Acronis Backup Recovery Advanced Server - 11.5 Command-Line Reference

Acronis Backup & Recovery 11.5
Command-Line Reference
Applies to the following editions:
|
Advanced Server |
|
Virtual Edition |
|
Advanced Server SBS Edition |
|
Advanced Workstation |
|
Server for Linux |
|
Server for Windows |
|
Workstation |
Copyright Statement
Copyright © Acronis International GmbH, 2002-2012. All rights reserved.
“Acronis” and “Acronis Secure Zone” are registered trademarks of Acronis International GmbH.
"Acronis Compute with Confidence", “Acronis Startup Recovery Manager”, “Acronis Active Restore” and the Acronis logo are trademarks of Acronis International GmbH.
Linux is a registered trademark of Linus Torvalds.
VMware and VMware Ready are trademarks and/or registered trademarks of VMware, Inc. in the United States and/or other jurisdictions.
Windows and MS-DOS are registered trademarks of Microsoft Corporation.
All other trademarks and copyrights referred to are the property of their respective owners.
Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder.
Distribution of this work or derivative work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained from the copyright holder.
DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID.
Third party code may be provided with the Software and/or Service. The license terms for such third-parties are detailed in the license.txt file located in the root installation directory. You can always find the latest up-to-date list of the third party code and the associated license terms used with the Software and/or Service at http://kb.acronis.com/content/7696
Acronis patented technologies
Technologies used in this product are covered by the following patents: U.S. Patent # 7,047,380; U.S. Patent # 7,246,211; U.S. Patent # 7,318,135; U.S. Patent # 7,366,859; U.S. Patent # 7,636,824; U.S. Patent # 7,831,789; U.S. Patent # 7,886,120; U.S. Patent # 7,934,064; U.S. Patent # 7,949,635; U.S. Patent # 7,979,690; U.S. Patent # 8,069,320; U.S. Patent # 8,073,815; U.S. Patent # 8,074,035.
2 |
Copyright © Acronis, Inc., 2000-2012 |
Table of contents
1 Command-line utility overview .............................................................................................. |
7 |
|
1.1 |
Installation ................................................................................................................................. |
7 |
1.2 |
Backward compatibility and upgrade ........................................................................................ |
8 |
1.3 |
Syntax......................................................................................................................................... |
8 |
1.4 |
Local, remote and centralized management........................................................................... |
10 |
1.5 |
Uninstallation........................................................................................................................... |
12 |
1.6 |
List of abbreviated names ....................................................................................................... |
12 |
2 |
Commands .......................................................................................................................... |
13 |
||
|
2.1 |
Commands by services ............................................................................................................ |
13 |
|
|
2.1.1 |
Disk, file, virtual machine backup................................................................................................................. |
13 |
|
|
2.1.2 |
Application backup........................................................................................................................................ |
15 |
|
|
2.2 |
help .......................................................................................................................................... |
17 |
|
|
2.3 |
Backup and recovery ............................................................................................................... |
17 |
|
|
2.3.1 |
Disks and volumes......................................................................................................................................... |
17 |
|
|
2.3.2 |
Files................................................................................................................................................................. |
23 |
|
|
2.3.3 |
Virtual machines............................................................................................................................................ |
25 |
|
|
2.3.4 |
Microsoft Exchange....................................................................................................................................... |
30 |
|
|
2.4 |
Operations with archives and backups.................................................................................... |
36 |
|
|
2.4.1 |
Archives.......................................................................................................................................................... |
36 |
|
|
2.4.2 |
Backups .......................................................................................................................................................... |
38 |
|
|
2.4.3 |
Mounting ....................................................................................................................................................... |
44 |
|
|
2.5 |
Operations with Acronis Secure Zone ..................................................................................... |
46 |
|
|
2.5.1 |
create asz ....................................................................................................................................................... |
46 |
|
|
2.5.2 |
cleanup asz..................................................................................................................................................... |
47 |
|
|
2.5.3 |
delete asz_files .............................................................................................................................................. |
47 |
|
|
2.5.4 |
delete asz ....................................................................................................................................................... |
48 |
|
|
2.6 |
Operations with Acronis Startup Recovery Manager .............................................................. |
49 |
|
|
2.6.1 |
activate asrm ................................................................................................................................................. |
49 |
|
|
2.6.2 |
deactivate asrm............................................................................................................................................. |
49 |
|
|
2.7 |
Operations with tapes ............................................................................................................. |
50 |
|
|
2.7.1 |
list tape_libraries........................................................................................................................................... |
50 |
|
|
2.7.2 |
list tape_drives .............................................................................................................................................. |
50 |
|
|
2.8 |
Operations with vaults............................................................................................................. |
51 |
|
|
2.8.1 |
validate vault ................................................................................................................................................. |
51 |
|
|
2.9 |
Operations with disks .............................................................................................................. |
52 |
|
|
2.9.1 |
clone disk ....................................................................................................................................................... |
52 |
|
|
2.10 |
Administration operations....................................................................................................... |
52 |
|
|
2.10.1 |
Collecting information .................................................................................................................................. |
52 |
|
|
2.10.2 |
Plans ............................................................................................................................................................... |
55 |
|
|
2.10.3 |
Tasks............................................................................................................................................................... |
58 |
|
|
2.10.4 |
Licenses.......................................................................................................................................................... |
60 |
|
3 |
Parameters.......................................................................................................................... |
62 |
|
3.1 Access to a physical machine................................................................................................... |
62 |
3 |
|
Copyright © Acronis, Inc., 2000-2012 |
3.1.1 |
host................................................................................................................................................................. |
62 |
|
3.1.2 |
service ............................................................................................................................................................ |
62 |
|
3.1.3 |
address........................................................................................................................................................... |
62 |
|
3.2 |
Virtual machines ...................................................................................................................... |
63 |
|
3.2.1 |
Access to a virtual machine .......................................................................................................................... |
63 |
|
3.2.2 |
New virtual machine..................................................................................................................................... |
64 |
|
3.3 |
Access to Microsoft Exchange ................................................................................................. |
65 |
|
3.3.1 |
exchange_credentials ................................................................................................................................... |
65 |
|
3.3.2 |
items............................................................................................................................................................... |
65 |
|
3.3.3 |
Specifying Exchange data ............................................................................................................................. |
66 |
|
3.4 |
Location ................................................................................................................................... |
67 |
|
3.4.1 |
loc ................................................................................................................................................................... |
67 |
|
3.4.2 |
arc................................................................................................................................................................... |
67 |
|
3.4.3 |
backup............................................................................................................................................................ |
68 |
|
3.4.4 |
target.............................................................................................................................................................. |
69 |
|
3.4.5 |
target_arc....................................................................................................................................................... |
70 |
|
3.4.6 |
mailbox_location........................................................................................................................................... |
70 |
|
3.5 |
Disks and volumes ................................................................................................................... |
71 |
|
3.5.1 |
disk ................................................................................................................................................................. |
71 |
|
3.5.2 |
nt_signature................................................................................................................................................... |
71 |
|
3.5.3 |
volume ........................................................................................................................................................... |
72 |
|
3.5.4 |
start ................................................................................................................................................................ |
73 |
|
3.5.5 |
size.................................................................................................................................................................. |
73 |
|
3.6 |
Backup parameters.................................................................................................................. |
74 |
|
3.6.1 |
backuptype .................................................................................................................................................... |
74 |
|
3.6.2 |
cleanup........................................................................................................................................................... |
74 |
|
3.6.3 |
Comments...................................................................................................................................................... |
74 |
|
3.6.4 |
copy_only....................................................................................................................................................... |
75 |
|
3.6.5 |
exclude........................................................................................................................................................... |
75 |
|
3.6.6 |
express ........................................................................................................................................................... |
