
Version 1.0
August 2020
702P08324
Xerox
®
AltaLink
®
Series
Security Information and Event
Management Reference Guide

©2020 Xerox Corporation. All rights reserved. Xerox®, Xerox and Design®, AltaLink®, FreeFlow®, SMARTsend®, Scan
to PC Desktop
Interface Platform
®
, MeterAssistant®, SuppliesAssistant®, Xerox Secure Access Unified ID System®, Xerox Extensible
®
, Global Print Driver®, and Mobile Express Driver®are trademarks of Xerox Corporation in the
United States and / or other countries.
®
Adobe
PostScript
Apple
Mac OS
Google Cloud Print
, Adobe PDF logo, Adobe®Reader®, Adobe®Type Manager®, ATM™, Flash®, Macromedia®, Photoshop®, and
®
are trademarks or registered trademarks of Adobe Systems, Inc.
®
, Bonjour®, EtherTalk™, TrueType®, iPad®, iPhone®, iPod®, iPod touch®, AirPrint®and the AirPrint Logo®, Mac®,
®
, and Macintosh®are trademarks or registered trademarks of Apple Inc. in the U.S. and other countries.
™
web printing service, Gmail™webmail service, and Android™mobile technology platform are
trademarks of Google, Inc.
®
HP-GL
, HP-UX®, and PCL®are registered trademarks of Hewlett-Packard Corporation in the United States and/or
other countries.
®
IBM
and AIX®are registered trademarks of International Business Machines Corporation in the United States and/or
other countries.
McAfee
®
, ePolicy Orchestrator®, and McAfee ePO™are trademarks or registered trademarks of McAfee, Inc. in the
United States and other countries.
Microsoft
®
, Windows Vista®, Windows®, Windows Server®, and OneDrive®are registered trademarks of Microsoft
Corporation in the United States and other countries.
Mopria is a trademark of the Mopria Alliance.
®
Novell
, NetWare®, NDPS®, NDS®, IPX™, and Novell Distributed Print Services™ are trademarks or registered
trademarks of Novell, Inc. in the United States and other countries.
PANTONE
SGI
®
and other Pantone, Inc. trademarks are the property of Pantone, Inc.
®
and IRIX®are registered trademarks of Silicon Graphics International Corp. or its subsidiaries in the United
States and/or other countries.
Sun, Sun Microsystems, and Solaris are trademarks or registered trademarks of Oracle and/or its affiliates in the
United States and other countries.
®
UNIX
is a trademark in the United States and other countries, licensed exclusively through X/ Open Company Limited.
Wi-Fi CERTIFIED Wi-Fi Direct
®
is a trademark of the Wi-Fi Alliance.

Table of Contents
1 Introduction...............................................................................................................................9
SIEM Overview.......... ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ........ 10
Configuring SIEM. ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ....... 10
Supported Printers ..... ..... ........................... ..... ...................... ..... ..... ................. ..... ..... ..... ....... 11
2 Device Configuration .............................................................................................................13
Configuration Overview........ ..... ..... ...................... ..... ........................... ..... ...................... ..... .. 14
Configuring SIEM...... ..... ..... ..... ...................... ..... ...................... ..... ........................... ..... ..... ... 15
Configuring a SIEM Destination ..... ..... ..... ................. ..... ..... ..... ............ ..... ..... ..... ................... 16
Editing a SIEM Destination ........ ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. . 17
3 Message Format .....................................................................................................................19
Message Format Overview .......... ..... ..... ...................... ..... ........................... ..... ...................... 20
Syslog Message Format............ ..... ..... ..... ................. ..... ..... ...................... ..... ......................... 21
Severity Levels ... ..... ................. ..... ..... ...................... ..... ........................... ..... ...................... ... 22
4 Message List ............................................................................................................................23
Message List Overview .......... ..... ........................... ........................... ..... ..... ................. ..... ..... . 29
CEF Key Name Mapping ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ............. 30
1 System Startup .. ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ...................... 32
2 System Shutdown . ..... ...................... ..... ........................... ..... ...................... ..... ..... .............. 33
3 Standard Disk Overwrite Started ..... ..... ..... ...................... ..... ........................... ..... ............... 34
4 Standard Disk Overwrite Complete .......... ..... ........................... ..... ...................... ..... ..... ....... 35
5 Print Job ... ...................... ..... ..... ................. ..... ..... ..... ..... ............ ..... ..... ..... ................. ..... .... 36
6 Network Scan Job ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ............... 37
7 Server Fax Job.... ..... ................. ..... ..... ...................... ..... ........................... ..... ...................... 38
8 Internet Fax Job......... ..... ..... ...................... ..... ........................... ..... ...................... ..... ..... .... 39
9 Email Job.. ..... ..... ..... ................. ..... ..... ...................... ..... ........................... ..... ..................... 40
10 Audit Log Disabled....... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... 41
11 Audit Log Enabled.... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... .... 42
12 Copy Job.. ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ... 43
13 Embedded Fax Job .................... ..... ..... ................. ..... ..... ..... ............ ..... ..... ..... ..... .............. 44
14 LAN Fax Job ... ........................... ..... ..... ................. ..... ..... ..... ............ ..... ..... ..... ..... .............. 45
16 Full Disk Overwrite Started ... ...................... ..... ..... ...................... ..... ..... ................. ..... ..... .. 46
17 Full Disk Overwrite Complete................ ..... ...................... ..... ..... ................. ..... ..... ..... ..... ... 47
20 Scan to Mailbox Job................... ..... ...................... ..... ..... ................. ..... ..... ..... ................. . 48
21 Delete File/Dir...... ..... ..... ..... ...................... ..... ...................... ..... ........................... ..... ..... ... 49
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
3

Table of Contents
23 Scan to Home ............... ..... ..... ................. ..... ..... ..... ..... ............ ..... ..... ..... ................. ..... .... 50
24 Scan to Home Job ..... ................. ..... ..... ...................... ..... ..... ...................... ..... .................. 51
27 Postscript Passwords .. ..... ..... ................. ..... ..... ...................... ..... ..... ...................... ..... ....... 52
29 Network User Login.... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ....... 53
30 SA Login ............... ..... ..... ...................... ..... ........................... ..... ...................... ..... ..... ....... 54
31 User Login . ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. . 55
32 Service Login Diagnostics ........ ..... ........................... ..... ...................... ..... ..... ................. .... 56
33 Audit Log Download ........ ..... ........................... ........................... ..... ..... ................. ..... ..... . 57
34 Immediate Job Overwrite Enablement ........ ..... ...................... ..... ..... ..... ............ ..... ..... ..... . 58
35 SA PIN Changed . ..... ...................... ..... ..... ...................... ..... ...................... ..... ..... .............. 59
36 Audit Log File Saved... ..... ..... ................. ..... ..... ...................... ..... ..... ...................... ..... ....... 60
37 Force Traffic over Secure Connection.......................... ..... ...................... ..... ..... ................. . 61
38 Security Certificate . ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... 62
39 IPsec... ................. ..... ..... ........................... ..... ...................... ..... ...................... ..... ..... ..... ... 63
40 SNMPv3........ ..... ..... ...................... ..... ...................... ..... ..... ...................... ..... ..... ............... 64
41 IP Filtering Rules .......... ..... ........................... ..... ...................... ..... ..... ................. ..... ..... ..... 65
42 Network Authentication Configuration.... ..... ...................... ..... ...................... ..... ............... 66
43 Device Clock .. ..... ..... ..... ................. ..... ..... ...................... ..... ..... ...................... ..... .............. 67
44 Software Upgrade.. ..... ..... ................. ..... ..... ...................... ..... ........................... ..... ........... 68
45 Clone File Operations . ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... .. 69
46 Scan Metadata Validation.. ..... ................. ..... ..... ..... ..... ............ ..... ..... ..... ................. ..... .... 70
47 Xerox Secure Access Configuration.... ..... ................. ..... ..... ...................... ..... ..................... 71
48 Service Login Copy Mode ............... ..... ..... ...................... ..... ........................... ..... .............. 72
49 Smartcard Login .................. ..... ..... ..... ............ ..... ..... ..... ..... ............ ..... ..... ..... ................... 73
50 Process Terminated......... ..... ..... ..... ................. ..... ..... ...................... ..... ........................... .. 74
51 Scheduled Disk Overwrite Configuration.............. ..... ..... ...................... ..... ..... .................... 75
53 Saved Jobs Backup.............. ..... ..... ..... ................. ..... ..... ...................... ..... ..... .................... 76
54 Saved Jobs Restore..... ............ ..... ..... ..... ..... ............ ..... ..... ..... ...................... ..... ................. 77
57 Session Timer Logout ... ..... ..... ..... ................. ..... ..... ...................... ..... ........................... ..... 78
58 Session Timeout Interval Change ...................... ..... ..... ................. ..... ..... ..... ................. ..... 79
59 User Permissions.. ..... ..... ..... ..... ................. ..... ..... ...................... ..... ..... ...................... ..... ... 80
60 Device Clock NTP Configuration ..... ..... ...................... ..... ..... ...................... ..... ..... .............. 81
61 Device Administrator Role Permission.................. ..... ...................... ..... ..... ................. ..... ... 82
62 Smartcard Configuration. ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ..... .. 83
63 IPv6 Configuration.. ..... ..... ............ ..... ..... ..... ...................... ..... ..... ...................... ..... .......... 84
64 802.1x Configuration.. ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...... 85
65 Abnormal System Termination ............. ..... ...................... ..... ..... ...................... ..... ..... ..... ... 86
66 Local Authentication Enablement ... ................. ..... ..... ..... ................. ..... ..... ..... ................. . 87
67 Web User Interface Login Method............. ..... ..... ...................... ..... ...................... ..... ..... ... 88
68 FIPS Mode Configuration ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ....... 89
69 Xerox Secure Access Login. ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... 90
70 Print from USB Enablement................. ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... .... 91
71 USB Port Enablement.... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ..... ......... 92
4
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Table of Contents
72 Scan to USB Enablement ..... ........................... ..... ...................... ..... ..... ................. ..... ..... .. 93
73 System Log Download............. ..... ..... ..... ................. ..... ..... ...................... ..... ..................... 94
74 Scan to USB Job. ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... .................... 95
75 Remote Control Panel Configuration . ..... ........................... ..... ...................... ..... ..... ........... 96
76 Remote Control Panel Session . ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ................ 97
77 Remote Scan Feature Enablement. ..... ................. ..... ..... ..... ................. ..... ..... ..... ............... 98
78 Remote Scan Job Submitted .. ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... 99
79 Remote Scan Job Completed... ...................... ..... ..... ..... ............ ..... ..... ..... ..... ............ ..... .. 100
80 SMTP Connection Encryption ... ..... ..... ................. ..... ..... ..... ................. ..... ..... .................. 101
81 Email Domain Filtering Rule . ..... ..... ..... ............ ..... ..... ..... ..... ............ ..... ..... ..... ................. 102
82 Software Verification Test Started ..... ..... ................. ..... ..... ...................... ..... ................... 103
83 Software Verification Test Complete ............ ..... ..... ..... ................. ..... ..... ...................... ... 104
84 McAfee Security State................ ..... ..... ...................... ..... ........................... ..... ................ 105
85 McAfee Security Event . ..... ..... ...................... ..... ...................... ..... ..... ................. ..... ..... ... 106
87 McAfee Agent ... ..... ...................... ..... ........................... ..... ...................... ..... ..... ............. 107
88 Digital Certificate Import Failure.................. ..... ...................... ..... ..... ................. ..... ..... ... 108
89 Device User Account Management ..... ...................... ..... ..... ................. ..... ..... ..... ............ 109
90 Device User Account Password Change ..... ..... ..... ..... ................. ..... ..... ...................... ..... . 110
91 Embedded Fax Job Secure Print Passcode. ..... ................. ..... ..... ..... ................. ..... ..... ..... .. 111
92 Scan to Mailbox Folder Password ............. ..... ..... ..... ................. ..... ..... ...................... ..... .. 112
93 Embedded Fax Mailbox Passcode ..... ..... ..... ............ ..... ..... ..... ..... ................. ..... ..... .......... 113
94 FTP / SFTP Filing Passive Mode ............ ..... ...................... ..... ..... ................. ..... ..... ..... ..... . 114
95 Embedded Fax Forwarding Rule .. ..... ...................... ..... ........................... ..... .................... 115
96 Allow Weblet Installation . ...................... ..... ..... ................. ..... ..... ..... ..... ............ ..... ..... .... 116
97 Weblet Installation .. ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ..... ....... 117
98 Weblet Enablement ............... ..... ...................... ..... ..... ...................... ..... ..... ................. ... 118
99 Network Connectivity Configuration... ................. ..... ..... ...................... ..... ..... .................. 119
100 Address Book Permissions .................... ..... ..... ...................... ..... ..... ..... ............ ..... ..... .... 120
101 Address Book Export ..... ..... ..... ..... ................. ..... ..... ...................... ..... ........................... 121
102 Software Upgrade Policy....... ..... ...................... ..... ..... ................. ..... ..... ..... ................. .. 122
103 Supplies Plan Activation ........ ..... ........................... ..... ...................... ..... ..... ................. .. 123
104 Plan Conversion . ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ...... 124
105 IPv4 Configuration.. ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ........... 125
106 SA PIN Reset.... ..... ...................... ..... ...................... ..... ..... ...................... ..... ..... ............. 126
107 Convenience Authentication Login ..... ..... ...................... ..... ..... ................. ..... ..... ..... ..... . 127
108 Convenience Authentication Configuration ... ..... ................. ..... ..... ..... ................. ..... ..... 128
109 Embedded Fax Passcode Length ............. ..... ...................... ..... ...................... ..... ..... ..... . 129
110 Custom Authentication Login.... ..... ..... ..... ............ ..... ..... ..... ..... ................. ..... ..... .......... 130
111 Custom Authentication Configuration.. ..... ..... ................. ..... ..... ..... ................. ..... ..... .... 131
112 Billing Impression Mode.. ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ... 132
114 Clone File Installation Policy ............... ..... ...................... ..... ..... ................. ..... ..... ..... ..... 133
115 Save For Reprint Job. ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... 134
116 Web User Interface Access Permission... ..... ...................... ..... ..... ...................... ..... ........ 135
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
5

