Page 1
ZyWALL USG 50
Unified Security Gateway
Default Login Details
LAN Port P3, P4
IP Address https://192.168.1.1
User Name admin
Password 1234
www.zyxel.com
Version 2.21
Edition 2, 11/2010
www.zyxel.com
Copyright © 2010
ZyXEL Communications Corporation
Page 2

Page 3

About This User's Guide
About This User's Guide
Intended Audience
This manual is intended for people who want to want to configure the ZyWALL
using the Web Configurator.
How To Use This Guide
•Read Chapter 1 on page 31 chapter for an overview of features available on the
ZyWALL.
•Read Chapter 3 on page 43 for web browser requirements and an introduction
to the main components, icons and menus in the ZyWALL Web Configurator.
•Read Chapter 4 on page 59 if you’re using the installation wizard for first time
setup and you want more detailed information than what the real time online
help provides.
•Read Chapter 5 on page 69 if you’re using the quick setup wizards and y ou want
more detailed information than what the real time online help provides.
• It is highly recommended you read Chapter 6 on page 87 for detailed
information on essential terms us ed in the ZyWALL, what prerequisites are
needed to configure a feature and how to use that feature.
• It is highly recommended you read Chapter 7 on page 109 for ZyWALL
application examples.
• Subsequent chapters are arranged by menu item as defined in the Web
Configurator. Read each chapter carefully for detailed information on that menu
item.
• To find specific information in this guide, use the Contents Overview, the
Table of Contents, the Index, or search the PDF file. E-mail
techwriters@zyxel.com.tw if you cannot find the information you require.
Related Documentation
•Quick Start Guide
The Quick Start Guide is designed to show you how to make the ZyWALL
hardware connections and access the Web Configurator wizards. (See the
wizard real time help for information on configuring each screen.) It also
contains a connection diagram and package contents list.
•CLI Reference Guide
The CLI Reference Guide explains how to use the Command-Line Interface (CLI)
to configure the ZyWALL.
Note: It is recommended you use the Web Configurator to configure the ZyWALL.
ZyWALL USG 50 User’s Guide
3
Page 4

About This User's Guide
• Web Configurator Online Help
Click the help icon in any screen for help in configuring that screen and
supplementary information.
• ZyXEL Web Site
Please refer to www.zyxel.com
product certifications.
for additional support documentation and
User Guide Feedback
Help us help you. Send all User Guide-related comments, questi ons or suggestions
for improvement to the following address, or use e-mail instead. Thank you!
The Technical Writing Team,
ZyXEL Communications Corp.,
6 Innovation Road II,
Science-Based Industrial Park,
Hsinchu, 300, Taiwan.
E-mail: techwriters@zyxel.com.tw
Need More Help?
More help is available at www.zyx el.com.
4
• Download Library
Search for the latest product updates and documentation from this link. Read
the Tech Doc Overview to find out how to efficiently use the User Guide, Quick
Start Guide and Command Line Interface Reference Guide in order to better
understand how to use your product.
• Knowledge Base
If you have a specific question about your product, the answer may be here.
This is a collection of answers to previously asked questions about ZyXEL
products.
ZyWALL USG 50 User’s Guide
Page 5

About This User's Guide
•Forum
This contains discussions on ZyXEL prod ucts. Learn from others who use ZyXEL
products and share your experiences as well.
Customer Support
Should problems arise that cannot be solved by the methods listed above, you
should conta ct your vendor. If you cannot contact your vendor, then contact a
ZyXEL office for the region in which you bought the device.
See http://www.zyxel.com/web/contact_us.php for contact information. Please
have the following informatio n ready when you contact an office.
• Product model and serial number.
•Warranty Information.
• Date that you received your device.
• Brief description of the problem and the steps you took to solve it.
Disclaimer
Graphics in this book may differ slightly from the product due to differences in
operating systems, operating system versions, or if you installed updated
firmware/software fo r y our dev ice. Ev ery effort has been made to ensur e that the
information in this manual is accurate.
ZyWALL USG 50 User’s Guide
5
Page 6

Document Conventions
Warnings and Notes
These are how warnings and notes are shown in this User’s Guide.
Warnings tell you about things that could harm you or your device.
Note: Notes tell you other important information (for example, other things you may
need to configure or helpful tips) or recommendations.
Syntax Conventions
• The ZyWALL may be referred to as the “ZyWALL”, the “device”, the “system” or
the “product” in this User’s Guide.
• Product labels, screen names, field labels and field choices are all in bold font.
Document Conventions
• A key stroke is denoted by square brackets and uppercase text, for example,
[ENTER] means the “enter” or “ret urn” key on your keyboard.
• “Enter” means for you to type one or more characters and then press the
[ENTER] key. “Select” or “choose” means for you to use one of the predefined
choices.
• A right angle bracket ( > ) within a screen name denotes a mouse click. For
example, Maintenance > Log > Log Setting means you first click
Maintenance in the navigation panel, then the Log sub menu and finally the
Log Setting tab to get to that screen.
• Units of measurement may denote the “metric” value or the “scientific” value.
For example, “k” for kilo may denote “1000” or “1024”, “M” for mega may
denote “1000000” or “1048576” and so on.
• “e.g.,” is a shorthand for “for instance”, and “i.e.,” means “that is” or “in other
words”.
6
ZyWALL USG 50 User’s Guide
Page 7
Document Conventions
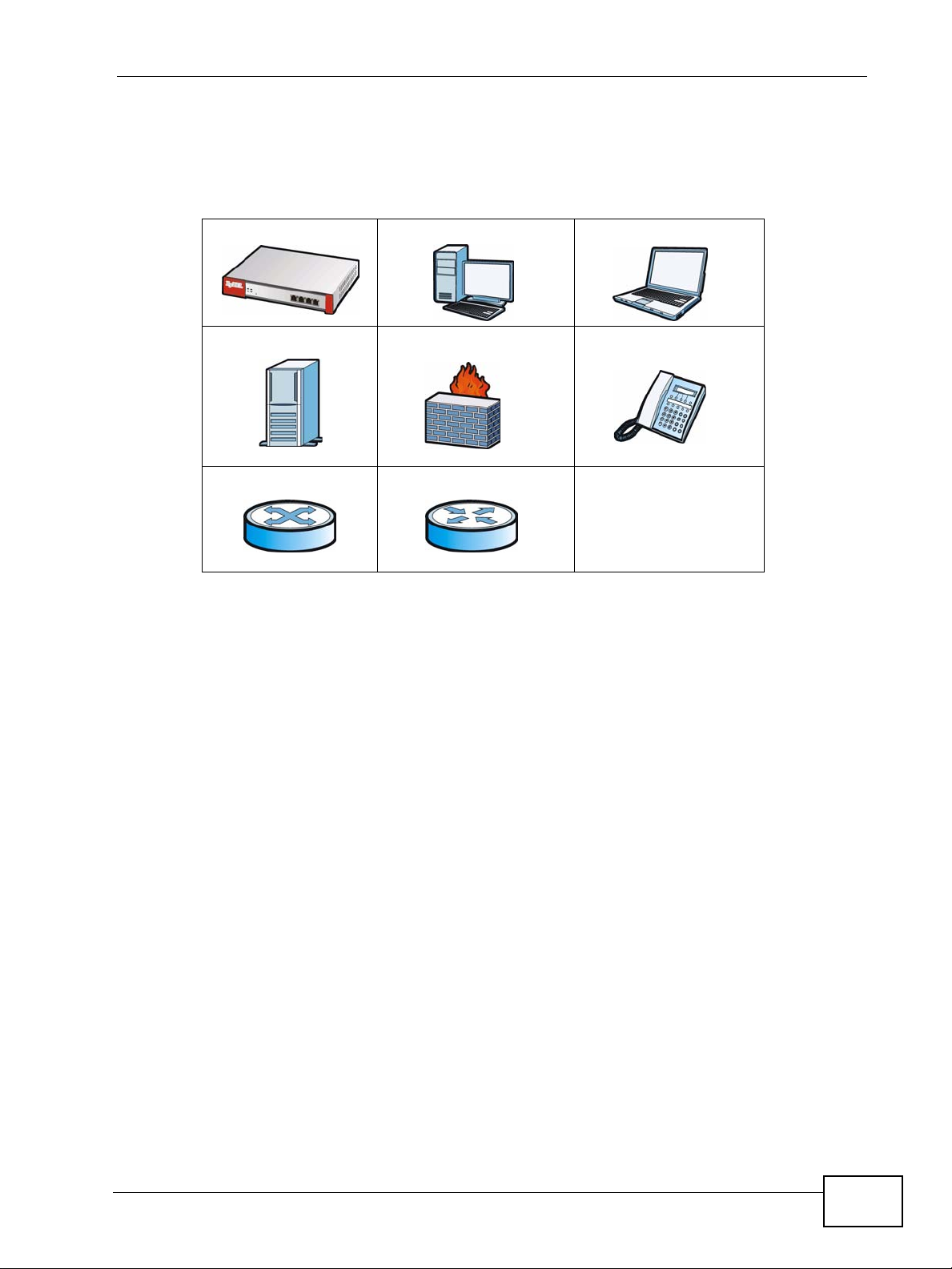
Icons Used in Figures
Figures in this User’s Guide may use the following generic icons. The ZyWALL icon
is not an exact representation of your device.
ZyWALL Computer Notebook computer
Server Firewall Telephone
Switch Router
ZyWALL USG 50 User’s Guide
7
Page 8

Safety Warnings
• Do NOT use this product near water, for example, in a wet basement or near a swimming
pool.
• Do NOT expose your device to dampness, dust or corrosive liquids.
• Do NOT store things on the device.
• Do NOT install, use, or service this device during a thunderstorm. There is a remote risk
of electric shock from lightning.
• Connect ONLY suitable accessories to the device.
• Do NOT open the device or unit. Opening or removing covers can expose you to
dangerous high voltage points or other risks. ONLY qualified service personnel should
service or disassemble this device. Please contact your vendor for further information.
• Make sure to connect the cables to the correct ports.
• Place connecting cables carefully so that no one will step on them or stumble over them.
• Always disconnect all cables from this device before servicing or disassembling.
• Use ONLY an appropriate power adaptor or cord for your device. Connect it to the right
supply voltage (for example, 110V AC in North America or 230V AC in Europe).
• Do NOT remove the plug and connect it to a power outlet by itself; always attach the plug
to the power adaptor first before connecting it to a power outlet.
• Do NOT allow anything to rest on the power adaptor or cord and do NOT place the
product where anyone can walk on the power adaptor or cord.
• Do NOT use the device if the power adaptor or cord is damaged as it might cause
electrocution.
• If the power adaptor or cord is damaged, remove it from the device and the power
source.
• Do NOT attempt to repair the power adaptor or cord. Contact your local vendor to order a
new one.
• Do not use the device outside, and make sure all the connections are indoors. There is a
remote risk of electric shock from lightning.
• CAUTION: RISK OF EXPLOSION IF BATTERY (on the motherboard) IS REPLACED BY AN
INCORRECT TYPE. DISPOSE OF USED BATTERIES ACCORDING TO THE INSTRUCTIONS.
Dispose them at the applicable collection point for the recycling of electrical and
electronic equipment. For detailed information about recycling of this product, please
contact your local city office, your household waste disposal service or the store where
you purchased the product.
• Do NOT obstruct the device ventilation slots, as insufficient airflow may harm your
device.
Safety Warnings
8
Your product is marked with this symbol, which is known as the WEEE mark. WEEE
stands for Waste Electronics and Electrical Equipment. It means that used electrical
and electronic products should not be mixed with general waste. Used electrical and
electronic equipment should be treated separately.
ZyWALL USG 50 User’s Guide
Page 9

Contents Overview
Contents Overview
User’s Guide ........................................................................................................ ...................29
Introducing the ZyWALL ............................................................................................................ 31
Features and Applications ......................................................................................................... 37
Web Configurator ............................................. ... ... ... .... ............................................. ... ... .......... 43
Installation Setup Wizard .................................... ............................................................. ..........59
Quick Setup ............................................................................................................................... 69
Configuration Basics .............. ... ... .............................................................................................. 87
Tutorials ................................................................................................................................... 109
Technical Reference ............................................................................................................155
Dashboard ............................................................................................................................... 157
Monitor ...................................... ....................... ...................... ....................... ........................... 169
Registration ............................................................................................................................. 209
Interfaces ..................................... ....................................................... ..................................... 215
Trunks .................................................... .......................................... ........................................ 271
Policy and Static Routes ..........................................................................................................281
Routing Protocols ....................................................................................................................297
Zones .................................. ................... ................... .................... ................... .........................311
DDNS ...................................................................................................................................... 315
NAT ................................. ............................. .............................. ............................. ................. 321
HTTP Redirect ......................................................................................................................... 331
ALG ......................................................................................................................................... 335
IP/MAC Binding ....................................................................................................................... 343
Authentication Policy .......... ... ................................................ .... ... ........................................... 349
Firewall .................................................................................................................................... 357
IPSec VPN ................... ... .............................................. ... ... ... .... ... ... ........................................ 375
SSL VPN ..................................................................................................................................411
SSL User Screens ................................................................................................................... 421
SSL User Application Screens ................................................................................................ 431
ZyWALL SecuExtender .. .... ... ... ...............................................................................................433
Application Patrol .....................................................................................................................437
Anti-Virus ................................................................................................................................. 463
IDP ............................... .................... ................... ................... .................... ..............................479
ADP ......................................................................................................................................... 513
Content Filtering ....... ... ............................................................................................................533
Content Filter Reports ............................................................................................................. 557
Anti-Spam ................................................................................................................................ 565
User/Group .............................................................................................................................. 583
ZyWALL USG 50 User’s Guide
9
Page 10

Contents Overview
Addresses .............................. ................... .................... ................... ................... ..................... 599
Services ................................. ....................................................... ........................................... 605
Schedules ................................. ................................................. ...............................................611
AAA Server .............................................................................................................................. 617
Authentication Method ................................. ................................................. ... ... .... ................. 627
Certificates ................................... ....................... ....................... ...................... ........................ 633
ISP Accounts ......................................... ... ... .... ... ... ..................................................................655
SSL Application ....................................................................................................................... 659
Endpoint Security .................................................................................................................... 665
System ................................... ...................... ....................... ....................... .............................. 675
Log and Report ........................................................................................................................ 723
File Manager ....................... ... ... ... .... ... ................................................ ... .... .............................. 737
Diagnostics .............................................................................................................................. 749
Reboot ..................................................................................................................................... 755
Shutdown ......................................... ............................. ............................. .............................. 757
Troubleshooting ..................................................... .................................................................. 759
Product Specifications ............................................................................................................. 775
10
ZyWALL USG 50 User’s Guide
Page 11

Table of Contents
Table of Contents
About This User's Guide..........................................................................................................3
Document Conventions............................................................................................................6
Safety Warnings ........................................................................................................................8
Contents Overview ...................................................................................................................9
Table of Contents....................................................................................................................11
Part I: User’s Guide................................................................................ 29
Chapter 1
Introducing the ZyWALL ........................................................................................................31
1.1 Overview and Key Default Settings .....................................................................................31
1.2 Rack-mounted Installation ................................................................................................... 32
1.2.1 Rack-Mounted Installation Procedure ........................................................................ 32
1.3 Front Panel ......................................... ... .... ............................................. ... ... .... ... ... .............33
1.3.1 Front Panel LEDs .......................................... ............................................................. 33
1.4 Management Overview .......... .... ... ... ................................................ .... ... .............................34
1.5 Starting and Stopping the ZyWALL ............................ ... ... .... ................................................ 35
Chapter 2
Features and Applications.....................................................................................................37
2.1 Features ............................................. ... .... ... ............................................. ... .... ... ... .............37
2.2 Applications .................................................. ... ... .... ... ... ... .... ................................................ 39
2.2.1 VPN Connectivity ............. ............................................. ... ... ... .... ... ... .......................... 40
2.2.2 SSL VPN Network Access ........ ... .... ... ... ... .... ... ... ............................................. ... .... ... 40
2.2.3 User-Aware Access Control ....................................................................................... 42
2.2.4 Multiple WAN Interfaces ................... ... ... ... .... ... ... ....................................................... 42
Chapter 3
Web Configurator....................................................................................................................43
3.1 Web Configurator Requirements ......................................................................................... 43
3.2 Web Configurator Access ....................................................................................................43
3.3 Web Configurator Screens Overview .................................................................................. 45
3.3.1 Title Bar .................................. ... ............................................. .... ... ... .......................... 45
3.3.2 Navigation Panel .......... .... ... ... ... ................................................................................. 47
ZyWALL USG 50 User’s Guide
11
Page 12

Table of Contents
3.3.3 Main Window .......................... ... ............................................. .... ... ... ... .... ... ... .............52
3.3.4 Tables and Lists .. ... ... ... .... ... ... ............................................. ... .... ... ... ... .... ...................54
Chapter 4
Installation Setup Wizard.......................................................................................................59
4.1 Installation Setup Wizard Screens ...................................................................................... 59
4.1.1 Internet Access Setup - WAN Interface ..................................................................... 59
4.1.2 Internet Access: Ethernet .......................................................................................... 60
4.1.3 Internet Access: PPPoE ............................................................................................. 62
4.1.4 Internet Access: PPTP .............................................................................................. 63
4.1.5 ISP Parameters ................................... ... ... .... ... ... ............................................. ... .... ... 64
4.1.6 Internet Access Setup - Second WAN Interface ........................................................ 65
4.1.7 Internet Access - Finish .............................................................................................66
4.2 Device Registration ........................................................................................................... 66
Chapter 5
Quick Setup.............................................................................................................................69
5.1 Quick Setup Overview ............................... ... ... ... .... ... ... ... .... ... ... .......................................... 69
5.2 WAN Interface Quick Setup .................................................................................................70
5.2.1 Choose an Ethernet Interface .................................................................... ... ... ... .... ... 70
5.2.2 Select WAN Type ............................. ... ... ... .... ............................................. ... ... ... .......70
5.2.3 Configure WAN Settings ............................................................................................ 71
5.2.4 WAN and ISP Connection Settings ............................................................................ 72
5.2.5 Quick Setup Interface Wizard: Summary ................................................................... 74
5.3 VPN Quick Setup .......... ... ... ... .... ............................................. ... ... ... .... ... ............................. 75
5.4 VPN Setup Wizard: Wizard Type ......................................................................................... 76
5.5 VPN Express Wizard - Scenario ......................................................................................... 77
5.5.1 VPN Express Wizard - Configuration ........................... ... ... ... .... ... ... ... ....................... 78
5.5.2 VPN Express Wizard - Summary ....................................................................... .... ... 79
5.5.3 VPN Express Wizard - Finish .................................................................................... 80
5.5.4 VPN Advanced Wizard - Scenario ............................................................................ 81
5.5.5 VPN Advanced Wizard - Phase 1 Settings ............................................................... 82
5.5.6 VPN Advanced Wizard - Phase 2 ............................................................................. 84
5.5.7 VPN Advanced Wizard - Summary ........................................................................... 85
5.5.8 VPN Advanced Wizard - Finish ................................................................................. 86
Chapter 6
Configuration Basics..............................................................................................................87
12
6.1 Object-based Configuration .......................................................................... .... ... ... .............87
6.2 Zones, Interfaces, and Physical Ports ................................................................................. 88
6.2.1 Interface Types .................................................... ... .... ... ... ... ... .... ... ... .......................... 89
6.2.2 Default Interface and Zone Configuration .................................................................. 89
6.3 Terminology in the ZyWALL ................... .... ... ... ... .... ... ... ............................................. ... .... ... 91
ZyWALL USG 50 User’s Guide
Page 13

