Page 1

User Guide
Omada Cloud Controller
OC200
1910012442 REV 1.0.0
September 2018
Page 2

CONTENTS
1 Quick Start ....................................................................................................................... 1
1.1 Deploy the OC200 .......................................................................................................................................................2
1.1.1 Deploy the OC200 and EAPs in the Same Subnet .................................................................................. 2
1.1.2 Deploy the OC200 and EAPs in Different Subnets ................................................................................. 2
1.2 Determine the Management Method ....................................................................................................................4
1.2.1 Management on the Local Network ............................................................................................................. 4
1.2.2 Management via Cloud Access......................................................................................................................4
1.3 Inform the EAPs of the OC200's Address ...........................................................................................................5
1.4 Log in to OC200 ............................................................................................................................................................7
1.4.1 On the Local Network ........................................................................................................................................ 7
1.4.2 Via Omada Cloud ................................................................................................................................................. 7
1.4.3 Do the Basic Configurations............................................................................................................................7
1.4.4 Log In to the Management Interface ......................................................................................................... 10
1.5 Create Sites and Adopt EAPs ............................................................................................................................... 11
1.5.1 Create Sites ........................................................................................................................................................ 11
1.5.2 Adopt the EAPs ................................................................................................................................................. 11
1.6 Monitor and Manage the EAPs ............................................................................................................................. 12
2 Monitor and Manage the Network .........................................................................14
2.1 Monitor the Network with the Map .....................................................................................................................15
2.1.1 Add a Map ............................................................................................................................................................ 15
2.1.2 Monitor the EAPs on the Map ...................................................................................................................... 17
2.2 View the Statistics of the Network .....................................................................................................................18
2.2.1 View the Client Distribution on SSID ......................................................................................................... 18
2.2.2 Have a Quick Look at EAPs and Clients ................................................................................................... 18
2.2.3 View Current Usage-Top EAPs ................................................................................................................... 19
2.2.4 View Recent Activities .................................................................................................................................... 19
2.3 Monitor and Manage the EAPs ............................................................................................................................. 20
Page 3

2.3.1 Manage the EAPs in Different Status ........................................................................................................ 20
2.3.2 View the Detailed Information of EAPs..................................................................................................... 21
2.3.3 Manage the EAPs in the Action Column .................................................................................................. 22
2.4 Monitor and Manage Clients ................................................................................................................................. 23
2.4.1 View the Current Information of Clients .................................................................................................. 23
2.4.2 Manage Clients in the Action Column ....................................................................................................... 24
2.5 View Clients Statistics During the Specified Period ................................................................................... 24
2.5.1 Select a Specified Period .............................................................................................................................. 24
2.5.2 View the History Information of Clients ................................................................................................... 25
2.5.3 Manage Clients in the Action Column ....................................................................................................... 25
2.6 Manage the Rogue APs List ..................................................................................................................................26
2.6.1 Manage the Untrusted Rogue APs List .................................................................................................... 26
2.6.2 Manage the Trusted Rogue APs List ......................................................................................................... 26
2.7 View Past Guest Authorization .............................................................................................................................27
2.8 View Logs ..................................................................................................................................................................... 28
2.9 View Alerts ...................................................................................................................................................................28
3 Configure the EAPs Globally ................................................................................... 29
3.1 Wireless Network ...................................................................................................................................................... 30
3.1.1 Add Wireless Networks .................................................................................................................................. 30
3.1.2 Configure Advanced Wireless Parameters ............................................................................................ 35
3.1.3 Configure Band Steering ............................................................................................................................... 37
3.1.4 Configure Mesh ................................................................................................................................................. 38
3.2 Access Control ..........................................................................................................................................................42
3.3 Portal Authentication ...............................................................................................................................................43
3.3.1 No Authentication............................................................................................................................................. 44
3.3.2 Simple Password .............................................................................................................................................. 48
3.3.3 Local User ............................................................................................................................................................ 52
3.3.4 Voucher ................................................................................................................................................................ 59
3.3.5 SMS ........................................................................................................................................................................ 67
Page 4

3.3.6 Facebook ............................................................................................................................................................. 72
3.3.7 External RADIUS Server ................................................................................................................................. 73
3.3.8 External Portal Server ..................................................................................................................................... 78
3.4 Free Authentication Policy .................................................................................................................................... 79
3.5 MAC Filter ....................................................................................................................................................................80
3.6 Scheduler ..................................................................................................................................................................... 82
3.7 QoS ................................................................................................................................................................................. 84
3.8 Site Settings ...............................................................................................................................................................87
3.8.1 LED ......................................................................................................................................................................... 87
3.8.2 Device Account ................................................................................................................................................. 88
3.8.3 Reboot Schedule .............................................................................................................................................. 88
3.8.4 Log Settings ....................................................................................................................................................... 89
3.8.5 Batch Upgrade ................................................................................................................................................... 90
3.8.6 SSH ........................................................................................................................................................................ 92
3.8.7 Management VLAN .......................................................................................................................................... 93
4 Omada Cloud Service ................................................................................................ 94
4.1 Configure the Cloud Access ................................................................................................................................. 95
4.1.1 Enable Cloud Access ...................................................................................................................................... 95
4.1.2 Manage the Cloud Users ............................................................................................................................... 95
4.2 Manage the OC200 via Omada Cloud ................................................................................................................97
4.2.1 Access the OC200 via Omada Cloud ....................................................................................................... 98
4.2.2 Change your TP-Link ID information .......................................................................................................100
5 Configure the EAPs Separately .......................................................................... 101
5.1 View the Information of the EAP ....................................................................................................................... 102
5.1.1 Overview ............................................................................................................................................................102
5.1.2 LAN .......................................................................................................................................................................102
5.1.3 Radio ....................................................................................................................................................................103
5.2 View Clients Connecting to the EAP ............................................................................................................... 103
5.2.1 User ......................................................................................................................................................................103
Page 5

5.2.2 Guest ...................................................................................................................................................................104
5.3 View Mesh Information of the EAP .................................................................................................................. 104
5.3.1 Uplinks ................................................................................................................................................................104
5.3.2 Downlinks ..........................................................................................................................................................105
5.4 Configure the EAP ................................................................................................................................................. 105
5.4.1 Basic Config ......................................................................................................................................................105
5.4.2 IP Setting ............................................................................................................................................................106
5.4.3 Radio ....................................................................................................................................................................107
5.4.4 Load Balance ....................................................................................................................................................108
5.4.5 WLANs ................................................................................................................................................................109
5.4.6 Trunk Settings..................................................................................................................................................109
5.4.7 Rogue AP Detection ......................................................................................................................................110
5.4.8 Local LAN Port Settings (Only for EAP115-Wall and EAP225-Wall) ...........................................110
5.4.9 Forget this AP ..................................................................................................................................................111
6 Manage the OC200 .................................................................................................. 112
6.1 Status ......................................................................................................................................................................... 113
6.2 User Account ........................................................................................................................................................... 113
6.3 General Setting ....................................................................................................................................................... 114
6.3.1 Configure Basic Settings .............................................................................................................................115
6.3.2 Configure Network Settings .......................................................................................................................115
6.3.3 Configure Mail Server ...................................................................................................................................116
6.4 History Data Retention ......................................................................................................................................... 117
6.5 Backup&Restore..................................................................................................................................................... 118
6.6 Auto Backup ............................................................................................................................................................. 119
6.7 Maintenance ............................................................................................................................................................ 121
7 Application Example ............................................................................................... 122
7.1 Basic Configuration ............................................................................................................................................... 123
7.2 Advanced Settings ................................................................................................................................................ 123
7.2.1 Monitor the EAPs with Map .........................................................................................................................123
Page 6

7.2.2 Configure Portal Authentication ...............................................................................................................124
7.2.3 Create a SSID for the Employees .............................................................................................................126
7.2.4 Configure Scheduler .....................................................................................................................................127
Page 7

1
OC200 is a hardware Omada Cloud Controller, which is running with a built-in software controller.
OC200 can manage multiple EAPs centrally just as the software controller does. The difference is
that the software controller needs to run in a management host, which is unnecessary for OC200.
You just need to pre-configure the OC200, then keep it running in your network.
Follow the steps below to complete the basic settings of OC200.
Deploy the OC200
·
Determine the Management Method
·
Inform the EAPs of the OC200's Address
·
Log in to OC200
·
Create Sites and Adopt EAPs
·
Monitor and Manage the EAPs
·
Quick Start
1
Page 8
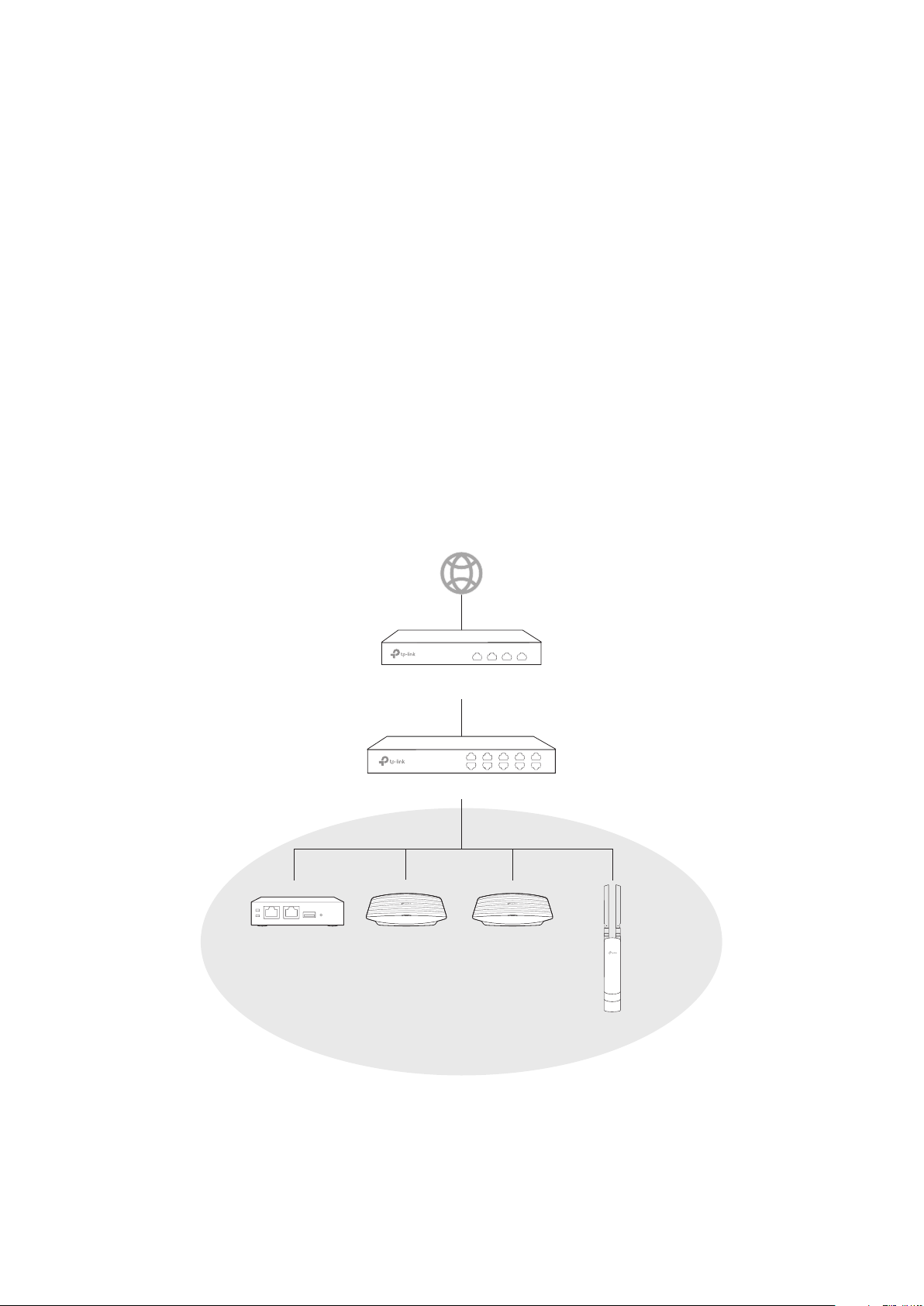
1.1 Deploy the OC200
There are two kinds of network topologies which are suitable for OC200 deployment:
The OC200 and EAPs are in the same subnet.
·
The OC200 and EAPs are in different subnets.
·
Determine your topology according to your need and refer to the following introductions to build
your network topology.
1.1.1 Deploy the OC200 and EAPs in the Same Subnet
If your need to deploy the OC200 and EAPs in the same subnet, refer to the following network
topology.
A router acts as a DHCP server to assign IP addresses to EAPs, clients and OC200. The OC200 and
the EAPs are in the same subnet.
Router
Layer 2 Switch
OC200
IP: 192.168.0.100/24
Subnet: 192.168.0.0/24
EAPEAP
EAP
1.1.2 Deploy the OC200 and EAPs in Different Subnets
If your need to deploy the OC200 and EAPs in different subnets, refer to the following network
topology.
2
Page 9
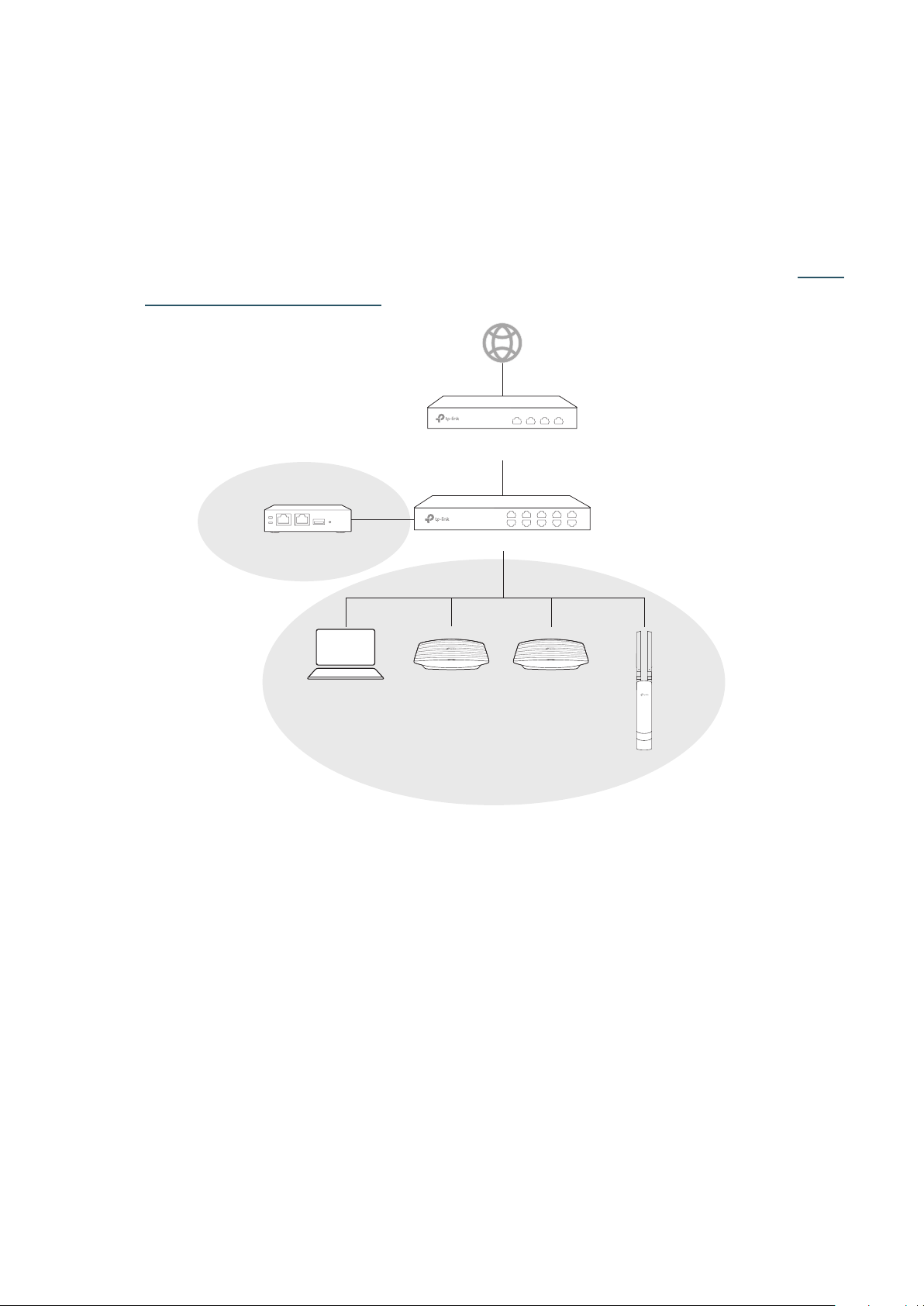
A router acts as the gateway of the network. A layer 3 switch acts as a DHCP server to assign IP
addresses to EAPs, OC200 and clients. The EAPs are in subet 1, of which the IP network segment is
192.168.0.0/24; the OC200 is in subnet 2, of which the IP network segment is 192.168.1.0/24.
For the EAPs and the OC200 are in the different networksegment, the EAPs cannot find the OC200
directly. To help the EAPs find the OC200, you need to install an Omada Discover Utility on a host
which is in the same subnet with the EAPs. For how to use Omada Discovery Utility, refer to Inform
the EAPs of the OC200’s Address.
Router
Subnet 2: 192.168.1.0/24
IP: 192.168.1.100/24
Omada
Discovery Utility
Host A
IP: 192.168.0.100/24
Layer 3 SwitchOC200
Subnet 1: 192.168.0.0/24
EAPEAP
EAP
3
Page 10
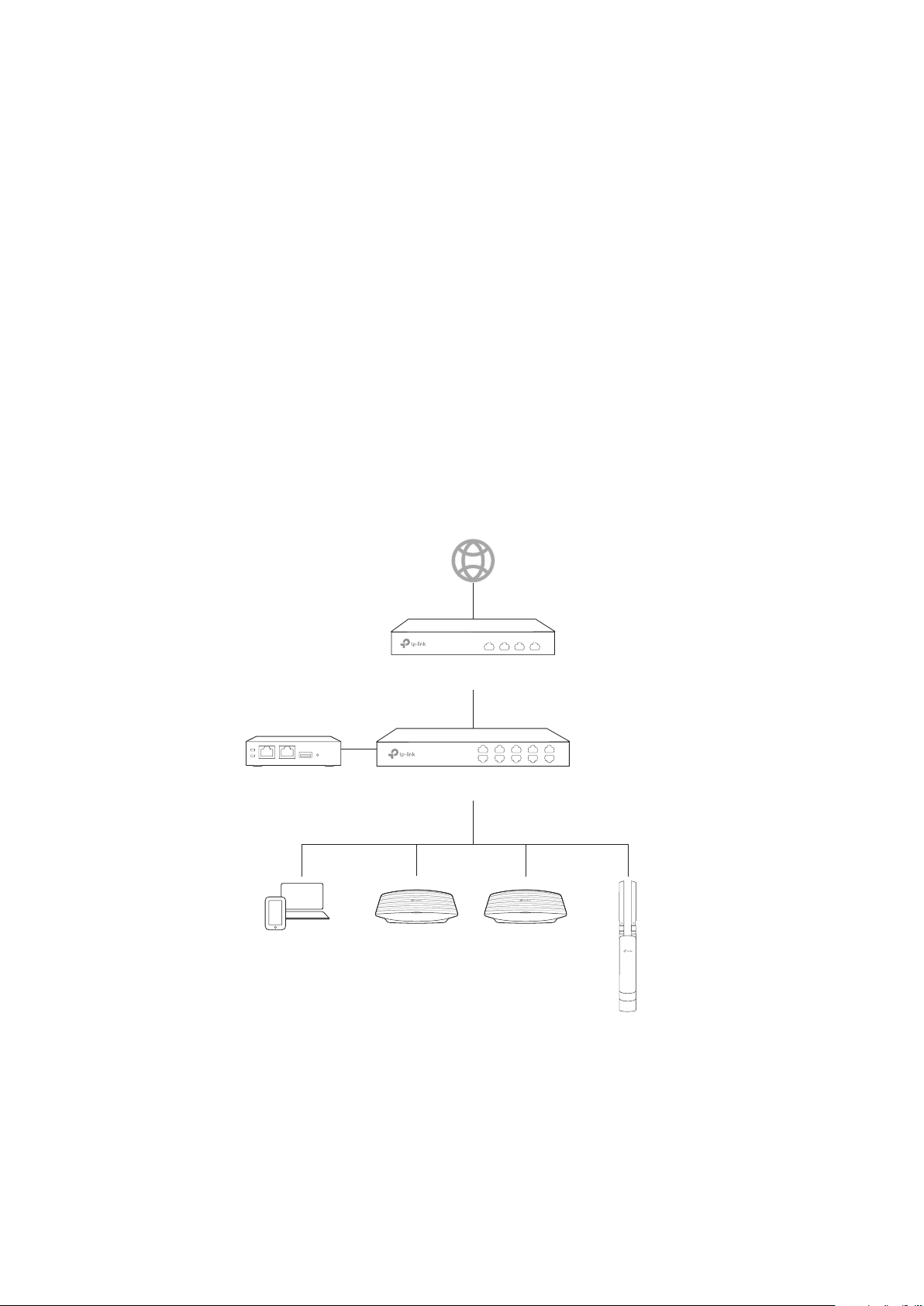
1.2 Determine the Management Method
EAPEAP
EAP
Management Device
Router
SwitchOC200
OC200 supports two flexible management methods to centrally manage EAPs:
Management on the local network
·
Management via Cloud Access
·
Determine your management method according to your need and refer to the following
introductions to build your network toplogy.
1.2.1 Management on the Local Network
To manage EAPs locally, please deploy your management host on the local network. The following
topology is an example for the deployment of the management host. As long as there is a route
for the management host to access the OC200, the management host can log in to the OC200 to
manage the EAPs. For how to log in to the OC200, please refer to
On the Local Network
.
1.2.2 Management via Cloud Access
If you need to manage EAPs remotely, for example, your EAPs are in your office but you want to
manage them at home, you can manage the EAPs via cloud access.
4
Page 11
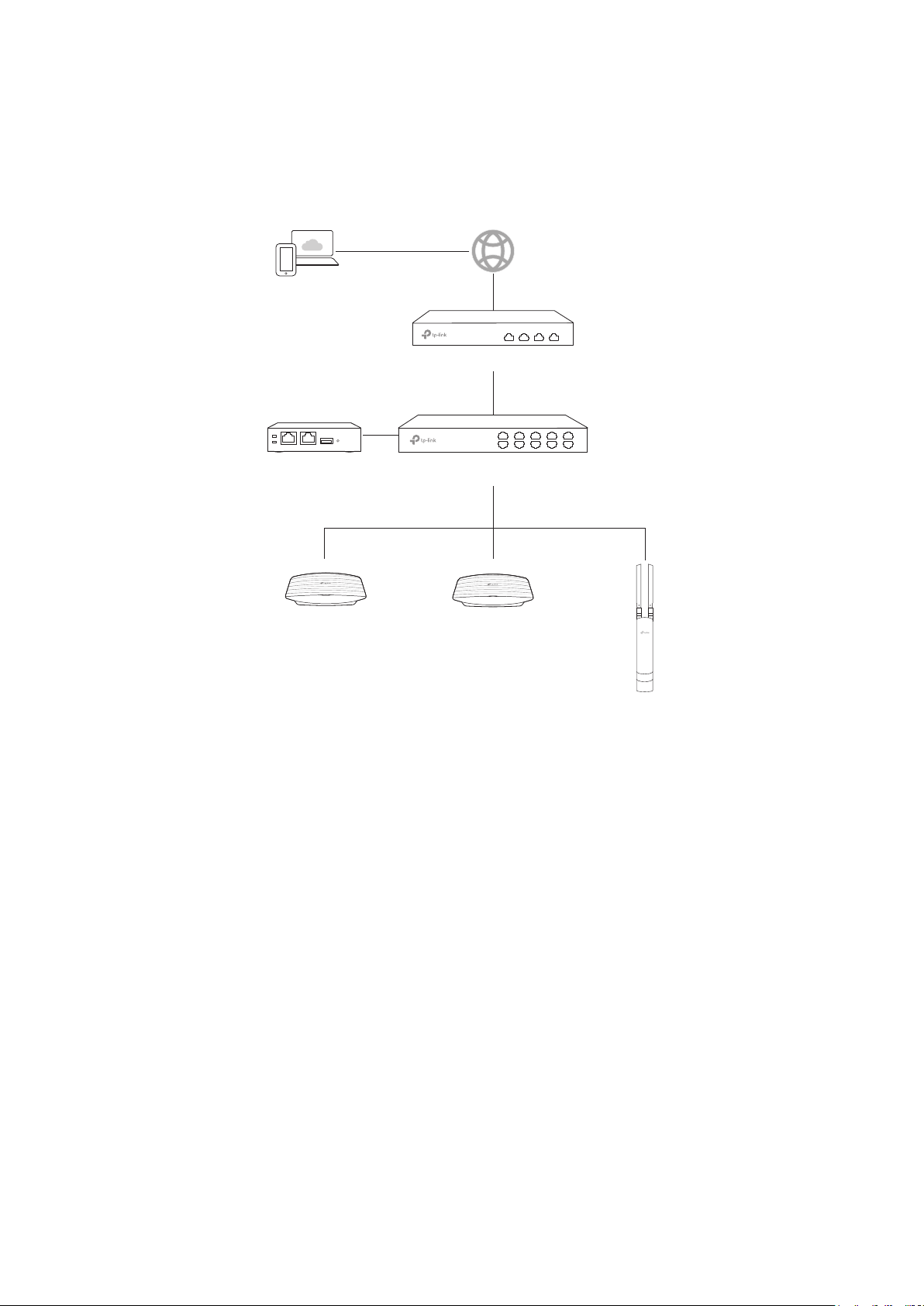
The following topology is a typical example. You just need to deploy your OC200 and EAPs on your
local network, and use a management device to control them remotely. On the management device,
you can open a web browser to remotely launch the OC200 via Omada Cloud. For more details
about Cloud Access, refer to
Management Device
Omada Cloud Service.
Router
SwitchOC200
EAPEAP
EAP
1.3 Inform the EAPs of the OC200's Address
If your OC200 and EAPs are in the same network subnet, you can skip this section.
If your OC200 and EAPs are in different subnets, you need to install Omada Discovery Utility on a
host that is in the same network segment with the EAPs. Omada Discovery Utility can help EAPs find
the OC200.
System Requirements
Windows 7/8/10/Server
Mac OS X 10.7/10.8/10.9/10.10/10.11
Install and Use Omada Discovery Utility
Follow the steps below to install Omada Discovery Utility and use it to inform the EAPs of the
OC200's IP address:
5
Page 12
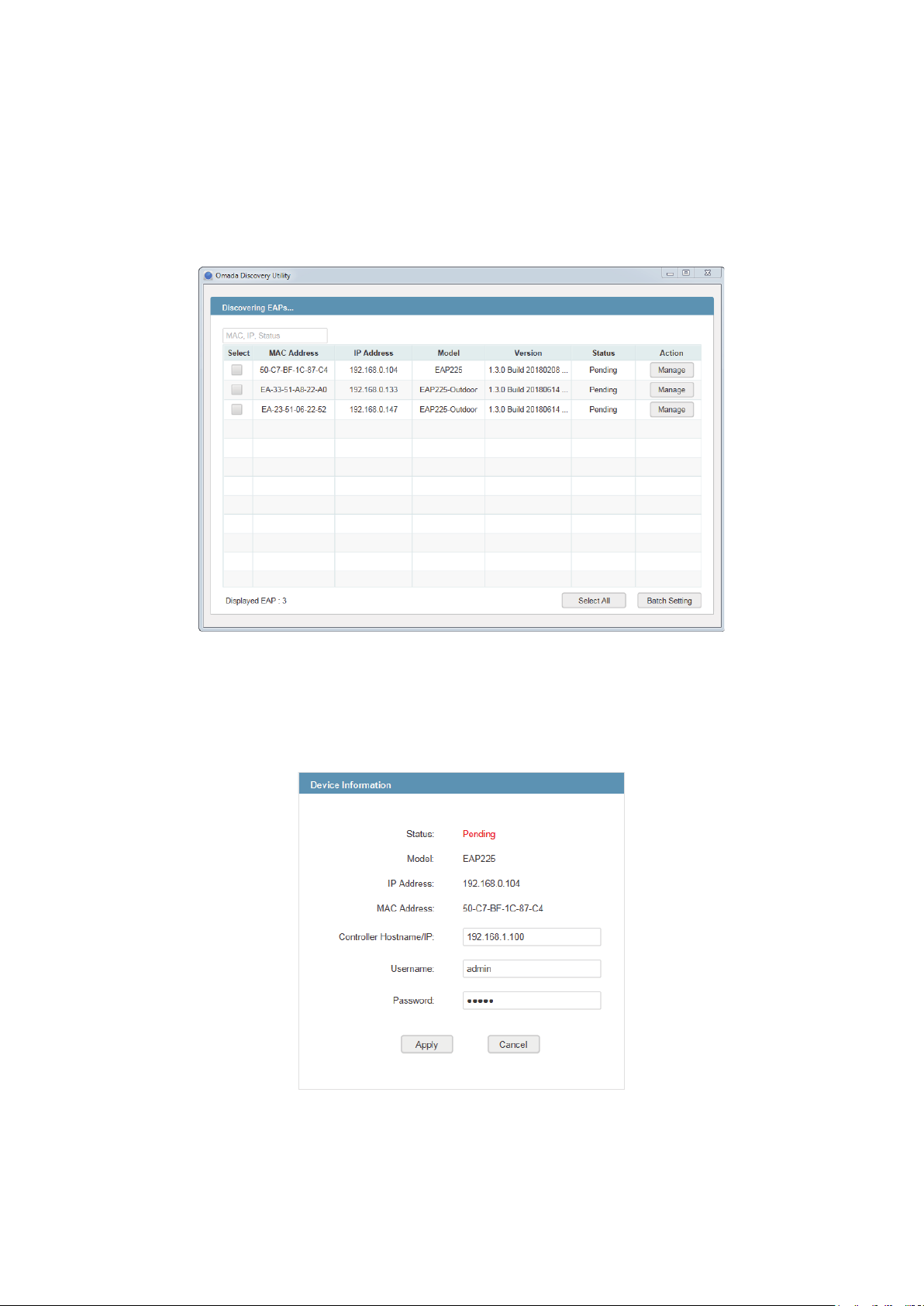
1. Download the installation file from the website
https://www.tp-link.com/en/download/EAP-
Controller.html#EAP_Discovery_Tool
Discovery Utility.
2. Open the Omada Discovery Utility and the following window will pop up. This window shows the
information of all EAPs in the same LAN.
. Then follow the instructions to properly install Omada
3. Click Manage in the Action column or select multiple EAPs and click Batch Setting.
4. Enter the hostname or IP address of the OC200.
5. Enter the EAP’s username and password (both are admin by default).
6. Click Apply to inform the EAP of the OC200’s hostname or IP address. And then the connection
can be established between the EAP and the OC200.
6
Page 13

