Page 1

Administrator’s Handbook
ARRIS® Embedded Software Version 9.1.2
ARRIS® NVG595 Fiber Business Gateway
Page 2

Administrator’s Handbook
Copyright
©ARRIS Enterprises, Inc. 2013 All rights reserved. No part of this publication may be reproduced in any form or by any means or
used to make any derivative work (such as translation, transformation, or adaptation) without written permission from ARRIS
Enterprises, Inc. (“ARRIS”). ARRIS reserves the right to revise this publication and to make changes in content from time to time
without obligation on the part of ARRIS to provide notification of such revision or change.
ARRIS and the ARRIS logo are all trademarks of ARRIS Enterprises, Inc. Other trademarks and trade names may be used in this
document to refer to either the entities claiming the marks and the names of their products. ARRIS disclaims proprietary interest in
the marks and names of others.
ARRIS provides this guide without warranty of any kind, implied or expressed, including, but not limited to, the implied warranties of
merchantability and fitness for a particular purpose. ARRIS may make improvements or changes in the product(s) described in this
manual at any time.
The capabilities, system requirements, and/or compatibility with third-party products described herein are subject to change without
notice.
EXCEPT AS INDICATED IN THE APPLICABLE SYSTEM PURCHASE AGREEMENT, THE SYSTEM, DOCUMENTATION AND
SERVICES ARE PROVIDED "AS IS", AS AVAILABLE, WITHOUT WARRANTY OF ANY KIND. ARRIS GROUP, INC. (“ARRIS”)
DOES NOT WARRANT THAT THE SYSTEM WILL MEET CUSTOMER'S REQUIREMENTS, OR THAT THEIR OPERATION WILL
BE UNINTERRUPTED OR ERROR-FREE, OR THAT ANY ERRORS CAN OR WILL BE FIXED. ARRIS HEREBY DISCLAIMS ALL
OTHER WARRANTIES, EXPRESS OR IMPLIED, ORAL OR WRITTEN, WITH RESPECT TO THE SYSTEM AND SERVICES
INCLUDING, WITHOUT LIMITATION, ALL IMPLIED WARRANTIES OF TITLE, NON-INFRINGEMENT, INTEGRATION,
MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE AND ALL WARRANTIES ARISING FROM ANY COURSE
OF DEALING OR PERFORMANCE OR USAGE OF TRADE.
EXCEPT AS INDICATED IN THE APPLICABLE SYSTEM PURCHASE AGREEMENT, ARRIS SHALL NOT BE LIABLE
CONCERNING THE SYSTEM OR SUBJECT MATTER OF THIS DOCUMENTATION, REGARDLESS OF THE FORM OF ANY
CLAIM OR ACTION (WHETHER IN CONTRACT, NEGLIGENCE, STRICT LIABILITY OR OTHERWISE), FOR ANY (A) MATTER
BEYOND ITS REASONABLE CONTROL, (B) LOSS OR INACCURACY OF DATA, LOSS OR INTERRUPTION OF USE, OR
COST OF PROCURING SUBSTITUTE TECHNOLOGY, GOODS OR SERVICES, (C) INDIRECT, PUNITIVE, INCIDENTAL,
RELIANCE, SPECIAL, EXEMPLARY OR CONSEQUENTIAL DAMAGES INCLUDING, BUT NOT LIMITED TO, LOSS OF
BUSINESS, REVENUES, PROFITS OR GOODWILL, OR (D) DIRECT DAMAGES, IN THE AGGREGATE, IN EXCESS OF THE
FEES PAID TO IT HEREUNDER FOR THE SYSTEM OR SERVICE GIVING RISE TO SUCH DAMAGES DURING THE 12MONTH PERIOD PRIOR TO THE DATE THE CAUSE OF ACTION AROSE, EVEN IF COMPANY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES. THESE LIMITATIONS ARE INDEPENDENT FROM ALL OTHER PROVISIONS OF THIS
AGREEMENT AND SHALL APPLY NOTWITHSTANDING THE FAILURE OF ANY REMEDY PROVIDED HEREIN.
All ARRIS products are furnished under a license agreement included with the product. If you are unable to locate a copy of the
license agreement, please contact ARRIS
Part number: 592050-002-00
Revision: 9.1.2
Page 3

Table of Contents
Table of Contents
CHAPTER 1 - Introduction. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
About ARRIS® Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Documentation Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
eneral . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
G
Internal Web Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Command Line Interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Organization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
A Word About Example Screens . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
CHAPTER 2 - Device Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Important Safety Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
POWER SUPPLY INSTALLATION. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
TELECOMMUNICATION INSTALLATION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
PRODUCT VENTILATION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
ARRIS® Gateway Status Indicator Lights . . . . . . . . . . . . . . . . . . . . . . . 13
Set up the ARRIS Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Microsoft Windows: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Macintosh MacOS 8 or higher or Mac OS X: . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Attaching a Fiber Optic Module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Accessing the Web Management Interface . . . . . . . . . . . . . . . . . . . . 20
IP Diagnostics Page Redirect. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Offline Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Device Status page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
vice Access Code . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
De
Tab Bar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Links Bar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Device List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
System Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Access Code . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Remote Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Restart Device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Broadband . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Configure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Fiber Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Local Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Configure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Wi-Fi . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Wi-Fi Security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
MAC Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Wi-Fi Scan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Subnets & DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Page 4

Administrator’s Handbook
IP Allocation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Voice . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Line Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Call Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
Packet Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
Working with Packet Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
NAT/Gaming . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Custom Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Public Subnet Hosts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
P Passthrough . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
I
Firewall Advanced . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .80
Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Update . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Resets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Syslog . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Event Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
NAT Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
CHAPTER 3 - Basic Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Status Indicator Lights . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .92
LED Function Summary Matrix. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
Factory Reset Switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .98
Log Event Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .99
CHAPTER 4 - Command Line Interface . . . . . . . . . . . . . . . . . . . . . . . . . 103
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .105
Starting and Ending a CLI Session . . . . . . . . . . . . . . . . . . . . . . . . . . . .107
ogging In. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
L
Ending a CLI Session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Using the CLI Help Facility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .108
About SHELL Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .108
SHELL Prompt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
SHELL Command Shortcuts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
SHELL Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Common Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
WAN Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
About CONFIG Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
CONFIG Mode Prompt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Navigating the CONFIG Hierarchy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Entering Commands in CONFIG Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Guidelines: CONFIG Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Displaying Current Gateway Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Step Mode: A CLI Configuration Technique. . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Page 5

Table of Contents
Validating Your Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
CONFIG Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Connection commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Filterset commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Global Filterset (“IPv6 Firewall”) commands . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Queue commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
IP Gateway commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
IPv6 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
IP DNS commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
IP IGMP commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
NTP commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Application Layer Gateway (ALG) commands . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Dynamic DNS Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
Link commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .144
Management commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
Remote access commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Physical interfaces commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
PPPoE relay commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
NAT Pinhole commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
Security Stateful Packet Inspection (SPI) commands . . . . . . . . . . . . . . . . . . . . 155
VoIP commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Targeted Ad Insertion commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
System commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
Debug Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
claimer & Warning Text . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
Dis
Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
CLI CShell Commands (debug mode) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
CHAPTER 5 - Technical Specifications and Safety Information. . . . . . 175
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
ower Supply . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .175
P
Environment. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Software and protocols. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Agency approvals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
Manufacturer’s Declaration of Conformance . . . . . . . . . . . . . . . . . . 177
Important Safety Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
47 CFR Part 68 Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
FCC Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
FCC Statements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .180
RF Exposure Statement: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
Electrical Safety Advisory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
Caring for the Environment by Recycling . . . . . . . . . . . . . . . . . . . . . 182
Beskyttelse af miljøet med genbrug . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
Umweltschutz durch Recycling. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
Cuidar el medio ambiente mediante el reciclaje . . . . . . . . . . . . . . . . . . . . . . . 182
Recyclage pour le respect de l'environnement . . . . . . . . . . . . . . . . . . . . . . . . . 182
Milieubewust recycleren. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
Dba³oÊç o Êrodowisko - recykling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
Page 6

Administrator’s Handbook
Cuidando do meio ambiente através da reciclagem . . . . . . . . . . . . . . . . . . . . 183
Var rädd om miljön genom återvinning. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
Copyright Acknowledgments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .185
Open Source Software Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
Appendix A - ARRIS® Gateway Captive Portal Implementation . . . . . 209
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .210
Captive Portal RPC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 211
_00D09E_GetCaptivePortalParams RPC:. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 211
X
X_00D09E_SetCaptivePortalParams RPC: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 212
Appendix B - Quality of Service (QoS) Examples . . . . . . . . . . . . . . . . . 213
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .214
Downstream QoS: Ethernet Switch . . . . . . . . . . . . . . . . . . . . . . . . . .216
Downstream QoS: Egress queues . . . . . . . . . . . . . . . . . . . . . . . . . . . .217
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 219
Page 7
CHAPTER 1 Introduction
About ARRIS® Documentation
NOTE::
ARRIS provides a suite of technical information for its family of intelligent enterprise and consumer Gateways.
I
t consists of:
Administrator’s Handbook
Dedicated User Manuals
Specific White Papers
This guide describes the wide variety of features and functionality of the ARRIS® Gateway, when used in
Router mode. The ARRIS® Gateway may also be delivered in Bridge mode. In Bridge mode, the Gateway acts
as a pass-through device and allows the workstations on your LAN to have public addresses directly on the
Internet.
The documents are available in electronic form as Portable Document Format (PDF) files. They are viewed (and
printed) from Adobe Acrobat Reader, Exchange, or any other application that supports PDF files.
They are downloadable from the ARRIS website:
http://www.arrisi.com/consumer
7
Page 8

Administrator’s Handbook
Documentation Conventions
General
This manual uses the following conventions to present information:
Convention (Typeface) Description
ans serif
bold s
u
underlined sans serif Web GUI page links
nderlined sans serif
derlined sans serif underlined sans serif
un
terminal
bold terminal
Italic Italic type indicates the complete titles of manuals.
Internal Web Interface
Convention (Graphics) Description
Menu commands and button names
Computer display text
User-entered text
Denotes an “excerpt” from a Web page or the visual truncation of a
Web page
Denotes an area of emphasis on a Web page
C
ommand Line Interface
Syntax conventions for the ARRIS® Gateway command line interface are as follows:
Convention Description
straight ([ ]) brackets in cmd line Optional command arguments
curly ({ }) brackets, with values sepa-
rated with vertical bars (|).
bold terminal type face
italic terminal type face
Alternative values for an argument are presented in curly ({ }) brackets, with values separated with vertical bars (|).
User-entered text
Variables for which you supply your own values
8
Page 9

Organization
This guide consists of five chapters, two appendices, and an index. It is organized as follows:
Chapter 1, “Introduction” — Describes the ARRIS
structure of this guide. It gives a table of conventions.
Chapter 2, “Device Configuration” — Describes how to get up and running with your ARRIS® Gateway.
Chapter 3, “Basic Troubleshooting” — Gives some simple suggestions for troubleshooting problems with
your Gateway’s initial configuration.
Chapter 4, “Command Line Interface” — Describes all the current text-based commands for both the
HELL and CONFIG modes. A summary table and individual command examples for each mode is provided.
S
Chapter 5, “Technical Specifications and Safety Information” — Presents system and device specifica-
tions and important compliance and safety statements.
Appendix A ARRIS® Gateway Captive Portal Implementation — Describes the ARRIS® Gateway Captive
Portal Implementation
Appendix B Quality of Service (QoS) Examples — Describes the ARRIS® Gateway Quality of Service (QoS)
Implementation
®
document suite, the purpose of, the audience for, and
A Word About Example Screens
This manual contains many example screen illustrations. Since ARRIS® Gateways offer a wide variety of features
and functionality, the example screens shown may not appear exactly the same for your particular Gateway or
setup as they appear in this manual. The example screens are for illustrative and explanatory purposes, and
should not be construed to represent your own unique environment.
9
Page 10

Administrator’s Handbook
10
Page 11

CHAPTER 2 Device Configuration
Most users will find that the basic Quick Start configuration insert that is shipped with the device is all that
t
hey ever need to use. For more advanced users, this section provides a a rich set of features that can be used
for more in-depth configuration. The following topics cover installation in Router Mode.
This chapter covers:
“Important Safety Instructions” on page 12
“ARRIS® Gateway Status Indicator Lights” on page 13
“Set up the ARRIS Gateway” on page 16
“Accessing the Web Management Interface” on page 20
“Device Status page” on page 22
“Tab Bar” on page 24
“Broadband” on page 32
“Local Network” on page 37
“Wi-Fi” on page 41
“Voice” on page 52
“Firewall” on page 58
“Diagnostics” on page 80
11
Page 12

