Page 1

User Manual
Unified Services Router
D-Link Corporation
Copyright © 2014
http://www.dlink.com
Page 2

Unified Services Router User Manual
User Manual
DSR-150 / 150N /250 / 250N / DSR-500 / 500N / 1000 / 1000N
D-Link Services Router
Version 1.09b
Copyright © 2014
Copyright Notice
This publication, including all photographs, illustrations and software, is protected under
international copyright laws, with all rights reserved. Neither this manual, nor any of the
material contained herein, may be reproduced without written consent of the author.
Disclaimer
The information in this document is subject to change without notice. The manufacturer makes
no representations or warranties with respect to the contents hereof and specifically disclaim
any implied warranties of merchantability or fitness for any particular purpose. The
manufacturer reserves the right to revise this publication and to make changes from time to
time in the content hereof without obligation of the manufacturer to notify any person of such
revision or changes.
Limitations of Liability
UNDER NO CIRCUMSTANCES SHALL D-LINK OR ITS SUPPLIERS BE LIABLE FOR
DAMAGES OF ANY CHARACTER (E.G. DAMAGES FOR LOSS OF PROFIT, SOFTWARE
RESTORATION, WORK STOPPAGE, LOSS OF SAVED DATA OR ANY OTHER
COMMERCIAL DAMAGES OR LOSSES) RESULTING FROM THE APPLICATION OR
IMPROPER USE OF THE D-LINK PRODUCT OR FAILURE OF THE PRODUCT, EVEN IF
D-LINK IS INFORMED OF THE POSSIBILITY OF SUCH DAMAGES. FURTHERMORE, DLINK WILL NOT BE LIABLE FOR THIRD-PARTY CLAIMS AGAINST CUSTOMER FOR
LOSSES OR DAMAGES. D-LINK WILL IN NO EVENT BE LIABLE FOR ANY DAMAGES
IN EXCESS OF THE AMOUNT D-LINK RECEIVED FROM THE END-USER FOR THE
PRODUCT.
1
Page 3

Unified Services Router User Manual
Table of Contents
Chapter 1. Introduction ........................................................................................................................... 11
1.1 About this User Manual .......................................................................................... 12
1.2 Typographical Conventions ................................................................................... 12
Chapter 2. Configuring Your Network: LAN Setup ............................................................................. 13
2.1 LAN Configuration................................................................................................... 13
2.1.1 LAN DHCP Reserved IPs ...................................................................................... 16
2.1.2 LAN DHCP Leased Clients.................................................................................... 18
2.1.3 LAN Configuration in an IPv6 Network ................................................................ 18
2.1.4 Configuring IPv6 Router Advertisements ............................................................ 21
2.2 VLAN Configuration ................................................................................................ 24
2.2.1 Associating VLANs to ports ................................................................................... 25
2.2.2 Multiple VLAN Subnets .......................................................................................... 27
2.2.3 VLAN configuration ................................................................................................. 28
2.3 Configurable Port: DMZ Setup .............................................................................. 29
2.4 Universal Plug and Play (UPnP) ........................................................................... 30
2.5 Captive Portal .......................................................................................................... 32
2.5.1 Captive Portal Setup ............................................................................................... 32
2.5.2 Captive Portals on a VLAN .................................................................................... 35
Chapter 3. Connecting to the Internet: WAN Setup ........................................................................... 36
3.1 Internet Setup Wizard ............................................................................................. 36
3.2 WAN Configuration ................................................................................................. 37
3.2.1 WAN Port IP address ............................................................................................. 37
3.2.2 WAN DNS Servers ................................................................................................. 38
3.2.3 DHCP WAN ............................................................................................................. 38
3.2.4 PPPoE ...................................................................................................................... 38
3.2.5 Russia L2TP and PPTP WAN ............................................................................... 41
3.2.6 Russia Dual Access PPPoE .................................................................................. 42
3.2.7 WAN Configuration in an IPv6 Network ............................................................... 43
3.2.8 Checking WAN Status ............................................................................................ 45
3.3 Bandwidth Controls................................................................................................. 46
3.3.1 Bandwidth Controls in Bridge Mode ..................................................................... 49
3.4 Features with Multiple WAN Links ........................................................................ 50
3.4.1 Auto Failover ............................................................................................................ 51
3.4.2 Load Balancing ........................................................................................................ 51
3.4.3 Protocol Bindings .................................................................................................... 53
3.4.4 IP Aliasing ................................................................................................................ 54
3.5 Routing Configuration ............................................................................................. 56
3.5.1 Routing Mode .......................................................................................................... 56
3.5.2 Dynamic Routing (RIP) .......................................................................................... 58
3.5.3 Static Routing .......................................................................................................... 59
3.5.4 OSPFv2 .................................................................................................................... 60
3.5.5 OSPFv3 .................................................................................................................... 62
3.5.6 6to4 Tunneling ......................................................................................................... 64
3.5.7 ISATAP Tunnels ...................................................................................................... 65
3.6 Configurable Port - WAN Option .......................................................................... 65
3.7 WAN 3 (3G) Configuration ..................................................................................... 66
2
Page 4

Unified Services Router User Manual
3.8 WAN Port Settings .................................................................................................. 68
Chapter 4. Wireless Access Point Setup ............................................................................................. 70
4.1 Wireless Settings Wizard ....................................................................................... 70
4.1.1 Wireless Network Setup Wizard ........................................................................... 71
4.1.2 Add Wireless Device with WPS ............................................................................ 71
4.1.3 Manual Wireless Network Setup........................................................................... 72
4.2 Wireless Profiles ..................................................................................................... 72
4.2.1 WEP Security .......................................................................................................... 73
4.2.2 WPA or WPA2 with PSK ........................................................................................ 74
4.3 Creating and Using Access Points ....................................................................... 74
4.3.1 Primary benefits of Virtual APs: ............................................................................ 76
4.4 Tuning Radio Specific Settings ............................................................................. 77
4.5 WMM ......................................................................................................................... 77
4.6 Wireless distribution system (WDS) ..................................................................... 78
4.7 Advanced Wireless Settings.................................................................................. 80
4.8 Wi-Fi Protected Setup (WPS) ............................................................................... 81
Chapter 5. Securing the Private Network ............................................................................................ 83
5.1 Firewall Rules .......................................................................................................... 83
5.2 Defining Rule Schedules........................................................................................ 84
5.3 Configuring Firewall Rules ..................................................................................... 85
5.4 Configuring IPv6 Firewall Rules ............................................................................ 90
5.4.1 Firewall Rule Configuration Examples ................................................................. 91
5.5 Security on Custom Services ................................................................................ 95
5.6 ALG support ............................................................................................................. 98
5.7 VPN Passthrough for Firewall ............................................................................... 99
5.8 Bridge Mode Firewall ............................................................................................ 100
5.9 Application Rules .................................................................................................. 102
5.10 Web Content Filtering ........................................................................................... 103
5.10.1 Content Filtering ................................................................................................ .... 103
5.10.2 Approved URLs ..................................................................................................... 104
5.10.3 Blocked Keywords ................................................................................................ 105
5.10.4 Export Web Filter .................................................................................................. 106
5.11 IP/MAC Binding ..................................................................................................... 107
5.12 Intrusion Prevention (IPS).................................................................................... 108
5.13 Protecting from Internet Attacks ......................................................................... 109
5.14 IGMP Proxy to manage multicast traffic ............................................................ 111
Chapter 6. IPsec / PPTP / L2TP VPN ................................................................................................ 113
6.1 VPN Wizard ........................................................................................................... 115
6.2 Configuring IPsec Policies ................................................................................... 117
6.2.1 Extended Authentication (XAUTH) ..................................................................... 121
6.2.2 Internet over IPsec tunnel .................................................................................... 122
6.3 Configuring VPN clients ....................................................................................... 122
6.4 PPTP / L2TP Tunnels ........................................................................................... 122
6.4.1 PPTP Tunnel Support .......................................................................................... 122
3
Page 5

Unified Services Router User Manual
6.4.2 L2TP Tunnel Support ........................................................................................... 124
6.5 GRE Tunnel Support ............................................................................................ 127
6.6 OpenVPN Support ................................................................................................ 128
6.6.1 OpenVPN Remote Network ................................................................................ 130
6.6.2 OpenVPN Authentication ..................................................................................... 131
Chapter 7. SSL VPN ............................................................................................................................. 133
7.1 Groups and Users ................................................................................................. 135
7.1.1 Users and Passwords .......................................................................................... 141
7.1.2 Adding many users to the Local User Database .............................................. 142
7.2 Using SSL VPN Policies ...................................................................................... 143
7.2.1 Using Network Resources ................................................................................... 146
7.3 Application Port Forwarding ................................................................................ 147
7.4 SSL VPN Client Configuration ............................................................................ 149
7.5 User Portal ............................................................................................................. 152
7.5.1 Creating Portal Layouts ....................................................................................... 152
Chapter 8. Advanced Configuration Tools ......................................................................................... 155
8.1 USB Device Setup ................................................................................................ 155
8.2 USB share port ...................................................................................................... 156
8.3 SMS service ........................................................................................................... 158
8.4 External Authentication ........................................................................................ 159
8.4.1 POP3 Server .......................................................................................................... 159
8.4.2 NT Domain Server ................................................................................................ 161
8.4.3 RADIUS Server ..................................................................................................... 162
8.4.4 Active Directory Server ........................................................................................ 165
8.4.5 LDAP Server .......................................................................................................... 166
8.5 Authentication Certificates ................................................................................... 167
8.6 Advanced Switch Configuration .......................................................................... 169
8.7 Package Manager ................................................................................................. 169
Chapter 9. Administration & Management ......................................................................................... 173
9.1 Configuration Access Control .............................................................................. 173
9.1.1 Admin Settings ...................................................................................................... 173
9.1.2 Remote Management ........................................................................................... 174
9.1.3 CLI Access ............................................................................................................. 175
9.2 SNMP Configuration ............................................................................................. 175
9.3 Configuring Time Zone and NTP ........................................................................ 177
9.4 Log Configuration .................................................................................................. 178
9.4.1 Defining What to Log ............................................................................................ 178
9.4.2 Sending Logs to E-mail or Syslog ...................................................................... 183
9.4.3 Event Log Viewer in GUI...................................................................................... 185
9.5 Backing up and Restoring Configuration Settings ........................................... 186
9.6 Generating DBGLOGs ......................................................................................... 188
9.7 Upgrading Router Firmware ................................................................................ 188
9.8 Upgrading Router Firmware via USB................................................................. 189
9.9 Dynamic DNS Setup ............................................................................................. 190
9.10 Using Diagnostic Tools ........................................................................................ 191
4
Page 6

Unified Services Router User Manual
9.10.1 Ping ......................................................................................................................... 192
9.10.2 Trace Route ........................................................................................................... 192
9.10.3 DNS Lookup .......................................................................................................... 193
9.10.4 Router Options ...................................................................................................... 193
9.11 Localization ............................................................................................................ 194
Chapter 10. Router Status and Statistics ............................................................................................. 195
10.1 System Overview .................................................................................................. 195
10.1.1 Device Status ........................................................................................................ 195
10.1.2 Resource Utilization .............................................................................................. 197
10.2 Traffic Statistics ..................................................................................................... 200
10.2.1 Wired Port Statistics ............................................................................................. 200
10.2.2 Wireless Statistics ................................................................................................. 201
10.3 Active Connections ............................................................................................... 202
10.3.1 Sessions through the Router ............................................................................... 202
10.3.2 Wireless Clients..................................................................................................... 204
10.3.3 LAN Clients ............................................................................................................ 204
10.3.4 Active VPN Tunnels .............................................................................................. 205
Chapter 11. Trouble Shooting ................................................................................................................ 207
11.1 Internet connection ............................................................................................... 207
11.2 Date and time ........................................................................................................ 209
11.3 Pinging to Test LAN Connectivity ....................................................................... 209
11.3.1 Testing the LAN path from your PC to your router .......................................... 209
11.3.2 Testing the LAN path from your PC to a remote device ................................. 210
11.4 Restoring factory-default configuration settings ............................................... 211
Chapter 12. Credits ................................................................................................................................. 213
Appendix A. Glossary .............................................................................................................................. 214
Appendix B. Factory Default Settings ................................................................................................... 217
Appendix C. Standard Services Available for Port Forwarding & Firewall Configuration .............. 218
Appendix D. Log Output Reference ....................................................................................................... 219
Appendix E. RJ-45 Pin-outs .................................................................................................................... 273
Appendix F. Product Statement ............................................................................................................. 274
5
Page 7

Unified Services Router User Manual
List of Figures
Figure 1: Setup page for LAN TCP/IP settings ...................................................................................... 16
Figure 2: LAN DHCP Reserved IPs ......................................................................................................... 17
Figure 3: LAN DHCP Leased Clients ...................................................................................................... 18
Figure 4: IPv6 LAN and DHCPv6 configuration ..................................................................................... 20
Figure 5: Configuring the Router Advertisement Daemon ................................................................... 23
Figure 6: IPv6 Advertisement Prefix settings ......................................................................................... 24
Figure 7: Adding VLAN memberships to the LAN ................................................................................. 25
Figure 8: Port VLAN list ............................................................................................................................. 26
Figure 9: Configuring VLAN membership for a port .............................................................................. 27
Figure 10: Multiple VLAN Subnets ........................................................................................................... 28
Figure 11: VLAN Configuration ................................................................................................ ................. 29
Figure 12: DMZ configuration ................................................................................................................... 30
Figure 13: UPnP Configuration ................................................................................................ ................. 31
Figure 14: Active Runtime sessions ........................................................................................................ 32
Figure 15: Captive Portal Profile List ....................................................................................................... 33
Figure 16: Customized Captive Portal Setup ......................................................................................... 34
Figure 17: Blocking specific clients by their MAC address ................................................................... 35
Figure 18: VLAN based configuration of Captive Portals ..................................................................... 35
Figure 19: Internet Connection Setup Wizard ........................................................................................ 36
Figure 20: Manual WAN configuration................................ ................................................................ ..... 38
Figure 21: PPPoE configuration for standard ISPs ............................................................................... 39
Figure 22: WAN configuration for Japanese Multiple PPPoE (part 1) ................................................ 40
Figure 23: WAN configuration for Japanese Multiple PPPoE (part 2) ................................................ 41
Figure 24: Russia L2TP ISP configuration .............................................................................................. 42
Figure 25: Russia Dual access PPPoE configuration ........................................................................... 43
Figure 27: IPv6 WAN Setup page ............................................................................................................ 44
Figure 28: Connection Status information for both WAN ports ............................................................ 46
Figure 29: List of Configured Bandwidth Profiles ................................................................................... 47
Figure 30: Bandwidth Profile Configuration ............................................................................................ 48
Figure 31: Traffic Selector Configuration ................................................................................................ 49
Figure 32: Bridge Bandwidth Profile Configuration ................................................................................ 50
Figure 33: Bridge Traffic Selector Configuration .................................................................................... 50
Figure 34: Load Balancing is available when multiple WAN ports are configured and Protocol
Bindings have been defined ................................................................................................... 53
6
Page 8

Unified Services Router User Manual
Figure 35: Protocol binding setup to associate a service and/or LAN source to a WAN and/or
destination network .................................................................................................................. 54
Figure 36: Configuring the IP Alias .......................................................................................................... 55
Figure 37: IP Alias Configuration................................ ................................................................ .............. 55
Figure 38: Routing Mode to determine traffic routing between WAN and LAN ................................. 57
Figure 39: Static route configuration fields ............................................................................................. 60
Figure 40: OSPFv2 configured parameters ............................................................................................ 61
Figure 41: OSPFv2 configuration ............................................................................................................. 62
Figure 42: OSPFv3 configured parameters ............................................................................................ 63
Figure 43: OSPFv3 configuration ............................................................................................................. 64
Figure 44: 6 to 4 tunneling ......................................................................................................................... 64
Figure 45: ISATAP Tunnels Configuration .............................................................................................. 65
Figure 46: WAN3 configuration for 3G internet ...................................................................................... 67
Figure 47: Physical WAN port settings .................................................................................................... 69
Figure 48: Wireless Network Setup Wizards ................................ ................................ .......................... 71
Figure 49: List of Available Profiles shows the options available to secure the wireless link ......... 73
Figure 50: Profile configuration to set network security ........................................................................ 74
Figure 51: Virtual AP configuration .......................................................................................................... 75
Figure 52: List of configured access points (Virtual APs) shows one enabled access point on the
radio, broadcasting its SSID ................................................................................................... 76
Figure 53: Radio card configuration options ........................................................................................... 77
Figure 54: Wi-Fi Multimedia ...................................................................................................................... 78
Figure 55: Wireless Distribution System ................................................................................................. 79
Figure 56: Advanced Wireless communication settings ....................................................................... 81
Figure 57: WPS configuration for an AP with WPA/WPA2 profile ....................................................... 82
Figure 58: List of Available Firewall Rules .............................................................................................. 84
Figure 59: List of Available Schedules to bind to a firewall rule .......................................................... 85
Figure 60: Example where an outbound SNAT rule is used to map an external IP address
(209.156.200.225) to a private DMZ IP address (10.30.30.30) ........................................ 88
Figure 61: The firewall rule configuration page allows you to define the To/From zone, service,
action, schedules, and specify source/destination IP addresses as needed. ................. 89
Figure 62: The IPv6 firewall rule configuration page allows you to define the To/From zone,
service, action, schedules, and specify source/destination IP addresses as needed. .. 90
Figure 63: List of Available IPv6 Firewall Rules ..................................................................................... 91
Figure 64: Schedule configuration for the above example. .................................................................. 94
Figure 65: List of user defined services. ................................................................................................. 97
Figure 66: Custom Services configuration .............................................................................................. 97
7
Page 9

Unified Services Router User Manual
Figure 67: Available ALG support on the router..................................................................................... 99
Figure 68: Passthrough options for VPN tunnels ................................................................................. 100
Figure 69: List of Available Application Rules showing 4 unique rules ............................................ 103
Figure 70: Content Filtering used to block access to proxy servers and prevent ActiveX controls
from being downloaded ......................................................................................................... 104
Figure 71: Two trusted domains added to the Approved URLs List ................................................. 105
Figure 72: One keyword added to the block list ................................................................................... 106
Figure 73: Export Approved URL list ..................................................................................................... 107
Figure 74: The following example binds a LAN host’s MAC Address to an IP address served by
DSR. If there is an IP/MAC Binding violation, the violating packet will be dropped and
logs will be captured .............................................................................................................. 108
Figure 75: Intrusion Prevention features on the router ....................................................................... 109
Figure 76: Protecting the router and LAN from internet attacks ........................................................ 110
Figure 77: Enabling IGMP Proxy for the LAN ....................................................................................... 112
Figure 78: Example of Gateway-to-Gateway IPsec VPN tunnel using two DSR routers connected
to the Internet .......................................................................................................................... 113
Figure 79: Example of three IPsec client connections to the internal network through the DSR
IPsec gateway ........................................................................................................................ 114
Figure 80: VPN Wizard launch screen .................................................................................................. 115
Figure 81: IPsec policy configuration ..................................................................................................... 118
Figure 82: IPsec policy configuration continued (Auto policy via IKE) .............................................. 119
Figure 83: IPsec policy configuration continued (Auto / Manual Phase 2)....................................... 121
Figure 84: PPTP tunnel configuration – PPTP Client .......................................................................... 123
Figure 85: PPTP VPN connection status .............................................................................................. 123
Figure 86: PPTP tunnel configuration – PPTP Server ........................................................................ 124
Figure 87: L2TP tunnel configuration – L2TP Server .......................................................................... 126
Figure 88: L2TP tunnel configuration – L2TP Client ........................................................................... 127
Figure 89: GRE Tunnel configuration .................................................................................................... 128
Figure 90: OpenVPN configuration ........................................................................................................ 130
Figure 91: OpenVPN Remote Network ................................................................................................. 131
Figure 92: OpenVPN Authentication ...................................................................................................... 132
Figure 93: Example of clientless SSL VPN connections to the DSR ................................................ 134
Figure 94: List of groups .......................................................................................................................... 135
Figure 95: User group configuration ...................................................................................................... 136
Figure 96: SSLVPN Settings ................................................................................................................... 137
Figure 97: Group login policies options ................................................................................................ . 138
Figure 98: Browser policies options ....................................................................................................... 139
8
Page 10