76 |
|
3.6.7 |
fixed_drive ..................................................................................................................................................... |
77 |
|
3.6.8 |
include............................................................................................................................................................ |
77 |
|
3.6.9 |
plain_archive ................................................................................................................................................. |
78 |
|
3.6.10 |
raw.................................................................................................................................................................. |
78 |
|
3.6.11 |
Backup options.............................................................................................................................................. |
79 |
|
3.7 |
Recovery parameters............................................................................................................... |
86 |
|
3.7.1 |
database......................................................................................................................................................... |
86 |
|
3.7.2 |
database_location......................................................................................................................................... |
86 |
|
3.7.3 |
destination_database ................................................................................................................................... |
86 |
|
3.7.4 |
disk_location.................................................................................................................................................. |
87 |
|
3.7.5 |
exclude........................................................................................................................................................... |
87 |
|
3.7.6 |
ext2_3............................................................................................................................................................. |
88 |
|
3.7.7 |
fat16_32......................................................................................................................................................... |
88 |
|
3.7.8 |
file................................................................................................................................................................... |
88 |
|
3.7.9 |
log_location ................................................................................................................................................... |
88 |
|
3.7.10 |
outlookmachine ............................................................................................................................................ |
89 |
|
3.7.11 |
overwrite........................................................................................................................................................ |
89 |
|
3.7.12 |
pit.................................................................................................................................................................... |
89 |
|
3.7.13 |
power_on....................................................................................................................................................... |
90 |
|
3.7.14 |
preserve_mbr ................................................................................................................................................ |
90 |
|
3.7.15 |
recover_absolute_path ................................................................................................................................ |
90 |
|
3.7.16 |
recovery_point .............................................................................................................................................. |
91 |
|
3.7.17 |
target_disk ..................................................................................................................................................... |
91 |
|
4 |
|
|
Copyright © Acronis, Inc., 2000-2012 |
3.7.18 |
target_volume............................................................................................................................................... |
91 |
|
3.7.19 |
type................................................................................................................................................................. |
92 |
|
3.8 |
Mounting parameters.............................................................................................................. |
92 |
|
3.8.1 |
rw.................................................................................................................................................................... |
92 |
|
3.8.2 |
letter............................................................................................................................................................... |
93 |
|
3.8.3 |
mount_point.................................................................................................................................................. |
93 |
|
3.9 Acronis Secure Zone parameters............................................................................................. |
93 |
||
3.9.1 |
asz_size .......................................................................................................................................................... |
93 |
|
3.10 |
Filtering.................................................................................................................................... |
94 |
|
3.10.1 |
content_path................................................................................................................................................. |
94 |
|
3.10.2 |
content_type ................................................................................................................................................. |
94 |
|
3.10.3 |
filter_available_for_backup.......................................................................................................................... |
95 |
|
3.10.4 |
filter_date ...................................................................................................................................................... |
95 |
|
3.10.5 |
filter_guid....................................................................................................................................................... |
95 |
|
3.10.6 |
filter_host....................................................................................................................................................... |
95 |
|
3.10.7 |
filter_machines.............................................................................................................................................. |
96 |
|
3.10.8 |
filter_name .................................................................................................................................................... |
96 |
|
3.10.9 |
filter_state...................................................................................................................................................... |
96 |
|
3.10.10 |
filter_status.................................................................................................................................................... |
96 |
|
3.10.11 |
filter_type ...................................................................................................................................................... |
96 |
|
3.10.12 |
filter_user....................................................................................................................................................... |
97 |
|
3.11 |
General parameters................................................................................................................. |
97 |
|
3.11.1 |
credentials ..................................................................................................................................................... |
97 |
|
3.11.2 |
Error handling................................................................................................................................................ |
97 |
|
3.11.3 |
file_params .................................................................................................................................................... |
98 |
|
3.11.4 |
force_yes........................................................................................................................................................ |
98 |
|
3.11.5id 99
|
3.11.6 |
log................................................................................................................................................................... |
99 |
|
|
3.11.7 |
log_format ..................................................................................................................................................... |
99 |
|
|
3.11.8 |
oss_numbers ................................................................................................................................................. |
99 |
|
|
3.11.9 |
output............................................................................................................................................................. |
99 |
|
|
3.11.10 |
password...................................................................................................................................................... |
100 |
|
|
3.11.11 |
progress........................................................................................................................................................ |
100 |
|
|
3.11.12 |
reboot........................................................................................................................................................... |
100 |
|
|
3.11.13 |
silent_mode................................................................................................................................................. |
101 |
|
|
3.11.14 |
use_registry_defaults.................................................................................................................................. |
101 |
|
4 |
Usage examples................................................................................................................. |
101 |
||
|
4.1 |
Backup and recovery ............................................................................................................. |
101 |
|
|
4.1.1 |
Disks and volumes....................................................................................................................................... |
101 |
|
|
4.1.2 |
Files............................................................................................................................................................... |
104 |
|
|
4.1.3 |
Virtual machines.......................................................................................................................................... |
105 |
|
|
4.1.4 |
Microsoft Exchange..................................................................................................................................... |
106 |
|
|
4.2 |
Operations with archives and backups.................................................................................. |
108 |
|
|
4.2.1 |
Archives........................................................................................................................................................ |
108 |
|
|
4.2.2 |
Backups ........................................................................................................................................................ |
109 |
|
|
4.2.3 |
Mounting ..................................................................................................................................................... |
110 |
|
|
4.3 |
Operations with Acronis Secure Zone ................................................................................... |
111 |
|
|
4.4 |
Operations with Acronis Startup Recovery Manager ............................................................ |
112 |
|
|
4.5 |
Operations with tapes ........................................................................................................... |
112 |
|
|
4.6 |
Operations with vaults........................................................................................................... |
112 |
|
5 |
|
|
|
Copyright © Acronis, Inc., 2000-2012 |
4.7 |
Operations with disks ............................................................................................................ |
113 |
|
4.8 |
Administration operations..................................................................................................... |
113 |
|
4.8.1 |
Collecting information ................................................................................................................................ |
113 |
|
4.8.2 |
Plans ............................................................................................................................................................. |
113 |
|
4.8.3 |
Tasks............................................................................................................................................................. |
114 |
|
4.8.4 |
Licenses........................................................................................................................................................ |
114 |
|
4.9 |
Selecting logical volumes and MD devices for backup .......................................................... |
115 |
|
4.10 |
Scheduling backups under Linux using the cron service ....................................................... |
115 |
|
5 Comparison of the old and new command-line syntax ........................................................ |
116 |
||
6 acronis_encrypt utility ....................................................................................................... |
117 |
||
6 |
Copyright © Acronis, Inc., 2000-2012 |
1 Command-line utility overview
Acronis Backup & Recovery 11.5 supports the command-line interface with the acrocmd utility.
