Page 1

Page 2

Page 3

T
able of Contents
Introduction 1-1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Description 1-1
About
Organization 1-5
Chapter Summary
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
This Manual
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
1-3
1-5
Station Hardware 2-1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
General 2-1
Communication
Processor 2-8
I/O Chassis
Power
Cables 2-13
Other
Chapter Summary
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Adapter Module
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Supply
Optional Equipment
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
2-2
2-9
2-10
2-13
2-13
Module Installation 3-1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
General 3-1
Switch
Keying 3-7
Installation
Cable
Commands 4-1
General 4-1
Protected/Unprotected 4-3
Write Commands
Bit Write Commands
Read Command
Accessible
Accessible
Accessible
Accessible
Chapter Summary
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Settings
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Connections
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
In The I/O Slot
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Data T
able Locations - PLC-2 Processors
Data T
able Locations - PLC Processors
Data T
able Locations - PLC-3 Processors
Data T
able Locations - PLC-4 Microtrol Processors 4-1
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . .
. . . . . . . . . . .
3-1
3-8
3-9
4-4
4-5
4-7
4-7
4-9
4-10
4-15
Communication Zone Rungs 5-1 . . . . . . . . . . . . . . . . . . . . . . . . . .
General 5-1
Header Rungs
Memory Access Rungs
Command Rungs
Delimiter
Chapter Summary
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Rung
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
5-3
5-4
5-7
5-1
5-12
1
1
i
Page 4

T
able of Contents
Status Words 6-1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
General 6-1
START/DONE Word
REMOTE/LOCAL
Error
Chapter Summary
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
F
AULT Word
Code Storage W
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
ord
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
6-2
6-3
6-5
6-7
Command Initiation, Execution, and Monitoring 7-1 . . . . . . . . . . .
General 7-1
START/DONE
Controlling
REMOTE/LOCAL
Timeout Preset Value
Chapter Summary
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Bit T
iming
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
The Start Bit
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
F
AUL
T Bit Monitoring
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . .
7-1
7-4
7-10
7-14
7-19
Station Interfacing 8-1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
General 8-1
Floating Master
Commands From A Computer
Chapter Summary
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
8-1
8-5
8-9
Start-up and Troubleshooting 9-1 . . . . . . . . . . . . . . . . . . . . . . . . .
General 9-1
Start-up
Start-up Procedures
Troubleshooting 9-18
Chapter Summary
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
and T
roubleshooting Aids
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
9-1
9-12
9-23
Design Aids and Documentation 10-1 . . . . . . . . . . . . . . . . . . . . . . .
General 10-1
Program Summary
Forms 10-2
Memory Maps
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
10-1
10-2
Error Code Listing A-1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
ii
Page 5

Introduction
Chapter
1
Description
An Allen-Bradley Data Highway extends the capabilities of
programmable controllers by letting them exchange data with each other
and with other intelligent RS-232-C devices. Data Highway integrates
individual controllers into a larger automated manufacturing network. On
a single Data Highway cable, as many as 64 separate programmable
controllers and computers can be connected over a distance of 10,000
feet (3,048m).
The unit that interfaces PLC-2 family programmable controllers to this
network, and makes communication possible, is an A-B Communication
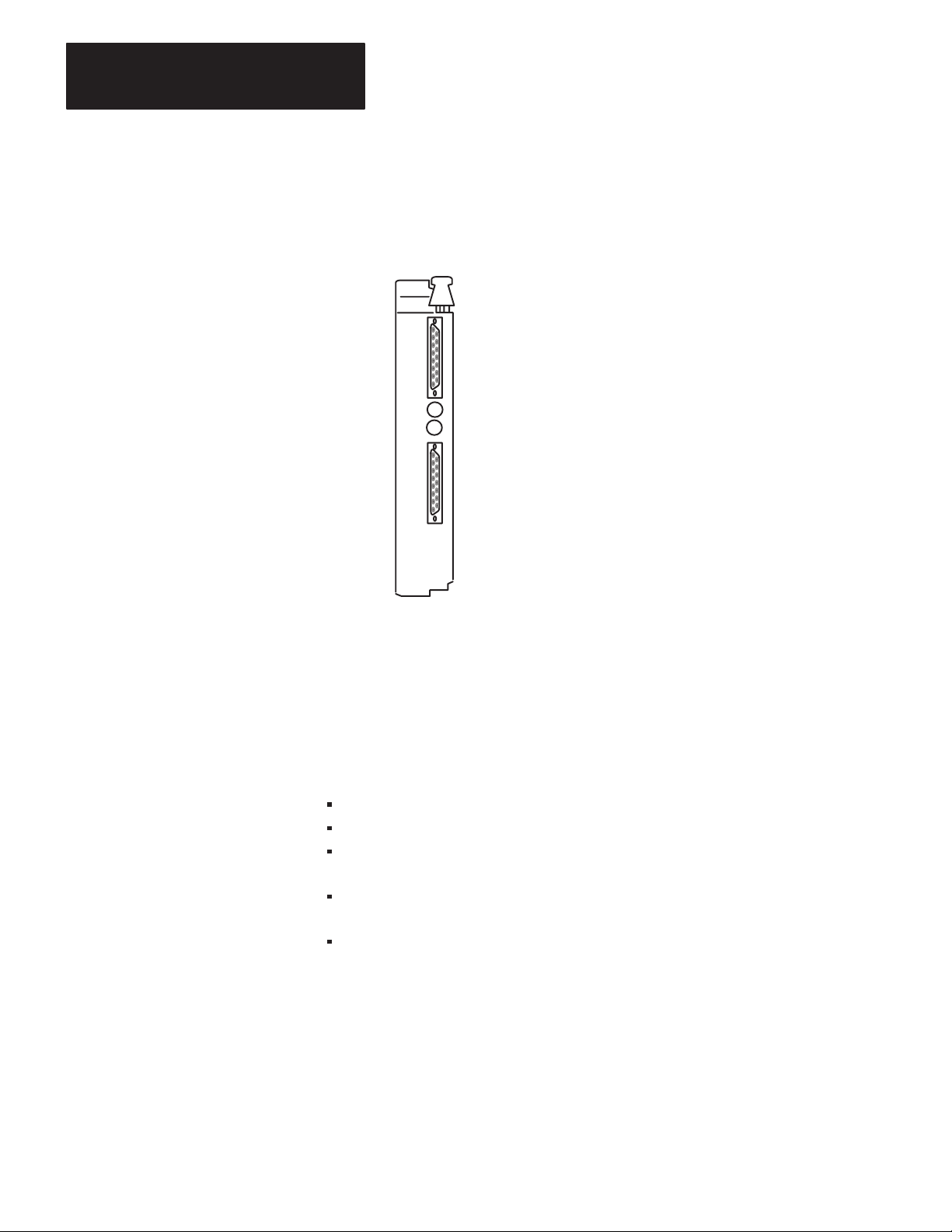
Adapter Module (cat. no. 1771-KA2). (See Figure 1.1) It is a Data
Highway station interface module and is used with Bulletin 1772
programmable controller processors. These processors are:
PLC-2 Processor (cat. no. 1772-LR)
PLC-2/20 Processor (cat. no. 1772-LP1, -LP2)
PLC-2/30 Processor (cat. no. 1772-LP3)
Figure 1.1
Communication
Adapter Module (cat. no. 1771-KA2)
10862-I
Mini-PLC-2 Processor (cat. no. 1772-LN1, -LN2, -LN3)
Mini-PLC-2/05 (cat. no. 1772-LS, LSP)
1–1
Page 6
Chapter 1
Introduction
Mini-PLC-2/15 (cat. no. 1772-LV)
This module enables communication of memory data between these
processors, and from any of these processors to other processors on the
Data Highway via communication adapter modules.
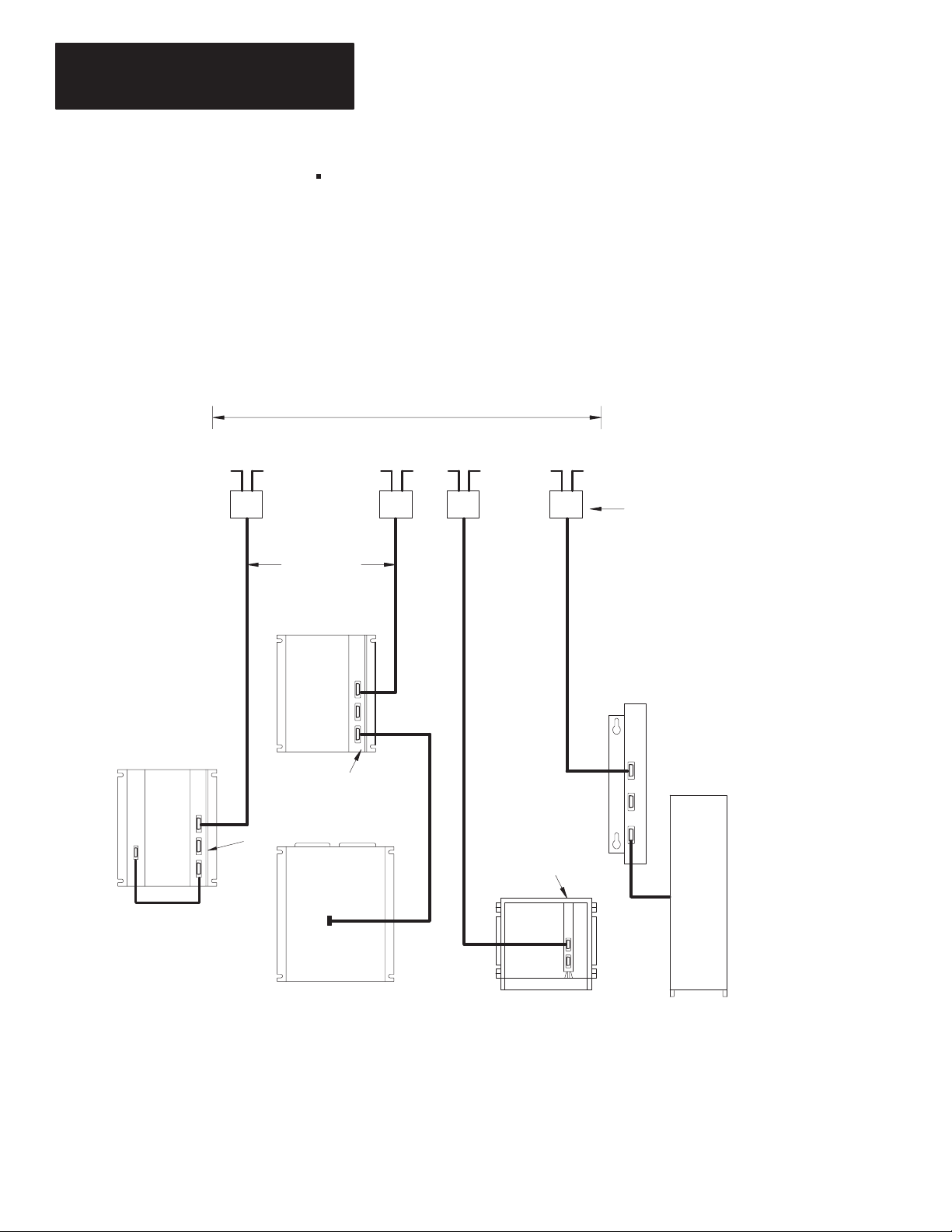
A typical Data Highway configuration is shown in Figure 1.2.
Figure 1.2
Representative
10,000 feet (3,048 meters) maximum
Data Highway Cable Trunkline
Data Highway Configuration
1770-SC
Station
Connector
Mini-PLC-2,
Mini-PLC-2/05,
or Mini-PLC-2/15
Programmable Controller
Cable Droplines
100 feet
(30.5 meters)
maximum
I/O Rack
Communication Adapter
Module
(cat. no. 1771-KA2)
PLC-2 Family
Programmable Controller
Communication
Adapter Module
(cat. no. 1775-KA)
PLC-3
Communication Controller
Module
(cat. no. 1771-KE/KF)
Mini
Computer
12210
About This Manual
1–2
The terms “communication adapter module” and “1771-KA2” and
“KA2” are interchanged throughout the manual.
Page 7
Chapter 1
Introduction
This manual describes installation, operation, and programming
necessary to use the KA2 communication adapter module. Use this
manual with the other manuals and publications pertinent to your system.
Table 1.A lists other available Data Highway manuals and Table 1.B lists
PC manuals.
T
able 1.A
Data
Highway Documentation
Old
Publication
Number
1774-819 1774-6.5.8 User’
1771-822 1771-6.5.15 User’
1771-823 1771-6.5.16 User’
1773-801 1773-6.5.2 User’
1775-802 1775-6.5.1 User’
1771--811 1771-6.5.8 User’
1770-810 1770-6.2.1
New
Publication
Number
Module (cat. no. 1771-KA)
Module (cat. no. 1771-KE/KF)
Module (cat. no. 1771-KX1)
Communication Interface Module (cat. no.
1773-KA)
Module (cat. no. 1775-KA)
Interface Module (cat. no. 1771-KG)
Data Highway Cable Installation Manual
Title
s Manual, Communication Adapter
s Manual, Communication Controller
s Manual, PROVOX system Interface
s Manual, PLC-4 Microtrol
s Manual, Communication Adapter
s Manual, PLC-2 Family/RS-232-C
1–3
Page 8
Chapter 1
Introduction
T
able 1.B
Manuals for Allen-Bradley Programmable Controllers
Old
Controller
Mini-PLC-2
Program. Cont.
Mini-PLC-2/05 1772-830
Mini-PLC-2/15
Program. Cont.
PLC-2/20
Program. Cont.
PLC-2/30
Program. Cont.
PLC
Program. Cont.
PLC-3
Program. Cont.
PLC-4 Microtrol
Number
1772-820
1772-821
1772-831
1772-803
1772-804
1772-807
1772-802
1772-807
1772-806
1774-812
1774-800
1775-800
1775-801
1773-800 1773-6.5.1
New
Number
1772-6.6.3
1772-6.8.4
1772--6.6.6
1772-6.8.6
1772-6.6.1
1774-6.8.2
1772-6.6.2
1772-6.8.1
1772-6.6.2
1772-6.8.3
1774-6.6.2
1774-6.8.1
1775-6.7.1
1775-6.4.1
Manual TItle
Assembly and Installation
Programming and Operation
Assembly and Installation
Programming and Operations
Assembly and Installation
Programming and Operations
Assembly and Installation
Programming and Operations
Assembly and Installation
Programming and Operations
Assembly and Installation
Programming and Operations
Installation and Operations
Programming
Product Guide
To use this manual, 1772-6.5.1, knowledge of the particular
progammable controller being used in your application is essential.
Because you connect the communication adapter module to an operating
programmable controller, you must have a good understanding of
programmable controller operation, installation, memory structure, and
programming.
1–4
Publications are available for each Allen-Bradley programmable
controller. All publications in Table 1.A and Table 1.B are available from
an A-B sales office, or from Allen-Bradley Publications, 6100 Industrial
Court, Greendale, WI 53129.
Features of a 1772-KA2
Here are some of the KA2’s features:
New commands have been added to the 1771-KA2 that simplify
upload and download procedures.
A KA2 lets you to change (remotely) the size of the PC data table.
(New with 1772-KA2 module.)
It has second module or “daisy chain” capability. (New with 1772-KA
2 module.)
Uses ladder diagram instructions for ease of programming.
Offers memory write protection through programming and switch
selection.
Page 9

Chapter 1
Introduction
Controls communication without need for a host computer.
Has automatic error checking of data it receives.
Has self-checking diagnostics.
Shows status and diagnostics with LED indicators and error codes.
Controls DONE and REMOTE/LOCAL FAULT memory bits as status
and diagnostic indicators.
Automatically re-tries messages.
Automatically recovers from master station fault condition.
Has selectable priority levels for commands.
Is compatible with industrial terminal system.
Installs easily.
Organization
Chapter Summary
The chapters in this manual are organized as follows and each chapter
closes with a summary:
Chapter 2 describes the hardware components that make up a Data
Highway station.
Chapter 3 outlines procedures for module installation.
Chapter 4 describes programmed commands and memory access.
Chapter 5 describes programming of the communication zone of
program.
Chapter 6 describes status words that are controlled by the module at
its station processor.
Chapter 7 outlines programming that is necessary to initiate and
monitor command execution.
Chapter 8 describes station interface module interaction along the Data
Highway.
Chapter 9 describes start-up and troubleshooting tools and procedures.
Chapter 10 provides aids to design and documentation of a Data
Highway that uses a communication adapter module.
This chapter discussed:
Features of a 1771-KA2 Communication Adapter Module
How the module fits into an A-B Data Highway system
What a 1771-KA2 does, and the A-B PLC data processor it works with
Publications available for Data Highway and PLC-2 family PCs
In chapter 2 you will learn about a Data Highway station and the KA2’s
role in station function.
1–5
Page 10