Unified Services Router User Manual
Figure 99: IP policies options .................................................................................................................. 140
Figure 100: Available Users with login status and associated Group ............................................... 141
Figure 101: User configuration options ................................................................................................. 142
Figure 102: Import a CSV file with multiple users to the User Database ......................................... 142
Figure 103: List of SSL VPN polices (Global filter) .............................................................................. 144
Figure 104: SSL VPN policy configuration ............................................................................................ 145
Figure 105: List of configured resources, which are available to assign to SSL VPN policies ..... 147
Figure 106: List of Available Applications for SSL Port Forwarding.................................................. 149
Figure 107: SSL VPN client adapter and access configuration ......................................................... 150
Figure 108: Configured client routes only apply in split tunnel mode ............................................... 151
Figure 109: List of configured SSL VPN portals. The configured portal can then be associated
with an authentication domain .............................................................................................. 152
Figure 110: SSL VPN Portal configuration ........................................................................................... 154
Figure 111: USB Device Detection ........................................................................................................ 156
Figure 112: USB SharePort .................................................................................................................... 157
Figure 113: SMS Service – Send SMS ................................................................................................. 158
Figure 114: SMS Service – Receive SMS ............................................................................................ 159
Figure 115: POP3 Authentication Server configuration ...................................................................... 160
Figure 116: POP3 CA file upload ........................................................................................................... 161
Figure 117: NT Domain Authentication Server configuration ............................................................. 162
Figure 118: RADIUS Server configuration ............................................................................................ 164
Figure 119: Active Directory Authentication Server configuration ..................................................... 165
Figure 120: LDAP Authentication Server configuration ...................................................................... 166
Figure 121: Certificate summary for IPsec and HTTPS management ............................................. 168
Figure 122: Advanced Switch Settings .................................................................................................. 169
Figure 123: Device Drivers ...................................................................................................................... 170
Figure 124: Installation of driver/language pack .................................................................................. 171
Figure 125: Selection of Installed Language ........................................................................................ 172
Figure 126: User Login policy configuration ......................................................................................... 173
Figure 127: Admin Settings ..................................................................................................................... 174
Figure 128: Remote Management from the WAN ............................................................................... 175
Figure 129: SNMP Users, Traps, and Access Control ........................................................................ 176
Figure 130: SNMP system information for this router ......................................................................... 177
Figure 131: Date, Time, and NTP server setup ................................................................................... 178
Figure 132: Facility settings for Logging ............................................................................................... 180
Figure 133: Log configuration options for traffic through router ......................................................... 182
9
Page 11

Unified Services Router User Manual
Figure 134: IPv6 Log configuration options for traffic through router ................................................ 183
Figure 135: E-mail configuration as a Remote Logging option .......................................................... 184
Figure 136: Syslog server configuration for Remote Logging (continued) ................................ ....... 185
Figure 137: VPN logs displayed in GUI event viewer ......................................................................... 186
Figure 138: Restoring configuration from a saved file will result in the current configuration being
overwritten and a reboot ....................................................................................................... 187
Figure 139: Firmware version information and upgrade option ......................................................... 189
Figure 140: Firmware upgrade and configuration restore/backup via USB ..................................... 190
Figure 141: Dynamic DNS configuration ............................................................................................... 191
Figure 142: Router diagnostics tools available in the GUI ................................................................. 192
Figure 143: Sample trace route output .................................................................................................. 193
Figure 144: Localization........................................................................................................................... 194
Figure 145: Device Status display .......................................................................................................... 196
Figure 146: Device Status display (continued) ..................................................................................... 197
Figure 147: Resource Utilization statistics ............................................................................................ 198
Figure 148: Resource Utilization data (continued) .............................................................................. 199
Figure 149: Resource Utilization data (continued) .............................................................................. 200
Figure 150: Physical port statistics ........................................................................................................ 201
Figure 151: AP specific statistics ............................................................................................................ 202
Figure 152: List of current Active Firewall Sessions ............................................................................ 203
Figure 153: List of connected 802.11 clients per AP ........................................................................... 204
Figure 154: List of LAN hosts ................................................................................................................. 205
Figure 155: List of current Active VPN Sessions ................................................................................. 206
10
Page 12

Unified Services Router User Manual
Chapter 1. Introduction
D-Link Services Routers offer a secure, high performance networking solution to
address the growing needs of small and medium businesses. Integrated high-speed IEEE
802.11n and 3G wireless technologies offer comparable performance to traditional
wired networks, but with fewer limitations. Optimal network security is provided via
features such as virtual private network (VPN) tunnels, IP Security ( IPsec), Point-toPoint Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), and Secure
Sockets Layer (SSL). Empower your road warriors with clientless remote access
anywhere and anytime using SSL VPN tunnels.
With the D-Link Services Router you are able to experience a diverse set of benefits:
Comprehensive Management Capabilities
The DSR-500, DSR-500N, DSR-1000 and DSR-1000N include dual-WAN
Gigabit Ethernet which provides policy-based service management ensuring
maximum productivity for your business operations. The failover feature
maintains data traffic without disconnecting when a landline connection is lost.
The Outbound Load Balancing feature adjusts outgoing traffic across two WAN
interfaces and optimizes the system performance resulting in high availability.
The solution supports configuring a port as a dedicated DMZ port allowing you
to isolate servers from your LAN.
DSR-150/150N/250/250N producst have a single WAN interface, and thus it does
not support Auto Failover and Load Balancing scenarios.
Superior Wireless Performance
Designed to deliver superior wireless performance, the DSR -500N and DSR1000N include 802.11 a/b/g/n support, allowing for operation on either the 2.4
GHz or 5 GHz radio bands. Multiple In Multiple Out (MIMO) technology
allows the DSR-500N and DSR-1000N to provide high data rates with minimal
“dead spots” throughout the wireless coverag e area.
DSR-150N, DSR-250N and DSR-500N support the 2.4GHz radio band only.
Flexible Deployment Options
The DSR-1000 / 1000N supports Third Generation (3G) Networks via an
extendable USB 3G dongle. This 3G network capability offers an additional
secure data connection for networks that provide critical services. The DSR1000N can be configured to automatically switch to a 3G network whenever a
physical link is lost.
Robust VPN features
A fully featured virtual private network (VPN) provides your mobile workers
and branch offices with a secure link to your network. The DSR150/150N/250/250N, DSR-500/500N and DSR-1000 /1000N are capable of
simultaneously managing 5, 5, 10, 20 Secure Sockets Layer (SSL) VPN tunnels
respectively, empowering your mobile users by providing remote access to a
central corporate database. Site-to-site VPN tunnels use IP Security (IPsec)
Protocol, Point-to-Point Tunneling Protocol (PPTP), or Layer 2 Tunneling
11
Page 13

Unified Services Router User Manual
Protocol (L2TP) to facilitate branch office connectivity through encrypted
virtual links. The DSR-150/150N, DSR-250/250N, DSR-500/500N and DSR-
1000/1000N support 10, 25, 35 and 75 simultaneous IPsec VPN tunnels
respectively.
Efficient D-Link Green Technology
As a concerned member of the global community, D-Link is devoted to
providing eco-friendly products. D-Link Green Wi-Fi and D-Link Green
Ethernet save power and prevent waste. The D-Link Green WLAN scheduler
reduces wireless power automatically during off-peak hours. Likewise the DLink Green Ethernet program adjusts power usage based on the detected cable
length and link status. In addition, compliance with RoHS (Restriction of
Hazardous Substances) and WEEE (Waste Electrical and Electronic Equipment)
directives make D-Link Green certified devices the environmentally responsible
choice.
Support for the 3G wireless WAN USB dongle is only available for DSR-1000 and
DSR-1000N.
1.1 About this User Manual
This document is a high level manual to allow new D-Link Services Router users to
configure connectivity, setup VPN tunnels, establish firewall rules and perform
general administrative tasks. Typical deployment and use case scenarios are described
in each section. For more detailed setup instructions and explanations of each
configuration parameter, refer to the online help that can be accessed from each page
in the router GUI.
1.2 Typographical Conventions
The following is a list of the various terms, followed by an example of how that term
is represented in this document:
Product Name – D-Link Services Router.
o Model numbers DSR-500/500N/1000/1000N/250/250N/150/150N
GUI Menu Path/GUI Navigation – Monitoring > Router Status
Important note –
12
Page 14

Chapter 2. Configuring Your Network: LAN Setup
It is assumed that the user has a machine for management connected to the LAN to the router. The LAN
connection may be through the wired Ethernet ports available on the router, or once the initial setup is
complete, the DSR may also be managed through its wireless interface as it is bridged with the LAN.
Access the router ’s graphical user interface (GUI) for management by using any web browser, such as
Microsoft Internet Explorer or Mozilla Firefox:
Go to http://192.168.10.1 (default IP address) to d isplay the ro uter’s management login screen.
Default login credentials for the management GUI:
Username: admin
Password: admin
If the ro uter’s LAN IP address was c ha nged, use that IP address in the navigation bar of the browser to
access the router’s management UI.
2.1 LAN Configuration
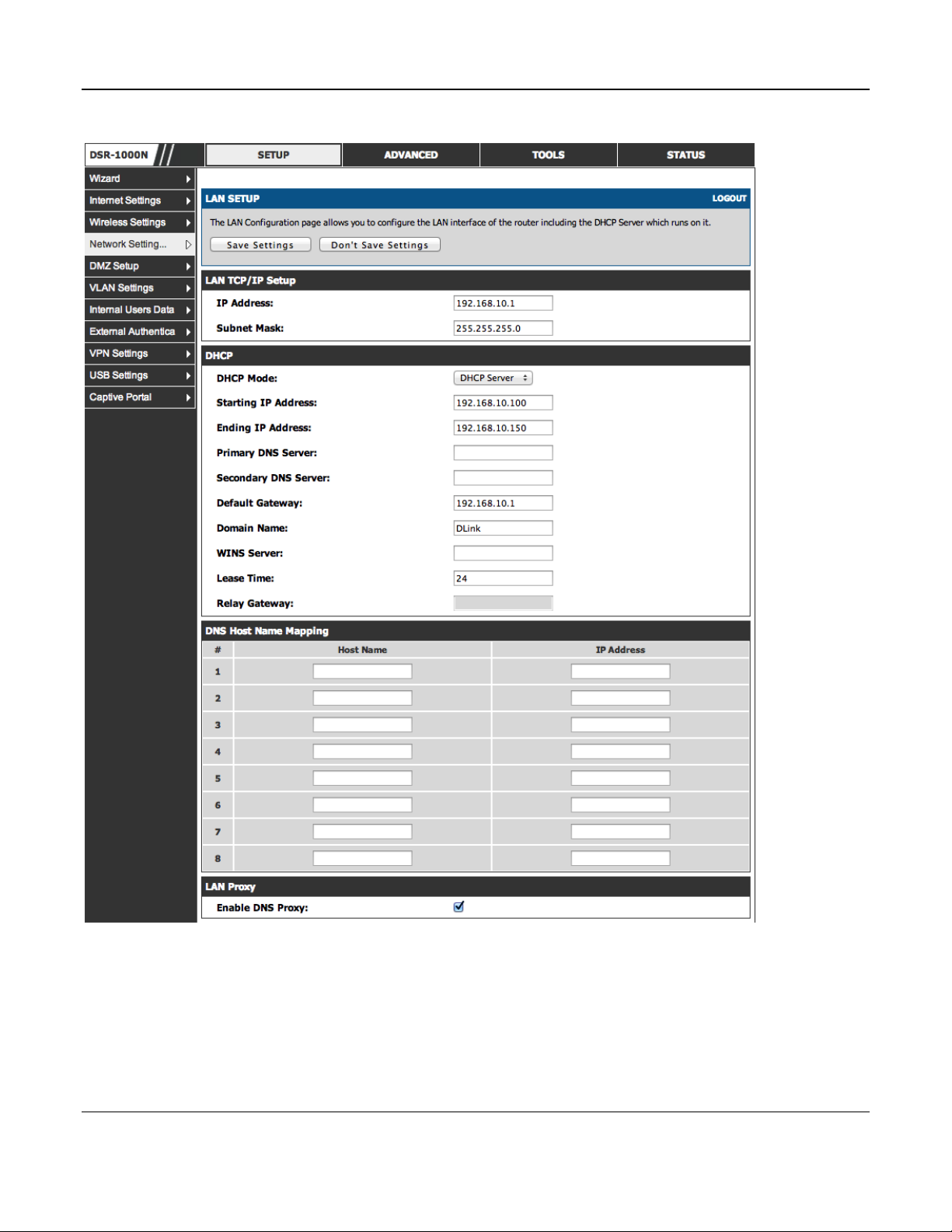
Setup > Network Settings > LAN Configuration
By default, the router functions as a Dynamic Host Configuration Protocol (DHCP) server to the hosts
on the WLAN or LAN network. With DHCP, PCs and other LAN devices can be assigned IP
addresses as well as addresses for DNS servers, Windows Internet Name Service (WINS) servers, and
the default gateway. With the DHCP server enabled the router’s IP address ser ves as th e gateway
address for LAN and WLAN clients. The PCs in the LAN are assigned IP addresses from a pool of
addresses specified in this procedure. Each pool address is tested before it is assigned to avoid
duplicate addresses on the LAN.
For most applications the default DHCP and TCP/IP settings are satisfactory. If you want another PC
on your network to be the DHCP server or if you are manually configuring the network settings of all
of your PCs, set the DHCP mode to ‘none’. DHCP relay can be used to forward DHCP lease
information from another LAN device tha t is the net work’s DHCP server; t hi s is particularl y useful
for wireless clients.
Instead of using a DNS server, you can use a Windows Internet Naming Service (WINS) server. A
WINS server is the equivalent of a DNS server but uses the NetBIOS protocol to resolve hostnames.
The router includes the WINS server IP address in the DHCP configuration when acknowledging a
DHCP request from a DHCP client.
You can also enable DNS proxy for the LAN. When this is enabled the router then as a proxy for all
DNS requests and communicate s with the ISP’s DNS servers. W hen disabled all DHCP clients recei ve
the DNS IP addresses of the ISP.
To configure LAN Connectivity, please follow the steps below:
1. In the LAN Setup page, enter the following information for your router:
IP address (factory default: 192.168.10.1).
Page 15

Unified Services Router User Manual
If you change the IP address and click Save Settings, the GUI will not respond. Open a new connection
to the new IP address and log in again. Be sure the LAN host (the machine used to manage the router)
has obtained IP address from newly assigned pool (or has a sta tic IP address in the ro uter’s LAN
subnet) before accessing the router via changed IP address.
Subnet mask (factory default: 255.255.255.0).
2. In the DHCP section, select the DHCP mode:
None: the router’s DHCP server is disabled for the LAN
DHCP Server. With this option the router assigns an IP address within the specified range
plus additional specified information to any LAN device that requests DHCP served
addresses.
DHCP Relay: With this option enabled, DHCP clients on the LAN can receive IP address
leases and corresponding information from a DHCP server on a different subnet. Specify
the Relay Gateway, and when LAN clients make a DHCP request it will be passed along to
the server accessible via the Relay Gateway IP address.
If DHCP is being enabled, enter the following DHCP server parameters:
Starting and Ending IP Addresses: Enter the first and last continuous addresses in the IP
address pool. Any new DHCP client joining the LAN is assigned an IP address in this
range. The default starting address is 192.168.10.2. The default ending address is
192.168.10.100. These addresse s shou ld be in the same IP address subnet as the router’s
LAN IP address. You may wish to save part of the subnet range for devices with statically
assigned IP addresses in the LAN.
Primary and Secondary DNS servers: If configured domain name system (DNS) servers are
available on the LAN enter their IP addresses here.
Default Gateway: By default this setting has the router’s LAN IP address. It can be
customized to any valid IP within the LAN sub ne t, in the e vent that the network’s gateway
is not this router. In this case the DHCP server will give the configured IP address as the
Default Gateway to its DHCP clients.
Domain Name: This is the network domain name used for identification.
WINS Server (optional): Enter the IP address for the WINS server or, if present in your
network, the Windows NetBIOS server.
Lease Time: Enter the time, in hours, for which IP addresses are leased to clients.
Relay Gateway: Enter the gateway address. This is the only configuration parameter
required in this section when DHCP Relay is selected as its DHCP mode
3. In the DNS Host Name Mapping section:
14
Page 16

