Page 1

HP StoreOnce
VSA Backup system
Abstract
This is the user guide for HP StoreOnce VSA Backup system and is intended for users who install, operate and maintain the
HP StoreOnce Backup system.
Always check www.hp.com/go/storage/docs for the most current documentation, including localized versions (in PDF format)
for your product. (Search on Product Name and select the Product Manuals option.)
Refer to the Quick Specs on http://www.hp.com/go/storeonce for supported features for your model and the current status.
HP Part Number: TC458-96025
Published: July 2014
Edition: 2
Page 2

© Copyright 2011–2014 Hewlett-Packard Development Company, L.P.
Confidential computer software. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial
Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under
vendor's standard commercial license.
The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express
warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall
not be liable for technical or editorial errors or omissions contained herein.
Warranty
WARRANTY STATEMENT: To obtain a copy of the warranty for this product, see the warranty information website:
http://www.hp.com/go/storagewarranty
Acknowledgments
Linear Tape-Open, LTO, LTO Logo, Ultrium and Ultrium Logo are trademarks of Quantum Corp, HP and IBM in the US, other countries or both.
Microsoft, Windows, Windows NT, and Windows XP are U.S. registered trademarks of Microsoft Corporation. Intel and Itanium are trademarks
or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries.
The HP StoreOnce Backup system product firmware includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://
www.openssl.org/).
Revision History
June 2013Revision 1
First edition.
July 2014Revision 2
Second edition, issued with the 3.11.0 version of HP StoreOnce software.
Page 3

Contents
1 Getting started...........................................................................................7
This guide................................................................................................................................7
Overview of The HP StoreOnce Backup system.............................................................................7
User types and user roles...........................................................................................................7
Powering off and on..................................................................................................................8
Deployment of the Virtual Storage Appliance...............................................................................8
Navigating the HP StoreOnce Graphical User Interface (GUI)........................................................9
Navigating the online help......................................................................................................10
The StoreOnce CLI..................................................................................................................12
Licensing...............................................................................................................................12
Security Features....................................................................................................................12
2 StoreOnce functions..................................................................................14
Overview of the HP StoreOnce page.........................................................................................14
System information and status...................................................................................................14
3 VTL (Virtual Tape Libraries) functions...........................................................16
VTL Configuration page...........................................................................................................16
iSCSI Settings tab..............................................................................................................16
Libraries page........................................................................................................................16
Device Details tab..............................................................................................................17
To create a new library (administrators only).....................................................................19
To edit library details (administrators only)........................................................................20
To delete a library (administrators only)............................................................................21
Emulation types for tape devices..........................................................................................21
Interface Information tab.....................................................................................................22
Active Connections tab.......................................................................................................23
Cartridges tab...................................................................................................................23
To create a cartridge (administrators only)........................................................................25
To delete a cartridge (administrators only)........................................................................25
To delete all or a range of cartridges (administrators only)..................................................26
To write protect a cartridge (administrators only)...............................................................26
To edit maximum cartridge size (administrators only)..........................................................27
To move or unload cartridges.........................................................................................27
Make Replication Target libraries visible to the host.....................................................................28
4 NAS functions..........................................................................................30
NAS Configuration page.........................................................................................................30
CIFS Server tab......................................................................................................................30
Configuring user authentication............................................................................................32
Configuring CIFS Server with AD and CIFS Share with AD domain users........................................34
NFS Server tab.......................................................................................................................42
Shares (NAS).........................................................................................................................43
Creating a CIFS share........................................................................................................45
Creating an NFS share and setting permissions.....................................................................47
5 Replication functions.................................................................................50
What is an appliance?............................................................................................................50
How do I identify the IP address of a Service Set?..................................................................51
Status tab..............................................................................................................................52
Partner Appliances (Replication)...............................................................................................52
Target Appliances tab........................................................................................................53
Source Appliances tab.......................................................................................................55
Contents 3
Page 4

Source Appliance Permissions tab........................................................................................56
Local Settings (Replication) tab.................................................................................................57
General settings tab...........................................................................................................58
Bandwidth Limiting tab.......................................................................................................59
Blackout Windows tab........................................................................................................60
Event History (Replication) tab..................................................................................................60
VT Mappings (Replication).......................................................................................................61
Source and target library mappings.....................................................................................62
Running the replication wizard (virtual tape devices)...............................................................64
Recovering a Source Appliance (Virtual Tape devices)............................................................67
NAS Mappings (Replication)....................................................................................................70
Source and target share details............................................................................................71
Running the replication wizard (NAS)...................................................................................72
Recovering a Source Appliance (NAS shares)........................................................................76
Reverse replication using the wizard................................................................................76
Promoting a Target Share over the WAN using NAS.........................................................79
6 HP StoreOnce Catalyst functions.................................................................80
What is HP StoreOnce Catalyst?..............................................................................................80
StoreOnce Catalyst terminology................................................................................................81
StoreOnce Catalyst page.........................................................................................................81
StoreOnce Catalyst Status tab..............................................................................................82
StoreOnce Catalyst Settings tab...........................................................................................83
StoreOnce Catalyst Clients tab............................................................................................84
StoreOnce Catalyst Blackout Windows tab............................................................................85
StoreOnce Catalyst Bandwidth Limiting Windows tab.............................................................86
Catalyst Stores page...............................................................................................................87
Store details tab................................................................................................................88
Permissions tab (administrators only).....................................................................................90
Item summary tab..............................................................................................................90
Data jobs tab....................................................................................................................92
Outbound copy jobs tab.....................................................................................................95
Inbound copy jobs tab........................................................................................................99
System information messages.............................................................................................103
7 Housekeeping function............................................................................105
The Housekeeping page........................................................................................................105
Configuring blackout windows................................................................................................108
Pausing housekeeping...........................................................................................................108
8 StoreOnce reporting...............................................................................110
Activity report.......................................................................................................................110
Reporting page....................................................................................................................111
9 Storage Reporting..................................................................................113
Storage Report.....................................................................................................................113
10 Access and Device Configuration............................................................114
Device Configuration page....................................................................................................114
User Management................................................................................................................114
To add a user (Admin only)...............................................................................................115
To add a group (Admin only)............................................................................................116
To modify a user..............................................................................................................117
To delete a user or group (Admin only)...............................................................................118
Email..................................................................................................................................118
Test email.......................................................................................................................119
Events (Email)..................................................................................................................119
4 Contents
Page 5

To manage email notifications...........................................................................................120
Support Ticket......................................................................................................................120
Data collection................................................................................................................121
Collect Data...............................................................................................................122
Download data collection............................................................................................122
Delete data collection..................................................................................................123
11 Events..................................................................................................124
To delete events from the log..................................................................................................124
12 Basic troubleshooting............................................................................126
Accessing the CLI.................................................................................................................126
Password problems...............................................................................................................126
Pulling a Support Ticket.........................................................................................................126
Licensing problems...............................................................................................................127
Multiple users.......................................................................................................................127
Connecting to the StoreOnce Backup system from the backup application....................................127
Timeout problems with NAS CIFS shares..................................................................................127
NFS State handle error..........................................................................................................128
If backup or replication fails...................................................................................................128
Catalyst troubleshooting........................................................................................................129
Performance.........................................................................................................................129
StoreOnce Backup system configuration problems.....................................................................129
Upgrade licenses..................................................................................................................129
13 Advanced troubleshooting......................................................................131
Software update process.......................................................................................................131
If the HP StoreOnce Backup system runs out of disk space..........................................................131
Reduced performance using Data in Flight Encryption................................................................131
14 SNMP.................................................................................................132
SNMP (Configuration)...........................................................................................................132
HP Systems Insight Manager.............................................................................................132
15 Key Parameters.....................................................................................137
StoreOnce VSA Backup.........................................................................................................137
16 Support and other resources...................................................................138
Contacting HP......................................................................................................................138
Subscription service..........................................................................................................138
Related information...............................................................................................................138
Websites........................................................................................................................138
Typographic conventions.......................................................................................................139
Customer self repair..............................................................................................................139
A Upgrading to StoreOnce software, version 3.11.x........................................141
Previous networking models...................................................................................................141
Network model with StoreOnce software version 3.11.0 and later................................................142
Bonding modes...............................................................................................................142
VLAN subnets with HP StoreOnce Backup................................................................................143
VLAN guidelines..............................................................................................................143
Example network environment...........................................................................................144
Updating to StoreOnce 3.11.0 software....................................................................................144
Worked example .................................................................................................................144
View current configuration.................................................................................................145
Modifying the current configuration....................................................................................146
Best practise...............................................................................................................146
To add a third subnet ......................................................................................................147
To add VLAN subnets.......................................................................................................147
Contents 5
Page 6

To modify the existing 10GbE portset and add a VLAN subnet..........................................147
To create a new portset that is VLAN enabled and add a VLAN subnet..............................148
To add IP addresses to a subnet.........................................................................................148
To add Data in Flight Encryption........................................................................................149
License requirements....................................................................................................149
Configuring the client...................................................................................................149
Configuring the StoreOnce Backup system......................................................................149
Configuring IPsec on the media server...........................................................................150
Encryption with replication...........................................................................................150
B Regulatory information............................................................................151
Belarus Kazakhstan Russia marking.........................................................................................151
Turkey RoHS material content declaration.................................................................................151
Ukraine RoHS material content declaration..............................................................................151
Warranty information............................................................................................................151
Index.......................................................................................................153
6 Contents
Page 7

1 Getting started
The following topics are covered in this chapter:
• This guide (page 7)
• Overview of HP StoreOnce Backup products (page 7)
• User types and user roles (page 7)
• Navigating the StoreOnce Graphical User Interface (GUI) (page 9)
• Navigating the online help (page 10)
• The StoreOnce CLI (page 12)
• Licensing (page 12)
This guide
This guide contains detailed information on using the StoreOnce GUI and includes some Command
Line Interface commands and troubleshooting information.
• Tasks available only in the StoreOnce GUI are described only in this guide.
• Tasks available in both the GUI and CLI are described in this guide. (The CLI command is
described in greater detail in the HP StoreOnce Backup system CLI Reference Guide.)
• Tasks only available in the CLI are described fully in the HP StoreOnce Backup system CLI
Reference Guide. Those tasks may not be described in this guide.
Overview of The HP StoreOnce Backup system
The HP StoreOnce VSA extends the StoreOnce portfolio with the agility and flexibility of StoreOnce
as a virtual appliance. Install into an existing vSphere (v5.x) environment without the need for
dedicated hardware. Once installed and powered on, StoreOnce VSA is used by backup and
recovery applications as a backup target in the same way as physical StoreOnce appliances.
StoreOnce VSA can be deployed using either SEM or via a vSphere client specific hardware. The
StoreOnce VSA is available to purchase by license, which includes HP StoreOnce Catalyst and
Replication support.
The StoreOnce VSA model, TC458A and D4T77A:
• Description: A virtual machine with ten 1TB disks
• Ports: 2 x 1GBE ports
• Storage expansion: Up to ten virtual disks of 1TB
• Interfaces supported: iSCSI only
User types and user roles
User roles
Two roles define the permissions associated with a user; admin and user. Two default user accounts,
one for each role, are created automatically when the system is installed:
• Administrator: Authorized users can create and edit management and StoreOnce functions
via the GUI and CLI. The default login and password are Admin and admin. The permissions
role of the Administrator is admin. You cannot delete this account, but you can and should
modify its password. Note that once the Admin account password has been changed, its
password cannot be changed back to admin as this password is not sufficiently complex. The
This guide 7
Page 8
only way to revert that password back to admin is via the HPresetpassword account which is
only available on the local console of the device.
• Operator: This account limits access to the GUI and CLI to monitoring and viewing. The default
login and password are Operator and operator. The permissions role of the Operator is user.
User types
After installation, an Administrator can configure additional user accounts and assign permissions
roles (admin or user) and passwords to these users. See the HP StoreOnce Backup system user
guide.
There are three types of user accounts:
• Local User (with an administrator or user permissions role): Local users log in locally.
• External User (with an administrator or user permissions role): User logs in as a domain user.
An external user is a Microsoft Active Directory user.
• External Group (with an administrator or user permissions role): An external user is a Microsoft
Active Directory group. Members of the group log in as domain users. If after creating a group
you then set up a member of that group as an individual user (external user) and give them
an administrator role, that user will be an administrator, even if the group role is set to user.
This is because role permissions set through Add User take precedence over role permissions
set through Add Group.
Any user with an admin role has the same permissions as the default Administrator. Any user with
a user role will have the same permissions as the default Operator.
NOTE: To add external users or groups, first add the StoreOnce device to an AD domain.
Connection to an AD Domain is configured through the NAS CIFS server tab on the StoreOnce
GUI. See Configuring CIFS Server with AD and CIFS Share with AD domain users (page 34).
IMPORTANT: If Admin credentials are lost, the Admin password can be reset through the account
“HPresetpassword”. This account is password protected and is only accessible from the StoreOnce
console and CLI. HP recommends the end-user change the HPresetpassword password after
installation and store it in an offline Password Security tool.
Tip
To identify current user rights view the title bar of the GUI. This shows your user Type, Name, and
Role. See (page 10).
Powering off and on
HP recommends using the CLI commands to power off and on the system instead of using the
“power off” and “power on” controls on the hypervisor. See the HP StoreOnce VSA Deployoment
and Configuration guide for more information.
Deployment of the Virtual Storage Appliance
HP StoreOnce VSA is a software-only version of the HP StoreOnce Backup System. Packaged as
a virtual appliance, it can be deployed and run on a vmware vSphere hypervisor (v5.x) or Hyper-V
Manager installed by the customer. Once deployed, the customer has access to web management
via the StoreOnce GUI or command line management via the CLI. The StoreOnce VSA Backup
System supports 10 x 1 TB virtual disks.
8 Getting started
Page 9

