Acronis Backup 12.5 User Guide

Acronis Backup 12.5
Update 1
USER GUIDE
Table of contents
1 |
What's new in Acronis Backup.......................................................................................... |
7 |
|
1.1 |
What's new in Update 1 ............................................................................................................ |
7 |
|
1.2 |
What's new in Acronis Backup 12.5........................................................................................... |
7 |
|
2 |
Installation ...................................................................................................................... |
9 |
|
2.1 |
Installation overview ................................................................................................................. |
9 |
|
2.2 |
Components............................................................................................................................. |
11 |
|
2.3 |
Software requirements............................................................................................................ |
13 |
|
2.3.1 |
Supported web browsers ............................................................................................................................. |
13 |
|
2.3.2 Supported operating systems and environments ...................................................................................... |
14 |
||
2.3.3 Supported Microsoft SQL Server versions................................................................................................... |
17 |
||
2.3.4 Supported Microsoft Exchange Server versions......................................................................................... |
17 |
||
2.3.5 Supported Microsoft SharePoint versions .................................................................................................. |
17 |
||
2.3.6 Supported Oracle Database versions .......................................................................................................... |
17 |
||
2.3.7 |
Supported virtualization platforms.............................................................................................................. |
18 |
|
2.3.8 |
Linux packages............................................................................................................................................... |
20 |
|
2.3.9 Compatibility with encryption software...................................................................................................... |
22 |
||
2.4 |
System requirements............................................................................................................... |
23 |
|
2.5 |
Supported file systems ............................................................................................................ |
24 |
|
2.6 |
On-premise deployment.......................................................................................................... |
26 |
|
2.6.1 Installing the management server ............................................................................................................... |
26 |
||
2.6.2 Adding machines via the web interface ...................................................................................................... |
29 |
||
2.6.3 |
Installing agents locally ................................................................................................................................. |
33 |
|
2.6.4 |
Managing licenses......................................................................................................................................... |
37 |
|
2.7 |
Cloud deployment ................................................................................................................... |
38 |
|
2.7.1 |
Preparation.................................................................................................................................................... |
38 |
|
2.7.2 |
Proxy server settings..................................................................................................................................... |
39 |
|
2.7.3 |
Installing agents............................................................................................................................................. |
40 |
|
2.7.4 |
Activating the account .................................................................................................................................. |
41 |
|
2.8 |
Deploying agents through Group Policy.................................................................................. |
42 |
|
2.9 |
Updating agents....................................................................................................................... |
43 |
|
2.10 |
Uninstalling the product .......................................................................................................... |
43 |
|
3 |
Accessing the backup console......................................................................................... |
45 |
|
3.1 |
Configuring a web browser for Integrated Windows Authentication ..................................... |
45 |
|
3.1.1 Adding the console to the list of local intranet sites .................................................................................. |
46 |
||
3.1.2 Adding the console to the list of trusted sites............................................................................................. |
48 |
||
4 |
Backup console views .................................................................................................... |
51 |
|
5 |
Backup .......................................................................................................................... |
52 |
|
5.1 |
Backup plan cheat sheet.......................................................................................................... |
53 |
|
5.2 |
Selecting data to back up......................................................................................................... |
56 |
|
5.2.1 |
Selecting files/folders.................................................................................................................................... |
56 |
|
5.2.2 |
Selecting system state .................................................................................................................................. |
57 |
|
5.2.3 |
Selecting disks/volumes................................................................................................................................ |
58 |
|
5.2.4 |
Selecting ESXi configuration ......................................................................................................................... |
60 |
|
2 |
|
Copyright © Acronis International GmbH, 2002-2017 |
|
5.3 |
Selecting a destination............................................................................................................. |
60 |
|
5.3.1 |
About Secure Zone........................................................................................................................................ |
62 |
|
5.4 |
Schedule................................................................................................................................... |
64 |
|
5.4.1 |
Schedule by events ....................................................................................................................................... |
66 |
|
5.4.2 |
Start conditions ............................................................................................................................................. |
67 |
|
5.5 |
Retention rules ........................................................................................................................ |
70 |
|
5.6 |
Encryption................................................................................................................................ |
71 |
|
5.7 |
Notarization ............................................................................................................................. |
72 |
|
5.8 Conversion to a virtual machine.............................................................................................. |
73 |
||
5.8.1 |
Conversion to a virtual machine in a backup plan...................................................................................... |
74 |
|
5.9 |
Replication ............................................................................................................................... |
75 |
|
5.9.1 |
Considerations for users with the Advanced license.................................................................................. |
76 |
|
5.10 Starting a backup manually ..................................................................................................... |
76 |
||
5.11 |
Backup options ........................................................................................................................ |
77 |
|
5.11.1 |
Alerts .............................................................................................................................................................. |
79 |
|
5.11.2 |
Backup consolidation.................................................................................................................................... |
79 |
|
5.11.3 |
Backup file name........................................................................................................................................... |
79 |
|
5.11.4 |
Backup format ............................................................................................................................................... |
82 |
|
5.11.5 |
Backup validation .......................................................................................................................................... |
83 |
|
5.11.6 |
Backup start conditions ................................................................................................................................ |
84 |
|
5.11.7 |
Changed block tracking (CBT)....................................................................................................................... |
84 |
|
5.11.8 |
Cluster backup mode .................................................................................................................................... |
84 |
|
5.11.9 |
Compression level......................................................................................................................................... |
86 |
|
5.11.10 |
Email notifications......................................................................................................................................... |
86 |
|
5.11.11 |
Error handling................................................................................................................................................ |
86 |
|
5.11.12 |
Fast incremental/differential backup .......................................................................................................... |
87 |
|
5.11.13 |
File filters........................................................................................................................................................ |
88 |
|
5.11.14 |
File-level backup snapshot ........................................................................................................................... |
89 |
|
5.11.15 |
File-level security........................................................................................................................................... |
89 |
|
5.11.16 |
Log truncation................................................................................................................................................ |
90 |
|
5.11.17 |
LVM snapshotting ......................................................................................................................................... |
90 |
|
5.11.18 |
Mount points................................................................................................................................................. |
90 |
|
5.11.19 |
Multi-volume snapshot................................................................................................................................. |
91 |
|
5.11.20 |
Performance.................................................................................................................................................. |
91 |
|
5.11.21 |
Pre/Post commands...................................................................................................................................... |
92 |
|
5.11.22 |
Pre/Post data capture commands............................................................................................................... |
94 |
|
5.11.23 |
SAN hardware snapshots.............................................................................................................................. |
95 |
|
5.11.24 |
Scheduling...................................................................................................................................................... |
95 |
|
5.11.25 |
Sector-by-sector backup............................................................................................................................... |
96 |
|
5.11.26 |
Splitting .......................................................................................................................................................... |
96 |
|
5.11.27 |
Tape management........................................................................................................................................ |
97 |
|
5.11.28 |
Task failure handling ..................................................................................................................................... |
99 |
|
5.11.29 |
Volume Shadow Copy Service (VSS) ............................................................................................................ |
99 |
|
5.11.30 |
Volume Shadow Copy Service (VSS) for virtual machines ....................................................................... |
100 |
|
5.11.31 |
Weekly backup ............................................................................................................................................ |
100 |
|
5.11.32 |
Windows event log ..................................................................................................................................... |
100 |
|
6 |
Recovery ..................................................................................................................... |
101 |
|
6.1 |
Recovery cheat sheet............................................................................................................. |
101 |
|
6.2 |
Creating bootable media ....................................................................................................... |
101 |
|
6.3 |
Recovering a machine............................................................................................................ |
102 |
|
6.3.1 |
Physical machine......................................................................................................................................... |
102 |
|
3 |
|
Copyright © Acronis International GmbH, 2002-2017 |
|
6.3.2 |
Physical machine to virtual......................................................................................................................... |
|
104 |
|
6.3.3 |
Virtual machine ........................................................................................................................................... |
|
106 |
|
6.3.4 |
Recovering disks by using bootable media ............................................................................................... |
|
107 |
|
6.3.5 |
Using Universal Restore.............................................................................................................................. |
|
108 |
|
6.4 |
Recovering files...................................................................................................................... |
|
110 |
|
6.4.1 |
Recovering files by using the web interface.............................................................................................. |
|
110 |
|
6.4.2 |
Downloading files from the cloud storage ................................................................................................ |
|
111 |
|
6.4.3 |
Verifying file authenticity with Notary Service.......................................................................................... |
|
112 |
|
6.4.4 |
Signing a file with ASign .............................................................................................................................. |
|
113 |
|
6.4.5 |
Recovering files by using bootable media................................................................................................. |
|
114 |
|
6.4.6 |
Extracting files from local backups............................................................................................................. |
|
114 |
|
6.5 |
Recovering system state........................................................................................................ |
|
115 |
|
6.6 |
Recovering ESXi configuration............................................................................................... |
|
115 |
|
6.7 |
Recovery options ................................................................................................................... |
|
116 |
|
6.7.1 |
Backup validation ........................................................................................................................................ |
|
117 |
|
6.7.2 |
Date and time for files ................................................................................................................................ |
