Netgear DG834G, DG834GB User Manual

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
NETGEAR, Inc.
4500 Great America Parkway
Santa Clara, CA 95054 USA
Phone 1-888-NETGEAR
202-10006-05
June 2005
202-10006-05, June 2005

© 2005 by NETGEAR, Inc. All rights reserved.
Trademarks
NETGEAR is a trademark of Netgear, Inc.
Microsoft, Windows, and Wi ndow s NT are registered trademar ks of Microsoft Corporation.
Other brand and product names are registered trademarks or trademarks of their respective holders.
Statement of Conditions
In the interest of improving internal design, operational function, and/or reliability, NETGEAR reserves the right to
make changes to the products described in this document without notice.
NETGEAR does not assume any liability that may occur due to the use or application of the product(s) or circuit
layout(s) described herein.
Federal Communications Commission (FCC) Compliance Notice: Radio Frequency Notice
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to
part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and
used in accordance with the instruct ions, may cause harmf ul interference to radio communications. However, there is no
guarantee that interference will not occur in a particular installation. If this equipment does cause harmful interference to
radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try
to correct the interference by one or more of the following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
Federal Communications Commission (FCC) Radiation Exposure Statement
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled environment. In order to avoid
the possibility of exceeding the FCC radio frequency exposure limits, human proximity to the antenna shall not be less
than 20 cm (8 inches) during normal operation.
EN 55 022 Declaration of Conformance
This is to certify that the DG834G Wireless ADSL Firewall Router is shielded against the generation of radio
interference in accordance with the application of Council Directive 89/336/EEC, Article 4a. Conformity is declared by
the application of EN 55 022 Class B (CISPR 22).
Bestätigung des Herstellers/Importeurs
Es wird hiermit bestätigt, daß das DG834G Wireless ADSL Firewall Router gemäß der im BMPT-AmtsblVfg 243/1991
und Vfg 46/1992 aufgeführten Bestimmungen entstört ist. Das vorschriftsmäßige Betreiben einiger Geräte (z.B.
ii
202-10006-05, June 2005

Testsender) kann jedoch gewissen Beschränkungen unterliegen. Lesen Sie dazu bitte die Anmerkungen in der
Betriebsanleitung.
Das Bundesamt für Zulassungen in der Telekommunikation wurde davon unterrichtet, daß dieses Gerät auf den Markt
gebracht wurde und es ist berechtigt, die Serie auf die Erfüllung der Vorschriften hin zu überprüfen.
Certificate of the Manufacturer/Importer
It is hereby certified that the DG834G Wireless ADSL Firewall Router has been suppressed in accordance with the
conditions set out in the BMPT-AmtsblVfg 243/1991 and Vfg 46/19 92. The operation of some equipment (for example,
test transmitters) in accordance with the regulations may, however, be subject to certain restrictions. Please refer to the
notes in the operating instructions.
Federal Office for Telecommunications Approvals has been notified of the placing of this equipment on the market
and has been granted the right to test the series for compliance with the regulations.
Voluntary Control Council for Interference (VCCI) Statement
This equipment is in the second category (information equipment to be used in a residential area or an adjacent area
thereto) and conforms to the standards set by the Voluntary Control Council for Interference by Data Processing
Equipment and Electronic Office Machines aimed at preventing radio interference in such residential areas.
When used near a radio or TV receiver , it may become the cause of radio interference.
Read instructions for correct handling.
Customer Support
Refer to the Support Information Card that shipped with your DG834G Wireless ADSL Firewall Router.
World Wide Web
NETGEAR maintains a World Wide Web home page that you can access at the universal resource locator (URL)
http://www.netgear.com. A direct connection to the Internet and a Web browser such as Internet Explorer
or Netscape are required.
Product and Publication Details
Model Number: DG834G
Publication Date: June 2005
Product Family: router
Product Name: DG834G Wireless ADSL Firewall Router
Home or Business Product: Business
Language: English
Publication Part Number: 202-10006-05
202-10006-05, June 2005
iii

iv
202-10006-05, June 2005

Contents
Chapter 1
About This Manual
Audience, Scope, Conventions, and Formats ................................................................1-1
How to Use This Manual ................................................................................................1-2
How to Print this Manual .................................................................................................1-3
Chapter 2
Introduction
About the Router ............................................................................................................2-1
Key Features ..................................................................................................................2-1
A Powerful, True Firewall .........................................................................................2-2
802.11 Standards-based Wireless Networking .. .... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ..2-2
Easy Installation and Management ..........................................................................2-3
Protocol Support ......................................................................................................2-3
Virtual Private Networking (VPN) .............................................................................2-5
Content Filtering .......................................................................................................2-5
Auto Sensing and Auto Uplink™ LAN Ethernet Connections ..................................2-5
What’s in the Box? ..........................................................................................................2-5
The Router’s Front Panel .........................................................................................2-6
The Router’s Rear Panel .........................................................................................2-7
Chapter 3
Connecting the Router to the Internet
What You Need Before You Begin ..................................................................................3-1
ADSL Microfilter Requirements ................................................................................3-1
ADSL Microfilter .................................................................................................3-1
ADSL Microfilter with Built-In Splitter .................................................................3-2
Ethernet Cabling Requirements ............................................................................... 3-2
Computer Hardware Requirements .........................................................................3-2
LAN Configuration Requirements ............................................................................3-2
Internet Configuration Requirements ....................................................................... 3-3
Contents v
202-10006-05, June 2005

Where Do I Get the Internet Configuration Parameters? ............................. ............3-3
Record Your Internet Connection Information ..........................................................3-3
Connecting the DG834G to Your LAN ............................................................................3-5
How to Connect the Router ......................................................................................3-5
Auto-Detecting Your Internet Connection Type ..............................................................3-9
Wizard-Detected PPPoE Login Account Setup ............ ....... ...... ....... ...... ...... ....... ...3-10
Wizard-Detected PPPoA Login Account Setup ............ ....... ...... ....... ...... ...... ....... ...3-11
Wizard-Detected Dynamic IP Account Setup .........................................................3-11
Wizard-Detected IP Over ATM Account Setup ......................................................3-12
Wizard-Detected Fixed IP (Static) Account Setup ........................................ ..........3-13
Testing Your Internet Connection ..................................................................................3-14
Manually Configuring Your Internet Connec tion ........................ ... ... ... .... ... ... ................3-14
How to Perform Manual Configuration ...................................................................3-15
Internet Connection Requires Login and Uses PPPoE ...................................3-16
Internet Connection Requires Login and Uses PPPoA ...................................3-17
Internet Connection Does Note Require A Login ............................................3-18
ADSL Settings ........................................................................................................3-19
Chapter 4
Wireless Configuration
Considerations for a Wireless Network ..........................................................................4-1
Observe Performance, Placement, and Range Guidelines ................... ... ... ............4-1
Implement Appropriate Wireless Security ................................................................4-2
Understanding Wireless Settings ...................................................................................4-3
How to Set Up and Test Basic Wireless Connectivity ..............................................4-7
How to Restricting Wireless Access to Your Network ..............................................4-8
Restricting Access to Your Network by Turning Off Wireless Connectivity ........4-9
Restricting Wireless Access Based on the Wireless Network Name (SSID) .....4-9
Restricting Wireless Access Based on the Wireless Station Access List ..........4-9
Choosing WEP Authentication and Security Encryption Methods ................... ... ...4-11
Authentication Type Selection ......................................................................... 4-11
Encryption Choices ..........................................................................................4-12
How to Configure WEP ..........................................................................................4-13
How to Configure WPA-PSK ..................................................................................4-14
vi Contents
202-10006-05, June 2005

