VMware ESXI - 6.7 Instruction Manual

vSphere Security
17 APR 2018
VMware vSphere 6.7
VMware ESXi 6.7
vCenter Server 6.7

vSphere Security
You can find the most up-to-date technical documentation on the VMware website at:
https://docs.vmware.com/
If you have comments about this documentation, submit your feedback to
docfeedback@vmware.com
VMware, Inc.
3401 Hillview Ave.
Palo Alto, CA 94304
www.vmware.com
Copyright © 2009–2018 VMware, Inc. All rights reserved. Copyright and trademark information.
VMware, Inc. 2

Contents
About vSphere Security 7
Security in the vSphere Environment 9
1
Securing the ESXi Hypervisor 9
Securing vCenter Server Systems and Associated Services 11
Securing Virtual Machines 12
Securing the Virtual Networking Layer 13
Passwords in Your vSphere Environment 15
Security Best Practices and Resources 16
vSphere Permissions and User Management Tasks 18
2
Understanding Authorization in vSphere 19
Managing Permissions for vCenter Components 25
Global Permissions 28
Using Roles to Assign Privileges 31
Best Practices for Roles and Permissions 34
Required Privileges for Common Tasks 35
Securing ESXi Hosts 39
3
General ESXi Security Recommendations 39
Certificate Management for ESXi Hosts 51
Customizing Hosts with the Security Profile 67
Assigning Privileges for ESXi Hosts 83
Using Active Directory to Manage ESXi Users 86
Using vSphere Authentication Proxy 88
Configuring Smart Card Authentication for ESXi 96
Using the ESXi Shell 98
UEFI Secure Boot for ESXi Hosts 102
Securing ESXi Hosts with Trusted Platform Module 105
ESXi Log Files 107
VMware, Inc.
Securing vCenter Server Systems 110
4
vCenter Server Security Best Practices 110
Verify Thumbprints for Legacy ESXi Hosts 116
Verify that SSL Certificate Validation Over Network File Copy Is Enabled 117
Required Ports for vCenter Server and Platform Services Controller 118
Additional vCenter Server TCP and UDP Ports 123
3

vSphere Security
Securing Virtual Machines 126
5
Enable or Disable UEFI Secure Boot for a Virtual Machine 126
Limit Informational Messages From Virtual Machines to VMX Files 127
Prevent Virtual Disk Shrinking 128
Virtual Machine Security Best Practices 129
Virtual Machine Encryption 139
6
How vSphere Virtual Machine Encryption Protects Your Environment 140
vSphere Virtual Machine Encryption Components 142
Encryption Process Flow 143
Virtual Disk Encryption 145
Prerequisites and Required Privileges for Encryption Tasks 146
Encrypted vSphere vMotion 147
Encryption Best Practices, Caveats, and Interoperability 148
Use Encryption in Your vSphere Environment 154
7
Set up the Key Management Server Cluster 155
Create an Encryption Storage Policy 162
Enable Host Encryption Mode Explicitly 163
Disable Host Encryption Mode 164
Create an Encrypted Virtual Machine 164
Clone an Encrypted Virtual Machine 165
Encrypt an Existing Virtual Machine or Virtual Disk 166
Decrypt an Encrypted Virtual Machine or Virtual Disk 167
Change the Encryption Policy for Virtual Disks 169
Resolve Missing Key Issues 170
Unlock Locked Virtual Machines 172
Resolve ESXi Host Encryption Mode Issues 172
Re-Enable ESXi Host Encryption Mode 173
Set Key Management Server Certificate Expiration Threshold 174
vSphere Virtual Machine Encryption and Core Dumps 174
Securing Virtual Machines with Virtual Trusted Platform Module 179
8
Add a Virtual Trusted Platform Module to a Virtual Machine 181
Enable Virtual Trusted Platform Module for an Existing Virtual Machine 182
Remove Virtual Trusted Platform Module from a Virtual Machine 182
Identify Virtual Trusted Platform Enabled Virtual Machines 183
View vTPM Module Device Certificates 183
Export and Replace vTPM Module Device Certificates 184
VMware, Inc. 4

vSphere Security
Securing Windows Guest Operating Systems with Virtualization-based
9
Security 186
Virtualization-based Security Best Practices 186
Enable Virtualization-based Security on a Virtual Machine 187
Enable Virtualization-based Security on an Existing Virtual Machine 188
Enable Virtualization-based Security on the Guest Operating System 189
Disable Virtualization-based Security 190
Identify VBS-Enabled Virtual Machines 190
Securing vSphere Networking 192
10
Introduction to vSphere Network Security 192
Securing the Network With Firewalls 193
Secure the Physical Switch 197
Securing Standard Switch Ports with Security Policies 197
Securing vSphere Standard Switches 198
Standard Switch Protection and VLANs 200
Secure vSphere Distributed Switches and Distributed Port Groups 201
Securing Virtual Machines with VLANs 202
Creating Multiple Networks Within a Single ESXi Host 204
Internet Protocol Security 207
Ensure Proper SNMP Configuration 211
vSphere Networking Security Best Practices 211
Best Practices Involving Multiple vSphere Components 216
11
Synchronizing Clocks on the vSphere Network 216
Storage Security Best Practices 219
Verify That Sending Host Performance Data to Guests Is Disabled 223
Setting Timeouts for the ESXi Shell and vSphere Web Client 223
Managing TLS Protocol Configuration with the TLS Configurator Utility 225
12
Ports That Support Disabling TLS Versions 225
Enabling or Disabling TLS Versions in vSphere 227
Perform an Optional Manual Backup 227
Enable or Disable TLS Versions on vCenter Server Systems 229
Enable or Disable TLS Versions on ESXi Hosts 230
Enable or Disable TLS Versions on External Platform Services Controller Systems 232
Scan vCenter Server for Enabled TLS Protocols 233
Revert TLS Configuration Changes 234
Enable or Disable TLS Versions on vSphere Update Manager on Windows 236
Defined Privileges 240
13
Alarms Privileges 241
VMware, Inc. 5

vSphere Security
Auto Deploy and Image Profile Privileges 242
Certificates Privileges 243
Content Library Privileges 244
Cryptographic Operations Privileges 245
Datacenter Privileges 247
Datastore Privileges 247
Datastore Cluster Privileges 248
Distributed Switch Privileges 249
ESX Agent Manager Privileges 249
Extension Privileges 250
External Stats Provider Privileges 250
Folder Privileges 250
Global Privileges 251
Health Update Provider Privileges 252
Host CIM Privileges 252
Host Configuration Privileges 252
Host Inventory 253
Host Local Operations Privileges 254
Host vSphere Replication Privileges 255
Host Profile Privileges 255
Network Privileges 255
Performance Privileges 256
Permissions Privileges 256
Profile-driven Storage Privileges 257
Resource Privileges 257
Scheduled Task Privileges 258
Sessions Privileges 258
Storage Views Privileges 259
Tasks Privileges 259
Transfer Service Privileges 260
Virtual Machine Configuration Privileges 260
Virtual Machine Guest Operations Privileges 262
Virtual Machine Interaction Privileges 263
Virtual Machine Inventory Privileges 271
Virtual Machine Provisioning Privileges 272
Virtual Machine Service Configuration Privileges 273
Virtual Machine Snapshot Management Privileges 274
Virtual Machine vSphere Replication Privileges 274
dvPort Group Privileges 275
vApp Privileges 275
vServices Privileges 276
vSphere Tagging Privileges 277
VMware, Inc. 6
About vSphere Security
vSphere Security provides information about securing your vSphere® environment for VMware® vCenter
Server and VMware ESXi.
To help you protect your vSphere environment, this documentation describes available security features
and the measures that you can take to safeguard your environment from attack.
Table 1.
Topics Content Highlights
Permissions and User Management
Host Security Features
Virtual Machine Encryption
vSphere Security
Highlights
n
Permissions model (roles, groups, objects).
n
Creating custom roles.
n
Setting permissions.
n
Managing global permissions.
n
Lockdown mode and other security profile features.
n
Host smart card authentication.
n
vSphere Authentication Proxy.
n
UEFI Secure Boot.
n
Trusted Platform Module (TPM).
n
How does VM encryption work?
n
KMS setup.
n
Encrypting and decrypting VMs.
n
Troubleshooting and best practices.
®
Guest OS Security
n
Virtual Trusted Platform Module (vTPM).
n
Virtualization Based Security (VBS).
Managing TLS Protocol Configuration Changing TLS protocol configuration using a command-line
utility.
Security Best Practices and Hardening Best practices and advice from VMware security experts.
n
vCenter Server security
n
Host security
n
Virtual machine security
n
Networking security
vSphere Privileges Complete listing of all vSphere privileges supported in this
release.
VMware, Inc. 7
vSphere Security
Related Documentation
A companion document, Platform Services Controller Administration, explains how you can use the
Platform Services Controller services, for example, to manage authentication with vCenter Single Sign-On
and to manage certificates in your vSphere environment.
In addition to these documents, VMware publishes a Hardening Guide for each release of vSphere,
accessible at http://www.vmware.com/security/hardening-guides.html. The Hardening Guide is a
spreadsheet with entries for different potential security issues. It includes items for three different risk
profiles. This vSphere Security document does not include information for Risk Profile 1 (highest security
environment such as top-secret government).
Intended Audience
This information is for experienced Windows or Linux system administrators who are familiar with virtual
machine technology and data center operations.
vSphere Web Client and vSphere Client (HTML5-Based
Client)
Task instructions in this guide are based on the vSphere Web Client. You can also perform most of the
tasks in this guide by using the vSphere Client. The vSphere Client user interface terminology, topology,
and workflow are closely aligned with the same aspects and elements of the vSphere Web Client user
interface. You can apply the vSphere Web Client instructions to the vSphere Client unless otherwise
instructed.
Note In vSphere 6.7, most of the vSphere Web Client functionality is implemented in the vSphere Client.
For an up-to-date list of the unsupported functionality, see Functionality Updates for the vSphere Client.
VMware, Inc. 8