|
117 |
|
6.7.3 |
Error handling.............................................................................................................................................. |
|
117 |
|
6.7.4 |
File exclusions.............................................................................................................................................. |
|
118 |
|
6.7.5 |
File-level security......................................................................................................................................... |
|
118 |
|
6.7.6 |
Flashback...................................................................................................................................................... |
|
118 |
|
6.7.7 |
Full path recovery........................................................................................................................................ |
|
118 |
|
6.7.8 |
Mount points............................................................................................................................................... |
|
119 |
|
6.7.9 |
Performance................................................................................................................................................ |
|
119 |
|
6.7.10 |
Pre/Post commands.................................................................................................................................... |
|
119 |
|
6.7.11 |
SID changing ................................................................................................................................................ |
|
120 |
|
6.7.12 |
VM power management ............................................................................................................................ |
|
121 |
|
6.7.13 |
Windows event log ..................................................................................................................................... |
|
121 |
|
7 |
Operations with backups ............................................................................................. |
|
121 |
|
7.1 |
The Backups tab..................................................................................................................... |
|
121 |
|
7.2 |
Mounting volumes from a backup......................................................................................... |
|
122 |
|
7.3 |
Deleting backups.................................................................................................................... |
|
123 |
|
8 |
Operations with backup plans ...................................................................................... |
|
124 |
|
9 |
The Plans tab ............................................................................................................... |
|
124 |
|
9.1 |
Off-host data processing........................................................................................................ |
|
125 |
|
9.1.1 |
Backup replication....................................................................................................................................... |
|
125 |
|
9.1.2 |
Validation..................................................................................................................................................... |
|
126 |
|
9.1.3 |
Cleanup ........................................................................................................................................................ |
|
128 |
|
9.1.4 |
Conversion to a virtual machine ................................................................................................................ |
|
129 |
|
10 |
Bootable media ........................................................................................................... |
|
130 |
|
10.1 |
Bootable Media Builder......................................................................................................... |
|
130 |
|
10.1.1 |
Linux-based bootable media...................................................................................................................... |
|
130 |
|
10.1.2 |
WinPE-based bootable media.................................................................................................................... |
|
141 |
|
10.2 |
Connecting to a machine booted from media....................................................................... |
|
144 |
|
10.3 |
Registering media on the management server ..................................................................... |
145 |
||
10.4 |
Configuring iSCSI and NDAS devices...................................................................................... |
|
146 |
|
10.5 |
Startup Recovery Manager.................................................................................................... |
|
147 |
|
10.6 |
Acronis PXE Server................................................................................................................. |
|
148 |
|
4 |
|
|
Copyright © Acronis International GmbH, 2002-2017 |
|
10.6.1 Installing Acronis PXE Server ...................................................................................................................... |
148 |
||
10.6.2 Setting up a machine to boot from PXE .................................................................................................... |
149 |
||
10.6.3 |
Work across subnets................................................................................................................................... |
149 |
|
11 |
Protecting mobile devices ............................................................................................ |
150 |
|
12 |
Protecting Microsoft applications................................................................................. |
154 |
|
12.1 |
Prerequisites.......................................................................................................................... |
155 |
|
12.2 |
Database backup.................................................................................................................... |
156 |
|
12.2.1 |
Selecting SQL databases ............................................................................................................................. |
157 |
|
12.2.2 Selecting Exchange Server data ................................................................................................................. |
157 |
||
12.2.3 Protecting Always On Availability Groups (AAG) ...................................................................................... |
158 |
||
12.2.4 Protecting Database Availability Groups (DAG)........................................................................................ |
159 |
||
12.3 |
Application-aware backup ..................................................................................................... |
161 |
|
12.3.1 |
Required user rights.................................................................................................................................... |
161 |
|
12.4 |
Mailbox backup...................................................................................................................... |
162 |
|
12.4.1 Selecting Exchange Server mailboxes........................................................................................................ |
162 |
||
12.5 |
Recovering SQL databases..................................................................................................... |
163 |
|
12.5.1 |
Recovering system databases .................................................................................................................... |
165 |
|
12.5.2 Attaching SQL Server databases ................................................................................................................ |
165 |
||
12.6 |
Recovering Exchange databases............................................................................................ |
166 |
|
12.6.1 Mounting Exchange Server databases ...................................................................................................... |
167 |
||
12.7 |
Recovering Exchange mailboxes and mailbox items ............................................................. |
168 |
|
12.7.1 |
Recovering mailboxes................................................................................................................................. |
169 |
|
12.7.2 |
Recovering mailbox items .......................................................................................................................... |
170 |
|
12.8 |
Changing the SQL Server or Exchange Server access credentials.......................................... |
172 |
|
13 |
Protecting Office 365 mailboxes ................................................................................... |
172 |
|
13.1 |
Selecting Office 365 mailboxes.............................................................................................. |
173 |
|
13.2 |
Recovering Office 365 mailboxes and mailbox items............................................................ |
174 |
|
13.2.1 |
Recovering mailboxes................................................................................................................................. |
174 |
|
13.2.2 |
Recovering mailbox items .......................................................................................................................... |
174 |
|
13.3 |
Changing the Office 365 access credentials .......................................................................... |
175 |
|
14 |
Protecting Oracle Database.......................................................................................... |
175 |
|
15 |
Active Protection ......................................................................................................... |
175 |
|
16 |
Special operations with virtual machines...................................................................... |
177 |
|
16.1 |
Running a virtual machine from a backup (Instant Restore)................................................. |
177 |
|
16.1.1 |
Running the machine.................................................................................................................................. |
177 |
|
16.1.2 |
Deleting the machine.................................................................................................................................. |
178 |
|
16.1.3 |
Finalizing the machine ................................................................................................................................ |
179 |
|
16.2 |
Working in VMware vSphere................................................................................................. |
179 |
|
16.2.1 Replication of virtual machines.................................................................................................................. |
179 |
||
16.2.2 |
LAN-free backup.......................................................................................................................................... |
184 |
|
16.2.3 Using SAN hardware snapshots ................................................................................................................. |
187 |
||
16.2.4 Using a locally attached storage................................................................................................................. |
191 |
||
16.2.5 |
Virtual machine binding.............................................................................................................................. |
192 |
|
16.2.6 Changing the vSphere access credentials.................................................................................................. |
194 |
||
16.2.7 Agent for VMware - necessary privileges.................................................................................................. |
194 |
||
16.3 |
Machine migration................................................................................................................. |
197 |
|
5 |
|
Copyright © Acronis International GmbH, 2002-2017 |
|
16.4 |
Windows Azure and Amazon EC2 virtual machines .............................................................. |
197 |
|
17 |
Monitoring and reporting............................................................................................. |
198 |
|
17.1 |
Dashboard.............................................................................................................................. |
198 |
|
17.2 |
Reports................................................................................................................................... |
199 |
|
17.3 |
Configuring the severity of alerts .......................................................................................... |
201 |
|
18 |
Device groups .............................................................................................................. |
202 |
|
18.1 |
Creating a static group........................................................................................................... |
203 |
|
18.2 |
Adding devices to static groups............................................................................................. |
203 |
|
18.3 |
Creating a dynamic group...................................................................................................... |
204 |
|
18.4 |
Applying a backup plan to a group ........................................................................................ |
207 |
|
19 |
Advanced storage options............................................................................................ |
207 |
|
19.1 |
Tape devices .......................................................................................................................... |
207 |
|
19.1.1 What is a tape device?................................................................................................................................ |
207 |
||
19.1.2 Overview of tape support........................................................................................................................... |
208 |
||
19.1.3 Getting started with a tape device............................................................................................................. |
212 |
||
19.1.4 |
Tape management...................................................................................................................................... |
216 |
|
19.2 |
Storage nodes ........................................................................................................................ |
224 |
|
19.2.1 Installing a storage node and a catalog service ........................................................................................ |
224 |
||
19.2.2 Adding a managed location........................................................................................................................ |
225 |
||
19.2.3 |
Location encryption .................................................................................................................................... |
226 |
|
19.2.4 |
Deduplication best practices ...................................................................................................................... |
227 |
|
19.2.5 |
Data catalog................................................................................................................................................. |
229 |
|
19.2.6 |
Cataloging best practices............................................................................................................................ |
230 |
|
20 |
System settings............................................................................................................ |
230 |
|
20.1 |
Email server ........................................................................................................................... |
230 |
|
20.2 |
Email notifications ................................................................................................................. |
231 |
|
20.3 |
Default backup options.......................................................................................................... |
232 |
|
21 |
Administering user accounts and organization units ..................................................... |
232 |
|
21.1 |
On-premise deployment........................................................................................................ |
232 |
|
21.1.1 |
Administrators and units ............................................................................................................................ |
233 |
|
21.1.2 |
Adding administrators ................................................................................................................................ |
234 |
|
21.1.3 |
Creating units............................................................................................................................................... |
235 |
|
21.2 |
Cloud deployment ................................................................................................................. |
235 |
|
22 |
Troubleshooting .......................................................................................................... |
236 |
|
23 |
Glossary ...................................................................................................................... |
238 |
|
6 |
Copyright © Acronis International GmbH, 2002-2017 |

1 What's new in Acronis Backup
1.1 What's new in Update 1
Support for Citrix XenServer 7.0, 7.1, 7.2, and Red Hat Virtualization 4.1 (p. 18)
Support for Debian 8.6, 8.7, 8.8, 9, and Ubuntu 17.04
Support for Windows Storage Server 2016
The capability to use a PostgreSQL database with the management server under Linux (p. 29)
A utility for agent mass deployment and upgrade.
