Page 1
Using the Conguration Menu (continued)
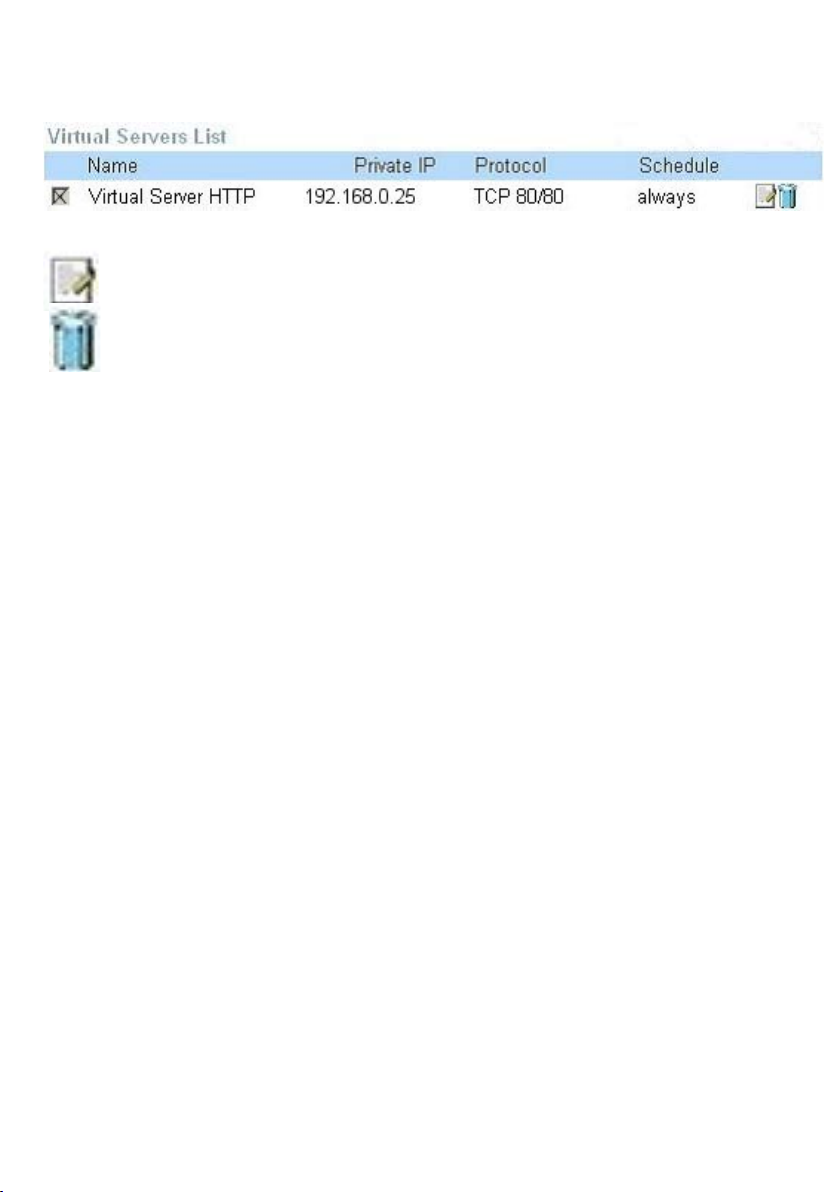
Advanced > Virtual Server continued
Click on this icon to edit the virtual service
Click on this icon to delete the virtual service
Example #2:
If you have an FTP server that you wanted Internet users to access by WAN port
2100 and only during the weekends, you would need to enable it as such. FTP
server is on LAN computer 192.168.0.30. FTP uses port 21, TCP.
Name: FTP Server
Private IP: 192.168.0.30
Protocol Type: TCP
Private Port: 21
Public Port: 2100
Schedule: From: 01:00AM to 01:00AM, Sat to Sun
All Internet users who want to access this FTP Server
must connect to it from port 2100. This is an example of
port redirection and can be useful in cases where there
are many of the same servers on the LAN network.
21
Page 2
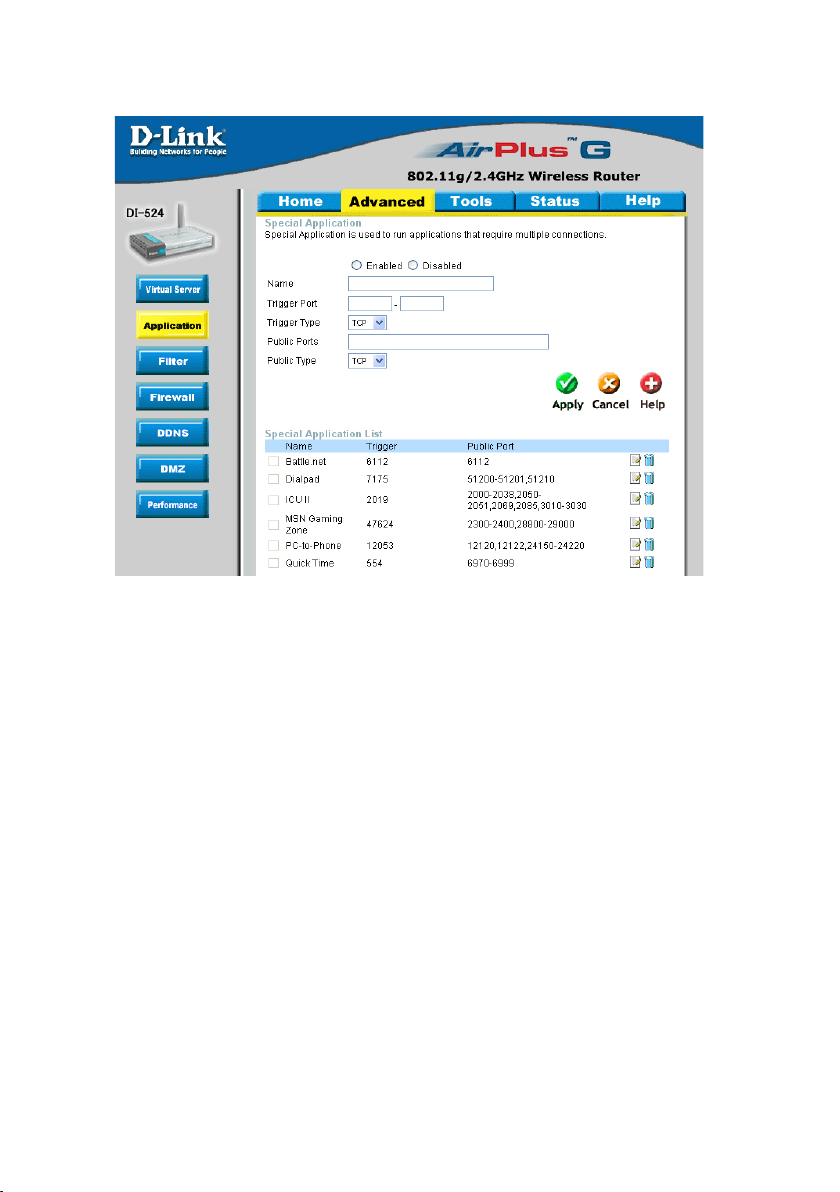
Using the Conguration Menu (continued)
Advanced > Applications
Some applications require multiple connections, such as Internet gaming, video
conferencing, Internet telephony and others. These applications have difculties working
through NAT (Network Address Translation). Special Applications makes some of these
applications work with the DI-524. If you need to run applications that require multiple
connections, specify the port normally associated with an application in the “Trigger Port”
eld, select the protocol type as TCP or UDP, then enter the public ports associated
with the trigger port to open them for inbound trafc.