Security in the vSphere
Environment 1
The components of a vSphere environment are secured out of the box by several features such as
authentication, authorization, a firewall on each ESXi host, and so on. You can modify the default setup in
many ways. For example, you can set permissions on vCenter objects, open firewall ports, or change the
default certificates. You can take security measures for different objects in the vCenter object hierarchy,
for example, vCenter Server systems, ESXi hosts, virtual machines, and network and storage objects.
A high-level overview of different areas of vSphere that require attention helps you plan your security
strategy. You also benefit from other vSphere Security resources on the VMware Web site.
This chapter includes the following topics:
n
Securing the ESXi Hypervisor
n
Securing vCenter Server Systems and Associated Services
n
Securing Virtual Machines
n
Securing the Virtual Networking Layer
n
Passwords in Your vSphere Environment
n
Security Best Practices and Resources
Securing the ESXi Hypervisor
The ESXi hypervisor is secured out of the box. You can further protect ESXi hosts by using lockdown
mode and other built-in features. For consistency, you can set up a reference host and keep all hosts in
sync with the host profile of the reference host. You can also protect your environment by performing
scripted management, which ensures that changes apply to all hosts.
You can enhance protection of ESXi hosts that are managed by vCenter Server with the following actions.
See the Security of the VMware vSphere Hypervisor white paper for background and details.
Limit ESXi access By default, the ESXi Shell and SSH services are not running and only the
root user can log in to the Direct Console User Interface (DCUI). If you
decide to enable ESXi or SSH access, you can set timeouts to limit the risk
of unauthorized access.
VMware, Inc. 9

vSphere Security
Users who can access the ESXi host must have permissions to manage
the host. You set permissions on the host object from the vCenter Server
system that manages the host.
Use named users and
least privilege
Minimize the number of
open ESXi firewall
ports
Automate ESXi host
management
By default, the root user can perform many tasks. Do not allow
administrators to log in to the ESXi host using the root user account.
Instead, create named administrator users from vCenter Server and assign
those users the Administrator role. You can also assign those users a
custom role. See Create a Custom Role.
If you manage users directly on the host, role management options are
limited. See the vSphere Single Host Management - VMware Host Client
documentation.
By default, firewall ports on your ESXi host are opened only when you start
a corresponding service. You can use the vSphere Web Client or ESXCLI
or PowerCLI commands to check and manage firewall port status.
See ESXi Firewall Configuration.
Because it is often important that different hosts in the same data center
are in sync, use scripted installation or vSphere Auto Deploy to provision
hosts. You can manage the hosts using scripts. Host profiles are an
alternative to scripted management. You set up a reference host, export the
host profile, and apply the host profile to all hosts. You can apply the host
profile directly or as part of provisioning with Auto Deploy.
Take advantage of
lockdown mode
Check VIB package
integrity
See Use Scripts to Manage Host Configuration Settings and see the
vCenter Server Installation and Setup documentation for information about
vSphere Auto Deploy.
In lockdown mode, ESXi hosts can be accessed only through
vCenter Server by default. Starting with vSphere 6.0, you can select strict
lockdown mode or normal lockdown mode. You can define Exception Users
to allow direct access to service accounts such as backup agents.
See Lockdown Mode.
Each VIB package has an associated acceptance level. You can add a VIB
to an ESXi host only if the VIB acceptance level is the same or better than
the acceptance level of the host. You cannot add a CommunitySupported or
PartnerSupported VIB to a host unless you explicitly change the host's
acceptance level.
See Manage the Acceptance Levels of Hosts and VIBs.
VMware, Inc. 10

vSphere Security
Manage ESXi
certificates
Consider Smart card
authentication
Consider ESXi account
lockout
In vSphere 6.0 and later, the VMware Certificate Authority (VMCA)
provisions each ESXi host with a signed certificate that has VMCA as the
root certificate authority by default. If company policy requires it, you can
replace the existing certificates with certificates that are signed by a third-
party or an enterprise CA.
See Certificate Management for ESXi Hosts.
Starting with vSphere 6.0, ESXi supports the use of smart card
authentication instead of user name and password authentication. For
additional security, you can configure smart card authentication. Two-factor
authentication is also supported for vCenter Server.
See Configuring Smart Card Authentication for ESXi.
Starting with vSphere 6.0, account locking is supported for access through
SSH and through the vSphere Web Services SDK. By default, a maximum
of 10 failed attempts is allowed before the account is locked. The account is
unlocked after two minutes by default.
Note The Direct Console Interface (DCUI) and the ESXi Shell do not
support account lockout.
See ESXi Passwords and Account Lockout.
Security considerations for standalone hosts are similar, though the management tasks might differ. See
the vSphere Single Host Management - VMware Host Client documentation.
Securing vCenter Server Systems and Associated Services
Your vCenter Server system and associated services are protected by authentication through vCenter
Single Sign-On and by authorization through the vCenter Server permissions model. You can modify the
default behavior, and you can take additional steps to limit access to your environment.
As you protect your vSphere environment, consider that all services that are associated with the
vCenter Server instances must be protected. In some environments, you might protect several
vCenter Server instances and one or more Platform Services Controller instances.
Harden all vCenter host
machines
Learn about the
vCenter certificate
model
The first step in protecting your vCenter environment is hardening each
machine on which vCenter Server or an associated service runs. Similar
considerations apply to a physical machine or a virtual machine. Always
install the latest security patches for your operating system and follow
industry standard best practices to protect the host machine.
By default, the VMware Certificate Authority provisions each ESXi host,
each machine in the environment, and each solution user with a certificate
signed by VMCA. The environment works out of the box, but if company
policy requires it, you can change the default behavior. See the Platform
Services Controller Administration documentation for details.
VMware, Inc. 11

vSphere Security
For additional protection, explicitly remove expired or revoked certificates
and failed installations.
Configure vCenter
Single Sign-On
Assign roles to named
users or groups
Set up NTP Set up NTP for each node in your environment. The certificate
vCenter Server and associated services are protected by the vCenter
Single Sign-On authentication framework. When you first install the
software, you specify a password for the administrator of the vCenter
Single Sign-On domain, administrator@vsphere.local by default. Only that
domain is initially available as an identity source. You can add other identity
sources, either Active Directory or LDAP, and set a default identity source.
Going forward, users who can authenticate to one of those identity sources
can view objects and perform tasks if they are authorized to do so. See the
Platform Services Controller Administration documentation for details.
For better logging, associate each permission that you give on an object
with a named user or group and a predefined role or custom role. The
vSphere 6.0 permissions model allows great flexibility through multiple
ways of authorizing users or groups. See Understanding Authorization in
vSphere and Required Privileges for Common Tasks.
Restrict administrator privileges and the use of the administrator role. If
possible, do not use the anonymous Administrator user.
infrastructure requires an accurate time stamp and does not work correctly
if the nodes are out of sync.
See Synchronizing Clocks on the vSphere Network.
Securing Virtual Machines
To secure your VMs, keep the guest operating systems patched and protect your environment just as you
protect your physical machine. Consider disabling unnecessary functionality, minimize the use of the VM
console, and follow other best practices.
Protect the guest
operating system
Disable unnecessary
functionality
To protect your guest operating system, make sure that it uses the most
recent patches and, if appropriate, anti-spyware and anti-malware
applications. See the documentation from your guest operating system
vendor and, potentially, other information available in books or on the
Internet for that operating system.
Check that unnecessary functionality is disabled to minimize potential
points of attack. Many of the features that are used infrequently are
disabled by default. Remove unnecessary hardware and disable certain
features such as host-guest filesystem (HGFS) or copy and paste between
the VM and a remote console.
See Disable Unnecessary Functions Inside Virtual Machines.
VMware, Inc. 12