Unlike the trueimagecmd utility used in the older Acronis products, acrocmd does not contain any tools that physically execute the commands. It merely provides the command-line interface to Acronis Backup & Recovery 11.5 components—agents, storage nodes and the management server.
Once installed on a Windows or Linux machine, the acrocmd utility can be run from any folder or directory. This utility is also available when operating in both Linux-based and PE-based bootable media.
1.1Installation
Stand-alone editions of Acronis Backup & Recovery 11.5
If you have installed a stand-alone edition of Acronis Backup & Recovery 11.5, the command-line utility is already on your machine. Only local management of this machine is available. This means that any command or script for this machine can be run only locally.
Editions with centralized management
Advanced editions of Acronis Backup & Recovery 11.5 enable you to perform local, remote and centralized management (p. 10) of any machine where an Acronis Backup & Recovery 11.5 agent is installed.
As with Management Console, you install the command-line utility on the machine from which you prefer to operate (run commands or scripts). The machine may run Windows or Linux. Using the command-line utility, you can manage a Windows machine from a machine running Linux or vice versa.
Installation steps
In Linux, the command-line utility is installed by default with Management Console or Agent for Linux.
In Windows, you install the utility from the setup file as a separate component. To access this component in the installer, select the I want to manually select the Acronis components and customize the installation process check box. Or, you can extract and run the corresponding .msi file.
To install the command-line utility from the .msi file:
1.Run the Acronis Backup & Recovery 11.5 setup file.
2.Click Extract installation files.
3.Select the check box corresponding to the AcronisCommandLineTool.msi file.
4.Specify the folder where to extract the file.
5.Click Extract.
6.After the file is successfully extracted, click Finish.
7.Go to the folder where the AcronisCommandLineTool.msi file is extracted, and launch the file.
8.Follow the Install Wizard instructions on the screen.
7 |
Copyright © Acronis, Inc., 2000-2012 |

Installation paths
The default installation paths are:
%ProgramFiles%\Acronis\CommandLineTool (in 32-bit Windows)
%ProgramFiles(x86)%\Acronis\CommandLineTool (in 64-bit Windows)
/usr/lib/Acronis/CommandLineTool (in Linux)
1.2Backward compatibility and upgrade
Upgrading the command-line utility from Acronis Backup & Recovery 10
When you upgrade a stand-alone edition of Acronis Backup & Recovery 10 to Acronis Backup & Recovery 11.5, no additional actions are needed to upgrade the command-line utility.
When you upgrade an edition with centralized management, the software installs the command-line utility on every machine where an agent is installed. No additional actions are needed.
Backward compatibility
The Acronis Backup & Recovery 11.5 command-line utility is backward compatible with the Acronis Backup & Recovery 10 command-line utility. You can continue using the old syntax. Just type acrocmd instead of trueimagecmd.
To continue using your existing scripts, edit the scripts so that trueimagecmd is replaced with acrocmd. If your scripts contain the path to the trueimagecmd utility, replace it with the path to the acrocmd utility. Retain all other parameters and values.
Before switching to acrocmd, make sure that all the product components are upgraded. Acronis Backup & Recovery 10 does not support acrocmd.
Combination of the old and new syntaxes is acceptable within a script, but is not acceptable within a command string. When you create new scripts, we recommend that you use the new syntax.
Even when using the old syntax, logs and commands' output will appear in the new format.
Extensions of backup file names
The behavior of the /filename parameter with the backup commands is slightly different in Acronis Backup & Recovery 10 and Acronis Backup & Recovery 11.5. Unlike Acronis Backup & Recovery 10, where the extension of a backup file is exactly the same as you specify in the parameter value, Acronis Backup & Recovery 11.5 adds the *.tib extension to this value.
For example:
In Acronis Backup & Recovery 10, if you specify /filename:<path>my_backup.bak, the backup file name will be my_backup.bak
In Acronis Backup & Recovery 11.5, if you specify /filename:<path>my_backup.bak, the backup file name will be my_backup.bak.tib. However, if you specify
/filename:<path>my_backup.tib, the backup file name will also be my_backup.tib.
1.3Syntax
acrocmd has the following format:
8 |
Copyright © Acronis, Inc., 2000-2012 |

acrocmd <command> --<parameter 1>=<value list 1> … --<parameter N>=<value list N>
Typographic conventions
Descriptions of commands and parameters use the following specific typographic conventions.
Between angle brackets (<>) – information that the user must supply. Example: <IP address or hostname>
Between braces ({}); choices separated by pipe (|) – a set of choices from which the user must choose only one. Example: {on|off}.
Parameter values
For some parameters, you should specify only one value. The description of such value is written in the singular. For example, if you see --arc=<archive name>, specify only one archive name in this parameter.
For some parameters, you can enter one or more values. The description of such values is written in the plural. For example, if you see --volume=<volume numbers>, you can specify a list of volume numbers in this parameter.
Separators
A parameter name and a value list can be separated by either an equals sign or a space character. Values in a value list can be separated by either a comma or a space character.
Examples:
acrocmd backup disk --disk=1,2 acrocmd backup disk --disk=1 2 acrocmd backup disk --disk 1,2 acrocmd backup disk --disk 1 2
Enclosing parameter values that contain commas and space characters
General view |
Example |
|
|
"<value with space character>" |
--include="C:\my documents" |
|
|
\"<value with comma>\" |
--include=\"E:\Employees(A,B)\" |
|
|
"\"<value with space character and |
--include="\"D:\my photos\my wife, my kids |
comma>\"" |
and me\"" |
|
|
Files with input parameters
acrocmd supports files with input parameters. The contents of an input parameter file are concatenated with the parameters in the command line.
