/1, enter the following commands.
device(config)# interface ethernet 1/1
device(config-if-1/1)# ip address 10.45.6.1 255.255.255.0
You also can enter the IP address and mask in CIDR format, as follows.
device(config-if-1/1)# ip address 10.45.6.1/24
Syntax: no ip address ip- addr ip-mask [ ospf-ignore | ospf-passive | secondary ]
or
Syntax: no ip address ip-addr/mask-bits [ ospf-ignore | ospf-passive | secondary ]
38 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 39

Assigning an IP address to a loopback interface
The ospf-ignore and ospf-passive parameters modify the Layer 3 switch defaults for adjacency
formation and interface advertisement. Use one of these parameters if you are configuring multiple IP
subnet addresses on the interface but you want to prevent OSPF from running on some of the subnets:
• ospf-passive - This option disables adjacency formation with OSPF neighbors. By default, when
OSPF is enabled on an interface, the software forms OSPF router adjacencies between each primary
IP address on the interface and the OSPF neighbor attached to the interface.
• ospf-ignore - This option disables OSPF adjacency formation and also disables advertisement of the
interface into OSPF. The subnet is completely ignored by OSPF.
NOTE
The ospf-passive option disables adjacency formation but does not disable advertisement of the
interface into OSPF. To disable advertisement in addition to disabling adjacency formation, you must
use the ospf-ignore option.
Use the secondary parameter if you have already configured an IP address within the same subnet on
the interface.
NOTE
When you configure more than one address in the same subnet, all but the first address are secondary
addresses and do not form OSPF adjacencies.
NOTE
All physical IP interfaces on BrocadeFastIron Layer 3 devices share the same MAC address. For this
reason, if more than one connection is made between two devices, one of which is a BrocadeFastIron
Layer 3 device, Brocade recommends the use of virtual interfaces. It is not recommended to connect
two or more physical IP interfaces between two routers.
Assigning an IP address to a loopback interface
Loopback interfaces are always up, regardless of the states of physical interfaces. They can add
stability to the network because they are not subject to route flap problems that can occur due to
unstable links between a Layer 3 switch and other devices. You can configure up to eight loopback
interfaces on a Chassis Layer 3 switch devices. You can configure up to four loopback interfaces on a
Compact Layer 3 switch.
You can add up to 24 IP addresses to each loopback interface.
NOTE
If you configure the BrocadeLayer 3 switch to use a loopback interface to communicate with a BGP4
neighbor, you also must configure a loopback interface on the neighbor and configure the neighbor to
use that loopback interface to communicate with the BrocadeLayer 3 switch. Refer to Assigning an IP
address to a loopback interface.
To add a loopback interface, enter commands such as those shown in the following example.
device(config-bgp-router)# exit
device(config)# interface loopback 1
device(config-lbif-1)# ip address 10.0.0.1/24
Syntax: interface loopback num
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 39
53-1003087-04
Page 40

Assigning an IP address to a virtual interface
The num parameter specifies the virtual interface number. You can specify from 1 to the maximum
number of virtual interfaces supported on the device. To display the maximum number of virtual
interfaces supported on the device, enter the show default values command. The maximum is listed
in the System Parameters section, in the Current column of the virtual-interface row.
Assigning an IP address to a virtual interface
A virtual interface is a logical port associated with a Layer 3 Virtual LAN (VLAN) configured on a Layer
3 switch. You can configure routing parameters on the virtual interface to enable the Layer 3 switch to
route protocol traffic from one Layer 3 VLAN to the other, without using an external router.
You can configure IP routing interface parameters on a virtual interface. This section describes how to
configure an IP address on a virtual interface. Other sections in this chapter that describe how to
configure interface parameters also apply to virtual interfaces.
NOTE
The Layer 3 switch uses the lowest MAC address on the device (the MAC address of port 1 or 1/1) as
the MAC address for all ports within all virtual interfaces you configure on the device.
To add a virtual interface to a VLAN and configure an IP address on the interface, enter commands
such as the following.
6
device(config)# vlan 2 name IP-Subnet_10.1.2.0/24
device(config-vlan-2)# untag ethernet 1 to 4
device(config-vlan-2)# router-interface ve1
device(config-vlan-2)# interface ve1
device(config-vif-1)# ip address 10.1.2.1/24
The first two commands in this example create a Layer 3 protocol-based VLAN name "IPSubnet_10.1.2.0/24" and add a range of untagged ports to the VLAN. The router-interface command
creates virtual interface 1 as the routing interface for the VLAN.
Syntax: router-interface venum
The num variable specifies the virtual interface number. You can enter a number from 1 through 4095.
When configuring virtual routing interfaces on a device, you can specify a number from 1 through
4095. However, the total number of virtual routing interfaces that are configured must not exceed the
system-max limit of 512. For more information on the number of virtual routing interfaces supported,
refer to "Allocating memory for more VLANs or virtual routing interfaces" section in the FastIron
Ethernet Switch Platform and Layer 2 Switching Configuration Guide.
The last two commands change to the interface configuration level for the virtual interface and assign
an IP address to the interface.
Syntax: interface venum
Configuring IP follow on a virtual routing interface
IP Follow allows multiple virtual routing interfaces to share the same IP address. With this feature, one
virtual routing interface is configured with an IP address, while the other virtual routing interfaces are
configured to use that IP address, thus, they "follow" the virtual routing interface that has the IP
address. This feature is helpful in conserving IP address space.
6
The Brocade feature that allows routing between VLANs within the same device, without the need for external routers,
is called Integrated Switch Routing (ISR).
40 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 41

Deleting an IP address
Configuration limitations and feature limitations for IP Follow on a virtual routing
interface
• When configuring IP Follow, the primary virtual routing interface should not have ACL or DoS
Protection configured. It is recommended that you create a dummy virtual routing interface as the
primary and use the IP-follow virtual routing interface for the network.
• Global Policy Based Routing is not supported when IP Follow is configured.
• IPv6 is not supported with IP Follow.
• FastIron devices support IP Follow with OSPF and VRRP protocols only.
Configuration syntax for IP Follow on a virtual routing interface
Configure IP Follow by entering commands such as the following.
device(config)# vlan 2 name IP-Subnet_10.1.2.0/24
device(config-vlan-2)# untag ethernet 1 to 4
device(config-vlan-2)# router-interface ve1
device(config-vlan-2)# interface ve 1
device(config-vif-1)# ip address 10.10.2.1/24
device(config-vif-1)# interface ve 2
device(config-vif-2)# ip follow ve 1
device(config-vif-2)# interface ve 3
device(config-vif-3)# ip follow ve 1
Syntax:[no] ip follow venumber
For number, enter the ID of the virtual routing interface.
Use the no form of the command to disable the configuration.
Virtual routing interface 2 and 3 do not have their own IP subnet addresses, but are sharing the IP
address of virtual routing interface 1.
Deleting an IP address
To delete an IP address, enter the no ip address command.
device(config-if-e1000-1)# no ip address 10.1.2.1
This command deletes IP address 10.1.2.1. You do not need to enter the subnet mask.
To delete all IP addresses from an interface, enter the no ip address * command.
device(config-if-e1000-1)# no ip address *
Syntax: [no] ip address ip-addr | *
Configuring 31-bit subnet masks on point-to-point networks
NOTE
31-bit subnet masks are supported on FSX, FCX, ICX 6610, and ICX 7750 devices running the full
Layer 3 image.
To conserve IPv4 address space, a 31-bit subnet mask can be assigned to point-to-point networks.
Support for an IPv4 address with a 31-bit subnet mask is described in RFC 3021.
With IPv4, four IP addresses with a 30-bit subnet mask are allocated on point-to-point networks. In
contrast, a 31-bit subnet mask uses only two IP addresses: all zero bits and all one bits in the host
portion of the IP address. The two IP addresses are interpreted as host addresses, and do not require
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 41
53-1003087-04
Page 42

Configuring an IPv4 address with a 31-bit subnet mask
broadcast support because any packet that is transmitted by one host is always received by the other
host at the receiving end. Therefore, directed broadcast on a point-to-point interface is eliminated.
IP-directed broadcast CLI configuration at the global level, or the per interface level, is not applicable
on interfaces configured with a 31-bit subnet mask IP address.
When the 31-bit subnet mask address is configured on a point-to-point link, using network addresses
for broadcast purposes is not allowed. For example, in an IPV4 broadcast scheme, the following
subnets can be configured:
• 10.10.10.1 - Subnet for directed broadcast: {Network-number , -1}
• 10.10.10.0 - Subnet for network address: {Network-number , 0}
In a point-to-point link with a 31-bit subnet mask, the previous two addresses are interpreted as host
addresses and packets are not rebroadcast.
Configuring an IPv4 address with a 31-bit subnet mask
To configure an IPv4 address with a 31-bit subnet mask, enter the following commands.
You can configure an IPv4 address with a 31-bit subnet mask on any interface (for example, Ethernet,
loopback, VE, or tunnel interfaces).
device(config)# interface ethernet 1/1/5
device(config-if-e1000-1/5)# ip address 10.9.9.9 255.255.255.254
You can also enter the IP address and mask in the Classless Inter-domain Routing (CIDR) format, as
follows.
device(config-if-e1000-1/1/5)# ip address 10.9.9.9/31
Syntax: [no] ip address ip-address ip-mask
Syntax: [no] ip address ip-address/subnet-mask-bits
The ip-address variable specifies the host address. The ip-mask variable specifies the IP network
mask. The subnet -mask-bits variable specifies the network prefix mask.
To disable configuration for an IPv4 address with a 31-bit subnet mask on any interface, use the no
form of the command.
You cannot configure a secondary IPv4 address with a 31-bit subnet mask on any interface. The
following error message is displayed when a secondary IPv4 address with a 31-bit subnet mask is
configured.
Error: Cannot assign /31 subnet address as secondary
Configuration example
FIGURE 2 Configured 31- bit and 24-bit subnet masks
Router A is connected to Router B as a point-to-point link with 10.1.1.0/31 subnet. There are only two
available addresses in this subnet, 10.1.1.0 on Router A and 10.1.1.1 on Router B,
42 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 43

Displaying information for a 31-bit subnet mask
Routers B and C are connected by a regular 24-bit subnet. Router C can either be a switch with many
hosts belonging to the 10.2.2.2/24 subnet connected to it, or it can be a router.
Router A
RouterA(config)# interface ethernet 1/1/1
RouterA(config-if-e1000-1/1/1)# ip address 10.1.1.0/31
Router B
RouterB(config)# interface ethernet 1/1/1
RouterB(config-if-e1000-1/1/1)# ip address 10.1.1.1/31
RouterB(config-if-e1000-1/1/1)# exit
RouterB(config# interface ethernet 1/3/1
RouterB(config-if-e1000-1/3/1)# ip address 10.2.2.1/24
Router C
RouterC(config# interface ethernet 1/3/1
RouterC(config-if-e1000-1/3/1)# ip address 10.2.2.2/24
Displaying information for a 31-bit subnet mask
Use the following commands to display information for the 31-bit subnet mask:
• show run interface
• show ip route
• show ip cache
Configuring DNS resolver
The Domain Name System (DNS) resolver is a feature in a Layer 2 or Layer 3 switch that sends and
receives queries to and from the DNS server on behalf of a client.
You can create a list of domain names that can be used to resolve host names. This list can have more
than one domain name. When a client performs a DNS query, all hosts within the domains in the list can
be recognized and queries can be sent to any domain on the list.
After you define a domain name, the Brocade device automatically appends the appropriate domain to
a host and forwards it to the DNS servers for resolution.
For example, if the domain "ds.company.com" is defined on a Layer 2 or Layer 3 switch and you want to
initiate a ping to "mary", you must reference only the host name instead of the host name and its
domain name. For example, you could enter the following command to initiate the ping.
Brocade:> ping mary
The Layer 2 or Layer 3 switch qualifies the host name by appending a domain name (for example,
mary.ds1.company.com). This qualified name is sent to the DNS server for resolution. If there are four
DNS servers configured, it is sent to the first DNS server. If the host name is not resolved, it is sent to
the second DNS server. If a match is found, a response is sent back to the client with the host IP
address. If no match is found, an "unknown host" message is returned.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 43
53-1003087-04
Page 44

Defining DNS server addresses
FIGURE 3 DNS resolution with one domain name
Defining DNS server addresses
You can configure the Brocade device to recognize up to four DNS servers. The first entry serves as
the primary default address. If a query to the primary address fails to be resolved after three attempts,
the next DNS address is queried (also up to three times). This process continues for each defined
DNS address until the query is resolved. The order in which the default DNS addresses are polled is
the same as the order in which you enter them.
To define DNS servers, enter the ip dns server-address command.
device(config)# ip dns server-address 10.157.22.199 10.96.7.15 10.95.7.25 10.98.7.15
Syntax: [no] ip dns server-address ip-addr [ ip-addr ] [ ip-addr ] [ ip-addr ]
In this example, the first IP address entered becomes the primary DNS address and all others are
secondary addresses. Because IP address 10.98.7.15 is the last address listed, it is also the last
address consulted to resolve a query.
Defining a domain list
If you want to use more than one domain name to resolve host names, you can create a list of domain
names. For example, enter the commands such as the following.
device(config)# ip dns domain-list company.com
device(config)# ip dns domain-list ds.company.com
device(config)# ip dns domain-list hw_company.com
device(config)# ip dns domain-list qa_company.com
device(config)#
The domain names are tried in the order you enter them
Syntax: no ip dns domain-list domain-name
44 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 45

Using a DNS name to initiate a trace route
Using a DNS name to initiate a trace route
Suppose you want to trace the route from a BrocadeLayer 3 switch to a remote server identified as
NYC02 on domain newyork.com. Because the NYC02@ds1.newyork.com domain is already defined on
the Layer 3 switch, you need to enter only the host name, NYC02, as noted in the following example.
device# traceroute nyc02
Syntax: traceroute [ vrf vrf ] host-ip-addr [ maxttlvalue ] [ minttl value ] [ numeric ] [ timeout value ] [
source-ip ip add r]
The only required parameter is the IP address of the host at the other end of the route.
After you enter the command, a message indicating that the DNS query is in process and the current
gateway address (IP address of the domain name server) being queried appear on the screen. When
traceroute fails, an error occurs as shown in the last two lines in the given example.
Type Control-c to abort
Sending DNS Query to 10.157.22.199
Tracing Route to IP node 10.157.22.80
To ABORT Trace Route, Please use stop-traceroute command.
Traced route to target IP node 10.157.22.80:
IP Address Round Trip Time1 Round Trip Time2
10.95.6.30 93 msec 121 msec
Trace route to target IP node 10.157.22.80 failed.
IP: Errno(9) No response from target or intermediate node
NOTE
In the previous example, 10.157.22.199 is the IP address of the domain name server (default DNS
gateway address), and 10.157.22.80 represents the IP address of the NYC02 host.
Configuring packet parameters
You can configure the following packet parameters on Layer 3 switches. These parameters control how
the Layer 3 switch sends IP packets to other devices on an Ethernet network. The Layer 3 switch
always places IP packets into Ethernet packets to forward them on an Ethernet port.
• Encapsulation type - The format for the Layer 2 packets within which the Layer 3 switch sends IP
packets.
• Maximum Transmission Unit (MTU) - The maximum length of IP packet that a Layer 2 packet can
contain. IP packets that are longer than the MTU are fragmented and sent in multiple Layer 2
packets. You can change the MTU globally or an individual ports:
‐ Global MTU - The default MTU value depends on the encapsulation type on a port and is
1500 bytes for Ethernet II encapsulation and 1492 bytes for SNAP encapsulation.
‐ Port MTU - A port default MTU depends on the encapsulation type enabled on the port.
Changing the encapsulation type
The Layer 3 switch encapsulates IP packets into Layer 2 packets, to send the IP packets on the
network. (A Layer 2 packet is also called a MAC layer packet or an Ethernet frame.) The source
address of a Layer 2 packet is the MAC address of the Layer 3 switch interface sending the packet. The
destination address can be one of the following:
• The MAC address of the IP packet destination. In this case, the destination device is directly
connected to the Layer 3 switch.
• The MAC address of the next-hop gateway toward the packet destination.
• An Ethernet broadcast address.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 45
53-1003087-04
Page 46