Chapter 1
Introduction
1–6
Page 11
Station Hardware
Chapter
2
General
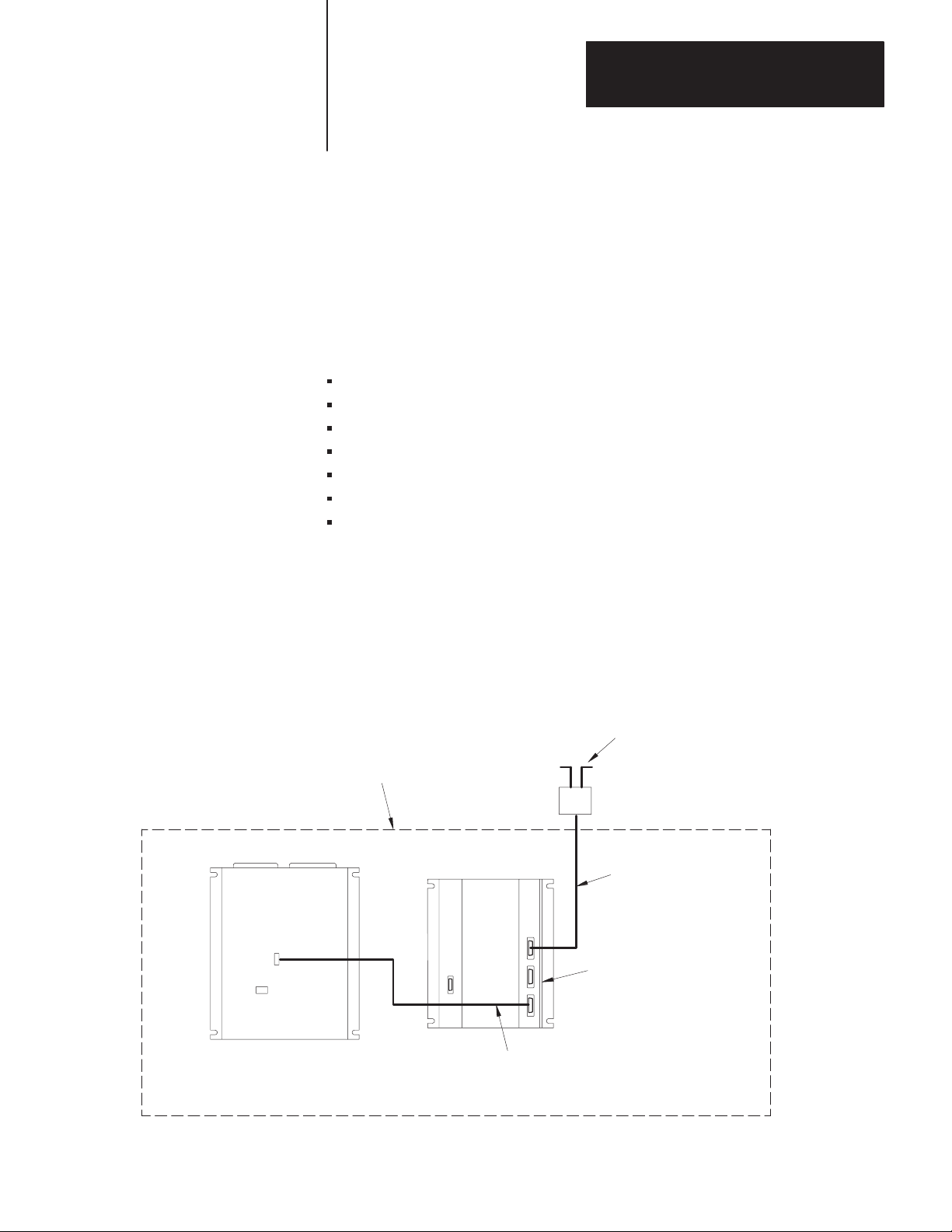
The following components make up a Data Highway station with a PLC-2
family PC:
Communication Adapter Module
Processor
PLC-2 I/O adapter module for PLC-2/20 and PLC-2/30 processors
Bulletin 1771 I/O chassis
Power supply
Data Highway/Processor cable
Data Highway cable dropline
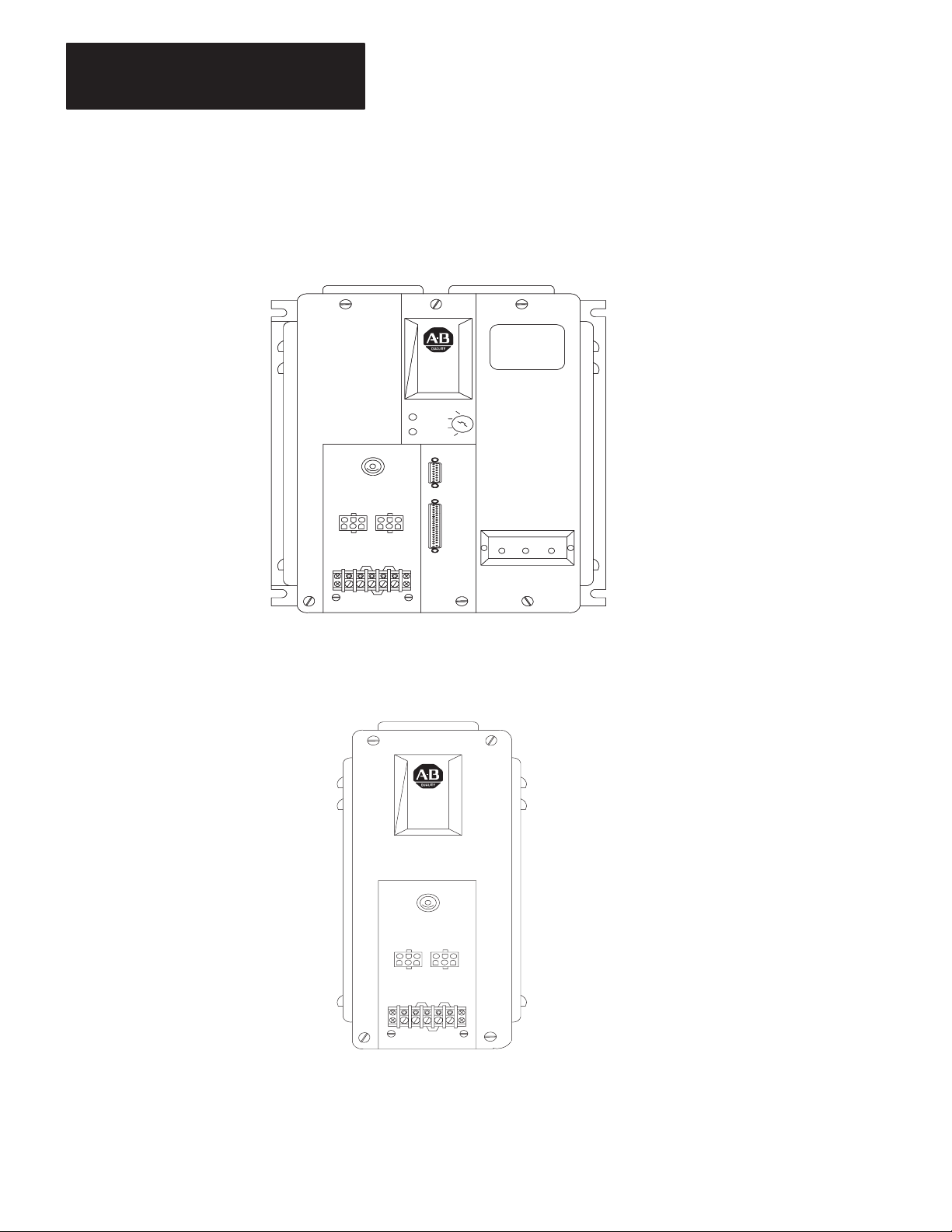
Figure 2.1 shows the configuration of a typical Data Highway station for
PLC-2/20 and PLC-2/30 processors. Figure 2.2 shows a typical
configuration for the mini-processor module.
Figure 2.1
Typical
Station Configuration--PLC-2/20 and PLC-2/30 Processors
Data Highway
Cable Trunkline
Station
Processor
I/O Chassis
Data Highway
Processor Cable
(cat. no. 1771-CR)
Station
Dropline
100 feet
maximum
Communication
Adapter
Module
(cat. no. 1771-KA2)
12326
2-1
Page 12
Chapter 2
Station Hardware
Figure 2.2
Typical
Station Configuration--Mini-PLC-2, Mini-PLC-2/05, and Mini-PLC-2/15 Controllers
Data Highway Cable
Trunkline
Station
Mini-Processor Module
(cat. no. 1772-LV, -LS, -LSP;
1772-LN1, -LN2, -LN3)
System
Power Supply
Data Highway
Processor Cable
(cat. no. 1771-CN.-CO)
Communication Adapter
Module (cat. no. 1771-KA)
Station
Dropline
Connection for
Programming
Terminal
12327
As these figures illustrate, the term “station” combines both the
communication adapter module and its connected programmable
controller processor. (When specifying only the individual processor or
communication adapter module at a station, the terms “station processor”
or “station communication adapter module” are used.)
Communication Adapter Module
2-2
The following sections describe the functions and compatibility of each
station hardware component.
A communication adapter module (cat. no. 1772-KA2) provides the
interface between all PLC-2 family PCs and other stations on the Data
Highway. (Refer to Figure 2.3). The module has sockets for cable
Page 13
Chapter 2
Station Hardware
connection, switches for enabling or disabling specific module operations,
and indicators to aid in monitoring module behavior and in
troubleshooting. Subsequent sections describe each of these parts of the
module and other aspects of module hardware that are significant in its
set-up and installation.
Each communication adapter module in a Data Highway installation must
have a unique station number. This station number is used to address
commands to the module from other stations.
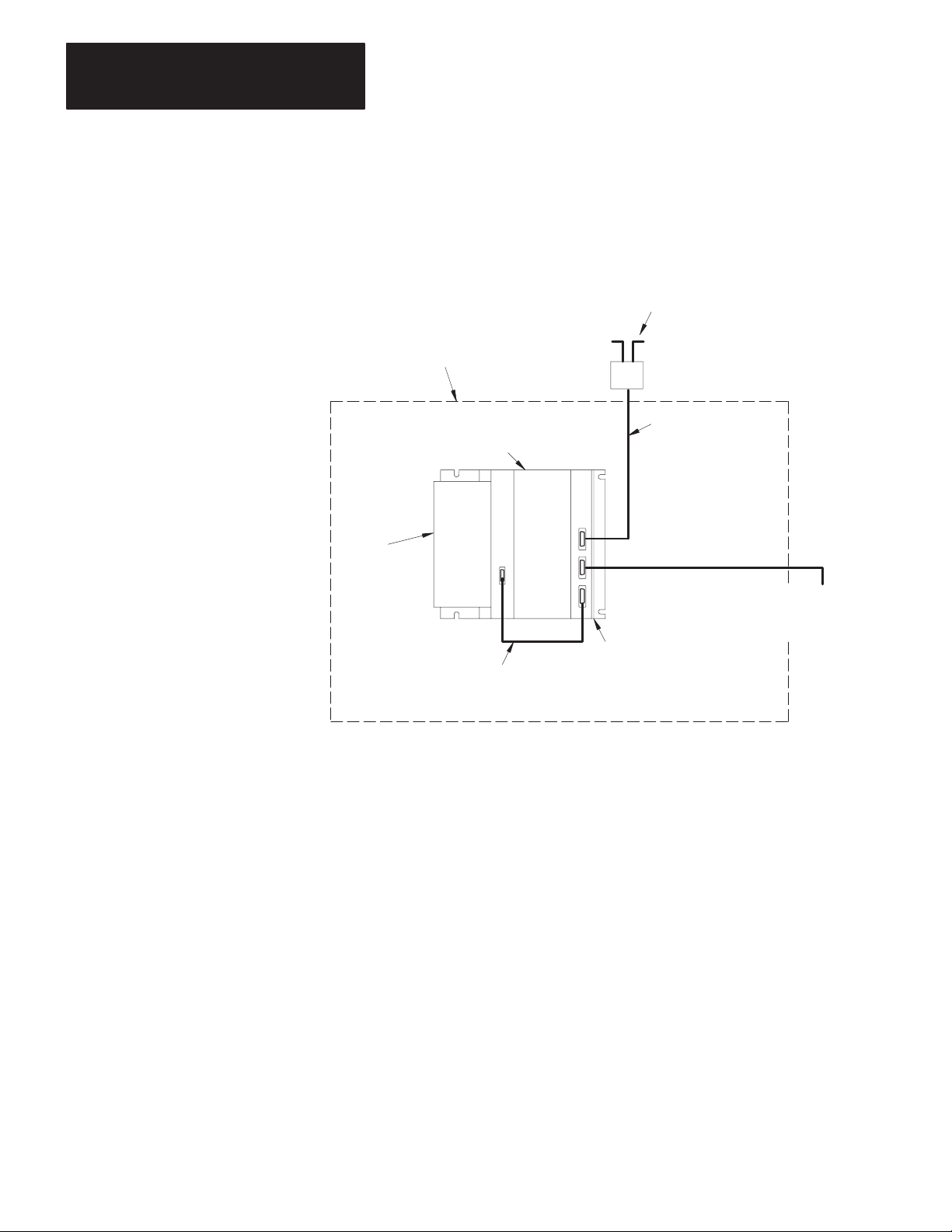
Figure 2.3
Communication
Adapter Module (cat. no. 1771-KA2)
(Side view)
Indicator
Connectors
10862-I
Switch Cover
Connectors
The front of a 1772-KA2 module has 3 cable connectors labeled:
DATA HIGHWAY
PROGRAM INTERFACE
PROCESSOR
See Figure 2.4.
2-3
Page 14
Chapter 2
Station Hardware
Figure 2.4
Module
“Program Panel”
or “Interface”
Socket on
Processor
Connection Summary
Data Highway Cable
(User-Assembled)
Program Panel Interconnect Cable
(Cat. no. 1772-TC)
Data Highway
Processor Cable
(cat.no. 1771-CN, -CO, -CR)
Industrial Terminal System
(cat. no. 1770-T1 and T2)
Data Highway Connector
The upper connector of the module accepts the 15-pin Data Highway
dropline cable. Through this connection, a single KA2 module can
communicate with as many as 63 other Data Highway stations.
Module transmitting and receiving circuitry on this channel are
transformer-coupled to the Data Highway link. This design permits
differential transmission of data with high common-mode noise immunity.
Electrically, transformer coupling provides isolation between module
logic circuitry and the Data Highway cable.
Program Interface Connector
10863-I
2-4
The middle outlet on the module connects to an industrial terminal system
(cat. no. 1770-T1, -T3), or to a second KA2, or to a 1771-KG series B
module.
Page 15

Chapter 2
Station Hardware
To connect any programming terminal to the PROGRAM INTERFACE
connector, use a program panel interconnect cable (cat. no. 1772-TC).
With a 1772-KA2 module installed, the PROGRAM INTERFACE
connector substitutes for the PROGRAM PANEL connector on PLC-2/20
or PLC-2/30 processors or the INTERFACE socket on the Mini-PLC-2,
Mini-PLC-2/05, or Mini-PLC-2/15. This means that all interaction
between the processor and the programming terminal is controlled
through the communication adapter module. This interaction includes
program entry and any functions that involve peripheral devices except
cassette loads--including report generation, contact histograms, and
generation of program copies on paper or on punched tape.
The communication rate over this channel is 9600 baud.
Optical-electrical isolation is provided between receiving circuitry on this
channel and module logic circuitry.
NOTE: The PROGRAM INTERFACE connector need not connect to a
programming terminal for the module to operate. This connector serves as
a programming terminal connection whenever such a device is needed for
program entry, editing or monitoring.
Processor Connector
The lower connector of the module connects to the station PLC-2/20 or
PLC-2/30 processor, or Mini-processor module. (Refer to Figure 2.1 and
Figure 2.2) A Data Highway/Processor cable, described in section titled
“Cables,” is used for this connection.
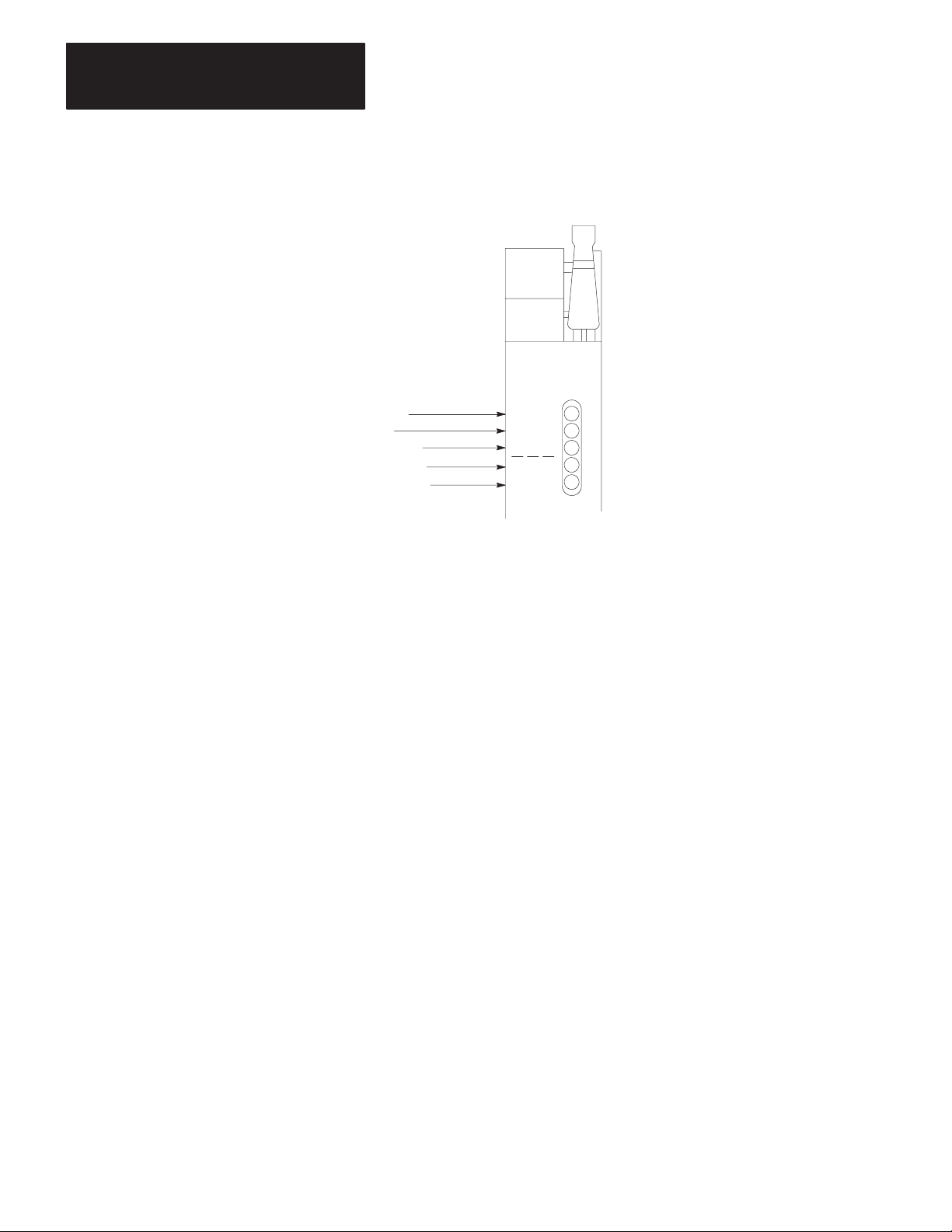
Indicators
There are 5 LED indicators on the front of the module, as seen in
Figure 2.5.
These indicators are useful for monitoring module activity and for
troubleshooting. Three green indicators show module status during
normal receiving and transmitting of messages. Two red indicators show
the status of module diagnostics.
2-5
Page 16
Chapter 2
Station Hardware
Figure 2.5
Module
Indicators
COMM
ADAPTER
Transmitting
Receiving
Message Ready
Program Status
Processor Link
Status
XMTG
RCVG
RDY
PROG
PROC
XMTG
The green transmitting indicator turns on when the module is current
master of the Data Highway. When this indicator is on, therefore, the
communication adapter module is transmitting messages on the Data
Highway communication link, or it is polling.
RCVG
The receiving indicator turns on when the module is receiving a message
addressed to it. Otherwise, RCVG is off.
When both the RCVG and XMTG indicators are on, the module is current
master of the Data Highway and is polling. (The section titled “Polling,”
in chapter 8, describes polling procedure.)
2-6
RDY
The green message ready indicator turns on when the module has
messages ready to transmit. With this indicator on, the module is ready to
assume mastership when it is polled.
Page 17