vSphere Security
Use templates and
scripted management
Minimize use of the
virtual machine console
Consider UEFI secure
boot
VM templates enable you to set up the operating system so that it meets
your requirements, and to create other VMs with the same settings.
If you want to change VM settings after initial deployment, consider using
scripts, for example, PowerCLI. This documentation explains how to
perform tasks using the GUI. Consider using scripts instead of the GUI to
keep your environment consistent. In large environments, you can group
VMs into folders to optimize scripting.
For information on templates, see Use Templates to Deploy Virtual
Machines and the vSphere Virtual Machine Administration. For information
on PowerCLI, see the VMware PowerCLI documentation.
The virtual machine console provides the same function for a VM that a
monitor on a physical server provides. Users with access to a virtual
machine console have access to VM power management and to removable
device connectivity controls. As a result, virtual machine console access
might allow a malicious attack on a VM.
Starting with vSphere 6.5, you can configure your VM to use UEFI boot. If
the operating system supports secure UEFI boot, you can select that option
for your VMs for additional security. See Enable or Disable UEFI Secure
Boot for a Virtual Machine.
Securing the Virtual Networking Layer
The virtual networking layer includes virtual network adapters, virtual switches, distributed virtual
switches, and ports and port groups. ESXi relies on the virtual networking layer to support
communications between VMs and their users. In addition, ESXi uses the virtual networking layer to
communicate with iSCSI SANs, NAS storage, and so on.
vSphere includes the full array of features necessary for a secure networking infrastructure. You can
secure each element of the infrastructure, such as virtual switches, distributed virtual switches, and virtual
network adapters, separately. In addition, consider the following guidelines, discussed in more detail in
Chapter 10 Securing vSphere Networking.
Isolate network traffic Isolation of network traffic is essential to a secure ESXi environment.
Different networks require different access and level of isolation. A
management network isolates client traffic, command-line interface (CLI) or
API traffic, and third-party software traffic from normal traffic. Ensure that
the management network is accessible only by system, network, and
security administrators.
VMware, Inc. 13

vSphere Security
See ESXi Networking Security Recommendations.
Use firewalls to secure
virtual network
elements
You can open and close firewall ports and secure each element in the
virtual network separately. For ESXi hosts, firewall rules associate services
with corresponding firewalls and can open and close the firewall according
to the status of the service. See ESXi Firewall Configuration.
You can also open ports on Platform Services Controller and
vCenter Server instances explicitly. See Required Ports for vCenter Server
and Platform Services Controller and Additional vCenter Server TCP and
UDP Ports.
Consider network
security policies
Network security policies provide protection of traffic against MAC address
impersonation and unwanted port scanning. The security policy of a
standard or distributed switch is implemented in Layer 2 (Data Link Layer)
of the network protocol stack. The three elements of the security policy are
promiscuous mode, MAC address changes, and forged transmits.
See the vSphere Networking documentation for instructions.
Secure VM networking The methods that you use to secure VM networking depend on several
factors, including:
n
The guest operating system that is installed.
n
Whether the VMs operate in a trusted environment
Consider VLANs to
protect your
environment
Secure connections to
virtualized storage
Virtual switches and distributed virtual switches provide significant
protection when used with other common security practices, such as
installing firewalls.
See Chapter 10 Securing vSphere Networking.
ESXi supports IEEE 802.1q VLANs. VLANs let you segment a physical
network. You can use VLANs to further protect the VM network or storage
configuration. When you use VLANS, two VMs on the same physical
network cannot send packets to or receive packets from each other unless
they are on the same VLAN.
See Securing Virtual Machines with VLANs.
A VM stores operating system files, program files, and other data on a
virtual disk. Each virtual disk appears to the VM as a SCSI drive that is
connected to a SCSI controller. A VM is isolated from storage details and
cannot access the information about the LUN where its virtual disk resides.
The Virtual Machine File System (VMFS) is a distributed file system and
volume manager that presents virtual volumes to the ESXi host. You are
responsible for securing the connection to storage. For example, if you are
using iSCSI storage, you can set up your environment to use CHAP. If
required by company policy, you can set up mutual CHAP. Use
vSphere Web Client or CLIs to set up CHAP.
VMware, Inc. 14

vSphere Security
See Storage Security Best Practices.
Evaluate the use of
IPSec
In addition, evaluate whether VMware NSX for vSphere is a good solution for securing the networking
layer in your environment.
ESXi supports IPSec over IPv6. You cannot use IPSec over IPv4.
See Internet Protocol Security.
Passwords in Your vSphere Environment
Password restrictions, password expiration, and account lockout in your vSphere environment depend on
the system that the user targets, who the user is, and how policies are set.
ESXi Passwords
ESXi password restrictions are determined by the Linux PAM module pam_passwdqc. See the Linux
manpage for pam_passwdqc and see ESXi Passwords and Account Lockout.
Passwords for vCenter Server and Other vCenter Services
vCenter Single Sign-On manages authentication for all users who log in to vCenter Server and other
vCenter services. The password restrictions, password expiration, and account lockout depend on the
user's domain and on who the user is.
vCenter Single Sign-On
Administrator
Other Users of the
vCenter Single Sign-On
Domain
Other Users Password restrictions, password expiration, and account lockout for all
The password for the vCenter Single Sign-On administrator is
administrator@vsphere.local by default or administrator@mydomain if you
specified a different domain during installation. This password does not
expire. In all other regards, the password must follow the restrictions that
are set in the vCenter Single Sign-On password policy. See Platform
Services Controller Administration for details.
If you forget the password for this user, search the VMware Knowledge
Base system for information on resetting this password. The reset requires
additional privileges such as root access to the vCenter Server system.
Passwords for other vsphere.local users, or users of the domain that you
specified during installation, must follow the restrictions that are set by the
vCenter Single Sign-On password policy and lockout policy. See Platform
Services Controller Administration for details. These passwords expire after
90 days by default. Administrators can change the expiration as part of the
password policy.
If you forget your vsphere.local password, an administrator user can reset
the password using the dir-cli command.
other users are determined by the domain (identity source) to which the
user can authenticate.
VMware, Inc. 15

