Page 1

ADMINISTRATION
Cisco RV215W Wireless-N VPN Firewall
GUIDE
Page 2

Revised Sep 2014
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list
of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their
respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Page 3
Contents
Chapter 4: Introduction 9
Verifying the Hardware Installation 9
Using Setup Wizard 10
Configuration Next Steps 11
Using the Getting Started Page 11
Saving Changes 13
Connecting to Your Wireless Network 13
Chapter 5: Viewing the Device Status 14
Viewing the Dashboard 14
Viewing the System Summary 16
Viewing Wireless Statistics 19
Viewing the VPN Status 20
Viewing the IPSec Connection Status 21
Viewing Logs 22
Viewing Connected Devices 23
Viewing Port Statistics 23
Viewing the Guest Network Status 24
Viewing the Mobile Network Status 25
Chapter 6: Configuring Networking 26
Configuring the WAN Settings 27
Configuring the Wired WAN Connections 27
Configuring DHCP 27
Configuring Static IP 27
Configuring PPPoE 28
Configuring PPTP 29
Configuring L2TP 30
Configuring Optional Settings 32
Configuring a Mobile Network 32
Global Settings 33
Mobile Network Setup 34
RV215W Wireless-N VPN Firewall Administration Guide 3
Page 4
Contents
Bandwidth Cap Setting 35
E-mail Setting 36
Setting Failover and Recovery 36
WAN/USB Device Update 37
Configuring the LAN Settings 38
Changing the Device Management IP Address 38
Configuring the DHCP Server 39
Configuring VLANs 40
Configuring Static DHCP 42
Viewing DHCP Leased Clients 43
Configuring a DMZ Host 43
Configuring RSTP 44
Port Management 45
Cloning the MAC Address 46
Configuring Routing 47
Configuring the Operating Mode 47
Configuring Dynamic Routing 48
Configuring Static Routing 49
Viewing the Routing Table 50
Configuring Dynamic DNS 50
Configuring the IP Mode 52
Configuring IPv6 53
Configuring the IPV6 WAN Connection 53
Configuring IPv6 LAN Connections 57
Configuring IPv6 Static Routing 59
Configuring Routing (RIPng) 60
Configuring Tunneling 61
Viewing IPv6 Tunnel Status 62
Configuring Router Advertisement 62
Configuring Advertisement Prefixes 64
Chapter 7: Configuring the Wireless Network 66
RV215W Wireless-N VPN Firewall Administration Guide 4
Page 5
Contents
Wireless Security 66
Wireless Security Tips 66
General Network Security Guidelines 68
Cisco RV215W Wireless Networks 68
Configuring Basic Wireless Settings 69
Editing the Wireless Network Settings 71
Configuring the Security Mode 72
Configuring MAC Filtering 75
Configuring Time of Day Access 76
Configuring the Wireless Guest Network 76
Configuring Advanced Wireless Settings 78
Configuring WDS 81
Configuring WPS 82
Chapter 8: Configuring the Firewall 84
Cisco RV215W Firewall Features 84
Configuring Basic Firewall Settings 85
Configuring Remote Management 88
Configuring Universal Plug and Play 89
Managing Firewall Schedules 89
Adding or Editing a Firewall Schedule 89
Configuring Services Management 90
Configuring Access Rules 91
Adding Access Rules 92
Creating an Internet Access Policy 94
Adding or Editing an Internet Access Policy 94
Configuring Port Forwarding 96
Configuring Single Port Forwarding 96
Configuring Port Range Forwarding 97
Configuring Port Range Triggering 98
RV215W Wireless-N VPN Firewall Administration Guide 5
Page 6
Contents
Chapter 9: Configuring VPN 100
VPN Tunnel Types 100
VPN Clients 101
Configuring PPTP 101
Configuring QuickVPN 102
Configuring NetBIOS over VPN 102
Creating and Managing PPTP Users 102
Creating and Managing QuickVPN Users 103
Importing VPN Client Settings 104
Configuring Basic Site-to-Site IPsec VPN Settings 104
Viewing Default Values 106
Configuring Advanced VPN Parameters 106
Managing IKE Policies 106
Adding or Editing IKE Policies 107
Managing VPN Policies 109
Adding or Editing VPN Policies 109
Configuring Certificate Management 112
Configuring VPN Passthrough 114
Chapter 10: Configuring Quality of Service (QoS) 116
Configuring Bandwidth Management 116
Configuring Bandwidth 117
Configuring Bandwidth Priority 117
Configuring QoS Port-Based Settings 119
Configuring CoS Settings 120
Configuring DSCP Settings 121
Chapter 11: Administering Your Router 122
Setting Password Complexity 123
Configuring User Accounts 124
Setting the Session Timeout Value 125
RV215W Wireless-N VPN Firewall Administration Guide 6
Page 7
Contents
Configuring Simple Network Management (SNMP) 125
Configuring SNMP System Information 125
Editing SNMPv3 Users 126
Configuring the SNMP Traps 127
Using Diagnostic Tools 128
Network Tools 128
Configuring Port Mirroring 130
Configuring Logging 130
Configuring Logging Settings 130
Configuring E-mail Settings 132
Configuring Bonjour 134
Configuring Date and Time Settings 134
Backing Up and Restoring the System 135
Backing Up the Configuration Settings 136
Restoring the Configuration Settings 137
Copying the Configuration Settings 138
Generating an Encryption Key 138
Upgrading Firmware or Changing the Language 139
Upgrading Firmaware Automatically 139
Upgrading Firmware Manually 140
Changing the Language 141
Restarting the Cisco RV215W 141
Restoring the Factory Defaults 142
Running the Setup Wizard 142
Appendix A: Using Cisco QuickVPN 143
Overview 143
Before You Begin 143
Installing the Cisco QuickVPN Software 144
Installing from the CD-ROM 144
Downloading and Installing from the Internet 146
RV215W Wireless-N VPN Firewall Administration Guide 7
Page 8
Contents
Using the Cisco QuickVPN Software 146
Appendix B: Where to Go From Here 149
RV215W Wireless-N VPN Firewall Administration Guide 8
Page 9

Introduction
!
This chapter provides information to guide you through the installation process,
and get started using the browser-based Device Manager.
4
• Verifying the Hardware Installation
• Using Setup Wizard
• Using the Getting Started Page
• Connecting to Your Wireless Network
Verifying the Hardware Installation
Configure the device to connect to your wired and wireless networks using the
Cisco RV215W Wireless-N VPN Firewall Quick Start Guide.
CAUTION Use the 12V , 1.67 a power supply pr ovided with the device. Using a different power
supply could cause poor performance or damage the device.
To verify the hardware installation and connection to the Internet, complete the
following tasks:
STEP 1 Check the LED states. For more information, see Cisco RV215W Wireless-N VPN
Firewall Quick Start Guide provided with the device.
STEP 2 Connect a computer to an available LAN port and verify that you can connect to a
website on the Internet, such as www.cisco.com.
STEP 3 Using a PC with a wireless feature, connect to a website on the Internet, such as
ww w.cisco.com. To configure your radio, see Connecting to Your Wireless
Network.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 9
Page 10
Introduction
Using Setup Wizard
Using Setup Wizard
Setup Wizard and Device Manager are supported on Microsoft Internet Explorer
6.0 or later, Mozilla Firefox 3.0 or later, and Apple Safari 3.0 or later.
To use Setup Wizard:
STEP 1 Start the computer that you connected to a LAN port.
Your compute r becom es a DH CP cl ien t of the d evice and r eceiv es an I P ad dr ess in
the 192.168.1.xxx range.
STEP 2 Launch a web browser and enter 192.168.1.1 in the Address bar. This is the
default IP address of the device.
A message appears about the site security certificate. The device uses a self-
signed security certificate and this message appears because the device is not
known to your computer.
4
STEP 3 Click Continue to this website (or the option shown on your particular web
browser) to go to the web site. The login page displays.
STEP 4 Enter the user name and password.
The default user name is cisco. The default password is cisco. Passwords are
case sensitive .
STEP 5 Click Log In. Setup Wizard starts.
STEP 6 Follow the on-screen instructions to set up the device.
Setup Wizard tries to automatically detect and configure your connection. If it
cannot, Setup Wizard might ask you for information about your Internet connection.
You might need to contact your ISP to obtain this information.
After Setup Wizard is done configuring the device, you are required to change the
default password. Follow the on-screen instructions. After changing the default
password, the Getting Started page appears.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 10
Page 11

Introduction
Using the Getting Started Page
Configuration Next Steps
Although Setup Wizard automatically configures the device, we suggest
customizing some settings to provide better security and performance:
4
• If you already hav e a DHCP server on your network and you do not want the
device to act as a network DHCP server, disable the server . See Configuring
the LAN Settings.
• Configure your V irtual Private Network (VPN) by using QuickVPN. QuickVPN
is included on the CD that shipped with your firewall. See Appendix A,
“Using the Cisco QuickVPN Software.”
• The device supports up to four wireless networks. You can only set up one
wireless network (or SSID) by using Setup Wizard. To configure additional
wireless networks using Device Manager, see Configuring the Wireless
Network.
Using the Getting Started Page
The Getting Started page displays the most common device configuration tasks.
Use the links on this page to jump to the relevant configuration page.
This page appears every time you start Device Manager. To change this behavior,
check Don’t show on start up.
Initial Settings
Change Default
Administrator Passwor d
Launch Setup Wizard Launches the Setup Wizard. Follow the on-screen
Displays the Users page where you can change
the administrator password and set up a guest
account. See Configuring User Accounts.
instructions.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 11
Page 12

Introduction
Using the Getting Started Page
4
Configure WAN Settings Opens the Internet Setup page to change
parameters such as the router host name. See
Configuring the WAN Settings.
Configure LAN Settings Opens the LAN Configuration page to modify the
LAN parameters, such as the management IP
address. See Configuring the LAN Settings.
Configure Wireless
Settings
Quick Access
Upgrade Router
Firmware
Add VPN Clients Opens the VPN Clients page to manage virtual
Configure Remote
Management Access
Device Status
System Summary Displays the System Summary page that shows
Open the Basic Settings page to manage the
radio. See Configuring the Wireless Network.
Open the Firmware/Language Upgrade page to
update the router firmware or language pack. See
Upgrading Firmware or Changing the Language.
private networks. See VPN Clients.
Opens the Basi c Se tt in g s page to enable the basic
features of the router. See Configuring Basic
Firewall Settings.
the state of the router. See Viewing the System
Summary.
Wireless Status Displays the Wireless Statistics page that shows
the state of the radio. See Viewing Wireless
Statistics.
VPN Status Displays the VPN Status page that lists the VPN
managed by this router. See Viewing the VPN
Status.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 12
Page 13

Introduction
Connecting to Your Wireless Network
Other Resources
Support Click to open the Cisco support page.
Forums Click to visit Cisco online support forums.
Saving Changes
When you finish making changes on a configuration page, click Save to save the
changes in flash memory, or click Cancel to undo your changes.
Connecting to Your Wireless Network
4
To connect a client device (such as a computer) to your wireless network,
configure the wireless connection on the device with the wireless security
information you configured for your device using Setup Wizard.
The following steps are provided as an example; it might be necessary to
configure client device differently. For instructions that are specific to the client
device, consult the device documentation.
STEP 1 Open the wireless connection settings window or program for your device.
Your computer might have special software installed to manage wireless
connections, or you might find the wireless connections under the Control Panel in
the Network Connections or Network and Internet window. (The location
depends on your operating system.)
STEP 2 Enter the network name (SS I D) you chose for your network in Setup Wizard.
STEP 3 Choose the type of encryption and enter the security key that you specified in
Setup Wizard.
If you did not enable security (not recommended), leave the wireless encryption
fields that were configured with the security type and passphrase blank.
STEP 4 Verify your wireless connection and save your settings.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 13
Page 14
Introduction
Connecting to Your Wireless Network
4
Cisco RV215W Wireless-N VPN Firewall Administration Guide 14
Page 15

