Nortel Networks 8600 User Manual

Ethernet Routing Switch
8600
Engineering
>Simple Network Management Protocol (SNMP) for ERS 8600 Technical Configuration Guide
Enterprise Business Solutions
Document Date: April 4, 2007
Document Number: NN48500-564
Document Version: 2.1

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
Nortel is a recognized leader in delivering communications capabilities that enhance the human experience, ignite and power global commerce, and secure and protect the world’s most critical information. Serving both service provider and enterprise customers, Nortel delivers innovative technology solutions encompassing end-to-end broadband, Voice over IP, multimedia services and applications, and wireless broadband designed to help people solve the world’s greatest challenges. Nortel does business in more than 150 countries. For more information, visit Nortel on the Web at www.nortel.com.
Copyright © 2008 Nortel Networks. All Rights Reserved.
While the information in this document is believed to be accurate and reliable, except as otherwise expressly agreed to in writing NORTEL PROVIDES THIS DOCUMENT "AS IS" WITHOUT WARRANTY OR CONDITION OF ANY KIND, EITHER EXPRESS OR IMPLIED. The information and/or products described in this document are subject to change without notice. Nortel Networks, the Nortel Networks logo and the Globemark are trademarks of Nortel Networks.
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
1 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
Abstract
This Technical Configuration Guide (TCG) provides an overview on how to configure SNMP (Simple Network Management Protocol) on the Nortel Ethernet Routing Switch (ERS) 8600.
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
2 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
||
Table of Contents |
|
|
||
1. |
SNMPV3 OVERVIEW.............................................................................................................. |
|
5 |
|
2. |
SNMP UPGRADE CONSIDERATIONS.................................................................................. |
|
6 |
|
|
2.1 |
HIDDEN FILE DETAILS......................................................................................................... |
|
6 |
3. |
BLOCKING SNMP................................................................................................................... |
|
7 |
|
|
3.1 |
BLOCKING SNMPV1/2 ONLY .............................................................................................. |
|
7 |
|
3.2 |
BLOCKING SNMP VIA AN ACCESS POLICY – PRIOR TO SOFTWARE RELEASE 3.7.9 OR 4.1..... 7 |
||
|
3.3 |
SNMP GROUP ACCESS POLICY – RELEASE 3.7.9, 4.1 OR HIGHER....................................... |
9 |
|
|
3.4 |
NEW DEFAULT COMMUNITY STRINGS IN HIGH SECURE (HSECURE) MODE ........................... |
20 |
|
4. |
SNMP SETTINGS.................................................................................................................. |
|
21 |
|
5. |
SNMP WITH RADIUS AUTHENTICATION AND ACCOUNTING ........................................ |
23 |
||
6. |
CONFIGURING SNMPV3...................................................................................................... |
|
24 |
|
|
6.1 |
LOADING THE DES OR AES ENCRYPTION MODULE............................................................ |
24 |
|
|
6.2 |
ADDING A NEW SNMPV3 USER TO USM TABLE ................................................................ |
24 |
|
|
6.3 |
ASSIGN USM USER TO USM GROUP ................................................................................ |