Table of Contents
6.4 Packet Flow ........................................ ............................................. .... ... ... ... .... ... ... .............91
6.4.1 Routing Table Checking Flow ..................................................................................... 92
6.4.2 NAT Table Checking Flow ............................. ... ... ... .... ... ... ... ... .... ................................ 94
6.5 Feature Configuration Overview ......................................................................................... 95
6.5.1 Feature ...................................... ... .... ... ... ... .... ... ............................................. ... ... ....... 95
6.5.2 Licensing Registration ............................ ... .... ... ... ... .... ... ... .......................................... 96
6.5.3 Licensing Update ................................................... .... ... ... ... ... .... ... ... ... ....................... 96
6.5.4 Interface .................... ... .............................................. ... ... ... ... .... ... ... .......................... 96
6.5.5 Trunks ............. .... ... ............................................. ... .... ... ... .......................................... 97
6.5.6 Policy Routes ................... ............................................. ... ... ... .... ... ... ... ....................... 97
6.5.7 Static Routes .................................... ... ... ... .............................................. ... ... ... ... ....... 98
6.5.8 Zones ............................................................ ... ... ... ............................................. ....... 98
6.5.9 DDNS ..... ............................................. ... ... .... ... ............................................. ... ... ....... 99
6.5.10 NAT .......................................................................................................................... 99
6.5.11 HTTP Redirect .......................................................................................................... 99
6.5.12 ALG ........................................................................................................................ 100
6.5.13 Auth. Policy ............................................................................................................100
6.5.14 Firewall ................................................................................................................... 101
6.5.15 IPSec VPN ............................................................................................................. 102
6.5.16 SSL VPN ................................................................................................................ 102
6.5.17 Application Patrol ...................................................................................................102
6.5.18 Anti-Virus ................................................................................................................ 103
6.5.19 IDP ......................................................................................................................... 103
6.5.20 ADP ........................................................................................................................ 103
6.5.21 Content Filter ..........................................................................................................104
6.5.22 Anti-Spam ...............................................................................................................104
6.6 Objects ............................................ ... ... .... ............................................. ... ... .... ... ..............105
6.6.1 User/Group ....................... ... ... ............................................. ... .... ... ... ... .... .................106
6.7 System ............. ............................................. ... ... .... ............................................. ..............106
6.7.1 DNS, WWW, SSH, TELNET, FTP, SNMP, Vantage CNM ........................................ 106
6.7.2 Logs and Reports ..................................................................................................... 107
6.7.3 File Manager ....................... ... ... ... ............................................................................ 107
6.7.4 Diagnostics ................ ... .... ... ... ... ... .............................................. ... ... ... .... .................108
6.7.5 Shutdown .................. ... .............................................. ... ... ... ... .... ... ... ........................108
Chapter 7
Tutorials.................................................................................................................................109
7.1 How to Configure Interfaces, Port Roles, and Zones ........................................................ 109
7.1.1 Configure a WAN Ethernet Interface ............................. ... ... ... .... ... ... ... .... ... ... ... ... .... ..110
7.1.2 Configure Port Roles .................................................................................................111
7.1.3 Configure the DMZ Interface for a Local Network ............... ...................................... 111
7.1.4 Configure Zones ........................... .... ... ... ... ................................................................112
7.2 How to Configure a Cellular Interface . ... ................................................. ... ... ......................113
ZyWALL USG 50 User’s Guide
13
Page 14

Table of Contents
7.3 How to Configure Load Balancing ......................................................................................115
7.3.1 Set Up Available Bandwidth on Ethernet Interfaces .................................................115
7.3.2 Configure the WAN Trunk .........................................................................................116
7.4 How to Set Up an IPSec VPN Tunnel .................................................................................118
7.4.1 Set Up the VPN Gateway ..........................................................................................119
7.4.2 Set Up the VPN Connection ..................................................................................... 120
7.4.3 Configure Security Policies for the VPN Tunnel ...................................... ................. 121
7.5 How to Configure User-aware Access Control .................................................................. 122
7.5.1 Set Up User Accounts .............................................................................................. 122
7.5.2 Set Up User Groups ................................................................................................. 123
7.5.3 Set Up User Authentication Using the RADIUS Server ............................. ... ... ... .....124
7.5.4 Web Surfing Policies With Bandwidth Restrictions .................................................. 126
7.5.5 Set Up MSN Policies ................................................................................................ 129
7.5.6 Set Up Firewall Rules ............................................................................................... 130
7.6 How to Use a RADIUS Server to Authenticate User Accounts based on Groups ............. 131
7.7 How to Use Endpoint Security and Authentication Policies ............................................... 133
7.7.1 Configure the Endpoint Security Objects .................................................................133
7.7.2 Configure the Authentication Policy ......................................................................... 135
7.8 How to Configure Service Control ..................................................................................... 136
7.8.1 Allow HTTPS Administrator Access Only From the LAN ......................................... 137
7.9 How to Allow Incoming H.323 Peer-to-peer Calls .................................................. ... ... .... . 139
7.9.1 Turn On the ALG .............................. ... ............................................. ... .... ... ... ...........140
7.9.2 Set Up a NAT Policy For H.323 ................................................................................ 140
7.9.3 Set Up a Firewall Rule For H.323 ............................................................................ 142
7.10 How to Allow Public Access to a Web Server ............................. ... ....... ...... ....... ...... ....... . 143
7.10.1 Create the Address Objects ...................................................................................144
7.10.2 Configure NAT ........................................................................................................ 144
7.10.3 Set Up a Firewall Rule ........................................................................................... 145
7.11 How to Use an IPPBX on the DMZ .................................................................................. 146
7.11.1 Turn On the ALG .................................................................................................... 148
7.11.2 Create the Address Objects ................................................................................... 148
7.11.3 Setup a NAT Policy for the IPPBX .......................................................................... 149
7.11.4 Set Up a WAN to DMZ Firewall Rule for SIP .......................................................... 150
7.11.5 Set Up a DMZ to LAN Firewall Rule for SIP ...... ... .... ... ... ........................................ 151
7.12 How to Use Multiple Static Public WAN IP Addresses for LAN to WAN Traffic ............... 152
7.12.1 Create the Public IP Address Range Object ............ .............................................. 152
7.12.2 Configure the Policy Route .................................................................................... 153
Part II: Technical Reference................................................................ 155
Chapter 8
Dashboard.............................................................................................................................157
14
ZyWALL USG 50 User’s Guide
Page 15

Table of Contents
8.1 Overview ............. ............................................. ... .... ... ... ... .... .............................................. 157
8.1.1 What Yo u Can Do in this Chapter ............................................................................ 157
8.2 The Dashboard Screen ..................................................................................................... 157
8.2.1 The CPU Usage Screen ........................................................................................... 162
8.2.2 The Memory Usage Screen ................... ... .... ... ... ... .... .............................................. 163
8.2.3 The Active Sessions Screen .................................................................................... 164
8.2.4 The VPN Status Screen ...... ... ... ............................................................................... 165
8.2.5 The DHCP Table Screen ..........................................................................................165
8.2.6 The Number of Login Users Screen .............................. ... ... ..................................... 166
Chapter 9
Monitor...................................................................................................................................169
9.1 Overview ............. ............................................. ... .... ... ... ... .... .............................................. 169
9.1.1 What Yo u Can Do in this Chapter ............................................................................ 169
9.2 The Port Statistics Screen ................................................................................................170
9.2.1 The Port Statistics Graph Screen .................... ... ... ................................................. . 172
9.3 Interface Status Screen ..................................................................................................... 173
9.4 The Traffic Statistics Screen ..............................................................................................175
9.5 The Session Monitor Screen ................ .... ... ... ... .... ... ... ... ................................................. . 178
9.6 The DDNS Status Screen .................................................................................................. 181
9.7 IP/MAC Binding Monitor ....................................................................................................181
9.8 The Login Users Screen ................................................................................................... 182
9.9 Cellular Status Screen ..................... ... ............................................. .... ... ... ... .... ... ... ...........183
9.9.1 More Information .... ... ...............................................................................................185
9.10 Application Patrol Statistics .............................................................................................186
9.10.1 Application Patrol Statistics: General Setup ............. ... ... ... ... .... ... ... ... .... ... ... ... ... .... . 187
9.10.2 Application Patrol Statistics: Bandwidth Statistics .................................................. 188
9.10.3 Application Patrol Statistics: Protocol Statistics ..................................................... 189
9.10.4 Application Patrol Statistics: Individual Protocol Statistics by Rule ....................... 190
9.11 The IPSec Monitor Screen .............................................................................................. 191
9.11.1 Regular Expressions in Searching IPSec SAs ....................................................... 192
9.12 The SSL Connection Monitor Screen ..............................................................................193
9.13 The Anti-Virus Statistics Screen ...................................................................................... 194
9.14 The IDP Statistics Screen ........... ... ... ............................................................................... 196
9.15 The Content Filter Statistics Screen ................................................................................ 198
9.16 Content Filter Cache Screen ........................................................................................... 200
9.17 The Anti-Spam Statistics Screen ..................................................................................... 203
9.18 The Anti-Spam Status Screen .........................................................................................205
9.19 Log Screen ......................................................................................................................206
Chapter 10
Registration...........................................................................................................................209
10.1 Overview .......................................................................................................................... 209
ZyWALL USG 50 User’s Guide
15
Page 16

Table of Contents
10.1.1 What You Can Do in this Chapter .......................................................................... 209
10.1.2 What you Need to Know ........................................................................................ 209
10.2 The Registration Screen ...................................................................................................211
10.3 The Service Screen ......................................................................................................... 213
Chapter 11
Interfaces...............................................................................................................................215
11.1 Interface Overview ........................................................................................................... 215
11.1.1 What You Can Do in this Chapter ......................... .... ... ... ... ... .... ... ... ........................ 215
11.1.2 What You Need to Know ........................................................................................ 216
11.2 Port Role ....................... ... ............................................. .... ... ... ... ... .................................. 218
11.3 Ethernet Summary Screen ............................................................................................... 219
11.3.1 Ethernet Edit ..........................................................................................................221
11.3.2 Object References ..................................................................................................230
11.4 PPP Interfaces ................................................................................................................231
11.4.1 PPP Interface Summary ......................................................................................... 232
11.4.2 PPP Interface Add or Edit ..................................................................................... 233
11.5 Cellular Configuration Screen (3G) ..................................................................................237
11.5.1 Cellular Add/Edit Screen ......... ... .... ........................................................................ 239
11.6 VLAN Interfaces .............................................................................................................. 246
11.6.1 VLAN Summary Screen ......................................................................................... 248
11.6.2 VLAN Add/Edit ...................................................................................................... 249
11.7 Bridge Interfaces ............................................................................................................. 256
11.7.1 Bridge Summary .....................................................................................................258
11.7.2 Bridge Add/Edit ................................................... .... ... ... ... ... .... ... ........................... 259
11.7.3 Virtual Interfaces Add/Edit ...................................................................................... 264
11.8 Interface Technical Reference ......................................................................................... 266
Chapter 12
Trunks....................................................................................................................................271
12.1 Overview .......................................................................................................................... 271
12.1.1 What You Can Do in this Chapter .......................................................................... 271
12.1.2 What You Need to Know ........................................................................................ 272
12.2 The Trunk Summary Screen ................................................. ... ... ... .... ... ... ... .... ... ... ... ... .....276
12.3 Configuring a Trunk ........................................................................................................ 277
12.4 Trunk Technical Reference .............................................................................................. 279
Chapter 13
Policy and Static Routes......................................................................................................281
13.1 Policy and Static Routes Overview .................................................................................. 281
13.1.1 What You Can Do in this Chapter .......................................................................... 281
13.1.2 What You Need to Know ....................................................................................... 282
13.2 Policy Route Screen ........................................................................................................ 284
16
ZyWALL USG 50 User’s Guide
Page 17

Table of Contents
13.2.1 Policy Route Edit Screen ....................................................................................... 287
13.3 IP Static Route Screen ....................................................................................................291
13.3.1 Static Route Add/Edit Screen ................................................................................. 292
13.4 Policy Routing Technical Reference ................................................................................ 293
Chapter 14
Routing Protocols .................................................................................................................297
14.1 Routing Protocols Overview ............................................................................................ 297
14.1.1 What You Can Do in this Chapter .......................................................................... 297
14.1.2 What You Need to Know ........................................................................................ 297
14.2 The RIP Screen ... ... .... ... ... ... .... ... ................................................ ... .... ... ........................... 298
14.3 The OSPF Screen ............... .... ... ... ................................................ .... ... ... ........................299
14.3.1 Configuring the OSPF Screen .................................. ......... .......... .......... ......... ........ 303
14.3.2 OSPF Area Add/Edit Screen .................................................................................306
14.3.3 Virtual Link Add/Edit Screen ................................................................................. 307
14.4 Routing Protocol Technical Reference ............................................................................ 308
Chapter 15
Zones .....................................................................................................................................311
15.1 Zones Overview ................................................................................................................311
15.1.1 What You Can Do in this Chapter ...........................................................................311
15.1.2 What You Need to Know ........................................................................................ 312
15.2 The Zone Screen ..................................... ... ................................................ .... ... ..............313
15.3 Zone Edit ........................................................................................................................ 314
Chapter 16
DDNS......................................................................................................................................315
16.1 DDNS Overview .............................................................................................................. 315
16.1.1 What You Can Do in this Chapter .......................................................................... 315
16.1.2 What You Need to Know ........................................................................................ 315
16.2 The DDNS Screen ...........................................................................................................316
16.2.1 The Dynamic DNS Add/Edit Screen ...................................................................... 318
Chapter 17
NAT.........................................................................................................................................321
17.1 NAT Overview .................................................................................................................. 321
17.1.1 What You Can Do in this Chapter .......................................................................... 321
17.1.2 What You Need to Know ........................................................................................ 322
17.2 The NAT Screen .................................. .... ... ... ... .... ................................................ ... ... ..... 322
17.2.1 The NAT Add/Edit Screen . ... ... ... .... ........................................................................ 324
17.3 NAT Technical Reference ................................................................................................327
Chapter 18
HTTP Redirect.......................................................................................................................331
ZyWALL USG 50 User’s Guide
17
Page 18

Table of Contents
18.1 Overview .......................................................................................................................... 331
18.1.1 What You Can Do in this Chapter .......................................................................... 331
18.1.2 What You Need to Know ........................................................................................ 332
18.2 The HTTP Redirect Screen ............................................................................................. 333
18.2.1 The HTTP Redirect Edit Screen ............................................................................. 334
Chapter 19
ALG ........................................................................................................................................335
19.1 ALG Overview ................................................................................................................. 335
19.1.1 What You Can Do in this Chapter .......................................................................... 335
19.1.2 What You Need to Know ........................................................................................ 336
19.1.3 Before You Begin ...................................................................................................339
19.2 The ALG Screen .............................................................................................................. 339
19.3 ALG Technical Reference ................................................................................................ 341
Chapter 20
IP/MAC Binding.....................................................................................................................343
20.1 IP/MAC Binding Overview ............................................................................................... 343
20.1.1 What You Can Do in this Chapter .......................................................................... 343
20.1.2 What You Need to Know ........................................................................................ 344
20.2 IP/MAC Binding Summary ............................................................................................... 344
20.2.1 IP/MAC Binding Edit ............................................................................................... 345
20.2.2 Static DHCP Edit .................................................................................................... 346
20.3 IP/MAC Binding Exempt List ........................................................................................... 347
Chapter 21
Authentication Policy...........................................................................................................349
21.1 Overview .......................................................................................................................... 349
21.1.1 What You Can Do in this Chapter .......................................................................... 349
21.1.2 What You Need to Know ........................................................................................ 350
21.2 Authentication Policy Screen ........................................................................................... 350
21.2.1 Creating/Editing an Authentication Policy .............................................................. 353
Chapter 22
Firewall...................................................................................................................................357
22.1 Overview .......................................................................................................................... 357
22.1.1 What You Can Do in this Chapter .......................................................................... 357
22.1.2 What You Need to Know ........................................................................................ 358
22.1.3 Firewall Rule Example Applications ....................................................................... 360
22.1.4 Firewall Rule Configuration Example ..................................................................... 363
22.2 The Firewall Screen ................. ... ... ... ... ................................................. ... ... .... ................. 365
22.2.1 Configuring the Firewall Screen ............................... .............................................. 366
22.2.2 The Firewall Add/Edit Screen ................................................................................. 369
18
ZyWALL USG 50 User’s Guide
Page 19