Chapter 5
Protecting Your Network
Protecting Access to Your DG834G Wireless ADSL Firewall Router .............................5-1
How to Change the Built-In Password .....................................................................5-1
Changing the Administrator Login Timeout ..............................................................5-2
Configuring Basic Firewall Services ...............................................................................5-2
Blocking Keywords, Sites, and Services ......... ... .... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ..5-3
How to Block Keywords and Sites ...........................................................................5-3
Firewall Rules .................................................................................................................5-5
Inbound Rules (Port Forwarding) .............................. ............................................... 5-6
Inbound Rule Example: A Local Public Web Server ..........................................5-6
Inbound Rule Example: Allowing Videoconferencing ........................................ 5-8
Considerations for Inbound Rules .....................................................................5-8
Outbound Rules (Service Blocking) .........................................................................5-9
Outbound Rule Example: Blocking Instant Messenger .....................................5-9
Order of Precedence for Rules ..............................................................................5-11
Services ................................. ................................................ .......................................5-12
How to Define Services ..........................................................................................5-12
Setting Times and Scheduling Firewall Services ................................................ .......... 5-13
How to Set Your Time Zone ...................................................................................5-13
How to Schedule Firewall Services ........................................................................5-14
Chapter 6
Managing Your Network
Backing Up, Restoring, or Erasing Your Settings ...........................................................6-1
How to Back Up the Configuration to a File ............................................................. 6-1
How to Restore the Configuration from a File .............................. ............................6-2
How to Erase the Configuration ...............................................................................6-2
Upgrading the Router’s Firmware .................... ......... .......... .......... .......... ......... .......... .....6-2
How to Upgrade the Router Firmware .....................................................................6-3
Network Management Information .................................................................................6-4
Viewing Router Status and Usage Statistics ....................... ... ... ... .... ... ... ... ... .... ... ... ..6-4
Viewing Attached Devices ........................................................................................6-9
Viewing, Selecting, and Saving Logged Information ................................................6-9
Selecting What Information to Log ..................................................................6-11
Saving Log Files on a Server ..........................................................................6-12
Contents vii
202-10006-05, June 2005

Examples of Log Messages ...................................................................................6-12
Activation and Administration ..........................................................................6-12
Dropped Packets .............................................................................................6-12
Enabling Security Event E-mail Notification .................................................................6-13
Running Diagnostic Utilities and Rebooting the Router ................................................6-14
Enabling Remote Management ....................................................................................6-15
Configuring Remote Management .........................................................................6-15
Chapter 7
Advanced Configuration
Configuring Advanced Security ......................................................................................7-1
Setting Up A Default DMZ Server ............................................................................7-1
How to Configure a Default DMZ Server ...........................................................7-2
Connect Automatically, as Required ........................................................................7-3
Disable Port Scan and DOS Protection ...................................................................7-3
Respond to Ping on Internet WAN Port ...................................................................7-3
MTU Size .................................................................................................................7-3
Configuring LAN IP Settings ...........................................................................................7-3
DHCP ................................. .............................................................. ........................7-5
Use Router as DHCP server ................................................. .... ... ... ... ... .... ... ... ..7-5
Reserved IP addresses .....................................................................................7-6
How to Configure LAN TCP/IP Settings ...................................................................7-7
Configuring Dynamic DNS .......................................................................................7-7
How to Configure Dynamic DNS ..............................................................................7-8
Using Static Routes ........................................................................................................7-9
Static Route Example ...............................................................................................7-9
How to Configure Static Routes .............................................................................7-10
Universal Plug and Play (UPnP) ...................................................................................7-12
Chapter 8
Virtual Private Networking (Advanced Feature)
Overview of VPN Configuration ......................................................................................8-2
Client-to-Gateway VPN Tunnels ..............................................................................8-2
Gateway-to-Gateway VPN Tunnels .........................................................................8-2
Planning a VPN ..............................................................................................................8-3
VPN Tunnel Configuration .................................. ... .......................................... ... .... ... ... ..8-6
How to Set Up a Client-to-Gateway VPN Configuration .................................................8-6
viii Contents
202-10006-05, June 2005

Step 1: Configuring the Client-to-Gateway VPN Tunnel on the DG834G ................8-7
Step 2: Configuring the NETGEAR ProSafe VPN Client on the Remote PC .........8-12
How to Set Up a Gateway-to-Gateway VPN Configuration ....... ................................... 8-20
VPN Tunnel Control ..................... .... ... ... ... .... ... ... ... ... .... .......................................... ......8-27
Activating a VPN Tunnel ........................................................................................8-27
Using the VPN Status Page to Activate a VPN Tunnel ....................................8-27
Activate the VPN Tunnel by Pinging the Remote Endpoint .............................8-28
Start Using a VPN Tunnel to Active It ..............................................................8-30
Verifying the Status of a VPN Tunnel .....................................................................8-30
Deactivating a VPN Tunnel ....... ... ... ... .... ................................................................8-32
Using the Policy Table on the VPN Policies Page to Deactivate a VPN Tunnel 8-32
Using the VPN Status Page to Deactivate a VPN Tunnel ......... ... ... ... ... .... ... ...8-33
Deleting a VPN Tunnel ...........................................................................................8-35
How to Set Up VPN Tunnels in Special Circumstances ...............................................8-35
Using Auto Policy to Configure VPN Tunnels ........................................................8-36
Configuring VPN Network Connection Parameters ......... ... ... .... ... ... ... ... .... ... ...8-36
Example of Using Auto Policy .........................................................................8-41
Using Manual Policy to Configure VPN Tunnels ....................................................8-48
Chapter 9
Troubleshooting
Basic Functioning ...........................................................................................................9-1
Power LED Not On ...................................................................................................9-2
Test LED Never Turns On or Test LED Stays On .....................................................9-2
LAN or WAN Port LEDs Not On ...............................................................................9-2
Troubleshooting the Web Configuration Interface ..........................................................9-3
Troubleshooting the ISP Connection ..............................................................................9-4
ADSL link .................................................................................................................9-4
WAN LED Blinking Yellow ..................................................................................9-4
WAN LED Off ......................................... ... ... ....................................... ... .... ... ... ..9-4
Obtaining a WAN IP Address .... ... ... .......................................... ... .... ... ... ..................9-5
Troubleshooting PPPoE or PPPoA .......................................................................... 9-6
Troubleshooting Internet Browsing ..........................................................................9-6
Troubleshooting a TCP/IP Network Using the Ping Utility ..............................................9-7
Testing the LAN Path to Your Router .......................................................................9-7
Testing the Path from Your Computer to a Remote Device .....................................9-8
Contents ix
202-10006-05, June 2005