vSphere Security
vCenter Single Sign-On supports one default identity source. Users can log
in to the corresponding domain with the vSphere Web Client with just their
user names. If users want to log in to a non-default domain, they can
include the domain name, that is, specify user@domain or domain\user.
The domain password parameters apply to each domain.
Passwords for vCenter Server Appliance Direct Console User
Interface Users
The vCenter Server Appliance is a preconfigured Linux-based virtual machine that is optimized for
running vCenter Server and the associated services on Linux.
When you deploy the vCenter Server Appliance, you specify these passwords.
n
Password for the root user of the appliance Linux operating system.
n
Password for the administrator of the vCenter Single Sign-On domain, administrator@vsphere.local
by default.
You can change the root user password and perform other vCenter Server Appliance local user
management tasks from the appliance console. See vCenter Server Appliance Configuration.
Security Best Practices and Resources
If you follow best practices, your ESXi and vCenter Server can be as secure as or even more secure than
an environment that does not include virtualization.
This manual includes best practices for the different components of your vSphere infrastructure.
Table 1‑1. Security Best Practices
vSphere component Resource
ESXi host Chapter 3 Securing ESXi Hosts
vCenter Server system vCenter Server Security Best Practices
Virtual machine Virtual Machine Security Best Practices
vSphere Networking vSphere Networking Security Best Practices
This manual is only one of the sources you need to ensure a secure environment.
VMware security resources, including security alerts and downloads, are available on the Web.
VMware, Inc. 16
vSphere Security
Table 1‑2. VMware Security Resources on the Web
Topic Resource
VMware security policy, up-to-date security alerts,
security downloads, and focus discussions of
security topics.
Corporate security response policy http://www.vmware.com/support/policies/security_response.html
Third-party software support policy http://www.vmware.com/support/policies/
Compliance and security standards, as well as
partner solutions and in-depth content about
virtualization and compliance
Information on security certifications and validations
such as CCEVS and FIPS for different versions of
the components of vSphere.
http://www.vmware.com/go/security
VMware is committed to helping you maintain a secure environment. Security
issues are corrected in a timely manner. The VMware Security Response
Policy states our commitment to resolve possible vulnerabilities in our
products.
VMware supports a variety of storage systems, software agents such as
backup agents, system management agents, and so forth. You can find lists
of agents, tools, and other software that supports ESXi by searching
http://www.vmware.com/vmtn/resources/ for ESXi compatibility guides.
The industry offers more products and configurations than VMware can test.
If VMware does not list a product or configuration in a compatibility guide,
Technical Support will attempt to help you with any problems, but cannot
guarantee that the product or configuration can be used. Always evaluate
security risks for unsupported products or configurations carefully.
http://www.vmware.com/go/compliance
https://www.vmware.com/support/support-resources/certifications.html
Hardening guides for different versions of vSphere
and other VMware products.
Security of the VMware vSphere Hypervisor white
paper
https://www.vmware.com/support/support-resources/hardening-guides.html
http://www.vmware.com/files/pdf/techpaper/vmw-wp-secrty-vsphr-hyprvsr-
uslet-101.pdf
VMware, Inc. 17

vSphere Permissions and User
Management Tasks 2
Authentication and authorization govern access. vCenter Single Sign-On supports authentication, which
means it determines whether a user can access vSphere components at all. Each user must also be
authorized to view or manipulate vSphere objects.
vSphere supports several different authorization mechanisms, discussed in Understanding Authorization
in vSphere. The focus of the information in this section is how vCenter Server permission model works
and how to perform user management tasks.
vCenter Server allows fine-grained control over authorization with permissions and roles. When you
assign a permission to an object in the vCenter Server object hierarchy, you specify which user or group
has which privileges on that object. To specify the privileges, you use roles, which are sets of privileges.
Initially, only the administrator user for the vCenter Single Sign-On domain, administrator@vsphere.local
by default, is authorized to log in to the vCenter Server system. That user can then proceed as follows:
1 Add an identity source in which users and groups are defined to vCenter Single Sign-On. See the
Platform Services Controller Administration documentation.
2 Give privileges to a user or group by selecting an object such as a virtual machine or a
vCenter Server system and assigning a role on that object for the user or group.
Roles, Privileges, and Permissions
(http://link.brightcove.com/services/player/bcpid2296383276001?
bctid=ref:video_roles_privileges_permissions_vsphere_web_client)
This chapter includes the following topics:
n
Understanding Authorization in vSphere
n
Managing Permissions for vCenter Components
n
Global Permissions
n
Using Roles to Assign Privileges
n
Best Practices for Roles and Permissions
n
Required Privileges for Common Tasks
VMware, Inc.
18