1.4 Log in to OC200
To use OC200 to manage EAPs, you first need to log in to OC200. There are two situations:
Login in to the OC200 on the local network
·
Login in to the OC200 via Omada cloud
·
1.4.1 On the Local Network
Follow the steps below to enter the management interface of OC200 on the local network:
1. Make sure that your management device has the route to access the OC200.
2. Check the DHCP server (typically a router) for OC200’s IP Address. The default fallback IP of
address OC 200 is 192.168.0.253.
The fallback IP address is used when OC200 fails to get dynamic IP address from the DHCP server
Tips:
3. Launch a web browser and type OC200’s IP address in the address bar, then press Enter
(Windows) or Return (Mac).
1.4.2 Via Omada Cloud
Follow the steps below to log in to OC200 via Omada cloud:
1. Make sure that your management device and OC200 can access the internet.
2. Launch a web browser and visit https://omada.tplinkcloud.com in the address bar, then press
Enter (Windows) or Return (Mac).
3. Enter your TP-Link ID and password to log in. Then click Add Cloud Controller and follow the
instructions to add your OC200.
4. Click Launch in the Action column to visit the management interface of OC200.
1.4.3 Do the Basic Configurations
In the web browser you can see the configuration page. Follow the setup wizard to complete the
basic settings for OC200.
7
Page 14
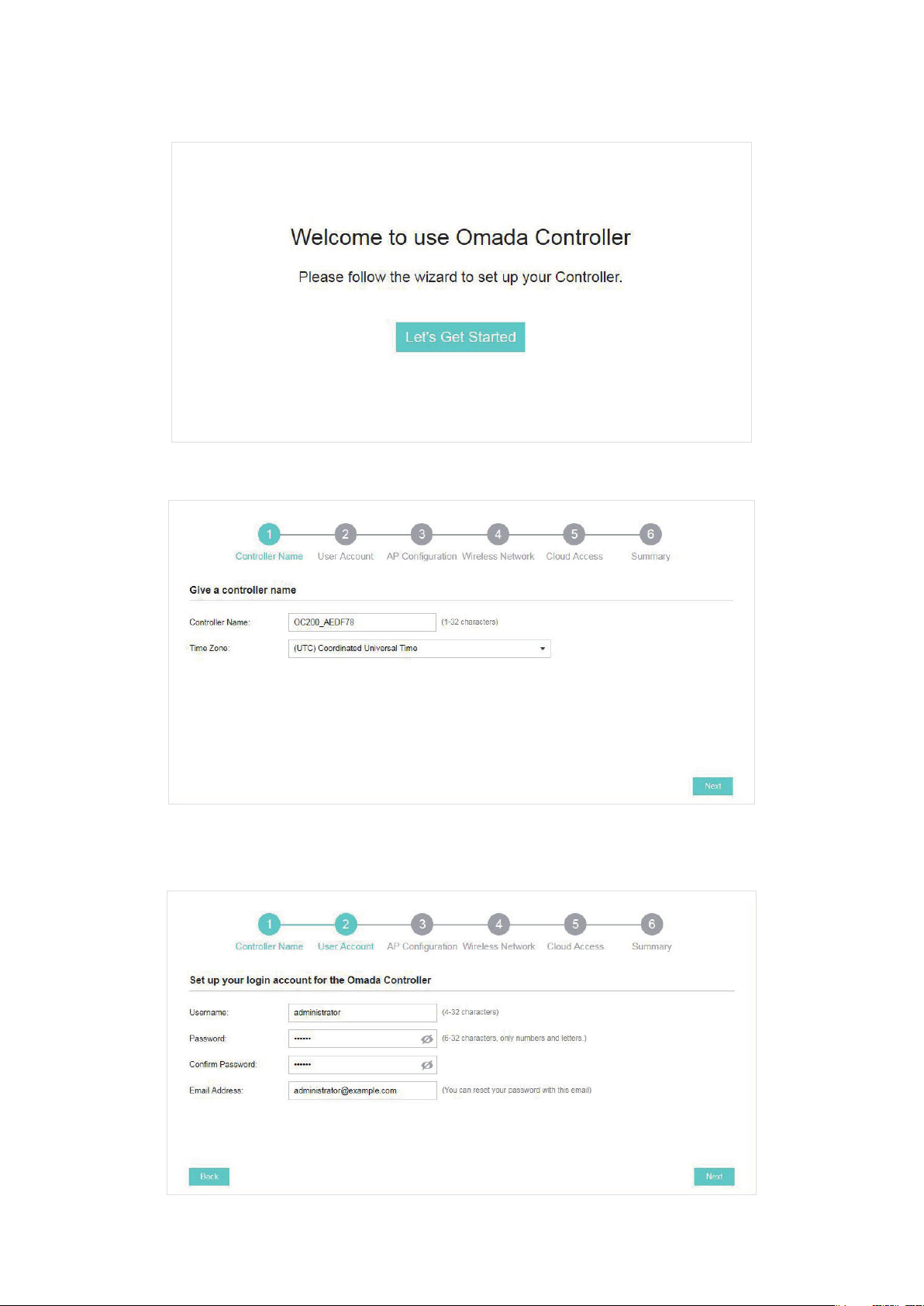
1. Click Let’s Get Started.
2. Specify a name for OC200 and select the time zone. Click Next.
3. Specify a username and password for the login account. Specify the email address to receive
the emails and reset your password if necessary. Click Next.
8
Page 15
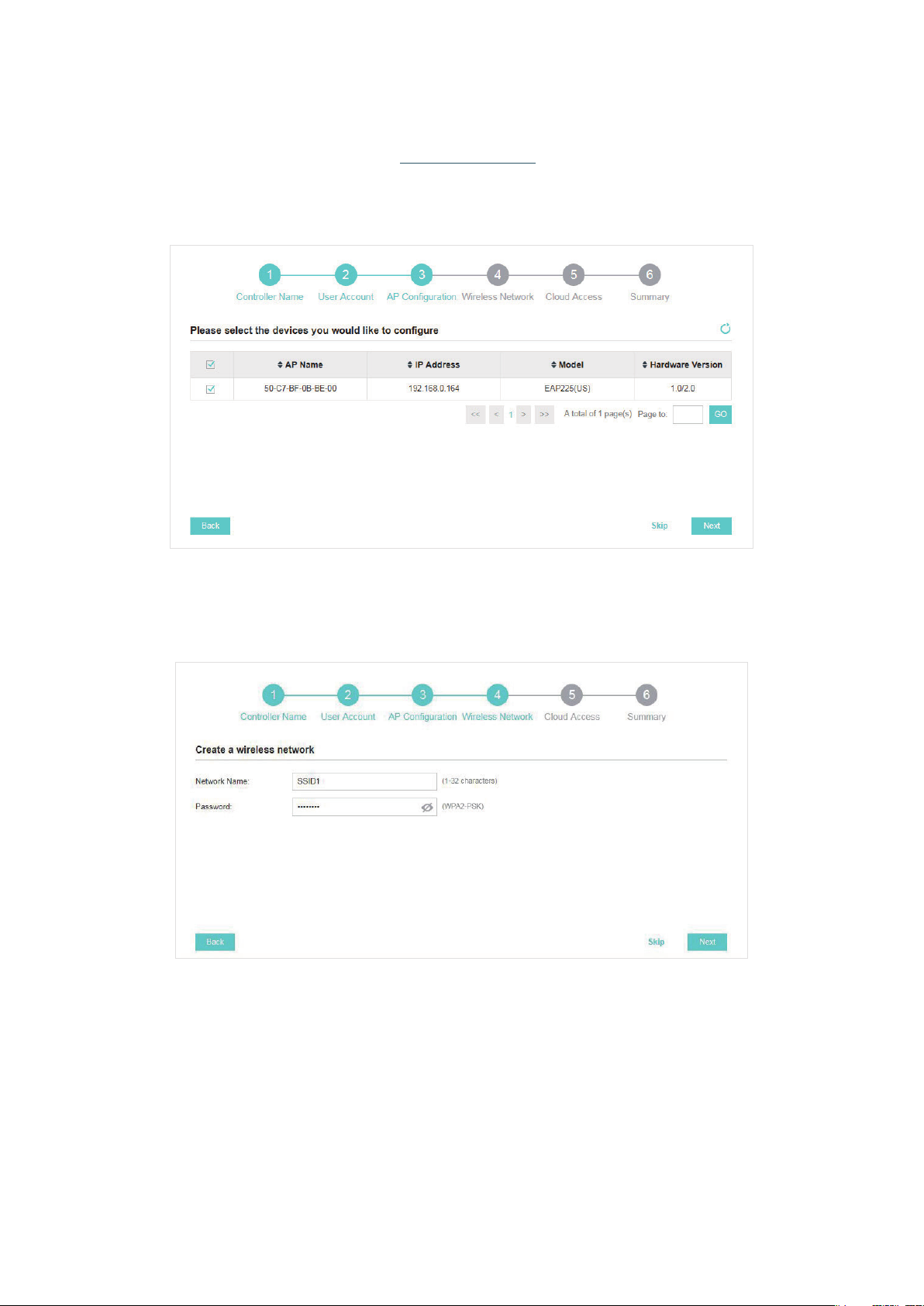
Note:
After logging into OC200, set a mail server so that you can receive emails and reset your password in case that
you forget the password. Please refer to Configure Mail Server.
4. The setup page displays all the detected EAPs in the network. Select one or more EAPs to be
managed and click Next.
5. Set an SSID name (wireless network name) and password for the EAPs to be managed. OC200
will create two wireless networks, a 2.4GHz one and a 5GHz one, both encrypted in WPA2-PSK
mode. Click Next.
6. If you want to manage EAPs via Omada cloud, enable the Cloud Access button, and bind your
TP-Link ID to your OC200, and then click Next. If you want to manage EAPs on the local network,
you can just click Skip. For more details about Omada Cloud, please refer to
Service.
9
Omada Cloud
Page 16
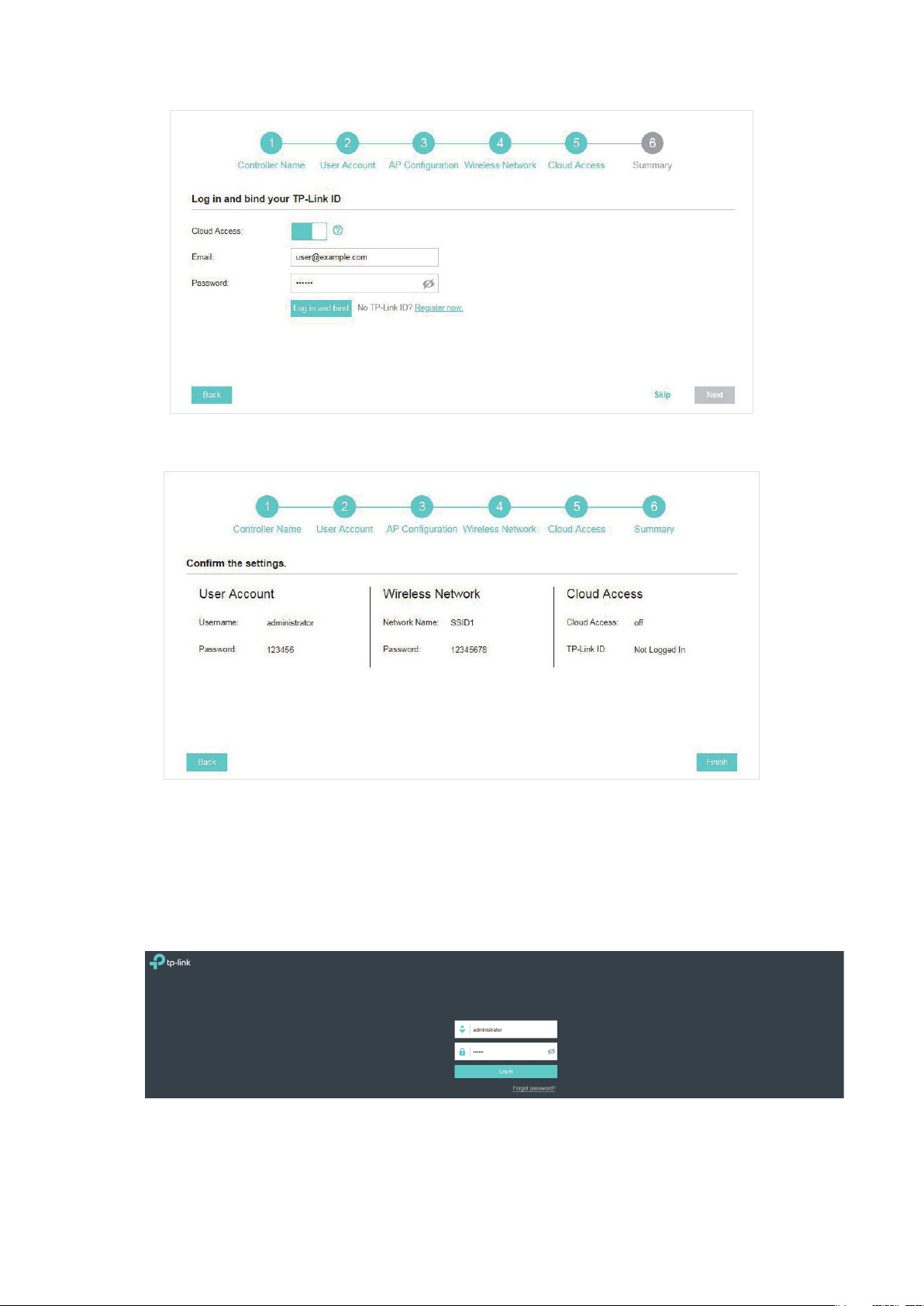
7. Review your settings and click Finish.
1.4.4 Log In to the Management Interface
Once the basic configurations are finished, the browser will be redirected to the following page.
Log in to the management interface using the username and password you have set in the basic
configurations.
10
Page 17
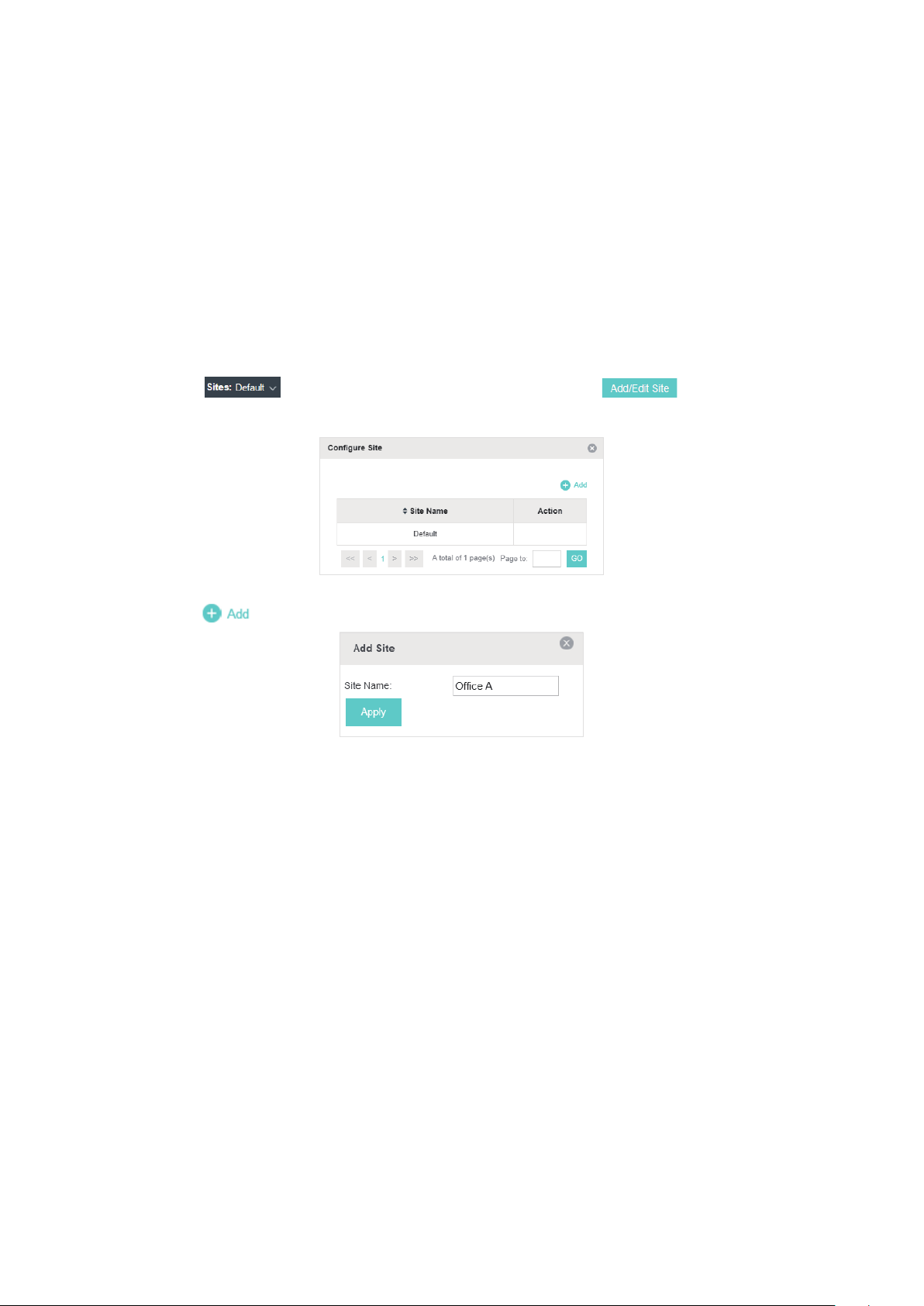
1.5 Create Sites and Adopt EAPs
OC200 can manage multiple EAP networks, which are called sites. Multiple sites are logically
separated, and each site has its own configurations. There is an initial site named Default. If you
have no need to manage EAPs with differnt sites, you can use the default site and skip the Create
Sites section. However, Adopt the EAPs is a necessary step to manage the EAPs.
1.5.1 Create Sites
Follow the steps below to add sites.
1. Click
window will pop up.
2. Click
3. Click Apply to create the site.
in the top left corner of the page and select , and then the following
and set a name for the site.
1.5.2 Adopt the EAPs
OC200 can discover all EAP devices currently connected in the network and display their
connection status. All EAPs are in Pending status when first discovered by OC200. To manage
the EAPs, you need to adopt them. In the quick setup process, OC200 will automatically adopt the
selected EAPs using the default username and password (both are admin). However, if you have
changed the username or password of your EAPs before, OC200 cannot automatically adopt them,
and you need to refer to the following steps to adopt them manually.
To ensure that all EAPs are adopted, follow the steps below:
1. Select a site and go to Access Points > Pending. The table displays all the EAPs that have not
been adopted.
11
Page 18
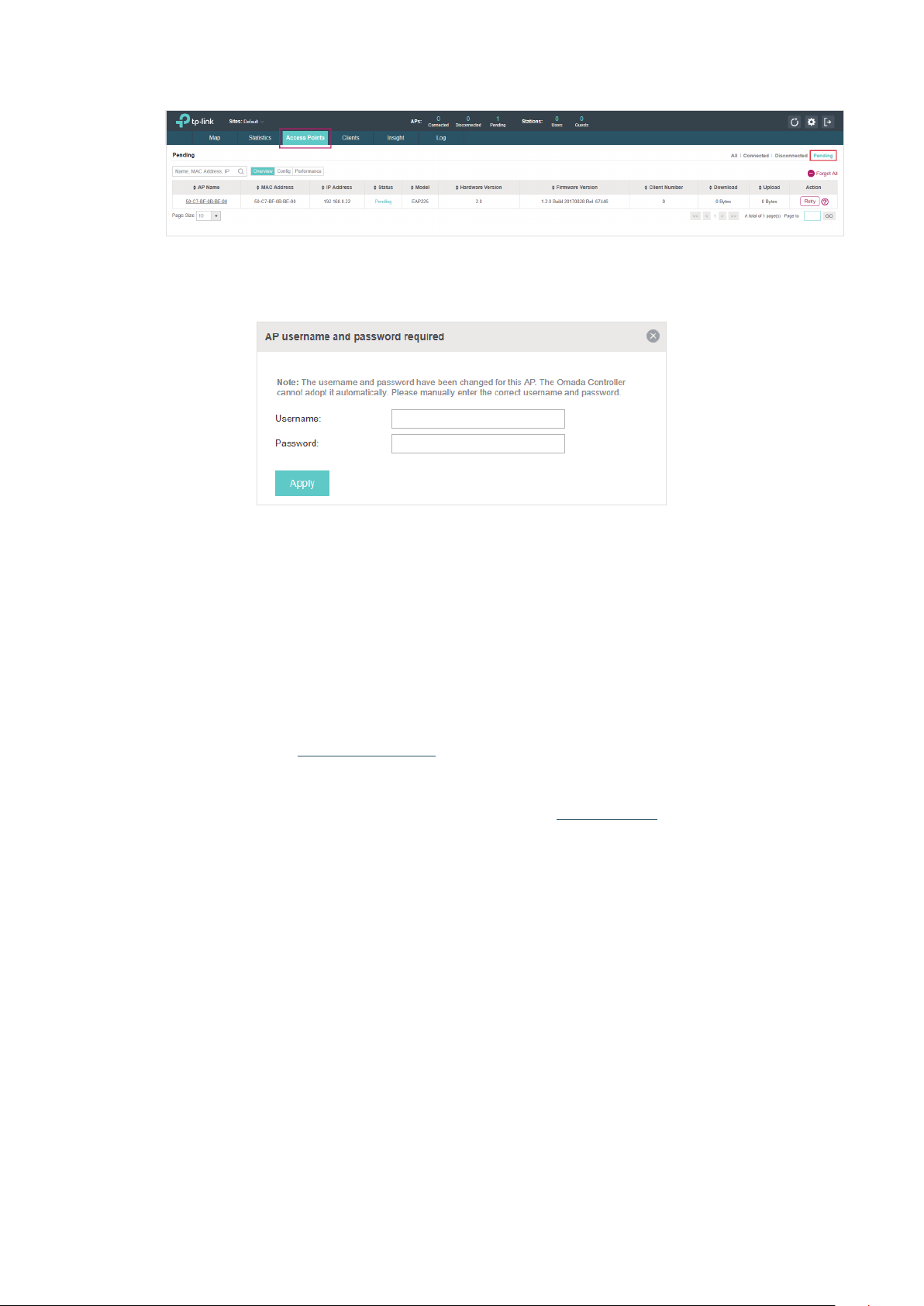
2. Click the Retry button in the Action column and enter the current username and password of the
EAP. Click Apply.
Tips:
If you have a new discovered EAP, you can click the Adopt button in the Action column to adopt the EAP.
·
OC200 will automatically adopt the EAP using the default username and password (both are admin).
If you have multiple new discovered EAPs, and all of them have the default username and password (both
·
are admin), you can click the Batch Adopt button to adopt them in batch. But if there are any EAPs with the
Retry button, it means that the username and password of these EAPs have been changed. You need to first
adopt them before batch adopt the rest EAPs.
3. After EAPs are adopted, the status will change from Pending to Connected. All the EAPs’
username and password will become the same as those of the OC200's administrator account
you created in the Basic Configuration.
Tips:
If you want to change the EAPs' username and password, refer to Device Account.
1.6 Monitor and Manage the EAPs
When all the configurations above are finished, you can centrally monitor and manage the EAPs via
the OC200's management interface. The management interface is divided into three sections as
the following figure shows.
12
Page 19
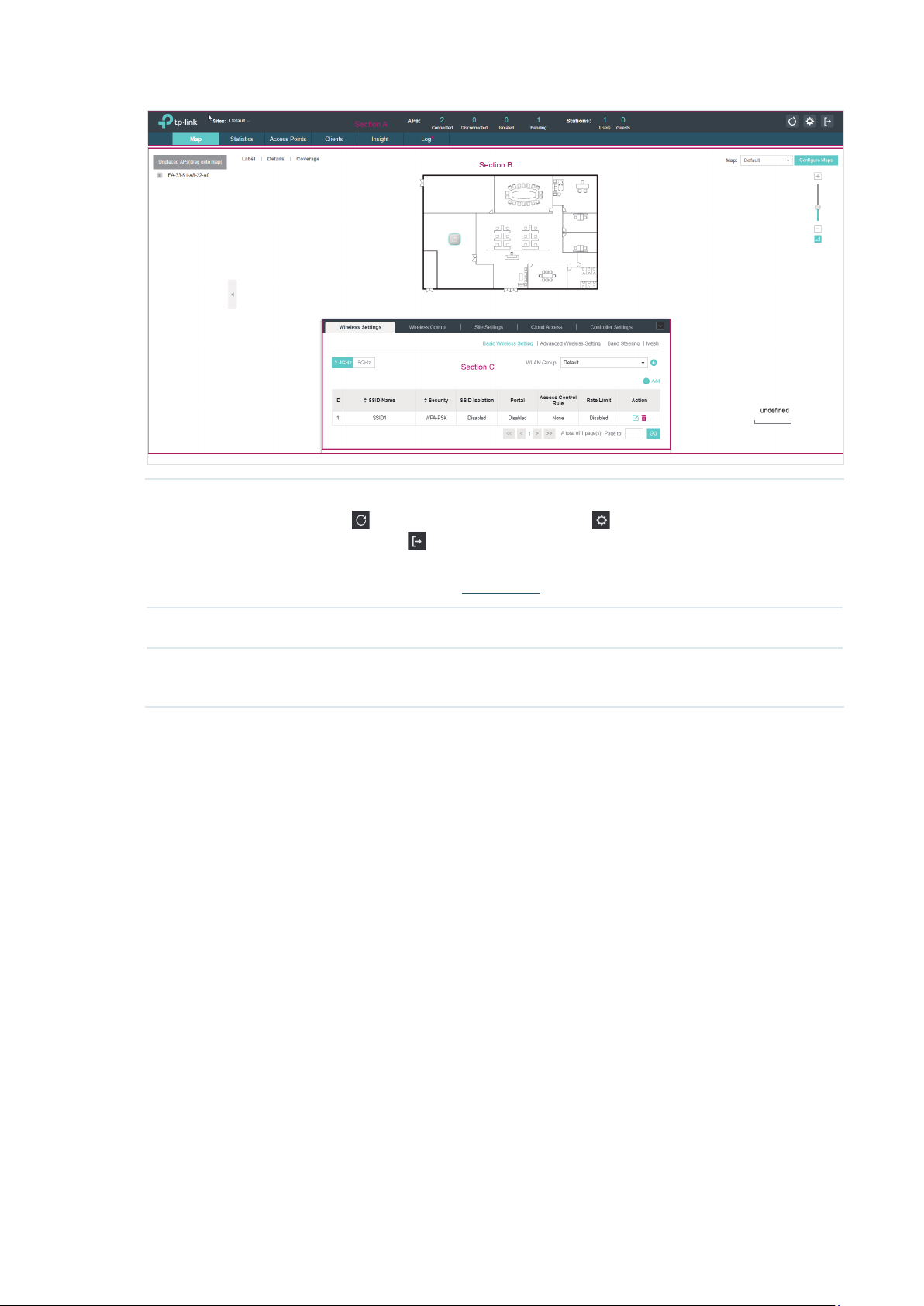
Section A In Section A, you can check the status of EAPs and clients in the network. Also, you
can click
network, and click
Furthermore, the Sites allows you to group your EAPs and manage them in batches.
To configure sites, refer to Create Sites.
Section B In Section B, you can centrally monitor and manage the EAPs and clients.
Section C In Section C, you can globally configure the wireless network. The global
configurations will take effect on all the adopted EAPs.
to refresh the current page, click to globally configure the wireless
to sign out from the management interface.
13
Page 20