Table of Contents
117 System Log Push to Xerox ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... .. 136
120 Mopria Print Enablement .. ...................... ..... ........................... ........................... ..... ..... . 137
123 Near Field Communication (NFC) Enablement ............. ..... ...................... ..... ..... ............ 138
124 Invalid Login Attempt Lockout ................. ..... ..... ................. ..... ..... ..... ................. ..... ..... 139
125 Secure Protocol Log Enablement ..... ..... ...................... ..... ..... ...................... ..... ..... ......... 140
126 Display Device Information Configuration.. ..... ................. ..... ..... ...................... ..... ........ 141
127 Successful Login After Lockout Expired.. ..... ...................... ..... ..... ...................... ..... ........ 142
128 Erase Customer Data ................. ..... ...................... ..... ..... ................. ..... ..... ..... ............. 143
129 Audit Log SFTP Scheduled Configuration..... ................. ..... ..... ..... ................. ..... ..... ....... 144
130 Audit Log SFTP Transfer ... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... .. 145
131 Remote Software Download Policy.... ...................... ..... ..... ................. ..... ..... ..... ............ 146
132 AirPrint & Mopria Scanning Configuration................ ..... ...................... ..... ..... ................ 147
133 AirPrint & Mopria Scan Job Submitted............... ..... ........................... ..... ...................... . 148
134 AirPrint & Mopria Scan Job Completed.... ...................... ..... ..... ...................... ..... ..... ..... . 149
136 Remote Services NVM Write. ..... ................. ..... ..... ...................... ..... ..... ...................... ... 150
137 FIK Install via Remote Services............. ..... ..... ................. ..... ..... ..... ..... ............ ..... ..... .... 151
138 Remote Services Data Push .................... ..... ...................... ..... ..... ...................... ..... ..... .. 152
139 Remote Services Enablement . ..... ..... ................. ..... ..... ...................... ..... ....................... 153
140 Restore Backup Installation Policy.. ...................... ..... ..... ...................... ..... .................... 154
141 Backup File Downloaded . ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ... 155
142 Backup File Restored ............. ..... ........................... ..... ...................... ..... ..... ................. .. 156
144 User Permission Role Assignment ... ..... ..... ............ ..... ..... ..... ..... ................. ..... ..... .......... 157
145 User Permission Role Configuration. ..... ..... ..... ................. ..... ..... ...................... ..... ..... .... 158
146 Admin Password Reset Policy Configuration ................... ..... ..... ...................... ..... ..... ..... 159
147 Local User Account Password Policy ....... ..... ..... ..... ................. ..... ..... ...................... ..... .. 160
148 Restricted Administrator Login ..... ..... ........................... ..... ...................... ..... ..... ............ 161
149 Restricted Administrator Role Permission....... ..... ..... ..... ................. ..... ..... ...................... 162
150 Logout............ ..... ..... ...................... ..... ...................... ..... ..... ...................... ..... ..... ......... 163
151 IPP Configuration .......... ..... ........................... ..... ...................... ..... ..... ................. ..... .... 164
152 HTTP Proxy Server Configuration.. ..... ............ ..... ..... ..... ..... ............ ..... ..... ..... ................. 165
153 Remote Services Software Download ............ ..... ..... ..... ..... ............ ..... ..... ..... ................. 166
154 Restricted Administrator Permission Role Configuration.......... ..... ..... ..... ..... ............ ..... .. 167
155 Weblet Installation Security Policy ... ..... ..... ...................... ..... ...................... ..... ............. 168
156 Lockdown and Remediate Security Enablement............ ..... ..... ...................... ..... ..... ....... 169
157 Lockdown Security Check Complete..... ..... ............ ..... ..... ..... ..... ................. ..... ..... .......... 170
158 Lockdown Remediation Complete . ................. ..... ..... ...................... ..... .......................... 171
159 Send Engineering Logs on Data Push .. ..... ...................... ..... ..... ...................... ..... ..... ..... 172
160 Print Submission of Clone Files Policy ............. ..... ..... ..... ................. ..... ..... ..................... 173
161 Network Troubleshooting Data Capture . ..... ........................... ..... ...................... ..... ..... .. 174
162 Network Troubleshooting Data Download ... ...................... ..... ..... ...................... ..... ..... .. 175
163 DNS-SD Record Data Download . ........................... ..... ...................... ..... ..... ................. .. 176
164 One-Touch App Management ....... ..... ..... ...................... ..... ..... ................. ..... ..... ..... ..... . 177
165 SMB Browse Enablement ... ................. ..... ..... ...................... ..... ...................... ..... ..... ..... 178
6
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Table of Contents
166 Standard Job Data Removal Started . ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... .. 179
167 Standard Job Data Removal Complete.............. ..... ..... ..... ................. ..... ..... ..... ............. 180
168 Full Job Data Removal Started ............ ..... ..... ..... ................. ..... ..... ...................... ..... ..... 181
169 Full Job Data Removal Complete............ ..... ..... ..... ................. ..... ..... ...................... ..... .. 182
170 Scheduled Job Data Removal Configuration. ..... ..... ...................... ..... ..... ................. ..... . 183
171 Cross-Origin-Resource-Sharing (CORS) ........ ..... ..... ..... ................. ..... ..... ...................... ... 184
172 One-Touch App Export .. ..... ..... ..... ................. ..... ..... ...................... ..... ..... ...................... 185
173 Fleet Orchestrator Trust Operations.. ...................... ..... ..... ...................... ..... ..... ............. 186
174 Fleet Orchestrator Configuration.. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ....... 187
175 Fleet Orchestrator - Store File for Distribution....... ..... ...................... ..... ..... ................. ... 188
176 Xerox Configuration Watchdog Enablement...... ..... ..... ..... ................. ..... ..... ..... ............. 189
177 Xerox Configuration Watchdog Check Complete ........ ..... ..... ................. ..... ..... ..... ......... 190
178 Xerox Configuration Watchdog Remediation Complete . ..... ..... ................. ..... ..... ..... ...... 191
179 ThinPrint Configuration........ ..... ..... ...................... ..... ..... ...................... ..... .................... 192
180 iBeacon Active ............... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..................... 193
181 Network Troubleshooting Feature ........................ ..... ...................... ..... ..... ................. ... 194
182 POP3 Connection Encryption (TLS) ........................... ..... ...................... ..... ..... ................ 195
183 FTP Browse Configuration ..... ..... ..... ...................... ..... ........................... ..... ................... 196
184 SFTP Browse Configuration . ........................... ........................... ..... ..... ................. ..... .... 197
189 Smart Proximity Sensor “Sleep on Departure” Enablement ..... ..... ..... ..... ..... ............ ..... .. 198
190 Cloud Browsing Enablement. ..... ..... ..... ..... ............ ..... ..... ..... ...................... ..... ..... .......... 199
192 Scan to Cloud Job . ...................... ..... ........................... ..... ...................... ..... ..... ............. 200
193 Xerox Workplace Cloud Enablement.. ..... ..... ................. ..... ..... ..... ................. ..... ..... ....... 201
194 Scan To Save FTP and SFTP Credentials Policy Configured... ..... ..... ..... ................. ..... ..... 202
195 Card Reader ............... ..... ..... ...................... ..... ...................... ..... ..... ................. ..... ..... ... 203
196 EIP App Management.. ...................... ..... ...................... ..... ..... ...................... ..... ..... ..... . 204
197 EIP App Enablement .................... ..... ........................... ..... ...................... ..... ..... ............ 205
199 Card Reader Upgrade Policy..................... ..... ..... ................. ..... ..... ..... ................. ..... ..... 206
200 Card Reader Upgrade Attempted ..... ................. ..... ..... ..... ................. ..... ..... .................. 207
204 Syslog Server Configuration ....... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ......... 208
205 TLS Configuration......... ..... ..... ..... ..... ............ ..... ..... ..... ................. ..... ..... ...................... 209
208 Canceled Job ... ..... ..... ................. ..... ..... ........................... ..... ...................... ..... ............. 210
More Information............ ..... ...................... ..... ..... ................. ..... ..... ..... ..... ............ ..... ..... .... 211
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
7

Table of Contents
8
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

1
Introduction
This chapter contains:
• SIEM Overview............. ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ......... 10
• Supported Printers ........ ..... ........................... ..... ...................... ..... ..... ................. ..... ..... ..... ..... ... 11
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
9
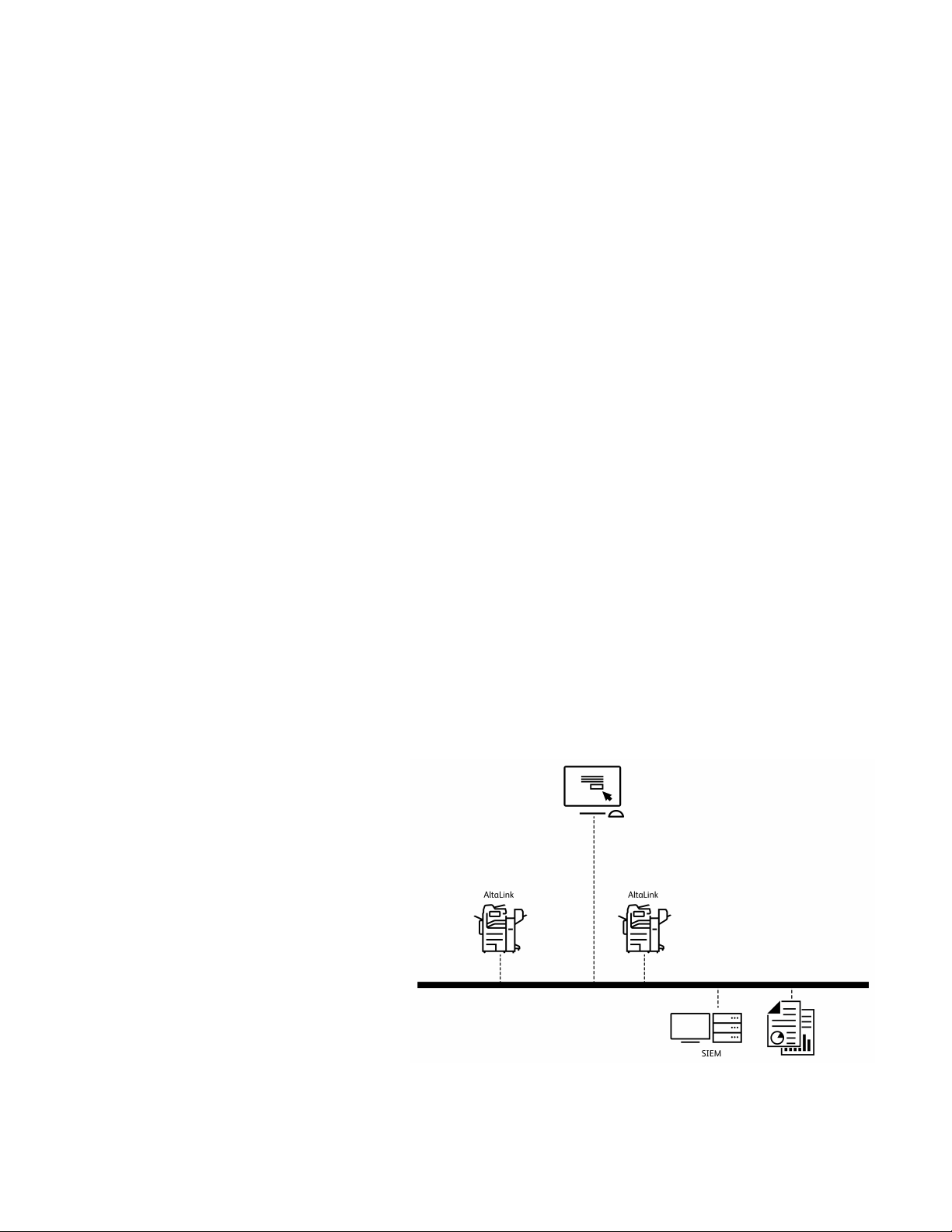
Introduction
SIEM Overview
Security Information Event Management (SIEM) products and services are designed to support the
analysis of security alerts that applications and network hardware generate. SIEM systems offer
advanced analytics and real-time monitoring, including data and application monitoring. SIEM
gathers security event information from the entire network, to centralize data collection and ensure
that Xerox
Supported Xerox
Enterprise Security Manager, LogRhythm, and Splunk Enterprise Security. The SIEM feature enables
your Xerox
syslog protocol. SIEM solutions can provide predefined report templates for most compliance
mandates, such as HIPAA.
Syslog messages that your Xerox device generates are sent automatically to SIEM destinations for
analysis and reporting. In a SIEM system, an administrator can view the events that occurred over a
specific time period, for example, to investigate a security breach. Through security event correlation,
SIEM systems analyze the network for potential threats. Unusual activity in one part of the network
does not always indicate a breach, but multiple unusual activities can indicate an issue.
Events are sent as they occur. Events are transmitted in Common Event Format (CEF), which a SIEM
system can interpret.
For further information about security solutions for your Xerox
com/security, navigate to the AltaLink page, then select your device.
®
AltaLink®devices are included with other networked devices.
®
AltaLink®devices include SIEM firmware support for connections to McAfee
®
AltaLink®device to send security events directly to compatible SIEM systems using the
®
AltaLink®device, go to www.xerox.
CCoonnffiigguurriinngg SSIIEEMM
You can configure up to three SIEM destinations and control the events that are sent to each
destination, based on the level of severity. The severity levels correspond to the syslog severity codes.
SIEM is configured using the SIEM settings in the Embedded Web Server.
To configure your Xerox AltaLink device to input to a SIEM system:
• Access the SIEM settings and select
the destination required.
• Enable sharing for the SIEM
destination.
• Enter the name for the SIEM
destination.
• Select a Transport Protocol to use for
transporting events to the SIEM
destinations.
• Enter the SIEM syslog server details.
• Test the connection to the server.
• Select a logging severity level.
• The device sends event data to the
SIEM system for analysis and
reporting.
For full instructions on configuring SIEM, refer to Device Configuration.
10
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Introduction
Supported Printers
The following devices support the SIEM feature and can be enabled to send audit log events directly
to compatible SIEM systems using the syslog protocol.
• Xerox
• Xerox
®
AltaLink®Series C8130/8135/8145/8155/8170 Multifunction Printers
®
AltaLink®Series B8145/8155/8170 Multifunction Printers
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
11

Introduction
12
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

2
Device Configuration
This chapter contains:
• Configuration Overview................ ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ... 14
• Configuring SIEM.............. ..... ........................... ..... ...................... ..... ..... ................. ..... ..... ..... .... 15
• Configuring a SIEM Destination ... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... .................... 16
• Editing a SIEM Destination .. ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...... 17
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
13

Device Configuration
Configuration Overview
This section describes how to configure and enable the Security Information and Event Management
(SIEM) feature on your Xerox device.
Configuration steps are performed using the Embedded Web Server on the device.
You can configure up to three SIEM destinations and control the events that are sent to each
destination, based on the level of severity. The severity levels correspond to the syslog severity codes.
14
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Device Configuration
Configuring SIEM
To configure the Security Information and Event Management (SIEM) feature:
1. In the Embedded Web Server, click Properties→Security→Logs→SIEM.
Note: Alternatively, to access the SIEM page from the Connectivity setup page, click
Properties→Connectivity→Setup. For SIEM, click Edit.
At the SIEM page, the status area displays the time stamp of the last device event and shows the
enablement state of SIEM destinations.
2. To view the stored events log, click View Events.
The latest syslog events appear in reverse order. The event log can display up to 20,000 events.
To download the events log, click Download Events, then save the syslog.txt file to a folder
on your computer.
3. The Share Events area shows the status of SIEM destinations. The statuses include the following:
• event range; host name settings: The SIEM destination is configured and is enabled
to receive events in the specified range.
• Configured; Not Sharing: The SIEM destination is configured, but is not enabled to
receive events.
• Not Configured: The SIEM destination is not configured.
4. To send a test to the SIEM destinations, click Send Sample Event. At the prompt, click Send. A
sample event is sent to all destinations that are configured and enabled.
Note: If no destinations are configured, the Send Sample Event function is not available.
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
15

