Page 1

HP Insight Vulnerability and Patch Manager software 6.0 User Guide
HP Part Number: 579547-001
Published: January 2010, First Edition
Page 2

© Copyright 2005, 2009 Hewlett-Packard Development Company, L.P.
Legal Notices
Confidential computer software. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial
Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under
vendor's standard commercial license.
The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express
warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall
not be liable for technical or editorial errors or omissions contained herein.
Acknowledgments
Microsoft, Windows, Windows Vista, Windows NT, and Windows XP are U.S. registered trademarks of Microsoft Corporation.
Intended audience
This document is for the person who installs and configures servers and storage systems. HP assumes you are qualified in the servicing of computer
equipment and trained in recognizing hazards in products with hazardous energy levels.
Page 3

Table of Contents
1 Introduction...............................................................................................6
Vulnerability and Patch Manager features...................................................................................................6
Service name changes.............................................................................................................................7
2 Using Vulnerability and Patch Manager.........................................................9
Prerequisites...........................................................................................................................................9
Accessing Vulnerability and Patch Manager...............................................................................................9
Using the interface..................................................................................................................................9
Acquiring updates.................................................................................................................................10
Scanning for vulnerabilities....................................................................................................................11
Deploying patches................................................................................................................................12
Reviewing Vulnerability and Patch Manager events....................................................................................12
Scan events.....................................................................................................................................12
Patch events....................................................................................................................................13
Acquisition events............................................................................................................................14
Miscellaneous events........................................................................................................................14
Using the Change VPM Credentials Utility................................................................................................15
3 Backing up and restoring Vulnerability and Patch Manager............................16
Backing up components.........................................................................................................................16
Restoring components ...........................................................................................................................16
Reinstalling Vulnerability and Patch Manager to a new host........................................................................16
4 Uninstalling Vulnerability and Patch Manager..............................................17
Remaining Vulnerability and Patch Manager files......................................................................................17
Reinstalling Vulnerability and Patch Manager ...........................................................................................18
5 Troubleshooting........................................................................................19
Uninstalling Vulnerability and Patch Manager...........................................................................................19
Remaining Vulnerability and Patch Manager files.................................................................................20
Reinstalling Vulnerability and Patch Manager......................................................................................20
Vulnerability scans................................................................................................................................20
Vulnerability and Patch Manager cannot access target systems..............................................................20
Windows..................................................................................................................................20
Windows XP..............................................................................................................................20
Linux target systems.....................................................................................................................21
Scan reports cannot be viewed..........................................................................................................21
A scan was submitted but never started..............................................................................................21
Scan results are inaccurate because of overlapping tasks.................................................................21
Current patch information is not displayed in scan reports................................................................21
Patches................................................................................................................................................21
Patches fail to download with a timeout error ......................................................................................21
VPM Patch Agent installation fails.......................................................................................................22
A patch acquisition was started, but no patches are visible...................................................................22
HTTP 300 errors received during patch acquisition...............................................................................22
Patches appear in a scan report but are not successfully deployed..........................................................23
Check for missing patches.................................................................................................................23
Validating VPM Patch Agent installation..............................................................................................23
Patch installation status reports are not current or do not match information that appears in scan reports......23
Other tools report that a Windows system is patched, but Vulnerability and Patch Manager reports patches
needed..........................................................................................................................................23
Patch source for vendor patches is Microsoft or Red Hat...................................................................23
Multiple events listed in Systems Insight Manager for patch deployments............................................24
STAT Scanner update error listed in the Systems Insight Manager event log........................................24
Radia internal error listed in the Systems Insight Manager event log...................................................24
“Abuse of Service” error occurs when attempting to acquire Red Hat patches.....................................24
Validate Installed Patches event does not complete ..............................................................................24
Table of Contents 3
Page 4

Systems Insight Manager integration........................................................................................................24
6 Support and other resources......................................................................25
Information to collect before contacting HP...............................................................................................25
How to contact HP................................................................................................................................25
Registering for software technical support and update service.....................................................................25
How to use your software technical support and update service.............................................................25
Warranty information.......................................................................................................................25
Typographic conventions........................................................................................................................25
Related documents................................................................................................................................26
Index.........................................................................................................27
4 Table of Contents
Page 5

List of Tables
2-1 Interface access................................................................................................................................9
2-2 Vulnerability and Patch Manager icons..............................................................................................10
2-3 Provided scan definitions..................................................................................................................11
2-4 Vulnerability and Patch Manager scan events.....................................................................................13
2-5 VPM patch events............................................................................................................................13
2-6 VPM acquisition events....................................................................................................................14
2-7 Miscellaneous Vulnerability and Patch Manager events........................................................................14
5
Page 6