Restoring the Default Configuration and Password ............... .........................................9-9
Using the Reset button .............................................................................................9-9
Problems with Date and Time .........................................................................................9-9
Appendix A
Technical Specifications
Appendix B
Network and Routing Basics
Related Publications ...................................................................................................... B-1
Basic Router Concepts .................................................................................................. B-1
What is a Router? ................................................................................................... B-1
Routing Information Protocol ................................................................................... B-2
IP Addresses and the Internet ......................................... .... ... ... ... .... ... ... ... ... .... ... ... . B-2
Netmask .................................... ................................................................ ..............B-4
Subnet Addressing .................................................................................................. B-4
Private IP Addresses ................................. ... ... ... .......................................... ........... B-7
Single IP Address Operation Using NAT ................................................................. B-7
MAC Addresses and Address Resolution Protocol ................................................. B-8
Related Documents ................................................................................................. B-9
Domain Name Server .............................................................................................. B-9
IP Configuration by DHCP .............................. ... .... ... .......................................... ... . B-9
Internet Security and Firewalls .................................................................................... B-10
What is a Firewall? ................................................................................................ B-10
Stateful Packet Inspection ............................... ... .... ... ... ... .... ... ... ... .... ... ... ... ... .... ..... B-10
Denial of Service Attack .........................................................................................B-11
Ethernet Cabling ................................. ... ... .... ... .......................................... ... ... ... .... ... ...B-11
Category 5 Cable Quality .......................................................................................B-11
Inside Twisted Pair Cables .................................................................................... B-12
Uplink Switches, Crossover Cables, and MDI/MDIX Switching ............................ B-13
Appendix C
Preparing Your Network
Preparing Your Computers for TCP/IP Networking ......................................... ... .... ... ... . C-1
Configuring Windows 95, 98, and Me for TCP/IP Networking ....................................... C-2
Installing or Verifying Windows Networking Components ....................................... C-2
Enabling DHCP to Automatically Configure TCP/IP Settings in Windows 95B, 98, and Me
C-4
Selecting the Windows’ Internet Access Method .................................................... C-6
x Contents
202-10006-05, June 2005

Verifying TCP/IP Properties .................................................................................... C-6
Configuring Windows NT4, 2000 or XP for IP Networking ............................................C-7
Installing or Verifying Windows Networking Components ....................................... C-7
DHCP Configuration of TCP/IP in Windows XP, 2000, or NT4 ..................... ... ... .... ... ... . C-8
DHCP Configuration of TCP/IP in Windows XP ..................................................... C-8
DHCP Configuration of TCP/IP in Windows 2000 ................................................ C-10
DHCP Configuration of TCP/IP in Windows NT4 .................................................. C-13
Verifying TCP/IP Properties for Windows XP, 2000, and NT4 ......................... ... .. C-15
Configuring the Macintosh for TCP/IP Networking ...................................................... C-16
MacOS 8.6 or 9.x ...................... ... ... ... .... ... ... ... .......................................... ............C-16
MacOS X ...... ... .......................................... .......................................... ..................C-16
Verifying TCP/IP Properties for Macintosh Computers ... .... ... ... ... .... ... ... ... ... .... .....C-17
Verifying the Readiness of Your Internet Account ....................................................... C-18
Are Login Protocols Used? ................................................................................... C-18
What Is Your Configuration Information? ..............................................................C-18
Obtaining ISP Configuration Information for Windows Computers .......................C-19
Obtaining ISP Configuration Information for Macintosh Computers .....................C-20
Restarting the Network ................................................................................................ C-21
Appendix D
Wireless Networking Basics
Wireless Networking Overview .............................. ... .... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ....D-1
Infrastructure Mode .................................................................................................D-1
Ad Hoc Mode (Peer-to-Peer Workgroup) ................................................................ D-2
Network Name: Extended Service Set Identification (ESSID) ................................D-2
Authentication and WEP Data Encryption .............................................. ... ... ... ... .... ... ... . D-2
802.11 Authentication ..............................................................................................D-3
Open System Authentication .............................. .... ... ... ... .... ... ... ... .... ....................... D-3
Shared Key Authentication ......................................................................................D-4
Overview of WEP Parameters ................................................................................ D-5
Key Size .................................................................................................................. D-6
WEP Configuration Options ...................... ... ... ... .... ... ... ... .... ... ... ... .... ... ... .................D-7
Wireless Channels ....................... .... ... ... ... ..................................................................... D-7
WPA Wireless Security ..................................................................................................D-8
How Does WPA Compare to WEP? ........................................................................ D-9
How Does WPA Compare to IEEE 802.11i? ........................................................ D-10
Contents xi
202-10006-05, June 2005

What are the Key Features of WPA Security? ...................................................... D-10
WPA Authentication: Enterprise-level User
Authentication via 802.1x/EAP and RADIUS ..................................................D-12
WPA Data Encryption Key Management ........................................................ D-14
Is WPA Perfect? ................................. .... ... ... ... ... .... .......................................... .....D-16
Product Support for WPA ......................................................................................D-16
Supporting a Mixture of WPA and WEP Wireless Clients is Discouraged ......D-16
Changes to Wireless Access Points ............................................................... D-16
Changes to Wireless Network Adapters .........................................................D-17
Changes to Wireless Client Programs .......................... ......................... ......... D-18
Appendix E
Virtual Private Networking
What is a VPN? ............................................................................................................. E-1
What Is IPSec and How Does It Work? ......................................................................... E-2
IPSec Security Features .............................. ... ... .... ... ... ... .... .................................... E-2
IPSec Components ...................... ... ... .... ... .......................................... .................... E-2
Encapsulating Security Payload (ESP) ................................................................... E-3
Authentication Header (AH) ............................... .... ... ... .......................................... . E-4
IKE Security Association ........... .......................................... ... ... ... ........................... E-4
Mode ...................................... ...................... .................... ...................... ........... E-5
Key Management .................................................................................................... E-6
Understand the Process Before You Begin ................................................................... E-6
VPN Process Overview ......... ... ... .......................................... ........................................ E-7
Network Interfaces and Addresses ......................................................................... E-7
Interface Addressing ......................................................................................... E-7
Firewalls ........................................................................................................... E-8
Setting Up a VPN Tunnel Between Gateways ........................................................ E-8
VPNC IKE Security Parameters ......... ... ... .... ............................................................... E-10
VPNC IKE Phase I Parameters ............................................................................. E-10
VPNC IKE Phase II Parameters .............................................................................E-11
Testing and Troubleshooting .........................................................................................E-11
Additional Reading ...................... .... ... .......................................... ... ... .... ......................E-11
Appendix F
NETGEAR VPN Configuration
DG834G to FVL328 ......................... ... ... ... .... ...................................... .... ... ... ... ... .... ... ... ..F-1
Configuration Profile .................................. ... ... ... .... ... ... ... .... ... ..................................F-1
xii Contents
202-10006-05, June 2005