The customer is able to create the following backup target devices on the HP StoreOnce VSA:
• Catalyst stores
• iSCSI VT libraries
• CIFS NAS shares
The virtual appliance is fully compatible with StoreOnce hardware products for replication and
Catalyst Copy functions and is fully integrated within HP StoreOnce Enterprise Manager, both for
ease of management and for ease of deployment.
There are two methods of deployment:
• Using Hyper-V Manager
• Using vSphere Client (v5.x)
Instructions for deployment are in the HP StoreOnce VSA Deployment and Configuration guide.
Please consult the guide to deploy your StoreOnce VSA backup system.
Navigating the HP StoreOnce Graphical User Interface (GUI)
The HP StoreOnce GUI and CLI together make up the Management Console. While there is overlap
in what operations you can perform, not all operations are available from both interfaces.
The HP StoreOnce GUI is the main interface for:
• Monitoring the status and health of the HP StoreOnce Backup system and all configured backup
devices
• Creating and modifying VTL and NAS StoreOnce backup targets and Catalyst stores
• Managing replication relationships and housekeeping
To run the StoreOnce GUI
Log on to the StoreOnce GUI using a browser on any machine connected to the management
network; see “User types and user roles” (page 7) for default login information. The HP StoreOnce
Backup system uses a secure network connection.
Enter: https://<IP_address> .
NOTE: Entering http: in the URL path will automatically forward to the https: secure network
connection.
The StoreOnce GUI displays the Login prompt.
NOTE: The web browser requires Active Scripting or JavaScript enabled. If both are disabled,
some browser buttons may not be displayed.
Navigating the HP StoreOnce Graphical User Interface (GUI) 9
Page 10

GUI components
The GUI includes:
• Title bar: Displays the HP StoreOnce Backup system model, the user name and role, and
contains the Logout and Help buttons.
NOTE: After 15 minutes of inactivity, the session times out and returns to the Login screen.
• System Status (top left side panel): Displays the last time the system was updated (the machine
time) and a count of event status categories.
The three icons described below are used in the System Status area. They do not identify the
event that has affected the status. To view the individual events for more detail, select Events
from the Navigator, as described in Events (page 124).
Indicates standard information.
Indicates a warning state. Attention is needed but the error is not critical to the successful operation of
the device. For example, a single disk failure occurs or disks are installed in an expansion shelf but
not licensed.
Indicates a critical state. The system requires immediate attention. This icon may also appear in the
Details area of the screen with a red square background (rather than a red circle).
• Navigator (left side panel): Displays available GUI topics and enables navigation to selected
topic pages. A + sign next to a topic indicates additional options; click + to expand the
selection and click — to contract the selection.
• Topic page (main window): Initially, the main window displays the top-level StoreOnce topic
page. Select another topic from the Navigator to display the page for that selection. Some
Topic pages require selection of an item, such as a library, NAS share, or Catalyst store in
the top half of the page to display details specific to the selected item in the lower half of
page. Some Topic pages include multiple tabs within the page, for example the VTL—Libraries
page. Select a tab to display information and actions appropriate to that tab.
Navigating the online help
The Help link in the top right-hand corner of each page displays context-sensitive information for
the current page.
10 Getting started
Page 11
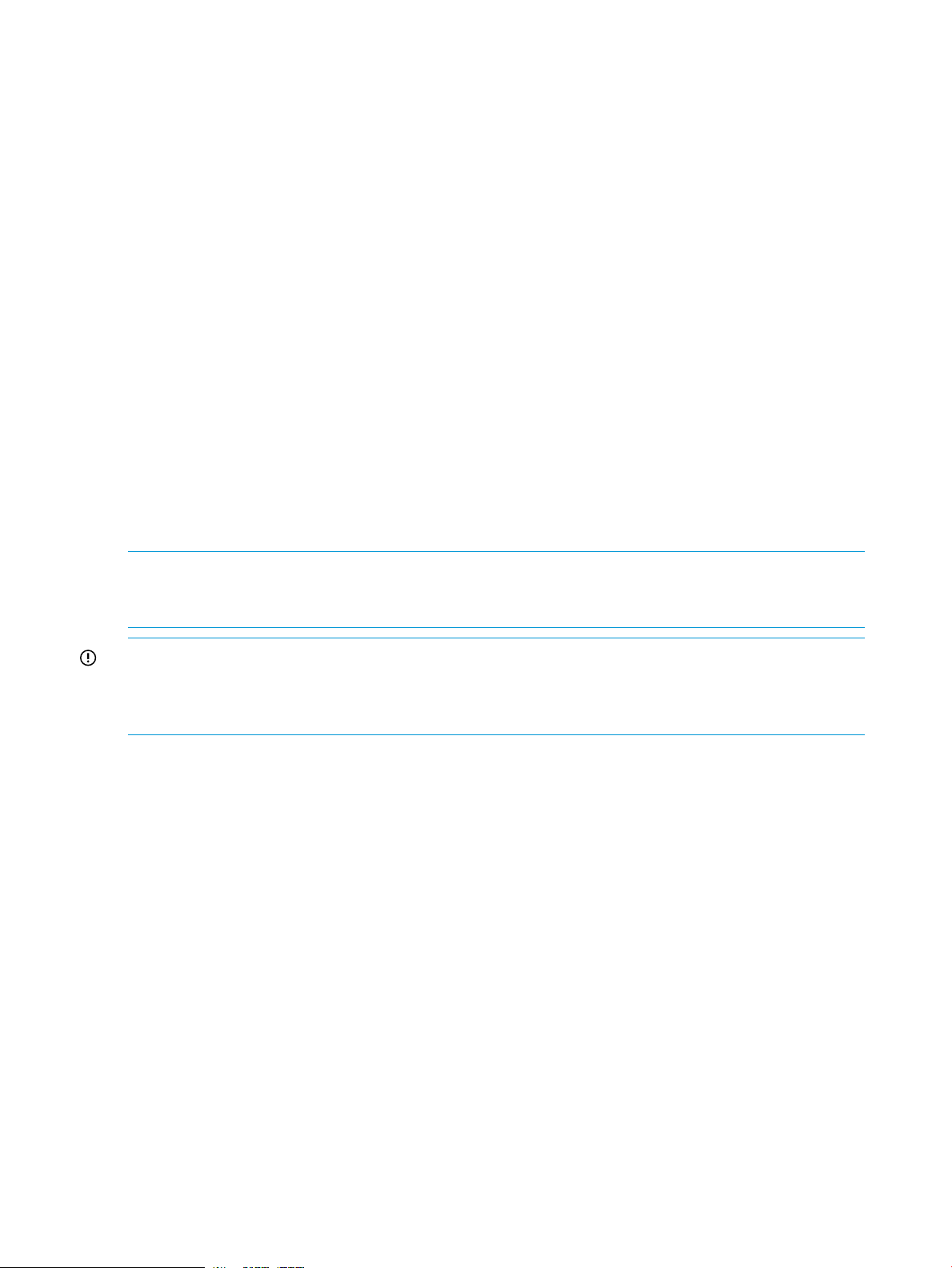
The following example displays the Help when selected from the NAS Mappings page.
• Click and drag on a side or a corner to expand or contract the Help window.
• The header displays the page where the help was called. Links navigate to the next or previous
pages; the titles of the next and previous pages are beneath the respective links.
• The footer also provides navigation options. Select home to access the help Home page which
provides access to the complete online help and Contents, Search, and Index options. Resize
the page to view all of the content.
Navigating the online help 11
Page 12

The StoreOnce CLI
The StoreOnce Command Line Interface (CLI) provides an alternative way of administering and
monitoring the system. Some tasks are only accessible from the StoreOnce CLI.
StoreOnce CLI commands require an SSH client application (freely available from the internet) and
must be run from a SSH terminal session as described in Accessing the CLI (page 126).
See the HP StoreOnce Backup system CLI Reference Guide for more information about the StoreOnce
CLI commands.
Licensing
HP StoreOnce VSA has a single license that enables StoreOnce Catalyst and Replication. The
license also includes the security features of Data at Rest Encryption, Data in Flight Encryption, and
Secure Erase.
Security Features
The security features of Data at Rest Encryption, Data in Flight Encryption, and Secure Erase are
part of the VSA license.
NOTE: StoreOnce replication can be encrypted at the Network layer. This feature is included in
the Security license. See the HP StoreOnce Backup system CLI Reference Guide for more details;
review the networking configuration commands such as net add encryption.
Data at Rest Encryption
When enabled, the Data at Rest Encryption security feature protects data at rest on a stolen,
discarded, or replaced disk from forensic attack.
Creation of a new VTL library, Catalyst store, or NAS share provides the option to enable encryption
if the license was already applied. Once enabled, encryption will automatically be performed on
the data before it is written to disk. Encryption cannot be disabled once it is configured for a library,
Catalyst store, or NAS share.
When creating an encrypted library, Catalyst store, or NAS share, the key store is updated with
the encryption key. This key store may be backed up and saved securely offsite in case the original
key store is corrupted. However, keep only the latest version of the key store as a backup. The key
store on the StoreOnce Backup system is updated each time you create a library, Catalyst store,
or NAS share. The StoreOnce CLI command that backs up the key store also encrypts it, ensuring
it can only be decrypted by the HP StoreOnce backup system.
NOTE: Each configured library, Catalyst store, or NAS share uses a different key. The StoreOnce
software automatically tracks which key is relevant to which device in the Key Store File. Keys are
automatically re-applied to the correct device if the key store file is restored.
IMPORTANT: Be very diligent about backing up your keystore if you are creating encrypted
stores or libraries. See the HP StoreOnce Backup system CLI Reference Guide for more information
about the StoreOnce CLI commands for backing up and restoring key stores.
Data in Flight Encryption
When enabled, the Data in Flight Encryption security feature protects data that is in transit from
forensic attack using the IPsec protocol. The data can be moving between two StoreOnce Backup
appliances or a StoreOnce Backup appliance and a backup server.
Data in Flight Encryption is configured using the net [add/modify/delete] encryption
commands in the CLI; see the HP StoreOnce Backup system CLI Reference Guide for more
information.
12 Getting started
Page 13