Device Configuration
Configuring a SIEM Destination
To configure a Security Information and Event Management (SIEM) destination:
1. In the Embedded Web Server, click Properties→Security→Logs→SIEM.
2. In the Share Events area, click the row for the destination that you need to configure. The
destination settings window appears.
3. To enable the destination to receive events, for Enable Sharing, click the toggle button.
4. In the Destination Name field, type a name for the SIEM destination.
5. In the Connection area, configure the settings.
a. To select a protocol for transporting events to the configured destinations, for Transport
Protocol, select an option:
• TCP/TLS (Secure/Recommended): This is a reliable protocol. This option is the default
and is the most secure.
• TCP: This is a reliable protocol.
• UDP
Note: Transmission Control Protocol (TCP) is a reliable protocol that performs well with
networks that are linked physically and with hosts that are stationary. TCP checks that
all data packets are delivered to the receiving host, and retransmits any lost packets.
This process ensures that all transmitted data is received eventually.
b. For Host (Syslog Server), specify a destination by host name, IPv4, or IPv6 address.
Note:
• The device supports destination port numbers from 1–65535.
• If you select TCP/TLS, the default port number is 6514.
• If you select TCP or UDP, the default port number is 514.
6. To test the connection:
a. Ensure that sharing is enabled.
b. Click Test Connection.
c. If the ping to the destination fails, verify the configuration, then retest the connection.
7. In the Event Policies area, click Event Range. In the Event Range window, select a logging severity
level, then click Save. The default is severity level 4.
Note: When you select a severity level, messages for that level and more critical levels are
sent to the SIEM destination.
8. Click Save.
9. To send a test to the SIEM destinations, click Send Sample Event. At the prompt, click Send. A
sample event is sent to all destinations that are configured and enabled. Check with the SIEM
Administrator to confirm that their SIEM system received the Xerox device event.
Note: If no destinations are configured, the Send Sample Event function is not available.
16
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Device Configuration
Editing a SIEM Destination
To edit a Security Information and Event Management (SIEM) destination:
1. In the Embedded Web Server, click Properties→Security→Logs→SIEM.
2. In the Share Events area, click the row for the destination that you need to edit.
3. At the prompt, select an option:
• To view or modify the destination settings, click Edit. For details, refer to Configuring a SIEM
Destination.
• To clear the destination settings, click Reset. At the confirmation prompt, click Reset.
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
17

Device Configuration
18
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

3
Message Format
This chapter contains:
• Message Format Overview .................. ..... ...................... ..... ..... ................. ..... ..... ..... ................. . 20
• Syslog Message Format.................... ..... ..... ...................... ..... ...................... ..... ..... ..................... 21
• Severity Levels . ..... ..... ...................... ..... ...................... ..... ..... ...................... ..... ..... ................. .... 22
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
19

Message Format
Message Format Overview
Syslog messages that your Xerox device generates include the log message and a standard set of
data that provides details about the event. Information about the source Xerox device, when the
event happened, the severity level, and a description of the syslog event are provided.
Syslog messages use the RFC 5424 Syslog Protocol, and are reported using Common Event Format
(CEF). CEF standard format was developed by ArcSight. CEF is an extensible, text-based format,
designed to support multiple device types. CEF defines a syntax for log records that comprises a
standard header and variable extension, which are formatted as key-value pairs.
Xerox syslog event messages are composed of the following predefined fields:
<109>
SYSLOG-MSG
SYSLOG-HEADER
CEF Header
CEF Message
2020-04-12T19:20:50-05:00
SalesNEteam
CEF:0
Xerox
Altalink C8135
111.009.009.23300
1
System startup
5
dvchost=SalesNEteam deviceExternalId=
GN1592376
20
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
Message Format
Syslog Message Format
The following table lists each of the syslog message fields and provides a description and example of
the data that is generated for each field.
Fields
SYSLOGHEADER
PRI The PRI number is known as the
Description Example
<109>
Priority value (PRIVAL) and
represents both the Facility and
Severity. The Priority value is
calculated by multiplying the
Facility code by 8, then adding
the numerical value of the
Severity.
Note: Xerox devices use
Log Audit Facility code 13.
TIMESTAMP yyyy-mm-ddThh:mm:ss+-ZONE 2020-04-12T19:20:50-
05:00
HOSTNAME Hostname of the device SalesNEteam
CEF Header CEF:Version CEF:0 CEF:0
Device Vendor Device manufacturer Xerox
Device Product Device model name Altalink C8135
Device Version Device Software Version 111.009.009.23300
Device Event ClassIDAudit Log ID 1
Name Description of the event System startup
Severity Syslog severity 5
CEF Message [Extension] The audit log event entry data,
formatted in CEF format
dvchost=SalesNEteam
deviceExternalId=
GN1592376
Example of a complete event:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |1 | System startup |5|dvchost=SalesNEteam
deviceExternalId=GN1592376
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
21
Message Format
Severity Levels
The System Administrator can control the events that are sent to SIEM systems based on severity.
Syslog messages that are generated by Xerox devices use the following severity levels, as defined in
the RFC 5424 Syslog Protocol:
Numerical
Code
0 Emergency System is unusable
1 Alert Action must be taken immediately
2 Critical Critical conditions
3 Error Error conditions
4 Warning Warning conditions
Severity Level Description
5 Notice Normal but significant condition
6 Informational Informational messages
7 Debug Debug-level messages
22
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

4
Message List
This chapter contains:
• Message List Overview ............. ..... ...................... ..... ..... ...................... ..... ..... ................. ..... ..... .. 29
• CEF Key Name Mapping ... ..... ................. ..... ..... ...................... ..... ..... ...................... ..... .............. 30
• 1 System Startup ..... ..... ...................... ..... ........................... ..... ...................... ..... ..... ................. . 32
• 2 System Shutdown ................. ..... ...................... ..... ..... ...................... ..... ..... ................. ..... ..... .. 33
• 3 Standard Disk Overwrite Started......................... ..... ...................... ..... ..... ................. ..... ..... ..... 34
• 4 Standard Disk Overwrite Complete ............. ..... ........................... ..... ...................... ..... ..... ..... ... 35
• 5 Print Job . ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ..... ...................... ..... 36
• 6 Network Scan Job ... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ................ 37
• 7 Server Fax Job.. ..... ..... ...................... ..... ........................... ..... ...................... ..... ..... ................. . 38
• 8 Internet Fax Job................. ..... ...................... ..... ..... ...................... ..... ..... ................. ..... ..... ..... 39
• 9 Email Job ..... ..... ..... ..... ................. ..... ..... ...................... ..... ...................... ..... ..... ...................... 40
• 10 Audit Log Disabled ............... ..... ..... ...................... ..... ........................... ..... ...................... ..... . 41
• 11 Audit Log Enabled............ ..... ..... ...................... ..... ........................... ..... ...................... ..... ..... 42
• 12 Copy Job ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... .... 43
• 13 Embedded Fax Job . ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ............... 44
• 14 LAN Fax Job . ..... ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ............... 45
• 16 Full Disk Overwrite Started . ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ... 46
• 17 Full Disk Overwrite Complete.............. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... .... 47
• 20 Scan to Mailbox Job................. ..... ..... ..... ................. ..... ..... ..... ............ ..... ..... ..... ..... .............. 48
• 21 Delete File/Dir.............. ..... ..... ...................... ..... ...................... ..... ..... ................. ..... ..... ..... .... 49
• 23 Scan to Home . ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... 50
• 24 Scan to Home Job ... ..... ...................... ..... ........................... ..... ...................... ..... ..... .............. 51
• 27 Postscript Passwords ..... ..... ..... ...................... ..... ........................... ........................... ..... ..... ... 52
• 29 Network User Login.. ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ............. 53
• 30 SA Login . ................. ..... ..... ...................... ..... ........................... ..... ...................... ..... ..... ..... ... 54
• 31 User Login.. ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... 55
• 32 Service Login Diagnostics ...................... ..... ........................... ..... ...................... ..... ..... ........... 56
• 33 Audit Log Download .... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... .... 57
• 34 Immediate Job Overwrite Enablement .. ..... ................. ..... ..... ..... ................. ..... ..... ..... ........... 58
• 35 SA PIN Changed ................. ..... ........................... ..... ...................... ..... ..... ................. ..... ..... .. 59
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
23

Message List
• 36 Audit Log File Saved. ..... ..... ..... ...................... ..... ........................... ........................... ..... ..... ... 60
• 37 Force Traffic over Secure Connection.. ..... ...................... ..... ..... ................. ..... ..... ..... .............. 61
• 38 Security Certificate.. ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... .............. 62
• 39 IPsec. ..... ...................... ..... ........................... ..... ...................... ..... ..... ................. ..... ..... ..... .... 63
• 40 SNMPv3................ ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ........... 64
• 41 IP Filtering Rules .................. ........................... ..... ...................... ..... ..... ..... ............ ..... ..... ..... . 65
• 42 Network Authentication Configuration.. ..... ........................... ..... ...................... ..... ..... ........... 66
• 43 Device Clock................. ..... ..... ..... ................. ..... ..... ...................... ..... ........................... ..... .... 67
• 44 Software Upgrade..... ..... ..... ...................... ..... ...................... ..... ..... ...................... ..... ..... ....... 68
• 45 Clone File Operations ............... ..... ..... ..... ............ ..... ..... ..... ................. ..... ..... ..... ................... 69
• 46 Scan Metadata Validation..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... 70
• 47 Xerox Secure Access Configuration.. ..... ...................... ..... ..... ...................... ..... ...................... 71
• 48 Service Login Copy Mode . ................. ..... ..... ...................... ..... ...................... ..... ..... ............... 72
• 49 Smartcard Login. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ..... ......... 73
• 50 Process Terminated ................. ..... ..... ...................... ..... ........................... ..... ...................... ... 74
• 51 Scheduled Disk Overwrite Configuration ...................... ..... ........................... ..... ..................... 75
• 53 Saved Jobs Backup ..... ................. ..... ..... ...................... ..... ........................... ..... ..................... 76
• 54 Saved Jobs Restore... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... .................. 77
• 57 Session Timer Logout ..... ............ ..... ..... ..... ................. ..... ..... ........................... ...................... 78
• 58 Session Timeout Interval Change ... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. . 79
• 59 User Permissions .......... ..... ..... ..... ................. ..... ..... ...................... ..... ..... ...................... ..... .... 80
• 60 Device Clock NTP Configuration ........ ..... ...................... ..... ..... ...................... ..... ..... ............... 81
• 61 Device Administrator Role Permission................ ..... ..... ..... ................. ..... ..... ..... ............ ..... .... 82
• 62 Smartcard Configuration.... ..... ..... ................. ..... ..... ...................... ..... ........................... ..... ... 83
• 63 IPv6 Configuration..... ..... ..... ................. ..... ..... ...................... ..... ........................... ..... ........... 84
• 64 802.1x Configuration ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ....... 85
• 65 Abnormal System Termination ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ... 86
• 66 Local Authentication Enablement . ..... ..... ............ ..... ..... ..... ..... ............ ..... ..... ..... ................... 87
• 67 Web User Interface Login Method................ ..... ........................... ..... ...................... ..... ..... .... 88
• 68 FIPS Mode Configuration ... ..... ...................... ..... ........................... ..... ...................... ..... ..... ... 89
• 69 Xerox Secure Access Login.... ..... ..... ...................... ..... ..... ...................... ..... ...................... ..... . 90
• 70 Print from USB Enablement... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... 91
• 71 USB Port Enablement.. ..... ..... ............ ..... ..... ..... ...................... ..... ........................... ............... 92
• 72 Scan to USB Enablement ... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ... 93
• 73 System Log Download................ ..... ..... ..... ................. ..... ..... ...................... ..... ...................... 94
• 74 Scan to USB Job.... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ..................... 95
24
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
• 75 Remote Control Panel Configuration ................. ..... ..... ..... ................. ..... ..... ..... ............ ..... .... 96
• 76 Remote Control Panel Session ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... .... 97
• 77 Remote Scan Feature Enablement.... ..... ..... ................. ..... ..... ..... ................. ..... ..... ................ 98
• 78 Remote Scan Job Submitted ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. . 99
• 79 Remote Scan Job Completed. ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ... 100
• 80 SMTP Connection Encryption .. ...................... ..... ........................... ..... ...................... ..... ..... . 101
• 81 Email Domain Filtering Rule ............... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ....... 102
• 82 Software Verification Test Started ... ..... ..... ................. ..... ..... ...................... ..... .................... 103
• 83 Software Verification Test Complete..... ..... ................. ..... ..... ........................... ..... ............... 104
• 84 McAfee Security State.. ...................... ..... ...................... ..... ..... ................. ..... ..... ..... ............ 105
• 85 McAfee Security Event.. ..... ........................... ..... ...................... ..... ..... ................. ..... ..... ..... .. 106
• 87 McAfee Agent ................. ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ... 107
• 88 Digital Certificate Import Failure..................... ..... ...................... ..... ..... ..... ............ ..... ..... .... 108
• 89 Device User Account Management ... ..... ...................... ..... ..... ................. ..... ..... ..... ............. 109
• 90 Device User Account Password Change ........ ..... ..... ...................... ..... ..... ...................... ..... .. 110
• 91 Embedded Fax Job Secure Print Passcode.... ..... ..... ................. ..... ..... ...................... ..... ........ 111
• 92 Scan to Mailbox Folder Password. ..... ..... ..... ................. ..... ..... ...................... ..... ................... 112
• 93 Embedded Fax Mailbox Passcode ... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ........... 113
• 94 FTP / SFTP Filing Passive Mode..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... . 114
• 95 Embedded Fax Forwarding Rule................. ..... ...................... ..... ..... ................. ..... ..... ..... ..... 115
• 96 Allow Weblet Installation ..... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................ 116
• 97 Weblet Installation ..... ..... ..... ............ ..... ..... ..... ...................... ..... ........................... ..... ........ 117
• 98 Weblet Enablement... ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ..... 118
• 99 Network Connectivity Configuration. ..... ...................... ..... ........................... ..... ................... 119
• 100 Address Book Permissions........ ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................ 120
• 101 Address Book Export ............. ..... ........................... ..... ...................... ..... ..... ................. ..... . 121
• 102 Software Upgrade Policy .......... ..... ...................... ..... ..... ................. ..... ..... ..... ................. ... 122
• 103 Supplies Plan Activation ...................... ..... ........................... ..... ...................... ..... ..... ......... 123
• 104 Plan Conversion .......... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... . 124
• 105 IPv4 Configuration..... ..... ................. ..... ..... ...................... ..... ........................... ..... ............ 125
• 106 SA PIN Reset....... ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ......... 126
• 107 Convenience Authentication Login ... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... .. 127
• 108 Convenience Authentication Configuration . ..... ..... ..... ................. ..... ..... ...................... ..... . 128
• 109 Embedded Fax Passcode Length. ........................... ..... ...................... ..... ..... ................. ..... . 129
• 110 Custom Authentication Login....... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ........... 130
• 111 Custom Authentication Configuration ..... ..... ..... ...................... ..... ..... ...................... ..... ..... 131
Xerox
®
AltaLink®Series
25
Security Information and Event Management Reference Guide