Step-By-Step Conf iguration .................... ... ... ... ... .... ... ... ... .... ... ... ... .... ... ... ... ... .... ... .....F-2
DG834G with FQDN to FVL328 .....................................................................................F-6
Configuration Profile .................................. ... ... ... .... ... ... ... .... ... ..................................F-6
The Use of a Fully Qualified Domain Name (FQDN) .........................................F-7
Step-By-Step Conf iguration ................ .... ... ... ... ... .... ... ... .......................................... ..F-8
Configuration Summary (Telecommuter Example) .......................................................F-13
Setting Up the Client-to-Gateway VPN Configuration (Telecommuter Example) .........F-14
Step 1: Configuring the Client-to-Gateway VPN Tunnel on the VPN Router at the
Employer’s Main Office ..........................................................................................F-14
Step 2: Configuring the NETGEAR ProSafe VPN Client on the Remote PC at the
Telecommuter’s Home Office .......... ... .... ... ... ... ... .......................................... ..........F-16
Monitoring the VPN Tunnel (Telecommuter Example) ........................ .......... .......... ...... F-25
Viewing the PC Client’s Connection Monitor and Log Viewer ................................F-25
Viewing the VPN Router’s VPN Status and Log Information .................................F-27
Glossary
Contents xiii
202-10006-05, June 2005