2
With OC200 you can monitor the EAP devices and centrally manage your wireless network. This
chapter includes the following sections:
Monitor the Network with the Map
·
View the Statistics of the Network
·
Monitor and Manage the EAPs
·
Monitor and Manage Clients
·
View Clients Statistics during the Specified Period
·
Manage the Rogue APs List
·
View Past Guest Authorization
·
View Logs
·
Monitor and Manage the Network
View Alerts
·
14
Page 21
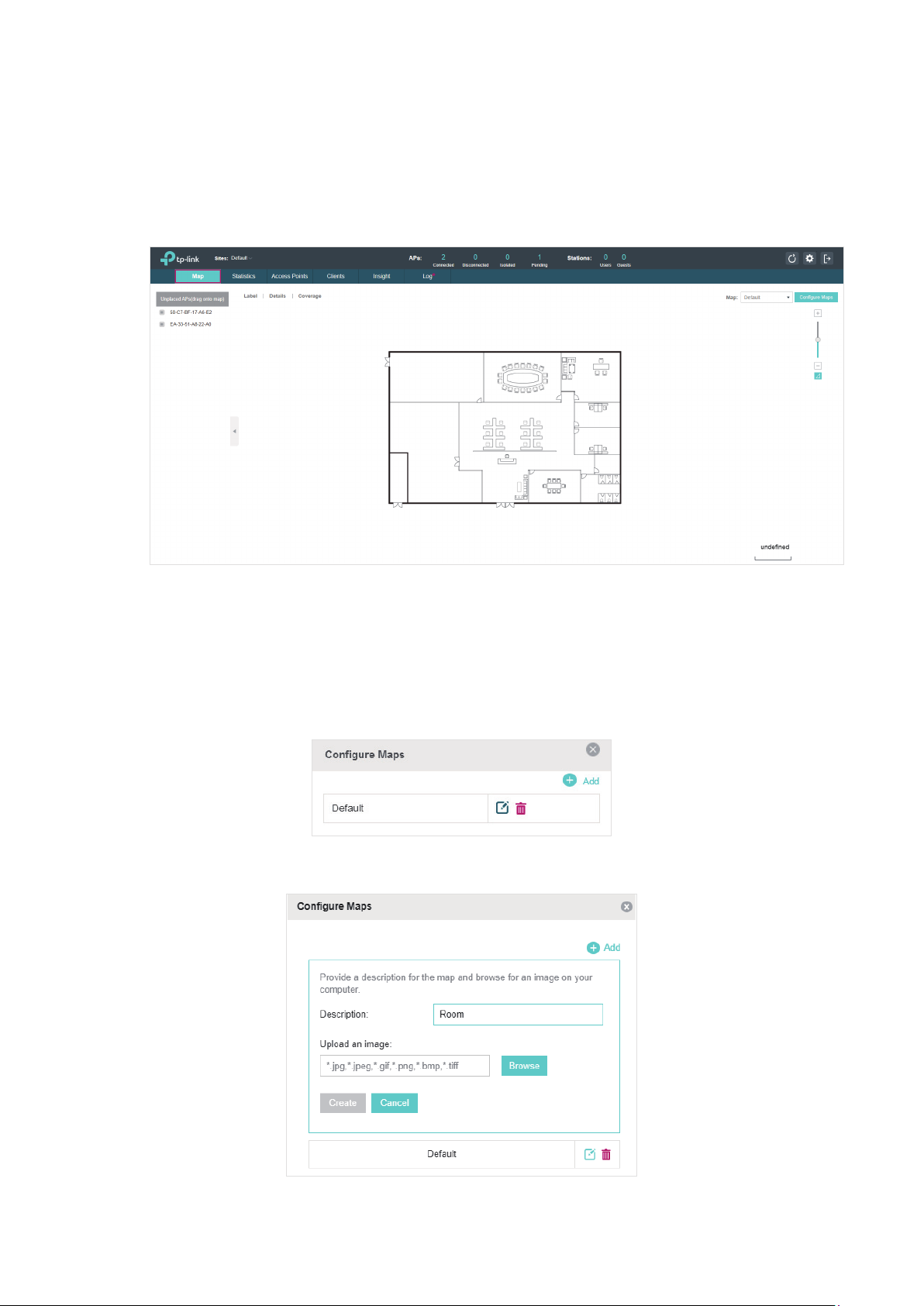
2.1 Monitor the Network with the Map
You can upload your local map images and monitor the status and coverage range of each EAP with
the map. When you initially launch OC200, a default map is displayed as the following figure shows.
Follow the instructions below to add your own map and manage the EAPs via the map.
2.1.1 Add a Map
Prepare a map image in .jpg, .jpeg, .gif, .png, .bmp, .tiff format. And then follow the steps below to
add the map to the OC200.
1. Click Configure Maps on the upper right corner of map and click Add.
2. Enter the map description, select your map image, and click Create.
15
Page 22
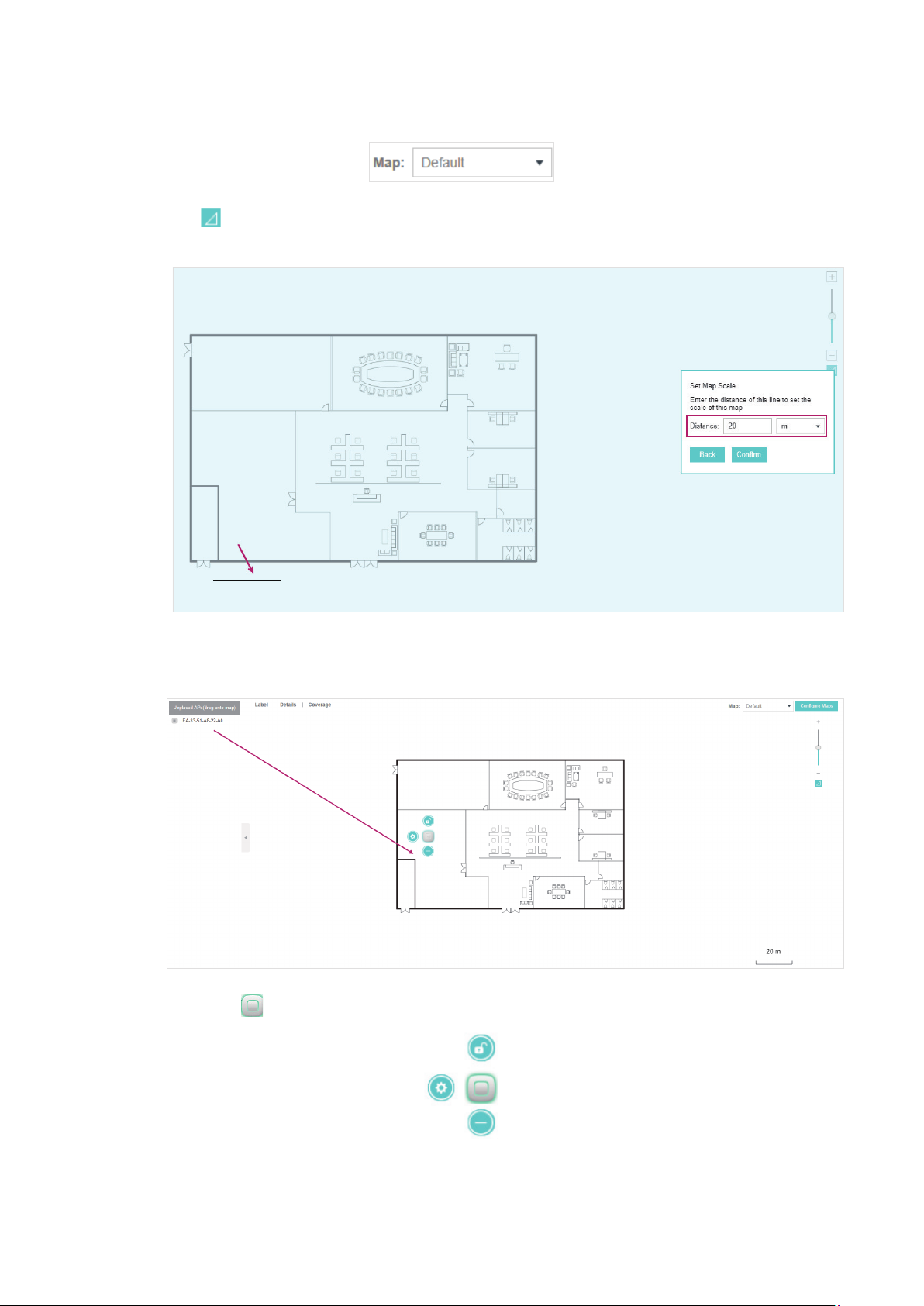
3. Select your local map from the drop-down list on the upper right corner of map area.
4. Click . Draw a line on the map and enter the distance the line represents. Then the OC200 will
compute and generate the map scale automatically based on your configuration.
5. Drag the EAPs from the Unplaced APs list to the appropriate locations on the map according to
their actual locations.
You can click to reveal additional options:
16
Page 23
Lock the selected EAP in the current location on the map.
Unlock the selected EAP and you can drag it to another location.
Display the EAP's details and configure the wireless parameters. Refer to
the EAPs Separately
Remove the selected EAP back into the Unplaced APs list.
2.1.2 Monitor the EAPs on the Map
Click any of the following options to display EAP Label, Details, and Coverage on the map.
Label Display the EAP’s name. The default name is the MAC address of the EAP.
Details Display the EAP’s name, MAC address, IP address, transmitting/receiving channel,
number of connected users, and number of connected guests.
Coverage Display a visual representation of the wireless range covered by EAPs. The actual
signal coverage may be smaller than the visual coverage on the map because the
obstacles around the EAPs will weaken the signal.
Configure
.
17
Page 24
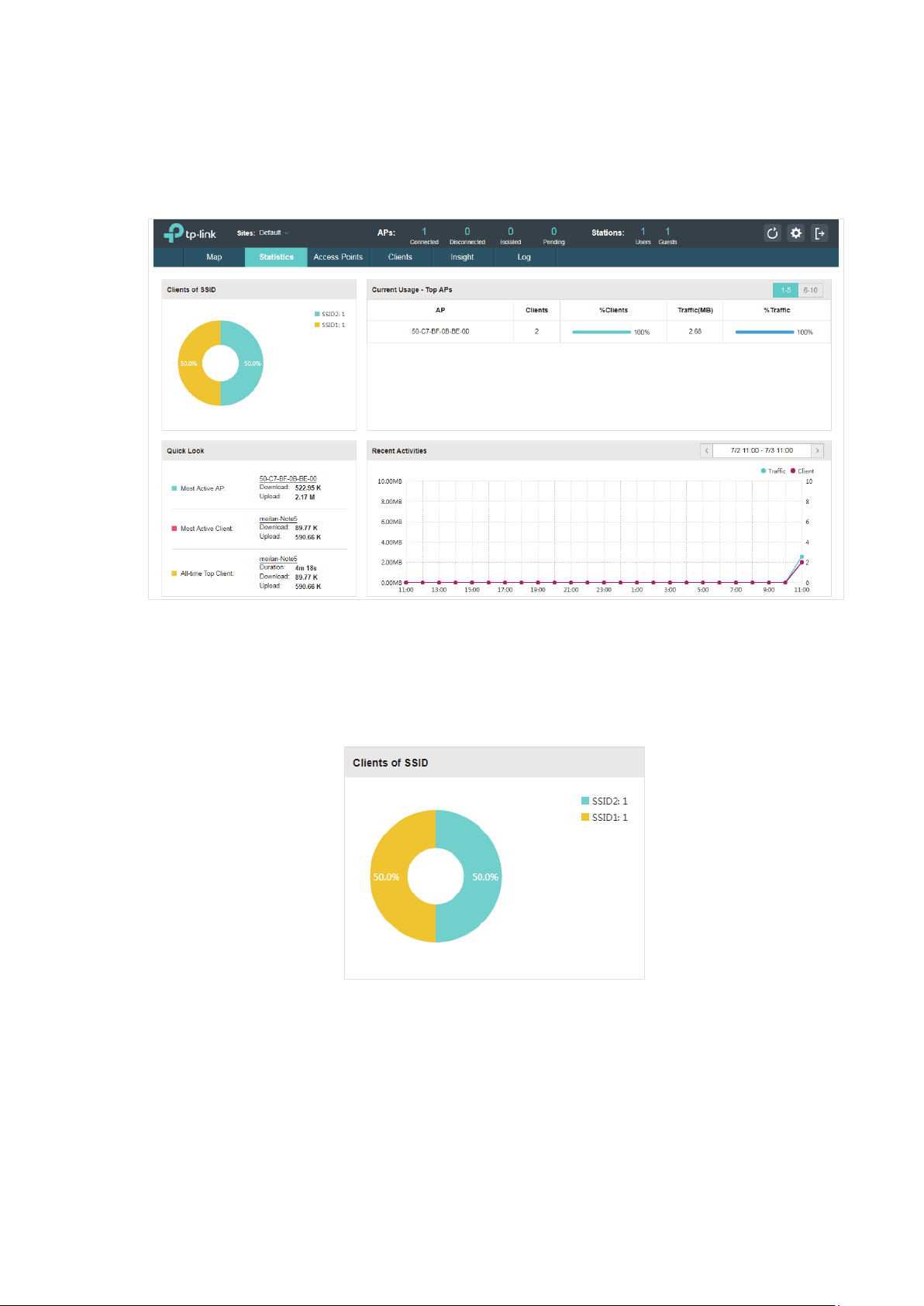
2.2 View the Statistics of the Network
OC200 collects all statistics of the managed EAPs and displays the statistical information via
graphs, pie charts and tables, providing an overview of your wireless network.
2.2.1 View the Client Distribution on SSID
A visual pie chart shows the client distribution on each SSID. For example, the SSID1 has one client,
which occupies 50% of all the clients.
2.2.2 Have a Quick Look at EAPs and Clients
This tab displays the Most Active AP, the Most Active Clients and the All-Time Top Client. You can
click the MAC address of the EAP or the client to see more details.
18
Page 25
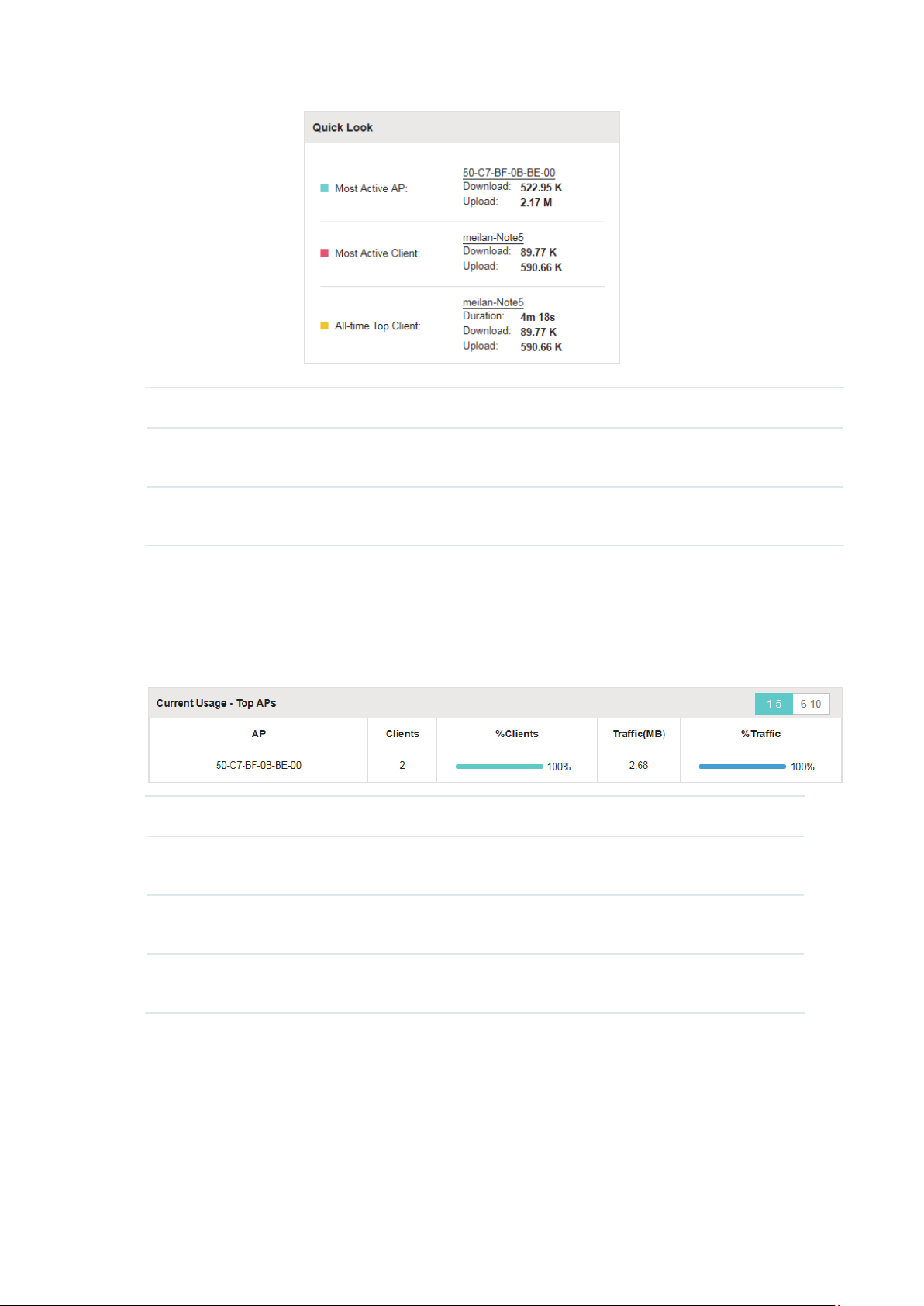
Most Active AP The current connected AP with the maximum traffic.
Most Active
Client
All-time Top
Client
The current connected client with the maximum traffic.
The client with the maximum traffic among all the clients that have ever accessed the
EAP network.
2.2.3 View Current Usage-Top EAPs
This tab lists the number of connected clients and the data traffic condition of the ten APs that use
the most traffic currently.
Clients The amount of clients connected to this EAP.
%Clients The proportion of current connected clients to the Top EAPs' total client
amount.
Traffic (MB) The total amount of data transmitted by this EAP, which equals the sum of the
transmission traffic of all the current clients that connect to the AP.
%Traffic The proportion of the EAP's current data transmission amount to the Top EAPs'
total transmission amount.
2.2.4 View Recent Activities
The Recent Activities statistics can be toggled between a view for the past specific 24 hours and
one for the past specific 30 days.
The left ordinate axis indicates the traffic and the right one represents the number of the clients.
The abscissa axis shows the selected time period. Traffic indicates a visual graph of the network
19
Page 26
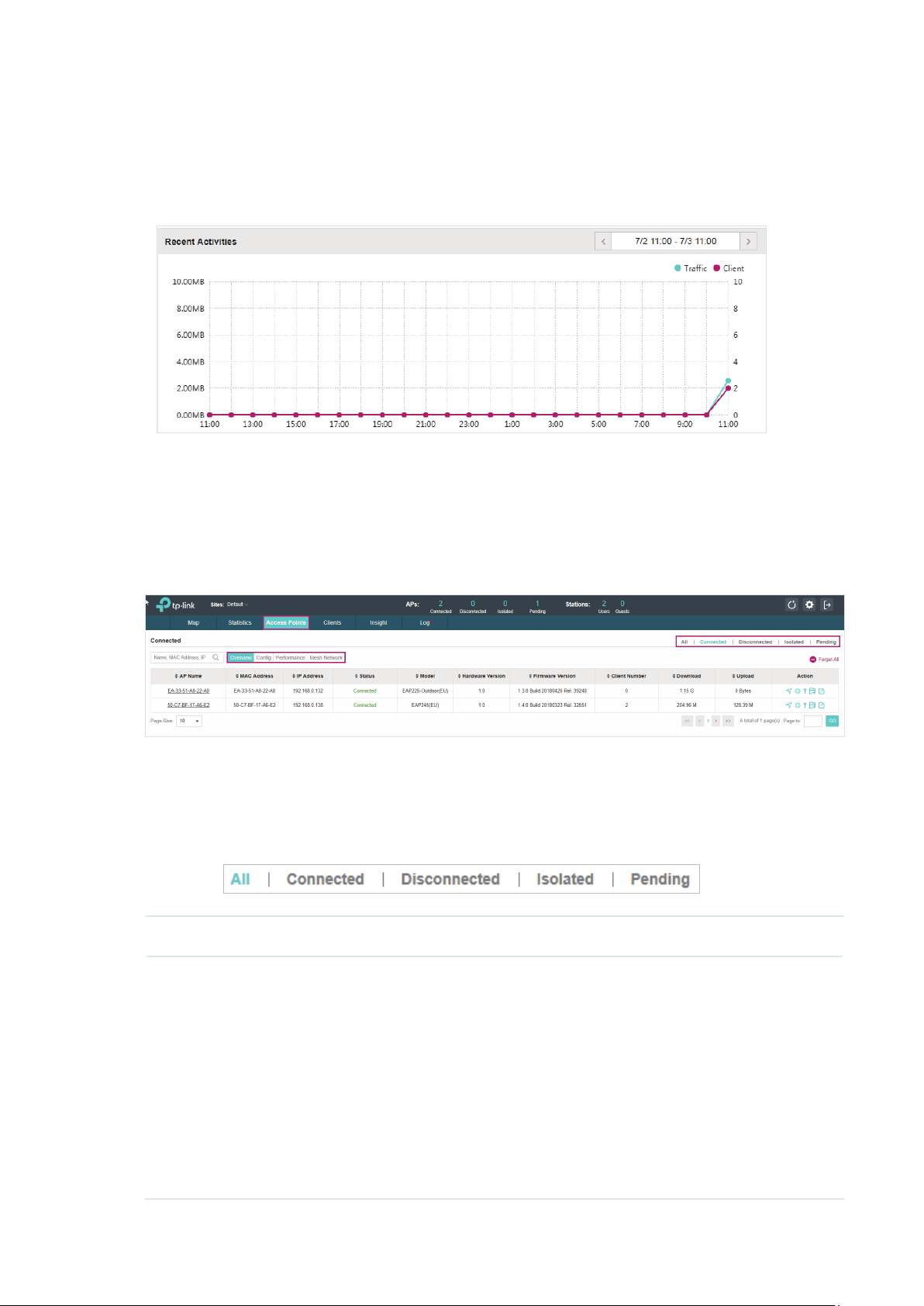
traffic during the selected time period. Client indicates a visual graph of the number of the
connected clients during the selected time period. For example, the statistics information at 15:00
indicates the traffic size and client number from 14:00 to 15:00. In the following figure, at 11 o’clock,
the traffic is about 3MB and there is 2 clients connected to the AP.
2.3 Monitor and Manage the EAPs
OC200 can discover all the EAP devices currently connected to the network and display the
information of them on the Access Points page.
2.3.1 Manage the EAPs in Different Status
According to their connection status, EAPs are divided into four categories: connected,
disconnected, isolated and pending. You can view the EAPs in different status on different pages:
All Displays the information of all EAPs in different status.
Connected Displays the connected EAPs.
The status of connected EAPs includes two cases: Connected and Connected
(Wireless).
Connected: After you adopt a wired EAP in Pending status, its status will become
Provisioning, then Configuring and Connected eventually.
Connected (Wireless): In a mesh network, if an EAP has a successful wireless uplink,
its status will become Adopting (Wireless) and then Connected (Wireless).
Only connected EAPs can be managed. A connected EAP will turn into a pending one
after you forget it. You can refer to
on the page to forget all the connected EAPs.
Forget this AP
to forget an EAP or click Forget All
20
Page 27
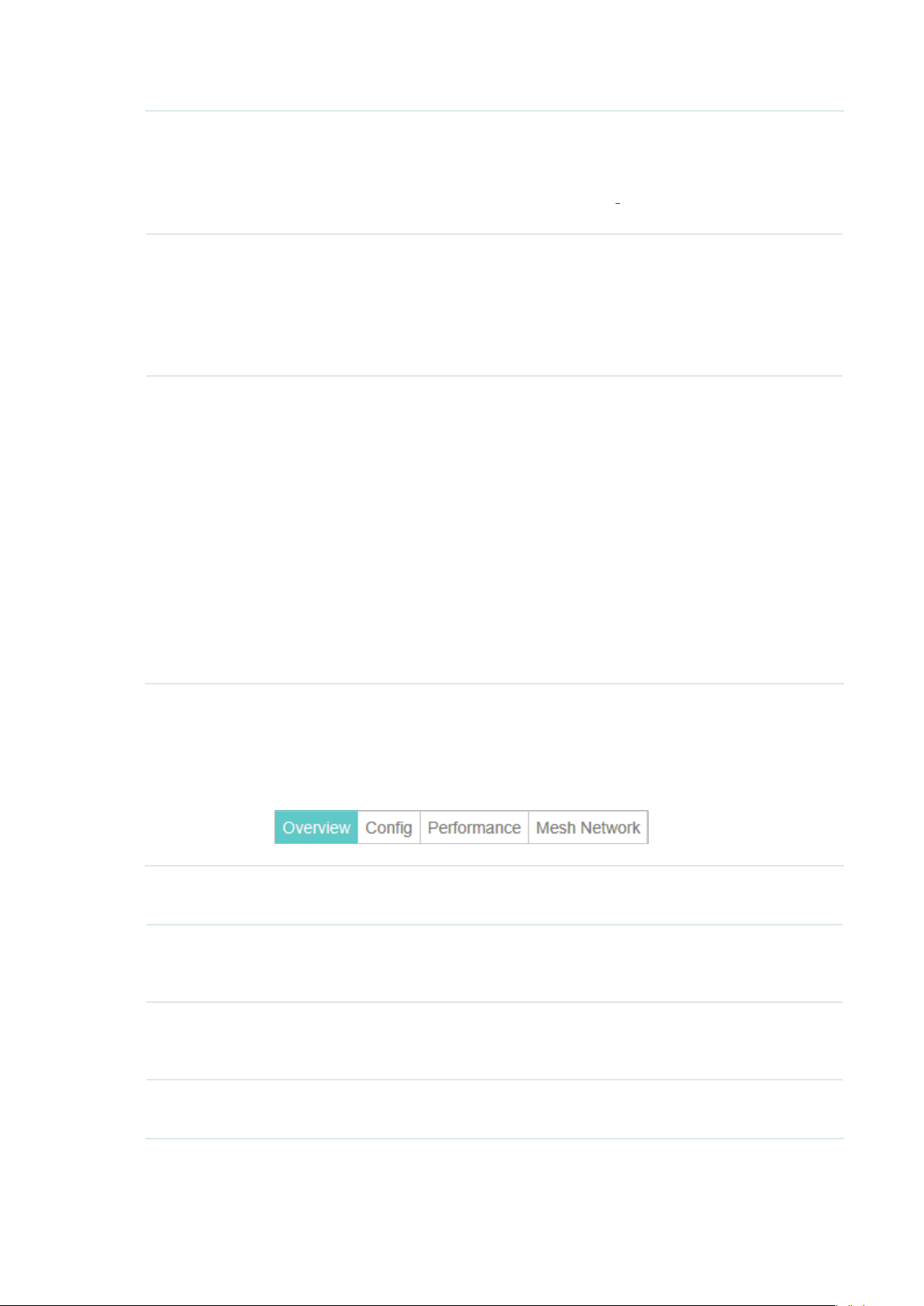
Disconnected Displays the disconnected EAPs.
If a connected EAP powers off or disconnects from the OC200, it will be in
Disconnected status. When a disconnected EAP is reset to factory defaults or forgot,
it will turn into a pending one again. You can refer to
click Forget All on the page to forget all the disconnected EAPs.
Isolated Displays the isolated EAPs.
In a mesh network, when the EAP which has been managed before by OC200 connects
to the network wirelessly and cannot reach the gateway, it goes into the Isolated
state. The isolated EAP searches for wireless uplink and the LED on the device turns
green and flashes off every 5 seconds. To know more about mesh network, refer to
Configure Mesh
Pending Displays the pending EAPs.
The status of pending EAPs includes three cases: Pending, Pending (Wireless) and
Managed by others.
Pending: All the EAPs with wired network connection are in pending status by default
when first discovered by OC200.
Pending (Wireless): The factory default EAP with mesh functions and no wired network
connection is in Pending (Wireless) status when first discovered by OC200.
Managed by others: An EAP is located on the same network as the OC200, but has
been already managed by an existing Omada controller before. You can provide the
username/password to unbind the EAP from the existing controller and begin adoption
in current controller.
.
Forget this AP
to forget a EAP or
Only after pending EAPs are adopted and connected, you can manage them. To adopt
pending EAPs, refer to
Adopt the EAPs
2.3.2 View the Detailed Information of EAPs
You can click Overview, Config,Performance or Mesh Network tab to view different detailed
information of EAPs.
Overview Displays the EAP's name, MAC address, IP address, status, model, hardware version,
firmware version, number of connected clients and download/upload bytes.
Config Displays the EAP’s name, MAC address, IP address, status, model, hardware version,
firmware version, WLAN Group bounded with the 2G and 5G of the EAP, and radio of
the 2G and 5G.
Performance Displays the EAP’s name, MAC address, IP address, status, model, hardware version,
firmware version, number of connected 2G clients and 5G clients, TX(Downloaded
Traffic), RX(Uploaded Traffic), TX 2G and TX 5G.
.
Mesh Network Displays the EAP’s name, MAC address, IP address, status, model, hardware version,
firmware version, number of connected clients, hops, uplink APs and downlink APs.
21
Page 28