|
25 |
|
6.4 |
ASSIGNING THE USM GROUP ACCESS LEVEL.................................................................... |
27 |
|
|
6.5 |
ASSIGNING THE MIB VIEW TO THE USM GROUP ................................................................ |
28 |
|
|
6.6 |
CREATING A MIB VIEW ..................................................................................................... |
|
29 |
7. |
CONFIGURATION EXAMPLE: CHANGING SNMP COMMUNITIES .................................. |
30 |
||
|
7.1 |
CONFIGURATION EXAMPLE: SNMP COMMUNITIES WITH RELEASE 3.5................................. |
30 |
|
7.2CONFIGURATION EXAMPLE: CHANGING THE DEFAULT SNMP COMMUNITY NAME WITH
RELEASE 3.7 OR 4.1..................................................................................................................... |
31 |
7.3CONFIGURATION EXAMPLE: ADDING A NEW SNMP COMMUNITY TO AN EXISTING SNMP
GROUP MEMBER .......................................................................................................................... |
31 |
|
7.4 |
TESTING SNMP USING DEVICE MANAGER ........................................................................ |
34 |
7.5 |
CONFIGURATION EXAMPLE: CHANGING THE MIB VIEW FOR AN SNMPV1/2 COMMUNITY...... |
34 |
8. CONFIGURATION EXAMPLE USING SNMPV3.................................................................. |
36 |
|
8.1 |
TESTING SNMPV3 USING DEVICE MANAGER .................................................................... |
37 |
9. SOFTWARE BASELINE ....................................................................................................... |
39 |
|
10. |
REFERENCE DOCUMENTATION.................................................................................... |
40 |
11. APPENDIX A: CONFIGURATION FILES ......................................................................... |
41 |
|
11.1 |
FROM CONFIGURATION EXAMPLE 7.5................................................................................ |
41 |
11.2 |
FROM CONFIGURATION EXAMPLE 8................................................................................... |
41 |
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
3 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
List of Figures |
|
|
Figure 1: SNMPv3 USM................................................................................................................... |
|
5 |
Figure 2: MIB Structure.................................................................................................................. |
|
29 |
List of Tables |
|
|
Table 1: New Default Password Settings ...................................................................................... |
|
20 |
Table 2: New Default Community Settings .................................................................................... |
|
20 |
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
4 |
SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
1. SNMPv3 Overview
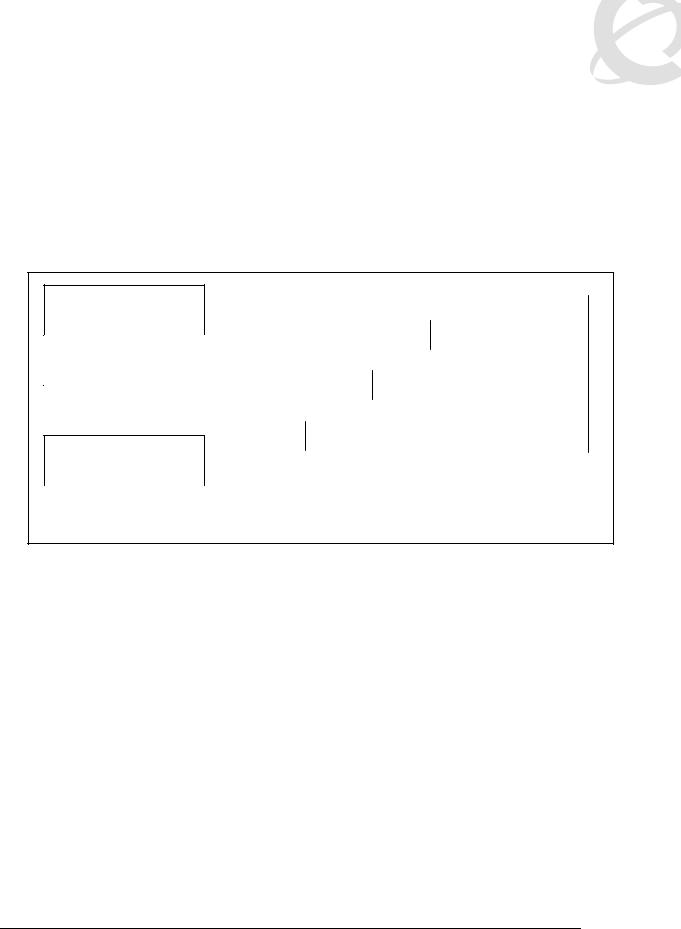
SNMPv3 is the third version of the Internet-Standard Management Framework and is derived from and builds upon both the original Internet-Standard Management Framework (SNMPv1) and the second Internet-Standard Management Framework (SNMPv2). SNMPv3 is not a stand-alone replacement for SNMPv1 and/or SNMv2. It defines security capabilities to be used in conjunction with SNMPv2 (preferred) or SNMPv1. As shown in the Figure 1 below, SNMPv3 specifies a User Security Model (USM) that uses a payload of either a SNMPv1 or a SNMPv2 protocol data unit (PDU).