Message List
• 112 Billing Impression Mode ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... ..... .... 132
• 114 Clone File Installation Policy... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... 133
• 115 Save For Reprint Job.... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ...................... ..... . 134
• 116 Web User Interface Access Permission. ..... ..... ...................... ..... ........................... ..... ......... 135
• 117 System Log Push to Xerox ... ..... ..... ................. ..... ..... ...................... ..... ........................... ... 136
• 120 Mopria Print Enablement ..... ...................... ..... ...................... ..... ..... ...................... ..... ..... .. 137
• 123 Near Field Communication (NFC) Enablement .. ..... ...................... ..... ..... ................. ..... ..... 138
• 124 Invalid Login Attempt Lockout ... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... . 139
• 125 Secure Protocol Log Enablement ........ ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ..... 140
• 126 Display Device Information Configuration..... ...................... ..... ..... ...................... ..... ......... 141
• 127 Successful Login After Lockout Expired ..... ..... ...................... ..... ..... ...................... ..... ......... 142
• 128 Erase Customer Data .................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ......... 143
• 129 Audit Log SFTP Scheduled Configuration... ..... ...................... ..... ........................... ..... ........ 144
• 130 Audit Log SFTP Transfer . ..... ..... ..... ................. ..... ..... ...................... ..... ........................... ... 145
• 131 Remote Software Download Policy.. ..... ...................... ..... ..... ................. ..... ..... ..... ............. 146
• 132 AirPrint & Mopria Scanning Configuration................... ..... ..... ................. ..... ..... ..... ............ 147
• 133 AirPrint & Mopria Scan Job Submitted.................. ..... ..... ...................... ..... ..... ................. .. 148
• 134 AirPrint & Mopria Scan Job Completed.. ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... .. 149
• 136 Remote Services NVM Write.... ..... ...................... ..... ........................... ..... ...................... .... 150
• 137 FIK Install via Remote Services................ ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... 151
• 138 Remote Services Data Push . ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ... 152
• 139 Remote Services Enablement ...................... ..... ...................... ..... ...................... ..... ..... ..... . 153
• 140 Restore Backup Installation Policy ..... ........................... ..... ...................... ..... ..... ................ 154
• 141 Backup File Downloaded .......... ..... ..... ..... ..... ............ ..... ..... ..... ...................... ..... ............... 155
• 142 Backup File Restored ..... ...................... ..... ...................... ..... ..... ...................... ..... ..... ......... 156
• 144 User Permission Role Assignment . ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ........... 157
• 145 User Permission Role Configuration......... ..... ..... ...................... ..... ........................... ..... ..... 158
• 146 Admin Password Reset Policy Configuration ...................... ..... ..... ................. ..... ..... ..... ..... . 159
• 147 Local User Account Password Policy..... ...................... ..... ........................... ..... ................... 160
• 148 Restricted Administrator Login ........ ..... ........................... ..... ...................... ..... ..... ............. 161
• 149 Restricted Administrator Role Permission ............... ..... ..... ...................... ..... ...................... . 162
• 150 Logout .................... ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ..... 163
• 151 IPP Configuration........... ..... ...................... ..... ..... ...................... ..... ..... ................. ..... ..... ... 164
• 152 HTTP Proxy Server Configuration..... ..... ................. ..... ..... ..... ................. ..... ..... .................. 165
• 153 Remote Services Software Download ... ................. ..... ..... ..... ................. ..... ..... .................. 166
• 154 Restricted Administrator Permission Role Configuration. ................. ..... ..... ..... ................. ... 167
26
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
• 155 Weblet Installation Security Policy.... ..... ........................... ..... ...................... ..... ..... ............ 168
• 156 Lockdown and Remediate Security Enablement.................... ..... ........................... ..... ........ 169
• 157 Lockdown Security Check Complete... ..... ..... ................. ..... ..... ..... ................. ..... ..... ........... 170
• 158 Lockdown Remediation Complete ....... ..... ........................... ..... ...................... ..... ..... ......... 171
• 159 Send Engineering Logs on Data Push ..... ..... ...................... ..... ..... ...................... ..... ..... ..... . 172
• 160 Print Submission of Clone Files Policy ..... ..... ................. ..... ..... ..... ................. ..... ..... ........... 173
• 161 Network Troubleshooting Data Capture ................. ..... ..... ..... ................. ..... ..... ..... ............ 174
• 162 Network Troubleshooting Data Download . ..... ..... ................. ..... ..... ..... ................. ..... ..... ... 175
• 163 DNS-SD Record Data Download .......... ..... ...................... ..... ..... ...................... ..... ..... ......... 176
• 164 One-Touch App Management .......... ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... ....... 177
• 165 SMB Browse Enablement . ........................... ..... ...................... ..... ...................... ..... ..... ..... . 178
• 166 Standard Job Data Removal Started.. ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ...... 179
• 167 Standard Job Data Removal Complete ..... ................. ..... ..... ..... ................. ..... ..... .............. 180
• 168 Full Job Data Removal Started .................... ..... ..... ...................... ..... ...................... ..... ..... . 181
• 169 Full Job Data Removal Complete ... ................. ..... ..... ...................... ..... ........................... ... 182
• 170 Scheduled Job Data Removal Configuration.... ..... ..... ..... ............ ..... ..... ..... ..... ............ ..... .. 183
• 171 Cross-Origin-Resource-Sharing (CORS) ..... ..... ............ ..... ..... ..... ...................... ..... ............... 184
• 172 One-Touch App Export .......... ..... ..... ...................... ..... ........................... ..... ...................... . 185
• 173 Fleet Orchestrator Trust Operations ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ......... 186
• 174 Fleet Orchestrator Configuration ..... ..... ..... ..... ..... ................. ..... ..... ...................... ..... ........ 187
• 175 Fleet Orchestrator - Store File for Distribution ..... ..... ..... ..... ................. ..... ..... ..... ................ 188
• 176 Xerox Configuration Watchdog Enablement.............. ..... ..... ..... ................. ..... ..... .............. 189
• 177 Xerox Configuration Watchdog Check Complete. ...................... ..... ..... ..... ............ ..... ..... .... 190
• 178 Xerox Configuration Watchdog Remediation Complete ............... ..... ..... ..... ................. ..... . 191
• 179 ThinPrint Configuration................ ..... ........................... ..... ...................... ..... ..... ................ 192
• 180 iBeacon Active . ................. ..... ..... ..... ..... ............ ..... ..... ..... ................. ..... ..... ...................... 193
• 181 Network Troubleshooting Feature....... ..... ..... ...................... ..... ..... ................. ..... ..... ..... ..... 194
• 182 POP3 Connection Encryption (TLS) ... ..... ................. ..... ..... ..... ................. ..... ..... ..... ............ 195
• 183 FTP Browse Configuration ........ ..... ..... ...................... ..... ........................... ..... .................... 196
• 184 SFTP Browse Configuration .......... ..... ........................... ..... ...................... ..... ..... ................ 197
• 189 Smart Proximity Sensor “Sleep on Departure” Enablement ............. ..... ..... ..... ................. ... 198
• 190 Cloud Browsing Enablement......... ..... ..... ..... ................. ..... ..... ...................... ..... ................ 199
• 192 Scan to Cloud Job ............ ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... . 200
• 193 Xerox Workplace Cloud Enablement ..... ..... ..... ..... ................. ..... ..... ...................... ..... ........ 201
• 194 Scan To Save FTP and SFTP Credentials Policy Configured........... ..... ..... ...................... ..... . 202
• 195 Card Reader ....................... ........................... ..... ...................... ..... ..... ..... ............ ..... ..... .... 203
Xerox
®
AltaLink®Series
27
Security Information and Event Management Reference Guide

Message List
• 196 EIP App Management ..... ...................... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... .. 204
• 197 EIP App Enablement . ...................... ..... ...................... ..... ..... ...................... ..... ..... ............. 205
• 199 Card Reader Upgrade Policy.. ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... . 206
• 200 Card Reader Upgrade Attempted ... ..... ..... ................. ..... ..... ...................... ..... ................... 207
• 204 Syslog Server Configuration...................... ..... ..... ................. ..... ..... ..... ..... ............ ..... ..... .... 208
• 205 TLS Configuration ................. ..... ..... ..... ................. ..... ..... ...................... ..... ...................... . 209
• 208 Canceled Job .... ...................... ..... ..... ...................... ..... ..... ................. ..... ..... ..... ................ 210
• More Information ............... ..... ..... ................. ..... ..... ..... ................. ..... ..... ..... ................. ..... ..... 211
28
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
Message List Overview
This section provides a list of the syslog messages that are generated by Xerox devices. Events are
transmitted in Common Event Format (CEF) and are sent as they occur.
System Administrators can use the message lists provided to analyze reported data, identify specific
events, and investigate issues. A list of the standard CEF key names is provided to help administrators
understand the message data that is generated.
For detailed information about the settings and features related to the record events, refer to the
System Administrator Guide for your printer available at www.xerox.com/office/support, or the
Embedded Web Server Help.
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
29
Message List
CEF Key Name Mapping
This table provides information about the standard CEF key names that are used in syslog event
messages that your Xerox device generates. The key name used in the messages, the full name of the
field, and a description of each name is provided.
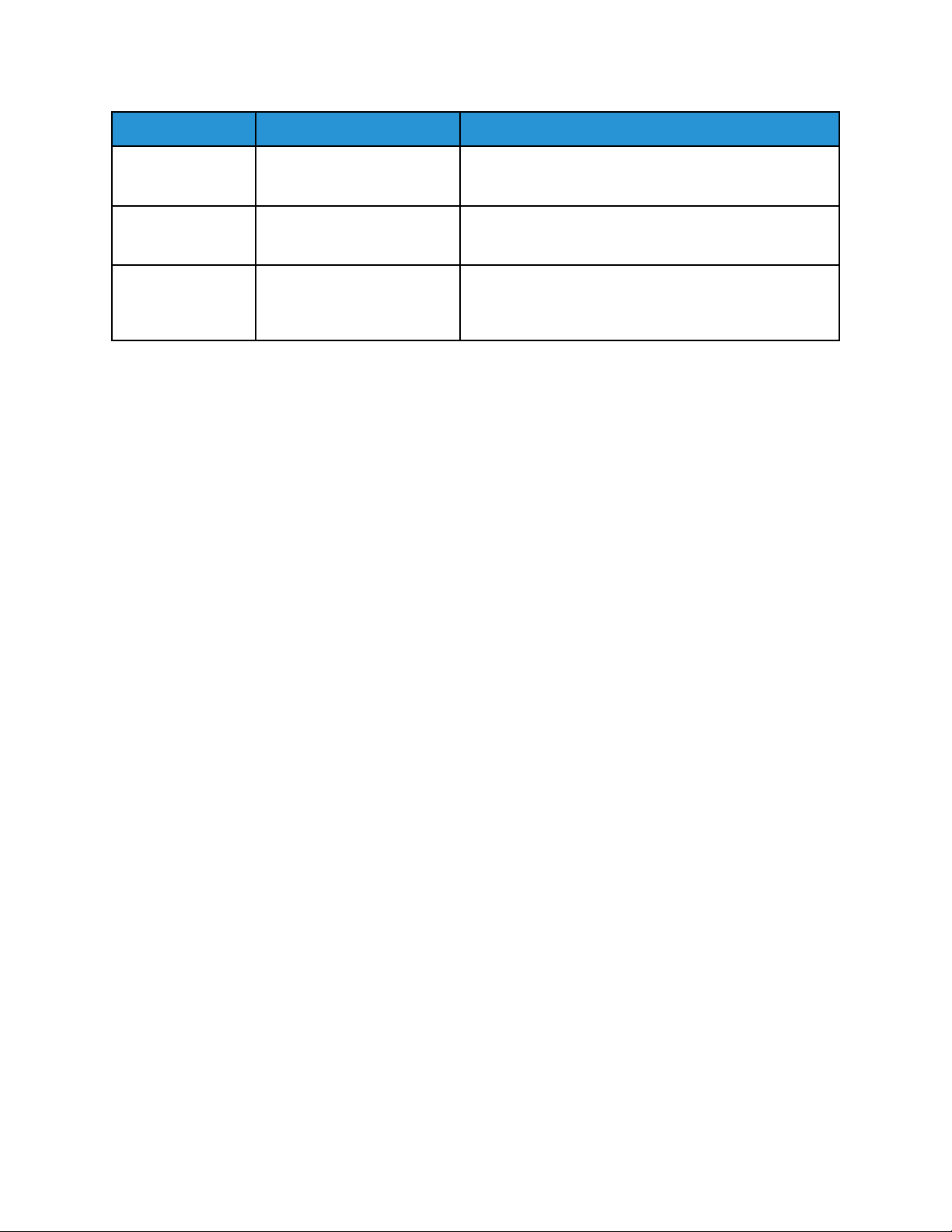
Key Name
suser sourceUserName Identifies the source user by name, which is usually the
duser destinationUserName Identifies the user associated with the event
dvchost deviceHostName Displays the device name that is configured for the
deviceExternalId deviceExternalId Displays the serial number of the device.
act deviceAction Identifies the action taken by the device. Also shows
dst destinationAddress Displays a destination IPv4 address, IPv6 address, or
src sourceAddress Displays a source or session IPv4 address or IPv6
Full Name
Description
user logged in to the device when the event occurs.
Additionally, email addresses are mapped into the
UserName fields.
destination or target.
device.
the action taken after job completion.
host name.
address.
fileType fileType Shows the file types used in an event.
fname filename Shows the file names of files used in an event.
msg message Provides additional information about an event.
outcome eventOutcome Identifies the outcome of an event.
reason Reason Identifies the reason an event was generated.
request requestUrl Displays the URL that was accessed during an event.
spriv sourceUserPrivileges Shows the user privilege or role assigned to the user
during an event.
sproc sourceProcessName Displays the name of the event source process.
sourceServiceName sourceServiceName Identifies the service that is responsible for generating
the event.
30
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
Message List
Key Name
xrxjob1 Job Name - (Xerox Custom
xrxaccUID1 Accounting User ID-Name -
xrxaccAID1 Accounting Account ID -
Full Name
Key Name)
(Xerox Custom Key Name)
Name (Xerox Custom Key
Name)
Description
Shows the Job Name used on the Xerox device.
Identifies the Accounting User ID used on the Xerox
device.
Identifies the Accounting Account ID used on the Xerox
device.
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
31

Message List
1 System Startup
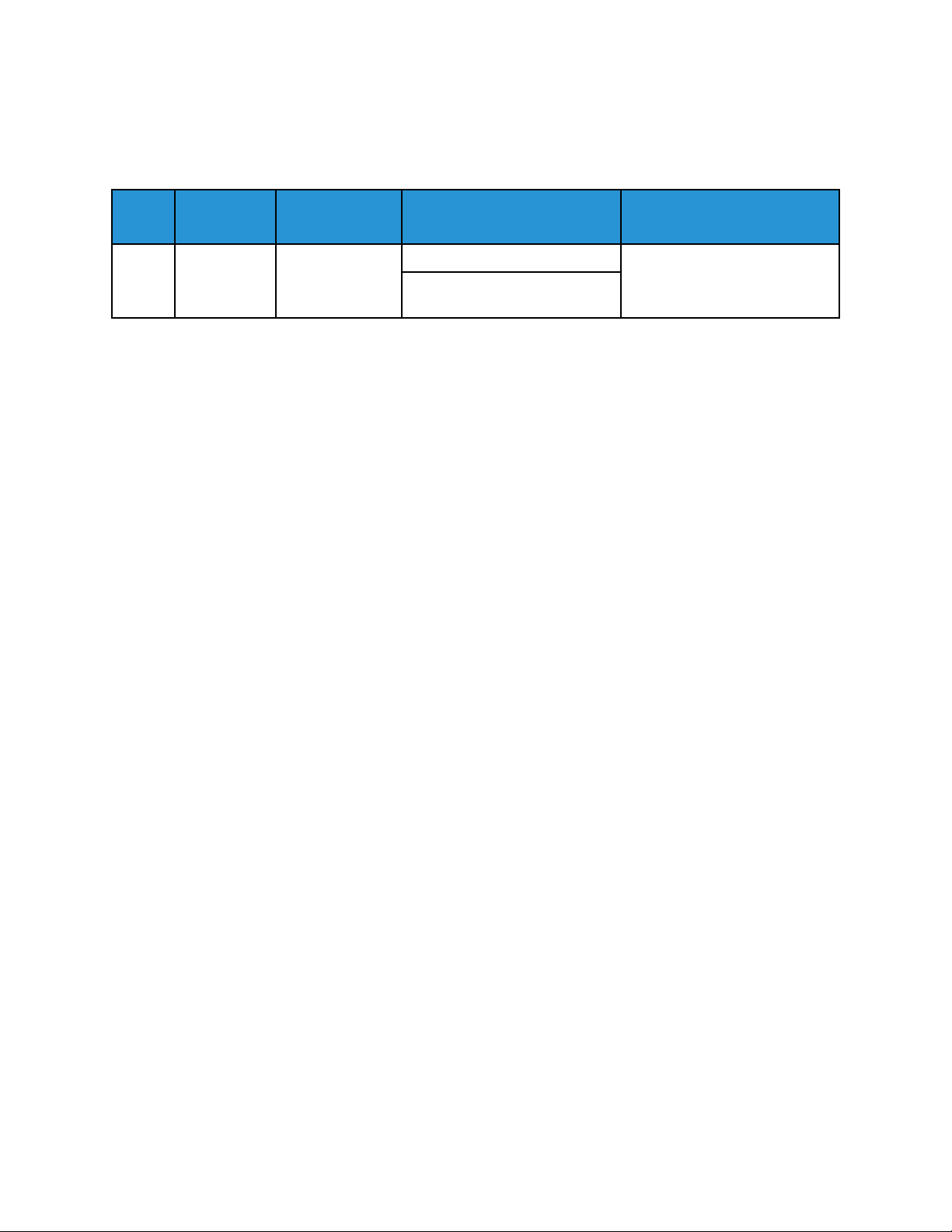
When the device is powered on or restarts, a System Startup event is recorded.
Event
ID
1 System
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |1 | System startup |5|dvchost=SalesNEteam
deviceExternalId=GN123456
Event
Description Syslog Severity
5–Notice dvchost=Device Name
Startup
Event Data Additional Information
deviceExternalId=Device Serial
Number
32
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
Message List
2 System Shutdown
When the device is powered off or a shutdown occurs, a System Shutdown event is recorded.
Event
ID
2 System
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
109.009.009.21000 |2 | System shutdown |5|dvchost=SalesNEteam
deviceExternalId=GN123456
Event
Description
Shutdown
Syslog
Severity
5–Notice dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
33