Secure Erase
Secure Erase can be enabled for all store types. This feature enables allows secure erasure of data
that was backed up as part of a regular backup job. The Secure Erase feature can only be enabled
after store or library creation (edit the store or library to enable Secure Erase). All data written to
disk once Secure Erase is enabled will be securely erased upon data deletion. For example, you
may have unintentionally backed up confidential data and need to be sure that it has been securely
erased. Work with the backup application to trigger the Secure Erase, for example by forcing the
format of a cartridge. The backup application sends the request to delete the data and the deletion
is carried out as part of the Housekeeping function.
WARNING! To immediately remove data, ensure the backup application is configured correctly.
Rotation and retention policies may need to be revisited to ensure that the data is expired.
NOTE: The Secure Erase process may take some time depending on the Housekeeping workload.
Only chunks not referenced by any other items can be securely erased. If a chunk is referenced
by another item which is not marked for Secure Erase, then the referenced chunk will not be erased,
securely or otherwise. Use the backup application when performing a Secure Erase on stores,
shares, or libraries that have Secure Erase enabled.
Security Features 13
Page 14
2 StoreOnce functions
The following topics are covered in this chapter:
• Overview of the HP StoreOnce page (page 14)
• System information and status (page 14)
Overview of the HP StoreOnce page
The initial page at GUI logon provides important information about system status and processes
that are running (see System information and status (page 14)).
It also provides access to individual StoreOnce functions, which are available as sub topics (click
+ to display them in the Navigator).
• VTL (Virtual Tape Libraries) functions (page 16)
• NAS functions (page 30)
• Replication functions (page 50)
• HP StoreOnce Catalyst functions (page 80)
• Housekeeping (page 105)
• StoreOnce reporting (page 110)
System information and status
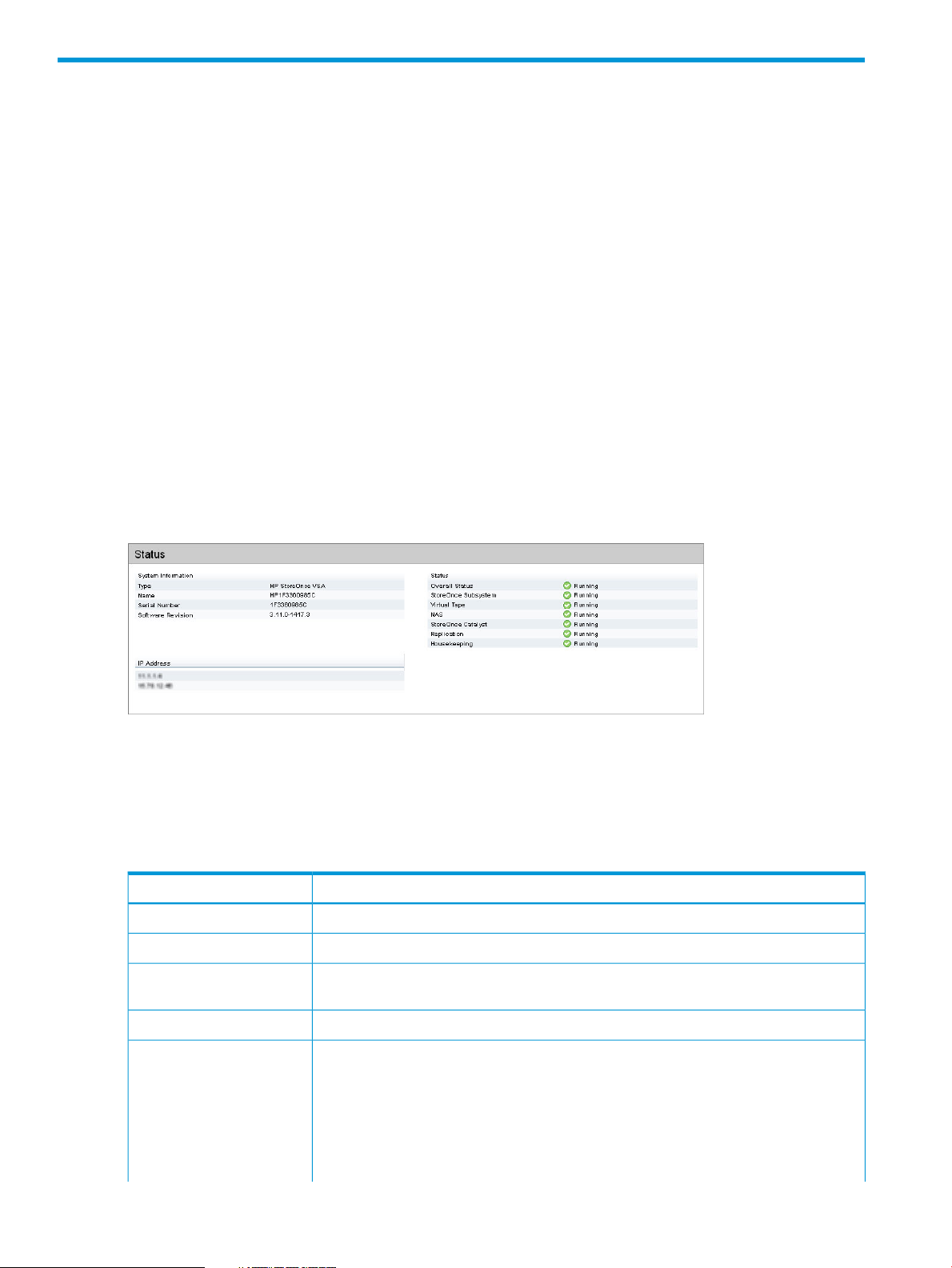
System information
This section provides information unique to an individual HP StoreOnce Backup system.
Table 1 System information parameters
DescriptionParameter
The model of StoreOnce Backup system.Type
The name of the StoreOnce Backup system.Name
Serial Number
IP Address
The serial number of the StoreOnce Backup system (use this number when contacting HP
Support).
The software revision running on the StoreOnce Backup system.Software Revision
The IP addresses configured for the StoreOnce Backup system. This is the IP address that
you should use when targeting backups and setting up replication mappings and Catalyst
jobs.
If vLAN tagging has been configured on your network, there is an option to expand the
list so that you can see all the vLAN IP addresses that have been configured. For more
information about vLAN tagging, see your product’s HP StoreOnce Backup system
Installation and Configuration guide.
14 StoreOnce functions
Page 15

Table 1 System information parameters (continued)
DescriptionParameter
HP StoreOnce VSA Backup systems may have up to two IP addresses depending on how
the network is configured. See the HP StoreOnce VSA Deployment and Configuration
guide for more information.
Status
This section provides details about the rolled-up system status of the system and the status of the
services running.
Table 2 Status parameters
DescriptionParameter
The state of the system.Overall Status
StoreOnce Subsystem
The status of the background support processes such as EventManager and
ResourceManager.
The status of the VTL service.Virtual Tape
The status of the NAS service.NAS
The status of the StoreOnce Catalyst service.StoreOnce Catalyst
The status of the Replication service.Replication
The status of the Housekeeping service.Housekeeping
System information and status 15
Page 16
3 VTL (Virtual Tape Libraries) functions
The following topics are covered in this chapter:
• VTL page (page 16)
• Libraries page (page 16)
• Make Replication Target libraries visible to the host (page 28)
VTL Configuration page
Select VTL from the HP StoreOnce menu to display the current VTL configuration.
The HP StoreOnce–VTL page includes the following tabs:
• iSCSI Settings tab (page 16)
NOTE: Equivalent StoreOnce CLI commands are available for the tasks described in this section.
See the HP StoreOnce Backup system CLI Reference Guide.
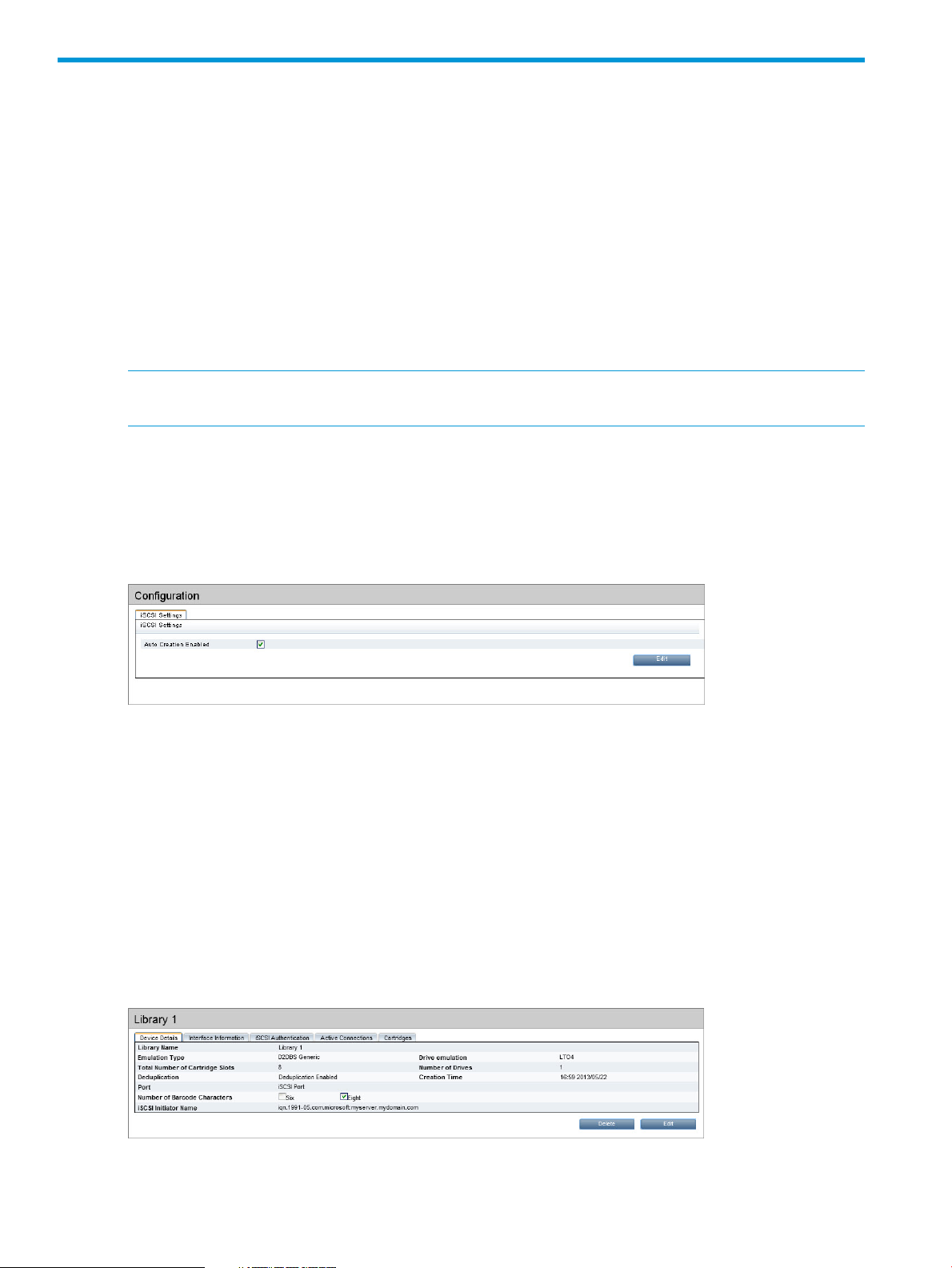
iSCSI Settings tab
By default, a new library is automatically created whenever a new server first connects to the HP
StoreOnce Backup system using the iSCSI initiator. Users with an Admin login may use this page
to disable this feature.
Click Edit and make sure the Auto Creation Enabled box is unchecked.
Libraries page
Click VTL — Libraries in the Navigator panel to display existing libraries.
The top half of the Libraries page shows all libraries configured for the appliance. Click on a library
to display its details in the lower half of the page. Users with an Admin login may edit these settings
and delete or create libraries.
The lower half of the Libraries page contains tabs that display information relevant to the selected
library:
• Device details tab (page 17)
• Interface information tab (page 22)
• Cartridges tab (page 23)
16 VTL (Virtual Tape Libraries) functions
Page 17
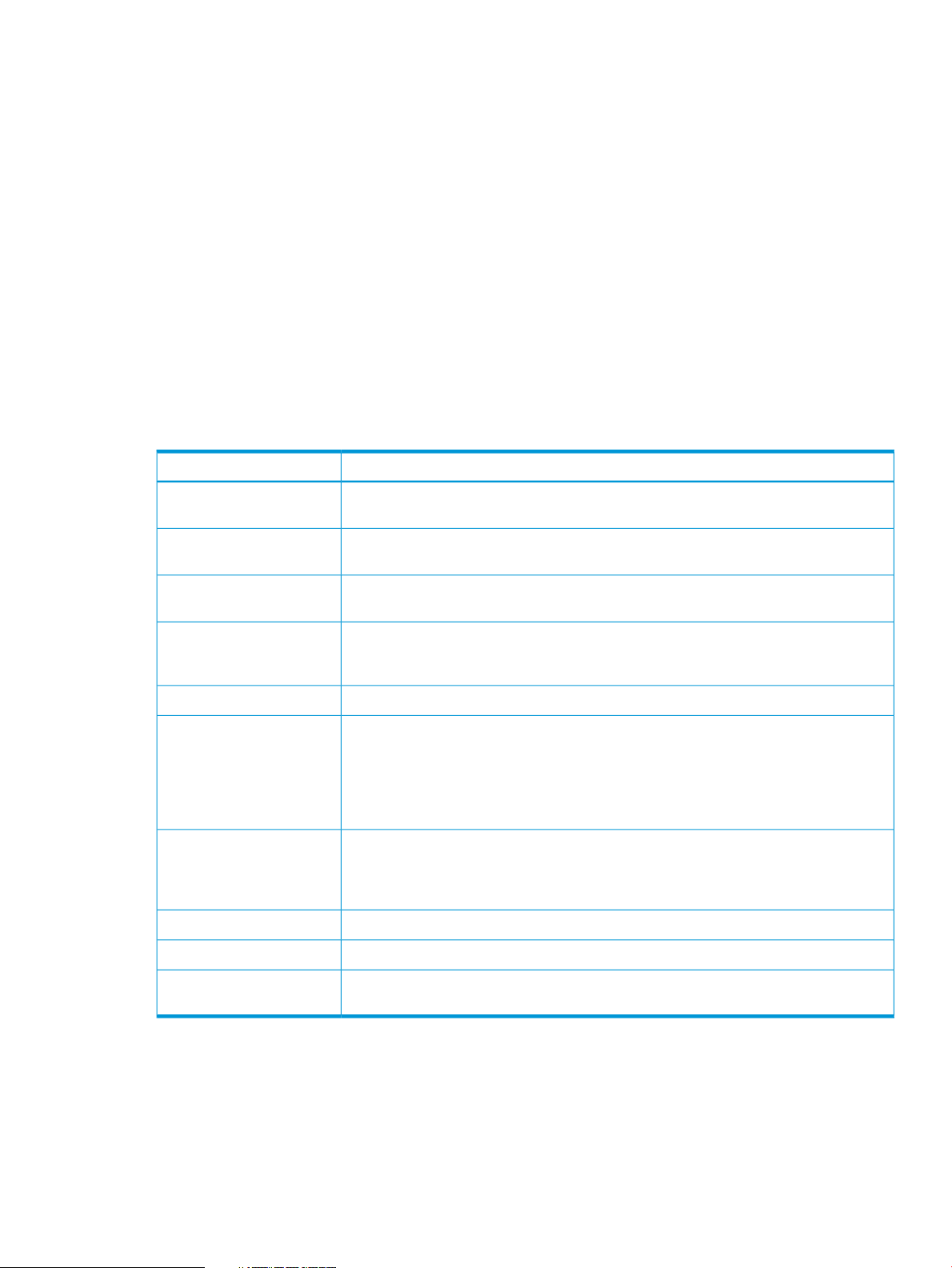
Working with the Libraries list (top half of page)
The Libraries list in the top half of the page provides columns of details.
• To sort the list according to a column, click on the column heading and select Sort Ascending
or Sort Descending.
• To hide or show columns, click on any column heading, select Columns and uncheck or check
the preferred columns.
• Users with an Admin login may also create libraries. Click Create.
See Create a library (page 19) for more information.
• Users with an Admin login may edit details on some of the tabs for individual libraries (not
all tabs have editable information). The relevant GUI buttons are on the tab. For example,
each Edit button shall trigger edit mode only for the current tab. When in edit mode, each
tab shall have its own Update and Cancel buttons. If a user changes tab while in edit mode
a warning dialog advises that any changes they have made will be lost.
The Delete button is on the Device Details tab only and will delete the entire library.
Table 3 Libraries parameters (top half of page)
DescriptionParameter
Name
Replication Role
Status
Connection
Cartridges / Slots
Port
Identifies the selected device (library). HP recommends usnig a name that identifies the
host or backup job with which it is associated.
The role of the library, which may be non-replicating, replication source or replication
target.
The status of the library, which may be online, offline, notstarted, failed to start, stopping,
creating, or deleting.
Indicates whether the library is connected. Possible values are: Connected – A client
device is connected to any device (robotics or drive) within this library. Not Connected
– No device is connected to this library.
The emulation type used by the backup software. It is selected when you create a device.Device Type
The number of cartridges or slots available on the device, which is determined by the
Emulation types for tape device selected when the device was created. You can reduce
the number of slots in the Device Details tab for a library selected on this page, but this
will only remove the highest empty slots. Once it reaches a slot number that contains
data, it will not allow you to reduce the number further on this page, even if earlier slots
are blank. You must first use the Cartridges tab to make the slot empty.
Identifies the port to which the host is connected for backup and restore. The number of
ports available in the drop-down menu depends upon the interfaces that your model
supports and your network configuration.
There is always one iSCSI port.
The amount of user data stored on the library.User Data Stored
The actual size used on disk (after deduplication).Size On Disk
Dedupe Ratio
Device Details tab
This tab displays device-specific information for the selected library.
Users with an Admin login may perform the following tasks from this tab:
• Create a library (page 19)
• Edit a library (page 20)
The deduplication ratio achieved on the data on the library. If deduplication is disabled,
the column displays “Dedupe Disabled.”
Libraries page 17
Page 18