1 Introduction
HP Insight Vulnerability and Patch Manager is an all-in-one vulnerability assessment and patch management
tool integrated into HP Insight Control, simplifying and consolidating the proactive identification and resolution
of issues that impact server availability into one central console.
IMPORTANT: HP is phasing out the HP Vulnerability and Patch Manager software (VPM) from Insight
Control. Technical support will be offered based on the Technical Support and Upgrade offerings for HP
Insight Control sold through November 2009. HP Insight Control licenses include 1 year of Technical Support
& Update, which you can upgrade to 3, 4, or 5 years. Depending on the purchase date of Insight Control
licenses and technical support extension, support for Vulnerability and Patch Manager functionality will end
no later than November 2012.
Starting with the Insight software 6.0 DVD, Vulnerability and Patch Manger will no longer be available.
However, existing users of the vulnerability and patch management capabilities can upgrade to Vulnerability
and Patch Manger 6.0 by downloading the software and manually installing it on the CMS. You can
download the software from Software depot.
Vulnerability and Patch Manager features
• Combined vulnerability assessment and patch management—A single tool seamlessly combines the
assessment and the remediation of vulnerabilities, reducing operational complexity.
• Integration into Systems Insight Manager—Integration enables you to use existing functionality such as
discovery, identification, scheduling, role-based security, notification, and group-based actions,
eliminating the need to recreate these tasks in multiple tools for vulnerability assessment and patch
management.
• Comprehensive vulnerability assessment—Coverage of vulnerabilities reported in all leading vulnerability
databases ensures comprehensive assessment. Vulnerability assessment identifies vulnerabilities reported
in the Common Vulnerabilities and Exposures (CVE) list, the Federal Computer Incident Response Center
(FedCIRC) vulnerability catalog, the SANS Top 20 Internet Security Vulnerabilities list, the Computer
Emergency Response Team (CERT) advisories list, and the U.S. Department of Energy Computer Incident
Advisories Center (CIAC) bulletins.
• Automated acquisition, scheduled deployment, and continuous enforcement of patches:
Automatically collects new vulnerability updates and patches directly from vendor sources, such
•
as a vendor’s web-based patch repository. Updates can be acquired outside the firewall and
imported into the patch repository in infrastructures where firewall policies prevent HTTP and FTP
downloads.
• Scheduled deployment, scheduled reboots after deployment, and checkpoint-restarts ensure that
patches are deployed with minimal impact on network resources and enable patches to be managed
from a central point.
• Unique desired-state management automatically and continuously ensures that patches remain
applied in their proper state. If patches are corrupt, they are automatically reinstalled to bring the
system to the desired level of patches.
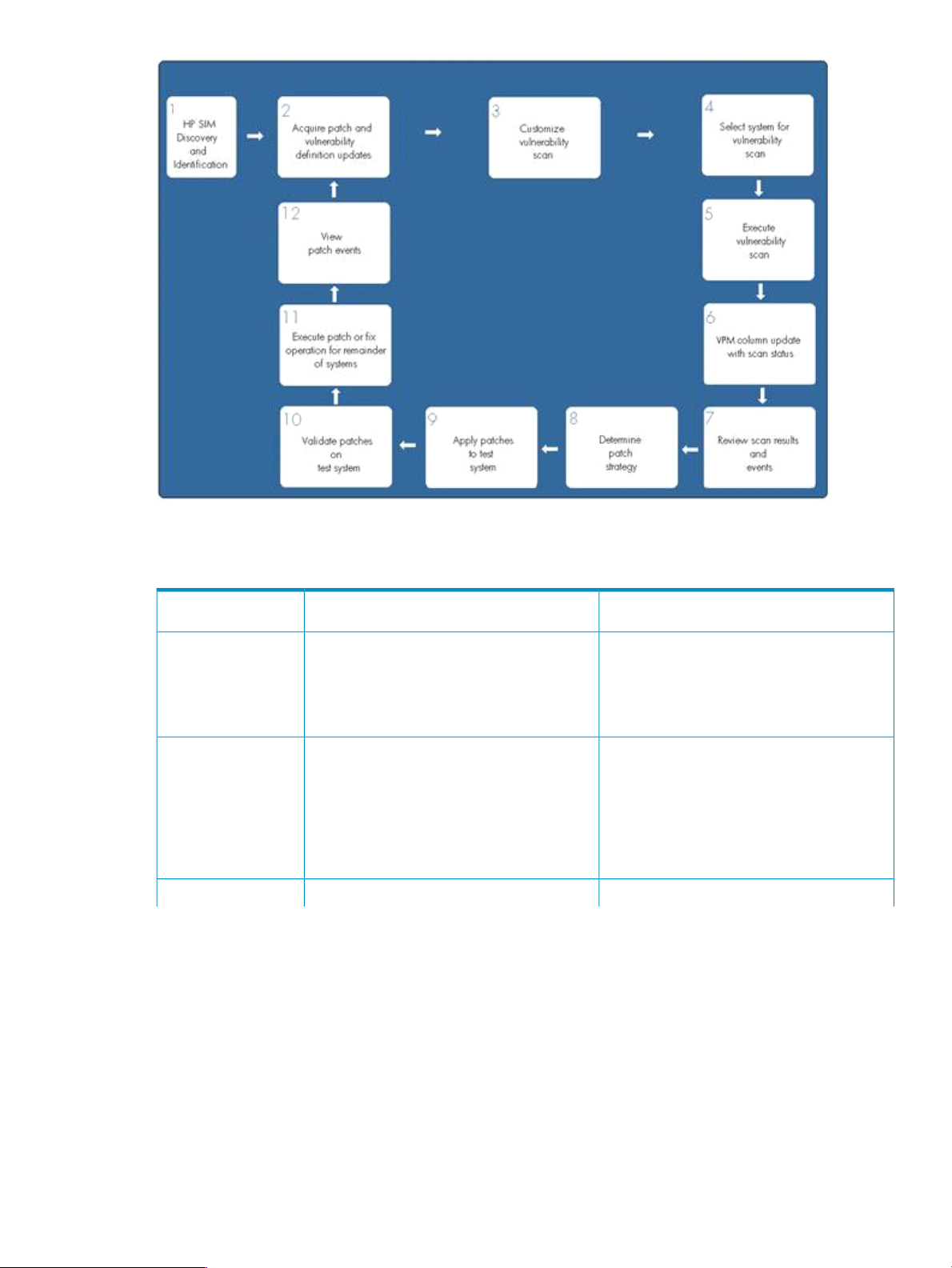
The following figure illustrates the Vulnerability and Patch Manager operation model.
Vulnerability and Patch Manager features 6
Page 7
Service name changes
The following table lists service name changes between Vulnerability and Patch Manager 3.x and 6.x.
Manager items
• ••STAT-SCANNER
version
• Acquisition utility
version
Radia services
Version 6.xVersion 3.xVulnerability and Patch
• 7.8• 7.2• RADIA version
6.4.66.4.5
• •3.0 6.0
• HP CA Configuration Server• HP CA Configuration Server
• •HP CA Messaging Server HP CA Messaging Server
•• HP CA Patch Manager ServerHP CA Patch Manager Server
• •HP Client Automation MSI Redirector HP Client Automation MSI Redirector
•• HP Client Notify DaemonHP Client Notify Daemon
• •HP Client Automation Scheduler Daemon HP Client Automation Scheduler Daemon
SQL Server (GUARDIAN), STATEngineSQL Server (GUARDIAN), STATEngineScanner Services
Service name changes 7
Page 8
Manager items
Version 6.xVersion 3.xVulnerability and Patch
Stat Engine (for Scanner 6.x only)Stat Engine (for Scanner 6.x only)
• Install command for
Vulnerability and
Patch Manager
• Install Command for
Acquisition tool on
DVD
Other dependency
checks by Vulnerability
and Patch Manager
Vulnerability and Patch
Manager registry keys:
• Key
• Command
installer removed
• \\VPM\WIN_IA32\acquiretool\setup.exe
• •TCP/IP TCP/IP
HP SIM and Vulnerability and Patch Manager
versions, HP SIM 5.3 required
• HKEY_LOCAL_MACHINE\\
SOFTWARE\\Microsoft\\
• HKEY_LOCAL_MACHINE\\
SOFTWARE\\Microsoft\\ • HKEY_LOCAL_MACHINE\\
• Stand-alone GUI installer• Command line with /silent, but stand-alone GUI
• \\VPM\WIN_IA32\acquiretool\setup.exe
• Microsoft® SQL Server• Microsoft® SQL Server
•• HP SIM and Vulnerability and Patch Manager
versions, HP SIM 5.3 and above required,
HP SIM 6.0 recommended
• HKEY_LOCAL_MACHINE\\
SOFTWARE\\Microsoft\\
Windows\\CurrentVersion\\Uninstall\\Windows\\CurrentVersion\\Uninstall\\
Windows\\CurrentVersion\\Uninstall\\HP Vulnerability And Patch Management_is1
HP Insight Vulnerability And Patch Manager_is1
SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\
Windows\\CurrentVersion\\Uninstall\\HP Vulnerability And Patch Management_is1
Windows\\CurrentVersion\\Uninstall\\
HP Insight Vulnerability And Patch Manager_is1
8 Introduction
Page 9
2 Using Vulnerability and Patch Manager
Prerequisites
The following are the prerequisites for using the Vulnerability and Patch Manager software:
• VPM: Microsoft .NET Framework 3.0 is a requirement for accessing the VPM 6.0 functionalities (as a
requirement for the Radia 7.8 version).
• Acquire Tool: Microsoft .NET Framework 3.0 or later for installing the Acquire tool.
NOTE: If the prerequisites are not met, the Acquisition tool pops up a message to install the prerequisite
softwares before installing the Acquire tool.
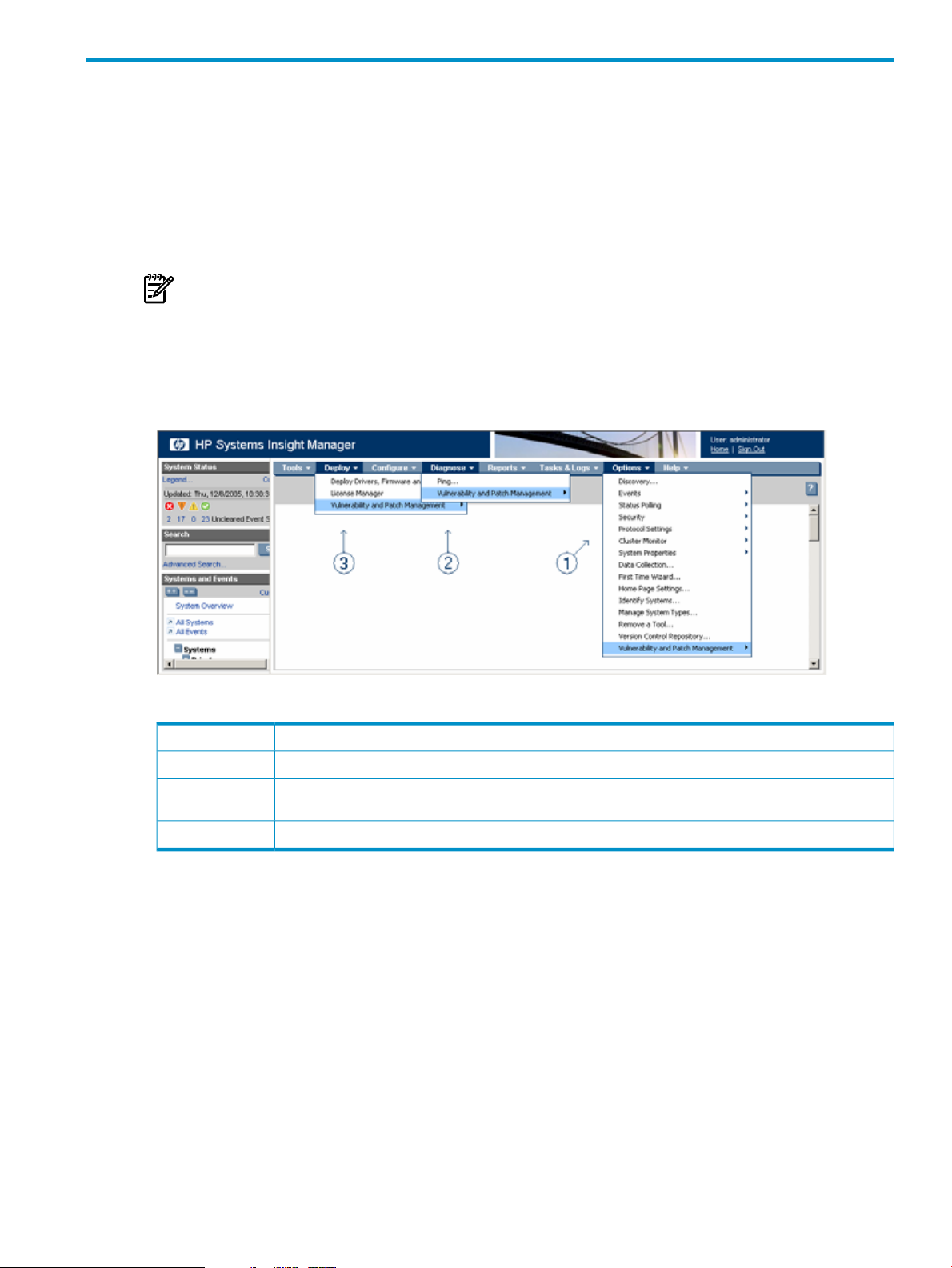
Accessing Vulnerability and Patch Manager
To access Vulnerability and Patch Manager from the HP SIM toolbar menu, select Vulnerability and Patch
Manager from the HP SIM Deploy, Diagnose, or Options menus.
Table 2-1 Interface access
2
Using the interface
Vulnerability and Patch Manager vulnerability information appears in the VPM column of the HP SIM console,
shown circled in the following figure. Initially, the icon depicted in the column displays Vulnerability and
Patch Manager eligibility information for the target system in the specific row. After target servers are licensed
and a vulnerability scan is performed, the column displays the combined status of the last vulnerability scan
on the target system (patch status does not appear in the column). Click the icon to display detailed information
about the system status of the Vulnerability and Patch Manager.
ActionMenu
Configure settings and acquire updates.1
Perform or customize vulnerability scans, and view scan results, patch installation status, patches installed by
VPM, patch reboot status, and the patch repository.
Deploy patches, validate installed patches, and deploy the VPM Patch Agent.3
Prerequisites 9
Page 10