The DI-524 provides some predened applications in the table on the bottom of the
web page. Select the application you want to use and enable it.
Note! Only one PC can use each Special Application tunnel.
Name:
Trigger Port:
Trigger Type:
Public Port:
Public Type:
This is the name referencing the special application.
This is the port used to trigger the application. It can be either
a single port or a range of ports.
This is the protocol used to trigger the special application.
This is the port number on the WAN side that will be used
to access the application. You may dene a single port or a
range of ports. You can use a comma to add multiple ports or
port ranges.
This is the protocol used for the special application.
22
Page 3
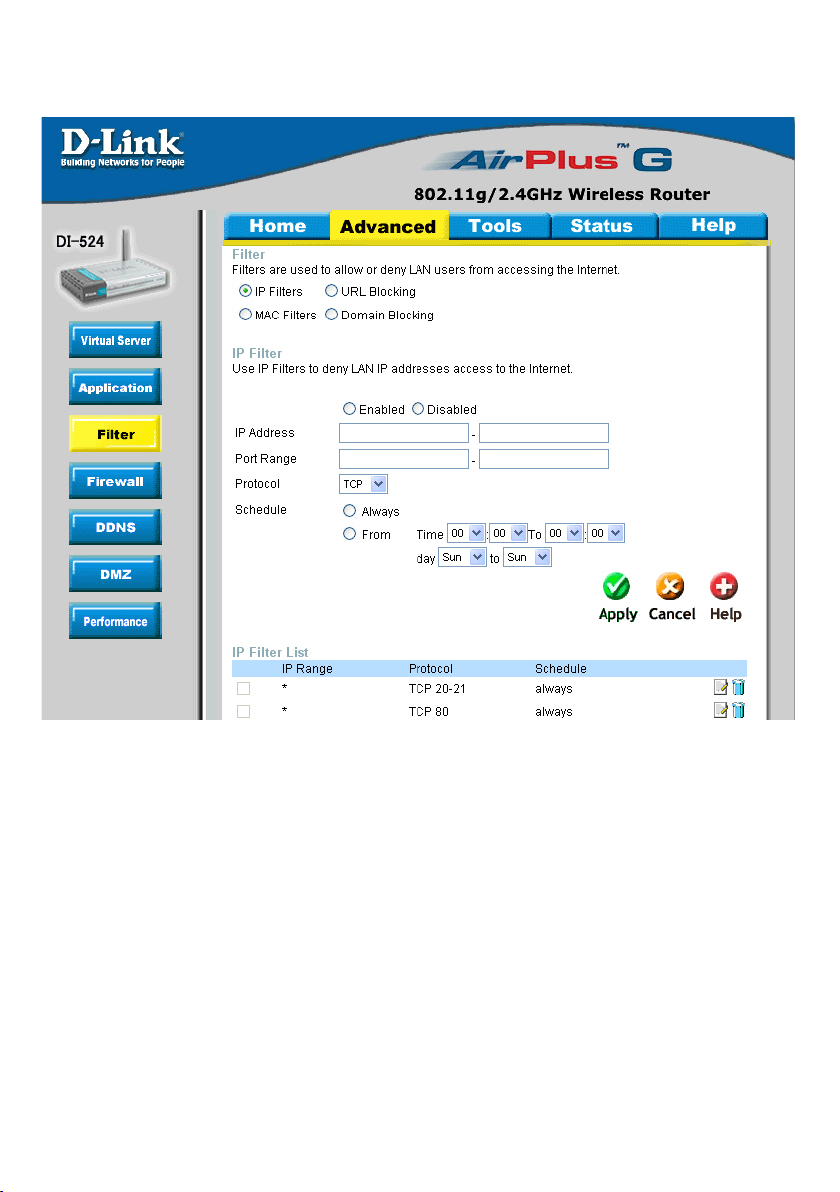
Using the Conguration Menu (continued)
Advanced > Filters > IP Filters
Filters are used to deny or allow LAN (Local Area Network) computers from accessing
the Internet. The DI-524 can be setup to deny internal computers by their IP or MAC
addresses. The DI-524 can also block users from accessing restricted web sites.
IP Filters:
IP Address:
Port Range:
Protocol Type:
Schedule:
IP Filter is used to deny LAN IP addresses from accessing
the Internet. You can deny specic port numbers or all ports
for the specic IP address.
The IP address of the LAN computer that will be denied
access to the Internet.
The single port or port range that will be denied access to the
Internet.
Select the protocol type
This is the schedule of time when the IP Filter will be enabled.
23
Page 4