• Delete a library (page 21)
• Make Replication Target libraries visible to the host (page 28)
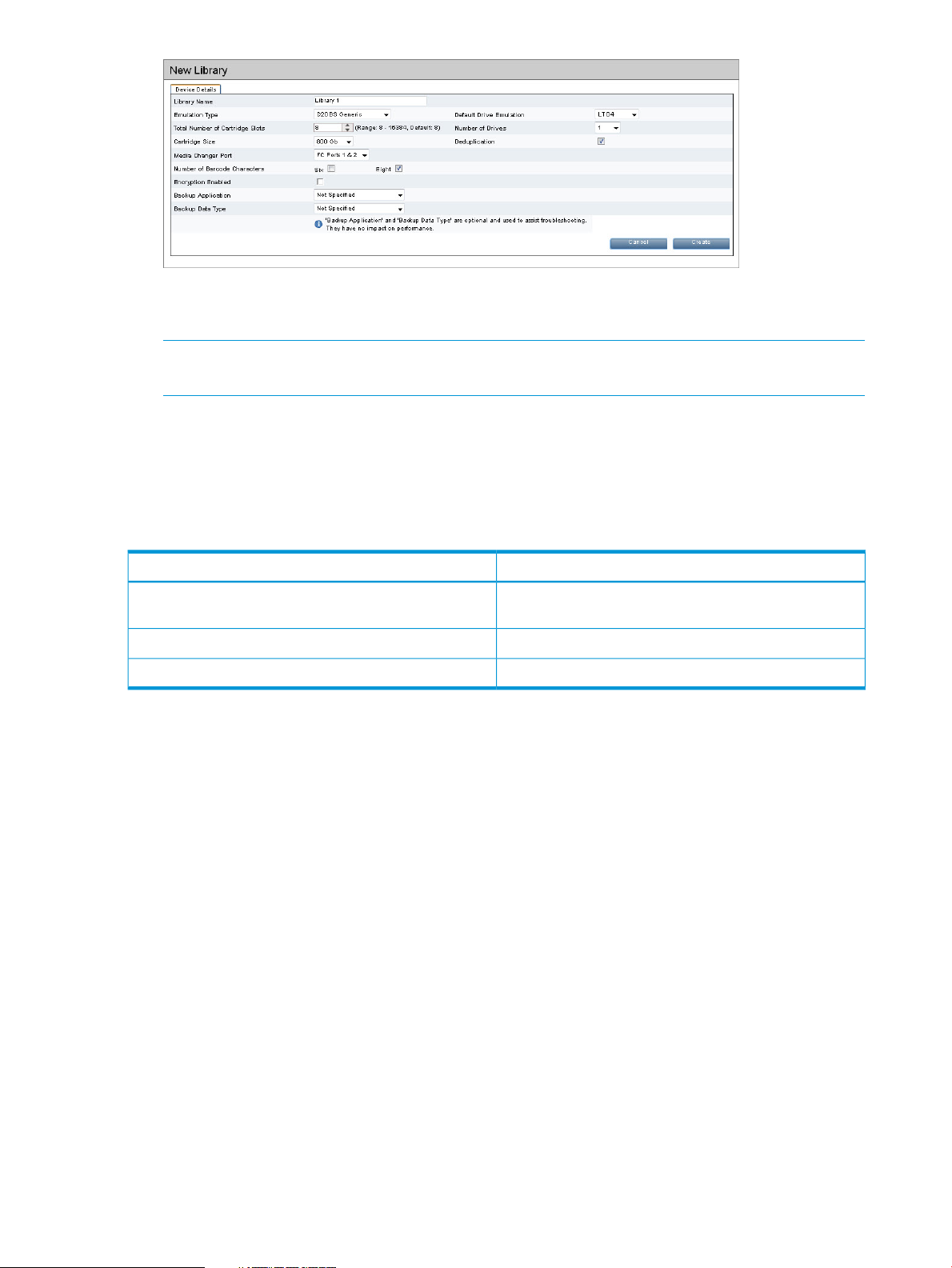
Table 4 Device Details tab
DescriptionField
Library Name
Emulation Type
Drive emulation
Total Number of
Cartridge Slots
The name used to identify a particular library. Enter a name that identifies the host or backup
job with which it is associated.
The emulation type of the library. The HP StoreOnce Backup system supports a number of
emulation types. . See also Emulation types for tape device (page 21). The emulation type
determines the available embedded drives and cartridge slots. For example, if you select
HP MSL G3 Series (2x24), the device emulates an MSL 2024 Library with two embedded
tape drives and a possible total of 24 cartridge slots. Consult your backup application
technical support information for information about device types they support.
The drive emulation type, HP LTO–2, 3, 4, 5 or 6, determines the default capacity of the
cartridges within the library device and the iSCSI inquiry string information provided to the
backup application. Tape cartridge capacities can be increased at any time (but not
decreased), as long as the cartridge is blank, regardless of the drive emulation generation
number.
If you selected D2DBS Generic for the Library Emulation Type, Ultrium VT is an option for
drive emulation. This is a generic Ultrium device which is clearly identifiable as virtual.
Where supported by the backup application, HP recommends that D2DBS Generic and
Ultrium VT are used in preference to the other emulation types.
All drives on a library configured with the IBM-TS3500 emulation type will use the IBM-LTO3
drive emulation type. If the library is then changed to a different emulation type, the drives
will change to the new emulation type.
If you edit this field, the new setting applies only to the next drives that are created within
the library, it is not retrospectively applied to existing drives.
Define the number of cartridge slots in the library. The number of slots available depends
upon the Emulation Type selected. Each slot is automatically populated with a new cartridge
upon creation. The cartridge capacity corresponds to the Drive Emulation type.
You can change the maximum size of the cartridge as long as it is blank. This means that
the value can only be changed after the device is created and before it is accessed by the
backup application.
Number of Drives
Deduplication
Media Changer Port
18 VTL (Virtual Tape Libraries) functions
The default number of drives is determined by the Emulation Type selected. If increasing the
number of drives, DO NOT exceed the maximum number of libraries and drives that a host
can physically access: see StoreOnce key parameters (page 137). The number of drives can
only be edited during library creation from this field. After library creation, there is a separate
button to Add/Remove drives.
Enables deduplication if the check box is selected (default); unselect to create a
non-deduplication library. Deduplication cannot be enabled or disabled once the library is
created.
The date the library was created is generated automatically.Creation Time
Identifies the port on the HP StoreOnce Backup system to which the device is connected.
This will be the port used for the Library device as well as the default port for embedded
tape drives. The number of ports available in the drop-down menu depends upon the
interfaces that your model supports and your network configuration.
There is always one iSCSI port.
Page 19