For information about how to use this utility, refer to http://kb.acronis.com/content/60137
1.2 What's new in Acronis Backup 12.5
Important These new features are available in on-premise deployments only. They will be propagated to cloud deployments in future releases.
New features available in all on-premise deployments
Backup
A new backup format (p. 82) that increases the backup speed and reduces the size of backups
Up to five locations for replication in a backup plan (p. 75)
Conversion to a virtual machine in a backup plan (p. 73)
Schedule by events (p. 66)
Setting conditions for backup plan execution (p. 67)
Predefined Grandfather-Father-Son (GFS) backup scheme (p. 64)
SFTP as a backup location (p. 60)
Default backup options stored on the management server (p. 232)
Selection of the backup method (full or incremental) when starting a backup manually (p. 76)
Backup options:
Email notifications (p. 86):
Specify the email notifications subject
Notifications are now based on alerts instead of backup activity results. You can customize the list of alerts that trigger a notification.
Backup file name (p. 79)
Backup start conditions (p. 84)
Recovery
Manual disk mapping. The capability to recover individual disks or volumes (p. 102).
Bootable media
Startup Recovery Manager (p. 147)
Applications
Backing up Microsoft Exchange Server mailboxes (p. 162)
7 |
Copyright © Acronis International GmbH, 2002-2017 |
Virtualization
The capability to assign a virtual machine to a specific agent (p. 192) (VM binding)
Operations with backups
Mounting volumes in the read/write mode (p. 122)
ASign allows a backed-up file to be signed by several people (p. 113)
Notifications and alerts
The capability to configure the severity of an alert (via the configuration file) (p. 201)
Device status is now derived from alerts instead of backup activity results. This covers a wider range of events, for example, missed backups or ransomware activities.
Acronis Active Protection
Proactive protection from ransomware by detecting suspicious processes (p. 175)
Usability improvements
Dashboard - a customizable set of more than 20 widgets that are updated in real time (p. 198)
A new section in the UI shows all backup plans and other plans (p. 124)
The capability to set an encryption password in Backup Monitor (p. 71)
New features available with the Advanced licenses only
Administering
Customizable reports that can be sent or saved on a schedule (p. 199)
Roles on the management server: create units and assign administrators to them (p. 233)
Group management: built-in and custom groups of devices (p. 202)
Acronis Notary: prove that a file is authentic and unchanged since it was backed up (p. 72)
New backup locations
Acronis Storage Node with deduplication (p. 224)
Support for tape devices (p. 207)
Bootable media
Working with bootable media via the backup console (p. 145)
Automated backup and recovery by execution of a predefined or custom script (p. 133)
PXE Server for network boot (p. 148)
Applications
Support for Database Availability Groups (DAG) in Microsoft Exchange Server (p. 159)
Support for AlwaysOn Availability Group (AAG) in Microsoft SQL Server (p. 158)
Protecting Oracle Database (p. 175)
Virtualization
Backing up ESXi virtual machines from NetApp hardware snapshots (p. 187)
Backing up Citrix XenServer, Red Hat Virtualization (RHV/RHEV), Kernel-based Virtual Machines (KVM), and Oracle virtual machines (by installing an agent into the guest system) (p. 11)
Operations with backups
Conversion to a virtual machine, validation, replication, and retention of backups can be performed on a schedule by a dedicated agent (p. 125)
8 |
Copyright © Acronis International GmbH, 2002-2017 |

Cataloging - a separate catalog service enables search throughout all backups in managed locations (p. 229)
2 Installation
2.1Installation overview
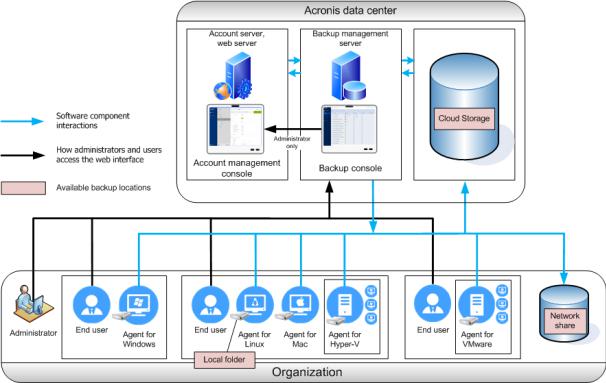
Acronis Backup supports two methods of deployment: on-premise and cloud. The main difference between them is the location of Acronis Backup Management Server.
Acronis Backup Management Server is the central point for managing all of your backups. With the on-premise deployment, it is installed in your local network; with the cloud deployment, it is located in one of the Acronis data centers. The web interface to this server is named a backup console.
Both types of deployment require that a backup agent is installed on each machine that you want to back up. The supported types of storage are also the same. The cloud storage space is sold separately from the Acronis Backup licenses.
On-premise deployment
On-premise deployment means that all of the product components are installed in your local network. This is the only deployment method available with a perpetual license. Also, you have to use this method if your machines are not connected to the Internet.
Management server location
You can install the management server on a machine running either Windows or Linux.
Installation in Windows is recommended because you will be able to deploy agents to other machines from the management server. With the Advanced license, it is possible to create
9 |
Copyright © Acronis International GmbH, 2002-2017 |
organizational units and add administrators to them. This way, you can delegate backup management to other people whose access permissions will be strictly limited to the corresponding units.
Installation in Linux is recommended in a Linux-only environment. You will need to install an agent locally on the machines that you want to back up.
Cloud deployment
Cloud deployment means that the management server is located in one of the Acronis data centers. The benefit of this approach is that you do not need to maintain the management server in your local network. You can think of Acronis Backup as of a backup service provided to you by Acronis.
Access to the account server enables you to create user accounts, set service usage quotas for them, and create groups of users (units) to reflect the structure of your organization. Every user can access the backup console, download the required agent, and install it on their machines in minutes.
Administrator accounts can be created at the unit or organization level. Each account has a view scoped to their area of control. Users have access only to their own backups.
The following table summarizes differences between the on-premise and cloud deployments.
10 |
Copyright © Acronis International GmbH, 2002-2017 |
|
On-premise deployment |
|
Cloud deployment |
|
|
|
|
|
On-premise management server |
|
Unit and account management |
Unit and account management with the Advanced |
|
A subscription license is required |
|
|
license only |
|
No Agent for VMware (Virtual Appliance) |
|
|
|
|
Both subscription and perpetual licenses can be used |
|
Mobile backup to cloud |
|
Agent for VMware (Virtual Appliance) and Agent for |
|
|
|
|
VMware (Windows) |
|
|
WAN optimization for replication of virtual machines |
|
|
|
|
(replica seeding) |
|
|
|
Bootable Media Builder |
|
|
Backup and disk management in bootable media |
|
|
|
Upgrade from previous versions of Acronis Backup, |
|
|
|
|
including Acronis Backup for VMware |
|
|
Participation in the Acronis Customer Experience |
|
|
|
|
Program |
|
|
Features introduced in version 12.5, which affects only |
|
|
|
|
on-premise deployments. See "What's new in Acronis |
|
|
|
Backup 12.5" (p. 7). |
|
|
|
|
|
|
2.2Components
Agents
Agents are applications that perform data backup, recovery, and other operations on the machines managed by Acronis Backup.
Choose an agent, depending on what you are going to back up. The following table summarizes the information, to help you decide.