Changing the MTU
The entire IP packet, including the source and destination address and other control information and
the data, is placed in the data portion of the Layer 2 packet. Typically, an Ethernet network uses one
of two different formats of Layer 2 packet:
• Ethernet II
• Ethernet SNAP (also called IEEE 802.3)
The control portions of these packets differ slightly. All IP devices on an Ethernet network must use
the same format. BrocadeLayer 3 switches use Ethernet II by default. You can change the IP
encapsulation to Ethernet SNAP on individual ports if needed.
NOTE
All devices connected to the Layer 3 switch port must use the same encapsulation type.
To change the IP encapsulation type on interface 5 to Ethernet SNAP, enter the following commands.
device(config)# interface ethernet 5
device(config-if-e1000-5)# ip encapsulation snap
Syntax: ip encapsulation{ snap | ethernet_ii }
Changing the MTU
The Maximum Transmission Unit (MTU) is the maximum length of IP packet that a Layer 2 packet can
contain. IP packets that are longer than the MTU are fragmented and sent in multiple Layer 2 packets.
You can change the MTU globally or on individual ports.
The default MTU is 1500 bytes for Ethernet II packets and 1492 for Ethernet SNAP packets.
MTU enhancements
Brocade devices contain the following enhancements to jumbo packet support:
• Hardware forwarding of Layer 3 jumbo packets - Layer 3 IP unicast jumbo packets received on a
port that supports the frame MTU size and forwarded to another port that also supports the frame
MTU size are forwarded in hardware. Previous releases support hardware forwarding of Layer 2
jumbo frames only.
• ICMP unreachable message if a frame is too large to be forwarded - If a jumbo packet has the Do
not Fragment (DF) bit set, and the outbound interface does not support the packet MTU size, the
Brocade device sends an ICMP unreachable message to the device that sent the packet.
NOTE
These enhancements apply only to transit traffic forwarded through the Brocade device.
Configuration considerations for increasing the MTU
• The MTU command is applicable to VEs and physical IP interfaces. It applies to traffic routed
between networks.
• For ICX 7750, the IPv4 and IPv6 MTU values are the same. Modifying one also changes the value
of the other.
• For ICX 7750, the minimum IPv4 and IPv6 MTU values for both physical and virtual interfaces are
1280.
46 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 47

IP Configuration
• You cannot use this command to set Layer 2 maximum frame sizes per interface. The global jumbo
command causes all interfaces to accept Layer 2 frames.
• When you increase the MTU size of a port, the increase uses system resources. Increase the MTU
size only on the ports that need it. For example, if you have one port connected to a server that uses
jumbo frames and two other ports connected to clients that can support the jumbo frames, increase
the MTU only on those three ports. Leave the MTU size on the other ports at the default value (1500
bytes). Globally increase the MTU size only if needed.
Forwarding traffic to a port with a smaller MTU size
NOTE
This feature is not supported on FastIron X Seriess.
In order to forward traffic from a port with 1500 MTU configured to a port that has a smaller MTU (for
example, 750) size, you must apply the mtu-exceed forward global command. To remove this setting,
enter the mtu-exceed hard-drop command. MTU-exceed hard-drop is the default state of the router.
Syntax: mtu-exceed { forward | hard-drop }
• forward - fragments and forwards a packet from a port with a larger MTU to a port with a smaller
MTU.
• hard-drop - resets to default, removes the forward function.
Globally changing the Maximum Transmission Unit
The Maximum Transmission Unit (MTU) is the maximum size an IP packet can be when encapsulated
in a Layer 2 packet. If an IP packet is larger than the MTU allowed by the Layer 2 packet, the Layer 3
switch fragments the IP packet into multiple parts that will fit into the Layer 2 packets, and sends the
parts of the fragmented IP packet separately, in different Layer 2 packets. The device that receives the
multiple fragments of the IP packet reassembles the fragments into the original packet.
You can increase the MTU size to accommodate jumbo packet sizes up to 10,200 bytes.
To globally enable jumbo support on all ports of a FastIron device, enter commands such as the
following.
device(config)# jumbo
device(config)# write memory
device(config)# end
device# reload
Syntax: [no] jumbo
NOTE
You must save the configuration change and then reload the software to enable jumbo support.
Changing the MTU on an individual port
By default, the maximum Ethernet MTU sizes are as follows:
• 1500 bytes - The maximum for Ethernet II encapsulation
• 1492 bytes - The maximum for SNAP encapsulation
When jumbo mode is enabled, the maximum Ethernet MTU sizes are as follows:
• For ICX 6610 devices
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 47
53-1003087-04
Page 48

Changing the router ID
‐ 10,200 bytes - The maximum for Ethernet II encapsulation (Default MTU: 9216)
‐ 10,174 bytes - The maximum for SNAP encapsulation (Default MTU: 9216)
• For ICX 6630, ICX 6630-C12, and ICX 6450 devices
‐ 10,178 bytes - The maximum for Ethernet II encapsulation (Default MTU: 9216)
‐ 10,174 bytes - The maximum for SNAP encapsulation (Default MTU: 9216)
• For other devices
‐ 10,218 bytes - The maximum for Ethernet II encapsulation (Default MTU: 9216)
‐ 10,214 bytes - The maximum for SNAP encapsulation (Default MTU: 9216)
NOTE
If you set the MTU of a port to a value lower than the global MTU and from 576 through 1499, the port
fragments the packets. However, if the port MTU is exactly 1500 and this is larger than the global
MTU, the port drops the packets. For ICX 7750, the minimum IPv4 and IPv6 MTU values for both
physical and virtual interfaces are 1280.
NOTE
You must save the configuration change and then reload the software to enable jumbo support.
To change the MTU for interface 1/5 to 1000, enter the following commands.
device(config)# interface ethernet 1/5
device(config-if-1/5)# ip mtu 1000
device(config-if-1/5)# write memory
device(config-if-1/5)# end
device# reload
Syntax: [no] ip mtu num
The num parameter specifies the MTU. Ethernet II packets can hold IP packets from 576 through 1500
bytes long. If jumbo mode is enabled, Ethernet II packets can hold IP packets up to 10,218 bytes long.
Ethernet SNAP packets can hold IP packets from 576 through 1492 bytes long. If jumbo mode is
enabled, SNAP packets can hold IP packets up to 10,214 bytes long. The default MTU for Ethernet II
packets is 1500. The default MTU for SNAP packets is 1492.
Path MTU discovery (RFC 1191) support
FastIron X Series devices support the path MTU discovery method described in RFC 1191. When the
Brocade device receives an IP packet that has its Do not Fragment (DF) bit set, and the packet size is
greater than the MTU value of the outbound interface, then the Brocade device returns an ICMP
Destination Unreachable message to the source of the packet, with the Code indicating "fragmentation
needed and DF set". The ICMP Destination Unreachable message includes the MTU of the outbound
interface. The source host can use this information to help determine the maximum MTU of a path to a
destination.
RFC 1191 is supported on all interfaces.
Changing the router ID
In most configurations, a Layer 3 switch has multiple IP addresses, usually configured on different
interfaces. As a result, a Layer 3 switch identity to other devices varies depending on the interface to
which the other device is attached. Some routing protocols, including Open Shortest Path First (OSPF)
and Border Gateway Protocol version 4 (BGP4), identify a Layer 3 switch by just one of the IP
48 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 49

Specifying a single source interface for specified packet types
addresses configured on the Layer 3 switch, regardless of the interfaces that connect the Layer 3
switches. This IP address is the router ID.
NOTE
Routing Information Protocol (RIP) does not use the router ID.
NOTE
If you change the router ID, all current BGP4 sessions are cleared.
By default, the router ID on a BrocadeLayer 3 switch is one of the following:
• If the router has loopback interfaces, the default router ID is the IP address configured on the lowest
numbered loopback interface configured on the Layer 3 switch. For example, if you configure
loopback interfaces 1, 2, and 3 as follows, the default router ID is 10.9.9.9/24:
‐ Loopback interface 1, 10.9.9.9/24
‐ Loopback interface 2, 10.4.4.4/24
‐ Loopback interface 3, 10.1.1.1/24
• If the device does not have any loopback interfaces, the default router ID is the lowest numbered IP
interface configured on the device.
If you prefer, you can explicitly set the router ID to any valid IP address. The IP address cannot be in
use on another device in the network.
NOTE
Brocade Layer 3 switches use the same router ID for both OSPF and BGP4. If the router is already
configured for OSPF, you may want to use the router ID that is already in use on the router rather than
set a new one. To display the router ID, enter the show ip command at any CLI level.
To change the router ID, enter a command such as the following.
device(config)# ip router-id 10.157.22.26
Syntax: ip router-id ip-addr
The ip-addr parameter can be any valid, unique IP address.
NOTE
You can specify an IP address used for an interface on the BrocadeLayer 3 switch, but do not specify
an IP address in use by another device.
Specifying a single source interface for specified packet types
NOTE
This feature is supported on Brocade FCX Series switches, FastIron X Series Layer 3 switches, ICX
6610,ICX 6430, and ICX 6450 switches.
When the Layer 3 switch originates a packet of one of the following types, the source address of the
packet is the lowest-numbered IP address on the interface that sends the packet:
• Telnet
• TACACS/TACACS+
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 49
53-1003087-04
Page 50

IP Configuration
• TFTP
• RADIUS
• Syslog
• SNTP
• SSH
• SNMP traps
You can configure the Layer 3 switch to always use the lowest-numbered IP address on a specific
Ethernet, loopback, or virtual interface as the source addresses for these packets. When configured,
the Layer 3 switch uses the same IP address as the source for all packets of the specified type,
regardless of the ports that actually sends the packets.
Identifying a single source IP address for specified packets provides the following benefits:
• If your server is configured to accept packets only from specific IP addresses, you can use this
feature to simplify configuration of the server by configuring the Brocade device to always send the
packets from the same link or source address.
• If you specify a loopback interface as the single source for specified packets, servers can receive
the packets regardless of the states of individual links. Thus, if a link to the server becomes
unavailable but the client or server can be reached through another link, the client or server still
receives the packets, and the packets still have the source IP address of the loopback interface.
The software contains separate CLI commands for specifying the source interface for specific packets.
You can configure a source interface for one or more of these types of packets separately.
The following sections show the syntax for specifying a single source IP address for specific packet
types.
Telnet packets
To specify the lowest-numbered IP address configured on a virtual interface as the device source for
all Telnet packets, enter commands such as the following.
device(config)# interface loopback 2
device(config-lbif-2)# ip address 10.0.0.2/24
device(config-lbif-2)# exit
device(config)# ip telnet source-interface loopback 2
The commands in this example configure loopback interface 2, assign IP address 10.0.0.2/24 to the
interface, then designate the interface as the source for all Telnet packets from the Layer 3 switch.
The following commands configure an IP interface on an Ethernet port and designate the address port
as the source for all Telnet packets from the Layer 3 switch.
device(config)# interface ethernet 1/4
device(config-if-1/4)# ip address 10.157.22.110/24
device(configif-1/4)# exit
device(config)# ip telnet source-interface ethernet 1/4
Syntax: [no] ip telnet source-interface ethernet { [slotnum/]portnum | loopback num | venum }
The slotnum variable is required on chassis devices.
The portnum variable is a valid port number.
The num variable is a loopback interface or virtual interface number.
50 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 51

IP Configuration
TACACS/TACACS+ packets
To specify the lowest-numbered IP address configured on a virtual interface as the device source for all
TACACS/TACACS+ packets, enter commands such as the following.
device(config)# interface ve 1
device(config-vif-1)# ip address 10.0.0.3/24
device(config-vif-1)# exit
device(config)# ip tacacs source-interface ve 1
The commands in this example configure virtual interface 1, assign IP address 10.0.0.3/24 to the
interface, then designate the interface as the source for all TACACS/TACACS+ packets from the Layer
3 switch.
Syntax: [no] ip tacacs source-interface ethernet { [slotnum/]portnum | loopback num | venum }
The slotnumvariable is required on chassis devices.
The portnum variable is a valid port number.
The num variable is a loopback interface or virtual interface number.
RADIUS packets
To specify the lowest-numbered IP address configured on a virtual interface as the device source for all
RADIUS packets, enter commands such as the following.
device(config)# interface ve 1
device(config-vif-1)# ip address 10.0.0.3/24
device(config-vif-1)# exit
device(config)# ip radius source-interface ve 1
The commands in this example configure virtual interface 1, assign IP address 10.0.0.3/24 to the
interface, then designate the interface as the source for all RADIUS packets from the Layer 3 switch.
Syntax: [no] ip radius source-interface ethernet { [slotnum/]portnum | loopback num | venum }
The slotnum variable is required on chassis devices.
The portnum variable is a valid port number.
The num variable is a loopback interface or virtual interface number.
TFTP packets
To specify the lowest-numbered IP address configured on a virtual interface as the device source for all
TFTP packets, enter commands such as the following.
device(config)# interface ve 1
device(config-vif-1)# ip address 10.0.0.3/24
device(config-vif-1)# exit
device(config)# ip tftp source-interface ve 1
The commands in this example configure virtual interface 1, assign IP address 10.0.0.3/24 to the
interface, then designate the interface's address as the source address for all TFTP packets.
Syntax: [no] ip tftp source-interface ethernet { [slotnum/]portnum | loopback num | venum }
The slotnumvariable is required on chassis devices.
The portnum variable is a valid port number.
The num variable is a loopback interface or virtual interface number.
The default is the lowest-numbered IP address configured on the port through which the packet is sent.
The address therefore changes, by default, depending on the port.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 51
53-1003087-04
Page 52

IP Configuration
Syslog packets
To specify the lowest-numbered IP address configured on a virtual interface as the device source for
all Syslog packets, enter commands such as the following.
device(config)# interface ve 1
device(config-vif-1)# ip address 10.0.0.4/24
device(config-vif-1)# exit
device(config)# ip syslog source-interface ve 1
The commands in this example configure virtual interface 1, assign IP address 10.0.0.4/24 to the
interface, then designate the interface's address as the source address for all Syslog packets.
Syntax: [no] ip syslog source-interface ethernet { [slotnum/]portnum | loopback num | venum }
The slotnum variable is required on chassis devices.
The portnum variable is a valid port number.
The num variable is a loopback interface or virtual interface number.
The default is the lowest-numbered IP or IPv6 address configured on the port through which the
packet is sent. The address therefore changes, by default, depending on the port.
SNTP packets
To specify the lowest-numbered IP address configured on a virtual interface as the device source for
all SNTP packets, enter commands such as the following.
device(config)# interface ve 1
device(config-vif-1)# ip address 10.0.0.5/24
device(config-vif-1)# exit
device(config)# ip sntp source-interface ve 1
The commands in this example configure virtual interface 1, assign IP address 10.0.0.5/24 to the
interface, then designate the interface's address as the source address for all SNTP packets.
Syntax: no ip sntp source-interface ethernet { [slotnum/]portnum | loopbacknum | venum }
The slotnum variable is required on chassis devices.
The portnum variable is a valid port number.
The num variable is a loopback interface or virtual interface number.
The default is the lowest-numbered IP or IPv6 address configured on the port through which the
packet is sent. The address therefore changes, by default, depending on the port.
SSH packets
NOTE
When you specify a single SSH source, you can use only that source address to establish SSH
management sessions with the Brocade device.
To specify the numerically lowest IP address configured on a loopback interface as the device source
for all SSH packets, enter commands such as a the following.
device(config)# interface loopback 2
device(config-lbif-2)# ip address 10.0.0.2/24
device(config-lbif-2)# exit
device(config)# ip ssh source-interface loopback 2
52 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 53