For example, the command
acrocmd backup disk -f params.txt
where the content of the file params.txt is
--disk=1 --loc=e:\my_backups |
--arc=archive123 |
equals to |
|
|
|
acrocmd backup disk --disk=1 |
--loc=e:\my_backups --arc=archive123 |
9 |
Copyright © Acronis, Inc., 2000-2012 |

1.4Local, remote and centralized management
Advanced editions of Acronis Backup & Recovery 11.5 enable you to perform local, remote and centralized management of any machine where an Acronis Backup & Recovery 11.5 agent is installed.
Local management
For local management, you install the command-line utility on the same machine where the Acronis Backup & Recovery 11.5 agent is installed. The operations are performed under the user account you are logged on with.
Example
To view all disks of the local machine, run the following command:
acrocmd list disks
Remote management
For remote management, you install the command-line utility on the machine from which you prefer to operate (run commands or scripts).
Along with the command, you specify:
the IP address or host name of the remote machine that has an Acronis Backup & Recovery 11.5 agent (--host)
credentials (a pair of user name and password) for access to that machine
The user whose credentials you specify must be a member of the Acronis Remote Users security group on that machine. The operations are performed under this user account.
Example
To view all disks of a remote machine, run the following command:
acrocmd list disks --host=<IP address or hostname> --credentials=<user name>,<password>
Centralized management
Commands on a machine
Through Acronis Backup & Recovery 11.5 Management Server, you can manage any registered machine using the credentials of the management server's administrator. Credentials for each remote machine are not required.
For a number of commands, you can specify comma-separated addresses of multiple machines. The operation will be executed on all the specified machines one after another.
Along with the command, you specify:
the IP address or host name of the machine that has an Acronis Backup & Recovery 11.5 agent (--address)
the IP address or host name of the management server (--host)
the name of the management server service (--service=ams)
credentials for access to the management server
10 |
Copyright © Acronis, Inc., 2000-2012 |
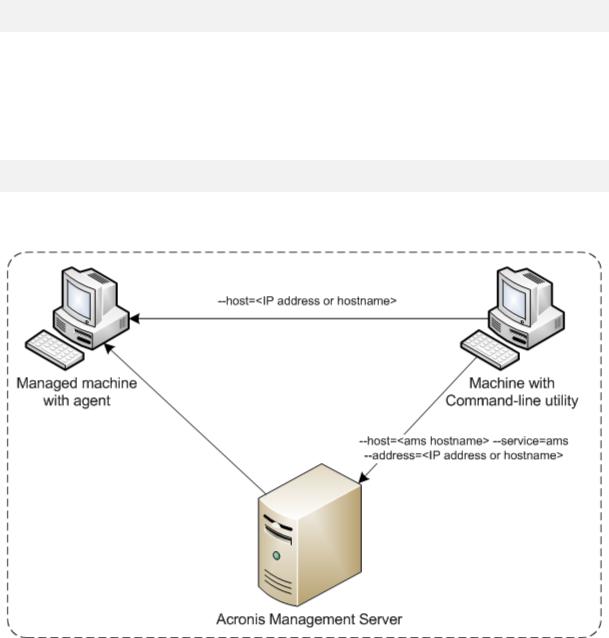
The user whose credentials you specify must be a member of the Acronis Centralized Admins security group on the management server. If you are running the command-line utility on a different machine, the user must also be a member of the Acronis Remote Users security group on the management server.
The operations on the machine are performed under the account of the agent service running on that machine (Acronis Agent User account).
Example
To view all disks of a machine through the management server, run the following command:
acrocmd list disks --host=<ams hostname> --credentials=<user name>,<password> --service=ams --address=<IP address or hostname>
Commands on the management server
There are commands that can be executed by the management server itself.
Example
To view the current activities of the management server, run the following command:
acrocmd list activities --host=<ams hostname> --credentials=<user name>,<password> --service=ams
The below diagram shows options of access to a managed machine directly or via Acronis Backup & Recovery 11.5 Management Server.
Options of access to a managed machine
11 |
Copyright © Acronis, Inc., 2000-2012 |

1.5Uninstallation
Uninstallation in Linux
In Linux, run the following commands to uninstall the command-line utility:
#cd /usr/lib/Acronis/CommandLineTool/uninstall
#./uninstall
To uninstall the command-line utility in the unattended mode, run the ./uninstall commands with the -a parameter.
Uninstallation in Windows
When you uninstall Acronis Backup & Recovery 11.5 by clicking Start -> All Programs -> Acronis -> Uninstall Acronis Backup & Recovery 11.5, the command-line utility is uninstalled along with all product components.
To uninstall the command-line utility separately from the product
1.Run the Acronis Backup & Recovery 11.5 setup file.
2.Click Extract installation files.
3.Select the check box corresponding to the AcronisCommandLineTool.msi file.
4.Specify the folder where to extract the file.
5.Click Extract.
6.After the file is successfully extracted, click Close.
7.Run the following command:
msiexec /uninstall <path>\AcronisCommandLineTool.msi /qb where <path> is the folder where the file is extracted.
If you have an edition with centralized management, you can also uninstall the command-line utility from the setup file. To do so, run the Acronis Backup & Recovery 11.5 setup file, click Install Acronis Backup & Recovery 11.5, then click Modify, and then clear the check box next to the name of the command-line utility.
1.6List of abbreviated names
This document uses the following abbreviated names.
AMS – Acronis Backup & Recovery 11.5 Management Server and this component's service.
MMS – Acronis Managed Machine Service, the service running on a machine where an Acronis agent is installed.
ASN – Acronis Backup & Recovery 11.5 Storage Node and this component's service.
Agent for ESX(i) – Acronis Backup & Recovery 11.5 Agent for VMware vSphere ESX(i).
12 |
Copyright © Acronis, Inc., 2000-2012 |
2 Commands
This section lists the supported commands and compatible parameters.
When using the command-line utility, you can view the information about the supported commands by means of the help (p. 17) command.
2.1Commands by services
2.1.1Disk, file, virtual machine backup
The following table summarizes the commands that can be executed by the Acronis services. For questions on how to connect to an Acronis service, please see the --service (p. 62) command description.