Administrator’s Handbook
Important Safety Instructions
POWER SUPPLY INSTALLATION
Connect the power supply cord to the power jack on the ARRIS
priate electrical outlet. There is no power (on / off) switch to power off the device.
®
Gateway. Plug the power supply into an appro-
CAUTION:
Depending on the power supply provided with the product, either the direct plug-in power supply blades,
power supply cord plug or the appliance coupler serves as the mains power disconnect. It is important that
the direct plug-in power supply, socket-outlet or appliance coupler be located so it is readily accessible.
TELECOMMUNICATION INSTALLATION
When using your telephone equipment, basic safety precautions should always be followed to reduce the risk
f fire, electric shock and injury to persons, including the following:
o
Do not use this product near water, for example, near a bathtub, wash bowl, kitchen sink or laundry tub, in a
wet basement or near a swimming pool.
Avoid using a telephone (other than a cordless type) during an electrical storm. There may be a remote risk
of electrical shock from lightning.
Do not use the telephone to report a gas leak in the vicinity of the leak.
CAUTION: The external phone should be UL Listed and the connections should be made in accordance with
Article 800 of the NEC.
PRODUCT VENTILATION
The ARRIS® Gateway is intended for use in a business. Ambient temperatures around this product should not
exceed 104 F (40 C). It should not be used in locaƟons exposed to outside heat radiaƟon or trapping of its
own heat. When properly installed the product should have at least one inch of clearance on all sides except
the bottom and should not be placed inside tightly enclosed spaces unless proper ventilation is provided.
SAVE THESE INSTRUCTIONS
12
Page 13
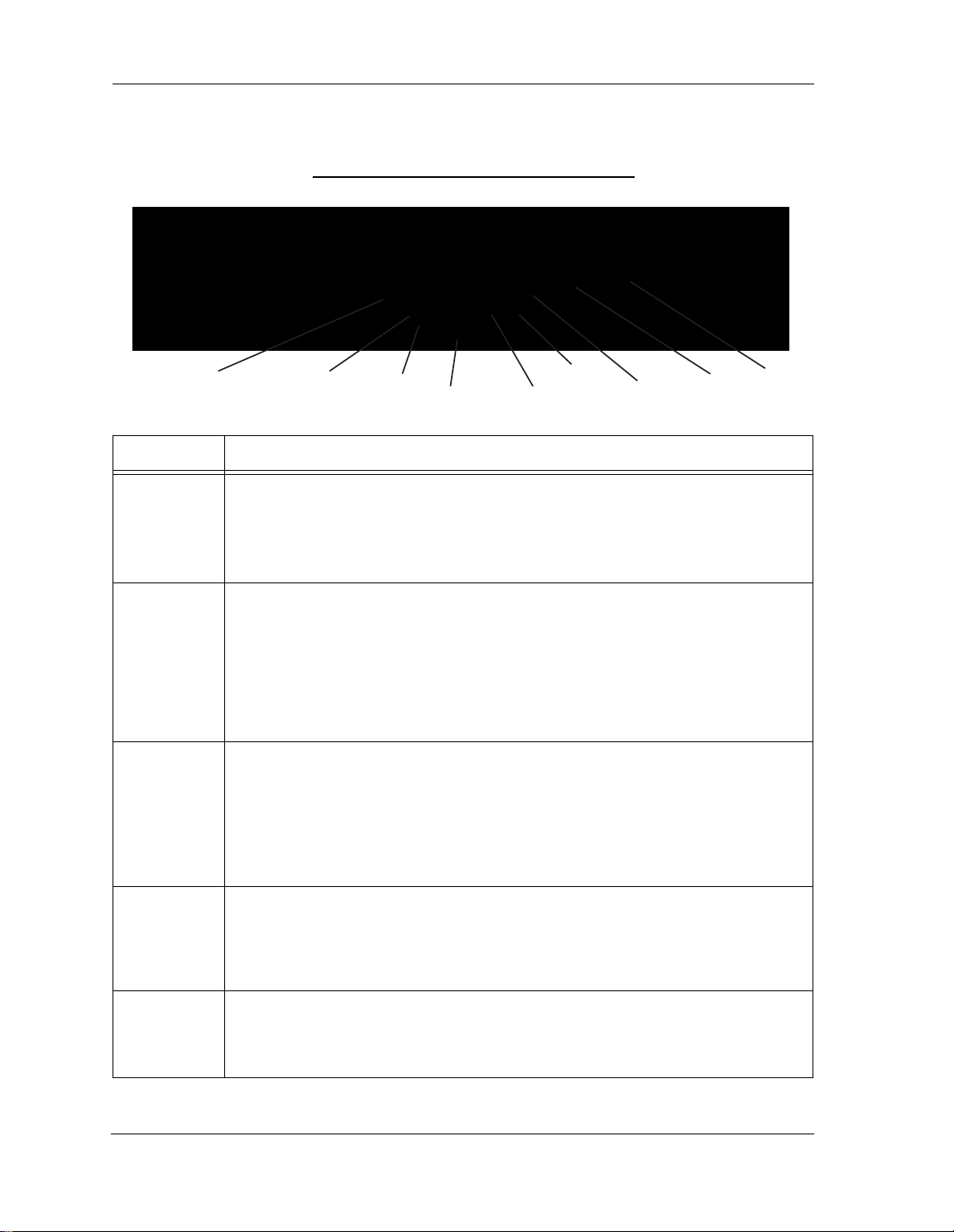
ARRIS® Gateway Status Indicator Lights
Side View
0OWER
%THERNET
7I&I
"ROABAND
%THERNET
"ROADBAND
&IBER
3ERVICE
0HONE
0HONE
703
0OWER
%THERNET
7I&I
"ROABAND
%THERNET
"ROADBAND
&IBER
3ERVICE
0HONE
0HONE
703
Colored LEDs on your ARRIS
LED Action
Solid Green = The device is powered.
Flashing Green = A Power-On Self-Test (POST) is in progress
Power*
*During
Firmware
Upgrade
During Boot
rocess
p
Flashing Red = A POST failure (not bootable) or device malfunction occurred.
Orange/Amber = during firmware upgrade (see below)
Off = The unit has no AC power.
During the software installation, you will lose internet and phone service. The LEDs will function as
follows:
1. As firmware is being loaded into flash, the LEDs will operate normally as described.
2. The installation will take a few minutes –
During this phase, the Power LED will flash Orange/Amber during firmware upgrade
(flash writing to memory) and all other LEDs will be off.
3. The Gateway will restart automatically.
As the device reboots, the POWER ON LED behavior will happen.
• Power LED = GREEN/FLASH
• All other LED = OFF
If the device does not boot, and fails its self test or fails to perform initial load of the bootloader:
• Power LED = RED/FLASH
• ALL other LED = OFF
If the device boots and then detects a failure:
Power LED = GREEN/FLASH starting POST and then all LEDs will FLASH RED, including Power LED.
®
Gateway indicate the status of various port activity.
ARRIS® Gateway NVG595 status indicator lights
Ethernet
Wi-Fi
Solid Green = Powered device connected to the associated port (includes devices with wake-on-LAN
capability where a slight voltage is supplied to the Ethernet connection).
Flickering Green = Activity seen from devices associated with the port. The flickering of the light is
synchronized to actual data traffic.
Off = The device is not powered, no cable or no powered devices connected to the associated ports.
Solid Green = Wi-Fi is powered.
Flickering Green = Activity seen from devices connected via Wi-Fi. The flickering of the light is syn-
chronized to actual data traffic.
Off = The device is not powered or no powered devices connected to the associated ports.
13
Page 14
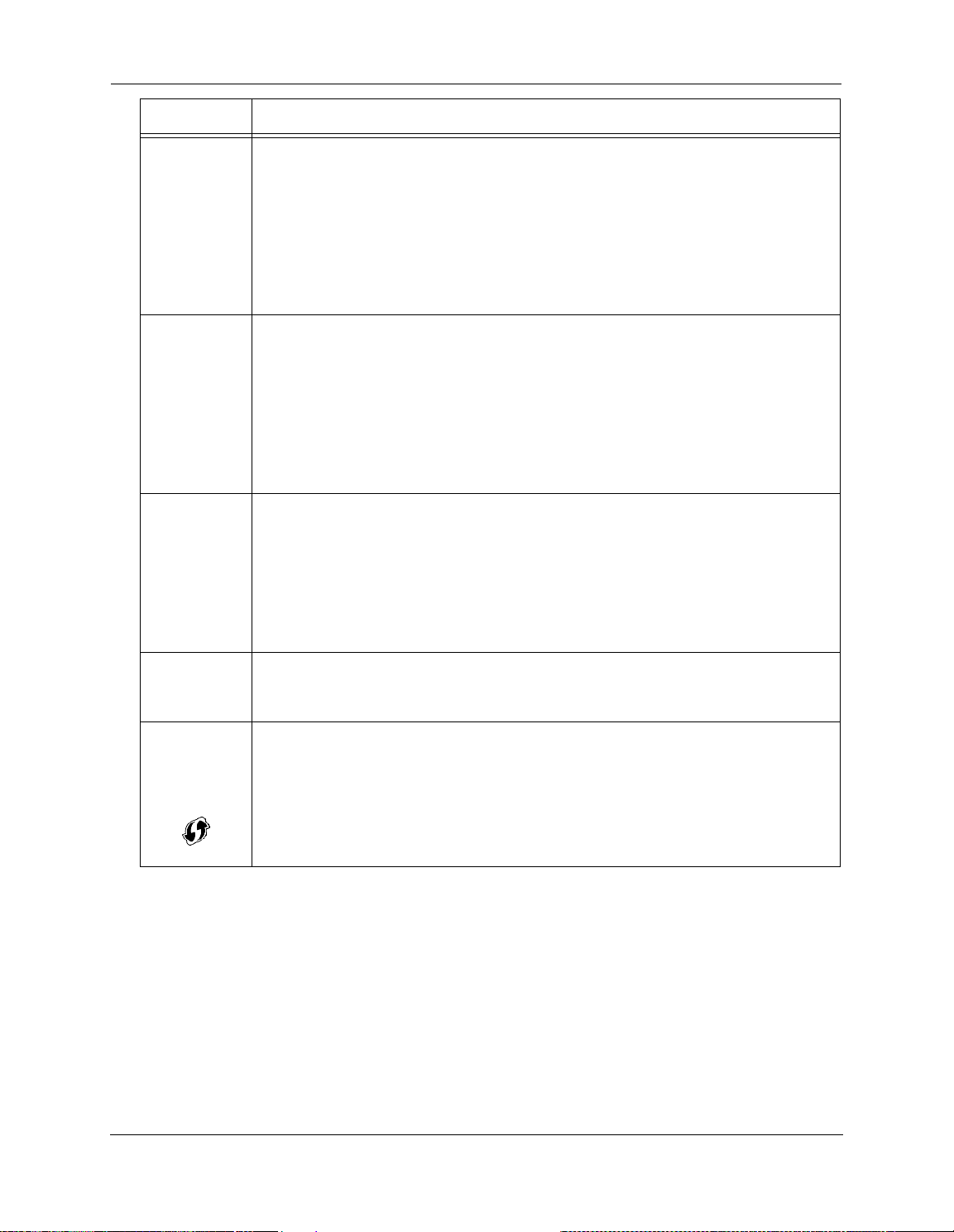
Administrator’s Handbook
LED A
Solid Green = Good broadband connection.
Flashing Green & Red = If the broadband connection fails to be established for more than three
consecutive minutes the LED switches to Flashing Green when attempting or waiting to establish
Broadband
Eth
ernet
Broadband
Fiber
Service
a broadband connection alternating with a five second steady Red. This pattern continues until the
broadband connection is successfully established.
Flashing Red = No signal on the line. This is only used when ther
ing sequence.
Off = The device is not powered.
Solid Green = Good broadband connection.
Flashing Green & Red = If the broadband connection fails to be established for more than three
consecutive minutes the LED switches to Flashing Green when attempting or waiting to establish
a broadband connection alternating with a five second steady Red. This pattern continues until the
broadband connection is successfully established.
Flashing Red = No signal on the line. This is only used when there is no signal, not during the train-
ing sequence.
Off = The device is not powered.
Solid Green = IP connected (The device has a WAN IP address from DHCP or 802.1x authentication
and the broadband connection is up)
Flashing Green = Attempting connection, attempting IEEE 802.1X authentication or attempting to
obtain DHCP information.
Red = Device attempted to become IP connected and failed (no DHCP response, 802.1x authentica-
tion failed, no IP address from IPCP, etc.). The Red state times out after two minutes and the Service
indicator light returns to the Off state.
Off = The device is not powered or the broadband connection is not present.
ction
e is no signal, not during the train-
Phone 1, 2
WPS
(opens after
using WPS
button)
Solid Green
Flashing Green = Indicates a telephone is off-hook on the associated VoIP line.
Off = VoIP not in use, line not registered or Gateway power off.
Solid Green = Wi-Fi Protected Setup has been completed successfully. It should stay on for 5 minutes
or until push button is pressed again.
Flashing Green = for 2 mins. Indicates when WPS is broadcasting.
Flashing Red = for 2 min, when there is a Session overlap detected (possible security risk) in scenario.
Solid Red = Error unrelated to security, such as failed to find any partner, or WPS is disabled. It should
stay Solid Red for 5 min or until push button is pressed again.
Off = The device is not powered, no cable or no powered devices connected to the associated ports.
= The associated VoIP line has been registered with a SIP proxy server.
14
Page 15

ARRIS® Gateway NVG595 Rear View
LED Action
Orange/Amber when a Gigabit Ethernet device is connected to each port.
Ethernet
1, 2, 3, 4
Green when 10/100 Ethernet device is connected.
Flash for Ethernet traffic passing.
Off = The device is not powered, or no powered devices connected to the associated ports.
NOTE:
The NVG595 supports two VoIP lines over one RJ14 VoIP port. In order to con-
nect two phone lines the supplied inner/outer pair splitter adapters must be
attached to the RJ14 VoIP port in order to terminate both lines. This is a special-purpose splitter. You must only use the inner/outer pair splitter adapters
supplied by AT&T.
15
Page 16
Administrator’s Handbook
Set up the ARRIS Gateway
Refer to your Quickstart Guide for instructions on how to connect your ARRIS
PC or local area network, and your Internet access point, whether it is a Fiber connection or a Gigabit Ethernet
connection . Different ARRIS® Gateway models are supplied for any of these connections. If Dynamic Addressing is not enabled on your PC, perform the following.
®
gateway to your power source,
Microsoft Windows:
1. Navigate to the TCP/IP Properties Control Panel.
ome Windows versions follow a path like this:
S
Start menu -> Settings -> Control Panel -> Network (or Network
and Dial-up Connections -> Local Area Connection -> Properties)
-> TCP/IP [your_network_card] or Internet Protocol [TCP/IP] ->
Properties
Some Windows versions follow a path like this:
Start menu -> Control Panel -> Network and Internet Connections -> Network Connections -> Local Area Connection
-> Properties -> Internet Protocol [TCP/IP] -> Properties
2. Select Obtain an IP address automatically.
3. Select Obtain DNS server address automatically, if available.
4. Remove any previously configured Gateways, if available.
5. OK the settings. Restart if prompted.
Windows Vista and Windows 7 obtain an IP address automatically by default. You may not need to configure it
at all.
16
Page 17

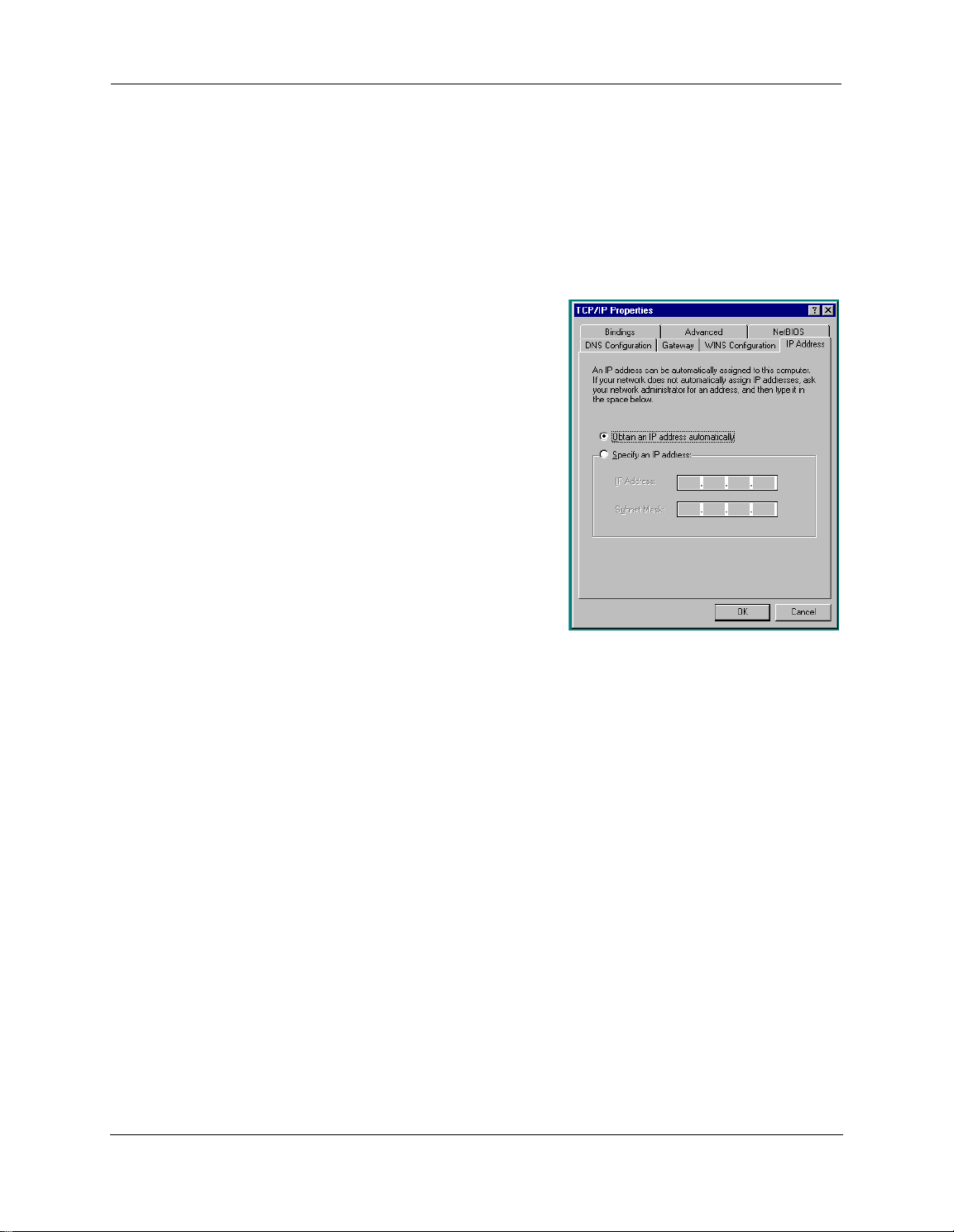
To check;
1
. Open the Networking Control Panel and select Internet Protocol Version 4 (TCP/IPv4).
2. Click the Properties button. The Internet Protocol Version 4 (TCP/IPv4) Properties window should appear
as shown.
3. Set the radio buttons to the values shown above, and click the OK button.
17
Page 18
Administrator’s Handbook
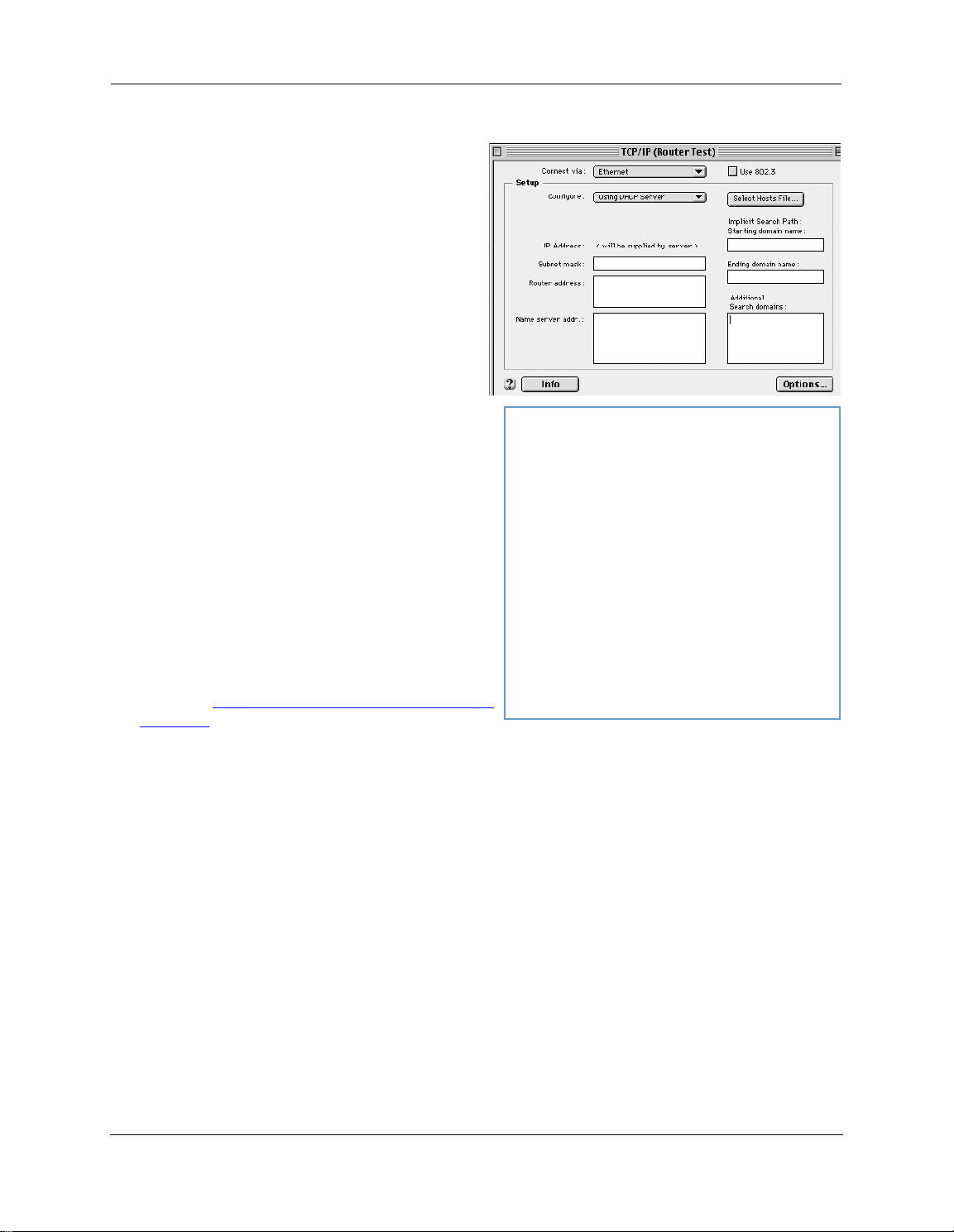
Macintosh MacOS 8 or higher or Mac OS X:
1. Access the TCP/IP or Network control panel.
M
acOS follows a path like this:
Apple Menu -> Control Panels -> TCP/IP Control
Panel
Mac OS X follows a path like this:
ple Menu -> System Preferences -> Network
Ap
2. Select Built-in Ethernet
3. Select Configure Using DHCP
4. Close and Save, if prompted.
Proceed to “
on page 20.
Accessing the Web Management Interface”
18
Page 19