Note that Agent for Windows is installed along with Agent for Exchange, Agent for SQL, Agent for Active Directory, and Agent for Oracle. If you install, for example, Agent for SQL, you also will be able to back up the entire machine where the agent is installed.
|
What are you going to |
|
Which agent to install? |
|
Where to install it? |
|
Agent availability |
||
|
|
|
|
||||||
|
|
|
|||||||
|
|
|
|
|
|
|
|||
|
back up? |
|
|
|
|
|
|
||
|
|
|
|
|
|
On-prem |
|
Cloud |
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
||
|
|
|
|
||||||
|
|
|
|
|
|
|
|
|
|
|
Physical machines |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
Disks, volumes, and files |
|
Agent for Windows |
|
+ |
|
+ |
|||
|
|
|
|
|
|
|
|||
on physical machines |
|
|
|
|
|
|
|
|
|
running Windows |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Disks, volumes, and files |
|
Agent for Linux |
|
+ |
|
+ |
|||
|
|
|
|
|
|
|
|||
on physical machines |
|
|
|
On the machine that will be backed up. |
|
|
|
||
running Linux |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Disks, volumes, and files |
|
Agent for Mac |
|
+ |
|
+ |
|||
|
|
|
|
|
|
|
|||
on physical machines |
|
|
|
|
|
|
|
|
|
running macOS |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Applications |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
11 |
|
|
|
Copyright © Acronis International GmbH, 2002-2017 |
|
||||

|
What are you going to |
|
Which agent to install? |
|
Where to install it? |
|
Agent availability |
||
|
|
|
|
||||||
|
|
|
|
||||||
|
|
|
|||||||
|
|
|
|||||||
|
|
|
|
|
|
|
|||
|
back up? |
|
|
|
|
|
|
||
|
|
|
|
|
|
On-prem |
|
Cloud |
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
||||
|
|
|
|
|
|
|
|
|
|
SQL databases |
|
Agent for SQL |
|
On the machine running Microsoft SQL |
+ |
+ |
|||
|
|
|
|
|
|
||||
|
|
|
|
|
Server. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
On the machine running the Mailbox role |
|
|
|
|
|
|
|
|
|
of Microsoft Exchange Server. |
|
|
+ |
|
|
|
|
|
|
If only mailbox backup is required, the |
|
|
||
Exchange databases and |
|
Agent for Exchange |
|
+ |
|
No |
|||
|
|
agent can be installed on any Windows |
|
||||||
mailboxes |
|
|
|
|
|
|
mailbox |
||
|
|
|
machine that has network access to the |
|
|
|
|||
|
|
|
|
|
|
|
|
backup |
|
|
|
|
|
|
machine running the Client Access role of |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Microsoft Exchange Server. |
|
|
|
|
|
|
|
|
|
|
|
|
||
Microsoft Office 365 |
|
Agent for Office 365 |
|
On a Windows machine that is connected |
+ |
+ |
|||
|
|
|
|
|
|
||||
mailboxes |
|
|
|
to the Internet. |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Machines running Active |
|
Agent for Active Directory |
|
On the domain controller. |
+ |
+ |
|||
|
|
|
|
|
|
||||
Directory Domain |
|
|
|
|
|
|
|
|
|
Services |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Machines running Oracle |
|
Agent for Oracle |
|
On the machine running Oracle Database |
+ |
|
– |
||
|
|
|
|
|
|
||||
Database |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Virtual machines |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
VMware ESXi virtual |
|
Agent for VMware |
|
On a Windows machine that has network |
+ |
+ |
|||
|
|
|
|
|
|
||||
machines |
|
(Windows) |
|
access to vCenter Server and to the |
|
|
|
|
|
|
|
|
|
|
virtual machine storage.* |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Agent for VMware |
|
On the ESXi host. |
+ |
|
– |
|
|
|
|
|
|
|
|
|
||
|
|
|
(Virtual Appliance) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Hyper-V virtual |
|
Agent for Hyper-V |
|
On the Hyper-V host. |
+ |
+ |
|||
|
|
|
|
|
|
||||
machines |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Virtual machines hosted |
|
|
|
|
+ |
+ |
|||
|
|
|
|
|
|
|
|
||
on Windows Azure |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Virtual machines hosted |
|
|
|
|
+ |
+ |
|||
|
|
|
|
|
|
|
|
||
on Amazon EC2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Citrix XenServer virtual |
|
|
|
|
|
|
|
|
|
machines |
|
The same as for physical |
|
On the machine that will be backed up. |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Red Hat Virtualization |
|
machines** |
|
|
|
|
|
||
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
||
(RHV/RHEV) virtual |
|
|
|
|
+*** |
+ |
|||
machines |
|
|
|
|
|||||
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
Kernel-based Virtual |
|
|
|
|
|
|
|
|
|
Machines (KVM) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Oracle virtual machines |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Mobile devices |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Mobile devices running |
|
Mobile app for Android |
|
|
|
– |
+ |
||
|
|
|
|
|
|
|
|||
Android |
|
|
|
On the mobile device that will be backed |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Mobile devices running |
|
Mobile app for iOS |
|
up. |
|
– |
+ |
||
|
|
|
|
|
|
|
|||
iOS |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
12 |
|
|
|
Copyright © Acronis International GmbH, 2002-2017 |
|||||
*If your ESXi uses a SAN attached storage, install the agent on a machine connected to the same SAN. The agent will back up the virtual machines directly from the storage rather than via the ESXi host and LAN. For detailed instructions, refer to "LAN-free backup" (p. 184).
**A virtual machine is considered virtual if it is backed up by an external agent. If an agent is installed in the guest system, the backup and recovery operations are the same as with a physical machine. Nevertheless, the machine is counted as virtual when you set quotas for the number of machines in a cloud deployment.
***With an Acronis Backup Advanced Virtual Host license, these virtual machines are considered as virtual (per host licensing is used). With an Acronis Backup Virtual Host license, these machines are considered as physical (per machine licensing is used).
Other components
|
Component |
|
Function |
|
Where to install it? |
Availability |
|
|
|
|
|||||
|
|
|
|
|
|||
|
|
|
|
|
|
On-prem |
Cloud |
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
Management Server |
|
Manages the agents. |
|
On a machine running Windows or Linux. |
+ |
– |
|
|
|
|
|
||||
|
|
|
Provides the web |
|
|
|
|
|
|
|
interface to users. |
|
|
|
|
|
|
|
|
|
|
|
|
Monitoring Service |
|
Provides the dashboard |
|
On the machine running the |
+ |
– |
|
|
|
|
|
||||
|
|
|
and reporting |
|
management server. |
|
|
|
|
|
functionality. |
|
|
|
|
|
|
|
|
|
|
|
|
Bootable Media Builder |
|
Creates bootable media. |
|
On a machine running Windows or Linux. |
+ |
– |
|
|
|
|
|
||||
|
|
|
|
|
|
|
|
Backup Monitor |
|
Enables users to monitor |
|
On a machine running Windows or |
+ |
+ |
|
|
|
|
|
||||
|
|
|
backups outside the web |
|
macOS. |
|
|
|
|
|
interface. |
|
|
|
|
|
|
|
|
|
|
|
|
Command-Line Tool |
|
Provides the |
|
On a machine running Windows or Linux. |
+ |
+ |
|
|
|
|
|
||||
|
|
|
command-line interface. |
|
|
|
|
|
|
|
|
|
|
|
|
Storage Node |
|
Stores backups. Is |
|
On a machine running Windows. |
+ |
– |
|
|
|
|
|
||||
|
|
|
required for cataloging |
|
|
|
|
|
|
|
and deduplication. |
|
|
|
|
|
|
|
|
|
|
|
|
Catalog Service |
|
Performs cataloging of |
|
On a machine running Windows. |
+ |
– |
|
|
|
|
|
||||
|
|
|
backups on storage |
|
|
|
|
|
|
|
nodes. |
|
|
|
|
|
|
|
|
|
|
|
|
PXE Server |
|
Enables booting machines |
|
On a machine running Windows. |
+ |
– |
|
|
|
|
|
||||
|
|
|
into bootable media |
|
|
|
|
|
|
|
through the network. |
|
|
|
|
|
|
|
|
|
|
|
|
2.3Software requirements
2.3.1Supported web browsers
The web interface supports the following web browsers:
Google Chrome 29 or later
Mozilla Firefox 23 or later
Opera 16 or later
Windows Internet Explorer 10 or later
Microsoft Edge 25 or later
Safari 8 or later running in the OS X and iOS operating systems
13 |
Copyright © Acronis International GmbH, 2002-2017 |
In other web browsers (including Safari browsers running in other operating systems), the user interface might be displayed incorrectly or some functions may be unavailable.
2.3.2Supported operating systems and environments
2.3.2.1Agents
Agent for Windows
Windows XP Professional SP3 (x86, x64)
Windows Server 2003 SP1/2003 R2 and later – Standard and Enterprise editions (x86, x64) Windows Small Business Server 2003/2003 R2
Windows Vista – all editions
Windows Server 2008 – Standard, Enterprise, Datacenter, and Web editions (x86, x64) Windows Small Business Server 2008
Windows 7 – all editions
Windows Server 2008 R2 – Standard, Enterprise, Datacenter, Foundation, and Web editions Windows MultiPoint Server 2010/2011/2012
Windows Small Business Server 2011 – all editions
Windows 8/8.1 – all editions (x86, x64), except for the Windows RT editions Windows Server 2012/2012 R2 – all editions
Windows Storage Server 2003/2008/2008 R2/2012/2012 R2/2016 Windows 10 – Home, Pro, Education, Enterprise, and IoT Enterprise editions Windows Server 2016 – all installation options, except for Nano Server
Agent for SQL, Agent for Exchange (for database backup and application-aware backup), Agent for Active Directory
Each of these agents can be installed on a machine running any operating system listed above and a supported version of the respective application.