Viewing the Device Status
This chapter describes how to view real-time statistics and other information
about the device.
• Viewing the Dashboard
• Viewing the System Summary
• Viewing Wireless Statistics
5
• Viewing the VPN Status
• Viewing Logs
• Viewing Connected Devices
• Viewing Port Statistics
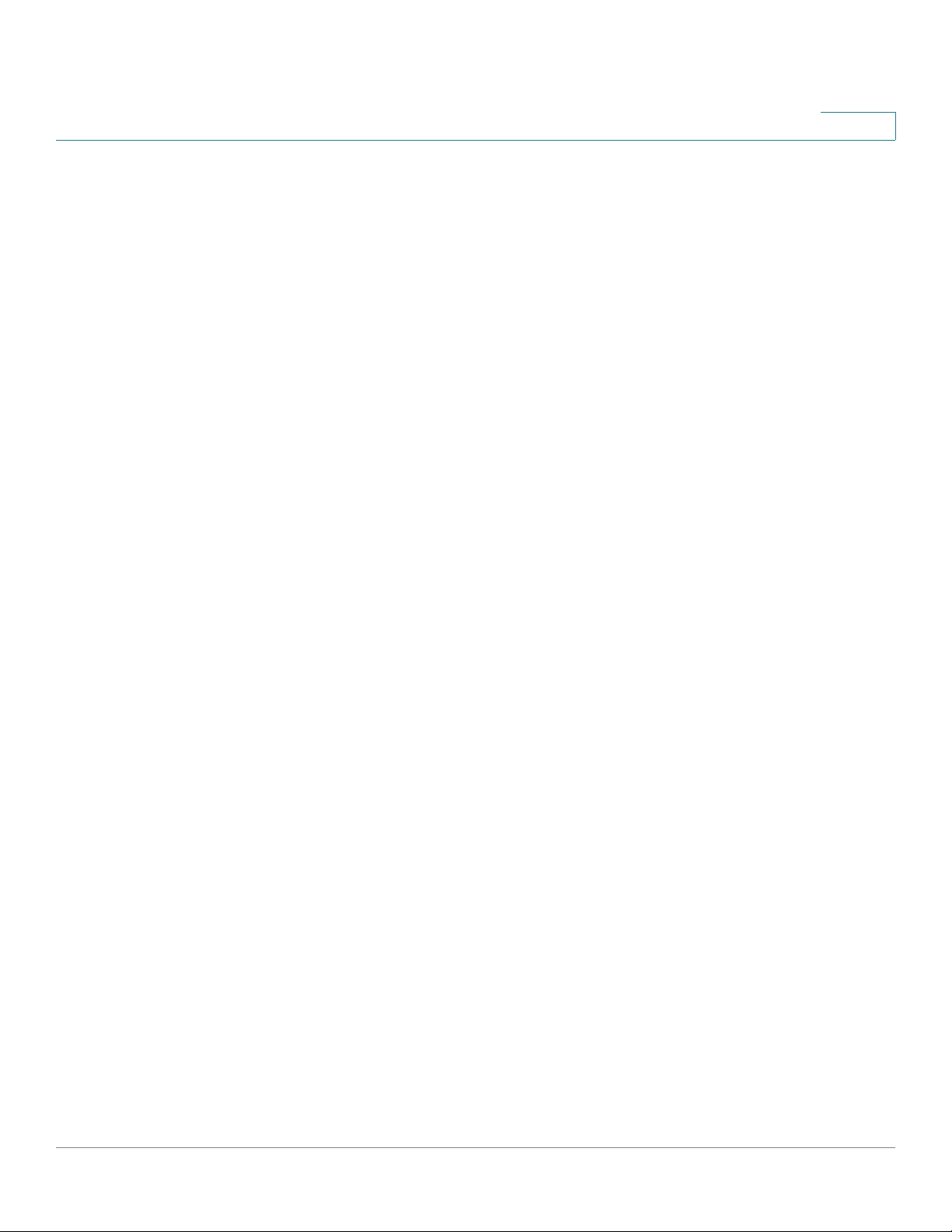
Viewing the Dashboard
The Dashboard page provides important router information.
To view the Dashboard, choose Status > Dashboard.
To change the refresh rate of the statistics and parameter values displa y ed, select
the frequency from the Refresh Rate drop-down menu.
To display an interactive view of the router back panel, click Show Panel View.
The back panel view shows you the ports that are connected to a device (lit
green).
• To view a port connection information, mouse-over the port.
• To refresh the port information, click Refresh.
• To close the port information window, click Close.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 14
Page 16
Viewing the Device Status
Viewing the Dashboard
The Dashboard page displays the following:
Device Information
Resource Utilization
5
• System Name—Name of the device.
• Firmware Version—Firmware version the device is currently running.
• Serial Number—Serial number of the device.
• CPU—CPU utilization.
• Memory—Memory utilization.
• Current Time—Time of day.
• System Up Time—How long the system has been running.
Syslog Summary
Indicates whether logging is enabled for these event categories:
• Emergency
• Alert
• Critical
• Error
• Warning
To view the logs, click details. For more information see Viewing Logs.
To manage logs, click manage logging. For more information, see Configuring
Logging Settings.
LAN (Local Network) Interface
• MAC Address—The MAC address of the device.
• IPv4 Address—Management IP address of the device.
• IPv6 Address—Management IP address of the device (when IPv6 is
enabled).
• DHCP Ser ver—Status of the device IPv4 DHCP server (enabled or
disabled).
Cisco RV215W Wireless-N VPN Firewall Administration Guide 15
Page 17
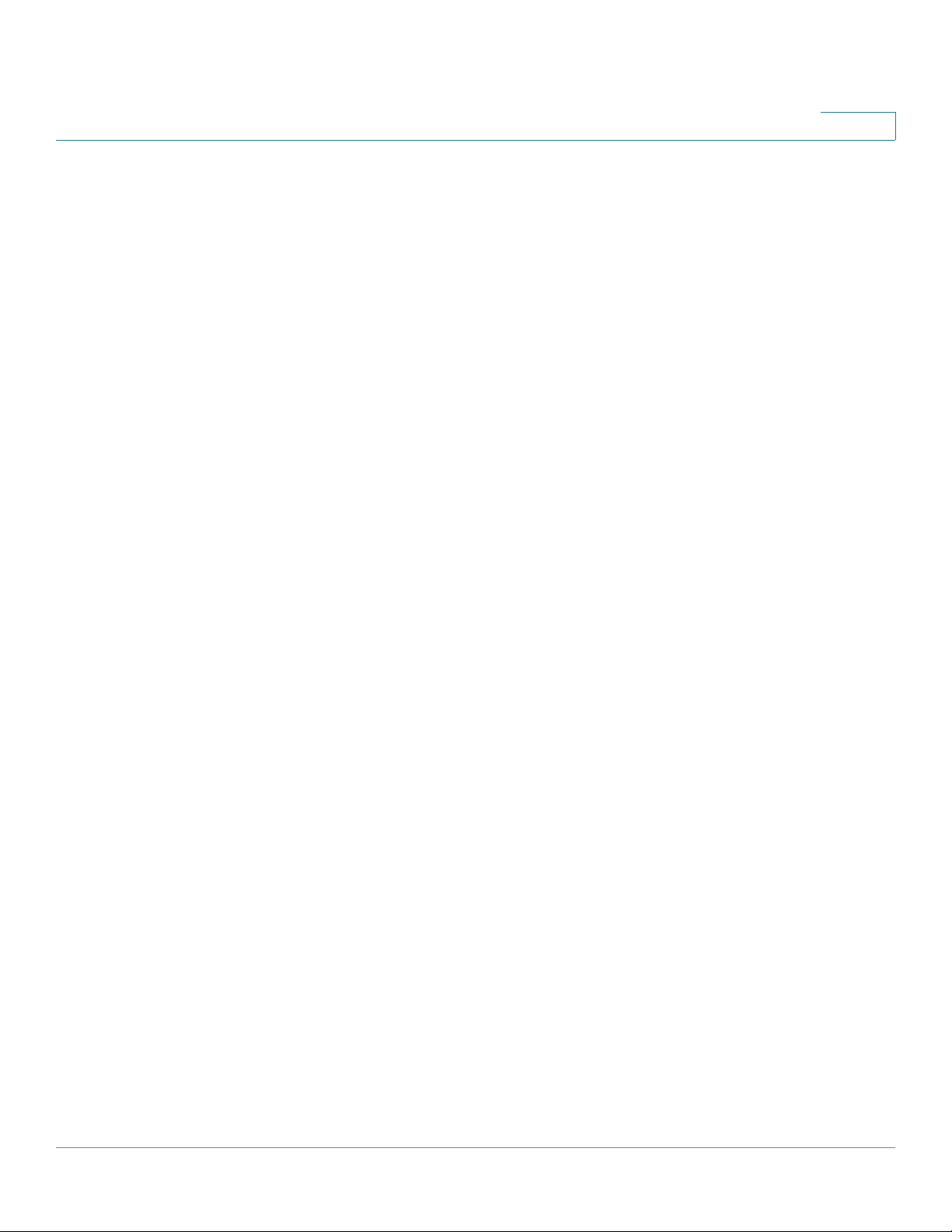
Viewing the Device Status
Viewing the System Summary
To view the LAN settings , c lick details. For more information, see Configuring the
LAN Settings.
WAN (Mobile Network) Information
To view the WAN settings, click details. For more information see Configuring the
Wired WAN Connections.
WAN (Internet) Information
5
• DHCPv6 Server—Status of the router IPv6 DHCP server (enabled or
disabled).
• IPv4 Address—IPv4 address of the USB p o rt.
• State—State of the mobile network WAN connection (up or down).
• IPv4 Address—IPv4 address of the router WAN port.
• IPv6 Address—IPv6 address of the router WAN port, if IPv6 is enabled.
• State—State of the wired WAN connection (up or down).
To view the WAN settings, click details. For more information see Configuri ng t he
Wired WAN Connections.
Wireless Networks
Lists the status of the four wireless network SSIDs.
To view the router wireless settings, click details. For more information see
Viewing Wireless Statistics.
VPN
QuickVPN Users—Number of QuickVPN users.
PPTP—Number of Point-to-Point Tunneling Protocol (PPTP) users.
Viewing the System Summary
The Sys tem Summ ary page displays a summary of the device values, such as the
firmware version and serial number.
To view a summary of system settings, choose Status > System Summary.
To go to the related window, click the underscored parameter. For example, to
modify the LAN IP address, click LAN IP. The LAN Configuration window appears.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 16
Page 18
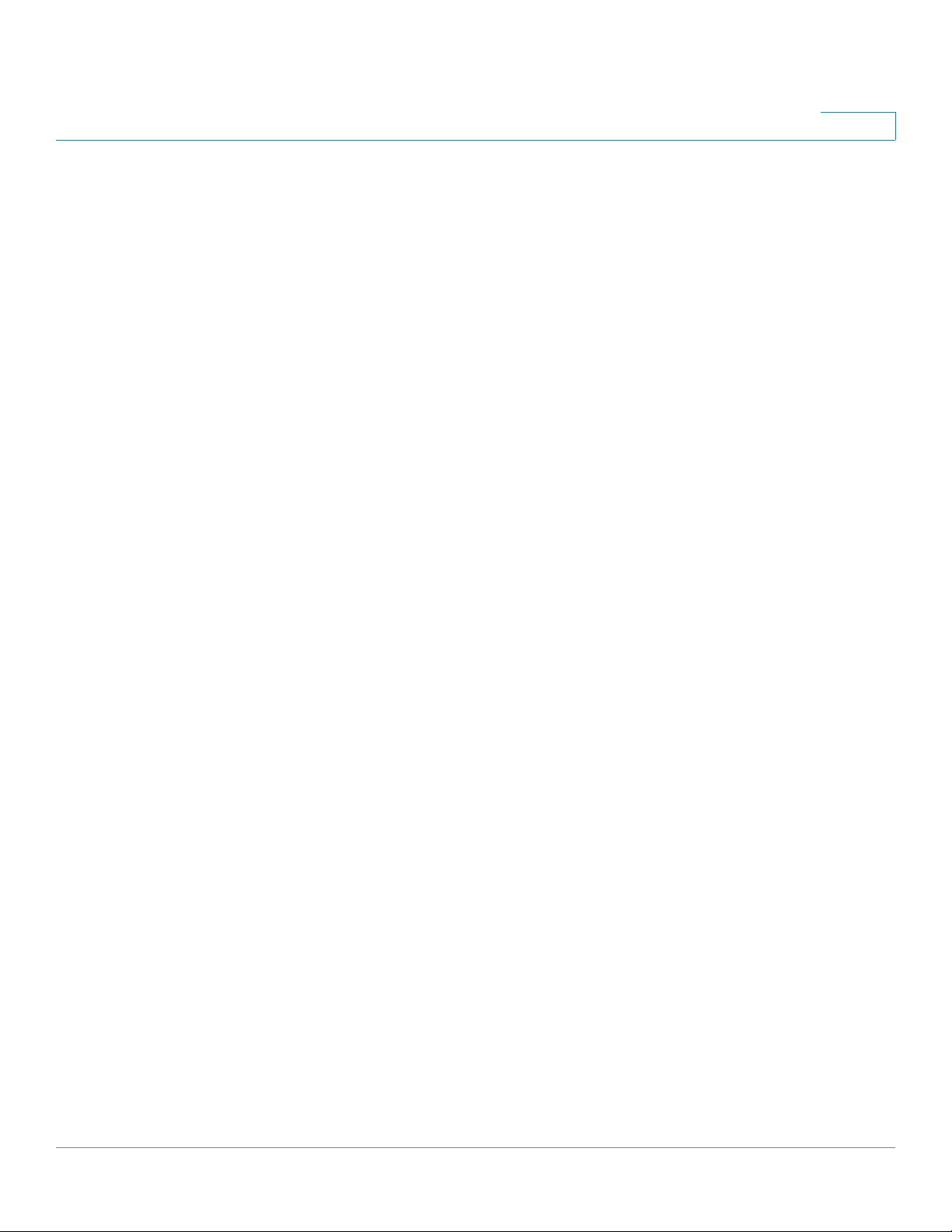
Viewing the Device Status
Viewing the System Summary
Click Refresh to obtain the latest information.
The System Summary page displays this information:
System Information
5
• Firmware Version—Current software version the device is running.
• Firmware MD5 Checksum—The message-digest algorithm used to verify
the integrity of files.
• Locale—The language installed on the router.
• Language Version—The version of the installed language pack. The
language pack version should be compatible with the currently installed
firmware. In some cases, an older language pack may be used with a newer
firmware image. The router will check the language pack version to see if it
is compatible with the current firmware version.
• Language MD5 Checksum—The MD5 checksum of the language pack.
• CPU Model—Chipset of CPU currently used.
• Serial Number—Serial number of the device.
• System Up Time—How long the system has been running.
• Current Time—Time of day.
• PID VID—Product ID and version ID of the device.
IPv4 Configuration
• LAN IP—LAN IP address of the device.
• WAN IP—WAN IP address of the device. You can release the current IP
address and obtain a new one by clicking Release or Renew.
• Gateway—IP address of the gateway to w hich the device is connected (for
example, the cable modem).
• Mode—Displays Gateway if NAT is enabled, or Router.
• DNS 1—Primary DNS server IP address of the WAN port.
• DNS 2—Secondary DNS server IP address of the WAN port.
• DDNS—Indicates whether the Dynamic DNS is enabled or disabled.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 17
Page 19
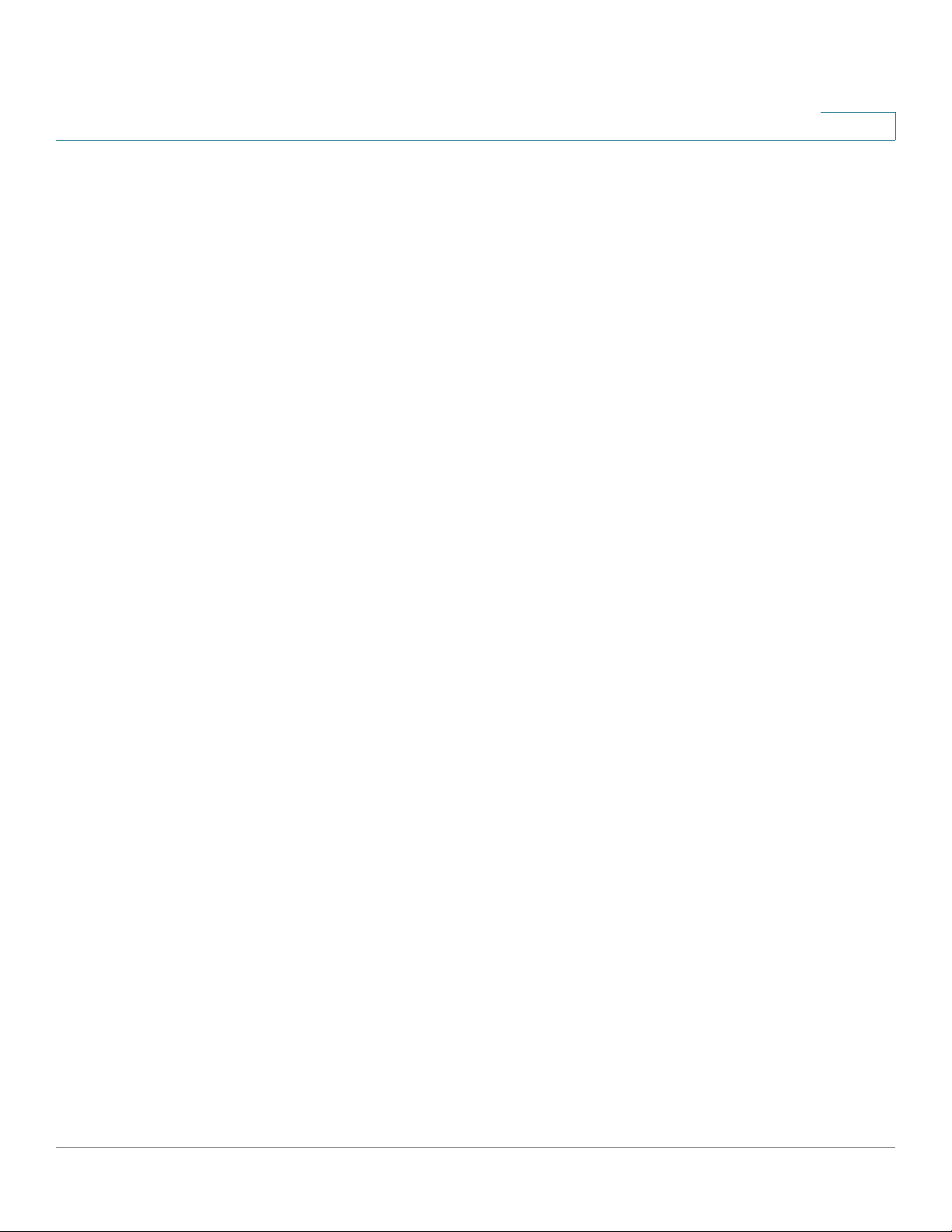
Viewing the Device Status
Viewing the System Summary
IPv6 Configuration
Wireless Summary
5
• LAN IP—LAN IP address of the device.
• WAN IP—WAN IP address of the device.
• Gateway—IP address of the gateway to w hich the device is connected (for
example, the cable modem).
• NTP—Network Time Protocol ser ver (hostname or IPv6 address).
• Prefix Delegation—IPv6 prefix returned from the device at the ISP that is
given to IP addresses on the device.
• DNS 1—IP address of the primary DNS server.
• DNS 2—IP address of the secondary DNS server.
• SSID 1—Public name of the first wireless network.
- Security—Security setting for SSID 1.
• SSID 2—Public name of the second wireless network.
- Security—Security setting for SSID 2.
• SSID 3—Public name of the third wireless network.
- Security—Security setting for SSID 3.
• SSID 4—Public name of the fourth wireless network.
- Security—Security setting for SSID 4.
Firewall Setting Status
• DoS (Denial of Service)—Indicates whether DoS prevention is on or off.
• Block WAN Request—Indicates whether WAN request blocking is on or
off.
• Remote Management—Indicates whether or not Device Manager can be
accessed remotely.
VPN Setting Status
• QuickVPN Connecti ons Available—Number of available QuickVPN
connections.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 18
Page 20

Viewing the Device Status
Viewing Wireless Statistics
• PPTP VPN Connections Available—Number of available PPTP VPN
connections.
• Connected QuickVPN Users—Number of connected QuickVPN users.
• Connected PPTP VPN Users—Number of connected PPTP VPN users.
Viewing Wireless Statistics
The Wireless Statistics page shows wireless statistics for the device radio.
To view wireless statistics, choose Status > Wireless Statistics.
To change the refresh rate, choose a refresh rate from the Refresh Rate drop-
down menu.
5
To show the bytes in kilobytes (KB) and the numerical data in rounded-up values,
check Show Simplified Statistic Data and click Save. By default, byte data is
displayed in bytes and other numerical data is displayed in long form.
To reset the wireless statistics counters, click Clear Count. Also the counters are
reset when the device is rebooted.
The Wireless Statistics page displays this information:
SSID Name The name of the wireless network.
Packet Number of received and sent wireless packets
reported to the radio over all configured and active
SSIDs.
Byte Number of received and sent bytes of information
reported to the radio, over all configured SSIDs.
Error Number of received and sent packet errors reported to
the radio, over all configured SSIDs.
Dropped Number of received and sent packets dropped by the
radio, over all configured SSIDs.
Multicast Number of multicast packets sent over this radio.
Collisions Number of packet collisions reported to the router.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 19
Page 21