Table 2-2 Vulnerability and Patch Manager icons
• Vulnerability and Patch Manager cannot access the system because
proper authentication information was not provided.
• The system is either not supported or connected.
• Vulnerability and Patch Manager cannot access the system registry or
file system.
Risk assessmentStatusIcon
HighCritical vulnerabilities have been detected.
MediumMajor vulnerabilities have been detected.
Low and warningMinor vulnerabilities have been detected.
NoneNo vulnerabilities have been detected.
UnknownThe Unknown icon might appear for the following reasons:
cannot run for the following reasons:
• The system is not licensed.
• The system is licensed, but a scan has not yet been performed.
Click any status icon to display additional information for the system. Clicking the Normal, Minor, or Major
icons opens a new page where you can view the last scan results for the system. A new scan can also be
launched from this page.
Clicking for a system displays an explanatory page listing possible reasons why status is not available
for the system and options to enable the Vulnerability and Patch Manager.
Acquiring updates
To ensure that Vulnerability and Patch Manager is up to date with the latest security information and obtain
new vulnerability scan definitions and patches, you must complete patch acquisitions on a regular basis. Do
not schedule patch acquisition tasks to run while vulnerability scans are running. Patch acquisition tasks
cause vulnerability scans to abort.
You can acquire update using Vulnerability and Patch Manager through Systems Insight Manager (see
Vulnerability and Patch Manager online help), or using the VPM Acquisition Utility.
To use the VPM Acquisition Utility:
1. If you have not already registered with Lumension, you must complete the the registration process. These
credentials are required to use the VPM Acuisiton utility.
To register, click the register link on the Vulnerablity and Patch Management update settings page.
You will receive a confirmation email.
2. From the selected system, access the VPM Acquisition Utility.
UnknownThis system is available for licensing, but Vulnerability and Patch Manager
UnknownVulnerability and Patch Manager cannot be licensed on this system.No icon
10 Using Vulnerability and Patch Manager
Page 11

3. Follow the on-screen instructions, selecting the appropriate update information for your server environment
when prompted.
4. Click Schedule, and then select a time to acquire daily Vulnerability and Patch Manager updates.
Updates might not be available daily, but scheduling the event daily ensures that you obtain critical
updates promptly. Updates to scan definitions are usually available a few days after new patches are
released.
5. To run the patch acquisition, click Run Now.
The vulnerability and patch acquisition process begins. You can monitor the progress of the acquisition
at C:\Program Files\HP\VPM Acquisition Utility\logs\patch-acquire.log. To
manually scroll through the log file during the acquisition, clear the Enable auto-scroll checkbox.
The Acquisition Log displays the progress of the acquisition. Disregard any messages that appear on
the log screen.
The acquisition process might appear to stall (hang) when downloading large files.
IMPORTANT: Acquiring patches from the Red Hat Network requires the network connection to remain
connected for the duration of the acquisition operation. If the network goes down, you must restart the patch
acquisition.
Scanning for vulnerabilities
Vulnerability and Patch Manager provides a variety of scan definitions. You can use these scans to search
for vulnerabilities or modify them to suit the specific needs of your environment. You can create custom scans
from the default system scans. When default system scans are updated, the custom scans are also updated
with corresponding vulnerability updates.
The following table lists the provided scan definitions that are provided with Vulnerability and Patch Manager
and a brief description of each.
Table 2-3 Provided scan definitions
4_0*
CrossPlatform
DescriptionScan definition
Windows NT® 4.0 vulnerabilities
Microsoft AdvisoriesAdvisory
Autofixable vulnerabilitiesAutoFix
Microsoft® and Linux vulnerabilities
Known and unknown locations file checksFileChecks
Known location file checksFileCheck_KnownLocation
Unknown location file checksFileCheck_UnknownLocation
Internet Explorer vulnerabilitiesIE
IIS vulnerabilitiesIIS
Linux vulnerabilitiesLinux
Malware checksMalware
Password policy checkPassword
Windows NT password policyPasswordChecker
All policy checkPolicy
SQL Server vulnerabilitiesSqlServer
Windows 2000 vulnerabilitiesW2K
XP
Windows 2003 vulnerabilitiesW2K3
Windows® XP vulnerabilities
Windows 2008 server vulnerabilitiesWindows 2008
Scanning for vulnerabilities 11
Page 12