Agent for Exchange (for mailbox backup)
This agent can be installed on a machine with or without Microsoft Exchange Server. Windows Server 2008 – Standard, Enterprise, Datacenter, and Web editions (x86, x64) Windows Small Business Server 2008
Windows 7 – all editions
Windows Server 2008 R2 – Standard, Enterprise, Datacenter, Foundation, and Web editions Windows MultiPoint Server 2010/2011/2012
Windows Small Business Server 2011 – all editions
Windows 8/8.1 – all editions (x86, x64), except for the Windows RT editions Windows Server 2012/2012 R2 – all editions
Windows Storage Server 2008/2008 R2/2012/2012 R2 Windows 10 – Home, Pro, Education, and Enterprise editions
Windows Server 2016 – all installation options, except for Nano Server
Agent for Office 365
Windows Server 2008 – Standard, Enterprise, Datacenter, and Web editions (x64 only)
14 |
Copyright © Acronis International GmbH, 2002-2017 |
Windows Small Business Server 2008
Windows Server 2008 R2 – Standard, Enterprise, Datacenter, Foundation, and Web editions Windows Small Business Server 2011 – all editions
Windows 8/8.1 – all editions (x64 only), except for the Windows RT editions Windows Server 2012/2012 R2 – all editions
Windows Storage Server 2008/2008 R2/2012/2012 R2/2016 (x64 only) Windows 10 – Home, Pro, Education, and Enterprise editions (x64 only) Windows Server 2016 – all installation options (x64 only), except for Nano Server
Agent for Oracle
Windows Server 2008 – Standard, Enterprise, Datacenter, and Web editions (x86, x64) Windows Server 2012 – Standard, Enterprise, Datacenter, and Web editions (x86, x64)
Agent for Linux
Linux with kernel from 2.6.9 to 4.9 and glibc 2.3.4 or later Various x86 and x86_64 Linux distributions, including:
Red Hat Enterprise Linux 4.x, 5.x, 6.x, 7.0, 7.1, 7.2, 7.3
Ubuntu 9.10, 10.04, 10.10, 11.04, 11.10, 12.04, 12.10, 13.04, 13.10, 14.04, 14.10, 15.04, 15.10, 16.04, 16.10, 17.04
Fedora 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24 SUSE Linux Enterprise Server 10 and 11
SUSE Linux Enterprise Server 12 – supported on file systems, except for Btrfs Debian 4, 5, 6, 7.0, 7.2, 7.4, 7.5, 7.6, 7.7, 8.0, 8.1, 8.2, 8.3, 8.4, 8.5, 8.6, 8.7, 8.8, 9 CentOS 5.x, 6.x, 7, 7.1, 7.2, 7.3
Oracle Linux 5.x, 6.x, 7.0, 7.1, 7.2, 7.3 – both Unbreakable Enterprise Kernel and Red Hat Compatible Kernel
CloudLinux 5.x, 6.x, 7, 7.1 ClearOS 5.x, 6.x, 7, 7.1
Before installing the product on a system that does not use RPM Package Manager, such as an Ubuntu system, you need to install this manager manually; for example, by running the following command (as the root user): apt-get install rpm
Agent for Mac
OS X Mavericks 10.9
OS X Yosemite 10.10
OS X El Capitan 10.11
macOS Sierra 10.12 – Apple File System (APFS) is not supported
Agent for VMware (Virtual Appliance)
This agent is delivered as a virtual appliance for running on an ESXi host.
VMware ESXi 4.1, 5.0, 5.1, 5.5, 6.0, 6.5
Agent for VMware (Windows)
This agent is delivered as a Windows application for running in any operating system listed above for Agent for Windows with the following exceptions:
32-bit operating systems are not supported.
15 |
Copyright © Acronis International GmbH, 2002-2017 |
Windows XP, Windows Server 2003/2003 R2, and Windows Small Business Server 2003/2003 R2 are not supported.
Agent for Hyper-V
Windows Server 2008 (x64 only) with Hyper-V Windows Server 2008 R2 with Hyper-V Microsoft Hyper-V Server 2008/2008 R2 Windows Server 2012/2012 R2 with Hyper-V Microsoft Hyper-V Server 2012/2012 R2 Windows 8, 8.1 (x64 only) with Hyper-V
Windows 10 – Pro, Education, and Enterprise editions with Hyper-V
Windows Server 2016 with Hyper-V – all installation options, except for Nano Server Microsoft Hyper-V Server 2016
2.3.2.2Management Server (for on-premise deployment only)
In Windows
Windows Server 2008 – Standard, Enterprise, and Datacenter editions (x86, x64) Windows Small Business Server 2008
Windows 7 – all editions (x86, x64)
Windows Server 2008 R2 – Standard, Enterprise, Datacenter, and Foundation editions Windows MultiPoint Server 2010/2011/2012
Windows Small Business Server 2011 – all editions
Windows 8/8.1 – all editions (x86, x64), except for the Windows RT editions Windows Server 2012/2012 R2 – all editions
Windows Storage Server 2008/2008 R2/2012/2012 R2/2016
Windows 10 – Home, Pro, Education, Enterprise, and IoT Enterprise editions Windows Server 2016 – all installation options, except for Nano Server
In Linux
Linux with kernel from 2.6.18 to 4.9 and glibc 2.3.4 or later Various x86_64 Linux distributions, including:
Red Hat Enterprise Linux 4.x, 5.x, 6.x, 7.0, 7.1, 7.2, 7.3
Ubuntu 9.10, 10.04, 10.10, 11.04, 11.10, 12.04, 12.10, 13.04, 13.10, 14.04, 14.10, 15.04, 15.10, 16.04, 16.10, 17.04
Fedora 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24 SUSE Linux Enterprise Server 10, 11, 12
Debian 4, 5, 6, 7.0, 7.2, 7.4, 7.5, 7.6, 7.7, 8.0, 8.1, 8.2, 8.3, 8.4, 8.5, 8.6, 8.7, 8.8, 9 CentOS 5.x, 6.x, 7, 7.1, 7.2, 7.3
Oracle Linux 5.x, 6.x, 7.0, 7.1, 7.2, 7.3 – both Unbreakable Enterprise Kernel and Red Hat Compatible Kernel
CloudLinux 5.x, 6.x, 7, 7.1
2.3.2.3Storage Node (for on-premise deployment only)
Windows Server 2008 – Standard, Enterprise, and Datacenter editions (x64 only)
16 |
Copyright © Acronis International GmbH, 2002-2017 |
Windows Small Business Server 2008 Windows 7 – all editions (x64 only)
Windows Server 2008 R2 – Standard, Enterprise, Datacenter, and Foundation editions Windows MultiPoint Server 2010/2011/2012
Windows Small Business Server 2011 – all editions
Windows 8/8.1 – all editions (x64 only), except for the Windows RT editions Windows Server 2012/2012 R2 – all editions
Windows Storage Server 2008/2008 R2/2012/2012 R2/2016 Windows 10 – Home, Pro, Education, and Enterprise editions Windows Server 2016 – all installation options, except for Nano Server
2.3.3Supported Microsoft SQL Server versions
Microsoft SQL Server 2016
Microsoft SQL Server 2014
Microsoft SQL Server 2012
Microsoft SQL Server 2008 R2
Microsoft SQL Server 2008
Microsoft SQL Server 2005
2.3.4Supported Microsoft Exchange Server versions
Microsoft Exchange Server 2016 – all editions.
Microsoft Exchange Server 2013 – all editions, Cumulative Update 1 (CU1) and later.
Microsoft Exchange Server 2010 – all editions, all service packs. Mailbox backup and granular recovery from database backups are supported starting with Service Pack 1 (SP1).
Microsoft Exchange Server 2007 – all editions, all service packs. Mailbox backup and granular recovery from database backups are not supported.
2.3.5Supported Microsoft SharePoint versions
Acronis Backup 12.5 supports the following Microsoft SharePoint versions:
Microsoft SharePoint 2013
Microsoft SharePoint Server 2010 SP1
Microsoft SharePoint Foundation 2010 SP1
Microsoft Office SharePoint Server 2007 SP2*
Microsoft Windows SharePoint Services 3.0 SP2*
*In order to use SharePoint Explorer with these versions, you need a SharePoint recovery farm to attach the databases to.
The backups or databases from which you extract data must originate from the same SharePoint version as the one where SharePoint Explorer is installed.
2.3.6Supported Oracle Database versions
Oracle Database version 11g, all editions
Oracle Database version 12c, all editions.
17 |
Copyright © Acronis International GmbH, 2002-2017 |

Only single-instance configurations are supported.
2.3.7Supported virtualization platforms
The following table summarizes how various virtualization platforms are supported.