PDU Processing (SNMPv1 or SNMPv2)
Message Processing
(SNMPv3 USM)
UDP
|
|
SNMP PDU |
|
|
|
|
|
|
|
V3-MH |
SNMP PDU |
|
|
|
|
|
|
UDP-H |
V3-MH |
SNMP PDU |
|
|
|
|
|
|
|
|
|
|
|
|
|
IP |
|
IP-H |
UDP-H |
|
V3-MH |
|
SNMP PDU |
|
|
|
|
|
|
|
|
|
|
|
|
|
IP-H |
= IP header |
|
||
PDU |
= Protocol Data Unit |
|
|
|||||
USM |
= User Based Security |
|
UDP-H = UDP header |
|
||||
|
|
|
|
V3-MH = SNMPv3 message header |
||||
Figure 1: SNMPv3 USM
Authentication within the User-based Security Model (USM) allows the recipient of the message to verify whom the message is from and whether the message has been altered. As per RFC 2574, if authentication is used, the entire message is checked for the integrity. Authentication uses a secret key to produce a fingerprint of the message, which is included in the message. The receiving entity uses the same secret key to validate the fingerprint. Currently there are 2 authentication protocols defined, HMAC-MD5 and HMAC-SHA-96 for use with USM.
While the USM provides the user-name/password authentication and privacy services, control access to management information (MIB) must be defined. The View-based Access Control Module (VACM) is used to define a set of services that an application can use for checking access rights (read, write, notify) to a particular object. VACM uses the ASN.1 notation (3.6.1.4) or the name of the SNMP MIB branch, i.e. Org.Dod.Internet.Private. The administrator can define a MIB group view for a user to allow access to an appropriate portion of the MIB matched to an approved security level. The three security levels are:
•NoAuthNoPriv-Communication without authentication and privacy
•AuthNoPriv-Communication with authentication (MD5 or SHA) and without privacy
•AuthPriv-Communication with authentication (MD5 or SHA) and privacy (DES or AES)
NOTE: Please refer to the Ethernet Routing Switch 8600 4.1 release notes (Part number 317177- D Rev 01) regarding important information regarding SNMPv3. Special considerations need to be considered regarding hidden and encrypted that contains community table information.
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
5 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
2. SNMP Upgrade Considerations
Please note the following when upgrading software on the ERS8600.
Starting in software release 3.7 and continued to software release 4.1.x, the CLI command save config creates a hidden and encrypted file that contains the SNMP community table information. For security purposes, the save config command also removes reference to the existing SNMP community strings in the newly created configuration file. Please note that if you only have one CPU, and if you swap the CPU, you must backup all hidden files or else all the password and SNMP references will be lost. If you do not backup the hidden files, you must reconfigure your trap receivers and community strings every time you change the CPU.
The commands to change the SNMP Community strings and trap receivers in software release 3.3 have changed in software releases 3.5, 3.7, 4.0, and 4.1.x. However, even though software releases 3.5, 3.7, 4.0, and 4.1.x use the same commands, in software release 3.7 and 4.1.x only, the SNMP community strings and trap receivers are stored in a hidden and encrypted file and are not found in the configuration file. This is similar with software releases 3.5 and 4.0; however the files are stored in a hidden non-encrypted file. Upgrades from 3.7 to 4.1.x, all files are translated as-is. Please see section 3.3.3 for more details.
2.1 Hidden File Details
Backup the following configuration files to either via FTP, a TFTP server or a PCMCIA card:
•shadov.txt
•snmp_usm.txt
•snmp_comm.txt
•password.txt
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
6 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
3. Blocking SNMP
By default, SNMP access is enabled. You can disable SNMP; this includes SNMPv1/v2 and SNMPv3, access to the ERS 8600 by using the following commands:
•ERS-8610:5# config bootconfig flags block-snmp true
•ERS-8610:5#save boot
•ERS-8610:5#boot -y
To re-enable SNMP access, type in the following command:
•ERS-8610:5# config bootconfig flags block-snmp false
3.1Blocking SNMPv1/2 Only
If you wish to allow only SNMPv3 access, you can disable SNMPv1/2 by configuring the SNMPv3 MIB view. Portions of the MIB can be configured to either include or exclude access at an MIB OID level. This is explained in section 5.5. For SNMPv3, this can be done on a per-user basic. For SNMPv1/v2, it can be done on a global/community basis. By default, SNMPv1/v2 is permitted access to all MIB OIDs under 1.3 in the MIB OID tree with the exception with sections related to the SNMP USM, VACM, and Community MIBs. This cannot be altered, but, if an additional exclusion statement is added, the entire usable MIB can be disabled through SNMPv1/v2. Specifically, if the entire MIB tree under 1.3.6 (iso org dod) is excluded, none of the switches public or private MIBs will be accessible.