Table 4 Device Details tab (continued)
DescriptionField
Number of Barcode
Characters
Encryption Enabled
Secure Erase Mode
Backup Application
Data Type
iSCSI Initiator Name
(iSCSI devices only)
Enables configuration of the barcodes for the library to display six or eight characters. The
HP StoreOnce Backup system generates barcodes automatically for cartridges. When entering
a barcode manually, 8 characters are required. If the 6–character barcode is selected, the
StoreOnce Backup system will truncate to the top six characters, removing the top two
characters of an 8–character barcode, i.e. barcode 1ABCDEFG will truncate to BCDEFG.
The barcode is displayed with the truncated characters in brackets on the Cartridges tab,
(1A)BCDEFG.
Enables Data at Rest Encryption if you applied a Security license. Encryption cannot be
enabled or disabled once a library is created; it can only be enabled at library creation. If
enabled, encryption is performed prior to writing data to disk for this library. The correct
license must be applied to enable encryption.
Enables Secure Erase if you have applied the Security license. “None” leaves it disabled
(default). To enable, select the number of preferred Overwrite Passes (1, 3, 5, or 7). This is
the number of times the data is written over after deletion. See “Secure Erase” (page 13)
for information about the Secure Erase feature.
The backup application used on the system. This optional field is provided to assist with
support troubleshooting and has no impact on performance or deduplication efficiency.
The type of data being protected by the backups. This optional field is provided to assist
with support troubleshooting and has no impact on performance or deduplication efficiency.
This is the Initiator Node Name of the host that will back up to this device. You must enter
it manually when you are creating a new device. If you are using the Microsoft iSCSI Initiator,
you can find the name by running the iSCSI Initiator on the host and copying the Initiator
Node Name from the General tab.
NOTE: iSCSI multi-initiator mode is not supported.
To create a new library (administrators only)
HP recommends:
• Only configure the libraries that you need
• Only configure the number of cartridges that you are likely to need
NOTE: Refer to the HP StoreOnce Backup system Concepts and Configuration Guidelines,
available on the HP Support web site, for guidelines on setting up a backup policy/job within
backup applications. This document is helpful in determining the required number of libraries and
cartridges.
You can add cartridge slots at a later date to expand the system and remove individual blank
cartridges from a library without deleting the whole library.
1. To create a new library device for the host, click Create in the upper left corner of the screen.
2. Enter the appropriate details in the Device details tab (page 17).
To enable Data at Rest Encryption for the new library, configure it at this time by checking the
Encryption Enabled box. This feature requires a license. If the license is not installed, an
information message is displayed next to the check box stating Not Licensed. See “Security
Features” (page 12) and “Licensing” (page 12) for more information.
NOTE: The Replication Wizard does not allow creation of an encrypted target library. If a
replication target library needs encryption enabled, you must create the library on the target
appliance before replication mapping to it.
Libraries page 19
Page 20
3. Click Create. The Cartridges tab is only generated after the library is created. The information
on the Interface Information tab is generated automatically.
NOTE: Once the library has been created, you can enable Secure Erase. See “Edit a
library” (page 20) for more information.
Guidelines on creating libraries
The table below illustrates maximum configurations for libraries and drives, but this number may
be limited if you have already created NAS shares and Catalyst stores. For more detailed device
configuration examples see the HP StoreOnce Concepts and Configuration Guidelines.
Table 5 Maximum number of libraries and drives/slots per library
emulation)
To edit library details (administrators only)
It is possible to edit some, but not all, device details after creating a library.
StoreOnce VSA
16Maximum drives per library/appliance (D2DBS and ESL
96Maximum cartridges per library (D2DBS and ESL emulation)
3200Maximum cartridge size (GB)
• Delete cartridges by reducing the number of slots on the Devices page. This will only remove
the highest-numbered empty slots. Once the Delete operation reaches a slot number that
contains a cartridge, it will not allow further reduction on the Details page, even if previous
slots are empty. To open previous slots first use the Cartridges tab to delete the cartridge from
the slot.
• Changing the cartridge size (by changing the emulation type) on this page will only change
newly-added cartridges; it does not change the size of cartridges that were already created.
• You can reduce the number of drives but, if you go to 0, the port setting will change to "No
Port".
The Number of Drives field can only be edited during library creation. After library creation,
there is a separate button to Add/Remove drives.
• You cannot change the library type to a type that has a smaller set of maximum values (e.g.
number of cartridges) than is currently set.
• You cannot enable or disable deduplication.
• Once the library is created and the correct license is applied, the Secure Erase Mode box
appears on the Device Details tab. The selection box defaults to None, meaning Secure Erase
is disabled. To enable Secure Erase, select the preferred number of Overwrite Passes (1, 3,
5, or 7). If enabled, this feature allows you to securely erase confidential data that may have
20 VTL (Virtual Tape Libraries) functions
Page 21
unintentionally been backed up as part of a regular backup job. See “Security
Features” (page 12) and “Licensing” (page 12) for more information.
1. Select the device in the list to display its details and then click on Edit.
2. Amend details as appropriate and click Update to apply them.
To add/remove drives
1. Click Add/Remove drive.
2. The maximum number of drives is shown, below which you can edit the Number of Drives.
3. Click OK. If you provide an invalid value the text box will be surrounded in a red border.
To delete a library (administrators only)
Select the required device and then click Delete on the Device Details tab to delete it. You will be
prompted to confirm deletion.
WARNING! All data on the device will be deleted. The library's deduplication store is also deleted.
It may take some time to delete all the files and free space on the HP StoreOnce Backup system.
If Secure Erase is enabled for this store, this data will be deleted securely.
Emulation types for tape devices
HP StoreOnce Backup systems emulate a range of physical tape devices listed in Emulation types.
Table 6 Emulation types for tape devices
DescriptionEmulation type
D2DBS Generic
EML E Series
ESL E Series
If supported by your backup application, this is the preferred emulation type because it does
not emulate any physical library types in existence and is, therefore, clearly identifiable as
a StoreOnce device. It is the most flexible emulation type available; however, backup
application support varies by software vendor.
If you have selected D2DBS Generic for the Library Emulation Type, you will be able to
select Ultrium VT for the drive emulation. This is a generic Ultrium device which is clearly
identifiable as virtual. Backup application support for Ultrium VT is common, but not quite
as complete as the D2DBS library type, so its not possible to use it with all backup software.
NOTE: Symantec prefers their customers use this emulation type with BackupExec and
Netbackup.
An enterprise tape library solution that allows you to configure up to 500 drives and up to
4096 cartridges per library (HP 4900 = up to 16384 cartridges per library).
An enterprise tape solution that allows you to configure up to 500 drives and up to 4096
cartridges per library (HP 4900 = up to 16384 cartridges per library).
IBM-TS3500
MSL G3 Series (2x24)
A tape library device that appears as a native IBM TS3500 device in a TSM environment
to allow use of standard IBM drivers. The emulation type is configured at the library level.
Therefore, all drives on a library configured with the IBM-TS3500 emulation type will use
the IBM-LTO3 drive emulation type. If the library is then changed to a different emulation
type, the drives will change to the new emulation type.
A tape library device with a maximum of two embedded Ultrium tape drives and 24 cartridge
slots. It should be used when implementing rotation schemes which involve simultaneous
backup jobs to two devices. This emulation type is widely supported by backup applications.
Libraries page 21
Page 22
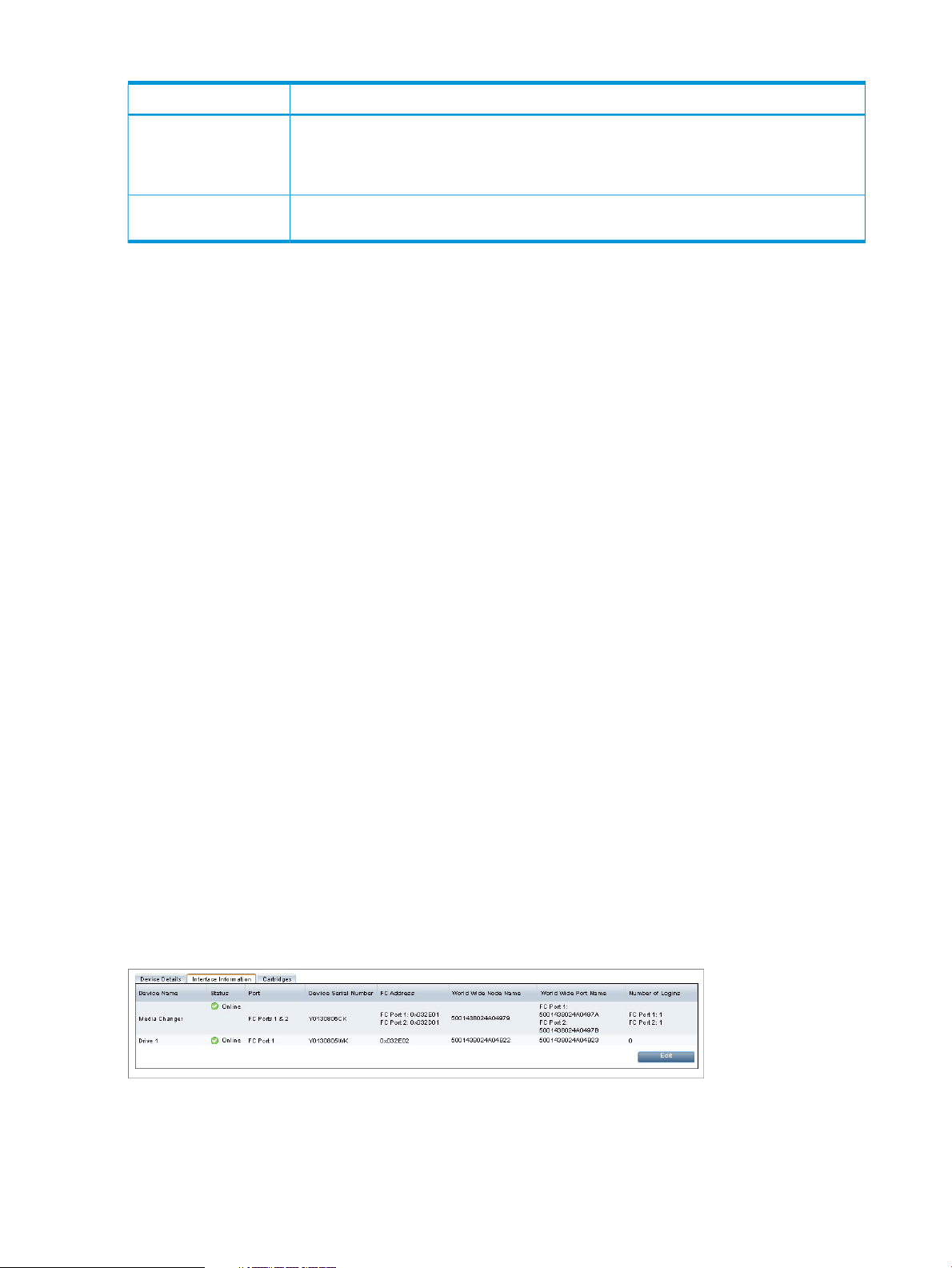
Table 6 Emulation types for tape devices (continued)
DescriptionEmulation type
MSL G3 Series (4x48)
MSL G3 Series (8x96)
A tape library device with a maximum of four embedded Ultrium tape drives and 48 cartridge
slots. It should be used when implementing rotation schemes which involve simultaneous
backup jobs to more than two devices or those that use a large number of cartridges devices.
This emulation type is widely supported by backup applications.
A tape library device with a maximum of eight embedded Ultrium tape drives and 96
cartridge slots.
Flexible emulation
The ESL, EML and D2DBS emulations are particularly flexible because they allow you to configure
a large number of drives per library. The main benefits are that a large number of drives allows:
• more concurrent streams on backups which are throttled due to host application throughput,
such as multi-streamed backups from a database.
• a single library (and therefore deduplication store) to contain similar data from backups that
must run in parallel to increase deduplication ratio.
If using these flexible emulation types, the following factors should also be considered:
• An important consideration when configuring VTL devices is that the library and each drive
that you configure for it counts as a separate device. There are practical limitations on the
number of devices that each host and Fibre Channel switch or HBA can access. See StoreOnce
key parameters (page 137).
For iSCSI VTL devices, a single Windows or Linux host can only access a maximum of 64
devices. A single library with 63 drives is the most that a single host can access. Configuring
a single library with more than 63 drives will result in not all devices in the library being seen
(which may include the library device). The same limitation could be hit with multiple libraries
and fewer drives per library.
• The total device value also applies to NAS shares and Catalyst stores. If you configure the
full value as VTL devices, you will not be able to configure any NAS shares or Catalyst stores
for that .
• Refer to the HP StoreOnce Backup system Concepts and Configuration Guidelines for maximum
and recommended values.
Interface Information tab
This tab shows interface information for the media changer and drives on the selected library.
The information for the Interface Information tab is generated automatically and manual configuration
is discouraged.
The following information is provided for a device that is configured to use the Fibre Channel
interface.
iSCSI interface
The following information is provided for a device that is configured to use the iSCSI interface.
22 VTL (Virtual Tape Libraries) functions
Page 23

Table 7 iSCSI Interface Information
DescriptionField
Device Name
Device Serial Number
Name
Active Connections tab
This shows the Session information of any active connections to the library; it displays information
about open iSCSI sessions. All details are generated automatically and cannot be edited.
If a device is showing as not connected, this indicates that the iSCSI Initiator on the host has not
logged on. Log on using the iSCSI Initiator and set the device as a Persistent Target for that host
to ensure that it will automatically log on again whenever the host is rebooted.
The device name lists all of the devices for the specific Library. There will be an entry for the
Medium Changer, and for each of the drives configured.
This defines the port to which each media changer or drive is connected.Port
This is a unique serial number for the device. It is generated automatically by the HP
StoreOnce Backup system and cannot be edited.
This is provided when the device is created.World Wide Node
This is generated automatically by the HP StoreOnce Backup system for iSCSI devices.iSCSI Target Name
This is generated automatically by the HP StoreOnce Backup system for iSCSI devices.iSCSI Alias
Cartridges tab
This tab shows cartridge information for the selected library.
Users with an Admin login can perform the following tasks from this tab:
• Create a cartridge (page 25)
• Delete a cartridge (page 25)
• Write protect a cartridge (page 26)
• Edit maximum cartridge size (page 27)
• Move or unload a cartridge (page 27)
Libraries page 23
Page 24

Table 8 Cartridge tab parameters
DescriptionField
Location
Barcode
Mapped Slot
Identifies each element of the library available to hold a cartridge. The types of elements
are:
• Mail slot: a dedicated slot used to hold a cartridge that is ready for exporting to or
importing from physical tape. The Mail slot is not used with HP StoreOnce models.
• Tape drive: populated when there is activity on a cartridge. You can move a cartridge
into a tape drive by using the Move Cartridge drop-down menu in Edit mode.
• Slot n: one of the standard library slots.
A barcode is an 8– or 6–digit, alphanumeric, unique identifier for a cartridge within the HP
StoreOnce Backup system. Barcodes are shared with the backup application upon request.
The backup application can choose to assign its own internal identifier to the cartridge but,
if it does so, the backup application cannot assign this identifier to the Cartridge barcode.
Barcodes are generated automatically but may be edited by the user. When editing the
barcode:
• It must be unique and must not start with the letters “CLN” or “DG” because these are
reserved designations for cleaning and diagnostic cartridges.
• It should be a minimum of 6 characters. Valid ASCII characters are A-Z, a-z, 0–9.
Barcodes are always displayed as 8 characters with letters in capitals on the StoreOnce
GUI and CLI (padded with space characters) regardless of the size selected. However,
if the Number of Barcode Characters is set to 6, only the rightmost 6 characters will be
visible to the backup software, i.e. barcode 1ABCDEFG will truncate to BCDEFG.
(Truncated barcode characters are shown in brackets in the Cartridges tab.)
Check box indicates whether the slot is included in a replication mapping configuration. It
cannot be edited from this page.
The actual used capacity in MB or GB.Used Size
Max Size
Write Protected
Last Written
Defaults to the appropriate capacity for the drive emulation type selected on the Devices
tab. This value may be changed if the Used Size is Blank, see below. The maximum value
allowed is 3200 GB.
Check box that enables (checked) and disables (unchecked) write protection, see “Write
protect a cartridge” (page 26).
Identifies when the cartridge was last written to and is useful when identifying data for
copying or exporting.
NOTE: Additional columns appear when function buttons are selected below, such as Create,
Move, and Delete.
24 VTL (Virtual Tape Libraries) functions
Page 25
Empty slots
Empty slots are slots containing no cartridges and all the fields are empty.
• Tape drive row: A library consists of two devices: a tape drive and changer device. This
location refers to the tape drive element of the library and is normally only populated when
the backup application on the host is writing to or reading from the library.
• Mail slot row: This location is the slot used for importing and exporting cartridges from a
library. It is provided by StoreOnce virtual libraries for compatibility with backup applications
but is not used.
• Numbered slot row: This slot is empty after a Delete operation or after the backup application
has moved data to the mail slot for export.
Once a numbered slot is empty, the Create button may be used to create a new blank cartridge.
To create a cartridge (administrators only)
NOTE: You can only create a cartridge in an empty slot.
Click the Create button. In the Add Cartridge column, empty slots are checked.
Select individual slots by clicking the appropriate check boxes. After selected the slots where
cartridges should be added, click Create.
Alternatively, click Create all to create a blank cartridge of the size/emulation type selected when
the library was first configured in all empty slots.
• If you create a cartridge in an empty slot, the backup application must inventory it (add it to
its database or catalog) before the backup application can access the cartridge.
• If you create a cartridge in an empty mail slot, use the backup application to move the blank
new cartridge to an empty cartridge slot without requiring an inventory. This saves processing
time.
Restart the backup application services to see the new cartridges.
To delete a cartridge (administrators only)
To delete individual cartridges, select individual slots by clicking the appropriate check boxes in
the Delete Cartridge column. Then click Delete.
Libraries page 25
Page 26