Chapter 2
Station Hardware
PROG
The red program status indicator tells you the status of module checks on
the communication zone rungs of the user program. (The section titled
“Overall Format,” chapter 5, describes these rungs.) The module first
checks these rungs at power-up. When it locates the header rung of this
zone, the module turns the PROG indicator on. After it checks the rungs,
provided no errors are found, the module turns the PROG indicator OFF.
However, if the module detects any programming error in the
communication zone of the program, this indicator remains ON. In this
event, the module cannot function. You must check the communication
zone of the program and correct any errors. (Start-up procedures are
described in chapter 9.)
PROC
The red processor link status indicator gives the status of error-checking
diagnostics for communication adapter/processor communication. The
PROC indicator is normally off.
Should the 1771-KA2 module detect an error in data transmission with
the processor, it turns the PROC indicator on. This may mean one of the
following:
Disconnection of the Data Highway/Processor cable between the
communication adapter and the processor
Fault in processor operation
Incorrect selection of processor link communication rate on the module
(Refer to section titled “Write Option Switch Assembly,” chapter 3).
The section titled “Module Indicators,” in chapter 9, describes the use of
indicators in troubleshooting.
Switches
There are 3 sets of switches on the 1771-KA2 module circuit board. These
switches are beneath the small switch cover plate on the component-side
cover of the module. (Refer to Figure 2.3).
The programmer selects the settings of these switches for each
communication adapter module, based upon such variables as station
number, command capabilities, and type of station processor. Switch
settings are a part of module installation, described in chapter 3.
2-7
Page 18

Chapter 2
Station Hardware
Module Specification Summary
Table 2.A lists operating specifications for a 1771-KA2 module.
T
able 2.A
Operating
Specifications
Function
Interface entire PLC-2 family
•
programmable controller to the Data
Highway
Location
Bulletin 1771 I/O Chassis (any slot
•
except furthest left)
Communication Channels
• T
o Data Highway
• T
o programming terminal or second
module in daisy chain
• T
o processor or first module in daisy
chain
Communication Rates
• T
o Data Highway: 57.6k baud
(Recommended)
• T
o programming terminal or second
module: 9.6k buad
• T
o processor: 91.2k baud for
processor (except PLC-2, cat. no.
1772-LR); 9.6k baud for first
communication module or PLC-2family processor
.
Compatible Power Supplies
•
System power supply (cat. no. 1771-P1)
•
Auxiliary power supply (cat. no. 1772-P2)
•
System power supply module (cat. no.
1772-P1, series B or later)
•
Auxiliary power supply (cat. no. 1772-P2
series B or later)
•
Power supply module 1771-P3
•
Power supply module 1771-P4
•
Power supply module 1771-P5
Ambient T
• 32o to 140oF (0o to 60oC) (operational)
• -40o to 185oF (-40o - 85oC) (storage)
Humidity Rating
•
Keying
•
•
Power Supply Requirement
•
emperature Rating
5% to 95% (without condensation)
Module slotted for I/O chassis keying
band positioning.
Positions 4-6, 22-24
+5V DC at 1.2A (max.)
Processor
2-8
This manual uses the term “processor” as a general term for any of the
PLC-2 family processors. Individual processors are specified only when
some distinction must be made.
The normal operating sequence of the station processor is not changed by
a communication adapter module, that is, the processor carries out its scan
of input and output modules and execution of the user program as though
the communication adapter module weren’t there.
Page 19

Chapter 2
Station Hardware
The interaction between a KA2 module and its station processor occurs in
memory control. The station KA2 can read data from and write data into
processor memory, based on various user-programmed commands.
Commands that originate at a station communication adapter module can
control only data table areas of processor memory. Commands generated
by a computer that is connected to the Data Highway through a
communication controller module (cat. no. 1771-KE/KF) can control
both data table and user program memory areas.
Note that the processor continues to execute the user program and to
control output devices, whether or not the station communication adapter
module is in operation. Thus, disconnection of the Data Highway cable or
faulted operation of the communication adapter module does not cause
shutdown of the station processor.
I/O Chassis
A-B designed the 1771-KA2 module to fit in a Bulletin 1771 I/O chassis
assembly (cat. no. 1771-A1,-A2,-A4). This chassis houses Mini-PLC-2,
Mini-PLC-2/05 and Mini-PLC-2/15 programmable controllers. With one
of these controllers, you can use any unoccupied I/O slot for
communication adapter modules.
With PLC-2/20 and PLC-2/30 programmable controllers, use a Bulletin
1771 I/O chassis as an I/O rack. In this case, the 1771-KA2 module can
be installed in any chassis slot except the one furthest left. This left-most
slot must be occupied by a PLC-2 I/O adapter module (cat. no. 1771-AL
or 1771-AS), shown in Figure 2.6, or a backplane jumper board assembly
(cat. no. 1771-EY).
A Bulletin 1771 I/O chassis is usually mounted within an enclosure. We
recommend proper grounding of this enclosure because it minimizes the
effect of noise from the surrounding industrial environment. (Grounding
procedures for the Bulletin 1771 I/O chassis are described in publication
1772-6.6.3).
2-9
Page 20
Chapter 2
Station Hardware
Figure 2.6
1771-AL
Adapter Module
Power Supply
PLC-2
I/O ADAPTER
10864-I
A 1771-KA2 module gets its power from the backplane. It requires +5V
DC at 1.2 amperes (max.). The following power supplies are compatible:
System power supply (cat. no. 1771-P1)
Auxiliary power supply (cat. no. 1771-P2)
PLC-2 system power supply module (cat. no. 1772-P1, series B or
later)
PLC-2 auxiliary power supply (cat. no. 1777-P2, and 1777-P4 series B
or later)
Modular power supplies (cat. no. 1771-P3, -P4, -P5)
You must connect one of these supplies to the I/O chassis that contains the
KA2 communication adapter module. In a Mini-PLC-2, or a
Mini-PLC-2/15 this is the system power supply, shown in Figure 2.7. In a
Mini-PLC-2/05, you must use a 1771-P3, -P4, or P5 power supply.
2-10
Page 21
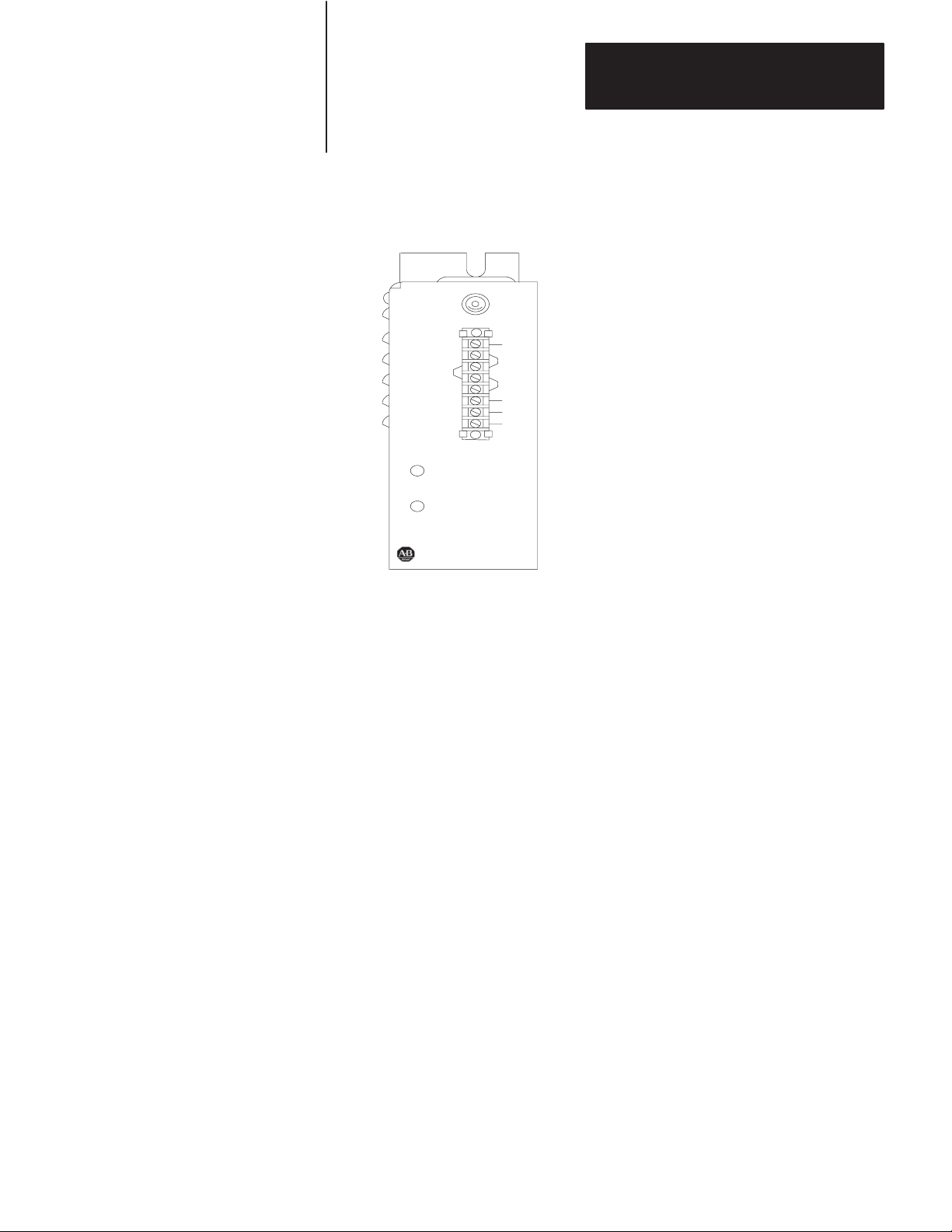
Figure 2.7
1771-P1
Chapter 2
Station Hardware
System Power Supply
Battery
Low
DC ON
ALLEN-BRADLEY
10865-I
When using the PLC-2/20 or PLC-2/30 processor, any of these supplies
can power the I/O chassis so long as core memory is not being used.
(Refer to processor manuals.) An auxiliary power supply (cat. no.
1771-P2) closely resembles the system power supply shown in Figure 2.7.
PLC-2 power supply module (cat. no. 1772-P1) is not a separate unit, but
is enclosed within the metal chassis of the PLC-2/20 or PLC-2/30
processor.
PLC-2 power supplies must be series B or later for communication
adapter module compatibility. On both of these supplies, a label on the
front edge of the circuit board identifies the series level. To locate this
label, remove AC power from the supply and remove the metal front plate
that covers the module. If the label shows the catalog number but not the
series level, the module is series A. Otherwise, series B or later is
indicated.
2-11
Page 22
Chapter 2
Station Hardware
Figure 2.8
PLC-2
Power Supplies
AC FUSE
AC FUSE
PLC
PLC
2/30
2/30
a. PLC-2 System Power Supply Module
AC FUSE
10236-I
10236a-I
2-12
b. PLC-2 Auxiliary Power Supply
Page 23

Chapter 2
Station Hardware
Cables
A 1771-KA2 module requires the following cables for installation:
Data Highway/Processor cable (cat. no. 1771-CN,-CO,-CR)
User-assembled Data Highway cable
Figure 2.1 and Figure 2.2 show the connections made with these cables.
You can order Data Highway/Processor cables in 3 lengths:
1.5 ft. (cat. no. 1771-CN)
3.5 ft. (cat. no. 1771-CO)
10.5 ft. (cat. no. 1771-CR)
The 2 shorter cables are intended for connection to a Mini-PLC-2,
Mini-PLC-2/05, or Mini-PLC-2/15 module. A 10.5 ft. cable is used with
PLC-2, PLC-2/20 or PLC-2/30 processors.
You must assemble and install your own Data Highway cable, dropline
and trunkline segments. A separate publication, Data Highway Cable,
Assembly and Installation Manual, publication 1770-6.2.1, gives
information on layout, make-up, and installation of the cable.
Other Optional Equipment
Chapter Summary
In addition to the components shown in Figure 2.1 and Figure 2.2, you
can install your own equipment at or near the Data Highway station. The
chief purpose of additional components is to provide diagnostic or
monitoring information. Such devices as alarms, displays and indicators
can be controlled from output modules of the programmable controller to
provide operating or fault information to plant personnel.
Minimally, a single indicator should be installed to alert your personnel to
a REMOTE or LOCAL FAULT condition that prevents normal message
transfer. The significance of REMOTE/LOCAL FAULT bits, and the
recommended programming to monitor these bits, is described in chapter
7.
This chapter told you the:
Components of an A-B Data Highway system
Role of a 1771-KA2, its connectors, switches, and indicators
Specs of a 1771-KA2
Where a KA2 resides and how it is connected to its station
Optional equipment possibilities at a Data Highway station
In chapter 3 you will read about KA2 switches and installation.
2-13
Page 24

Chapter 2
Station Hardware
2-14
Page 25

Module Installation
Chapter
3
General
Switch Settings
This chapter outlines procedures for preparation, installation, and
connection of a 1771–KA2 module. Before performing these procedures,
you should check component compatibility and the station set–up
recommendations in chapter 2.
There are 3 sets of switches on a 1771–KA2 circuit board:
Write option switch assembly
Station no. switch group
Data Highway baud rate switch assembly
Refer to Figure 3.1. The switches at each station communication adapter
module must be set as the programmer specifies. To access these
switches, loosen the two screws that hold the small cover plate to the side
of the module. Then, rotate this cover plate to expose the switches.
Figure 3.1
Module
Switches
Write
Option
Switch Assembly
12345
O
N
O
F
F
6
O
N
O
F
F
12
O
N
O
F
F
12
O
N
O
F
F
12
3
Station Number Switch Group
3
O
N
O
F
F
12
Data Highway
Baud Rate
Switch Assembly
12329
3-1
Page 26

Chapter 3
Module Installation
Use the tip of a ball–point or other pointed instrument to set these
switches. Do not use a pencil, as lead could jam the switch.
For troubleshooting purposes, we recommend that the programmer
document the required switch settings for each 1771–KA2. Use form
5030, in chapter 10, to record switch settings for the module at each
station. That way, should replacement of the module be required, switches
on the replacements can be set quickly.
Write Option Switch Assembly
The first rocker switch assembly from the left is the write option switch
assembly. (Refer to Figure 3.2). In this assembly, switches numbered 1
through 5 enable or disable different types of write and bit write
commands from being received by, or sent from, the communication
adapter module. (Note that the unprotected read command is not affected
by any of these switch settings.) Switch no. 6 enables and disables daisy
chain operation. See FIRST/SECOND MODULE at end of this section.
Figure 3.2
Write
Option Switch Assembly
Execute Unprotected
Write Commands
Receive Protected
Commands
12
O
N
O
F
F
Send Unprotected
Commands
* After revision D, the name and function of switch 3 changed to ”Execute download in RUN program.”
3456
Shutdown / Auto Restart*
• On–Shutdown
• Off–Auto Restart
Received Priviledged
Write
Enable/Disable
• On–First Module
• Off–Second Module
The following paragraphs describe settings for these switches.
RECEIVE PROTECTED COMMAND SWITCH
12330
3-2
Switch no. 1 of the write options switch assembly determines whether the
module is enabled to receive and execute protected write and bit write
commands from other stations. Set this switch as follows:
Page 27