To disable SNMPv1/v2 only, enter the following command:
•PP8600-B:6# config snmp-v3 mib-view create v1v2only 1.3.6 type exclude
At this point, SNMPv1/v2 will be disabled and only SNMPv3 will be allowed.
3.2Blocking SNMP via an Access Policy – Prior to Software Release 3.7.9 or 4.1
You can also enable or disable SNMP via an Access Policy. Overall, the Access Policy feature on the ERS 8600 supports the following feature:
•Access level: Specifies the access level of the trusted as hostreadOnly (ro), readWrite (rw), or readWriteAll (rwa)
•Mode: Indicates whether a packet having a source IP address that matches this entry should be permitted to enter the device or denied access.
•Service: Indicates the protocol to which this entry should be applied. Choices are telnet, snmp, tftp, ftp, http, rlogin, and/or ssh.
•Precedence: Indicates the precedence of the policy. The lower the number, the higher the precedence (1 to 128).
•Network Address and Network Mask: Indicates the source network IP address and mask. An address of 0.0.0.0 specifies any address on the network.
•Host: Indicates the trusted IP address of the host performing rlogin or rsh into the device. Applies only to rlogin and rsh.
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
7 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
•Access-strict: Sets the access level strictly.
To add an access policy, you must first enable the access policy feature globally by entering the following command:
•ERS-8606:5# config sys access-policy enable <true/false>
After the access policy feature has been enabled globally, to add a new access policy, enter the following command:
a)Add a new policy
•ERS-8606:5# config sys access-policy policy <1..65535>
b)After entering the above command, enter the appropriate parameters:
•ERS-8606:5# config sys access-policy policy <1..65535> ?
Sub-Context: service Current Context:
accesslevel <ro|rw|rwa> access-strict <true|false> create
delete disable enable
host <ipaddr> info
mode <allow|deny> name <name>
network <addr/mask> precedence <precedence> username <string>
c)Add the services to the newly created access policy:
•ERS-8606:5# config sys access-policy policy <1..65535> service ?
Sub-Context: Current Context:
ftp <enable|disable> http <enable|disable> info
rlogin <enable|disable> snmp <enable|disable> ssh <enable|disable> telnet <enable|disable> tftp <enable|disable>
Please refer to publication number 314997-C titled Important Security Information for the 8000 Series Switch for more details on Access Policies.
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
8 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
3.2.1 Configuration Example: Blocking SNMP via an Access Policy
In this example, we will create an access policy to not allow SNMP for any user coming from network 172.30.x.y/16.
a)Enable access policy globally:
•ERS-8606:5# config sys access-policy enable true
b)Add a new policy, in this example, since it is the first policy, we will simply create policy 2 and name it policy2:
•ERS-8606:5# config sys access-policy policy 2 create
•ERS-8606:5# config sys access-policy policy 2 name policy2
c)Add network 172.30.0.0/16 to policy 2:
•ERS-8606:5# config sys access-policy policy 2 network 172.30.0.0/16
d)Add read/write/all access level to policy 2:
•ERS-8606:5# config sys access-policy policy 2 accesslevel rwa
e)Disable SNMP service for policy 2:
•ERS-8606:5# config sys access-policy policy 2 service snmp disable
After the policy has been created, enter the following command to view policy 2:
• ERS-8606:5# show sys access-policy info policy2
AccessPolicyEnable: on
Id: 2
Name: policy2
PolicyEnable: true
Mode: allow
Service: http|telnet|ssh
Precedence: 128
NetAddr: 172.30.0.0
NetMask: 255.255.0.0
TrustedHostAddr: 0.0.0.0
TrustedHostUserName: none
AccessLevel: readWriteAll
AccessStrict: false
Usage: 337
3.3SNMP Group Access Policy – Release 3.7.9, 4.1 or Higher
In release 3.7.9 or 4.1, a new policy enhancement was added that allows the administrator to specify a group or groups for SNMPv3 access. With SNMPv3, the community name is not mapped to an access level, but determined only through VACM. This allows the administrator to create separate policies for SNMP users based on USM or community and associate them to groups.