Platform |
Backup at a hypervisor |
Backup from inside a |
|
|
level (agentless backup) |
guest OS |
|
|
|
||
|
|
|
|
|
VMware |
|
|
|
|
|
|
|
|
|
|
VMware vSphere versions: 4.1, 5.0, 5.1, 5.5, |
|
|
|
|
|
6.0, 6.5 |
|
|
|
|
|
VMware vSphere editions: |
|
|
|
|
|
VMware vSphere Essentials* |
|
|
|
|
|
VMware vSphere Essentials Plus* |
+ |
+ |
|
|
|
|
|
|
|
||
VMware vSphere Standard* |
|
|
|
|
|
VMware vSphere Advanced |
|
|
|
|
|
VMware vSphere Enterprise |
|
|
|
|
|
VMware vSphere Enterprise Plus |
|
|
|
|
|
|
|
|
|
|
|
VMware vSphere Hypervisor (Free ESXi)** |
|
+ |
|
|
|
|
|
|
|
|
|
VMware Server (VMware Virtual server) |
|
|
|
|
|
VMware Workstation |
|
+ |
|
|
|
VMware ACE |
|
|
|
||
|
|
|
|
||
VMware Player |
|
|
|
|
|
|
|
|
|
|
|
|
Microsoft |
|
|
|
|
|
|
|
|
|
|
Windows Server 2008 (x64) with Hyper-V |
|
|
|
|
|
Windows Server 2008 R2 with Hyper-V |
|
|
|
|
|
Microsoft Hyper-V Server 2008/2008 R2 |
|
|
|
|
|
Windows Server 2012/2012 R2 with Hyper-V |
|
|
|
|
|
Microsoft Hyper-V Server 2012/2012 R2 |
+ |
+ |
|
|
|
|
|
|
|
||
Windows 8, 8.1 (x64) with Hyper-V |
|
|
|
|
|
Windows 10 with Hyper-V |
|
|
|
|
|
Windows Server 2016 with Hyper-V – all |
|
|
|
|
|
installation options, except for Nano Server |
|
|
|
|
|
Microsoft Hyper-V Server 2016 |
|
|
|
|
|
|
|
|
|
|
|
Microsoft Virtual PC 2004 and 2007 |
|
+ |
|
|
|
Windows Virtual PC |
|
|
|
||
|
|
|
|
||
|
|
|
|
|
|
Microsoft Virtual Server 2005 |
|
+ |
|
|
|
|
|
|
|
|
|
|
Citrix |
|
|
|
|
|
|
|
|
|
|
Citrix XenServer 4.1.5, 5.5, 5.6, 6.0, 6.1, 6.2, 6.5, |
|
Only fully virtualized |
|||
7.0, 7.1, 7.2 |
|
(aka HVM) guests |
|||
|
|
|
|
||
18 |
Copyright © Acronis International GmbH, 2002-2017 |
||||

|
Platform |
Backup at a hypervisor |
Backup from inside a |
|
|
|
level (agentless backup) |
guest OS |
|
|
|
|
||
|
|
|
|
|
|
Red Hat and Linux |
|
|
|
|
|
|
|
|
Red Hat Enterprise Virtualization (RHEV) 2.2, |
|
|
|
|
3.0, 3.1, 3.2, 3.3, 3.4, 3.5, 3.6 |
|
+ |
|
|
|
|
|
|
|
Red Hat Virtualization (RHV) 4.0, 4.1 |
|
|
|
|
|
|
|
|
|
Kernel-based Virtual Machines (KVM) |
|
+ |
|
|
|
|
|
|
|
|
|
|
|
|
Parallels
Parallels Workstation |
|
+ |
|
|
|
Parallels Server 4 Bare Metal |
|
+ |
|
|
|
Oracle |
|
|
|
|
|
Oracle VM Server 3.0 and 3.3 |
|
+ |
|
|
|
Oracle VM VirtualBox 4.x |
|
+ |
|
|
|
Amazon |
|
|
|
|
|
Amazon EC2 instances |
|
+ |
|
|
|
Microsoft Azure |
|
|
|
|
|
Azure virtual machines |
|
+ |
|
|
|
*In these editions, the HotAdd transport for virtual disks is supported on vSphere 5.0 and later. On version 4.1, backups may run slower.
**Backup at a hypervisor level is not supported for vSphere Hypervisor because this product restricts access to Remote Command Line Interface (RCLI) to read-only mode. The agent works during the vSphere Hypervisor evaluation period while no serial key is entered. Once you enter a serial key, the agent stops functioning.
Limitations
Fault tolerant machines
Agent for VMware backs up a fault tolerant machine only if fault tolerance was enabled in VMware vSphere 6.0 and later. If you upgraded from an earlier vSphere version, it is enough to disable and enable fault tolerance for each machine. If you are using an earlier vSphere version, install an agent in the guest operating system.
Independent disks and RDM
Agent for VMware does not back up Raw Device Mapping (RDM) disks in physical compatibility mode or independent disks. The agent skips these disks and adds warnings to the log. You can avoid the warnings by excluding independent disks and RDMs in physical compatibility mode from the backup plan. If you want to back up these disks or data on these disks, install an agent in the guest operating system.
Pass-through disks
Agent for Hyper-V does not back up pass-through disks. During backup, the agent skips these disks and adds warnings to the log. You can avoid the warnings by excluding pass-through disks from the backup plan. If you want to back up these disks or data on these disks, install an agent in the guest operating system.
Encrypted virtual machines (introduced in VMware vSphere 6.5)
19 |
Copyright © Acronis International GmbH, 2002-2017 |

Encrypted virtual machines are backed up in an unencrypted state. If encryption is critical to you, enable encryption of backups when creating a backup plan (p. 71).
Recovered virtual machines are always unencrypted. You can manually enable encryption after the recovery is complete.
If you back up encrypted virtual machines, we recommend that you also encrypt the virtual machine where Agent for VMware is running. Otherwise, operations with encrypted machines may be slower than expected. Apply the VM Encryption Policy to the agent's machine by using vSphere Web Client.
Encrypted virtual machines will be backed up via LAN, even if you configure the SAN transport mode for the agent. The agent will fall back on the NBD transport because VMware does not support SAN transport for backing up encrypted virtual disks.
Secure Boot (introduced in VMware vSphere 6.5)
Secure Boot is disabled after a virtual machine is recovered as a new virtual machine. You can manually enable this option after the recovery is complete.
2.3.8Linux packages
To add the necessary modules to the Linux kernel, the setup program needs the following Linux packages:
The package with kernel headers or sources. The package version must match the kernel version.
The GNU Compiler Collection (GCC) compiler system. The GCC version must be the one with which the kernel was compiled.
The Make tool.
The Perl interpreter.
The names of these packages vary depending on your Linux distribution.
In Red Hat Enterprise Linux, CentOS, and Fedora, the packages normally will be installed by the setup program. In other distributions, you need to install the packages if they are not installed or do not have the required versions.
Are the required packages already installed?
To check whether the packages are already installed, perform these steps:
1.Run the following command to find out the kernel version and the required GCC version: cat /proc/version
This command returns lines similar to the following: Linux version 2.6.35.6 and gcc version 4.5.1
2.Run the following command to check whether the Make tool and the GCC compiler are installed:
make -v gcc -v
For gcc, ensure that the version returned by the command is the same as in the gcc version in step 1. For make, just ensure that the command runs.
3.Check whether the appropriate version of the packages for building kernel modules is installed:
In Red Hat Enterprise Linux, CentOS, and Fedora, run the following command: yum list installed | grep kernel-devel
In Ubuntu, run the following commands:
20 |
Copyright © Acronis International GmbH, 2002-2017 |

dpkg --get-selections | grep linux-headers dpkg --get-selections | grep linux-image
In either case, ensure that the package versions are the same as in Linux version in step 1.
4.Run the following command to check whether the Perl interpreter is installed: perl --version
If you see the information about the Perl version, the interpreter is installed.
Installing the packages from the repository
The following table lists how to install the required packages in various Linux distributions.
|
Linux |
|
Package names |
How to install |
|
|
distribution |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Red Hat |
|
kernel-devel |
The setup program will download and install the packages |
||
Enterprise |
|
gcc |
automatically by using your Red Hat subscription. |
||
Linux |
|
make |
|
|
|
|
|
|
|
|
|
|
|
|
perl |
Run the following command: |
|
|
|
|
|
|
|
|
|
|
|
yum install perl |
|
|
|
|
|
||
CentOS |
|
kernel-devel |
The setup program will download and install the packages |
||
Fedora |
|
gcc |
automatically. |
||
|
make |
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
perl |
Run the following command: |
|
|
|
|
|
|
|
|
|
|
|
yum install perl |
|
|
|
|
|
||
Ubuntu |
|
linux-headers |
Run the following commands: |
||
|
|
|
linux-image |
|
|
|
|
|
gcc |
sudo apt-get update |
|
|
|
|
sudo apt-get install linux-headers-`uname -r` |
|
|
|
|
|
make |
|
|
|
|
|
sudo apt-get install linux-image-`uname -r` |
|
|
|
|
|
perl |
|
|
|
|
|
sudo apt-get install gcc-<package version> |
|
|
|
|
|
|
|
|
|
|
|
|
sudo apt-get install make |
|
|
|
|
|
sudo apt-get install perl |
|
|
|
|
|
|
|
The packages will be downloaded from the distribution's repository and installed.