Chapter 3
Module Installation
ON – Enables execution of received protected commands.
OFF – Disables received protected commands.
Note that both an ON setting of this switch and a memory access rung are
required to allow execution of received protected commands. (Memory
Access rungs are described in chapter 5.)
This switch does not prevent the module from receiving and executing
unprotected commands from another station. (A separate switch,
described subsequently, enables or disables execution of received
unprotected commands.)
EXECUTE UNPROTECTED WRITE COMMANDS SWITCH
Switch 2 determines whether the module can receive and execute
unprotected write and bit write commands from other stations. Set this
switch as follows:
ON – Enables received unprotected write and bit write commands to
be executed.
OFF – Disables the module from executing received unprotected write
and bit write commands
Note that this switch does not disable unprotected read commands from
being received and executed by the module.
SHUTDOWN/AUTOMATIC RESTART SWITCH
On modules before revision D, switch 3 presents the option, after a hard
error, of restarting the 1771–KA2, or shutting it down.
ON – Shuts down the module
OFF – Automatically restarts itself
When a hard error occurs it normally indicates fairly severe
communication problems that should be corrected before starting. Such
errors usually involve bad cabling or noise.
REVISION D
The third switch in the Write Option Switch assembly on the 1771–KA2
module (formerly the Shutdown/Automatic Restart Switch) will change
function for revision D and become the Execute Download in Run
Program switch.
3-3
Page 28

Chapter 3
Module Installation
RECEIVE PRIVILEGED WRITE SWITCH
Switch 4 determines whether the module can execute received privileged
write commands. These commands can be issued only from a computer
connected through a communication controller module (cat. no.
1771–KE/KF).
These commands give the computer the capability to alter the user
program memory of the station processor. Set this switch as follows:
ON – Enables a 1771–KA2 to execute received privileged write
commands
OFF – Disables the 1771–KA2 from executing received privileged
write commands.
SEND UNPROTECTED COMMANDS SWITCH
Switch 5 determines whether the module can send unprotected write or bit
write commands to another station. Set this switch as follows:
ON – Enables the module to send unprotected write and bit write
commands
OFF – Disables the module from sending unprotected write and bit
write commands
This switch does not prevent unprotected read commands from being sent
by a communication adapter module.
FIRST/SECOND MODULE
Use switch 6 for first/second module selection. Set switch:
ON – Use this setting when connected directly to any compatible
processor except PLC–2 (1772–LR).
OFF – Use this setting when the KA2 module is connected to a
PLC–2 (1772–LR), a 1771–KG series B module, or another KA2
module.
3-4
Station No. Switch Group
You must designate a unique station number for each communication
adapter module on a Data Highway. This designation is made by the
programmer and switch–selected on the station number switch group of
the module.
Page 29
Chapter 3
Module Installation
The station number switch group comprises 3 switch assemblies (SW2,
SW3, SW4) on the module circuit board, as Figure 3.3 indicates. These
switches determine the station number of each communication adapter
module.
SWITCH SETTING
No. 1 No. 2
OFF OFF
OFF ON
ON OFF
ON ON
a. First Digit
The station number is a 3–digit octal number from 010
110
–3768. Each of the 3 switch assemblies in this group is set to
8
represent an individual digit of this station number. Figure 3.3 shows the
combination of switch settings for each digit.
Figure 3.3
Station
Number Switch Settings
12
O
N
O
F
F
SW2 SW3 SW4
O
N
O
F
F
DIGIT
0
1
2
3
12
3
12
O
N
O
F
F
No. 1 No. 2
OFF OFF
OFF OFF
OFF ON
OFF ON
ON
ON
ON
ON
b. Second and Third Digits
–077
8
3
ON
ON
OFF
SWITCH SETTING DIGIT
No. 3
OFF
ON
OFF
ON
OFF
OFF
ON
ON
OFF
ON
OFF
ON
ON
OFF
0
1
2
3
4
5
6
7
8
or
OFF
12331
3-5
Page 30
Chapter 3
Module Installation
In this binary–coded octal numbering arrangement, each switch has an
associated binary value: 1, 2, or 4 if set ON, 0 if set OFF. The value of
each individual digit of the station number is the sum of the binary values
in its corresponding switch assembly. Table 3.A gives an example for the
settings of this switch group.
T
able 3.A
Switch
Setting Example: Station No. 037
STATION
NO. DIGITS
SWITCH NO.
SWITCH
SETTING
0 3 7
1 2 1 2 3 1 2 3
OFF OFF OFF ON ON ON ON ON
Note that the switches allow a range of station numbers from 0008 to 377
(256 possible numbers). However, there are practical reasons for using
the the range 010
–077
8
and 110
8
–3768. These station numbers are
8
addressable from any station using an industrial terminal. PLC–2 family
programmable controllers cannot address 000
Also, station 377
is an illegal address on the Data Highway. To optimize
8
response times, use consecutive station numbers beginning with 010
to 0078 or 1008 to 1078.
8
.
8
Data Highway Baud Rate Switch Assembly
The switch assembly labeled SW5 on the module circuit board is the data
highway baud rate switch assembly. (Refer to Figure 3.4). The switches
in this assembly must be set for the baud rate being used on the Data
Highway communication link.
Figure 3.4
Data
Highway Baud Rate Switch Assembly
8
3-6
12
O
N
O
F
F
Both switches ON for
57.6K Baud Rate
Page 31

Chapter 3
Module Installation
The module is shipped with these switches set for 57.6K baud. Both
switches are set ON for this communication rate. This baud rate is the
intended Data Highway communication rate.
CAUTION: Do not set these switches for any other baud rate.
Incorrect setting of these switches may cause faulted data
transmission on the Data Highway communication link. This
may disable Data Highway operation until the switch setting is
corrected.
After rechecking all switch settings, replace the cover plate on the
module.
Keying
The I/O slot designated for the 1771–KA2 communication adapter
module should be keyed to admit only that module. Plastic keying bands,
shipped with the I/O chassis, accomplish this purpose. These keying
bands provide for only one type of module in a slot.
On the rear edge of the communication adapter module are 2 slots.
Position the keying bands on the backplane connector to align with these
slots. For the communication adapter module, position keying bands on
the upper backplane connector between these numbers printed on the
backplane:
4 and 6
22 and 24
Refer to Figure 3.5. Use needle–nose pliers to insert or remove keying
bands.
3-7
Page 32

Chapter 3
Module Installation
Figure 3.5
Keying
Band Position
Keying
Bands
2
4
6
8
10
12
14
16
18
20
22
24
26
28
30
32
34
36
Installation In The I/O Slot
Follow these procedures to install the module:
1. Turn I/O chassis power off. (This refers to the power supply that
connects to the I/O chassis at its backplane.
CAUTION: To avoid module damage, always be certain that
power to the I/O chassis is off before insertion or removal of the
KA2.
2. Insert the keying bands, as described in section titled “Keying.”
3. Insert the module into its designated slot. Plastic tracks on the top
and bottom of the slot guide the module into position. Do not force
the module into its backplane connectors. Rather, apply a firm, even
pressure to seat the module in its slot.
4. Snap the plastic chassis latch over the module. This secures the
module firmly in the I/O chassis.
3-8
Page 33

Chapter 3
Module Installation
Cable Connections
The following cable connections are made to a communication adapter
module:
Data Highway cable
Program panel interconnect cable (cat. no. 1772–TC)
Data Highway/Processor cable (cat. no. 1771–CR, –CO,–CN)
At set up, all cable connections to the module can be made with power on.
After the program is up and running, however, it is safer to make
connections with power off because of the possibility of noise that
connecting will make. Also, again after the program is running, a module
should only be connected to a Data Highway with power off. A
powered–up module that is disconnected from the Data Highway will be
in the polling state and cause a highway fault if it is re–connected. This is
the same as connecting two active highway segments (which also should
not be done).
Data Highway Connection
The module connects to the Data Highway communication link by means
of a user–assembled dropline. This dropline connects to the trunkline of
the Data Highway at a 1770–SC station connector (Figure 3.6), or a
1770–XG tee connector.
3-9
Page 34

Chapter 3
Module Installation
Figure 3.6
Data
Highway Cable Connection
1770–SC Station Connector
Trunkline
Dropline
(100 feet maximum)
Communication Adapter
Module (cat. no. 1771–KA2)
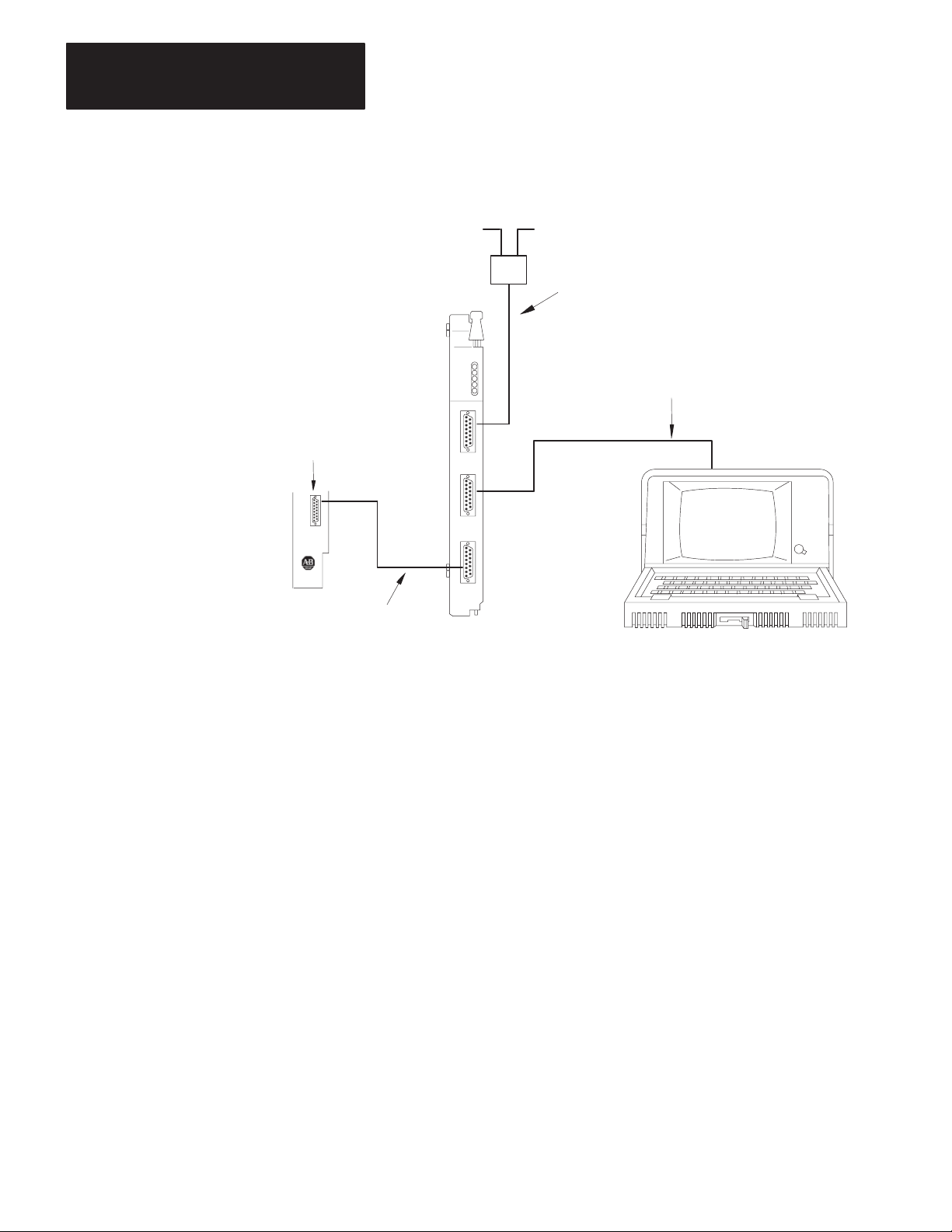
Program Panel Interconnect Cable Connection
The center connector of the communication adapter module is labeled
PROGRAM INTERFACE. When the module is installed and connected
to the processor, this socket connects an industrial terminal system (cat.
no. 1770–T1, –T3).
To connect with any of these terminals, use the program panel
interconnect cable (cat. no. 1772–TC). Figure 3.7 shows the
programming terminal connections to the communication adapter module.
When an industrial terminal is connected this way, you can perform all
terminal functions except cassette loads, or dumps. You must disconnect
the KA2 perform these functions.
3-10
Page 35

Figure 3.7
Industrial
Chapter 3
Module Installation
Terminal Connection
Channel A
Program Panel Interconnect
Cable (cat. no. 1772-TC)
10219a-I
Data Highway/Processor Cable Connector
The bottom connector of a 1771–KA2 module is labeled PROCESSOR.
The communication module communicates with the station processor
through this connector. The Data Highway/Processor cable (cat. no.
1771–CN, –CO, –CR) connects from this socket to a socket on the fact of
the station processor. On a PLC–2/20 or PLC–2/30 this is the connector
labeled PROGRAM PANEL; on a Mini–PLC–2 or Mini–PLC–2/15, the
connector is labeled INTERFACE. (Refer to Figure 3.8) and on a
Mini–PLC–2/05 the socket is labeled INTFC.
3-11
Page 36

Chapter 3
Module Installation
Figure 3.8
Data
Highway/Processor Cable Connection
PLC-2/20
Processor
PLC
2/20
AC FUSE
Connector
Labeled
“Program
Panel”
Communication Adapter
Module (cat.no. 1771-KA2)
Processor
Connector
Data Highway Processor
Cable (cat.no. 1771-CR)
a. Connection to PLC-2/20 or PLC-2/30 Processor
Mini-PLC-2/15
Module
Connector
Labeled
“Interface”
b. Connection to Mini-PLC-2, Mini-PLC-2/05, and Mini-PLC-2/15
Data Highway Processor
Cable (cat.no. 1771-CN, -CO)
Communication Adapter
Module (cat.no. 1771-KA2)
Processor
Connector
10865-I
A Second Link
To provide a second communication link at a data highway station, you
can connect a KA2 module to another KA2 or to an A–B 1771–KG
(series B) interface module to provide an RS–232–C link and a Data
Highway link. These links enable communication with, say, a PLC–2
family processor on the highway, and a stand–alone computer.
3-12
In such a scheme, the 1771–KG module can be connected directly to the
PLC–2 family processor, and the KA2 connected to the PROGRAM
INTERFACE connector of the 1771–KG, or vice versa.
Page 37

Commands
Chapter
4
General
The primary function of a KA2 module is to transfer data to and from its
station processor. The module is instructed to transfer specific units of
data by user-programmed commands. The communication adapter module
transmits and receives the following set of non-privileged commands:
Protected write
Protected bit write
Unprotected write
Unprotected bit write
Read
These commands are of three general types: write, bit write, and read.
(Refer to Figure 4.1). The write and read commands transfer word data
between the data table of the local station processor and the data table of a
remote station processor. The bit write command controls ON/OFF status
of one or more memory bits at a remote station processor.
Figure 4.1
Module
Command Summary
Data Table at
Local Station Processor
16-Bit Words
Data Table at
Remote Station Processor
Write
Bit Write
Individual Bit
Read
16-Bit Words
Communication
Adapter Module
4-1
Page 38

Chapter 4
Commands
Privileged Commands
This chapter describes functions of these commands and their access to
data table locations at station processors. A KA2 module can also receive
privileged commands from a computer or another intelligent RS-232-C
device through a 1771-KE/KF communication controller module. These
privileged commands and their functions (briefly) include:
Diagnostic counters reset - resets to zero all diagnostic timers &
counters in the station interface module.
Diagnostic loop - use to check integrity of transmission over
communication link.
Diagnostic read - reads up to 244 bytes of data from PROM or RAM of
station interface module.
Diagnostic status - reads a block of station information from station
interface module; reply includes station information in module’s data
field.
Enter download mode - puts PLC-2 family processor into download
mode. Use before sending physical write commands to station.
Enter upload mode (new on KA2 module) - puts PLC-2 family
processor into upload mode. Use before sending physical reads to
station.
Exit download/upload mode - takes PLC-2 family processor out of
upload/download mode. Use to restart processor after uploading or
downloading.
Physical read - reads bytes of data from PC data table or program
memory. Use the upload contents of PLC-2 family processor memory
to computer.
Physical write - writes bytes of data into PC data table or program
memory. Use to download computer contents to PLC-2 family
processor memory.
Set data table size* - sets data table size for PLC-2 family processor.
Use before physical writes on PLC-2 family processor. All PLC-2
family data tables are configurable, but some have wider ranges than
others. Check the appropriate manual for the processor in your
application.
4-2
Later chapters cover the following:
Command programming (chapter 5)
Command status bits (chapter 6)
Command initiation and execution monitoring (chapter 7)
Page 39

Chapter 4
Commands
Terminology: Remote/Local Station
In this and later chapters, we use the terms “remote station” or “local
station.” The local station is the point of reference. When describing the
commands, for instance, the local station is the one sending the command.
A remote station is any station that receives a command from the local
station.
Figure 4.1 illustrates this terminology.
Protected/Unprotected
Each 1771-KA2 module command has a prefix, either “protected” or
“unprotected.” This prefix denotes memory access of the command. The
distinction between these command types is:
Protected commands can access (write into) only specified data table
areas. The program in the receiving station processor controls these areas.
In that program, a memory access rung determines which data table areas
will accept protected write or protected bit write commands. (Rungs are
described in chapter 5.) The receiving station ignores protected
commands that are not defined by the memory access rung.
Unprotected commands require no memory access rung, and they can
read or write into any addressable data table word in the receiving station
processor.
The primary distinction between these commands is program restriction
of memory access. Switch selections can also be made on the module for
write protection, to enable/disable execution of many of these commands.
(Chapter 3 gives switch selections.)
Figure 4.2 summarizes the distinction between protected and unprotected
commands.
4-3
Page 40