|
|
|
|
|
MMS |
|
|
|
|
|
|
|
|
|
|
|
|
|
Command |
AMS |
Agent for |
Agent for |
|
Agent for |
Bootable |
ASN |
|
Windows |
Linux |
|
ESX(i) or |
media |
|||
|
|
|
|
|
||||
|
|
|
|
|
|
Hyper-V |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Backup and recovery |
|
|
|
|
|
list disks (p. 17) |
|
+ |
+ |
|
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
backup disk (p. 18) |
|
+ |
+ |
|
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
recover disk (p. 19) |
|
+ |
+ |
|
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
recover mbr (p. 21) |
|
+ |
+ |
|
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
recover lvm_structure |
|
|
|
|
|
Linux-base |
|
|
|
|
|
|
|
d |
|
||
(p. 22) |
|
|
|
|
|
|
||
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
backup file (p. 23) |
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
recover file (p. 24) |
|
+ |
+ |
|
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
list vmservers (p. 25) |
+ |
|
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
list vms (p. 26) |
+ |
|
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
backup vm (p. 27) |
+* |
|
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
recover vm (p. 28) |
+* |
+ (create |
|
|
+ (create vm |
|
|
|
|
vm files) |
|
|
on a server) |
|
|
||
|
|
|
|
|
|
|
||
|
|
Operations with archives and backups |
|
|
||||
list archives (p. 36) |
+ |
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
export archive (p. 36) |
+ |
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
validate archive (p. 37) |
+ |
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
delete archive (p. 38) |
+ |
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
list backups (p. 38) |
+ |
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
list content (p. 39) |
+ |
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
validate backup (p. 40) |
+ |
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
13 |
|
|
|
|
Copyright © Acronis, Inc., 2000-2012 |
|||
|
|
|
|
|
|
MMS |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Command |
AMS |
Agent for |
Agent for |
|
Agent for |
Bootable |
ASN |
|
|
Windows |
Linux |
|
ESX(i) or |
media |
||||
|
|
|
|
|
|
||||
|
|
|
|
|
|
|
Hyper-V |
|
|
|
|
|
|
|
|
|
|
|
|
export backup (p. 40) |
+ |
|
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
replicate backup (p. 41) |
+ |
|
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
convert full (p. 42) |
+ |
|
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
consolidate backup (p. |
+ |
|
+ |
+ |
|
+ |
+ |
|
|
|
|
|
|
|
|
|
|
||
43) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
delete backup (p. 44) |
+ |
|
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
list mounts (p. 44) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
mount (p. 45) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
umount (p. 46) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
Operations with Acronis Secure Zone |
|
|
||||
create asz (p. 46) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
cleanup asz (p. 47) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
delete asz_files (p. 47) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
delete asz (p. 48) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
||
|
|
Operations with Acronis Startup Recovery Manager |
|
|
|||||
activate asrm (p. 49) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
deactivate asrm (p. 49) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Operations with tapes |
|
|
|
|
|
list tape_libraries (p. |
|
|
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
50) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
list tape_drives (p. 50) |
|
|
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Operations with vaults |
|
|
|
|
|
validate vault (p. 51) |
+ |
|
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Operations with disks |
|
|
|
|
|
clone disk (p. 52) |
|
|
+ |
+ |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Administration operations |
|
|
|||
get log (p. 52) |
+ |
|
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
list activities (p. 53) |
+ |
|
+ |
+ |
|
+ |
|
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
sysinfo (p. 54) |
+ |
|
+ |
+ |
|
+ |
+ |
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
list plans (p. 55) |
+ |
|
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
delete plan (p. 55) |
+ |
|
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
export plan (p. 56) |
+ |
|
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
import plan (p. 56) |
+ |
|
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
disable plan (p. 57) |
+ |
|
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
enable plan (p. 57) |
+ |
|
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
14 |
|
|
|
|
|
Copyright © Acronis, Inc., 2000-2012 |
|||
|
|
|
|
MMS |
|
|
|
|
|
|
|
|
|
|
|
Command |
AMS |
Agent for |
Agent for |
|
Agent for |
Bootable |
ASN |
Windows |
Linux |
|
ESX(i) or |
media |
|||
|
|
|
|
||||
|
|
|
|
|
Hyper-V |
|
|
|
|
|
|
|
|
|
|
list tasks (p. 58) |
+ |
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
run task (p. 59) |
+ |
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
stop task (p. 59) |
+ |
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
delete task (p. 60) |
+ |
+ |
+ |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
list licenses (p. 60) |
|
+ |
+ |
|
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
* The AMS service does not execute these commands by itself. It only defines which Agent for ESX(i) or Agent for Hyper-V can execute the command and transmits the command to the corresponding MMS.
2.1.2Application backup
The following table summarizes the commands that can be executed by the Acronis services. For questions on how to connect to an Acronis service, please see the --service (p. 62) command description.
|
|
|
|
|
|
MMS |
|
|
|
|
Command |
AMS |
|
|
|
|
|
ASN |
|
|
Agent for |
Reserved |
|
Reserved |
Reserved |
||||
|
|
|
|
|
|
||||
|
|
|
|
Exchange |
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Backup and recovery |
|
|
|
|
|
list |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
exchange_databases (p. |
|
|
|
|
|
|
|
|
|
30) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
list |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
exchange_mailboxes (p. |
|
|
|
|
|
|
|
|
|
30) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
backup |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
exchange_database (p. |
|
|
|
|
|
|
|
|
|
31) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
backup |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
exchange_mailbox (p. |
|
|
|
|
|
|
|
|
|
32) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
recover |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
exchange_database (p. |
|
|
|
|
|
|
|
|
|
33) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
recover |
|
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
exchange_mailbox (p. |
|
|
|
|
|
|
|
|
|
34) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Operations with archives and backups |
|
|
||||
list archives (p. 36) |
+ |
|
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
export archive (p. 36) |
+ |
|
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
validate archive (p. 37) |
+ |
|
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
delete archive (p. 38) |
+ |
|
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
15 |
|
|
|
|
|
Copyright © Acronis, Inc., 2000-2012 |
|||
|
|
|
|
|
MMS |
|
|
|
|
Command |
AMS |
|
|
|
|
|
ASN |
|
Agent for |
Reserved |
|
Reserved |
Reserved |
|||
|
|
|
|
|
||||
|
|
|
Exchange |
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
list backups (p. 38) |
+ |
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
list content (p. 39) |
+ |
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
validate backup (p. 40) |
+ |
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
export backup (p. 40) |
+ |
+* |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
replicate backup (p. 41) |
+ |
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
delete backup (p. 44) |
+ |
+** |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
Operations with tapes |
|
|
|
|
|
list tape_libraries (p. |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
50) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
list tape_drives (p. 50) |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
Operations with vaults |
|
|
|
|
|
validate vault (p. 51) |
+ |
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
Administration operations |
|
|
|||
get log (p. 52) |
+ |
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
list activities (p. 53) |
+ |
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
sysinfo (p. 54) |
+ |
+ |
|
|
|
|
+ |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
list plans (p. 55) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
delete plan (p. 55) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
export plan (p. 56) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
import plan (p. 56) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
disable plan (p. 57) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
enable plan (p. 57) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
list tasks (p. 58) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
run task (p. 59) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
stop task (p. 59) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
delete task (p. 60) |
+ |
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
list licenses (p. 60) |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
*When exporting a transaction log backup, the data from the entire backup chain (the full database backup plus the set of subsequent transaction log backups including the selected one) is copied to a single backup. Transaction log files will be applied to the database during recovery.
When exporting an incremental mailbox backup, the data from the backup chain (the full backup plus the set of the subsequent incremental mailbox backups including the selected one) is consolidated into a single backup.