Unified Services Router User Manual
Host Name: Provide a valid host name
IP address: Provide the IP address of the host name,
4. In the LAN proxy section:
Enable DNS Proxy: To enable the router to act as a proxy for all DNS requests and
co mmunicate with the ISP’s DNS servers, cl ic k the checkbo x.
5. Click Save Settings to apply all changes.
15
Page 17
Unified Services Router User Manual
Figure 1: Setup page for LAN TCP/IP settings
2.1.1 LAN DHCP Reserved IPs
Setup > Network Settings > LAN DHCP Reserved IPs
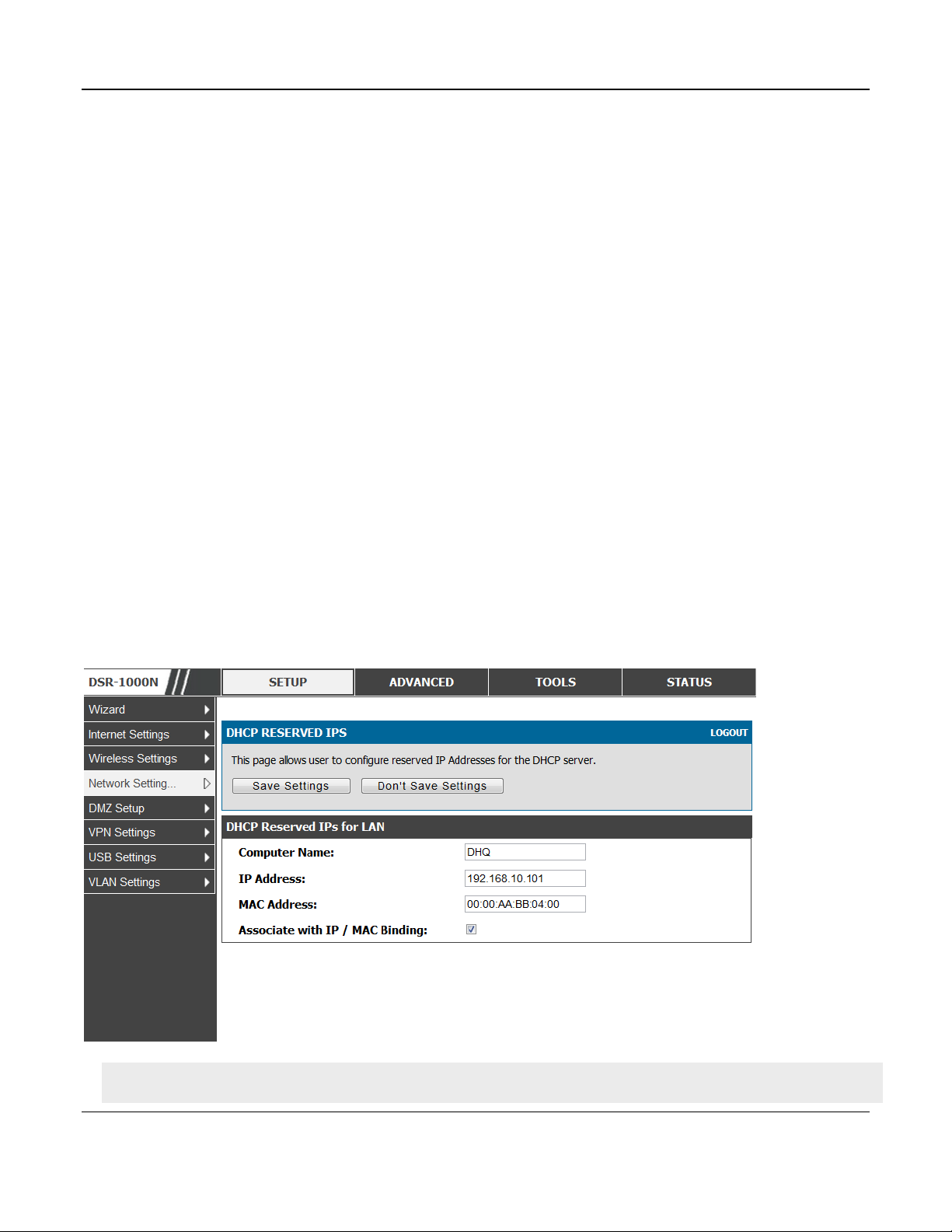
The router’s DHCP server can assign TCP/IP configurations to computers in the LAN explicitly by
adding client's network interface hardware address and the IP address to be assigned to that client in
DHCP server's database. Whenever DHCP server receives a request from client, hardware address of
16
Page 18
Unified Services Router User Manual
that client is compared with the hardware address list present in the database, if an IP address is
already assigned to that computer or device in the database , the customized IP address is configured
otherwise an IP address is assigned to the client automatically from the DHCP pool.
Computer Name: The user defined name for the LAN host.
IP Addresses: The LAN IP address of a host that is reserved by the DHCP server.
MAC Addresses: The MAC address that will be assigned the reserved IP address when it is on the
LAN.
Associate with IP/MAC Binding: When the user enables this option the Computer Name, IP and
MAC addresses are associated with the IP/MAC binding.
The actions that can be taken on list of reserved IP addresses are:
Select: Selects all the reserved IP addresses in the list.
Edit: Opens the LAN DHCP Reserved IP Configuration page to edit the selected binding rule.
Delete: Deletes the selected IP address reservation(s)
Add: Opens the LAN DHCP Reserved IP Configuration page to add a new binding rule.
Figure 2: LAN DHCP Reserved IPs
Note the following limits for the number of DHCP Reserved IP addresses per product:
17
Page 19
Unified Services Router User Manual
o DSR-150/150N: 32
o DSR-250/250N: 64
o DSR-500/500N: 96
o DSR-1000/1000N: 128
2.1.2 LAN DHCP Leased Clients
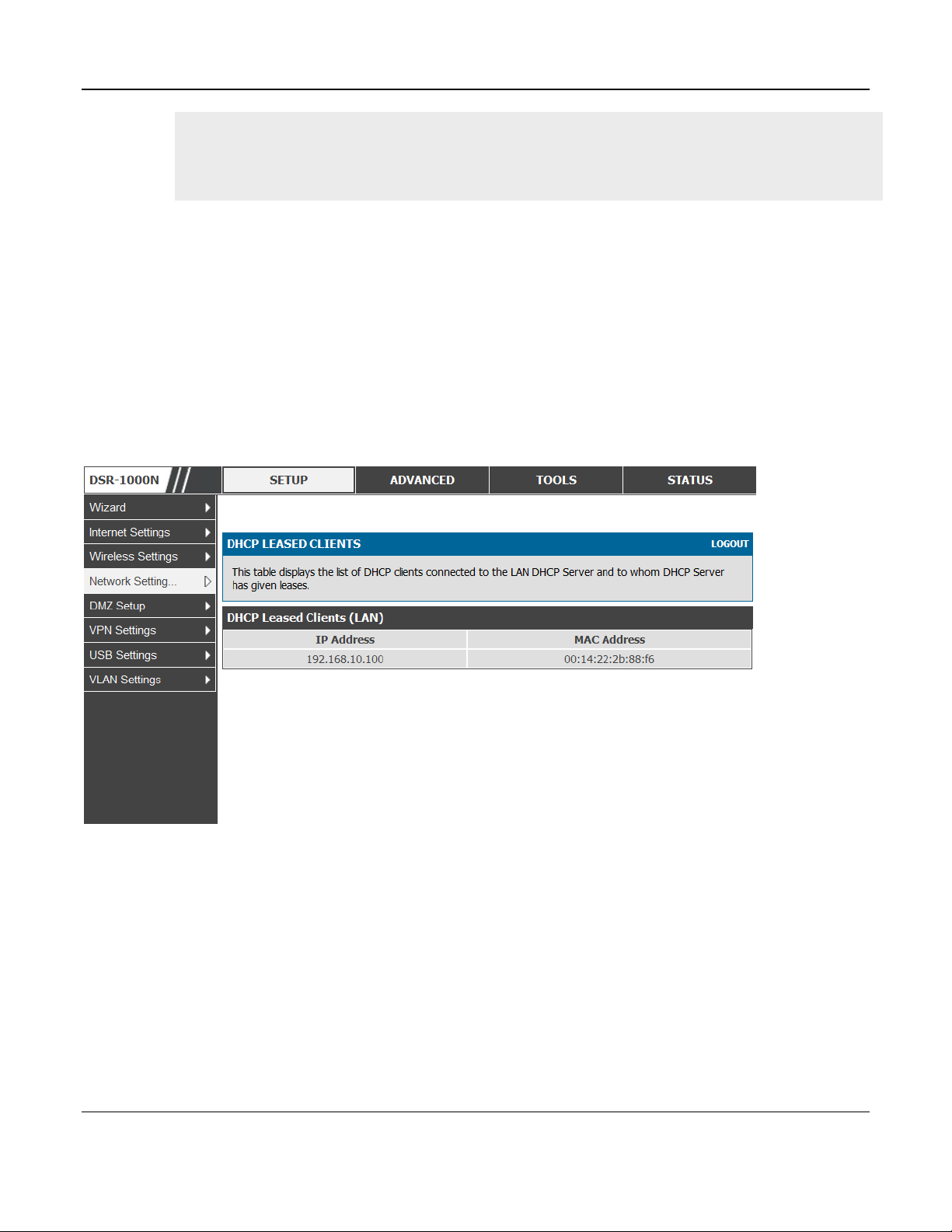
Setup > Network Settings > LAN DHCP Leased Clients
This page provides the list of clients connect to LAN DHCP server.
Figure 3: LAN DHCP Leased Clients
IP Addresses: The LAN IP address of a host that matches the reserved IP list.
MAC Addresses: The MAC address of a LAN host that has a configured IP address reservation.
2.1.3 LAN Configuration in an IPv6 Network
Advanced > IPv6 > IPv6 LAN > IPv6 LAN Config
(1) In IPv6 mode, the LAN DHCP server is disabled by default (similar to IPv4 mode). The
DHCPv6 server will serve IPv6 addresses from configured address pools with the IPv6 Prefix
Length assigned to the LAN.
18
Page 20
Unified Services Router User Manual
IPv4 / IPv6 mode must be enabled in the Advanced > IPv6 > IP mode to enable IPv6 configuration
options.
LAN Settings
The default IPv6 LAN address for the router is fec0::1. You can change this 128 bit IPv6 address
based on your network requirements. The other field that defines the LAN settings for the router is
the prefix length. The IPv6 network (subnet) is identified by the initial bits of the address called the
prefix. By default this is 64 bits long. All hosts in the network have common initial bits for their
IPv6 address; the number of common initial bits in the network’ s address es is set by the prefix
length field.
19
Page 21
Unified Services Router User Manual
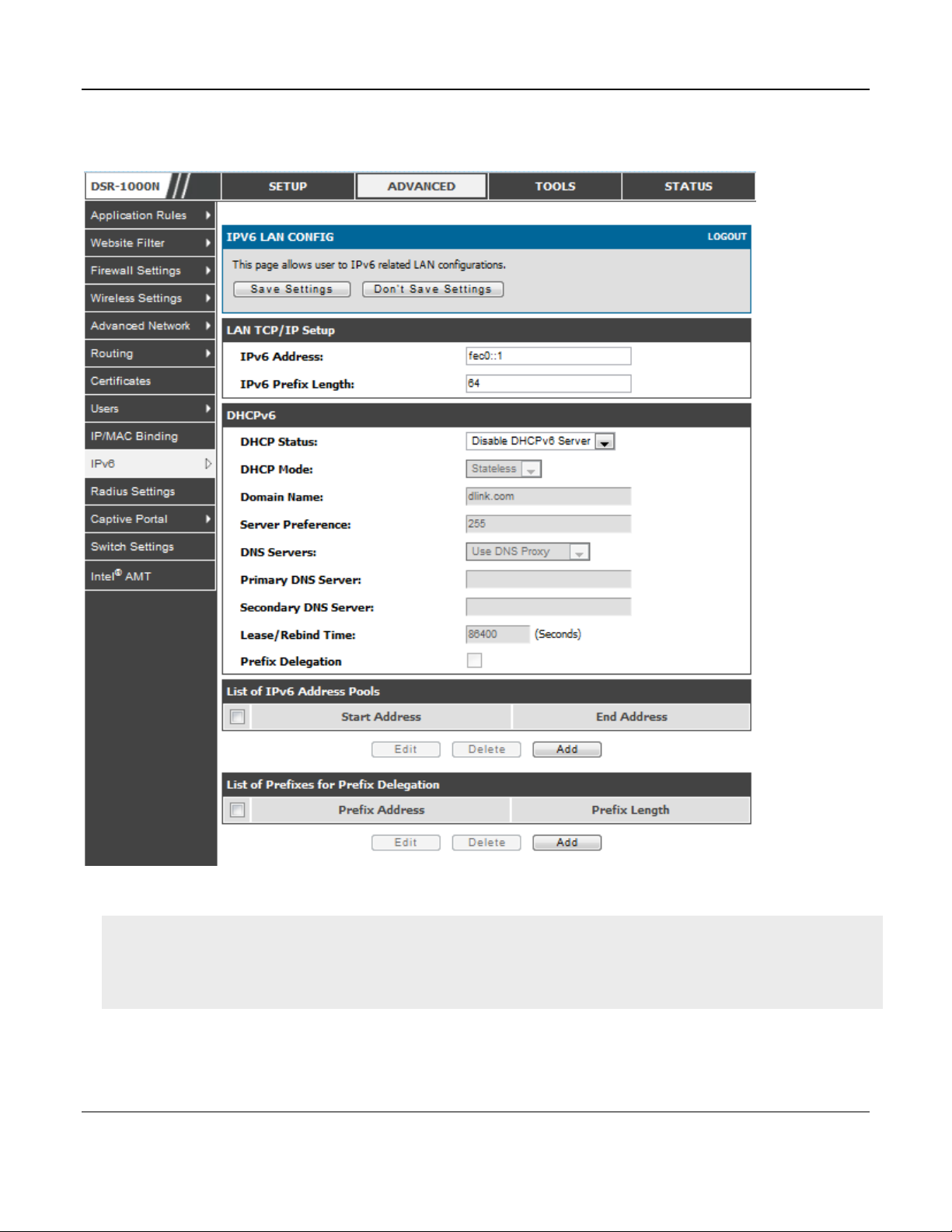
Figure 4: IPv6 LAN and DHCPv6 configuration
If you change the IP address and click Save Settings, the GUI will not respond. Open a new connection
to the new IP address and log in again. Be sure the LAN host (the machine used to manage the router)
has obtained IP address from newly assi gned po ol (or has a static IP address in the router’s LAN
subnet) before accessing the router via changed IP address.
As with an IPv4 LAN network, the router has a DHCPv6 server. If enabled, the router assigns an IP
address within the specified range plus additional specified information to any LAN PC that
requests DHCP served addresses.
The following settings are used to configure the DHCPv6 server:
20
Page 22

Unified Services Router User Manual
DHCP Mode: The IPv6 DHCP server is either stateless or stateful. If stateless is selected an
external IPv6 DHCP server is not required as the IPv6 LAN hosts are auto-configured by this
router. In this case the router advertisement daemon (RADVD) must be configured on this
device and ICMPv6 router discovery messages are used by the host for auto-configuration.
There are no managed addresses to serve the LAN nodes. If stateful is selected the IPv6 LAN
host will rely on an external DHCPv6 server to provide required configuration settings
The domain name of the DHCPv6 server is an optional setting
Server Preference is used to indicate the preference level of this DHCP server. DHCP advertise
messages with the highest server preference value to a LAN host are preferred over other DHCP
server advertise messages. The default is 255.
The DNS server details can be manually entered here (primary/secondary options. An
alternative is to allow the LAN DHCP client to receive the DNS server details from the ISP
directly. By selecting Use DNS proxy, this router acts as a proxy for all DNS requests and
communicates with the ISP’s DNS server s (a WAN configuration parameter).
Primary and Secondary DNS servers: If there is configured domain name system (DNS) servers
available on the LAN enter the IP addresses here.
Lease/Rebind time sets the duration of the DHCPv6 lease from this router to the LAN client.
IPv6 Address Pools
This feature allows you to define the IPv6 delegation prefix for a range of IP addresses to be served
by the gateway’s D HCPv6 server. Using a delegation prefix you can automate the process of
informing other networking equipment on the LAN of DHCP information specific for the assigned
prefix.
Prefix Delegation
The following settings are used to configure the Prefix Delegation:
Prefix Delegation: Select this option to enable prefix delegation in DHCPv6 server. This option
can be selected only in Stateless Address Auto Configuration mode of DHCPv6 server.
Prefix Address: IPv6 prefix address in the DHCPv6 server prefix pool
Prefix Length: Length prefix address
2.1.4 Configuring IPv6 Router Advertisements
Router Advertisements are analogous to IPv4 DHCP assignments for LAN clients, in that the router
will assign an IP address and supporting network information to devices that are configured to
accept such details. Router Advertisement is required in an IPv6 network is required for stateless
auto configuration of the IPv6 LAN. By configuring the Router Advertisement Daemon on this
router, the DSR will listen on the LAN for router solicitations and respond to these LAN hosts with
router advisements.
21
Page 23