Message List
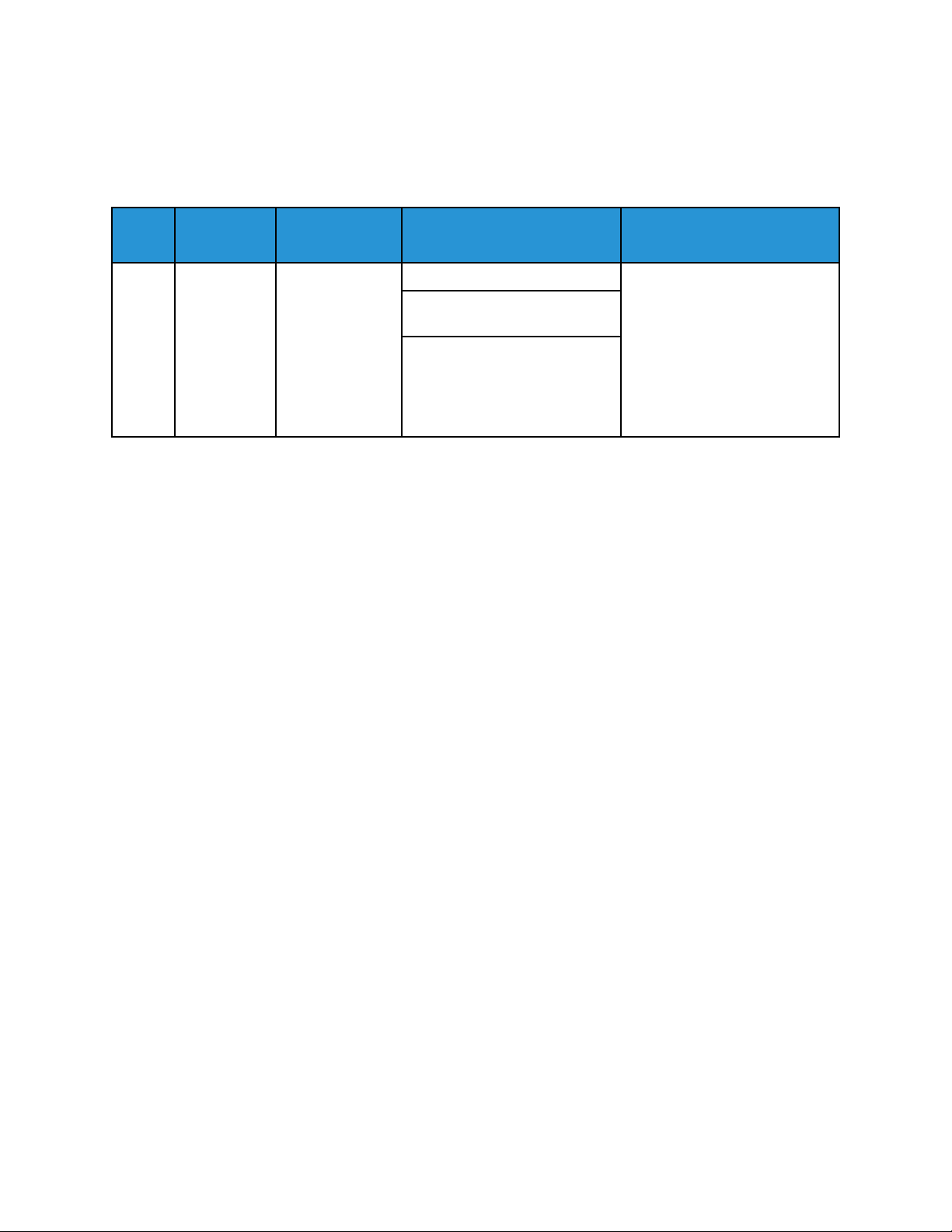
3 Standard Disk Overwrite Started
When a manual or scheduled Standard Disk Overwrite starts, a Standard Disk Overwrite Started event
is recorded.
Event
ID
3 Standard
Event
Description
Disk
Overwrite
Started
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
• This event applies to
devices with a hard disk
drive (HDD), and does not
apply to devices fitted with
a solid-state drive (SSD).
• This event applies to
manual and scheduled
Standard On-Demand
Image Overwrite (ODIO).
• The User Name is the
name of the user that
started, enabled, or
configured the scheduled
ODIO.
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |3 | Standard disk overwrite started |5|suser=Admin
dvchost=SalesNEteam deviceExternalId=GN123456
34
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
Message List
4 Standard Disk Overwrite Complete
When a manual or scheduled Standard Disk Overwrite completes, a Standard Disk Overwrite
Complete event is recorded.
Event
ID
4 Standard
Event
Description
Disk
Overwrite
Complete
Syslog
Severity
5–Notice dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
outcome=Completion Status
• This event applies to
devices with a hard disk
drive (HDD), and does not
apply to devices fitted with
a solid-state drive (SSD).
• This event applies to
manual and scheduled
Standard On-Demand
Image Overwrite (ODIO).
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |4 | Standard disk overwrite complete |5|dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Success
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
35

Message List
5 Print Job
On completion of a print Job, a Print Job event is recorded. Print jobs include jobs submitted using a
print driver, a USB drive, the Embedded Web Server, EIP Apps, AirPrint, Mopria, or another Internet
Printing Protocol (IPP).
Event
ID
5 Print Job 6–Informational xrxjob1=Job Name Accounting User ID can be for
Event
Description
Syslog
Severity
Event Data Additional Information
suser=User Name
sourceServiceName=Cloud
Service | Print From USB | Print
From URL
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
Job Based Accounting (JBA) or
Xerox Standard Accounting.
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |5 | Print job |6|xrxjob1=SalesReport suser=JSmith
sourceServiceName=Print From URL outcome=Success act=IIO Not Applicable
xrxaccUID1=JSmith xrxaccAID1=Sales
36
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
6 Network Scan Job
When a workflow scan job is completed and filed to any network location, a Network Scan Job event
is recorded.
Event
ID
6 Network
Event
Description
Scan Job
Syslog
Severity
6–Informational xrxjob1=Job Name
Event Data Additional Information
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
msg=total-number-netdestination + net-destination
• The event is triggered on
job completion.
• EIP apps can create scan
jobs that do not always
relate directly to the name
of the app, for example,
Scan to Cloud Email.
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |6 | Network scan job |6|xrxjob1=SalesReport suser=JSmith
outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith xrxaccAID1=Sales
msg=1 13.61.23.216:446
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
37

Message List
7 Server Fax Job
When a server fax job completes, a Server Fax Job event is recorded.
Event
ID
7 Server Fax
Event
Description
Job
Syslog
Severity
6–Informational xrxjob1=Job Name The event is triggered on job
Event Data Additional Information
completion.
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
msg=Total-fax-recipient-phonenumbers + fax-recipient-phonenumbers + net-destination
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |7 | Server fax job |6|xrxjob1=SalesReport suser=JSmith
outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith xrxaccAID1=Sales
msg=1 04425808899 13.61.17.230:443
38
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

8 Internet Fax Job
When an internet fax job completes, an Internet Fax Job event is recorded.
Message List
Event
ID
8 Internet Fax
Event
Description
Job
Syslog
Severity
6–Informational xrxjob1=Job Name
Event Data Additional Information
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
msg=Total-number-of-smtprecipients + smtp-recipients
• The event occurs when
internet fax data is sent,
received or printed.
• The event is triggered on
job completion.
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |8 | Internet fax job |6|xrxjob1=SalesReport suser=JSmith
outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith xrxaccAID1=Sales
msg=1 Jane Doe <jane.doe@acme.com>
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
39

Message List
9 Email Job
When an email job completes, an Email Job event is recorded. Both the Email app and the Scan To
app can create email jobs.
Event
ID
9 Email Job 6–Informational xrxjob1=Job Name The event is triggered on
Event
Description
Syslog
Severity
Event Data Additional Information
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
msg=Encryption On or Off +
total-number-of-smtprecipients + smtp-recipients
completion of an outgoing
email job.
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |9 | Email job |6|xrxjob1=SalesReport suser=JSmith
outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith xrxaccAID1=Sales
msg=Encryption-Off 1 jane.doe@acme.com
40
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
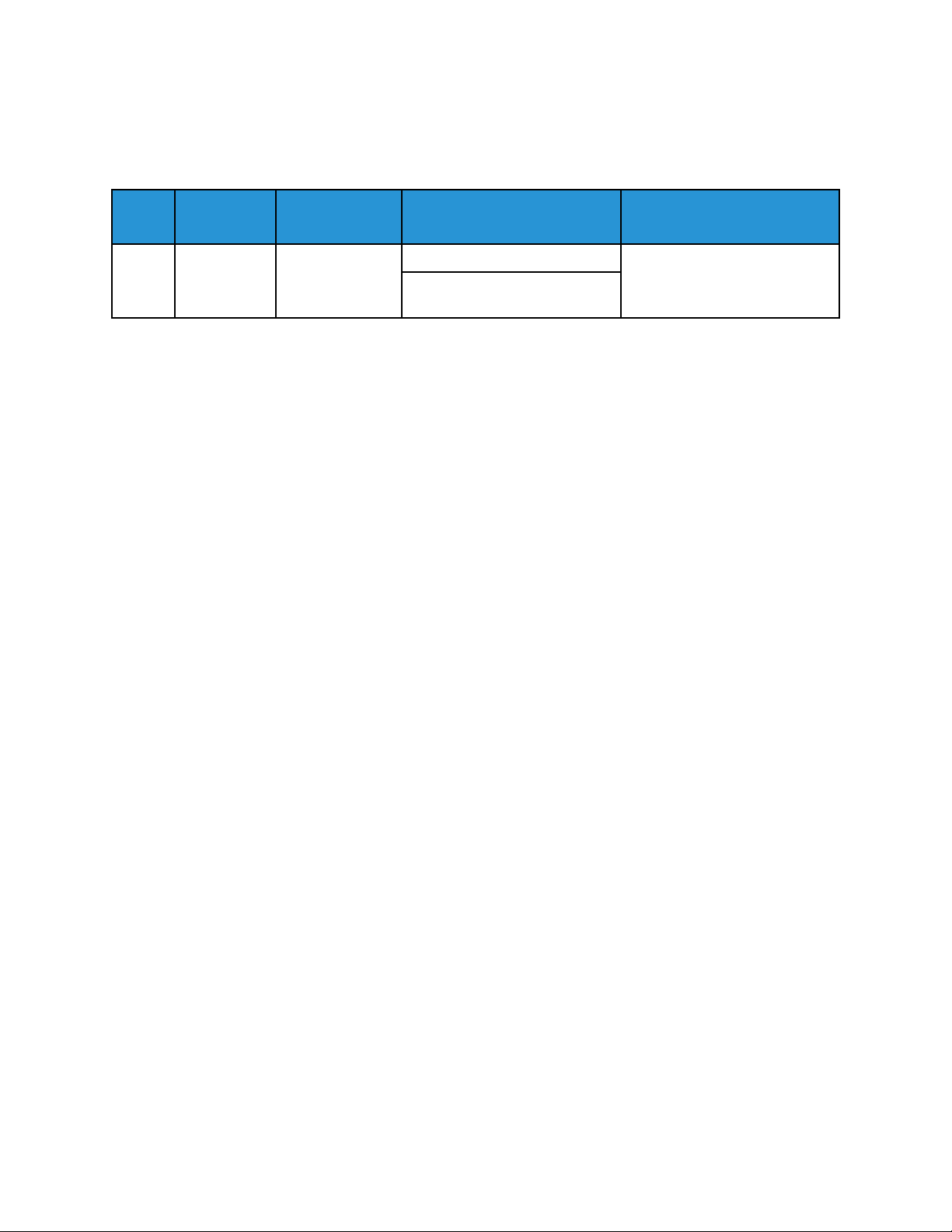
10 Audit Log Disabled
When the audit log is disabled, an Audit Log Disabled event is recorded.
Message List
Event
ID
10 Audit Log
Example Message:
<105> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |10 | Audit log disabled |1|dvchost=SalesNEteam
deviceExternalId=GN123456
Event
Description
Disabled
Syslog
Severity
1–Alert dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
41

Message List
11 Audit Log Enabled
When the audit log is enabled, an Audit Log Enabled event is recorded.
Event
ID
11 Audit Log
Example Message:
<108> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |11 | Audit log enabled |4|dvchost=SalesNEteam
deviceExternalId=GN123456
Event
Description
Enabled
Syslog
Severity
4–Warning dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
42
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