ARP parameter configuration
The commands in this example configure loopback interface 2, assign IP address 10.0.0.2/24 to the
interface, then designate the interface as the source for all SSH packets from the Layer 3 switch.
Syntax: no ip ssh source-interface ethernet { [slotnum/]portnum | loopback num | venum }
The slotnum parameter is required on chassis devices.
The portnum parameter is a valid port number.
The num parameter is a loopback interface or virtual interface number.
SNMP packets
To specify a loopback interface as the SNMP single source trap, enter commands such as the following.
device(config)# interface loopback 1
device(config-lbif-1)# ip address 10.0.0.1/24
device(config-lbif-1)# exit
device(config)# snmp-server trap-source loopback 1
The commands in this example configure loopback interface 1, assign IP address 10.00.1/24 to the
loopback interface, then designate the interface as the SNMP trap source for this device. Regardless of
the port the Brocade device uses to send traps to the receiver, the traps always arrive from the same
source IP address.
Syntax: no snmp-server trap-source ethernet { [slotnum/]portnum | loopback num | venum }
The slotnum variable is required on chassis devices.
The portnum variable is a valid port number.
The num variable is a loopback interface or virtual interface number.
ARP parameter configuration
Address Resolution Protocol (ARP) is a standard IP protocol that enables an IP Layer 3 switch to obtain
the MAC address of another device interface when the Layer 3 switch knows the IP address of the
interface. ARP is enabled by default and cannot be disabled.
NOTE
Brocade Layer 2 switches also support ARP. However, the configuration options described later in this
section apply only to Layer 3 switches, not to Layer 2 switches.
How ARP works
A Layer 3 switch needs to know a destination MAC address when forwarding traffic, because the Layer
3 switch encapsulates the IP packet in a Layer 2 packet (MAC layer packet) and sends the Layer 2
packet to a MAC interface on a device directly attached to the Layer 3 switch. The device can be the
packet final destination or the next-hop router toward the destination.
The Layer 3 switch encapsulates IP packets in Layer 2 packets regardless of whether the ultimate
destination is locally attached or is multiple router hops away. Since the Layer 3 switch IP route table
and IP forwarding cache contain IP address information but not MAC address information, the Layer 3
switch cannot forward IP packets based solely on the information in the route table or forwarding cache.
The Layer 3 switch needs to know the MAC address that corresponds with the IP address of either the
packet locally attached destination or the next-hop router that leads to the destination.
For example, to forward a packet whose destination is multiple router hops away, the Layer 3 switch
must send the packet to the next-hop router toward its destination, or to a default route or default
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 53
53-1003087-04
Page 54

Rate limiting ARP packets
network route if the IP route table does not contain a route to the packet destination. In each case, the
Layer 3 switch must encapsulate the packet and address it to the MAC address of a locally attached
device, the next-hop router toward the IP packet destination.
To obtain the MAC address required for forwarding a datagram, the Layer 3 switch does the following:
• First, the Layer 3 switch looks in the ARP cache (not the static ARP table) for an entry that lists the
To ensure the accuracy of the ARP cache, each dynamic entry has its own age timer. The timer is
reset to zero each time the Layer 3 switch receives an ARP reply or ARP request containing the IP
address and MAC address of the entry. If a dynamic entry reaches its maximum allowable age, the
entry times out and the software removes the entry from the table. Static entries do not age out and
can be removed only by you.
• If the ARP cache does not contain an entry for the destination IP address, the Layer 3 switch
ARP requests contain the IP address and MAC address of the sender, so all devices that receive the
request learn the MAC address and IP address of the sender and can update their own ARP caches
accordingly.
MAC address for the IP address. The ARP cache maps IP addresses to MAC addresses. The
cache also lists the port attached to the device and, if the entry is dynamic, the age of the entry. A
dynamic ARP entry enters the cache when the Layer 3 switch receives an ARP reply or receives an
ARP request (which contains the sender IP address and MAC address). A static entry enters the
ARP cache from the static ARP table (which is a separate table) when the interface for the entry
comes up.
broadcasts an ARP request out all its IP interfaces. The ARP request contains the IP address of the
destination. If the device with the IP address is directly attached to the Layer 3 switch, the device
sends an ARP response containing its MAC address. The response is a unicast packet addressed
directly to the Layer 3 switch. The Layer 3 switch places the information from the ARP response into
the ARP cache.
NOTE
The ARP request broadcast is a MAC broadcast, which means the broadcast goes only to devices that
are directly attached to the Layer 3 switch. A MAC broadcast is not routed to other networks. However,
some routers, including BrocadeLayer 3 switches, can be configured to reply to ARP requests from
one network on behalf of devices on another network.
NOTE
If the router receives an ARP request packet that it is unable to deliver to the final destination because
of the ARP timeout and no ARP response is received (the Layer 3 switch knows of no route to the
destination address), the router sends an ICMP Host Unreachable message to the source.
Rate limiting ARP packets
You can limit the number of ARP packets the Brocade device accepts during each second. By default,
the software does not limit the number of ARP packets the device can receive. Since the device sends
ARP packets to the CPU for processing, if a device in a busy network receives a high number of ARP
packets in a short period of time, some CPU processing might be deferred while the CPU processes
the ARP packets.
To prevent the CPU from becoming flooded by ARP packets in a busy network, you can restrict the
number of ARP packets the device will accept each second. When you configure an ARP rate limit,
the device accepts up to the maximum number of packets you specify, but drops additional ARP
packets received during the one-second interval. When a new one-second interval starts, the counter
restarts at zero, so the device again accepts up to the maximum number of ARP packets you
specified, but drops additional packets received within the interval.
54 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 55

Changing the ARP aging period
To limit the number of ARP packets the device will accept each second, enter the rate-limit-arp
command at the global CONFIG level of the CLI.
device(config)# rate-limit-arp 100
This command configures the device to accept up to 100 ARP packets each second. If the device
receives more than 100 ARP packets during a one-second interval, the device drops the additional ARP
packets during the remainder of that one-second interval.
Syntax:[no] rate-limit-arp num
The num parameter specifies the number of ARP packets and can be from 0 through 100. If you specify
0, the device will not accept any ARP packets.
NOTE
If you want to change a previously configured the ARP rate limiting policy, you must remove the
previously configured policy using the no rate-limit-arp command before entering the new policy.
Changing the ARP aging period
When the Layer 3 switch places an entry in the ARP cache, the Layer 3 switch also starts an aging
timer for the entry. The aging timer ensures that the ARP cache does not retain learned entries that are
no longer valid. An entry can become invalid when the device with the MAC address of the entry is no
longer on the network.
The ARP age affects dynamic (learned) entries only, not static entries. The default ARP age is ten
minutes. On Layer 3 switches, you can change the ARP age to a value from 0 through 240 minutes.
You cannot change the ARP age on Layer 2 switches. If you set the ARP age to zero, aging is disabled
and entries do not age out.
To globally change the ARP aging parameter to 20 minutes, enter the ip arp-age command.
device(config)# ip arp-age 20
Syntax: ip arp-age num
The num parameter specifies the number of minutes and can be from 0 through 240. The default is 10.
If you specify 0, aging is disabled.
To override the globally configured IP ARP age on an individual interface, enter a command such as the
following at the interface configuration level.
device(config-if-e1000-1/1)# ip arp-age 30
Syntax: [no] ip arp-age num
The num parameter specifies the number of minutes and can be from 0 through 240. The default is the
globally configured value, which is 10 minutes by default. If you specify 0, aging is disabled.
Enabling proxy ARP
Proxy ARP allows a Layer 3 switch to answer ARP requests from devices on one network on behalf of
devices in another network. Since ARP requests are MAC-layer broadcasts, they reach only the devices
that are directly connected to the sender of the ARP request. Thus, ARP requests do not cross routers.
For example, if Proxy ARP is enabled on a Layer 3 switch connected to two subnets, 10.10.10.0/24 and
10.20.20.0/24, the Layer 3 switch can respond to an ARP request from 10.10.10.69 for the MAC
address of the device with IP address 10.20.20.69. In standard ARP, a request from a device in the
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 55
53-1003087-04
Page 56

Creating static ARP entries
10.10.10.0/24 subnet cannot reach a device in the 10.20.20.0 subnet if the subnets are on different
network cables, and thus is not answered.
NOTE
An ARP request from one subnet can reach another subnet when both subnets are on the same
physical segment (Ethernet cable), because MAC-layer broadcasts reach all the devices on the
segment.
Proxy ARP is disabled by default on BrocadeLayer 3 switches. This feature is not supported on
BrocadeLayer 2 switches.
You can enable proxy ARP at the Interface level, as well as at the Global CONFIG level, of the CLI.
NOTE
Configuring proxy ARP at the Interface level overrides the global configuration.
Enabling proxy ARP globally
To enable IP proxy ARP on a global basis, enter the ip proxy-arp command.
device(config)# ip proxy-arp
To again disable IP proxy ARP on a global basis, enter the no ip proxy-arp command.
device(config)# no ip proxy-arp
Syntax: [no] ip proxy-arp
Enabling IP ARP on an interface
NOTE
Configuring proxy ARP at the Interface level overrides the global configuration.
To enable IP proxy ARP on an interface, enter the following commands.
device(config)# interface ethernet 5
device(config-if-e1000-5)# ip proxy-arp enable
To again disable IP proxy ARP on an interface, enter the following command.
device(config)# interface ethernet 5
device(config-if-e1000-5)# ip proxy-arp disable
Syntax: [no] ip proxy-arp { enable | disable }
NOTE
By default, gratuitous ARP is disabled for local proxy ARP.
Creating static ARP entries
Brocade Layer 3 switches have a static ARP table, in addition to the regular ARP cache. The static
ARP table contains entries that you configure.
56 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 57

IP Configuration
Static entries are useful in cases where you want to pre-configure an entry for a device that is not
connected to the Layer 3 switch, or you want to prevent a particular entry from aging out. The software
removes a dynamic entry from the ARP cache if the ARP aging interval expires before the entry is
refreshed. Static entries do not age out, regardless of whether the Brocade device receives an ARP
request from the device that has the entry address.
NOTE
You cannot create static ARP entries on a Layer 2 switch.
The maximum number of static ARP entries you can configure depends on the software version running
on the device.
To create a static ARP entry, enter a command such as the following.
device(config)# arp 1 10.53.4.2 0000.0054.2348 ethernet 1/2
Syntax: arp num ip-addr mac-addr ethernet port
The num parameter specifies the entry number. You can specify a number from 1 up to the maximum
number of static entries allowed on the device.
The ip-addr parameter specifies the IP address of the device that has the MAC address of the entry.
The mac-addr parameter specifies the MAC address of the entry.
Changing the maximum number of entries the static ARP table can hold
NOTE
The basic procedure for changing the static ARP table size is the same as the procedure for changing
other configurable cache or table sizes. Refer to the section "Displaying system parameter default
values" in the FastIron Ethernet Switch Platform and Layer 2 Switching Configuration Guide .
To increase the maximum number of static ARP table entries you can configure on a BrocadeLayer 3
switch, enter commands such as the following at the global CONFIG level of the CLI.
device(config)# system-max ip-static-arp 1000
device(config)# write memory
device(config)# end
device# reload
NOTE
You must save the configuration to the startup-config file and reload the software after changing the
static ARP table size to place the change into effect.
Syntax: system-max ip-static-arp num
The num parameter indicates the maximum number of static ARP entries and can be within one of
these ranges, depending on the software version running on the device.
Static ARP entry support TABLE 6
Default maximum Configurable minimum Configurable maximum
FastIron X Series and Brocade FCX Series devices
512 512 6000
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 57
53-1003087-04
Page 58

ARP Packet Validation
Static ARP entry support (Continued)TABLE 6
Default maximum Configurable minimum Configurable maximum
ICX 6430 and ICX 6450 devices
256 64 1024
ICX 6610
512 512 6000
Enabling learning gratuitous ARP
Learning gratuitous ARP enables Brocade Layer 3 devices to learn ARP entries from incoming
gratuitous ARP packets from the hosts which are directly connected. This help achieve faster
convergence for the hosts when they are ready to send traffic.
A new ARP entry is created when a gratuitous ARP packet is received. If the ARP is already existing,
it will be updated with the new content.
To enable IP ARP learn gratuitous ARP, enter commands such as the following:
Brocade (config)# ip arp learn-gratuitous-arp
Brocade (config)# no ip arp learn-gratuitous-arp
Syntax: [no] ip arp learn-gratuitous-arp
The no form of the command disables learn gratuitous ARP from the device.
Use show run command to see whether ARP is enabled or disabled. Similarly, use show arp
command to see the newly learnt ARP entries.
ARP Packet Validation
Validates ARP Packets to avoid traffic interruption or loss.
To avoid traffic interruption or loss, ARP Packet Validation allows the user to detect and drop ARP
packets that do not pass the ARP validation process. ARP Packet Validation is disabled by default and
can be enabled at the global configuration level. This functionality can be configured for the destination
MAC address, the IP address and the source MAC address or with a combination of these
parameters. The Ethernet header contains the destination MAC address and source MAC address,
while the ARP packet contains the sender hardware address and target hardware address.
Follow these steps to perform checks on the incoming ARP Packets.
1. Enter the global configuration mode.
2. Run the ip arp inspection validate [dst-mac | ip | src-mac] command to perform a check on any
incoming ARP packets. Use one of the following parameters to run the validation check.
• dst-mac
The destination MAC address in the Ethernet header must be the same as the target hardware
address in the ARP body. This validation is performed for the ARP response packet. When the
destination MAC address validation is enabled, the packets with different MAC addresses are
classified as invalid and are dropped.
• src-mac
58 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 59

Ingress ARP packet priority
The source MAC address in the Ethernet header and the sender hardware address in the ARP
body must be the same. This validation is performed for the ARP request and response packets.
When the source MAC validation is enabled, the packets with different MAC addresses are
classified as invalid and are dropped.
• ip
Each ARP packet has a sender IP address and target IP address. The target IP address cannot
be invalid or an unexpected IP address in the ARP response packet. The sender IP address
cannot be an invalid or an unexpected IP address in the ARP request and response packets.
Addresses include 0.0.0.0, 255.255.255.255, and all IP multicast addresses. When the IP address
validation is enabled, the packets with invalid and unexpected IP addresses are classified as
invalid and are dropped.
The following example shows validating ARP Packets for the destination MAC
address.
device(config)# configuration terminal
device(config)#ip arp inspection validate dst-mac
Ingress ARP packet priority
You can configure the priority of the ingress ARP packets to an optimum value that depends on your
network configuration and traffic volume. Ingress ARP packets have a default priority value of 4. At the
default priority value, ingress ARP packets may get dropped because of high traffic volume or non-ARP
packets with higher priority values. This can cause devices to become unreachable. If the ingress ARP
packets have higher priority values than the default priority value, a high volume of ARP traffic may lead
to drops in control traffic. This may cause traffic loops in the network.
NOTE
You cannot change the priority of the ingress ARP packets on the management port.
Configuring the priority of ingress ARP packets
To configure the priority of ingress ARP packets, use the arp-internal-priority priority-value
command in global configuration mode.
The following example shows the priority of ingress ARP packets set to level 7.
Brocade(config)# arp-internal-priority 7
Configuring forwarding parameters
The following configurable parameters control the forwarding behavior of BrocadeLayer 3 switches:
• Time-To-Live (TTL) threshold
• Forwarding of directed broadcasts
• Forwarding of source-routed packets
• Ones-based and zero-based broadcasts
All these parameters are global and thus affect all IP interfaces configured on the Layer 3 switch.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 59
53-1003087-04
Page 60