Table of Contents
22.3 The Session Limit Screen ................................................................................................370
22.3.1 The Session Limit Add/Edit Screen ........................................................................ 372
Chapter 23
IPSec VPN..............................................................................................................................375
23.1 IPSec VPN Overview .......................................................................................................375
23.1.1 What You Can Do in this Chapter .......................................................................... 375
23.1.2 What You Need to Know ........................................................................................ 376
23.1.3 Before You Begin ...................................................................................................378
23.2 The VPN Connection Screen .......................................................................................... 378
23.2.1 The VPN Connection Add/Edit (IKE) Screen ......................................................... 380
23.2.2 The VPN Connection Add/Edit Manual Key Screen .............................................. 387
23.3 The VPN Gateway Screen .............................................................................................. 390
23.3.1 The VPN Gateway Add/Edit Screen ...................................................................... 391
23.4 IPSec VPN Background Information ............................................................................... 399
Chapter 24
SSL VPN.................................................................................................................................411
24.1 Overview ...........................................................................................................................411
24.1.1 What You Can Do in this Chapter ...........................................................................411
24.1.2 What You Need to Know .........................................................................................411
24.2 The SSL Access Privilege Screen ................................................................................... 413
24.2.1 The SSL Access Policy Add/Edit Screen .............................................................. 414
24.3 The SSL Global Setting Screen .................. ... ... .... ................................................ ... ... .... . 416
24.3.1 How to Upload a Custom Logo .............................................................................. 418
24.4 Establishing an SSL VPN Connection ............................................................................. 419
Chapter 25
SSL User Screens.................................................................................................................421
25.1 Overview .......................................................................................................................... 421
25.1.1 What You Need to Know ........................................................................................ 421
25.2 Remote User Login ..........................................................................................................422
25.3 The SSL VPN User Screens ................................................ ... ... ... .... ... ... ... .... ... ... ... ........427
25.4 Bookmarking the ZyWALL ............................................................................................... 428
25.5 Logging Out of the SSL VPN User Screens ....................................................................428
Chapter 26
SSL User Application Screens ............................................................................................431
26.1 SSL User Application Screens Overview ........................................................................ 431
26.2 The Application Screen ...................................................................................................431
Chapter 27
ZyWALL SecuExtender.........................................................................................................433
ZyWALL USG 50 User’s Guide
19
Page 20

Table of Contents
27.1 The ZyWALL SecuExtender Icon .................................................................................... 433
27.2 Statistics .......................................................................................................................... 434
27.3 View Log ..........................................................................................................................435
27.4 Suspend and Resume the Connection ....................... ..................................................... 435
27.5 Stop the Connection ........................................................................................................ 436
27.6 Uninstalling the ZyWALL SecuExtender .......................................................................... 436
Chapter 28
Application Patrol.................................................................................................................437
28.1 Overview .......................................................................................................................... 437
28.1.1 What You Can Do in this Chapter .......................................................................... 437
28.1.2 What You Need to Know ....................................................................................... 438
28.1.3 Application Patrol Bandwidth Management Examples ........................................... 443
28.2 Application Patrol General Screen ..................................................................................447
28.3 Application Patrol Applications ........................................................................................ 448
28.3.1 The Application Patrol Edit Screen ........................................................................ 449
28.3.2 The Application Patrol Policy Edit Screen ............................................................. 453
28.4 The Other Applications Screen ........................................................................................ 456
28.4.1 The Other Applications Add/Edit Screen ................................................................ 459
Chapter 29
Anti-Virus...............................................................................................................................463
29.1 Overview .......................................................................................................................... 463
29.1.1 What You Can Do in this Chapter .......................................................................... 463
29.1.2 What You Need to Know ........................................................................................ 464
29.1.3 Before You Begin ...................................................................................................465
29.2 Anti-Virus Summary Screen ............. ................................................. ... ... ... .... ... ... ... ... .... . 466
29.2.1 Anti-Virus Policy Add or Edit Screen ......................................................................469
29.3 Anti-Virus Black List .........................................................................................................471
29.4 Anti-Virus Black List or White List Add/Edit ..................................................................... 472
29.5 Anti-Virus White List ...... ... ... .... ... ... ... ... .... ... ... ... ................................................. ... ... ... ..... 473
29.6 Signature Searching ........................................................................................................ 474
29.7 Anti-Virus Technical Reference ........................................................................................ 477
Chapter 30
IDP..........................................................................................................................................479
30.1 Overview .......................................................................................................................... 479
30.1.1 What You Can Do in this Chapter .......................................................................... 479
30.1.2 What You Need To Know ....................................................................................... 479
30.1.3 Before You Begin ...................................................................................................480
30.2 The IDP General Screen ................................................................................................. 481
30.3 Introducing IDP Profiles ................................................................................................. 483
30.3.1 Base Profiles ..........................................................................................................484
20
ZyWALL USG 50 User’s Guide
Page 21

Table of Contents
30.4 The Profile Summary Screen .......................................................................................... 485
30.5 Creating New Profiles ...................................................................................................... 486
30.5.1 Procedure To Create a New Profile ........................................................................ 486
30.6 Profiles: Packet Inspection ............................................................................................. 487
30.6.1 Profile > Group View Screen .................................................................................. 487
30.6.2 Policy Types ........................................................................................................... 490
30.6.3 IDP Service Groups ...............................................................................................491
30.6.4 Profile > Query View Screen .................................................................................. 493
30.6.5 Query Example ...................................................................................................... 495
30.7 Introducing IDP Custom Signatures ............................................................................... 497
30.7.1 IP Packet Header ...................................................................................................497
30.8 Configuring Custom Signatures ..................... ....................... ...................... ..................... 498
30.8.1 Creating or Editing a Custom Signature ................................................................ 500
30.8.2 Custom Signature Example ........................................... ... ..................................... 506
30.8.3 Applying Custom Signatures ..................................................................................508
30.8.4 Verifying Custom Signatures .................................................................................. 509
30.9 IDP Technical Reference .................................................................................................510
Chapter 31
ADP ........................................................................................................................................513
31.1 Overview .......................................................................................................................... 513
31.1.1 ADP and IDP Comparison ..................................................................................... 513
31.1.2 What You Can Do in this Chapter ......................................................................... 513
31.1.3 What You Need To Know ....................................................................................... 513
31.1.4 Before You Begin ...................................................................................................514
31.2 The ADP General Screen ........................ ................................................... ..................... 5 15
31.3 The Profile Summary Screen .......................................................................................... 516
31.3.1 Base Profiles ..........................................................................................................517
31.3.2 Configuring The ADP Profile Summary Screen .....................................................517
31.3.3 Creating New ADP Profiles ............................ ........................................................ 518
31.3.4 Traffic Anomaly Profiles ........................................................................................ 518
31.3.5 Protocol Anomaly Profiles ................................... .... ... ... ... ..................................... 521
31.3.6 Protocol Anomaly Configuration ............................................................................. 521
31.4 ADP Technical Reference ................................................................................................ 525
Chapter 32
Content Filtering...................................................................................................................533
32.1 Overview .......................................................................................................................... 533
32.1.1 What You Can Do in this Chapter .......................................................................... 533
32.1.2 What You Need to Know ........................................................................................ 533
32.1.3 Before You Begin ...................................................................................................535
32.2 Content Filter General Screen .................... ....................................................... ..............535
32.3 Content Filter Policy Add or Edit Screen ......................................................................... 538
ZyWALL USG 50 User’s Guide
21
Page 22

Table of Contents
32.4 Content Filter Profile Screen ..........................................................................................540
32.5 Content Filter Categories Screen ................................................................................... 540
32.5.1 Content Filter Blocked and Warning Messages ..................................................... 552
32.6 Content Filter Customization Screen .............................................................................. 553
32.7 Content Filter Technical Reference ................................................................................. 555
Chapter 33
Content Filter Reports..........................................................................................................557
33.1 Overview .......................................................................................................................... 557
33.2 Viewing Content Filter Reports ............................................. ........................................... 557
Chapter 34
Anti-Spam..............................................................................................................................565
34.1 Overview .......................................................................................................................... 565
34.1.1 What You Can Do in this Chapter .......................................................................... 565
34.1.2 What You Need to Know ........................................................................................ 565
34.2 Before You Begin ............................................................................................................. 567
34.3 The Anti-Spam General Screen ....................................................................................... 567
34.3.1 The Anti-Spam Policy Add or Edit Screen ................................................ .............. 569
34.4 The Anti-Spam Black List Screen .................................................................................... 571
34.4.1 The Anti-Spam Black or White List Add/Edit Screen ...................................... ... .... . 573
34.4.2 Regular Expressions in Black or White List Entries ............................................... 574
34.5 The Anti-Spam White List Screen ....................................................................................575
34.6 The DNSBL Screen ......................................................................................................... 576
34.7 Anti-Spam Technical Reference ...................................................................................... 578
Chapter 35
User/Group............................................................................................................................583
35.1 Overview .......................................................................................................................... 583
35.1.1 What You Can Do in this Chapter .......................................................................... 583
35.1.2 What You Need To Know ....................................................................................... 583
35.2 User Summary Screen .................................................................................................... 586
35.2.1 User Add/Edit Screen ........................... .......... .......... ......... .......... .......... ......... ........ 586
35.3 User Group Summary Screen ......................................................................................... 589
35.3.1 Group Add/Edit Screen .......................................................................................... 590
35.4 Setting Screen ................................................................................................................ 591
35.4.1 Default User Authentication Timeout Settings Edit Screens ..................................594
35.4.2 User Aware Login Example ............... ... ... .... ... ........................................................ 596
35.5 User /Group Technical Reference ................................................................................... 597
Chapter 36
Addresses..............................................................................................................................599
36.1 Overview .......................................................................................................................... 599
22
ZyWALL USG 50 User’s Guide
Page 23

Table of Contents
36.1.1 What You Can Do in this Chapter .......................................................................... 599
36.1.2 What You Need To Know ....................................................................................... 599
36.2 Address Summary Screen ....................... ........................................................................ 599
36.2.1 Address Add/Edit Screen ....................................................................................... 601
36.3 Address Group Summary Screen ............................... ....................... ......................... ..... 602
36.3.1 Address Group Add/Edit Screen ............................................................................ 603
Chapter 37
Services.................................................................................................................................605
37.1 Overview .......................................................................................................................... 605
37.1.1 What You Can Do in this Chapter .......................................................................... 605
37.1.2 What You Need to Know ........................................................................................ 605
37.2 The Service Summary Screen ....................... .......................... .......................... .............. 606
37.2.1 The Service Add/Edit Screen ............................ ..................................................... 608
37.3 The Service Group Summary Screen ........................ ... .... ... ... ... ... .... ... ... ... .... ................. 6 08
37.3.1 The Service Group Add/Edit Screen ...................................................................... 610
Chapter 38
Schedules..............................................................................................................................611
38.1 Overview ...........................................................................................................................611
38.1.1 What You Can Do in this Chapter ...........................................................................611
38.1.2 What You Need to Know .........................................................................................611
38.2 The Schedule Summary Screen ...................................................................................... 612
38.2.1 The One-Time Schedule Add/Edit Screen ............................................................. 613
38.2.2 The Recurring Schedule Add/Edit Screen ............................................... ... ... ... .... . 614
Chapter 39
AAA Server............................................................................................................................617
39.1 Overview .......................................................................................................................... 617
39.1.1 Directory Service (AD/LDAP) ................................................................ ................. 617
39.1.2 RADIUS Server ...................................................................................................... 618
39.1.3 ASAS ...................................................................................................................... 618
39.1.4 What You Can Do in this Chapter .......................................................................... 618
39.1.5 What You Need To Know ....................................................................................... 619
39.2 Active Directory or LDAP Server Summary ..................................................................... 621
39.2.1 Adding an Active Directory or LDAP Server ............. ............ ............. ............. ........ 621
39.3 RADIUS Server Summary ............................................................................................... 623
39.3.1 Adding a RADIUS Server ...................................................................................... 625
Chapter 40
Authentication Method.........................................................................................................627
40.1 Overview .......................................................................................................................... 627
40.1.1 What You Can Do in this Chapter .......................................................................... 627
ZyWALL USG 50 User’s Guide
23
Page 24

Table of Contents
40.1.2 Before You Begin ...................................................................................................627
40.1.3 Example: Selecting a VPN Authentication Method ................................................ 627
40.2 Authentication Method Objects ...................................... .................................... .............. 628
40.2.1 Creating an Authentication Method Object ........................................... ... ... ... ... .... . 629
Chapter 41
Certificates ............................................................................................................................633
41.1 Overview .......................................................................................................................... 633
41.1.1 What You Can Do in this Chapter .......................................................................... 633
41.1.2 What You Need to Know ........................................................................................ 633
41.1.3 Verifying a Certificate .............................................................................................635
41.2 The My Certificates Screen ............................................................................................. 637
41.2.1 The My Certificates Add Screen ............................................................................ 638
41.2.2 The My Certificates Edit Screen ........... ............................................. .... ... ... ... ... .... . 643
41.2.3 The My Certificates Import Screen ........................................................................ 646
41.3 The Trusted Certificates Screen ..................................................................................... 647
41.3.1 The Trusted Certificates Edit Screen .................................................................... 648
41.3.2 The Trusted Certificates Import Screen ................................................................652
41.4 Certificates Technical Reference ..................................................................................... 653
Chapter 42
ISP Accounts.........................................................................................................................655
42.1 Overview .......................................................................................................................... 655
42.1.1 What You Can Do in this Chapter .......................................................................... 655
42.2 ISP Account Summary .................................................................................................... 655
42.2.1 ISP Account Edit ................................................................................................... 656
Chapter 43
SSL Application ....................................................................................................................659
43.1 Overview .......................................................................................................................... 659
43.1.1 What You Can Do in this Chapter .......................................................................... 659
43.1.2 What You Need to Know ........................................................................................ 659
43.1.3 Example: Specifying a Web Site for Access .......................................................... 660
43.2 The SSL Application Screen .......................... ... .... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .... . 661
43.2.1 Creating/Editing a Web-based SSL Application Object ......................................... 662
Chapter 44
Endpoint Security.................................................................................................................665
44.1 Overview .......................................................................................................................... 665
44.1.1 What You Can Do in this Chapter .......................................................................... 666
44.1.2 What You Need to Know ........................................................................................ 666
44.2 Endpoint Security Screen ........ ................................................ ... ... .... ... ... ... .... ... ... ... ... .... . 667
44.3 Endpoint Security Add/Edit .............................................................................................. 669
24
ZyWALL USG 50 User’s Guide
Page 25

Table of Contents
Chapter 45
System...................................................................................................................................675
45.1 Overview .......................................................................................................................... 675
45.1.1 What You Can Do in this Chapter .......................................................................... 675
45.2 Host Name ....................................................................................................................... 676
45.3 Date and Time ................................................................................................................ 676
45.3.1 Pre-defined NTP Time Servers List ............................................. ... ... .... ... ... ... ... .... . 679
45.3.2 Time Server Synchronization ................................................................................. 680
45.4 Console Port Speed ......................................................................................................... 681
45.5 DNS Overview ................................................................................................................. 681
45.5.1 DNS Server Address Assignment .......................................................................... 682
45.5.2 Configuring the DNS Screen ................................ .......................................... ........ 682
45.5.3 Address Record .................................................................................................... 685
45.5.4 PTR Record ........................................................................................................... 685
45.5.5 Adding an Address/PTR Record ............................................................................ 685
45.5.6 Domain Zone Forwarder ............... ............................................. ... ... .... ................. 686
45.5.7 Adding a Domain Zone Forwarder ................................. ........................................ 6 86
45.5.8 MX Record ............................................................................................................687
45.5.9 Adding a MX Record ..............................................................................................688
45.5.10 Adding a DNS Service Control Rule ................................................................... . 688
45.6 WWW Overview ..............................................................................................................689
45.6.1 Service Access Limitations .................................................................................... 689
45.6.2 System Timeout ..................................................................................................... 690
45.6.3 HTTPS ...................................................................................................................690
45.6.4 Configuring WWW Service Control ........................................................................ 691
45.6.5 Service Control Rules ............................................................................................ 695
45.6.6 Customizing the WWW Login Page ....................................................................... 695
45.6.7 HTTPS Example ....................................................................................................699
45.7 SSH .............................................................................................................................. 706
45.7.1 How SSH Works ......................................................... ... ... ... .... ... ... ........................ 707
45.7.2 SSH Implementation on the ZyWALL ..................................................................... 708
45.7.3 Requirements for Using SSH ................................................................................. 708
45.7.4 Configuring SSH ....................................................................................................708
45.7.5 Secure Telnet Using SSH Examples ...................................................................... 710
45.8 Telnet ...............................................................................................................................711
45.8.1 Configuring Telnet .................................................................................................. 712
45.9 FTP ................................................................................................................................. 713
45.9.1 Configuring FTP .....................................................................................................713
45.10 SNMP ........................................................................................................................... 715
45.10.1 Supported MIBs ................................................................................................... 717
45.10.2 SNMP Traps ......................................................................................................... 717
45.10.3 Configuring SNMP ............................................................................................... 717
45.11 Vantage CNM ........................ ... ... ... ... .... ........................................................................ 719
ZyWALL USG 50 User’s Guide
25
Page 26

Table of Contents
45.11.1 Configuring Vantage CNM .. ... ... ................................................. ... ... ..................... 720
45.12 Language Screen .........................................................................................................722
Chapter 46
Log and Report .....................................................................................................................723
46.1 Overview .......................................................................................................................... 723
46.1.1 What You Can Do In this Chapter .......................................................................... 723
46.2 Email Daily Report ..........................................................................................................723
46.3 Log Setting Screens ....................................................................................................... 725
46.3.1 Log Setting Summary ............................................................................................. 726
46.3.2 Edit System Log Settings ......................................................................................727
46.3.3 Edit Remote Server Log Settings .......................................................................... 732
46.3.4 Active Log Summary Screen ................................ ............. .......... ............. ............. . 734
Chapter 47
File Manager..........................................................................................................................737
47.1 Overview .......................................................................................................................... 737
47.1.1 What You Can Do in this Chapter .......................................................................... 737
47.1.2 What you Need to Know ........................................................................................ 737
47.2 The Configuration File Screen .............................. ...................................................... .....740
47.3 The Firmware Package Screen ...................................................................................... 744
47.4 The Shell Script Screen .......................... ....................................................... .................746
Chapter 48
Diagnostics............................................................................................................................749
48.1 Overview .......................................................................................................................... 749
48.1.1 What You Can Do in this Chapter .......................................................................... 749
48.2 The Diagnostic Screen ....................................................................................................749
48.3 The Packet Capture Screen ............................................................................................750
48.3.1 The Packet Capture Files Screen .......................................................................... 752
48.3.2 Example of Viewing a Packet Capture File .............................. ... ... ... .... ... ... ... ... .....753
Chapter 49
Reboot....................................................................................................................................755
49.1 Overview .......................................................................................................................... 755
49.1.1 What You Need To Know ....................................................................................... 755
49.2 The Reboot Screen .........................................................................................................755
Chapter 50
Shutdown...............................................................................................................................757
50.1 Overview .......................................................................................................................... 757
50.1.1 What You Need To Know ....................................................................................... 757
50.2 The Shutdown Screen ..................................................................................................... 757
26
ZyWALL USG 50 User’s Guide
Page 27