Unified Services Router User Manual
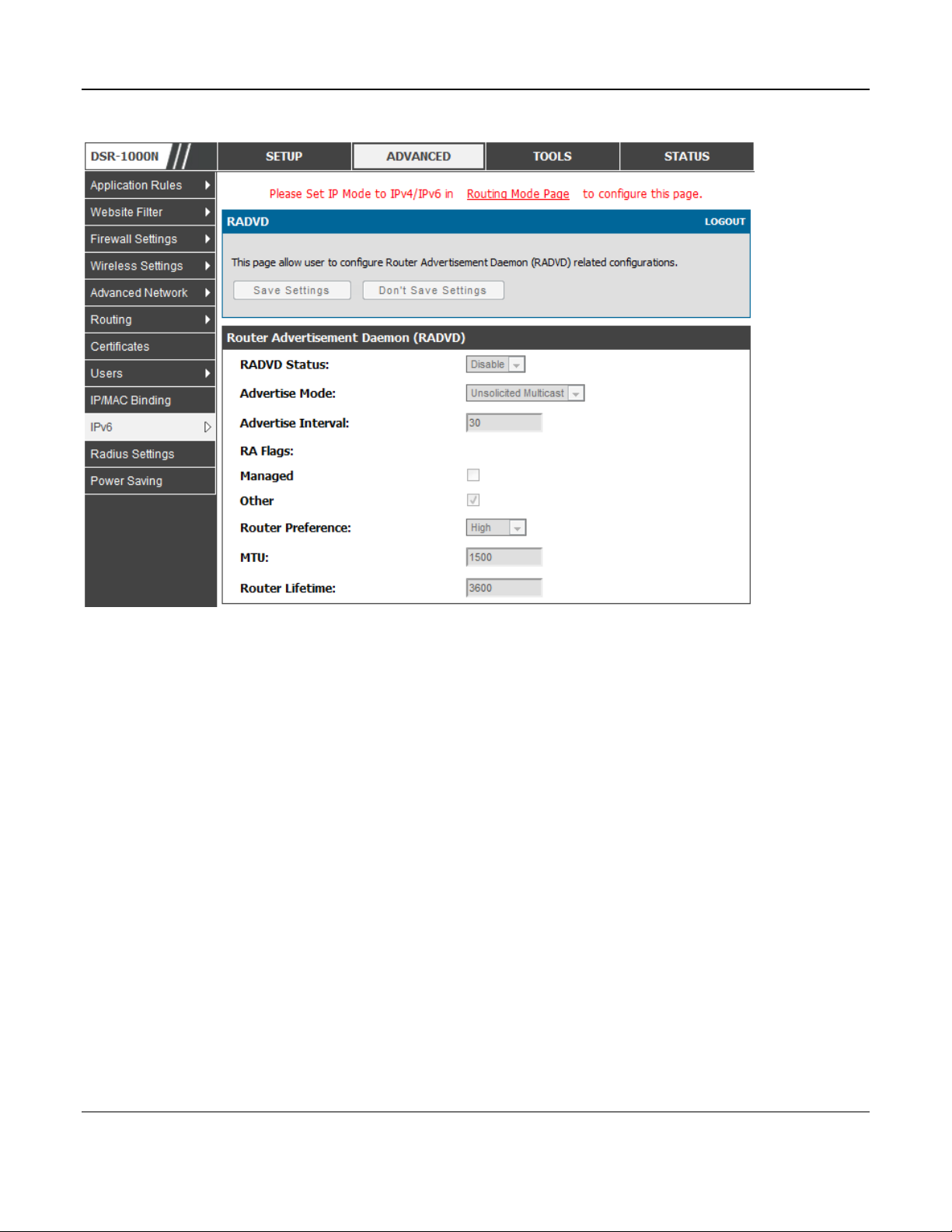
RADVD
Advanced > IPv6 > IPv6 LAN > Router Advertisement
To support stateless IPv6 auto configuration on the LAN, set the RADVD status to Enable. The
following settings are used to configure RADVD:
Advertise Mode: Select Unsolici ted Multicast to send router advertise me nts (RA’s) to all
interfaces in the multicast group. To restrict RA’s to well-known IPv6 addresses on the
LAN, and thereby reduce overall network traffic, select Unicast only.
Advertise Interval: When advertisements are unsolicited multicast packets, this interval sets
the maximum time between advertisements from the interface. The actual duration between
advertisements is a random value between one third of this field and this field. The default
is 30 seconds.
RA Flags: The router advertiseme nts (RA’s) can be sent with one or both of these fla gs.
Chose Managed to use the administered /stateful protocol for address auto configuration. If
the Other flag is selected the host uses administered/stateful protocol for non-address auto
configuration.
Router Preference: this low/medium/high parameter determines the preference associated
with the RADVD process of the router. This is useful if there are other RADVD enabled
devices on the LAN as it helps avoid conflicts for IPv6 clients.
MTU: The router advertisement will set this maximum transmission unit (MTU) value for all
nodes in the LAN that are auto configured by the router. The default is 1500.
Router Lifetime: This value is present in RA’s a nd in dicates the usefulness o f t hi s router as
a default router for the interface. The default is 3600 seconds. Upon expiration of this value,
a new RADVD exchange must take place between the host and this router.
22
Page 24
Unified Services Router User Manual
Figure 5: Configuring the Router Advertisement Daemon
Advertisement Prefixes
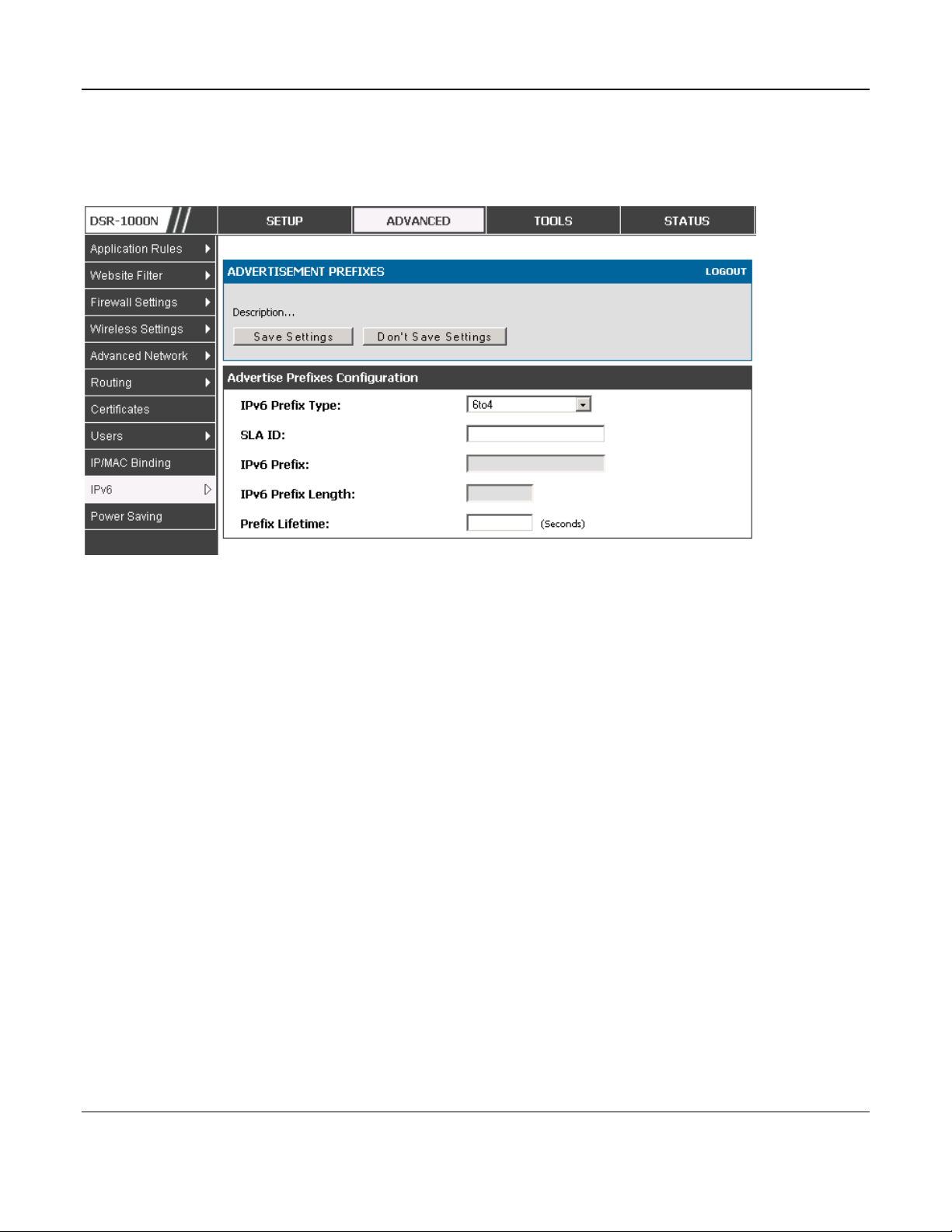
Advanced > IPv6 > IPv6 LAN > Advertisement Prefixes
The router advertisements configured with advertisement prefixes allow this router to inform hosts
how to perform stateless address auto configuration. Router advertisements contain a list of subnet
prefixes that allow the router to determine neighbors and whether the host is on the same link as the
router.
The following prefix options are available for the router advertisements:
IPv6 Prefix Type: To ensure hosts support IPv6 to IPv4 tunnel select the 6to4 prefix type.
Selecting Global/Local/ISATAP will allow the nodes to support all other IPv6 routing
options
SLA ID: The SLA ID (Site-Level Aggregation Identifier) is available when 6to4 Prefixes are
selected. This should be the in terface ID of the router’s LAN interface used fo r rout er
advertisements.
IPv6 Prefix: When using Global/Local/ISATAP prefixes, this field is used to define the IPv6
network advertised by this router.
IPv6 Prefix Length: This value indicates the number contiguous, higher order bits of the
IPv6 address that define up the network portion of the address. Typically this is 64.
23
Page 25
Unified Services Router User Manual
Prefix Lifetime: This defines the duration (in seconds) that the requesting node is allowed to
use the advertised prefix. It is analogous to DHCP lease time in an IPv4 network.
Figure 6: IPv6 Advertisement Prefix settings
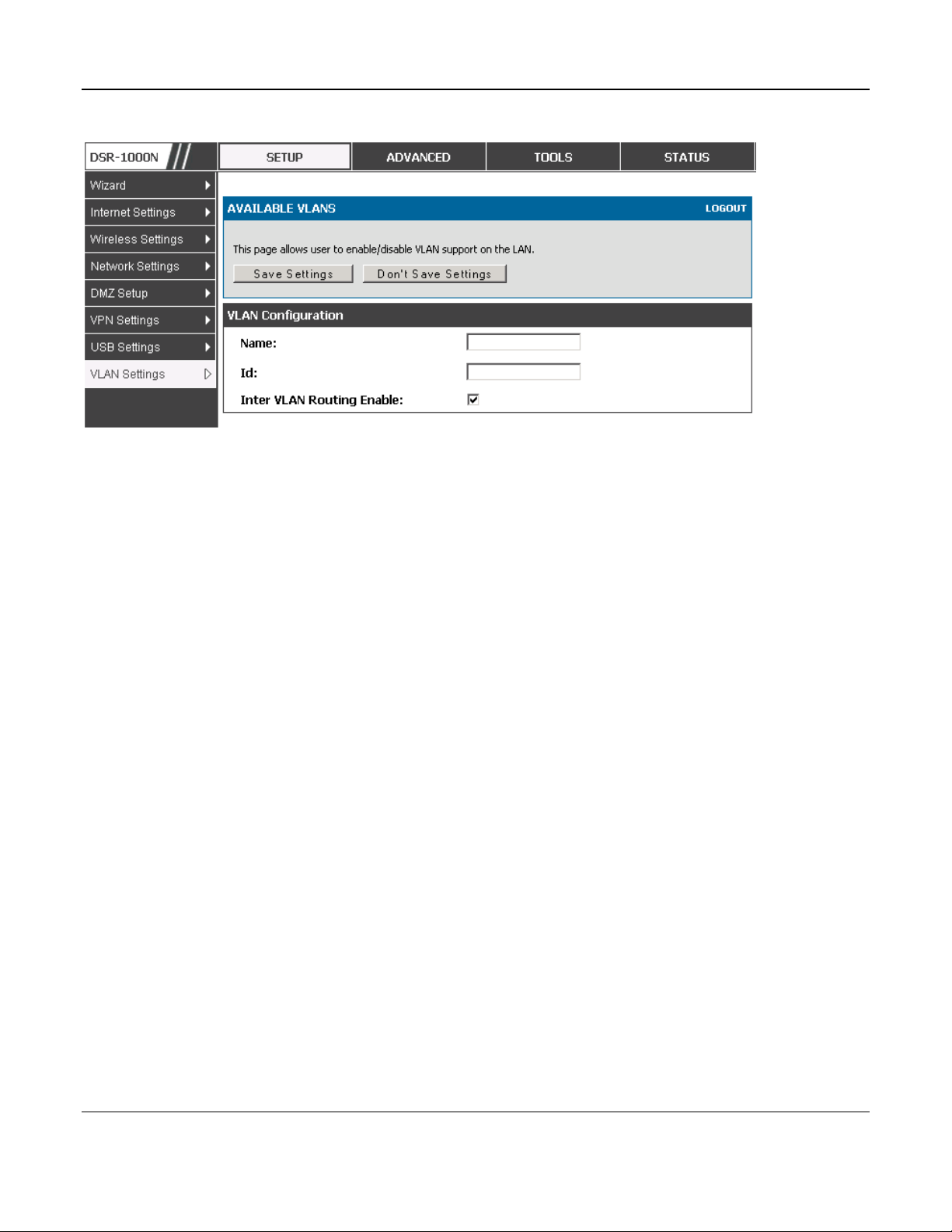
2.2 VLAN Configuration
The router supports virtual network isolation on the LAN with the use of VLANs. LAN devices can be
configured to communicate in a sub network defined by VLAN identifiers. LAN ports can be assigned
unique VLAN IDs so that traffic to and from that physical port can be isolated from the general LAN.
VLAN filtering is particularly useful to limit broadcast packets of a device in a large network
VLAN support is enabled by default in the router. In the VLAN Configuration page, enable VLAN
support on the router and then proceed to the next section to define the virtual network.
Setup > VLAN Settings > Available VLAN
The Available VLAN page shows a list of configured VLANs by name and VLAN ID. A VLAN
membership can be created by clicking the Add button below the List of Available VLANs.
A VLAN membership entry consists of a VLAN identifier and the numerical VLAN ID wh ich is
assigned to the VLAN membership. The VLAN ID value can be any number from 2 to 4091. VLAN
ID 1 is reserved for the default VLAN, which is used for untagged frames received on the interface.
By enabling Inter VLAN Routing, you will allow traffic from LAN hosts belonging to this VLAN ID
to pass through to other configured VLAN IDs that have Inter VLAN Routing enabled.
24
Page 26
Unified Services Router User Manual
Figure 7: Adding VLAN memberships to the LAN
2.2.1 Associating VLANs to ports
In order to tag all traffic through a specific LAN port with a VLAN ID, you can associate a VLAN
to a physical port.
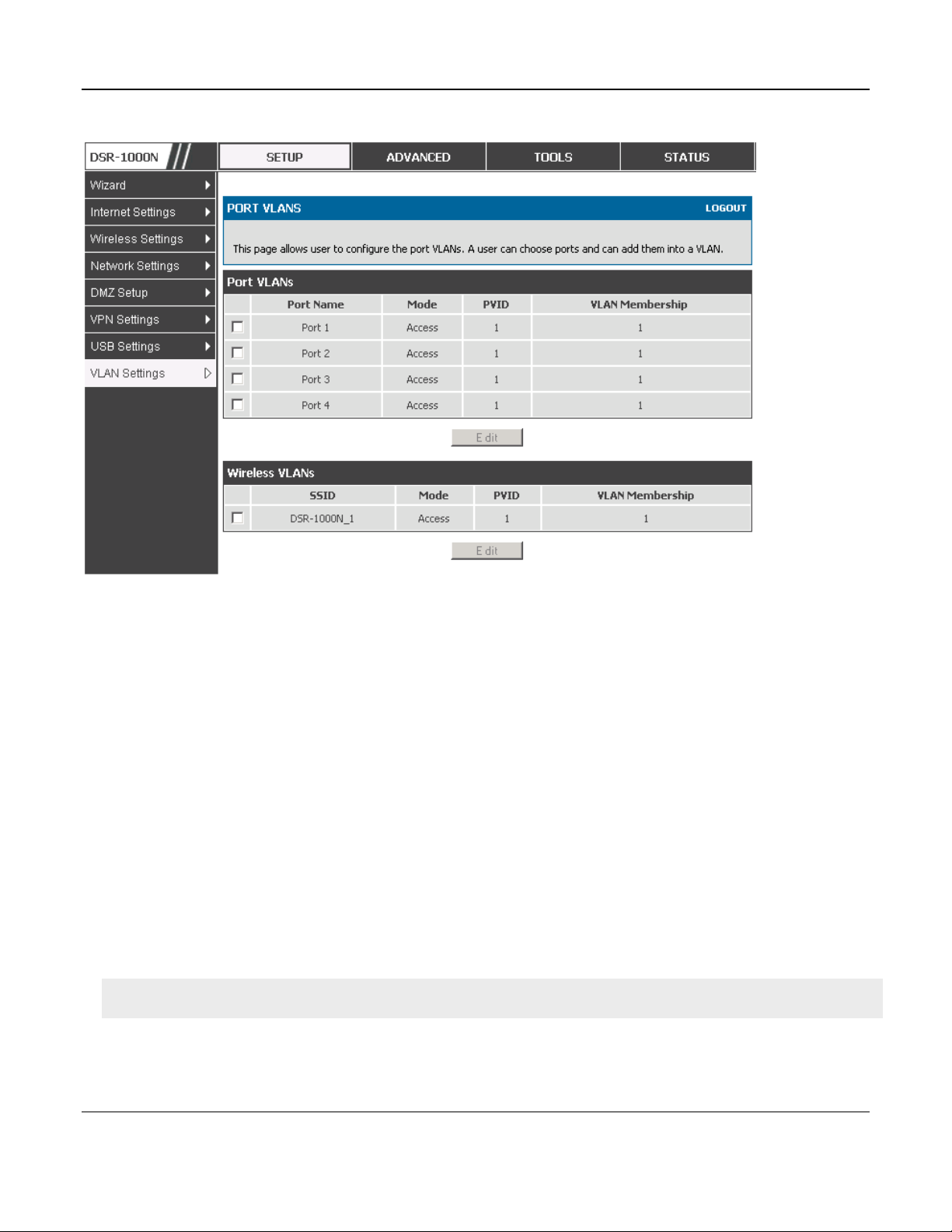
Setup > VLAN Settings > Port VLAN
VLAN membership properties for the LAN and wireless LAN are listed on this page. The VLAN
Port table displays the port identifier, the mode setting for that port and VLAN membership
information. The configuration page is accessed by selecting one of the four physical ports or a
configured access point and clicking Edit.
The edit page offers the following configuration options:
Mode: The mode of this VLAN can be General, Access, or Trunk. The default is access.
In General mode the port is a member of a user selectable set of VLANs. The port sends
and receives data that is tagged or untagged with a VLAN ID. If the data into the port is
untagged, it is assigned the defined PVID. In the configuration from Figure 4, Port 3 is a
General port with PVID 3, so untagged data into Port 3 will be assigned PVID 3. All tagged
data sent out of the port with the same PVID will be untagged. This is mode is typically
used with IP Phones that have dual Ethernet ports. Data coming from phone to the switch
port on the router will be tagged. Data passing through the phone from a connected device
will be untagged.
25
Page 27
Unified Services Router User Manual
Figure 8: Port VLAN list
In Access mode the port is a member of a single VLAN (and only one). All data going into
and out of the port is untagged. Traffic through a port in access mode looks like any other
Ethernet frame.
In Trunk mode the port is a member of a user selectable set of VLANs. All data going into
and out of the port is tagged. Untagged coming into the port is not forwarded, except for
the default VLAN with PVID=1, which is untagged. Trunk ports multiplex traffic for
multiple VLANs over the same physical link.
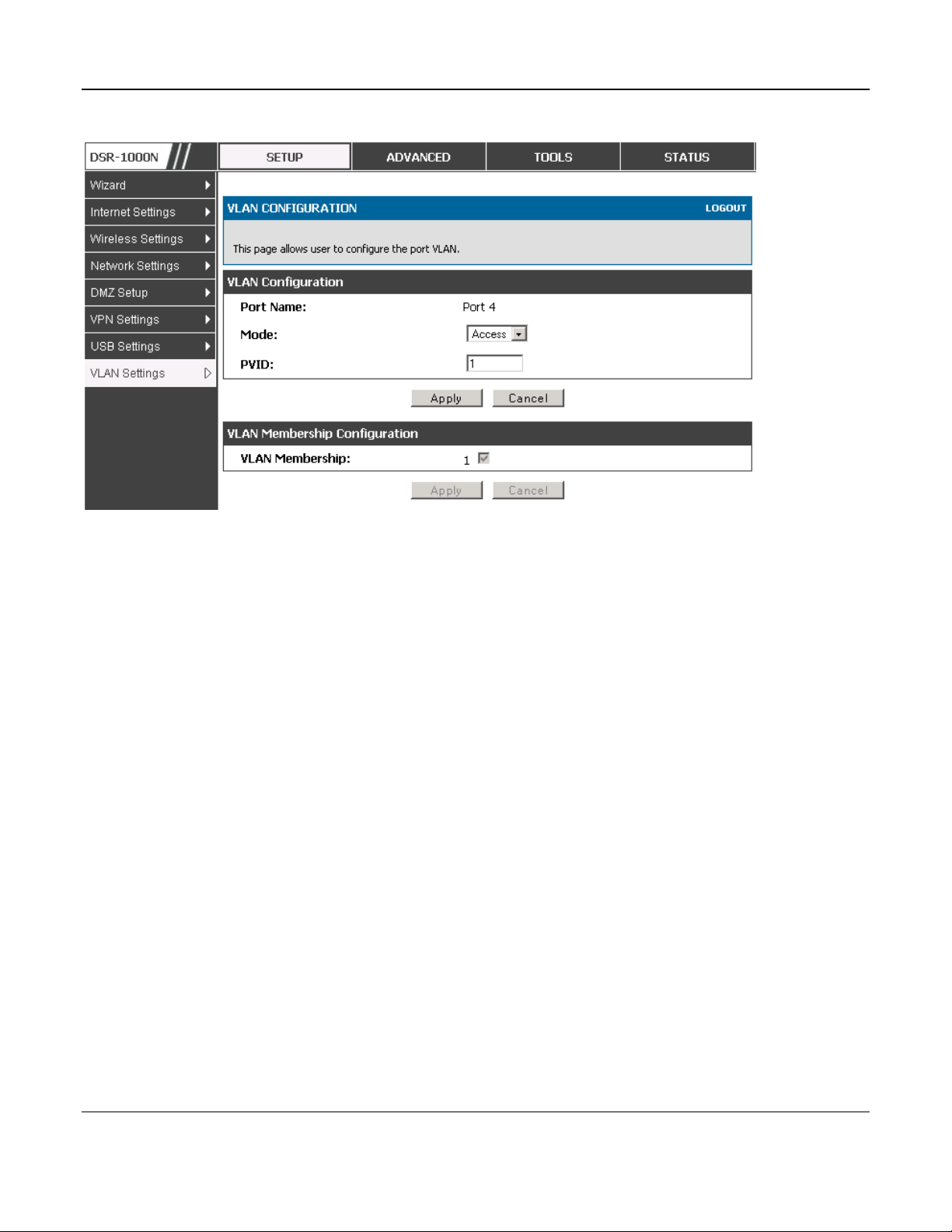
Select PVID for the port when the General mode is selected.
Configured VLAN memberships will be displayed on the VLAN Membership Configuration
for the port. By selecting one more VLAN membership options for a General or Trunk port,
traffic can be routed between the selected VLAN membership IDs
The DSR-150 / 150N does not support General mode for port VLANs due to hardware limitations.
26
Page 28
Unified Services Router User Manual
Figure 9: Configuring VLAN membership for a port
2.2.2 Multiple VLAN Subnets
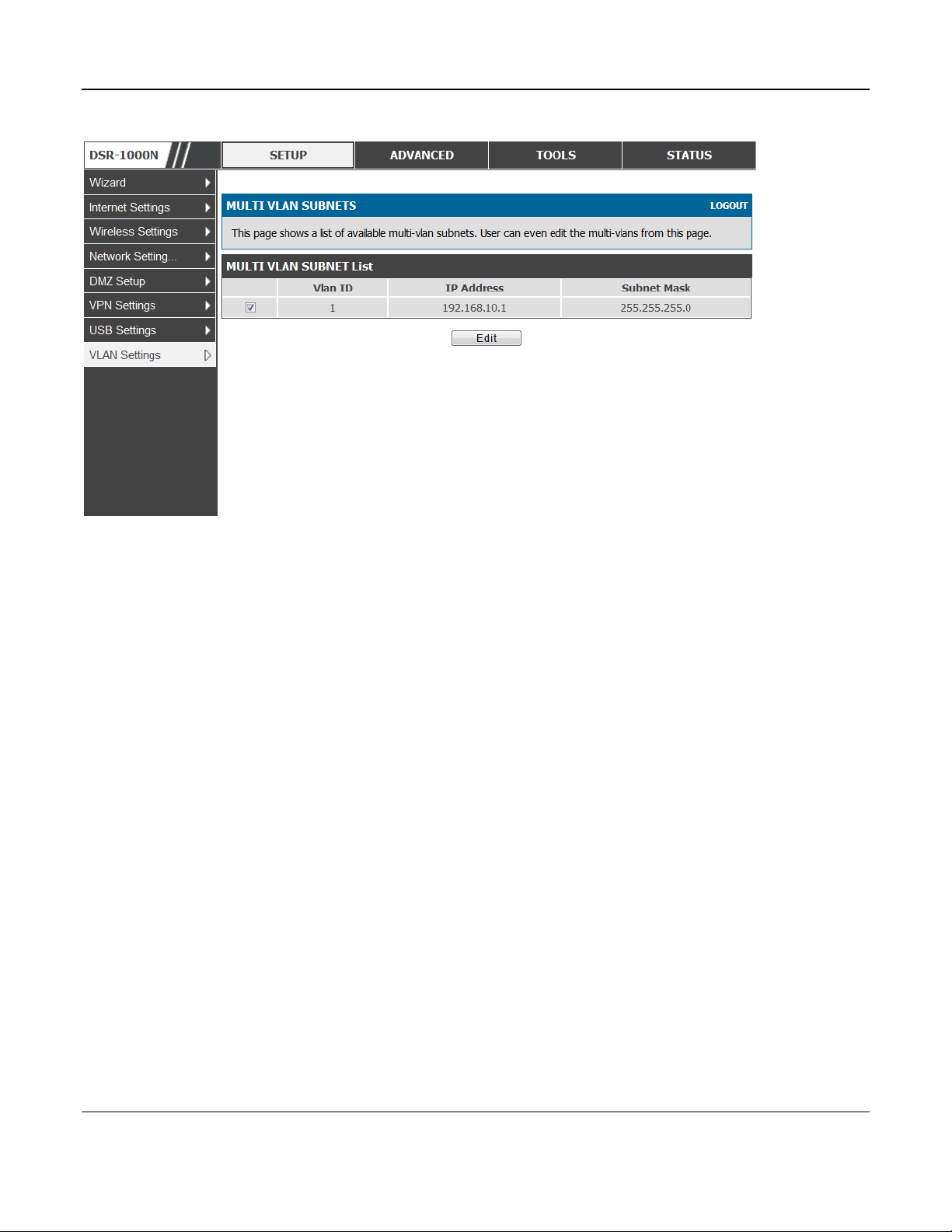
Setup > VLAN Settings > Multi VLAN Settings
This page shows a list of available multi-VLAN subnets. Each configured VLAN ID can map
directly to a subnet within the LAN. Each LAN port can be assigned a unique IP address and a
VLAN specific DHCP server can be configured to assign IP address leases to devices on this VLAN.
VLAN ID: The PVID of the VLAN that will have all member devices be part of the same subnet
range.
IP Address: The IP address associated with a port assigned this VLAN ID.
Subnet Mask: Subnet Mask for the above IP Address
27
Page 29
Unified Services Router User Manual
Figure 10: Multiple VLAN Subnets
2.2.3 VLAN configuration
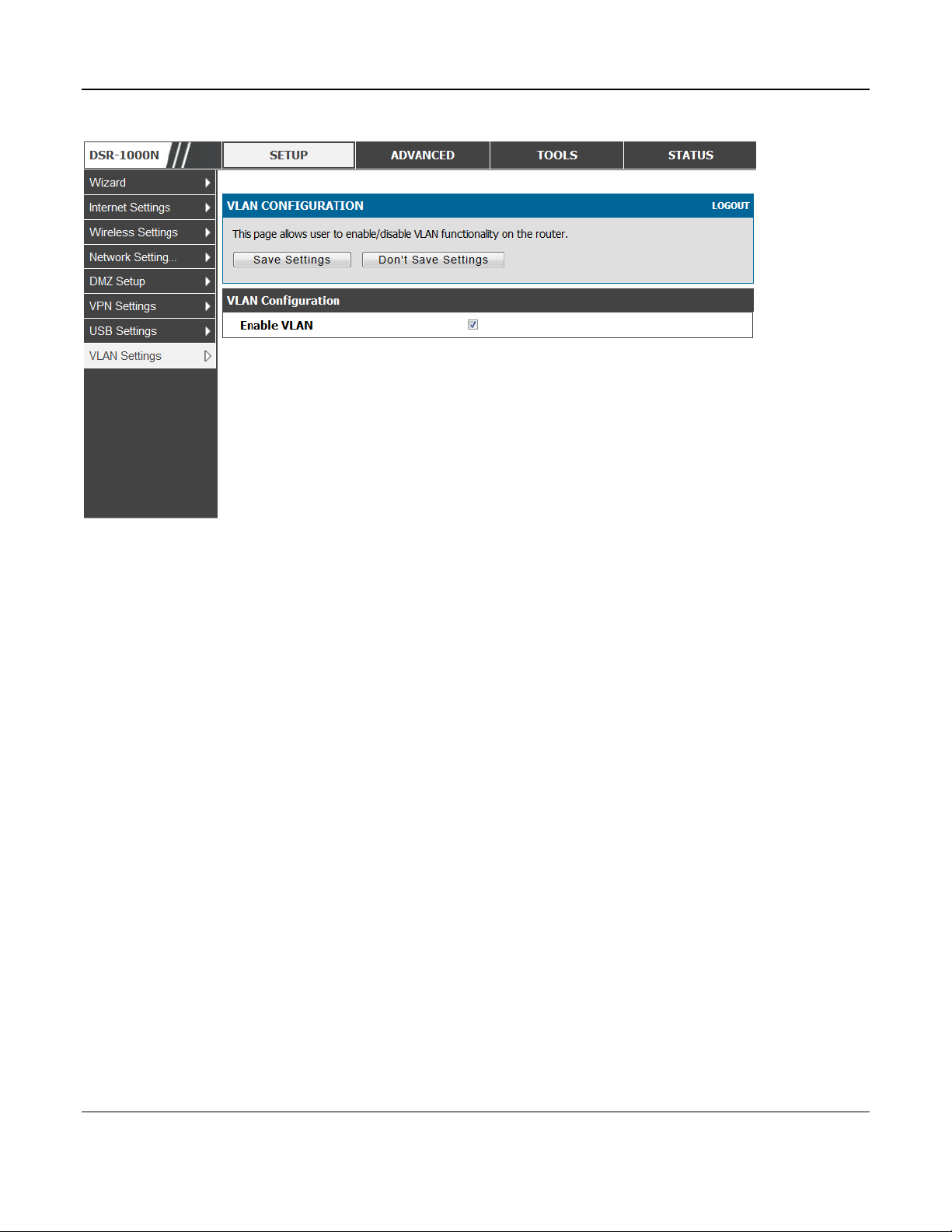
Setup > VLAN Settings > VLAN configuration
This page allows enabling or disabling the VLAN function on the router. Virtual LANs can be
created in this router to provide segmentation capabilities for firewall rules and VPN policies. The
LAN network is considered the default VLAN. Check the Enable VLAN box to add VLAN
functionality to the LAN.
28
Page 30
Unified Services Router User Manual
Figure 11: VLAN Configuration
2.3 Configurable Port: DMZ Setup
This router supports one of the physical ports to be configured as a secondary WAN Ethernet port or a
dedicated DMZ port. A DMZ is a sub network that is open to the public but behind the firewall. The
DMZ adds an additional layer of security to the LAN, as specific services/ports that are exposed to
the internet on the DMZ do not have to be exposed on the LAN. It is recommended that hosts that
must be exposed to the internet (such as web or email servers) be placed in the DMZ network.
Firewall rules can be allowed to permit access specific services/ports to the DMZ from both the LAN
or WAN. In the event of an attack to any of the DMZ nodes, the LAN is not necessarily vulnerable as
well.
Setup > DMZ Setup > DMZ Setup Configuration
DMZ configuration is identical to the LAN configuration. There are no restrictions on the IP address
or subnet assigned to the DMZ port, other than the fact that it cannot be identical to the IP address
given to the LAN interface of this gateway.
29
Page 31