Changing the TTL threshold
Changing the TTL threshold
The time to live (TTL) threshold prevents routing loops by specifying the maximum number of router
hops an IP packet originated by the Layer 3 switch can travel through. Each device capable of
forwarding IP that receives the packet decrements (decreases) the packet TTL by one. If a device
receives a packet with a TTL of 1 and reduces the TTL to zero, the device drops the packet.
The default value for the TTL threshold is 64. You can change the TTL threshold to a value from 1
through 255.
To modify the TTL threshold to 25, enter the ip ttl command.
device(config)# ip ttl 25
Syntax: ip ttl ttl-threshold
Enabling forwarding of directed broadcasts
A directed broadcast is an IP broadcast to all devices within a single directly-attached network or
subnet. A net-directed broadcast goes to all devices on a given network. A subnet-directed broadcast
goes to all devices within a given subnet.
NOTE
A less common type, the all-subnets broadcast, goes to all directly-attached subnets. Forwarding for
this broadcast type also is supported, but most networks use IP multicasting instead of all-subnet
broadcasting.
Forwarding for all types of IP directed broadcasts is disabled by default. You can enable forwarding for
all types if needed. You cannot enable forwarding for specific broadcast types.
To enable forwarding of IP directed broadcasts, enter the ip directed-broadcast command.
device(config)# ip directed-broadcast
Syntax: [no] ip directed-broadcast
Brocade software makes the forwarding decision based on the router's knowledge of the destination
network prefix. Routers cannot determine that a message is unicast or directed broadcast apart from
the destination network prefix. The decision to forward or not forward the message is by definition only
possible in the last hop router.
To disable the directed broadcasts, enter the no ip directed-broadcast command in the CONFIG
mode.
device(config)# no ip directed-broadcast
To enable directed broadcasts on an individual interface instead of globally for all interfaces, enter
commands such as the following.
device(config)# interface ethernet 1/1
device(config-if-1/1)# ip directed-broadcast
Syntax: [no] ip directed-broadcast
60 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 61

Disabling forwarding of IP source-routed packets
Disabling forwarding of IP source-routed packets
A source-routed packet specifies the exact router path for the packet. The packet specifies the path by
listing the IP addresses of the router interfaces through which the packet must pass on its way to the
destination. The Layer 3 switch supports both types of IP source routing:
• Strict source routing - requires the packet to pass through only the listed routers. If the Layer 3 switch
receives a strict source-routed packet but cannot reach the next hop interface specified by the
packet, the Layer 3 switch discards the packet and sends an ICMP Source-Route-Failure message to
the sender.
NOTE
The Layer 3 switch allows you to disable sending of the Source-Route-Failure messages.
• Loose source routing - requires that the packet pass through all of the listed routers but also allows
the packet to travel through other routers, which are not listed in the packet.
The Layer 3 switch forwards both types of source-routed packets by default. To disable the feature, use
either of the following methods. You cannot enable or disable strict or loose source routing separately.
To disable forwarding of IP source-routed packets, enter the no ip source-route command.
device(config)# no ip source-route
Syntax: [no] ip source-route
To re-enable forwarding of source-routed packets, enter the ip source-route command.
device(config)# ip source-route
Enabling support for zero-based IP subnet broadcasts
By default, the Layer 3 switch treats IP packets with all ones in the host portion of the address as IP
broadcast packets. For example, the Layer 3 switch treats IP packets with 10.157.22.255/24 as the
destination IP address as IP broadcast packets and forwards the packets to all IP hosts within the
10.157.22.x subnet (except the host that sent the broadcast packet to the Layer 3 switch).
Most IP hosts are configured to receive IP subnet broadcast packets with all ones in the host portion of
the address. However, some older IP hosts instead expect IP subnet broadcast packets that have all
zeros instead of all ones in the host portion of the address. To accommodate this type of host, you can
enable the Layer 3 switch to treat IP packets with all zeros in the host portion of the destination IP
address as broadcast packets.
NOTE
When you enable the Layer 3 switch for zero-based subnet broadcasts, the Layer 3 switch still treats IP
packets with all ones the host portion as IP subnet broadcasts too. Thus, the Layer 3 switch can be
configured to support all ones only (the default) or all ones and all zeroes.
NOTE
This feature applies only to IP subnet broadcasts, not to local network broadcasts. The local network
broadcast address is still expected to be all ones.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 61
53-1003087-04
Page 62

Disabling ICMP messages
To enable the Layer 3 switch for zero-based IP subnet broadcasts in addition to ones-based IP subnet
broadcasts, enter the following command.
device(config)# ip broadcast-zero
device(config)# write memory
device(config)# end
device# reload
NOTE
You must save the configuration and reload the software to place this configuration change into effect.
Syntax: [no] ip broadcast-zero
Disabling ICMP messages
Brocade devices are enabled to reply to ICMP echo messages and send ICMP Destination
Unreachable messages by default.
You can selectively disable the following types of Internet Control Message Protocol (ICMP)
messages:
• Echo messages (ping messages) - The Layer 3 switch replies to IP pings from other IP devices.
• Destination Unreachable messages - If the Layer 3 switch receives an IP packet that it cannot
deliver to its destination, the Layer 3 switch discards the packet and sends a message back to the
device that sent the packet to the Layer 3 switch. The message informs the device that the
destination cannot be reached by the Layer 3 switch.
Disabling replies to broadcast ping requests
By default, Brocade devices are enabled to respond to broadcast ICMP echo packets, which are ping
requests.
To disable response to broadcast ICMP echo packets (ping requests), enter the following command.
device(config)# no ip icmp echo broadcast-request
Syntax: [no] ip icmp echo broadcast-request
If you need to re-enable response to ping requests, enter the following command.
device(config)# ip icmp echo broadcast-request
Disabling ICMP destination unreachable messages
By default, when a Brocade device receives an IP packet that the device cannot deliver, the device
sends an ICMP Unreachable message back to the host that sent the packet. You can selectively
disable a Brocade device response to the following types of ICMP Unreachable messages:
• Administration - The packet was dropped by the Brocade device due to a filter or ACL configured
on the device.
• Fragmentation-needed - The packet has the Do not Fragment bit set in the IP Flag field, but the
Brocade device cannot forward the packet without fragmenting it.
• Host - The destination network or subnet of the packet is directly connected to the Brocade device,
but the host specified in the destination IP address of the packet is not on the network.
62 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 63

Enabling ICMP Redirect Messages
• Port - The destination host does not have the destination TCP or UDP port specified in the packet. In
this case, the host sends the ICMP Port Unreachable message to the Brocade device, which in turn
sends the message to the host that sent the packet.
• Protocol - The TCP or UDP protocol on the destination host is not running. This message is different
from the Port Unreachable message, which indicates that the protocol is running on the host but the
requested protocol port is unavailable.
• Source-route-failure - The device received a source-routed packet but cannot locate the next-hop
IP address indicated in the packet Source-Route option.
You can disable the Brocade device from sending these types of ICMP messages on an individual
basis. To do so, use the following CLI method.
NOTE
Disabling an ICMP Unreachable message type does not change the Brocade device ability to forward
packets. Disabling ICMP Unreachable messages prevents the device from generating or forwarding the
Unreachable messages.
To disable all ICMP Unreachable messages, enter the no ip icmp unreachable command.
device(config)# no ip icmp unreachable
Syntax: [no] ip icmp unreachable { host | protocol | administration | fragmentation-needed | port |
source-route-fail }
• If you enter the command without specifying a message type (as in the example above), all types of
ICMP Unreachable messages listed above are disabled. If you want to disable only specific types of
ICMP Unreachable messages, you can specify the message type. To disable more than one type of
ICMP message, enter the no ip icmp unreachable command for each messages type.
• The administration parameter disables ICMP Unreachable (caused by Administration action)
messages.
• The fragmentation-needed parameter disables ICMP Fragmentation-Needed But Do not-Fragment
Bit Set messages.
• The host parameter disables ICMP Host Unreachable messages.
• The port parameter disables ICMP Port Unreachable messages.
• The protocol parameter disables ICMP Protocol Unreachable messages.
• The source-route-fail parameter disables ICMP Unreachable (caused by Source-Route-Failure)
messages.
To disable ICMP Host Unreachable messages but leave the other types of ICMP Unreachable
messages enabled, enter the following commands instead of the command shown above.
device(config)# no ip icmp unreachable host
If you have disabled all ICMP Unreachable message types but you want to re-enable certain types, for
example ICMP Host Unreachable messages, you can do so by entering the following command.
device(config)# ip icmp unreachable host
Enabling ICMP Redirect Messages
You can enable and disable IPv4 ICMP redirect messages globally or on individual Virtual Ethernet (VE)
interfaces but not on individual physical interfaces.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 63
53-1003087-04
Page 64

Static routes configuration
NOTE
Some FSX devices do not generate ICMP redirect and network unreachable messages.
NOTE
The device forwards misdirected traffic to the appropriate router, even if you disable the redirect
messages.
By default, IP ICMP redirect over global level is disabled and a Brocade Layer 3 Switch does not send
an ICMP redirect message to the source of a misdirected packet in addition to forwarding the packet to
the appropriate router. To enable ICMP redirect messages globally, enter the following command at
the global CONFIG level of the CLI:
device(config)# ip icmp redirect
Syntax: [no] ip icmp redirect
To disable ICMP redirect messages on a specific virtual interface, enter the following command at the
configuration level for the virtual interface:
Brocade(config-vlan-10)# interface ve 10
Brocade(config-vif-10)# no ip redirect
Syntax: [no] ip redirect
Static routes configuration
The IP route table can receive routes from the following sources:
• Directly-connected networks - When you add an IP interface, the Layer 3 switch automatically
creates a route for the network the interface is in.
• RIP - If RIP is enabled, the Layer 3 switch can learn about routes from the advertisements other
RIP routers send to the Layer 3 switch. If the route has a lower administrative distance than any
other routes from different sources to the same destination, the Layer 3 switch places the route in
the IP route table.
• OSPF - Refer to RIP, but substitute "OSPF" for "RIP".
• BGP4 - Refer to RIP, but substitute "BGP4" for "RIP".
• Default network route - A statically configured default route that the Layer 3 switch uses if other
default routes to the destination are not available.
• Statically configured route - You can add routes directly to the route table. When you add a route
to the IP route table, you are creating a static IP route. This section describes how to add static
routes to the IP route table.
Static route types
You can configure the following types of static IP routes:
64 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 65

Static IP route parameters
• Standard - the static route consists of the destination network address and network mask, and the IP
address of the next-hop gateway. You can configure multiple standard static routes with the same
metric for load sharing or with different metrics to provide a primary route and backup routes.
• Interface-based - the static route consists of the destination network address and network mask,
and the Layer 3 switch interface through which you want the Layer 3 switch to send traffic for the
route. Typically, this type of static route is for directly attached destination networks.
• Null - the static route consists of the destination network address and network mask, and the "null0"
parameter. Typically, the null route is configured as a backup route for discarding traffic if the primary
route is unavailable.
Static IP route parameters
When you configure a static IP route, you must specify the following parameters:
• The IP address and network mask for the route destination network.
• The route path, which can be one of the following:
‐ The IP address of a next-hop gateway
‐ An Ethernet port
‐ A virtual interface (a routing interface used by VLANs for routing Layer 3 protocol traffic
among one another)
‐ A "null" interface. The Layer 3 switch drops traffic forwarded to the null interface.
You also can specify the following optional parameters:
• The metric for the route - The value the Layer 3 switch uses when comparing this route to other
routes in the IP route table to the same destination. The metric applies only to routes that the Layer 3
switch has already placed in the IP route table. The default metric for static IP routes is 1.
• The administrative distance for the route - The value that the Layer 3 switch uses to compare this
route with routes from other route sources to the same destination before placing a route in the IP
route table. This parameter does not apply to routes that are already in the IP route table. The default
administrative distance for static IP routes is 1.
The default metric and administrative distance values ensure that the Layer 3 switch always prefers
static IP routes over routes from other sources to the same destination.
Multiple static routes to the same destination provide load sharing and redundancy
You can add multiple static routes for the same destination network to provide one or more of the
following benefits:
• IP load balancing - When you add multiple IP static routes for the same destination to different nexthop gateways, and the routes each have the same metric and administrative distance, the Layer 3
switch can load balance traffic to the routes’ destination.
• Path redundancy - When you add multiple static IP routes for the same destination, but give the
routes different metrics or administrative distances, the Layer 3 switch uses the route with the lowest
administrative distance by default, but uses another route to the same destination if the first route
becomes unavailable.
Static route states follow port states
IP static routes remain in the IP route table only so long as the port or virtual interface used by the route
is available. If the port or virtual routing interface becomes unavailable, the software removes the static
route from the IP route table. If the port or virtual routing interface becomes available again later, the
software adds the route back to the route table.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 65
53-1003087-04
Page 66

Configuring a static IP route
This feature allows the Layer 3 switch to adjust to changes in network topology. The Layer 3 switch
does not continue trying to use routes on unavailable paths but instead uses routes only when their
paths are available.
The static route is configured on Switch A, as shown in the CLI example following the figure.
FIGURE 4 Example of a static route
The following command configures a static route to 10.95.7.0, using 10.95.6.157 as the next-hop
gateway.
device(config)# ip route 10.95.7.0/24 10.95.6.157
When you configure a static IP route, you specify the destination address for the route and the nexthop gateway or Layer 3 switch interface through which the Layer 3 switch can reach the route. The
Layer 3 switch adds the route to the IP route table. In this case, Switch A knows that 10.95.6.157 is
reachable through port 1/2, and also assumes that local interfaces within that subnet are on the same
port. Switch A deduces that IP interface 10.95.7.188 is also on port 1/2.
The software automatically removes a static IP route from the IP route table if the port used by that
route becomes unavailable. When the port becomes available again, the software automatically readds the route to the IP route table.
Configuring a static IP route
To configure an IP static route with a destination address of 10.0.0.0 255.0.0.0 and a next-hop router
IP address of 10.1.1.1, enter a command such as the following.
device(config)# ip route 10.0.0.0 255.0.0.0 10.1.1.1
To configure a static IP route with an Ethernet port instead of a next-hop address, enter a command
such as the following.
device(config)# ip route 10.128.2.69 255.255.255.0 ethernet 4/1
The command in the previous example configures a static IP route for destination network
10.128.2.69/24. Since an Ethernet port is specified instead of a gateway IP address as the next hop,
the Layer 3 switch always forwards traffic for the 10.128.2.69/24 network to port 4/1. The command in
the following example configures an IP static route that uses virtual interface 3 as its next hop.
device(config)# ip route 10.128.2.71 255.255.255.0 ve 3
The command in the following example configures an IP static route that uses port 2/2 as its next hop.
device(config)# ip route 10.128.2.73 255.255.255.0 ethernet 2/2
Syntax: ip route dest-ip-addr dest-mask { next-hop-ip-addr | ethernet [ slotnum/]portnum | venum } [
metric ] [ distance num ]
or
Syntax: ip route dest-ip-addr/mask-bits { next-hop-ip-addr | ethernet [ slotnum/]portnum | venum } [
metric ] [ distance num ]
66 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 67

Configuring a "Null" route
The dest-ip-addr is the route destination. The dest-mask is the network mask for the route destination IP
address. Alternatively, you can specify the network mask information by entering a forward slash
followed by the number of bits in the network mask. For example, you can enter 10.0.0.0 255.255.255.0
as 10.0.0.0/.24.
The next-hop-ip-addr is the IP address of the next-hop router (gateway) for the route.
If you do not want to specify a next-hop IP address, you can instead specify a port or interface number
on the . The num parameter is a virtual interface number. If you instead specify an Ethernet port, the
portnum is the port number (including the slot number, if you are configuring a Layer 3 switch). In this
case, the Layer 3 switch forwards packets destined for the static route destination network to the
specified Layer 3 switch interface. Conceptually, this feature makes the destination network like a
directly connected network, associated with a specific Layer 3 switch interface.
NOTE
The port or virtual interface you use for the static route next hop must have at least one IP address
configured on it. The address does not need to be in the same subnet as the destination network.
The metric parameter can be a number from 1 through 16. The default is 1.
NOTE
If you specify 16, RIP considers the metric to be infinite and thus also considers the route to be
unreachable.
The distancenum parameter specifies the administrative distance of the route. When comparing
otherwise equal routes to a destination, the Layer 3 switch prefers lower administrative distances over
higher ones, so make sure you use a low value for your default route. The default is 1.
NOTE
The Layer 3 switch will replace the static route if the it receives a route with a lower administrative
distance.
NOTE
You can also assign the default router as the destination by entering 0.0.0.0 0.0.0.0 xxx.xxx.xxx.xxx.
Configuring a "Null" route
You can configure the Layer 3 switch to drop IP packets to a specific network or host address by
configuring a "null" (sometimes called "null0") static route for the address. When the Layer 3 switch
receives a packet destined for the address, the Layer 3 switch drops the packet instead of forwarding it.
To configure a null static route, use the following CLI method.
To configure a null static route to drop packets destined for network 10.157.22.x, enter the following
commands.
device(config)# ip route 10.157.22.0 255.255.255.0 null0
device(config)# write memory
Syntax: ip route ip-addr ip-mask null0 [ metric ] [ distance num ]
or
Syntax: ip route ip-addr /mask-bits null0 [ metric ] [ distance num ]
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 67
53-1003087-04
Page 68