Chapter 4
Commands
Memory
Word
Address
Figure 4.2
Protected/Unprotected
Command Distinction
An unprotected
command can
access any area
of data table
memeory at a
receiving station
processor
A protected
021
>
022
023
End of
Data
Table
a. Access Definition
command can access
only specified
>
areas (determined
by memory access
rung in receiving
station) of memory
Branch Start
Instruction
G
021 023
G G
10866-I
010
b. Memory Access Branch (typical)
NOTE: For most write and bit write operations between station
processors, protected commands should be used. Because memory access
must be allowed by the program at the receiving station processor,
protected commands allow programmed write protection, which gives the
programmer an added degree of control over command execution.
Unprotected commands provide the same functions in transferring data,
but without this write protection at the receiving station.
Write Commands
4-4
A write command transfers word data from the local station processor to a
remote station. A single write command can send from 1 to 121
consecutive data table words.
There are 2 types of write commands that can be sent from a station
communication adapter module:
Protected write
Unprotected write
The distinction between these types of commands is their memory access.
Protected write commands are not executed by the receiving station unless
a memory access rung is programmed at that station and switch 1 on write
options is set. Because this allows added control over data transfer, use of
protected commands is recommended.
Page 41

Chapter 4
Commands
A write command can control data table words at any station processor.
However, certain data table areas at each type of processor have a special
function and should not be controlled by write commands. (Sections
titled “Accessible Data Table Locations-PLC-2 Processors” and
“Accessible Data Table Locations-PLC Processors” cover data table
control.)
Bit Write Commands
Bit write commands control the ON/OFF status of bits in a remote station
data table. Unlike read or write commands, bit write commands do not
transfer data table memory data. Instead, the programmed command rung
itself specifies which bits are to be set on or off when the command is
executed. (Refer to chapter 5.)
There are 2 types of bit write commands that can be sent from a
communication adapter module:
Protected bit write
Unprotected bit write
The distinction between these commands is their memory access.
Protected bit write commands are not executed by the receiving station
unless a memory access rung defining the appropriate memory area is
programmed at that station and switch 1 is set. Because this write
protection feature allows added control over command execution, use of
protected commands is recommended.
A bit write command can control data table areas at any station processor.
However, certain data table words at each type of processor have a special
function and should not be controlled by bit write commands. (Data table
control is the subject of sections titled “Accessible Data Table
Locations-PLC-2 Processors” and “Accessible Data Table Locations-PLC
Processors”).
On each 1771-KA2 communication adapter module, the sending and
receiving of write messages can be enabled or disabled by switch settings.
(Refer to chapter 3.)
Bit Write Access
The bit write command can be used to control any accessible data table
bit. However, this command must not be used to control the following:
Any bit whose status is controlled by a programmed output instruction.
Any bit in a byte that also contains program-controlled bits.
4-5
Page 42

Chapter 4
Commands
This first restriction simply states that no bit should be directly controlled,
that is, addressed, by both an output instruction at its local station
processor and a bit write command from some remote station processor.
Bit write commands are generally used to set storage bits in a station
processor data table. These storage bits may then be examined in the user
program as conditions to energize an output bit. This indirect
programming technique allows control using bit write commands, but
helps to prevent the confusion that can result if an individual bit is
controlled from both an OUTPUT ENERGIZE instruction and a bit write
command.
Figure 4.3 gives an example of an indirect programming technique used to
control bit 01001, which is addressed by an output instruction, with a bit
write command. Here storage bit 12104 is controlled by the bit write
command. This bit is then examined by the program to control the status
of bit 01001. The output bit, 01001, cannot be directly addressed by the
bit write command. However, by controlling the storage bit and
examining it in the program, the same effect is achieved.
Figure 4.3
Bit
Control Use (example)
Control of this output
desired. However bit
already addressed by
Input
11113
a. Original Rung
Input Output
11113
Storage Bit
12104
Control bit through
bit write command to
control output 01001.
b. Recommended Technique
output intructions
Output
01001
01001
4-6
Page 43

Chapter 4
Commands
The second restriction listed above applies when the destination station is
a PLC-2 family PC. For these processors, when the station
communication adapter module receives a bit write command it
manipulates the 8-bit byte of the 16-bit memory word in which the
addressed bit is located. (This may be the low byte, containing bits 00-07,
or the high byte, containing bits 10-17.) Should program instructions
control other bits within the same byte, there is a slight possibility that the
communication adapter module may write over programmed status for
these program-controlled bits. This would occur only if the program
caused a bit to be altered during the time the communication adapter
module was executing a received bit write command.
Therefore, when using the bit write command, address only bits within a
byte that is set aside exclusively for control by these commands.
Read Command
Accessible Data Table Locations
- PLC-2 Processors
The unprotected read command transfers word data from a remote station
processor to the local station data table. A single unprotected read
command can access from 1 to 122 consecutive data table words.
The unprotected read command is not restricted by user programming.
This command can read data table words from any remote station
processor, regardless of either memory access rung programming or
module switch settings.
Because this command controls data table words at its local station
processor, the rules for data table control apply when using this command.
(Data table control is the subject of sections titled “Accessible Data Table
Locations-PLC-2 Processors” and “Accessible Data Table Locations-PLC
Processor”).
When it executes a read, write, or bit write command, the communication
adapter module controls data table locations at a station processor. This
section outlines the recommendations for control of data table locations in
PLC-2 family processors.
A KA2 module executes read, write, or bit write commands to control any
accessible data table words in any of these processors. It also controls
user-selected status words in the data table of these processors. (Status
words are described in chapter 6.) A KA2 can access most data table
words. However, certain memory areas in these processors have special
functions that prevent control of these areas by the module. The
following are data table areas with a special function in these processors:
4-7
Page 44

Chapter 4
Commands
Processor work areas
Input image table
Word 027
Later paragraphs describe the limitations in controlling each of these
areas. Access to all other data table areas is subject to the requirements of
the programmer.
Processor Work Areas
The processor work areas for PLC-2 family processors are addresses
000-007 and 100-107. These areas are used for specific processor
functions and are not accessible to commands from a station
communication adapter module. The processor prevents an attempt to
write data into this area from a remote station KA2. Note also that an
attempt to read data from this area causes all 0’s to be read.
Only privileged commands from a computer can write into or read from
this area of the data table.
Input Image Table
The input image table areas for these processors are addressed as follows:
PLC-2 processor: 110-127
PLC-2/30 processor: 110-177
PLC-2/20 processor: 110-177
Mini-PLC-2 processor module: 110-117
Mini-PLC-2/05 processor: 110-117
Mini-PLC-2/15 processor: 110-117
Please see appropriate processor manuals (Table 1.B) for details.
This area of memory is updated each input scan. Any data written into it
will be cleared on the next input scan. This limits use of the input image
table as a storage area for values or bits. Note, however, that the input
image table may be read from or written to another station. This control
restriction applies only when attempting to write data into the input image
table using a command from a communication adapter module.
4-8
Word 027
Word 027 has a special function with PLC-2 family processors. For
example, bits 02710-02717 are used for report generation; bit 02700
Page 45

Chapter 4
Commands
indicates a low-battery condition. Because of these special functions, care
must be exercised in controlling word 027 with a write or bit write
command.
The processor does not prevent data from being written to this data table
word.
Accessible Data Table Locations
- PLC Processors
When it executes a read, write, or bit write command, the communication
adapter module controls data table locations at a station processor. When
addressing a command to a Bulletin 1774 PLC processor, note that there
are certain data table areas with a special function. These data table areas
are not to be used for control by communication adapter module
commands:
Any input image table word that has a corresponding input module in a
Bulletin 1778 or 1771 I/O rack
Word 377
Word 000
Input Image Table
When an input image table word in the PLC processor data table is
unused, that is, has no corresponding input module in an I/O rack, that
word can be used for storage. However, should an input module
correspond to that word, the data in the word is updated from the input
module each I/O scan.
Note that this restriction does not prevent any word of the input image
table from being written to another station. This control restriction applies
only when attempting to write data into input image table locations.
Word 377
Word 377 has special status functions within the PLC processor. For this
reason, the communication adapter module must not execute write or bit
write commands into this word.
A read command from a local station can address word 377 at a remote
station PLC processor.
4-9
Page 46

Chapter 4
Commands
Word 000
Reserve word 000 of the PLC processor output image table when using a
KA2. This means that commands from another station must not be
programmed to control word 000 or any of its bits.
Accessible Data Table Locations
- PLC-3 Processors
Each PLC/PLC-2 station on a Data Highway can read from or write to
only one specific buffer file at a PLC-3 station. That is the PLC-3 input
file with a number that corresponds to the station number of the
PLC/PLC-2 station. For example, the read/write files assigned to
PLC/PLC-2 stations 1 to 100 (octal) would be as follows:
PLC/PLC-2
Number (octal)
Station
000
001 I001
002 I002
003 I003
004 I004
005 I005
006 I006
007 I007
010 I010
011 I011
012 I012
. .
. .
. .
0770 I077
100 I100
Assigned PLC-3 Input File
for Read/W
rite Access
I008
I009 (Not assigned)
4-10
PLC/PLC-2 station numbers are octal, while PLC-3 input files have
decimal addresses. This means that PLC-3 input files with an 8 or 9 in
their addresses are not used for read/write access by a PLC/PLC-2 station.
The only exception to these rules is that station number 000 is assigned
input file I008.
Page 47

Chapter 4
Commands
The PLC/PLC-2 station can use either protected or unprotected
commands to access its assigned PLC-3 file. Note, however, that the
PLC/PLC-2 station cannot access its assigned file until you create and
allocate that file. To create a PLC-3 file, use the CREATE command
described in the PLC-3 Programming Manual (publication 1775-6.4.1).
Accessible Data Table Locations
- PLC-4 Microtrol Processors
Programmable controllers can send the following non-privileged
commands to a 1773-KA interface module:
unprotected read
unprotected write
unprotected bit write
protected write
protected bit write
A 1773-KA module accepts non-privileged commands like other Data
Highway interface modules with one exception: the 1773-KA module
does not have memory protection rungs. Instead, you set switches that
allow or disallow the module to receive protected and unprotected
commands.
The PLC-4 Microtrol controller uses a four-digit address for its input,
output, flags, store, timer and counter bits. (Timer and Counter status bits
require an additional two digits.) When you issue a command from
another programmable controller or computer, do not enter these
addresses; instead, enter an address code. It is important that you
understand these addresses, however, to see how they relate to address
codes.
4-11
Page 48

Chapter 4
Commands
The addressing scheme is summarized in this chart:
T
able 4.A
Internal
Addressing of a PLC-4 Microtrol Controller
T
ype of
Address
I=Input 1-8 01-20
O=Output 1-8 01-12
Controller
I.D.
Bit
Address Range
X=Flags 1-8
S=Stores 1-8 01-99
T
ype of
Address
T = T
imer 1-8 01-32
C = Counter
(1)
Flag bits 31 and 32 have a special significance. See the PLC-4 Microtrol Product Guide
(publication 1773-800).
Controller
I.D.
1-8 01-32
Timer/Counter
(1)
01-32
Number
Bit
Description
15 - T
imer Clock
16 - Enable
31 - T
imer T
iming
32 - Done
15 - Count -Down Enable
16 - Count-Up Enable
31 - Overflow Underflow
32 - Done
The memory map for a PLC-4 Microtrol controller, ID #1, shown in
Figure 4.4, includes data on inputs, outputs and flags of each active
controller on the loop.
4-12
Each member of the PLC-4 Microtrol loop, including the interface
module, shares the status of the input, output, and flag bits for each
controller on the loop. This becomes significant when you want to
determine response time.
Each time you enter a non-privileged command, you must enter an
address code. This becomes significant when you want to determine
response time.
Page 49

Figure 4.4
Memory
Chapter 4
Commands
Map for Controller 1
Inputs, Outputs
and Flags for
each Controller
on Loop
Controller 1’s Stores
Controller 1’s
Timers/Counters
1–32
Controller 1
Controller 2
Controller 3
Controller 4
Controller 5
Controller 6
Controller 7
Controller 8
S101–S199
Timer/Counter 1
Timer/Counter 32
20 inputs
1101–1120
12 Outputs
O101–O112
32 Flags
X101–X132
Accumulated
Value
16 15
Preset
Value
32 31
Your Program
Sequencer Tables
Each time you enter a non-privileged command, you must enter an
address code. This code designates what part of the controller’s memory
the command will affect. Note that this is a code, and not a true memory
address. A memory address code is a 3-4 digit code that represents a
word (16 bits) in the data table of a PLC-4 Microtrol controller. The
right-most digit of an address code represents the controller ID number in
octal. For example,
4-13
Page 50

Chapter 4
Commands
address code 010
addresses the first controller - controller 1 - while
address code 011
addresses the second controller - controller 2.
A PLC-4 Microtrol uses a decimal addressing scheme (Table 4.A). The
PLC-2 family of programmable controllers use an octal addressing
scheme. Thus, you must convert the PLC-4 Microtrol’s decimal addresses
to octal.
Address codes are divided into four sets:
1. store words
2. input, output, and flag words
3. input, output and flag area
4. timer/counter words
When using these address codes, observe these restrictions:
1. Do not address more than one set at a time. For example, if you want
to read both the store and the input words of controller 1, send one
command to read the store area, and a second command to read the
input words.
2. Do not address more than one controller at a time. For example, if
you want to read the store area of both controller 1 and controller 2,
send two separate read commands.
4-14
3. Do not send a command to a controller that is in program mode. A
controller in program mode is not an active member of the loop,
because its data table is not being updated.
Page 51

Chapter 4
Commands
Chapter Summary
This chapter told you about the 1771-KA2’s:
Station terminology
Commands, protected and unprotected, reads & writes
Processors’ input image table addresses, locations
In chapter 5 you will learn about rungs, codes, and more commands.
4-15
Page 52

Chapter 4
Commands
4-16
Page 53

Chapter
Communication Zone Rungs
5
General
At the beginning of the ladder-diagram program, you enter a special set of
rungs that dictate communication adapter module activity. The KA2 scans
this set of rungs at power-up for operating information.
WARNING: Do not make on-line edits of the communication
zone. Since the module scans the communication zone only
when it powers up or when the processor changes state (from
program to run), the changes will not affect module operation
until you cycle power to the 1771-KA2 module or change the
operating mode of the processor. Attempting such edits may
cause unexpected communication on the Data Highway.
Communication zone rungs use the standard controller instruction set.
However, the meaning of these instructions and addresses differs
significantly from their meaning in standard ladder-diagram
programming. For this reason, each programmed element in a
communication zone rung must be understood as it is described in this
chapter, not as it would normally be understood in a ladder- diagram logic
context.
In several instances, the 3- or 5-digit number entered above the
communication zone rung element has no relation to an actual data table
address. This chapter specifically identifies this type of number as either
a station number or code. Where one of these designations is given, the
actual data table bit or word at that address is not affected by KA2 module
operation and may be used in the balance of the user program.
For the purpose of this description, the reference point is termed the local
station. All other stations are then considered remote stations. These rungs
are entered at the local station so that it can send commands to, or receive
commands from a remote station.
Obviously, this reference point is not fixed. Each station - as it is being
programmed - is considered the local station at that time.
5-1
Page 54

Chapter 5
Communication Zone Rungs
Overall Format
The overall format for the communication zone of program is shown in
Figure 5.1. This figure shows each type of rung that can be entered in this
zone.
The actual communication zone rungs for any station processor may vary
significantly from those shown in Figure 5.1. The length of this program
area is a function of the number of remote stations processors with which
the local station processor communicates and the number of transmissions
of data with these remote stations.
Figure 5.1
Communication
Zone Format (general)
Command
Rungs
Header
Rung
Memory
Access
Rung
Read/
Write
Bit
Write
Delimiter
Rung
Start
011
077
1
[G]
020
[G]
017
[G]
03210 02000 016
03211 01702 12000
1
1
Header and delimiter rungs are required for each
station processor. Memory access and command rungs
are programmed as needed.
015
[G]
[G]
070
076
[G]
[G]
063
065
[G]
[G]
[][]
[G]
[][]
[][][]
12004 12005 12006
12010 12011 13511
017
022
[G]
[G]
010
060
[G]
[G]
022
024
[G]
[G]
12001 12002
[][][]
[][][]
022
[G]
062
[G]
12003
12007
12600
[]
[]
[]
02707
(
)
L
OFF
02707
(
02707
(
02707
(
02707
(
U
)
)
)
)
5-2
Page 55

Chapter 5
Communication Zone Rungs
The order of these communication zone rungs is as follows:
1. Header rung
2. Memory access rung(s) (as needed)
3. Command rung(s) (as needed)
4. Delimiter rung
These rungs must always appear in this order at the beginning of the
ladder diagram program. If you are using two KA2 modules, or a
combination of KA2 and -KG modules with the same processor, enter one
immediately after the other.
Header Rungs
As a minimum requirement, each station processor must have a header
rung and a delimiter rung. This provides the advantage of an ERROR
CODE storage word, controlled by the module as a diagnostic indicator.
If you are using two communication modules with the same processor,
(possible with 1771-KA2 and 1771-KG series B modules only) you must
program a separate and complete communication zone for each module.
Modules must have different station numbers.
The figures in this chapter show 3-digit addresses above most GET
instructions, but not the 3-digit data value displayed below the GET
symbol. This convention is used for clarity, since, for the most part, only
the 3-digit GET address is significant when entering a program. In
entering communication zone rungs, you needn’t program any data into
GET instructions.
A header rung, as shown in Figure 5.2, indicates the beginning of the
communication zone. For the communication adapter module (cat. no.
1771-KA2), the output position of this rung is always the LATCH 02707
instruction.
5-3
Page 56