Unified Services Router User Manual
Figure 12: DMZ configuration
For DSR-500N and 1000N, in order to configure a DMZ port, the router’s con fi gurable port must be
set to DMZ in the Setup > Internet Settings > Configurable Port page.
2.4 Universal Plug and Play (UPnP)
Advanced > Advanced Network > UPnP
Universal Plug and Play (UPnP) is a feature that allows the router to discovery devices on the network
that can communicate with the router and allow for auto configuration. If a network device is detected
by UPnP, the router can open internal or external ports for the traffic protocol r equired by that
network device.
Once UPnP is enabled, you can configure the router to detect UPnP-supporting devices on the LAN
(or a configured VLAN). If disabled, the router will not allow for automatic device configuration.
Configure the following settings to use UPnP:
30
Page 32

Unified Services Router User Manual
Advertisement Period: This is the frequency that the router broadcasts UPnP information over the
network. A large value will minimize network traffic but cause delays in identifying new UPnP
devices to the network.
Advertisement Time to Live: This is expressed in hops for each UPnP packet. This is the number of
steps a packet is allowed to propagate before being discarded. Small values will limit the UPnP
broadcast range. A default of 4 is typical for networks with few switches.
Figure 13: UPnP Configuration
UPnP Port map Table
The UPnP Port map Table has the details of UPnP devices that respond to the router ’s advertisements.
The following information is displayed for each detected device:
Active: A yes/no indicating whether the port of the UPnP device that established a connection is
currently active
Protocol: The network protocol (i.e. HTTP, FTP, etc.) used by the DSR
Int. Port (Internal Port): The internal ports opened by UPnP (if any)
Ext. Port (External Port): The external ports opened by UPnP (if any)
IP Address: The IP address of the UPnP device detected by this router
Click Refresh to refresh the portmap table and search for any new UPnP devices.
31
Page 33

Unified Services Router User Manual
2.5 Captive Portal
LAN users can gain internet access via web portal authentication with the DSR. Also referred to as
Run-Time Authentication, a Captive Portal is ideal for a web café scenario where users initiate
HTTP connection requests for web access but are not interested in accessing any LAN services.
Firewall policies underneath will define which users require authentication for HTTP access, and
when a matching user request is made the DSR will intercept the request and prompt for a username
/ password. The login credentials are compared against the Runtime Authentication users in user
database prior to granting HTTP access.
DSR-150/150N/250/250N does not have support for the Captive Portal feature.
Captive Portal is available for LAN users only and not for DMZ hosts.
Setup > Captive Portal >Captive Portal Sessions
The active run time internet sessions through the router’ s firewall are listed in the below table.
These users are present in the local or external user database and have had their login credentials
approved for internet access. A ‘Disconnect’ butto n allows the DSR admin to selective ly drop an
authenticated user. The “Blo ck MAC” button will result in the selected client being ad ded to the
blocked list, and the current and future sessions from this client will be prevented.
Figure 14: Active Runtime sessions
2.5.1 Captive Portal Setup
Setup > Captive Portal >Captive Portal Setup
Captive Portal is a security mechanism to selectively provide authentication on certain interfaces.
This page displays configured custom Captive Portal profiles and indicates which are in use.
32
Page 34

Unified Services Router User Manual
Figure 15: Captive Portal Profile List
List of Available Profiles: Any one of these profiles can be used for Captive Portal Login page
while enabling Captive Portal.
Click “Add” in the Captive Portal setup p age to allow defining customized captive portal login page
information (Page Background Color, Header Details, Header Caption, Login Section Details,
Advertisement Details, Footer Details and Captive Portal Header Image).
Setup > Captive Portal > Customized Captive Portal Setup
To create a new Captive Portal, a profile with a unique policy name is to be created. The profile
governs the entry screen shown to new sessions, and the browser message and background color /
header can be customized to identify the service provider for internet access.
33
Page 35

Unified Services Router User Manual
Figure 16: Customized Captive Portal Setup
Setup > Captive Portal > Block Clients
Access for specific clients can be regulated by the Captive Portal as well. The Block Client page
allows one to define a MAC address that will always be denied access through all configured
Captive Portals.
34
Page 36

Unified Services Router User Manual
Figure 17: Blocking specific clients by their MAC address
2.5.2 Captive Portals on a VLAN
Setup > VLAN Settings > VLAN Configuration
Captive Portals can be enabled on a per-VLAN basis. Hosts of a particular VLAN can be directed to
authenticate via the Captive Portal, which may be a customized portal with unique instructions and
branding as compared to another VLAN. The most critical aspect of this configuration page is
choosing the authentication server. All users (VLAN hosts) that want to gain internet access via the
selected Captive Portal will be authenticated through the selected server.
Figure 18: VLAN based configuration of Captive Portals
35
Page 37

Unified Services Router User Manual
Chapter 3. Connecting to the Internet: WAN Setup
This router has two WAN ports that can be used to establish a connection to the internet. The following
ISP connection types are supported: DHCP, Static, PPPoE, PPTP, L2TP, 3G Internet (via USB modem).
It is assumed that you have arranged for internet service with your Internet Service Provider (ISP).
Please contact your ISP or network administrator for the configuration information that will be required
to setup the router.
3.1 Internet Setup Wizard
Setup > Wizard > Internet
The Internet Connection Setup Wizard is available for users new to networking. By going through a
few straightforward configuration pages you can take the information provided by your ISP to get
your WAN connection up and enable internet access for your network.
Figure 19: Internet Connection Setup Wizard
You can start using the Wizard by logging in with the administrator password for the router. Once
authenticated set the time zone that you are located in, and then choose the type of ISP connection
type: DHCP, Static, PPPoE, PPTP, L2TP. Depending on the connection type a username/password
may be required to register this router with the ISP. In most cases the default settings can be used if
the ISP did not specify that parameter. The last step in the Wizard is to click the Connect button,
which confirms the settings by establishing a link with the ISP. Once connected, you can move on and
configure other features in this router.
3G Internet access with a USB modem is supported on WAN3. The Internet Connection Setup Wizard
assists with the primary WAN port (WAN1) configuration only.
36
Page 38

Unified Services Router User Manual
3.2 WAN Configuration
Setup > Internet Settings > WAN1 Setup
You must either allow the router to detect WAN connection type automatically or configure manually
the following basic settings to enable Internet connectivity:
ISP Connection type: Based on the ISP you have selected for the primary WAN link for this
router, choose Static IP address, DHCP client, Point-to-Point Tunneling Protocol (PPTP), Pointto-Point Protocol over Ethernet (PPPoE), Layer 2 Tunneling Protocol (L2TP). Required fields for
the selected ISP type become highlighted. Enter the following information as needed and as
provided by your ISP:
PPPoE Profile Name. This menu lists configured PPPoE profiles, particularly useful when
configuring multiple PPPoE connections (i.e. for Japan ISPs that have multiple PPPoE support).
ISP login information. This is required for PPTP and L2TP ISPs.
User Name
Password
Secret (required for L2TP only)
MPPE Encryption: For PPTP links, your ISP may require you to enable Microsoft Point-to-Point
Encryption (MPPE).
Split Tunnel (supported for PPTP and L2TP connection). This setting allows your LAN hosts to
access internet sites over this WAN link while still permitting VPN traffic to be directed to a VPN
configured on this WAN port.
If sp lit tunnel is enabled, DSR won’t expect a default ro ut e fro m the ISP server. In such case, user has
to take care of routing manually by configuring the routing from Static Routing page.
Connectivity Type: To keep the connection always on, click Keep Connected. To log out after the
connection is idle for a period of time (useful if your ISP costs are based on logon times), click Idle
Timeout and enter the time, in minutes, to wait before disconnecting in the Idle Time field.
My IP Address: Enter the IP address assigned to you by the ISP.
Server IP Address: Enter the IP address of the PPTP or L2TP server.
DSR-150/150N/250/250N doesn’t have a dual WAN s up port.
3.2.1 WAN Port IP address
Your ISP assigns you an IP address that is either dynamic (newly generated each time you log in) or
static (permanent). The IP Address Source option allows you to define whether the address is
37
Page 39

Unified Services Router User Manual
statically provided by the ISP or should be received dynamically at each login. If static, enter your
IP address, IPv4 subnet mask, and the ISP gateway’s IP address. PPTP and L2TP ISPs also can
provide a static IP address and subnet to configure, however the default is to receive that
information dynamically from the ISP.
3.2.2 WAN DNS Servers
The IP Addresses of WAN Domain Name Servers (DNS) are typically provided dynamically from
the ISP but in some cases you can define the static IP addresses of the DNS servers. DNS servers
map Internet domain names (example: www.google.com) to IP addresses. Click to indicate whether
to get DNS server addresses automatically from your ISP or to use ISP -sp ecified addresses. If it’s
latter, enter addresses for the primary and secondary DNS servers. To avoid connectivity problems,
ensure that you enter the addresses correctly.
3.2.3 DHCP WAN
For DHCP client connections, you can choose the MAC address of the router to register with the
ISP. In some cases you ma y need to clone the L AN host’s MAC ad dress i f the I SP is registered with
that LAN host.
Figure 20: Manual WAN configuration
3.2.4 PPPoE
Setup > Internet Settings
38
Page 40

Unified Services Router User Manual
The PPPoE ISP settings are defined on the WAN Configuration page. There are two types of PPPoE
ISP’s supported by the DSR: the standard username/password PPPoE and Japan Multiple PPPoE.
Figure 21: PPPoE configuration for standard ISPs
Most PPPoE ISP’s use a single control and data connection, and r equire username / passwor d
credentials to login and authenticate the DSR with the ISP. The ISP connection type for this case is
“PPPoE (User name/Passwo rd)”. T he G UI will pro mpt yo u fo r authentic ation, service, and
connection settings in order to establish the PPPoE link.
For so me ISP’ s, most pop ular in J apan, the use of “Japanese Multiple P PPoE” is required in order to
establish concurrent primary and secondary PPPoE connections between the DSR and the ISP. The
Primary connection is used for the bulk of data and internet traffic and the Secondary PPPoE
connection carries ISP specific (i.e. control) traffic between the DSR and the ISP.
39
Page 41

Unified Services Router User Manual
Figure 22: WAN configuration for Japanese Multiple PPPoE (part 1)
There are a few key elements of a multiple PPPoE connection:
Primary and secondary connections are concurrent
Each session has a DNS server source for domain name lookup, this can be assigned by t he ISP or
configured through the GUI
The DSR acts as a DNS proxy for LAN users
Only HT TP req uest s t hat specific ally ide ntify the secondary connection ’s domain name (for example
*.flets) will use the secondary profile to access the content available through this secondary PPPoE
terminal. All other HTTP / HTTPS requests go through the primary PPPoE connection.
40
Page 42