DescriptionScan definition
Vista
* This scan definition is not included with the current version of Vulnerability and Patch Manager and only exists if previous versions
of the software have been installed.
For more information on vulnerability scanning, see the Vulnerability and Patch Manager online help.
• To perform a vulnerability scan, select Diagnose→Vulnerability and Patch Manager→Scan→Scan
for Vulnerabilities.
• To customize vulnerability scan definitions, select Diagnose→Vulnerability and Patch
Manager→Customize Scan..
• Deleting a customized vulnerability scan, select Diagnose→Vulnerability and Patch
Manager→Customize Scan., select the scan, and then click Delete.
• To view vulnerability scan results, select Diagnose→Vulnerability and Patch Manager→Scan→View
Results by Scan Name or select Diagnose→Vulnerability and Patch Manager→Scan→View
Results by System.
• To delete vulnerability scan results, select Diagnose→Vulnerability and Patch Manager→Scan→Vie w
Results by Scan Name or select Diagnose→Vulnerability and Patch Manager→Scan→View
Results by System, select the targets, and then click Delete.
Deploying patches
You can deploy patches immediately or schedule deployment for a later time. You can select patches
individually from the database for deployment to all systems or any combination of specified systems without
performing a scan, or deploy patches for all vulnerabilities identified in a particular scan. Patches come
from the software vendor and update existing software, registry, or configuration settings or files.
Information about patches:
• If required by the installed or remvoed patch, target systems are rebooted based on the reboot
information obtained from the original patch source. Reboot information might occasionally inaccurately
indicate whether a patch installation requires a reboot.
• If multiple patches requiring reboots are applied, target systems are only rebooted one time after all
patches are applied. Required reboots are deferred and performed later. HP recommends performing
required reboots as soon as possible because the status of patched systems might be unstable when a
required reboot is deferred.
• To determine patch applicability, the Vulnerability and Patch Manager might enhance patch detection
criteria to be more precise than vendor information. These patches are displayed with an asterisk in
the Patch Source column. HP in no way modifies the patch itself.
• Risk and Vulnerability ID information might not display because this information was not available at
the time the patch was acquired. The information will display when the vulnerability database is updated
to include this information.
• By default, patches are sorted by the latest release date. Select a column heading to re-sort patches.
Windows Vista® vulnerabilities
• Target systems that are down at the time of a scheduled patch application are patched when the system
is brought online.
For more information on deploying patches, see the Vulnerability and Patch Manager online help.
Reviewing Vulnerability and Patch Manager events
Vulnerability and Patch Manager creates events in Systems Insight Manager. These events can be viewed
with all Systems Insight Manager events in the Events list or independently in the VPM Events list.
Scan events
The following table lists the events created by the Vulnerability and Patch Manager scanning components.
12 Using Vulnerability and Patch Manager
Page 13

Table 2-4 Vulnerability and Patch Manager scan events
OccursDescriptionEvent
Completed VPM Scan for System
Patch events
The following table lists the events created by the Vulnerability and Patch Manager patching components.
Table 2-5 VPM patch events
A vulnerability scan has been submittedSubmitted VPM Scan
A group vulnerability scan has startedStarted VPM Scan
A vulnerability scan has started on a systemStarted VPM Scan for System
A group vulnerability scan has completedCompleted VPM Scan
A vulnerability scan has completed on a
system
A failure has occurred during a VPM scanFailed VPM Scan
When a scan is submitted. If another scan
is already running, this scan is queued.
When a scan is started for all systems
selected in the scan operation. Each
individual system also has a scan start event.
Individual machines are scanned one at a
time.
At the start of the scan for each individual
system.
When a scan is completed for all systems
selected in the scan operation. Each
individual system also has a scan completion
event. Individual machines are scanned one
at a time.
At the completion of the scan for each
individual system.
When an entire scan fails to complete
because of an internal error. Check the
system event log for more information.
OccursDescriptionEvent
Submitted VPM Patch
VPM Patch Start
VPM Patch Ended with Success
VPM Patch Ended with Failure
A Vulnerability and Patch Manager patch
has been submitted.
A group VPM patch has started.Started VPM Patch
A VPM patch has started on a system.Started VPM Patch for System
A group VPM patch has completed.Completed VPM Patch
A vulnerability patch installation has begun
on the target system
A VPM patch has completed on a system.Completed VPM Patch for System
A vulnerability patch installation has ended
on the target system with the status of
successful.
A vulnerability patch installation has ended
on the target system with the status of
failure.
When one or more patches have been
submitted.
When one or more patches have been
started for all systems selected in the patch
operation. Each individual system also has
a start event.
When one or more patches have been
started for an individual system.
When all patches have been completed for
all systems selected in the patch operation.
Each individual system also has a completion
event.
When a vulnerability patch installation has
been started on the target system. A software
update or bulletin is being applied to the
target system.
When all patches have been completed for
an individual system.
When a vulnerability patch installation has
ended on the target system with the status
of successful.
When a vulnerability patch installation has
ended on the target system with the status
of failure. Follow up might be required to
determine the actual cause and remedy to
the failure. It might be useful to examine any
patch event details related to this patch.
VPM Patch Current Status
VPM Patch Agent is reporting the current
status of a patch on the target device.
Reviewing Vulnerability and Patch Manager events 13
The status is reported after the reboot. When
VPM Patch Agent reports the current status
of a patch on the target device because of
a patch requiring a reboot.
Page 14
OccursDescriptionEvent
VPM Patch Not Applicable
Failed VPM Patch
Failed VPM Patch for a System
Radia Generic error
Acquisition events
The following table lists the events created by the Vulnerability and Patch Manager patch acquisition.
Table 2-6 VPM acquisition events
Started VPM Acquisition
VPM Scan Definitions Updated
The selected patch is not applicable to the
selected system and therefore is not
applied.
A failure has occurred during a
Vulnerability and Patch Manager patch
operation.
A failure has occurred during a VPM patch
operation for a particular system.
A failure has occurred during the
Vulnerability and Patch Manager patch
operation.
Acquisition of vulnerability updates and
patches has started
Successfully updated vulnerability scan
definitions
When the selected patch is not applicable
to the selected system.
When one or more patches fails to complete
because of an internal error. Check the
system event log for more information.
When an individual system fails to complete
because of an internal error. Check the
system event log for more information.
This error occurs when you attempt to apply
a patch that is not present in the RCS
database.
OccursDescriptionEvent
When acquisition of scan definitions,
patches for selected operating systems and
applications has started. This operation
might take a few minutes depending on the
number of items being downloaded.
When scan definition files have been
updated successfully as part of an
acquisition.
VPM Scan Definitions Up-to-date
Completed VPM Acquisition
Failed VPM Acquisition
Failed VPM Scan Definitions Update
Failed VPM Update
Miscellaneous events
The following lists the miscellaneous events created by Vulnerability and Patch Manager.
Table 2-7 Miscellaneous Vulnerability and Patch Manager events
Installed Vulnerability and Patch Manager
Removed Vulnerability and Patch Manager
No updates required for the vulnerability
scan definitions, already up to date
Acquisition of vulnerability updates and
patches has completed
A failure has occurred during a VPM patch
acquisition
Updates for the vulnerability scan
definitions failed
Updates for the vulnerability scanner
component of VPM failed
Vulnerability and Patch Manager has been
installed
The Vulnerability and Patch Manager
product has been removed from this
Systems Insight Manager Server
When scan definition files do not need to
be updated as part of an acquisition.
When acquisition of scan definitions and
patches for selected operating systems and
applications is complete.
When acquisition of scan definitions and
patches for selected operating systems and
applications has failed.
When acquisition of scan definitions has
failed.
When acquisition of updated code that
scans configuration issues has failed.
OccursDescriptionEvent
When installation of Vulnerability and Patch
Manager successfully completes.
When uninstallation of Vulnerability and
Patch Manager successfully completes.
VPM Security Access Violation
Vulnerability and Patch Manager Scan
Definition Creation Failure
14 Using Vulnerability and Patch Manager
Vulnerability and Patch Manager is
reporting a security violation
Vulnerability and Patch Manager could not
write a new vulnerability scan definition
file
When the Vulnerability and Patch Manager
plug-in (on the HP Insight Control server)
does not have the right credentials to access
the scanner service (on the Vulnerability and
Patch Manager server).
When a custom scan definition cannot be
created. This event can indicate a lack of
disk space or permission problems.
Page 15