Chapter 5
Communication Zone Rungs
Figure 5.2
Header
Rung
Local
Station
Number
Address of
Error Code
Storage Word
011
[G]
000
Timeout
Preset
Code
077
[G]
000 000
015
[G]
02707
(
OFF
)
L
The 3 GET instructions in the header rung list the following:
Local station number
Address of ERROR CODE storage word
Timeout preset code
The local station number is a 3-digit number switch-selected on the
1771-KA2 module. This is an octal number from 010
110
to 3768.
8
to 0778 or from
8
The ERROR CODE storage word is a status word in the data table of the
local station processor, controlled by the communication adapter.
(Section titled “Error Code Storage Word,” chapter 6, describes the
significance of the ERROR CODE storage word.)
Memory Access Rungs
5-4
The timeout preset code gives a programmed timeout interval for
command completion. Based on the 3-digit value entered in the address
field of this GET instruction, the communication adapter module monitors
command execution for all commands sent from a station. In the
examples in this publication, the number 015 is entered as the timeout
preset code. This value, which designates a 5-second timeout preset, is
suitable for most applications. The significance of this preset code, its
computation, and timeout considerations are described in section titled
“Timeout Preset Value,” chapter7.
The memory access rung defines data table words that you can access
with the following commands:
Protect write
Protect bit write
Protected commands, received from a remote station, may control only
those local station processor memory areas listed in memory access rungs.
Page 57

Chapter 5
Communication Zone Rungs
(Note that memory access rungs are not needed to allow unprotected
commands; only protected commands require a memory access rung.)
A memory access rung is composed of one or more memory access
branches, as shown in Figure 5.3.A. In this format, a BRANCH START
precedes a group of 3 GET instructions. The first GET instruction address
is the station number of a remote station. The next 2 GET addresses
define the word boundaries of the accessible data table area in the local
station processor. The specified remote station may control any bit or
word within three boundaries through protected commands.
Figure 5.3.B. illustrates the memory area that is now accessible to
protected commands from remote station 010, due to the memory access
branch of Figure 5.3.A.
Multiple memory access branches can be listed in a single memory access
rung. Each group of 3 GET instructions must be preceded by a BRANCH
START instruction. (This is true in all cases, even when only one
memory access branch is defined.) BRANCH END instructions can be
used to fit the memory access rung into the ladder diagram-display
format.
Use output instruction, OUTPUT ENERGIZE 02707, to fit the memory
access rung into the proper display format. (This output instruction has no
significance in memory access rung logic.)
5-5
Page 58

Chapter 5
Communication Zone Rungs
Figure 5.3
Memory
Access Example
Branch Start
Instruction
(Required)
Memory Access
Boundaries in
Local Station
Data Table
Remote
Station No.
010 020 023
a) Memory Access Branch b) Local Station Processor
Starting
Address
GGG
Ending
Address
Branch End
Instruction
(Required)
Area
Accessible to
Protected Commands
From Remote
Station No. 010
Data Table
Figure 5.4 shows a memory access rung with multiple branches. This
rung lists the remote station that may control specific data table words
with protected commands, as follows:
Words
020
023
5-6
Branch
Start
Instructions
Begin
Each
Branch
020
[G]
000
017
[G]
000
Station no. 020 can control words 070-076
Station no. 017 can control words 063-065 and word 022
Station no. 010 can control words 060-062
As shown in Figure 5.4, a single remote station processor may be
identified in more than one memory access rung branch.
Figure 5.4
Memory
070
076
[G]
[G]
000
000 000
063
065
[G]
[G]
000 000 000 000 000
Access Rung (typical)
017
022
022
[G]
[G]
[G]
000 000
010
060
[G]
[G]
[G]
062
Use Branch End
Instructions
as Needed
One Branch End
Instruction Must
Precede Output
Instruction
02707
(
)
Page 59

Chapter 5
Communication Zone Rungs
For practical reasons, do not exceed the display area of the programming
terminal when entering these rungs. You can program more than one
memory access rung if needed. Note, however, that should multiple
memory access rungs be required, you must enter them in succession in
the communication zone, immediately following the header rung and
before any command rung.
Command Rungs
The command rungs direct the data transfer operations of the
communication adapter module. The command rung lists the type of
command and the memory areas affected and allows command execution
to be initiated in the user program.
There are 2 basic command rung formats that differ only in terms of the
unit of memory which they control. The basic command rung formats
are:
Word command format
Bit command format
Use the word command format for commands that transfer one or more
data table words between stations. These are unprotected write, read, and
protected write commands.
Use the bit command format for commands that control, from one station,
one or more data table bits at another station processor. These are
unprotected bit write and protected bit write commands.
In both formats the command rung begins in a similar manner. (Refer to
Figure 5.5). The first rung element is an EXAMINE ON instruction,
addressing the START bit. The second rung element, termed the
command code, tells the remote station number, type, and priority of the
command. (Section titled “Message Priority,” chapter 8, describes
command priority.) For most commands, normal priority is preferred.
5-7
Page 60

Chapter 5
Communication Zone Rungs
Figure 5.5
Command
Rung Format
Start
Bit
Command
Code
AAAPX
[]
02707
(
REFER TO FIGURES
5.6 AND 5.7
AAA – REMOTE STATION NO.
P – PRIORITY INDICATOR
1 = PRIORITY MESSAGE
0 = NORMAL MESSAGE
X – COMMAND TYPE
0 = PROTECTED WRITE
1 = UNPROTECTED READ
2 = PROTECTED BIT WRITE
3 = UNPROTECTED WRITE
4 = UNPROTECTED BIT WRITE
)[]
After the command code, the command rung then lists the memory areas
affected by the command. The format of this area varies, based upon the
type of memory area controlled by the command.
5-8
The length of the communication zone in PLC-2 family PCs is limited by
the memory available inside the communication module. Very few
applications approach this limit, but if you program too many command
rungs, the value 26 will appear in the error code word when you place the
processor in RUN or RUN/PROGRAM mode.
Each command rung ends with an OUTPUT ENERGIZE 02707 element.
This instruction is used solely for the purpose of fitting the command rung
into the proper display format. The output instruction of the command
rung has no significance in program logic.
Examine START Bit
Each command rung has a unique START bit in a memory word selected
by the programmer. (Refer to section titled “START/DONE Word,”
chapter 6). The START bits are examined by the communication adapter
module. When a START bit is on, the communication adapter module
carries out the programmed command.
Page 61

Chapter 5
Communication Zone Rungs
The START bit is controlled by the program. This allows a command to
be initiated only when necessary. (Programming methods for START bit
control are given in chapter 7.)
Command Code
The second element in a command rung, the command code, identifies the
following:
Remote station number
Priority status of the command (priority or normal)
Type of command
NOTE: The command code uses the address of an EXAMINE ON
instruction, but does not examine or control any bit in the data table of the
local station processor.
Start
Bit
032
Legend
AAA
BBB
CCC
Figure 5.5 shows the coding for this rung element.
Word Command Format
When the command code specifies a protected write, read, or unprotected
write command, use the format shown in Figure 5.6.
Figure 5.6
Word
Command Format
Command
Code
020
10
Remote Station Processor
Data Table Address
Beginning word address of remote station processor for write/read operation
Beginning Word Address of local station processor for write/read operation
Ending Word Address at local station processor for write/read operation
00
AAA
G
Local Station Processor
Data Table Boundaries
BBB
G
CCC
G
027
07
5-9
Page 62

Chapter 5
Communication Zone Rungs
This format uses 3 GET statements. The address position of the first GET
statement lists a remote station data table word. The specified command
operation begins at this memory location. The second and third GET
statements define the starting and ending boundaries of the data table
words in the local station processor. These words are the beginning and
ending data table locations for the words to be transferred in the write or
read operation.
In write operations, data words are written to a remote station from the
local station data table. For a write command, the first GET element in the
command rung lists a beginning address at the remote station. Data is to
be written into this word, and succeeding words from the local station
data table. The second and third GET elements in this type of rung list
starting and ending boundaries for the word or words to be written from
the local station data table.
In a read operation, data words are read from a remote station processor
into the local station data table. The first GET element in the unprotected
read command rung lists the beginning address from which data is to be
read. Remote data table words are read in succession, beginning with this
address. Words are read only into the area of the local data table bounded
by the second and third GET elements in the rung.
Only one set of GET instructions, as shown in Figure 5.6, can be
programmed in a single command rung.
Bit Command Format
When the command code specifies a protected bit write or unprotected bit
write command, use the format shown in Figure 5.7.
5-10
Page 63

Figure 5.7
Bit
Command Format
Area May Contain Any Legal
Combination Of These Instructions:
Chapter 5
Communication Zone Rungs
Start
Bit
Command
Code
Branch Start
(If Needed)
HHH
FFFFF
HH
.
.
FFFFF
/
IIIII
/
Set bit EEEEE in remote station data table on
–] [–
Set bit FFFFF in remote station data table off
–] / [–
GGG
/
JJJ
/
GG
JJ
027
07
.
EEEEE
Legend:
EEEEE
This format uses EXAMINE elements that address bits in the remote
station processor. These elements control remote station data table bits as
follows:
-] [- EXAMINE ON - This rung element instructs the remote station
communication adapter module to turn the addressed bit on.
-]/[- EXAMINE OFF - This rung element instructs the remote station
communication adapter module to turn the addressed bit off.
Delimiter Rung
Program these elements immediately after the command code. Any
combination of these elements may make up this type of command rung.
Where necessary, BRANCH START instructions and a BRANCH END
instruction can be used to fit these elements into the display area of the
programming terminal. For practical reasons, do not exceed this display
area. Multiple rungs of this type can be used as necessary.
The delimiter rung ends the communication zone of program. With
PLC-2 family processors, this rung always has the format shown in
Figure 5.8.
5-11
Page 64

Chapter 5
Communication Zone Rungs
Figure 5.8
Delimiter
Rung
027
07
U
Chapter Summary
Chapter 5 was the RUNG chapter; it discussed:
Communication zone rungs
Communication zone of program
Header rungs
Memory access rungs
Command rungs
Start bit, command code and word command format
Bit command format with EXAMINE ON, EXAMINE OFF elements
In chapter 6 you will read about bit storage, fault words, and error codes.
5-12
Page 65

Status Words
Chapter
6
General
A 1771-KA2 communication adapter module controls certain data table
words specified in the local station processor by the programmer. These
data table words indicate the status of command execution and provide
various types of diagnostic information for start-up and troubleshooting.
These locations are:
One or more pairs of adjacent words for START/DONE and
REMOTE/LOCAL FAULT bit storage
An ERROR CODE storage word
Refer to Figure 6.1. The programmer specifies the locations of these
status words when entering the communication zone rungs, as described
in chapter 5. Two START/DONE and REMOTE/LOCAL FAULT bit
storage words are defined by selection of the START bit in a command
rung. You specify the ERROR CODE storage word in the header rung.
Figure 6.1
Adjacent
Status W
Start Bit
ord
0270703210
G
G G
Selection of Start Bit
Automatically Desig–
nates Bits in Two
Adjacent Words
Word 032
Word 033
Bits for Command Rung Shown
A.
Command Rung
Start Bits Done Bits
Program
Controlled
Remote Fault Bits Local Fault Bits
B.
Start/Done and Remote/Local Fault Words
Communication
Adapter Controlled
6-1
Page 66

Chapter 6
Status Words
Any accessible data table words can be used as status words in the station
processor. Note that the same recommendations for data table control
given in section titled “Accessible Data Table Locations - PLC-2
Processors,” chapter 4, should be followed when selecting status words.
That is, processor work areas, input image table words and word 027
should not be used as status words.
START/DONE Word
The START/DONE word is the first of a pair of adjacent status words for
communication adapter module use. This word stores a START bit and
corresponding DONE bit for each of up to 8 commands. (NOTE: should
more than 8 command rungs be programmed at a station, additional pairs
of START/DONE and REMOTE/LOCAL FAULT words can be used.)
The START bit for any command is always in the upper byte (bits 10-17)
of the START/DONE word. The DONE bit for this command is then the
corresponding bit in the lower byte (bits 00-07) of the same word.
In Figure 6.1.A the sample command rung examines bit 03210 as its
START bit. As Figure 6.1.B shows, the corresponding DONE bit is bit
03200. Note that the 5-digit address of START/DONE bits for each
command differs only in the fourth digit: the START bit always has a “1”
in the fourth digit, the DONE bit always has a “0.”
As its name implies, the START bit initiates command execution. This bit,
controlled by the user program, is set ON to initiate the sending of a
command. The communication adapter module monitors the status of
START bits and executes the corresponding command when its START
bit is set ON.
6-2
The DONE bit as its name implies, indicates command completion. This
bit, controlled by the KA2, is set ON when a command is executed.
Each command rung examines a unique START bit. Thus, one pair of
START/DONE and REMOTE/LOCAL FAULT words has enough bits for
up to 8 command rungs. Should more command rungs be programmed,
select additional word pairs as necessary.
To optimize memory use and minimize the time required by the
communication adapter module to scan START bits, use all 8 START bits
in one word pair before using another START/DONE word. For the same
reason, when programming communication zone rungs, group in
sequential fashion command rungs that use the same START/DONE
word.
Page 67

Chapter 6
Status Words
REMOTE/LOCAL FAULT Word
As Figure 6.1 shows, the selection of a START bit in the program not only
causes a corresponding DONE bit to be controlled in the same word, but
also causes REMOTE and LOCAL FAULT bits to be controlled in the
next data table word. A REMOTE FAULT and LOCAL FAULT bit are
controlled for each command. For a command, the position of each of
these FAULT bits within their respective bytes corresponds directly to the
position of START and DONE bits for that command.
The KA2 controls REMOTE and LOCAL FAULT bits. The module sets a
FAULT bit ON when a command cannot be executed due to a
hardware-related fault either between stations or between the remote
station communication adapter module and its station processor.
Figure 6.2 summarizes the significance of these bits.
Figure 6.2
REMOTE/LOCAL FAUL
Processor
PLC
2/20
AC FUSE
T Bit Significance
Local Fault
Possible Sources:
• Disconnected data highway cable
•
Power off at receiving station
interface module
•
Unused remote staiton no. address
•
Station interface moduel at local
or remote station has disconnected
itself as a result of link monitoring
•
Automatic timeout at sending
station
Sending
Station
Remote Fault
Possible Sources:
•
Remote station processor
in program load (or prog)
mode
•
Command not executed due to
module switch setting at
receiving station
•
Fault at remote station processor
•
Power off at remote station processor
Disconnected data highway/processor cable
•
Error detected in communication zone of
•
program at remote station proccessor
Processor
PLC
2/20
AC FUSE
Receiving (Remote) Station
10866-I
6-3
Page 68

Chapter 6
Status Words
REMOTE FAULT bits are in the upper byte of this word. A REMOTE
FAULT bit is set ON when a command is received at a remote station but
cannot be executed by the remote station. This may mean one of the
following:
Remote station processor has detected a fault in its own operation or
has shut down.
Remote station processor has power OFF.
Remote station processor has mode select switch in PROGRAM LOAD
(or PROG) mode.
Cable between remote station adapter and processor is disconnected or
faulty.
Module switch setting prevents execution of the received command.
Error has been detected in communication zone of program at remote
station processor (PROG indicator may be ON).
A REMOTE FAULT bit indicates that the remote station communication
adapter or controller module received a message, but could not
communicate with its station processor to execute that command.
LOCAL FAULT bits are in the lower byte of this word, bits 00-07. A
LOCAL FAULT bit is set when the local station cannot confirm delivery
of the message to the remote station. This may mean one of the
following:
Automatic timeout of command completion by communication adapter
module.
Disconnection of the local or remote station interface module from the
Data Highway cable
Loss of power to the remote station communication adapter module
Unused station number addressed by the command.
Excessive noise along the Data Highway cable caused by other
equipment in the industrial environment.
At the same time it sets a REMOTE or LOCAL FAULT bit ON, the KA2
enters a 2-digit ERROR CODE into the ERROR CODE storage word.
(The ERROR CODE storage word is described in the following section.)
6-4
By monitoring these bits in the program, operators can be alerted to
hardware conditions that prevent normal transmission and execution of
commands. (Programming techniques for monitoring FAULT bits are
described in chapter 7.)
Page 69

Chapter 6
Status Words
Error Code Storage Word
When a command cannot be carried out due to a user programming error
or a discrepancy in data handled by the communication adapter module,
an ERROR CODE may be written into a data table memory word. The
programmer selects the error code storage word and lists it in the header
rung of the communication zone of program. This word stores the most
recent error code written by the KA2.
Figure 6.3 shows the structure of the ERROR CODE storage word. The
lower byte of this word (bits 00-07) stores any ERROR CODE entered by
the module. In this byte the ERROR CODE is represented as a 2-digit
binary coded decimal (BCD) number from 00-99. Table A.1 (Appendix
A) lists and describes these ERROR CODES.
Figure 6.3
ERROR
CODE Word Format
2–Digit Value:
Reference Number
(for codes 01–26)
Counter (for codes 30–99)
Error Codes 00–99
in BCD Format
(Refer to Table 6–A)
17 16 15 14 13 12 11 10 07 06 05 04 03 02 01 00
0–9 0–9 0–9 0–9
ERROR CODES can be grouped as follows:
Codes 01-29 generally indicate that some programming error has been
detected in the communication zone of program. These codes are
intended to indicate errors or processor communication faults detected
at power-up. The program status indicator (PROG) may be on if one of
these codes is displayed.
Codes 30-99 generally indicate that some programming or hardware
related fault has been detected during attempts at communication
between stations. Codes 30-99 serve as diagnostic indicators after the
initial power-up checks of program have been completed.
A code in this 30-99 group is displayed whenever a REMOTE or LOCAL
FAULT bit is set ON.
6-5
Page 70