Attaching a Fiber Optic Module
The following procedure details how to attach an SFP SX/LX connector to the NVG595 and attach the fiber
o
ptic cable to the Optic module.
WARNING!
1. Insert the SFP SX/LX fiber optic module into the Fiber port on the rear of the NVG595. Push it in firmly until
it clicks. The label on the module should be facing upward when the module is inserted. Failure to ensure
this could cause damage to the module.
Laser output can cause serious eye damage. The lasers used in this device produce
ight that is invisible to the naked eye. Assume at all times that the fiber optic cables
l
and optical ports are radiating light energy. When connecting or handling the fiber
cables or connectors, it is imperative that no one looks into the tip of the fiber.
2. Remove the rubber protective cap from the end of the SFP SX/LX fiber optic module.
3. Remove the protective plastic caps from the end of the fiber cable and insert the fiber cable into the SFP SX/
LX fiber optic module. Push firmly until the latch on the end of the connector locks over the fiber cable.
19
Page 20
Administrator’s Handbook
Accessing the Web Management Interface
1. Run your Web browser application, such as Firefox or Microsoft Internet Explorer, from the computer conn
ected to the ARRIS® Gateway.
2. Enter http://192.168.7.254 in the Location text box. Once the network type is determined, The Device Status
Page opens.
3. Check to make sure the Broadband and Service LEDs are lit GREEN to verify that the connection to the
nternet is active.
I
IP Diagnostics Page Redirect
In the event that your connection to the Internet fails, the Broadband LED will flash RED and you will be redi-
ected to the IP Diagnostics page.
r
Follow the on-screen troubleshooting suggestions.
20
Page 21

For additional troubleshooting information, see “
page 91.
When your connection is restored or the problem is resolved, the Broadband LED will turn GREEN.
NOTE:
F
or AT&T this function is enabled by default. See the CLI command “set management lan-redirect
Offline Troubleshooting
If the WAN is down, the following information is displayed at the top of the page:
enable [ off | on ]” on page 150
Diagnostics” on page 80 and “Basic Troubleshooting” on
21
Page 22
Administrator’s Handbook
Device Status page
After you have performed the basic Easy Login configuration, any time you log in to your ARRIS
will access the ARRIS® Gateway Home Page.
You access the Home Page by typing http://192.168.7.254 in your web browser’s location box.
Device Access Code
You may be required to provide your Device Access Code in order to access the web management configura-
ion pages. The Device Access Code is unique to your device. It is printed on a label on the bottom of the
t
Gateway.
®
Gateway you
Enter your Device Access Code and click the Continue
The Device Status Page opens.
22
Continue button.
ontinueContinue
C
Page 23
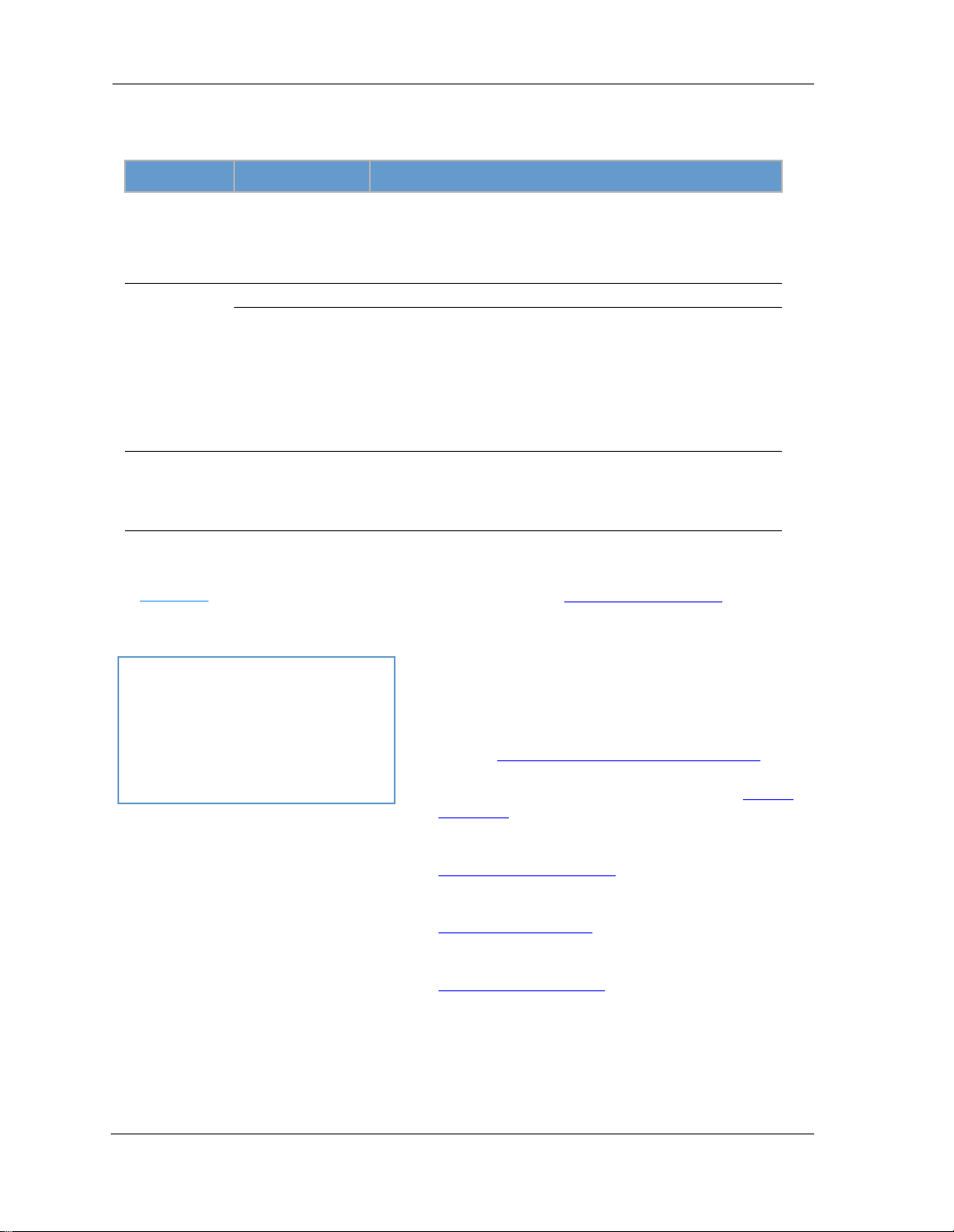
DeviceStatusWindow
T
he Device Status displays the following information in the center section:
(icon) Field Description
(Broadband)
(Wi-Fi)
(Voice)
roadband
B
Connection
Status Your Wi-Fi signal may be ‘On’ or ‘Off’.
Band Indicates the current band the Wi-Fi is in, either 2.4 Ghz or 5.0 Ghz.
Network ID (SSID) This is the name or ID that is displayed to a client scan. The default
Authentication Type The type of Wi-Fi encryption security in use. May be Disabled, WPA
Password Wi-Fi network encryption key in use.
Line 1 Indication of VoIP or other phone connection.
Line 2 Indication of VoIP or other phone connection.
‘Waiting for ’ is displayed while the Gateway is training. This should
change to ‘Up’ within two minutes.
‘Up’ is displayed when the session is established.
‘Down’ indicates inability to establish a connection; possible line failure.
SSID for the Gateway is attxxx where xxx is the last 3 digits of the
serial number located on the side of the Gateway.
or WEP, Default Key or Manual.
Some fields may or may not display, depending on your particular setup.
Diagnostics button will connect you to the Troubleshoot page. See “Diagnostics” on page 80.
The Diagnostics
iagnosticsDiagnostics
D
The right-hand frame displays some links to commonly performed tasks for easy access.
Display additional troubleshooting steps - OR -
o to AT&T online support for troubleshooting and
G
repair »
This link will connect you to the IP Diagnostics page with
help for troubleshooting and the AT&T Help Desk information. See “IP Diagnostics Page Redirect” on page 20.
Modify your Wi-Fi security or settings »
This link will connect you to the Wi-Fi page. See “Wi-Fi”
on page 41.
Restart your device »
This link will connect you to the Restart Device page. See
“Restart Device” on page 31.
Find a computer on your Local Network »
This link will connect you to the Device List page. See
“Device List” on page 25.
Adjust firewall settings for gaming and applications »
This link will connect you to the NAT/Gaming page. See
“NAT/Gaming” on page 69.
23
Page 24
Administrator’s Handbook
Tab Bar
The tab bar is located at the top of every page, allowing you to move freely about the site.
T
he tabs reveal a succession of pages that allow you to manage or configure several features of your Gateway.
Each tab is described in its own section.
Help
Help is provided in your Gateway. Help is available in the right hand frame on every page in the Web interface.
f the Show Help button is displayed, click it to open the Help. If the Hide Help button is displayed click it to
I
close the Help window.
Here is an example:
The page shown here is displayed when you are on the System Informa-
tion page.
Links Bar
The links bar at the top of each page allows you to configure different aspects of the features displayed on the
age. For example, on the Home Summary page, the button bar is shown below:
p
Click the links below to be taken to each section.
“Device Status page” on page 22
“Device List” on page 25
“System Information” on page 27
“Access Code” on page 28
“Remote Access” on page 29
“Restart Device” on page 31
24
Page 25
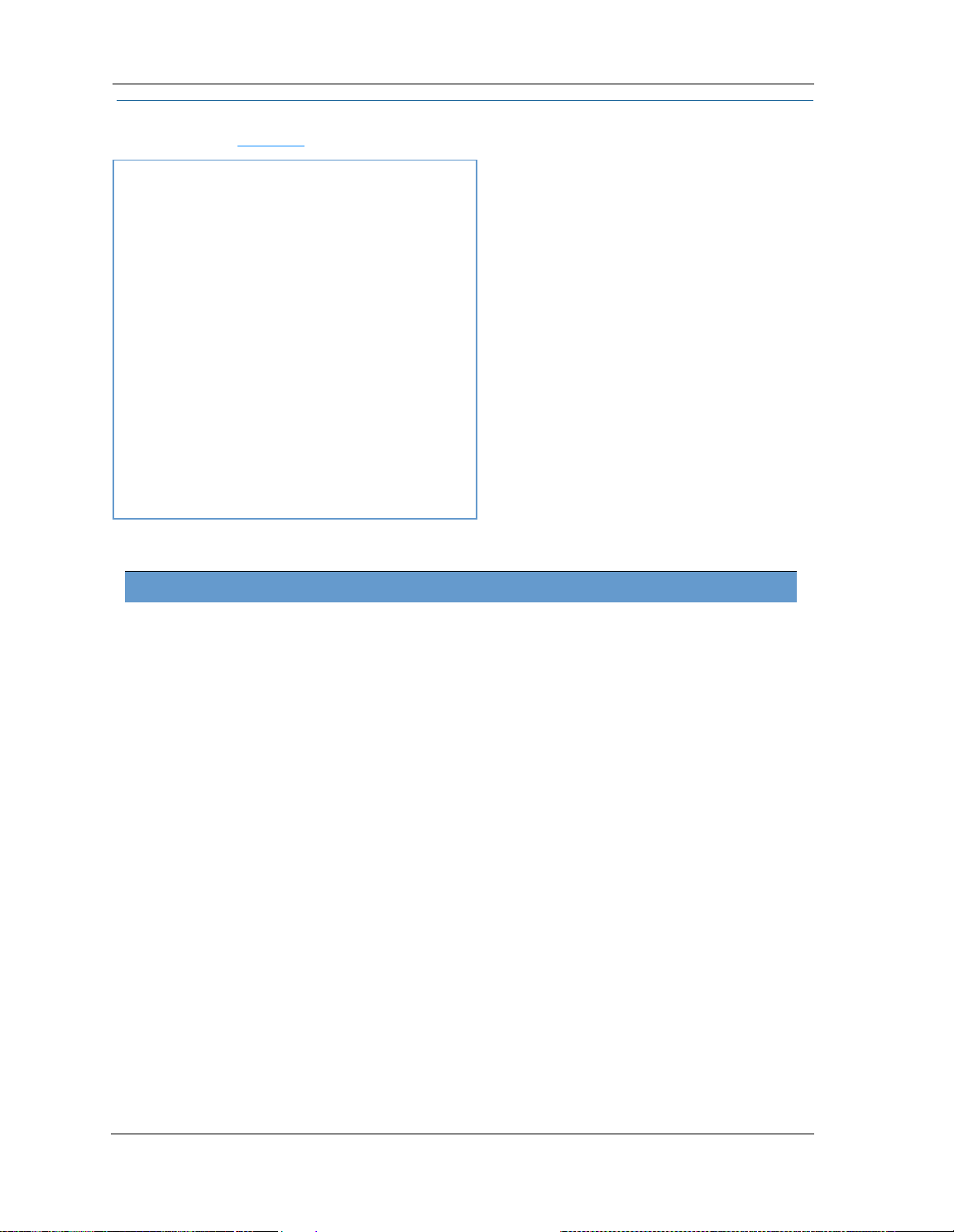
Link: Device List
When you click the Device List
This view displays the following information:
Local Network Devices Displays the IPv4 Address, Network Name, and MAC Address of devices con-
MAC Address Client device’s unique hardware address.
IPv4 Address / Name Client device’s IP address or device network name.
Last Activity Date and time of last traffic for this client device
Status May be off or on.
Allocation Type of IP address assignment, for example, Static or DHCP.
Connection Type Type of connection, for example, Ethernet or Wi-Fi
Device List link, the Device List page opens.
Device List Device List
Local Network Devices
nected to this device on your local area network.
25
Page 26
Administrator’s Handbook
For Wi-Fi client connections, the Device List displays the familiar bars indicating signal strength, as follows:
C
Click the Scan for Devices
Clear Device List button to update the Local Network summary.
lick the Clear Device List
lear Device ListClear Device List
C
Scan for Devices button to seek out other devices that have been connected since the last Local Net-
Scan for DevicesScan for Devices
work summary update.
26
Page 27
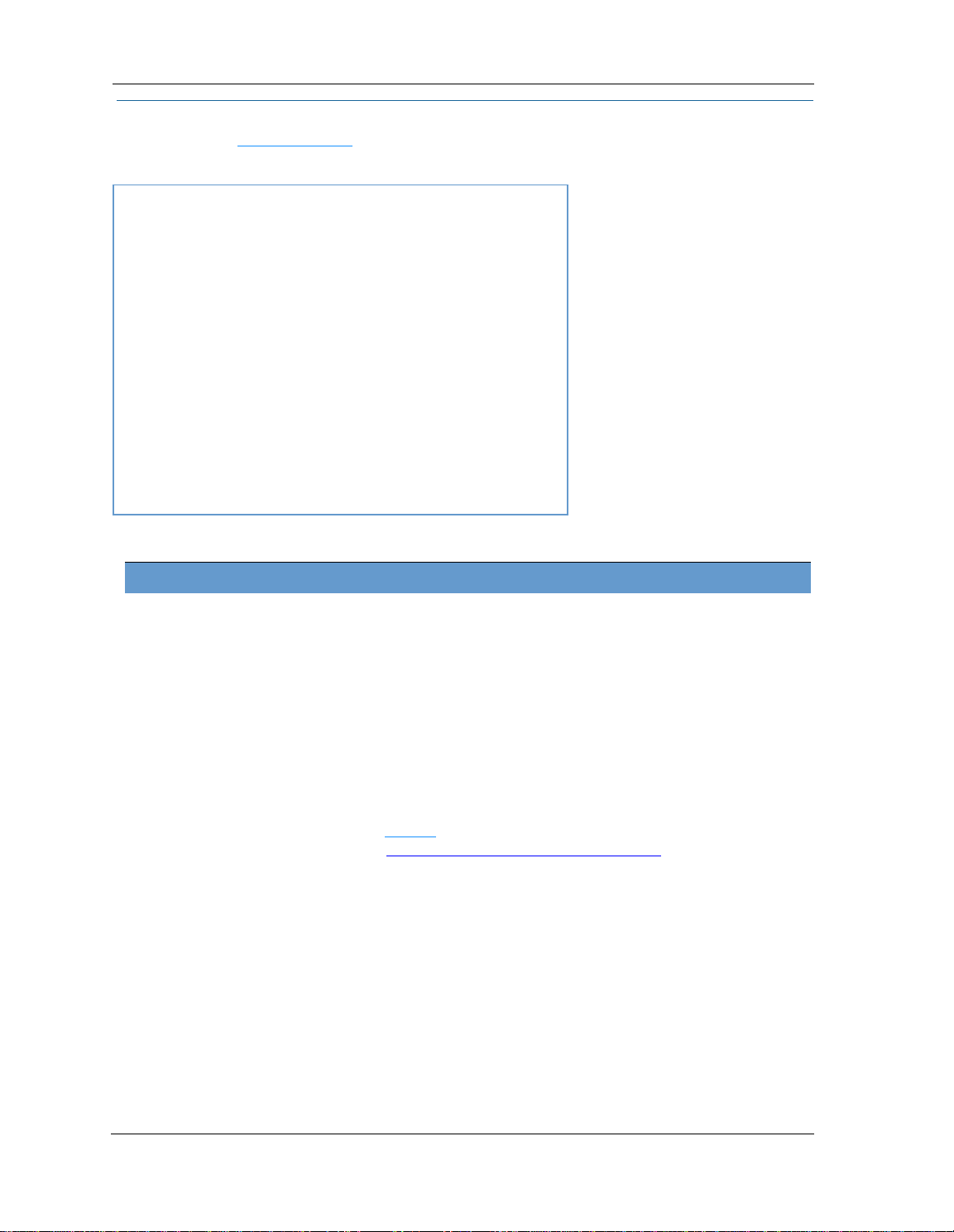
Link: System Information
When you click the System Information
This view displays the following information:
Manufacturer This is the manufacturer’s identifier name.
Model Number This is the manufacturer’s model number.
Serial Number This is the unique serial number of your Gateway.
Software Version This is the version number of the current embedded software in your Gateway.
MAC Address Unique hardware address of this Gateway unit.
First Use Date Date and Time when the Gateway is first used. This field changes to the current date
Time Since Last Reboot Elapsed time since last reboot of the Gateway in days:hr:min:sec.
Current Date/Time Current system date and time in days:hr:min:sec.
Datapump Version Underlying operating system software datapump version
Legal Disclaimer Clicking the Licenses
System Information link, the System Information page opens.
System InformationSystem Information
System Information
and time after a reset to factory defaults.
Licenses link displays a listing of software copyright attributions also
ensesLicenses
Lic
shown here:“Copyright Acknowledgments” on page 186.
27
Page 28
Administrator’s Handbook
Link: Access Code
Access to your Gateway is controlled through an account named admin. The default Admin password for your
Gateway is the unique Access Code printed on the label on the side or bottom of your Gateway.
As the Admin, you can change this password to a different one of your own choosing between 8 and 20 characters long. The new password must also include two characters from any these categories: alpha, number, and
special characters.
Example: “fru1tfl13s_likeabanana”
ter your Old Access Code, your New Access Code, and click the Use New Access Code
En
Use New Access Code button. The new Access
se New Access CodeUse New Access Code
U
Code takes effect immediately.
You can always return to the original default password by clicking the Use Default Access Code
Use Default Access Code button.
Use Default Access CodeUse Default Access Code
28
Page 29