OccursDescriptionEvent
Vulnerability and Patch Manager Scan
Definition Removal Failure
Vulnerability and Patch Manager Scanner
Service Unreachable
VPM Results Structure Creation Failure
VPM Results Creation Failure
VPM Results Removal Failure
Failed VPM Patch Agent Install
Vulnerability and Patch Manager could not
remove a vulnerability scan definition file
Vulnerability and Patch Manager could not
make a connection to the vulnerability
scanner service
Vulnerability and Patch Manager could not
create its results directory
Vulnerability and Patch Manager could not
write a results file
Vulnerability and Patch Manager failed to
remove a results file from the Vulnerability
and Patch Manager results area
The VPM Patch Agent has been installedInstalled VPM Patch Agent
A failure has occurred in the VPM Patch
Agent installation
When one or more custom scan definitions
are not removed as a part of the delete
operation from the Customize Scan
operation.
When Vulnerability and Patch Manager has
found a problem trying to contact the
scanner service either because of a network
problem or because STAT Scanner service
is not operational (for example, IIS service
is not running on the VPM server).
When Vulnerability and Patch Manager
cannot create the directory structure required
to receive the scan results.
When a custom scan definition cannot be
created. This event can indicate a lack of
disk space or permission problems.
When one or more reports are not removed
as a part of the delete operation from the
View Results by System or View Results by
Scan Name process.
When the VPM Patch Agent deploys
successfully to a system as part of a licensing
operation or the Deploy VPM Patch Agent
operation.
When the VPM Patch Agent fails to deploy
to a system as part of a licensing operation
or the Deploy VPM Patch Agent operation.
Vulnerability and Patch Manager might not
have permission to access the system. If the
system type is Unknown or Unmanaged, the
VPM Patch Agent must be deployed from
the Deploy VPM Patch Agent menu so the
operating system type can be manually
selected.
Started VPM Patch Removal
VPM Generic Radia Error
started
A patch removal operation has completedCompleted VPM Patch Removal
An error has been detected in the Radia
Patch Manager component of Vulnerability
and Patch Manager
Using the Change VPM Credentials Utility
You can use the Change VPM Credentials Utility to update Vulnerability and Patch Manager credentials:
• When the credentials or IP address of the Systems Insight Manager server have been changed
• When the credentials of the account used to install Vulnerability and Patch Manager have been changed
To update the Vulnerability and Patch Manager credentials:
1. From the Vulnerability and Patch Manager server, click Start→Programs→HP Insight Software→HP
Insight vulnerability and Patch Manager Pack→Change VPM Credentials.
2. Select whether to change Vulnerability and Patch Manager or database credentials, and then click OK.
3. If changing Vulnerability and Patch Manager credentials enter your current user credentials and IP
address, select whether to a secure connection to the VPM server, and then click Change.
4. If changing database credentials, enter your current database credentials, and then click Change.
When removal of a patch starts.A patch removal operation has been
When a patch is successfully removed from
a system.
When an error occurs while attempting to
apply a patch. See the event details for more
information.
Using the Change VPM Credentials Utility 15
Page 16

3 Backing up and restoring Vulnerability and Patch Manager
Vulnerability and Patch Manager application files are tightly coupled to Systems Insight Manager and its
components. There are also Vulnerability and Patch Manager subcomponents, which can place files in other
locations. A number of tables exist in databases, which require special tools to back up effectively.
Use the following guidelines to preserve the history of previous scan results and the list of patches installed
on each target system. Backup and restore can be done by preserving individual components.
Before beginning the process, review the following:
• The Systems Insight Manager file/directory structure and database layout
• The Vulnerability and Patch Manager file and directory structure
Backing up components
Systems Insight Manager must be offline to back up components. To back up individual components:
1. Back up the Vulnerability and Patch Manager files under the Systems Insight Manager directory.
2. Back up Systems Insight Manager directory tree and the Systems Insight Manager database. For
instructions, see the
on the operating system.
Restoring components
This procedure restores the Vulnerability and Patch Manager historical scan and patch data to the point
where it was backed up. After completing the process, HP recommends running a scan to restore current
Vulnerability and Patch Manager status.
To restore components:
1. Restore Systems Insight Manager and the Systems Insight Manager database from the backup files.
2. Install Vulnerability and Patch Manager.
3. Perform vulnerability definitions update.
HP Systems Insight Manager User Guide
. This procedure might be different depending
Reinstalling Vulnerability and Patch Manager to a new host
This process removes the patch and vulnerability database, save the historical files, and reinstalls THE
Vulnerability and Patch Manager to a new host. After completing the process you must reload the patch and
vulnerability database. To reinstall the Vulnerability and Pathc Manager to a new host:
1. Connect to the system housing the remote Vulnerability and Patch Manager server (not the Systems
Insight Manager server).
2. Uninstall Vulnerability and Patch Manager using either the Start menu or the Add or Remove Programs
option in the Control Panel.
3. When prompted to remove the data files, select NO to keep the historical files.
4. Connect to the system housing the Systems Insight Manager Server.
5. Install the Vulnerability and Patch Manager package, using the Systems Insight Manager server as the
host for Vulnerability and Patch Manager.
6. After the entire installation process is complete, reboot the system, to make sure all files are released
and installed correctly.
NOTE: You must redeploy the patch agents to direct them to the new Vulnerability and Patch Manager
server before patching.
NOTE: Before acquiring Linux Patches you must re-apply the Red Hat network SID files to the new
Vulnerability and Patch Manager server.
7. Using Systems Insight Manager, request a Patch Acquisition. The entire patch database must be reloaded.
8. Rescan your servers to update Vulnerability status.
Backing up components 16
Page 17