2.3.3 Manage the EAPs in the Action Column
You can execute the corresponding operation to the EAP by clicking an icon in the Action column.
Locate the EAP in the map.
Reboot the EAP.
Upgrade the EAP.
You can click Check for upgrade to detect if the current firmware is the latest version.
The latest firmware for the EAP can be detected by the controller automatically. And
you can upgrade the EAP online.
Click Browse to locate and choose the upgrade file in your computer, then click
Upgrade to install the latest EAP firmware. The Status will appear as Upgrading until
the process is complete and the EAP reconnects to the OC200.
Move the EAP to a site.
Select a site that has been created and click Apply. You can group all the EAPs by this
way and centrally manage them on each site.
22
Page 29
Configure the EAP.
For detailed instructions about how to configure the EAP on this window, refer to
Configure the EAPs Separately
Note:
Only managed EAPs can be rebooted or upgraded.
·
The EAP which is managed by the OC200 can not be logged in to its own management interface. To log in to
·
the EAP’s own management interface, forget the EAP first.
.
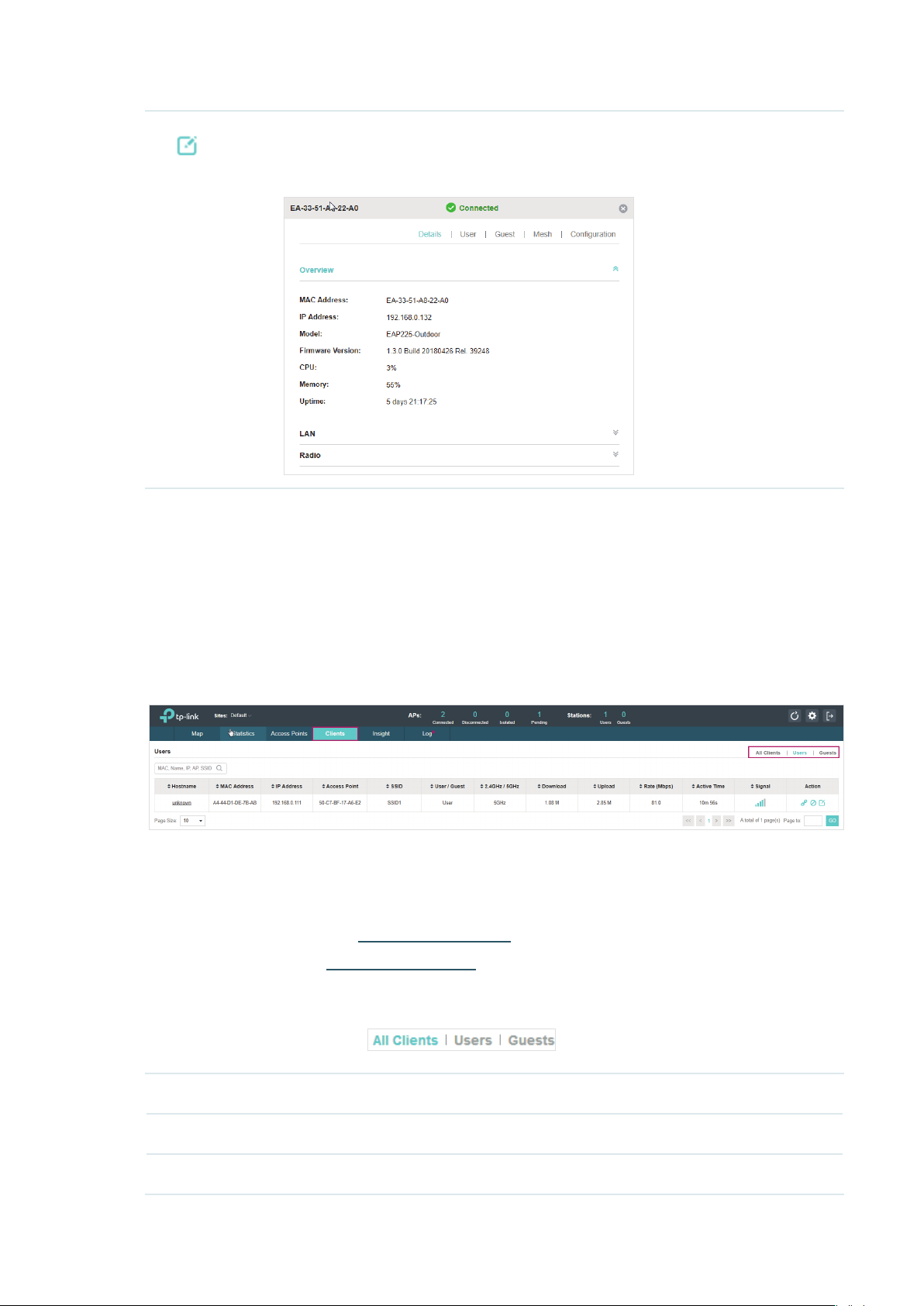
2.4 Monitor and Manage Clients
The Clients tab displays the clients connected to the EAP network.
2.4.1 View the Current Information of Clients
The clients are divided into two types: User and Guest. Users are the clients connected to the EAP
wireless network without the Portal Authentication. Guests are the clients connected to the EAP
wireless network with the Portal Authentication.
You can click the following tabs to respectively view the detailed information of users and guests.
All Clients The page displays the information of all clients including users and guests.
Users The page displays the information of Users.
Guests The page displays the information of Guests.
23
Page 30
2.4.2 Manage Clients in the Action Column
You can execute the corresponding operation to the EAP by clicking an icon in the Action column:
Reconnect the client to the network.
Restrict the client's access to the network.
Configure the rate limit of the client and view the connection history.
Enter the download limit and upload limit and click Apply.
If the client is a Guest, you can click this icon to cancel the authorization for it.
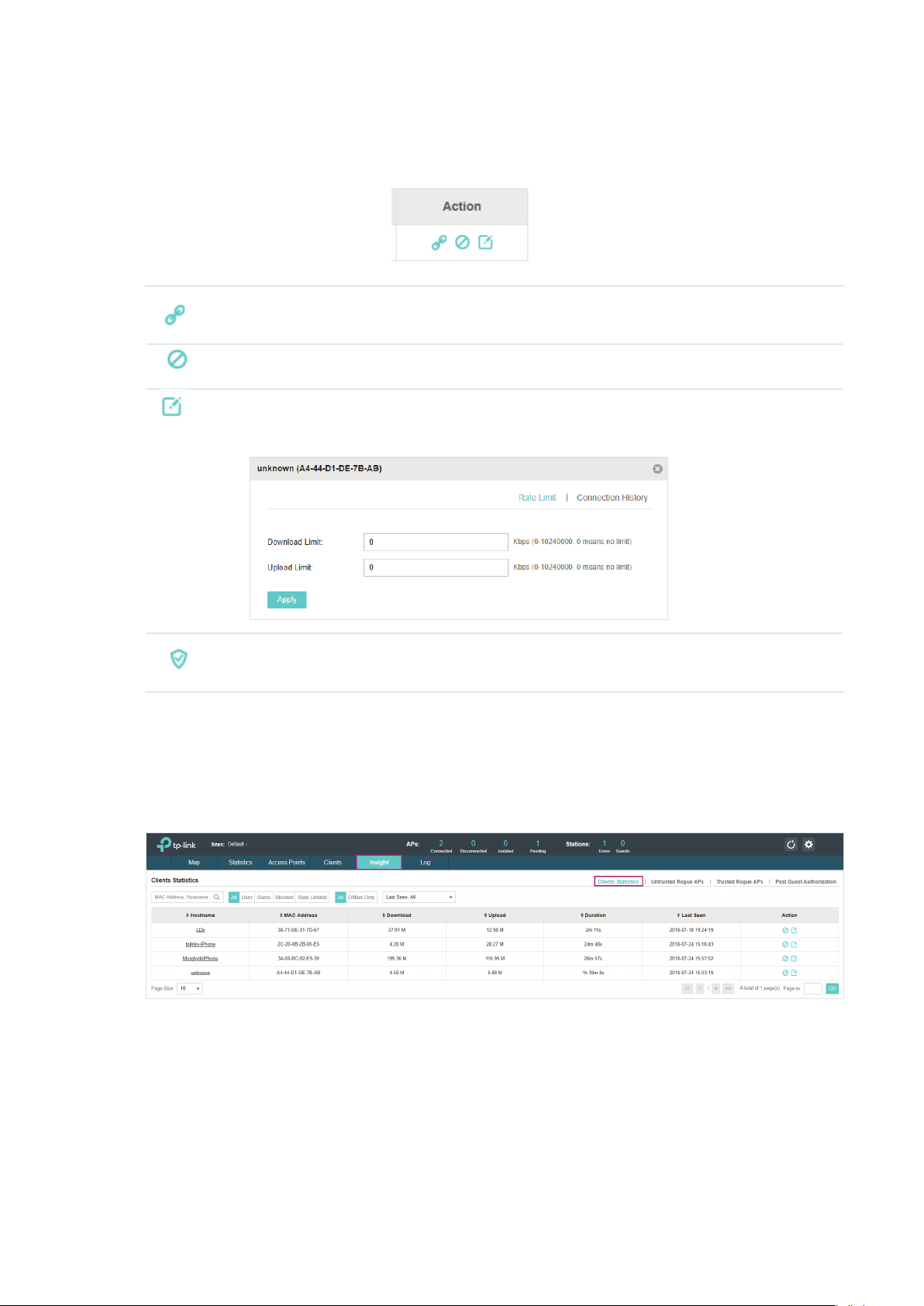
2.5 View Clients Statistics During the Specified Period
The Clients Statistics page under the Insight tab displays the information of clients that have
connected to the EAPs network during a specified period.
2.5.1 Select a Specified Period
Select a period from the drop-down menu. Then the page will display clients that have connected to
the EAPs network during the period.
24
Page 31