Viewing the Device Status
Viewing the VPN Sta tus
Viewing the VPN Status
The VPN page displays the status of VPN connections.
To view VPN user connection status, choose Status > VPN Status.
The VPN page displays this information:
Username The username of the VPN user associated with the
Remote IP Displays the IP address of the remote QuickVPN client.
5
QuickVPN PPTP tunnel.
This could be a NAT/Public IP if the client is behind the
NAT router.
Status Displays the current status of the QuickVPN client.
OFFLINE means that the QuickVPN tunnel is not
initiated or established by the VPN user. ONLINE
means that the QuickVPN tunnel initiated or
established by the VPN user, is active.
Start Time Time when the VPN user e stablished a connection.
End Time Time when the VPN user ended a connection.
Duration (Seconds) Duration of time between the VPN user establishing
and ending a connection.
Protocol Protocol that the user uses.
You can change the status of a connection to either establish or disconnect the
configured VPN client.
To terminate an active VPN connection, click Disconnect.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 20
Page 22
Viewing the Device Status
Viewing the IPSec Connection Status
Viewing the IPSec Connection Status
The IPsec connection status shows the status of active VPN policies on the
device. (These policies are configured on the VPN > Advanced VPN Setup page.)
To view the IPsec connection status:
STEP 1 Choose Status > IPSec Connection Status. The table displays the following
information:
• Refresh Rate—Choose the rate at which you want the data display to clear
and display the newest data.
• Show Simplified Statistic Data—By default, byte data is displayed in bytes
and other numerical data is displayed in long form. To show the bytes in
kilobytes (KB) and the numerical data in rounded-up form, check Show
Simplified Statistic Data.
5
• Policy Name—Name of the VPN policy for which data is displayed.
• Local or Remote—Displays the local and remote IP addresses.
• Start Time and End Time—Displays the start and end times of the IPsec
connections.
• Duration—Displays the elapsed time for which the connection is or was
active.
• Packet—Displays the received (Rx) and transmitted (Tx) packets on the
connection.
• Byte—Displays the received (Rx) and transmitted (Tx) bytes on the
connection.
• State—Displays the state of the connection (for example, active or not
connected).
• Action—Displays actions you can perform on the connection (for example,
disconnect).
• Ext Action—Displays if you can switch between the primary and the
secondary VPN connections. If the Rollback enable check box on the
Advanced VPN Parameters page is checked, the Switch button is dimmed.
STEP 2 If you made any changes, click Save.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 21
Page 23
Viewing the Device Status
Viewing Logs
Viewing Logs
The View Logs page displays the device logs.
To view the logs, choose Status > View Logs.
To display the latest log entries, click Refresh Logs.
To filter logs or specify the severity of logs to display, check the boxes next to the
log type and click Go. Note that all log types above a selected log type are
automatically included and you cannot deselect them. For example, choosing error
logs automatically includes emergency, alert, and critical logs in addition to error
logs.
The event severity levels are list ed from the highest severity to the lowest severity ,
as follows:
5
• Emergency—System is not usable.
• Alert—Action is needed.
• Critical—System is in a critical condition.
• Error—System is in error condition.
• Warning—System warning occurred.
• Notification—System is functioning properly, but a system notice occurred.
• Informational—Device information.
• Debugging—Provides detailed information about an event.
To delete all entries in the log window, click Clear Logs.
To save all log messages from the firewall to the local hard drive, click Save Logs.
To save log messages to an external USB device, click Save Log to USB.
To specify the number of entries to show per page, choose a number from the
drop-down menu.
Use the page navigation buttons to move between log pages.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 22
Page 24
Viewing the Device Status
Viewing Connected Devices
Viewing Connected Devices
The Connected Device s page displays information about the active devices
connected to the device.
The IPv4 ARP Table displays information from devices that have responded to the
device Address Resolution Protocol (ARP) request. If a device does not respond to
the request, it is removed from the list.
The IPv6 NDP Table displays all IPv6 Neighbor Discover Protocol (NDP) devices
connected to the device local link.
To view connected devices, choose Status > Connected Devices.
To specify the types of interfaces to display, select a value from the Filter drop-
down menu:
5
All—All devices connected to the router.
Wireless—All devices connected through the wireless interface.
Wired—All devices connected through the Ethernet ports on the router.
WDS—All Wireless Distribution System (WDS) device connected to the router.
Viewing Port Statistics
The Port Statistics page displays port detailed activity.
To view port statistics, choose Status > Port Statistics.
To cause the page to re-read the statistics from the router and refresh the page,
choose a refresh rate from the Refresh Rate drop-down menu.
To show the bytes in kilobytes (KB) and the numerical data in rounded-up form,
check Show Simplified Statistic Data and click Save. By default, byte data is
displayed in bytes and other numerical data is displayed in long form.
To reset the port statistics counters, click Clear Count.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 23
Page 25

Viewing the Device Status
Viewing the Guest Network Sta tus
The Port Statistics page displays this information:
Interface Name of the network interface.
Packet Number of received/sent packets.
Byte Number of received/sent bytes of information per second.
Error Number of received/sent packet errors.
Dropped Number of received/sent packets that were dropped.
Multicast Number of multicast packets sent over this radio.
Collisions Number of signal collisions that occurred on this port. A
5
collision occurs when the port tries to send data at the
same time as a port on another router or computer that is
connected to this port.
Viewing the Guest Network Status
The guest network statistics displays information about the wireless guest
network configured on the device.
To view the guest network status, choose Status > GuestNet Status. The following
information is displayed:
• Host Name—Device connected to the guest network.
• IP Address—IP address assigned to the connected device.
• MAC Address—MAC or hardware address of the connected device.
• Time Left—Time remaining that the device can be connected to the guest
network. (Time limits are configured in the Wireless > Basic Settings >
Guest Net Settings page.)
• Action—Actions you can perform on the connected device (for example,
disconnect).
Cisco RV215W Wireless-N VPN Firewall Administration Guide 24
Page 26
Viewing the Device Status
Viewing the Mobile Network Sta tus
Viewing the Mobile Network Status
The mobile network statistics about the mobile 3G/4G network and
communication device (dongle) configured on the device.
To view the mobile network status, choose Status > Mobile Network. The
following information is displayed:
• Connection—Device connected to the guest network.
• Internet IP Address—IP address assigned to the USB device.
• Subnet Mask—Subnet mask of the USB device.
• Default Gateway—IP address of the default gateway.
• Connection Up Time—How long the link has b een up.
5
• Current Session Usage—Volume of data being received (Rx) and
transmitted (Tx) on the mobile link.
• Manufacturer—Card manufacturer name.
• Card Model—Card model number.
• Card Firmware—Card firmware version.
• SIM Status—Subscriber identification module (SIM) status.
• IMS—The unique identification associated with the GSM, UMTS, or LTE
network mobile phone users.
• Carrier—Mobile network carrier.
• Service Type—Type of service accessed.
• Signal Strength—Strength of the wireless mobile network signal.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 25
Page 27

Configuring Networking
This chapter describes how to configure the device network settings.
• Configuring the WAN Settings
• Configuring the LAN Settings
• Cloning the MAC Address
• Configuring Routing
6
• Port Management
• Configuring Dynamic DNS
• Configuring the I P Mode
• Configuring IPv6
Cisco RV215W Wireless-N VPN Firewall Administration Guide 26
Page 28

Configuring Networking
Configuring the WAN Settings
Configuring the WAN Settings
An Internet connection can be established through the WAN port or a wireless
modem installed in the USB port. This section describes configuration of the W AN,
mobile network, and failover and recovery.
Configuring the Wired WAN Connections
Configuring WAN properties for an IPv4 network differs depending on which type
of Internet connection you have.
Configuring DHCP
If your Internet Service Provider (ISP) uses the Dynamic Host Control Protocol
(DHCP) to assign you an IP address, you receive an IP address that is dynamically
generated each time you log in.
6
To configure the DHCP WAN settings:
STEP 1 Choose Networking > WAN.
STEP 2 From the Internet Connection Type drop-down menu, select Automatic
Configuration - DHCP.
STEP 3 Click Save.
Configuring Static IP
If your ISP assigned you a permanent IP address, perform the following steps to
configure your WAN settings:
STEP 1 Choose Networking > WAN.
STEP 2 From the Internet Connection Type drop-down menu, choose Static IP.
STEP 3 Enter this information:
Internet IP Address IP address of the firewall WAN port.
Subnet mask Subnet mask of the firewall WAN port.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 27
Page 29

Configuring Networking
Configuring the WAN Settings
STEP 4 Click Save.
STEP 1 Choose Networking > WAN.
STEP 2 From the Internet Connection Type drop-down menu, choose PPPoE.
6
Default Gateway IP address of the default gateway.
Static DNS 1 IP address of the primary DNS server.
Static DNS 2 IP address of the secondary DNS server.
Configuring PPPoE
To configure the Point-to-Point Protocol over Ethernet (PPPoE) settings:
STEP 3 Enter the following information (you might need to contact your ISP to obtain your
PPPoE login information):
Username The username assigned by the ISP.
Password The password assigned by the ISP.
Connect on Demand Select this option if your ISP charges based on the
amount of time that you are connected. When you
select this option, the Internet connection is on only
when traffic is present. If the connection is idle—
that is, no traffic is flowing—the conne ction is
closed. If you click Connect on Demand, enter the
number of minutes after which the connection
shuts off in the Max Idle Time field.
Keep Alive When you select this option, the Internet
connection is always on. In the redial period field,
enter the number of seconds after which the
device attempts to reconnect if it is disconnected.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 28
Page 30
Configuring Networking
Configuring the WAN Settings
6
Authentication Type Auto-negotiation—The server sends a
configuration request specifying the security
algorithm set on it. The devic e then sends back
authentication credentials with the security type
sent by the server.
PAP—Password Authentication Protocol (PAP),
used by Point-to-Point Protocol to connect to the
ISP.
CHAP—Challenge Handshake Authentication
Protocol (CHAP) requires that both the client and
server know the plaintext of the secret to use ISP
services.
MS-CHAP or MS-CHAPv2—The Microsoft
version of CHAP, used to access ISP services.
STEP 4 Click Save.
Configuring PPTP
To configure the PPTP settings:
STEP 1 Choose Networking > WAN.
STEP 2 From the Internet Connection Type drop-down menu, choose PPTP.
STEP 3 Enter this information:
Internet IP Address IP address of the WAN port.
Subnet mask Subnet mask of the WAN port.
Default Gateway IP address of the default gateway.
PPTP Server IP address of the Point-To-Point Tunneling Protocol
(PPTP) server.
Username The username assigned to you by the ISP.
Password The password assigned to you by the ISP.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 29
Page 31

Configuring Networking
Configuring the WAN Settings
6
Connect on Demand Select this option if your ISP charges based on the
amount of time that you are connected. When you
select this option, the Internet connection is on only
when traffic is present. If the connection is idle—
that is, no traffic is flowing—the conne ction is
closed. If you click Connect on Demand, enter the
number of minutes after which the connection
shuts off in the Max Idle Time field.
Keep Alive When you select this option, the Internet
connection is always on. In the redial period field,
enter the number of seconds after which the
device attempts to reconnect if it is disconnected.
Authentication Type Choose the authentication typ e:
Auto-negotiation—The server sends a
configuration request specifying the security
algorithm set on it. The devic e then sends back
authentication credentials with the security type
sent earlier by the server.
PAP—The device uses the Password
Authentication Protocol (PAP) to connect to the ISP.
CHAP—The device uses the Challenge Handshake
Authentication Protocol (CHAP) when connecting
with the ISP.
MS-CHAP or MS-CHAPv2—The device uses
Microsoft Challenge Handshake Authentication
Protocol when connecting with the ISP.
STEP 4 (Optional) To configure the optional settings, see Configuring Optional Settings.
STEP 5 Click Save.
Configuring L2TP
To configure the L2TP settings:
STEP 1 Choose Networking > WAN.
STEP 2 From the Internet Connection Type drop-down menu, choose L2TP.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 30
Page 32

Configuring Networking
Configuring the WAN Settings
STEP 3 Enter this information:
6
Internet IP Address Enter the IP address of the WAN port.
Subnet mask Enter the subnet mask of the WAN port.
Default Gateway Enter the IP address of the default gateway.
L2TP Server Enter the IP address of the L2TP server.
Username Enter your username assigned to you by the ISP.
Password Enter your password assigned to you by the ISP.
Connect on Demand Select this option if your ISP charges based on the
amount of time that you are connected. When you
select this option, the Internet connection is on only
when traffic is present. If the connection is idle—
that is, no traffic is flowing—the conne ction is
closed. If you click Connect on Demand, enter the
number of minutes after which the connection
shuts off in the Max Idle Time field.
Keep Alive When you select this option, the Internet
connection is always on. In the redial period field,
enter the number of seconds after which the
device attempts to reconnect if it is disconnected.
Authentication Type Auto-negotiation—The server sends a
configuration request specifying the security
algorithm set on it. The devic e then sends back
authentication credentials with the security type
sent by the server.
PAP—Password Authentication Protocol (PAP) is
used to connect to the ISP.
CHAP—Challenge Handshake Authentication
Protocol (CHAP) is used to connect to the ISP.
MS-CHAP or MS-CHAPv2—Microsoft Challenge
Handshake Authentication Protocol is used to
connect to the ISP.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 31
Page 33

Configuring Networking
Configuring the WAN Settings
STEP 4 Click Save.
STEP 1 In the Optional Settings section, configure the following settings:
6
Configuring Optional Settings
To configure optional settings:
Host Name Host name of the device.
Domain Name Domain name for your network.
MTU The maximum transmission unit (MTU) is the size of
the largest packet that can be sent over the
network.
Size MTU size.
STEP 2 Click Save.
Configuring a Mobile Network
Use the Mobile Network page to configure the device to connect to a Mobile
Broadband USB modem that is connected to its USB interface.
The standard MTU value for Ethernet networks is
usually 1500 bytes. For PPPoE connections, the
value is 1492 bytes.
Unless a change is required by your ISP, we
recommend that you choose Auto. The default
MTU size is 1500 bytes.
If your ISP requires a custom MTU setting, choose
Manual and enter the MTU size.
To display the Mobile Network window, choose Networking > WAN > Mobile
Network.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 32
Page 34

Configuring Networking
Configuring the WAN Settings
STEP 1 Connect the USB modem. If the modem is supported, it is automatically detected
STEP 2 Select Auto or Manual connection mode. Ethernet Connection Reco very works
6
Global Settings
To install a USB modem:
and appears on the Mobile Network page.
only if the Connect Mode is set to Auto.
• To enable your modem to establish a connection automatically, select Auto
mode. If you select Auto, you must also either set a Connect on Demand time
or select Keep Alive. Connect on Demand terminates the Internet connection
after it is inactive for the specified period of time (Max Idle Time).
If your Internet connection is terminated due to inactivity, the modem
automatically establishes a connection when a user attempts to access the
Internet. In the Max Idle Time field, enter the number of minutes of idle time
that can elapse before the Internet connection terminates. Choos ing Keep
Alive keeps the connection up at all times.
• To connect or disconnect your modem connection manually, select Manual
mode.
The device displays the current modem connection status that includes initializing,
connecting, disconnecting, or disconnected.
STEP 3 Verify that the Card Status field shows that your mobile card is Connected.
These messages might also appear:
• Please set APN manually (because the device is unable to determine the
access point name)
• Searching for service...
• no SIM card
• SIM locked
• SIM busy
• SIM r eady
• pin code needed
• pin code error
• Card is locked
Cisco RV215W Wireless-N VPN Firewall Administration Guide 33
Page 35

Configuring Networking
Configuring the WAN Settings
6
• Card is not activated
• Card initialized error
• error
Mobile Network Setup
If it is necessary to change any of the mobile network parameters in the Mobile
Network Setup area, click the Manual radio button in the Configure Mode field.
The device automatically detects supported modems and lists the appropriate
configuration parameters. The SIM PIN can be modified in either Auto or Manual
mode.
The Card Model shows the model of the modem in the USB port. Unsupported
cards are reported as unrecognized.
To override any of the other parameters, select Manual and complete the
following fields:
Field Description
Access Point Name
(APN)
Dial Number Dial number provided by your mobile network ser vice
User Name
Password
SIM Check SIM card check enable or disable.
SIM PIN PIN code associated with your SIM card. This field is
Server Name Name of the server for the Internet connection (if
Authentication Authentication used by your service provider . The value
Internet network that the mobile device is connecting to.
Enter the access point name provided by your mobile
network service provider. If you do not know the name
of the access p o int, contact your service provider.
provider for the Internet connection.
User name and password provided by your mobile
network service provider.
only displayed for GSM SIM cards.
provided by your service provider).
can be changed by choosing the authentication type
from the drop-down list. The default is Auto. If you do
not know which type of authentication to use, select
Auto.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 34
Page 36