Link: Remote Access
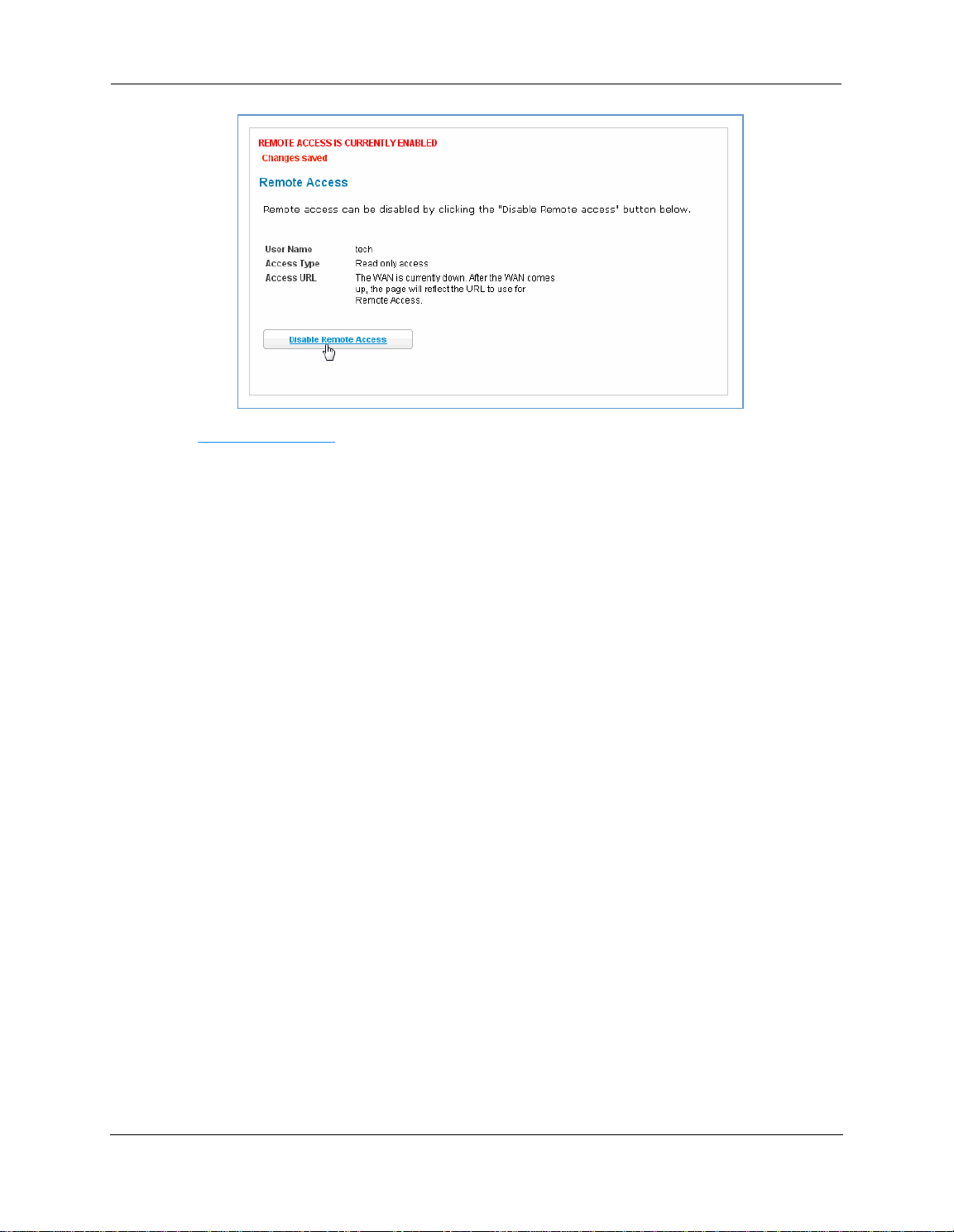
The Remote Access page lets you grant access to your NVG595 Gateway to other users on the WAN. This function can be used for advanced troubleshooting or remote configuration.
WARNING
E
If Remote access is not currently enabled, the Remote Access page will let you configure and enable it. If
remote access has been enabled, the Remote Access Page will indicate that, and provides a button to disable
it.
nabling remote access allows anyone who knows or can determine the password, port ID, and URL
(address) of your NVG595 Gateway to view any configuration settings or change the operation of your gateway.
To enable Remote Access:
1. Enter a password. This password must be at least 8 characters long, and must include at least two of the following types of characters:
alphabetic (letter) characters,
numeric (number) characters,
special characters (! @ # $ % ^ & * , etc)
If necessary, set a custom port number for secure HTTP access to the NVG595 remote access session in the
2.
Port Value field.
3. Click the Access Type radio button to select the desired level of access:
Read only access - to allow the remote access session to view, but not change, the configuration and col-
lected statistics of the gateway.
Update access - to allow the session to make changes to the gateway’s configuration.
4. Click Enable Remote Access
The NVG595 updates the Remote Access page and displays the current remote access settings, shows the URL
that a remote access client must use to connect to the remote access session, and provides a button for ending
the remote access session. The remote access client will need to connect to the URL shown on the Remote
Access page, and will need to log in with the username “tech” and the password configured when access was
enabled.
Enable Remote Access.
Enable Remote AccessEnable Remote Access
29
Page 30
Administrator’s Handbook
To end (disable) an existing remote access configuration:
C
lick the Disable Remote Access
Disable Remote Access button under the Access URL.
isable Remote AccessDisable Remote Access
D
30
Page 31

Link: Restart Device
When the Gateway is restarted, it will disconnect all users, initialize all its interfaces, and load the Operating
System Software.
In some cases, when you make configuration changes, you may be required restart for the changes to take
effect.
31
Page 32

Administrator’s Handbook
Broadband
When you click the Broadband
Broadband tab, the Broadband Status page opens.
B
roadbandBroadband
The Broadband Status page displays information about the Gateway’s Ethernet WAN connection(s) to the
nternet.
I
Broadband Status
Broadband Connection
Source
Broadband Connection May be Up (connected) or Down (disconnected).
Broadband IPv4 Address The public IP address of your device, whether dynamically or statically assigned.
Gateway IPv4 Address Your ISP's gateway router IP address.
MAC Address Your Gateway’s unique hardware address identifier.
Primary DNS The IP Address of the Primary Domain Name Server.
Secondary DNS The IP Address of the backup Domain Name Server, if available.
Primary DNS Name The name of the Primary Domain Name Server.
Secondary DNS Name The name of the backup Domain Name Server, if available.
MTU Maximum Transmittable Unit before packets are broken into multiple packets.
The communications technology providing the ARRIS® Gateway broadband uplink.
Ethernet Statistics (Ethernet WAN)
Line State Up or Down
32
Page 33

Current Speed L
Current Duplex Full- or Half-duplex
Receive Packets Number of packets received
Transmit Packets Number of packets sent
Receive Bytes Number of bytes received
Transmit Bytes Number of bytes sent
Receive Unicast Receive Unicast statistics
Transmit Unicast Transmit Unicast statistics
Receive Multicast Receive Multicast statistics
Transmit Multicast Transmit Multicast statistics
Receive Drops Received packets dropped
Transmit Drops Sent packets dropped
Receive Errors Count of received errored packets that were fixed successfully without a retry.
Transmit Errors Number of times data packets have had to be resent due to errors in transmission.
Collisions Count of packet collisions.
ine speed
IPv6
Status May be Enabled or Unavailable.
Global Unicast IPv6 Address The public IPv6 address of your device, whether dynamically or statically assigned.
Border Relay IPv4 Address The public IPv4 address of your device.
IPv4 Statistics
Transmit Packets IPv4 packets transmitted.
Transmit Errors Errors on IPv4 packets transmitted.
Transmit Discards IPv4 packets dropped.
IPv6 Statistics
Transmit Packets IPv6 packets transmitted.
Transmit Errors Errors on IPv6 packets transmitted.
Transmit Discards IPv6 packets dropped.
33
Page 34

Administrator’s Handbook
Link: Configure
When you click the Configure
of broadband connection should it change in the future.
Broadband Source Override - Auto (automatically detected), Fiber, or Ethernet.
Configure link, the Broadband Configure screen opens. Here you can reconfigure your type
ConfigureConfigure
Maximum allowable MTU - The WAN connection is automatically configured. However, you can adjust the
aximum Transmittable Unit value, if your service provider suggests it. The default 1500 is the maximum
M
value, but some services require other values. 1492 is common.
If you make any change here, click the Save
Save button.
SaveSave
34
Page 35

Link: Fiber Status
When you click the Fiber Status
Fiber Status link, the Fiber Status screen opens.
Fiber StatusFiber Status
The Fiber Status view povides information about the devices Fiber Ethernet WAN connection.
Fiber Status
Optical WAN Operational
Status
Fiber Module The type of connector detected by the device.
Length SMF-km Supported link length in kilometers.
Length SMF Supported link length in units of 100 meters.
Length 50uM Supported link length for 50 micrometer OM2 fiber (units of 10 meters).
Length 62dot5uM Supported link length for 62.5 micrometer OM1 fiber (units of 10 meters).
Length OM3 Supported link length for 50 micrometer OM3 fiber (units of 10 meters).
Vendor Name SFP vendor’s name.
Vendor OUI IEEE company id for the SFP vendor.
Vendor PN SFP module’s vendor part number.
Vendor Rev SFP module’s revision level for the part number.
Vendor SN SFP module’s serial number from the vendor.
Vendor Date Code In format <yymmddxx> where “xx” is vendor specific and may be blank
OPT Cooled Trans Whether the transceiver is cooled or uncolled.
OPT Powerlvl Power level operation of either 1 or 2.
OPT Linear Rcvr Indicates if the Receiver is a conventional or Linear receiver.
When connected to a fiber source, displays whether or not the WAN is operational.
35
Page 36

Administrator’s Handbook
OPT Rate Select I
OPT Tx Disable Ability to disable the serial output 1 = implemented, 0 = not implemented.
OPT Tx Fault TX_FAULT is implemented, 1 = implemented, 0 = not implemented.
OPT Inverted LOS Also known as signal detect, 1 = implemented, 0 = not implemented.
OPT LOS Loss of signal. 1 = implemented, 0 = not implemented.
DMC Type Legacy Reserved. Always 0
DMC Type Implemented Diag monitoring, 1 = implemented, 0 = not implemented.
DMC Type Internal Cal The device is internally calibrated.
DMC Type External Cal The device is externally calibrated.
DMC Type Rx Avg Pwr The type of power measurement. Either Modulation Amplitude method or Average
EOC Alarm implemented 1 = implemented, 0 = not implemented.
EOC Soft Tx Disable TX_DISABLE control and monitoring, 1 = implemented, 0 = not implemented.
EOC Soft Tx Fault TX_FAULT monitoring, 1 = implemented, 0 = not implemented.
EOC Soft Rx LOS RX_LOS monitoring, 1 = implemented, 0 = not implemented.
EOC Soft Rate Select Soft Rate_Select control and monitoring, 1 = implemented, 0 = not implemented.
SFF 8079 App Select Application select implemented from the standard SFF 8079, 1 = implemented, 0 = not
SFF 8431 Rate Select Rate select implemented from standard 8431, 1 = implemented, 0 = not imple-
SFF Ver Compliance Reference 3.12 table in SFF 8742. Rev 9.3 or rev 9.5.
ndicates whether Rate Select is implemented. 1 = implemented, 0 = not imple-
mented.
power method.
implemented.
mented..
36
Page 37

Local Network
When you click the Local Network
Local Network tab, the Local Network Status page opens.
L
ocal NetworkLocal Network
The Local Network Status page displays information about the Gateway’s local area network.
f you click the Run Congestion Detection
I
Run Congestion Detection button, the device will generate statistics for each of the 11 channels
Run Congestion DetectionRun Congestion Detection
available, displaying:
Channel number
AP (Access Point) Count
Congestion Score (1 - 10) - note that higher values m
ean lower congestion.
The Wi-Fi congestion feature provides simple data to the user to show the level of network congestion in each
Wi-Fi channel. This data can be used to determine router placement or to determine which channels to avoid.
The display currently tells the user how many Access Points (APs) are active within each channel, and provides
a score of 1 - 10 to indicate how clear the channel is. A higher score indicates less congestion in a channel, so a
channel with a 10 indicates a channel extremely clear of Wi-Fi traffic and noise. Alternatively, a score of 1 indicates more severe congestion in a channel.
You can clear the current statistics information by clicking the Clear Statistics
Clear Statistics button. This view provides the fol-
Clear StatisticsClear Statistics
lowing information.
37
Page 38