12 Copy Job
When copy job completes, a Copy Job event is recorded.
Message List
Event
ID
12 Copy Job 6–Informational xrxjob1=Job Name The event is triggered on job
Event
Description
Syslog
Severity
Event Data Additional Information
completion.
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |12 | Copy job |6|xrxjob1=SalesReport suser=JSmith
outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith xrxaccAID1=Sales
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
43
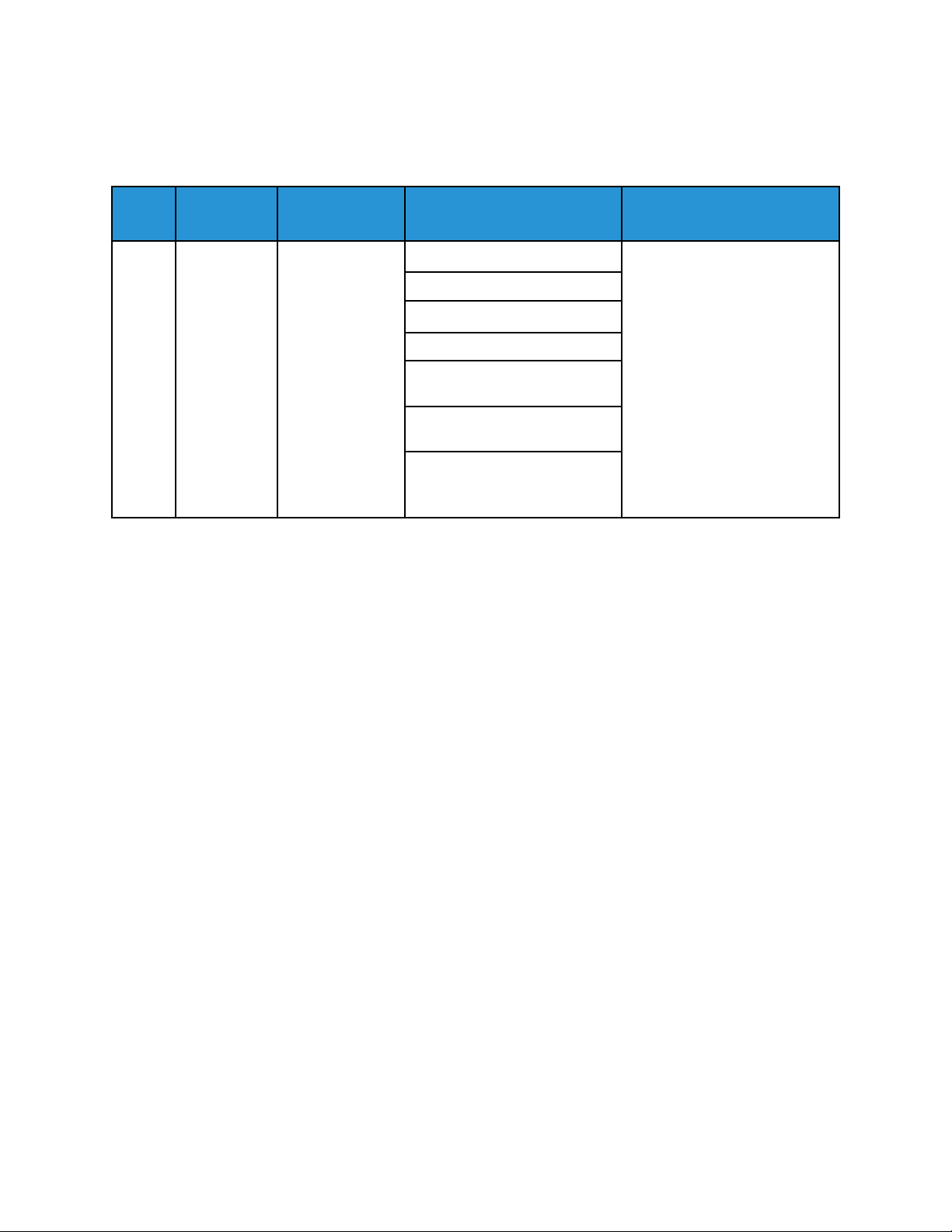
Message List
13 Embedded Fax Job
When an embedded fax job completes, an Embedded Fax Job event is recorded.
Event
ID
13 Embedded
Event
Description
Fax Job
Syslog
Severity
6–Informational xrxjob1=Job Name The event is triggered on job
Event Data Additional Information
completion.
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
msg=Total-fax-recipientphone-numbers + Faxrecipient-phone-numbers
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |13 | Embedded fax job |6|xrxjob1=SalesReport suser=
JSmith outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith
xrxaccAID1=Sales msg=1 04422889966
44
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
14 LAN Fax Job
You can send a fax job from your computer using the print driver. On completion of a fax job that was
sent using the print driver, a LAN Fax Job event is recorded.
Event
ID
14 LAN Fax Job 6–Informational xrxjob1=Job Name The event is triggered on job
Event
Description
Syslog
Severity
Event Data Additional Information
completion.
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
msg=Total-fax-recipient-phonenumbers + Fax-recipientphone-numbers
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |14 | LAN fax job |6|xrxjob1=SalesReport suser=JSmith
outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith xrxaccAID1=Sales
msg=1 04422669933
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
45

Message List
16 Full Disk Overwrite Started
When a full disk overwrite starts, a Full Disk Overwrite Started event is recorded.
Event
ID
16 Full Disk
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |16 | Full disk overwrite started |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456
Event
Description
Overwrite
Started
Syslog
Severity
5–Notice suser=User Name This event applies to devices
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
with a hard disk drive (HDD),
and does not apply to devices
fitted with a solid-state drive
(SSD).
46
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

17 Full Disk Overwrite Complete
When a full disk overwrite completes, a Full Disk Overwrite Complete event is recorded.
Message List
Event
ID
17 Full Disk
Event
Description
Overwrite
Complete
Syslog
Severity
5–Notice dvchost=Device Name This event applies to devices
Event Data Additional Information
deviceExternalId=Device Serial
Number
outcome=Completion Status
with a hard disk drive (HDD),
and does not apply to devices
fitted with a solid-state drive
(SSD).
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |17 | Full disk overwrite complete |5|dvchost=SalesNEteam
deviceExternalId=GN123456 outcome=Success
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
47

Message List
20 Scan to Mailbox Job
When a scan to mailbox job completes, a Scan to Mailbox Job event is recorded.
Event
ID
20 Scan to
Event
Description
Mailbox Job
Syslog
Severity
6–Informational xrxjob1=Job Name
Event Data Additional Information
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
• The event is triggered on
job completion.
• Mailboxes are located on
the internal storage of the
device.
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |20 | Scan to mailbox job |6|xrxjob1=SalesReport suser=
JSmith outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith
xrxaccAID1=Sales
48
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
21 Delete File/Dir
When a file or directory is deleted from the device Hard Disk Drive (HDD), a Delete File/Dir event is
recorded.
Event
ID
21 Delete File/
Event
Description
Dir
Syslog
Severity
4–Warning sourceServiceName=Service This event applies to saved
Event Data Additional Information
fname=Job Name / Dir Name
suser=User Name
outcome=Completion Status
act=IIO Status
jobs and network
troubleshooting data capture.
Example Message:
<108> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |21 | Delete file/dir |4|sourceServiceName=Print fname=
SalesReport suser=JSmith outcome=Success act=IIO Success
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
49

Message List
23 Scan to Home
When the Scan to Home app is enabled or disabled, a Scan to Home event is recorded.
Event
ID
23 Scan to
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |23 | Scan to home |6|suser=Admin dvchost=SalesNEteam
deviceExternalId=GN123456 outcome=Enabled
Event
Description
Home
Syslog
Severity
6–Informational suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
50
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

24 Scan to Home Job
When a Scan to Home job completes, a Scan to Home Job event is recorded.
Message List
Event
ID
24 Scan to
Event
Description
Home Job
Syslog
Severity
6–Informational xrxjob1=Job Name
Event Data Additional Information
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
msg=total-number-netdestination + net-destination
• The event is triggered on
job completion.
• The job is scanned to the
home directory of the
current authenticated user.
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |24 | Scan to home job |6|xrxjob1=SalesReport suser=
JSmith outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith
xrxaccAID1=Sales msg=1 192.168.1.6
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
51

Message List
27 Postscript Passwords
When PostScript passwords are enabled, disabled, or changed, a Postscript Passwords event is
recorded.
Event
ID
27 Postscript
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |27 | Postscript passwords |6|dvchost=SalesNEteam
deviceExternalId=GN123456 act=StartJobPassword outcome=Changed
Event
Description
Passwords
Syslog
Severity
6–Informational dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
act=StartupMode |
SystemParamsPassword |
StartJobPassword
outcome=Status
52
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

29 Network User Login
When the devices authenticates a network user, a Network User Login event is recorded.
Message List
Event
ID
29 Network
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |29 | Network User login |6|suser=JSmith dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Success
Event
Description
User Login
Syslog
Severity
6–Informational suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
53

Message List
30 SA Login
When any user who has administrative rights logs in to the device, an SA Login event is recorded.
Event
ID
30 SA Login 6–Informational suser=User Name
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |30 | SA login |6|suser=Admin dvchost=SalesNEteam
deviceExternalId=GN123456 outcome=Success
Event
Description
Syslog
Severity
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
54
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

31 User Login
When the local user database authenticates a user login, a User Login event is recorded.
Message List
Event
ID
31 User Login 6–Informational suser=User Name
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |31 | User login |6|suser=JSmith dvchost=SalesNEteam
deviceExternalId=GN123456 outcome=Success
Event
Description
Syslog
Severity
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
55

Message List
32 Service Login Diagnostics
When a Xerox service representative logs in to the diagnostic mode on the device, a Service Login
Diagnostic event is recorded.
Event
ID
32 Service Login
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |32 | Service login diagnostics |5|sourceServiceName=
Copy dvchost=SalesNEteam deviceExternalId=GN123456 outcome=Success
Event
Description
Diagnostics
Syslog
Severity
5–Notice sourceServiceName=Service
Event Data Additional Information
Name
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
If an invalid pin is entered for
this event, failed is recorded
in the message.
56
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
33 Audit Log Download
When the audit log is downloaded from the device, an Audit Log Download event is recorded.
Event
ID
33 Audit Log
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |33 | Audit log download |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 msg=Web UI outcome=Success
Event
Description
Download
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
msg=Destination
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
57
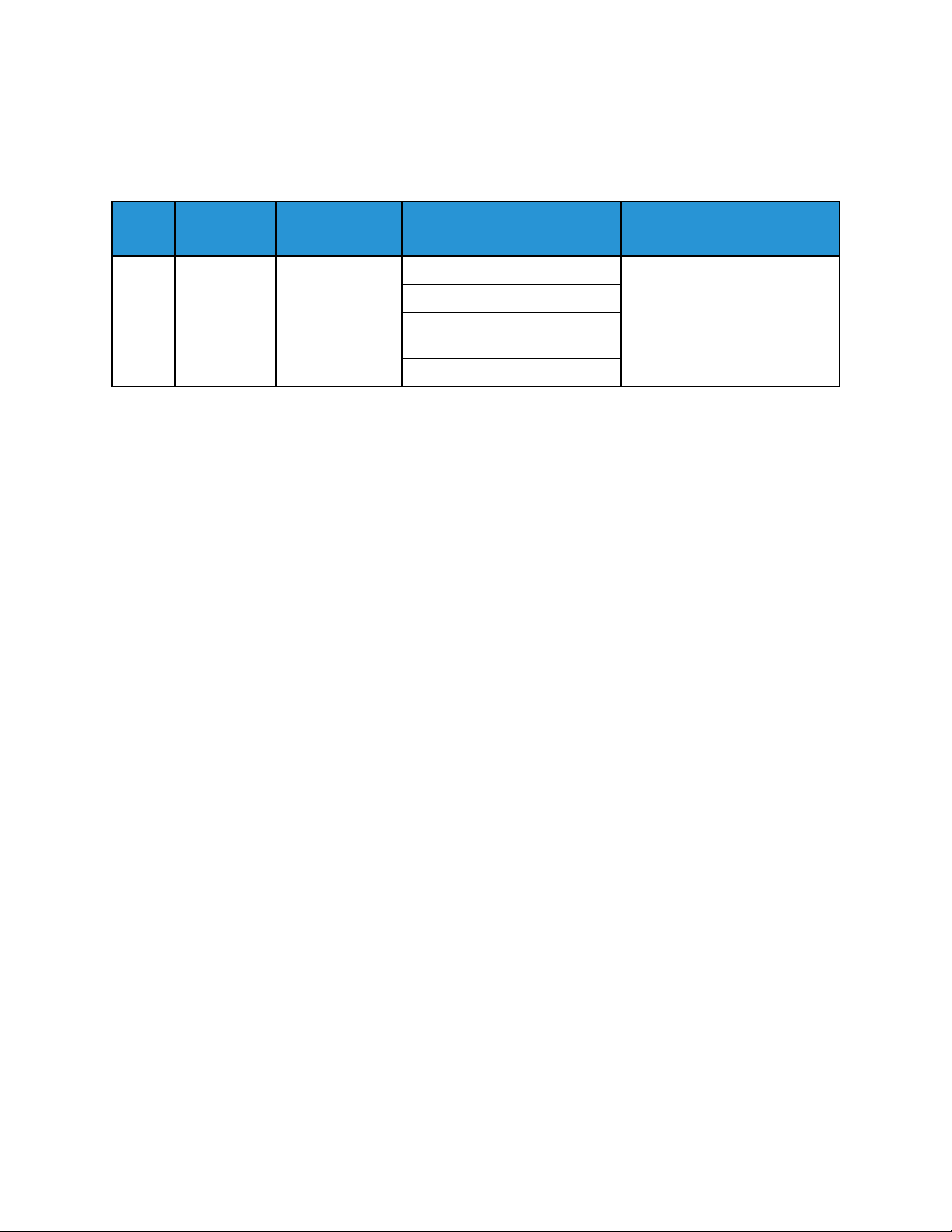
Message List
34 Immediate Job Overwrite Enablement
When the Immediate Job Overwrite feature is enabled or disabled, an Immediate Job Overwrite
Enablement event is recorded.
Event
ID
34 Immediate
Event
Description
Job
Overwrite
Enablement
Syslog
Severity
5–Notice suser=User Name This event applies to devices
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Status
with a hard disk drive (HDD),
and does not apply to devices
fitted with a solid-state drive
(SSD).
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |34 | Immediate job overwrite enablement |5|suser=Admin
dvchost=SalesNEteam deviceExternalId=GN123456 outcome=Enabled
58
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
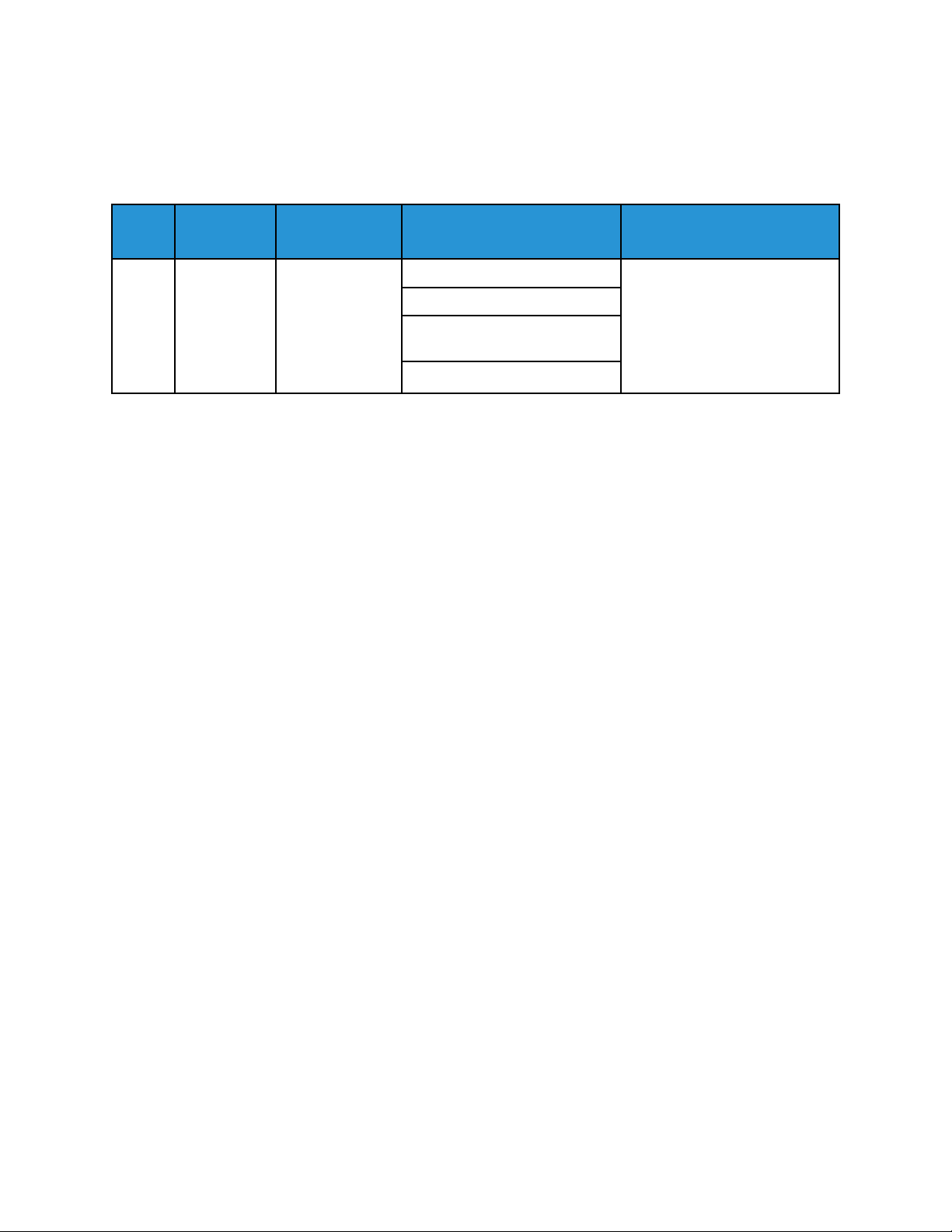
Message List
35 SA PIN Changed
When the system administrator admin account password is changed, an SA PIN Changed event is
recorded.
Event
ID
35 SA PIN
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |35 | SA PIN changed |5|suser=Admin dvchost=SalesNEteam
deviceExternalId=GN123456 outcome=Success
Event
Description
Changed
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
59