Unified Services Router User Manual
When Japanese multiple PPPoE is configured and secondary connection is up, some predefined routes are added
on that interface. These routes are needed to access the internal domain of the ISP where he hosts various
services. These routes can even be configured through the static routing page as well.
Figure 23: WAN configuration for Japanese Multiple PPPoE (part 2)
3.2.5 Russia L2TP and PPTP WAN
For Russia L2TP WAN connections, you can choose the address mode of the connection to get an IP
address from the ISP or configure a static IP address provided by the ISP. For DHCP client
connections, you can choose the MAC address of the router to register with the ISP. In some cases
you ma y ne ed to clone the L AN host’s MAC address if the ISP is registered with tha t LAN host.
41
Page 43

Unified Services Router User Manual
Figure 24: Russia L2TP ISP configuration
3.2.6 Russia Dual Access PPPoE
For Russia dual access PPPoE connections, you can choose the address mode of the connection to
get an IP address from the ISP or configure a static IP address provided by the ISP.
42
Page 44

Unified Services Router User Manual
Figure 25: Russia Dual access PPPoE configuration
3.2.7 WAN Configuration in an IPv6 Network
Advanced > IPv6 > IPv6 WAN1 Config
For IPv6 WAN connections, this router can have a static IPv6 address or receive connection
information when configured as a DHCPv6 client. In the case where the ISP assigns you a fixed
address to access the internet, the static configuration settings must be completed. In addition to the
IPv6 address assigned to your router, the IPv6 prefix length defined by the ISP is needed. The
default IPv6 Gateway address is the server at the ISP that this router will connect to for accessing
the internet. The primary and secondary DNS servers on the ISP’s IPv6 n etwork are used for
resolving internet addresses, and these are provided along with the static IP address and prefix
length from the ISP.
When the ISP allows you to obtain the WAN IP settings via DHCP, you need to provide details for
the DHCPv6 client configuration. The DHCPv6 client on the gateway can be either stateless or
43
Page 45

Unified Services Router User Manual
stateful. If a state ful client is selected the gateway will connect to the I SP’s DHCPv6 server for a
leased address. For stateless DHCP there need not be a DHCPv6 server available at the ISP, rather
ICMPv6 discover messages will originate from this gateway and will be used for auto configuration.
A third option to specify the IP address and prefix length of a preferred DHCPv6 server is available
as well.
Figure 26: IPv6 WAN Setup page
Prefix Delegation: Select this option to request router advertisement prefix from any available
DHCPv6 servers available on the ISP, the obtained prefix is updated to the advertised prefixes on
the LAN side. This option can be selected only in Stateless Address Auto Configuration mode of
DHCPv6 Client.
When IPv6 is PPPoE type, the following PPPoE fields are enabled.
44
Page 46

Unified Services Router User Manual
Username: Enter the username required to log in to the ISP.
Password: Enter the password required to login to the ISP.
Authentication Type: The type of Authentication in use by the profile: Auto -
Negotiate/PAP/CHAP/MS-CHAP/MS-CHAPv2.
Dhcpv6 Options: The mode of Dhcpv6 client that will start in this mode: disable
dhcpv6/stateless dhcpv6/stateful dhcpv6/stateless dhcpv6 with prefix delegation.
Primary DNS Server: Enter a valid primary DNS Server IP Address.
Secondary DNS Server: Enter a valid secondary DNS Server IP Address.
Click Save Settings to save your changes.
3.2.8 Checking WAN Status
Setup > Internet Settings > WAN1 Status
The status and summary of configured settings for both WAN1, WAN2 and WAN3 are available on
the WAN Status page. You can view the following key connection status information for each WAN
port:
Connection time: The connection uptime
Connection type: Dynamic IP or Static IP
Connection state: This is whether the WAN is connected or disconnected to an ISP. The
Link State is whether the physical WAN connection in place; the Link State can be UP (i.e.
cable inserted) while the WAN Connection State is down.
IP address / subnet mask: IP Address assigned
Gateway IP address: WAN Gateway Address
45
Page 47

Unified Services Router User Manual
Figure 27: Connection Status information for both WAN ports
The WAN status page allows you to Enable or Disable static WAN links. For WAN settings that are
dynamically received from the ISP, you can Renew or Release the link parameters if required.
3.3 Bandwidth Controls
Advanced > Advanced Network > Traffic Management > Bandwidth Profiles
Bandwidth profiles allow you to regulate the traffic flow from the LAN to WAN 1 or WAN 2. This is
useful to ensure that low priority LAN users (like guests or HTTP service) do not monopolize the
available WAN’s bandwidth for cost -savings or bandwidth-priority-allocation purposes.
46
Page 48

Unified Services Router User Manual
Bandwidth profiles configuration consists of enabling the bandwidth control feature from the GUI and
adding a profile which defines the control parameters. The profile can then be associated with a
traffic selector, so that bandwidth profile can be applied to the traffic matching the selectors.
Selectors are elements like IP addresses or services that would trigger the configured bandwidth
regulation.
Figure 28: List of Configured Bandwidth Profiles
To create a new bandwidth profile, click Add in the List of Bandwidth Profiles. The following
configuration parameters are used to define a bandwidth profile:
Profile Name: This identifier is used to associate the configured profile to the traffic selector
You can choose to limit the bandwidth either using priority or rate.
If using priority “Low”, “Hi gh”, and “Med ium” can be sele cted. If there is a low priority
profile associated with traffic selector A and a high priority profile associated with traffic
selector B, then the WAN bandwidth allocation preference will be to traffic selector B
packets.
For finer control, the Rate profile type can be used. With this option the minimum and
maximum bandwidth allowed by this profile can be limited.
Choose the WAN interface that the profile should be associated with.
47
Page 49

Unified Services Router User Manual
Figure 29: Bandwidth Profile Configuration
Advanced > Advanced Network > Traffic Management > Traffic Selectors
Once a profile has been created it can then be associated with a traffic flow from the LAN to WAN.
To create a traffic selector, click Add on the Traffic Selectors page. Traffic selector configuration
binds a bandwidth profile to a type or source of LAN traffic with the following settings:
Available profiles: Assign one of the defined bandwidth profiles
Service: You can have the selected bandwidth regulation apply to a specific service (i.e. FTP)
from the LAN. If you do not see a service that you want, you can configure a custom service
through the Advanced > Firewall Settings > Custom Services page. To have the profile
apply to all services, select ANY.
Traffic Selector Match Type: this defines the parameter to filter against when applying the
bandwidth profile. A specific machine on the LAN can be identified via IP address or MAC
address, or the profile can apply to a LAN port or VLAN group. As well a wireless network can
be selected by its BSSID for bandwidth shaping. In order to restrict services from all IP
addresses or specific subnets, the subnet mask field can be configured in conjunction with the
IP address to regulate inbound traffic.
48
Page 50

Unified Services Router User Manual
Figure 30: Traffic Selector Configuration
3.3.1 Bandwidth Controls in Bridge Mode
Advanced > Advanced Network > Traffic Management > Bridge Bandwidth Profiles
Advanced > Advanced Network > Traffic Management > Bridge Traffic Selectors
The above traffic management applies to classical or NAT routing modes. When the system is in
bridge mode (where the LAN1 and WAN2/DMZ ports are in the same network), traffic management
factors in traffic type and bandwidth available on the ports part of the bridge.
For Bandwidth Profiles, the major difference between the options available in bridge mode
compared to standard classical / NAT routing mode is the interface options are not applicable. There
is no association of the bandwidth profile with a particular outbound or inbound interface as this
profile can only apply to the bridge network. Similarly, Traffic Selectors for bridge mode do not
factor in port / SSID / VLAN as these concepts to not apply to the bridge network.
49
Page 51

Unified Services Router User Manual
Figure 31: Bridge Bandwidth Profile Configuration
Figure 32: Bridge Traffic Selector Configuration
3.4 Features with Multiple WAN Links
This router supports multiple WAN links. This allows you to take advantage of failover and load
balancing features to ensure certain internet dependent services are prioritized in the event of unstable
WAN connectivity on one of the ports.
Setup > Internet Settings > WAN Mode
To use Auto Failover or Load Balancing, WAN link failure detection must be configured. This
involves accessing DNS servers on the internet or ping to an internet address (user defined). If
required, you can configure the number of retry attempts when the link seems to be disconnected or
the threshold of failures that determines if a WAN port is down.
50
Page 52

Unified Services Router User Manual
3.4.1 Auto Failover
In this case one of your WAN ports is assigned as the primary internet link for all internet traffic.
The secondary WAN port is used for redundancy in case the primary link goes down for any reason.
Both WAN ports (primary and secondary) must be con fi gured to connect to the respective ISP’s
before enabling this feature. The secondary WAN port will remain unconnected until a failure is
detected on the primary link (either port can be assigned as the primary). In the event of a failure on
the primary port, all internet traffic will be rolled over to the backup port. When configured in Auto
Failover mode, the link status of the primary WAN port is checked at regular intervals as defined by
the failure detection settings.
Note that bothWAN1, WAN2 and WAN3 can be configured as the primary internet link.
Auto-Rollover using WAN port
Primary WAN: Selected WAN is the primary link (WAN1/WAN2/WAN3)
Secondary WAN: Selected WAN is the secondary link.
Failover Detection Settings: To check connectivity of the primary internet link, one of the following
failure detection methods can be selected:
DNS lookup using WAN DNS Servers: DNS Lookup of the DNS Servers of the primary link
is used to detect primary WAN connectivity.
DNS lookup using DNS Servers: DNS Lookup of the custom DNS Servers can be specified
to check the connectivity of the primary link.
Ping these IP addresses: These IP's will be pinged at regular intervals to check the
connectivity of the primary link.
Retry Interval is: The number tells the router how often it should run the above configured
failure detection method.
Failover after: This sets the number of retries after which failover is initiated.
DSR-1000, DSR-1000N, DSR-500, DSR-500N, DSR-250, DSR-250N, DSR-150, and DSR-150N
support 3G USB Modem as a failover link when the internet access is lost.
3.4.2 Load Balancing
This feature allows yo u to use mul tiple W AN links (and pres umably multiple ISP’s) simultaneously.
After configuring more than one WAN port, the load balancing option is available to carry traffic
over more than one link. Protocol bindings are used to segregate and assign services over one WAN
port in order to manage internet flow. The configured failure detection method is used at regular
intervals on all configured WAN ports when in Load Balancing mode.
DSR currently support three algorithms for Load Balancing:
Round Robin: This algorithm is particularly useful when the connection speed of one WAN port
greatly differs from another. In this case you can define protocol bindings to route low-latency
services (such as VOIP) over the higher-speed link and let low-volume background traffic (such as
SMTP) go over the lower speed link. Protocol binding is explained in next section.
Spillover: If Spillover method is selected, the primary WAN acts as a dedicated link until a defined
bandwidth threshold are reached. After this, the secondary WAN will be used for new connections.
Inbound connections on the secondary WAN are permitted with this mode, as the spillover logic
51
Page 53

Unified Services Router User Manual
governs outbound connections moving from the primary to secondary WAN. You can configure
spillover mode by using following options:
Load Tolerance: It is the percentage of bandwidth after which the router switches to secondary
WAN.
Max Bandwidth: This sets the maximum bandwidth tolerable by the primary WAN for outbound
traffic.
If the link bandwidth of outbound traffic goes above the load tolerance value of max bandwidth, the
router will spillover the next connections to secondary WAN.
For example, if the maximum bandwidth of primary WAN is 1 Kbps and the load tolerance is set to
70. Now every time a new connection is established the bandwidth increases. After a certain number
of connections say bandwidth reached 70% of 1Kbps, the new outbound connections will be spilledover to secondary WAN. The maximum value of load tolerance is 80% and the minimum is 20%.
DSR-1000, DSR-1000N, DSR-500 and DSR-500N support the traffic load balancing between physical
WAN port and the 3G USB Modem.
Load balancing is particularly useful when the connection speed of one WAN port greatly differs
from another. In this case you can define protocol bindings to route low-latency services (such as
VOIP) over the higher-speed link and let low-volume background traffic (such as SMTP) go over
the lower speed link.
52
Page 54

Unified Services Router User Manual
Figure 33: Load Balancing is available when multiple WAN ports are configured and
Protocol Bindings have been defined
3.4.3 Protocol Bindings
Advanced > Routing > Protocol Bindings
Protocol bindings are useful when the Load Balancing feature is in use. Choosing from a list of
configured services or any of the user-defined services, the type of traffic can be assigned to go over
only one of the available WAN ports. For increased flexibility the source network or machines can
53
Page 55

Unified Services Router User Manual
be specified as well as the destination network or machines. For example the VOIP traffic for a set
of LAN IP addresses can be assigned to one WAN and any VOIP traffic from the remaining IP
addresses can be assigned to the other WAN link. Protocol bindings are only applicable when load
balancing mode is enabled and more than one WAN is configured.
Figure 34: Protocol binding setup to associate a service and/or LAN source to a WAN
and/or destination network
3.4.4 IP Aliasing
Setup>Internet Settings>IP Aliasing
A single WAN ethernet port can be accessed via multiple IP addresses by adding an alias to the port.
This is done by configuring an IP Alias address.
54
Page 56

Unified Services Router User Manual
Figure 35: Configuring the IP Alias
Interface: Sets the interface on which IP Alias is being configured.
IP Address: Sets the IP address of the IP Alias.
Subnet Mask: Sets the Subnet Mask of the IP Alias.
Click Save Settings to save your changes.
Click Don't Save Settings to revert to the previous settings.
Figure 36: IP Alias Configuration
List of IP Aliases
The List of IP Aliases displays the configured IP Aliases on the router.
Interface Name: The interface on which the Alias was configured.
IP Address: The IP Address of the configured IP Alias.
Subnet Mask: The Subnet Mask of the configured IP Alias.
Edit: Opens the IP Alias configuration page to edit the selected IP Alias.
Add: Opens the IP Alias configuration page to add a new IP Alias.
55
Page 57

Unified Services Router User Manual
Delete: Deletes the selected IP Aliases.
3.5 Routing Configuration
Routing between the LAN and WAN will impact the way this router handles traffic that is received on
any of its physical interfaces. The routing mode of the gateway is core to the behavior of the traffic
flow between the secure LAN and the internet.
3.5.1 Routing Mode
Setup > Internet Settings > Routing Mode
This device supports classical routing, network address translation (NAT), and transport mode
routing.
With classical routing, devices on the LAN can be directly accessed from the internet by their
public IP addresses (assuming appropriate firewall settings). If your ISP has assigned an IP
address for each of the computers that you use, select Classic Routing.
NAT is a technique which allows several computers on a LAN to share an Internet connection.
The computers on the LAN use a "private" IP address range while the WAN port on the router
is configured with a single "public" IP address. Along with connection sharing, NAT also hides
internal IP addresses from the computers on the Internet. NAT is required if your ISP has
assigned only one IP address to you. The computers that connect through the router will need to
be assigned IP addresses from a private subnet.
When Transparent Routing Mode is enabled, NAT is not performed on traffic between LAN and
WAN. Broadcast and multicast packets that arrive on the LAN interface are switched to the
WAN and vice versa, if they do not get filtered by firewall or VPN policies. To maintain the
LAN and WAN in the same broadcast domain select Transparent mode, which allows bridging
of traffic from LAN to WAN and vice versa, except for router-terminated traffic and other
management traffic. All DSR features (such as 3G modem support) are supported in
transparent mode assuming the LAN and WAN are configured to be in the same broadcast
domain.
NAT routing has a feature called “NAT Hair-pinning” that allows internal net wo rk users on the LAN
and DMZ to access internal servers (e.g. an internal FTP server) using their externally-known domain
name. This is also referred to as “NAT loopback” since LAN ge nerated traffic is redirected through the
firewall to reach LAN servers by their external name.
When Bridge Mode routing is enabled, the first physical LAN port and secondary WAN/DMZ
(port 2) interfaces are bridged together at Layer 2, creating an aggregate network. The other
LAN ports and the primary WAN (WAN1) are not part of this bridge, and the router asks as a
56
Page 58

Unified Services Router User Manual
NAT device for these other ports. With Bridge mode for the LAN port 1 and WAN2/DMZ
interfaces, L2 and L3 broadcast traffic as well as ARP / RARP packets are passed through.
When WAN2 receives tagged traffic the tag information will be removed before the packet is
forwarded to the LAN port 1 interface.
Bridge mode option is available on DSR-500 / 500N / 1000 / 1000N products only.
Figure 37: Routing Mode to determine traffic routing between WAN and LAN
57
Page 59

Unified Services Router User Manual
3.5.2 Dynamic Routing (RIP)
DSR- 150/150N/250/250N does not support RIP.
Setup > Internet Settings > Routing Mode
Dynamic routing using the Routing Information Protocol (RIP) is an Interior Gateway Protocol
(IGP) that is common in LANs. With RIP this router can exchange routing information with other
supported routers in the LAN and allow for dynamic adjustment of routing tables in order to adapt to
modifications in the LAN without interrupting traffic flow.
The RIP direction will define how this router sends and receives RIP packets. Choose between:
Both: The router both broadcasts its routing table and also processes RIP information
received from other routers. This is the recommended setting in order to fully utilize RIP
capabilities.
Out Only: The router broadcasts its routing table periodically but does not accept RIP
information from other routers.
In Only: The router accepts RIP information from other routers, but does not broadcast its
routing table.
None: The router neither broadcasts its route table nor does it accept any RIP packets from
other routers. This effectively disables RIP.
The RIP version is dependent on the RIP support of other routing devices in the
LAN.
Disabled: This is the setting when RIP is disabled.
RIP-1 is a class-based routing version that does not include subnet information. This is the
most commonly supported version.
RIP-2 includes all the functionality of RIPv1 plus it supports subnet information. Though
the data is sent in RIP-2 format for both RIP-2B and RIP-2M, the mode in which packets are
sent is different. RIP-2B broadcasts data in the entire subnet while RIP-2M sends data to
multicast addresses.
If RIP-2B or RIP-2M is the selected version, authentication between this router and other routers
(configured with the same RIP version) is required. MD5 authentication is used in a first/second key
exchange process. The authentication key validity lifetimes are configurable to ensure that the
routing information exchange is with current and supported routers detected on the LAN.
58
Page 60

Unified Services Router User Manual
3.5.3 Static Routing
Advanced > Routing > Static Routing
Advanced > IPv6 > IPv6 Static Routing
Manually adding static routes to this device allows you to define the path selection of traffic from
one interface to another. There is no communication between this router and other devices to
account for changes in the path; once configured the static route will be active and effective until
the network changes.
The List of Static Routes displays all routes that have been added manually by an administrator and
allows several operations on the static routes. The List of IPv4 Static Routes and List of IPv6 Static
Routes share the same fields (with one exception):
Name: Name of the route, for identification and management.
Active: Determines whether the route is active or inactive. A route can be added to the table
and made inactive, if not needed. This allows routes to be used as needed without deleting
and re-adding the entry. An inactive route is not broadcast if RIP is enabled.
Private: Determines whether the route can be shared with other routers when RIP is enabled.
If the route is made private, then the route will not be shared in a RIP broadcast or
multicast. This is only applicable for IPv4 static routes.
Destination: the route will lead to this destination host or IP address.
IP Subnet Mask: This is valid for IPv4 networks only, and identifies the subnet that is
affected by this static route
Interface: The physical network interface (WAN1, WAN2, WAN3, DMZ or LAN), through
which this route is accessible.
Gateway: IP address of the gateway through which the destination host or network can be
reached.
Metric: Determines the priority of the route. If multiple routes to the same destination exist,
the route with the lowest metric is chosen.
59
Page 61