Administrator’s Handbook
Local Network Status
Device IPv4 Address The Gateway’s own IP address on the network.
DHCP Netmask The Gateway’s own netmask on the network.
DHCPv4 Start Address The starting IP address of the DHCP range served by the Gateway.
DHCPv4 End Address The ending IP address of the DHCP range served by the Gateway.
DHCP Leases Available The number of IP addresses of the DHCP range available to be served by the Gateway.
DHCP Leases Allocated The number of IP addresses of the DHCP range currently being served by the Gateway.
DHCP Primary Pool Source pool of the IP addresses served by the Gateway, Public or Private.
IPv6
Status May be Enabled or Unavailable.
Global IPv6 Address The public IPv6 address of your device, whether dynamically or statically assigned.
Link-local IPv6 Address The private IPv6 address of your device, whether dynamically or statically assigned.
Router Advertisement Prefix The IPv6 prefix to include in router advertisements.
IPv6 Delegated LAN Prefix The IPv6 network address prefix that identifies the gateway network.
IPv4 Statistics
Transmit Packets IPv4 packets transmitted.
Transmit Errors Errors on IPv4 packets transmitted.
Transmit Discards IPv4 packets dropped.
IPv6 Statistics
Transmit Packets IPv6 packets transmitted.
Transmit Errors Errors on IPv6 packets transmitted.
Transmit Discards IPv6 packets dropped.
Wi-Fi Status
Wi-Fi Radio Status Indicates whether the Wi-Fi radio is Enabled or Disabled.
Network Name (SSID) This is the name or ID that is displayed to a client scan. The default SSID for the Gate-
way is attxxx where xxx is the last 3 digits of the serial number located on the side of
the Gateway.
Hide Network Name SSID May be either On or Off. If On, your SSID will not appear in a client scan.
Bamd The currently selected Wi-Fi band, either 2.4 Ghz or 5.0 Ghz
Wi-Fi Security The type of Wi-Fi encryption security in use. May be Disabled, WPA or WEP, Default
Key or Manual.
Password The Wi-Fi password if security is WEP or WPA.
Mode The Wi-Fi standard in operation on this device..
Bandwidth The capacity of the Wi-Fi LAN to carry traffic in megahertz.
Current Radio Channel The radio channel that your Wi-Fi network is broadcasting on.
Radio Channel Selection May be set to automatic or manually selected. Automatic indicates that the device
selects the best channel for its environment. Fixed indicates that the user has specified the desired channel.
MAC Address Filtering On indicates that the device is inspecting MAC addresses before connecting Wi-Fi cli-
ents.
Power Level May be adjusted up to 100%, lower if multiple Wi-Fi access points are in use, and
might interfere with each other.
38
Page 39

Wi-Fi MAC Address Shows the information of the MAC address of the Wi-Fi subsystem.
Wi-Fi Network Statistics
Transmit Bytes Number of bytes transmitted on the Wi-Fi network.
Receive Bytes Number of bytes received on the Wi-Fi network.
Transmit Packets Number of packets transmitted on the Wi-Fi network.
Receive Packets Number of packets received on the Wi-Fi network.
Transmit Error Packets This is the number of errors on packets transmitted on the Wi-Fi network.
Receive Error Packets This is the number of errors on packets received on the Wi-Fi network.
Transmit Discard Packets This is the number of packets transmitted on the Wi-Fi network that were dropped.
Receive Discard Packets This is the number of packets received on the Wi-Fi network that were dropped.
LAN Ethernet Statistics
State up or down
Transmit Speed This is the maximum speed of which the port is capable.
Transmit Packets This is the number of packets sent out from the port.
Transmit Bytes This is the number of bytes sent out from the port.
Transmit Dropped This is the number of packets sent out from the port that were dropped.
Transmit Errors This is the number of errors on packets sent out from the port.
Receive Packets This is the number of packets received on the port.
Receive Bytes This is the number of bytes received on the port.
Receive Unicast This is the number of unicast packets received on the port.
Receive Multicast This is the number of multicast packets received on the port.
Receive Dropped This is the number of packets received on the port that were dropped.
Receive Errors This is the number of errors on packets received on the port.
The links at the top of the Local Network page access a series of pages to allow you to configure and monitor
f
eatures of your device. The following sections give brief descriptions of these pages.
“Configure” on page 40
“Wi-Fi” on page 41
“MAC Filtering” on page 46
“Wi-Fi Scan” on page 47
“Subnets & DHCP” on page 48
“IP Allocation” on page 50
39
Page 40

Administrator’s Handbook
Link: Configure
When you click the Configure
For each Ethernet Port, 1 through 4, you can select:
Ethernet – Auto (the default self-sensing rate), 10M full- or half-duplex, 100M full- or half-duplex, or 1G full-
r half-duplex.
o
MDI-X – Auto (the default self-sensing crossover setting), off, or on.
Configure link, the Configure page for the Ethernet LAN opens.
ConfigureConfigure
Click the Save
Save button.
SaveSave
40
Page 41

Link: Wi-Fi
When you click the Wi-Fi
ments.
Wi-Fi link the Wi-Fi page opens. The Wi-Fi page displays the status of your Wi-Fi LAN ele-
Wi-FiWi-Fi
The Wi-Fi page’s center section contains a summary of the Wi-Fi Access Point’s configuration settings and
operational status.
Summary Information
Field Status and/or Description
General Information
Wi-Fi Operation May be either On or Off.
Network Name (SSID) This is the name or ID that is displayed to a client scan. The default SSID for the Gateway
is attxxx where xxx is the last 3 digits of the serial number located on the side of the
gateway.
Hide Network Name SSID May be either Off or On. If On, your SSID will not appear in a client scan.
Band Choose between 2.4 and 5.0 Ghz. If 5.0 is chosen, all devices connecting to this device
must support 802.11n.
Security The type of Wi-Fi encryption security in use. May be OFF-No Privacy, WPA-PSK or
WEP, Default Key or Manual.
WPA Version If WPA is selected, may be Both, WPA-1, or WPA-2,.
WEP Password Length May be 10 characters for 40/64-bit, or 26 characters for 128-bit WP encryption.
41
Page 42

Administrator’s Handbook
Network Password H
Mode Will be 802.11B only, 802.11G only, 802.11N only, 802.11 B/G or 802.11 B/G/N. These
Bandwidth The capacity of the Wi-Fi LAN to carry traffic in Megahertz, 20 or 40.
Channel The radio channel that your Wi-Fi network is broadcasting on. This should be left at the
Power Level May be adjusted up to 100%, lower if multiple Wi-Fi access points are in use, and might
Wi-Fi Protected Setup (WPS) May be either On or Off.
T
he Wi-Fi Operation function is automatically enabled by default. If you uncheck the checkbox, the Wi-Fi
Options are disabled, and the Wi-Fi Access Point will not provide or broadcast its Wi-Fi LAN services.
Network Name (SSID) – preset to a number unique to your unit. You can either leave it as is, or change it by
entering a freeform name of up to 32 characters, for example “Hercule’s Wi-Fi LAN”. On client PCs’ software,
this might also be called the Network Name. The Wi-Fi ID is used to identify this particular Wi-Fi LAN.
Depending on their operating system or client Wi-Fi card, users must either:
• select from a list of available Wi-Fi LANs that appear in a scanned list on their client
• or enter this name on their clients in order to join this Wi-Fi LAN.
Hide Network Name SSID – If enabled, this mode hides the Wi-Fi network from the scanning features of
Wi-Fi client computers. Hiding the SSID prevents casual detection of your Wi-Fi network by unwanted neighbors and passers-by. The gateway WLAN will not appear when clients scan for access points. If Hide SSID is
enabled, you must remember and enter your SSID when adding clients to the Wi-Fi LAN.
NOTE:
hile hiding the SSID may prevent casual discovery of your Wi-Fi network, enabling security is the only true
Security, WPA Version, WEP Password Length, Password – see “Wi-Fi Security” on page 44.
Mode – The pull-down menu allows you to select and lock the Gateway into the Wi-Fi transmission mode
you want: B/G/N, B-only, B/G, G-only, or N-only.
For compatibility with clients using 802.11b (up to 11 Mbps transmission), 802.11g (up to 20+ Mbps),
802.11a (up to 54 Mbit/s using the 5 GHz band), or 802.11n (from 54 Mbit/s to 600 Mbit/s with the use of
four spatial streams at a channel width of 40 MHz), select B/G/N. To limit your Wi-Fi LAN to one mode or the
ther, select G-only, N-only, or B-only, or some combination that applies to your setup.
o
W
method of securing your network.
ere you can enter a manual encryption key.
will vary depending on the Band selected.
default Automatic.
interfere with each other.
NOTE:
f you choose to limit the operating mode to 802.11b or 802.11g only, clients using the mode you excluded
Bandwidth – use a single 20MHz channel (20MHz setting) , or combine two 20MHz channels (40MHz set-
ting) to increase data speeds. The 40MHz mode may only be selected if the Mode setting is 801.11 B/G/N or
802.11 N-Only. To prevent interference with lower bandwidth clients, the Wi-Fi network will revert to
20MHz operation if non-compatible (802.11B, 802.11G, or 20MHz 802.11N) clients are detected.
Channel (1 through 11, for North America) on which the network will broadcast. This is a frequency range
within the 2.4Ghz band. The Automatic setting allows the Wi-Fi Access Point to determine the best channel
to broadcast automatically.
Power Level – Sets the Wi-Fi transmit power, scaling down the Wi-Fi Access Point’s Wi-Fi transmit coverage
by lowering its radio power output. Default is 100% power. Transmit power settings are useful in large venues with multiple Wi-Fi routers where you want to reuse channels. Since there are only three non-overlapping channels in the 802.11 spectrum, it helps to size the Wi-Fi Access Point’s cell to match the location. This
allows you to install a router to cover a small “hole” without conflicting with other routers nearby.
Wi-Fi Protected Setup (WPS) is a not a security protocol. It is an easier way to add and securely configure-
new clients to your WLAN.
By default, Privacy is set to Wi-Fi Protected Access (WPA-PSK) with a 12 character security key. WPS allows
you to securely share your exact security configuration with a new client that you are adding to the WLAN,
without needing to look up and type this security key. Clients may be added using the WPS button on the
router, or by entering the client WPS PIN on this page.
I
will not be able to connect.
42
Page 43

Not all client Wi-Fi devices support WPS. Refer to their documentation.
E
nter your WPS PIN and click the Submit
Follow the instructions that came with your Wi-Fi client.
Submit button.
SubmitSubmit
43
Page 44

Administrator’s Handbook
Wi-Fi Security
By default, Wi-Fi Security is set to W
Pre-Shared Key).
Other options are available from the Security pull-down menu:
WEP - Manual: WEP Security is a Privacy option that is based on encryption between the Router and any PCs
“clients”) you have with Wi-Fi cards. For this encryption to work, both your Wi-Fi Access Point and each cli-
(
ent must share the same Wi-Fi ID (SSID), and both must be using the same encryption keys. See “WEP-Man-
ual” on page 45.
PA-PSK with a pre-defined WPA-Default Key (Wi-Fi Protected Access
NOTE:
W
WPA-PSK: allows you to enter your own key, the most secure option for your Wi-Fi network. The key can be
etween 8 and 63 characters, but for best security it should be at least 20 characters.
b
If you select WPA-PSK as your privacy setting, the WPA Version pull-down menu allows you to select the
WPA version(s) that will be required for client connections. Choices are:
Both, for maximum interoperability,
WPA-1, for backward compatibility,
WPA-2, for maximum security.
All clients must support the version(s) selected in order to successfully connect.
Be sure that your Wi-Fi client adapter supports this option. Not all Wi-Fi clients support WPA-PSK.
OFF - No Privacy: This mode disables privacy on your network, allowing any Wi-Fi users to connect to your
Wi-Fi LAN. Use this option if you are using alternative security measures such as VPN tunnels, or if your network is for public use.
Click the Save
EP is a less current and less secure authentication method than WPA-PSK. It may be required if your Wi-Fi
clients do not support WPA.
Save button.
SaveSave
44
Page 45

WEP-Manual
Y
ou can provide a level of data security by enabling WEP (Wired Equivalent Privacy) for encryption of network
data. You can enable 40- or 128-bit WEP Encryption (depending on the capability of your client Wi-Fi card) for
IP traffic on your LAN.
WEP - Manual allows you to enter your own encryption keys manually. This is a difficult process, but only
needs to be done once. Avoid the temptation to enter all the same characters.
Password Length: The pull-down menu selects the length of each encryption key. The longer the key, the
tronger the encryption and the more difficult it is to break the encryption.
s
Password: You enter a key using hexadecimal digits. For 40/64-bit encryption, you need ten digits; 26 digits for
128-bit WEP. Hexadecimal characters are 0 – 9, and a – f.
Examples:
40 bits: 02468ACE02
128 bits: 0123456789ABCDEF0123456789
Any WEP-enabled client must have an identical key of the same length as the Router, in order to successfully
receive and decrypt the traffic. Similarly, the client also has a ‘default’ key that it uses to encrypt its transmissions. In order for the Router to receive the client’s data, it must likewise have the identical key of the same
length.
Click the Save
Save button.
SaveSave
45
Page 46

Administrator’s Handbook
Link: MAC Filtering
When you click the MAC Filtering
MAC Filtering allows you to specify which client PCs are allowed to join the Wi-Fi LAN by unique hardware
(MAC) address.
To enable this feature, select Blacklist or Whitelist from the MAC ing Type menu. Blacklist means that
nly MAC addresses you specify will be denied access; Whitelist means that only MAC addresses you specify
o
will be allowed access.
You add Wi-Fi clients that you want to Whitelist or Blacklist for your Wi-Fi LAN by selecting them from the
List of MACs or by entering the MAC addresses in the Manual Entry field provided.
Click the Add
MAC Filtering link the MAC Filtering page opens.
MAC FilteringMAC Filtering
Add button.
ddAdd
A
Your entries will be added to a list of clients that will be either authorized (Whitelisted) or disallowed (Blacklisted) depending on your selection.
Click the Save
Save button.
SaveSave
You can Add or Delete any of your entries later by returning to this page.
46
Page 47

Link: Wi-Fi Scan
Your device automatically checks for the best channel to broadcast Wi-Fi services. However, in some cases it
may be useful to switch to a different channel on which the network will broadcast.
Channel selection depends on government regulated radio frequencies that vary from region to region. Channel selection can have a significant impact on performance, depending on other Wi-Fi activity close to this
device. You need not select a channel at any of the computers on your Wi-Fi network, they will automatically
scan available channels seeking a Wi-Fi device broadcasting on the SSID for which they are configured.
This scan will disconnect any Wi-Fi client devices from the Wi-Fi network.
If you want to scan for a different channel on which the device will broadcast, click the Continue
Continue button.
ontinueContinue
C
47
Page 48

Administrator’s Handbook
Link: Subnets & DHCP
When you click the Subnets & DHCP
Subnets & DHCP link, the Subnets & DHCP page opens.
Subnets & DHCPSubnets & DHCP
The Server configuration determines the functionality of your DHCP Settings. This functionality enables the
Gateway to assign a single IP address of 192.168.7.64 through 192.168.7.253 to the LAN.
Private LAN Subnet
Private LAN Subnet
rivate LAN SubnetPrivate LAN Subnet
P
Device IPv4 Address: The IP address of your Gateway as seen from the LAN
Subnet Mask: Subnet mask of your LAN
DHCP Server
DHCP Server
DHCP ServerDHCP Server
DHCP Server Enable: If you have a dedicated source of DHCP assigned addresses on your LAN, choose off
from the pull-down menu. By default the NVG595 will act as a DHCP server and should be set to On.
DHCPv4 Start Address: First IP address in the range being served to your LAN by the Gateway's DHCP
server
DHCPv4 End Address: Last IP address in the range being served to your LAN by the Gateway's DHCP server
DHCP Lease: Specifies the default length for DHCP leases issued by the Router. Enter lease time in
dd:hh:mm:ss (days/hours/minutes/seconds) format.
48
Page 49

Public Subnet
Public Subnet
P
ublic SubnetPublic Subnet
Public Subnet Enable: If you select On from the pull-down menu, you can enable a second subnet to dis-
tribute public addresses to DHCP clients; this means that IP addresses assigned to LAN clients will be public
addresses
Public IPv4 Address: The IP address of your Gateway as seen from the WAN
Public Subnet Mask: Public subnet mask
DHCPv4 Start Address: First IP address in the range being served from a DHCP public pool.
DHCPv4 End Address: Last IP address in the range being served from a DHCP public pool.
Primary DHCP Pool: Choose the source of the DHCP pool IP address assignment by selecting either the Pri-
ate (local to your LAN) or Public (assigned remotely) radio button.
v
Cascaded Router
Cascaded Router
Cascaded RouterCascaded Router
Cascaded Router Enable: If you have another router behind this Gateway, choose On from the pull-down
menu.
Cascaded Router Address: If you chose On from the pull-down menu, enter the IP address of the router
you are using behind this Gateway in the LAN Private IP subnet range.
Network Address: If you chose On from the pull-down menu, enter the Network Address that defines the
range of IP addresses available to clients of the router you are using behind this Gateway.
Subnet Mask: If you chose On from the pull-down menu, enter the subnet mask for the Network Address
that defines the range of IP addresses available to clients of the router you are using behind this Gateway
If you make any changes here, click the Save
Save button, and if prompted, restart the Gateway.
SaveSave
49
Page 50