2.5.2 View the History Information of Clients
You can click the client's MAC address to get its connection history and configure the Rate Limit
feature for this client. In addition, you can click the following tabs to view the information of different
types of clients:
All The page displays the history information of all the clients.
User
Guest
Blocked The page displays the clients that have been blocked.
Rate Limited The page displays the clients that have been limited upload or download rate.
All The page displays the history information of all clients.
Offline Only The page displays the history information of the off-line clients.
The page displays the history information of Users.
Users are the clients connected to the EAP wireless network without the
Authentication
The page displays the history information of Guests.
Guests are the clients connected to the EAP wireless network with the
Authentication
.
.
2.5.3 Manage Clients in the Action Column
Portal
Portal
You can execute the corresponding operation to the EAP in the Action column:
Block the client's access to the network.
25
Page 32

Resume the client's access.
Configure the rate limit of the client and view the connection history.
Remove the limit to the client’s upload or download rates.
2.6 Manage the Rogue APs List
A Rogue AP is an access point that has been installed on a secure network without explicit
authorization from a system administrator. The OC200 can scan all channels to detect all nearby
EAPs. If rogue APs are detected, they will be shown on the Untrusted Rogue APs list. Besides, you
can move the untrusted rogue APs to the Trusted Rogue APs list.
By default, the Rogue AP Detection feature is disabled. To allow your EAP to detect nearby APs, you
need to enable this feature for this EAP. You can refer to Rogue AP Detection.
2.6.1 Manage the Untrusted Rogue APs List
The Untrusted Rogue APs page displays the detailed information of untrusted rogue APs.
You can execute the corresponding operation to the EAP in the Action column:
Move the untrusted rogue AP to the Trusted Rogue APs list.
Delete this record.
Delete all records.
2.6.2 Manage the Trusted Rogue APs List
The Trusted Rogue APs page displays the detailed information of trusted rogue APs.
26
Page 33

You can execute the corresponding operation to the EAP by clicking an icon in the Action column:
Move the trusted rogue AP to the Untrusted Rogue APs list.
Export and download the current Trusted Rogue APs list and save it on your PC.
Import a saved Trusted Rogue APs list. If the MAC address of an AP appears in list, it will
not be detected as a rogue AP.
Please follow the steps below:
1. Select Replace (replace the current Trusted Rogue APs list with the one you import) or
Merge (add the APs in the file to the current Trusted Rogue APs list).
2. Click Browse to locate the file and choose it.
3. Click Import to import the Trusted Rogue APs list.
2.7 View Past Guest Authorization
The Past Guest Authorization page displays the details about all the clients that accessed the
network during a certain time period. You can select a period in the drop-down list.
27
Page 34

2.8 View Logs
The logs of OC200 can effectively record, classify and manage the system information of the
managed EAPs, providing powerful support for you to monitor network operation and diagnose
malfunctions. The Logs page displays EAP's MAC address, level, occurred time and content.
2.9 View Alerts
You can see the status change of your EAPs on the Unarchived Alerts page. You can click or
to move unarchived alerts to the Archived Alerts page.
As follows, the Archived Alerts page displays the alerts archived by you. You can click or
to delete the records.
28
Page 35

3
This chapter introduces the global configurations applied to all the managed EAPs. To configure a
specific EAP, please refer to Chapter 5 Configure the EAPs Separately.
In global configurations, you can configure the following items:
Wireless Network
·
Access Control
·
Portal Authentication
·
Free Authentication Policy
·
MAC Filter
·
Scheduler
·
QoS
·
Congure the EAPs Globally
Site Settings
·
29
Page 36

3.1 Wireless Network
In addition to the wireless network you created in Quick Start, you can add more wireless networks
and configure the advanced wireless parameters to improve the network quality.
3.1.1 Add Wireless Networks
To add wireless networks, follow the steps below.
1. Go to Wireless Settings > Basic Wireless Setting.
2. Select a band frequency and click at the right of
to add a WLAN group. WLAN groups are an easy way to quickly deploy EAPs by creating a
template-based set of SSIDs with wireless parameters. Different WLAN groups can be applied
to different EAPs. If you have no need to group your wireless networks, you can use the default
WLAN group and skip this step.
3. Specify a name for the group and click Apply.
4. Select the brand frequency and WLAN group .
5. Click
6. Configure the parameters in the following window.
to add an SSID to the specific WLAN group.
30
Page 37

SSID Name Enter an SSID name contains up to 32 characters.
Wireless Vlan ID Set a VLAN ID for the wireless network. Wireless networks with the same VLAN
ID are grouped to a VLAN.
The value ranges from 0 to 4094. 0 means VLAN function is disabled.
SSID Broadcast With the option enabled, EAPs will broadcast the SSID to the nearby hosts, so
that those hosts can find the wireless network identified by this SSID. If this
option is disabled, users must enter the SSID manually to connect to the EAP.
Enabled by default.
Security Mode
SSID Isolation With the option enabled, the devices connected in the same SSID of the same
Access Control Rule
Select the security mode of the wireless network.
None: The hosts can access the wireless network without authentication.
WEP/WPA-Enterprise/WPA-PSK
accessing the wireless network. For the network security, you are suggested to
encrypt your wireless network. Settings vary in different security modes and the
details are in the following introduction.
AP cannot communicate with each other.
Disabled by default.
Select an Access Control rule for this SSID. For more information, refer to
Access Control
.
31
: The hosts need to get authenticated before
Page 38