**Backups that have no dependencies are deleted without any limitations. A backup that has dependencies cannot be deleted separately from its dependent backups.
16 |
Copyright © Acronis, Inc., 2000-2012 |
2.2help
The command provides the information about the supported commands.
Type acrocmd help to get the list of all available commands.
Type acrocmd help <text fragment> to get the list of all commands that begin with the fragment you specified.
For example, acrocmd help ba lists the following commands: backup disk, backup file, etc.
Type acrocmd help <complete command name> to view the information about this command.
For example, acrocmd help backup disk displays the information about the backup disk command.
2.3Backup and recovery
2.3.1Disks and volumes
The commands listed in this section can be executed on a machine where Agent for Windows or Agent for Linux is installed.
2.3.1.1list disks
Lists available disk groups, disks, volumes and unallocated space.
Examples (p. 101)
Parameters
Units of measurement
--size_measure={s|kb|mb|gb}
Measure of the size of disks and volumes. If not specified, the value is mb.
--start_measure={s|kb|mb|gb}
Measure of the offset of volumes. If not specified, the value is mb.
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99) {-f|--file_params}=<full local path> (p. 98)
Access to a remote machine (advanced editions only)
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
--address=<IP address or hostname> (p. 62)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
17 Copyright © Acronis, Inc., 2000-2012
Access to a virtual machine (Virtual edition only)
{--vmid=<virtual machine ID>|--vmname=<virtual machine name>|--vmconfig=<path>} (p. 63)
2.3.1.2backup disk
Creates a backup of the specified disks or volumes. If neither the --disk nor the --volume parameter is specified, the command backs up all volumes.
Examples (p. 101)
Parameters
What to back up
--disk=<disk numbers> (p. 71) --volume=<volume numbers> (p. 72)
--oss_numbers (p. 99) --exclude_hidden (p. 75) --exclude_mask=<masks> (p. 75) --exclude_names=<names> (p. 75) --exclude_system (p. 75)
Where to save the backup
--loc=<path> (p. 67)
--credentials=<user name>,<password>,encrypted (p. 97)
--arc=<archive name> (p. 67)
--password=<password>,encrypted (p. 100)
How to back up
--archive_comment=<comments> (p. 74) --backup_comment=<comments> (p. 74) --backuptype={full|incremental|differential} (p. 74) --cleanup (p. 74)
--fixed_drive (p. 77) --plain_archive (p. 78)
--raw (p. 78)
Backup options
--cataloging={full|fast} (p. 79) --compression={none|normal|high|max} (p. 80) --encryption={none|aes128|aes192|aes256} (p. 80) --fast (p. 81)
--force_yes (p. 98) --hdd_speed=<speed>{kb|p} (p. 81) --ignore_bad_sectors (p. 81) --multi_volume_snapshot={true|false} (p. 82) --network_speed=<speed>{kb|p} (p. 82) --post_cmd=<command> (p. 83) --pre_cmd=<command> (p. 83)
18 Copyright © Acronis, Inc., 2000-2012
--process_priority={low|normal|high} (p. 83) --reboot_after (p. 100)
--retry_count=<number of attempts> (p. 97)
--retry_delay=<delay> (p. 97) --silent_mode={on|off} (p. 101) --split=<size> (p. 84) --use_registry_defaults (p. 101)
--use_vss={none|auto|software_auto|software|hardware|acronis|native} (p. 85)
Tape management options
--tape_eject_successful (p. 84) --tape_full_empty (p. 84) --tape_overwrite (p. 84)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99)
--progress (p. 100)
{-f|--file_params}=<full local path> (p. 98)
Access to a remote machine (advanced editions only)
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
--address=<IP addresses or hostnames> (p. 62)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
2.3.1.3recover disk
Recovers the specified disk or volume. You can recover only one disk or volume at a time.
A disk is always recovered along with its MBR. When you recover a volume, the MBR is not recovered. You can use the recover mbr (p. 21) command in this case.
Examples (p. 101)
Parameters
What to recover
--loc=<path> (p. 67)
--credentials=<user name>,<password>,encrypted (p. 97)
--arc=<archive name> (p. 67)
--password=<password>,encrypted (p. 100)
--backup=<backup ID> (p. 68) --disk=<disk number> (p. 71)
--nt_signature={auto|new|backup|existing} (p. 71)
--volume=<volume number> (p. 72)
--oss_numbers (p. 99)
19 Copyright © Acronis, Inc., 2000-2012
Where to recover
--target_disk=<disk number> (p. 91) --target_volume=<volume number> (p. 91)
Recovering a disk
If the --target_disk parameter is specified, the software will recover to the specified disk.
If the --target_disk parameter is not specified, the software will first try to recover to the original disk, namely, to that very disk you backed up. If the original disk is not found, the command will fail.
Recovering a volume
If the --target_volume parameter is specified, the software will recover to the specified volume.
If the --target_volume parameter is not specified, and the --target_disk parameter is specified, the software will try to recover to the first unallocated space of a suitable size on the specified disk. If no unallocated space of a suitable size is found, the command will fail.
If neither the --target_volume parameter nor the --target_disk parameter is specified, the software will first try to recover to the original volume, namely, to that very volume you backed up. If the original volume is not found, the software will recover to the first unallocated space of a suitable size. If no unallocated space of a suitable size is found, the command will fail.
A volume will not be considered original if its size, location or other physical parameters have been changed after backup. Changing the volume letter or label does not prevent the software from recognizing the volume.
--start=<offset>{s|kb|mb|gb} (p. 73) --size=<volume size>{s|kb|mb|gb} (p. 73)
How to recover
--fat16_32 (p. 88) --ext2_3 (p. 88) --preserve_mbr (p. 90)
--type={active|primary|logical} (p. 92)
--active_restore
If the parameter is specified, the Acronis Active Restore technology is enabled.
Recovery options
--force_yes (p. 98) --reboot (p. 100) --reboot_after (p. 100)
--retry_count=<number of attempts> (p. 97)
--retry_delay=<delay> (p. 97) --silent_mode={on|off} (p. 101) --use_registry_defaults (p. 101)
Acronis Universal Restore parameters
--ur_driver=<INF file name>
Specifies using Acronis Universal Restore and the mass storage driver to be installed.
--ur_path=<search folder>
20 Copyright © Acronis, Inc., 2000-2012
Specifies using Acronis Universal Restore and the path to the driver storage.
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99)
--progress (p. 100)
{-f|--file_params}=<full local path> (p. 98)
Access to a remote machine (advanced editions only)
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
--address=<IP addresses or hostnames> (p. 62)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
2.3.1.4recover mbr
Recovers the MBR from a disk or volume backup.