Chapter 6
Status Words
The upper byte of the ERROR CODE storage word (bits 10-17) stores a
2-digit BCD value. This value gives supplemental error or fault
information, depending on the type of ERROR CODE displayed. It may
have one of two meanings:
Reference number
Counter
For ERROR CODES 01-29, the upper byte stores a 2-digit reference
number. This number points to the location of a programming error
within the communication zone of program. This error may be an
incorrect instruction or an improper address entered within a rung of the
communication zone. In this numbering scheme, the header rung of the
communication zone of program is designated as “00.” Subsequent
communication zone rungs are numbered sequentially.
Note that ERROR CODES 01-29 are intended as aids in start-up
debugging of the communication zone of program. Thus, the reference
number stored in this word can be a valuable tool for debugging purposes.
For ERROR CODES 30-99, the upper byte stores a 2-digit counter. This
counter shows the number of ERROR CODES 30-99 written into the
storage word by the communication adapter module. The counter
increments each time a different ERROR CODE storage word.
These codes are generally to be displayed on a programming terminal
rather than used in application programming. They have special value in
station start-up, when programming errors are detected in the
communication zone of program.
By viewing the header rung of the communication zone, the programmer
can examine a displayed ERROR CODE and the least significant digit of
the counter in this word. (Section titled “Header Rung,” chapter 5,
describes a header rung.)
In some instances, however, it may be preferable to display the 2-digit
error code using a 7-segment BCD numerical display controlled from
output modules of the controller. This 7-segment display, mounted at an
operator’s station, can provide a useful troubleshooting aid for quickly
locating fault conditions.
6-6
Page 71

Chapter 6
Status Words
Chapter Summary
This was the WORD and CODE chapter and it discussed:
START/DONE, REMOTE/LOCAL FAULT bit storage
REMOTE/LOCAL fault word
Error code storage word (Error code list is in Appendix A.)
Chapter 7 continues discussion about command initiation, control bits,
fault words, and monitoring.
6-7
Page 72

Chapter 6
Status Words
6-8
Page 73

Chapter
7
Command Initiation, Execution, and Monitoring
General
START/DONE Bit Timing
This chapter describes the support programming for commands at each
station processor. This programming uses the START/DONE and
REMOTE/LOCAL FAULT bits, described in chapter 6, to initiate and
monitor command execution. Using these recommended techniques, the
programmer coordinates communication zone programming with his
application program.
The START bit that initiates a command is program-controlled; the
DONE bit, which indicates command completion, is communication
adapter module-controlled. The timing relationship of START and DONE
bits is used by the programmer to initiate and terminate commands. The
following sections describe this relationship in normal operation and
describe the automatic responses that result from faulted operation.
Normal Operation
Command execution begins when the user program turns a START bit
ON, normally with a LATCH instruction. The 1771-KA2 communication
adapter module detects the ON state of this bit and then begins the
operations necessary to format and transmit a command message.
When the remote station communication adapter module receives the
command message, it acknowledges it. Then, while normal Data Highway
operation continues, the remote station communication adapter module
executes the command and prepares a reply message. (A reply message is
sent for each type of command.) The remote station communication
adapter module responds to a poll for mastership, then transmits its reply
message to the local (sending) station. (Refer to chapter 8 for a
description of mastership and polling.)
When the local station communication adapter module receives the reply,
it sets the done bit on at the local station processor. The DONE bit, in
turn, is examined in the user program to turn OFF the START bit.
After the START bit has been turned OFF (unlatched), the communication
adapter module resets the DONE bit.
7-1
Page 74

Chapter 7
Command Initiation, Execution, and
Monitoring
ABCD
Figure 7.1 shows the timing of START and DONE bits for a command.
The significance of START/DONE bit status is summarized in Table 7.A.
Figure 7.1
START/DONE
Bit T
iming - Normal Operation
Start
Bit
Done
Bit
On
Off
On
Off
Command/
Response
Time
Legend:
A
Start bit turned on by the program
Done bit set on by the 1771–KA2
B
communication adapter module to
indicate that a command has been completed.
C
Start bit turned off by the program
Done bit set off by the 1771–KA2
D
communication adapter module after
it senses that the start bit has been set off.
T
able 7.A
ST
ART/DONE Bit Status
Processor
Scan
Communication
Adapter Scan
7-2
Status Significance
Start
Bit
Done
Bit
0 0 Idle
1 0
1 1
0 1
Command initiated or in progress
Command/reply operation complete
The processor
, based on the program,
acknowledges completion of the
command/reply operation (transient condition,
since the communication adapter turns the
DONE bit OFF in its next scan.)
Page 75

Chapter 7
ÉÉÉÉ
ÉÉÉÉ
Command Initiation, Execution, and
Monitoring
Faulty Operation
Certain fault conditions can prevent normal reception and execution of
commands by the receiving station. To indicate the source of such fault
conditions, the KA2 controls REMOTE and LOCAL FAULT bits at the
station processor.
In general, the LOCAL FAULT bit indicates that the local station cannot
confirm delivery of a command to the remote station. The REMOTE
FAULT bit, on the other hand, indicates that the intended receiving station
communication adapter module has received the command message, but
is unable to execute the command at its station processor. (For a quick
summary of the distinction between these FAULT types, refer to Figure
6.3.)
Start
Bit
Remote or
Local Fault
Bit
Done
Bit
On
Off
On
Off
On
Off
The timing relationship of these FAULT bits in command execution is
shown in Figure 7.2. In this example, the command initiated at the setting
of the START bit executed due to some fault condition. The
communication adapter module, detecting this fault condition, sets either
a LOCAL or REMOTE FAULT bit.
Figure 7.2
START/FAULT
ABC
Bit T
Command/
Response
Time
iming - Faulted Operation
D
Communication
Adapter Scan
Legend: Start bit turned on by the program
A
Remote fault or local bit set on
B
by the communication adapter module to
indicate that a fault condition has been detected.
C
Start bit turned off by program
Fault bit turned off by the communication
D
adapter module after it senses that start
bit has been turned off.
7-3
Page 76

Chapter 7
Command Initiation, Execution, and
Monitoring
Recall that the START bit is program-controlled. The REMOTE/LOCAL
FAULT bits, meanwhile, are controlled by the 1771-KA2 module. The
programmer must keep this relationship in mind when planning START
bit control and FAULT bit monitoring in the ladder-diagram program.
Note from Figure 7.2 that the FAULT bit, once ON, remains ON until the
START bit is reset (turned OFF). Only after it has detected that the
program-controlled START bit is OFF does the communication adapter
module then turn the FAULT bit OFF. Note also that the DONE bit is not
set ON in the event of a fault condition.
NOTE: In the special case where the START bit is turned OFF by the
program before the KA2 sets a DONE or FAULT bit, attempts to send that
command are terminated. The LOCAL FAULT bit is pulsed ON for
approximately 60 msec in this instance. This type of situation may occur,
for example, if some event is programmed to UNLATCH the START bit
before command completion.
Controlling The Start Bit
The user program controls the START bit: setting it ON to initiate
command execution, turning it OFF after command completion or after a
fault is detected. Normally, the START bit is turned ON by a LATCH
instruction, OFF by an UNLATCH instruction. The use of retentive
LATCH/UNLATCH instructions is best suited for the timing relationship
of START, DONE, and FAULT bits and helps to keep programming
simple and straightforward.
To LATCH the START bit, the program examines application conditions.
These may include input/output device data, values, or other information
from the controlled process. For the most part, an application condition
used to initiate a command is one of these general types:
The ON or OFF status of some I/O device
Transition of some I/O device
Timed condition
To UNLATCH the START bit, the program examines the response from
the communication adapter module. This response may be one of the
following:
DONE bit
REMOTE FAULT bit
LOCAL FAULT bit
7-4
Page 77

Chapter 7
Command Initiation, Execution, and
Monitoring
Thus, the rung used to UNLATCH the START bit examines these three
possible responses in parallel branches of the ladder diagram program.
Section titled “ON/OFF Input Status,” “Transition,” and “Timed” describe
the most commonly used forms of START bit control. Each section
describes a different method for initiating command execution; all
examples show how the program uses both DONE and FAULT bits to
UNLATCH the START bit.
An important assumption underlies the examples outlined in sections
titled “ON/OFF Input Status,” “Transition,” and “Timed” and shown in
Figures 7.3 through 7.5. Here, the program automatically re-tries
transmission of a command in the event of a fault. Only the DONE bit
terminates attempts at command execution; a LOCAL or REMOTE
FAULT bit response causes the program to re-initiate command execution.
(This type of programmed re-try is not to be confused with the re-try
procedure of the 1771-KA2 module itself; transparent to user
programming, the module automatically attempts several re-tries of a
message before it sets a FAULT bit. Section titled “Floating Master,” in
chapter 8, describes these automatic re-tries of the module.)
Programmed re-try has distinct advantages. As the communication
adapter module continuously tries to send the command message, any
data content of the message (for a write command) is continuously
updated. As soon as the fault condition is corrected, the message is sent,
with the latest data. In addition, once the command is completed, the
program automatically UNLATCHES the START bit. This eliminates the
need for a manual reset of the START bit when a fault condition is
corrected.
ON/OFF Input Status
The ON or OFF status of an input device can be used to LATCH the
START bit. Figure 7.3 shows rungs for this type of command initiation.
7-5
Page 78

Chapter 7
Command Initiation, Execution, and
Monitoring
Figure 7.3
Status-Initiated
Command
11111
03202
Local
Fault
03302
Remote
Fault
03312
Remote
Fault
03312/03302
InputDone
11111
Local
FaultInput
/
/
Start
032
L
Start
032
U
12
12
In this example, the first rung is programmed to LATCH the START bit
when the input, bit 11111, is ON, provided that both FAULT bits are OFF.
The second rung is programmed to UNLATCH the START bit based on
the response of the communication adapter module.
7-6
In normal operation, the START bit is LATCHED by the input 11111; the
FAULT bits, initially, are OFF. This causes the command message to be
formatted and sent. Then, when the command is completed, the DONE
bit is set ON by the communication adapter module. Note that the input
bit, 11111, must also be OFF to UNLATCH the START bit in this
example. With this arrangement, the command message is sent only once;
input 11111 must be turned OFF, then ON again, to execute this command
a second time. In normal operation, the START bit, after successful
command completion, remains ON until input 11111 goes OFF. (Recall
from Figure 7.1 that the communication adapter module holds the DONE
bit ON until after the START bit is turned OFF.)
Should a fault condition prevent normal execution, these rungs provide a
programmed re-try of the command. A REMOTE or LOCAL FAULT bit
resets the START bit in the second rung. In the first rung, the START bit
is LATCHED again after the communication adapter module resets the
FAULT bit. (As Figure 7.2 shows, the 1771-KA2 module resets a FAULT
bit only after the START bit has been turned OFF.)
Page 79

Chapter 7
Command Initiation, Execution, and
Monitoring
Even though the FAULT bits are continually reset with this method, their
usefulness must not be overlooked. The section titled “REMOTE/FAULT
Bit Monitoring” outlines a useful method to monitor FAULT bits and
control an output indicator based on FAULT bit status.
In some applications, it may be useful to send a command continuously
between stations. With the example of Figure 7.3, this can be
accomplished by eliminating the EXAMINE OFF instruction for input
11111 in the second rung. This would cause the command to be sent
continuously as long as input 11111 remains ON.
Transition
The transition of an input device from ON to OFF and from OFF to ON
can be used to LATCH the START bit. This allows a command to be sent
each time a condition changes state. Figure 7.4 shows example rungs for
this type of command initiation.
7-7
Page 80

Chapter 7
Command Initiation, Execution, and
Monitoring
Figure 7.4
Transition-Initiated
Command
Rung 1
Rung 2
Rung 3
Rung 4
CompareInput
/
01111
/
Compare
01111
Remote
Fault
Local
Fault
11111
Input
11111
Input
11111
Transi–
tion
02000 03312/03302
Done
03202
Transition
02000
L
OFF
Compare
01111
Start
03212
/
L
OFF
Start
03212
U
7-8
Rung 5
Local Fault
03302
Remote Fault
03312
Done
03202
Transition
02000
U
Page 81

Chapter 7
Command Initiation, Execution, and
Monitoring
In this example, a storage bit, called the “transition” bit, is manipulated to
control the sending of the command. This bit is LATCHED whenever a
transition of input 11111 is detected, UNLATCHED only when the DONE
bit is set ON. A “compare” bit, 01111 in this example, is used to
manipulate the transition bit. In rung 2, the compare bit is controlled to
match the ON/OFF status of the input. Because the input and the compare
bit are programmed to have matching states, both ON or both OFF, the
conditions of RUNG 1 can be TRUE only when the input has just
changed from ON to OFF or from OFF to ON. Thus rung 1 conditions set
up a “one-shot,” TRUE only long enough to LATCH the transition bit.
Note that these rung conditions are FALSE as soon as the processor scans
rung 2. The order of these rungs is important for this reason.
With the transition bit LATCHED, the START bit, in turn, is LATCHED
in rung 3. This initiates the command. In normal operation, the DONE bit
UNLATCHES the START bit in rung 4 and then UNLATCHES the
transition bit in rung 5. In faulted operation, however, rungs 3 and 4
repeatedly re-try the command in much the same manner as in the
example of Figure 7.3.
Timed
The START bit may be LATCHED periodically to send a command at a
user-determined time interval. Figure 7.5 shows example rungs for this
type of command initiation.
7-9
Page 82

Chapter 7
Command Initiation, Execution, and
Monitoring
Figure 7.5
Timer-Initiated
Command
Done
02
032
/
Timed Bit
15
046
Done
02
032
Local Fault
033
02
Remote Fault
033
12
046
TON
1.0
PR 010
AC 000
Start
032
L
Start
032
U
12
12
REMOTE/LOCAL FAULT Bit
Monitoring
7-10
In this example, timed bit 04615 is used to initiate the command at every
preset interval, 10 seconds. This bit is examined to LATCH the START
bit. The DONE, LOCAL FAULT, and REMOTE FAULT bit are
examined in parallel branches to UNLATCH the START bit.
In normal operation, after the command is executed, the DONE bit is set
ON by the communication adapter module. This causes the program to
UNLATCH the START bit. The timer then begins timing again once the
DONE bit is set OFF. (As Figure 7.1 shows, the DONE bit is reset only
after the START bit is reset.)
Note that this programming causes continuous re-try of a command in the
event of faulted operation.
When it cannot execute a command, the Communication adapter module
sets a REMOTE or LOCAL FAULT bit ON. These bits, in the data table
of the station processor, are located in the word immediately following the
START/DONE bit word. They indicate not only that a command was not
Page 83

Chapter 7
Command Initiation, Execution, and
Monitoring
executed, but also point to the general type of fault condition that
prevented command completion.
The user program must monitor the REMOTE and LOCAL FAULT bits
for each command. The recommendations of this section describe two
methods for monitoring FAULT bits and using these bits to signal a fault
condition.
Diagnostic FAULT Rungs
The purpose of monitoring REMOTE/LOCAL FAULT bits is to control
one or more output indicators to signal a fault condition. Fault indicators
controlled for this purpose may be as simple as a warning light or an
annunciator, or as complex as a line printer or CRT terminal used to
display a fault message. By controlling the fault indicator device, the user
program can alert user personnel to the nature and location of a fault
condition.
To monitor the REMOTE and LOCAL FAULT bits, a programmer must
understand their timing relationship to the corresponding START bit.
Figure 7.2 summarizes this relationship.
The section titled “Controlling the Start Bit” showed how the FAULT bit
can be programmed to UNLATCH the START bit in a fault situation and
thus provide automatic re-tries through the program. When used in this
manner, however, a FAULT bit will be rapidly cycled ON and OFF if a
fault is detected. Because the fault bit can be constantly changing state at
a rapid rate, the program must use some method of detecting this transient
state of any FAULT bit and of controlling the output device based on this
state.
Figure 7.6 shows a simple method for the control of a fault indicator.
Here, either the REMOTE or LOCAL FAULT bit can LATCH the output
indicator ON. The indicator remains ON until the DONE bit is energized.
This then UNLATCHES the output indicator in the second rung of
Figure 7.6. This example allows for the transience of the FAULT bits,
since the first rung need only be TRUE once for the output indicator to be
latched.
7-11
Page 84

Chapter 7
Command Initiation, Execution, and
Monitoring
Figure 7.6
FAULT
Bit Diagnostic Rungs (Single Command Example)
Remote Fault
10
033
Local Fault
033
00
Done
03200
Output
Indicator
01000
L
OFF
Output
Indicator
00
010
U
The method of Figure 7.6 can be extended to monitor multiple commands
from a station, controlling multiple output indicators as necessary.
However, where more than one command is being sent from a station, the
use of multiple output indicators may not be practical. In this instance, a
single output indicator can be used to signal all REMOTE or LOCAL
FAULT conditions for commands from that station. Figure 7.7 shows a
method for fault indicator control assuming multiple commands.
7-12
Page 85

Figure 7.7
FAULT
Bit Diagnostic Rungs (Multiple Commands Example)
Chapter 7
Command Initiation, Execution, and
Monitoring
Rung 1
07
033
Rung 2
033
Rung 3
Local Fault
Remote Fault Status
Rung 4
Timed Bit
/
17
/
Status
055
/
055
/
030
033
033
00
01
15
Local Fault
Status
055
06
/
16
/
033
033
05
033 04/033 03/033 02/033 01/033 00
/
15
033 14/033 13/033 12/03311/033 10
/
/
/
00
Remote Fault
Status
055
01
030
TOF
0.1
PR 020
AC 000
Output
Indicator
00
010
This example shows the FAULT bit monitoring for 8 commands. The 8
LOCAL FAULT bits are monitored in rung 1. As long as all 8 bits are
OFF, status bit 05500 remains ON. However, should any LOCAL FAULT
bit be ON, status bit 05500 is de-energized. In rung 2, the 8 REMOTE
FAULT bits are monitored in the same manner, to control status bit 05501.
The status bits controlled by rungs 1 and 2 are, in turn, used to control an
OFF-DELAY timer in rung 3. The OFF-DELAY timer begins to time
when either of the status bits goes from OFF to ON, that is, when rung
conditions go from TRUE to FALSE. Bit 03015, the timed bit of the
timer, controls the output indicator. As soon as the conditions of the timer
in rung 3 are TRUE, this bit is set ON causing the indicator to be
energized. Once ON, this bit remains on as long as the timer is timing,
that is, for at least as long as the preset interval. In the example of
Figure 7.7, this preset is set at 2 seconds. This value is not critical but
should exceed 0.5 seconds for practical purposes.
7-13
Page 86