Table of Contents
Chapter 51
Troubleshooting....................................................................................................................759
51.1 Resetting the ZyWALL .....................................................................................................773
51.2 Getting More Troubleshooting Help ................................................................................. 774
Chapter 52
Product Specifications.........................................................................................................775
52.1 Power Adaptor Specifications .......................................................................................... 780
Appendix A Log Descriptions...............................................................................................783
Appendix B Common Services.............................................................................................841
Appendix C Importing Certificates........................................................................................845
Appendix D Open Software Announcements.......................................................................871
Appendix E Legal Information..............................................................................................917
Index.......................................................................................................................................921
ZyWALL USG 50 User’s Guide
27
Page 28

Table of Contents
28
ZyWALL USG 50 User’s Guide
Page 29
PART I
User’s Guide
29
Page 30

30
Page 31

CHAPTER 1
Introducing the ZyWALL
This chapter gives an overview of the ZyWALL. It explains the front panel ports,
LEDs, introduces the management methods, and lists different ways to start or
stop the ZyWALL.
1.1 Overview and Key Default Settings
The ZyWALL is a comprehensive security device. Its flexible configuration helps
network administrators set up the network and enforce security policies efficiently.
In addition, the ZyWALL provides excellent throughput, making it an ideal solution
for reliable, secure service.
The ZyWALL’s security features include VPN, firewall, anti-virus, content filtering,
IDP (Intrusion Detection and Prevention), ADP (Anomaly Detection and
Protection), and certificates. It also provides bandwidth management, Instant
Messaging (IM) and Peer to Peer (P2P) control, NAT, port forwarding, policy
routing, DHCP server and many other powerful features. Flexible configuration
helps you set up the network and enforce security policies efficiently. See Chapter
2 on page 37 for a more detailed overview of the ZyWALL’s features.
The ZyWALL provides ex cellent throughput with the reliability of dual WAN Gigabit
Ethernet ports and load balancing. You can also use a 3G cellular USB (not
included) for a third WAN connection.
The ZyWALL lets you set up multiple networks for your company. The DeMilitarized Zone (DMZ) increases LAN security by providing separate ports for
connecting publicly accessible servers. The ZyWALL also provides two separate
LAN networks. Y ou can set ports to be part of the LAN1, or DMZ. Alternatively, you
can deploy the ZyWALL as a transparent firewall in an existing network with
minimal configuration.
ZyWALL USG 50 User’s Guide
31
Page 32

Chapter 1 Introducing the ZyWALL
1.2 Rack-mounted Installation
The ZyWALL can be mounted on an EIA standard size, 19-inch rack or in a wiring
closet with other equipment. Follow the steps below to mount your ZyWALL on a
standard EIA rack using a rack-mounting kit. Make sure the rack will safely
support the combined weight of all the equipment it contains and that the position
of the ZyWALL does not make the rack unstable or top-heavy. Take all necessary
precautions to anchor the rack securely before installing the unit.
Note: Leave 10 cm of clearance at the sides and 20 cm in the rear.
Use a #2 Phillips screwdriver to install the screws.
Note: Failure to use the proper screws may damage the unit.
1.2.1 Rack-Mounted Installation Procedure
1 Align one bracket with the holes on one side of the Z yW ALL and secure it with the
included bracket screws (smaller than the rack-mounting screws).
2 Attach the other bracket in a similar fashion.
Figure 1 Attaching Mounting Brackets and Screws
32
ZyWALL USG 50 User’s Guide
Page 33

Chapter 1 Introducing the ZyWALL
3 After attaching both mounting brackets, position the ZyWALL in the rack by lining
up the holes in the brackets with the appropriate holes on the rack. Secure the
ZyWALL to the rack with the rack-mounting screws.
Figure 2 Rack Mounting
1.3 Front Panel
This section introduces the ZyWALL’s front panel.
Figure 3 ZyWALL Front Panel
1.3.1 Front Panel LEDs
The following table describes the LEDs.
Table 1 Front Panel LEDs
LED COLOR STATUS DESCRIPTION
PWR Off The ZyWALL is turned off.
Green On The ZyWALL is turned on.
Red On There is a hardware component failure. Shut down
Breathing The ZyWALL is in power saving mode.
the device, wait for a few minutes and then restart
the device (see Section 1.5 on page 35). If the LED
turns red again, then please contact your vendor.
ZyWALL USG 50 User’s Guide
33
Page 34

Chapter 1 Introducing the ZyWALL
Table 1 Front Panel LEDs (continued)
LED COLOR STATUS DESCRIPTION
SYS Green Off The ZyWALL is not ready or has failed.
On The ZyWALL is ready and running.
Blinking The ZyWALL is booting.
Red On The ZyWALL had an error or has failed.
1, 2 ... Green Off There is no traffic on this port.
Blinking The ZyWALL is sending or receiving packets on this
port.
Orange Off There is no connection on this port.
On This port has a successful link.
1.4 Management Overview
You can use the following ways to manage the ZyWALL.
Web Configurator
The Web Configurator allows easy ZyWALL setup and management using an
Internet browser. This User’s Guide provides information about the Web
Configurator.
Figure 4 Managing the ZyWALL: Web Configurator
Command-Line Interface (CLI)
The CLI allows you to use text-based commands to configure the ZyWALL. You can
access it using remote management (for example, SSH or Telnet) or via the
console port. See the Command Reference Guide for more information about the
CLI.
34
ZyWALL USG 50 User’s Guide
Page 35

Chapter 1 Introducing the ZyWALL
Console Port
You can use the console port to manage the ZyWALL using CLI commands. See
the Command Reference Guide for more information about the CLI.
The default settings for the console port are as follows.
Table 2 Console Port Default Settings
SETTING VALUE
Speed 115200 bps
Data Bits 8
Parity None
Stop Bit 1
Flow Control Off
1.5 Starting and Stopping the ZyWALL
Here are some of the ways to start and stop the ZyWAL L.
Always use Maintenance > Shutdown > Shut down or the shutdown
command before you turn off the ZyWALL or remove the power. Not
doing so can cause the firmware to become corrupt.
Table 3 Starting and Stopping the ZyWALL
METHOD DESCRIPTION
Turning on the
power
Rebooting the
ZyWALL
Using the RESET
button
Clicking
Maintenance >
Shutdown >
Shutdown or
using the shutdown
command
Disconnecting the
power
A cold start occurs when you turn on the power to the ZyWA LL. The
ZyWALL powers up, checks the hardware, and starts the system
processes.
A warm start (without powering down and powering up again)
occurs when you use the Reboot button in the Reboot screen or
when you use the reboot command. The ZyWALL writes all cached
data to the local storage, stops the system processes, and then does
a warm start.
If you press the RESET button, the ZyWALL sets the configuration
to its default values and then reboots.
Clicking Maintenance > Shutdown > Shutdown or using the
shutdown command writes all cached data to the local storage and
stops the system processes. Wait for the device to shut down and
then manually turn off or remove the power. It does not turn off the
power.
Power off occurs when you turn off the power to the ZyWALL. The
ZyWALL simply turns off. It does not stop the system processes or
write cached data to local storage.
ZyWALL USG 50 User’s Guide
35
Page 36

Chapter 1 Introducing the ZyWALL
The ZyWALL does not stop or start the system processes when you apply
configuration files or run shell scripts although you may temporarily lose access to
network resources.
36
ZyWALL USG 50 User’s Guide
Page 37

CHAPTER 2
Features and Applications
This chapter introduces the main features and applications of the ZyWALL.
2.1 Features
The ZyWALL’s security features include VPN, firewall, anti-virus, content filtering,
IDP (Intrusion Detection and Prevention), ADP (Anomaly Detection and
Protection), and certificates. It also provides bandwidth management, NAT, port
forwarding, policy routing, DHCP server and many other powerful features.
The rest of this section provides more information about the features of the
ZyWALL.
High Availability
To ensure the ZyWALL provides reliable, secure Internet access, set up one or
more of the following:
• Multiple WAN ports and configure load balancing between these ports.
• One or more 3G (cellular) connections.
Virtual Private Networks (VPN)
Use IPSec, SSL to provide secure communication between two sites over the
Internet or any insecure network that uses TCP/IP for communication. The
ZyWALL also offers hub-and-spoke IPSec VPN.
Flexible Security Zones
Many security settings are made by zone, not by interface, port, or network. As a
result, it is much simpler to set up and to change security settings in the ZyWALL.
You can create y our own custom zones. You can add interfaces and VPN tunnels to
zones.
ZyWALL USG 50 User’s Guide
37
Page 38

Chapter 2 Features and Applications
Firewall
The ZyWALL’ s firew all is a stateful inspection firew all. The Z yWALL rest ricts access
by screening data packets against defined access rules. It can also inspect
sessions. For example, traffic from one zone is not allowed unless it is ini tiated by
a computer in another zone first.
Intrusion Detection and Prevention (IDP)
IDP (Intrusion Detection and Protection) can detect malicious or suspicious
packets and respond instantaneously. It detects pattern-based attacks in order to
protect against network-based intrusions. See Section 30.6.2 on page 490 for a
list of attacks that the ZyWALL can protect against. You can also create your own
custom IDP rules.
Anomaly Detection and Prevention (ADP)
ADP (Anomaly Detection and Prevention) can detect malicious or suspicious
packets and respond instantaneously. It can detect:
• Anomalies based on violations of protocol standards (RFCs – Requests for
Comments)
• Abnormal flows such as port scans.
The ZyWALL’s ADP protects against network-based intrusions. See Section 31.3.4
on page 518 and Section 31.3.5 on page 521 for more on the kinds of attacks that
the ZyWALL can protect against. You can also create your own custom ADP rules.
Bandwidth Management
Bandwidth management allows you to allocate network resources according to
defined policies. This policy-based bandwidth allocation helps your network to
better handle applications such as Internet access, e-mail, Voice-over-IP (VoIP),
video conferencing and other business-critical applications.
Content Filter
Content filtering allows schools and businesses to create and enforce Internet
access policies tailored to the needs of the organization.
You can also subscribe to category-based content filtering that allows your
ZyWALL to check web sites against an external database of dynamically-updated
ratings of millions of web sites. You then simply select categories to block or
monitor, such as pornography or racial intolerance, from a pre-defined list.
38
ZyWALL USG 50 User’s Guide
Page 39

Chapter 2 Features and Applications
Anti-Virus Scanner
With the anti-virus packet scanner, your ZyWALL scans files transmitting through
the enabled interfaces into the network. The ZyWALL helps stop threats at the
network edge before they reach the local host computers.
Anti-Spam
The anti-spam feature can mark or discard spam. Use the white list to identify
legitimate e-mail. Use the black list to identify spam e-mail. The ZyWALL can also
check e-mail against a DNS black list (DNSBL) of IP addresses of servers that are
suspected of being used by spammers.
Application Patrol
Application patrol (App. Patrol) manages instant messenger (IM), peer-to-peer
(P2P) applications like MSN and BitTorrent. You can even control the use of a
particular application’s individual features (like text messaging, voice, video
conferencing, and file transfers). Application patrol has powerful bandwidth
management including traffic prioritization to enhance the performance of delaysensitive applications like voice and video. You can also use an option that gives
SIP priority over all other traffic. This maximizes SIP traffic throughput for
improved VoIP call sound quality.
2.2 Applications
These are some example applications for your ZyWALL. See also Chapter 7 on
page 109 for configuration tutorial examples.
ZyWALL USG 50 User’s Guide
39
Page 40

Chapter 2 Features and Applications
2.2.1 VPN Connectivity
Set up VPN tunnels with other companies, branch offices, telecommuters, and
business travelers to provide secure access to your network. You can also set up
additional connections to the Internet to provide better service.
Figure 5 Applications: VPN Connectivity
2.2.2 SSL VPN Network Access
You can configure the ZyWALL to provide SSL VPN network access to remote
users.
40
ZyWALL USG 50 User’s Guide
Page 41

2.2.2.1 Full Tunnel Mode
In full tunnel mode, a virtual connection is created for remote users with private
IP addresses in the same subnet as the local network. This allows them to access
network resources in the same way as if they were part of the internal network.
Figure 6 Network Access Mode: Full Tunnel Mode
192.168.1.100
Chapter 2 Features and Applications
https;//
LAN (192.168.1.X)
Web Mail File Share
Web-based Application
Non-Web
Application
Server
ZyWALL USG 50 User’s Guide
41
Page 42

Chapter 2 Features and Applications
2.2.3 User-Aware Access Control
Set up security policies that restrict access to sensitive information and shared
resources based on the user who is trying to access it.
Figure 7 Applications: User-Aware Access Control
2.2.4 Multiple WAN Interfaces
Set up multiple connections to the Internet on the same port, or set up multiple
connections on different ports. In either case, you can balance the loads between
them.
Figure 8 Applications: Multiple WAN Interfaces
42
ZyWALL USG 50 User’s Guide
Page 43

CHAPTER 3
Web Configurator
The ZyWALL Web Configurator allows easy ZyWALL setup and management using
an Internet browser.
3.1 Web Configurator Requirements
In order to use the Web Configurator, you must
• Use Internet Explorer 7 or later, or Firefox 1.5 or later
• Allow pop-up windows (blocked by default in Windows XP Service Pack 2)
• Enable JavaScripts (enabled by default)
• Enable Java permissions (enabled by default)
• Enable cookies
The recommended screen resolution is 1024 x 768 pixels.
3.2 Web Configurator Access
1 Make sure your ZyWALL hardware is properly connected. See the Quick Start
Guide.
ZyWALL USG 50 User’s Guide
43
Page 44

Chapter 3 Web Configurator
2 Open your web browser, and go to http://192.168.1.1. By default, the ZyWALL
automatically routes this request to its HTTPS server, and it is recommended to
keep this setting. The Login screen appears.
Figure 9 Login Screen
3 Type the user name (default: “admin”) and password (default: “1234”).
If your account is configured to use an ASAS auth entication server, use the OTP
(One-Time Password) token to generate a number. Enter it in the One-Time
Password field. The number is only good for one login. You must use the token to
generate a new number the next time you log in.
4 Click Login. If you logged in using the default user name and password, the
Update Admin Info screen (Figure 10 on page 44) appears. Otherwise, the
dashboard (Figure 11 on page 45) appears.
Figure 10 Update Admin Info Screen
44
ZyWALL USG 50 User’s Guide
Page 45

B
Chapter 3 Web Configurator
5 The screen above appears every time you log in using the default user name and
default password. If you change the password for the default user account, this
screen does not appear anymore.
Follow the directions in this screen. If you change the default password, the Login
screen (Figure 9 on page 44) appears after you click Apply. If you click Ignore,
the Installation Setup Wizard opens if the ZyWALL is using its default
configuration (see Chapter 4 on page 59); otherwise the dashboard appears as
shown next.
Figure 11 Dashboard
A
C
3.3 Web Configurator Screens Overview
The Web Configurator screen is di vided into these parts (as illustr ated in Figure 11
on page 45):
• A - title bar
• B - navigation panel
• C - main window
3.3.1 Title Bar
The title bar provides some icons in the upper right corner.
Figure 12 Title Bar
ZyWALL USG 50 User’s Guide
45
Page 46

Chapter 3 Web Configurator
The icons provide the following functions.
Table 4 Title Bar: Web Configurator Icons
LABEL DESCRIPTION
Logout Click this to log out of the Web Configurator.
Help Click this to open the help page for the current screen.
About Click this to display basic information about the ZyWALL.
Site Map Click this to see an overview of links to the Web Configurator screens.
Object
Reference
Console Click this to open the console in which you can use the command line
CLI Click this to open a popup window that displays the CLI commands sent
3.3.1.1 About
Click this to display basic information about the ZyWALL.
Click this to open a screen where you can check which configuration
items reference an object.
interface (CLI). See the CLI Reference Guide for details on the
commands.
by the Web Configurator.
Figure 13 Title Bar
The following table describes labels that can appear in this screen.
Table 5 Title Bar: Web Configurator Icons
LABEL DESCRIPTION
Boot Module This shows the version number of the software that handles the booting
process of the ZyWALL.
Current
Version
Released Date This shows the date (yyyy-mm-dd) and time (hh:mm:ss) when the
OK Click this to close the screen.
This shows the firmware version of the ZyWALL.
firmware is released.
46
ZyWALL USG 50 User’s Guide
Page 47

3.3.2 Navigation Panel
Use the menu items on the navigation panel to open screens to configure Z yW ALL
features. Click the arrow in the middle of the right edge of the navigation panel to
hide the navigation panel menus or drag it to resize them. The following sections
introduce the ZyWALL’s navigation panel menus and their screens.
Figure 14 Navigation Panel
Chapter 3 Web Configurator
3.3.2.1 Dashboard
The dashboard displays general device information, system status, system
resource usage, licensed service status, and interface status in widgets that you
can re-arrange to suit your needs. See Chapter 8 on page 157 for details on the
dashboard.
3.3.2.2 Monitor Menu
The monitor menu screens display status and statistics information.
Table 6 Monitor Menu Screens Summary
FOLDER OR LINK TAB FUNCTION
System Status
Port Statistics Displays packet statistics for each physical port.
Interface Status Displays general interface information and packet
Traffic Statistics Collect and display traffic statistics.
Session Monitor Displays the status of all current sessions.
DDNS Status Displays the status of the ZyWALL’s DDNS domain names.
IP/MAC Binding Lists the devices that have received an IP address from
Login Users Lists the users currently logged into the ZyWALL.
Cellular Status Displays details about the ZyWALL’ s 3G connection status.
statistics.
ZyWALL interfaces using IP/MAC binding.
ZyWALL USG 50 User’s Guide
47
Page 48