vSphere Security
Understanding Authorization in vSphere
vSphere supports several models with fine-grained control for determining whether a user is allowed to
perform a task. vCenter Single Sign-On uses group membership in a vCenter Single Sign-On group to
decide what you are allowed to do. Your role on an object or your global permission determines whether
you're allowed to perform other tasks in vSphere.
Authorization Overview
vSphere 6.0 and later allows privileged users to give other users permissions to perform tasks. You can
use global permissions, or you can use local vCenter Server permissions to authorize other users for
individual vCenter Server instances.
vCenter Server
Permissions
Global Permissions Global permissions are applied to a global root object that spans solutions.
Group Membership in
vCenter Single Sign-On
Groups
ESXi Local Host
Permissions
The permission model for vCenter Server systems relies on assigning
permissions to objects in the object hierarchy. Each permission gives one
user or group a set of privileges, that is, a role for a selected object. For
example, you can select a virtual machine and select Add Permission
assign a role to a group of users in a domain that you select. That role
gives those users the corresponding privileges on the VM.
For example, if both vCenter Server and vRealize Orchestrator are
installed, you can use global permissions. For example, you can give a
group of users Read permissions to all objects in both object hierarchies.
Global permissions are replicated across the vsphere.local domain. Global
permissions do not provide authorization for services managed through
vsphere.local groups. See Global Permissions.
Members of a vsphere.local group can perform certain tasks. For example,
you can perform license management if you are a member of the
LicenseService.Administrators group. See the Platform Services Controller
Administration documentation.
If you are managing a standalone ESXi host that is not managed by a
vCenter Server system, you can assign one of the predefined roles to
users. See the vSphere Single Host Management - VMware Host Client
documentation.
For managed hosts, assign roles to the ESXi host object in the
vCenter Server inventory.
VMware, Inc. 19
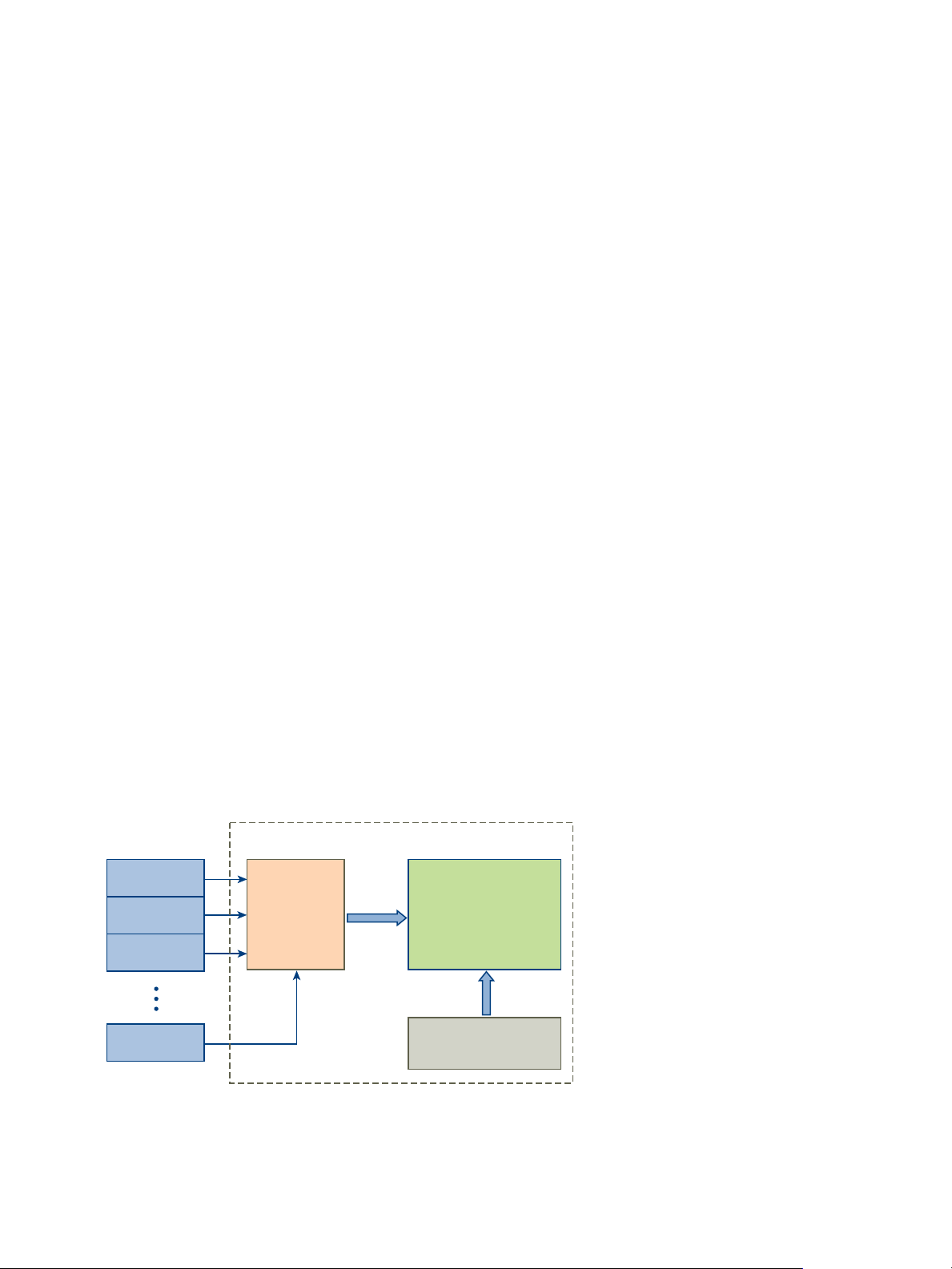
Permission
vSphere object
User or group
Role
Privilege
Privilege
Privilege
Privilege
vSphere Security
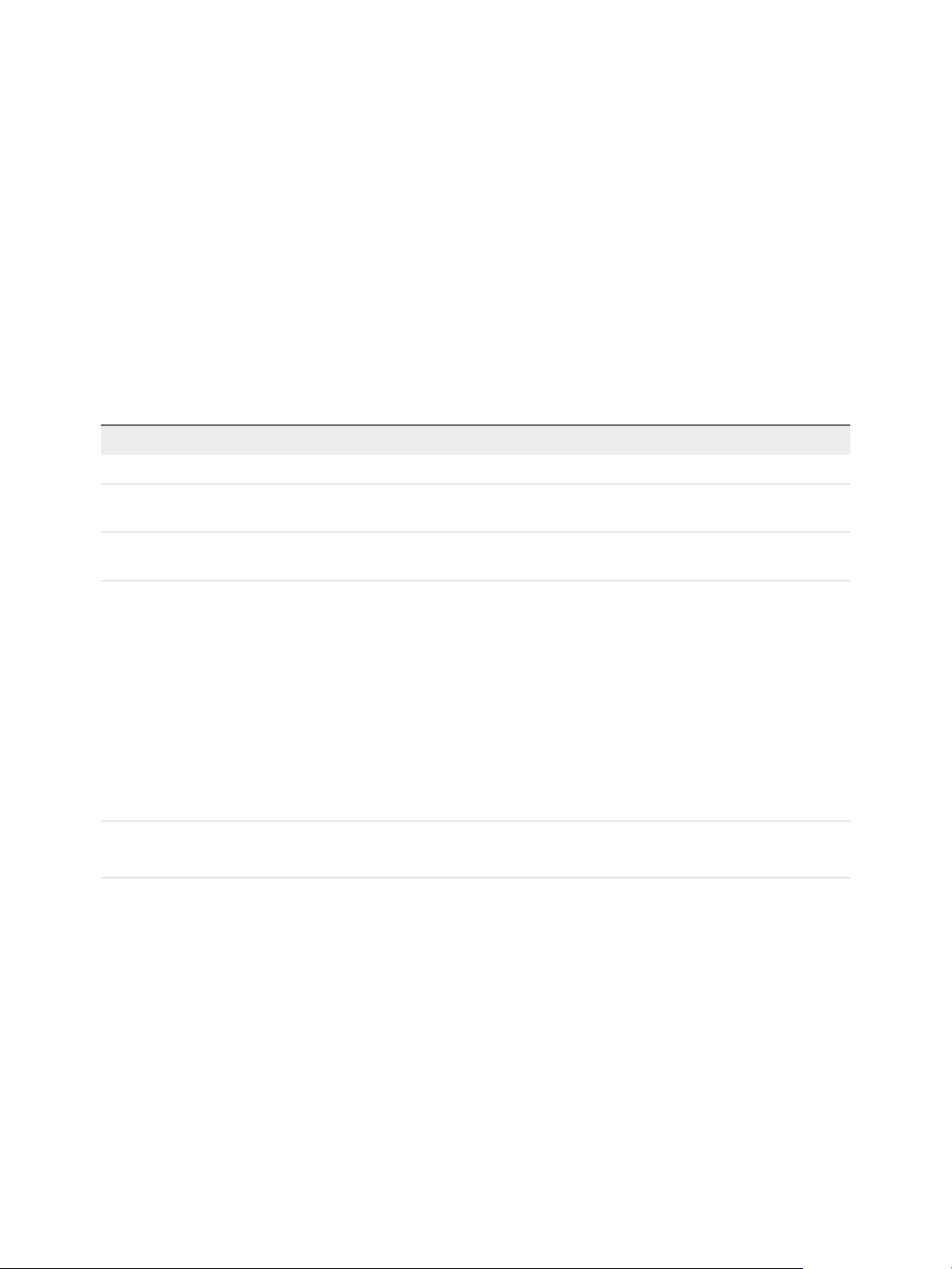
Understanding the Object-Level Permission Model
You authorize a user or group to perform tasks on vCenter objects by using permissions on the object.
The vSphere permission model relies on assigning permissions to objects in the vSphere object
hierarchy. Each permission gives one user or group a set of privileges, that is, a role for the selected
object. For example, a group of users might have the ReadOnly role on one VM and the Administrator
role on another VM.
The following concepts are important.
Permissions Each object in the vCenter Server object hierarchy has associated
permissions. Each permission specifies for one group or user which
privileges that group or user has on the object.
Users and Groups On vCenter Server systems, you can assign privileges only to
authenticated users or groups of authenticated users. Users are
authenticated through vCenter Single Sign-On. Users and groups must be
defined in the identity source that vCenter Single Sign-On uses to
authenticate. Define users and groups using the tools in your identity
source, for example, Active Directory.
Privileges Privileges are fine-grained access controls. You can group those privileges