Following is the detailed introduction of WEP, WPA-Enterprise and WPA-PSK.
WEP
WEP is based on the IEEE 802.11 standard and less safe than WPA-Enterprise and WPA-PSK.
Note:
WEP is not supported in 802.11n mode or 802.11ac mode. If WEP is applied in 802.11n, 802.11 ac or 802.11n/
ac mixed mode, the clients may not be able to access the wireless network. If WEP is applied in 11b/g/n mode
(2.4GHz) or 11a/n (5GHz), the EAP device may work at a low transmission rate.
Type Select the authentication type for WEP.
Auto: The OC200 can select Open System or Shared Key automatically based on
the wireless station's capability and request.
Open System: Clients can pass the authentication and associate with the wireless
network without password. However, correct password is necessary for data
transmission.
Shared Key: Clients have to input password to pass the authentication, otherwise it
cannot associate with the wireless network or transmit data.
Key Selected Select one key to specify. You can configure four keys at most.
WEP Key Format Select ASCII or Hexadecima as the WEP key format.
ASCII: ASCII format stands for any combination of keyboard characters of the
specified length.
Hexadecimal: Hexadecimal format stands for any combination of hexadecimal
digits (0-9, a-f, A-F) with the specified length.
Key Type Select the WEP key length for encryption.
64Bit: Enter 10 hexadecimal digits or 5 ASCII characters.
128Bit: Enter 26 hexadecimal digits or 13 ASCII characters.
152Bit: Enter 32 hexadecimal digits or 16 ASCII characters.
Key Value Enter the WEP keys. The length and valid characters are affected by key type.
32
Page 39

WPA-Enterprise
The WPA-Enterprise mode requires a RADIUS server to authenticate clients. Since the WPA-
Enterprise can generate different passwords for different clients, it is much safer than WPA-PSK.
However, it costs much more to maintain and is usually used by enterprise.
Version Select the version of WPA-Enterprise.
Auto: The EAP will automatically choose the version used by each client device.
WPA/WPA2: Two versions of Wi-Fi Protected Access.
Encryption Select the Encryption type.
Auto: The default setting is Auto and the EAP will select TKIP or AES
automatically based on the client device's request.
TKIP: Temporal Key Integrity Protocol. TKIP is not supported in 802.11n mode,
802.11ac mode or 802.11n/ac mixed mode. If TKIP is applied in 802.11n,
802.11 ac or 802.11n/ac mixed mode, the clients may not be able to access the
wireless network of the EAP. If TKIP is applied in 11b/g/n mode (2.4GHz) or 11a/
n mode(5GHz), the device may work at a low transmission rate.
AES: Advanced Encryption Standard. We recommend you select AES as the
encryption type because it is more secure than TKIP.
RADIUS Server IP Enter the IP address of the RADIUS Server.
RADIUS Port Enter the port number of the RADIUS Server.
RADIUS Password Enter the shared secret key of the RADIUS server.
Group Key Update
Period
Specify a group key update period, which instructs the EAP how often it should
change the encryption keys. The value can be either 0 or 30~8640000 seconds.
0 means no change of the encryption key anytime.
33
Page 40

WPA-PSK
Based on a pre-shared key, WPA-PSK is characterized by high safety and simple settings and is
mostly used by common households and small businesses.
Version Select the version of WPA-PSK.
Auto: The EAP will automatically choose the version for each client device.
WPA-PSK: Pre-shared key of WPA.
WAP2-PSK: Pre-shared key of WPA2.
Encryption Select the Encryption type.
Auto: The default setting is Auto and the EAP will select TKIP or AES automatically
based on the client request.
TKIP: Temporal Key Integrity Protocol. TKIP is not supported in 802.11n mode,
802.11ac mode or 802.11n/ac mixed mode. If TKIP is applied in 802.11n, 802.11
ac or 802.11n/ac mixed mode, the clients may not be able to access the wireless
network of the EAP. If TKIP is applied in 11b/g/n mode (2.4GHz) or 11a/n mode(5GHz),
the device may work at a low transmission rate.
AES: Advanced Encryption Standard. We recommend you select AES as the
encryption type for it is more secure than TKIP.
Wireless
Password
Group Key
Update Period
Configure the wireless password with ASCII or Hexadecimal characters.
For ASCII, the length should be between 8 and 63 characters with combination of
numbers, letters (case-sensitive) and common punctuations. For Hexadecimal, the
length should be 64 characters (case-insensitive, 0-9, a-f, A-F).
Specify a group key update period, which instructs the EAP how often it should
change the encryption keys. The value can be either 0 or 30~8640000 seconds. 0
means the encryption keys will not be changed all the time.
7. Enable Rate Limit for the clients to guarantee the network balance. Enter the value for Download
Limit and Upload Limit. 0 means unlimited. Note that the download and upload rate will be limited
to the minimum of the value configured in SSID, client and portal configuration.
34
Page 41

8. Click Apply.
3.1.2 Configure Advanced Wireless Parameters
Proper wireless parameters can improve the network's stability, reliability and communication
efficiency. The advanced wireless parameters consist of Fast Roaming, Beacon Interval, DTIM
Period, RTS Threshold, Fragmentation Threshold and Airtime Fairness.
To configure the advanced wireless parameters, follow the steps below.
1. Go to Wireless Settings > Advanced Wireless Setting.
2. Enable Fast Roaming and configure the corresponding parameters.
35
Page 42

Fast Roaming With this option enabled, 11k/v capable clients can have improved fast
roaming experience when moving among different APs.
Dual Band 11k Report With this feature disabled, the OC200 provides candidate AP report that
contains the APs in the same band as the clients. With this feature enabled,
the controller provides candidate AP report that contains the APs in both
2.4GHz and 5GHz bands.
Force-disassociation The OC200 dynamically monitors the link quality of every associated client.
When the client’s current link quality drops below the predefined threshold
and there are some other APs with better signal, the current AP issues an
11v roaming suggestion to the client.
With Force-disassociation disabled, the AP only issues a roaming
suggestion, but whether to roam or nor is determined by the client.
With Force-disassociation enabled, the AP not only issues a roaming
suggestion but also disassociates the client after a while. Thus the client
is supported to re-associate to a better AP. This function is recommended
when there are sticky clients that don‘t roam.
3. Click Apply.
4. Select the band frequency
.
5. Configure the following parameters.
Beacon Interval Beacons are transmitted periodically by the EAP device to announce the
presence of a wireless network for the clients. Beacon Interval value determines
the time interval of the beacons sent by the device.
You can specify a value between 40 and 100ms. The default is 100ms.
DTIM Period The DTIM (Delivery Traffic Indication Message) is contained in some Beacon
frames. It indicates whether the EAP device has buffered data for client devices.
The DTIM Period indicates how often the clients served by this EAP device
should check for buffered data still on the EAP device awaiting pickup.
You can specify the value between 1-255 Beacon Intervals. The default value is 1,
indicating clients check for buffered data on the EAP device at every beacon. An
excessive DTIM interval may reduce the performance of multicast applications,
so we recommend you keep it by default.
RTS Threshold RTS (Request to Send) can ensure efficient data transmission. When RTS is
activated, the client will send a RTS packet to EAP to inform that it will send data
before it send packets. After receiving the RTS packet, the EAP notices other
clients in the same wireless network to delay their transmitting of data and
informs the requesting client to send data, thus avoiding the conflict of packet.
If the size of packet is larger than the RTS Threshold, the RTS mechanism will be
activated.
If you specify a low threshold value, RTS packets are sent more frequently
and help the network recover from interference or collisions that might occur
on a busy network. However, it also consumes more bandwidth and reduces
the throughput of the packet. We recommend you keep it by default. The
recommended and default value is 2347.
36
Page 43

Fragmentation
Threshold
Airtime Fairness With this option enabled, each client connecting to the EAP can get the same
The fragmentation function can limit the size of packets transmitted over the
network. If a packet exceeds the Fragmentation Threshold, the fragmentation
function is activated and the packet will be fragmented into several packets.
Fragmentation helps improve network performance if properly configured.
However, too low fragmentation threshold may result in poor wireless
performance caused by the extra work of dividing up and reassembling of
frames and increased message traffic. The recommended and default value is
2346 bytes.
amount of time to transmit data, avoiding low-data-rate clients to occupy
too much network bandwidth and improving the network throughput. We
recommend you enable this function under multi-rate wireless networks.
6. Click Apply.
3.1.3 Configure Band Steering
A client device that is capable of communicating on both the 2.4GHz and 5GHz frequency bands will
typically connect to the 2.4GHz band. However, if too many client devices are connected to an EAP
on the 2.4GHz band, the efficiency of communication will be diminished. Band Steering can steer
dual-band clients to the 5GHz frequency band which supports higher transmission rates and more
client devices, and thus to greatly improve the network quality.
To configure Band Steering, follow the steps below.
1. Go to Wireless Settings > Band Steering.
2. Check the box to enable the Band Steering function.
3. Configure the following parameters to balance the clients on both frequency bands:
37
Page 44

Connection Threshold/
Difference Threshold
Max Failures If a client repeatedly attempts to associate with the EAP on the 5GHz band
Connection Threshold defines the maximum number of clients connected
to the 5GHz band. The value of Connection Threshold is from 2 to 40, and
the default is 20.
Difference Threshold defines the maximum difference between the
number of clients on the 5GHz band and 2.4GHz band. The value of
Difference Threshold is from 1 to 8, and the default is 4.
When the following two conditions are both met, the EAP prefer to refuse
the connection request on 5GHz band and no longer steer other clients to
the 5GHz band:
1. The number of clients on the 5GHz band reaches the Connection
Threshold value.
2. The difference between the number of clients on the 2.4GHz band and
5GHz band reaches the Difference Threshold value.
and the number of rejections reaches the value of Max Failures, the EAP
will accept the request.
The value is from 0 to 100, and the default is 10.
4. Click Apply.
3.1.4 Configure Mesh
Mesh is used to establish a wireless network or expand a wired network through wireless
connection on 5GHz radio band. In practical application, it can help users to conveniently deploy
APs without requiring Ethernet cable. After mesh network establishes, the EAP devices can be
configured and managed within OC200 in the same way as wired EAPs. Meanwhile, because of
the ability to self-organize and self-configure, mesh also can efficiently reduce the configuration
overhead.
Note:
Only EAP225-Outdoor with specific firmware (version 1.3 or above) is available for mesh function currently.
·
Only the EAPs in the same site can establish a mesh network.
·
To understand how mesh can be used, the following terms used in OC200 will be introduced:
Root AP: The AP is managed by OC200 with a wired data connection that can be configured to
·
relay data to and from mesh APs (Downlink AP).
Isolated AP: When the EAP which has been managed before by OC200 connects to the network
·
wirelessly and cannot reach the gateway, it goes into the Isolated state.
Mesh AP: An isolated AP will be mesh AP after establishing a wireless connection to the AP with
·
network access.
Uplink AP/Downlink AP: Among mesh APs, the AP that offers the wireless connection for other
·
APs is Uplink AP. A Root AP or an intermediate AP can be the Uplink AP. And the AP that connects
38
Page 45

to the Uplink AP is called Downlink AP. An uplink AP can offer direct wireless connection for 4
Downlink APs at most.
Wireless Uplink: The action that a Downlink AP connects to the uplink AP.
·
Hops: In a deployment that uses a root AP and more than one level of wireless uplink with
·
intermediate APs, the uplink tiers can be referred to by root, first hop, second hop and so on. The
hops cannot be more than 3.
In a basic mesh network as shown below, there is a root AP that is connected by Ethernet
cable, while other isolated APs have no wired data connection. Mesh allows the isolated APs to
communicate with pre-configured root AP on the network. Once powered up, factory default or
unadopted EAP devices can sense the EAP in range and make itself available for adoption within
the OC200.
Internet
Wireless Uplink
Router (DHCP Server)
Wired LAN Connection
OC200
Switch
Root AP Mesh AP
(Hops: 1)
Mesh APs
After all the EAPs are adopted, a mesh network is established. Then the EAPs connected to the
network wirelessly also can broadcast SSIDs and relay network traffic to and from the network
through the uplink AP.
To establish a mesh network, follow the steps below.
Enable Mesh Function.
·
Adopt the Root AP.
·
Set up wireless uplink by adopting APs in Pending (Wireless) or Isolated status.
·
1. Go to Wireless Settings > Mesh.
39
Page 46

2. Check the box to enable the Mesh function.
3. Configure the following parameters to maintain the mesh network:
Auto Failover Enable or disable Auto Failover.
Auto Failover is used for the OC200 to automatically maintain the mesh
network. With this feature enabled, the OC200 can automatically select
an uplink AP for the isolated EAP to establish Wireless Uplink. Thus the
OC200 will automatically select a new uplink AP for the mesh EAPs to
when the original uplink fails.
Connectivity Detection Specify the method of Connection Detection.
In a mesh network, the APs can send ARP request packets to a fixed IP
address to test the connectivity. If the link fails, the status of these APs will
change to Isolated.
Auto (Recommended): Select this method and the mesh APs will send ARP
request packets to the default gateway for the detection.
Custom IP Address: Select this method and specify a desired IP address.
The mesh APs will send ARP request packets to the custom IP address
to test the connectivity. If the IP address of the AP is in different network
segments from the custom IP address, the AP will use the default gateway
IP address for the detection.
4. Click Apply.
5. Go to Access Points > Pending and adopt the Root AP. Then the status of the Root AP will
change into Connected.
6. Install the EAP that will uplink the Root AP wirelessly. Make sure the intended location is within
the range of Root AP. The EAPs that is waiting for Wireless Uplink includes two cases: factory
default EAPs and EAPs that has been managed by OC200 before.
40
Page 47

1 ) For the factory default EAP, after powering on the device, the EAP will be in Pending (Wireless)
status. Go to Access Points > Pending and adopt the EAPs in Pending (Wireless) status.
After adoption begins, the status of Pending (Wireless) EAP will become Adopting (Wireless) and
then Connected (Wireless). It should take roughly 2 minutes to show up Connected (Wireless)
within your OC200.
2 ) For the EAP that has been managed by OC200 before and cannot reach the gateway, it goes
into Isolated status when it is discovered again. Go to Access Points > Isolated, click
The following page will shown, go to Mesh, then click to connect the Uplink AP.
.
Once adoption has finished, your device can be managed by the OC200 in the same way as a
wired EAP. You can click the EAP’s name on the Access Points tab to view and configure the mesh
parameters of the EAP on the pop-up window. Please refer to View Mesh Information of the EAP.
41
Page 48

Tips:
You can manually select the uplink AP that you want to connect in the uplink EAP list. To build a mesh network
·
with better performance, we recommend that you select the Uplink AP with the strongest signal, least hop
and least Downlink AP.
You can enable Auto Failover to make the OC200 automatically select an uplink AP for the isolated EAP to
·
establish Wireless Uplink. And the OC200 will automatically select a new uplink AP for the mesh EAPs when
the original uplink fails.
3.2 Access Control
Access Control is used to block or allow the clients to access specific subnets. To configure
Access Control rules, follow the steps below.
1. Go to Wireless Control > Access Control.
2. Click to add a new Access Control rule.
3. Configure the following parameters.
42
Page 49

Rule Name Specify a name for this rule.
Rule Mode Select the mode for this rule.
Block: Select this mode to block clients to access the specific subnets.
Allow: Select this mode to allow clients to access the specific subnets.
Rule Members Specify the member subnets for this rule.
Subnets: Enter the subnet that will follow the rule mode in the format X.X.X.X/X
and click
Except Subnets: Enter the excepted subnet in the format X.X.X.X/X and click
. Up to 16 subnets can be added. The rule mode will not apply to the
subnet that is in both of the Subnets list and Except Subnets list.
. Up to 16 subnets can be added.
4. Click Apply.
5. Go to Wireless Settings > Basic Wireless Setting and enable Access Control function of a
selected SSID.
3.3 Portal Authentication
Portal authentication enhances the network security by providing authentication service to the
clients that just need temporary access to the wireless network. Such clients have to log into a
web page to establish verification, after which they will access the network as guests. What's more,
you can customize the authentication login page and specify a URL which the newly authenticated
clients will be redirected to.
To configure Portal Authentication, go to Wireless Control > Portal and click
.
Then the following window will pop up:
43
Page 50

These authentication methods are available:
No Authentication, Simple Password, Local User, Voucher
,
SMS, Facebook, External RADIUS Server
to configure each Portal authentication.
3.3.1 No Authentication
With No Authentication configured, clients can access the network without any authentication.
Follow the steps below to configure No Authentication:
1. Go to Wireless Settings > Basic Wireless Settings and create an SSID for the Portal.
2. Go back to the Portal configuration page. In the Basic Info section, complete the basic settings
for the portal authentication.
and
External Portal Server
.
The following sections introduce how
Congure the following parameters:
Portal Name Specify a name for the Portal.
SSID Select an SSID for the Portal.
44
Page 51

Authentication Type Select No Authentication.
Authentication
Timeout
Daily Limit With Daily Limit enabled, after authentication times out, the user cannot get
HTTPS Redirect With this function enabled, the unauthorized clients will be redirected to the
Redirect If you enable this function, the portal will redirect the newly authenticated
With Daily Limit disabled, the client's authentication will expire after the time
period you set and the client needs to log in on the web authentication page
again to access the network.
Options include 1 Hour, 8 Hours, 24 Hours, 7 Days and Custom. Custom
allows you to define the time in days, hours and minutes. The default value is
one hour.
With Daily Limit enabled, the client’s authentication will expire after the time
period you set and the client cannot log in again in the same day.
Options include 30 Minutes, 1 Hour, 2 Hours, 4 Hours and 8 Hours, Custom.
Custom allows you to define the time in hours and minutes. The default value
is 30 minutes.
authenticated again in the same day.
Portal page when they are trying to browse HTTPS websites.
With this function disabled, the unauthorized clients cannot browse HTTPS
websites or be redirected to the Portal page.
clients to the configured URL.
Redirect URL If the Redirect function above is enabled, enter the URL that a newly
authenticated client will be redirected to.
3. In the Login Page section, configure the login page for the Portal.
Congure the following parameters:
Background Select the background type. Two types are supported: Solid Color and
Picture.
Background Color If Solid Color is selected, configure your desired background color through
the color picker or by entering the RGB value manually.
45
Page 52

Background Picture If Picture is selected, click the Choose button and select a picture from
your PC. Drag and scale the clipping region to edit the picture and click
Confirm.
Logo Picture Click the Choose button and select a picture from your PC. Drag and scale
the clipping region to edit the picture and click Confirm.
In addtion, you can click
include Middle, Upper and Lower.
Welcome Information Specify the welcome information.
In addtion, you can click
welcome information through the color picker or by entering the RGB value
manually.
and configure the logo position. The options
and select your desired text color for the
Copyright Specify the copyright information.
In addtion, you can click
information through the color picker or by entering the RGB value manually.
and select your desired text color for Copyright
46
Page 53

Terms of Service Enable or disable Terms of Service. With this option enabled, specify the
terms of service in the following box.
Button
Click
Button Position: Set the position of the login button. The options include
Middle, Upper and Lower.
Button Color: Select your desired login button color through the color
picker or by entering the RGB value manually.
Button Text Color: Select your desired text color for the button through the
color picker or by entering the RGB value manually.
and configure the button.
4. In the Advertisement section, select whether display advertisement pictures for users and
configure the related parameters.
47
Page 54

Congure the following parameters:
Advertisement Specify whether to enable the Advertisement feature. With this feature
enabled, you can add advertisement pictures on the authentication page.
These advertisement pictures will be displayed before the login page
appears. You can also allow users to skip the advertisement by enabling
Allow to Skip Advertisement. The advertisement picture should be less than
2MB. And only JPG, PNG, BMP, GIF and JPEG file types are supported.
Picture Resource Upload advertisement pictures. When several pictures are added, they will
be played in a loop.
Advertisement
Duration Time
Picture Carousel
Interval
Allow Users To Skip
Advertisement
5. Click Apply.
3.3.2 Simple Password
With this Simple Password configured, clients are required to enter the correct password to pass
the authentication.
Follow the steps below to configure No Simple Password Portal:
1. Go to Wireless Settings > Basic Wireless Settings and create an SSID for the Portal.
Specify how long the advertisement will be displayed for. For this duration,
the pictures will be played in a loop. If the duration time is not enough for all
the pictures, the rest will not be displayed.
Specify the picture carousel interval. For example, if this value is set as 5
seconds, the first picture will be displayed for 5 seconds, followed by the
second picture for 5 seconds, and so on.
Specify whether to enable this feature. With this feature enabled, the user
can click the Skip button to skip the advertisement.
2. Go back to the Portal configuration page. In the Basic Info section, complete the basic settings
for the portal authentication.
Congure the following parameters:
Portal Name Specify a name for the Portal.
48
Page 55