Configuring Networking
Configuring the WAN Settings
STEP 4 Click Save to save your settings
6
Field Description
Service Type The most commonly available type of mobile data
service connection based on your area service signal. If
your location supports only one mobile data service,
you can limit your pref err ed option, reducing connection
setup times. The first selection always searches for
HSPDA/3G/UMTS service and switches automatically
to GPRS when it is available.
LTE Service Long-term Evolution (LTE) Service setting. Sele ct Auto
for a signal based on the area service signal. Select4G
only for only 4G signals. Select 3G only for only 3 G
signals.
Bandwidth Cap Setting
The device monitors the data activity across the mobile network link and when it
reaches a specific threshold, sends a notification.
To enable or disable Bandwidth Cap Tracking and set the limits:
STEP 1 Click Enabled or Disabled.
STEP 2 Select Monthly Renewal Date from the drop-down list to indicate which day of
the month the bandwidth cap is reset .
STEP 3 In the Monthly Bandwidth Cap field, enter the maximum amount of data in
megabytes that is allowed to pass before the device takes an action, such as
sending an email to an administrator.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 35
Page 37

Configuring Networking
Configuring the WAN Settings
6
E-mail Setting
When the bandwidth data limit is reached, an email message can be sent to the
administrator. To set up the target email address, check the Email to check box
and click Email Address. For more information, see Configuring E-mail Settings.
When enabled by checking the box, email is sent when:
• Mobile network usage has exceeded a given percentage.
• The device fails over to the backup pathway and recovers.
• At every interval specified while a mobile network link is active.
Set t ing Failover and Recovery
While both an Ethernet and a mobile network link might be available, only one
connection can be used to establish a WAN link at a time. When a WAN connection
fails, the device attempts to bring up a connection on another interface. This
feature is called Failover. When the primary WAN connection is restored, it drops
the backup connection. This feature is called Recovery.
STEP 1 Choose Networking > WAN > Failover & Recovery.
STEP 2 Choose if your primary network connection is an ethernet WAN connection or a
mobile network connection using a 3G USB dongle.
STEP 3 Click the Failover to Secondary Enable radio button to enable the device to
failover from the primary network connection and restore connectivity using the
secondary connection.
For example, your primary connection is an Ethernet WAN connection and the
WAN link goes down. The device attempts to restore the connection using a 3G
mobile network link on the USB interface. If Failover to Secondary Enable is not
enabled, the secondary connection is disabled.
STEP 4 Click the Recovery back to Primary Enable radio button to enable the device to
automatically revert to the primary connection and drop the secondary
connection. The WAN > Mobile Network Connect Mode must be set to Auto to
revert to a primary connection automatically.
STEP 5 In the Failover Check Interval field, enter the time (in seconds) after which the
device must attempt to detect the presence of traffic on the secondary
connection.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 36
Page 38

Configuring Networking
Configuring the WAN Settings
STEP 6 In the Recovery Check Interval field, enter the time (in seconds) after which the
STEP 7 Click the Switch back to Primary immediately when Primary is available radio
STEP 8 In the Recovery Ping field, enter the number of times the device must ping the
STEP 9 In the Connection Validation Site field, choose the location to ping during failover
6
device must attempt to detect the presence of traffic on the primary connection. If
the link is idle, the device pings a specified destination at the specified interval. If
there is a reply to the ping packet, the device assumes that the link is up and
attempts to revert to the primary network connection.
button or set a time in the Switch back to Primary in a specific time range field. If
you choose a specific time range, set the start and end time.
connection validation site after recovery . You can specify up to 5 recovery pings to
the site. By default, the device will ping the validation site once.
and recovery validation. You can choose the device’s gateway, DNS, or a custom
IP address as the validation site. If you choose a custom site, enter the IPv 4 or IPv6
address. By default , the device pings the default gateway to validate failover.
STEP 10 To troubleshoot your 3G mobile net work c onnection, click the 3G Diagnostic
Enable radio button. Set the time when the device must test the 3G connection
every day.
STEP 11 Click Save.
The WAN Interface table shows the status of the Ethernet WAN and mobile
network link to the Internet. Click the Status hyper link to view the port detail.
WAN/USB Device Update
Use this page to load the USB module files that support USB dongles. Contact
Cisco Support to acquire USB module files. The Dynamic Load USB Modem List
shows the 3G and 4G USB dongle module files that are supported on the device.
To delete a module file, select the module from the Dynamic Load USB Modem
List and click Delete.
To upload USB device firmware (a module) from the PC:
STEP 1 Verify that the USB dongle is not connected to the device.
STEP 2 Browse to and select the USB dongle module file.
STEP 3 Click Import.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 37
Page 39

Configuring Networking
Configuring the LAN Settings
STEP 4 Connect the US B dongle to the device.
Configuring the LAN Settings
The default DHCP and TCP/IP settings work for most applications. If you want
another PC on your network to be the DHCP server, or if you want to manually
configure the network settings of all of your devices, disable DHCP.
Also, instead of using a DNS server that maps Internet domain names (for example,
www.cisco.com) to IP addresses, you can use a Windows Internet Naming Service
(WINS) ser ver. A WINS server is the equivalent of a DNS server, but uses the
NetBIOS protocol to resolve hostnames. The device includes the IP address of the
WINS server in the DHCP configuration that the device sends to DHCP clients.
6
If the d e v i ce i s co nnected to a modem o r d e v i ce that has a co n f i g u red netwo r k o n
the same subnet (192.168.1.x), the device automatically changes the LAN subnet
to a random subnet based on 10.x.x.x, so there is no conflict with the subnet on the
WAN side of the device.
Changing the Device Management IP Address
The local device management IP address of the devic e is static and defaults to
192.168.1.1.
To change the local device management IP address :
STEP 1 Choose Networking > LAN > LAN Configuration.
STEP 2 In the IPv4 section, enter this information:
VLAN The VLAN number.
Local IP Address Local LAN IP address of the device. Ensure that this
IP address is not in use by another device.
Subnet mask Subnet mask for the local IP address. The default
subnet mask is 255.255.255.0.
STEP 3 Click Save.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 38
Page 40

Configuring Networking
Configuring the LAN Settings
6
After changing the device IP address, your PC is no longer able to display Device
Manager.
To display Device Manager, do one of the following:
• If DHCP is configured on the device, release and renew your PC IP address.
• Manually assign an IP address to your PC. The address must be on the same
subnetwork as the device. For example, if you change the device IPaddress
to 10.0.0 .1 , assign your PC an IP address in the range of 10.0.0.2 t o 10.0.0 .255.
Open a new browser window and enter the new IP address of the device to
reconnect.
Configuring the DHCP Server
By default, the device functions as a DHCP server to the hosts on the Wireless
LAN (WLAN) or wired LAN. It assigns IP addresses, and provides DNS server
addresses.
With DHCP enabled, the device assigns IP addresses to network devices on the
LAN from a pool of IPv4 addresses. The device tests each address before it is
assigned to avoid duplicate addresses on the LAN.
The default IP address pool is 192.168.1.100 to 192.168.1.149. To set a static IP
address on a network device, use an IP address outside the po ol. For example,
assuming the DHCP pool is set to the default parameters, static IP addresses from
192.168.1.2 to 192.168.1.99 IP address pool can be used. This prevents conflicts
with the DHCP IP address pool.
To configure DHCP settings:
STEP 1 Choose Networking > LAN > LAN Configuration.
STEP 2 (Optional) Select a VLAN to edit from the drop-down list.
STEP 3 In the DHCP Server field, select one of the following options:
Enable Allows the device to act as the DHCP server in the network.
Disable Disables DHCP on the device when you want to manually
configure the IP addresses of all of your network devices.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 39
Page 41

Configuring Networking
Configuring the LAN Settings
6
DHCP Relay Relays the IP addresses assigned by a another DHCP server
to the network devices.
If you enabled the device DHCP server, enter this information:
Starting IP Addre ss The first address in the IP address pool. Any DHCP
client joining the LAN is assigne d an IP address in
this range.
Maximum Number of
DHCP Users
IP Address Range (Read-only) The range of IP addresses available to
Client Lease time Duration (in hours) that IP addresses are leased to
Static DNS 1 IP address of the primary DNS server.
Static DNS 2 IP address of the secondary DNS server.
Static DNS 3 IP address of the tertiary DNS server.
WINS IP address of the primary WINS server.
STEP 4 If you selected DHCP Relay , enter the addr ess of the rela y gatewa y in the Remote
DHCP Server field. The relay gateway transmits DHCP messages to network
device, including those on other subnetworks.
STEP 5 Click Save.
The maximum number of DHCP clients.
the DHCP clients.
clients.
Configuring VLANs
A Virtual LAN (VLAN) is a group of endpoints in a network that are associated by
function or other shared characteristics. Unlike LANs that are typically
geographically based, VLANs can group endpoints without regard to the physical
location of the equipment or users.
The device has a default VLAN (VLAN 1) that cannot be deleted. You can create up
to four other VLANs on the device.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 40
Page 42

Configuring Networking
Configuring the LAN Settings
STEP 1 Choose Networking > LAN > VLAN Membership.
STEP 2 Click Add Row.
STEP 3 Enter this information:
6
To create a VL A N :
VLAN ID Numerical VLAN ID to assign to endpoints in the VLAN
membership. The number you enter must be between
3 to 4094. VLAN ID 1 is reserved for the default VLAN,
and is used for untagged frames received on the
interface.
Description A description that identifies the VLAN.
Inter VLAN Routing Allows an end station in one VLAN to communicate
Port 1
Port 2
Port 3
Port 4
STEP 4 Click Save.
with an end station in another VLAN.
You can associate VLANS on the device to the LAN
ports on the device. By default, all LAN ports belong to
VLAN1. You can edit these ports to associate them
with other VLANS. Choose the outgoing frame type for
each port:
Untagged—The interface is an untagged member of
the VLAN. Frames of the VLAN are sent untagged to
the port VLAN.
Tagged—The port is a tagged member of the VLAN.
Frames of the VLAN are sent tagged to the port VLAN.
Excluded—The port is currently not a member of the
VLAN. This is the default for all the ports when the
VLAN is first created.
To edit the settings of a VLAN, select the VLAN and click Edit. To delete a selected
VLAN, click Delete. Click Save to apply changes.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 41
Page 43

Configuring Networking
Configuring the LAN Settings
STEP 1 Choose Networking > LAN > Static DHCP.
STEP 2 From the VLAN drop-down menu, choos e a VLAN number.
STEP 3 Click Add Row.
STEP 4 Enter this information:
6
Configuring Static DHCP
You can configure the device to assign a specific IP address to a device with a
specific MAC address.
To configure static DHCP:
Description Description of the client.
IP Address IP address of the device. The IP address assigned should
be outside the pool of the DHCP addresses.
Static DHCP assignment means the DHCP server assigns
the same IP address to a defined MAC address every time
the device is connected to the network.
The DHCP server assigns the reserved IP address when
the device using the corresponding MAC address
requests an IP address.
MAC Address MAC address of the device.
The format for a MAC address is XX:XX:XX:XX:XX:XX
where X is a number from 0 to 9 (inclusive) or a letter
between A and F (inclusive).
To edit the settings of a static DHCP client, select the client and click Edit. To
delete a selected DHCP client, click Delete. Click Save to apply the changes.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 42
Page 44

Configuring Networking
Configuring the LAN Settings
STEP 1 In the row of the connected device, check Add to Static DHCP.
STEP 2 Click Save.
6
Viewing DHCP Leased Clients
You can view a list of endpoints on the network (identified by hostname, IP
address, or MAC address) and see the IP addresses assigned to them by the
DHCP server. The VLAN of the endpoints is also displayed.
To view the DHCP clients, choose Networking > LAN > DHCP Leased Clients.
For every VLAN defined on the device, a table displays a list of the clients
associated with the VLAN.
To assign a static IP address to one of the connected devices:
The DHCP server on the device always assigns the IP address shown when the
device requests an IP address.
Configuring a DMZ Host
The device supports demilitarized zones (DMZ). A DMZ is a subnetwork that is
open to the public but behind the firewall. A DMZ allows you to redirect packets
going to your WAN port IP address to a particular IP address in your LAN.
We recommended that you place hosts that must be exposed to the WAN (such as
web or e-mail servers) in the DMZ network. You can configure firewall rules to
allow access to specific services and ports in the DMZ from both the LAN or W AN.
In the event of an attack on any of the DMZ nodes, the LAN is not necessarily
vulnerable.
You must configure a fixed (static) IP address for the endpoint that you designate
as the DMZ host. You should assign the DMZ host an IP address in the same
subnet as the device LAN IP address, but it cannot be identical to the IP address
given to the LAN interface of this gateway.
To configure DMZ:
STEP 1 Choose Networking > LAN > DMZ Host.
STEP 2 Check Enable to enable DMZ on the network.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 43
Page 45

Configuring Networking
Configuring the LAN Settings
STEP 3 From the VLAN drop-down menu, choose the ID of the VLAN where DMZ is
STEP 4 In the Host IP Address field, enter the IP address of the DMZ host. The DMZ host
STEP 5 Click Save.
6
enabled.
is the endpoint that receives the redirected packets.
Configuring RSTP
Rapid Spanning Tree Protocol (RSTP) is a network protocol that prevents loops in
the network and dynamically reconfigures which physical links should forward
frames. To configure Rapid Spanning Tree Protocol (RTSP):
STEP 1 Choose Networking > LAN > RSTP.
STEP 2 Configure the following settings:
System Priority Choose the system priority from the drop-down
menu. You can choose from a system priority from
0 to 61440 in increments of 4096. Valid values are
0, 4096, 8192, 12288, 16384, 20480, 24576,
28672, 32768, 40960, 45056, 49152, 53248,
57344, and 61440.
The lower the system priority, the more likely the
device is to become the root in the spanning tree.
The default is 327688.
Hello Time The hello time is the time period tha t the r oot of the
spanning tree waits before sending hello
messages. Enter a number from 1 to 10 . The default
is 2.
Max Age The max age is the time period that the router waits
to receive a hello message. If the max age is
reached, the router tries to change the spanning
tree. Enter a number from 6 to 40. The default is 20.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 44
Page 46

Configuring Networking
Configuring the LAN Settings
STEP 3 In the Setting Table, configure the following settings:
6
Forward Delay The forward delay is the interval after which an
interface changes from the blocking to forwarding
state. Enter a number from 4 to 30. The default is
15.
Force Version Select the default protocol version to use. Select
Normal (use RSTP) or Compatible (compatible
with old STP). The default is Normal.
Protocol Enable Check to enable RSTP on the associated port.
RSTP is disabled by default.
Edge Check to specify that the associated port is an
edge port (end station). Uncheck to specify that the
associated por t is a link (bridge) to another STP
device. Edge port is enabled by default.
Path Cost Enter the RSTP path cost for the designated ports.
Use 0 for the default value (the device
automatically determines the path value). You can
also enter a number from 2 to 200000000.
STEP 4 Click Save.
Port Management
You can configure the speed and flow control settings of the device LAN ports.
To configure port speeds and flow control:
STEP 1 Choose Networking > Port Management .
STEP 2 Configure this information:
Port The port number.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 45
Page 47

Configuring Networking
Cloning the MAC Address
6
Link The port speed. If no device is connected to the
port, this field displays Down.
Mode Choose from the drop-down menu one of the
following port speeds:
• Auto Negotiation—The device and the
connect ed device choose a common speed .
• 10Mbps Half—10 Mbps in both directions,
but only one direction at a time.
• 10Mbps Full—10 Mbps in both directions
simultaneously.
• 100Mbps Half—100 Mbps in both
directions, but only one direction at a time.
Flow Control Check to enable flow control for this port.
STEP 3 Click Save.
Cloning the MAC Address
Sometimes, you may need to set the MAC address of the device WAN port to be
the same MAC address as your PC or some other MAC address. This is called
MAC address cloning.
• 100Mbps Full—100 Mbps in both
directions simultaneously.
Flow control is the process of managing the rate of
data transmission between two nodes to prevent a
fast sender from outrunning a slow receiver. It
provides a mechanism for the receiver to control
the transmission speed, so that the receiving node
is not overwhelmed with data from the transmitting
node.
For example, some ISPs register your computer NIC card MAC address when the
service is first installed. When you place a router behind the cable modem or DSL
modem, the MAC address from the device WAN port is not recognized by the ISP.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 46
Page 48

Configuring Networking
Configuring Routing
STEP 1 Choose Networking > MAC Address Clone.
STEP 2 In the MAC Address Clone field, check Enable to enable MAC address cloning.
STEP 3 To set the MAC address of the device WAN port, do one of the following:
STEP 4 Click Save.
6
In this case, to configure your device to be recognized by the ISP, clone the MAC
address of the WAN port to be the same as your computerMAC address.
To configure a MAC address clone:
• To set the MAC address of the WAN port to your PC MAC address, click
Clone My PC’s MAC.
• To specify a different MAC address, enter it in the MAC Address field.
Configuring Routing
Configure the routing options.
Configuring the Operating Mode
To configure the device operating mode:
STEP 1 Choose Networking > Routing.
STEP 2 In the Operating Mode field, select one of the following options:
Gateway (Recommended) Click this button to set the device
to act as a gateway.
Keep this default setting if the device is hosting
your network connection to the Internet and is
performing the routing functions.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 47
Page 49