into roles, which you can then map to users or groups.
Roles Roles are sets of privileges. Roles allow you to assign permissions on an
object based on a typical set of tasks that users perform. Default roles,
such as Administrator, are predefined on vCenter Server and cannot be
changed. Other roles, such as Resource Pool Administrator, are predefined
sample roles. You can create custom roles either from scratch or by cloning
and modifying sample roles. See Create a Custom Role.
Figure 2‑1. vSphere Permissions
To assign permissions to an object, you follow these steps:
1 Select the object to which you want to apply the permission in the vCenter object hierarchy.
VMware, Inc. 20
vSphere Security
2 Select the group or user that should have privileges on the object.
3 Select individual privileges or a role, that is a set of privileges, that the group or user should have on
the object.
By default, permissions propagate, that is the group or user has the selected role on the selected
object and its child objects.
vCenter Server offers predefined roles, which combine frequently used privilege sets. You can also create
custom roles by combining a set of roles.
Permissions must often be defined on both a source object and a destination object. For example, if you
move a virtual machine, you need privileges on that virtual machine, but also privileges on the destination
data center.
See the following information.
To find out about... See...
Creating custom roles. Create a Custom Role
All privileges and the objects to which you can apply the
privileges
Sets of privileges that are required on different objects for
different tasks.
Chapter 13 Defined Privileges
Required Privileges for Common Tasks
The permissions model for standalone ESXi hosts is simpler. See Assigning Privileges for ESXi Hosts.
Hierarchical Inheritance of Permissions
When you assign a permission to an object, you can choose whether the permission propagates down
the object hierarchy. You set propagation for each permission. Propagation is not universally applied.
Permissions defined for a child object always override the permissions that are propagated from parent
objects.
The figure illustrates the inventory hierarchy and the paths by which permissions can propagate.
Note Global permissions support assigning privileges across solutions from a global root object. See
Global Permissions.
VMware, Inc. 21
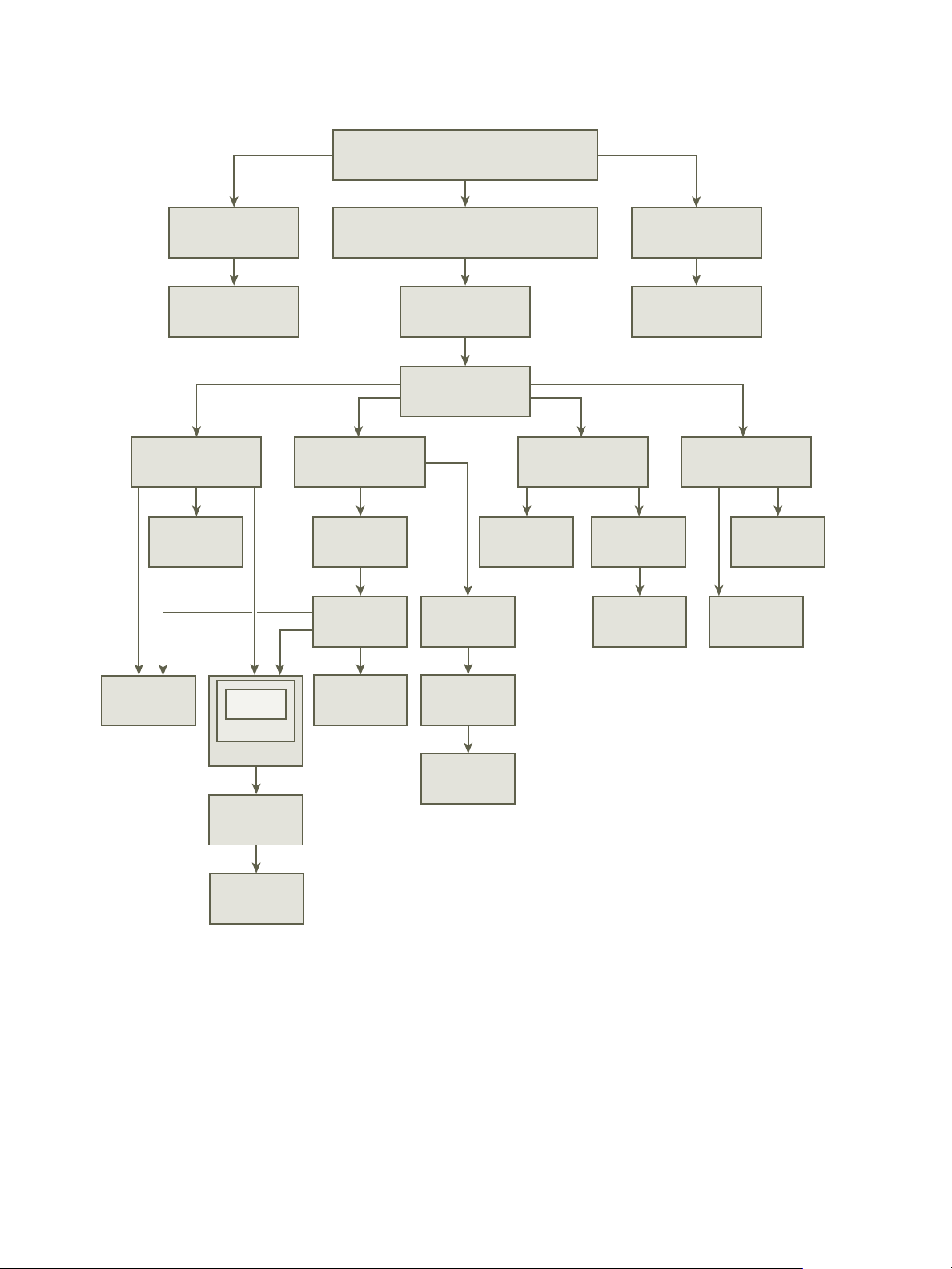
template
host
VDS datastore
cluster
vApp
vApp
vApp
virtual
machine
virtual
machine
resource
pool
resource
pool
virtual
machine
virtual
machine
resource
pool
standard
switch
datastore
cluster
distributed
port group
VM folder host folder
data center
vCenter Server
(vCenter Server instance level)
network
folder
datastore
folder
data center
folder
root object
(global permissions level)
tag category
tag
content library
library item
vSphere Security
Figure 2‑2. vSphere Inventory Hierarchy
Most inventory objects inherit permissions from a single parent object in the hierarchy. For example, a
datastore inherits permissions from either its parent datastore folder or parent data center. Virtual
machines inherit permissions from both the parent virtual machine folder and the parent host, cluster, or
resource pool simultaneously.
For example, you can set permissions for a distributed switch and its associated distributed port groups,
by setting permissions on a parent object, such as a folder or data center. You must also select the option
to propagate these permissions to child objects.
VMware, Inc. 22