4 Uninstalling Vulnerability and Patch Manager
You can use either of the following methods to uninstall Vulnerability and Patch Manager. The Vulnerability
and Patch Manager uninstallation must be performed from the Vulnerability and Patch Manager server.
Vulnerability and Patch Manager scan results can be retained after uninstallation. The last scan performed
can be accessed from the VPM column. If you choose to delete scan results, the VPM column is set to an
initialized state.
IMPORTANT:
Be sure that no vulnerability scans, patch deployments, or patch acquisitions are running. Close all
•
browsers before attempting to uninstall Vulnerability and Patch Manager.
• Vulnerability and Patch Manager licenses are not removed from target systems when Vulnerability and
Patch Manager is uninstalled.
To uninstall Vulnerability and Patch Manager with the uninstaller:
1. Select Start→Programs→HP Insight Software→HP Insight vulnerability and Patch Manager
Pack→Uninstall VPM.
2. When prompted, select whether to remove the VPM data stored on the Systems Insight Manager server,
such as scan reports and Vulnerability and Patch Manager tasks. If data is removed, then it is cleared
from the Systems Insight Manager systems list.
3. When prompted, select whether to remove the patch database.
4. When uninstall is complete, the Systems Insight Manager service is automatically restarted.
5. Delete the Vulnerability and Patch Manager directory. The default location is C:\Program
Files\HP\VPM.
To uninstall Vulnerability and Patch Manager from the Control Panel:
1. Select Add or Remove Programs.
2. Select HP Insight Vulnerability and Patch Manager→Change/Remove.
3. When prompted, select whether to remove the Vulnerability and Patch Manager data stored on the
Systems Insight Manager server, such as scan reports and Vulnerability and Patch Manager tasks. Data
that appears in the Systems Insight Manager systems list is cleared if data is removed.
4. When prompted, select whether to remove the patch database.
5. When uninstallation is complete, the Systems Insight Manager service is automatically restarted.
6. Delete the Vulnerability and Patch Manager directory. The default installation location is C:\Program
Files\HP\VPM.
Remaining Vulnerability and Patch Manager files
A Vulnerability and Patch Manager uninstallation does not remove all Vulnerability and Patch Manager files
from the server. The following files remain after uninstallation:
• Target systems:
C:\Program Files\Hewlett-Packard\HPCA\ManagementAgent\nvdkit.exe•
• C:\Program Files\Hewlett-Packard\HPCA\ManagementAgent\rma.tkd
• C:\Program Files\Hewlett-Packard\HPCA\ManagementAgent\rma.log
• Systems Insight Manager/VPM server:
<Systems Insight
•
Manager_folder>\hpwebadmin\webapps\ROOT\mxportal\VPM\column\vpmcolmain.jps
• <Systems Insight
Manager_folder>\hpwebadmin\webapps\ROOT\mxportal\VPM\column\vpmbase.html
• <Systems Insight
Manager_folder>\hpwebadmin\webapps\ROOT\mxportal\home\STATScanner 1
Remaining Vulnerability and Patch Manager files 17
Page 18

The VPM Results directory remains only if you select to retain Vulnerability and Patch Manager data during
the uninstallation.
Reinstalling Vulnerability and Patch Manager
If an updated version of Vulnerability and Patch Manager is installed after a previous version has been
uninstalled, the entitlement list could be lost for all managed target systems. To prevent this, be sure that you
uninstall and reinstall the updated VPM Patch Agent to all target systems.
18 Uninstalling Vulnerability and Patch Manager
Page 19

5 Troubleshooting
This chapter identifies and provides solutions for commonly encountered Vulnerability and Patch Manager
issues, as well as answers to frequently asked questions.
Uninstalling Vulnerability and Patch Manager
Use either of the following methods to uninstall Vulnerability and Patch Manager. The Vulnerability and Patch
Manager uninstallation must be performed from the Vulnerability and Patch Manager server.
Vulnerability and Patch Manager scan results can be retained after uninstallation. The last scan performed
can be accessed from the VPM column. If you choose to delete scan results, the VPM column is set to an
initialized state.
IMPORTANT:
Be sure that no vulnerability scans, patch deployments, or patch acquisitions are running. Close all
•
browsers before attempting to uninstall Vulnerability and Patch Manager.
• Vulnerability and Patch Manager licenses are not removed from target systems when Vulnerability and
Patch Manager is uninstalled.
To uninstall Vulnerability and Patch Manager with the uninstaller:
1. Select Start→Programs→HP Insight Software→HP Insight vulnerability and Patch Manager
Pack→Uninstall VPM.
2. When prompted, select whether to remove the Vulnerability and Patch Manager data stored on the
Systems Insight Manager server, such as scan reports and Vulnerability and Patch Manager tasks. If
data is removed, then it is cleared from the Systems Insight Manager systems list.
3. When prompted, select whether to remove the patch database.
4. When uninstall is complete, the Systems Insight Manager service is automatically restarted.
5. Delete the Vulnerability and Patch Manager directory. The default locations are C:\Program
Files\HP\VPM and C:\Program Files\HP\Systems Insight
Manager\hpwebadmin\webapps\ROOT\mxportal\VPM.
To uninstall Vulnerability and Patch Manager from the Control Panel:
1. Select Add or Remove Programs.
2. Select HP Insight Vulnerability and Patch Manager→Change/Remove.
3. When prompted, select whether to remove the Vulnerability and Patch Manager data stored on the
Systems Insight Manager server, such as scan reports and Vulnerability and Patch Manager tasks. Data
that appears in the Systems Insight Manager systems list is cleared if data is removed.
4. When prompted, select whether to remove the patch database.
5. When uninstallation is complete, the Systems Insight Manager service is automatically restarted.
6. Delete the Vulnerability and Patch Manager directory. The default installation locations are C:\Program
Files\HP\VPM and C:\Program Files\HP\Systems Insight
Manager\hpwebadmin\webapps\ROOT\mxportal\VPM.
Uninstalling Vulnerability and Patch Manager 19
Page 20

Remaining Vulnerability and Patch Manager files
A Vulnerability and Patch Manager uninstallation does not remove all Vulnerability and Patch Manager files
from the server. The following files remain after uninstallation:
• Target systems:
C:\Program Files\Hewlett-Packard\HPCA\ManagementAgent\nvdkit.exe•
• C:\Program Files\Hewlett-Packard\HPCA\ManagementAgent\rma.tkd
• C:\Program Files\Hewlett-Packard\HPCA\ManagementAgent\rma.log
• Systems Insight Manager/Vulnerability and Patch Manager server:
<Systems Insight
•
Manager_folder>\hpwebadmin\webapps\ROOT\mxportal\VPM\column\vpmcolmain.jps
• <Systems Insight
Manager_folder>\hpwebadmin\webapps\ROOT\mxportal\VPM\column\vpmbase.html
• <Systems Insight
Manager_folder>\hpwebadmin\webapps\ROOT\mxportal\home\STATScanner 1
The Vulnerability and Patch Manager Results directory remains only if you select to retain Vulnerability and
Patch Manager data during the uninstallation.
Reinstalling Vulnerability and Patch Manager
If an updated version of Vulnerability and Patch Manager is installed after a previous version has been
uninstalled, the entitlement list could be lost for all managed target systems. To prevent this, be sure that you
uninstall and reinstall the updated VPM Patch Agent to all target systems.
Vulnerability scans
Vulnerability and Patch Manager cannot access target systems
If Vulnerability and Patch Manager cannot perform accurate scanning on a target system because of access
problems, verify the following information depending on the target operating system.
Windows
• The account used to scan the target system is a member of the Administrator group or Domain
Administrator group for that system.
• Client for Microsoft Networks is installed and enabled.
• Vulnerability and Patch Manager has share-level access to all target systems.
• Remote Registry Service is started.
• File and Printer Sharing protocol is installed and enabled.
• Default Administrative Shares are enabled.
• Server Service is started.
• Simple File Sharing is disabled.
• The Internet Connection Firewall is configured correctly or disabled, and the target system is configured
to respond to ping commands.
• The Computer Name/Domain network component is defined.
Windows XP
Verify that Simple File Sharing is disabled on Windows® XP Professional machines that are not part of a
domain. Simple File Sharing is enabled by default, disabling network access to Administrative shares on
the machine.
20 Troubleshooting
Page 21