Configuring Networking
Configuring Routing
STEP 3 Click Save.
6
Router (For advanced users only) Click this button to set
the device to act as a router.
Select this option if the device is on a network with
other routers.
Enabling the Router mode disables NAT (Network
Address Translation) on the device.
Configuring Dynamic Routing
Routing Information Protocol (RIP) is an Interior Gateway Protocol (IGP) that is
commonly used in internal networks. It allows the router to exchange its routing
information automatically with other routers, and allows it to dy na mically adjust it s
routing tables and adapt to changes in the network.
Dynamic Routing (RIP) enables the device to automatically adjust to physical
changes in the network layout and exchange routing tables with the other routers.
The router determines the network packets’ route based on the fewest number of
hops between the source and the destination. RIP is disabled by default.
NOTE RIP is disabled by default on the device.
To configure dynamic routing:
STEP 1 Choose Networking > Routing.
STEP 2 Configure the following settings:
RIP Check Enable to enable RIP. This allows the device
to use RIP to route traffic.
RIP Send Packet Version Select the RIP Send Packet Version (RIPv1 or
RIPv2).
The version of RIP used to send routing updates to
other routers on the network depends on the
configuration settings of the other routers. RIPv2 is
backward compatible with RIPv1.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 48
Page 50

Configuring Networking
Configuring Routing
STEP 3 Click Save.
6
RIP Recv Packet Version Choose the RIP Receive Packet Version.
Configuring Static Routing
You can configure static routes to direct packets to the destination network. A
static route is a predetermined pathway that a packet must travel to reach a
specific host or network.
Some ISPs require static routes to build your routing table instead of using
dynamic routing protocols. Static routes do not require CPU resources to
exchange routing information with a peer router.
You can also use static routes to reach peer routers that do not support dynamic
routing protocols. Static routes can be used together with dynamic routes. The
device supports up to 30 static routes.
Be careful not to introduce routing loops in your network.
To configure static routing:
STEP 1 Choose Networking > Routing.
STEP 2 From the Route Entries drop-down menu, choose a route entry.
To delete the route entry, click Delete This Entry.
STEP 3 Configure the following settings for the selected route entry:
Enter Route Name Enter the name of the route.
Destination LAN IP Enter the IP address of the destination LAN.
Subnet Mask Enter the subnet mask of the destination network.
Gateway Enter the IP address of the gateway used for this
route.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 49
Page 51

Configuring Networking
Viewing the Routing Table
Interface Select the interface to which packets for this route
STEP 4 Click Save.
Viewing the Routing Table
6
are sent:
• LAN & Wireless—Click this button to direct
packets to the LAN and wireless network.
• Internet (WAN)—Click this button to direct
packets to the Internet (WAN).
The routing table contains information about the topology of the network
immediately around it.
To view the routing information on your network, choose Networking > Routing
Table and choose one of the following:
• Show IPv4 Routing Table—The routing table is displayed with the fields
configured in the Networking > Routing page.
• Show IPv 6 Routing Table—The routing table is displayed with the fields
configured in the Networking > IPv6 pages.
Configuring Dynamic DNS
Dynamic DNS (DDNS) is an Internet service that allows routers with varying public
IP addresses to be located using Internet domain names. To us e DDNS, you must
set up an account with a DDNS provider such as DynDNS.com, TZO.com,
3322.org, or noip.com.
The router notifies dynamic DNS servers of changes in the WAN IP address, so
that any public services on your network can be accessed by using the domain
name.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 50
Page 52

Configuring Networking
Configuring Dynamic DNS
STEP 1 Choose Networking > Dynamic DNS.
STEP 2 From the DDNS Service drop-down menu, choose Disable to disable this service
STEP 3 If you do not have a DDNS account, click the URL of the service to visit the
STEP 4 Configure this information:
6
To configure DDNS:
or choose the DDNS service to use.
selected DDNS ser vice's website so that you can create an account.
E-mail Address (TZO.com and noip.com) Email address you used to
create the DDNS account.
Username (DynDNS.com and 3322.org) Username of the
DDNS account.
Password Password of the DDNS account.
Verify Password (TZO.com, DynDNS.com, and noip.com) Password
confirmation of the DDNS account.
Host Name (DynDNS.com, 3322.org, and noip.com) Host name
of the DDNS server.
Domain Name (TZO.com) Name of the domain that is used to
access the network.
Update Interval Choose one of the following options to set the
frequency with which to update the IP addess and
the domain name to the DDNS server:
Never—Never update.
Weekly—Update every week at 00:MM on
Monday, where MM is a randomly picked number
between 0 and 59. By default, Weekly is chosen.
Semi-monthly—Update on the first and the
fifteenth day of the month at 00:MM, where MM is a
randomly picked number between 0 and 59.
Monthly—Update on the first day of the month at
00:MM, where MM is a randomly picked number
between 0 and 59.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 51
Page 53

Configuring Networking
Configuring the IP Mode
Internet IP Address (Read-only) Internet IP address of the device.
Status (Read-only) Indicates that the DDNS update has
STEP 5 To test the DDNS configuration, click Test Configuration.
STEP 6 Click Save.
Configuring the IP Mode
Wide area network configuration properties are configurable for both IPv4 and
IPv6 networks. You can enter information about your Internet connection type and
other parameters in these pages.
6
completed successfully or the acc ount update
information sent to the DDNS server failed.
To select an IP mode:
STEP 1 Choose Networking > IP Mode.
STEP 2 From the IP Mode drop-down menu, choose one of the following options:
LAN:IPv4, WAN:IPv4 Use IPv4 on the LAN and WAN ports.
LAN:IPv6, WAN:IPv4 Use IPv6 on the LAN ports and IPv4 on the WAN
ports.
LAN:IPv6, WAN:IPv6 Use IPv6 on the LAN and WAN ports .
LAN:IPv4+IPv6,
WAN:IPv4
LAN:IPv4+IPV6,
WAN:IPv4+IPv6
LAN:IPv4, WAN:IPv6 Use IPv4 on the LAN and IPv6 on the WAN ports.
Use IPv4 and IPv6 on the LAN ports and IPv4 on the
WAN ports.
Use IPv4 and IPv6 on both the LAN and WAN ports.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 52
Page 54

Configuring Networking
Configuring IPv6
STEP 3 (Optional) If you are using 6to4 tunneling, which allows IPv6 packets to be
transmitted over an IPv4 network, do the following:
a. Click Show Static 6to4 DNS Entry.
b. In the Domain and IP fields, enter up to five domain-to-IP mappings.
The 6to4 tunneling featur e is typically used when a site or end user wants to
connect to the IPv6 Internet using the existing IPv4 network.
STEP 4 Click Save.
Configuring IPv6
6
Internet Protocol version 6 (IPv6) is a version of the Internet Protocol (IP) intended
to succeed Internet Protocol version 4 (IPv4). Configuring WAN properties for an
IPv6 network depends on the type of Internet connection that you have.
Configuring the IPV6 WAN Connection
You can configure the device to be a DHCPv6 client of the ISP for this WAN or to
use a static IPv6 address provided by the ISP.
To configure IPv6 WAN settings on your device, you must first set the IP mode to
one of the following modes:
• LAN:IPv6, WAN:IPv6
• LAN:IPv4+IPv6, WAN:IPv4
• LAN:IPv4+IPv6, WAN:IPv4+IPv6
See Configuring the IP Mode for instructions on how to set the IP mode.
Configuring DHCPv6
If your ISP provides you with a dynamically assigned address, configure the
device as a DHCPv6 client.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 53
Page 55

Configuring Networking
Configuring IPv6
STEP 1 Choose Networking > IPv6 > IPv6 WAN Configuration.
STEP 2 In the WAN Connection Type field, select Automatic Configuration-DHCPv6.
STEP 3 Click Save.
STEP 1 Choose Networking > IPv6 > IPv6 WAN Configuration.
6
To configure the device to be a DHCPv6 client:
Configuring a Static IPv6 WAN Address
If your ISP assigns you a fixed address to access the WAN, configure the dev ice t o
use a static IPv6 address.
To configure a static IPv6 WAN address:
STEP 2 From the WAN Connection Type menu, select Static IPv6.
STEP 3 Enter this information:
IPv6 Address IPv6 address of the WAN port.
IPv 6 Pre f ix Length Length of the IPv6 prefix (typically defined by the
ISP). The IPv6 network (subnet) is identified by the
initial bits of the address called the prefix. All hosts
in the subnetwork have the identical prefix.
For example, in the IPv6 address
2001:0DB8:AC10:FE01:: the prefix is 2001.
Default IPv6 Gateway IPv6 address of the default gateway. This is
typically the IP address of the server at the ISP.
Static DNS 1 IP address of the primary IPv6 DNS server.
Static DNS 2 IP address of the secondary IPv6 DNS server.
STEP 4 Click Save.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 54
Page 56

Configuring Networking
Configuring IPv6
STEP 1 Choose Networking > IPv6 > IPv6 WAN Configuration.
STEP 2 In the WAN Connection Type field, choose PPPoE IPv6.
STEP 3 Enter the following inf o rmation (it might be necessary to contact your ISP to obtain
6
Configuring PPPoE IPv6 Settings
You can run IPv4 PPPoE, IPv6 PPPoE, or both. If you run both, your IPv6 WAN
PPPoE settings must match your IPv4 WAN PPPoE settings. If they do not match, a
message is displayed asking if you want to set the IPv6 protocol to match the IPv4
protocol. . For more information, see Configuring PPPoE.
To configure the PPPoE IPv6 settings:
your PPPoE login information):
Username Username assigned to you by the ISP.
Password Password assigned to you by the ISP.
Connect on Demand If your ISP charges based on the amount of time
that you are connected, select the radio button.
When selected, the Internet connection is active
only when traffic is present. If the conne ction is
idle—that is, no traffic is flowing—the connection is
closed. In the Max Idle Time field, enter the number
of minutes that must elapse with no traffic detected
on the link before the link is shut down.
Keep Alive Keeps the WAN link up by sending a keep alive
message through the port. In the redial period field,
enter the number of seconds after which the
device attempts to reconnect if it is disconnected.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 55
Page 57

Configuring Networking
Configuring IPv6
6
Authentication Type Authentication types:
Auto-negotiation—A server sends a configuration
request specifying the security algorithm set on
the server. The device replies with its
authentication credentials, including the security
type sent by the server.
PAP—Use the Password Authentication Protocol
(PAP) to connect to the ISP.
CHAP—Use Challenge Handshake Authentication
Protocol (CHAP) to connect with the ISP.
MS-CHAP or MS-CHAPv2—Use Microsoft
Challenge Handshake Authentication Protocol to
connect to the ISP.
Service Name Name that your ISP might require to log onto the
PPPoE server.
MTU The maximum transmission unit (MTU) or the size of
the largest packet that can be sent over the
network.
Unless a change is required by your ISP, we
recommend that you choose Auto. The standard
MTU value for Ethernet networks is 1500 bytes. For
PPPoE connections, the value is 1492 bytes. If your
ISP requires a custom MTU setting, choose
Manual.
Size MTU size. If your ISP requires a custom MTU
setting, enter the MTU size.
Address Mode Dynamic or static address mode. If you choose
static, enter the IPv6 address in the next field.
IPv 6 Pre f ix Length IPv6 prefix length.
Default IPv6 Gateway IP address of the default IPv6 gateway.
Static DNS 1 IP address of the primary DNS server.
Static DNS 2 IP address of the secondary DNS server.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 56
Page 58

Configuring Networking
Configuring IPv6
STEP 4 Click Save.
6
Configuring IPv6 LAN Connections
In the IPv6 mode, the LAN DHCP server is enabled by default (similar to the IPv4
mode). The DHCPv6 server assigns IPv6 addresses from configured address
pools that use the IPv6 prefix length assigned to the LAN.
To configure IPv6 LAN settings on your device, you must first set the IP mode to
one of the following modes:
• LAN:IPv6, WAN:IPv4
• LAN:IPv6, WAN:IPv6
• LAN:IPv4+IPv6, WAN:IPv4
• LAN:IPv4+IPv6, WAN:IPv4+IPv6
See Configuring the IP Mode for more information on how to set the IP mode.
To configure IPv6 LAN settings:
STEP 1 Choose Networking > IPv6 > IPv6 LAN Configuration.
STEP 2 Enter the following information to configure the IPv6 LAN address:
IPv6 Address Enter the IPv6 address of the device.
The default IPv6 address for the ga teway is fec0::1
(or FEC0:0000:0000:0000:0000:0000:0000:0001).
Y o u can change this 128-bit IPv6 address based on
your network requirements.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 57
Page 59

Configuring Networking
Configuring IPv6
STEP 3 Click Save or continue to configure IPv6 DHCP LAN settings.
STEP 4 Enter the following information to configure the DHCPv6 settings:
6
IPv 6 Pre f ix Length Enter the IPv6 prefix length.
The IPv6 network (subnet) is identified by the initial
bits of the address called the prefix. By default, the
prefix is 64 bits long.
All hosts in the network have the identical initial bits
for their IPv6 address; you set the number of
common initial bits in the network addresses in this
field.
DHCP Status Check to enable the DHCPv6 server.
When enabled, the device assigns an IP address
within a specified range and provides additional
information to any LAN endpoint that requests
DHCP addresses.
Domain Name (Optional) Domain name of the DHCPv6 server.
Serv er Pre ferenc e Server preference level of this DHCP server. DHCP
advertise messages with the highest server
preference value to a LAN host are preferred over
other DHCP server advertise messages.
The default is 255.
Static DNS 1 IPv6 address of the primary DNS server on the ISP
IPv6 network.
Static DNS 2 IPv6 address of the secondary DNS server on the
ISP IPv6 network.
Client Lease Time Client lease time duration (in seconds) for which
IPv6 addresses are leased to endpoints on the
LAN.
STEP 5 Choose Networking > IPv6 > IPv6 LAN Configuration.
STEP 6 In the IP v6 Address Pools Table, clic k Add Row.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 58
Page 60

Configuring Networking
Configuring IPv6
STEP 7 Enter this information:
STEP 8 Click Save.
6
Start Address Starting IPv6 address of the pool.
End Address Ending IPv6 address of the pool.
IPv 6 Pre f ix Length Prefix length that determines the number of
common initial bits in the network addresse s.
To edit the settings of a pool, select the pool and click Edit. To delete a selected
pool, click Delete. Click Save to apply changes.
Configuring IPv6 Static Routing
You can configure static routes to direct packets to the destination network. A
static route is a predetermined pathway that a packet must travel to reach a
specific host or network.
Some ISPs require static routes to build a routing table instead of using dynamic
routing protocols. Static routes do not require CPU resources to exchange routing
information with a peer router.
You can also use static routes to reach peer routers that do not support dynamic
routing protocols. Static routes can be used together with dynamic routes. Be
careful not to introduce routing loops in your network.
To create a static route:
STEP 1 Choose Networking > IPv6 > IPv6 Static Routing.
STEP 2 In the list of static routes, click Add Row.
STEP 3 Enter this information:
Name Route name.
Destination IPv6 address of the destination host or network for
this route.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 59
Page 61

Configuring Networking
Configuring IPv6
6
Prefix Length Number of prefix bits in the IPv6 address that define
the destination subnet.
Gateway IPv6 address of the gateway through which the
destination host or network can be reached.
Interface Interface for the route: LAN, WAN, or 6to4.
Metric Priority of the route. Choose a value between 2 and 15.
If multiple routes to the same destination exist, the
route with the lowest metric is used.
Active Check to make the route active. When you add a route
in an inactive state, it is listed in the routing table, but is
not used by the device.
Entering an inactive route is useful if the route is not
available when you add the route. When the network
becomes available, you can enable the route.
STEP 4 Click Save.
To edit the settings of a route, select the route and click Edit. To delete a selected
route, click Delete. Click Save to apply changes.
Configuring Routing (RIPng)
RIP Next Generation (RIPng) is a routing protocol based on the distance vector
(D-V) algorithm. RIPng uses UDP packets to exchange routing information through
port 521.
RIPng uses a hop count to measure the distance to a destination. The hop count is
referred to as metric, or cost. The hop count from a router to a directly-connected
network is 0. The hop count between two directly-connected routers is 1. When
the hop count is greater than or equal to 16, the destination network or host is
unreachable.
By default, the routing update is sent every 30 seconds. If the router receives no
routing updates from a neighbor after 180 seconds, the routes learned from the
neighbor are considered as unreachable. After another 240 seconds, if no routing
update is received, the router removes these routes from the routing table.
On the device, RIPng is disabled by default.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 60
Page 62