Using the Conguration Menu (continued)
Advanced > Filters > URL Blocking
URL Blocking is used to deny LAN computers from accessing specic web sites by the
URL. A URL is a specially formatted text string that denes a location on the Internet.
If any part of the URL contains the blocked word, the site will not be accessible and
the web page will not display. To use this feature, enter the text string to be blocked
and click Apply. The text to be blocked will appear in the list. To delete the text, just
highlight it and click Delete.
Filters-
URL Blocking-
Keywords-
Select the lter you wish to use; in this case, URL Blocking
was chosen.
Select Enabled or Disabled.
Enter the keywords in this eld. Block URLs which contain
keywords listed below.
24
Page 5

Using the Conguration Menu
Advanced > Filters > MAC Filters
(continued)
Use MAC (Media Access Control) Filters to allow or deny LAN (Local Area Network)
computers by their MAC addresses from accessing the Network. You can either manually
add a MAC address or select the MAC address from the list of clients that are currently
connected to the Broadband Router.
Filters-
MAC Filters-
Name-
MAC Address-
DHCP Client-
Select the lter you wish to use; in this case, MAC lters was
chosen.
Choose Disable MAC lters; allow MAC addresses listed
below; or deny MAC addresses listed below.
Enter the name here.
Enter the MAC Address.
Select a DHCP client from the pull-down list; click Clone to
copy that MAC Address.
25
Page 6