Chapter 7
Command Initiation, Execution, and
Monitoring
The OFF-DELAY timer is useful in this application because it is
continually reset when its rung conditions go TRUE. This means that the
timed bit, 03015, remains on for as long as any FAULT bit is changing
state during programmed re-tries. This keeps the output indicator on until
after the DONE bit indicates command completion.
NOTE: Using the rungs of Figure 7.7, the indicator goes ON
automatically at power-up, or whenever the mode select switch on the
processor is changed from the PROGRAM LOAD (or PROG) mode to
any other mode. However, the indicator only remains on initially for the
preset interval; after this time, the indicator is valid for fault conditions.
Rungs 1 and 2 examine all 8 FAULT bits of each type. Should fewer than
8 command rungs be programmed at a station processor, fewer bits need
be examined. Then, should command rungs be added subsequently, the
appropriate bits could be addressed in rungs 1 and 2. Conversely, if more
than 8 command rungs were programmed at a station, additional rungs
would be needed to examine both REMOTE and LOCAL FAULT bits for
the additional commands. Status bits controlled by these additional rungs
could then be examined in branches of rung 3, parallel to those shown.
Timeout Preset Value
Of course, other methods can be used to monitor REMOTE and LOCAL
FAULT bits. Such factors as availability of output terminals, memory
space, and type of application dictate the specifics of FAULT bit
monitoring and program response.
Use of FAULT bits in start-up and troubleshooting procedures is described
in chapter 9.
In addition to its REMOTE/LOCAL FAULT bit control, a 1771-KA2
module also provides an automatic timer for monitoring command
completion. While it functions automatically during module operation,
the timer uses a preset value entered in the user program. This feature
enables the module to monitor command execution time without using
timer (TON) instructions in the user program.
Figure 7.8 shows the significance of the timeout preset interval. From the
time the START bit is set ON, the module must set either a DONE bit or a
REMOTE or LOCAL FAULT bit within the timeout preset interval.
Should the module detect no DONE or FAULT bit response within the
preset interval, some type of fault is assumed. As a response to this type
of timeout situation, the module sets the LOCAL FAULT bit ON and
7-14
Page 87

Chapter 7
Command Initiation, Execution, and
Monitoring
enters the value 37 in the lower byte of the ERROR CODE storage word
of the header rung.
Figure 7.8
Timeout
Preset Significance
Header Rung
(Representation)
G G G (L)
Code ”37” Entered
if
Timeout Occurs
Start
Bit
Done
Bit
Remote
Fault
Bit
On
Off
On
Off
On
Off
Code
QQQ
X37
Timeout Preset Interval,
Within this Period
Done or Fault Bit Expected
Local
Fault
Bit
On
Off
Local Fault
Bit Set if
Timeout Occurs
Time
7-15
Page 88

Chapter 7
Command Initiation, Execution, and
Monitoring
Timeout preset monitoring is intended as a backup for the other
communication monitoring functions of the module. It is designed to
signal any condition where the module has not completed its
communication with another station or detected some fault condition
within a short time. Because this timer is primarily intended as a backup
for some LOCAL FAULT type of situation, its preset value is not critical.
In the examples in this manual, a nominal value of 5 seconds, coded 015,
is programmed as the timeout preset value. This value is appropriate for
most applications.
Programming the Preset Code
The timeout preset code for Data Highway communication is entered in
the header rung of the communication zone of program. The address field
of the third GET instructions in this rung is used for the timeout preset
code. Figure 7.8 shows the position of this rung element.
The 3-digit address of a GET instruction is an octal (base 8) number.
Because only octal values can be entered in this address field the timeout
preset value is a code, computed as outlined in this section.
As section titled “Timeout Preset Value” points out, the timeout preset is
not a critical value. For most applications, a 5-second present is
acceptable. The code for this timeout preset is 015. However, there may
be instance where another timeout preset interval is desired. Table 7.B
lists the 3-digit codes for intervals from 1 to 10 seconds. Note that values
listed provide nominal values that will vary with activity level in the KA2.
T
able 7.B
Timeout
Preset Codes
T
imeout Interval
(Sec,) Code
1 011
2 012
3 013
4 014
5 015
6 016
7 017
8 020
9 021
10 022
7-16
Page 89

Chapter 7
Command Initiation, Execution, and
Monitoring
If it is necessary to use a value other than those provided in Table 7.B,
compute the 3-digit timeout preset code as follows:
1. Select a timeout preset interval. This interval must be at least one
second.
For the purpose of computing the code, label this number “S.”
EXAMPLE: desired interval = 7 seconds = S
2. Compute a decimal (base 10) number using the desired interval of
step 1 in the following formula:
S + 8
EXAMPLE: S + 8 = 15
3. Convert this value to a 3-digit octal (base 8) value.
EXAMPLE: 15
10
= 17
8
For a brief description of decimal-to octal conversion, refer to chapter 13
of publication 1772-821, Programming and Operations Manual,
Mini-PLC-2 Programmable Controller. You can disable the timeout by
using the value 010.
User-Programmed Timeout (Optional)
The automatic timeout of a 1771-KA2 communication adapter module
has a backup function. This automatic monitoring routine continuously
checks module interaction with other Data Highway stations, timing the
execution of commands. This automatic timeout does not check module
communication with its own station processor. For a backup check on
module/processor communication, an optional programmed ON-DELAY
timer instruction (TON) can be used.
With proper module/processor communication, the module sets either a
DONE bit or a REMOTE or LOCAL FAULT bit as a response to a
command. However, in the event of faulted module/processor
communication or faulted module operation, a response bit might not be
set. Instead, the START bit would remain on in this instance until the
fault situation was corrected. Several programming methods can be used
7-17
Page 90

Chapter 7
Command Initiation, Execution, and
Monitoring
to detect such a condition; the simplest of these methods uses an
ON-DELAY timer. Figure 7.9 shows typical rungs that can be
programmed for this purpose.
Figure 7.9
Typical
User-Programmed T
imeout
12
Done
032 02
/
Remote Fault
12
033
/
Local Fault
02
033
/
060
TON
0.1
PR 100
AC 000
Output
Indicator
01002
Start
032
Timed Bit
060 15
In the first rung of this figure, timer 060 times the interval between the
setting of the START bit for a command and the DONE, LOCAL FAULT,
or REMOTE FAULT response of the module. If no response is received
within the preset interval of this timer, here 10 seconds, a fault may be
indicated and bit 06015 set ON. The second rung examines this bit to turn
on a warning indicator. Depending on the individual application, this bit
could also be used to enable or disable various parts of the program.
7-18
The preset value of this programmed TON instruction is not critical. For
this type of backup monitoring, the programmed preset must exceed the
timeout preset interval entered as a code in the header rung. (Remember
that the automatic timeout of the module gives a LOCAL FAULT
response to a command, which would indicate normal module/processor
communication, but faulted communication with some other station.)
As with automatic timeout preset monitoring, a user-programmed timeout
is useful as a backup to the other monitoring functions of the
Page 91

Chapter 7
Command Initiation, Execution, and
Monitoring
communication adapter module. (REMOTE and LOCAL FAULT bits at
other stations indicate the same types of faults that can be detected using a
user-programmed timeout.) A programmed timeout would not be
necessary for each command from a station. Instead, a single command at
each station can be monitored in this manner. Select a command that is
sent regularly for this type of monitoring.
There may be other instances where program monitoring of commands is
useful. In some cases, a user-programmed timeout may be used to
monitor the execution time of critical commands. An application may
require that a critical message, such as a priority command, be sent within
a certain limited amount of time. A programmed TON instruction can be
used for this purpose; here, however, its preset interval will generally be
shorter than the interval entered as the timeout preset for the module.
Chapter Summary
This chapter dovetailed with chapter 6. It discussed command initiation,
execution, and monitoring and their association with:
START/DONE bit timing
Normal operation
START/DONE bit status
Faulty operation
Control of START bit
ON/OFF input status
Transition of an input device from ON to OFF and OFF to ON
Timed start bits
Diagnostic FAULT rungs
Timeout preset values
Programming a preset code
Optional user-programmed timeouts
Chapter 8 discusses interfacing a KA2 with other modules on a Data
Highway, mastership of the highway and Data Highway computer
commands.
7-19
Page 92

Chapter 7
Command Initiation, Execution, and
Monitoring
7-20
Page 93

Station Interfacing
Chapter
8
General
To execute commands, a 1771-KA2 communication adapter module at
one station interacts with all other stations interface modules on the Data
Highway. This chapter describes this interaction of station interface
modules.
Because much of this interaction is transparent to user programming, the
information given here is largely for background. However, an
understanding of station interaction is useful in optimizing use of each
individual communication adapter module and of the Data Highway as a
whole. Specifically, the information aids in an understanding of the
following:
Floating master operation and polling
Message types
Sequence of messages for command execution
Acknowledgements
Re-tries of transmitted messages
Priority command designation
Automatic disconnection of faulted master
Commands that can be sent by computer
Floating Master
Central to the interaction of station interface modules is the concept of
shared mastership--the floating master. With this arrangement, no single
station controls the Data Highway communication link at all times.
Instead, each station vies for mastership based on its need to send
messages.
The advantage of this arrangement is that Data Highway operation can
continue even if one or more stations are unable to maintain
communication. Thus, disconnection of a station or a fault at a station
processor or communication adapter module does not disable
communication between other operating stations. This minimizes the
need for redundancy in many applications.
8-1
Page 94

Chapter 8
Station Interfacing
Mastership
A Data Highway cable links as many as 64 stations. Because this cable
has a single pair of wires, only one station can transmit at a time. When a
station interface module gains control of this data link to transmit
messages, that station has mastership.
When one station interface module is master, all other station interface
modules assume a “slave” or receive mode. This enables these stations to
receive and acknowledge messages sent to them. The relationship
between the master station interface module and all other stations is
shown in Figure 8.1.
Figure 8.1
Master
Station Functions
Master
Station
All
Other
Stations
1. Send Command/Reply Messages
Acknowledgment
2. Send Polling Message Sequence
Signal if Ready
12360
8-2
As master, a communication adapter module can send the following types
of messages:
Command
Reply
Polling
Page 95

Chapter 8
Station Interfacing
The function of both command and reply messages is the transfer of data
between stations. As soon as the communication module attains
mastership, it sends its command and reply messages (up to a maximum
number--16 for the 1771-KA2).
After the module sends its command and reply messages, it transmits a
sequence of polling messages. By this sequence, it selects the next station
to be master of the Data Highway communication link.
Command Messages
A command message from the master communication adapter module
instructs another station interface module to execute a command. In
general, a command from a communication adapter module can do one of
the following:
Write data table data to another station
Write bit status to another station
Request data table data from another station through a read command
The command rung, entered in the communication zone of user program,
instructs the communication adapter module to format a command
message. Once this message is sent, execution of the command begins.
(Command types, execution, and programming are described in chapters 4
through 7.)
Each command message causes a reply message to be generated by the
receiving station.
Reply Messages
Reply messages are generated by a station in response to command
messages that it receives. The reply message indicates whether the
command message was received and whether the station interface module
has completed the sequence of events required of it for command
execution. For commands that write data, the reply message indicates
whether the write operation has been completed at the receiving station.
For commands that read data the reply message contains the data
specified by the command. If the command was not executed
successfully, the reply message contains an indication of the error in the
STS byte.
8-3
Page 96

Chapter 8
Station Interfacing
The reply message is an automatic function of communication adapter
module operation, transparent to the user program. To send a reply
message, a station must have mastership.
Acknowledgement
When a station receives a message addressed to it, whether it is a
command or reply message, the receiving station sends an
acknowledgement. The acknowledgement is merely a signal that confirms
that a message has been received. Transparent to the user program, the
acknowledgement is an automatic function of communication adapter
module operation.
The acknowledgement serves 2 basic functions: it indicates that the
receiving station is operating and has received the message, and it
indicates that the received command or reply message is in intelligible
format. Should the proper acknowledgment not be received, a fault in the
receiving module may be indicated. In this event, the master station
communication adapter module re-tries transmission of the message. The
communication adapter module attempts several re-tries for a command
or reply message. Re-tries are automatic, transparent to the user program.
If re-tries are unsuccessful, a LOCAL FAULT bit may be set ON at the
local (sending) station processor. (LOCAL FAULT bits are described in
chapter 6.)
Acknowledgements are sent only by a station that is in the receive mode,
not the current master station.
Message Priority
Each message transmitted over the Data Highway communication link has
one of these priority levels: normal and priority.
These priority levels determine the order in which stations obtain
mastership and the order in which messages are transmitted. Priority
messages of a given type (either command, reply, or polling) will always
be transmitted before normal messages of the same type.
The programmer designates a priority level for each command message.
The command code, an element in each command rung, specifies the
priority level of the command message. The station that receives a
command message automatically establishes the same priority level for its
8-4
Page 97

Chapter 8
Station Interfacing
corresponding reply message. (The command code is described in
chapter 5.)
Priority commands are executed ahead of normal commands throughout
the command/reply message cycle. For this reason, a command should be
given priority designation only when special handling of specific data is
required. Using an excessive number of priority commands defeats the
purpose of this feature and could delay or inhibit the transmission of
normal messages.
When a station communication adapter module has a priority command or
reply message ready for transmission, the module responds to the next
priority poll to gain mastership.
Polling
No single station is permanent master of the Data Highway
communication link. Each station bids for mastership when it needs to
send a message. The station interface module at the current master station
conducts a poll to select the next master station. A poll is an orderly,
systematic method to determine which stations have messages to send,
and to select one of these stations as master.
The mechanics of the polling algorithm are essentially transparent to you.
This is because the communication modules handle this automatically.
However, the polling algorithm does lead to the following basic rules that
you should follow to optimize Data Highway performance:
Number your stations sequentially whenever possible, and
Keep the number of high priority messages as low as possible.
Large numbers of high priority messages slow all traffic on the network.
In general, you should limit the number of high priority messages to less
than 1% of the total traffic on the Data Highway.
Commands From A Computer
A communication adapter module can execute commands from a
computer connected through a communication controller module (cat. no.
1771-KE or -KF). The command set of the computer includes the
command set of the 1771-KA2 module:
Protected write
Protected bit write
Unprotected read
Unprotected write
8-5
Page 98

Chapter 8
Station Interfacing
Unprotected bit write
These commands have the same execution sequence and memory access
as the same commands from a communication adapter module.
In addition to these commands, the command set from the computer
includes the following, which can be executed by a PLC-2 family
processor:
Privileged read
Privileged write
Diagnostic loop
Enter download mode
Enter upload mode (New for 1771-KA2)
Exit upload/download mode
Diagnostic read
Diagnostic counters reset
Set data table size (New for 1771-KA2)
Diagnostic Status
Privileged commands give the computer the capability to read from or
write into the entire processor memory. This includes both data
commands and user program areas. Privileged commands are used
chiefly to load programs from a computer to a station processor on the
Data Highway.
During program downloading, outputs are held in their last state by the
processor. However, at the computer programmer’s option, privileged
write commands can also be used to change data table values during a
download of program. (Refer to publications 1771-6.5.8 and
1771-6.5.15.)
Diagnostic commands affect only the communication adapter module at a
station, not the station processor. These commands access the read/write
memory of the communication adapter module. They provide a check of
module activity and permit computer control of specific aspects of
communication adapter module behavior. A summary of diagnostic
commands and their functions is given in Table 8.A.
8-6
Page 99

Chapter 8
Station Interfacing
able 8.A
T
Diagnostic
Diagnostic loop Echoes transmitted data back in reply message
Diagnostic read
Diagnostic counters
reset
Diagnostic status Allows access to 28 bytes of processor and
Command Summary
Command Function
Copies up to 245 bytes of data from module
memory
Resets all diagnostic error counters n the module
module status information
Other commands are available for communication with other processors,
but will return an error code if sent to a PLC-2 family processor.
Indications of Upload, Download (Earlier revisions)
If you are using a revision of the 1771-KA2 module before revision D, or
a revision of the 1770-T3 terminal before revision G, and are uploading or
downloading, the 1770-T3 terminal will:
display a mode select menu and a communication fault message
clear all force instructions
(Later Revisions)
When you connect a 1770-T3 terminal (revision G or later) to a
1771-KA2 module (series A, revision D or later) and perform program
uploads with the 1770-T3 terminal in the PLC-2 mode, the terminal does
the following:
Uploads
1. Displays the prompt:
UPLOAD IN PROGRESS - PLEASE WAIT FOR COMPLETION
2. disables the PLC-2 mode
3. displays the prompt:
UPLOAD COMPLETED - PRESS ANY KEY TO CONTINUE
4. re-enables the PLC-2 mode and forces are maintained after you press
any key
8-7
Page 100

Chapter 8
Station Interfacing
Downloads
For program downloads with the 1770-T3 terminal in the PLC-2 mode,
the terminal:
1. displays the prompt:
DOWNLOAD IN PROGRESS - ALL FORCES CLEARED
2. displays a mode select menu
3. displays the prompt:
DOWNLOAD COMPLETED - ALL FORCES CLEARED
4. displays a mode select menu
When you connect a 1770-T3 terminal (revision G) to a 1771-KA2
module (series A, revision D) and perform program uploads when the
1770-T3 terminal is not in PLC-2 mode, the terminal displays a mode
select menu and the following prompts:
1. UPLOAD IN PROGRESS - PLEASE WAIT FOR COMPLETION
2. UPLOAD COMPLETED
If you perform program downloads when the terminal is not in PLC-2
mode, the terminal displays a mode select menu and the following
prompts:
1. DOWNLOAD IN PROGRESS - PLEASE WAIT FOR
COMPLETION
2. DOWNLOAD COMPLETED
8-8
 Loading...
Loading...