xiv Contents
202-10006-05, June 2005
Chapter 1
About This Manual
This chapter describes the intended audience, scope, conventions, and formats of this manual.
Audience, Scope, Conventions, and Formats
This reference manual assumes that the reader has basic to intermediate computer and Internet
skills. However, basic computer network, Internet, firewall, and VPN technologies tutorial
information is provided in the Appendices and on the Netgear website.
This guide uses the following typographical conventions:
Table 1-1. Typographical Conventions
italics Emphasis, books, CDs, URL names
bold User input
fixed Screen text, file and server names, extensions, commands, IP addresses
This guide uses the following formats to highlight special messages:
Note: This format is used to highlight information of importance or special interest.
This manual is written for the DG834G wireless router according to these specifications:
Table 1-2. Manual Scope
Product Version DG834G Wireless ADSL Firewall Router
Manual Publication Date June 2005
Note: Product updates are available on the NETGEAR, Inc. Web site at
http://kbserver.netgear.com/products/DG834G.asp.
About This Manual 1-1
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
How to Use This Manual
The HTML version of this manual includes the following:
• Buttons, and , for browsing forwards or backwards through the manual one page
at a time
• A button that displays the table of contents and an button. Double-click on a
link in the table of contents or index to navigate directly to where the topic is described in the
manual.
• A button to access the full NETGEAR, Inc. online knowledge base for the
product model.
• Links to PDF versions of the full manual and individual chapters.
1-2 About This Manual
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
How to Print this Manual
To print this manual you can choose one of the following several options, according to your needs.
• Printing a Page in the HTML View.
Each page in the HTML version of the manual is dedicated to a major topic. Use the Print
button on the browser toolbar to print the page contents.
• Printing a Chapter.
Use the PDF of This Chapter link at the top left of any page.
– Click the PDF of This Chapter link at the top right of any page in the chapter you want to
print. The PDF version of the chapter you were viewing opens in a browser window.
Note: Your computer must have the free Adobe Acrobat reader installed in order to view
and print PDF files. The Acrobat reader is available on the Adobe Web site at
http://www.adobe.com.
– Click the print icon in the upper left of the window.
Tip: If your printer supports printing two pages on a single sheet of paper, you can save
paper and printer ink by selecting this feature.
• Printing the Full Manual.
Use the Complete PDF Manua l link at the top left of any page.
– Click the Complete PDF Manual link at the top left of any page in the manual. The PDF
version of the complete manual opens in a browser window.
– Click the print icon in the upper left of the window.
Tip: If your printer supports printing two pages on a single sheet of paper, you can save
paper and printer ink by selecting this feature.
About This Manual 1-3
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
1-4 About This Manual
202-10006-05, June 2005
Chapter 2
Introduction
This chapter describes the features of the NETGEAR DG834G Wireless ADSL Firewall Router.
The DG834G wireless router is a combination of a built-in ADSL modem, router, 4-port switch,
and firewall which enables your entire network to safely share an Internet connection that
otherwise is used by a single computer.
Note: If you are unfamiliar with networking and routing, refer to Appendix B, “Network
and Routing Basics” to become more familiar with the terms and procedures used in this
manual.
About the Router
The DG834G Wireless ADSL Firewall Router provides continuous, high-speed 10/100 Ethernet
access between your Ethernet devices. The DG834G wireless router enables your entire network
to share an Internet connection through the built-in ADSL modem that otherwise is used by a
single computer. With minimum setup, you can install and use the router within minutes.
The DG834G wireless router provides multiple Web content filtering options, plus e-mail
browsing activity, reporting, and instant alerts. Parents and network administrators can establish
restricted access policies based on time of day, Web site addresses, and address keywords. They
can also share high-speed ADSL Internet access for up to 253 personal computers. The included
firewall and Network Address Translation (NAT) features protect you from hackers.
Key Features
The DG834G wireless router provides the following features:
• A built-in ADSL modem
• A powerful, true firewall
• 802.11g standards-based wireless networking
Introduction 2-1
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
• Easy, Web-based setup for installation and management
• Extensive Internet protocol support
• Trustworthy VPN Communications over the Internet
• VPN Wizard for easy VPN configuration
• Content filtering
• Auto Sensing and Auto Uplink™ LAN Ethernet connections
These features are discussed below.
A Powerful, True Firewall
Unlike simple Internet sharing NAT routers, the DG834G is a true firewall, using stateful packet
inspection to defend against hacker attacks. Its firewall features include:
• Denial of Service (DoS) protection
Automatically detects and thwarts Denial of Service (DoS) attacks such as Ping of Death,
SYN Flood, LAND Attack and IP Spoofing.
• Blocks unwanted traffic from the Internet to your LAN.
• Blocks access from your LAN to Internet locations or services that you specify as off-limits.
• Logs security incidents
The DG834G will log security events such as blocked incoming traffic, port scans, attacks,
and administrator logins. You can configure the router to email the log to you at specified
intervals. You can also configure the router to send immediate alert messages to your email
address or email pager whenever a significant event occurs.
802.11 Standards-based Wireless Networking
The DG834G wireless router includes an 802.11g-compliant wireless access point, providing
continuous, high-speed 10/100 Mbps access between your wireless and Ethernet devices. The
access point provides:
• 802.11g Standards-based wireless networking at up to 54 Mbps
• Works with both 802.11g and 802.11b wireless devices
• 64-bit and 128-bit WEP encryption security
• WEP keys can be entered manually or generated by passphrase
2-2 Introduction
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