Using the Conguration Menu
Advanced > Filters > Domain Blocking
(continued)
Domain Blocking is used to allow or deny LAN (Local Area Network) computers from
accessing specic domains on the Internet. Domain blocking will deny all requests to
a specic domain such as http and ftp. It can also allow computers to access specic
sites and deny all other sites.
Filters-
Select the lter you wish to use; in this case, Domain Blocking was chosen.
Domain Blocking-
Disabled-
Allow-
Deny-
Blocked Domains-
Select Disabled to disable Domain Blocking
Allows users to access all domains except Blocked Domains
Denies users access to all domains except
Permitted Domains
Enter the Blocked Domains in this eld
Permitted
Domains-
Enter the Permitted Domains in this eld
26
Page 7

Using the Conguration Menu (continued)
Advanced > Firewall
Firewall Rules is an advanced feature used to deny or allow trafc from passing
through the DI-524. It works in the same way as IP Filters with additional settings. You
can create more detailed access rules for the DI-524. When virtual services are created
and enabled, it will also display in Firewall Rules. Firewall Rules contain all network
rewall rules pertaining to IP (Internet Protocol).
In the Firewall Rules List at the bottom of the screen, the priorities of the rules are from
top (highest priority) to bottom (lowest priority.)
Note:
The DI-524 MAC Address ltering rules have precedence over the Firewall Rules.
Firewall Rules-
Name-
Action-
Source-
Destination-
Schedule-
Enable or disable the Firewall
Enter the name
Allow or Deny
Enter the IP Address range
Enter the IP Address range; the Protocol;
and the Port Range
Select Always or enter the Time Range.
27
Page 8

Using the Conguration Menu (continued)
Advanced > DDNS
Users who have a Dynamic DDNS account may use this feature on the DI-524.
Provider-
Host Name-
Username/Email-
Password/Key-
Select from the list of DDNS servers available.
Enter your DDNS account host name.
Enter your DDNS account username.
Enter your DDNS account password.
28
Page 9

Using the Conguration Menu (continued)
Advanced > DMZ
If you have a client PC that cannot run Internet applications properly from behind the DI524, then you can set the client up for unrestricted Internet access. It allows a computer
to be exposed to the Internet. This feature is useful for gaming purposes. Enter the IP
address of the internal computer that will be the DMZ host. Adding a client to the DMZ
(Demilitarized Zone) may expose your local network to a variety of security risks, so
only use this option as a last resort.
DMZ-
IP Address-
Enable or Disable the DMZ. The DMZ (Demilitarized Zone)
allows a single computer to be exposed to the internet. By
default the DMZ is disabled.
Enter the IP Address of the computer to be in the DMZ
29
Page 10

Using the Conguration Menu (continued)
Advanced > Performance
Beacon Interval-
RTS Threshold-
Fragmentation-
DTIM Interval-
Wireless Mode-
TX Rates-
SSID Broadcast-
Beacons are packets sent by an Access Point to synchronize
a wireless network. Specify a value. 100 is the default setting
and is recommended.
This value should remain at its default setting of 2432. If incon
sistent data ow is a problem, only a minor modication should
be made.
The fragmentation threshold, which is specied in bytes, determines whether packets will be fragmented. Packets exceeding
the 2346 byte setting will be fragmented before transmission.2346 is the default setting
(Delivery Trafc Indication Message) 3 is the default setting. A
DTIM is a countdown informing clients of the next window for
listening to broadcast and multicast messages.
Select Short or Long Preamble. The Preamble denes the
length of the CRC block (Cyclic Redundancy Check is a common technique for detecting data transmission errors) for
communication between the wireless router and the roaming
wireless network adapters. Note: High network trafc areas
should use the shorter preamble type.
Auto is the default selection. Selct from the drop down menu.
Choose Enabled to broadcast the SSID across the network.
All devices on a network must share the same SSID (Service
Set Identier) to establish communication. Choose Disabled
if you do not wish to broadcast the SSID over the network.
-
30
 Loading...
Loading...