CAUTION: A dialog is displayed, warning that all data will be lost and asking you to confirm
the Delete action.
NOTE: You cannot delete cartridges that are currently in drives, that are mapped for replication,
or that are in the delete pending, erase pending, or creating state.
If you click Cancel, the cartridges will not be deleted and you remain in delete mode. Click Delete
to continue and the selected cartridges will be deleted. The GUI does not differentiate between
cartridges with data and blank cartridges.
NOTE: You can also delete cartridges by reducing the number of slots on the Devices page, but
this only removes the highest slots with no or blank cartridges. Once the Delete operation reaches
a slot number that contains a cartridge with data, it will not reduce the number further on the Details
page even if earlier slots are blank. First use the Cartridges tab to reconfigure the slots to a blank
state.
To delete all or a range of cartridges (administrators only)
To delete all the cartridges in the library at once, click Delete All. This opens a window with several
options:
• Delete — Remove cartridges (default): completely deletes the cartridges
• Erase — Erase cartridge data: deletes the data but leaves the cartridge configurations intact
You can also determine which cartridges to delete or erase:
• All Cartridges
• Range: enter the first and last slot to be included in the delete or erase.
Finally, if you select the “Delete cartridges with data” check box, cartridges containing data will
be deleted. If unselected, only blank cartridges are deleted. After all of the options are selected,
click OK. A confirmation box appears; click OK.
NOTE: You cannot delete cartridges that are currently in drives, that are mapped for replication,
or that are in the delete pending, erase pending, or create state.
To write protect a cartridge (administrators only)
1. Click Edit for the selected library.
2. Check the Write Protected check boxfor the cartridge(s).
26 VTL (Virtual Tape Libraries) functions
Page 27
3. Click Update. Your backup application will not be able to write any more data to the
cartridge(s).
To edit maximum cartridge size (administrators only)
The Max Size defaults to the appropriate capacity for the drive emulation type selected on the
Devices tab, but this value is editable. The maximum value allowed is 3200 GB.
NOTE: The maximum size indicates the maximum amount of user data that can be written to that
cartridge, assuming uncompressed data; it will only be committed when data is written to it.
Changing the maximum space does not affect actual disk usage or save disk space but may be
useful if you know you will be moving data to a physical tape with a smaller cartridge capacity.
1. Click Edit for the selected library.
2. Select a value from the drop-down menu, and click Update.
To move or unload cartridges
You can move cartridges, but only to an empty Location (tape drive or numbered slot).
• Click the Move button. The Move Cartridge drop-down menu lists available empty slots. (Empty
numbered slots are created when a cartridge is deleted.)
• Use the Unload all Cartridges button to return all cartridges to default slots.
Libraries page 27
Page 28

The move and unload options may be useful to re-align the library configuration against the backup
application. For example, if the backup application has crashed or if the backup application does
not support the Move Medium command, the library and the backup application can become out
of sync.
NOTE: You cannot move or unload cartridges that are in the delete pending, erase pending, or
create state.
Make Replication Target libraries visible to the host
NOTE: See Replication functions (page 50) for more details on replication configuration.
Replication Target libraries are not normally visible to the host, but you can configure devices to
make them visible to backup applications. This allows the backup application to:
• Move cartridges from storage slots to drives in the library.
• Perform read and verify operations on the cartridge (but not write).
• Perform load/unload operations on the tape device.
WARNING! Use with care. If the backup application can see both source and target libraries,
the application cannot distinguish between the source library and the target library because the
barcodes are duplicated in the two locations.
Why make target libraries visible?
It may be useful to make a target library visible to the backup application on the host to:
• Confirm replication is working correctly and check the integrity of the replicated backup by
doing a test restore.
• Perform manual tape copy jobs (sometimes called tape offload) to any tape device on the
network using the backup application.
IMPORTANT: You cannot change data on a Target library cartridge; you may only load it
temporarily into a physical tape device to read it.
28 VTL (Virtual Tape Libraries) functions
Page 29

Best practices for using this feature
WARNING! Failure to follow best practices may cause instability and damage to your backup
system and data. Cartridges can be marked as unusable or the backup application can attempt
to write to target cartridges.
• Verify no replication jobs to the selected target cartridge are in progress.
• Verify no backup jobs to the mapped source cartridges are scheduled.
• Verify the backup application media server instance to be used is not within the same
cell/domain that can access the source cartridge.
• Import the data on the target cartridge into the backup application (this operation must be
repeated after each replicate operation to the cartridge).
• Perform the desired operation on the cartridge, which may be:
Verify the cartridge using the backup application either with a verify command or by
◦
performing a restore.
◦ Copy the cartridge to a physical tape device connected to the media server.
How is a target device made visible?
1. Create the replication mapping as normal. See Running the replication wizard (virtual tape
devices) (page 64), as appropriate.
2. From the host that has access to the target library on the VTL — Libraries page, select the
target library in the Libraries list.
3. Click Edit.
4. The Port defaults to None. Select the appropriate iSCSI Port.
5. Click Update.
6. Make the target library visible from other hosts. Configure the Fibre Channel fabric to make
the host visible. Target visibility persists even if the power fails or if the replication mapping
is removed.
NOTE: To remove target visibility, reset the Port to None.
Make Replication Target libraries visible to the host 29
Page 30

4 NAS functions
This page provides access to the following StoreOnce NAS functions:
• NAS Configuration (page 30), allows users to configure CIFS and NFS servers and permissions
• Shares (NAS) (page 43), allows users to view and manage NAS shares
NAS Configuration page
Select NAS from the StoreOnce menu item to display the NAS configuration page.
Two tabs allow configuration of a CIFS Server or an NFS Server for the shares.
• The CIFS server provides CIFS interface shares that provide backup targets to Windows servers.
See CIFS Server tab (page 30).
• The NFS server provides NFS interface shares that provide backup targets to UNIX and Linux
servers. See NFS Server tab (page 42).
CIFS Server tab
There are two configuration stages when creating a backup target share that Windows users can
access; both stages are implemented from the Web Management Interface:
• Configure authentication for the StoreOnce Backup system CIFS server. These settings then
apply to the appliance and all NAS CIFS shares created on it.
• Create NAS CIFS shares on the HP StoreOnce Backup system. See Creating a CIFS
share (page 45).
Configuring the CIFS server
1. Select NAS on the StoreOnce GUI.
2. Select the CIFS Server tab. It displays the authentication settings.
NOTE: The CIFS Server tab also shows the SMB Signing field. This feature improves security
at the protocol level and will be available in an upcoming release.
3. Click Edit to modify the authentication settings.
Three authentication options provide different levels of security for CIFS NAS shares: None
(default), User, and AD (Windows Active Directory). Before configuring the settings, determine
the appropriate setting for the particular network and collect any additional information that
may be required to complete the configuration.
NOTE: AD authentication joins the StoreOnce Backup system to an AD domain and is not
unique to NAS shares. It is also required when adding external users or external groups from
an AD domain to the StoreOnce Backup system, see User Management (page 114).
30 NAS functions
Page 31

• None (no authentication)
This provides a simple CIFS server configuration that allows for the creation of shares
with no authentication. Any user or computer can mount and access the shares created
on the HP StoreOnce Backup system with this setting.
• User authentication
This provides a method of securing the CIFS shares to be accessed only by specified users
local to the CIFS Server. Once the server is configured to User mode, it is possible to
create new local users by selecting Create User. See Configuring user
authentication (page 32) for more information.
• Active Directory (AD) authentication
This allows the CIFS server to join a Windows Active Directory domain. Access to
individual CIFS shares is managed from the Windows domain controller server which
provides the names of domain users and groups with access. See Configuring CIFS Server
with AD and CIFS Share with AD domain users (page 34) for detailed instructions.
4. Click Update. A popup window will advise that if you update the CIFS Server settings, any
backup or restore jobs in progress for it will fail.
5. After reading the advisory, click Continue (or Cancel).
IMPORTANT: When switching authentication modes, the user must log out and back into
the Windows client before the new authentication settings will work.
6. The system is now configured to create CIFS NAS shares. See Creating a CIFS share (page 45).
Connecting to the NAS target device on Windows
To access the NAS CIFS target device from a Windows server on the network, enter the following
in Windows Explorer:
• <StoreOnce server name>/<share name>
Or <IP address>/<share name>.
It is also possible to connect using \\<Fully Qualified domain name>\<share
name>.
NOTE:
This information is also provided in the StoreOnce GUI for the share: Select a share under
NAS–Shares and on the Share tab look for the Network Path.
• If User authentication was set for the CIFS server, a prompt will require a user name and
password, which will be:
<StoreOnce server name>\<user name> <password> or <StoreOnce IP
address>\<user name> <password>.
The share can also be mounted through the Map Network Drive utility in Windows or through
the Command Prompt utility with the net use command.
net use z:\\192.168.2.1\Share_3 /user:192.168.2.1\User1<password>
CIFS Server tab 31
Page 32

This command will mount Share_3 available from StoreOnce device 192.168.2.1 locally
on the server on z: drive using local StoreOnce CIFS server User1 credentials.
• If AD authentication was set for the CIFS server, a prompt will require a user name and
password, which will be:
/user:mydomainname\mydomainuser<mydomainuserpassword>
The share can also be mounted through the Map Network Drive utility in Windows or through
the Command Prompt utility with the net use command.
net use z:\\192.168.2.1\Share_3 /user:192.168.2.1\User1<password>
This will mount Share_3 available from StoreOnce device 192.168.2.1 locally on the server
on z: drive using the ‘mydomainname’ domain user User1 and its credentials.
Configuring user authentication
Once the server has been set to User mode, you can create new local users.
1. On the CIFS Server tab select Create User.
2. Provide a username and password and click Update.
These users can then be individually allowed to access any of the shares that are created.
When creating a new user in User Authentication mode, the user must log out and back into
Windows before they can access the newly created share.
3. Navigate to HP StoreOnce—NAS-Shares to provide individual users access to specific shares.
Create a NAS CIFS Share; on the Permissions tab. It shows No Access.
4. Click Edit and change it to Access. Click Update.
IMPORTANT: A warning is displayed to advise that any backup or restore jobs in progress
will fail.
Confirm the update by clicking Yes.
5. In Windows, navigate to Computer, right click and select Map Network Drive...
Specify the drive letter for connection and the network path of the share.
32 NAS functions
Page 33

6. Enter the user credentials.
7. This provides the user with access to the share.
Deleting a user
1. To delete a user, first disconnect the mapped share.
2. On the StoreOnce—NAS—Shares page, display the Permissions tab for the Share, and edit
it to be No Access.
CIFS Server tab 33
Page 34

3. Navigate to the StoreOnce-NAS—CIFS Server tab. Select the user and click Delete.
4. Click OK in the confirmation box. The user no longer exists in the system.
Configuring CIFS Server with AD and CIFS Share with AD domain users
To grant external users or groups (AD domain users) access to NAS shares:
1. Set the Authentication mode to AD on the NAS CIFS server tab. See “Configuring the CIFS
server” (page 30).
2. Add the StoreOnce device to an AD domain. See “Adding the StoreOnce device to an AD
Domain” (page 35).
3. Add any required users or groups to the active directory to grant access to the AD domain.
See “Adding users and groups to an AD domain” (page 36).
4. Create and manage NAS shares on the AD domain. See “Managing shares on an AD domain”
(page 39).
5. Create local administrators for the CIFS server. See “To create Local Administrators for the
CIFS server” (page 41).
NOTE: To create external users or groups on the StoreOnce Backup system (using the User
Management GUI or CLI function), first use the NAS CIFS server tab to set the Authentication mode
to AD, join an AD domain, and create any required users or groups. This is required even when
not using NAS shares as target devices.
Prerequisites
• Domain Name
• Domain Controller running:
Windows server 2003◦
◦ Windows server 2003 R2
◦ Windows server 2008
◦ Windows server 2008 R2
◦ Windows server 2012
◦ Windows server 2012 R2
• User account on Domain Controller, which should be the Domain Administrator or Delegated
user with Domain Administrative rights.
• User account on server running DNS to add entries.
• The system time on the StoreOnce Backup system must be correct and in sync with that of the
domain controller. Using the StoreOnce CLI time commands on the StoreOnce Backup system
to synchronize with a time server ensures accurate time keeping. See the HP StoreOnce Backup
system CLI Reference Guide for details.
IMPORTANT: AD Domain Support: StoreOnce models support configuration in a multi-domain
tree forest but do not support multi-forest domain topologies.
34 NAS functions
Page 35

Adding the StoreOnce device to an AD Domain
To join a domain:
1. Connect to the StoreOnce Web Management Interface and navigate to the NAS—CIFS Server
page.
2. Select the Edit button and choose AD from the drop-down menu.
NOTE: You must manually create an entry for the StoreOnce appliance in the DNS server
so the appliance can be resolved using its domain qualified appliance name. The StoreOnce
appliance will not automatically provide the information when joining the domain.
3. Provide the name of the intended domain, for example, “mydomain.local”.
4. Select Update. If the domain controller is found, a popup box will request credentials of a
user with permission to join the domain.
IMPORTANT: Joining or leaving the domain will result in failure of any backup or restore
operations that are currently running.
5. Provide the credentials (<User Name> and <Password>) of the Domain Administrator or
a delegated user with Domain Administrative rights and select Register.
6. After a short delay (the time is dependent on the topology and size of the AD Domain) the
computer will become a member of the domain and a Success dialog is displayed.
Configuring CIFS Server with AD and CIFS Share with AD domain users 35
Page 36