Unified Services Router User Manual
Figure 38: Static route configuration fields
3.5.4 OSPFv2
Advanced > Routing > OSPF
OSPF is an interior gateway protocol that routes Internet Protocol (IP) packets solely within a single
routing domain. It gathers link state information from available routers and constructs a topology map
of the network.
OSPF version 2 is a routing protocol which described in RFC2328 - OSPF Version 2. OSPF is IGP
(Interior Gateway Protocols).OSPF is widely used in large networks such as ISP backbone and
enterprise networks.
DSR-150, DSR-150N, DSR-250 and DSR-250 don't support OSPFv2.
60
Page 62

Unified Services Router User Manual
Figure 39: OSPFv2 configured parameters
Interface: The physical network interface on which OSPFv2 is Enabled/Disabled.
Status: This column displays the Enable/Disable state of OSPFv2 for a particular interface.
Area: The area to which the interface belongs. Two routers having a common segment; their
interfaces have to belong to the same area on that segment. The interfaces should belong to the same
subnet and have similar mask.
Priority: Helps to determine the OSPFv2 designated router for a network. The router with the highest
priority will be more eligible to become Designated Router. Setting the value to 0, makes the router
ineligible to become Designated Router. The default value is 1.Lower value means higher priority.
HelloInterval: The number of seconds for HelloInterval timer value. Setting this value, Hello packet
will be sent every timer value seconds on the specified interface. This value must be the same for all
routers attached to a common network. The default value is 10 seconds.
DeadInterval: The numb er of seco nds that a device’s hello packets must not ha ve been seen before its
neighbors declare the OSPF router down. This value must be the same for all routers attached to a
common network. The default value is 40 seconds.
OSPF requires these intervals to be exactly the same between two neighbors. If any of these intervals
are different, these routers will not become neighbors on a particular segment
Cost: The cost of sending a packet on an OSPFv2 interface.
Authentication Type:. This column displays the type of authentication to be used for OSPFv2.If
Authentication type is none the interface does not authenticate OSPF packets. If Authentication Type
is Simple then OSPF packets are authenticated using simple text key. If Authentication Type is MD5
then the interface authenticates OSPF packets with MD5 authentication.
61
Page 63

Unified Services Router User Manual
Figure 40: OSPFv2 configuration
3.5.5 OSPFv3
Advanced > IPv6 > OSPF
Open Shortest Path First version 3 (OSPFv3) supports IPv6 . To enable an OSPFv3 process on a
router, you need to enable the OSPFv3 process globally, assign the OSPFv3 process a router ID, and
enable the OSPFv3 process on related interfaces.
DSR-150, DSR-150N, DSR-250 and DSR-250 don't support OSPFv3.
62
Page 64

Unified Services Router User Manual
Figure 41: OSPFv3 configured parameters
Interface: The physical network interface on which OSPFv3 is Enabled/Disabled.
Status: This column displays the Enable/Disable state of OSPFv3 for a particular interface.
Priority: Helps to determine the OSPFv3 designated router for a network. The router with the highest
priority will be more eligible to become Designated Router. Setting the value to 0, makes the router
ineligible to become Designated Router. The default value is 1.Lower Value means higher priority.
HelloInterval: The number of seconds for HelloInterval timer value. Setting this value, Hello packet
will be sent every timer value seconds on the specified interface. This value must be the same for all
routers attached to a common network. The default value is 10 seconds.
DeadInterval: The number of seconds that a devic e’s hel lo packet s mus t not have been seen before its
neighbors declare the OSPF router down. This value must be the same for all routers attached to a
common network. The default value is 40 seconds.
OSPF requires these intervals to be exactly the same between two neighbors. If any of these intervals
are different, these routers will not become neighbors on a particular segment
Cost: The cost of sending a packet on an OSPFv3 interface.
63
Page 65

Unified Services Router User Manual
Figure 42: OSPFv3 configuration
3.5.6 6to4 Tunneling
Advanced > IPv6 > 6to4 Tunneling
6to4 is an Internet transition mechanism for migrating from IPv4 to IPv6, a system that
allows IPv6 packets to be transmitted over an IPv4 network. Select the check box to
Enable Automatic Tunneling and allow traffic from an IPv6 LAN to be sent over an
IPv4 Option to reach a remote IPv6 network.
Figure 43: 6 to 4 tunneling
64
Page 66

Unified Services Router User Manual
3.5.7 ISATAP Tunnels
Advanced > IPv6 > 6to4 Tunneling
ISATAP (Intra-Site Automatic Tunnel Addressing Protocol) is an IPv6 transition
mechanism meant to transmit IPv6 packets between dual-stack nodes on top of an IPv4
network. ISATAP specifies an IPv6-IPv4 compatibility address format as well as a means
for site border router discovery. ISATAP also specifies the operation of IPv6 over a
specific link layer - that being IPv4 used as a link layer for IPv6.
Figure 44: ISATAP Tunnels Configuration
ISATAP Subnet Prefix: This is the 64-bit subnet prefix that is assigned to the logical
ISATAP subnet for this intranet. This can be obtained from your ISP or internet registry,
or derived from RFC 4193.
End Point Address: This is the endpoint address for the tunnel that starts with this router.
The endpoint can be the LAN interface (assuming the LAN is an IPv4 network), or a
specific LAN IPv4 address.
IPv4 Address: The end point address if not the entire LAN.
3.6 Configurable Port - WAN Option
This router supports one of the physical ports to be configured as a secondary WAN Ethernet port or a
dedicated DMZ port. If the port is selected to be a secondary WAN interface, all configuration pages
relating to WAN2 are enabled.
65
Page 67

Unified Services Router User Manual
3.7 WAN 3 (3G) Configuration
This router supports one of the physical ports WAN3 to be configured for 3G internet access.
Setup > Internet Settings > WAN3 Setup
WAN3 configuration for the 3G USB modem is available only on WAN3 interface.
There are a few key elements of WAN 3 configuration.
Reconnect Mode: Select one of the following options
o Always On: The connection is always on.
o Username: Enter the username required to log in to the ISP.
o On Demand: The connection is automatically ended if it is idle for a specified number of
minutes. Enter the number of minutes in the Maximum Idle Time field. This feature is
useful if your ISP charges you based on the amount of time that you are connected.
Password: Enter the password required to login to the ISP.
Dial Number: Enter the number to dial to the ISP.
Authentication Protocol: Select one of None, PAP or CHAP Authentication Protocols to connect
to the ISP.
APN: Enter the APN (Access Point Name) provided by the ISP.
Domain Name System (DNS) Servers
Domain name servers (DNS) convert Internet names such as www.dlink.com, to IP addresses to
route traffic to the correct resources on the Internet. If you configure your router to get an IP
address dynamically from the ISP, then you need to specify the DNS server source in this section.
DNS Server Source: Choose one of the following options:
o Get Dynamically from ISP: Choose this option if your ISP did not assign a static DNS IP
address.
o Use These DNS Servers: Choose this option if your ISP assigned a static DNS IP address
for you to use. Also complete the fields that are highlighted white in this section.
o Primary DNS Server: Enter a valid primary DNS Server IP Address.
o Secondary DNS Server: Enter a valid secondary DNS Server IP Address.
Configurable Port: This page allows you to assign the functionality intended for the Configurable
Port. Choose from the following options:
o WAN: If this option is selected, configure the WAN3. The WAN Mode options are now
available as there are two WAN ports for the gateway.
66
Page 68

Unified Services Router User Manual
o DMZ: If this option is selected, you are able to configure the DMZ port on the DMZ
Configuration menu.
Click Save Settings to save your changes.
Click Don't Save Settings to revert to the previous settings.
Figure 45: WAN3 configuration for 3G internet
Cellular 3G internet access is available on WAN3 via a 3G USB modem for DSR-1000 and DSR1000N. The cellular ISP that provides the 3G data plan will provide the authentication requirements
to establish a connection. The dial Number and APN are specific to the cellular carriers. Once the
connection type settings are configured and saved, navigate to the WAN status page (Setup >
Internet Settings > WAN3 Status) and Enable the WAN3 link to establish the 3G connection.
The 3G USB modem can be configured as the third WAN in DSR-1000 and DSR- 1000N.
67
Page 69

Unified Services Router User Manual
3.8 WAN Port Settings
Advanced > Advanced Network > WAN Port Setup
The physical port settings for each WAN link can be defined here. If your ISP account defines the
WAN port speed or is associated with a MAC address, this information is required by the router to
ensure a smooth connection with the network.
The default MTU size supported by all ports is 1500. This is the largest packet size that can pass
through the interface without fragmentation. This size can be increased, however large packets can
introduce network lag and bring down the interface speed. Note that a 1500 byte size packet is the
largest allowed by the Ethernet protocol at the network layer.
The port speed can be sensed by the router when Auto is selected. With this option the optimal port
settings are determined by the router and network. The duplex (half or full) can be defined based on
the port support, as well as one of three port speeds: 10 Mbps, 100 Mbps and 1000 Mbps (i.e. 1
Gbps). The default setting is 100 Mbps for all ports.
The default MAC address is defined during the manufacturing process for the interfaces, and can
uniquely identify this router. You can customi ze ea ch WAN port’s MAC address as needed, either by
letting the WAN port assume the current LAN host’s MAC address or b y e nt ering a MAC address
manually.
68
Page 70

Unified Services Router User Manual
Figure 46: Physical WAN port settings
The 3G USB Modem can be configured as dedicated WAN2 for DSR-500 and DSR-500N as well as
dedicated WAN3 for DSR-1000 and DSR-1000N.
69
Page 71

Unified Services Router User Manual
Chapter 4. Wireless Access Point Setup
This router has an integrated 802.11n radio that allows you to create an access point for wireless LAN
clients. The security/encryption/authentication options are grouped in a wireless Profile, and each
configured profile will be available for selection in the AP configuration menu. The profile defines
various parameters for the AP, including the security between the wireless client and the AP, and can
be shared between multiple APs instances on the same device when needed.
Up to four unique wireless networks can be created b y configuri ng multiple “virtual” APs. Each such
virtual AP appears as an independent AP (unique SSID) to supported clients in the environment, but is
actually running on the same physical radio integrated with this router.
You will need the following information to configure your wireless network:
Types of devices expected to access the wireless network and their supported Wi-Fi™ modes
The router ’s geographical region
The security settings to use for securing the wireless network.
Profiles may be thought of as a grouping of AP parameters that can then be applied to not just one but
multiple AP instances (SSIDs), thus avoiding duplication if the same parameters are to be used on
multiple AP instances or SSIDs.
4.1 Wireless Settings Wizard
Setup > Wizard > Wireless Settings
The Wireless Network Setup Wizard is available for users new to networking. By going through a few
straightforward configuration pages you can enable a Wi-Fi™ ne twork on yo ur LAN a nd allow
supported 802.11 clients to connect to the configured Access Point.
70
Page 72

Unified Services Router User Manual
Figure 47: Wireless Network Setup Wizards
4.1.1 Wireless Network Setup Wizard
This wizard provides a step-by-step guide to create and secure a new access point on the router. The
network name (SSID) is the AP identifier that will be detected by supported clients. The Wizard
uses a TKIP+AES cipher for WPA / WPA2 security; depending on support on the client side,
devices associate with this AP using either WPA or WPA2 security with the same pre-shared key.
The wizard has the option to automatically generate a network key for the AP. This key is the preshared key for WPA or WPA2 type security. Supported clients that have been given this PSK can
associate with this AP. The default (auto-assigned) PSK is “pa ssphrase”.
The last step in the Wizard is to click the Connect button, which confirms the s ettings and enables
this AP to broadcast its availability in the LAN.
4.1.2 Add Wireless Device with WPS
With WPS enabled on your router, the selected access point allows supported WPS clients to join
the network very easily. When the Auto option for connecting a wireless device is chose, you will be
presented with two common WPS setup options:
71
Page 73

Unified Services Router User Manual
Personal Identification Number (PIN): The wireless device that supports WPS may have
an alphanumeric PIN, and if entered in this field the AP will establish a link to the client.
Click Connect to complete setup and connect to the client.
Push Button Configuration (PBC): for wireless devices that support PBC, press and hold
down on this button and within 2 minutes, click the PBC connect button. The AP will detect
the wireless device and establish a link to the client.
You need to enable at least one AP with WPA/WPA2 security and also enable WPS in the Advanced
> Wireless Settings > WPS page to use the WPS wizard.
4.1.3 Manual Wireless Network Setup
This button on the Wizard page will link to the Setup> Wireless Settings> Access Points page.
The manual options allow you to create new APs or modify the parameters of APs created by the
Wizard.
4.2 Wireless Profiles
Setup > Wireless Settings > Profiles
The profile allows you to assign the security type, encryption and authentication to use when
connecting the AP to a wireles s clie nt. The defa ult mode is “open”, i.e. no securit y. This mode is
insecure as it allows any compatible wireless clients to connect t o an AP configured with this security
profile.
To create a new profile, use a unique profile name to identify the combination of settings. Configure a
unique SSID that will be the identifier used by the clients to communicate to the AP using this
profile. By choosing to broadcast the SSID, compatible wireless clients within range of the AP can
detect thi s profile’s availability.
The AP offers all advanced 802.11 security modes, including WEP, WPA, WPA2 and WPA+WPA2
options. The security of the Access point is configured by the Wireless Security Type section:
Open: se le ct this option to create a public “open” net work to allo w unauthenticated devices to
access this wireless gateway.
WEP (Wired Equivalent Privacy): this option requires a static (pre-shared) key to be shared
between the AP and wireless client. Note that WEP does not support 802.11n data rates; is it
appropriate for legacy 802.11 connections.
WPA (Wi-Fi Protected Access): For stronger wireless security than WEP, choose this option. The
encryption for WPA will use TKIP and also CCMP if required. The authentication can be a preshared key (PSK), Enterprise mode with RADIUS server, or both. Note that WPA does not support
802.11n data rates; is it appropriate for legacy 802.11 connections.
WPA2: this security type uses CCMP encryption (and the option to add TKIP encryption) on either
PSK (pre-shared key) or Enterprise (RADIUS Server) authentication.
72
Page 74

Unified Services Router User Manual
WPA + WPA2: this uses both encryption algorithms, TKIP and CCMP. WPA clients will use TKIP
and WPA2 clients will use CCMP encryption algorithms.
“WPA+WPA2” i s a security option that allows devices to connect to an AP using the strongest
security that it supports. This mode allows legacy devices that only support WPA2 keys (such as an
older wireless printer) to connect to a secure AP where all the other wireless clients are using WPA2.
Figure 48: List of Available Profiles shows the options available to secure the
wireless link
4.2.1 WEP Security
If WEP is the chosen security option, you must set a unique static key to be shared with clients that
wish to access this secured wireless network. This static key can be generated from an easy-toremember passphrase and the selected encryption length.
Authentication: select between Open System, or Shared Key schemes
Encryption: select the encryption key size -- 64 bit WEP or 128 bit WEP. The larger size
keys provide stronger encryption, thus making the key more difficult to crack
WEP Passphrase: enter an alphanumeric phrase and click Generate Key to generate 4 unique
WEP keys with length determined by the encryption key size. Next choose one of the keys
to be used for authentication. The selected key must be shared with wireless clients to
connect to this device.
73
Page 75

Unified Services Router User Manual
Figure 49: Profile configuration to set network security
4.2.2 WPA or WPA2 with PSK
A pre-shared key (PSK) is a known passphrase configured on the AP and client both and is used to
authenticate the wireless client. An acceptable passphrase is between 8 to 63 characters in length.
4.3 Creating and Using Access Points
Setup > Wireless Settings > Access Points
Once a profile (a group of security settings) is created, it can be assigned to an AP on the router. The
AP SSID can be configured to broadcast its availability to the 802.11 environment can be used to
establish a WLAN network.
74
Page 76

Unified Services Router User Manual
The AP configuration page allows you to create a new AP and link to it one of the available
profiles. This router supports multiple AP’s refer red to as virtual access points (VAP s) . Each
virtual AP that has a unique SSIDs appears as an independent access point to clients. This
valuable feature allows the router’s radio to b e confi gured i n a way to optimize secur ity a nd
throughput for a group of clients as required by the user. To create a VAP, click the “add”
button on the Setup > Wireless Settings > Access Points page. After setting the AP name,
the profile dropdown menu is used to select one of the configured profiles.
The AP Name is a unique identifier used to manage the AP from the GUI, and is not the SSID that is
detected by clients when the AP has broadcast enabled.
Figure 50: Virtual AP configuration
A valuable power saving feature is the start and stop time control for this AP. You can conserve on
the radio power by disabling the AP when it is not in use. For example on evenings and weekends if
you know there are no wireless clients, the start and stop time will enable/disable the access point
automatically.
Once the AP settings are configured, you must enable the AP on the radio on the Setup > Wireless
Settings > Access Points page. The status field changes to “Enabled” if the AP is available to
accept wireless clients. If the AP is configured to broadcast its SSID (a profile parameter), a green
check mark indicating it is broadcasting will be shown in the List of Available Access points.
75
Page 77

Unified Services Router User Manual
Figure 51: List of configured access points (Virtual APs) shows one enabled access
point on the radio, broadcasting its SSID
The clients connected to a particular AP can be viewed by using the Status Button on the List of
Available Access Points. Traffic statistics are shown for that individual AP, as compared to the
summary stats for each AP on the Statistics table. Connected clients are sorted by the MAC address
and indicate the security parameters used by the wireless link, as well as the time connected to this
particular AP. Clicking the Details button next to the connected client will give the detailed send and
receive traffic statistics for the wireless link between this AP and the client.
4.3.1 Primary benefits of Virtual APs:
Optimize throughput: if 802.11b, 802.11 g, and 802.11n clients are expected to access the
LAN via this router, creating 3 VAPs will allow you to manage or shape traffic for each
group of clients. A unique SSID can be created for the network of 802.11b clients and
another SSID can be assigned for the 802.11n clients. Each can have different security
parameters – remember, the SSID and security of the link is determined by the profile. In
this way legacy clients can access the network without bringing down the overall throughput
of more capable 802.11n clients.
Optimize security: you may wish to support select legacy clients that only offer WEP
security while using WPA2 security for the majority of clients for the radio. By creating two
VAPs configured with different SSIDs and different security parameters, both types of
clients can connect to the LAN. Since WPA2 is more secure, you may want to broadcast this
SSID and not broadcast the SSID for the VAP with WEP since it is meant to be used for a
few legacy devices in this scenario.
76
Page 78

Unified Services Router User Manual
4.4 Tuning Radio Specific Settings
Setup > Wireless Settings > Radio Settings
The Radio Settings page lets you configure the channels and power levels available for the AP ’s
enabled on the DSR. The router has a dual band 802.11n radio, meaning either 2.4 GHz or 5 GHz
frequency of operation can be selected (not concurrently though). Based on the selected operating
frequency, the mode selection will let you define whether legacy connections or only 802.11n
connections (or both) are accepted on configured APs.
Figure 52: Radio card configuration options
The ratified 802.11n support on this radio requires selecting the appropriate broadcast (NA or NG
etc.) mode, and then defining the channel spacing and control side band for 802.11n traffic. The
default settings are appropriate for most networks. For example, changing the channel spacing to 40
MHz can improve bandwidth at the expense of supporting earlier 802.11n clients.
The available transmission channels are governed by regulatory constraints based on the region
setting of the router. The maximum transmission power is similarly governed by regulatory limits;
you have the option to decrease from the default maximum to reduce the signal strength of traffic out
of the radio.
4.5 WMM
Setup > Wireless Settings > WMM
Wi-Fi Multimedia (WMM) provides basic Quality of service (QoS) features to IEEE 802.11 networks.
WMM prioritizes traffic according to four Access Categories (AC) - voice, video, best effort, and
background.
77
Page 79