Naming a static IP route
To display the maximum value for your device, enter the show default values command. The
maximum number of static IP routes the system can hold is listed in the ip-static-route row in the
System Parameters section of the display. To change the maximum value, use the system-max ip-
static-route command at the global CONFIG level.
The ip-addr parameter specifies the network or host address. The Layer 3 switch will drop packets that
contain this address in the destination field instead of forwarding them.
The ip-mask parameter specifies the network mask. Ones are significant bits and zeros allow any
value. For example, the mask 255.255.255.0 matches on all hosts within the Class C subnet address
specified by ip-addr . Alternatively, you can specify the number of bits in the network mask. For
example, you can enter 10.157.22.0/24 instead of 10.157.22.0 255.255.255.0.
The null0 parameter indicates that this is a null route. You must specify this parameter to make this a
null route.
The metric parameter adds a cost to the route. You can specify from 1 through 16. The default is 1.
The distance num parameter configures the administrative distance for the route. You can specify a
value from 1 through 255. The default is 1. The value 255 makes the route unusable.
NOTE
The last two parameters are optional and do not affect the null route, unless you configure the
administrative distance to be 255. In this case, the route is not used and the traffic might be forwarded
instead of dropped.
Naming a static IP route
You can assign a name to a static IP route. A static IP route name serves as a description of the route.
The name can be used to more readily reference or identify the associated static route.
NOTE
The static route name is an optional feature. It does not affect the selection of static routes.
The Brocade device does not check for the uniqueness of names assigned to static routes. Static
routes that have the same or different next hop(s) can have the same or different name(s). Due to this,
the same name can be assigned to multiple static routes to group them. The name is then used to
reference or identify a group of static routes.
The option to assign a name to a static route is displayed after you select either an outgoing interface
type or configure the next hop address.
To assign a name to a static route, enter commands such as the following.
device(config)# ip route 10.22.22.22 255.255.255.255 eth 1/1 name abc
OR
device(config)# ip route 10.22.22.22 255.255.255.255 10.1.1.1 name abc
Syntax: [no] ip route dest-ip-addrdest-mask | dest-ip-addr/mask-bitsnext-hop-ip-addr | ethernet slot/
port | ve num [ metric ] [ tag num ] [ distance num ] [ name string ]
Enter the static route name for namestring. The maximum length of the name is 128 bytes.
The output of the show commands displays the name of a static IP route if there is one assigned.
68 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 69

Changing the name of a static IP route
The show run command displays the entire name of the static IP route. The show ip static route
command displays an asterisk (*) after the first twelve characters if the assigned name is thirteen
characters or more. The show ipv6 static route command displays an asterisk after the first two
characters if the assigned name is three characters or more.
When displayed in show run , a static route name with a space in the name will appear within quotation
marks (for example, "brcd route").
Changing the name of a static IP route
To change the name of a static IP route, enter the static route as configured. Proceed to enter the new
name instead of the previous name. See the example below.
Static IP route with the original name "abc":
device(config)# ip route 10.22.22.22 255.255.255.255 10.1.1.1 name abc
Change the name of "abc" to "xyz":
device(config)# ip route 10.22.22.22 255.255.255.255 10.1.1.1 name xyz
In this example, "xyz" is the set as the new name of the static IP route.
Deleting the name of a static IP route
To delete the name of a static IP route, use the no command. See the example below.
Static IP route with the name "xyz":
device(config)# ip route 10.22.22.22 255.255.255.255 10.1.1.1 name xyz
To remove the name "xyz" from the static IP route, specify both "name" and the string, in this case
"xyz".
device(config)#no ip route 10.22.22.22 255.255.255.255 10.1.1.1 name xyz
The static route no longer has a name assigned to it.
Configuring load balancing and redundancy using multiple static routes to the same destination
You can configure multiple static IP routes to the same destination, for the following benefits:
• IP load sharing - If you configure more than one static route to the same destination, and the routes
have different next-hop gateways but have the same metrics, the Layer 3 switch load balances
among the routes using basic round-robin. For example, if you configure two static routes with the
same metrics but to different gateways, the Layer 3 switch alternates between the two routes.
• Backup Routes - If you configure multiple static IP routes to the same destination, but give the
routes different next-hop gateways and different metrics, the Layer 3 switch will always use the route
with the lowest metric. If this route becomes unavailable, the Layer 3 switch will fail over to the static
route with the next-lowest metric, and so on.
NOTE
You also can bias the Layer 3 switch to select one of the routes by configuring them with different
administrative distances. However, make sure you do not give a static route a higher administrative
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 69
53-1003087-04
Page 70

Configuring standard static IP routes and interface or null static routes to the same destination
distance than other types of routes, unless you want those other types to be preferred over the static
route.
The steps for configuring the static routes are the same as described in the previous section. The
following sections provide examples.
To configure multiple static IP routes, enter commands such as the following.
device(config)# ip route 10.128.2.69 255.255.255.0 10.157.22.1
device(config)# ip route 10.128.2.69 255.255.255.0 10.111.10.1
The commands in the previous example configure two static IP routes. The routes go to different nexthop gateways but have the same metrics. These commands use the default metric value (1), so the
metric is not specified. These static routes are used for load sharing among the next-hop gateways.
The following commands configure static IP routes to the same destination, but with different metrics.
The route with the lowest metric is used by default. The other routes are backups in case the first route
becomes unavailable. The Layer 3 switch uses the route with the lowest metric if the route is available.
device(config)# ip route 10.128.2.69 255.255.255.0 10.157.22.1
device(config)# ip route 10.128.2.69 255.255.255.0 10.111.10.1 2
device(config)# ip route 10.128.2.69 255.255.255.0 10.1.1.1 3
In this example, each static route has a different metric. The metric is not specified for the first route,
so the default (1) is used. A metric is specified for the second and third static IP routes. The second
route has a metric of two and the third route has a metric of 3. Thus, the second route is used only of
the first route (which has a metric of 1) becomes unavailable. Likewise, the third route is used only if
the first and second routes (which have lower metrics) are both unavailable.
Configuring standard static IP routes and interface or null static routes to the same
destination
You can configure a null0 or interface-based static route to a destination and also configure a normal
static route to the same destination, so long as the route metrics are different.
When the Layer 3 switch has multiple routes to the same destination, the Layer 3 switch always
prefers the route with the lowest metric. Generally, when you configure a static route to a destination
network, you assign the route a low metric so that the Layer 3 switch prefers the static route over other
routes to the destination.
This feature is especially useful for the following configurations. These are not the only allowed
configurations but they are typical uses of this enhancement:
• When you want to ensure that if a given destination network is unavailable, the Layer 3 switch drops
(forwards to the null interface) traffic for that network instead of using alternate paths to route the
traffic. In this case, assign the normal static route to the destination network a lower metric than the
null route.
• When you want to use a specific interface by default to route traffic to a given destination network,
but want to allow the Layer 3 switch to use other interfaces to reach the destination network if the
path that uses the default interface becomes unavailable. In this case, give the interface route a
lower metric than the normal static route.
NOTE
You cannot add a null or interface-based static route to a network if there is already a static route of
any type with the same metric you specify for the null or interface-based route.
In the example, two static routes configured for the same destination network. One of the routes is a
standard static route and has a metric of 1. The other static route is a null route and has a higher
70 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 71

IP Configuration
metric than the standard static route. The Layer 3 switch always prefers the static route with the lower
metric. In this example, the Layer 3 switch always uses the standard static route for traffic to destination
network 192.168.7.0/24, unless that route becomes unavailable, in which case the Layer 3 switch sends
traffic to the null route instead.
FIGURE 5 Standard and null static routes to the same destination network
The next example shows another example of two static routes. In this example, a standard static route
and an interface-based static route are configured for destination network 192.168.6.0/24. The
interface-based static route has a lower metric than the standard static route. As a result, the Layer 3
switch always prefers the interface-based route when the route is available. However, if the interfacebased route becomes unavailable, the Layer 3 switch still forwards the traffic toward the destination
using an alternate route through gateway 192.168.8.11/24.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 71
53-1003087-04
Page 72

Configuring a default network route
FIGURE 6 Standard and interface routes to the same destination network
To configure a standard static IP route and a null route to the same network, enter commands such as
the following.
device(config)# ip route 192.168.7.0/24 192.168.6.157/24 1
device(config)# ip route 192.168.7.0/24 null0 3
The first command configures a standard static route, which includes specification of the next-hop
gateway. The command also gives the standard static route a metric of 1, which causes the Layer 3
switch to always prefer this route when the route is available.
The second command configures another static route for the same destination network, but the
second route is a null route. The metric for the null route is 3, which is higher than the metric for the
standard static route. If the standard static route is unavailable, the software uses the null route.
To configure a standard static route and an interface-based route to the same destination, enter
commands such as the following.
device(config)# ip route 192.168.6.0/24 ethernet 1/1 1
device(config)# ip route 192.168.6.0/24 192.168.8.11/24 3
The first command configured an interface-based static route through Ethernet port 1/1. The command
assigns a metric of 1 to this route, causing the Layer 3 switch to always prefer this route when it is
available. If the route becomes unavailable, the Layer 3 switch uses an alternate route through the
next-hop gateway 192.168.8.11/24.
Configuring a default network route
The Layer 3 switch enables you to specify a candidate default route without the need to specify the
next hop gateway. If the IP route table does not contain an explicit default route (for example,
0.0.0.0/0) or propagate an explicit default route through routing protocols, the software can use the
default network route as a default route instead.
72 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 73

Configuring a default network route
When the software uses the default network route, it also uses the default network route's next hop
gateway as the gateway of last resort.
This feature is especially useful in environments where network topology changes can make the next
hop gateway unreachable. This feature allows the Layer 3 switch to perform default routing even if the
default network route's default gateway changes.
The feature thus differs from standard default routes. When you configure a standard default route, you
also specify the next hop gateway. If a topology change makes the gateway unreachable, the default
route becomes unusable.
For example, if you configure 10.10.10.0/24 as a candidate default network route, if the IP route table
does not contain an explicit default route (0.0.0.0/0), the software uses the default network route and
automatically uses that route's next hop gateway as the default gateway. If a topology change occurs
and as a result the default network route's next hop gateway changes, the software can still use the
default network route. To configure a default network route, use the following CLI method.
If you configure more than one default network route, the Layer 3 switch uses the following algorithm to
select one of the routes.
1. Use the route with the lowest administrative distance.
2. If the administrative distances are equal:
• ‐ Are the routes from different routing protocols (RIP, OSPF, or BGP4)? If so, use the route
with the lowest IP address.
‐ If the routes are from the same routing protocol, use the route with the best metric. The
meaning of "best" metric depends on the routing protocol:
‐ RIP - The metric is the number of hops (additional routers) to the destination. The best
route is the route with the fewest hops.
‐ OSPF - The metric is the path cost associated with the route. The path cost does not
indicate the number of hops but is instead a numeric value associated with each route.
The best route is the route with the lowest path cost.
‐ BGP4 - The metric is the Multi-exit Discriminator (MED) associated with the route. The
MED applies to routes that have multiple paths through the same Autonomous System.
The best route is the route with the lowest MED.
Configuring a default network route
You can configure up to four default network routes.
To configure a default network route, enter commands such as the following.
device(config)# ip default-network 10.157.22.0
device(config)# write memory
Syntax: ip default-network ip-addr
The ip-addr parameter specifies the network address.
To verify that the route is in the route table, enter the following command at any level of the CLI.
device# show ip route
Total number of IP routes: 2
Start index: 1 B:BGP D:Connected R:RIP S:Static O:OSPF *:Candidate default
Destination NetMask Gateway Port Cost Type
1 10.157.20.0 255.255.255.0 0.0.0.0 lb1 1 D
2 10.157.22.0 255.255.255.0 0.0.0.0 4/11 1 *D
This example shows two routes. Both of the routes are directly attached, as indicated in the Type
column. However, one of the routes is shown as type "*D", with an asterisk (*). The asterisk indicates
that this route is a candidate default network route.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 73
53-1003087-04
Page 74

Configuring IP load sharing
Configuring IP load sharing
The IP route table can contain more than one path to a given destination. When this occurs, the Layer
3 switch selects the path with the lowest cost as the path for forwarding traffic to the destination. If the
IP route table contains more than one path to a destination and the paths each have the lowest cost,
then the Layer 3 switch uses IP load sharing to select a path to the destination.
IP load sharing uses a hashing algorithm based on the source IP address, destination IP address, and
protocol field in the IP header, TCP, and UDP information.
NOTE
IP load sharing is based on next-hop routing, and not on source routing.
NOTE
The term "path" refers to the next-hop router to a destination, not to the entire route to a destination.
Thus, when the software compares multiple equal-cost paths, the software is comparing paths that
use different next-hop routers, with equal costs, to the same destination.In many contexts, the terms
"route" and "path" mean the same thing. The term "path" is used in this section to refer to an individual
next-hop router to a destination, while the term "route" refers collectively to the multiple paths to the
destination. Load sharing applies when the IP route table contains multiple, equal-cost paths to a
destination.
7
NOTE
Brocade devices also perform load sharing among the ports in aggregate links. Refer to "Trunk group
load sharing" section in the FastIron Ethernet Switch Platform and Layer 2 Switching Configuration
Guide .
How multiple equal-cost paths enter the IP route table
IP load sharing applies to equal-cost paths in the IP route table. Routes that are eligible for load
sharing can enter the table from any of the following sources:
• IP static routes
• Routes learned through RIP
• Routes learned through OSPF
• Routes learned through BGP4
Administrative distance for each IP route
The administrative distance is a unique value associated with each type (source) of IP route. Each
path has an administrative distance. The administrative distance is not used when performing IP load
sharing, but the administrative distance is used when evaluating multiple equal-cost paths to the same
destination from different sources, such as RIP, OSPF and so on.
The value of the administrative distance is determined by the source of the route. The Layer 3 switch
is configured with a unique administrative distance value for each IP route source.
When the software receives multiple paths to the same destination and the paths are from different
sources, the software compares the administrative distances of the paths and selects the path with the
lowest distance. The software then places the path with the lowest administrative distance in the IP
7
IP load sharing is also called "Equal-Cost Multi-Path (ECMP)" load sharing or just "ECMP"
74 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 75