7. Launch the “Active Directory Users and Computers” management tool (type dsa.msc from
the command line or launch from Administrative Tools) to verify there is an entry for the
StoreOnce device CIFS server and that the StoreOnce Backup system can be “managed”
(Action—Manage from the menu) by the domain.
NOTE: Using Action—Manage might prompt an error message that the RPC server is
unavailable because the StoreOnce appliance does not support all of the management systems
of a Windows server. However, this error does not prevent the management of shared folders.
Adding users and groups to an AD domain
The AD domain management tool interface varies by system. The following portrays one example.
1. Open the active directory management tool. Navigate to the user folder.
2. To create a new group in the AD domain:
• Right click on the Users folder and select Create a New Group.
36 NAS functions
Page 37

• The AD domain address appears at the top of the dialog box (<domainname/users>).
Enter a group name and select Global for group scope and Security for group type. Click
OK. This new group can be added on the CIFS server tab to provide NAS server
permissions or added using the User Management tool to provide StoreOnce device
permissions.
3. To create a new user in the AD domain:
• Right click on the Users folder and select Create a New User.
• Enter the user’s first name and last name, full name, and a logon name. After the logon
name the domain address is listed. This logon name and domain address is used to log
in to access the shares or device (username@domainname).
Configuring CIFS Server with AD and CIFS Share with AD domain users 37
Page 38

• Click Next. Enter a password and password confirmation. If User must change password
at next login is selected and the user logs in through the CLI, the user will be prompted
to change the password (only at the first login; subsequent logins will not require a
password change).
• Click Next. The final screen displays the user logon name and a mention of the required
password change (if that was selected on the previous screen). Click Finish.
4. You can now grant access permissions to either NAS shares only on the NAS CIFS Server tab
or to all StoreOnce features using the User Management tool.
38 NAS functions
Page 39

Managing shares on an AD domain
Now that the HP StoreOnce Backup system is part of a domain and can be managed, it is possible
to create shares and grant access permission to them for domain account users or groups. There
are two ways for users to be granted access permissions to the NAS shares on the CIFS server:
• As remote users configured through the Windows Computer Management tool: Run MMC
and install the computer management plug-in (management console). Once remote users are
configured through the windows computer management tool (which must be run through
MMC), permissions can be applied per share using the StoreOnce GUI.
• As local users with Delegated Admin permissions configured through the HP StoreOnce GUI.
These users have Admin rights to all shares created on the NAS CIFS server.
NOTE: The StoreOnce appliance only supports the Shared Folders utility within the Windows
Computer Management. Any other Windows Computer Management utilities are not supported.
1. Create a share on the Backup system to be used as a backup target by selecting NAS—Share
from the Web Management Interface and clicking Create.
2. Provide a share name and description, then select the CIFS protocol and click Create.
3. The share will start and its status will change to Online.
4. Provide a list of users who can access this share through the Windows Computer Management
tool. Select the Shared Folders—Share option to display the available shares on the StoreOnce
Backup system. In addition to the user configured shares, there will be two “default shares”
called C$ and IPC$. These shares cannot be used for backup.
Configuring CIFS Server with AD and CIFS Share with AD domain users 39
Page 40

5. Select the newly created Backup share and select Properties from the Action menu.
6. Select the Share Permissions tab and Add a user or group of users from the domain, then
specify the level of permission that the users will receive. Finally, select Apply.
40 NAS functions
Page 41

7. It is now possible to access the newly created share from any Windows server on the domain
using the credentials of anyone who has permission to access the share. If a permitted user
is logged into Windows, access to the share is granted automatically with those permissions.
IMPORTANT: When switching from None or User authentication mode to AD authentication
mode, HP recommends that the user logs out and back into the Windows client where the
share is mounted. This ensures the new authentication settings of the CIFS server are enforced.
NOTE: The HP StoreOnce Backup system does not support creating shares from Windows
Computer Management Consoles. Shares must be created from the StoreOnce Management
Console.
To create Local Administrators for the CIFS server
After adding the StoreOnce device to the AD domain, a new Local Administrators section appears
on the lower half of the CIFS server tab. This allows the creation of users with Administrator access
to all shares created on the CIFS server. (The section provides a way of implementing Delegated
Administration, which is not available for the StoreOnce device from the Active Directory
Management tool.)
IMPORTANT: When adding AD domain users through the CIFS server tab, the users are
automatically created as Local Administrators whether or not they are admin users on the AD
domain.
Configuring CIFS Server with AD and CIFS Share with AD domain users 41
Page 42

1. To add a user, click Create User.
2. Enter the domain name and user name and click Update.
Leaving an AD Domain
The user may wish to Leave an AD domain in order to:
• Temporarily leave, then rejoin the same domain.
• Join a different AD Domain.
• Put the StoreOnce Backup system into either No Authentication or Local User Authentication
modes.
The user can click the Leave AD option on the NAS—CIFS Server GUI page to leave. The user can
then rejoin the same domain. If joining a different AD domain or changing modes, the user clicks
the Edit button on the page and selects the new domain or mode.
NFS Server tab
HP StoreOnce Backup systems provide an NFS interface that enables configuration of the HP
StoreOnce Backup system with NFS file shares as target for backups from UNIX and Linux servers.
Two configuration stages, implemented from the StoreOnce GUI, are used to create a file share
that UNIX and Linux users can access.
• Create a list of NFS hosts that can mount the NFS shares.
• Create NFS NAS shares on the StoreOnce Backup system and specify access permissions for
list of hosts, see Creating an NFS share and setting permissions (page 47).
Specifying NFS hosts
1. Log on to the StoreOnce GUI for the appliance.
2. Select NAS.
3. Select the NFS Server tab.
42 NAS functions
Page 43

4. Click Add and provide a Host Name and Description. Click Update.
NOTE: A host with the ‘*' wildcard, added by default, allows any host to access a share.
You can have a maximum of 50 hosts on the NFS server (including the wildcard).
5. Create NFS NAS shares on the StoreOnce Backup system and specify access permissions for
a list of hosts. See Creating an NFS share and setting permissions (page 47).
Connecting to the NAS share on UNIX or Linux
To access the NAS share from a UNIX or Linux server on the network, use the mount command.
The actual syntax of the command depends on the operating system.
IMPORTANT: See the HP StoreOnce Backup system Linux and UNIX Configuration Guide for
more detailed information. Verify the correct mount options to ensure good performance and
deduplication ratio. These options may be different from normal use.
Problems connecting
The following sequence causes problems when connecting to an NFS share:
1. Creating an NFS share and mounting it on a Linux box.
2. Deleting the share on the StoreOnce Backup system without unmounting it from the Linux box.
3. Recreating the share again using the same name.
In this scenario, the Linux client assigns a new set of inodes to the new share, but when trying to
access the old mount point uses the previous set of inodes and cannot connect.
Reboot the host Linux system and the connection will work again.
Shares (NAS)
This page is used to view and manage all NAS target devices (referred to as shares) for both CIFS
and NFS servers.
IMPORTANT: It is important to understand that the HP StoreOnce network share is intended to
be used ONLY by backup applications that “back up to disk”. Do not use the NAS target device
as a drag-and-drop general file store. The one exception to this rule is when using the NAS share
to seed an appliance for replication.
Shares (NAS) 43
Page 44

Creating NAS shares
Users with an Admin login may create NAS shares. The process varies slightly depending upon
whether creating a CIFS or NFS share, see:
• CIFS: Creating a CIFS share (page 45)
• NFS: Creating an NFS share and setting permissions (page 47)
Shares can be configured as version 2 (default) or version 1. The difference is in the maximum
number of files per share permitted: 25,000 for version 1 shares and 1,000,000 for version 2
shares. Configuring a version 1 share is only recommended for replication compatibility with
another appliance on an older software version that only supports version 1 shares. Once
configured, you can change the share version from 1 to 2 but you cannot change from 2 to 1. The
maximum number of shares depends upon the product model and the number of other devices
(including VTL libraries and Catalyst stores) already created. See StoreOnce key
parameters (page 137).
Editing share details
Users with an Admin login may edit the Description, Write Protection, and Secure Erase settings
for existing NAS shares. Write protection prevents access initially or protects data after it has been
backed up for compliance purposes. Data at Rest Encryption cannot be edited; that feature is only
enabled or disabled at the time of share creation.
1. Select the share on the Shares page and click Edit.
NOTE:
The Network Path field is not displayed when you select Edit. However, if you display the
Network Paths tab, you can copy the share path if required. If your StoreOnce Backup system
is configured on a Virtual LAN, this tab will display all the VLAN IP addresses available for
that share.
If the correct license was applied, enable Secure Erase by selecting the number of Overwrite
Passes from the Secure Erase Mode drop down box. This field does not appear until after the
share is created.
2. Make the required changes and click Update.
44 NAS functions
Page 45

NOTE: You can change a share from version 1 to version 2, but you cannot change from
version 2 to version 1. In addition, you cannot change from version 1 to version 2 if replication
mapping is in place; you must first remove the replication mapping, ensure both the source
and target devices are on StoreOnce software version 3.11.0 or higher (upgrade if necessary),
change the source and target shares to version 2, and then reapply the replication mapping.
3. A popup window advises that if you update the Share settings, any backup or restore jobs in
progress will fail. Click Yes (or No).
Applied changes take effect immediately. If the NAS server (service) must restart, a warning
is provided to the user, which they can accept to allow all shares to temporarily go offline.
You cannot change the share name after it is created.
If a share is converted from Read/Write to Read Only, any open items will be forced closed,
which may result in inconsistencies if they are being written to by a backup application. The
user will be warned that this could occur before the change is made.
Deleting share details
Users with an Admin login may delete a share. Select the share in the list and click Delete.
Creating a CIFS share
A note about permissions
Each share has a Permissions tab. The options available on this tab depend on the type of
Authentication selected when you configured the CIFS Server.
• If None (No Authentication) was selected, the Permissions tab is disabled.
• If User Authentication was selected, there will be a list of users. Set the access permissions for
that share for each user in the list to Access or No Access. See Configuring user
authentication (page 32) for an example.
• If AD Authentication was selected, share permissions are managed from the AD Domain. See
Configuring CIFS Server with AD and CIFS Share with AD domain users (page 34) for an
example.
To create a CIFS share
1. Select NAS—Share on the StoreOnce GUI to display the Share page. This page is used to
manage all shares for both CIFS and NFS servers.
2. Click Create.
Shares (NAS) 45
Page 46

3. Provide the following information:
• Name: the name that will be used to identify the share in Windows.
• Description: a text description of the share (optional).
• Access Protocol: select CIFS.
• Share Version: leave as version 2, or change to version 1 if replicating to or from an
existing version 1 share. See “Creating NAS shares” (page 44) for a description of the
share types.
• Write Protection: Only used to prevent further backup to the share. If enabled, any backup
jobs currently using that share will fail.
• Deduplication Enabled: Enables deduplication if the check box is selected (default); unselect
to create a non-deduplication share. Deduplication cannot be enabled or disabled once
the share is created.
• Encryption Enabled: To enable Data at Rest Encryption for the new share, check this box.
This feature requires a special license. If the license is not installed, an information message
is displayed next to the check boxstating Not Licensed. See “Security Features” (page 12)
and “Licensing” (page 12) for more information.
4. Click Create. It will take a few minutes for the status of the new share to go Online.
5. After creating the share, if the correct license was applied the Secure Erase Mode drop down
box appears. Enable Secure Erase by selecting a number of Overwrite Passes. See “Editing
share details” (page 44).
The Network Path details are provided by the Management Console and are displayed in
the format:
<IP address>/<share name>.
It is also possible to connect using:
\\<Fully Qualified domain name>\<share name>.
There may be multiple entries under the Network Path, depending upon how the network was
configured at installation. You can click on Show all network paths or use the Network Paths
tab to display all available IP addresses.
6. If the CIFS server has been configured for User Authentication, select the share in the Shares
list to display the Permissions tab and list the users available on the server who can be assigned
access to NAS target devices. You can amend permissions for individual NAS target devices.
46 NAS functions
Page 47

Click Edit and check the appropriate Access or No Access button. Click Update to apply the
change.
7. The NAS target device is now available as a network drive and you can target it from the
backup application. It can also be mapped as a network drive in Windows.
NOTE: The NAS target device is not optimized for general purpose file storage. The HP
StoreOnce Backup system is a NAS deduplicating appliance that is optimized for backup.
Creating an NFS share and setting permissions
NOTE: Each share has a Permissions tab. The options available on this tab depend upon the
hosts added to the Hosts list during configuration of the NFS Server. On the Permissions tab, set
the access permissions for that share for each host in the list. Available options are: Read/Write
Access, Read-Only Access, or No Access.
1. Log on to the StoreOnce GUI.
2. Select NAS and display the Share tab. This tab is used to manage all shares for both CIFS
and NFS servers.
3. Click Create.
4. Provide the following information and click Create.
• Name: the name that will be used to identify the share in Windows.
• Description: a text description of the share (optional).
• Access Protocol: select NFS.
• Share Version: leave as version 2, or change to version 1 if replicating to or from an
existing version 1 share.
• Write Protection: Only used to prevent further backup to the share. If enabled, any backup
jobs currently using that share will fail.
Shares (NAS) 47
Page 48