Administrator’s Handbook
Link: IP Allocation
When you click the IP Allocation
IP Allocation link, the IP allocation page opens.
IP AllocationIP Allocation
NOTE:
I
The IP Allocation page lets you set aside or assign IP addresses to client devices on your network. With IP allocation, you can configure known devices to either use DHCP for dynamic IP address assignment, or set aside a
specific IP address for a client device.When IP allocation is enabled for a client, that device is assigned a predetermined IP address by the DHCP server of the NVG595. IP allocation lets you set up client devices as common DHCP systems, but ensures that they always receive the same IP address from the gateway.
The IP Allocation table shows a list of all identified and active client devices the NVG595 is serving.
To change the allocation method used by a client;
1. Locate the client in the IP Allocation table. The client may be identified by the Name value (in the IPv4
Address/Name column) or the device MAC address.
2. Click the Allocate
P Allocation functions require you to enter your NVG595 Gateway’s access code. Information on the device
code is provided in “Device Access Code” on page 22
Allocate button associated with the client entry.
llocateAllocate
A
50
Page 51

The IP Allocation window for the client opens.
3
. Scroll through the New Allocation values and select the address or method to use for the client’s DHCP
assignment:
Click “Address from DHCP Pool” to set the client to
ation).
Click any of the private fixed IP addresses (192.168.7.64 to 192.168.7.253) shown in the list to allocate that
IP address to the selected client.
4. Click the Save button to save the IP allocation settings. A red “Changes saved” message opens at the top of
the IP Allocation page.
accept any valid DHCP address available (standard oper-
51
Page 52

Administrator’s Handbook
Voice
If you click the Voice
Voice-over-IP (VoIP) refers to the ability to make voice telephone calls over the Internet. This differs from traditional phone calls that use the Public Switched Telephone Network (PSTN). VoIP calls use an Internet protocol,
Session Initiation Protocol (SIP), to transmit sound over a network or the Internet in the form of data packets.
The Voice page displays information about your VoIP p
phones, Line 1 and Line 2.
If either one or both are registered with a SIP server by your service provider or not registered, the Voice
page will display their Registration Details.
ink, the Voice Status page opens.
hone lines, if configured. Your Gateway supports two
The links at the top of the Voice page access a series of pages to allow you to configure and monitor features of
your device. The following sections give brief descriptions of these pages.
“Line Details” on page 53
“Call Statistics” on page 54
52
Page 53

Link: Line Details
When you click the Line Details
Line Details link, the Line Details page opens.
Line DetailsLine Details
If your service provider has enabled your VoIP phone
Line 1
Line 1 or Register Line 2
Line 1Line 1
To test if the lines are enabled, click the Ring Line 1
Register Line 2 button(s).
Register Line 2Register Line 2
Ring Line 1 or Ring Line 2
Ring Line 1 Ring Line 1
respective phone will ring for 30 seconds.
To update the display, click the Refresh
Refresh button.
RefreshRefresh
lines, you can register them by clicking the Register
Ring Line 2 button(s). If enabled and registered, the
Ring Line 2Ring Line 2
Register
Register Register
53
Page 54

Administrator’s Handbook
Link: Call Statistics
When you click Call Statistics
Call Statistics, the Call Statistics page opens.
Call StatisticsCall Statistics
54
Page 55

For Line 1 and Line 2:, the two available phone lines, the Call Statistics page displays the following informat
ion:
Call Statistics - Line 1 and Line 2
Last Call/Cumulative – Incoming/Outgoing
RTP Packet Loss Real-time Transport Protocol packets dropped
RTP Packet Loss percentage Percent of Real-time Transport Protocol packets dropped
Total RTCP Packets Total Real-time Transport Control Protocol packets
Average Inter Arrival Jitter This is calculated continuously in milliseconds as each data packet is received and
averaged.
Max Inter Arrival Jitter This is the maximum value in milliseconds recorded as each data packet is received.
Sum of Inter Arrival Jitter This is calculated continuously in milliseconds as each data packet is received and
totalled.
Sum of Inter Arrival Jitter
Squared
Sum of Franc Loss Fraction Lost: The fraction of RTP data packets lost since the previous SR or RR packet
Sum of Franc Loss Squared Fraction lost is squared with every RTCP SR or RR packet. Sum of all this will give the
Max One Way Delay One Way Delay will be calculated in milliseconds on every RTCP SR or RR packet. This
Sum of One Way Delay The sum of all the one way delays calculated in milliseconds on every RTCP packet is
Sum of One Way Delay
Squared
Avg Round Trip Time Average time in milliseconds from this local source to destination address and back
Max Round Trip Time Maximum amount of time in milliseconds from this local source to destination
Sum of Round Trip Time Sum of time in milliseconds from this local source to destination address and back
Sum of Round Trip Time
Squared
This is calculated continuously in milliseconds as each data packet is received and the
total is squared.
was sent. This fraction is defined to be the number of packets lost divided by the number of packets expected. This will be calculated on every RTCP SR packet. Sum of the
fraction lost is calculated with all the RTCP packets.
Sum of Franc Loss Squared.
value is (systime - lsr - r) / 2
lsr means last SR timestamp
r means delay since last SR.
displayed as Sum of One Way Delay.
One Way Delay is squared with every RTCP SR or RR packet. Sum of all this will give the
Sum of One Way Delay Squared.
again for all logged calls
address and back again for all logged calls
again for all logged calls
Sum squared of time from this local source to destination address and back again for
all logged calls
55
Page 56

Administrator’s Handbook
For Line 1 and Line 2:, the two available phone lines, the Call Summary section displays the following informat
ion:
Call Summary - Line 1 and Line 2
Current Call/Last Completed Call
Call Timestamp Da
Type May be Incoming or Outgoing
Duration Length of time in seconds of call connection
Codec in Use Audio codec used for decoding the call packet traffic.
Far-End Host Information SIP server IP information: IP address and port number
Far-End Caller Information Caller ID information, if available
te and Time of the current call
Cumulative Since Last Reset
Last Reset Timestamp Date and Time of the last call
Number of Calls Total number of calls for each VoIP line
Duration Time in seconds since the last call
Number of Incoming Calls Failed Number of Incoming calls that fail to connect
Number of Outgoing Calls Failed Number of Outgoing calls that fail to connect
56
Page 57

The following table is the simplified version of VOIP line/hook/etc. states during different conditions.
VOIP Line
1/2
Disable
Enabled
Enabled
Enabled
Enabled
T
he following table provides the state changes during the boot-up procedure.
VOIP Line
1/2
Disable
Enabled
Hook state WAN IP Reg-state
On/Off-hook UP Idle OFF N/A off
On-hook UP Registered ON N/A Solid
Off-hook UP R
On/off hook UP Failure OFF N/A off
On/off hook DOWN Idle OFF N/A off
egistered ON DIAL TONE Blink
WAN Status Hook State Reg-state
Down Off-hook Idle On-to-off off off
Down On/Off-hook Idle ON Congestion off
Up Off-hook Registered ON Congestion.
Voltage
Voltage
Enabled
FXS
FXS
Tone LED
Tone LED
ON
Dial Tone played
after the hook
state is
changed.
57
Page 58

Administrator’s Handbook
Firewall
When you click the Firewall
system firewall elements.
All computer operating systems are vulnerable to attack from outside sources, typically at the operating system or Internet Protocol (IP) layers. Stateful Inspection firewalls intercept and analyze incoming data packets
to determine whether they should be admitted to your private LAN, based on multiple criteria, or blocked.
Stateful inspection improves security by tracking data packets over a period of time, examining incoming and
outgoing packets. Outgoing packets that request specific types of incoming packets are tracked; only those
incoming packets constituting a proper response are allowed through the firewall.
Stateful inspection is a security feature that prevents unsolicited inbound access when NAT is disabled. You can
configure UDP and TCP “no-activity” periods that will also apply to NAT time-outs if stateful inspection is
enabled on the interface. Stateful Inspection parameters are active on a WAN interface only if enabled on your
system. Stateful inspection can be enabled on a WAN interface whether NAT is enabled or not.
Firewall tab, the Firewall Status page opens. The Firewall page displays the status of your
F
irewallFirewall
The center section displays the following:
Packet
IP Passthrough
NAT Default Server
Firewall Advanced
58
May be On or Off
May be On or Off
May be On or Off
May be On or Off
Page 59

The links at the top of the Firewall page access a series of pages to allow you to configure security features of
y
our device. The following sections give brief descriptions of these pages.
“Packet Filter” on page 60
“NAT/Gaming” on page 69
“Public Subnet Hosts” on page 74
“IP Passthrough” on page 75
“Firewall Advanced” on page 78
59
Page 60

Administrator’s Handbook
Link: Packet Filter
When you click the Packet
Packet Filter link the Packet Filter screen opens.
Packet Packet
Security should be a high priority for anyone administering a network connected to the Internet. Using packet
filters to control network communications can greatly improve your network’s security. The Packet Filter
engine allows creation of a maximum of eight Filtersets. Each Filterset can have up to eight rules configured.
WARNING:
ARRIS’s packet filters are designed to provide security for the Internet connections made to and from your network. You can customize the Gateway’s filtersets for a variety of packet filtering applications. Typically, you use
Before attempting to configure filters and filtersets, please read and understand this entire section thoroughly. The ARRIS Gateway incorporating NAT has advanced security features built in. Improperly adding filters and filtersets increases the possibility of loss of communication with the Gateway and the Internet.
Never attempt to configure filters unless you are local to the Gateway.
Although using filtersets can enhance network security, there are disadvantages:
• Filters are complex. Combining them in filtersets introduces subtle interactions, increasing the likelihood of
implementation errors.
• Enabling a large number of filters can have a negative impact on performance. Processing of packets will
take longer if they have to go through many checkpoints in addition to NAT.
• Too much reliance on packet filters can cause too little reliance on other security methods. Filtersets are
not a substitute for password protection, effective safeguarding of passwords, and general awareness of how
your network may be vulnerable.
60
Page 61

filters to selectively admit or refuse TCP/IP connections from certain remote networks and specific hosts. You
w
ill also use filters to screen particular types of connections. This is commonly called firewalling your network.
Before creating filtersets, you should read the next few sections to learn more about how these powerful security tools work.
Parts of a filter
A filter consists of criteria based on packet attribu
lowing attributes:
The source IP address (where the packet was sent from)
The destination IP address (where the packet is going)
The type of higher-layer Internet protocol the packet is carrying, such as TCP or UDP
Other filter attributes
There are three other attributes to each filter:
The filter’s order (i.e., priority) in the filterset
Whether the filter is currently active
Whether the filter is set to forward packets or to block (discard) packets
Design guidelines
Careful thought must go into designing a new filterset. You should consider the following guidelines:
Be sure the filterset’s overall purpose is clear from the beginning. A vague purpose can lead to a faulty set,
and that can actually make your network less secure.
Be sure each individual filter’s purpose is clear.
Determine how filter priority will affect the set’s actions. Test the set (on paper) by determining how the fil-
ters would respond to a number of different hypothetical packets.
Consider the combined effect of the filters. If every filter in a set fails to match on a particular packet, the
packet is:
• Forwarded if all the filters are configured to discard (not forward)
• Discarded if all the filters are configured to forward
• Discarded if the set contains a combination of forward and discard filters
tes. A typical filter can match a packet on any one of the fol-
An approach to using filters
The ultimate goal of network security is to prevent u
authorized access. Using filtersets is part of reaching that goal.
Each filterset you design will be based on one of the following approaches:
That which is not expressly prohibited is permitted.
That which is not expressly permitted is prohibited.
It is strongly recommended that you take the latter, and safer, approach to all of your filterset designs.
nauthorized access to the network without compromising
61
Page 62

Administrator’s Handbook
Working with Packet Filters
To work with filters, begin by accessing the Packet Filter page.
P
acket Filter
Enable/Disable Packet Filters – Click this button to globally turn your filters on or off.
Enable/Disable Packet Filters
nable/Disable Packet FiltersEnable/Disable Packet Filters
E
Packet Filter Rules
Buttons: Click either Add a ‘Drop’ Rule
Add a ‘Drop’ Rule or Add a ‘Pass’ Rule
Add a ‘Drop’ RuleAdd a ‘Drop’ Rule
Add a ‘Pass’ Rule button.
Add a ‘Pass’ RuleAdd a ‘Pass’ Rule
Action:
• drop: If you select drop, the specified packets will be blocked.
• pass: If you select pass, the specified packets will be forwarded.
62
Page 63

E
nter the Source IP Address or Destination IP Address this filter will match on.
As you create new Matches, the pull-down items change. There can only be one match from each Match
Type for a given rule. Match Types like Source Port, Destination Port, and TCP Flags are only available if other
matches (for example, Protocol =TCP) have previously been created.
Select Protocol, if necessary, from the pull-down menu: ICMP, TCP, UDP, or None to specify any another IP
transport protocol.
If you chose by number, enter the Protocol by number here.
If you chose by name, enter the Protocol by name here.
Enter the Source Port this filter will match on.
Enter the Destination Port this filter will match on.
If you selected ICMP, enter the ICMP Type here.
When you are finished configuring the filter, click the Enter Match
Enter Match button.
nter MatchEnter Match
E
The filter is automatically saved.
63
Page 64

Administrator’s Handbook
Packet Filter Rules List
Y
our entries are displayed as a table.
NOTE:
D
efault Forwarding Filter
If you create one or more filters that have a matching action of forward, then action on a packet matching
none of the filters is to block any traffic.
Therefore, if the behavior you want is to force the routing of a certain type of packet and pass all others
through the normal routing mechanism, you must configure one filter to match the first type of packet and
apply Force Routing. A subsequent filter is required to match and forward all other packets.
Management IP traffic
If the Force Routing filter is applied to source IP addresses, it may inadvertently block communication with
the router itself. You can avoid this by preceding the Force Routing filter with a filter that matches the destination IP address of the Gateway itself.
Example:
Assume a configured Custom Service/Hosted Application
8080-8080. Also assume that we want to allow only one external subnet access to this internal server,
207.53.17.0/24. And finally, assume that we want to disallow one IP address on that subnet, 207.53.17.9, from
access to that same server (perhaps they were abusing the system in some way). The rules we need are:
Input
ules:
R
Rule
Order
1 Drop 207.53.17.9 - TCP 8080
2 Pass 207.53.17.0/24 - TCP 8080
3 Drop - - TCP 8080
Action Source IP Destination IP Protocol
for an internal web server whose Global Port Range is
Source
Port
Destination
Port
64
Page 65

65
Page 66

Administrator’s Handbook
Example 2
T
he following example uses the GUI to detail how to create a public subnet.
1. Select Local Network -> Subnets & DHCP from the Web Managment GUI
2. Select On from the Public Subnet Enable drop down menu.
. Enter all applicable public subnet IP address information and select save
3
save at the bottom of the view.
savesave
4. Navigate to Firewall -> Packet Filter to create a packet filter that will allow specific traffic to flow to a public
LAN client
5. Scroll to the bottom of the screen and select Add a Pass Rule. This rule will allow traffic to flow through the
public subnet based on the match criteria that will be set up next.
. The new rule will be at the bottom of the Packet Rules list (as shown below).
6
66
Page 67

7. Select the Add Match
Add Match button below the new rule created in step 5. This opens the Match Entry view.
A
dd MatchAdd Match
8. For this example, the filter will be made based on a TCP port. So select Protocol from the Match Type drop
down menu, this automatically fills in TCP in the Match Value field. At this point do not enable the rule until
all criteria has been entered.
9. Click Enter Match
10.Select Add Match
Enter Match. This will return the GUI to the Packet Rules list.
Enter MatchEnter Match
Add Match below the rule created earlier.
Add MatchAdd Match
11.Select Destination Port from the Match Type drop down menu and enter 21 (this value corresponds to FTP)
n the Match Value entry box.
i
12.Click Enter Match
13.Select Add Match
Enter Match.
Enter MatchEnter Match
Add Match below the same rule created earlier.
Add MatchAdd Match
14.Select Destination IP Address from the Match Type drop down menu and enter the IP address entered in
Step 3 of this procedure.
15.Select the check box by Enable Rule and click Enter Match
Enter Match. The GUI is returned to the Packet Rules list and
Enter MatchEnter Match
the rule is active and grayed out and cannot be edited without first disabling the rule.
67
Page 68

Administrator’s Handbook
68
Page 69

Link: NAT/Gaming
When you click the NAT/Gaming
NAT/Gaming allows you to host internet applications when NAT is enabled. You can host different games and
oftware on different PCs.
s
From the Service pull-down menu, you can select any of a large number of predefined games and software.
(See “List of Supported Games and Software” on page 72.)
NAT/Gaming link, the NAT/Gaming page opens.
NAT/GamingNAT/Gaming
In addition to choosing from these predefined services you can also select a user defined custom service. (See
“Custom Services” on page 71.)
For each supported game or service, you can view the protocols and port ranges used by the game or service
by clicking the Service Details
Service Details button. For example:
ervice DetailsService Details
S
Select a hosting device from the Needed by Device pull-down menu.
1. Once you choose a software service or game, click Add
2. Select a PC to host the software from the Select Host Device pull-down menu and click Save
Add.
AddAdd
Save.
SaveSave
69
Page 70