For other Linux distributions, please refer to the distribution's documentation regarding the exact names of the required packages and the ways to install them.
Installing the packages manually
You may need to install the packages manually if:
The machine does not have an active Red Hat subscription or Internet connection.
The setup program cannot find the kernel-devel or gcc version corresponding to the kernel version. If the available kernel-devel is more recent than your kernel, you need to either update the kernel or install the matching kernel-devel version manually.
You have the required packages on the local network and do not want to spend time for automatic search and downloading.
Obtain the packages from your local network or a trusted third-party website, and install them as follows:
In Red Hat Enterprise Linux, CentOS, or Fedora, run the following command as the root user: rpm -ivh PACKAGE_FILE1 PACKAGE_FILE2 PACKAGE_FILE3
21 |
Copyright © Acronis International GmbH, 2002-2017 |

In Ubuntu, run the following command:
sudo dpkg -i PACKAGE_FILE1 PACKAGE_FILE2 PACKAGE_FILE3
Example: Installing the packages manually in Fedora 14
Follow these steps to install the required packages in Fedora 14 on a 32-bit machine:
1.Run the following command to determine the kernel version and the required GCC version: cat /proc/version
The output of this command includes the following:
Linux version 2.6.35.6-45.fc14.i686 gcc version 4.5.1
2.Obtain the kernel-devel and gcc packages that correspond to this kernel version:
kernel-devel-2.6.35.6-45.fc14.i686.rpm gcc-4.5.1-4.fc14.i686.rpm
3.Obtain the make package for Fedora 14: make-3.82-3.fc14.i686
4.Install the packages by running the following commands as the root user:
rpm -ivh kernel-devel-2.6.35.6-45.fc14.i686.rpm rpm -ivh gcc-4.5.1.fc14.i686.rpm
rpm -ivh make-3.82-3.fc14.i686
You can specify all these packages in a single rpm command. Installing any of these packages may require installing additional packages to resolve dependencies.
2.3.9Compatibility with encryption software
There are no limitations on backing up and recovering data that is encrypted by file-level encryption software.
Disk-level encryption software encrypts data on the fly. This is why data contained in the backup is not encrypted. Disk-level encryption software often modifies system areas: boot records, or partition tables, or file system tables. These factors affect disk-level backup and recovery, the ability of the recovered system to boot and access to Secure Zone.
You can back up the data encrypted by the following disk-level encryption software:
Microsoft BitLocker Drive Encryption
McAfee Endpoint Encryption
PGP Whole Disk Encryption.
To ensure reliable disk-level recovery, follow the common rules and software-specific recommendations.
Common installation rule
The strong recommendation is to install the encryption software before installing the backup agents.
The way of using Secure Zone
Secure Zone must not be encrypted with disk-level encryption. This is the only way to use Secure Zone:
1.Install the encryption software; then, install the agent.
2.Create Secure Zone.
22 |
Copyright © Acronis International GmbH, 2002-2017 |
3. Exclude Secure Zone when encrypting the disk or its volumes.
Common backup rule
You can do a disk-level backup in the operating system. Do not try to back up using bootable media.
Software-specific recovery procedures
Microsoft BitLocker Drive Encryption
To recover a system that was encrypted by BitLocker:
1.Boot from the bootable media.
2.Recover the system. The recovered data will be unencrypted.
3.Reboot the recovered system.
4.Turn on BitLocker.
If you only need to recover one partition of a multi-partitioned disk, do so under the operating system. Recovery under bootable media may make the recovered partition undetectable for Windows.
McAfee Endpoint Encryption and PGP Whole Disk Encryption
You can recover an encrypted system partition by using bootable media only.
If the recovered system fails to boot, rebuild Master Boot Record as described in the following Microsoft knowledge base article: https://support.microsoft.com/kb/2622803
2.4System requirements
The following table summarizes disk space and memory requirements for typical installation cases. The installation is performed with the default settings.
|
Components to be installed |
|
|
Occupied disk space |
|
Minimum memory |
|
|
|
||||
|
|
|
|
consumption |
||
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
Agent for Windows |
|
|
850 MB |
|
150 MB |
|
|
|
|
|
|
|
|
Agent for Windows and one of the following agents: |
|
|
|
|
|
|
|
Agent for SQL |
|
|
950 MB |
|
170 MB |
|
Agent for Exchange |
|
|
|
|
|
|
|
|
|
|
|
|
Agent for Windows and one of the following agents: |
|
|
|
|
|
|
Agent for VMware (Windows) |
|
|
1170 MB |
|
180 MB |
|
Agent for Hyper-V |
|
|
|
|
|
|
Agent for Office 365 |
|
|
500 MB |
|
170 MB |
|
|
|
|
|
|
|
|
Agent for Linux |
|
|
720 MB |
|
130 MB |
|
|
|
|
|
|
|
|
Agent for Mac |
|
|
500 MB |
|
150 MB |
|
|
|
|
|
|
|
|
For on-premise deployments only |
|
|
|
|
|
|
|
|
|
|
|
|
|
Management Server in Windows |
|
|
1.7 GB |
|
200 MB |
|
|
|
|
|
|
|
|
Management Server in Linux |
|
|
0.6 GB |
|
200 MB |
|
|
|
|
|
|
|
|
Management Server and Agent for Windows |
|
|
2.4 GB |
|
360 MB |
|
|
|
|
|
|
||
23 |
|
Copyright © Acronis International GmbH, 2002-2017 |
||||
Management Server and agents on a machine running |
|
|
Windows, Microsoft SQL Server, Microsoft Exchange Server, and |
3.35 GB |
400 MB |
Active Directory Domain Services |
|
|
|
|
|
Management Server and Agent for Linux |
1.2 GB |
340 MB |
|
|
|
Storage Node and Agent for Windows |
|
|
64-bit platform only |
|
|
To use deduplication, minimum 8 GB of RAM are required. |
1.1 GB |
330 MB |
|
|
|
For more information, see "Deduplication best practices" (p. |
|
|
227). |
|
|
|
|
|
While backing up, an agent typically consumes about 350 MB of memory (measured during a 500-GB volume backup). The peak consumption may reach 2 GB, depending on the amount and type of data being processed.
Bootable media or a disk recovery with a reboot requires at least 1 GB of memory.
A management server with one registered machine consumes 200 MB of memory. Each of the newly registered machines adds about 4 MB. Thus, a server with 100 registered machines consumes approximately 600 MB above the operating system and running applications. The maximum number of registered machines is 900-1000. This limitation originates from the management server's embedded SQLite.
You can overcome this limitation by specifying an external Microsoft SQL Server instance during the management server installation. With an external SQL database, up to 2000 machines can be registered without significant performance degradation.
2.5Supported file systems
A backup agent can back up any file system that is accessible from the operating system where the agent is installed. For example, Agent for Windows can back up and recover an ext4 file system if the corresponding driver is installed in Windows.
The following table summarizes the file systems that can be backed up and recovered. The limitations apply to both the agents and bootable media.
|
|
|
|
|
Supported by |
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
File system |
|
|
|
Win-PE |
|
Linux-based |
|
Mac bootable |
|
Limitations |
|
|
|
|
|
|
|
|||||
|
|
|
|
|
|
||||||
|
|
|
Agents |
|
bootable |
|
|
|
|
||
|
|
|
|
|
bootable media |
|
media |
|
|
||
|
|
|
|
|
media |
|
|
|
|
||
|
|
|
|
|
|
|
|||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
FAT16/32 |
|
|
+ |
+ |
+ |
|
|
|||
|
|
|
All agents |
|
|
|
|
|
|||
|
NTFS |
|
+ |
+ |
+ |
|
|
||||
|
|
|
|
|
|
|
|
|
|
|
No limitations |
|
ext2/ext3/ext4 |
|
|
+ |
+ |
- |
|
||||
|
|
|
|
|
|||||||
|
|
|
|
|
|
|
|
|
|||
|
HFS+ |
|
Agent for Mac |
- |
- |
+ |
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
JFS |
|
Agent for Linux |
- |
+ |
- |
|
Files cannot be excluded |
|||
|
|
|
from a disk backup |
||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
24 |
|
|
|
|
|
Copyright © Acronis International GmbH, 2002-2017 |
|||||

|
|
|
|
|
Supported by |
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
File system |
|
|
|
Win-PE |
|
Linux-based |
|
Mac bootable |
|
|
Limitations |
|
|
|
|
|
|
|
|
|||||
|
|
|
|
|
|
|
||||||
|
|
|
Agents |
|
bootable |
|
|
|
|
|
||
|
|
|
|
|
bootable media |
|
media |
|
|
|
||
|
|
|
|
|
media |
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
ReiserFS3 |
|
|
- |
+ |
- |
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|||
|
ReiserFS4 |
|
|
- |
+ |
- |
|
|
Files cannot be |
|||
|
|
|
|
|
|
|
|
|
|
|
|
excluded from a disk |
|
ReFS |
|
|
+ |
+ |
+ |
|
|
backup |
|||
|
|
|
|
|
|
|||||||
|
|
|
All agents |
|
|
|
|
|
|
|
Volumes cannot be |
|
|
XFS |
|
+ |
+ |
+ |
|
|
resized during a |
||||
|
|
|
|
|
||||||||
|
|
|
|
|
recovery |
|||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
Linux swap |
|
Agent for Linux |
- |
+ |
- |
|
|
No limitations |
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
The software automatically switches to the sector-by-sector mode when backing up drives with unrecognized or unsupported file systems. A sector-by-sector backup is possible for any file system that:
is block-based
spans a single disk
has a standard MBR/GPT partitioning scheme
If the file system does not meet these requirements, the backup fails.