Linux target systems
• TCP/IP network protocol is enabled.
• SSH is enabled and listening on the default port 22.
• Vulnerability and Patch Manager includes PuTTY SSH client and uses the plink session command and
PSCP secure copy, as well as SFTP secure file transfer commands. Both protocols 1.5 and 2.0 are
supported if they are correctly installed and functioning on the target system. To determine which
protocol is running, telnet to port 22 on the target system, read the return banner, and then press Enter.
• SSH-1.5—Only protocol 1.5 is supported.
• SSH-1.9—Protocol 1.5 and 2.0 are supported. Protocol 1.5 is attempted first.
• SSH-2.0—Only protocol 2.0 is supported, the newest and preferred session protocol.
Scan reports cannot be viewed
If scan reports cannot be viewed in .pdf format because Adobe Acrobat cannot be launched, perform the
following procedure:
1. From Internet Explorer, select Tools→Internet Options.
2. Click the Advanced tab, and then scroll to Security.
3. Clear the Do not save encrypted pages to disk option, and then click OK.
4. For more information, see http://support.microsoft.com/
default.aspx?scid=kb;en-us;812935&Product=ie600.
A scan was submitted but never started
All target systems scanned by Vulnerability and Patch Manager must have an IP address that appears in the
Systems Insight Manager console. If a scan is requested for a target system with no IP address, the scan
does not run and an internal error is generated. Be sure that all target systems being scanned have IP
addresses that appear in the Systems Insight Manager console.
Scan results are inaccurate because of overlapping tasks
Do not schedule patch acquisition tasks to run while vulnerability scans are running. Patch acquisition tasks
cause vulnerability scans to abort.
When scheduling vulnerability scans and patches, be sure the two processes do not overlap. Allow adequate
time for a vulnerability scan to complete before starting a patch. If a patch deployment runs during a
vulnerability scan, the scan results might be inaccurate or the target systems might reboot during the scan.
Current patch information is not displayed in scan reports
Scan definition updates are available a few days after the release of patches. You might have a patch in
your patch repository that does not appear in your scan results. You can apply the patch without a scan.
The VPM Patch Agent does not apply patches that are not appropriate. With the new patch reports, you
can also use the Validate VPM Patch Agent operation to determine where patches are needed. This operation
applies to patches only. The VPM Patch Agent does not report on non patch security vulnerabilities.
Patches
Patches fail to download with a timeout error
This error can occur when the internet connection speed is low. To work around this issue, do the following:
1. Locate the settings.xml file under \Program Files\HP\Systems Insight
Manager\hpwebadmin\webapps\ROOT\mxportal\VPM\config\ folder.
2. Locate the line <parameter name="timeout" value="xxxxxxx"/>.
3. Increase the timeout value. The timeout value is set in milliseconds
4. Restart Systems Insight Manager service and restart the acquire update task.
Patches 21
Page 22

VPM Patch Agent installation fails
The VPM Patch Agent is automatically deployed when systems are licensed to allow patches to be applied
to the systems. If a server type is identified as Unknown or Unmanaged with no identified operating system
in the Systems Insight Manager console, Vulnerability and Patch Manager automatically attempts to deploy
the VPM Patch Agent for Windows systems. The VPM Patch Agent deployment fails on Linux systems, and
event details display an error.
Be sure that the Red Hat library, compat libstdc++, is installed on Red Hat target systems.
The VPM Patch Agent installation can also fail because the WBEM credentials are not configured properly
to allow Vulnerability and Patch Manager to access target systems. For information about configuring WBEM
credentials, see the
HP Insight Software Installation and Configuration Guide
A patch acquisition was started, but no patches are visible
A patch acquisition can take quite a bit of time the first time it is run. It is not unusual for the acquisition to
take more than four hours, depending on how many operating systems are selected for download and the
speed of the Internet connection.
Progress of the acquisition can be monitored at:
<VPM_installation_folder>\Radia\IntegrationServer\logs\patch-acquire.log.
If the log file indicates that no patches are being acquired and there is a proxy server in the environment,
be sure you have properly configured Vulnerability and Patch Manager to access the proxy server by selecting
Options→Vulnerability and Patch Management→Settings. In addition, the proxy server must be
configured to allow both HTTP and FTP traffic.
If the patch-acquire.log is not being updated, the acquisition process might be hung. Search the
patch-acquire.log for the start of the last logged process id. Stop the nvdkit.exe with that process id running
on your Vulnerability and Patch Manager server. This action terminates the current acquisition and allows
the next acquisition to run.
HTTP 300 errors received during patch acquisition
Patch acquisition can generate events containing HTTP 300 errors for some older Microsoft patches, such
as:
Error downloading patch data for Bulletin MS02-050 at URL http://www.microsoft.com/technet/security/
bulletin/MS02-050.mspx.
.
22 Troubleshooting
Page 23

This message occurs because the Microsoft information pertaining to the patch location is incorrect and the
patch cannot be downloaded. HP is working to correct the metadata at the HP/Radia website for these older
patches, however this is ongoing maintenance. These corrections will automatically be downloaded each
time a patch acquisition is run. No updates are needed to Vulnerability and Patch Manager.
Patches appear in a scan report but are not successfully deployed
This can occur in the following situations:
• A vulnerability scan has identified vulnerabilities, patches were selected for deployment based on the
scan, and one or more of the selected patches were not located in the patch repository. Generally,
some of the patches will install successfully, while others do not install for an extended time. Patches
might not be available in the patch repository because all necessary operating systems were not selected
for patch acquisition, or only some patches have been acquired.
• The VPM Patch Agent has not been successfully installed on the system being patched.
• A patch deployment is attempted on a system for which the patch is not applicable. Vulnerability and
Patch Manager applies patches to target systems based on the operating system characteristics and
patch vulnerabilities. For example, a patch cannot be deployed when a Red Hat patch is selected for
deployment on a Windows target system.
Check for missing patches
Be sure that a patch acquisition has been selected for all operating systems in the server environment. Different
Microsoft patches can exist for each operating system associated with an advisory. To validate if a patch
has been acquired, click the advisory link to the operating system vendor. The patches for each operating
system are listed. Check the
<VPM_installation_folder>\Radia\IntegrationServer\Data\Patch\Microsoft\<bulletin
number> directory to verify that each patch has been acquired.
Check the file
<VPM_installation_folder>\Radia\IntegrationServer\Logs\patch-acquire.log for a
history of the last patch acquisition, including any errors. Patches downloaded through HTTP might have
been acquired successfully, but those requiring FTP are failing. If this occurs, validate the proxy and firewall
settings to be sure they are configured properly to enable FTP traffic.
Validating VPM Patch Agent installation
Check the Vulnerability and Patch Manager events to see if a successful Installed VPM Patch Agent event
exists for the system to be patched. If no event is present or if a Failed VPM Patch Agent Install event exists,
select Deploy→Vulnerability and Patch Manager→VPM Patch Agent to deploy the agent.
After the VPM Patch Agent installation and patch acquisition have been verified, reinitiate the patch installation
by selecting Deploy→Vulnerability and Patch Manager→Validate Installed Patches.
Patch installation status reports are not current or do not match information that appears in scan reports
Information that appears in patch reports is obtained during the most recent patch deployment task. If this
information is not current, update the patch installation status by validating installed patches.
Other tools report that a Windows system is patched, but Vulnerability and Patch Manager reports patches needed
Many other tools read the registry to determine if a patch is installed. In many cases, when a patch installation
fails, the registry is updated while the files remain unchanged. Vulnerability and Patch Manager verifies that
both the files and registry keys have been updated.
Patch source for vendor patches is Microsoft or Red Hat
To determine patch applicability, Vulnerability and Patch Manager might enhance patch detection criteria
to be more precise than vendor information. These patches appear with an asterisk in the Patch Source
column.
Patches 23
Page 24