Administrator’s Handbook
Each time you enable a software service or game your entry will be added to the list of Service names disp
layed on the NAT Configuration page.
To remove a game or software from the hosted list, choose the game or software you want to remove and click
Remove button.
the Remove
emoveRemove
R
70
Page 71

Custom Services
To configure a Custom Service, click the Add/Edit Services
Enter the following information:
Service Name: A unique identifier for the Custom Service.
Global Port Range: Range of ports on which incoming traffic will be received.
Base Host Port: The port number at the start of the port range your Gateway should use when forwarding
raffic of the specified type(s) to the internal IP address.
t
Protocol: Protocol type of Internet traffic, TCP or UDP.
Add/Edit Services button. The Custom Services page opens.
A
dd/Edit ServicesAdd/Edit Services
Once you define a Custom Service it becomes available in the Application Hosting Entry Service menu as one
of the services to select.
Click the Add
Add button.
ddAdd
A
Each time you enable a custom service your entry will be added to the list of Service names displayed on the
Custom Services page.
71
Page 72

Administrator’s Handbook
Changes are saved immediately.
T
o remove this Service, click the Delete
Delete button.
DeleteDelete
To edit this Service, click the Edit
NOTE:
You cannot edit a Custom Service if the Service is active; it must be inactive before it can be edited.
Edit button.
EditEdit
List of Supported Games and Software
AIM Talk Act of War - Direct Action Age of Empires II
Age of Empires, v.1.0 Age of Empires: The Rise of Rome,
v.1.0
Age of Wonders America's Army Apache
Asheron's Call Azureus Baldur's Gate I and II
Battlefield 1942 Battlefield Communicator Battlefield Vietnam
BitTornado BitTorrent Black and White
Blazing Angels Online Brothers in Arms - Earned in Blood Brothers in Arms Online
Buddy Phone CART Precision Racing, v 1.0 Calista IP Phone
Call of Duty Citrix Metaframe/ICA Client Close Combat III: The Russian Front,
Close Combat for Windows 1.0 Close Combat: A Bridge Too Far, v
2.0
Age of Mythology
v 1.0
Combat Flight Sim 2: WWII Pacific
Thr, v 1.0
Combat Flight Sim: WWII Europe
Series, v 1.0
Dark Reign Delta Force (Client and Server) Delta Force 2
Delta Force Black Hawk Down Diablo II Server Dialpad
DirecTV STB 1 DirecTV STB 2 DirecTV STB 3
Doom 3 Dues Ex Dune 2000
Empire Earth Empire Earth 2 F-16, Mig 29
F-22, Lightning 3 FTP Far Cry
Fighter Ace II GNUtella Grand Theft Auto 2 Multiplayer
H.323 compliant (Netmeeting,
CUSeeME)
Half Life Half Life 2 Steam Half Life 2 Steam Server
Half Life Steam Half Life Steam Server Halo
Hellbender for Windows, v 1.0 Heretic II Hexen II
Hotline Server ICQ 2001b ICQ Old
Counter Strike DNS Server
HTTP HTTPS
72
Page 73

IMAP Client I
Internet Phone Jedi Knight II: Jedi Outcast Kali
KazaA Lime Wire Links LS 2000
Lord of the Rings Online MSN Game Zone MSN Game Zone DX
MSN Messenger Mech Warrior 3 MechWarrior 4: Vengeance
Medal of Honor Allied Assault Microsoft Flight Simulator 2000 Microsoft Flight Simulator 98
Microsoft Golf 1998 Edition, v 1.0 Microsoft Golf 1999 Edition Microsoft Golf 2001 Edition
Midtown Madness, v 1.0 Monster Truck Madness 2, v 2.0 Monster Truck Madness, v 1.0
Motocross Madness 2, v 2.0 Motocross Madness, v 1.0 NNTP
Need for Speed 3, Hot Pursuit Need for Speed, Porsche Net2Phone
Operation FlashPoint Outlaws POP-3
PPTP PlayStation Network Quake 2
Quake 3 Quake 4 Rainbow Six
RealAudio Return to Castle Wolfenstein Roger Wilco
Rogue Spear SMTP SNMP
SSH server ShoutCast Server SlingBox
Soldier of Fortune StarCraft StarLancer, v 1.0
MAP Client v.3 IPSec IKE
Starfleet Command TFTP TeamSpeak
Telnet Tiberian Sun: Command and Con-
quer
Total Annihilation Ultima Online Unreal Tournament Server
Urban Assault, v 1.0 VNC, V irtual Network Computing Warlords Battlecry
Warrock Westwood Online, Command and
Conquer
Wolfenstein Enemy Territory World of Warcraft X-Lite
XBox 360 Media Center XBox Live 360 Yahoo Messenger Chat
Yahoo Messenger Phone ZNES eDonkey
eMule eMule Plus iTunes
mIRC Auth-IdentD mIRC Chat mIRC DCC - IRC DCC
pcAnywhere (incoming)
Timbuktu
Win2000 Terminal Server
73
Page 74

Administrator’s Handbook
Link: Public Subnet Hosts
Select Fierwall -> Public Subnet Hosts to open this view. This view provides the ability to create public subnet hosts. In order to create a public subnet host it must be enabled (turned on) in the Public Subnet section
of “Subnets & DHCP” on page 48. To create a Public Subnet, click on the Public Subnet hyperlink.
74
Page 75

Link: IP Passthrough
When you click the IP Passthrough
IP Passthrough
IP Passthrough link, the IP Passthrough page opens.
IP PassthroughIP Passthrough
The IP Passthrough feature allows a single PC on the
to it. It also provides PAT (NAPT) via the same public IP address for all other hosts on the private LAN subnet.
Using IP Passthrough, the public WAN IP is used to provide IP address translation for private LAN computers.
The public WAN IP is assigned and reused on a LAN computer.
LAN to have the ARRIS Gateway’s public address assigned
75
Page 76

Administrator’s Handbook
DHCP address serving can automatically serve the WAN IP address to a LAN computer.
W
hen DHCP is used for addressing the designated passthrough PC, the acquired or configured WAN address is
passed to DHCP, which will dynamically configure a single-servable-address subnet, and reserve the address for
the configured PC’s MAC address. This dynamic subnet configuration is based on the local and remote WAN
address and subnet mask.
The two DHCP modes assign the WAN IP information needed to the client automatically.
• You can select the MAC address of the PC you want to be the IP Passthrough client with fixed mode, or,
• with “first-come-first-served” – dynamic – the first client to renew its address will be assigned the WAN IP.
Manual mode is like statically configuring your PC. With Manual mode, you configure the TCP/IP Properties
of the LAN client PC you want to be the IP Passthrough client. You then manually enter the WAN IP address,
Gateway Address, etc. that matches the WAN IP address information of your ARRIS Gateway. This mode
works the same as the DHCP modes. Unsolicited WAN traffic will get passed to this client. The client is still
able to access the ARRIS Gateway and other LAN clients on the 192.168.1.x network, etc.
The Passthrough DHCP Lease – By default, the passthrough host's DHCP leases will be shortened to two
inutes. This allows for timely updates of the host's IP address, which will be a private IP address before the
m
WAN connection is established. After the WAN connection is established and has an address, the
passthrough host can renew its DHCP address binding to acquire the WAN IP address. You may alter this setting.
Click Save
Save. Changes take effect upon restart.
SaveSave
A restriction
Since both the Gateway and the passthrough host will use the same IP address, new sessions that conflict with
existing sessions will be rejected by the Gateway. For example, suppose you are a teleworker using an IPSec
tunnel from the Router and from the passthrough host. Both tunnels go to the same remote endpoint, such as
the VPN access concentrator at your employer’s office. In this case, the first one to start the IPSec traffic will be
allowed; the second one – since, from the WAN, it's indistinguishable – will fail.
76
Page 77

NAT Default Server
T
his feature allows you to:
Direct your Gateway to forward all externally initiated IP traffic (TCP and UDP protocols only) to a default
host on the LAN, specified by your entry in the Internal Address field.
Enable it for certain situations:
– Where you cannot anticipate what port number or packet protocol an in-bound application might use. For
example, some network games select arbitrary port numbers when a connection is opened.
– When you want all unsolicited traffic to go to a specific LAN host.
This feature allows you to direct unsolicited or non-specific traffic to a designated LAN station. With NAT “On”
in the Gateway, these packets normally would be discarded.
For instance, this could be application traffic where you don’t know (in advance) the port or protocol that will
be used. Some game applications fit this profile.
Click Save
Save. Changes take effect immediately.
aveSave
S
77
Page 78

Administrator’s Handbook
Link: Firewall Advanced
When you click the Firewall Advanced
Firewall Advanced link the Firewall Advanced screen opens.
Firewall AdvancedFirewall Advanced
All computer operating systems are vulnerable to attack from outside sources, typically at the operating system or Internet Protocol (IP) layers. Stateful Inspection firewalls intercept and analyze incoming data packets
to determine whether they should be admitted to your private LAN, based on multiple criteria, or blocked.
Stateful inspection improves security by tracking data packets over a period of time, examining incoming and
outgoing packets. Outgoing packets that request specific types of incoming packets are tracked; only those
incoming packets constituting a proper response are allowed through the firewall.
Stateful inspection is a security feature that prevents unsolicited inbound access when NAT is disabled. You can
configure UDP and TCP “no-activity” periods that will also apply to NAT time-outs if stateful inspection is
enabled on the interface. Stateful Inspection parameters are active on a WAN interface only if enabled on your
Gateway. Stateful inspection can be enabled on a WAN interface whether NAT is enabled or not.
DoS Protection – Denial-Of-Service attacks are common on the Internet, and can render an individual PC or a
hole network practically unusable by consuming all its resources. Your Gateway includes default settings to
w
78
Page 79

block the most common types of DoS attacks. For special requirements or circumstances, a variety of addit
ional blocking characteristics is offered. See the following table.
Menu item Function
Drop packets with invalid source or destination IP address
Protect against port scan Whether to detect and drop port scans.
Drop packets with unknown ether types
op packets with invalid TCP flags Whether packets with invalid TCP flag settings (NULL, FIN, Xmas, etc.)
Dr
Drop incoming ICMP Echo requests Whether all ICMP echo requests are to be dropped; On or Off.
Flood Limit Whether packet flooding should be detected and offending packets be
Flood rate limit Specifies the number limit of packets per second before dropping the
Flood burst limit Specifies the number limit of packets in a single burst before dropping the
Flood limit ICMP enable Whether ICMP traffic packet flooding should be detected and offending
Flood limit UDP enable Whether UDP traffic packet flooding should be detected and offending
Flood limit UDP Pass multicast Allows exclusion of UDP multicast traffic. On by default.
Flood limit TCP enable Allows exclusion of TCP traffic. Off by default.
Flood limit TCP SYN-cookie Allows TCP SYN cookies flooding to be excluded.
Neighbor Discovery Attack protection Prevents downstream traffic from an upstream device that sends excessive
ESP Header Forwarding Allows the use of Encapsulating Security Payload (ESP) data payload encryp-
thentication Header Forwarding Accept and forward IPSec packets with Authencation Headers, which may
Au
Reflexive ACL When IPv6 is enabled, Reflexive Access Control Lists can deny inbound IPv6
ESP ALG This feature helps ESP (IPSec encryption), work properly when using NAT.
SIP ALG This feature understands the SIP protocol used by the specific application
Whether packets with invalid source or destination IP address(es) are to be
dropped
Whether packets with unknown ether types are to be dropped
should be dropped
dropped; On or Off.
remainder.
remainder.
packets be dropped; On or Off.
packets be dropped; On or Off.
traffic but receives no replies; On or Off.
tion for IP Secure (IPsec) from qualifying endpoints; On or Off.
be used by some IPSec implementations to validate packet sources ; On or
Off.
traffic unless this traffic results from returning outgoing packets (except as
configured through firewall rules).
Can sometimes cause problems for non-NATed hosts (such as devices on the
Public LAN).
and does a protocol-packet inspection of traffic through it. A NAT router
with a built in SIP ALG can rewrite information within the SIP messages (SIP
heads and SDP body) making signalling and audio traffic between the client
behind NAT and the SIP endpoint possible.
If you make any changes here, click the Save
Save button.
aveSave
S
79
Page 80

Administrator’s Handbook
Diagnostics
When you click the Diagnostics
Diagnostics tab, the Troubleshoot page opens.
D
iagnosticsDiagnostics
This automated multi-layer test examines the functionality of the Router from the physical connections to the
data traffic being sent by users through the Router.
You can run all the tests in order by clicking the Run Full Diagnostics
Run Full Diagnostics button.
un Full DiagnosticsRun Full Diagnostics
R
The device will automatically test a number of components to determine any problems. You can see detailed
results of the tests by clicking the Details
Details buttons for each item. The details presented depend on the configura-
DetailsDetails
tion of your Router and your network type.
80
Page 81

Here is an example of the Ethernet Details screen.
T
est Internet Access
These tests send a PING from the modem to either the
LAN or WAN to verify connectivity. A PING could be
either an IP address (163.176.4.32) or Domain Name (www.mycompany.com). You enter a web address URL or
an IP address in the respective field.
Click the Ping
Ping, Trace
Trace, or NSLookup
PingPing
TraceTrace
NSLookup button.
NSLookupNSLookup
Results will be displayed in the Progress Window as they are generated.
Ping - tests the “reachability” of a particular network destination by sending an ICMP echo request and
waiting for a reply.
Traceroute - displays the path to a destination by showing the number of hops and the router addresses of
hese hops.
t
NSLookup - converts a domain name to its IP address and vice versa.
To use the Ping capability, type a destination address (domain name or IP address) in the text box and click the
Ping
Ping, Trace
Trace, or Lookup
PingPing
TraceTrace
Lookup button. The results are displayed in the Progress Window.
LookupLookup
This sequence of tests takes approximately one minute to generate results. Please wait for the test to run to
completion.
81
Page 82

Administrator’s Handbook
Each test generates one of the following result codes:
Result Meaning
* PASS: The test was successful.
* FAIL: The test was unsuccessful.
* SKIPPED: The test was skipped because a test on which it depended failed.
* PENDING: The test timed out without producing a result. Try running the test again.
* WARNING: The test was unsuccessful. The Service Provider equipment your Modem connects to may not
support this test.
B
elow are some specific tests:
Action If PING fails, possible causes are:
From the Check Connection page:
Ping the internet default gateway IP address Connection is down; Gateway’s IP address or subnet
mask are wrong; gateway router is down.
Ping an internet site by IP address Site is down.
Ping an internet site by name Servers are down; site is down.
From a LAN PC:
Ping the Modem’s LAN IP address IP address and subnet mask of PC are not on the same
scheme as the Modem; cabling or other connectivity
issue.
Ping an internet site by IP address PC's subnet mask may be incorrect, site is down.
Ping an internet site by name DNS is not properly configured on the PC, site is down.
82
Page 83

Link: Logs
When you click Logs
Logs, the Logs page opens.
LogsLogs
The current status of the device is displayed for all logs: System, Firewall, or VoIP. Choose the log you want to
isplay from the pull-down menu.
d
You can clear all log entries by clicking the Clear Log
You can save logs to a text (.TXT) file by clicking the Save to File
browser’s default download location on your hard drive. The file can be opened with your favorite text editor.
NOTE:
Some browsers, such as Internet Explorer for Windows XP, require that you specify the ARRIS® device’s URL
as a “Trusted site” in “Internet Options: Security”. This is necessary to allow the “download” of the log text
file to the PC.
Clear Log button.
Clear LogClear Log
Save to File button. This will download the file to your
Save to FileSave to File
83
Page 84

Administrator’s Handbook
The following is an example log portion saved as a .TXT file:
84
Page 85

Link: Update
When you click Update
Operating System Software is what makes your Gateway run and occasionally it needs to be updated. Your Cur-
rent software version is displayed at the top of the page.
To update your software from a file on your PC, you must first download the software from your Service Provider's Support Site to your PC's hard drive.
Browse your computer for the operating system file you downloaded and select the file.
Browse
rowseBrowse
B
Click the Update
The LEDs will operate normally as described in “Status Indicator Lights” on page 92.
The installation may take a few minutes and the web page will indicate a 3-part countdown before returning
you to the Home page; wait for it to complete. During the software installation, you will lose Internet and
phone service. The LEDs will function as follows:
During this phase, the LEDs will function as follows:
During this phase, the Power LED will flash Orange/Amber during firmware upgrade (flash writing to mem-
ry) and all other LEDs will be off.
o
The Gateway will restart automatically.
As the device reboots, the POWER ON LED behavior will happen.
Your new operating system will then be running.
Update, the Update page opens.
UpdateUpdate
Update button.
UpdateUpdate
85
Page 86