• Support for Wi-Fi Protected Access Pre-Shared Key (WPA-PSK) encryption and 802.1x
authentication
• Wireless access can be restricted by MAC address
Easy Installation and Management
You can install, configure, and operate the DG834G within minutes after connecting it to the
network. The following features simplify installation and management tasks:
• Browser-based management
Browser-based configuration allows you to easily configure your router from almost any type
of personal computer, such as Windows, Macintosh, or Linux. A user-friendly Setup Wizard is
provided and online help documentation is built into the browser-based Web Management
Interface.
• Smart Wizard
The router automatically senses the type of Internet connection, asking you only for the
information required for your type of ISP account.
• Remote management
The router allows you to log in to the Web management interface from a remote location via
the Internet. For security, you can limit remote management access to a specified remote IP
address or range of addresses, and you can choose a nonstandard port number.
• Diagnostic functions
The router incorporates built-in diagnostic functions such as Ping, DNS lookup, and remote
reboot. These functions allow you to test Internet connectivity and reboot the router. You can
use these diagnostic functions directly from the DG834G when you are connected on the LAN
or when you are connected over the Internet via the remote management function.
• Visual monitoring
The router’s front panel LEDs provide an easy way to monitor its status and activity.
• Flash erasable programmable read-only memory (EPROM) for firmware upgrades.
Protocol Support
The DG834G supports Transmission Control Protocol/Internet Protocol (TCP/IP) and Routing
Information Protocol (RIP). Appendix B, “Network and Routing Basics” provides further
information on TCP/IP.
Introduction 2-3
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
• The Ability to Enable or Disable IP Address Sharing by NAT
The DG834G allows several networked PCs to share an Internet account using only a single IP
address, which may be statically or dynamically assigned by your Internet service provider
(ISP). This technique, known as Network Address Translation (NAT), allows the use of an
inexpensive single-user ISP account. This feature can also be turned off comp let ely while
using the DG834G if you want to manage the IP address sche me yourself.
• Automatic Configuration of Attached PCs by DHCP
The DG834G dynamically assigns network configuration information, including IP, router,
and domain name server (DNS) addresses, to attached PCs on the LAN using the Dynamic
Host Configuration Protocol (DHCP). This feature greatly simplifies configuration of PCs on
your local network.
• DNS Proxy
When DHCP is enabled and no DNS addresses are specified, the router provides its own
address as a DNS server to the attached PCs. The router obtains actual DNS addresses from
the ISP during connection setup and forwards DNS requests from the LAN.
• Classical IP (RFC 1577)
Some Internet service providers, in Europe for example, use Classical IP in their ADSL
services. In such cases, the router is able to use the Classical IP address from the ISP.
• PPP over Ethernet (PPPoE)
PPP over Ethernet is a protocol for connecting remote hosts to the Internet over an ADSL
connection by simulating a dial-up connection. This feature eliminates the need to run a login
program such as EnterNet or WinPOET on your computer.
• PPP over ATM (PPPoA)
PPP over ATM is a protocol for connecting remote hosts to the Internet over an ADSL
connection by simulating an ATM connection.
• Dynamic DNS
Dynamic DNS services allow remote users to find your network using a domain name when
your IP address is not permanently assigned. The router contains a client that can connect to
many popular Dynamic DNS services to register your dynamic IP address.
• Universal Plug and Play (UPnP)
UPnP is a networking architecture that provides compatibility between networking
technologies. UPnP compliant routers provide broadband users at home and small businesses
with a seamless way to participate in online games, videoconferencing and other peer-to-peer
services.
2-4 Introduction
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
Virtual Private Networking (VPN)
The DG834G wireless router provides a secure encrypted connection between your local area
network (LAN) and remote networks or clients. It includes the following VPN features:
• Supports 8 VPN connections.
• Supports industry standard VPN protocols
The DG834G wireless router supports standard Manual or IKE keying methods, standard
MD5 and SHA-1 authentication methods, and standard DES and 3DES encryption methods. It
is compatible with many other VPN products.
• Supports 3DES encryption for maximum security.
• VPN Wizard based on VPNC recommended settings.
Content Filtering
With its content filtering feature, the DG834G prevents objectionable content from reaching your
PCs. The router allows you to control access to Internet content by screening for keywords within
Web addresses. You can configure the router to log and report attempts to access objectionable
Internet sites.
Auto Sensing and Auto Uplink™ LAN Ethernet Connections
With its internal 4-port 10/100 switch, the DG834G can connect to either a 10 Mbps standard
Ethernet network or a 100 Mbps Fast Ethernet network. The local LAN ports are autosensing and
capable of full-duplex or half-duplex operation.
TM
The router incorporates Auto Uplink
sense whether the Ethernet cable plugged into the port should have a ‘normal’ connection such as
to a computer or an ‘uplink’ connection such as to a switch or hub. That port will then configure
itself to the correct configuration. This feature also eliminates the need to worry about crossover
cables, as Auto Uplink will accommodate either type of cable to make the right connection.
technology. Each local Ethernet port will automatically
What’s in the Box?
The product package should contain the following items:
• DG834G Wireless ADSL Firewall Router
Introduction 2-5
202-10006-05, June 2005
Reference Manual for the Model Wireless ADSL Firewall Router DG834G
• AC power adapter (varies by region)
• Category 5 (Cat 5) Ethernet cable
• Telephone cable
• Microfilters (quantity and type vary by region)
• Wireless ADSL Firewall Router Resource CD, including:
—This guide
— Application Notes
• A printed Quick Installation Guide
• Warranty and Support Information cards
If any of the parts are incorrect, missing, or damaged, contact your NETGEAR dealer. Keep the
carton, including the original packing materials, in case you need to return the product for repair.