Chapter 3 Web Configurator
Table 6 Monitor Menu Screens Summary (continued)
FOLDER OR LINK TAB FUNCTION
AppPatrol Statistics Displays bandwidth and protocol statistics.
VPN Monitor
IPSec Displays and manages the active IPSec SAs.
SSL Lists users currently logged into the VPN SSL client portal.
Anti-X Statistics
Anti-Virus Collect and display statistics on the viruses that the
IDP Collect and display statistics on the intrusions that the
Content Filter Report Collect and display content filter statistics
Anti-Spam Report Collect and display spam statistics.
Log Lists log entries.
You can also log out individual users and delete related
session information.
ZyWALL has detected.
ZyWALL has detected.
Cache Manage the ZyWALL’s URL cache.
Status Displays how many mail sessions the ZyWALL is currently
checking and DNSBL (Domain Name Service-based spam
Black List) statistics.
3.3.2.3 Configuration Menu
Use the configuration menu screens to configure the ZyWALL’s features.
Table 7 Configuration Menu Screens Summary
FOLDER OR
LINK
Quick Setup Quickly configure WAN interfaces or VPN
Licensing
Registration Registration Register the device and activate trial services.
Signature
Update
Network
TAB FUNCTION
Service View the licensed service status and upgrade
Anti-Virus Update anti-virus signatures immediately or by a
IDP/AppPatrol Update IDP signatures immediately or by a
System Protect Update system-protect signatures immediately or
connections.
licensed services.
schedule.
schedule.
by a schedule.
48
ZyWALL USG 50 User’s Guide
Page 49

Chapter 3 Web Configurator
Table 7 Configuration Menu Screens Summary (continued)
FOLDER OR
LINK
Interface Port Role Use this screen to set the ZyWALL’s flexible ports
Routing Policy Route Create and manage routing policies.
Zone Configure zones used to define various policies.
DDNS Profile Define and manage the ZyWALL’s DDNS domain
NAT Set up and manage port forwarding rules.
HTTP Redirect Set up and manage HTTP redirection rules.
ALG Configure SIP, H.323, and FTP pass-through
IP/MAC
Binding
Auth. Policy Define rules to force user authentication.
Firewall Firewall Create and manage level-3 traffic rules.
VPN
IPSec VPN VPN Connection Configure IPSec tunnels.
SSL VPN Access Privilege Configure SSL VPN access rights for users and
TAB FUNCTION
as LAN1 or DMZ.
Ethernet Manage Ethernet interfaces and virtual Ethernet
interfaces.
PPP Create and manage PPPoE and PPTP interfaces.
Cellular Configure a cellular Internet connection for an
installed 3G card.
VLAN Create and manage VLAN interfaces and virtual
VLAN interfaces.
Bridge Create and manage bridges and virtual bridge
interfaces.
Trunk Create and manage trunks (groups of interfaces)
for load balancing and link High Availability (HA).
Static Route Create and manage IP static routing information.
RIP Configure device-level RIP settings.
OSPF Configure device-level OSPF settings, including
areas and virtual links.
names.
settings.
Summary Configure IP to MAC address bindings for devices
connected to each supported interface.
Exempt List Configure ranges of IP addresses to which the
ZyWALL does not apply IP/MAC binding.
Session Limit Limit the number of concurrent client NAT/firewall
sessions.
VPN Gateway Configure IKE tunnels.
groups.
Global Setting Configure the ZyWALL’s SSL VPN settings that
apply to all connections.
ZyWALL USG 50 User’s Guide
49
Page 50

Chapter 3 Web Configurator
Table 7 Configuration Menu Screens Summary (continued)
FOLDER OR
LINK
AppPatrol General Enable or disable traffic management by
Anti-X
Anti-Virus General Turn anti-virus on or off, set up anti-virus policies
IDP General Display and manage IDP bindings.
ADP General Display and manage ADP bindings.
Content Filter General Create and manage content filter policies.
Anti-Spam General Turn anti-spam on or off and manage anti-spam
Object
User/Group User Create and manage users.
Address Address Create and manage host, range, and network
TAB FUNCTION
application and see registration and signature
information.
Common Manage traffic of the most commonly used web,
file transfer and e-mail protocols.
IM Manage instant messenger traffic.
Peer to Peer Manage peer-to-peer traffic.
VoIP Manage VoIP traffic.
Streaming Manage streaming traffic.
Other Manage other kinds of traffic.
and check the anti-virus engine type and the anti-
virus license and signature status.
Black/White List Set up anti-virus black (blocked) and white
(allowed) lists of virus file patterns.
Signature Search for signatures by signature name or
attributes and configure how the ZyWALL uses
them.
Profile Create and manage IDP profiles.
Custom
Signatures
Profile Create and manage ADP profiles.
Filter Profile Create and manage the detailed filtering rules for
Black/White List Set up a black list to identify spam and a white list
DNSBL Have the ZyWALL check e-mail against DNS Black
Group Create and manage groups of users.
Setting Manage default settings for all users, general
Address Group Create and manage groups of addresses.
Create, import, or export custom signatures.
content filtering policies.
policies.
to identify legitimate e-mail.
Lists.
settings for user sessions, and rules to force user
authentication.
(subnet) addresses.
50
ZyWALL USG 50 User’s Guide
Page 51

Chapter 3 Web Configurator
Table 7 Configuration Menu Screens Summary (continued)
FOLDER OR
LINK
Service Service Create and manage TCP and UDP services.
Schedule Create one-time and recurring schedules.
AAA Server Active Directory-
Auth. Method Create and manage ways of authenticating users.
Certificate My Certificates Create and manage the ZyWALL’s certificates.
ISP Account Create and manage ISP account information for
SSL
Application
Endpoint
Security
System
Host Name Configure the system and domain name for the
Date/Time Configure the current date, time, and time zone in
Console
Speed
DNS Configure the DNS server and address records for
WWW Service Control Configure HTTP, HTTPS, and general
SSH Configure SSH server and SSH service settings.
TELNET Configure telnet server settings for the ZyWALL.
FTP Configure FTP server settings.
SNMP Configure SNMP communities and services.
Vantage CNM Configure and allow your ZyWALL to be managed
Language Select the Web Configurator language.
Log & Report
TAB FUNCTION
Service Group Create and manage groups of services.
Configure the default Active Directory settings.
Default
Active DirectoryGroup
LDAP-Default Configure the default LDAP settings.
LDAP-Group Create and manage groups of LDAP servers.
RADIUS-Default Configure the default RADIUS settings.
RADIUS-Group Create and manage groups of RADIUS servers.
Trusted
Certificates
Login Page Configure how the login and access user screens
Create and manage groups of Active Directory
servers.
Import and manage certificates from trusted
sources.
PPPoE/PPTP interfaces.
Create SSL web application objects.
Create Endpoint Security (EPS) objects.
ZyWALL.
the ZyWALL.
Set the console speed.
the ZyWALL.
authentication.
look.
by the Vantage CNM server.
ZyWALL USG 50 User’s Guide
51
Page 52

Chapter 3 Web Configurator
Table 7 Configuration Menu Screens Summary (continued)
FOLDER OR
LINK
Email Daily
Report
Log Setting Configure the system log, e-mail logs, and remote
TAB FUNCTION
3.3.2.4 Maintenance Menu
Use the maintenance menu screens to manage configuration and firmware files,
run diagnostics, and reboot or shut down the ZyWALL.
Table 8 Maintenance Menu Screens Summary
FOLDER OR
LINK
File Manager Configuration
Diagnostics Diagnostic Collect diagnostic information.
Reboot Restart the ZyWALL.
Shutdown Turn off the ZyWALL.
TAB FUNCTION
File
Firmware
Package
Shell Script Manage and run shell script files for the ZyWALL.
Packet Capture Capture packets for analysis.
Configure where and how to send daily reports and
what reports to send.
syslog servers.
Manage and upload configuration files for the
ZyWALL.
View the current firmware version and to upload
firmware.
3.3.3 Main Window
The main window shows the screen you select in the navigation panel. The main
window screens are discussed in the rest of this document.
Right after you log in, the Dashboard screen is display ed. See Chapter 8 on page
157 for more information about the Dashboard screen.
3.3.3.1 Warning Messages
Warning messages, such as those resulting from misconfiguration, display in a
popup window.
Figure 15 Warning Message
52
ZyWALL USG 50 User’s Guide
Page 53

3.3.3.2 Site Map
Click Site MAP to see an overview of links to the Web Configurator screens. Click
a screen’s link to go to that screen.
Figure 16 Site Map
Chapter 3 Web Configurator
3.3.3.3 Object Reference
Click Object Ref erence to open the Object Reference screen. Select the type of
object and the individual object and click Refresh to show which configuration
settings reference the object. The following example shows which configuration
settings reference the ldap-users user object (in this case the first firewall rule).
Figure 17 Object Reference
ZyWALL USG 50 User’s Guide
53
Page 54

Chapter 3 Web Configurator
The fields vary with the type of object. The following table describes labels that
can appear in this screen.
Table 9 Object References
LABEL DESCRIPTION
Object Name This identifies the object for which the configuration settings that use it
# This field is a sequential value, and it is not associated with any entry.
Service This is the type of setting that references the selected object. Click a
Priority If it is applicable, this field lists the referencing configuration item’s
Name This field identifies the configuration item that references the object.
Description If the referencing configuration item has a description configured, it
Refresh Click this to update the information in this screen.
Cancel Click Cancel to close the screen.
are displayed. Click the object’s name to display the object’s
configuration screen in the main window.
service’s name to display the service’s configuration screen in the main
window.
position in its list, otherwise N/A displays.
displays here.
3.3.3.4 CLI Messages
Click CLI to look at the CLI commands sent by the Web Configurator. The se
commands appear in a popup window, such as the following.
Figure 18 CLI Messages
Click Clear to remove the currently displayed information.
See the Command Reference Guide for information about the commands.
3.3.4 Tables and Lists
The Web Configurator tables and lists are quite flexible and provide several
options for how to display their entries.
54
ZyWALL USG 50 User’s Guide
Page 55

3.3.4.1 Manipulating Table Display
Here are some of the ways you can manipulate the We b Configurator tables.
1 Click a column heading to sort the table’s entries according to that column’s
criteria.
Figure 19 Sorting Table Entries by a Column’s Criteria
2 Click the down arrow next to a column heading for more options about how to
display the entries. The options available vary depending on the type of fields in
the column. Here are some examples of what you can do:
Chapter 3 Web Configurator
• Sort in ascending alphabetical order
• Sort in descending (reverse) alphabetical order
• Select which columns to display
• Group entries by field
• Show entries in groups
• Filter by mathematical operators (<, >, or =) or searching for text
Figure 20 Common Table Column Options
ZyWALL USG 50 User’s Guide
55
Page 56

Chapter 3 Web Configurator
3 Select a column heading cell’s right border and drag to re-size the column.
Figure 21 Resizing a Table Column
4 Select a column heading and drag and drop it to change the column order. A green
check mark displays next to the column’s title when you drag the column to a valid
new location.
Figure 22 Changing the Column Order
5 Use the icons and fields at the bottom of the table to navigate to different pages of
entries and control how many entries display at a time.
Figure 23 Navigating Pages of Table Entries
56
ZyWALL USG 50 User’s Guide
Page 57

3.3.4.2 Working with Table Entries
The tables have icons for working with table entries. A sample is shown next. You
can often use the [Shift] or [Ctrl] ke y t o sel e c t multiple entries to remove,
activate, or deactivate.
Figure 24 Common Table Icons
Here are descriptions for the most common table icons.
Table 10 Common Table Icons
LABEL DESCRIPTION
Add Click this to create a new entry. For features where the entry’s
position in the numbered list is important (features where the
ZyWALL applies the table’s entries in order like the firewall for
example), you can select an entry and click Add to create a new
entry after the selected entry.
Edit Double-click an entry or select it and click Edit to open a screen
where you can modify the entry’s settings. In some tables you can
just click a table entry and edit it directly in the table. For those types
of tables small red triangles display for table entries with changes
that you have not yet applied.
Remove To remove an entry, select it and click Remove. The ZyWALL
confirms you want to remove it before doing so.
Activate To turn on an entry, select it and click Activate.
Inactivate To turn off an entry, select it and click Inactivate.
Connect To connect an entry, select it and click Connect.
Disconnect To disconnect an entry, select it and click Disconnect.
Object References Select an entry and click Object References to open a screen that
shows which settings use the entry. See Section 11.3.2 on page 230
for an example.
Move To change an entry’s position in a numbered list, select it and click
Move to display a field to type a number for where you want to put
that entry and press [ENTER] to move the entry to the number that
you typed. For example, if you type 6, the entry you are moving
becomes number 6 and the previous entry 6 (if there is one) gets
pushed up (or down) one.
Chapter 3 Web Configurator
3.3.4.3 Working with Lists
When a list of available entries displays next to a list of selected entries, you can
often just double-click an entry to move it from one list to the other. In some lists
ZyWALL USG 50 User’s Guide
57
Page 58

Chapter 3 Web Configurator
you can also use the [Shift] or [Ctrl] key to select multiple entries, and then use
the arrow button to move them to the other list.
Figure 25 Working with Lists
58
ZyWALL USG 50 User’s Guide
Page 59

CHAPTER 4
Installation Setup Wizard
4.1 Installation Setup Wizard Screens
If you log into the Web Configurator when the ZyWALL is using its default
configuration, the first Installation Setup Wizard screen displays. This wizard
helps you configure Internet connection settings and activate subscription
services. This chapter provides information on configuring the Web Configurator's
installation setup wizard. See the feature-specific chapters in this User’ s Guide for
background information.
Figure 26 Installation Setup Wizard
• Click the double arrow in the upper right corner to display or hide the help.
•Click Go to Dashboard to skip the installation setup wizard or click Next to
start configuring for Internet access.
4.1.1 Internet Access Setup - WAN Interface
Use this screen to set how many WAN interfaces to configure and the first WAN
interface’s type of encapsulation and method of IP address assignment.
ZyWALL USG 50 User’s Guide
59
Page 60

Chapter 4 Installation Setup Wizard
The screens vary depending on the encapsulation type. Refer to information
provided by your ISP to know what to enter in each field. Leave a field blank if you
don’t have that information.
Note: Enter the Internet access information exactly as your ISP gave it to you.
Figure 27 Internet Access: Step 1
• I have two ISPs: Select this option to configure two Internet connections.
Leave it cleared to configure just one. This option appears when you are
configuring the first WAN interface.
• Encapsulation: Choose the Ethernet option when the WAN port is used as a
regular Ethernet. Otherwise, choose PPPoE or PPTP for a dial-up connection
according to the information from your ISP.
• WAN Interface: This is the interface you are configuring for Internet access.
• Zone: This is the security zone to which this interface and Internet connection
belong.
• IP Address Assignment: Select Auto if your ISP did not assign you a fix ed IP
address.
Select Static if the ISP assigned a fixed IP address.
4.1.2 Internet Access: Ethernet
This screen is read-only if you set the previous screen’ s IP Address Assignment
field to Auto. Use this screen to configure your IP address settings.
60
ZyWALL USG 50 User’s Guide
Page 61

Chapter 4 Installation Setup Wizard
Note: Enter the Internet access information exactly as given to you by your ISP.
Figure 28 Internet Access: Ethernet Encapsulation
• Encapsulation: This displays the type of Internet connection you are
configuring.
• First WAN Interface: This is the number of the interface that will connect with
your ISP.
• Zone: This is the security zone to which thi s int erface and Internet connection
will belong.
• IP Address: Enter your (static) public IP address. Auto d isplays if y ou selected
Auto as the IP Address Assignment in the previous screen.
The following fields display if you selected static IP address assignment.
• IP Subnet Mask: Enter the subnet mask for this WAN connection's IP address.
• Gateway IP Address: Enter the IP address of the router through which this
WAN connection will send traffic (the default gateway).
• First / Second DNS Server: These fields display if you selected static IP
address assignment. The Domain Name System (DNS) maps a domain name to
an IP address and vice versa. Enter a DNS server's IP address(es). The DNS
server is extremely important because without it, you must know the IP address
of a computer before you can access it. The ZyWALL uses these (in the order
you specify here) to resolve domain names for VPN, DDNS and the time server.
Leave the field as 0.0.0.0 if you do not want to configure DNS servers.
ZyWALL USG 50 User’s Guide
61
Page 62

Chapter 4 Installation Setup Wizard
4.1.3 Internet Access: PPPoE
Note: Enter the Internet access information exactly as given to you by your ISP.
Figure 29 Internet Access: PPPoE Encapsulation
4.1.3.1 ISP Parameters
• T ype the PPP oE Service Name from your service provider. PPPoE uses a service
name to identify and reach the PPPoE server. You can use alphanumeric and _@$./ characters, and it can be up to 64 characters long.
• Authentication Type - Select an authentication protocol for outgoing
connection requests. Options are:
• CHAP/PAP - Your ZyWALL accepts either CHAP or PAP when requested by
the remote node.
• CHAP - Your ZyWALL accepts CHAP only.
• PAP - Your ZyWALL accepts PAP only.
• MSCHAP - Your ZyWALL accepts MSCHAP only.
• MSCHAP-V2 - Your ZyWALL accepts MSCHAP-V2 only.
• Type the User Name given to you by your ISP. You can use alphanumeric and _@$./ characters, and it can be up to 31 characters long.
• Type the Password associated with the user name. Use up to 64 ASCII
characters except the [] and ?. This field can be blank.
• Select Nailed-Up if you do not want the connection to time out. Otherwise,
type the Idle Timeout in seconds that elapses before the router automatically
disconnects from the PPPoE server.
62
ZyWALL USG 50 User’s Guide
Page 63