Administrator’s Handbook
Link: Resets
When you click Resets
In some cases, you may need to clear all the configuration settings and start over again to program the ARRIS®
Gateway. You can perform a factory reset to do this.
It might also be useful to reset your connection to the Internet without deleting all of your configuration settings.
Click the Reset IP
the Internet, but will otherwise be unaffected.
Click the Reset Connection
phones.
Click the Reset Device
Click the Restart
Resets, the Resets page opens.
ResetsResets
Reset IP to refresh your Internet WAN IP address. LAN-side users will be briefly disconnected from
eset IPReset IP
R
Reset Connection button to disconnect and reconnect all of your connections, including your VoIP
Reset ConnectionReset Connection
Reset Device button to reset the Gateway back to its original factory default settings.
Reset DeviceReset Device
Restart button to reboot the device. Previous configuration settings are still retained.
RestartRestart
86
NOTE:
xercise caution before performing a Factory Reset. This will erase any configuration changes that you may
E
have made and allow you to reprogram your Gateway.
Page 87

Link: Syslog
When you click the Syslog
syslog protocol - RFC 3164) syslog client to report a number of subsets of the events entered in the device’s
logs.
Syslog link the Syslog configuration page opens. You can configure a UNIX-compatible (BSD
SyslogSyslog
You can enable or disable the Syslog client dynamical
previously unreported events.
You can specify the Syslog server’s address and port, if required, either in dotted decimal format or as a DNS
name up to 63 characters.
You can specify the UNIX syslog Facility to use by selecting from the Facility pull-down menu.
From the pull-down menu, you specify the Log Level in decreasing severity level: Emergency, Alert, Critical,
rror, Warning, Notice, Info, or Debug.
E
By toggling each event descriptor to either On or Off, you can determine which ones are logged and which
are ignored.
You will need to install a Syslog client daemon program on your PC and configure it to report the events you
specified in the Syslog configuration screen.
Click the Save
Save button.
SaveSave
ly. When enabled, it will report any appropriate and
87
Page 88

Administrator’s Handbook
Link: Event Notifications
When you click Event Notifications
If you check the Broadband Status Notification checkbox, the device will alert users on your network if the
onnection to the Internet should fail. In that event, troubleshooting suggestions will display.
c
Event Notifications, the Event Notifications page opens.
Event NotificationsEvent Notifications
88
Page 89

Link: NAT Table
When you click the NAT Table
NAT Table link, the NAT Table page opens.
NAT TableNAT Table
The NAT Table page displays the network address translation sessions in use by the Gateway. You can use the
pull-down menu to limit the displayed sessions to selected IP addresses.
To refresh all the sessions displayed, click the Reset
Reset button.
esetReset
R
89
Page 90

Administrator’s Handbook
90
Page 91

CHAPTER 3 Basic Troubleshooting
This section gives some simple suggestions for troubleshooting problems with your Gateway’s initial configurat
ion.
Before troubleshooting, make sure you have
read the User Manual;
plugged in all the necessary cables
set your PC’s TCP/IP controls to obtain an IP address automatically.
91
Page 92

Administrator’s Handbook
Side View
Power
Ethernet
Wi-Fi
Broadband Ethernet
Broadband Fiber
Service
Phone 1
Phone 2
WPS
Status Indicator Lights
The first step in troubleshooting is to check the status indicator lights (LEDs) in the order outlined below.
ARRIS® Gateway NVG595 status indicator lights
LED Action
Solid Green = The device is powered.
Flashing Green = A Power-On Self-Test (POST) is in progress
Power*
Flashing Red = A POST failure (not bootable) or device malfunction occurred.
Orange/Amber = during firmware upgrade (see below)
Off = The unit has no AC power.
*During
Firmware
Upgrade
During Boot
process
Ethernet
Wi-Fi
During the software installation, you will lose internet and phone service. The LEDs will function as
follows:
1. As firmware is being loaded into flash, the LEDs will operate normally as described.
2. The installation will take a few minutes –
During this phase, the Power LED willl flash Orange/Amber during firmware upgrade
(flash writing to memory) and all other LEDs will be off.
3. The Gateway will restart automatically.
As the device reboots, the POWER ON LED behavior will happen.
• Power LED = GREEN/FLASH
• All other LED = OFF
If the device does not boot, and fails its self test or fails to perform initial load of the bootloader:
• Power LED = RED/FLASH
• ALL other LED = OFF
If the device boots and then detects a failure:
Power LED = GREEN/FLASH starting POST and then all LEDs will FLASH RED, including Power
LED.
Solid Green = Powered device connected to the associated port (includes devices with wake-on-
LAN capability where a slight voltage is supplied to the Ethernet connection).
Flickering Green = Activity seen from devices associated with the port. The flickering of the light is
synchronized to actual data traffic.
Off = The device is not powered, no cable or no powered devices connected to the associated ports.
Solid Green = Wi-Fi is powered.
Flickering Green = Activity seen from devices connected via Wi-Fi. The flickering of the light is syn-
chronized to actual data traffic.
Off = The device is not powered or no powered devices connected to the associated ports.
92
Page 93

LED A
Solid Green = Good broadband connection.
Flashing Green & Red = If the broadband connection fails to be established for more than three
consecutive minutes the LED switches to Flashing Green when attempting or waiting to establish
Broadband
E
thernet
Broadband
Fiber
Service
a broadband connection alternating with a five second steady Red. This pattern continues until the
broadband connection is successfully established.
Flashing Red = No signal on the line. This is only used when ther
ing sequence.
Off = The device is not powered.
Solid Green = Good broadband connection.
Flashing Green & Red = If the broadband connection fails to be established for more than three
consecutive minutes the LED switches to Flashing Green when attempting or waiting to establish
a broadband connection alternating with a five second steady Red. This pattern continues until the
broadband connection is successfully established.
Flashing Red = No signal on the line. This is only used when there is no signal, not during the train-
ing sequence.
Off = The device is not powered.
Solid Green = IP connected (The device has a WAN IP address from DHCP or 802.1x authentication
and the broadband connection is up).
Flashing Green = Attempting connection, attempting IEEE 802.1X authentication or attempting to
obtain DHCP information.
Red = Device attempted to become IP connected and failed (no DHCP response, 802.1x authentica-
tion failed, no IP address from IPCP, etc.). The Red state times out after two minutes and the Service
indicator light returns to the Off state.
Off = The device is not powered or the broadband connection is not present.
ction
e is no signal, not during the train-
Phone 1, 2
WPS
(opens after
using WPS
button)
Solid Green
Flashing Green = Indicates a telephone is off-hook on the associated VoIP line.
Off = VoIP not in use, line not registered or Gateway power off.
Solid Green = Wi-Fi Protected Setup has been completed successfully. It should stay on for 5 minutes
or until push button is pressed again.
Flashing Green = for 2 mins. Indicates when WPS is broadcasting.
Flashing Red = for 2 min, when there is a Session overlap detected (possible security risk) in Scenario.
Solid Red = on Error unrelated to security, such as failed to find any partner, or protocol prematurely
aborted. It should stay Solid Red for 5 min or until push button is pressed again.
Off = WPS is not active, the device is not powered, no cable or no powered devices connected to the
associated ports.
= The associated VoIP line has been registered with a SIP proxy server.
93
Page 94

Administrator’s Handbook
Power Jack
Reset
RJ14
Optical Port
Gigabit Ethernet
Button
Port
(WAN)
Port (WAN)
Ethernet Ports
(LAN)
ARRIS® Gateway NVG595 Rear View
LED Action
Orange/Amber when a Gigabit Ethernet device is connected to each port.
Ethernet
1,2 3,4
Green when 10/100 Ethernet device is connected.
Flash for Ethernet traffic passing.
Off = The device is not powered, or no powered devices connected to the associated ports.
NOTE:
The NVG595 supports two VoIP lines over one RJ14 VoIP port. In order to con-
nect two phone lines the supplied inner/outer pair splitter adapters must be
attached to the RJ14 VoIP port in order to terminate both lines. This is a special-purpose splitter. You must only use the inner/outer pair splitter adapters
supplied by AT&T.
94
Page 95

LED Function Summary Matrix
Power
Ethernet
AN
L
Broadband
Ethernet
Solid Green
The device is
powered.
Solid Green =
Powered device
connected to the
associated port
(includes devices
with wake-onLAN capability
where a slight
voltage is supplied to the
Ethernet connection).
Solid Green =
Powered device
connected to the
associated port
(includes devices
with wake-onLAN capability
where a slight
voltage is supplied to the
Ethernet connection).
=
Flashing
Green = A
Power-On SelfTest (POST) is in
progress
Flashing
Green = Activ-
ity seen from
devices associated with the
port. The flickering of the light is
synchronized to
actual data traffic.
Flashing
Green = Activ-
ity seen from
devices associated with the
port. The flickering of the light is
synchronized to
actual data traffic.
Orange/Amber
= during firmware upgrade
(see “*During
Firmware
Upgrade” on
page 92)
Flashing Red =
A
POST failure
(not bootable) or
device malfunction occurred.
* When the
device encounters a POST failure, all indicator
lights on the
front of the
device continuously flash.
Flashing
Green and Red
= if the broadband connection
fails to be established for more
than three consecutive minutes
the LED
swsitches to
flashing green
when attemting
or waiting to
establish a
broadband connection alternating with a five
second steady
Red . This pat-
r contiues until
te
the connection is
established
Off = The unit
has no AC power.
Off = The device
is not powered,
no cable or no
powered devices
connected to the
associated ports.
Off = The device
is not powered,
no cable or no
powered devices
connected to the
associated ports.
95
Page 96

Administrator’s Handbook
Broadban
W
i-Fi
Service
Phone 1, 2
WPS
Solid Green =
Wi-Fi is powered.
Solid Green =
IP connected
(The device has a
WAN IP address
from DHCP or
802.1x authentication and the
broadband connection is up).
Solid Green
The associated
VoIP line has
been registered
with a SIP proxy
server.
Solid Green =
Wi-Fi Protected
Setup has been
completed successfully. It
should stay on
for 5 minutes or
until push button is pressed
again.
=
Flashing
Green = Activ-
ity seen from
devices connected via Wi-Fi.
The flickering of
the light is synchronized to
actual data traffic.
Flashing
Green =
Attempting PPP
connection.þ
Attempting IEEE
802.1X authentication or
attempting to
obtain DHCP
information.
Flashing
Green = Indi-
cates a telephone is off-hook
on the associated
VoIP line.
Flashing
Green = Indi-
cates when WPS
is broadcasting.
Solid Red =
Error unrelated
to security, such
as failed to find
any partner, or
protocol prematurely aborted. It
should stay Solid
Red for 5 min or
until push button is pressed
again.
Flashing
Green and Red
= if the broadband connection
fails to be established for more
than three consecutive minutes
the LED
swsitches to
flashing green
when attemting
or waiting to
establish a
broadband connection alternating with a five
second steady
Red . This pat-
r contiues until
te
the connection is
established
Red = Device
attempted to
become IP connected and failed
(no DHCP
response, 802.1x
authentication
failed, no IP
address from
IPCP, etc.). The
Red state times
out after two
minutes and the
Service indicator
light returns to
the Off state.
Flashing Red =
Session overlap
detected (possible security risk)
in Scenario.
Off = The device
is not powered
or no powered
devices connected to the
associated ports.
Off = The device
is not powered
or the broadband connection
is not present.
Off = VoIP not in
use, line not registered or Gateway power off.
Off = WPS is not
active, the device
is not powered,
no cable or no
powered devices
connected to the
associated ports.
96
Page 97

If a status indicator light does not look correct, look for these possible problems:
I
f LED is not
Lit
Possible problems
Power
Broadband
Ethernet
Make sure the power adapter is plugged into the Modem properly.
Try a known good wall outlet.
If a power strip is used, make sure it is switched on
Make sure the WAN ethernet or Fiber cable is connected to the modem properly.
Make sure the Ethernet cable is securely plugged into the Ethernet jack on the PC.
Make sure the Ethernet cable is securely plugged into the Ethernet port on the
Modem.
Make sure you have Ethernet drivers installed on the PC.
Make sure the PC’s TCP/IP Properties for the Ethernet Network Control Panel is set
to obtain an IP address via DHCP.
Make sure the PC has obtained an address in the 192.168.1.x range. (You may have
changed the subnet addressing.)
Make sure the PC is configured to access the Internet over a LAN.
Disable any installed network devices (Ethernet, Wi-Fi) that are not being used to
connect to the Modem.
.
97
Page 98

Administrator’s Handbook
Factory Reset Switch
Factory Reset Switch
If you lose your access code the following section shows how to reset the ARRIS® Gateway so that you can
a
ccess the configuration screens once again.
NOTE: Keep in mind that all of your settings will need to be reconfigured.
If you don't have an Access Code, the only way to access the ARRIS® Gateway is the following:
1. Referring to the diagram below, find the round Factory Reset Switch.
. Carefully press the reset switch.
2
If you press the factory reset button for less than ten (10) seconds, the device will be rebooted.
The indicator lights on the device will respond immediately and start blinking red within one (1) second of
the reset button being pressed.
This will occur independent of the fact that the button is still being pressed or has been released. The indicator lights will flash for a minimum of five seconds, even if the reset button is released prior to five seconds
after it has been depressed. If the reset button is held for more than 5 seconds, then it will continue to flash
until released or until 10 seconds (see below).
If you press the factory reset button for a longer period of time, the device will be reset to the factory
default shipped settings.
If the button is held for ten seconds, the Power indicator continues to flash, for an additional 5 seconds and
then the indicator lights will return to their normal operating mode, independent of whether or not the
reset button is still depressed.
98
Page 99

Log Event Messages
Administration Related Log Messages
1. administrative access attempted: T
2. administrative access authenticated and allowed:
3. administrative access allowed: If for some reason, a customer does not want password protection for the
4. administrative access denied invalid user name:
5. administrative access denied invalid password:
6. administrative access denied telnet access not allowed:
7. administrative access denied web access not allowed:
his log-message is generated whenever the user attempts to access the
router's management interface.
This log-message is generated whenever the user attempts to access the
router's management interface and is successfully authenticated and
allowed access to the management interface.
management interface, this log-message is generated whenever any user
attempts to access the router's management interface and is allowed access
to the management interface.
This log-message is generated whenever the user tries to access the router's
management interface and authentication fails due to incorrect user-name.
This log-message is generated whenever the user tries to access the router's
management interface and authentication fails due to incorrect password.
This log-message is generated whenever the user tries to access the router's
Telnet management interface from a Public interface and is not permitted
since Remote Management is disabled.
This log-message is generated whenever the user tries to access the router's
HTTP management interface from a Public interface and is not permitted
since Remote Management is disabled.
System Log Messages
1. Received NTP Date and Time: T
2. EN: IP up: This log-message is generated whenever Ethernet WAN comes up.
3. WAN: Ethernet WAN1 activated
at 100000 Kbps:
4. Device Restarted: This log-message is generated when the router has been restarted.
his log-message is generated whenever NTP receives Date and time from
the server.
This log-message is generated when the Ethernet WAN Link is up.
99
Page 100

Administrator’s Handbook
Access-related Log Messages
1. permitted: T
2. attempt: This log-message is generated whenever a packet attempts to traverse
3. dropped - violation of security
policy:
4. dropped - invalid checksum: This log-message is generated whenever a packet, traversing the router or
5. dropped - invalid data length: This log-message is generated whenever a packet, traversing the router or
6. dropped - fragmented packet: This log-message is generated whenever a packet, traversing the router, is
7. dropped - cannot fragment: This log-message is generated whenever a packet traversing the router is
8. dropped - no route found: This log-message is generated whenever a packet, traversing the router or
9. dropped - invalid IP version: This log-message is generated whenever a packet, traversing the router or
10. dropped - possible land attack: This log-message is generated whenever a packet, traversing the router or
11. TCP SYN flood detected: This log-message is generated whenever a SYN packet destined to the
12. Telnet receive DoS attack packets dropped:
13. dropped - reassembly timeout: This log-message is generated whenever packets, traversing the router or
14. dropped - illegal size: This log-message is generated whenever packets, traversing the router or
his log-message is generated whenever a packet is allowed to traverse
router-interfaces or allowed to access the router itself.
router-interfaces or attempts to access the router itself.
This log-message is generated whenever a packet, traversing the router or
destined to the router itself, is dropped by the firewall because it violates
the expected conditions.
destined to the router itself, is dropped because of invalid IP checksum.
destined to the router itself, is dropped because the IP length is greater than
the received packet length or if the length is too small for an IP packet.
dropped because it is fragmented, stateful inspection is turned ON on the
packet's transmit or receive interface, and deny-fragment option is enabled.
dropped because the packet cannot be sent without fragmentation, but the
do not fragment bit is set.
destined to the router itself, is dropped because no route is found to forward the packet.
destined to the router itself, is dropped because the IP version is not 4.
destined to the router itself, is dropped because the packet is TCP/UDP
packet and source IP Address and source port equals the destination IP
Address and destination port.
router's management interface is dropped because the number of SYN-sent
and SYN-receives exceeds one half the number of allowable connections in
the router.
This log-message is generated whenever TCP packets destined to the
router's telnet management interface are dropped due to overwhelming
receive data.
destined to the router itself, are dropped because of reassembly timeout.
destined to the router itself, are dropped during reassembly because of illegal packet size in a fragment.
100
 Loading...
Loading...