Examples (p. 101)
Parameters
What to recover
--loc=<path> (p. 67)
--credentials=<user name>,<password>,encrypted (p. 97)
--arc=<archive name> (p. 67)
--password=<password>,encrypted (p. 100)
--backup=<backup ID> (p. 68) --disk=<disk number> (p. 71)
Where to recover
--target_disk=<disk number> (p. 91)
Recovery options
--force_yes (p. 98) --reboot (p. 100) --reboot_after (p. 100)
--retry_count=<number of attempts> (p. 97)
--retry_delay=<delay> (p. 97) --silent_mode={on|off} (p. 101)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99) {-f|--file_params}=<full local path> (p. 98)
21 Copyright © Acronis, Inc., 2000-2012

Access to a remote machine (advanced editions only)
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
--address=<IP addresses or hostnames> (p. 62)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
2.3.1.5recover lvm_structure
Creates the same logical volume structure on the specified machine as in the backed up system. Use this command if you need to recover a Linux system, along with its software RAID or LVM structure, to a machine with different logical volume structure or without logical volumes.
The specified machine must be booted with Linux-based bootable media. Before executing the command, make sure that the machine has enough disks that are as big or bigger than the original disks. Execute the command prior to the recover disk (p. 19) command. Then, recover each volume to the corresponding volume of the target machine.
Caution: As a result of this command execution, the current volume structure on the machine will be replaced with the one stored in the backup. This will destroy the data that is currently stored on some or all of the machine's hard disks.
Examples (p. 101)
Parameters
What to recover
--loc=<path> (p. 67)
--credentials=<user name>,<password>,encrypted (p. 97)
--arc=<archive name> (p. 67)
--password=<password>,encrypted (p. 100)
--backup=<backup ID> (p. 68)
Recovery options
--force_yes (p. 98)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99)
--progress (p. 100)
{-f|--file_params}=<full local path> (p. 98)
Access to a remote machine (advanced editions only)
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
22 |
Copyright © Acronis, Inc., 2000-2012 |
2.3.2Files
The commands listed in this section can be executed on a machine where Agent for Windows or Agent for Linux is installed.
2.3.2.1backup file
Creates a backup of specified files and folders.
Examples (p. 104)
Parameters
What to back up
--include=<paths> (p. 77) --exclude_hidden (p. 75) --exclude_mask=<masks> (p. 75) --exclude_names=<names> (p. 75) --exclude_system (p. 75)
Where to save the backup
--loc=<path> (p. 67)
--credentials=<user name>,<password>,encrypted (p. 97)
--arc=<archive name> (p. 67)
--password=<password>,encrypted (p. 100)
How to back up
--archive_comment=<comments> (p. 74) --backup_comment=<comments> (p. 74) --backuptype={full|incremental|differential} (p. 74) --cleanup (p. 74)
--fixed_drive (p. 77) --plain_archive (p. 78)
Backup options
--cataloging={full|fast} (p. 79) --compression={none|normal|high|max} (p. 80) --encryption={none|aes128|aes192|aes256} (p. 80) --force_yes (p. 98)
--hdd_speed=<speed>{kb|p} (p. 81) --ignore_bad_sectors (p. 81) --multi_volume_snapshot={true|false} (p. 82) --network_speed=<speed>{kb|p} (p. 82) --post_cmd=<command> (p. 83) --pre_cmd=<command> (p. 83) --process_priority={low|normal|high} (p. 83) --reboot_after (p. 100)
--retry_count=<number of attempts> (p. 97)
--retry_delay=<delay> (p. 97) --silent_mode={on|off} (p. 101)
23 Copyright © Acronis, Inc., 2000-2012
--snapshot={always|possible|none} (p. 84) --split=<size> (p. 84) --use_registry_defaults (p. 101)
--use_vss={none|auto|software_auto|software|hardware|acronis|native} (p. 85)
Tape management options
--tape_eject_successful (p. 84) --tape_full_empty (p. 84) --tape_overwrite (p. 84)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99)
--progress (p. 100)
{-f|--file_params}=<full local path> (p. 98)
Access to a remote machine (advanced editions only)
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
--address=<IP addresses or hostnames> (p. 62)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
2.3.2.2recover file
Recovers files and folders from a file-level or disk-level backup.
Examples (p. 104)
Parameters
What to recover
--loc=<path> (p. 67)
--credentials=<user name>,<password>,encrypted (p. 97)
--arc=<archive name> (p. 67)
--password=<password>,encrypted (p. 100)
--backup=<backup ID> (p. 68)
--file=<paths> (p. 88)
--exclude=<files, folders and masks> (p. 87)
Where to recover
--target=<path> (p. 69)
--credentials=<user name>,<password>,encrypted (p. 97)
How to recover
24 |
Copyright © Acronis, Inc., 2000-2012 |
--overwrite={always|older|never} (p. 89) --recover_absolute_path (p. 90)
--recover_security={true|false}
This parameter is effective only when recovering from a file-level backup of Windows files. If the value is true or if the parameter is not specified, recover NTFS permissions for files along with the files themselves. Otherwise, the files will inherit the NTFS permissions from the folder to which they will be recovered.
--original_date
Recover files' original date and time from the backup. If not specified, the current date and time are assigned.
Recovery options
--force_yes (p. 98) --reboot (p. 100) --reboot_after (p. 100)
--retry_count=<number of attempts> (p. 97)
--retry_delay=<delay> (p. 97) --silent_mode={on|off} (p. 101) --use_registry_defaults (p. 101)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99)
--progress (p. 100)
{-f|--file_params}=<full local path> (p. 98)
Access to a remote machine (advanced editions only)
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
--address=<IP address or hostnames> (p. 62)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
2.3.3Virtual machines
The commands listed in this section are available in the Acronis Backup & Recovery 11.5 Virtual Edition only if Agent for ESX(i) or Agent for Hyper-V is installed. (This does not apply to the recover vm (p. 28) command.)
2.3.3.1list vmservers
Lists virtualization servers and server clusters that are present on the specified management server or that are accessible to Agent for ESX(i).
Examples (p. 105)
25 |
Copyright © Acronis, Inc., 2000-2012 |
Parameters
--filter_guid=<GUIDs> (p. 95) --filter_name=<names> (p. 96)
--filter_machines=<quantities of machines> (p. 96)
--filter_type=<server types> (p. 96)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99) {-f|--file_params}=<full local path> (p. 98)
Access to a remote machine (advanced editions only)
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
--address=<IP addresses or hostnames> (p. 62)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
2.3.3.2list vms
Lists virtual machines that are present on the specified management server or that are managed by Agent for ESX(i) or Agent for Hyper-V, depending on the service that will execute the command.