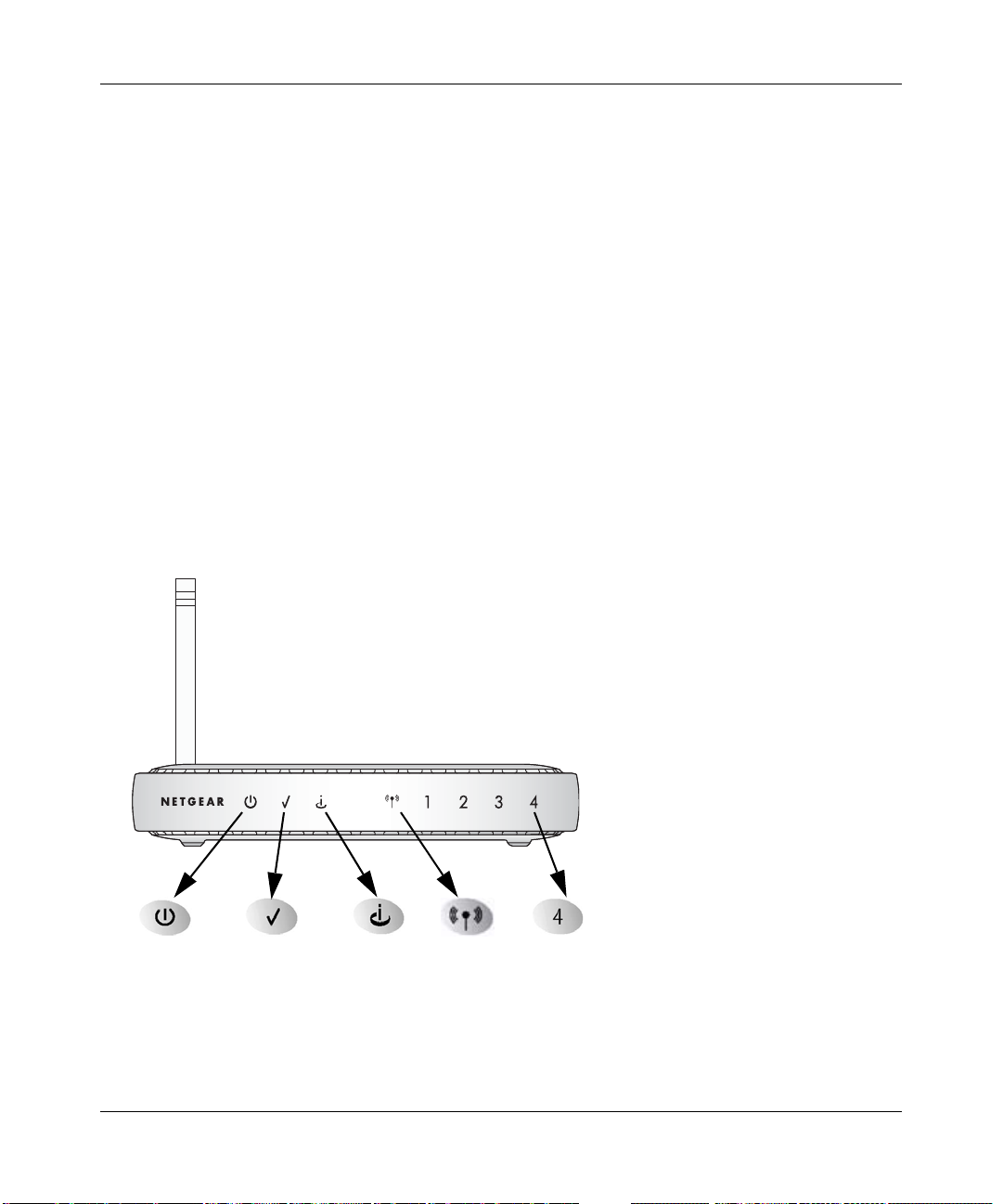
The Router’ s Front Panel
The DG834G Wireless ADSL Firewall Router front panel shown below contains status LEDs.
Power
Figure 2-1: DG834G Front Panel
Test
Internet W ireless
LAN
You can use the LEDs to verify various conditions. Table 2-1 lists and describes each LED on the
front panel of the router. These LEDs are green when lit.
2-6 Introduction
202-10006-05, June 2005
Reference Manual for the Model Wireless ADSL Firewall Router DG834G
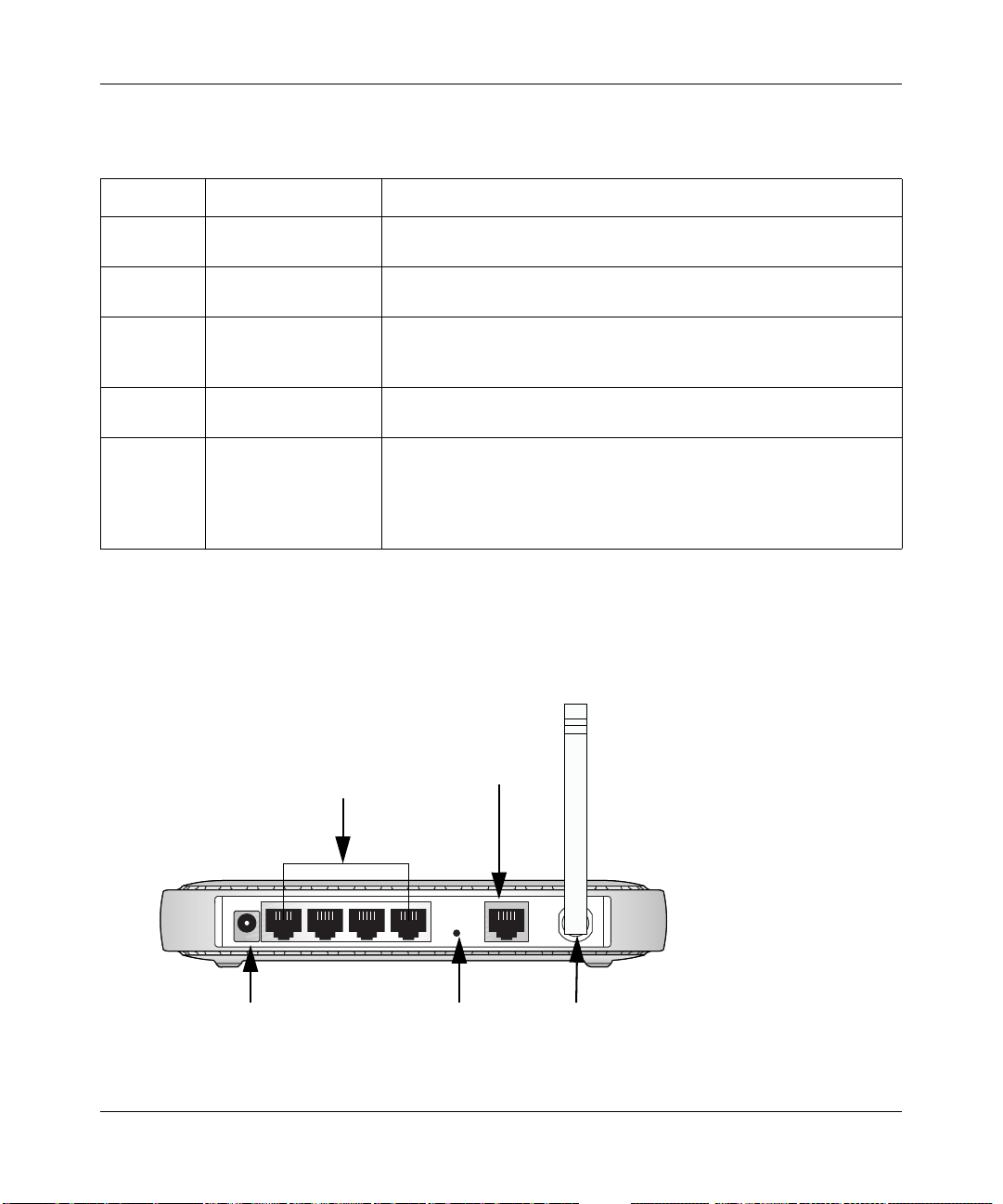
Table 2-1. LED Descriptions
Label Activity Description
Power On
Off
Test On
Off
Internet Blink -- Amber
On -- Green
Blink -- Green
Wireless On
Off
LAN On (Green)
Blink (Green)
On (Amber)
Blink (Amber)
Off
Power is supplied to the router.
Power is not supplied to the router.
The system is initializing.
The system is ready and running.
Indicates ADSL training.
The Internet port has detected a link with an attached device.
Data is being transmitted or received by the Internet port.
Indicates that the Wireless port is initialized.
The Wireless Access Point is turned off.
The Local port has detected a link with a 100 Mbps device.
Data is being transmitted or received at 100 Mbps.
The Local port has detected a link with a 10 Mbps device.
Data is being transmitted or received at 10 Mbps.
No link is detected on this port.
The Router’s Rear Panel
The rear panel of the DG834G Wireless ADSL Firewall Router (Figure 2-2) contains port
connections.
LAN
ADSL
Internet
Power
Reset
Wireless
Figure 2-2: DG834G Rear Panel
Introduction 2-7
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
Viewed from left to right, the rear panel contains the following elements:
• AC power adapter outlet
• Four Local Ethernet RJ-45 LAN ports for connecting the router to the local computers
• Factory Default Reset push button
• ADSL port for connecting the router to an ADSL line
• Wireless antenna
2-8 Introduction
202-10006-05, June 2005
Chapter 3
Connecting the Router to the Internet
This chapter describes how to set up the router on your Local Area Network (LAN) and connect to
the Internet. It describes how to configure your DG834G Wireless ADSL Firewall Router for
Internet access using the Setup Wizard, or how to manually configure your Internet connection.
What You Need Before You Begin
You need to prepare the following before you can establish an Internet connection through your
router:
1. The router connected to an ADSL line and a computer properly connected to the router as
explained below.
2. Active Internet service such as that provided by an ADSL account.
3. The Internet Service Provider (ISP) configuration information for your DSL account.
Note: If you purchased the DG834G in a country where a microfilter is not included, you must
acquire one.
ADSL Microfilter Requirements
ADSL technology uses the same wires as your telephone service. However, ADSL adds signals to
the telephone lines which create noise in the telephone service. You must use ADSL microfilters to
filter out these signals before they reach your telephone.
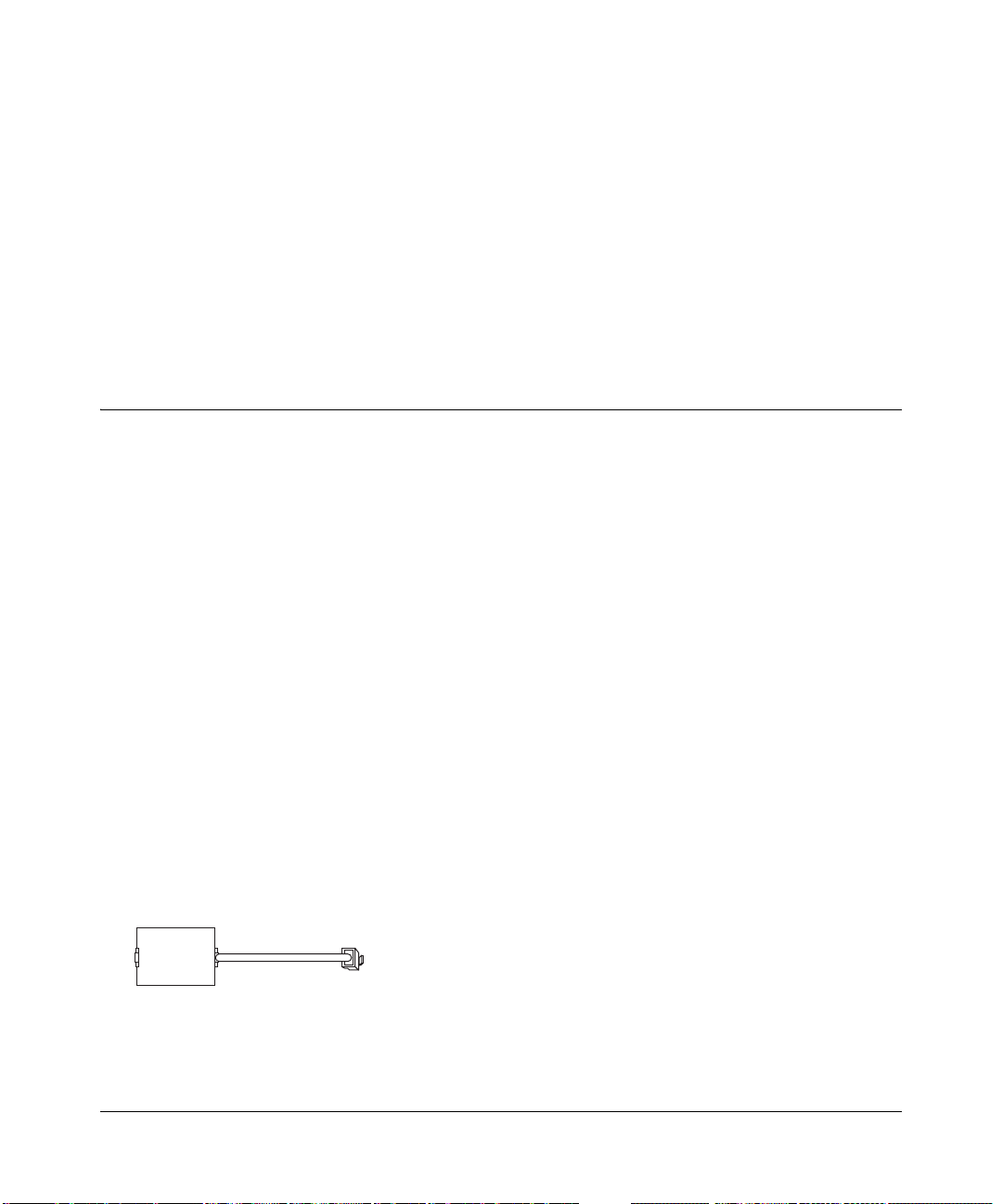
ADSL Microfilter
Phone
Figure 3-1: ADSL microfilter
Connecting the Router to the Internet 3-1
202-10006-05, June 2005
Reference Manual for the Model Wireless ADSL Firewall Router DG834G
Each device such as a telephone, fax machine, answering machine, or caller ID display will require
an ADSL microfilter.
Note: Do not connect the DG834G to the ADSL line through a microfilter unless the microfilter is
a combination microfilter/splitter specifically designed for this purpose. Doing so will prevent the
built-in ADSL modem in the DG834G from establishing a connection to the Internet. If you have
any doubts about this, connect the DG834G directly to the ADSL line.
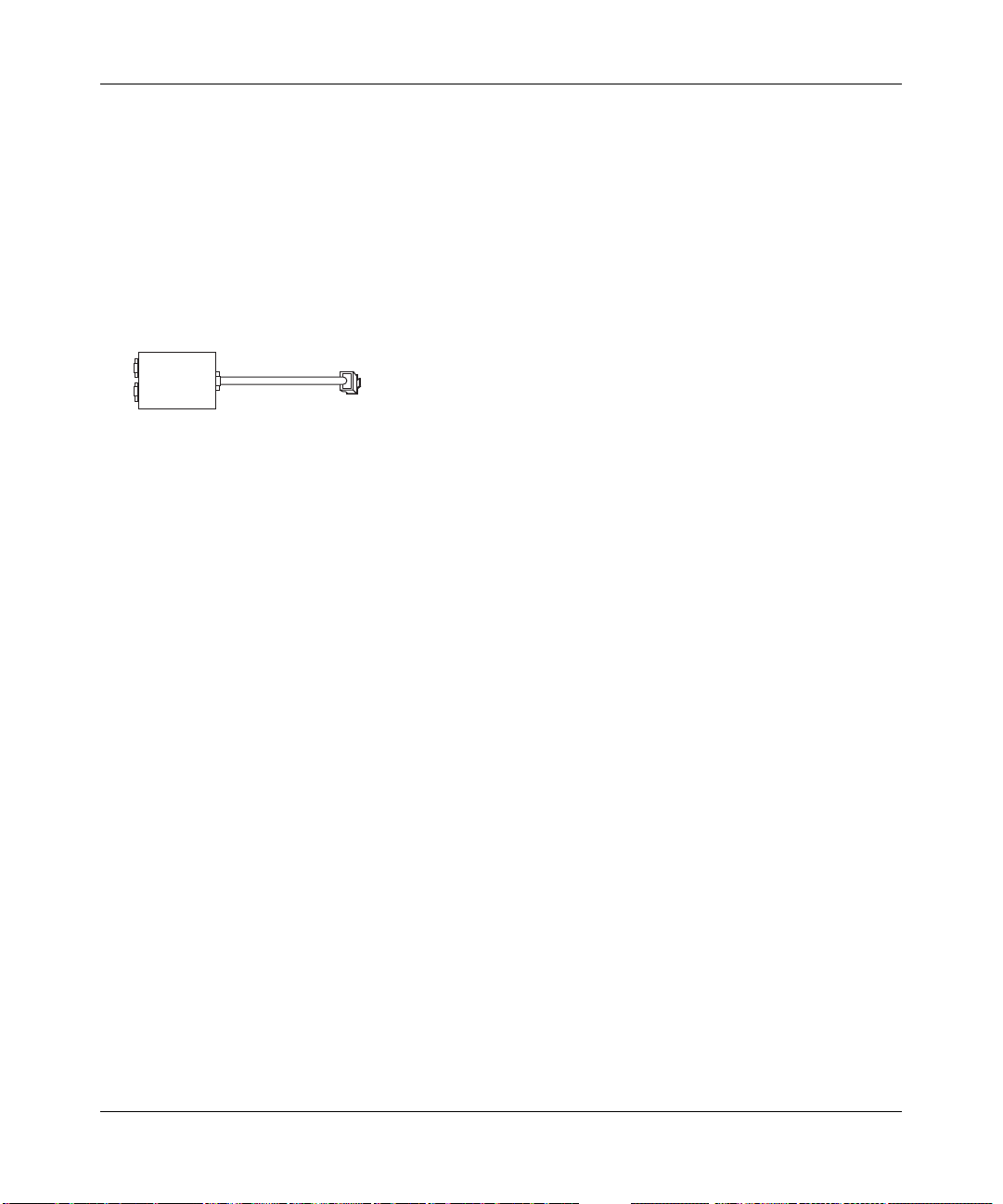
ADSL Microfilter with Built-In Splitter
DSL
Phone
Figure 3-2: ADSL microfilter with built-in splitter
Line
Use an ADSL microfilter with built-in splitter when there is a single wall outlet which must
provide connectivity for both the DG834G and telephone equipment.
Ethernet Cabling Requirements
The DG834G wireless router connects to your Ethernet LAN via twisted-pair cables. If the
computer will connect to your network at 100 Mbps, you must use a Category 5 (CA T5) cable such
as the one provided with your router.
Computer Hardware Requirements
To use the DG834G wireless router on your network, each computer must have an installed
Ethernet adapter and an Ethernet cable, or a 802.11g wireless adapter.
LAN Configuration Requirements
For the initial connection to the Internet and configuration of your router, you need to connect a
computer to the router which is set to automatically get its TCP/IP configuration from the router
via DHCP.
Note: Please refer to Appendix C, “Preparing Your Network” for assistance with DHCP
configuration.
3-2 Connecting the Router to the Internet
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
Internet Configuration Requirements
Depending on how your ISP set up your Internet account, you need one or more of these
configuration parameters to connect your router to the Internet:
• Virtual Path Identifier (VPI)/Virtual Channel Indentifier (VCI) parameters
• Multiplexing Method
• Host and Domain Names
• ISP Login Name and Password
• ISP Domain Name Server (DNS) Addresses
• Fixed or Static IP Address
Where Do I Get the Internet Configuration Parameters?
There are several ways you can gather the required Internet connection information.
• Your ISP should have provided you with all the information needed to connect to the Internet.
If you cannot locate this information, you can ask your ISP to provide it or you can try one of
the options below.
• If you have a computer already connected using the active Internet access account, you can
gather the configuration information from that computer.
• For Windows 95/98/ME, open the Network control panel, select the TCP/IP entry for the
Ethernet adapter, and click Properties.
• For Windows 2000/XP, open the Local Area Network Connection, select the TCP/IP entry
for the Ethernet adapter, and click Properties.
• For Macintosh computers, open the TCP/IP or Network control panel.
• You can also refer to the DG834G Resource CD for the NETGEAR Router ISP Guide which
provides Internet connection information for many ISPs.
Once you locate your Internet configuration parameters, you may want to record them on the next
page.
Record Your Internet Connection Information
Print the following page. Fill in the configuration parameters from your Internet Service Provider
(ISP).
Connecting the Router to the Internet 3-3
202-10006-05, June 2005