Configuring Networking
Configuring IPv6
STEP 1 Choose Networking > IPv6 > Routing (RIPng).
STEP 2 Check Enable.
STEP 3 Click Save.
6
To configure RIPng:
Configuring Tunneling
IPv6-to-IPv4 tunneling (6-to-4 tunneling) allows IPv6 packets to be transmitted
over an IPv4 network. IPv4 to IPv6 tunneling (4-to-6 tunneling) allows IPv4 packets
to be transmitted over an IPv6 network.
6 to 4 Tunneling
6-to-4 tunneling is typically used when a site or end user wants to connect to the
IPv6 Internet using the existing IPv4 network.
To configure 6-to-4 tunneling:
STEP 1 Select Networking > IPv6 > Tunneling.
STEP 2 In the 6 to 4 Tunneling field, check Enable.
STEP 3 Choose the type of tunneling (6to4 or 6RD [Rapid Deployment]).
STEP 4 For 6RD Tunneling, choose auto or manual.
STEP 5 Enter the following information:
• IPv6 Prefix
• IPv 6 Pre f ix Length
• Border Relay
• IPv4 Mask Length.
STEP 6 Click Save.
4 to 6 Tunneling
To configure 4-to-6 tunneling:
Cisco RV215W Wireless-N VPN Firewall Administration Guide 61
Page 63

Configuring Networking
Configuring IPv6
STEP 1 Select Networking > IPv6 > Tunneling.
STEP 2 In the 4 to 6 Tunneling field, check Enable.
STEP 3 Enter the local WAN IPv6 address on the device.
STEP 4 Enter the Remote IPv6 address, or the IP address of the remote endpoint.
STEP 5 Click Save.
6
Viewing IPv6 Tunnel Status
To view IPv6 tunnel status:
STEP 1 Choose Networking > IPv6 > IPv6 Tunnels Status.
STEP 2 Click Refresh to display the most up-to-date information.
This page displays information about the automatic tunnel set up through the
dedicated WAN interface. The table shows the name of tunnel and the IPv6
address that is created on the device.
Configuring Router Advertisement
The Router Advertisement Daemon (RADVD) on the device listens for router
solicitations in the IPv6 LAN and responds with router advertisements as required.
This is stateless IPv6 auto configuration, and the device distributes IPv6 prefixes
to all nodes on the network.
To configure the RADVD:
STEP 1 Choose Networking > IPv6 > Router Advertisement.
STEP 2 Enter this information:
RADVD Status Check Enable to enable RADVD.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 62
Page 64

Configuring Networking
Configuring IPv6
6
Advertise Mode Select one of the following modes:
Unsolicited Multicast—Send Router
Advertisements (RAs) to all interfaces belonging to
the multicast group.
Unicast only—Restrict advertisements to
well-known IPv6 addresse s only (RAs are sent to
the interface belonging to the known address only).
Advertise Interval Advertise interval (4–1800) for the Unsolicited
Multicast. The default is 30. The advertise inter val
is a random value between the Minimum Router
Advertisement Interval (MinRtrAdvInterval) and
Maximum Router Advertisement Interval
(MaxRtrAdvInterval).
MinRtrAdvInterval = 0.33 * MaxRtrAdvInterval
RA Flags Check Managed to use the administered/stateful
protocol for address auto configuration.
Check Other to use the administered/stateful
protocol of other, non-address information auto
configuration.
Router Preference Choose low, medium, or high from the drop-down
menu. The default is medium.
The router preference provides a preference
metric for default routers. The low, medium and
high values are signaled in unused bits in RA
messages. This extension is backward compatible,
both for routers (setting the router preference
value) and hosts (interpreting the router pref e r ence
value). These values are ignored by hosts that do
not implement router preference. This feature is
useful if there are other RADVD-enabled devices
on the LAN.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 63
Page 65

Configuring Networking
Configuring IPv6
STEP 3 Click Save.
6
MTU MTU size (0 or 1280 to 1500). The default is 1500
bytes.
The Maximum Transmit Unit (MTU) is the size of the
largest packet that can be sent over the network.
The MTU is used in RAs to ensure all nodes on the
network use the same MTU value when the LAN
MTU is not well-known.
Router Life Time Router lif etime value or the time in seconds that the
advertisement messages exists on the route. The
default is 3600 seconds.
Configuring Advertisement Prefixes
To configure the RADVD available prefixes:
STEP 1 Choose Networking > IPv6 > Advertisement Prefixes.
STEP 2 Click Add Row.
STEP 3 Enter this information:
IPv 6 Pre fix Type Choose one of the following types:
6to4—Allows IPv6 packets to be transmitted over
an IPv4 network. It is used when an end user wants
to connect to the IPv6 Internet using their existing
IPv4 connection.
Global/Local—A locally unique IPv6 address that
you can use in private IPv6 networks or a globally
unique IPv6 Internet address.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 64
Page 66

Configuring Networking
Configuring IPv6
6
SLA ID If you choose 6to4 as the IPv6 prefix type, enter
the Site-Level Aggregation Identifier (SLA ID).
The SLA ID in the 6to4 address prefix is set to the
interface ID of the interface on which the
advertisements are sent.
IPv6 Prefix If you choose Global/Local as the IPv6 prefix type,
enter the IPv6 prefix. The IPv6 prefix specifies the
IPv6 network address.
IPv 6 Pre f ix Length If you choose Global/Local as the IPv6 prefix type,
enter the prefix length. The prefix length variable is
a decimal value that indicates the number of
contiguous, higher-order bits of the address that
make up the network portion of the address.
Prefix Lifetime Prefix lifetime, or the length of time over which the
STEP 4 Click Save.
requesting router is allowed to use the prefix.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 65
Page 67

Configuring the Wireless Network
This chapter describes how to configure the device wireless network.
• Wireless Security
• Cisco RV215W Wireless Networks
• Configuring Basic Wireless Settings
• Configuring Advanced Wireless Settings
7
• Configuring WDS
• Configuring WPS
Wireless Security
Wireless networks are convenient and easy to install, so small businesses and
homes with high-speed Internet access are adopting them at a rapid pace.
Because wireless networking operates by sending information over radio waves,
it can be more vulnerable to intruders than a traditional wired network.
Wireless Security Tips
You cannot physically prevent someone from connecting to your wireless
network, but you can take the following steps to keep your network secure:
• Change the default wireless network name or SSID.
Wireless devices have a def a ult wireless network name or SSID. This is the
name of your wireless network, and can be up to 32 characters in length.
To protect your network, change the default wireless network name to a
unique name to distinguish your wireless network from other wireless
networks that may exist around you.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 66
Page 68

Configuring the Wireless Network
Wireless Security
When choosing names, do not use personal information (such as your
Social Securit y number) because this information may be available for
anyone to see when browsing for wireless networks.
• Change the default password.
For wireless products such as access points, routers, and gateways, you
are asked for a password when you want to change their settings. These
devices have a default password. The default password is often cisco.
Hackers know these default values and may try to use them to access your
wireless device and change your network set tings. To thwart unauthorized
access, customize the device password so that it is difficult to guess.
• Enable MAC address filtering.
Cisco routers and gateways give you the ability to enable MAC address
filtering. The MAC address is a unique series of numbers and letters
assigned to every networking device.
7
With MAC address filtering enabled, wireless network acc ess is provided
solely for wireless devices with specific MAC addresses. For example, you
can specify the MAC address of each computer in your network so that
only those computers can access your wireless network.
• Enable encryption.
Encryption protects data transmitted over a wireless network. Wi-Fi
Protect ed Access (WP A/WP A2) and Wir ed Equivalency Privacy (WEP) offer
different levels of security for wireless communication. Currently, devices
that are Wi-Fi certified are required to support WPA2, but are not required
to support WEP.
A network encrypted with WPA/WPA2 is more secure than a network
encrypted with WEP, because WPA /WPA2 uses dynamic key encryption.
To protect the inf ormation as it passes over the airwaves, enable the highest
level of encryption supported by your network equipment.
WEP is an older encryption standard and may be the only option available
on some older devices that do not support WPA.
• Keep wireless routers, access points, or gateways a way fr om e xterior walls
and windows.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 67
Page 69

Configuring the Wireless Network
Cisco RV215W Wireless Networks
• Turn wireless routers, access points, or gateways off when they are not
being used (at night, during vacations).
• Use strong passphrases that are at least eight characters in length.
Combine letters and numbers to avoid using standard words that can be
found in the dictionary.
General Network Security Guidelines
Wi r e l ess n e tw or k se c ur i ty i s u s e le ss if the underlying network is not secure. Cisco
recommends that you take the following precautions:
• Password-protect all computers on the network and individually password-
protect sensitive files.
• Change passwords on a regular basis.
7
• Install anti-virus software and personal firewall software.
• Disable file sharing (peer-to-peer) to prevent applications from using file
sharing without your consent.
Cisco RV215W Wireless Networks
The device provides four virtual wireless networks, or four SSIDs (Service Set
Identifier): ciscosb1, ciscosb2, ciscosb3, and ciscosb4. These are the default
names or SSIDs of these networks, but you can change these names to more
meaningful names. This table des cribes the default settings of these networks:
SSID Name ciscosb1 ciscosb2 ciscosb3 ciscosb4
Enabled Yes No No No
SSID
Broadcast
Enabled Disabled Disabled Disabled
Security
Mode
MAC Filter Disabled Disabled Disabled Disabled
VLAN 1111
Cisco RV215W Wireless-N VPN Firewall Administration Guide 68
Disabled
1
Disabled Disabled Disabled
Page 70

Configuring the Wireless Network
Configuring Basic Wireless Settings
SSID Name ciscosb1 ciscosb2 ciscosb3 ciscosb4
7
Wireless
Isolation
with SSID
WMM Enabled Enabled Enabled Enabled
WPS
Hardware
Button
1. When using Setup Wizard, select Best Security or Better Security to protect the device
from unauthorized access.
Disabled Disabled Disabled Disabled
Enabled Disabled Disabled Disabled
Configuring Basic Wireless Settings
You can use the Basic Sett ings page (Wireless > Basic Settings) to configure
basic wireless settings.
To configure basic wireless settings:
STEP 1 Choose Wireless > Basic Settings.
STEP 2 In the Radio field, check Enable to turn on the wireless radio. By default there is
only one wireless network enabled, ciscosb1.
STEP 3 In the Wireless Network Mode field, choose one of these options from the
drop-down menu:
B/G/N-Mixed Choose this option if you have Wireless-N,
Wireless-B, and Wireless-G devices in your
network. This is the default setting (recommended).
B Only Choose this option if you have only Wireless-B
devices in your network.
G Only Choose this option if you have only Wireless-G
devices in your network.
N Only Choose this option if you have only Wireless-N
devices in your network.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 69
Page 71

Configuring the Wireless Network
Configuring Basic Wireless Settings
B/G-Mixed Choose this option if you have Wireless-B and
G/N-Mixed Choose this option if you have Wireless-G and
STEP 4 If you chose B/G/N-Mixed, N-Only, or G/N Mixed, in the Wireless Band Selection
field, select the wireless bandwidth on your network (20MHz or 20/40MHz). If
you chose N-Only , you must use WPA2 security on your network. See Configuring
the Security Mode.
STEP 5 In the Wireless Channel field, choose the wireless channel from the drop-down
menu.
STEP 6 In the AP Management VLAN field, choose VLAN 1 if you are using the default
settings.
7
Wireless-G devices in your network.
Wireless-N devices in your network.
If you create additional VLANs, choose a value that corresponds with the VLAN
configured on other switches in the network. This is done for security purposes.
You might need to change the management VLAN to limit access to the device
Device Manager.
STEP 7 (Optional) In the U-APSD (WMM Power Save) field, check Enable to enable the
Unscheduled Automatic Power Save Delivery (U-APSD) feature, also r eferr ed to as
WMM Power Save, that allows the radio to conserve power.
U-APSD is a power-saving scheme optimized for real-time applications, such as
VoIP, transferring full-duplex data over WLAN. By classifying outgoing IP traffic as
Voice data, these types of applications can increase battery life by approximately
25% and minimize transmit delays.
STEP 8 (Optional) Configure the settings of the four wireless networks (see Editing the
Wireless Network Settings).
STEP 9 Click Save.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 70
Page 72

Configuring the Wireless Network
Configuring Basic Wireless Settings
Editing the Wireless Network Settings
The Wireless Table in the Basic Settings page (Wireless > Basic Settings) lists
the settings of the four wireless networks supported on the device.
To configure wireless network settings:
STEP 1 Check the box for the networks you want to configure.
STEP 2 Click the Edit button.
STEP 3 Configure these settings:
Enable SSID Click On to enable the network.
SSID Name Enter the name of the network.
7
SSID Broa dcast Check this box to enable SSID broadcast. If
VLAN Choose the VLAN associated with the network.
Wireless Isolation with SSID Check this box to enable wireless isolation
WMM (Wi-Fi Multimedia) Check this box to enable WMM.
WPS Hardware Button Check this box to map the device WPS button
STEP 4 Click Save.
SSID broadcast is enabled, the wireless router
advertises its availability to wireless-equipp ed
devices in the range of the router.
within the SSID.
on the front panel to this network.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 71
Page 73

Configuring the Wireless Network
Configuring Basic Wireless Settings
Configuring the Security Mode
You can configure one of the following security modes for wireless networks.
Configuring WEP
The WEP security mode offers weak security with a basic encryption method that
is not as secure as WPA. WEP may be required if your network devices do not
support WPA.
NOTE If you do not have to use WEP, we recommend that you use WPA2. If you are using
the Wireless-N only mode, you must use WPA2.
To configure the WEP security mode:
STEP 1 In the Wireless Table (Wireless > Basic Settings), check the box for the network
that you want to configure.
7
STEP 2 Click Edit Security Mode.
The Security Settings page appears.
STEP 3 In the Select SSID field, choose the SS ID for which to configure the security
settings.
STEP 4 From the Security M ode menu, choose WEP.
STEP 5 In the Authentication Type field, choose one of the following options:
• Open System—This is the default option.
• Shared Key—Select this option if your network administrator recommends
this setting. If you are unsure, select the default option.
In both cases, the wireless client must provide the correct shared key (password)
to access the wireless network.
STEP 6 In the Encryption field, choose the encryption type:
• 10/64-bit(10 hex digits)—Provides a 40-bit key.
• 26/128-bit(26 hex digits)—Pr ovides a a 104-bit ke y, which offers stronger
encryption, making the key more difficult to decode. We r ecommend 128-bit
encryption.
STEP 7 (Optional) In the Passphrase field, enter an alphanumeric phrase (longer than eight
characters for optimal security) and click Generate Key to generate four unique
WEP keys in the WEP Key fields.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 72
Page 74
Configuring the Wireless Network
Configuring Basic Wireless Settings
If you want to provide your own key, enter it directly in the Key 1 field
(recommended). The length of the key should be 5 ASCII characters (or 10
hexadecimal characters) for 64-bit WEP and 13 ASCII characters (or 26
hexadecimal characters) for 128-bit WEP. Valid hexadecimal characters are 0 to 9
and A to F.
STEP 8 In the TX Key field, choose which key to use as the shared key that devices must
use to access the wireless network.
STEP 9 Click Save to save your settings.
STEP 10 Click Back to go back to the Basic Settings page.
Configuring WPA-Personal, WPA2-Personal, and WPA2-Personal Mixed
The WPA Personal, WPA2 Personal, and the WPA2 Personal Mixed security
modes offer strong security to replace WEP.
7
• WPA-Personal—WPA is part of the wireless security standard (802.11i)
standardized by the Wi-Fi Alliance and was intended as an intermediate
measure to take the place of WEP while the 802.11i standard was being
prepared. WPA-Personal supports Temporal Key Integrity Protocol (TKIP)
and Advanced Encryption Standard (AES) encryption.
• WPA2-Personal—(Recommended) WPA2 is the implementation of the
security standard specified in the final 802.11i standard. WPA2 supports
AES encryption and this option uses Preshared Key (PSK) for
authentication.
• WPA2-Personal Mixed—Allows both WPA and WPA2 clients to connect
simultaneously using PSK authentication.
The personal authentication is the PSK that is an alphanumeric passphrase shared
with the wireless peer.
To configure the WPA Personal security mode:
STEP 1 In the Wireless Table (Wireless > Basic Settings), check the box for the network
you want to configure.
STEP 2 Click Edit Security Mode. The Security Settings page appears.
STEP 3 In the Select SSID field, choose the SS ID for which to configure the security
settings.
STEP 4 From the Security M ode menu, choose one of the three WPA Personal options.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 73
Page 75

Configuring the Wireless Network
Configuring Basic Wireless Settings
STEP 5 (WPA-Personal only) In the Encryption field, choose one of the following options:
• TKIP/AES—Choose TKIP/AES to ensure compatibility with older wireless
devices that may not support AES.
• AES—This option is more secure.
STEP 6 In the Secur i ty Key field, enter an alphanumeric phrase (8–63 ASCII characters or
64 hexadecimal digits). The password strength meter shows how secure the key
is: below minimum, weak, strong, very strong, or secure. We recommend using a
security key that registers on the strength meter as secure.
STEP 7 To show the security key as you are entering it, check the Unmask Password box.
STEP 8 In the Key Renewal field, enter the duration of time (600–7200 seconds) between
key renewals. The default value is 3600.
STEP 9 Click Save to save your settings.
7
STEP 10 Click Back to go back to the Basic Settings page.
Configuring WPA-Enterprise, WPA2-Enterprise, and WPA2-Enterprise Mixed
The WPA Enterprise, WPA2 Enterprise, and the W PA2 Enterprise Mixed security
modes allow you to use RADUIS server authentication.
• WPA-Enterprise—Allows you to use WPA with RADIUS s e rver
authentication.
• WPA2-Enterprise—Allows you to use WPA2 with RADIUS server
authentication.
• WPA2-Enterprise Mixed—Allows both WPA and WPA2 clients to connect
simultaneously using R AD I US authentication.
To configure the WPA Enterprise security mode:
STEP 1 In the Wireless Table (Wireless > Basic Settings), check the box for the network
you want to configure.
STEP 2 Click Edit Security Mode.
STEP 3 In the Select SSID field, choose the SS ID for which to configure the security
settings.
STEP 4 From the Security M ode menu, choose one of the three WPA Enterprise options.
STEP 5 (WPA-Enterprise only) In the Encryption field, choose one of the following options:
Cisco RV215W Wireless-N VPN Firewall Administration Guide 74
Page 76