The following items where added high-lighted in red below.
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
9 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
ERS-8610:5# config sys access-policy policy 1 ?
Sub-Context: service
Current Context:
accesslevel <level> access-strict <true|false> create
delete disable enable
host <ipaddr> info
mode <mode> name <name>
network <addr/mask> precedence <precedence>
snmp-group-add <group name> <model> snmp-group-del <group name> <model> snmp-group-info
username <string>
ERS-8610:5# config sys access-policy policy 1 service ?
Sub-Context:
Current Context:
ftp <enable|disable> http <enable|disable> info
rlogin <enable|disable> snmpv3 <enable|disable> ssh <enable|disable> telnet <enable|disable> tftp <enable|disable>
3.3.1 SNMPv3 Group Access Policy: Configuration Example
For this example, we wish to create a policy for read-write-all access and only allow telnet and SNMPv3 access only for SNMPv3 usm group named group_example. Please see Section 5 in regards to how to configure SNMPv3.
a)Enable access policies globally
•ERS-8606:5# config sys access-policy enable true
b)Assuming no access policies have been created, we can start with policy 2 and name the policy policy2.
•ERS-8606:5# config sys access-policy policy 2 create
•ERS-8606:5# config sys access-policy policy 2 name policy2
c)Add read/write/all access level to policy 2:
•ERS-8606:5# config sys access-policy policy 2 accesslevel rwa
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
10 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
d)Add the usm group ‘group_example’ to policy 2:
•ERS-8610:5# config sys access-policy policy 2 snmp-group-add group_example usm
e)Enable access strict enable
•ERS-8610:5# config sys access-policy policy 2 access-strict true
f)Enable telnet and SNMPv3 service:
•ERS-8610:5# config sys access-policy policy 2 service telnet enable
•ERS-8610:5# config sys access-policy policy 2 service snmpv3 enable
g)Enable policy 2:
•ERS-8610:5# config sys access-policy policy 2 enable
h)After the policy has been created, enter the following command to view policy 2:
•ERS-8606:5# show sys access-policy info policy2
AccessPolicyEnable: on
Id: 2
Name: policy2
PolicyEnable: true
Mode: allow
Service: telnet|snmpv3
Precedence: 10
NetAddr: 0.0.0.0
NetMask: 0.0.0.0
TrustedHostAddr: 0.0.0.0
TrustedHostUserName: none
AccessLevel: readWriteAll
AccessStrict: true
Usage: 3777
• ERS-8610:5# show sys access-policy snmp-group-info
snmpv3-groups : |
|
|
|
Policy 1 |
snmpv3-groups |
: |
|
|
Group |
Name |
Snmp-Model |
Policy 2 |
snmpv3-groups |
: |
|
|
Group |
Name |
Snmp-Model |
|
group_example |
|
usm |
3.3.2 SNMPv1/2 Group Access Policy: Configuration Example
As release 3.7 and 4.1 is based on the SNMPv3, you must add the SNMPv3 group name and model for both SNMPv1 and SNMPv2 when setting up an access policy. To view the SNMPv3 group name and model, please use the following as shown below. Note that the items highlighted in red need to be added when setting up the access policy.
•ERS8610-B:5# show snmp-v3 group-access
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
11 |

SNMP for ERS 8600 TCG |
|
v2.1 |
|
NN48500-564 |
|
========================================================================= |
|||||
|
|
VACM Group Access Configuration |
|
||
========================================================================= |
|||||
Group |
Prefix Model |
Level |
ReadV |
WriteV |
NotifyV |
------------------------------------------------------------------------- |
|||||
initial |
usm |
noAuthNoPriv root |
root |
root |
|
initial |
usm |
authPriv |
root |
root |
root |
readgrp |
snmpv1 |
noAuthNoPriv |
v1v2only |
|
org |
readgrp |
snmpv2c |
noAuthNoPriv |
v1v2only |
|
org |
v1v2grp |
snmpv1 |
noAuthNoPriv |
v1v2only |
v1v2only |
v1v2only |
v1v2grp |
snmpv2c |
noAuthNoPriv |
v1v2only |
v1v2only |
v1v2only |
esegroup |
usm |
authPriv |
org |
org |
|
sBladeGrp |
snmpv1 |
noAuthNoPriv |
sBladeView |
sBladeView sBladeView |
|
sBladeGrp |
snmpv2c |
noAuthNoPriv |
sBladeView |
sBladeView sBladeView |
|
9 out of 9 Total entries displayed
-------------------------------------------------------------------------
The following example will add a new access policy that will allow SNMPv1/2 and telnet.
a)Enable access policies globally
•ERS-8606:5# config sys access-policy enable true
b)Assuming no access policies have been created, we can start with policy 2 and name the policy policy2.