Reference Manual for the Model Wireless ADSL Firewall Router DG834G
ISP Multiplexing Method and Virtual Circuit Number: The default settings of your DG834G
Wireless ADSL Firewall Router will work fine for most ISPs. However, some ISPs use a specific
Multiplexing Method or a Virtual Circuit Number for either the Virtual Path Identifier (VPI) or
V irtual Channel Identifier (VCI). If your ISP provided you with a specific Multiplexing Method or
VPI/VCI number, then fill in the following:
Multiplexing Method, circle one: LLC-based or VC-based
VPI: ________
VCI: ___________
A number between 0 and 255.
A number between 1 and 65535.
ISP Login Name: The login name and password are case sensitive and must be entered exactly as
given by your ISP. Some ISPs use your full e-mail address as the login name. The Service Name is
not required by all ISPs. If you use a login name and password, then fill in the following:
Login Name: ______________________________
Password: __________________________ __
Service Name: _____________________________
Fixed or Static IP Address: If you have a static IP address, record the following information. For
example, 169.254.141.148 could be a valid IP address.
Fixed or Static Internet IP Address: ______
.______.______.______
Router IP Address: ______.______.______.______
Subnet Mask: ______.______.______.______
ISP DNS Server Addresses: If you were given DNS server addresses, fill in the following:
Primary DNS Server IP Address: ______
.______.______.______
Secondary DNS Server IP Address: ______.______.______.______
Host and Domain Names: Some ISPs use a specific host or domain name like CCA7324-A or
home. If you did not get host or domain names, use the following examples as a guide:
• If your main e-mail account with your ISP is aaa@yyy.com, then use aaa as your host name.
Your ISP might call this your account, user, host, computer, or system name.
• If your ISP’s mail server is mail.xxx.yyy.com, then use xxx.yyy.com as the domain name.
ISP Host Name: _________________________
ISP Domain Name: _______________________
For Wireless Access: For configuration of the wireless network, record the following:
Wireless Network Name (SSID): ________ ___ __ __ __ ___ __ __ _
WEP Authentication (circle one): Automatic, Open System, or Shared Key
WEP Encryption (circle one): 64 or 128; Passphrase or Key: _________________________
3-4 Connecting the Router to the Internet
202-10006-05, June 2005
 Loading...
Loading...