IP Configuration
route table. For example, if the Layer 3 switch has a path learned from OSPF and a path learned from
RIP for a given destination, only the path with the lower administrative distance enters the IP route
table.
Here are the default administrative distances on the BrocadeLayer 3 switch:
• Directly connected - 0 (this value is not configurable)
• Static IP route - 1 (applies to all static routes, including default routes and default network routes)
• Exterior Border Gateway Protocol (EBGP) - 20
• OSPF - 110
• RIP - 120
• Interior Gateway Protocol (IBGP) - 200
• Local BGP - 200
• Unknown - 255 (the router will not use this route)
Lower administrative distances are preferred over higher distances. For example, if the router receives
routes for the same network from OSPF and from RIP, the router will prefer the OSPF route by default.
NOTE
You can change the administrative distances individually. Refer to the configuration chapter for the
route source for information.
Since the software selects only the path with the lowest administrative distance, and the administrative
distance is determined by the path source, IP load sharing does not apply to paths from different route
sources. IP load sharing applies only when the IP route table contains multiple paths to the same
destination, from the same IP route source.
IP load sharing does not apply to paths that come from different sources.
Path cost
The cost parameter provides a common basis of comparison for selecting from among multiple paths to
a given destination. Each path in the IP route table has a cost. When the IP route table contains multiple
paths to a destination, the Layer 3 switch chooses the path with the lowest cost. When the IP route
table contains more than one path with the lowest cost to a destination, the Layer 3 switch uses IP load
sharing to select one of the lowest-cost paths.
The source of a path cost value depends on the source of the path:
• IP static route - The value you assign to the metric parameter when you configure the route. The
default metric is 1.
• RIP - The number of next-hop routers to the destination.
• OSPF - The Path Cost associated with the path. The paths can come from any combination of interarea, intra-area, and external Link State Advertisements (LSAs).
• BGP4 - The path Multi-Exit Discriminator (MED) value.
NOTE
If the path is redistributed between two or more of the above sources before entering the IP route table,
the cost can increase during the redistribution due to settings in redistribution filters.
Static route, OSPF, and BGP4 load sharing
IP load sharing and load sharing for static routes, OSPF routes, and BGP4 routes are individually
configured. Multiple equal-cost paths for a destination can enter the IP route table only if the source of
the paths is configured to support multiple equal-cost paths. For example, if BGP4 allows only one path
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 75
53-1003087-04
Page 76

How IP load sharing works
with a given cost for a given destination, the BGP4 route table cannot contain equal-cost paths to the
destination. Consequently, the IP route table will not receive multiple equal-cost paths from BGP4.
The load sharing state for all the route sources is based on the state of IP load sharing. Since IP load
sharing is enabled by default on all BrocadeLayer 3 switches, load sharing for static IP routes, RIP
routes, OSPF routes, and BGP4 routes also is enabled by default.
Default load sharing parameters for route sources TABLE 7
Route source Default maximum
number of paths
Static IP route 4
RIP 4
OSPF 4 6 8
BGP4 1 4 4
1 This value depends on the value for IP load sharing, and is not separately configurable.
1
1
Maximum number of paths
FSX FCX / ICX 6450 / ICX 6610 / ICX
6650 / ICX 7750
1
6
1
6
1
8
1
8
How IP load sharing works
When the Layer 3 switch receives traffic for a destination and the IP route table contains multiple,
equal-cost paths to that destination, the device checks the IP forwarding cache for a forwarding entry
for the destination. The IP forwarding cache provides a fast path for forwarding IP traffic, including
load-balanced traffic. The cache contains entries that associate a destination host or network with a
path (next-hop router).
• If the IP forwarding sharing cache contains a forwarding entry for the destination, the device uses
the entry to forward the traffic.
• If the IP load forwarding cache does not contain a forwarding entry for the destination, the software
selects a path from among the available equal-cost paths to the destination, then creates a
forwarding entry in the cache based on the calculation. Subsequent traffic for the same destination
uses the forwarding entry.
Response to path state changes
If one of the load-balanced paths to a cached destination becomes unavailable, or the IP route table
receives a new equal-cost path to a cached destination, the software removes the unavailable path
from the IP route table. Then the software selects a new path. Disabling or re-enabling load sharing
To disable IP load sharing, enter the following commands.
device(config)# no ip load-sharing
Syntax: no ip load-sharing
76 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 77

Changing the maximum number of ECMP (load sharing) paths
Changing the maximum number of ECMP (load sharing) paths
You can change the maximum number of paths the Layer 3 switch supports to a value from 2 through 8.
Maximum number of ECMP load sharing paths per deviceTABLE 8
FSX 800 / FSX 1600 FCX ICX6450 / ICX6610 / ICX6650 / ICX7750
6 8 8
For optimal results, set the maximum number of paths to a value at least as high as the maximum
number of equal-cost paths your network typically contains. For example, if the Layer 3 switch you are
configuring for IP load sharing has six next-hop routers, set the maximum paths value to six.
To change the number of IP load sharing paths, enter a command such as the following.
device(config)# ip load-sharing 6
Syntax: [no] ip load-sharing [ num ]
The num parameter specifies the number of paths and can be from 2 through 8, depending on the
device you are configuring.
ICMP Router Discovery Protocol configuration
The ICMP Router Discovery Protocol (IRDP) is used by BrocadeLayer 3 switches to advertise the IP
addresses of its router interfaces to directly attached hosts. IRDP is disabled by default. You can enable
the feature on a global basis or on an individual port basis:
• If you enable the feature globally, all ports use the default values for the IRDP parameters.
• If you leave the feature disabled globally but enable it on individual ports, you also can configure the
IRDP parameters on an individual port basis.
NOTE
You can configure IRDP parameters only an individual port basis. To do so, IRDP must be disabled
globally and enabled only on individual ports. You cannot configure IRDP parameters if the feature is
globally enabled.
When IRDP is enabled, the Layer 3 switch periodically sends Router Advertisement messages out the
IP interfaces on which the feature is enabled. The messages advertise the Layer 3 switch IP addresses
to directly attached hosts who listen for the messages. In addition, hosts can be configured to query the
Layer 3 switch for the information by sending Router Solicitation messages.
Some types of hosts use the Router Solicitation messages to discover their default gateway. When
IRDP is enabled on the BrocadeLayer 3 switch, the Layer 3 switch responds to the Router Solicitation
messages. Some clients interpret this response to mean that the Layer 3 switch is the default gateway.
If another router is actually the default gateway for these clients, leave IRDP disabled on the
BrocadeLayer 3 switch.
IRDP parameters
IRDP uses the following parameters. If you enable IRDP on individual ports instead of enabling the
feature globally, you can configure these parameters on an individual port basis:
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 77
53-1003087-04
Page 78

Enabling IRDP globally
• Packet type - The Layer 3 switch can send Router Advertisement messages as IP broadcasts or as
IP multicasts addressed to IP multicast group 224.0.0.1. The packet type is IP broadcast.
• Maximum message interval and minimum message interval - When IRDP is enabled, the Layer
3 switch sends the Router Advertisement messages every 450 - 600 seconds by default. The time
within this interval that the Layer 3 switch selects is random for each message and is not affected
by traffic loads or other network factors. The random interval minimizes the probability that a host
will receive Router Advertisement messages from other routers at the same time. The interval on
each IRDP-enabled Layer 3 switch interface is independent of the interval on other IRDP-enabled
interfaces. The default maximum message interval is 600 seconds. The default minimum message
interval is 450 seconds.
• Hold time - Each Router Advertisement message contains a hold time value. This value specifies
the maximum amount of time the host should consider an advertisement to be valid until a newer
advertisement arrives. When a new advertisement arrives, the hold time is reset. The hold time is
always longer than the maximum advertisement interval. Therefore, if the hold time for an
advertisement expires, the host can reasonably conclude that the router interface that sent the
advertisement is no longer available. The default hold time is three times the maximum message
interval.
• Preference - If a host receives multiple Router Advertisement messages from different routers, the
host selects the router that sent the message with the highest preference as the default gateway.
The preference can be a number from 0-4294967296. The default is 0.
Enabling IRDP globally
To globally enable IRDP, enter the following command.
device(config)# ip irdp
This command enables IRDP on the IP interfaces on all ports. Each port uses the default values for
the IRDP parameters. The parameters are not configurable when IRDP is globally enabled.
Enabling IRDP on an individual port
To enable IRDP on an individual interface and change IRDP parameters, enter commands such as the
following.
device(config)# interface ethernet 1/3
device(config-if-1/3)# ip irdp maxadvertinterval 400
This example shows how to enable IRDP on a specific port and change the maximum advertisement
interval for Router Advertisement messages to 400 seconds.
NOTE
To enable IRDP on individual ports, you must leave the feature globally disabled.
Syntax: [no] ip irdp { broadcast | multicast } [ holdtime seconds ] [ maxadvertinterval seconds ] [
minadvertinterval seconds ] [ preference number ]
The broadcast and multicast parameters specify the packet type the Layer 3 switch uses to send
Router Advertisement:
• broadcast - The Layer 3 switch sends Router Advertisement as IP broadcasts. This is the default.
• multicast - The Layer 3 switch sends Router Advertisement as multicast packets addressed to IP
multicast group 224.0.0.1.
The holdtimeseconds parameter specifies how long a host that receives a Router Advertisement from
the Layer 3 switch should consider the advertisement to be valid. When a host receives a new Router
78 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 79

Reverse Address Resolution Protocol configuration
Advertisement message from the Layer 3 switch, the host resets the hold time for the Layer 3 switch to
the hold time specified in the new advertisement. If the hold time of an advertisement expires, the host
discards the advertisement, concluding that the router interface that sent the advertisement is no longer
available. The value must be greater than the value of the maxadvertinterval parameter and cannot be
greater than 9000. The default is three times the value of the maxadvertinterval parameter.
The maxadvertinterval parameter specifies the maximum amount of time the Layer 3 switch waits
between sending Router Advertisements. You can specify a value from 1 to the current value of the
holdtime parameter. The default is 600 seconds.
The minadvertinterval parameter specifies the minimum amount of time the Layer 3 switch can wait
between sending Router Advertisements. The default is three-fourths (0.75) the value of the
maxadvertinterval parameter. If you change the maxadvertinterval parameter, the software
automatically adjusts the minadvertinterval parameter to be three-fourths the new value of the
maxadvertinterval parameter. If you want to override the automatically configured value, you can
specify an interval from 1 to the current value of the maxadvertinterval parameter.
The preferencenumber parameter specifies the IRDP preference level of this Layer 3 switch. If a host
receives Router Advertisements from multiple routers, the host selects the router interface that sent the
message with the highest interval as the host default gateway. The valid range is from 0 to
4294967296. The default is 0.
Reverse Address Resolution Protocol configuration
The Reverse Address Resolution Protocol (RARP) provides a simple mechanism for directly-attached
IP hosts to boot over the network. RARP allows an IP host that does not have a means of storing its IP
address across power cycles or software reloads to query a directly-attached router for an IP address.
RARP is enabled by default. However, you must create a RARP entry for each host that will use the
Layer 3 switch for booting. A RARP entry consists of the following information:
• The entry number - the entry sequence number in the RARP table.
• The MAC address of the boot client.
• The IP address you want the Layer 3 switch to give to the client.
When a client sends a RARP broadcast requesting an IP address, the Layer 3 switch responds to the
request by looking in the RARP table for an entry that contains the client MAC address:
• If the RARP table contains an entry for the client, the Layer 3 switch sends a unicast response to the
client that contains the IP address associated with the client MAC address in the RARP table.
• If the RARP table does not contain an entry for the client, the Layer 3 switch silently discards the
RARP request and does not reply to the client.
How RARP Differs from BootP and DHCP
RARP and BootP/DHCP are different methods for providing IP addresses to IP hosts when they boot.
These methods differ in the following ways:
• Location of configured host addresses:
‐ RARP requires static configuration of the host IP addresses on the Layer 3 switch. The
Layer 3 switch replies directly to a host request by sending an IP address you have
configured in the RARP table.
‐ The Layer 3 switch forwards BootP and DHCP requests to a third-party BootP/DHCP server
that contains the IP addresses and other host configuration information.
• Connection of host to boot source (Layer 3 switch or BootP/DHCP server):
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 79
53-1003087-04
Page 80

Disabling RARP
‐ RARP requires the IP host to be directly attached to the Layer 3 switch.
‐ An IP host and the BootP/DHCP server can be on different networks and on different
routers, so long as the routers are configured to forward ("help") the host boot request to
the boot server.
‐ You can centrally configure other host parameters on the BootP/DHCP server, in addition
to the IP address, and supply those parameters to the host along with its IP address.
To configure the Layer 3 switch to forward BootP/DHCP requests when boot clients and the boot
servers are on different subnets on different Layer 3 switch interfaces, refer to BootP and DHCP relay
parameter configuration on page 83.
Disabling RARP
RARP is enabled by default. To disable RARP, enter the following command at the global CONFIG
level.
device(config)# no ip rarp
Syntax: [no] ip rarp
To re-enable RARP, enter the following command.
device(config)# ip rarp
Creating static RARP entries
You must configure the RARP entries for the RARP table. The Layer 3 switch can send an IP address
in reply to a client RARP request only if create a RARP entry for that client.
To assign a static IP RARP entry for static routes on a Brocade router, enter a command such as the
following.
device(config)# rarp 1 0000.0054.2348 10.53.4.2
This command creates a RARP entry for a client with MAC address 0000.0054.2348. When the Layer
3 switch receives a RARP request from this client, the Layer 3 switch replies to the request by sending
IP address 192.53.4.2 to the client.
Syntax: rap number mac-addr ip-addr
The number parameter identifies the RARP entry number. You can specify an unused number from 1
to the maximum number of RARP entries supported on the device. To determine the maximum
number of entries supported on the device, refer to the section "Displaying and modifying system
parameter default settings" in the FastIron Ethernet Switch Platform and Layer 2 Switching
Configuration Guide .
The mac-addr parameter specifies the MAC address of the RARP client.
The ip-addr parameter specifies the IP address the Layer 3 switch will give the client in response to
the client RARP request.
Changing the maximum number of static RARP entries supported
The number of RARP entries the Layer 3 switch supports depends on how much memory the Layer 3
switch has. To determine how many RARP entries your Layer 3 switch can have, display the system
default information using the procedure in the section "Displaying system parameter default values" in
the FastIron Ethernet Switch Platform and Layer 2 Switching Configuration Guide .
80 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 81

Configuring UDP broadcast and IP helper parameters
If your Layer 3 switch allows you to increase the maximum number of RARP entries, you can use a
procedure in the same section to do so.
NOTE
You must save the configuration to the startup-config file and reload the software after changing the
RARP cache size to place the change into effect.
Configuring UDP broadcast and IP helper parameters
Some applications rely on client requests sent as limited IP broadcasts addressed to the UDP
application port. If a server for the application receives such a broadcast, the server can reply to the
client. Routers do not forward subnet directed broadcasts, so the client and server must be on the same
network for the broadcast to reach the server. If the client and server are on different networks (on
opposite sides of a router), the client request cannot reach the server.
You can configure the Layer 3 switch to forward clients‘ requests to UDP application servers. To do so:
• Enable forwarding support for the UDP application port, if forwarding support is not already enabled.
• Configure a helper adders on the interface connected to the clients. Specify the helper address to be
the IP address of the application server or the subnet directed broadcast address for the IP subnet
the server is in. A helper address is associated with a specific interface and applies only to client
requests received on that interface. The Layer 3 switch forwards client requests for any of the
application ports the Layer 3 switch is enabled to forward to the helper address.
Forwarding support for the following application ports is enabled by default:
• dns (port 53)
• tftp (port 69)
• time (port 37)
• tacacs (port 65)
NOTE
The application names are the names for these applications that the Layer 3 switch software
recognizes, and might not match the names for these applications on some third-party devices. The
numbers listed in parentheses are the UDP port numbers for the applications. The numbers come from
RFC 1340.
NOTE
Forwarding support for BootP/DHCP is enabled by default.
You can enable forwarding for other applications by specifying the application port number.
You also can disable forwarding for an application.
NOTE
If you disable forwarding for a UDP application, forwarding of client requests received as broadcasts to
helper addresses is disabled. Disabling forwarding of an application does not disable other support for
the application. For example, if you disable forwarding of Telnet requests to helper addresses, other
Telnet support on the Layer 3 switch is not also disabled.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 81
53-1003087-04
Page 82