SSID Select an SSID for the Portal.
Authentication Type Select Simple Password.
Password Set the password for authentication.
Authentication
Timeout
HTTPS Redirect With this function enabled, the unauthorized clients will be redirected to the
Redirect If you enable this function, the portal will redirect the newly authenticated
Redirect URL If the Redirect function above is enabled, enter the URL that a newly
The client's authentication will expire after the time period you set and
the client needs to log in the web authentication page again to access the
network.
Options include 1 Hour, 8 Hours, 24 Hours, 7 Days and Custom. Custom
allows you to define the time in days, hours and minutes. The default value is
one hour.
Portal page when they are trying to browse HTTPS websites.
With this function disabled, the unauthorized clients cannot browse HTTPS
websites or be redirected to the Portal page.
clients to the configured URL.
authenticated client will be redirected to.
3. In the Login Page section, configure the login page for the Portal.
Congure the following parameters:
Background Select the background type. Two types are supported: Solid Color and
Picture.
Background Color If Solid Color is selected, configure your desired background color through
the color picker or by entering the RGB value manually.
Background Picture If Picture is selected, click the Choose button and select a picture from
your PC. Drag and scale the clipping region to edit the picture and click
Confirm.
49
Page 56

Logo Picture Click the Choose button and select a picture from your PC. Drag and scale
the clipping region to edit the picture and click Confirm.
In addtion, you can click
include Middle, Upper and Lower.
Welcome Information Specify the welcome information.
In addtion, you can click
welcome information through the color picker or by entering the RGB value
manually.
and configure the logo position. The options
and select your desired text color for the
Copyright Specify the copyright information.
In addtion, you can click
information through the color picker or by entering the RGB value manually.
Terms of Service Enable or disable Terms of Service. With this option enabled, specify the
terms of service in the following box.
and select your desired text color for Copyright
50
Page 57

Input Box
Click
Select your desired color for the input box through the color picker or by
entering the RGB value manually.
and configure the input box.
Button
Click
Button Position: Set the position of the login button. The options include
Middle, Upper and Lower.
Button Color: Select your desired login button color through the color
picker or by entering the RGB value manually.
Button Text Color: Select your desired text color for the button through the
color picker or by entering the RGB value manually.
and configure the button.
4. In the Advertisement section, select whether display advertisement pictures for users and
configure the related parameters.
51
Page 58

Congure the following parameters:
Advertisement Specify whether to enable the Advertisement feature. With this feature
enabled, you can add advertisement pictures on the authentication page.
These advertisement pictures will be displayed before the login page
appears. You can also allow users to skip the advertisement by enabling
Allow to Skip Advertisement. The advertisement picture should be less than
2MB. And only JPG, PNG, BMP, GIF and JPEG file types are supported.
Picture Resource Upload advertisement pictures. When several pictures are added, they will
be played in a loop.
Advertisement
Duration Time
Picture Carousel
Interval
Allow Users To Skip
Advertisement
5. Click Apply.
3.3.3 Local User
With this Local User configured, clients are required to enter the correct username and password of
the login account to pass the authentication. You can create multiple accounts and assign different
accounts for different users.
Configure Local User Portal
Specify how long the advertisement will be displayed for. For this duration,
the pictures will be played in a loop. If the duration time is not enough for all
the pictures, the rest will not be displayed.
Specify the picture carousel interval. For example, if this value is set as 5
seconds, the first picture will be displayed for 5 seconds, followed by the
second picture for 5 seconds, and so on.
Specify whether to enable this feature. With this feature enabled, the user
can click the Skip button to skip the advertisement.
Follow the steps below to configure Local User Portal:
1. Go to Wireless Settings > Basic Wireless Settings and create an SSID for the Portal.
2. Go back to the Portal configuration page. In the Basic Info section, complete the basic settings
for the portal authentication.
52
Page 59

Congure the following parameters:
Portal Name Specify a name for the Portal.
SSID Select an SSID for the Portal.
Authentication Type Select Local User.
User Management
HTTPS Redirect With this function enabled, the unauthorized clients will be redirected to the
Redirect If you enable this function, the portal will redirect the newly authenticated
Redirect URL If the Redirect function above is enabled, enter the URL that a newly
You can click this button to configure user accounts for authentication later.
Please refer to
Portal page when they are trying to browse HTTPS websites.
With this function disabled, the unauthorized clients cannot browse HTTPS
websites or be redirected to the Portal page.
clients to the configured URL.
authenticated client will be redirected to.
Create Local User Accounts
.
3. In the Login Page section, configure the login page for the Portal.
Congure the following parameters:
Background Select the background type. Two types are supported: Solid Color and
Picture.
53
Page 60

Background Color If Solid Color is selected, configure your desired background color through
the color picker or by entering the RGB value manually.
Background Picture If Picture is selected, click the Choose button and select a picture from
your PC. Drag and scale the clipping region to edit the picture and click
Confirm.
Logo Picture Click the Choose button and select a picture from your PC. Drag and scale
the clipping region to edit the picture and click Confirm.
In addtion, you can click
include Middle, Upper and Lower.
Welcome Information Specify the welcome information.
In addtion, you can click
welcome information through the color picker or by entering the RGB value
manually.
and configure the logo position. The options
and select your desired text color for the
Copyright Specify the copyright information.
In addtion, you can click
information through the color picker or by entering the RGB value manually.
and select your desired text color for Copyright
54
Page 61

Terms of Service Enable or disable Terms of Service. With this option enabled, specify the
terms of service in the following box.
Input Box
Button
Click
Select your desired color for the input box through the color picker or by
entering the RGB value manually.
Click
Button Position: Set the position of the login button. The options include
Middle, Upper and Lower.
Button Color: Select your desired login button color through the color
picker or by entering the RGB value manually.
Button Text Color: Select your desired text color for the button through the
color picker or by entering the RGB value manually.
and configure the input box.
and configure the button.
55
Page 62

4. In the Advertisement section, select whether display advertisement pictures for users and
configure the related parameters.
Congure the following parameters:
Advertisement Specify whether to enable the Advertisement feature. With this feature
enabled, you can add advertisement pictures on the authentication page.
These advertisement pictures will be displayed before the login page
appears. You can also allow users to skip the advertisement by enabling
Allow to Skip Advertisement. The advertisement picture should be less than
2MB. And only JPG, PNG, BMP, GIF and JPEG file types are supported.
Picture Resource Upload advertisement pictures. When several pictures are added, they will
be played in a loop.
Advertisement
Duration Time
Picture Carousel
Interval
Allow Users To Skip
Advertisement
Specify how long the advertisement will be displayed for. For this duration,
the pictures will be played in a loop. If the duration time is not enough for all
the pictures, the rest will not be displayed.
Specify the picture carousel interval. For example, if this value is set as 5
seconds, the first picture will be displayed for 5 seconds, followed by the
second picture for 5 seconds, and so on.
Specify whether to enable this feature. With this feature enabled, the user
can click the Skip button to skip the advertisement.
5. Click Apply.
Create Local User Accounts
Follow the steps below to create the user accounts for authentication:
1. In the Basic Info section on the portal configuration page, click User Management. The
management page will appear. Go to the User page and click
.
2. The following window will pop up. Configure the required parameters and click Apply.
56
Page 63

Congure the following parameters:
Username Specify the username. The username should not be the same as any
existing one.
Password Specify the password. Users will be required to enter the username and
password when they attempt to access the network.
Authentication
Timeout
MAC Address Binding
Type
Specify the authentication timeout for formal users. After timeout, the users
need to log in at the web authentication page again to access the network.
There are three types of MAC binding: No Binding, Static Binding and
Dynamic Binding.
Static Binding: Specify a MAC address for this user account. Then only the
user with the this MAC address can use the username and password to
pass the authentication.
Dynamic Binding: The MAC address of the first user that passes the
authentication will be bound. Then only this user can use the username and
password to pass the authentication.
57
Page 64

Maximum Users Specify the maximum number of users able to use this account to pass the
authencitation.
Name Specify a name for identification.
Telephone Specify a telephone number for identification.
Rate Limit (Download) Select whether to enable download rate limit. With this option enabled, you
can specify the limit of download rate.
Rate Limit (Upload) Select whether to enable upload rate limit. With this option enabled, you
can specify the limit of upload rate.
Traffic Limit Select whether to enable traffic limit. With this option enabled, you can
specify the total traffic limit for the user. Once the limit is reached, the user
can no longer use this account to access the network.
3. In the same way, you can add more user accounts. The created user accounts will be displayed
in the list. Users can use the username and password of the account to pass the portal
authentication.
By default, the account Status is
You can also click this button to disable the user account. The icon will be changed to
, which means that the user account is enabled and valid.
, which
means that the user account is disabled.
Additionally, you can click to backup all the user account information into a CSV
le or XLS le and save the le to your PC. If needed, you can click
and select the
le to import the account information to the list.
Note:
Using Excel to open the CSV file may cause some numerical format changes, and the number may be
displayed incorrectly. If you use Excel to edit the CSV file, please set the cell format as text.
Manage the Guests
On the Guest page, you can view the information of clients that have passed the portal
authentication and manage the clients.
58
Page 65

You can select an icon to execute the corresponding operation:
Disconnect client.
Extend the effective time.
Create Operator Accounts
Operator account can be used to remotely manage the Local User Portal and Voucher Portal.
Other users can visit the URL https://OC200 Host’s IP Address:8043/hotspot (For example:
https://192.168.0.64:8043/hotspot) and use the Operator account to enter the portal management
page.
Note:
The users who enter the portal management page by Operator account can only create local user accounts
and vouchers and manage the clients.
Follow the steps below to create Operator account.
1. Go to the Operator page.
2. Click and the following window will pop up.
3. Specify the Name, Password and Notes of the Operator account.
4. Select Site Privileges from the drop-down list (multiple options available) for the Operator
account.
5. Click Apply to create an Operator account. Then other users can use this account to enter the
hotspot management page.
3.3.4 Voucher
With Voucher configured, you can distribute the vouchers automatically generated by the OC200
to the clients. Clients can use the vouchers to access the network.
59
Page 66

Configure Voucher Portal
Follow the steps below to configure Voucher Portal:
1. Go to Wireless Settings > Basic Wireless Settings and create an SSID for the Portal.
2. Go back to the Portal configuration page. In the Basic Info section, complete the basic settings
for the portal authentication.
Congure the following parameters:
Portal Name Specify a name for the Portal.
SSID Select an SSID for the Portal.
Authentication Type Select Voucher.
User Management
HTTPS Redirect With this function enabled, the unauthorized clients will be redirected to the
Redirect If you enable this function, the portal will redirect the newly authenticated
Redirect URL If the Redirect function above is enabled, enter the URL that a newly
You can click this button to configure vouchers for authentication later.
Please refer to
Portal page when they are trying to browse HTTPS websites.
With this function disabled, the unauthorized clients cannot browse HTTPS
websites or be redirected to the Portal page.
clients to the configured URL.
authenticated client will be redirected to.
Create Vouchers
.
3. In the Login Page section, configure the login page for the Portal.
60
Page 67

Congure the following parameters:
Background Select the background type. Two types are supported: Solid Color and
Picture.
Background Color If Solid Color is selected, configure your desired background color through
the color picker or by entering the RGB value manually.
Background Picture If Picture is selected, click the Choose button and select a picture from
your PC. Drag and scale the clipping region to edit the picture and click
Confirm.
Logo Picture Click the Choose button and select a picture from your PC. Drag and scale
the clipping region to edit the picture and click Confirm.
In addtion, you can click
include Middle, Upper and Lower.
Welcome Information Specify the welcome information.
In addtion, you can click
welcome information through the color picker or by entering the RGB value
manually.
and configure the logo position. The options
and select your desired text color for the
61
Page 68

Copyright Specify the copyright information.
In addtion, you can click
information through the color picker or by entering the RGB value manually.
Terms of Service Enable or disable Terms of Service. With this option enabled, specify the
terms of service in the following box.
and select your desired text color for Copyright
Input Box
Click
Select your desired color for the input box through the color picker or by
entering the RGB value manually.
and configure the input box.
62
Page 69

Button
Click
Button Position: Set the position of the login button. The options include
Middle, Upper and Lower.
Button Color: Select your desired login button color through the color
picker or by entering the RGB value manually.
Button Text Color: Select your desired text color for the button through the
color picker or by entering the RGB value manually.
and configure the button.
4. In the Advertisement section, select whether display advertisement pictures for users and
configure the related parameters.
Congure the following parameters:
Advertisement Specify whether to enable the Advertisement feature. With this feature
enabled, you can add advertisement pictures on the authentication page.
These advertisement pictures will be displayed before the login page
appears. You can also allow users to skip the advertisement by enabling
Allow to Skip Advertisement. The advertisement picture should be less than
2MB. And only JPG, PNG, BMP, GIF and JPEG file types are supported.
Picture Resource Upload advertisement pictures. When several pictures are added, they will
be played in a loop.
Advertisement
Duration Time
Specify how long the advertisement will be displayed for. For this duration,
the pictures will be played in a loop. If the duration time is not enough for all
the pictures, the rest will not be displayed.
63
Page 70

Picture Careusel
Interval
Specify the picture carousel interval. For example, if this value is set as 5
seconds, the first picture will be displayed for 5 seconds, followed by the
second picture for 5 seconds, and so on.
Allow Users To Skip
Advertisement
Specify whether to enable this feature. With this feature enabled, the user
can click the Skip button to skip the advertisement.
5. Click Apply.
Create Vouchers
Follow the steps below to create vouchers for authentication:
1. In the Basic Info section, click Voucher Manager. The voucher management page will appear. Go
to the Voucher page and click
2. The following window will pop up. Configure the required parameters and click Apply.
.
Congure the following parameters:
64
Page 71

Code Length Specify the length of the voucher codes to be created.
Amount Enter the voucher amount to be generated.
Type Select Single Use or Multi Use.
Single Use means one voucher can only be distributed to one client. Multi Use
means one voucher can be distributed to several clients, who can use the
same voucher to access the network at the same time.
If you select Multi Use, enter the value of Max Users. When the number of
clients who are connected to the network with the same voucher reaches the
value, no more clients can use this voucher to access the network.
Duration Select the period of validity of the Voucher.
The options include 8 hours, 2 days and User-defined. The period of valid of
the voucher is reckoned from the time when it is used for the first time.
Rate Limit
(Download)
Rate Limit (Upload) Select whether to enable upload rate limit. With this option enabled, you can
Traffic Limit Specify the total traffic limit for one voucher. Once the limit is reached, the
Notes Enter a description for the Voucher (optional).
Select whether to enable download rate limit. With this option enabled, you
can specify the limit of download rate.
specify the limit of upload rate.
client can no longer access the network using the voucher.
3. The Vouchers will be generated and displayed on the page.
4. Click to print a single voucher; click to print your selected vouchers;
click
to print all unused vouchers.
65
Page 72

5. Distribute the vouchers to clients, and then they can use the codes to pass authentication.
6. When the vouchers are invalid, you can click
delete the selected vouchers.
to delete the Voucher or click to
Manage the Guests
On the Guest page, you can view the information of clients that have passed the portal
authentication and manage the clients.
You can select an icon to execute the corresponding operation:
Restrict the client to access the network.
Extend the effective time.
Create Operator Accounts
Operator account can be used to remotely manage the Local User Portal and Voucher Portal.
Other users can visit the URL https://OC200 Host’s IP Address:8043/hotspot (For example:
https://192.168.0.64:8043/hotspot) and use the Operator account to enter the portal management
page.
66
Page 73

Note:
The users who enter the portal management page by Operator account can only create local user accounts
and vouchers and manage the clients.
Follow the steps below to create Operator account.
1. Go to the Operator page.
2. Click and the following window will pop up.
3. Specify the Name, Password and Notes of the Operator account.
4. Select Site Privileges from the drop-down list (multiple options available) for the Operator
account.
5. Click Apply to create an Operator account. Then other users can use this account to enter the
hotspot administrative system.
3.3.5 SMS
With SMS portal configured, client can get verification codes using their mobile phones and enter
the received codes to pass the authentication.
Follow the steps below to configure SMS Portal:
1. Go to www.twilio.com/try-twilio and get a Twilio account. Buy the Twilio service for SMS. Then
get the account information, including ACCOUNT SID, AUTH TOKEN and Phone number.
2. Go to Wireless Settings > Basic Wireless Settings and create an SSID for the Portal.
3. Go back to the Portal configuration page. In the Basic Info section, complete the basic settings
for the portal authentication.
67
Page 74

Congure the following parameters:
Portal Name Specify a name for the Portal.
SSID Select an SSID for the Portal.
Authentication Type Select SMS.
Twilio SID Enter the Account SID for Twilio API Credentials.
Auth Token Enter the Authentication Token for Twilio API Credentials.
Phone Number Enter the phone number that is used to send verification messages to the
clients.
Maximum Users A telephone can get several codes via messages one by one, and different
clients can use different codes to pass the authentication. However, the
number of clients that are allowed to be authenticated using the same
telephone at the same time has a upper limit.
Specify the upper limit in this field.
Authentication
Timeout
Preset Country Code Set the default country code that will be filled automatically on the
HTTPS Redirect With this function enabled, the unauthorized clients will be redirected to the
The client's authentication will expire after the time period you set and
the client needs to log in the web authentication page again to access the
network.
Options include 1 Hour, 8 Hours, 24 Hours, 7 Days and Custom. Custom
allows you to define the time in days, hours and minutes. The default value is
one hour.
authentication page.
Portal page when they are trying to browse HTTPS websites.
With this function disabled, the unauthorized clients cannot browse HTTPS
websites or be redirected to the Portal page.
68
Page 75

Redirect If you enable this function, the portal will redirect the newly authenticated
clients to the configured URL.
Redirect URL If the Redirect function above is enabled, enter the URL that a newly
authenticated client will be redirected to.
4. In the Login Page section, configure the login page for the Portal.
Congure the following parameters:
Background Select the background type. Two types are supported: Solid Color and
Picture.
Background Color If Solid Color is selected, configure your desired background color through
the color picker or by entering the RGB value manually.
Background Picture If Picture is selected, click the Choose button and select a picture from
your PC. Drag and scale the clipping region to edit the picture and click
Confirm.
Logo Picture Click the Choose button and select a picture from your PC. Drag and scale
the clipping region to edit the picture and click Confirm.
In addtion, you can click
include Middle, Upper and Lower.
and configure the logo position. The options
69
Page 76

Welcome Information Specify the welcome information.
In addtion, you can click
welcome information through the color picker or by entering the RGB value
manually.
Copyright Specify the copyright information.
In addtion, you can click
information through the color picker or by entering the RGB value manually.
and select your desired text color for the
and select your desired text color for Copyright
Terms of Service Enable or disable Terms of Service. With this option enabled, specify the
terms of service in the following box.
70
Page 77

Input Box
Click
Select your desired color for the input box through the color picker or by
entering the RGB value manually.
and configure the input box.
Button
Click
Button Position: Set the position of the login button. The options include
Middle, Upper and Lower.
Button Color: Select your desired login button color through the color
picker or by entering the RGB value manually.
Button Text Color: Select your desired text color for the button through the
color picker or by entering the RGB value manually.
and configure the button.
5. In the Advertisement section, select whether display advertisement pictures for users and
configure the related parameters.
Congure the following parameters:
71
Page 78

Advertisement Specify whether to enable the Advertisement feature. With this feature
enabled, you can add advertisement pictures on the authentication page.
These advertisement pictures will be displayed before the login page
appears. You can also allow users to skip the advertisement by enabling
Allow to Skip Advertisement. The advertisement picture should be less than
2MB. And only JPG, PNG, BMP, GIF and JPEG file types are supported.
Picture Resource Upload advertisement pictures. When several pictures are added, they will
be played in a loop.
Advertisement
Duration Time
Picture Careusel
Interval
Allow Users To Skip
Advertisement
6. Click Apply.
For more details about how to configure SMS Portal, you can go to https://www.tp-link.com/en/
configuration-guides.html and download the configuration guide for SMS Portal.
3.3.6 Facebook
With Facebook Portal configured, when clients connect to your Wi-Fi, they will be
redirected to your Facebook page. To access the internet, clients need to pass the
authentication on the page.
Specify how long the advertisement will be displayed for. For this duration,
the pictures will be played in a loop. If the duration time is not enough for all
the pictures, the rest will not be displayed.
Specify the picture carousel interval. For example, if this value is set as 5
seconds, the first picture will be displayed for 5 seconds, followed by the
second picture for 5 seconds, and so on.
Specify whether to enable this feature. With this feature enabled, the user
can click the Skip button to skip the advertisement.
Note:
OC200 will automatically create Free Authentication Policy entries for the Facebook Portal. You don’t need to
create them manually.
Follow the steps below to configure Facebook Portal:
1. Go to www.facebook.com and get a Facebook account. Create your Facebook page according
to your needs.
2. Go to Wireless Settings > Basic Wireless Settings and create an SSID for the Portal.
3. Go back to the Portal configuration page. In the Basic Info section, complete the settings for the
portal authentication.
72
Page 79