Examples (p. 105)
Parameters
--filter_available_for_backup={true|false} (p. 95) --filter_guid=<GUIDs> (p. 95) --filter_host=<hostnames> (p. 95) --filter_name=<names> (p. 96) --filter_state=<states> (p. 96) --filter_status=<statuses> (p. 96)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99) {-f|--file_params}=<full local path> (p. 98)
Access to a remote machine (advanced editions only)
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
26 Copyright © Acronis, Inc., 2000-2012
2.3.3.3backup vm
Creates a backup of specified disks and volumes of the specified virtual machines. If neither --disk nor --volume parameter is specified, the command backs up the entire machine.
Examples (p. 105)
Parameters
Access to a virtual machine
{--vmid=<virtual machine IDs>|--vmname=<virtual machine names>|--vmconfig=<paths>} (p. 63)
You can specify one or more virtual machines to be backed up.
--simultaneous_backup=<number>
Number of virtual machines to be backed up simultaneously by Agent for ESX(i) or Agent for Hyper-V. If not specified, each agent will back up virtual machines two at a time simultaneously. To back up machines one at a time, set the parameter value to 1.
What to back up
--disk=<disk numbers> (p. 71) --volume=<volume numbers> (p. 72)
--exclude_hidden (p. 75) --exclude_mask=<masks> (p. 75) --exclude_names=<names> (p. 75) --exclude_system (p. 75)
Where to save the backup
--loc=<path> (p. 67)
--credentials=<user name>,<password>,encrypted (p. 97)
--arc=<archive name> (p. 67)
--password=<password>,encrypted (p. 100)
How to back up
--archive_comment=<comments> (p. 74) --backup_comment=<comments> (p. 74) --backuptype={full|incremental|differential} (p. 74) --cleanup (p. 74)
--raw (p. 78)
Backup options
--cataloging={full|fast} (p. 79) --cbt_mode={on_if_enabled|on|off} (p. 79) --compression={none|normal|high|max} (p. 80) --encryption={none|aes128|aes192|aes256} (p. 80) --fast (p. 81)
--force_yes (p. 98) --hdd_speed=<speed>{kb|p} (p. 81) --network_speed=<speed>{kb|p} (p. 82) --process_priority={low|normal|high} (p. 83)
27 Copyright © Acronis, Inc., 2000-2012

--retry_count=<number of attempts> (p. 97)
--retry_delay=<delay> (p. 97) --silent_mode={on|off} (p. 101) --split=<size> (p. 84) --use_registry_defaults (p. 101)
Tape management options
--tape_eject_successful (p. 84) --tape_full_empty (p. 84) --tape_overwrite (p. 84)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99)
--progress (p. 100)
{-f|--file_params}=<full local path> (p. 98)
Access to a remote physical machine
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
2.3.3.4recover vm
Recovers a disk or volume backup onto a new or existing virtual machine. The recover vm command replaces and enhances the convert command which was available in earlier versions of the Acronis software.
The recover vm command can be executed by the following agents:
Agent for ESX(i) recovers a disk (volume) backup to a new or existing ESX(i) virtual machine.
Agent for Hyper-V recovers a disk (volume) backup to a new or existing Hyper-V virtual machine.
Agent for Windows recovers a disk (volume) backup to a new virtual machine of any of the following types: VMware Workstation, Microsoft Virtual PC, Parallels Workstation or Citrix XenServer Open Virtual Appliance (OVA).
Files of the fully configured and operational machine will be placed in the folder you select. You can start the machine using the respective virtualization software or prepare the machine files for further usage. The OVA virtual appliance can be imported to XenServer. Disks of a Virtual PC can be attached to a Hyper-V virtual machine.
A virtual machine must be powered off during the recovery to this machine. The target machine located on an ESX(i) or Hyper-V host will be powered off without a prompt. Please be sure to specify the correct machine.
Examples (p. 105)
Parameters
What to recover
28 |
Copyright © Acronis, Inc., 2000-2012 |
--loc=<path> (p. 67)
--credentials=<user name>,<password>,encrypted (p. 97)
--arc=<archive name> (p. 67)
--password=<password>,encrypted (p. 100)
--backup=<backup ID> (p. 68) --disk=<disk number> (p. 71) --volume=<volume number> (p. 72)
Where to recover
If you want to recover to an existing virtual machine:
{--vmid=<virtual machine ID>|--vmname=<virtual machine name>|--vmconfig=<path>} (p. 63)
If you want to recover to a new virtual machine:
--vmname=<virtual machine name> (p. 64)
--vmtype={vmware|virtualpc|parallels|citrix|redhat|xen} (p. 64) {--vmserver_name=<server name>|--vmserver_id=<server GUID>} (p. 64) --vmstorage=<path> (p. 64)
--credentials=<user name>,<password>,encrypted (p. 97)
Credentials for a network folder where a vmware, virtualpc, parallels, citrix, redhat, or xen virtual machine is to be created.
--target_disk=<disk number> (p. 91) --target_volume=<volume number> (p. 91) --start=<offset>{s|kb|mb|gb} (p. 73) --size=<volume size>{s|kb|mb|gb} (p. 73)
How to recover
--ext2_3 (p. 88) --fat16_32 (p. 88) --preserve_mbr (p. 90)
--type={active|primary|logical} (p. 92)
Recovery options
--force_yes (p. 98) --power_on (p. 90)
--retry_count=<number of attempts> (p. 97)
--retry_delay=<delay> (p. 97) --silent_mode={on|off} (p. 101) --use_registry_defaults (p. 101)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99)
--progress (p. 100)
{-f|--file_params}=<full local path> (p. 98)
Access to a remote machine (advanced editions only)
29 Copyright © Acronis, Inc., 2000-2012
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
Access to a specific service within a machine (advanced editions only)
--service={mms|ams} (p. 62)
2.3.4Microsoft Exchange
The commands listed in this section can be executed on a machine where Agent for Microsoft Exchange Server is installed.
2.3.4.1list exchange_databases
Lists storage groups (for Exchange 2003/2007) and databases.
Examples (p. 106)
Parameters
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99) {-f|--file_params}=<full local path> (p. 98)
--exchange_credentials=<user name>,<password>,encrypted (p. 65)
Access to a remote machine
--host=<IP address or hostname> (p. 62)
--credentials=<user name>,<password>,encrypted (p. 97)
--address=<IP address or hostname> (p. 62)
Access to a specific service within a machine
--service={mms|ams} (p. 62)
2.3.4.2list exchange_mailboxes
Lists mailboxes and public folders in the specified Exchange database.
Examples (p. 106)
Parameters
--mailbox_location=<path> (p. 70) --filter_name=<names> (p. 96)
General parameters
--log=<full path> (p. 99)
--log_format={structured|unstructured} (p. 99) --output={formatted|raw} (p. 99) {-f|--file_params}=<full local path> (p. 98)
--exchange_credentials=<user name>,<password>,encrypted (p. 65)
30 Copyright © Acronis, Inc., 2000-2012
 Loading...
Loading...