Message List
36 Audit Log File Saved
When the Audit Log file is saved to the device internal storage, an Audit Log File Saved event is
recorded.
Event
ID
36 Audit Log
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |36 | Audit log file saved |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Success
Event
Description
File Saved
Syslog
Severity
5–Notice suser=User Name This event precedes an Audit
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
Log Download activity.
60
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
37 Force Traffic over Secure Connection
When the Force Traffic over Secure Connection (HTTPS) setting is enabled, disabled, or terminated,
a Force Traffic over Secure Connection (HTTPS) event is recorded.
Event
ID
37 Force Traffic
Event
Description
over Secure
Connection
(HTTPS)
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
• HTTPS is used for the
connection to the
Embedded Web Server on
the device. Some webpages
are required to use HTTPS
regardless of the Force
Traffic over Secure
Connection (HTTPS)
setting.
• If the Completion Status
shows as Terminated,
the User Name is not
shown in the message.
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |37 | Force traffic over secure connection |5|suser=Admin
dvchost=SalesNEteam deviceExternalId=GN123456 outcome=Enabled
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
61

Message List
38 Security Certificate
When a digital certificate is created, imported, exported, or deleted, a Security Certificate event is
recorded.
Event
ID
38 Security
Event
Description
Certificate
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
• Digital certificates that
apply to this event include
the Xerox Device
Certificate, CA-Signed
certificates, Certificate
Authority (CA) certificates,
and Peer Device
certificates.
• Additionally, a Certificate
Signing Request (CSR)
triggers this event.
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |38 | Security certificate |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Created
62
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

39 IPsec
When IPsec is enabled, disabled, configured, or terminated, an IPsec event is recorded.
Message List
Event
ID
39 IPsec 5–Notice suser=User Name If the Completion Status
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |39 | IPsec |5|suser=Admin dvchost=SalesNEteam
deviceExternalId=GN123456 outcome=Configured
Event
Description
Syslog
Severity
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
shows as Terminated, the
User Name is not shown in the
message.
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
63

Message List
40 SNMPv3
When SNMPv3 is enabled, disabled, configured, or terminated, an SNMPv3 event is recorded.
Event
ID
40 SNMPv3 5–Notice suser=User Name If the Completion Status
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |40 | SNMPv3 |5|suser=Admin dvchost=SalesNEteam
deviceExternalId=GN123456 outcome=Configured
Event
Description
Syslog
Severity
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
shows as Terminated, the
User Name is not shown in the
message.
64
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
41 IP Filtering Rules
When an IP Filtering rule is added, edited, or deleted, an IP Filtering Rules event is recorded.
Event
ID
41 IP Filtering
Example Message:
<108> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |41 | IP Filtering Rules |4|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Rule Added
Event
Description
Rules
Syslog
Severity
4–Warning suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
65

Message List
42 Network Authentication Configuration
When the Login Method for the local user interface is changed to or from Validate on the Network, a
Network Authentication Configuration event is recorded.
Event
ID
42 Network
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |42 | Network authentication configuration |5|suser=
Admin dvchost=SalesNEteam deviceExternalId=GN123456 outcome=Configured
Event
Description
Authentication
Configuration
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
66
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
43 Device Clock
When the device clock settings for time zone, date and time, time format, or date format are
changed, a Device Clock event is recorded.
Event
ID
43 Device Clock 5–Notice suser=User Name
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |43 | Device clock |5|suser=Admin dvchost=SalesNEteam
deviceExternalId=GN123456 outcome=Time zone changed
Event
Description
Syslog
Severity
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
67
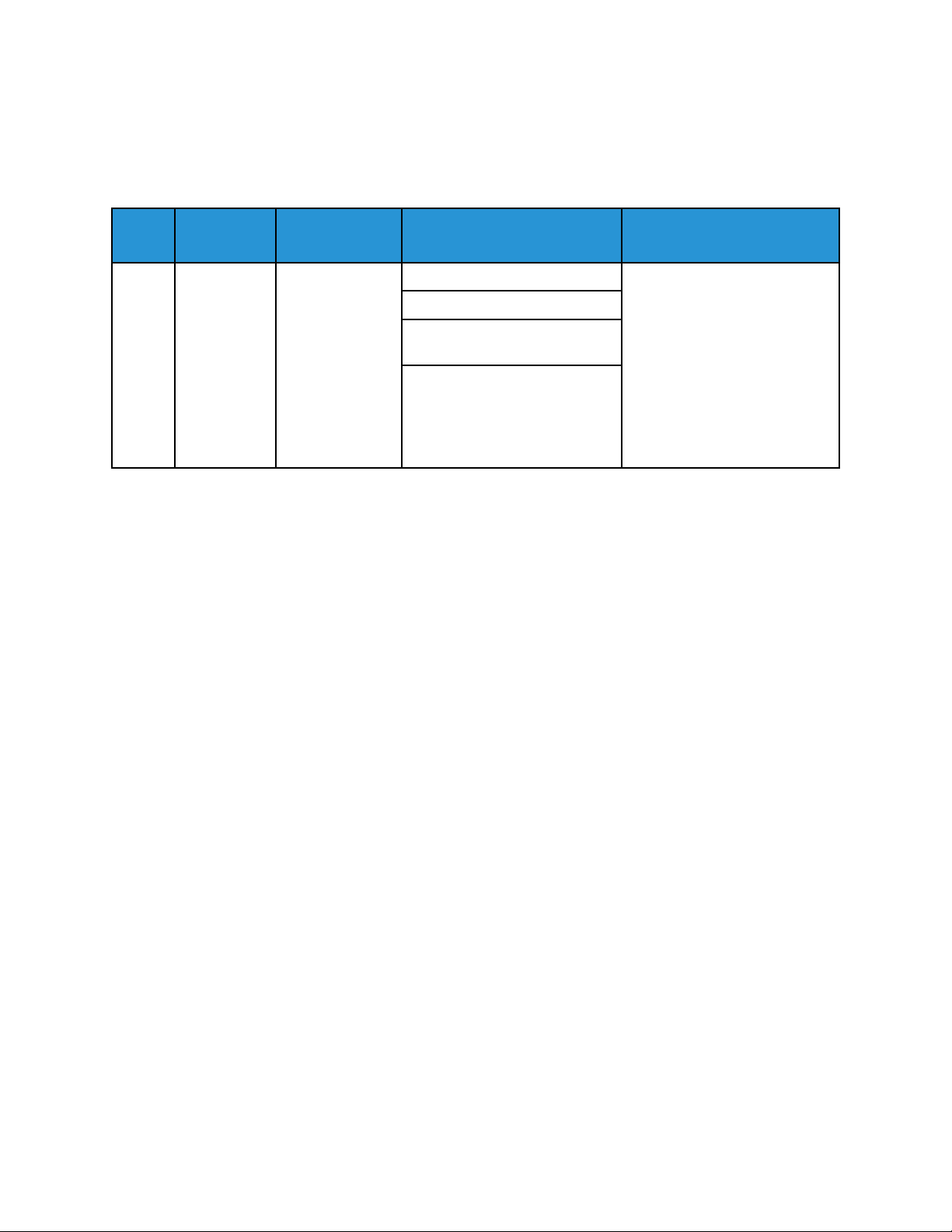
Message List
44 Software Upgrade
When a software installation is attempted, a Software Upgrade event is recorded. The event provides
the outcome of the installation attempt.
Event
ID
44 Software
Event
Description
Upgrade
Syslog
Severity
4–Warning suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
• For Fleet Orchestrator
installations, the file can be
downloaded, rather than
installed locally. For this
type of event, the
originator of the file is
recorded.
• For Fleet Orchestrator
installations, the User
Name shows as
DeviceFileDist.
Example Message:
<108> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |44 | Software upgrade |4|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Success
68
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
45 Clone File Operations
When a clone file is installed, downloaded, or submitted, a Clone File Operations event is recorded.
Event
ID
45 Clone File
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.210000 |45 | Clone file operations |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Clone file installed:
Success
Event
Description
Operations
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
69

Message List
46 Scan Metadata Validation
When the device attempts to validate metadata that a user enters during a Workflow Scanning job, a
Scan Metadata Validation event is recorded.
Event
ID
46 Scan
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |46 | Scan metadata validation |5|dvchost=SalesNEteam
deviceExternalId=GN123456 outcome=Metadata validation success
Event
Description
Metadata
Validation
Syslog
Severity
5–Notice dvchost=Device Name The message indicates
Event Data Additional Information
deviceExternalId=Device Serial
Number
outcome=Completion Status
whether the metadata
validation succeeded or failed.
70
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
47 Xerox Secure Access Configuration
When the Login Method for the local user interface is configured, or changed to or from Xerox Secure
Access, a Xerox Secure Access Configuration event is recorded.
Event
ID
47 Xerox Secure
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |47 | Xerox secure access configuration |5|dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Configured
Event
Description
Access
Configuration
Syslog
Severity
5–Notice dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
71

Message List
48 Service Login Copy Mode
When a Xerox service representative logs in to diagnostic mode to make test copies after they service
the device, a Service Login Copy Mode event is recorded.
Event
ID
48 Service Login
Example Message:
<109> 22020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |48 | Service login copy mode |5|sourceServiceName=
Service Name dvchost=SalesNEteam deviceExternalId=GN123456 outcome=
Success
Event
Description
Copy Mode
Syslog
Severity
5–Notice sourceServiceName=Service
Event Data Additional Information
Name
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
If an invalid login code is
entered, failed event 32
appears.
72
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

49 Smartcard Login
When a user logs in to the device using a smart card, a Smartcard Login event is recorded.
Message List
Event
ID
49 Smartcard
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |49 | Smartcard login |5|suser=JSmith dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Success
Event
Description
Login
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
73
Message List
50 Process Terminated
When an internal process is terminated, a Process Terminated event is recorded.
Event
ID
50 Process
Example Message:
<105> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |50 | Process terminated |1|dvchost=SalesNEteam
deviceExternalId=GN123456 sproc=File2EFax Name reason=Crash
Event
Description
Terminated
Syslog
Severity
1–Alert dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
sproc=Process Name
reason=Termination Reason
74
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
Message List
51 Scheduled Disk Overwrite Configuration
When a Scheduled Disk Overwrite is enabled, disabled, or configured, a Scheduled Disk Overwrite
Configuration event is recorded.
Event
ID
51 Scheduled
Event
Description
Disk
Overwrite
Configuration
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
• This event applies to
devices with a hard disk
drive (HDD), and does not
apply to devices fitted with
a solid-state drive (SSD).
• The Completion Status is
shown as one of the
following:
– Enabled
– Disabled
– Schedule Mode
Configured
– Schedule
Frequency
Configured
– Schedule Day Of
Week Configured
– Schedule Day Of
Month Configured
– Schedule Minute
Of Day Configured
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |51 | Scheduled disk overwrite configuration |5|suser=
Admin dvchost=SalesNEteam deviceExternalId=GN123456 outcome=Schedule Mode
Configured
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
75

Message List
53 Saved Jobs Backup
When saved jobs are backed up to an FTP server, a Saved Jobs Backup event is recorded.
Event
ID
53 Saved Jobs
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |53 | Saved jobs backup |6|fname=SalesReport suser=JSMith
outcome=Normal act=IIO Not Applicable
Event
Description
Backup
Syslog
Severity
6–Informational fname=File Name The User Name is the logged
Event Data Additional Information
suser=User Name
outcome=Completion Status
act=IIO Status
in user.
76
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
Message List
54 Saved Jobs Restore
When saved jobs that are backed up are restored to the device from an FTP server, a Saved Jobs
Restore event is recorded.
Event
ID
54 Saved Jobs
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |54 | Saved jobs restore |6|fname=SalesReport suser=
JSMith outcome=Normal act=IIO Not Applicable
Event
Description
Restore
Syslog
Severity
6–Informational fname=File Name The User Name is the logged
Event Data Additional Information
suser=User Name
outcome=Completion Status
act=IIO Status
in user.
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
77

Message List
57 Session Timer Logout
When a user is logged out of the local user interface or the Embedded Web Server because the
session times out, a Session Timer Logout event is recorded.
Event
ID
57 Session
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |57 | Session timer logout |6|dvchost=SalesNEteam
deviceExternalId=GN123456 msg=Web suser=JSmith src=198.51.100.0
Event
Description
Timer
Logout
Syslog
Severity
6–Informational dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
msg=Interface
suser=User Name
src=Session IP Address
78
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
58 Session Timeout Interval Change
When a user login session timeout value is changed, a Session Timeout Interval Change event is
recorded.
Event
ID
58 Session
Event
Description
Timeout
Interval
Change
Syslog
Severity
5–Notice dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
msg=Interface
suser=User Name
src=Session IP Address
outcome=Completion Status
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |58 | Session timeout interval change |5|dvchost=
SalesNEteam deviceExternalId=GN123456 msg=Web suser=JSmith src=
198.51.100.0 outcome=Success
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
79

Message List
59 User Permissions
When user permissions are configured, a User Permissions event is recorded.
Event
ID
59 User
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |59 | User permissions |5|dvchost=SalesNEteam
deviceExternalId=GN123456 msg=Web suser=JSmith src=198.51.100.0 outcome=
Configured
Event
Description
Permissions
Syslog
Severity
5–Notice dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
msg=Interface
suser=User Name
src=Session IP Address
outcome=Completion Status
80
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
60 Device Clock NTP Configuration
When an NTP server is enabled, disabled, or configured, a Device Clock NTP Configuration event is
recorded.
Event
ID
60 Device Clock
Event
Description
NTP
Configuration
Syslog
Severity
5–Notice dvchost=Device Name For the outcome to be
Event Data Additional Information
deviceExternalId=Device Serial
Number
act=Action
dst=NTP Server
outcome=Completion Status
successful, confirmation that
the device is communicating
with the NTP server is required.
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |60 | Device clock NTP configuration |5|dvchost=
SalesNEteam deviceExternalId=GN123456 act=Config NTP dst=198.51.100.0
outcome=Success
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
81