Congure the following parameters:
Portal Name Specify a name for the Portal.
SSID Select an SSID for the Portal.
Authentication Type Select Facebook.
Facebook Page
Configuration
Facebook Checkin
Location
HTTPS Redirect With this function enabled, the unauthorized clients will be redirected to the
Click this button to specify the Facebook Page.
If the Facebook page is successfully got by the OC200, the name of the
Facebook page will be displayed here.
Portal page when they are trying to browse HTTPS websites.
With this function disabled, the unauthorized clients cannot browse HTTPS
websites or be redirected to the Portal page.
For more details about how to configure Facebook Portal, you can go to https://www.tp-link.com/
en/configuration-guides.html and download the configuration guide for Facebook Portal.
3.3.7 External RADIUS Server
If you have a RADIUS server, you can configure External RADIUS Server Portal. With this type of
portal, you can get two types of portal customization: Local Web Portal and External Web Portal.
The authentication login page of Local Web Portal is provided by the built-in portal server of the
OC200. The External Web Portal is provided by external portal server.
Note:
OC200 will automatically create Free Authentication Policy entries for the External RADIUS Portal.
Follow the steps below to configure External RADIUS Server Portal:
1. Go to Wireless Settings > Basic Wireless Settings and create an SSID for the Portal.
2. Go back to the Portal configuration page. In the Basic Info section, complete the basic settings
for the portal authentication.
73
Page 80

Congure the following parameters:
Portal Name Specify a name for the Portal.
SSID Select an SSID for the Portal.
Authentication Type Select External RADIUS Server.
RADIUS Server IP Enter the IP address of the RADIUS server.
RADIUS Port Enter the port number you have set on the RADIUS server.
RADIUS Password Enter the password you have set on the RADIUS Server.
Authentication
Timeout
HTTPS Redirect With this function enabled, the unauthorized clients will be redirected to the
Redirect If you enable this function, the portal will redirect the newly authenticated
Redirect URL If the Redirect function above is enabled, enter the URL that a newly
The client's authentication will expire after the time period you set and
the client needs to log in the web authentication page again to access the
network.
Options include 1 Hour, 8 Hours, 24 Hours, 7 Days, Custom. Custom allows
you to define the time in days, hours, and minutes. The default value is one
hour.
Portal page when they are trying to browse HTTPS websites.
With this function disabled, the unauthorized clients cannot browse HTTPS
websites or be redirected to the Portal page.
clients to the configured URL.
Disabled by default.
authenticated client will be redirected to.
74
Page 81

Portal Customization Select Local Web Portal or External Web Portal.
Local Web Portal: If this option is selected, refer to step 4 to configure the
login page and step 5 to configure the advertisement.
External Web Portal: If this option is selected, follow the steps below.
1. Configure the external RADIUS server.
2. Enter the authentication login page's URL provided by the external portal
server in the External Web Portal URL field.
3. Local Web Portal is configured, configure the login page for the Portal in the Login Page section.
Congure the following parameters:
Background Select the background type. Two types are supported: Solid Color and
Picture.
Background Color If Solid Color is selected, configure your desired background color through
the color picker or by entering the RGB value manually.
Background Picture If Picture is selected, click the Choose button and select a picture from
your PC. Drag and scale the clipping region to edit the picture and click
Confirm.
Logo Picture Click the Choose button and select a picture from your PC. Drag and scale
the clipping region to edit the picture and click Confirm.
In addtion, you can click
include Middle, Upper and Lower.
and configure the logo position. The options
75
Page 82

Welcome Information Specify the welcome information.
In addtion, you can click
welcome information through the color picker or by entering the RGB value
manually.
Copyright Specify the copyright information.
In addtion, you can click
information through the color picker or by entering the RGB value manually.
and select your desired text color for the
and select your desired text color for Copyright
Terms of Service Enable or disable Terms of Service. With this option enabled, specify the
terms of service in the following box.
76
Page 83

Input Box
Click
Select your desired color for the input box through the color picker or by
entering the RGB value manually.
and configure the input box.
Button
Click
Button Position: Set the position of the login button. The options include
Middle, Upper and Lower.
Button Color: Select your desired login button color through the color
picker or by entering the RGB value manually.
Button Text Color: Select your desired text color for the button through the
color picker or by entering the RGB value manually.
and configure the button.
4. If Local Web Portal is configured, select whether display advertisement pictures for users and
configure the related parameters in the Advertisement section, .
Congure the following parameters:
77
Page 84

Advertisement Specify whether to enable the Advertisement feature. With this feature
enabled, you can add advertisement pictures on the authentication page.
These advertisement pictures will be displayed before the login page
appears. You can also allow users to skip the advertisement by enabling
Allow to Skip Advertisement.
Picture Resource Upload advertisement pictures. When several pictures are added, they will
be played in a loop.
Advertisement
Duration Time
Picture Careusel
Interval
Allow Users To Skip
Advertisement
Specify how long the advertisement will be displayed for. For this duration,
the pictures will be played in a loop. If the duration time is not enough for all
the pictures, the rest will not be displayed.
Specify the picture carousel interval. For example, if this value is set as 5
seconds, the first picture will be displayed for 5 seconds, followed by the
second picture for 5 seconds, and so on.
Specify whether to enable this feature. With this feature enabled, the user
can click the Skip button to skip the advertisement.
5. Click Apply.
3.3.8 External Portal Server
The option of External Portal Server is designed for the developers. They can customized their own
authentication type according to the interface provided by OC200, e.g. message authentication and
WeChat authentication etc.
1. Go to Wireless Settings > Basic Wireless Settings and create an SSID for the Portal.
2. Go back to the Portal configuration page. In the Basic Info section, complete the settings for the
portal authentication.
Portal Name Specify a name for the Portal.
SSID Select an SSID for the Portal.
Authentication Type Select External Portal Server.
78
Page 85

External Portal Server Enter the complete authentication URL that redirect to an external
portal server, for example:
http://192.168.0.147:8880/portal/index.php or http://192.168.0.147/
portal/index.html
HTTPS Redirect With this function enabled, the unauthorized clients will be redirected
to the Portal page when they are trying to browse HTTPS websites.
With this function disabled, the unauthorized clients cannot browse
HTTPS websites or be redirected to the Portal page.
3. Click Apply.
3.4 Free Authentication Policy
Free Authentication Policy allows some specified clients to access the network resources without
authentication. Follow the steps below to add free authentication policy.
1. Go to Wireless Control > Free Authentication Policy
2. Click and the following window will pop up.
.
3. Configure the following parameters. When all conditions are met, the client can access the
network without authentication.
79
Page 86

Policy Name Specify a name for the policy.
Match Mode Select the match mode for the policy. Two options are provided:
URL: With this option selected, configure an URL that is allowed to be visited
by the clients without authentication.
IP-MAC Based: With this option selected, configure Source IP Range,
Destination IP Range, Source MAC and Destination MAC to specify the
specific clients and service that will follow the Free Authentication feature.
URL Set the URL.
Source IP Range Set the Source IP Range with the subnet and mask length of the clients.
Destination IP Range Set the Destination IP Range with the subnet and mask length of the server.
Source MAC Set the MAC address of client.
Destination Port Enter the port the service uses.
Status Check the box to enable the policy.
4. Click Apply and the policy is successfully added.
3.5 MAC Filter
MAC filter can be used to allow or block the listed clients to access the network. Thereby it can
effectively control client's access to the wireless network.
Follow the steps below to configure MAC Filter.
1. Go to Wireless Control > MAC Filter to add MAC Filter group and group members.
1 ) Click and specify a name for the group.
2 ) Click Apply and the group will be successfully added as shown below.
80
Page 87

3 ) Click and enter a MAC address in the format as shown below.
4 ) Click Apply to add the MAC address into the MAC lter group.
2. You can add more groups or members according to your need.
Note:
You can click to export the group members to a excel file and save the file on your PC. If
needed, you can also click
to import the group members to the OC200.
3. Go to Wireless Control > MAC Filter Association to associate the added MAC Filter group with
SSID.
81
Page 88

1 ) Check the box and click Apply to enable MAC Filtering function.
2 ) Select a band frequency (2.4GHz or 5GHz) and a WLAN group.
3 ) In the MAC Filter Name column of the specied SSID, select a MAC Filter group in the drop-
down list. Then select Allow/Deny in the Action column to allow/deny the clients in the MAC
Filter group to access the network.
4 ) Click Apply in the Setting column.
3.6 Scheduler
With the Scheduler, the EAPs or its’ wireless network can automatically turn on or off at the time you
set. For example, you can use this feature to schedule the radio to operate only during the office
working time in order to achieve security goals and reduce power consumption. You can also use
the Scheduler to make clients can only access the wireless network during the time period you set
in the day.
Follow the steps below to configure Scheduler.
1. Go to Wireless Control > Scheduler.
1 ) Click and specify a name for the prole.
82
Page 89

2 ) Click Apply and the prole will be added.
3 ) Click and congure the parameters to specify a period of time.
4 ) Click Apply and the prole is successfully added in the list.
2. Go to Wireless Control > Scheduler Association.
83
Page 90

1 ) Check the box to enable Scheduler function.
2 ) Select Associated with SSID (the prole will be applied to the specic SSID on all the EAPs)
3 ) Select a band frequency (2.GHz or 5GHz) and a WLAN group.
4 ) In the Prole Name column of the specied SSID or AP, select a prole you added before in
5 ) Click Apply in the Setting column.
3.7 QoS
The OC200 allows you to configure the quality of service (QoS) on the EAP device for optimal
throughput and performance when handling differentiated wireless traffic, such as Voice-over-IP
(VoIP), other types of audio, video, streaming media, and traditional IP data.
or Associated with AP (the prole will be applied to all SSIDs on the specic EAP). Then click
Apply.
the drop-down list. Select Radio O/Radio On to turn on or o the wireless network during
the time interval set for the prole.
To configure QoS on the EAP device, you should set parameters on the transmission queues for
different types of wireless traffic and specify minimum and maximum wait times (through contention
windows) for transmission. In normal use, we recommend you keep the default values for the EAP
devices and station EDCA (Enhanced Distributed Channel Access).
Follow the steps below to configure QoS.
1. Go to Wireless Control > QoS.
2. Enable or disable the following features.
84
Page 91

Wi-Fi Multimedia (WMM) By default enabled. With WMM enabled, the EAP devices have the QoS
function to guarantee the high priority of the transmission of audio and
video packets.
If 802.11n only mode is selected in 2.4GHz (or 802.11n only, 802.11ac
only, or 802.11 n/ac mixed mode in 5GHz), the WMM should be enabled. If
WMM is disabled, the 802.11n only mode cannot be selected in 2.4GHz (or
802.11n only, 802.11ac only, or 802.11 n/ac mixed mode in 5GHz).
No Acknowledgment By default disabled. You can enable this function to specify that
the EAP devices should not acknowledge frames with Qos No Ack.
Acknowledgeable is recommended if VoIP phones access the network
through the EAP device.
Unscheduled Automatic
Power Save Delivery
By default enabled. As a power management method, it can greatly
improve the energy-saving capacity of clients.
3. Click AP EDCA Parameters and the following page will appear. AP EDCA parameters affect
traffic flowing from the EAP device to the client station. We recommend you use the defaults.
Queue Queue displays the transmission queue. By default, the priority from high to
low is Data 0, Data 1, Data 2, and Data 3. The priority may be changed if you
reset the EDCA parameters.
Data 0 (Voice)—Highest priority queue, minimum delay. Time-sensitive data
such as VoIP and streaming media are automatically sent to this queue.
Data 1 (Video)—High priority queue, minimum delay. Time-sensitive video
data is automatically sent to this queue.
Data 2 (Best Effort)—Medium priority queue, medium throughput and delay.
Most traditional IP data is sent to this queue.
Arbitration InterFrame Space
Minimum Contention
Window
Data 3 (Background)—Lowest priority queue, high throughput. Bulk data that
requires maximum throughput and is not time-sensitive is sent to this queue
(FTP data, for example).
A wait time for data frames. The wait time is measured in slots. Valid values
for Arbitration Inter-Frame Space are from 0 to 15.
A list to the algorithm that determines the initial random backoff wait time
(window) for retry of a transmission.
This value can not be higher than the value for the Maximum Contention
Window.
85
Page 92

Maximum Contention
Window
Maximum Burst Maximum Burst specifies the maximum burst length allowed for packet
The upper limit (in milliseconds) for the doubling of the random backoff value.
This doubling continues until either the data frame is sent or the Maximum
Contention Window size is reached.
This value must be higher than the value for the Minimum Contention
Window.
bursts on the wireless network. A packet burst is a collection of multiple
frames transmitted without header information. The decreased overhead
results in higher throughput and better performance.
4. Click Station EDCA Parameters and the following page will appear. Station EDCA parameters
affect traffic flowing from the client station to the EAP device. We recommend you use the
defaults.
Queue Queue displays the transmission queue. By default, the priority from high to
low is Data 0, Data 1, Data 2, and Data 3. The priority may be changed if you
reset the EDCA parameters.
Data 0 (Voice)—Highest priority queue, minimum delay. Time-sensitive data
such as VoIP and streaming media are automatically sent to this queue.
Data 1 (Video)—High priority queue, minimum delay. Time-sensitive video
data is automatically sent to this queue.
Data 2 (Best Effort)—Medium priority queue, medium throughput and delay.
Most traditional IP data is sent to this queue.
Data 3 (Background)—Lowest priority queue, high throughput. Bulk data that
requires maximum throughput and is not time-sensitive is sent to this queue
(FTP data, for example).
Arbitration InterFrame Space
Minimum Contention
Window
Maximum Contention
Window
A wait time for data frames. The wait time is measured in slots. Valid values
for Arbitration Inter-Frame Space are from 0 to 15.
A list to the algorithm that determines the initial random backoff wait time
(window) for retry of a transmission. This value can not be higher than the
value for the Maximum Contention Window.
The upper limit (in milliseconds) for the doubling of the random backoff value.
This doubling continues until either the data frame is sent or the Maximum
Contention Window size is reached.
This value must be higher than the value for the Minimum Contention
Window.
86
Page 93

TXOP Limit The TXOP Limit is a station EDCA parameter and only applies to traffic
5. Click Apply.
3.8 Site Settings
You can configure the site-specific settings on the Site Settings page. To switch sites, select a
different site from the Sites drop-down menu at the top of any screen.
flowing from the client station to the EAP device. The Transmission
Opportunity (TXOP) is an interval of time, in milliseconds, when a WME client
station has the right to initiate transmissions onto the wireless medium (WM)
towards the EAP device. The valid values are multiples of 32 between 0 and
8192.
3.8.1 LED
You can change the LED light status on the EAP devices on the page Site Settings > LED.
By default, the LED status is , which means that the LED lights of all the EAP devices on the site
are on. You can click this button to change the LED light status. The icon will be changed to
which means that all the LED lights are off.
,
87
Page 94

3.8.2 Device Account
When the EAP devices are adopted at the first time, their username and password will become the
same as those of the OC200 which are specified at Basic Configurations. You can specify a new
username and password for the adopted EAPs in batches.
Follow the steps below to change EAP devices’ username and password.
1. Go to Site Settings > Device Account.
2. Specify a new username and password for the EAP devices.
3. Click Apply.
Note:
The new account will be applied to EAP devices but not the OC200. To change the OC200’s username and
password, please refer to
3.8.3 Reboot Schedule
You can reboot all the EAPs in the network periodically as needed. Follow the steps below to
configure Reboot Schedule.
1. Go to Site Settings > Reboot Schedule.
User Account
.
2. Check the box to enable the function.
88
Page 95

3. Choose Daily, Weekly or Monthly in the Timing Mode drop-down list and set a specific time to
reboot the EAPs.
4. Click Apply.
3.8.4 Log Settings
Follow the steps below to choose the way to receive system logs.
1. Go to Site Settings > Log Setting.
2. Check the box to choose the way to receive system logs (you can choose more than one) and
click Apply. Two ways are available: Auto Mail Feature and Server.
Auto Mail Feature
If Auto Mail Feature is enabled, system logs will be sent to a specified mailbox. Check the box to
enable the feature and configure the parameters.
From Address Enter the sender's E-mail address.
To Address Enter the receiver's E-mail address.
SMTP Server Enter the IP address of the SMTP server.
89
Page 96

Enable Authentication You can check the box to enable mail server authentication. Enter the
sender's mail account name and password.
Time Mode Select Time Mode. System logs can be sent at specific time or time interval.
Fixation Time If you select Fixation Time, specify a fixed time to send the system log mails.
For example, 08:30 indicates that the mail will be sent at 8:30 am everyday.
Period Time If you select Period Time, specify a period time to regularly send the system
log mail. For example, 6 indicates that the mail will be sent every six hours.
More Client Detail Log With the option enabled, the logs of clients will be sent to the receiver’s
E-mail address.
Server
If Server is enabled, system logs will be sent to a server. Check the box to enable the feature and
configure the parameters.
System Log Server IP Enter the IP address of the server.
System Log Server Port Enter the port of the server.
More Client Detail Log With the option enabled, the logs of clients will be sent to the server.
3.8.5 Batch Upgrade
You can upgrade your EAP devices of the same model in batches using Batch Upgrade. Two
options are available for upgrading: upgrade online and upgrade manually.
Upgrade Online
The latest firmware for the EAPs can be detected by the OC200 automatically, and you can upgrade
the EAPs online. Thus you do not need to save the firmware files locally in advance.
Follow the steps below to upgrade the EAP devices online according to their model.
90
Page 97

1. Go to Site Settings > Batch Upgrade. The device model, amount, current rmware and available
rmware will appear on the Firmware list.
2. Click in the Action column to upgrade the device.
After upgrading, the device will reboot automatically.
Tips:
You can click to check if the latest firmware is available.
·
You can click in the Available Firmware column to view the release note of the firmware, which can help
·
you know the new features or improvements of this firmware.
Upgrade Manually
The latest firmware files can be downloaded from the in the download center of TP-Link Website.
Then you can upgrade the EAP devices manually.
Follow the steps below to upgrade the EAP devices maually according to their model.
1. Visit http://www.tp-link.com/en/support/download/
corresponding model.
to download the latest firmware file of the
91
Page 98

2. Go to Site Settings > Batch Upgrade.
3. Click in the Action column to upgrade the device.
4. Click Browse to locate and choose the proper firmware file for the model.
5. Click Upgrade to upgrade the device.
After upgrading, the device will reboot automatically.
Note:
The EAP device cannot be upgraded manually when you access the OC200 via Omada Cloud.
·
To avoid damage, please do not turn off the device while upgrading.
·
3.8.6 SSH
SSH is a protocol working in application layer and transport layer. It can provide a secure, remote
connection to a device. You can log in to the OC200 via SSH. Follow the steps below to configure
SSH on the OC200:
1. Go to Site Setting > SSH. Enter the port number of the SSH server.
92
Page 99

2. Check the box to enable SSH Login.
3. Click Apply.
3.8.7 Management VLAN
Management VLAN provides a safer way for you to manage the EAP. With Management VLAN
enabled, only the hosts in the management VLAN can manage the EAP. Since most hosts cannot
process VLAN TAGs, connect the management host to the network via a switch, and set up correct
VLAN settings for the switches on the network to ensure the communication between the host and
the EAP in the management VLAN.
Follow the steps below to configure Management VLAN.
1. Go to Site Setting > Management VLAN. Check the box to enable Management VLAN.
2. Specify the Management VLAN ID. The default VLAN ID is 1.
3. Click Apply.
93
Page 100

4
TP-Link Omada Cloud Service provides a better way to realize remote management. With Cloud
Access enabled on the OC200 and a TP-Link ID bound with your OC200, you can easily monitor
and manage your wireless network. To ensure that your EAPs stay new and get better over time,
the Omada Cloud will notify you when a newer firmware upgrade is available. Surely you can also
manage multiple OC200s with a single TP-Link ID.
Follow the steps below to configure Cloud Access and access the OC200 via Omada Cloud:
1.
Configure the Cloud Access
2.
Manage the OC200 via Omada Cloud
Omada Cloud Service
94
 Loading...
Loading...