Multiple events listed in Systems Insight Manager for patch deployments
Patch deployments create multiple events in Systems Insight Manager. There is a start event, a completion
event, and a patch current status event. The patch current status event evaluates the status of the patches
after the reboot has been completed.
STAT Scanner update error listed in the Systems Insight Manager event log
If STAT Scanner cannot access certain necessary files during a patch acquisition scanner update, a 3010
error appears in the Systems Insight Manager event log. The file update will be completed the next time a
reboot is performed.
Radia internal error listed in the Systems Insight Manager event log
A generic Radia internal error appears in the Systems Insight Manager event log if the patch repository is
viewed before a patch acquisition had been performed.
“Abuse of Service” error occurs when attempting to acquire Red Hat patches
The Red Hat network might be disabled if the network determines that patches have been acquired too
frequently. To resolve this issue, delete the registered system from the Red Hat network web interface at
https://rhn.redhat.com. Recreate the Red Hat credentials on the Red Hat server, and then copy to the
Vulnerability and Patch Manager server.
Validate Installed Patches event does not complete
Certain Vulnerability and Patch Manager events cannot complete successfully until after a system has been
scanned and patched at least one time. Be sure a system has been scanned and patched before attempting
to validate installed patches.
Systems Insight Manager integration
The Systems Insight Manager tool menus might not appear after a Vulnerability and Patch Manager installation
for any of the following reasons:
• The Systems Insight Manager user does not have appropriate privileges to access the menus. If a new
Systems Insight Manager user cannot view the Vulnerability and Patch Manager menus, be sure that
the user is authorized for All Tools or VPM Tools in Options→Security→Users and Authentication.
• A successful installation of Vulnerability and Patch Manager requires the user to have CMS administrative
privileges because changes are made to the Systems Insight Manager core and the tool menus.
• When installing Vulnerability and Patch Manager, you must use the credentials previously used when
installing Systems Insight Manager. Failure to do so results in an incorrect installation. Also, the user
name will not have appropriate privileges. Be sure the CMS user has privileges (toolbox and
authorizations) to use Vulnerability and Patch Manager. If the authorization is not correct, the menus
do not appear. To correct this issue, uninstall Vulnerability and Patch Manager and reinstall using the
correct credentials. Be sure that the CMS user that will be using Vulnerability and Patch Manager has
appropriate privileges. Privileges can include having authorization for a toolbox containing the
Vulnerability and Patch Manager tools.
• The Vulnerability and Patch Manager installation failed. Installation errors appear during installation
and in the log files.
24 Troubleshooting
Page 25

6 Support and other resources
Information to collect before contacting HP
Be sure to have the following information available before you contact HP:
• Software product name
• Hardware product model number
• Operating system type and version
• Applicable error message
• Third-party hardware or software
• Technical support registration number (if applicable)
How to contact HP
Use the following methods to contact HP technical support:
• In the United States, see the Customer Service / Contact HP United States website for contact options:
http://welcome.hp.com/country/us/en/contact_us.html
• In the United States, call 1-800-HP-INVENT (1-800-474-6836) to contact HP by telephone. This service
is available 24 hours a day, 7 days a week. For continuous quality improvement, conversations might
be recorded or monitored.
• In other locations, see the Contact HP Worldwide website for contact options:
http://welcome.hp.com/country/us/en/wwcontact.html
Registering for software technical support and update service
HP Insight software includes one year of 24 x 7 HP Software Technical Support and Update Service. This
service provides access to HP technical resources for assistance in resolving software implementation or
operations problems.
The service also provides access to software updates and reference manuals, either in electronic form or on
physical media as they are made available from HP. Customers who purchase an electronic license are
eligible for electronic updates only.
With this service, Insight software customers benefit from expedited problem resolution as well as proactive
notification and delivery of software updates. For more information about this service, see the following
website:
http://www.hp.com/services/insight
Registration for this service takes place following online redemption of the license certificate.
How to use your software technical support and update service
After you have registered, you will receive a service contract in the mail containing the Customer Service
phone number and your Service Agreement Identifier (SAID). You need your SAID when you contact technical
support. Using your SAID, you can also go to the Software Update Manager (SUM) web page at http://
www.itrc.hp.com to view your contract online and elect electronic delivery for product updates.
Warranty information
HP will replace defective delivery media for a period of 90 days from the date of purchase. This warranty
applies to all Insight software products.
Typographic conventions
Book Title
Linked Title
http://www.hp.com A Web site address that is a hyperlink to the site.
Title of a book or other document.
Title that is a hyperlink to a book or other document.
Information to collect before contacting HP 25
Page 26

Command Command name or qualified command phrase.
user input Commands and other text that you type.
computer output Text displayed by the computer.
Enter The name of a keyboard key. Note that Return and Enter both refer to the same
term Defined use of an important word or phrase.
variable The name of an environment variable, for example PATH or errno.
value A value that you may replace in a command or function, or information in a display
Related documents
In addition to this guide, the following resources are available:
•
HP Insight Vulnerability and Patch Manager software 6.0 Release Notes
•
HP Insight Vulnerability and Patch Manager software 6.0 Installation and Configuration Guide
key. A sequence such as Ctrl+A indicates that you must hold down the key labeled
Ctrl while pressing the A key.
that represents several possible values.
26 Support and other resources
Page 27

Index
F
features, 6
I
interface overview, 9
L
Linux target systems, 21
O
overview, 6
P
patch acquisition error, 21
process overview, 6
R
reinstalling Vulnerability and Patch Manager, 18, 20
S
scans
provided scans, 11
T
timeout error, 21
troubleshooting, 19
3010 error, 24
and Windows, 20
and Windows XP, 20
checking for missing patches, 23
HTTP 300 error, 22
multiple events, 24
overlapping tasks, 21
patch acquisition, 22
patch deployment, 23
patch information, 21
patch reports, 23
Radia internal error, 24
Red Hat patches, 24
reinstalling Vulnerability and Patch Manager, 18, 20
remaining files, 17, 20
scan results, 21
scans, 21
target system access, 20
target systems, 21
tool menus, 24
uninstalling Vulnerability and Patch Manager, 19
validation event, 24
VPM Patch Agent installation, 22, 23
vulnerability scans, 20
U
uninstalling, 17
uninstalling Vulnerability and Patch Manager, 19
27
 Loading...
Loading...