25 |
Copyright © Acronis International GmbH, 2002-2017 |

2.6On-premise deployment
An on-premise deployment includes a number of software components that are described in the "Components" (p. 11) section. The diagram below illustrates the component interaction and the ports required for this interaction. The arrow direction shows which component initiates a connection.
2.6.1Installing the management server
2.6.1.1Installation in Windows
To install the management server
1.Log on as an administrator and start the Acronis Backup setup program.
2.[Optional] To change the language the setup program is displayed in, click Setup language.
3.Accept the terms of the license agreement and select whether the machine will participate in the Acronis Customer Experience Program (CEP).
26 |
Copyright © Acronis International GmbH, 2002-2017 |
4. Leave the default setting Install a backup agent and Acronis Backup Management Server.
5.Do any of the following:
Click Install Acronis Backup.
This is the easiest way to install the product. Most of the installation parameters will be set to their default values.
The following components will be installed:
Management Server
Monitoring Service
Agent for Windows
Other agents (Agent for Hyper-V, Agent for Exchange, Agent for SQL, and Agent for Active Directory), if the respective hypervisor or application is detected on the machine
Bootable Media Builder
Command-Line Tool
Backup Monitor
Click Customize installation settings to configure the setup.
You will be able to select the components to be installed and to specify additional parameters. For details, refer to "Customizing installation settings" (p. 27).
Click Create .mst and .msi files for unattended installation to extract the installation packages. Review or modify the installation settings that will be added to the .mst file, and then click Generate. Further steps of this procedure are not required.
If you want to deploy agents through Group Policy, refer to "Deploying agents through Group Policy" (p. 42).
6.Proceed with the installation.
7.After the installation completes, click Close.
Customizing installation settings
This section describes settings that can be changed during installation.
27 |
Copyright © Acronis International GmbH, 2002-2017 |
Common settings
The components to be installed.
The folder where the product will be installed.
The accounts under which the services will run. You can choose one of the following:
Use Service User Accounts (default for the agent service)
Service User Accounts are Windows system accounts that are used to run services. The advantage of this setting is that the domain security policies do not affect these accounts' user rights. By default, the agent runs under the Local System account.
Create a new account (default for the management server service and the storage node service)
The account names will be Acronis Agent User, AMS User, and ASN User for the agent, management server, and the storage node services, respectively.
Use the following account
If you install the product on a domain controller, the setup program prompts you to specify existing accounts (or the same account) for each service. For security reasons, the setup program does not automatically create new accounts on a domain controller.
Also, choose this setting if you want the management server to use an existing Microsoft SQL server installed on a different machine and use Windows Authentication for the SQL Server.
If you chose the Create a new account or Use the following account option, ensure that the domain security policies do not affect the related accounts' rights. If an account is deprived of the user rights assigned during the installation, the component may work incorrectly or not work.
Management server installation
The database to be used by the management server.
By default, the built-in SQLite database is used. You can select any edition of Microsoft SQL Server 2012, Microsoft SQL Server 2014, or Microsoft SQL Server 2016. The instance you choose can also be used by other programs.
Before selecting an instance installed on another machine, ensure that SQL Server Browser Service and the TCP/IP protocol are enabled on that machine. For instructions on how to start SQL Server Browser Service, refer to: http://msdn.microsoft.com/en-us/library/ms189093.aspx. You can enable the TCP/IP protocol by using a similar procedure.
The port that will be used by a web browser to access the management server (by default, 9877) and the port that will be used for communication between the product components (by default, 7780). Changing the latter port after the installation will require re-registering of all of the components.
Windows Firewall is configured automatically during the installation. If you use a different firewall, ensure that the ports are open for both incoming and outgoing requests through that firewall.
Whether the agents and other components will access the management server by using its host name or the IP address.
By default, the host name is specified. You may need to change this setting if DNS is unable to resolve the host name to the IP address, which results in a component registration failure.
Agent installation
Whether the agent will connect to the Internet through an HTTP proxy server, when backing up to and recovering from the cloud storage.
28 |
Copyright © Acronis International GmbH, 2002-2017 |

If a proxy server is required, specify its host name or IP address and the port number.
2.6.1.2Installation in Linux
Preparation
1.Before installing the product on a system that does not use RPM Package Manager, such as an Ubuntu system, you need to install this manager manually; for example, by running the following command (as the root user): apt-get install rpm.
2.If you want to install Agent for Linux along with the management server, ensure that the necessary Linux packages (p. 20) are installed on the machine.
3.Choose the database to be used by the management server.
By default, the built-in SQLite database is used. As an alternative, you can use PostgreSQL. For information about how to configure the management server for using PostgreSQL, refer to http://kb.acronis.com/content/60395.
Note If you switch to PostgreSQL after the management server has been working for some time, you will have to add devices, configure backup plans and other settings from scratch.
Installation
To install the management server
1.As the root user, run the installation file.
2.Accept the terms of the license agreement.
3.[Optional] Select the components that you want to install. By default, the following components will be installed:
Management Server
Agent for Linux
Bootable Media Builder
4.Specify the port that will be used by a web browser to access the management server. The default value is 9877.
5.Specify the port that will be used for communication between the product components. The default value is 7780.
6.Click Next to proceed with the installation.
7.After the installation completes, select Open web console, and then click Exit. The backup console will open in your default web browser.
2.6.2Adding machines via the web interface
To start adding a machine to the management server, click All devices > Add.
If the management server is installed in Linux, you will be asked to select the setup program based on the type of the machine that you want to add. Once the setup program is downloaded, run it locally on that machine.
The operations described later in this section are possible if the management server is installed in Windows. In most cases, the agent will be silently deployed to the selected machine.
29 |
Copyright © Acronis International GmbH, 2002-2017 |
2.6.2.1Adding a machine running Windows
Preparation
1.For successful installation on a remote machine running Windows XP, the option Control panel > Folder options > View > Use simple file sharing must be disabled on that machine.
For successful installation on a remote machine running Windows Vista or later, the option
Control panel > Folder options > View > Use Sharing Wizard must be disabled on that machine.
2.For successful installation on a remote machine that is not a member of an Active Directory domain, User Account Control (UAC) must be disabled (p. 31).
3.File and Printer Sharing must be enabled on the remote machine. To access this option:
On a machine running Windows XP with Service Pack 2 or Windows 2003 Server: go to
Control panel > Windows Firewall > Exceptions > File and Printer Sharing.
On a machine running Windows Vista, Windows Server 2008, Windows 7, or later: go to
Control panel > Windows Firewall > Network and Sharing Center > Change advanced sharing settings.
4.Acronis Backup uses TCP ports 445 and 25001 for remote installation. Also, it uses TCP port 9876 for remote installation and for communication between the components.
Port 445 is automatically opened when you enable File and Printer Sharing. Ports 9876 and 25001 are automatically opened through Windows Firewall. If you use a different firewall, make sure that these three ports are open (added to exceptions) for both incoming and outgoing requests.
After the remote installation is complete, you can remove ports 445 and 25001 from exceptions. Port 25001 is automatically closed through Windows Firewall. Port 9876 needs to remain open.
Adding the machine
1.Click All devices > Add.
2.Click Windows or the button that corresponds to the application that you want to protect. Depending on the button you click, one of the following options is selected:
Agent for Windows
Agent for Hyper-V
Agent for SQL + Agent for Windows
Agent for Exchange + Agent for Windows
If you clicked Microsoft Exchange Server > Exchange mailboxes, and at least one Agent for Exchange is already registered, you are taken directly to step 5.
Agent for Active Directory + Agent for Windows
Agent for Office 365
3.Specify the host name or IP address of the machine, and the credentials of an account with administrative privileges on that machine.
4.Click Add.
5.If you clicked Microsoft Exchange Server > Exchange mailboxes in step 2, specify the machine where the Client Access server role (CAS) of Microsoft Exchange Server is enabled. For more information, refer to "Mailbox backup" (p. 162).
30 |
Copyright © Acronis International GmbH, 2002-2017 |
 Loading...
Loading...