4.1.3.2 WAN IP Address Assignments
• WAN Interface: This is the name of the interface that wi ll co n nect with your
ISP.
• Zone: This is the security zone to which thi s int erface and Internet connection
will belong.
• IP Address: Enter your (static) public IP address. Auto d isplays if y ou selected
Auto as the IP Address Assignment in the previous screen.
• First / Second DNS Server: These fields display if you selected static IP
address assignment. The Domain Name System (DNS) maps a domain name to
an IP address and vice versa. Enter a DNS server's IP address(es). The DNS
server is extremely important because without it, you must know the IP address
of a computer before you can access it. The ZyWALL uses these (in the order
you specify here) to resolve domain names for VPN, DDNS and the time server.
Leave the field as 0.0.0.0 if you do not w ant to configure DNS servers. If y ou do
not configure a DNS server, you must know the IP address of a machine in order
to access it.
4.1.4 Internet Access: PPTP
Chapter 4 Installation Setup Wizard
Note: Enter the Internet access information exactly as given to you by your ISP.
Figure 30 Internet Access: PPTP Encapsulation
ZyWALL USG 50 User’s Guide
63
Page 64

Chapter 4 Installation Setup Wizard
4.1.5 ISP Parameters
• Authentication Type - Select an authentication protocol for outgoing calls.
Options are:
• CHAP/PAP - Your ZyWALL accepts either CHAP or PAP when requested by
the remote node.
• CHAP - Your ZyWALL accepts CHAP only.
• PAP - Your ZyWALL accepts PAP only.
• MSCHAP - Your ZyWALL accepts MSCHAP only.
• MSCHAP-V2 - Your ZyWALL accepts MSCHAP-V2 only.
• Type the User Name given to you by your ISP. You can use alphanumeric and _@$./ characters, and it can be up to 31 characters long.
• Type the Password associated with the user name. Use up to 64 ASCII
characters except the [] and ?. This field can be blank. Re-type y our password in
the next field to confirm it.
• Select Nailed-Up if you do not want the connection to time out. Otherwise,
type the Idle Timeout in seconds that elapses before the router automatically
disconnects from the PPTP server.
4.1.5.1 PPTP Configuration
• Base Interface: This identifies the Ethernet interface you configure to connect
with a modem or router.
•Type a Base IP Address (static) assigned to you by your ISP.
• Type the IP Subnet Mask assigned to you by your ISP (if given).
• Server IP: Type the IP address of the PPTP server.
•Type a Connection ID or connection name. It must follow the “c:id” and
“n:name” format. For example, C:12 or N:My ISP. This field is optional and
depends on the requirements of your broadband modem or router. You can use
alphanumeric and -_: characters, and it can be up to 31 characters long.
4.1.5.2 WAN IP Address Assignments
• First WAN Interface: This is the connection type on the interface you are
configuring to connect with your ISP.
• Zone This is the security zone to whic h thi s in terface and Internet connection
will belong.
• IP Address: Enter your (static) public IP address. Auto displays if you selected
Auto as the IP Address Assignment in the previous screen.
• First / Second DNS Server: These fields display if you selected static IP
address assignment. The Domain Name System (DNS) maps a domain name to
an IP address and vice versa. Enter a DNS server's IP address(es). The DNS
server is extremely important because without it, you must know the IP address
of a computer before you can access it. The ZyWALL uses these (in the order
you specify here) to resolve domain names for VPN, DDNS and the time server.
Leave the field as 0.0.0.0 if you do not want to configure DNS servers.
64
ZyWALL USG 50 User’s Guide
Page 65

Chapter 4 Installation Setup Wizard
4.1.6 Internet Access Setup - Second WAN Interface
If you selected I have two ISPs, after you configure the First WAN Interface,
you can configure the Second WAN Interface. The screens for configuring the
second WAN interface are similar to the first (see Section 4.1.1 on page 59).
Figure 31 Internet Access: Step 3: Second WAN Interface
ZyWALL USG 50 User’s Guide
65
Page 66

Chapter 4 Installation Setup Wizard
4.1.7 Internet Access - Finish
You have set up your ZyWALL to access the Internet. After configuring the WAN
interface(s), a screen displays with your settings. If they are not correct, click
Back.
Figure 32 Internet Access: Ethernet Encapsulation
Note: If you have not already done so, you can register your ZyWALL with
myZyXEL.com and activate trials of services like Content Filter.
Click Next and use the following screen to perform a basic registration (see
Section 4.2 on page 66). If you want to do a more detailed registration or manage
your account details, click myZyXEL.com.
Alternatively, close the window to exit the wizard.
4.2 Device Registration
Use this screen to register your ZyWALL with myZXEL.com and activate trial
periods of subscription security features if you have not already done so. If the
ZyWALL is already registered this screen displays your user name and which trial
services are activated (if any). You can still activate any un-activated trial
services.
Note: You must be connected to the Internet to register.
66
ZyWALL USG 50 User’s Guide
Page 67

Chapter 4 Installation Setup Wizard
Use the Registration > Service screen to update your service subscription
status.
Registration
• Select new myZyXEL.com account if you haven’t created an account at
myZyXEL.com, select this option and configure the following fields to create an
account and register your ZyWALL.
• Select existing myZyXEL.com account if you already have an account at
myZyXEL.com and enter your user name and password in the fields below to
register your ZyWALL.
•Enter a User Name for your myZyXEL.com account. Use from six to 20
alphanumeric characters (and the underscore). Spaces are not allowed. Click
Check to verify that it is available.
• Password: Use six to 20 alphanumeric characters (and the underscore).
Spaces are not allowed. Type it again in the Confirm Password field.
• E-Mail Address: Enter your e-mail address. Use up to 80 alphanumeric
characters (periods and the underscore are also allowed) without spaces.
• Country Code: Select your country from the drop-down box list.
ZyWALL USG 50 User’s Guide
67
Page 68

Chapter 4 Installation Setup Wizard
• Trial Service Activation: You can try a trial service subscription. The trial
period starts the day you activate the trial. After the trial expires, you can buy
an iCard and enter the license key in the Registration > Service screen to
extend the service.
Figure 33 Registraton: Registered Device
68
ZyWALL USG 50 User’s Guide
Page 69

CHAPTER 5
Quick Setup
5.1 Quick Setup Overview
The Web Configurator's quick setup wizards help you configure Internet and VPN
connection settings. This chapter provides information on configuring the quick
setup screens in the Web Configurator. See the feature-specific chapters in this
User’s Guide for background information.
In the Web Configurator, click Configuration > Quick Setup to open the first
Quick Setup screen.
Figure 34 Quick Setup
• WAN Interface
Click this link to open a wizard to set up a WAN (Internet) connection. This
wizard creates matching ISP account settings in the ZyWALL if you use PPPoE or
PPTP. See Section 5.2 on page 70.
•VPN SETUP
Use VPN SETUP to configure a VPN (Virtual Private Network) tunnel for a
secure connection to another computer or network. See Section 5.4 on page 76.
ZyWALL USG 50 User’s Guide
69
Page 70

Chapter 5 Quick Setup
5.2 WAN Interface Quick Setup
Click WAN Interface in the main Quick Setup screen to open the WAN
Interface Quick Setup Wizard Welcome screen. Use these screens to
configure an interface to connect to the internet. Click Next.
Figure 35 WAN Interface Quick Setup Wizard
5.2.1 Choose an Ethernet Interface
Select the Ethernet interface that you want to configure for a WAN connection and
click Next.
Figure 36 Choose an Ethernet Interface
5.2.2 Select WAN Type
70
WAN Type Selection: Select the type of encapsulation this connection is to use.
Choose Ethernet when the WAN port is used as a regular Ethernet.
ZyWALL USG 50 User’s Guide
Page 71

Chapter 5 Quick Setup
Otherwise, choose PPPoE or PPTP for a dial-up connection according to the
information from your ISP.
Figure 37 WAN Interface Setup: Step 2
The screens vary depending on what encapsulation type you use. Refer to
information provided by your ISP to know what to enter in each field. Leave a field
blank if you don’t have that information.
Note: Enter the Internet access information exactly as your ISP gave it to you.
5.2.3 Configure WAN Settings
Use this screen to select whether the interface should use a fixed or dynamic IP
address.
Figure 38 WAN Interface Setup: Step 2
• WAN Interface: This is the interface you are configuring for Internet access.
• Zone: This is the security zone to which this interface and Internet connection
belong.
ZyWALL USG 50 User’s Guide
71
Page 72

Chapter 5 Quick Setup
• IP Address Assignment: Select Auto If your ISP did not assign you a fixed IP
address.
Select Static If the ISP assigned a fixed IP address.
5.2.4 WAN and ISP Connection Settings
Use this screen to configure the ISP and WAN interface settings. This screen is
read-only if you set the IP Address Assignment to Static.
Note: Enter the Internet access information exactly as your ISP gave it to you.
Figure 39 WAN and ISP Connection Settings: (PPTP Shown)
72
The following table describes the labels in this screen.
Table 11 WAN and ISP Connection Settings
LABEL DESCRIPTION
ISP Parameter This section appears if the interface uses a PPPoE or PPTP Internet
connection.
Encapsulation This displays the type of Internet connection you are configuring.
ZyWALL USG 50 User’s Guide
Page 73

Chapter 5 Quick Setup
Table 11 WAN and ISP Connection Settings (continued)
LABEL DESCRIPTION
Authentication
Type
User Name Type the user name given to you by your ISP. You can use
Password T ype the password associated with the user name above. Use up to 64
Retype to
Confirm
Nailed-Up Select Nailed-Up if you do not want the connection to time out.
Idle Timeout Type the time in seconds that elapses before the router automatically
PPTP
Configuration
Base Interface This displays the identity of the Ethernet interface you configure to
Base IP
Address
IP Subnet
Mask
Server IP Type the IP address of the PPTP server.
Connection ID Enter the connection ID or connection name in this field. It must
Use the drop-down list box to select an authentication protocol for
outgoing calls. Options are:
CHAP/PAP - Your ZyWALL accepts either CHAP or PAP when
requested by this remote node.
CHAP - Your ZyWALL accepts CHAP only.
PAP - Your ZyWALL accepts PAP only.
MSCHAP - Your ZyWALL accepts MSCHAP only.
MSCHAP-V2 - Your ZyWALL accepts MSCHAP-V2 only.
alphanumeric and -_
characters long.
ASCII characters except the [] and ?. This field can be blank.
Type your password again for confirmation.
disconnects from the PPPoE server. 0 means no timeout.
This section only appears if the interface uses a PPPoE or PPTP
Internet connection.
connect with a modem or router.
Type the (static) IP address assigned to you by your ISP.
Type the subnet mask assigned to you by your ISP (if given).
follow the "c:id" and "n:name" format. For example, C:12 or N:My
ISP.
This field is optional and depends on the requirements of your DSL
modem.
@$./ characters, and it can be up to 31
WAN Interface
Setup
WAN Interface This displays the identity of the interface you configure to connect
Zone This field displays to which security zone this interface and Internet
IP Address This field is read-only when the WAN interface uses a dynamic IP
ZyWALL USG 50 User’s Guide
You can use alphanumeric and -_
characters long.
with your ISP.
connection will belong.
address. If your WAN interface uses a static IP address, enter it in this
field.
: characters, and it can be up to 31
73
Page 74

Chapter 5 Quick Setup
Table 11 WAN and ISP Connection Settings (continued)
LABEL DESCRIPTION
First DNS
Server
Second DNS
Server
Back Click Back to return to the previous screen.
Next Click Next to continue.
These fields only display for an interface with a static IP address.
Enter the DNS server IP address(es) in the field(s) to the right.
Leave the field as 0.0.0.0 if you do not want to configure DNS
servers. If you do not configure a DNS server, you must know the IP
address of a machine in order to access it.
DNS (Domain Name System) is for mapping a domain name to its
corresponding IP address and vice versa. The DNS server is ex tremely
important because without it, you must know the IP address of a
computer before you can access it. The ZyWALL uses a system DNS
server (in the order you specify here) to resolve domain names for
VPN, DDNS and the time server.
5.2.5 Quick Setup Interface Wizard: Summary
This screen displays the WAN interface’s settings.
Figure 40 Interface Wizard: Summary WAN (PPTP Shown)
The following table describes the labels in this screen.
Table 12 Interface Wizard: Summary WAN
LABEL DESCRIPTION
Encapsulation This displays what encapsulation this interface uses to connect to the
Internet.
Service Name This field is read-only and only appears for a PPPoE interface. It displays
the PPPoE service name specified in the ISP account.
Server IP This field only appears for a PPTP interface. It displays the IP address of
the PPTP server.
74
ZyWALL USG 50 User’s Guide
Page 75

Chapter 5 Quick Setup
Table 12 Interface Wizard: Summary WAN
LABEL DESCRIPTION
User Name This is the user name given to you by your ISP.
Nailed-Up If No displays the connection will not time out. Yes means the ZyWALL
uses the idle timeout.
Idle Timeout This is how many seconds the connection can be idle before the router
automatically disconnects from the PPPoE server. 0 means no timeout.
Connection ID If you specified a connection ID, it displays here.
WAN Interface This identifies the interface you configure to connect with your ISP.
Zone This field displays to which security zone this interface and Internet
connection will belong.
IP Address
Assignment
First DNS
Server
Second DNS
Server
Close Click Close to exit the wizard.
This field displays whether the WAN IP address is static or dynamic
(Auto).
If the IP Address Assignment is Static, these fields display the DNS
server IP address(es).
5.3 VPN Quick Setup
Click VPN Setup in the main Quick Setup screen to open the VPN Setup
Wizard Welcome screen. The VPN wizard creates corresponding VPN connection
and VPN gateway settings and address objects that you can use later in
configuring more VPN connections or other features. Click Next.
Figure 41 VPN Quick Setup Wizard
ZyWALL USG 50 User’s Guide
75
Page 76

Chapter 5 Quick Setup
5.4 VPN Setup Wizard: Wizard Type
A VPN (Virtual Private Network) tunnel is a secure connection to another computer
or network. Use this screen to select which type of VPN connection you want to
configure.
Figure 42 VPN Setup Wizard: Wizard Type
Express: Use this wizard to create a VPN connection with another ZLD-based
ZyWALL using a pre-shared key and default security settings.
Advanced: Use this wizard to configure det a i led V PN security settings such as
using certificates. The VPN connection can be to another ZLD-based ZyWALL or
other IPSec device.
76
ZyWALL USG 50 User’s Guide
Page 77

5.5 VPN Express Wizard - Scenario
Click the Express radio button as shown in Figure 42 on page 76 to display the
following screen.
Figure 43 VPN Express Wizard: Step 2
Chapter 5 Quick Setup
Rule Name: Type the name used to identify this VPN connection (and VPN
gateway). Y ou may use 1-31 alphanumeric char acters, underscores (_), or dashes
(-), but the first character cannot be a number. This value is case-sensitive.
Select the scenario that best describes your intended VPN connection. The figure
on the left of the screen changes to match the scenario you select.
• Site-to-site - Choose this if the remote IPSec device has a static IP address or a
domain name. This ZyWALL can initiate the VPN tunnel.
• Site-to-site with Dynamic Peer - Choose this if the remote IPSec device has a
dynamic IP address. Only the remote IPSec device can initiate the VPN tunnel.
• Remote Access (Server Role) - Choose this to allow incoming connections from
IPSec VPN clients. The clients have dynamic IP addresses and are also known as
dial-in users. Only the clients can initiate the VPN tunnel.
• Remote Access (Client Role) - Choose this to connect to an IPSec server. This
ZyWALL is the client (dial-in user) and can initiate the VPN tunnel.
ZyWALL USG 50 User’s Guide
77
Page 78

Chapter 5 Quick Setup
5.5.1 VPN Express Wizard - Configuration
Figure 44 VPN Express Wizard: Step 3
• Secure Gateway: If Any displays in this field, it is not configurable for the
chosen scenario. If this field is configurable, enter the WAN IP address or
domain name of the remote IPSec device (secure gateway) to identify the
remote IPSec router by its IP address or a domain name. Use 0.0.0.0 if the
remote IPSec router has a dynamic WAN IP address.
• Pre-Shared Key: Type the password. Both ends of the VPN tunnel must use
the same password. Use 8 to 31 case-sensitive ASCII characters or 8 to 31 pairs
of hexadecimal (“0-9”, “A-F”) characters. Proceed a hexadecimal key with “0x”.
You will receive a PYLD_MALFORMED (payload malformed) packet if the same
pre-shared key is not used on both ends.
• Local Policy (IP/Mask): Type the IP address of a computer on your network.
You can also specify a subnet. This must match the remote IP address
configured on the remote IPSec device.
• Remote Policy (IP/Mask): If Any displays in this field, it is not configurable
for the chosen scenario. If this field is configurable, type the IP address of a
computer behind the remote IPSec device. You can also specify a subnet. This
must match the local IP address configured on the remote IPSec device.
78
ZyWALL USG 50 User’s Guide
Page 79

5.5.2 VPN Express Wizard - Summary
This screen provides a read-only summary of the VPN tunnel’s configuration and
also commands that you can copy and paste into another ZLD-based ZyWALL’s
command line interface to configure it.
Figure 45 VPN Express Wizard: Step 4
Chapter 5 Quick Setup
• Rule Name: Identifies the VPN gateway policy.
• Secure Gateway: IP address or domain name of the remote IPSec device. If
this field displays Any, only the remote IPSec device can initiate the VPN
connection.
• Pre-Shared Key: VPN tunnel password. It identifies a communicating party
during a phase 1 IKE negotiation.
• Local Policy: (Static) IP address and subnet mask of the computers on the
network behind your ZyWALL that can use the tunnel.
• Remote Policy: (Static) IP address and subnet mask of the computers on the
network behind the remote IPSec device that can use the tunnel. If this field
displays Any, only the remote IPSec device can initiate the VPN connection.
• Copy and paste the Configuration for Secure Gateway commands into
another ZLD-based ZyWALL’s command line interface to configure it to serve as
the other end of this VPN tunnel. You can also use a text editor to save these
commands as a shell script file with a “.zysh” filename extension. Then you can
use the file manager to run the script in order to configure the VPN connection.
See the commands reference guide for details on the commands displayed in
this list.
ZyWALL USG 50 User’s Guide
79
Page 80