Enabling forwarding for a UDP application
Enabling forwarding for a UDP application
If you want the Layer 3 switch to forward client requests for UDP applications that the Layer 3 switch
does not forward by default, you can enable forwarding support for the port. To enable forwarding
support for a UDP application, use the following method. You also can disable forwarding for an
application using this method.
NOTE
You also must configure a helper address on the interface that is connected to the clients for the
application. The Layer 3 switch cannot forward the requests unless you configure the helper address.
To enable the forwarding of NTP broadcasts, enter the following command.
device(config)# ip forward-protocol udp ntp
Syntax: [no] ip forward-protocol {udp udp-port-name | udp-port-num }
The udp-port-name parameter can have one of the following values. For reference, the corresponding
port numbers from RFC 1340 are shown in parentheses. If you specify an application name, enter the
name only, not the parentheses or the port number shown here:
• bootpc (port 68)
• bootps (port 67)
• discard (port 9)
• dns (port 53)
• dnsix (port 90)
• echo (port 7)
• mobile-ip (port 434)
• netbios-dgm (port 138)
• netbios-ns (port 137)
• ntp (port 123)
• tacacs (port 65)
• talk (port 517)
• time (port 37)
• tftp (port 69)
In addition, you can specify any UDP application by using the application UDP port number.
The udp-port-num parameter specifies the UDP application port number. If the application you want to
enable is not listed above, enter the application port number. You also can list the port number for any
of the applications listed above.
To disable forwarding for an application, enter a command such as the following.
device(config)# no ip forward-protocol udp ntp
This command disables forwarding of SNMP requests to the helper addresses configured on Layer 3
switch interfaces.
Configuring an IP helper address
To forward a client broadcast request for a UDP application when the client and server are on different
networks, you must configure a helper address on the interface connected to the client. Specify the
server IP address or the subnet directed broadcast address of the IP subnet the server is in as the
helper address.
82 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 83

BootP and DHCP relay parameter configuration
You can configure up to 16 helper addresses on each interface. You can configure a helper address on
an Ethernet port or a virtual interface.
To configure a helper address on interface 2 on chassis module 1, enter the following commands.
device(config)# interface ethernet 1/2
device(config-if-1/2)# ip helper-address 1 10.95.7.6
The commands in this example change the CLI to the configuration level for port 1/2, then add a helper
address for server 10.95.7.6 to the port. If the port receives a client request for any of the applications
that the Layer 3 switch is enabled to forward, the Layer 3 switch forwards the client request to the
server.
By default, IP helper does not forward client broadcast request to a server within the network.
To forward a client broadcast request when the client and server are on the same network, configure an
IP helper with unicast option on the interface connected to the client.
To configure an IP helper unicast option on interface 2 on chassis module 1, enter the following
commands:
device(config)# interface 1/2
device(config-if-1/2)ip helper-address 1 10.10.10.1 unicast
The IP helper with unicast parameter forwards the client request to the server 10.10.10.1 which is within
the network.
Syntax: ip helper-address num ip-addr (unicast)
The num parameter specifies the helper address number and can be from 1 through 16.
The ip-addr command specifies the server IP address or the subnet directed broadcast address of the
IP subnet the server is in.
The unicast parameter specifies that the client request must be forwarded to the server which is on the
same network.
BootP and DHCP relay parameter configuration
A host on an IP network can use BootP or DHCP to obtain its IP address from a BootP/DHCP server.
To obtain the address, the client sends a BootP or DHCP request. The request is a subnet directed
broadcast and is addressed to UDP port 67. A limited IP broadcast is addressed to IP address
255.255.255.255 and is not forwarded by the Brocade Layer 3 switch or other IP routers.
When the BootP or DHCP client and server are on the same network, the server receives the broadcast
request and replies to the client. However, when the client and server are on different networks, the
server does not receive the client request, because the Layer 3 switch does not forward the request.
You can configure the Layer 3 switch to forward BootP/DHCP requests. To do so, configure a helper
address on the interface that receives the client requests, and specify the BootP/DHCP server IP
address as the address you are helping the BootP/DHCP requests to reach. Instead of the server IP
address, you can specify the subnet directed broadcast address of the IP subnet the server is in.
BootP and DHCP relay parameters
The following parameters control the Layer 3 switch forwarding of BootP and DHCP requests:
• Helper address - The BootP/DHCP server IP address. You must configure the helper address on
the interface that receives the BootP/DHCP requests from the client. The Layer 3 switch cannot
forward a request to the server unless you configure a helper address for the server.
• Gateway address - The Layer 3 switch places the IP address of the interface that received the
BootP/DHCP request in the request packet Gateway Address field (sometimes called the Router ID
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 83
53-1003087-04
Page 84

Configuring an IP helper address
field). When the server responds to the request, the server sends the response as a unicast packet
to the IP address in the Gateway Address field. (If the client and server are directly attached, the
Gateway ID field is empty and the server replies to the client using a unicast or broadcast packet,
depending on the server.)
By default, the Layer 3 switch uses the lowest-numbered IP address on the interface that receives the
request as the Gateway address. You can override the default by specifying the IP address you want
the Layer 3 switch to use.
• Hop count - Each router that forwards a BootP/DHCP packet increments the hop count by 1.
Routers also discard a forwarded BootP/DHCP request instead of forwarding the request if the hop
count is greater than the maximum number of BootP/DHCP hops allows by the router. By default, a
Brocade Layer 3 switch forwards a BootP/DHCP request if its hop count is four or less, but discards
the request if the hop count is greater than four. You can change the maximum number of hops the
Layer 3 switch will allow to a value from 1 through 15.
NOTE
The BootP/DHCP hop count is not the TTL parameter.
Configuring an IP helper address
The procedure for configuring a helper address for BootP/DHCP requests is the same as the
procedure for configuring a helper address for other types of UDP broadcasts. Refer to Configuring an
IP helper address on page 82.
Configuring the BOOTP and DHCP reply source address
You can configure the Brocade device so that a BOOTP/DHCP reply to a client contains the server IP
address as the source address instead of the router IP address. To do so, enter the following
command at the Global CONFIG level of the CLI.
device(config)# ip helper-use-responder-ip
Syntax: [no] ip helper-use-responder-ip
Changing the IP address used for stamping BootP and DHCP requests
When the Layer 3 switch forwards a BootP/DHCP request, the Layer 3 switch "stamps" the Gateway
Address field. The default value the Layer 3 switch uses to stamp the packet is the lowest-numbered
IP address configured on the interface that received the request. If you want the Layer 3 switch to use
a different IP address to stamp requests received on the interface, use either of the following methods
to specify the address.
The BootP/DHCP stamp address is an interface parameter. Change the parameter on the interface
that is connected to the BootP/DHCP client.
To change the IP address used for stamping BootP/DHCP requests received on interface 1/1, enter
commands such as the following.
device(config)# interface ethernet 1/1
device(config-if-1/1)# ip bootp-gateway 10.157.22.26
These commands change the CLI to the configuration level for port 1/1, then change the BootP/DHCP
stamp address for requests received on port 1/1 to 10.157.22.26. The Layer 3 switch will place this IP
address in the Gateway Address field of BootP/DHCP requests that the Layer 3 switch receives on
port 1/1 and forwards to the BootP/DHCP server.
84 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 85

Changing the maximum number of hops to a BootP relay server
Syntax: ip bootp-gatewayip-addr
Changing the maximum number of hops to a BootP relay server
Each BootP or DHCP request includes a field Hop Count field. The Hop Count field indicates how many
routers the request has passed through. When the Layer 3 switch receives a BootP/DHCP request, the
Layer 3 switch looks at the value in the Hop Count field:
• If the hop count value is equal to or less than the maximum hop count the Layer 3 switch allows, the
Layer 3 switch increments the hop count by one and forwards the request.
• If the hop count is greater than the maximum hop count the Layer 3 switch allows, the Layer 3 switch
discards the request.
To change the maximum number of hops the Layer 3 switch allows for forwarded BootP/DHCP
requests, use either of the following methods.
NOTE
The BootP and DHCP hop count is not the TTL parameter.
To modify the maximum number of BootP/DHCP hops, enter the following command.
device(config)# bootp-relay-max-hops 10
This command allows the Layer 3 switch to forward BootP/DHCP requests that have passed through
ten previous hops before reaching the Layer 3 switch. Requests that have traversed 11 hops before
reaching the switch are dropped. Since the hop count value initializes at zero, the hop count value of an
ingressing DHCP Request packet is the number of Layer 3 routers that the packet has already
traversed.
Syntax: bootp-relay-max-hops max-hops
The max-hops parameter value can be 1 through 15.
DHCP Server
All FastIron devices can be configured to function as DHCP Servers.
NOTE
The DHCP server is platform independent and has no differences in behavior or configuration across all
FastIron platforms (FSX, FCX, and ICX).
Dynamic Host Configuration Protocol (DHCP) is a computer networking protocol used by devices
(DHCP clients) to obtain leased (or permanent) IP addresses. DHCP is an extension of the Bootstrap
Protocol (BOOTP). The differences between DHCP and BOOTP are the address allocation and renewal
process.
DHCP introduces the concept of a lease on an IP address. Refer to How DHCP Client-Based Auto-
Configuration and Flash image update works on page 100. The DHCP server can allocate an IP
address for a specified amount of time, or can extend a lease for an indefinite amount of time. DHCP
provides greater control of address distribution within a subnet. This feature is crucial if the subnet has
more devices than available IP address. In contrast to BOOTP, which has two types of messages that
can be used for leased negotiation, DHCP provides 7 types of messages. Refer to Supported Options
for DHCP Servers on page 102.
DHCP allocates temporary or permanent network IP addresses to clients. When a client requests the
use of an address for a time interval, the DHCP server guarantees not to reallocate that address within
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 85
53-1003087-04
Page 86

Configuration notes for DHCP servers
the requested time and tries to return the same network address each time the client makes a request.
The period of time for which a network address is allocated to a client is called a lease. The client may
extend the lease through subsequent requests. When the client is done with the address, they can
release the address back to the server. By asking for an indefinite lease, clients may receive a
permanent assignment.
In some environments, it may be necessary to reassign network addresses due to exhaustion of the
available address pool. In this case, the allocation mechanism reuses addresses with expired leases.
Configuration notes for DHCP servers
• DHCP server is supported in the Layer 2 and Layer 3 software images.
• In the event of a controlled or forced switchover, a DHCP client will request from the DHCP server
the same IP address and lease assignment that it had before the switchover. After the switchover,
the DHCP Server feature will be automatically re-initialized on the new active controller or
management module.
• For DHCP client hitless support in an IronStack, the stack mac command must be used to
configure the IronStack MAC address, so that the MAC address does not change in the event of a
switchover or failover. If stack mac is not configured, the MAC address/IP address pair assigned to
a DHCP client will not match after a switchover or failover. Furthermore, in the Layer 3 router
image, if the stack mac configuration is changed or removed and the management port has a
dynamic IP address, when a DHCP client tries to renew its lease from the DHCP server, the DHCP
server will assign a different IP address.
• If any address from the configured DHCP pool is used, for example by the DHCP server, TFTP
server, etc., you must exclude the address from the network pool. For configuration instructions,
refer to Specifying addresses to exclude from the address pool on page 93.
• Ensure that DHCP clients do not send DHCP request packets with Maximum Transmission Unit
(MTU) larger than 1500 bytes. Brocade devices do not support DHCP packets with MTU larger than
1500 bytes.
DHCP Option 82 support
The DHCP relay agent information option (DHCP option 82) enables a DHCP relay agent to include
information about itself when forwarding client-originated DHCP packets to a DHCP server. The DHCP
server uses this information to implement IP address or other parameter-assignment policies.
In a metropolitan Ethernet-access environment, the DHCP server can centrally manage IP address
assignments for a large number of subscribers. If DHCP option 82 is disabled, a DHCP policy can only
be applied per subnet, rather than per physical port. When DCHP option 82 is enabled, a subscriber is
identified by the physical port through which it connects to the network.
DHCP Server options
A FastIron configured as a DHCP server can support up to 1000 DHCP clients, offering them the
following options:
• NetBIOS over TCP/IP Name Server - Specifies a list of RFC1001/1002 NBNS name servers listed
in order of preference.
• Domain Name Server - Specifies a list of Domain Name System (RFC 1035) name servers
available to the client. Servers are listed in order of preference.
• Domain Name - Specifies the domain name the client should use when resolving hostnames using
the Domain Name system.
• Router Option - specifies a list of IP addresses for routers on the client subnet. Routers are listed
in order of preference.
• Subnet Mask - Specifies the client subnet mask (per RFC950).
86 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 87

Configuring DHCP Server on a device
• Vendor Specific Information - Allows clients and servers to exchange vendor-specific information.
• Boot File - Specifies a boot image to be used by the client
• Next Bootstrap Server - Configures the IP address of the next server to be used for startup by the
client.
• TFTP Server - Configures the address or name of the TFTP server available to the client.
A DHCP server assigns and manages IPv4 addresses from multiple address pools, using dynamic
address allocation. The DHCP server also contains the relay agent to forward DHCP broadcast
messages to network segments that do not support these types of messages.
FIGURE 7 DHCP Server configuration flow chart
Configuring DHCP Server on a device
Perform the following steps to configure the DHCP Server feature on your FastIron device:
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 87
53-1003087-04
Page 88

Default DHCP server settings
1. Enable DHCP Server by entering a command similar to the following.
device(config)# ip dhcp-server enable
2. Create a DHCP Server address pool by entering a command similar to the following.
device(config)# ip dhcp-server pool cabo
3. Configure the DHCP Server address pool by entering commands similar to the following.
device(config-dhcp-cabo)# network 172.16.1.0/24
device(config-dhcp-cabo)# domain-name brocade.com
device(config-dhcp-cabo)# dns-server 172.16.1.2 172.16.1.3
device(config-dhcp-cabo)# netbios-name-server 172.16.1.2
device(config-dhcp-cabo)# lease 0 0 5
4. To disable DHCP, enter a command similar to the following.
device(config)# no ip dhcp-server enable
The following sections describe the default DHCP settings, CLI commands and the options you can
configure for the DHCP Server feature.
Default DHCP server settings
DHCP server default settingsTABLE 9
Parameter Default Value
DHCP server Disabled
Lease database expiration time 86400 seconds
The duration of the lease for an assigned IP address 43200 seconds (one day)
Maximum lease database expiration time 86400 seconds
DHCP server with option 82 Disabled
DHCP server unknown circuit-ID for Option 82 Permit range lookup
IP distribution mechanism Linear
DHCP server CLI commands
DHCP server optional parameters commandsTABLE 10
Command Description
dbexpire Specifies how long, in seconds, the DHCP server should wait before aborting a
database transfer
option domain-name Specifies the domain name for the DHCP clients.
option domain-name-servers Specifies the Domain Name System (DNS) IP servers that are available to the
88 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
DHCP clients.
53-1003087-04
Page 89

DHCP server optional parameters commands (Continued)TABLE 10
Command Description
IP Configuration
option merit-dump Specifies the path name of a file into which the client’s core image should be
option root-path Specifies the name of the path that contains the client’s root filesystem in NFS
option router Adds the default router and gateway for the DHCP clients.
option subnet-mask Defines the subnet mask for the network.
option broadcast-address Defines a broadcast address for the network.
option wins-server Defines the NetBIOS Windows Internet Naming Service (WINS) name servers that
option log-servers Defines a list of log servers available to the client.
option bootstrap-server Specifies the IP address of the bootstrap server (the command fills the "siaddr"
placed in the event that the client crashes (the DHCP application issues an
exception in case of errors such as division by zero).
notation.
are available to Microsoft DHCP clients.
field in the DHCP packet).
DHCP Server CLI commands TABLE 11
Command Description
ip dhcp-server arp-pingtimeout sec
Specifies the time (in seconds) the server will wait for a response to an arp-ping
packet before deleting the client from the binding database. The minimum
setting is 5 seconds and the maximum time is 30 seconds.
NOTE
Do not alter the default value unless it is necessary. Increasing the value of this
timer may increase the time to get console access after a reboot.
clear ip dhcp-server binding Deletes a specific, or all leases from the binding database.
ip dhcp-server enable Enables the DHCP server feature.
no ip dhcp-server mgmt Disables DHCP server on the management port.
ip dhcp-server pool name Switches to pool configuration mode (config-dhcp-name# prompt) and creates
ip dhcp-server relay-agentecho enable
ip dhcp-server server-id Specifies the IP address of the selected DHCP server.
show ip dhcp-server binding Displays a specific lease entry, or all lease entries.
show ip dhcp-server addresspool
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 89
53-1003087-04
an address pool.
Enables relay agent echo (Option 82).
Displays a specific address pool or all address pools.
Page 90