Configuring the Wireless Network
Configuring Basic Wireless Settings
• TKIP/AES—Choose TKIP/AES to ensure compatibility with older wireless
devices that may not support AES.
• AES—This option is more secure.
STEP 6 In the RADIUS Server field, enter the IP address of the R A DIUS server.
STEP 7 In the RADIUS Port field, enter the port used to access the RADIUS server.
STEP 8 In the Shared Key field, enter an alphanumeric phrase.
STEP 9 In the Key Renewal field, enter the duration of time (600–7200 seconds) between
key renewals. The default value is 3600.
STEP 10 Click Save to save your settings.
STEP 11 Click Back to go back to the Basic Settings page.
7
Configuring MAC Filtering
You can use MAC Filt ering to permit or deny access to the wireless network based
on the MAC (hardware) address of the requesting device. For example, you can
enter the MAC addresses of a set of computers and only allow those computers to
access the network. You can configure MAC Filtering for each network or SSID.
To configure MAC filtering:
STEP 1 In the Wireless Table (Wireless > Basic Settings), check the box for the network
you want to configure.
STEP 2 Click Edit MAC Filtering. The Wireless MAC Filter page appears.
STEP 3 In the Edit MAC Filtering field, check the Enable box to enable MAC Filtering for
this SSID.
STEP 4 In the Connection Control field, choose the type of access to the wireless
network:
• Prevent—Select this option to prevent devices with the MAC addresses
listed in the MAC Address T able fr om accessing the wireless network. This
option is selected by default.
• Permit—Select this option to allow devices with the MAC addresses listed
in the MAC Address Table to access the wireless network.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 75
Page 77

Configuring the Wireless Network
Configuring Basic Wireless Settings
STEP 5 To show computers and other devices on the wireless network, click
Show Client List.
STEP 6 In the Save to MAC Address Filter List field, check the box to add the device to
the list of devices to be added to the MAC Address Table.
STEP 7 Click Add to MAC to add the selected devices in the Client List Table to the
MAC Address Table.
STEP 8 Click Save to save your settings.
STEP 9 Click Back to go back to the Basic Settings page.
Configuring Time of Day Access
7
To further protect your network, you can restrict access to it by specifying when
users can access the network.
To configure Time of Day Access:
STEP 1 In the Wireless Table (Wireless > Basic Settings), check the box for the network
you want to configure.
STEP 2 Click Time of Day Access. The Time of Day Access page appears.
STEP 3 In the Active Time field, check Enable to enable Time of Day Access.
STEP 4 In the Start Time and Stop Time fields, specify the time of day period when
access to the network is allowed.
STEP 5 Click Save.
Configuring the Wireless Guest Network
The device supports a wireless guest network that is separated from the other
wireless SSIDs, or networks, on the router. This router provides secure guest
access that is isolated from the rest of the network, and can be configured to
restrict access time and bandwidth used. The following restrictions and
configuration guidelines apply:
• One guest network can be configured for each device.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 76
Page 78

Configuring the Wireless Network
Configuring Basic Wireless Settings
• The guest network is configured as one of the four available SSIDs on the
device.
• The guest network cannot be configured on the AP Management VLAN
(VLAN ID 1).
To configure the guest network :
Create a New VLAN
STEP 1 In the Management Interface, choose Networking > LAN > VLAN Membership.
STEP 2 In the VLAN Setting Table, add a new VLAN for the guest network. For example,
click Add Row and enter the following:
• VLAN ID—Enter a number for the VLAN (for example, 4).
• Description—Enter a name for the VLAN (for example, guest-net).
7
STEP 3 Leave the ports as tagged and click Save.
Set Up the Guest Network
STEP 1 In the Management Interface, choose Wireless > Basic Settings.
STEP 2 In the Wireless Table, choose the SSID or network that you want to designate as
the guest network.
STEP 3 Click Edit. Change the SSID name to reflect the guest designation (for example,
guest-net
STEP 4 Check the SSID Broadcast box so that the network will appear as an available
wireless connection to clients searching for networks.
STEP 5 Check the Guest Network box to configure this SSID as the guest network.
STEP 6 Choose the VLAN you created for the guest network (or, if you have not yet
created a network, select Add New VLAN).
STEP 7 Click Save. The system notifies you that the physical Ethernet ports on the device
are excluded from the VLAN that you have assigned to the guest network. In
addition, Wireless Isolation with SSID and WMM are automatically enabled.
).
Cisco RV215W Wireless-N VPN Firewall Administration Guide 77
Page 79

Configuring the Wireless Network
Configuring Advanced Wireless Settings
Configure the Password and Other Options
STEP 1 In the Management Interface, choose Wireless > Basic Settings.
STEP 2 Under the Wireless Table, click Edit Guest Net.
STEP 3 Enter a password that users will enter to access the guest network.
STEP 4 Enter the password again to confirm.
STEP 5 Enter the time, in minutes, that the guest connection will be available for users.
7
STEP 6 (Optional) To restrict bandwidth usage by the guest network, check Enable Guest
Band w i d t h R es t r i c t i o n . (QoS must be enabled first; click the link to the Bandwidth
Management page if you need to configure QoS.) In the Available Bandwidth
enter the percentage of bandwidth to allocate to the guest network.
STEP 7 Click Save.
Configuring Advanced Wireless Settings
Advanced wireless settings should be adjusted only by an expert administrator;
incorrect settings can reduce wireless performance.
To configure advanced wireless settings:
STEP 1 Choose Wireless > Advanced Settings. The Advanced Settings page appears.
STEP 2 Configure these settings:
field,
Frame Bur st Enable this option to provide your wireless networks
with greater performance, depending on the
manufacturer of your wireless products. If you are not
sure how to use this option, keep the default (enabled).
WMM No
Acknowledgement
Cisco RV215W Wireless-N VPN Firewall Administration Guide 78
Click to enable this feature.
Enabling WMM No Acknowledgement can result in mor e
efficient throughput, but higher error rates in a noisy
Radio Frequency (RF) environment. Default setting is
disabled.
Page 80

Configuring the Wireless Network
Configuring Advanced Wireless Settings
Basic Rate The Basic Rate setting is not the rate of transmission but
7
a series of rates at which the Services Ready Platform
can transmit. The device advertises its basic rate to the
other wireless devices in your network, so they know
which rates will be used. The Services Ready Platform
will also advertise that it will automatically select the
best rate for transmission.
The default setting is Default, when the device can
transmit at all standard wireless rates (1 Mbps, 2 Mbps,
5.5 Mbps, 11 Mbps, 18 Mbps, 24 Mbps, 36 Mbps, 48
Mbps, and 54 Mbps). In addition to B and G speeds, the
device supports N speeds. Other options are 1-2 Mbps,
for use with older wireless technology , and All, when the
device can transmit at all wireless rates.
The Basic Rate is not the actual rate of data transmission.
If you want to specify the device rate of data
transmission, configure the Transmission Rate setting.
Transmission Rate The rate of data transmission should be set depending
on the speed of your wireless network. You can select
from a range of transmission speeds, or you can select
Auto to have the device automatically use the fastest
possible data rate and enable the Auto-Fallback feature.
Auto-Fallback will negotiate the best possible
connection speed between the device and a wireless
client. The default is Auto.
N Transmission
Rate
The rate of data transmission should be set depending
on the speed of your Wireless-N networking. You can
select from a range of transmission speeds, or you can
select Auto to have the device automatically use the
fastest possible data rate and enable the Auto-Fallback
featur e. Auto-Fallback will negotiate the best possible
connection speed between the device and a wireless
client. The default is Auto.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 79
Page 81

Configuring the Wireless Network
Configuring Advanced Wireless Settings
7
CTS Protection
Mode
Beacon Interval The Beacon Interval value indicates the frequency
DTIM Interval This value, between 1 and 255, indicates the interval of
The device will automatically use CTS (Clear-To-Send)
Protection Mode when your Wireless-N and Wireless-G
devices are experiencing severe problems and are not
able to transmit to the device in an environment with
heavy 802.11b traffic.
This function boosts the device ability to catch all
Wireless-N and Wireless-G transmissions but will
severely decrease performance. The default is Auto.
interval of the beacon. A beacon is a packet broadcast
by the device to synchronize the wireless network.
Enter a value between 40 and 3,500 milliseconds. The
default value is 100.
the Delivery Traffic Indication Message (DTIM). A DTIM
field is a countdown field informing clients of the next
window for listening to broadcast and multicast
messages.
Fragmentation
Threshold
When the device has buffered broadcast or multicast
messages for associated clients, it sends the next DTIM
with a DTIM Interval value. Its clients hear the beacons
and awaken to receive the broadcast and multicast
messages. The default value is 1.
This value specifies the maximum size for a packet
before data is fragmented into multiple packets. If you
experience a high packet error rate, you may slightly
increase the Fragmentation Threshold.
Setting the Fragmentation Threshold too low may result
in poor network performance. Only minor reduction of
the default value is recommended. In most cases, it
should remain at its default value of 2346.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 80
Page 82

Configuring the Wireless Network
Configuring WDS
RTS Threshold If you encounter inconsistent data flow, enter only minor
STEP 3 Click Save.
7
reductions. The default value of 2347 is recommended.
If a network packet is smaller than the preset Request to
Send (RTS) threshold size, the RTS/Clear to Send (CTS)
mechanism will not be enabled. The Services Ready
Platform sends RTS frames to a particular receiving
station and negotiates the sending of a data frame.
After receiving an RTS, the wireless station responds
with a CTS frame to acknowledge the right to begin
transmission.
Configuring WDS
A Wireless Distribution System (WDS) is a system that enables the wireless
interconnection of access points in a network. It allows a wireless network to be
expanded using multiple access points without the need for a wired backbone to
link them.
To establish a WDS link, the device and other remote WDS peers must be
configured in the same wireless network mode, wireless channel, wireless b and
selection, and encryption t y pes (None or WEP).
WDS is suppor ted on one SSID only.
To configure a WDS:
STEP 1 Choose Wireless > WDS.
STEP 2 Check the Allow wireless signal to be repeated by a repeater box to enable
WDS.
STEP 3 To manually enter the MAC address of a repeater click Manual, or choose Auto to
have the router automatically detect remote access points.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 81
Page 83

Configuring the Wireless Network
Configuring WPS
To select repeaters from the Available Networks table, click Show Site Survey to
display the A v ailab le Networks Table.
a. Click the check boxes to select up to three access points to use as repeaters.
b. Click Connect to add the MAC addresses of the selected access points to the
MAC field.
You can also enter the MAC addresses of up to three access points to use as
repeaters in the MAC 1, MAC 2, and MAC 3 fields.
STEP 4 Click Save.
Configuring WPS
7
Configure WPS to allow WPS-enabled devices to easily and securely connect to
the wireless network . Refer to your client device documentation for additional
instructions on setting up WPS on your client device.
To configure WPS:
STEP 1 Choose Wireless > WPS. The Wi-Fi Protected Setup page appears.
STEP 2 Select the wireless network on which to enable WPS from the SSID drop-down
menu.
STEP 3 Check WPS Enable to enable WPS. To disable WPS, uncheck the box.
STEP 4 Configure the WPS on client devices in one of the following three ways:
a. Click or press the WPS button on the client device and click the WPS icon on
this page.
b. Enter the WPS PIN number of the client and click Register.
c. Enter a PIN number for the router; use the router PIN number indicated.
Device PIN Status—WPA device personal identification number (PIN)
status.
Device PIN—Identifies the PIN of a device trying to connect.
PIN Lifetime—The lifetime of the key. If the time expires, a new key is
negotiated.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 82
Page 84

Configuring the Wireless Network
Configuring WPS
After you configure WPS, the following information appears at the bottom of the
WPS page: Wi-Fi Protected Setup Status, Network Name (SSID), and Security.
7
Cisco RV215W Wireless-N VPN Firewall Administration Guide 83
Page 85

Configuring the Firewall
This chapter describes how to configure the firewall properties of the device.
• Cisco RV215W Firewall Features
• Configuring Basic Firewall Settings
• Managing Firewall Schedules
• Configuring Services Management
8
• Configuring Access Rules
• Creating an Internet Access Policy
• Configuring Port Forwar ding
Cisco RV215W Firewall Features
You can secure your network by creating and applying rules that th e device uses
to selectively block and allow inbound and outbound Internet traffic. You then
specify how and to what devices the rules apply. To do so, you must define the
following:
• Services or traffic types (examples: web browsing, VoIP, other standard
services and also custom services that you define) that the router should
allow or block.
• Direction f or the traffic by specifying the source and destination of traffic;
this is done by specifying the From Zone (LAN/WAN/DMZ) and To Zone
(LAN/WAN/DMZ).
• Schedules as to when the router should apply rules.
• Keywords (in a domain name or on a URL of a web page) that the router
should allow or block.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 84
Page 86

Configuring the Firewall
Configuring Basic Firewall Settings
• Rules for allowing or blocking inbound and outbound Internet traffic for
• MAC addresses of devices whose inbound access to your network the
• Port triggers that signal the router to allow or block access to specified
• Reports and alerts that you want the router to send to you.
You can, for example, establish restricted-access policies based on time-of-day,
web addresses, and web address keywords. You can block Internet access by
applications and services on the LAN, such as chat rooms or games. You can block
only certain groups of PCs on your network from being accessed by the WAN or
public DMZ network.
Inbound (WAN to LAN/DMZ) rules restrict access to traffic entering your network,
selectively allowing only specific outside users to access specific local resources.
By default, all access from the insecure WAN side is blocked from accessing the
secure LAN, except in response to requests from the LAN or DMZ. To allow
outside devices to access services on the secure LAN, you must create a firewall
rule for each service.
8
specified services on spe c ified schedules.
router should block.
services as defined by port number.
If you want to allow incoming traffic, you must make the router's WAN port IP
address known to the public. This is called exposing your host. How you make
your address known depends on how the WAN ports are configured. For your
device, you may use the IP address if a static address is assigned to the W AN port,
or if your WAN address is dynamic, a DDNS (Dynamic DNS) name can be used.
Outbound (LAN/DMZ to WAN) rules restrict access to traffic leaving your network,
selectively allowing only specific local users to access specific outside resources.
The default outbound rule is to allow access from the secure zone (LAN) to either
the public DMZ or insecure WAN. To block hosts on the secure LAN from
accessing services on the outside (insecure WAN), you must create a firewall rule
for each service.
Configuring Basic Firewall Settings
To configure basic firewall settings:
STEP 1 Choose Firewall > Basic Settings.
STEP 2 Configure the following firewall settings:
Cisco RV215W Wireless-N VPN Firewall Administration Guide 85
Page 87

Configuring the Firewall
Configuring Basic Firewall Settings
Firewall Check Enable to configure firewall settings.
DoS Protection Check Enable to enable Denial of Service
Block WAN Request Blocks ping requests to the device from the WAN.
Web Access Choose the type of web access that can be used
8
protection.
to connect to the firewall: HTTP or HTTPS (secure
HTTP).
Remote Management
Remote Access
Remote Upgrade
Allowed Remote IP
Address
Remote Management
Port
IPv4 Multicast
Passthrough (IGMP
Proxy)
IPv 6 Multicast
Passthrough (IGMP
Proxy)
UPnP
Allow Users to Configure
Allow Users to Disable
Internet Access
Block Java Check to block Java applets. Java applets are
See Configuring Remote Management.
Check Enable to enable multicast passthrough for
IPv4.
Check Enable to enable multicast passthrough for
IPv6.
See Configuring Universal Plug and Play.
small programs embedded in web pages that
enable dynamic functionality of the page. A
malicious applet can be used to compromise or
infect computers.
Enabling this setting blocks Java applets from
being downloaded. Click Auto to automatically
block Java, or click Manual and enter a specific
port on which to block Java.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 86
Page 88