Chapter 5 Quick Setup
5.5.3 VPN Express Wizard - Finish
Now you can use the VPN tunnel.
Figure 46 VPN Express Wizard: Step 6
80
Note: If you have not already done so, use the myZyXEL.com link and register your
ZyWALL with myZyXEL.com and activate trials of services like Content Filter.
Click Close to exit the wizard.
ZyWALL USG 50 User’s Guide
Page 81

5.5.4 VPN Advanced Wizard - Scenario
Click the Advanced radio button as shown in Figure 42 on page 76 to di splay the
following screen.
Figure 47 VPN Advanced Wizard: Scenario
Chapter 5 Quick Setup
Rule Name: Type the name used to identify this VPN connection (and VPN
gateway). Y ou may use 1-31 alphanumeric char acters, underscores (_), or dashes
(-), but the first character cannot be a number. This value is case-sensitive.
Select the scenario that best describes your intended VPN connection. The figure
on the left of the screen changes to match the scenario you select.
• Site-to-site - Choose this if the remote IPSec device has a static IP address or a
domain name. This ZyWALL can initiate the VPN tunnel.
• Site-to-site with Dynamic Peer - Choose this if the remote IPSec device has a
dynamic IP address. Only the remote IPSec device can initiate the VPN tunnel.
• Remote Access (Server Role) - Choose this to allow incoming connections from
IPSec VPN clients. The clients have dynamic IP addresses and are also known as
dial-in users. Only the clients can initiate the VPN tunnel.
ZyWALL USG 50 User’s Guide
81
Page 82

Chapter 5 Quick Setup
• Remote Access (Client Role) - Choose this to connect to an IPSec server. This
ZyWALL is the client (dial-in user) and can initiate the VPN tunnel.
5.5.5 VPN Advanced Wizard - Phase 1 Settings
There are two phases to every IKE (Internet Key Exchange) negotiation – phase 1
(Authentication) and phase 2 (Key Exchange). A phase 1 exchange establ ishes an
IKE SA (Security Association).
Figure 48 VPN Advanced Wizard: Phase 1 Settings
• Secure Gateway: If Any displays in this field, it is not configurable for the
chosen scenario. If this field is configurable, enter the WAN IP address or
domain name of the remote IPSec device (secure gateway) to identify the
remote IPSec device by its IP address or a domain name. Use 0.0.0.0 if the
remote IPSec device has a dynamic WAN IP address.
• My Address (interface): Select an interface from the drop-down list box to
use on your ZyWALL.
• Negotiation Mode: Select Main for identity protection. Select Aggressive to
allow more incoming connections from dynamic IP addresses to use separate
passwords.
Note: Multiple SAs connecting through a secure gateway must have the same
negotiation mode.
• Encryption Algorithm: 3DES and AES use encryption. The longer the key, the
higher the security (this may affect throughput). Both sender and recei ver must
know the same secret key, which can be used to encrypt and decrypt the
message or to generate and verify a message authentication code. The DES
encryption algorithm uses a 56-bit key. Triple DES (3DES) is a variation on DES
82
ZyWALL USG 50 User’s Guide
Page 83

Chapter 5 Quick Setup
that uses a 168-bit key. As a result, 3DES is more secure than DES. It also
requires more processing power, resulting in increased latency and decreased
throughput. AES128 uses a 128-bit key and is faster than 3DES. AES192 uses a
192-bit key and AES256 uses a 256-bit key.
• Authentication Algorithm: MD5 gives minimal security. SHA-1 gives higher
security. MD5 (Message Digest 5) and SHA1 (Secure Has h Algorithm) are hash
algorithms used to authenticate pac ket data. The SHA1 algorithm is generally
considered stronger than MD5, but is slower.
• Key Group: DH5 is more secure than DH1 or DH2 (although it may affect
throughput). DH1 (default) refers to Diffie-Hellman Group 1 a 768 bit random
number. DH2 refers to Diffie-Hellman Group 2 a 1024 bit (1Kb) random number.
DH5 refers to Diffie-Hellman Group 5 a 1536 bit random number.
• SA Life Time: Set how often the ZyWALL renegotiates the IKE SA. A short SA
life time increases security, but renegotiation temporarily disconnects the VPN
tunnel.
• NAT Traversal: Select this if the VPN tunnel must pass through NAT (there is a
NAT router between the IPSec devices).
Note: The remote IPSec device must also have NAT traversal enabled. See the help
in the main IPSec VPN screens or the User’s Guide VPN, NAT, and NAT
Traversal on page 403 for more information.
• Dead Peer Detection (DPD) has the ZyWALL make sure the remote IPSec
device is there before transmitting data through the IKE SA. If there has been
no traffic for at least 15 seconds, the ZyWALL sends a message to the remote
IPSec device. If it responds, the ZyWALL transmits the data. If it does not
respond, the ZyWALL shuts down the IKE SA.
• Authentication Method: Select Pre-Shared Key to use a password or
Certificate to use one of the ZyWALL’s certificates.
ZyWALL USG 50 User’s Guide
83
Page 84

Chapter 5 Quick Setup
5.5.6 VPN Advanced Wizard - Phase 2
Phase 2 in an IKE uses the SA that was established in phase 1 to negot iate SAs for
IPSec.
Figure 49 VPN Advanced Wizard: Step 4
• Active Protocol: ESP is compatible with NAT, AH is not.
• Encapsulation: Tunnel is compatible with NAT, Transport is not.
• Encryption Algorithm: 3DES and AES use encryption. The longer the AES
key, the higher the security (this may affect throughput). Null uses no
encryption.
• Authentication Algorithm: MD5 gives minimal security. SHA-1 gives higher
security. MD5 (Message Digest 5) and SHA1 (Secure Has h Algorithm) are hash
algorithms used to authenticate pac ket data. The SHA1 algorithm is generally
considered stronger than MD5, but is slower.
• SA Life Time: Set how often the ZyWALL renegotiates the IKE SA. A short SA
life time increases security, but renegotiation temporarily disconnects the VPN
tunnel.
• Perfect Forward Secrecy (PFS): Disabling PFS allows faster IPSec setup, but is
less secure. Select DH1, DH2 or DH5 to enable PFS. DH5 is more secure than
DH1 or DH2 (although it may affect throughput). DH1 refers to Diffie-Hellman
Group 1 a 768 bit random number. DH2 refers to Diffie-Hellman Group 2 a 1024
bit (1Kb) random number. DH5 refers to Diffie-Hellman Group 5 a 1536 bit
random number (more secure, yet slower).
• Local Policy (IP/Mask): Type the IP address of a computer on your network.
You can also specify a subnet. This must match the remote IP address
configured on the remote IPSec device.
84
• Remote Policy (IP/Mask): Type the IP address of a computer behind the
remote IPSec device. You can also specify a subnet. This must match the local
IP address configured on the remote IPSec device.
• Nailed-Up: This displays for the site-to-site and remote access client role
scenarios. Select this to have the ZyWALL automatically renegotiate the IPSec
SA when the SA life time expires.
ZyWALL USG 50 User’s Guide
Page 85

5.5.7 VPN Advanced Wizard - Summary
This is a read-only summary of the VPN tunnel settings.
Figure 50 VPN Advanced Wizard: Step 5
Chapter 5 Quick Setup
• Rule Name: Identifies the VPN connection (and the VPN gateway).
• Secure Gateway: IP address or domain name of the remote IPSec device.
• Pre-Shared Key: VPN tunnel password.
• Certificate: The certificate the ZyWALL uses to identify itself when setting up
the VPN tunnel.
• Local Policy: IP address and subnet mask of the computers on the network
behind your ZyWALL that can use the tunnel.
• Remote Policy: IP address and subnet mask of the computers on the network
behind the remote IPSec device that can use the tunnel.
• Copy and paste the Configuration for Remote Gateway commands into
another ZLD-based ZyWALL’s command line interface.
•Click Save to save the VPN rule.
ZyWALL USG 50 User’s Guide
85
Page 86

Chapter 5 Quick Setup
5.5.8 VPN Advanced Wizard - Finish
Now you can use the VPN tunnel.
Figure 51 VPN Wizard: Step 6: Advanced
86
Note: If you have not already done so, you can register your ZyWALL with
myZyXEL.com and activate trials of services like Content Filter.
Click Close to exit the wizard.
ZyWALL USG 50 User’s Guide
Page 87

CHAPTER 6
Configuration Basics
This information is provided to help you configure the ZyW ALL effectively. Some of
it is helpful when you are just gett i n g st a r t ed. Some of it is provided for your
reference when you configure various features in the ZyWALL.
• Section 6.1 on page 87 introduces the ZyWALL’s object-based configuration.
• Section 6.2 on page 88 introduces zones, interfaces, and port groups.
• Section 6.3 on page 91 introduces some terminology and organization for the
ZyWALL.
• Section 6.4 on page 91 covers the ZyWALL’s packet flow.
• Section 6.5 on page 95 identifies the features you should conf igure before and
after you configure the main screens for each feature. For example, if you want
to configure a trunk for load-balancing, you should configure the member
interfaces before you configure the trunk. After you configure the trunk, you
should configure a policy route for it as well. (You might also have to configure
criteria for the policy route.)
• Section 6.6 on page 105 identifies the objects that store information used by
other features.
• Section 6.7 on page 106 introduces some of the tools available for system
management.
6.1 Object-based Configuration
The ZyWALL stores information or settings as objects. You use these objects to
configure many of the ZyWALL’s features and settings. Once you configure an
object, you can reuse it in configuring other features.
When you change an object’s settings, the ZyWALL automatically updates al l the
settings or rules that use the object. For example, if you create a schedule objec t,
you can have firewall, applicat ion patrol, content filter, and other settings use it. If
you modify the schedule, all the firewall, application patrol, content filter, and
other settings that use the schedule automatically apply the updated schedule.
You can create address objects based on an interface’s IP address, subnet, or
gateway. The Z y WALL automatically updates every rule or setting that uses these
objects whenever the interface’s IP address settings change. For example, if you
ZyWALL USG 50 User’s Guide
87
Page 88
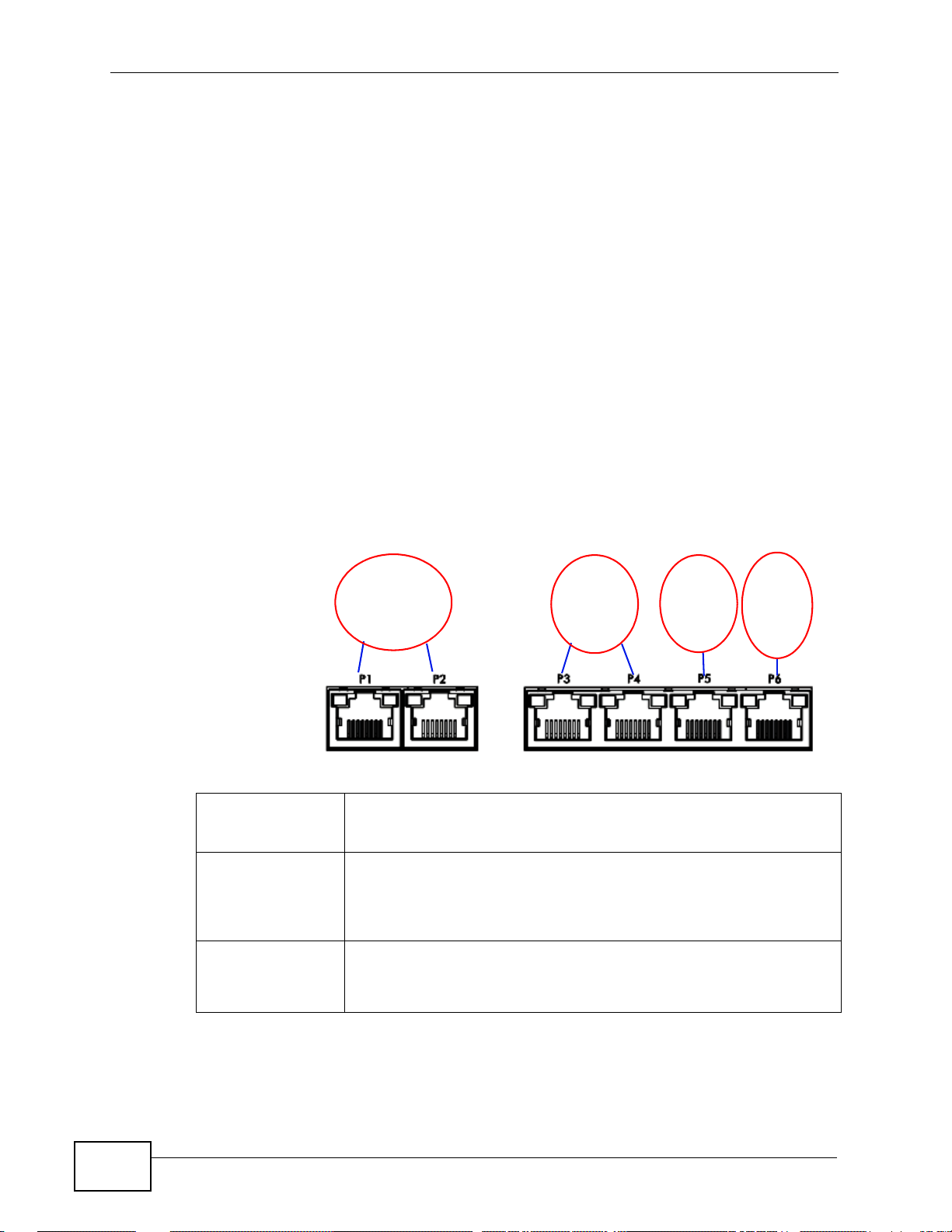
Chapter 6 Configuration Basics
change an Ethernet interface’s IP address, the ZyWALL automatically updates the
rules or settings that use the interface-based, LAN subnet address object.
You can use the Configuration > Objects screens to create objects before you
configure features that use them. If you are in a screen that uses objects, you can
also usually select Create new Object to be able to configure a new object. F or a
list of common objects, see Section 6.6 on page 105.
Use the Object Reference screen (Section 3.3.3.3 on page 53) to see what
objects are configured and which configuration settings reference specific objects.
6.2 Zones, Interfaces, and Physical Ports
Zones (groups of interfaces and VPN tunnels) simplify security settings. Here is an
overview of zones, interfaces, and physical ports in the ZyWALL.
Figure 52 Zones, Interfaces, and Physical Ethernet Ports
Zones
Interfaces
Physical Ports
WAN
wan1 wan2
LAN1
lan1
Table 13 Zones, Interfaces, and Physical Ethernet Ports
Zones
(WAN,LAN, DMZ)
Interfaces
(Ethernet,
VLAN,...)
Physical
Ethernet Ports
(P1, P2, ...)
A zone is a group of interfaces and VPN tunnels. Use zones to apply
security settings such as firewall, IDP, remote management, antivirus, and application patrol.
Interfaces are logical entities that (layer-3) packets pass through.
Use interfaces in configuring VPN, zones, trunks, DDNS, policy
routes, static routes, HTTP redirect, and NAT.
Port roles combine physical ports into interfaces.
The physical port is where you connect a cable. In configuration, you
use physical ports when configuring port groups. You use interfaces
and zones in configuring other features.
LAN2
lan2
DMZ
dmz
88
ZyWALL USG 50 User’s Guide
Page 89

6.2.1 Interface Types
There are many types of interfaces in the ZyWALL. In addition to being used in
various features, interfaces also describe the network that is directly connected to
the ZyWALL.
• Ethernet interfaces are the foundation for defining other interfaces and
network policies. Y o u also configure RIP and OSPF in these interfaces.
• Port groups create a hardware connection between physical ports at the layer2 (data link, MAC address) level. Port groups are created when you use the
Interface > Port Roles screen to set multiple physical ports to be part of the
same (lan1, lan2 or dmz) interface.
• PPP interfaces support Point-to-Point Protocols (PPPoE or PPTP). ISP accounts
are required for PPPoE/PPTP interfaces.
• VLAN interfaces recognize tagged frames. The ZyWALL automatically adds or
removes the tags as needed. Each VLAN can only be associated with one
Ethernet interface.
• Bridge interfaces create a software connection between Ethernet or VLAN
interfaces at the layer-2 (data link, MAC address) level. Then, you can configure
the IP address and subnet mask of the bridge. It is also possible to configure
zone-level security between the member interfaces in the bridge.
Chapter 6 Configuration Basics
• Virtual interfaces increase the amount of routing information in the ZyWALL.
There are three types: virtual Ethernet interfaces (also known as IP alias),
virtual VLAN interfaces, and virtual bridge interfaces.
6.2.2 Default Interface and Zone Configuration
This section introduces the ZyWALL’ s default zone member ph ysical interfaces and
the default configuration of those interfaces. The following figure uses letters to
denote public IP addresses or part of a private IP address.
ZyWALL USG 50 User’s Guide
89
Page 90

Chapter 6 Configuration Basics
Table 14 Default Network Topology ZyWALL USG 50 Default Port, Interface, and
Zone Configuration
PORT INTERFACE ZONE
P1, P2 wan1, wan2 WAN DHCP clients Connections to the Internet
P3, P4 lan1 LAN1 192.168.1.1, DHCP
P5 lan2 LAN2 192.168.2.1, DHCP
P6 dmz DMZ 19 2.168.3.1, DHCP
CONSOLE n/a None None Local management
IP ADDRESS AND DHCP
SETTINGS
server enabled
server enabled
server disabled
• The WAN zone contains the wan1 and wan2 interfaces (physical ports P1 and
P2). They use public IP addresses to connect to the Internet.
• The LAN1 zone contains the lan1 interface (a port group made up of physical
ports P3 and P4 on the Z yWALL). The LAN1 zone is a protected zone. The lan1
interface uses 192.168.1.1 and the connected devices use IP addresses in the
192.168.1.2 to 192.168.1.254 range.
• The LAN2 zone contains the lan2 interface. The LAN2 zone is a protected zone.
The lan2 interface uses 192.168.2.1 and the connected devices use IP
addresses in the 192.168.2.2 to 192.168.2.254 range.
• The DMZ zone contains the dmz interface (physical port P5). The DMZ zone has
servers that are available to the public. The dmz interface uses private IP
address 192.168.3.1 and the connected devices use private IP addresses in the
192.168.3.2 to 192.168.3.254 range.
SUGGESTED USE WITH
DEFAULT SETTINGS
Protected LAN
Protected LAN
Public servers (such as
web, e-mail and FTP)
90
ZyWALL USG 50 User’s Guide
Page 91