vSphere Security
Permissions take several forms in the hierarchy:
Managed entities Privileged users can define permissions on managed entities.
n
Clusters
n
Data centers
n
Datastores
n
Datastore clusters
n
Folders
n
Hosts
n
Networks (except vSphere Distributed Switches)
n
Distributed port groups
n
Resource pools
n
Templates
n
Virtual machines
n
vSphere vApps
Global entities You cannot modify permissions on entities that derive permissions from the
root vCenter Server system.
n
Custom fields
n
Licenses
n
Roles
n
Statistics intervals
n
Sessions
Multiple Permission Settings
Objects might have multiple permissions, but only one permission for each user or group. For example,
one permission might specify that Group A has Administrator privileges on an object. Another permission
might specify that Group B might have Virtual Machine Administrator privileges on the same object.
If an object inherits permissions from two parent objects, the permissions on one object are added to the
permissions on the other object. For example, assume that a virtual machine is in a virtual machine folder
and also belongs to a resource pool. That virtual machine inherits all permission settings from both the
virtual machine folder and the resource pool.
Permissions applied on a child object always override permissions that are applied on a parent object.
See Example 2: Child Permissions Overriding Parent Permissions.
VMware, Inc. 23
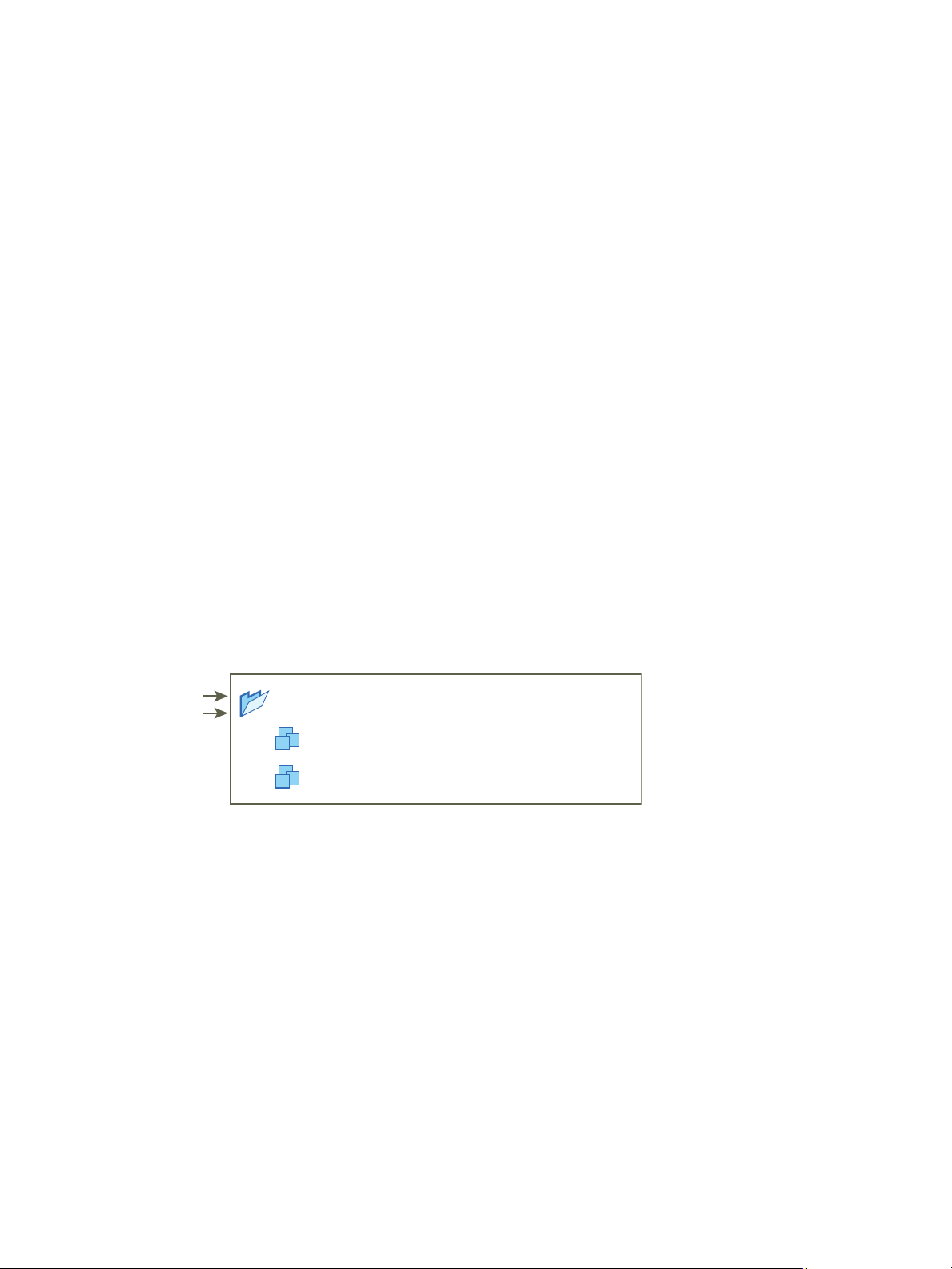
group B + role 2
user 1 has privileges
of role 1 and role 2
group A + role 1
VM A
VM B
VM Folder
vSphere Security
If multiple group permissions are defined on the same object and a user belongs to two or more of those
groups, two situations are possible:
n
No permission for the user is defined directly on the object. In that case, the user has the privileges
that the groups have on that object.
n
A permission for the user is defined directly on the object. In that case, the user's permission takes
precedence over all group permissions.
Example 1: Inheritance of Multiple Permissions
This example illustrates how an object can inherit multiple permissions from groups that are granted
permission on a parent object.
In this example, two permissions are assigned on the same object for two different groups.
n
Role 1 can power on virtual machines.
n
Role 2 can take snapshots of virtual machines.
n
Group A is granted Role 1 on VM Folder, with the permission set to propagate to child objects.
n
Group B is granted Role 2 on VM Folder, with the permission set to propagate to child objects.
n
User 1 is not assigned specific privileges.
User 1, who belongs to groups A and B, logs on. User 1 can both power on and take snapshots of VM A
and VM B.
Figure 2‑3. Example 1: Inheritance of Multiple Permissions
Example 2: Child Permissions Overriding Parent Permissions
This example illustrates how permissions that are assigned on a child object can override permissions
that are assigned on a parent object. You can use this overriding behavior to restrict user access to
particular areas of the inventory.
In this example, permissions are defined on two different objects for two different groups.
n
Role 1 can power on virtual machines.
n
Role 2 can take snapshots of virtual machines.
n
Group A is granted Role 1 on VM Folder, with the permission set to propagate to child objects.
n
Group B is granted Role 2 on VM B.
VMware, Inc. 24
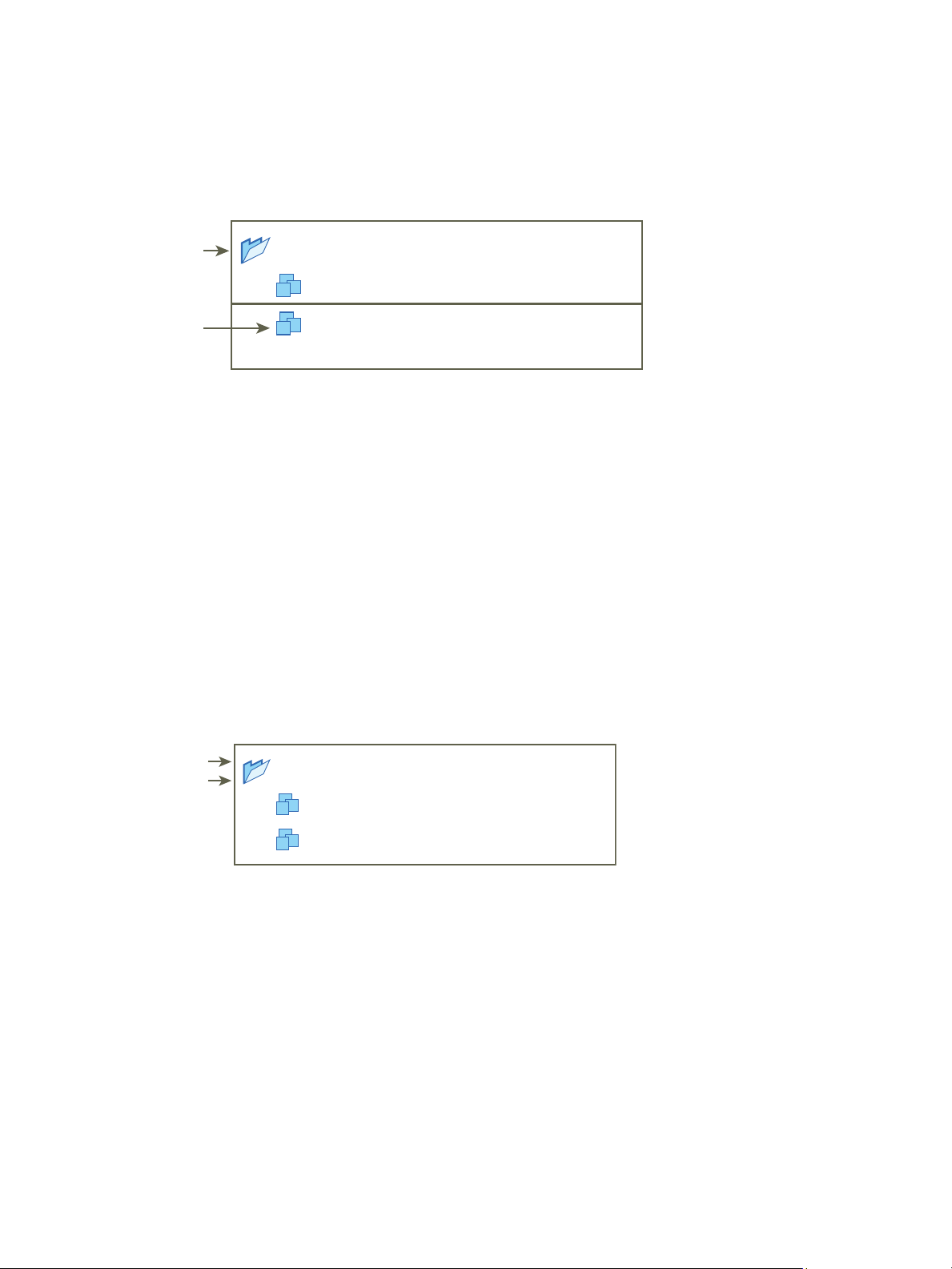
VM A
VM B
VM Folder
group B + role 2
user 1 has privileges
of role 1 only
user 1 has privileges
of role 2 only
group A + role 1
VM A
VM B
VM Folder
user 1 + no access
user 1 has no access to the folder
or the virtual machines
group A + role 1
vSphere Security
User 1, who belongs to groups A and B, logs on. Because Role 2 is assigned at a lower point in the
hierarchy than Role 1, it overrides Role 1 on VM B. User 1 can power on VM A, but not take snapshots.
User 1 can take snapshots of VM B, but not power it on.
Figure 2‑4. Example 2: Child Permissions Overriding Parent Permissions
Example 3: User Role Overriding Group Role
This example illustrates how the role assigned directly to an individual user overrides the privileges
associated with a role assigned to a group.
In this example, permissions are defined on the same object. One permission associates a group with a
role, the other permission associates an individual user with a role. The user is a member of the group.
n
Role 1 can power on virtual machines.
n
Group A is granted Role 1 on VM Folder.
n
User 1 is granted No Access role on VM Folder.
User 1, who belongs to group A, logs on. The No Access role granted to User 1 on VM Folder overrides
the role assigned to the group. User 1 has no access to VM Folder or VMs A and B.
Figure 2‑5. Example 3: User Permissions Overriding Group Permissions
Managing Permissions for vCenter Components
A permission is set on an object in the vCenter object hierarchy. Each permission associates the object
with a group or user and the group's or user's access roles. For example, you can select a virtual machine
object, add one permission that gives the ReadOnly role to Group 1, and add a second permission that
gives the Administrator role to User 2.
By assigning a different role to a group of users on different objects, you control the tasks that those users
can perform in your vSphere environment. For example, to allow a group to configure memory for the
host, select that host and add a permission that grants a role to that group that includes the
Host.Configuration.Memory Configuration privilege.
VMware, Inc. 25