•ERS-8606:5# config sys access-policy policy 2 create
•ERS-8606:5# config sys access-policy policy 2 name policy2
c)Add read/write/all access level to policy 2:
•ERS-8606:5# config sys access-policy policy 2 accesslevel rwa
d)Add the SNMPv1/2 group name and models to policy 2:
•ERS-8610:5# config sys access-policy policy snmp-group-add readgrp snmpv1
•ERS-8610:5# config sys access-policy policy 2 snmp-group-add readgrp snmpv2c
•ERS-8610:5# config sys access-policy policy snmp-group-add v1v2grp snmpv1
•ERS-8610:5# config sys access-policy policy snmp-group-add v1v2grp snmpv2c
If the ERS 8600 also contains a Web Switching Module (WSM) then access to the SNMPv1/2 Group “sBladeGrp” must also be configured. Enter the following commands to enable SNMP management of the WSM:
•ERS-8610:5# config sys access-policy policy snmp-group-add sBladeGrp snmpv1
•ERS-8610:5# config sys access-policy policy snmp-group-add sBladeGrp snmpv2c
e)Enable telnet and SNMPv3 service:
•ERS-8610:5# config sys access-policy policy 2 service telnet enable
•ERS-8610:5# config sys access-policy policy 2 service snmpv3 enable
f)Enable policy 2:
•ERS-8610:5# config sys access-policy policy 2 enable
g)After the policy has been created, enter the following command to view policy 2:
•ERS-8606:5# show sys access-policy info policy2
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
12 |

SNMP for ERS 8600 TCG |
v2.1 |
NN48500-564 |
AccessPolicyEnable: on
Id: 2
Name: policy2
PolicyEnable: true
Mode: allow
Service: telnet|snmpv3
Precedence: 10
NetAddrType: ipv4
NetAddr: 0.0.0.0
NetMask: 0.0.0.0
TrustedHostAddr: 47.133.58.69
TrustedHostUserName: none
AccessLevel: readWriteAll
AccessStrict: false
Usage: 385
•ERS-8610:5# show sys access-policy snmp-group-info
|
snmpv3-groups : |
|
Policy 1 |
snmpv3-groups: |
|
|
Group Name |
Snmp-Model |
Policy 2 |
snmpv3-groups: |
|
|
Group Name |
Snmp-Model |
|
readgrp |
snmpv1 |
|
readgrp |
snmpv2c |
|
v1v2grp |
snmpv1 |
|
v1v2grp |
snmpv2c |
3.3.3 SNMP Community Strings
For security reasons, the SNMP agent validates each request from an SNMP manager before responding to the request. This is accomplished by verifying that the manager belongs to a valid SNMP community. An SNMP community is a logical relationship between an SNMP agent and one or more SNMP managers (the manager software implements the protocols used to exchange data with SNMP agents). You define communities locally at the agent.
The agent establishes one community for each combination of authentication and access control characteristics that you choose. You assign each community a unique name (community string), and all members of a community have the same access privileges, either read-only or read-write:
•Read-only: members can view configuration and performance information.
•Read-write: members can view configuration and performance information, and also change the configuration.
By defining a community, an agent limits access to its MIB to a selected set of management stations. By using more than one community, the agent can provide different levels of MIB access to different management stations.
SNMP community strings are required for access to the switch using Device Manager or other SNMP-based management software. You set the SNMP community strings using the CLI. If you have read/write/all access authority, you can modify the SNMP community strings for access to the device through Device Manager.
In the ERS 8000 Series switch software release 3.7, the CLI command save config creates a hidden and encrypted file that contains the SNMP community table information. The SNMP
Nortel Confidential Information |
Copyright © 2008 Nortel Networks. All Rights Reserved. |
|
|
External Distribution |
13 |
 Loading...
Loading...