Message List
61 Device Administrator Role Permission
When Device Administrator role rights are granted or revoked for a user, a Device Administrator Role
Permission event is recorded.
Event
ID
61 Device
Example Message:
<108> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |61 | Device administrator role permission |4| dvchost=
SalesNEteam deviceExternalId=GN123456 suser=JSmith outcome=Grant
Event
Description
Administrator Role
Permission
Syslog
Severity
4–Warning dvchost=Device Name This event applies to users that
Event Data Additional Information
deviceExternalId=Device Serial
Number
suser=User Name
outcome=Completion Status
are registered on the device
user database only.
82
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
62 Smartcard Configuration
When the device Smart Card Authentication option is enabled, disabled, or configured, a Smartcard
Configuration event is recorded.
Event
ID
62 Smartcard
Event
Description
Configuration
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
msg=Card Type
outcome=Completion Status
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |62 | Smartcard configuration |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 msg=CAC/PIV outcome=Enabled
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
83

Message List
63 IPv6 Configuration
When IPv6 is configured, enabled, or disabled for the device wired or wireless network interfaces, an
IPv6 Configuration event is recorded.
Event
ID
63 IPv6
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |63 | IPv6 configuration |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Enabled Wireless
Event
Description
Configuration
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
84
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
64 802.1x Configuration
When 802.1x is configured, enabled, or disabled for the device wired network interfaces, an 802.1x
Configuration event is recorded.
Event
ID
64 802.1x
Event
Description
Configuration
Syslog
Severity
5–Notice suser=User Name This event applies to wired
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
network interfaces only. Any
wireless 802.1x changes are
covered in event 99.
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |64 | 802.1x Configuration |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Enabled
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
85

Message List
65 Abnormal System Termination
When the device restarts to solve a problem, an Abnormal System Termination event is recorded.
Event
ID
65 Abnormal
Example Message:
<104> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |65 | Abnormal system termination |0|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456
Event
Description
System
Termination
Syslog
Severity
0–Emergency dvchost=Device Name
Event Data Additional Information
deviceExternalId=Device Serial
Number
86
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
66 Local Authentication Enablement
When the Login Method for the local user interface or the Embedded Web Server is changed to or
from Validate on the Device, a Local Authentication Enablement event is recorded.
Event
ID
66 Local
Event
Description
Authentication
Enablement
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |66 | Local authentication enablement |5|suser=Admin
dvchost=SalesNEteam deviceExternalId=GN123456 outcome=Enabled
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
87

Message List
67 Web User Interface Login Method
When the Login Method for the Embedded Web Server is changed, a Web User Interface Login
Method event is recorded.
Event
ID
67 Web User
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |67 | Web user interface login method |5|suser=Admin
dvchost=SalesNEteam deviceExternalId=GN123456 msg=Network
Event
Description
Interface
Login
Method
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
msg=Authentication Method
Enabled
88
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
Message List
68 FIPS Mode Configuration
When any change is made to Federal Information Processing Standard (FIPS) mode, a FIPS Mode
Configuration event is recorded.
Event
ID
68 FIPS Mode
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |68 | FIPS mode configuration |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Enabled
Event
Description
Configuration
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
89

Message List
69 Xerox Secure Access Login
When a user logs in to the device using the Xerox Secure Access Unified ID System®, a Xerox Secure
Access Login event is recorded.
Event
ID
69 Xerox Secure
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |69 | Xerox secure access login |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Success
Event
Description
Access Login
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
90
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
70 Print from USB Enablement
When the Print From USB feature is enabled or disabled for the local user interface (LUI), a Print from
USB Enablement event is recorded.
Event
ID
70 Print from
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |70 | Print from USB enablement |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Enabled
Event
Description
USB
Enablement
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
91

Message List
71 USB Port Enablement
When a USB port on the device is enabled or disabled, a USB Port Enablement event is recorded.
Event
ID
71 USB Port
Example Message:
<108> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |71 | USB port enablement |4|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 msg=Front aux outcome=Enabled
Event
Description
Enablement
Syslog
Severity
4–Warning suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
msg=USB Port ID
outcome=Completion Status
92
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
72 Scan to USB Enablement
When the Scan to USB feature is enabled or disabled for the local user interface (LUI), a Scan to USB
Enablement event is recorded.
Event
ID
72 Scan to USB
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |72 | Scan to USB enablement |5|suser=Admin dvchost=
SalesNEteam deviceExternalId=GN123456 outcome=Enabled
Event
Description
Enablement
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
®
Xerox
Security Information and Event Management Reference Guide
AltaLink®Series
93

Message List
73 System Log Download
When a user or Xerox service representative downloads support logs from the device using the local
user interface or the Embedded Web Server, a System Log Download event is recorded.
Event
ID
73 System Log
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |73 | System log download |6|suser=Admin dvchost=
SalesNEteam fname=UsageLog.csv downloaded msg=USB device outcome=Success
Event
Description
Download
Syslog
Severity
6–Informational suser=User Name
Event Data Additional Information
dvchost=Device Name
fname=File names
downloaded
msg=Destination
outcome=Completion Status
94
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
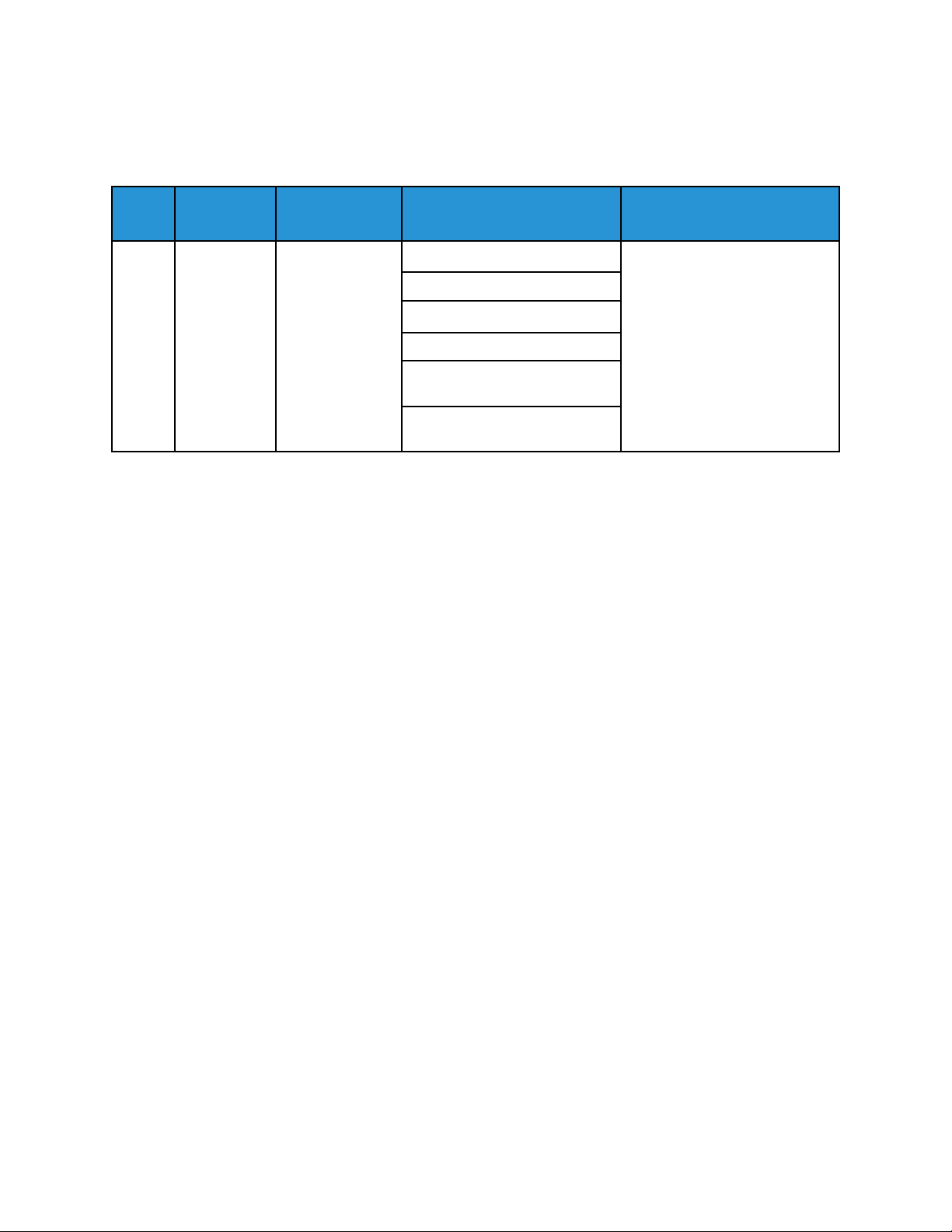
74 Scan to USB Job
On completion of a Scan to USB job, a Scan to USB Job event is recorded.
Message List
Event
ID
74 Scan to USB
Event
Description
Job
Syslog
Severity
6–Informational xrxjob1=Job Name
Event Data Additional Information
suser=User Name
outcome=Completion Status
act=IIO Status
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |74 | Scan to USB job |6|xrxjob1=SalesReport suser=JSmith
outcome=Success act=IIO Not Applicable xrxaccUID1=JSmith xrxaccAID1=Sales
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
95

Message List
75 Remote Control Panel Configuration
The Remote Control Panel allows you to access the control panel of the printer from a Web browser.
When the Remote Control Panel is enabled, disabled, or configured, a Remote Control Panel
Configuration event is recorded.
Event
ID
75 Remote
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |75 | Remote control panel configuration |5|suser=Admin
dvchost=SalesNEteam deviceExternalId=GN123456 outcome=Enabled
Event
Description
Control
Panel
Configuration
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
96
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
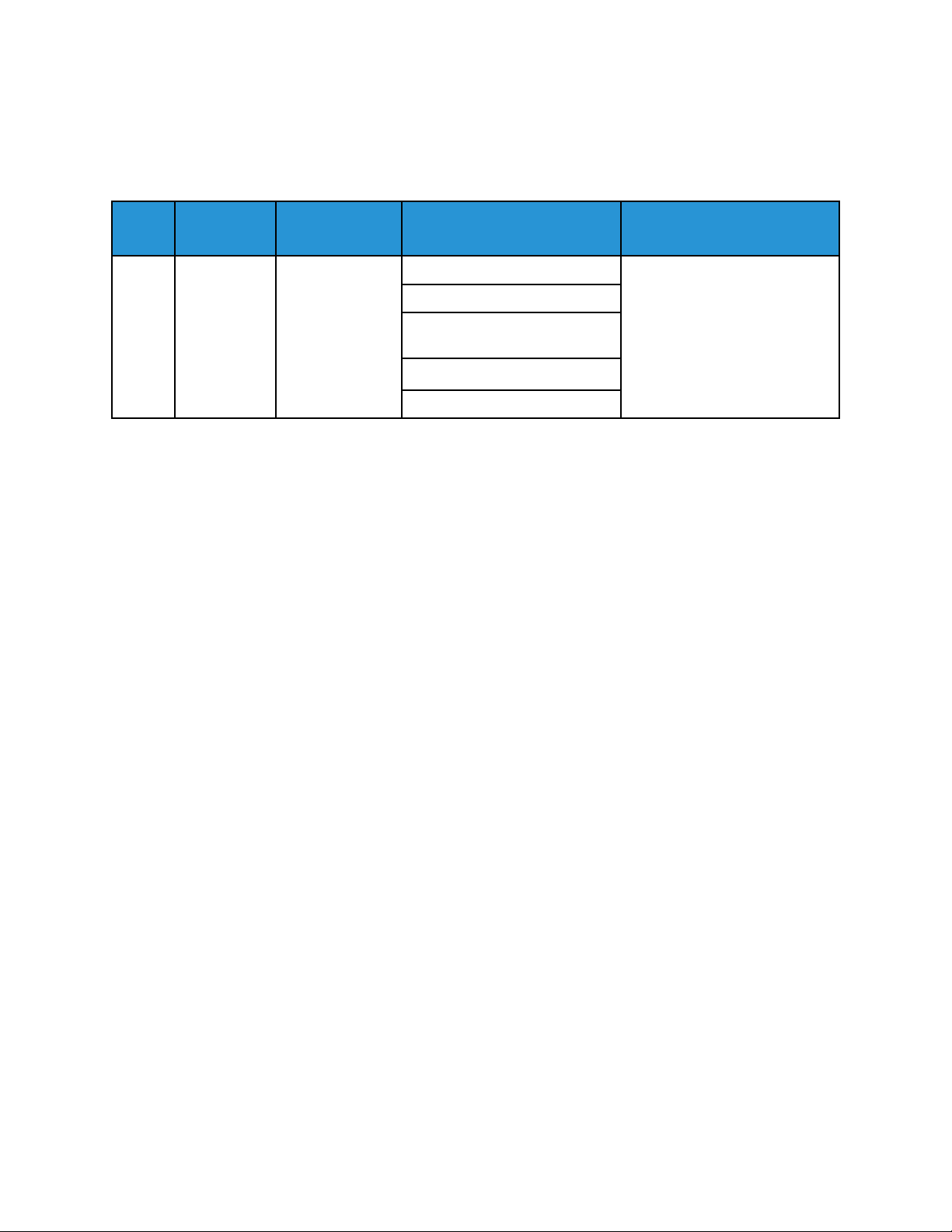
Message List
76 Remote Control Panel Session
When a Remote Control Panel session starts or ends, a Remote Control Panel Session event is
recorded.
Event
ID
76 Remote
Event
Description
Control
Panel
Session
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
src=Remote Client IP Address
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |76 | Remote control panel session |5|suser=JSmith
dvchost=SalesNEteam deviceExternalId=GN123456 outcome=Enabled src=
198.51.100.0
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
97

Message List
77 Remote Scan Feature Enablement
Remote Scanning enables users to scan images to a TWAIN-compliant application using the TWAIN
driver. When Remote Scanning is enabled or disabled, a Remote Scan Feature Enablement event is
recorded.
Event
ID
77 Remote Scan
Example Message:
<109> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |77 | Remote Scan feature enablement |5|suser=Admin
dvchost=SalesNEteam deviceExternalId=GN123456 outcome=Enabled
Event
Description
Feature
Enablement
Syslog
Severity
5–Notice suser=User Name
Event Data Additional Information
dvchost=Device Name
deviceExternalId=Device Serial
Number
outcome=Completion Status
98
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide

Message List
78 Remote Scan Job Submitted
When a remote scan job is submitted to the device, a Remote Scan Job Submitted event is recorded.
Event
ID
78 Remote Scan
Event
Description
Job
Submitted
Syslog
Severity
6–Informational suser=User Name
Event Data Additional Information
src=IP Address of submitting
client
dvchost=Device Name
deviceExternalId=Device Serial
Number
xrxjob1=Job Name
outcome=Completion Status
• This event is triggered on
submission of the job.
• The device can reject the
job.
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |78 | Remote scan job submitted |6|suser=JSmith src=
198.51.100.0 dvchost=SalesNEteam deviceExternalId=GN123456 xrxjob1=
SalesReport outcome=Accept request
®
Xerox
AltaLink®Series
Security Information and Event Management Reference Guide
99

Message List
79 Remote Scan Job Completed
On completion of a remote scan job, a Remote Scan Job Completed event is recorded.
Event
ID
79 Remote Scan
Event
Description
Job
Completed
Syslog
Severity
6–Informational xrxjob1=Job Name
Event Data Additional Information
suser=User Name
xrxaccUID1=Accounting User
ID-Name
xrxaccAID1=Accounting
Account ID-Name
outcome=Completion Status
act=IIO Status
msg=Destination
Example Message:
<110> 2020-04-12T19:20:50-05:00 SalesNEteam CEF:0|Xerox|Altalink C8135|
111.009.009.21000 |79 | Remote scan job completed |6|xrxjob1=SalesReport
suser=JSmith xrxaccUID1=JSmith xrxaccAID1=Sales act=IIO Not Applicable
Status msg=Web Service
100
Xerox®AltaLink®Series
Security Information and Event Management Reference Guide
 Loading...
Loading...