Unified Services Router User Manual
Figure 53: Wi-Fi Multimedia
Profile Name:
This field allows you to select the available profiles in wireless settings.
Enable WMM:
This field allows you to enable WMM to improve multimedia transmission.
Default Class of Service:
This field allows you to select the available Access Categories (voice, video, best effort, and
background).
4.6 Wireless distribution system (WDS)
Setup > Wireless Settings > WDS
Wireless distribution system is a system enabling the wireless interconnection of access points in a
network. This feature is only guaranteed to work only between devices of the same type.
78
Page 80

Unified Services Router User Manual
Figure 54: Wireless Distribution System
This feature is only guaranteed to work only between devices of the same type (i.e. using the same
chipset/driver). For example between two DSR250N boxes, or between two DSR1000N. It should also
interoperate between a DSR 1000N and DSR 500 N boxes since they are based on the same
chipset/driver.
When the user enables the WDS links use the same security configuration as the default access point.
The WDS links do not have true WPA/WPA2 support, as in there is no WPA key handshake
performed. Instead the Session Key to be used with a WDS Peer is computed using a hashing function
(similar to the one used for computing a WPA PMK). The inputs to this function are a PSK
(configurable by an administrator from the WDS page) and an internal "magic" string (nonconfigurable).
In effect the WDS links use TKIP/AES encryption, depending on the encryption configured for the
default AP. In case the default AP uses mixed encryption (TKIP + AES).The WDS link will use the
AES encryption scheme.
For a WDS link to function properly the Radio settings on the WDS peers have to be the same.
The WDS page would consist of two sections. The first section provides general WDS settings shared
by all its WDS peers.
WDS Enable - This would be a check box
79
Page 81

Unified Services Router User Manual
WDS Encryption - Displays the type of encryption used. It could be one of OPEN/64 bit WEP/128 bit
WEP/TKIP/AES (Use the term being used throughout the box i.e. either CCMP or AES).
WDS Passphrase - This is required if the encryption selected is TKIP/CCMP. We would expect it to
be within 8~63 ASCII characters. In the WDS configuration page this field is mandatory and has to be
same on the two WDS peers, when the security is configured in TKIP/AES mode. The WDS links use
this as the PSK for the connection.
DUT's Mac Address - This would be the mac address of this box. This should be configured in the
peer's WDS configuration page to be able to establish a WDS link with this box. This field in the
WDS Configuration section displays the device's mac address, which needs to be specified on the
WDS peer for making a connection to this device (Similarly the WDS peers MAC address will have to
be specified on this device for the WDS link to be established be tween the two devices).
The second section will have the list of configured WDS peers with buttons to Add/Delete Peer
entries. We support up to a maximum of 4 WDS links per box.
The both devices need to have same wireless settings (wireless mode, encryption, authentication
method, WDS passphrase, WDS MAC address and wireless SSID) when we configure WDS features in
DSR router.
The "Add WDS Peer" section allows the user to specify a WDS peer. The "WDS Peers" table displays
the list of WDS peers currently configured on the device. A maximum of 4 WDS peers can be
specified in any given mode.
4.7 Advanced Wireless Settings
Advanced > Wireless Settings > Advanced Wireless
Sophisticated wireless administrators can modify the 802.11 communication parameters in this page.
Generally, the default settings are appropriate for most networks. Please refer to the GUI integrated
help text for further details on the use of each configuration parameter.
80
Page 82

Unified Services Router User Manual
Figure 55: Advanced Wireless communication settings
4.8 Wi-Fi Protected Setup (WPS)
Advanced > Wireless Settings > WPS
WPS is a simplified method to add supporting wireless clients to the network. WPS is only applicable
for APs that employ WPA or WPA2 security. To use WPS, select the eligible VAPs from the
dropdown list of APs that have been configured with this security and enable WPS status for this AP.
The WPS Current Status section outlines the security, authentication, and encryption settings of the
selected AP. T hese are consistent with the AP ’s profile. There are two setup options available for
:
Personal Identification Number (PIN): The wireless device that supports WPS may have an
alphanumeric PIN, if so add the PIN in this field. The router will connect within 60 seconds of
clicking the “Configure via PIN” button imme diately below the PIN field . There is no LED
indication that a client has connected.
Push Button Configuration (PBC): for wireless devices that support PBC, press and hold down on
this button and within 2 minutes click the PBC connect button. The AP will detect the wireless
device and establish a link to the client.
More than one AP can use WPS, but only one AP can be used to establish WPS links to client at any
given time.
81
Page 83

Unified Services Router User Manual
Figure 56: WPS configuration for an AP with WPA/WPA2 profile
82
Page 84

Chapter 5. Securing the Private Network
You can secure your network by creating and applying rules that your router uses to
selectively block and allow inbound and outbound Internet traffic. You then specify
how and to whom the rules apply. To do so, you must define the following:
Services or traffic types (examples: web browsing, VoIP, other standard services
and also custom services that you define)
Direction for the traffic by specifying the source and destination of traffic; this is
done b y speci fying the “From Zone” (LAN/WAN/DMZ) and “To Zone”
(LAN/WAN/DMZ)
Schedules as to when the router should apply rules
Any Keywords (in a domain name or on a URL of a web page) that the router
should allow or block
Rules for allowing or blocking inbound and outbound Internet traffic for specified
services on specified schedules
MAC addresses of devices that should not access the internet
Port triggers that signal the router to allow or block access to specified services as
defined by port number
Reports and alerts that you want the router to send to you
You can, for example, establish restricted-access policies based on time-of-day, web
addresses, and web address keywords. You can block Internet access by applications
and services on the LAN, such as chat rooms or games. You can block just certain
groups of PCs on your network from being accessed by the WAN or public DMZ
network.
5.1 Firewall Rules
Advanced > Firewall Settings > Firewall Rules
Inbound (WAN to LAN/DMZ) rules restrict access to traffic entering your network,
selectively allowing only specific outside users to access specific local resources. By
default all access from the insecure WAN side are blocked from accessing the secure
LAN, except in response to requests from the LAN or DMZ. To allow outside devices
to access services on the secure LAN, you must create an inbound firewall rule for
each service.
If yo u wa nt to allow incoming tra ffic, you must make t he router’s W AN port IP
address known to the public. This is called “exposing your ho st.” Ho w you make your
address known depends on how the WAN ports are configured; for this router you
may use the IP address if a static address is assigned to the WAN port, or if your
WAN address is dynamic a DDNS (Dynamic DNS) name can be used.
Page 85

Unified Services Router User Manual
Outbound (LAN/DMZ to WAN) rules restrict access to traffic leaving your network,
selectively allowing only specific local users to access specific outside resources. The
default outbound rule is to allow access from the secure zone (LAN) to either the
public DMZ or insecure WAN. On other hand the default outbound rule is to deny
access from DMZ to insecure WAN. You can change this default behavior in the
Firewall Settings > Default Outbound Policy page. When the default outbound
policy is allow always, you can to block hosts on the LAN from accessing internet
services by creating an outbound firewall rule for each service.
Figure 57: List of Available Firewall Rules
5.2 Defining Rule Schedules
Tools > Schedules
Firewall rules can be enabled or disabled automatically if they are associated with a
configured schedule. The schedule configuration page allows you to define days of
the week and the time of day for a new schedule, and then this schedule can be
selected in the firewall rule configuration page.
All schedules will follow the time in the routers configured time zone. Refer to the
section on choosing your Time Zone and configuring NTP servers for more
information.
84
Page 86

Unified Services Router User Manual
Figure 58: List of Available Schedules to bind to a firewall rule
5.3 Configuring Firewall Rules
Advanced > Firewall Settings > Firewall Rules
All configured firewall rules on the router are displayed in the Firewall Rules list.
This list also indicates whether the rule is enabled (active) or not, and gives a
summary of the From/To zone as well as the services or users that the rule affects.
To create a new firewall rules, follow the steps below:
1. View the existing rules in the List of Available Firewall Rules table.
2. To edit or add an outbound or inbound services rule, do the following:
To edit a rule, click the checkbox next to the rule and click Edit to reach that r ule’s
configuration page.
To add a new rule, click Add to be taken to a ne w rule’s configuration page. Once
created, the new rule is automatically added to the original table.
3. Chose the From Zone to be the source of originating traffic: either the secure LAN, public
DMZ, or insecure WAN. For an inbound rule WAN should be selected as the From Zone.
4. Choose the To Zone to be the destination of traffic covered by this rule. If the From Zone
is the WAN, the To Zone can be the public DMZ or secure LAN. Similarly if the From
Zone is the LAN, then the To Zone can be the public DMZ or insecure WAN.
5. Parameters that define the firewall rule include the following:
Service: ANY means all traffic is affected by this rule. For a specific
service the drop down list has common services, or you can select a
custom defined service.
85
Page 87

Unified Services Router User Manual
Action & Schedule: Select one of the 4 actions that this rule defines:
BLOCK always, ALLOW always, BLOCK by schedule otherwise
ALLOW, or ALLOW by schedule otherwise BLOCK. A schedule must
be preconfigured in order for it to be available in the dropdown list to
assign to this rule.
Source & Destination users: For each relevant category, select the users
to which the rule applies:
Any (all users)
Single Address (enter an IP address)
Address Range (enter the appropriate IP address range)
Log: traffic that is filtered by this rule can be logged; this requires
configuring the router’s logging feature separately.
QoS Priority: Outbound rules (where To Zone = insecure WAN only)
can have the traffic marked with a QoS priority tag. Select a priority
level:
Normal-Service: ToS=0 (lowest QoS)
Minimize-Cost: ToS=1
Maximize-Reliability: ToS=2
Maximize-Throughput: ToS=4
Minimize-Delay: ToS=8 (highest QoS)
6. Inbound rules can use Destination NAT (DNAT) for managing traffic from the WAN.
Destination NAT is available when the To Zone = DMZ or secure LAN.
With an inbound allow rule you can enter the internal server address
that is hosting the selected service.
You can enable port forwarding for an incoming service specific rule
(From Zone = WAN) by selecting the appropriate checkbox. This will
allow the selected service traffic from the internet to reach the
appropriate LAN port via a port forwarding rule.
Translate Port Number: With port forwarding, the incoming traffic to
be forwarded to the port number entered here.
External IP address: The rule can be bound to a specific WAN interface
by selecting either the primary WAN or configurable port WAN as the
source IP address for incoming traffic.
86
Page 88

Unified Services Router User Manual
This router supports multi-NAT and so the External IP address does not necessarily
have to be the WAN address. On a single WAN interface, multiple public IP addresses
are supported. If your ISP assigns you more than one public IP address, one of these
can be used as your primary IP address on the WAN port, and the others can be
assigned to servers on the LAN or DMZ. In this way the LAN/DMZ server can be
accessed from the internet by its aliased public IP address.
7. Outbound rules can use Source NAT (SNAT) in order to map (bind) all LAN/DMZ traffic
matching the rule parameters to a specific WAN interface or external IP address (usually
provided by your ISP).
Once the new or modified rule parameters are saved, it appears in the master list of
firewall rules. To enable or disable a rule, click the checkbox next to the rule in the
list of firewall rules and choose Enable or Disable.
The router applies firewall rules in the order listed. As a general rule, you should move
the strictest rules (those with the most specific services or addresses) to the top of the
list. To reorder rules, click the checkbox next to a rule and click up or down.
87
Page 89

Unified Services Router User Manual
Figure 59: Example where an outbound SNAT rule is used to map an
external IP address (209.156.200.225) to a private DMZ IP
address (10.30.30.30)
88
Page 90

Unified Services Router User Manual
Figure 60: The firewall rule configuration page allows you to define the
To/From zone, service, action, schedules, and specify
source/destination IP addresses as needed.
89
Page 91

Unified Services Router User Manual
5.4 Configuring IPv6 Firewall Rules
Advanced > Firewall Settings > IPv6 Firewall Rules
All configured IPv6 firewall rules on the router are displayed in the Firewall Rules
list. This list also indicates whether the rule is enabled (active) or not, and gives a
summary of the From/To zone as well as the services or users that the rule affects.
Figure 61: The IPv6 firewall rule configuration page allows you to define
the To/From zone, service, action, schedules, and specify
source/destination IP addresses as needed.
90
Page 92

Unified Services Router User Manual
Parameter
Value
From Zone
Insecure (WAN1/WAN2/WAN3)
To Zone
Public (DMZ)
Service
HTTP
Action
ALLOW always
Send to Local Server (DNAT IP)
192.168.5.2 (web server IP address)
Destination Users
Any
Log
Never
Figure 62: List of Available IPv6 Firewall Rules
5.4.1 Firewall Rule Configuration Examples
Example 1: Allow inbound HTTP traffic to the DMZ
Situation: You host a public web server on your local DMZ network. You want to
allow inbound HTTP requests from any outside IP address to the IP address of your
web server at any time of day.
Solution: Create an inbound rule as follows.
Example 2: Allow videoconferencing from range of outside IP addresses
91
Page 93

Unified Services Router User Manual
Parameter
Value
From Zone
Insecure (WAN1/WAN2/WAN3)
To Zone
Secure (LAN)
Service
CU-SEEME:UDP
Action
ALLOW always
Send to Local Server (DNAT IP)
192.168.10.11
Destination Users
Address Range
From
132.177.88.2
To
134.177.88.254
Enable Port Forwarding
Yes (enabled)
Parameter
Value
From Zone
Insecure (WAN1/WAN2/WAN3)
To Zone
Public (DMZ)
Service
HTTP
Action
ALLOW always
Situation: You want to allow incoming videoconferencing to be initiated from a
restricted range of outside IP addresses (132.177.88.2 - 132.177.88.254), from a
branch office.
Solution: Create an inbound rule as follows. In the example, CUSeeMe (the video
conference service used) connections are allowed only from a specified range of
external IP addresses.
Example 3: Multi-NAT configuration
Situation: You want to configure multi-NAT to support multiple public IP
addresses on one WAN port interface.
Solution: Create an inbound rule that configures the firewall to host an additional
public IP address. Associate this address with a web server on the DMZ. If you
arrange with your ISP to have more than one public IP address for your use, you can
use the additional public IP addresses to map to servers on your LAN. One of these
public IP addresses is used as the primary IP address of the router. This address is
used to provide Internet access to your LAN PCs through NAT. The other addresses
are available to map to your DMZ servers.
The following addressing scheme is used to illustrate this procedure:
WAN IP address: 10.1.0.118
LAN IP address: 192.168.10.1; subnet 255.255.255.0
Web server host in the DMZ, IP address: 192.168.12.222
Access to Web server: (simulated) public IP address 10.1.0.52
92
Page 94

Unified Services Router User Manual
Send to Local Server (DNAT IP)
192.168.12.222 ( web server local IP address)
Destination Users
Single Address
From
10.1.0.52
WAN Users
Any
Log
Never
E
x
a
m
p
l
e
4: Bloc
Example 4: Block traffic by schedule if generated from specific range of machines
Use Case: Block all HTTP traffic on the weekends if the request originates from a
specific group of machines in the LAN having a known range of IP addresses, and
anyone coming in through the Network from the WAN (i.e. all remote users).
Configuration:
1. Setup a schedule:
To setup a schedule that affects traffic on weekends only, navigate to Security:
Schedule, and name the schedule “Wee ke nd”
Define “wee kend” to mean 12 am Saturday morning to 12 am Monday mor ni ng
– all day Saturday & Sunday
In the Scheduled days box, check that you want the schedule to be active for
“specific days”. Sele ct “Saturday” a nd “Sunday”
In the scheduled time of day, select “all day” – this will apply the schedule
between 12 am to 11:59 pm of the selected day.
Click apply – now schedule “Weekend” isolates all day Saturday and Sunday
from the rest of the week.
93
Page 95

Unified Services Router User Manual
Figure 63: Schedule configuration for the above example.
94
Page 96

Unified Services Router User Manual
2. Since we are trying to block HTTP requests, it is a service with To Zone: Insecure
(WAN1/WAN2/WAN3) that is to be blocked according to schedule “Weekend”.
3. Select the Action to “Block by Schedule, otherwise allow”. This will take a predefined
schedule and make sure the rule is a blocking rule during the defined dates/times. All
other times outside the schedule will not be affected by this firewall blocking rule
4. As we defined our schedule in schedule “Weekend”, this is available in the dropdown
menu
5. We want to block the IP range assigned to the marketing group. Let’s say they have IP
192.168.10.20 to 192.168.10.30. On the Source Users dropdown, select Address Range
and add this IP range as the From and To IP addresses.
6. We want to block all HTTP traffic to any services going to the insecure zone. The
Destination Users dropdown should be “any”.
7. We don’t need to change default QoS priority or Logging (unless desired) – clicking apply
will add this firewall rule to the list of firewall rules.
8. The last step is to enable this firewall rule. Select the rule, and click “enable” below the
list to make sure the firewall rule is active
5.5 Security on Custom Services
Advanced > Firewall Settings > Custom Services
Custom services can be defined to add to the list of services available during firewall
rule configuration. While common services have known TCP/UDP/ICMP ports for
95
Page 97

Unified Services Router User Manual
traffic, many custom or uncommon applications exist in the LAN or WAN. In the
custom service configuration menu you can define a range of ports and identify the
traffic type (TCP/UDP/ICMP) for this service. Once defined, the new service will
appear in the services list of the firewall rules configuration menu.
96
Page 98

Unified Services Router User Manual
Figure 64: List of user defined services.
Figure 65: Custom Services configuration
Created services are available as options for firewall rule configuration.
97
Page 99

Unified Services Router User Manual
Name: Name of the service for identification and management purposes.
Type: The layer 3 Protocol that the service uses. (TCP, UDP, BOTH, ICMP or
ICMPv6)
Port Type: This fields allows to select Port Range or Multiple Ports
ICMP Type: This field is enabled when the layer 3 protocol (in the Type field) is
selected as ICMP or ICMPv6. The ICMP type is a numeric value that can range
between 0 and 40, while for ICMPv6 the type ranges from 1 to 255. For a list of
ICMP types, visit the following URL: http://www.iana.org/assignments/icmp-
parameters.
Start Port: The first TCP, UDP or BOTH port of a range that the service uses. If the
service uses only one port, then the Start Port will be the same as the Finish Port.
Finish Port: The last port in the range that the service uses. If the service uses only
one port, then the Finish Port will be the same as the Start Port.
Port: The port that the service uses.
5.6 ALG support
Advanced > Firewall Settings > ALGs
Application Level Gateways (ALGs) are security component that enhance the firewall
and NAT support of this router to seamlessly support application layer protocols. In
some cases enabling the ALG will allow the firewall to use dynamic ephemeral TCP/
UDP ports to communicate with the known ports a particular client application (such
as H.323 or RTSP) requires, without which the admin would have to open large
number of ports to accomplish the same support. Because the ALG understands the
protocol used by the specific application that it supports, it is a very secure and
efficient way o f introducing support for client applications throug h the router ’s
firewall.
98
Page 100

Unified Services Router User Manual
Figure 66: Available ALG support on the router.
5.7 VPN Passthrough for Firewall
Advanced > Firewall Settings > VPN Passthrough
This router ’s firewall settings can be configured to allow encrypted VPN traffic for
IPsec, PPTP, and L2TP VPN tunnel connections between the LAN and internet. A
specific firewall rule or service is not appropriate to introduce this passthrough
support; instead the appropriate check boxes in the VPN Passthrough page must be
enabled.
99
 Loading...
Loading...