Configuring the Firewall
Configuring Basic Firewall Settings
Block Cookies Check to block cookies. Cookies are used to store
Block ActiveX Check to block ActiveX content. Similar to Java
8
session information by websites that usually
require login. However, several websites use
cookies to store tracking information and browsing
habits. Enabling this option filters out cookies from
being created by a website.
Many websites require that cookies be accepted in
order for the site to be accessed properly. Blocking
cookies can cause many websites to not function
properly.
Click Auto to automatically block cookies, or click
Manual and enter a specific port on which to block
cookies.
applets, ActiveX controls are installed on a
Windows computer while running Internet Explorer.
A malicious ActiveX control can be used to
compromise or infect computers.
Enabling this setting blocks ActiveX applets from
being downloaded.
Click Auto to automatically block ActiveX, or click
Manual and enter a specific port on which to block
ActiveX.
Block Proxy Check to block proxy servers. A proxy server (or
proxy) allows computers to route connections to
other computers through the proxy, thus
circumventing certain firewall rules.
For example, if connections to a specific IP address
are blocked by a firewall rule, the requests can be
routed through a proxy that is not blocked by the
rule, rendering the restriction ineffective. Enabling
this feature blocks proxy servers.
Click Auto to automatically block prox y servers, or
click Manual and enter a specific port on which to
block proxy servers.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 87
Page 89

Configuring the Firewall
Configuring Basic Firewall Settings
FTP ALG Click Auto to use the default FTP port 21. Click
STEP 3 Click Save.
Configuring Remote Management
You can enable remote management so you can access the device from a remote
WAN network.
To configure remote management, configure these settings on the Basic Settings
page:
8
Manual to enter the port number through which
you want to direct FTP traffic on the device.
Remote Management Check Enable to enable remote management.
Remote Access Choose the type of web access that can be used
to connect to the firewall: HTTP or HTTPS (secure
HTTP).
Remote Upgrade To allow remote upgrades of the device, check
Enable.
Allowed Remote IP
Address
Remote Management
Port
Click the Any IP Address button to allow remote
management from any IP address, or enter a
specific IP address in the address field.
Enter the port on which remote access is allowed.
The default port is 443. When remotely accessing
the router, you must enter the remote management
port as part of the IP address. For example:
https://<remote-ip>:<remote-port>, or
https://168.10.1.11:443
Cisco RV215W Wireless-N VPN Firewall Administration Guide 88
Page 90

Configuring the Firewall
!
Managing Firewall Schedules
CAUTION When remote management is enabled, the router is accessible to anyone who
8
knows its IP address. Because a malicious WAN user can reconfigure the device
and misuse it, we recommend that you change the administrator and any guest
passwords before continuing.
Configuring Universal Plug and Play
Universal Plug and Play (UPnP) allows automatic discovery of devices that can
communicate with the device.
To configure UPnP, configure these settings on the Basic Settings page:
UPnP Check Enable to enable UPnP.
Allow Users to Configure Check this box to allow UPnP port-mapping rules
Allow Users to Disable
Internet Access
Managing Firewall Schedules
You can create firewall schedules to apply firewall rules on specific days or at
specific times of the day.
Adding or Editing a Firewall Schedule
To create or edit a schedule:
to be set by users who have UPnP support enabled
on their computers or other UPnP-enabled devices.
If disabled, the device does not allow application to
add the forwarding rule.
Check this box to allow users to disable Internet
access.
STEP 1 Choose Firewall > Schedule Management.
STEP 2 Click Add Row.
STEP 3 In the Name field, enter a unique name to identify the schedule. This name is
available on the Fir ewall Rule Configuration page in the Select Schedule list. (See
Configuring Access R ul es.)
Cisco RV215W Wireless-N VPN Firewall Administration Guide 89
Page 91

Configuring the Firewall
Configuring Services Management
STEP 4 Under Schedu l ed D a y s, select whether you want the schedule to apply to all days
or specific days. If you choose Specific Days, check the box next to the days you
want to include in the schedule.
STEP 5 Under Scheduled Time of Day, select the time of day that you want the schedule
to apply. You can either choose All Times, or choose Specific Time. If you choose
Specific Time, enter the start and end times.
STEP 6 Click Save.
Configuring Services Management
When you create a firewall rule, you can specify a service that is controlled by the
rule. Common types of services are available for selection, and you can create
your own custom services.
8
The Services Management page allows you to create custom services against
which firewall rules can be defined. Once defined, the new service appears in the
List of Available Custom Services table.
To create a custom service:
STEP 1 Choose Firewall > Servi c e Management.
STEP 2 Click Add Row.
STEP 3 In the Service Name field, enter the service name for identification and
management purposes.
STEP 4 In the Protocol field, choose the Layer 4 protocol that the service uses from the
drop-down menu:
• TCP
• UDP
• TCP & UDP
• ICMP
STEP 5 In the Start Port field, enter the first TCP or UDP port of the range that the service
uses.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 90
Page 92

Configuring the Firewall
Configuring Access Rules
STEP 6 In the End Port field, enter the last TCP or UDP port of the range that the service
uses.
STEP 7 Click Save.
To edit an entry, select the entry and click Edit. Make your changes, then click
Save.
Configuring Access Rules
Configuring the Default Outbound Policy
The Access Rules page allows you to configure the default outbound policy for
the traffic that is directed from the secure network (LAN) to the non-secure
network (dedicated WAN/optional).
8
The default inbound policy for traffic flowing from the non-secure zone to the
secure zone is always blocked and cannot be changed.
To configure the default outbound policy:
STEP 1 Choose Firewall > Access Rules.
STEP 2 Choose Allow or Deny.
Note: Ensure that IPv6 support is enabled on the device to configure an IPv6
firewall. See Configuring IPv6.
STEP 3 Click Save.
Reordering Access Rules
The order in which access rules are displayed in the access rules table indicates
the order in which the rules are applied. You may want to r eor der the table to have
certain rules applied before other rules. For e xample, you ma y want t o apply a rule
allowing certain t y pes of traffic before blocking other types of traffic.
To reorder access rules:
STEP 1 Choose Firewall > Access Rules.
STEP 2 Click Reorder.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 91
Page 93

Configuring the Firewall
Configuring Access Rules
STEP 3 Check the box in the row of the rule that you want to move up or down and click
STEP 4 Click Save.
8
the up or down arrow to move the rule up or down one line, or select the desired
position of the rule in the drop-down list and click Move to.
Adding Access Rules
All configured firewall rules on the device are displayed in the Access Rules
Table. This list also indicates whether the rule is enabled (active) and gives a
summary of the from/to zone as well as the services and users the rule affects.
To create an access rule:
STEP 1 Choose Firewall > Access Rules.
STEP 2 Click Add Row.
STEP 3 In the Connection Type field, choose the source of originating traffic:
• Outbound (LAN > WAN)—Choose this option to create an outbound rule.
• Inbound (WAN > LAN)—Choose this option to create an inbound rule.
• Inbound (WAN > DMZ)—Choose this option to create an inbound rule.
STEP 4 From the Action drop-down menu, choose the action:
• Always Block—Always block the selected type of traffic.
• Always Allow—Never block the selected type of traffic.
• Block by schedule, otherwise allow—Blocks the selected type of traffic
according to a schedule.
• Allow by schedule, otherwise block—Allows the selected type of traffic
according to a schedule.
STEP 5 From the Services drop-down menu, choose the service to allow or block for this
rule. Choose All Traffic to allow the rule to apply to all applications and services,
or choose a single application to block:
• Domain Name System (DNS), UDP or TCP
• File Transfer Protocol (FTP)
• Hyptertext Transfer Protocol (HTTP)
Cisco RV215W Wireless-N VPN Firewall Administration Guide 92
Page 94

Configuring the Firewall
Configuring Access Rules
8
• Secure Hypertext Transfer Protocol (HTTPS)
• Trivial File Transfer Protocol (TFTP)
• Internet Message Access Protocol (IMAP)
• Network News Transport Protocol (NNTP)
• Post Office Protocol (POP3)
• Simple Network Management Protocol (SNMP)
• Simple Mail Transfer Protocol (SMTP)
• Telnet
• STRMWORKS
• Terminal Access Controller Access-Control System (TACACS)
• Telnet (command)
• Telnet Secondar y
• Telnet SSL
• Voice (SIP)
STEP 6 (Optional) Click Configure Services to go to the Service Managem ent page to
configure the services b efore applying access rules to them.
See Configuring Services Management for more information.
STEP 7 In the Source IP field, select the users to which the firewall rule applies:
• Any—The rule applies to traffic originating on any host in the local network.
• Single Address— The rule applies to traffic originating on a single IP address
in the local network. Enter the address in the Start field.
• Address Range—The rule applies to traffic originating from an IP address
located in a range of addresses. Enter the starting IP address in the Start
field, and the ending IP address in the Finish field.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 93
Page 95

Configuring the Firewall
Creating an Internet Access Policy
STEP 8 In the Log field, specify whether the packets for this rule should be logged.
To log details for all packets that match this rule, choose Always from the dropdown menu. For example, if an outbound rule for a schedule is selected as Block
Always, for every packet that tries to make an outbound connection for that
service, a message with the packet's source address and destination address
(and other information) is recorded in the log.
Enabling logging may generate a significant volume of log messages and is
recommended for debugging purposes only.
Choose Never to disable logging.
NOTE When traffic is going from the LAN or DMZ to the WAN, the system requires
rewriting the source or destination IP address of incoming IP packets as they pass
through the firewall.
STEP 9 In the QoS Priority field, assign a priority to IP packets of this service. The priorities
are defined by QoS Level: (1 (lowest), 2, 3, 4 (highest)).
8
STEP 10 In the Rule Status field, check the box to enable the new access rule.
STEP 11 Click Save.
Creating an Internet Access Policy
The device suppor ts several options for blocking Internet access. You can block
all Internet traffic, block Internet traffic to certain PCs or endpoints, or block
access to Internet sites by specifying keywords to block. If these keywords are
found in the site's name (for example, web site URL or newsgroup name), the site is
blocked.
Adding or Editing an Internet Access Policy
To create a Internet access policy:
STEP 1 Choose Firewall > Internet Access Policy.
STEP 2 Click Add Row.
STEP 3 In the Status field, check Enable.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 94
Page 96

Configuring the Firewall
Creating an Internet Access Policy
STEP 4 Enter a policy name for identification and management purposes.
STEP 5 From the Action drop-down menu, choose the type of access restriction you need:
• Always block—Always block Internet traffic. This blocks Internet traffic to
• Always allow—Always allow Internet traffic. You can refine this to block
• Block by schedule—Blocks Internet traffic according to a schedule (for
• Allow by schedule—Allows Internet traffic according to a schedule.
8
and from all endpoints. If you want to block all traffic but allow certain
endpoints to receive Internet traffic, see Step 7.
specified endpoints from Internet traffic; see Step 7. You can also allow all
Internet traffic except for certain websites; see Step 8.
example, if you wanted t o block Internet traffic during the weekda y business
hours, but allow it after hours and on weekends).
If you chose Block by schedule or Allow by schedule, click Confi gu r e Sc hed u les
to create a schedule. See Managing Firewall Schedules.
STEP 6 Choose a schedule from the drop-down menu.
STEP 7 (Optional) Apply the access policy to specific PCs to allow or block traffic coming
from specific devices:
a. In the Apply Access Policy to the Following PCs table, click Add Row.
b. From the Type drop-down menu, choose how to identify the PC (by MAC
address, by IP address, or by providing a range of IP addresses).
c. In the Value field, depending on what you chose in the previous step, enter the
one of the following:
• MAC address (xx : xx:xx:xx:xx:xx) of the PC to which the policy applies.
• The IP address of the of the PC to which the policy applies.
• The starting and ending IP addresses of the range of addresses to block (for
example, 192.168.1.2-192.168.1.253).
STEP 8 To block traffic from specific websites:
a. In the Website Blocking table, click Add Row.
b. From the Type drop-down menu, choose how to block a website (by
specifying the URL or by specifying a keyword that appears in the URL).
c. In the Value field, enter the URL or keyword used to block the website.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 95
Page 97

Configuring the Firewall
Configuring Port Forwarding
For example, t o block the example.com URL, choose URL Address from the
drop-down menu and enter example.com in the Value field. To block a URL
that has the keyword “example” in the URL, choose Keyword from the dropdown menu and enter example in the Value field.
STEP 9 Click Save.
Configuring Port Forwarding
Port forwarding is used to redirect traffic from the Internet from one port on the
W AN t o another port on the LAN. Common services are available or you can define
a custom service and associated ports to forward.
8
The Sing le Port Forwa rding Rules and Port Range Forwarding Rules pages list
all the available port forwarding rules for this device and allow you to configure
port forwarding rules.
NOTE Port forwarding is not appropriate for servers on the LAN, because there is a
dependency on the LAN device making an outgoing connection before incoming
ports are opened.
Some applications require that they receive data on a specific port or range of
ports in order to function properly when external devices connect to them. The
router must send all incoming data f o r that application only on the required port or
range of ports.
The gateway has a list of common applications and games with corresponding
outbound and inbound ports to open. You can also specify a port forwarding rule
by defining the type of traffic (TCP or UDP) and the range of incoming and
outgoing ports to open when enabled.
Configuring Single Port Forwarding
To add a single port forwarding rule:
STEP 1 Choose Firewall > Single Port Forwarding. A preexisting list of applications is
displayed.
STEP 2 In the Application field, enter the name of the application for which to configure
port forwarding.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 96
Page 98

Configuring the Firewall
Configuring Port Forwarding
STEP 3 In the External Port field, enter the port number that triggers this rule when a
STEP 4 In the Internal Port field, enter the port number used by the remote system to
STEP 5 In the Interface drop-down menu, choose Both (Ethernet & 3G), Ethernet, or 3G.
STEP 6 From the Protocol drop-down menu, choose a protocol (TCP, UDP, or TCP &
STEP 7 In the IP Address field, enter the IP address of the host on the LAN side to which
STEP 8 In the Enable field, check the Enable box to enable the rule.
STEP 9 Click Save.
8
connection request from outgoing traffic is made.
respond to the request it receives.
UDP).
the specific IP traffic will be forwarded. For example, you can forward HTTP traffic
to port 80 of the IP address of a web server on the LAN side.
Configuring Port Range Forwarding
To add a port range forwarding rule:
STEP 1 Choose Firewall > Port R ange Forwarding .
STEP 2 In the Application field, enter the name of the application for which to configure
port forwarding.
STEP 3 In the External Port field, specify the port number that will trigger this rule when a
connection request from outgoing traffic is made.
STEP 4 In the Start field, specify the port number that begins the range of ports to
forward.
STEP 5 In the End field, specify the port number that ends the range of ports to forward.
STEP 6 In the Interface drop-down menu, choose Both (Ethernet & 3G), Ethernet, or 3G.
STEP 7 From the Protocol drop-down menu, choose a protocol (TCP, UDP, or TCP &
UDP).
STEP 8 In the IP Address field, enter the IP address of the host on the LAN side to which
the specific IP traffic will be forwarded.
STEP 9 In the Enable field, check the Enable box to enable the rule.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 97
Page 99

Configuring the Firewall
Configuring Port Forwarding
STEP 10 Click Save.
8
Configuring Port Range Triggering
Port triggering allows devices on the LAN or DMZ to request one or more ports to
be forwarded to them. Port triggering waits for an outbound request from the LAN/
DMZ on one of the defined outgoing ports, and then opens an incoming port for
that specified type of traffic.
Port triggering is a form of dynamic port forwarding while an application is
transmitting data over the opened outgoing or incoming ports. Port triggering
opens an incoming port for a specific type of traffic on a defined outgoing port.
Port triggering is more flexible than static port forwarding (available when
configuring firewall rules) because a rule does not have to reference a specific
LAN IP or IP range. Ports are also not left open when not in use, which provides a
level of security that port forwarding does not offer.
NOTE Port triggering is not appropriate for servers on the LAN, since there is a
dependency on the LAN device making an outgoing connection before incoming
ports are opened.
Some applications require that, when external devices connect to them, they
receive data on a specific port or range of ports in order to function properly. The
router must send all incoming data f o r that application only on the required port or
range of ports. The gateway has a list of common applications and games with
corresponding outbound and inbound ports to open. You can also specify a port
triggering rule by defining the type of traffic (TCP or UDP) and the range of
incoming and outgoing ports to open when enabled.
To add a port triggering rule:
STEP 1 Choose Firewall > Port Range Triggering.
STEP 2 In the Application field, enter the name of the application for which to configure
port forwarding.
STEP 3 In the Triggered Range fields, enter the port number or range of port numbers that
will trigger this rule when a connection request from outgoing traffic is made. If the
outgoing connection uses only one port, enter the same port number in both
fields.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 98
Page 100

Configuring the Firewall
Configuring Port Forwarding
STEP 4 In the Forwarded Range fields, enter the port number or range of port numbers
STEP 5 In the Interface drop-down menu, choose Both (Ethernet & 3G), Ethernet, or 3G.
STEP 6 In the Enable field, check the Enable box to enable the rule.
STEP 7 Click Save.
8
used by the remote system to respond to the request it receives. If the incoming
connection uses only one port, then specify the same port number in both fields.
Cisco RV215W Wireless-N VPN Firewall Administration Guide 99
 Loading...
Loading...