6.3 Terminology in the ZyWALL
This section highlights some terminology or organization for ZLD-based ZyWALLs.
Table 15 ZLD ZyWALL Terminology
FEATURE / TERM ZLD ZYWALL FEATURE / TERM
IP alias Virtual interface
Gateway policy VPN gateway
Network policy (IPSec SA) VPN connection
Source NAT (SNAT) Policy route
Trigger port, port triggering Policy route
Address mapping Policy route
Address mapping (VPN) IPSec VPN
Interface bandwidth management
(outbound)
OSI level-7 bandwidth
management
General bandwidth management Policy route
Interface
Application patrol
Chapter 6 Configuration Basics
6.4 Packet Flow
Here is the order in which the ZyWALL applies its features and checks.
Traffic in > Defragmentation > ALG > Destination NAT > Routing > Stateful
Firewall > ADP > Application Classification > IDP > Anti- vi rus > Applicatio n Patrol
> Content Filter > Anti-Spam > SNAT > Bandwidth Management > Traffic Out.
ZyWALL USG 50 User’s Guide
91
Page 92

Chapter 6 Configuration Basics
Packet Flow The packet flow is as follows:
• Automatic SNAT and WAN trunk routing for traffic going from internal to
external interfaces (you don’t need to configure anything to all LAN to WAN
traffic).
The ZyWALL automatically adds al l of the external interfaces to the default W AN
trunk. External interfaces include ppp and cellular interfaces as well as any
Ethernet interfaces that are set as external interfaces.
Examples of internal interfaces are any Ethernet interfaces that you config ure as
internal interfaces.
• A policy route can be automatically disabled if the next-hop is dead.
• You do not need to set up policy routes for IPSec traffic.
• Policy routes can override direct routes.
• You do not need to set up policy routes for 1:1 NAT entries.
• You can create Many 1:1 NAT entries to translate a range of private network
addresses to a range of public IP addresses
• Static and dynamic routes have their own category.
6.4.1 Routing Table Checking Flow
When the ZyWALL receives packets it defragments them and applies destination
NAT. Then it examines the packets and determines how to route them. The
checking flow is from top to bottom. As soon as the packets match an entry in one
92
ZyWALL USG 50 User’s Guide
Page 93

Chapter 6 Configuration Basics
of the sections, the ZyWALL stops checking the packets against the routing table
and moves on to the other checks, for example the firewall check.
Figure 53 Routing Table Checking Flow
1 Direct-connected Subnets: The ZyWALL first checks to see if the packets are
destined for an address in the same subnet as one of the ZyWALL’ s interfaces. You
can override this and have the ZyWALL check the policy routes first by enabling
the policy route feature’s Use Policy Route to Override Direct Route option
(see Section 13.1 on page 281).
2 Policy Routes: These are the user-configured policy routes. Configure policy
routes to send packets through the appropriate interface or VPN tunnel. See
Chapter 13 on page 281 for more on policy routes.
3 1 to 1 and Many 1 to 1 NAT: These are the 1 to 1 NAT and many 1 to 1 NAT
rules. If a private network server will initiate sessions to the outside clients, create
a 1 to 1 NAT entry to have the ZyWALL translate the source IP address of the
server’s outgoing traffic to the same publ i c IP address that the outside clients use
to access the server. A many 1 to 1 NAT entry works like multiple 1 to 1 NA T rules.
It maps a range of private network servers that will init iate sessions to the outside
clients to a range of public IP addresses. See Section 17.2.1 on page 324 for
more.
ZyWALL USG 50 User’s Guide
93
Page 94
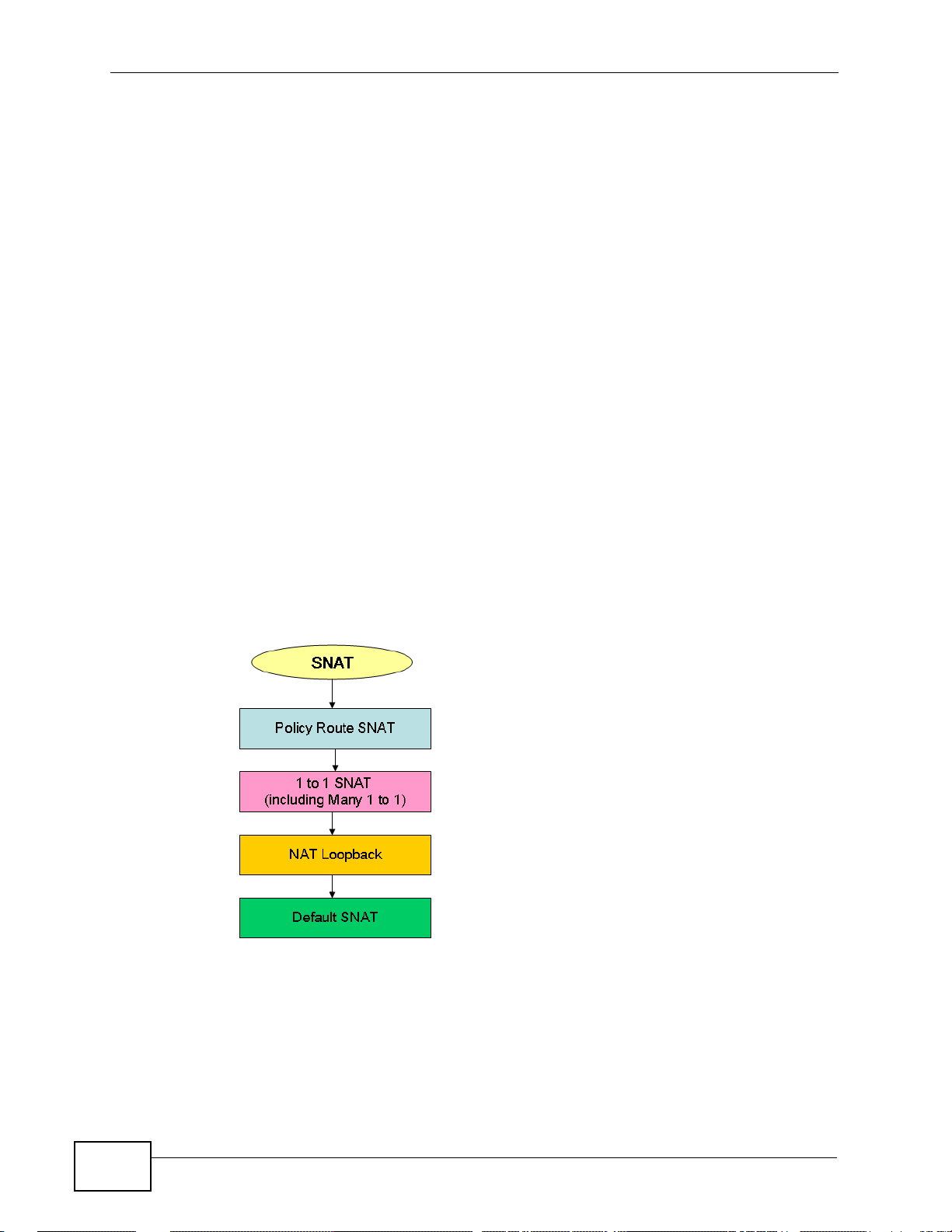
Chapter 6 Configuration Basics
4 Auto VPN Policy: The ZyWALL automatically creates these routing entries for the
VPN rules. Disabling the IPSec VPN feature’s Use Policy Route to control
dynamic IPSec rules option moves the routes for dynamic IPSec rules up above
the policy routes (see Section 23.2 on page 378).
5 Static and Dynamic Routes: This section contains the user-configured static
routes and the dynamic routing information learned from other routers through
RIP and OSPF. See Chapter 13 on page 281 for more information.
6 Default WAN Trunk: For any traffic coming in through an internal interface, if it
does not match any of the other routing entries, the ZyWALL forwards it through
the default WAN trunk. See Section 12.2 on page 276 for how to select which
trunk the ZyWALL uses as the default.
7 Main Routing Table: The default WAN trunk is expected to be used for any traffic
that did not match any earlier routing entries.
6.4.2 NAT Table Checking Flow
The checking flow is from top to bottom. As soon as the packets match an entry in
one of the sections, the ZyWALL stops checking the pack ets against the NAT table
and moves on to bandwidth management.
Figure 54 NAT Table Checking Flow
94
1 SNAT defined in the policy routes.
2 1 to 1 SNAT (including Many 1 to 1) is also included in the NAT table.
3 NAT loopback is now included in the NAT table instead of requiring a separate
policy route.
ZyWALL USG 50 User’s Guide
Page 95

Chapter 6 Configuration Basics
4 SNAT is also now performed by default and included in the NAT table.
6.5 Feature Configuration Overview
This section provides information about configuring the main features in the
ZyWALL. The features are listed in the same sequence as the menu item(s) in the
Web Configurator. Each feature description is organized as shown below.
6.5.1 Feature
This provides a brief description. See the appropriate chapter(s) in this User’s
Guide for more information about any feature.
This shows you the sequence of menu items and tabs you should click
MENU ITEM(S)
to find the main screen(s) for this feature. See the web help or the
related User’s Guide chapter for information about each screen.
These are other features you should configure before you configure
the main screen(s) for this feature.
If you did not configure one of the prerequisites first, you can often
PREREQUISITES
WHERE USED
Example: This provides a simple example to show you how to configure this
feature. The example is usually based on the network topology in Figure 14 on
page 90.
select an option to create a new object. After you create the object
you return to the main screen to finish configuring the feature.
You may not have to configure everything in the list of prerequisites.
For example, you do not have to create a schedule for a policy route
unless time is one of the criterion.
There are two uses for this.
These are other features you should usually configure or check right
after you configure the main screen(s) for this feature. For example,
you should usually create a policy route for a VPN tunnel.
You have to delete the references to this feature before you can delete
any settings. For example, you have to delete (or modify) all the
policy routes that refer to a VPN tunnel before you can delete the VPN
tunnel.
Note: PREQUISITES or WHERE USED does not appear if there are no prerequisites
or references in other features to this one. For example, no other features
reference DDNS entries, so there is no WHERE USED entry.
ZyWALL USG 50 User’s Guide
95
Page 96

Chapter 6 Configuration Basics
6.5.2 Licensing Registration
Use these screens to register your ZyWALL and subscribe to services like antivirus, IDP and application patrol, more SSL VPN tunnels, and content filtering. Y ou
must have Internet access to myZyXEL.com.
MENU ITEM(S)
PREREQUISITES
Configuration > Licensing > Registration
Internet access to myZyXEL.com
6.5.3 Licensing Update
Use these screens to update the ZyWALL’s signature packages for the anti-virus,
IDP and application patrol, and system protect features. You must have a valid
subscription to update the anti-virus and IDP/application patrol signatures. You
must have Internet access to myZyXEL.com.
MENU ITEM(S)
PREREQUISITES
Configuration > Licensing > Update
Registration (for anti-virus and IDP/application patrol), Internet
access to myZyXEL.com
6.5.4 Interface
See Section 6.2 on page 88 for background information.
Note: When you create an interface, there is no security applied on it until you assign
it to a zone.
96
Most of the features that use interfaces support Ethernet, PPPoE/PPTP, cellular,
VLAN, and bridge interfaces.
MENU ITEM(S)
PREREQUISITES
WHERE USED
Example: The dmz interface is in the DMZ zone and uses a private IP address. T o
configure dmz’s settings, click Network > Interface > Ethernet and then the
dmz’s Edit icon.
Configuration > Network > Interface (except Network >
Interface > Trunk)
Port groups (configured in the Interface > Port Grouping screen)
Zones, trunks, IPSec VPN, DDNS, policy routes, static routes, HTTP
redirect, NAT, application patrol
ZyWALL USG 50 User’s Guide
Page 97

6.5.5 Trunks
Use trunks to set up load balancing using two or more interfaces.
Chapter 6 Configuration Basics
MENU ITEM(S)
PREREQUISITES
WHERE USED
Example: See Chapter 7 on page 109.
6.5.6 Policy Routes
Use policy routes to override the ZyWALL’s default routing behavior in order to
send packets through the appropriate interface or VPN tunnel. You can also use
policy routes for bandwidth management (out of the ZyWALL), port triggering,
and general NAT on the source address. Y ou have to set up the criteria, next -hops,
and NAT settings first.
MENU ITEM(S)
PREREQUISITES
Configuration > Network > Interface > Trunk
Interfaces
Policy routes
Configuration > Network > Routing > Policy Route
Criteria: users, user groups, interfaces (incoming), IPSec VPN
(incoming), addresses (source, destination), address groups (source,
destination), schedules, services, service groups
Next-hop: addresses (HOST gateway), IPSec VPN, SSL VPN, trunks,
interfaces
NAT: addresses (translated address), services and service groups
(port triggering)
Example: Yo u have an FTP server connected to P6 (in the DMZ zone). You want
to limit the amount of FTP traffic that goes out from the FTP server through your
WAN connection.
1 Create an address object for the FTP server (Object > Address).
2 Click Configuration > Network > Routing > Policy Route to go to the policy
route configuration screen. Add a policy route.
3 Name the policy route.
4 Select the interface that the traffic comes in through (P3 in this example).
5 Select the FTP server’s address as the source address.
6 You don’t need to specify the destination address or the schedule.
7 For the service, select FTP.
ZyWALL USG 50 User’s Guide
97
Page 98

Chapter 6 Configuration Basics
8 For the Next Hop fields, select Interface as the Type if you have a single WAN
connection or Trunk if you have multiple WAN connections.
9 Select the interface that you are using for your WAN connection (wan1 and wan2
are the default WAN interfaces). If you hav e multiple W AN connections, select the
trunk.
10 Specify the amount of bandwidth FTP traffic can use. You may also want to set a
low priority for FTP traffic.
Note: The ZyWALL checks the policy rou tes in the order that they are listed. So make
sure that your custom policy route comes before any other routes that would
also match the FTP traffic.
6.5.7 Static Routes
Use static routes to tell the ZyWALL about networks not directly connected to the
ZyWALL.
MENU ITEM(S)
PREREQUISITES
6.5.8 Zones
See Section 6.2 on page 88 for background information. A zone is a group of
interfaces and VPN tunnels. The ZyWALL uses zones, not interfaces, in many
security settings, such as firewall rules and remote management.
Zones cannot overlap. Each interface and VPN tunnel can be assigned to at most
one zone. Virtual interfaces are automatically assigned to the same zone as the
interface on which they run. When you create a zone, the ZyWALL does not create
any firewall rules, assign an IDP profile, or configure remote management for the
new zone.
MENU ITEM(S)
PREREQUISITES
WHERE USED
Example: For example, to create the DMZ-2 z o ne, click Network > Zone and
then the Add icon.
Configuration > Network > Routing > Static Route
Interfaces
Configuration > Network > Zone
Interfaces, IPSec VPN, SSL VPN
Firewall, IDP, remote management, anti-virus, ADP, application patrol
98
ZyWALL USG 50 User’s Guide
Page 99

6.5.9 DDNS
Dynamic DNS maps a domain name to a dynamic IP address. The ZyWALL helps
maintain this mapping.
Chapter 6 Configuration Basics
MENU ITEM(S)
PREREQUISITES
6.5.10 NAT
Use Network Address Translation (NAT) to make computers on a private network
behind the ZyWALL available outside the private network.
The ZyWALL only checks regular (through-ZyWALL) firewall rules for packets that
are redirected by NAT, it does not check the to-ZyWALL firewall rules.
MENU ITEM(S)
PREREQUISITES
Example: Suppose you have an FTP server with a private IP address connected to
a DMZ port. You could configure a NAT rule to forwards FTP sessions from the
WAN to the DMZ.
1 Click Configuration > Network > NAT to configure the NAT entry. Add an entry.
Configuration > Network > DDNS
Interface
Configuration > Network > NAT
Interfaces, addresses (HOST)
2 Name the entry.
3 Select the WAN interface that the FTP traffic is to come in through.
4 Specify the public WAN IP address where the ZyWALL wil l recei ve the FTP packets .
5 In the Mapped IP field, list the IP address of the FTP server. The ZyWALL will
forward the packets received for the original IP address.
6 In Mapping Type, select Port.
7 Enter 21 in both the Original and the Mapped Port fields.
6.5.11 HTTP Redirect
Configure this feature to have the ZyWALL transparently forward HTTP (web)
traffic to a proxy server. This can speed up web browsing because the proxy server
keeps copies of the web pages that have been accessed so they are readily
available the next time one of your users needs to access that page.
ZyWALL USG 50 User’s Guide
99
Page 100

Chapter 6 Configuration Basics
The ZyWALL does not check to-ZyWALL firewall rules for packets that are
redirected by HTTP redirect. It does check regular (through-ZyWALL) firewall
rules.
MENU ITEM(S)
PREREQUISITES
Example: Suppose you want HTTP requests from y our LAN to go to a HTTP proxy
server at IP address 192.168.3.80.
1 Click Configuration > Network > HTTP Redirect.
2 Add an entry.
3 Name the entry.
4 Select the interface from which you want to redirect incoming HTT P requests
(lan1).
5 Specify the IP address of the HTTP proxy server.
6 Specify the port number to use for the HTTP traffic that you forward to the proxy
server.
Configuration > Network > HTTP Redirect
Interfaces
6.5.12 ALG
The ZyWALL’s Application Layer Gateway (ALG) allows VoIP and FTP applications
to go through NAT on the ZyWALL. You can also specify additional signaling port
numbers.
MENU ITEM(S)
6.5.13 Auth. Policy
Use authentication policies to control who can access the network. You can
authenticate users (require them to log in) and even perform Endpoint Security
(EPS) checking to make sure users’ computers comply with defined corporate
policies before they can access the network.
MENU ITEM(S)
PREREQUISITES
Configuration > Network > ALG
Configuration > Auth. Policy
Addresses, services, endpoint security objects, users, authentication
methods
100
ZyWALL USG 50 User’s Guide
 Loading...
Loading...