vSphere Security
To manage permissions from the vSphere Web Client, you need to understand the following concepts:
Permissions Each object in the vCenter Server object hierarchy has associated
permissions. Each permission specifies for one group or user which
privileges that group or user has on the object.
Users and Groups On vCenter Server systems, you can assign privileges only to
authenticated users or groups of authenticated users. Users are
authenticated through vCenter Single Sign-On. Users and groups must be
defined in the identity source that vCenter Single Sign-On uses to
authenticate. Define users and groups using the tools in your identity
source, for example, Active Directory.
Privileges Privileges are fine-grained access controls. You can group those privileges
into roles, which you can then map to users or groups.
Roles Roles are sets of privileges. Roles allow you to assign permissions on an
object based on a typical set of tasks that users perform. Default roles,
such as Administrator, are predefined on vCenter Server and cannot be
changed. Other roles, such as Resource Pool Administrator, are predefined
sample roles. You can create custom roles either from scratch or by cloning
and modifying sample roles. See Create a Custom Role.
You can assign permissions to objects at different levels of the hierarchy, for example, you can assign
permissions to a host object or to a folder object that includes all host objects. See Hierarchical
Inheritance of Permissions. You can also assign permissions to a global root object to apply the
permissions to all object in all solutions. See Global Permissions.
Add a Permission to an Inventory Object
After you create users and groups and define roles, you must assign the users and groups and their roles
to the relevant inventory objects. You can assign the same permissions to multiple objects simultaneously
by moving the objects into a folder and setting the permissions on the folder.
When you assign permissions from the vSphere Client, user and group names must match Active
Directory precisely, including case. If you upgraded from earlier versions of vSphere, check for case
inconsistencies if you experience problems with groups.
Prerequisites
On the object whose permissions you want to modify, you must have a role that includes the
Permissions.Modify permission privilege.
Procedure
1 Browse to the object for which you want to assign permissions in the vSphere Client object navigator.
2 Click the Permissions tab.
3 Click the Add icon, and click Add.
VMware, Inc. 26
vSphere Security
4 Select the user or group that will have the privileges defined by the selected role.
a From the Domain drop-down menu, select the domain for the user or group.
b Type a name in the Search box or select a name from the list.
The system searches user names, group names, and descriptions.
c Select the user or group and click Add.
The name is added to either the Users or Groups list.
d (Optional) Click Check Names to verify that the user or group exists in the identity source.
e Click OK.
5 Select a role from the Assigned Role drop-down menu.
The roles that are assigned to the object appear in the menu. The privileges contained in the role are
listed in the section below the role title.
6 (Optional) To limit propagation, deselect the Propagate to Child Objects check box.
The role is applied only to the selected object and does not propagate to the child objects.
7 Click OK to add the permission.
Change or Remove Permissions
After a user or group and role pair is set for an inventory object, you can change the role paired with the
user or group or change the setting of the Propagate check box. You can also remove the permission
setting.
Procedure
1 Browse to the object in the vSphere Web Client object navigator.
2 Click the Permissions tab.
3 Click a row to select a permission.
Task Steps
Change permissions a Click the Change role on permission icon.
b Select a role for the user or group from the Assigned Role drop-down menu.
c Toggle the Propagate to children check box if you want to make changes to
permission inheritance.
d Click OK
Remove permissions Click the Remove permission icon.
VMware, Inc. 27
vSphere Security
Change User Validation Settings
vCenter Server periodically validates its user and group lists against the users and groups in the user
directory. It then removes users or groups that no longer exist in the domain. You can disable validation or
change the interval between validations. If you have domains with thousands of users or groups, or if
searches take a long time to complete, consider adjusting the search settings.
For vCenter Server versions before vCenter Server 5.0, these settings apply to an Active Directory
associated with vCenter Server. For vCenter Server 5.0 and later, these settings apply to vCenter Single
Sign-On identity sources.
Note This procedure applies only to vCenter Server user lists. You cannot search ESXi user lists in the
same way.
Procedure
1 Browse to the vCenter Server system in the vSphere Web Client object navigator.
2 Select Configure and click Settings > General.
3 Click Edit and select User directory.
4 Change the values as needed and click OK.
Option Description
User directory timeout Timeout interval, in seconds, for connecting to the Active Directory server. This
value specifies the maximum amount of time vCenter Server allows a search to
run on the selected domain. Searching large domains can take a long time.
Query limit Select the check box to set a maximum number of users and groups that
vCenter Server displays.
Query limit size Maximum number of users and groups from the selected domain that
vCenter Server displays in the Select Users or Groups dialog box. If you enter 0
(zero), all users and groups appear.
Validation Deselect the check box to disable validation
Validation Period Specifies how often vCenter Server validates permissions, in minutes.
Global Permissions
Global permissions are applied to a global root object that spans solutions, for example, both
vCenter Server and vRealize Orchestrator. Use global permissions to give a user or group privileges for
all objects in all object hierarchies.
VMware, Inc. 28
vSphere Security
Each solution has a root object in its own object hierarchy. The global root object acts as a parent object
to the root objects for all solutions. You can assign global permissions to users or groups, and decide on
the role for each user or group. The role determines the set of privileges that the user or group has for all
objects in the hierarchy. You can assign a predefined role or create custom roles. See Using Roles to
Assign Privileges. It is important to distinguish between vCenter Server permissions and global
permissions.
vCenter Server
permissions
You usually apply a permission to a vCenter Server inventory object such
as an ESXi host or a virtual machine. When you do, you specify that a user
or group has a set of privileges, called a role, on the object.
Global permissions Global permissions give a user or group privileges to view or manage all
objects in each of the inventory hierarchies in your deployment.
If you assign a global permission and do not select Propagate, the users or
groups associated with this permission do not have access to the objects in
the hierarchy. They only have access to some global functionality such as
creating roles.
Important Use global permissions with care. Verify that you really want to assign permissions to all
objects in all inventory hierarchies.
Add a Global Permission
You can use global permissions to give a user or group privileges for all objects in all inventory
hierarchies in your deployment.
Important Use global permissions with care. Verify that you really want to assign permissions to all
objects in all inventory hierarchies.
Prerequisites
To perform this task, you must have Permissions.Modify permission privileges on the root object for all
inventory hierarchies.
Procedure
1 Click Administration and select Global Permissions in the Access Control area.
2 Click Manage, and click the Add permission icon.
3 Select the user or group that will have the privileges defined by the selected role.
a From the Domain drop-down menu, select the domain for the user or group.
b Type a name in the Search box or select a name from the list.
The system searches user names, group names, and descriptions.
c Select the user or group and click Add.
The name is added to either the Users or Groups list.
VMware, Inc. 29
vSphere Security
d (Optional) Click Check Names to verify that the user or group exists in the identity source.
e Click OK.
4 Select a role from the Assigned Role drop-down menu.
The roles that are assigned to the object appear in the menu. The privileges contained in the role are
listed in the section below the role title.
5 Decide whether to leave the Propagate to children check box selected.
If you assign a global permission and do not select Propagate, the users or groups associated with
this permission do not have access to the objects in the hierarchy. They only have access to some
global functionality such as creating roles.
6 Click OK.
Permissions on Tag Objects
In the vCenter Server object hierarchy, tag objects are not children of vCenter Server but are created at
the vCenter Server root level. In environments with multiple vCenter Server instances, tag objects are
shared across vCenter Server instances. Permissions for tag objects work differently than permissions for
other objects in the vCenter Server object hierarchy.
Only Global Permissions or Permissions Assigned to the Tag Object Apply
If you grant permissions to a user on a vCenter Server inventory object, such as a virtual machine, that
user can perform the tasks associated with the permission. However, the user cannot perform tag
operations on the object.
For example, if you grant the Assign vSphere Tag privilege to user Dana on host TPA, that permission
does not affect whether Dana can assign tags on host TPA. Dana must have the Assign vSphere Tag
privilege at the root level, that is, a global permission, or must have the privilege for the tag object.
Table 2‑1. How Global Permissions and Tag Object Permissions Aect What Users Can Do
vCenter Server Object-
Global Permission Tag-Level Permission
No tagging privileges assigned. Dana has Assign or
Unassign vSphere Tag
privileges for the tag.
Dana has Assign or Unassign
vSphere Tag privileges.
No tagging privileges assigned. No privileges assigned for the
No privileges assigned for the
tag.
tag.
Level Permission Effective Permission
Dana has Delete vSphere
Tag privileges on ESXi host
TPA.
Dana has Delete vSphere
Tag privileges on ESXi host
TPA.
Dana has Assign or
Unassign vSphere Tag
privileges on ESXi host TPA.
Dana has Assign or Unassign
vSphere Tag privileges for the
tag.
Dana has Assign or Unassign
vSphere Tag global privileges.
That includes privileges at the
tag level.
Dana does not have tagging
privileges on any object,
including host TPA.
VMware, Inc. 30
 Loading...
Loading...