Removing DHCP leases
DHCP Server CLI commands (Continued)TABLE 11
Command Description
show ip dhcp-server flash Displays the lease binding database that is stored in flash memory.
show ip dhcp-server summary Displays a summary of active leases, deployed address pools, undeployed
bootfile name Specifies a boot image to be used by the client.
deploy Deploys an address pool configuration to the server.
dhcp-default-router Specifies the IP address of the default router or routers for a client.
dns-server Specifies the IP addresses of a DNS server or servers available to the client.
domain-name Configures the domain name for the client.
lease Specifies the lease duration for an address pool. The default is a one-day
excluded-address Specifies an address or range of addresses to be excluded from the address
netbios-name-server Specifies the IP address of a NetBIOS WINS server or servers that are
network Configures the subnet network and mask of the DHCP address pool.
next-bootstrap-server Configures the IP address of the next server to be used for startup by the client.
tftp-server Configures the address or name of the TFTP server available to the client.
address pools, and server uptime.
lease.
pool.
available to Microsoft DHCP clients.
vendor-class Specifies the vendor type and configuration value for the DHCP client.
Removing DHCP leases
The clear ip dhcp-server binding command can be used to delete a specific lease, or all lease
entries from the lease binding database.
device(config)# clear ip dhcp-server binding *
Syntax: clear ip dhcp-server binding { address | * }
• address - The IP address to be deleted
• The wildcard ( *) clears all IP addresses
Enabling DHCP Server
The ip dhcp-server enable command enables DHCP Server, which is disabled by default.
Syntax: [no] ip dhcp-server enable
The no version of this command disables DHCP Server.
90 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 91

Disabling DHCP Server on the management port
Disabling DHCP Server on the management port
By default, when DHCP Server is enabled, it responds to DHCP client requests received on the
management port. If desired, you can prevent the response to DHCP client requests received on the
management port, by disabling DHCP Server support on the port. When disabled, DHCP client requests
that are received on the management port are silently discarded.
To disable DHCP Server on the management port, enter the following command at the global
configuration level of the CLI.
device(config)# no ip dhcp-server mgmt
To re-enable DHCP Server on the management port after it has been disabled, enter the ip dhcpserver mgmt command:
device(config)# ip dhcp-server mgmt
Syntax: [no] ip dhcp-server mgmt
Setting the wait time for ARP-ping response
At startup, the server reconciles the lease-binding database by sending an ARP-ping packet out to
every client. If there is no response to the ARP-ping packet within a set amount of time (set in seconds),
the server deletes the client from the lease-binding database. The minimum setting is 5 seconds and
the maximum is 30 seconds.
Syntax: ip dhcp-server arp-ping-timeout num
• num - The number of seconds to wait for a response to an ARP-ping packet.
NOTE
Do not alter the default value unless it is necessary. Increasing the value of this timer may increase the
time to get console access after a reboot.
Creating an address pool
The ip dhcp-server pool command puts you in pool configuration mode, and allows you to create an
address pool.
device(config)# ip dhcp-server pool
device(config-dhcp-name)# ip dhcp-server pool monterey
device(config-dhcp-monterey)#
These commands create an address pool named monterey.
Syntax: ip dhcp-server pool name
Configuration notes for creating an address pool
• If the DHCP server address is part of a configured DHCP address pool, you must exclude the DHCP
server address from the network pool. Refer to Specifying addresses to exclude from the address
pool on page 93.
• While in DHCP server pool configuration mode, the system will place the DHCP server pool in
pending mode and the DHCP server will not use the address pool to distribute information to clients.
To activate the pool, use the deploy command. Refer to Deploying an address pool configuration to
the server on page 92.
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 91
53-1003087-04
Page 92

Enabling relay agent echo (Option 82)
Enabling relay agent echo (Option 82)
The ip dhcp-server relay-agent-echo enable command activates DHCP Option 82, and enables the
DHCP server to echo relay agent information in all replies.
device(config)# ip dhcp-server relay-agent-echo enable
Syntax: ip dhcp-server relay-agent-echo enable
Configuring the IP address of the DHCP server
The ip dhcp-server command specifies the IP address of the selected DHCP server, as shown in this
example:
device(config)# ip dhcp-server 10.1.1.144
Syntax: ip dhcp-server server-identifier
• server-identifier - The IP address of the DHCP server
This command assigns an IP address to the selected DHCP server.
Configuring the boot image
The bootfile command specifies a boot image name to be used by the DHCP client.
device(config-dhcp-cabo)# bootfile foxhound
In this example, the DHCP client should use the boot image called "foxhound".
Syntax: bootfile name
Deploying an address pool configuration to the server
The deploy command sends an address pool configuration to the DHCP server.
device(config-dhcp-cabo)# deploy
Syntax: deploy
Specifying default routers available to the client
The dhcp-default-router command specifies the ip addresses of the default routers for a client.
Syntax: dhcp-default-router address [address, address]
Specifying DNS servers available to the client
The dns-server command specifies DNS servers that are available to DHCP clients.
device(config-dhcp-cabo)# dns-server 10.2.1.143, 10.2.2.142
Syntax: dns-server address [ address, address ]
92 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 93

Configuring the domain name for the client
Configuring the domain name for the client
The domain-name command configures the domain name for the client.
device(config-dhcp-cabo)# domain-name sierra
Syntax: domain-name domain
Configuring the lease duration for the address pool
The lease command specifies the lease duration for the address pool. The default is a one-day lease.
device(config-dhcp-cabo)# lease 1 4 32
In this example, the lease duration has been set to one day, four hours, and 32 minutes. You can set a
lease duration for just days, just hours, or just minutes, or any combination of the three.
Syntax: lease days hours minutes
Specifying addresses to exclude from the address pool
The excluded-address command specifies either a single address, or a range of addresses that are to
be excluded from the address pool.
device(config-dhcp-cabo)# excluded-address 10.2.3.44
Syntax: excluded-address { address | address-low address-high }
• address - Specifies a single address
• address-low address-high - Specifies a range of addresses
Configuring the NetBIOS server for DHCP clients
The netbios-name-server command specifies the IP address of a NetBIOS WINS server or servers
that are available to Microsoft DHCP clients.
device(config-dhcp-cabo)# netbios-name-server 192.168.1.55
Syntax: netbios-name-server address [ ,address2,address3 ]
Configuring the subnet and mask of a DHCP address pool
This network command configures the subnet network and mask of the DHCP address pool.
device(config-dhcp-cabo)# network 10.2.3.44/24
Syntax: network subnet/mask
Configuring a next-bootstrap server
The next-bootstrap-server command specifies the IP address of the next server the client should use
for boot up.
device(config-dhcp-cabo)# next-bootstrap-server 10.2.5.44
Syntax: next-bootstrap-server address
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 93
53-1003087-04
Page 94

Configuring the TFTP server
Configuring the TFTP server
The tftp-server command specifies the address or name of the TFTP server to be used by the DHCP
clients.
To configure a TFTP server by specifying its IP address, enter a command similar to the following.
device(config-dhcp-cabo)# tftp-server 10.7.5.48
To configure a TFTP server by specifying its server name, enter a command similar to the following.
device(config-dhcp-cabo)# tftp-server tftp.domain.com
Syntax:tftp-server { address | name server-name }
• address is the IP address of the TFTP server.
• name configures the TFTP server specified by server-name .
If DHCP options 66 (TFTP server name) and 150 (TFTP server IP address) are both configured, the
DHCP client ignores option 150 and tries to resolve the TFTP server name (option 66) using DNS.
Configuring a vendor type and configuration value for a DHCP client
The vendor-class command specifies the vendor-type and configuration value for a DHCP client.
device(config-dhcp-cabo)# vendor class ascii waikiki
Syntax: vendor-class { ascii | ip | hex } value
Displaying DHCP Server information
The following DHCP show commands can be entered from any level of the CLI.
Displaying active lease entries
The show ip dhcp-server binding command displays a specific active lease, or all active leases, as
shown in the following example:
device# show ip dhcp-server binding
The following output is displayed:
device# show ip dhcp-server binding
Bindings from all pools:
IP Address Client-ID/ Lease expiration Type
Hardware address
192.168.1.2 0000.005d.a440 0d:0h:29m:31s Automatic
192.168.1.3 0000.00e1.26c0 0d:0h:29m:38s Automatic
Syntax: show ip dhcp-server binding [ address ]
• address - Displays entries for this address only
show ip dhcp-server binding output descriptions TABLE 12
Field Description
IP address The IP addresses currently in the binding database
94 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 95

Displaying address-pool information
show ip dhcp-server binding output descriptions (Continued)TABLE 12
Field Description
Client ID/Hardware address The hardware address for the client
Lease expiration The time when this lease will expire
Type The type of lease
Displaying address-pool information
This show ip dhcp-server address-pool command displays information about a specific address pool,
or for all address pools.
device# show ip dhcp-server address-pools
Showing all address pool(s):
Pool Name: one
Time elapsed since last save: 0d:0h:6m:52s
Total number of active leases: 2
Address Pool State: active
IP Address Exclusions: 192.168.1.45
IP Address Exclusions: 192.168.1.99 192.168.1.103
Pool Configured Options:
bootfile: example.bin
dhcp-default-router: 192.168.1.1
dns-server: 192.168.1.100
domain-name: example.com
lease: 0 0 30
netbios-name-server: 192.168.1.101
network: 192.168.1.0 255.255.255.0
next-bootstrap-server: 192.168.1.102
tftp-server: 192.168.1.103
Syntax: show ip dhcp-server address-pool [ s ] [name]
• address-pools - If you enter address-pools, the display will show all address pools
• name - Displays information about a specific address pool
show ip dhcp-server address pools output descriptions TABLE 13
Field Description
Pool name The name of the address pool
Time elapsed since last save The time that has elapsed since the last save.
Total number of active leases The number of leases that are currently active.
Address pool state The state of the address pool (active or inactive).
IP Address exclusions IP addresses that are not included in the address pool
Pool configured options
bootfile The name of the bootfile
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 95
53-1003087-04
Page 96

Displaying lease-binding information in flash memory
show ip dhcp-server address pools output descriptions (Continued)TABLE 13
Field Description
dhcp-server-router The address of the DHCP server router
dns-server The address of the dns server
domain-name The name of the domain
lease The identifier for the lease
netbios-name server The address of the netbios name server
network The address of the network
next-bootstrap-server The address of the next-bootstrap server
tftp-server The address of the TFTP server
Displaying lease-binding information in flash memory
The show ip dhcp-server flash command displays the lease-binding database that is stored in flash
memory.
device# show ip dhcp-server flash
device# show ip dhcp-server flash
Address Pool Binding:
IP Address Client-ID/ Lease expiration Type
Hardware address
192.168.1.2 0000.005d.a440 0d:0h:18m:59s Automatic
192.168.1.3 0000.00e1.26c0 0d:0h:19m:8s Automatic
Syntax:show ip dhcp-server flash
show ip dhcp-server flash output descriptionsTABLE 14
Field Description
IP address The IP address of the flash memory lease-binding database
Client-ID/Hardware address The address of the client
Lease expiration The time when the lease will expire
Type The type of lease
96 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 97

Displaying summary DHCP server information
Displaying summary DHCP server information
The show ip dhcp-server summary command displays information about active leases, deployed
address-pools, undeployed address-pools, and server uptime.
device# show ip dhcp-server summary
DHCP Server Summary:
Total number of active leases: 2
Total number of deployed address-pools: 1
Total number of undeployed address-pools: 0
Server uptime: 0d:0h:8m:27s
Syntax: show ip dhcp-server summary
show ip dhcp-server summaryoutput descriptionsTABLE 15
Field Description
Total number of active leases Indicates the number of leases that are currently active
Total number of deployed address-pools The number of address pools currently in use.
Total number of undeployed address-pools The number of address-pools being held in reserve.
Server uptime The amount of time that the server has been active.
DHCP Server commandsTABLE 16
Command Description
option bootstrapfilename
default-lease-time
database tftp
database ftp
max-lease-time
option bootfile-name
Sets the name of the bootstrap file. The no form of this command removes the
name of the bootstrap file.
Specifies the duration of the lease for an IP address that is assigned from a
DHCP server to a DHCP client.
Defines the TFTP IP address server for storing the DHCP database, the name of
the stored file and the time period at which the stored database is synchronized
with the database on the device.
Defines the FTP IP address server for storing the DHCP database, the name of
the stored file and the time period at which the stored database is synchronized
with the database on the device.
Specifies the maximal duration of the leases in seconds.
Specifies the pathname of the boot file.
option tftp-server
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 97
53-1003087-04
Specifies the IP address of a TFTP server.
Page 98

DHCP Client-Based Auto-Configuration and Flash image update
DHCP Client-Based Auto-Configuration and Flash image update
NOTE
The DHCP Client-Based Auto-Configuration and Flash image update are platform independent and
have no differences in behavior or configuration across all platforms (FSX, FCX, and ICX).
DHCP Client-Based Auto-Configuration allows Layer 2 and Layer 3 devices to automatically obtain
leased IP addresses through a DHCP server, negotiate address lease renewal, and obtain flash image
and configuration files.
DHCP Client-Based Auto-Configuration occurs as follows.
1. The IP address validation and lease negotiation enables the DHCP client (a Brocade Layer 2 or
Layer 3 device) to automatically obtain and configure an IP address, as follows:
• ‐ One lease is granted for each Layer 2 device. if the device is configured with a static IP
address, the DHCP Auto-Configuration feature is automatically disabled.
‐ For a Layer 3 device, one leased address is granted (per device) to the interface that
first receives a response from the DHCP server.
2. If auto update is enabled, the TFTP flash image is downloaded and updated. The device compares
the filename of the requested flash image with the image stored in flash. If the filenames are
different, then the device will download the new image from a TFTP server, write the downloaded
image to flash, then reload the device or stack.
3. In the final step, TFTP configuration download and update, the device downloads a configuration
file from a TFTP server and saves it as the running configuration.
98 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
Page 99

Configuration notes and feature limitations for DHCP client-based auto-configuration
FIGURE 8 DHCP Client-Based Auto-Configuration
Configuration notes and feature limitations for DHCP client-based auto-configuration
• For Layer 3 devices, this feature is available for the default VLAN only. For Layer 2 devices, this
feature is available for default VLANs and management VLANs. This feature is not supported on
virtual interfaces (VEs), trunked ports, or LACP ports.
• Although the DHCP server may provide multiple addresses, only one IP address is installed at a
time.
• This feature is not supported together with DHCP snooping.
The following configuration rules apply to flash image update:
• To enable flash image update (ip dhcp-client auto-update enable command), also enable auto-
configuration (ip dhcp-client enable command).
• The image filename to be updated must have the extension .bin .
• The DHCP option 067 bootfile name will be used for image update if it has the extension .bin .
FastIron Ethernet Switch Layer 3 Routing Configuration Guide 99
53-1003087-04
Page 100

How DHCP Client-Based Auto-Configuration and Flash image update works
• The DHCP option 067 bootfile name will be used for configuration download if it does not have the
extension .bin .
• If the DHCP option 067 bootfile name is not configured or does not have the extension .bin , then
the auto-update image will not occur.
How DHCP Client-Based Auto-Configuration and Flash image update works
Auto-Configuration and Auto-update are enabled by default. To disable this feature, refer to Disabling
or re-enabling Auto-Configuration on page 103 and Disabling or re-enabling Auto-Update on page
103, respectively.
FIGURE 9 The DHCP Client-Based Auto-Configuration steps
100 FastIron Ethernet Switch Layer 3 Routing Configuration Guide
53-1003087-04
 Loading...
Loading...