• Deduplication Enabled: Enables deduplication if the check box is selected (default); unselect
to create a non-deduplication share. Deduplication cannot be enabled or disabled once
the share is created.
• Encryption Enabled: to enable Data at Rest Encryption for the new share, check this box.
This feature requires a special license. If the license is not installed, an information message
is displayed next to the check boxstating Not Licensed. See “Security Features” (page 12)
and “Licensing” (page 12) for more information.
The Network Path is <IP address>:/nas/<sharename>.
The option to enable Write Protection should only be used to prevent further backup to the
share. If enabled, any backup jobs currently using that share will fail.
5. Set permissions. Select the share and display the Permissions tab. You may set the access
permissions for that share for each host in the list. Check the appropriate box: Read/Write
Access, Read-Only Access, or No Access. At this time, you also have the option to disable
two additional items:
• Root Squash: By default, root_squash is enabled when NAS NFS stores are created. This
squashes the root permissions for the client so that it is not possible to access or create
files on the NFS server as root; the client always has non-root user permission. StoreOnce
3.9.0 introduced an option to allow users to disable NFS root_squash after a NFS store
has been created and gives a client permission to access or create files on the NFS share
as root user.
IMPORTANT: Unless “root” permission is required, do not disable root_squash (by
unticking the checkbox), as it can make the system insecure.
• Secure Ports: By default, secure ports are enabled when NAS NFS shares are created.
By default you can connect on the port below 1024 for NFS (Privileged ports). Disabling
Secure Ports allows connection to the ports higher than 1024 for NFS.
IMPORTANT: Unless required to connect to ports higher than 1024, do not disable
Secure Ports.
48 NAS functions
Page 49

6. Click Create.
A warning is displayed that any backup jobs in progress will fail. Click Yes to continue.
7. The share is now available as a network drive to be mounted from a UNIX or Linux server so
that it may be a target for the backup application. See the HP StoreOnce Linux/Unix
Configuration Guide for more information on mounting shares.
NOTE: The share is not optimized for general purpose file storage. The HP StoreOnce Backup
system is an NAS deduplicating appliance that is optimized for backup.
Once you have created the share, if the correct license has been applied, the Secure Erase
Mode drop down box appears. Enable Secure Erase by selecting a number of Overwrite
Passes. See “Editing share details” (page 44).
Best practices for mounting an NFS share
Use the —o forcedirectio or the —o sync option when configuring an NFS share to prevent
issues with “out of order delivery”. See the HP StoreOnce Linux/Unix Configuration Guide.
NOTE: The sync patches require an rpm update of the operating system before the —o sync or
-o forcedirectio mount options can be specified.
Table 9 NFS share mount options
OptionVersionOperating system
“sync” patch and —o sync mount option10SLES
-o sync mount option11
“sync” patch and —o sync mount option5RHEL
-o sync mount option6
—o forcedirectio option11iv2HP-UX
—o forcedirectio option11iv3
—o forcedirectio option9Solaris
—o forcedirectio option10
—o forcedirectio option5.3AIX
—o forcedirectio option6.1
—o forcedirectio option7.1
Shares (NAS) 49
Page 50

5 Replication functions
Select Replication from the StoreOnce menu item to display all aspects and tasks associated with
replication.
There are four tabs on the main Replication page and two further Navigator options for configuring
VT mappings and NAS mappings. The Status tab is the default.
Users with an Admin login can create mappings and configure replication. Operators can use this
page to view replication settings.
Replication settings
• Status tab (page 52)
• Partner Appliances tab (page 52)
• Local Settings tab (page 57)
• Event History tab (page 60)
Replication mappings
• VT Mappings (Replication) (page 61)
• Recovering a source appliance, VTL devices (page 67)
• NAS Mappings (Replication) (page 70)
• Recovering a source appliance (NAS shares) (page 76)
Replications actions are applied and monitored at appliance level. For a definition of an appliance,
see What is an appliance (page 50).
NOTE: With the current version of the software there are no equivalent CLI commands available
for the tasks described in this section.
HP strongly recommends reading the HP StoreOnce Concepts and Configuration Guidelines, which
is available from the HP web site. These guidelines provide a detailed discussion about replication
deployment strategies, terminology, and include examples using the Replication and Recovery
wizards.
NOTE: A license is required for replication on the target appliance.
What is an appliance?
Replication can take place between different models of StoreOnce Backup systems. The GUI refers
to both Replication Targets and Sources as appliances, so it is important to understand the different
meanings of “appliance” across the product models.
• In a StoreOnce 2700, 4500, 4700, and 4900, the appliance is the physical device or server
that contains the data to be replicated. All mapping is done using the physical IP addresses
of the target and source StoreOnce Backup systems.
• In a StoreOnce VSA, the appliance is the virtual device or server that contains the data to be
replicated. All mapping is done using the IP addresses of the target and source StoreOnce
Backup systems.
• In a StoreOnce 6500 and B6200, the appliance is the Service Set that contains the data to
be replicated. This means that each StoreOnce 6500 or B6200 Backup system has at least
two Service Sets that can be selected as appliances. (A fully expanded HP StoreOnce 6500
or B6200 Backup system would have eight Service Sets.) All mapping is done using the virtual
IP addresses of the target and source Service Sets.
Within this section of the GUI, the terms appliance and Service Set are synonymous.
50 Replication functions
Page 51

How do I identify the IP address of a Service Set?
When configuring replication between different models of StoreOnce Backup systems, be aware
that:
• Replication targets on a StoreOnce 26xx, 2700, 42xx, 44xx, 4500, 4700, and 4900 Backup
system require the IP address of the appliance.
• Replication targets on an StoreOnce VSA Backup system have two virtual NICs supported,
meaning you can have a maximum of two IP addresses for the VSA.
• Replication targets on a StoreOnce 6500 or B6200 Backup system require identification of
the Data VIF IP address of the appropriate Service Sets (also referred to as a node). Each HP
6500 and B6200 Backup system may have up to eight Service Sets (the minimum is two
Service Sets).
NOTE: Service Set Data VIF IP addresses are used for data traffic and are not the same as
the Cluster Management IP address used to log onto the HP StoreOnce Management Console.
You cannot configure the replication targets using the IP address used to log on to the HP
StoreOnce Management Console.
To identify the Data VIF IP from the HP StoreOnce GUI
1. Select the Service Set in the list on the HP StoreOnce page.
2. Locate its Data VIF IP at the bottom of the System Information.
To identify the Data VIF IP from the StoreOnce CLI
Use the net show config command and locate the Node Specific Parameters.
Identify the Network Virtual Data IP entries under each node. The following example is an
extract from the output of the net show config command:
# net show config
----------------------
Network Name: current
Network Description: Management on (2) 1Gb ports (bonded), Data/Replication on (2) 10Gb ports (bonded)
Write Protected: no
DNS Servers: 172.160.10.1
Port Sets: portSet1 portSet2
Management VIF: 172.160.20.1
----------------------
Number of Networks: 2
Number of VLANs configured: 0 out of possible 128
----------------------
Network: subnet1
----------------------
IP Addresses: 192.168.20.60,192.168.20.61,192.168.20.62,192.168.20.63
Net Mask: 255.255.0.0
Domain Name:
Gateway:
Default Network: no
Net Usage: data
What is an appliance? 51
Page 52

VLAN tag:
Port Set: portSet1 with these interfaces: eth5 eth7
Encryption Links:
Bonding Mode: 1 (Active Passive Bonding)
---------------------Network: subnet2
---------------------IP Addresses: 172.160.20.2,172.160.20.3
Net Mask: 255.255.224.0
Domain Name: mydomain.com
Gateway: 172.160.10.2
Default Network: yes
Net Usage: mgmt
VLAN tag:
Port Set: portSet2 with these interfaces: eth0 eth2
Encryption Links:
Bonding Mode: 1 (Active Passive Bonding)
Status tab
The top half of the Status tab contains information about replication throughput and active sessions.
• Replication Throughput Totals: These tables show an average throughput over a period time,
so they will not produce accurate data right away.
• Active Sessions: This identifies the number of source and target jobs that are running, and the
number of source appliances that are connected. This information is useful when monitoring
performance.
The bottom half of the Status tab contains a list of Active Jobs. Click and highlight any of the status
details to display more information about the job.
Partner Appliances (Replication)
The Partner Appliances tab displays the replication status of all Target and Source HP StoreOnce
Backup systems configured for use with this HP StoreOnce Backup system.
52 Replication functions
Page 53

There are three tabs:
• Target Appliances tab (page 53)
• Source Appliances tab (page 55)
• Source Appliance permissions (page 56)
The bottom half of the page displays information about any blackout windows that apply to the
selected appliance.
Target Appliances tab
This tab allows you to view the details of all target appliances. Users with an Admin login can use
the tab to:
• To add a target appliance (administrators only) (page 54)
• To edit or remove a Target Appliance (administrators only) (page 55)
• Run Traceroute (page 55)
NOTE: Although administrators can add Target Appliances on this page, it is not necessary to
do so before mapping configurations because this option is also available when running the
Replication wizard.
Summary appliance details and target appliance parameters
The following status details are shown for both Target and Source appliances.
Table 10 Summary Appliance details
The name of the appliance.Appliance Name
The health of the appliance; this shows you whether the appliance is running or not.Appliance Status
The IP address of the appliance.Appliance Address
The serial number of the appliance.Serial Number
The amount of free space on the appliance.Free Space
Whether the appliance is online or not.Online
The protocol of the appliance software.Protocol Version
Partner Appliances (Replication) 53
Page 54

Click on an appliance to view more detailed status information in the bottom half of the screen,
as described in the following table.
Table 11 Target appliance parameters
Target Appliance tab (some fields are editable).
Appliance Name
Appliance Address
Number
Number
Blackout Window Active
The name that is used to identify the Target Appliance. You specify it on the Local Appliance
tab of the partner appliance.
The product class of the appliance, such as HP 6500 or HP 4700.Product Class
The IP address of the Target Appliance. You specify it when you add the Target Appliance
and can edit it later.
The serial number of the Target Appliance; it cannot be edited.Serial Number
The port number that will be used for command protocol.Command Protocol Port
The port number that will be used for data protocol.Data Protocol Port
Indicates whether the Target Appliance is available or not.Available
Identifies the replication protocol in use.Replication Protocol
The amount of user data stored on the Target Appliance.User Data Stored
Shows the capacity of the Target Appliance.Capacity
Shows the amount of free space on the Target Appliance.Free Space
Shows the software version of the Target Appliance.Software Version
Shows the current system time.System Time
Shows whether a blackout window is currently active or not. This means that no replication
will occur.
Blackout Windows
Any blackout windows that have been specified will be reflected in this weekly calendar.
During these times, the selected Target Appliance is not available for replication.
Administrators may edit and delete blackout windows from here or from the Local Settings
tab.
To add a target appliance (administrators only)
1. Click Add Target Appliance.
Figure 1 Create new target appliance
2. Enter the Target Appliance Address.
54 Replication functions
Page 55

NOTE: If the Target Appliance is on an HP 6500 or B6200 Backup system, enter the Data
VIF IP address of the required Service Set. See How do I identify the IP address of a service
set? (page 51).
3. The default values for the Command and Data Protocol Port Numbers cannot be changed. If
replication needs to take place through a firewall, the network administrator must open (TCP)
ports 9387 (Command Protocol) and 9388 (Data Protocol).
4. Click Add Target Appliance.
To edit or remove a Target Appliance (administrators only)
• Select the appliance and click Edit to edit the Appliance Name, IP address, and protocol port
details of the target appliance.
• Select the appliance and click Delete to remove an appliance from the list of Target Appliances
available to that source.
Run Traceroute
Click Run Traceroute to verify the local appliance can communicate with the target appliance and
identify the number of hops and latency in the routing.
Source Appliances tab
This tab displays the details of all source appliances.
If the HP StoreOnce Backup system also has Replication Target libraries, there may be multiple
Source Appliances.
NOTE: Source Appliances are appliances that have added the local appliance or Service Set
as a Target Appliance. Only Source Appliances currently connected to the Target Appliance are
listed.
The Source Appliances tab is not editable.
Table 12 Source appliance parameters
Source Appliance tab (no fields are editable).
The name of the Source Appliance.Appliance Name
The product class of the appliance, such as HP B6200 or HP 4430.Product Class
The IP address of the Source Appliance.Appliance Address
The serial number of the Source Appliance.Serial Number
Indicates whether the Source Appliance is available or not.Available
The amount of data stored on the Source Appliance.User Data Stored
Shows the capacity of the Source Appliance.Capacity
Shows the amount of free space on the Source Appliance.Free Space
Shows the software version of the Source Appliance.Software Version
System Time
The day of the week and local time (in 24 hour time) of the system. The system time is set
using the CLI time commands; see the HP StoreOnce Backup System CLI Reference Guide
for details.
Blackout Windows
Any blackout windows that have been specified will be reflected in this weekly calendar.
During these times, the selected Source Appliance is not available for replication.
The throttling (bandwidth limiting) setting. See “Bandwidth Limiting tab” (page 59) for details.Throttling (Kbps)
Partner Appliances (Replication) 55
Page 56

Source Appliance Permissions tab
Source Appliance Permissions are disabled by default. In this state, there is no control over mapping
between share and library devices on the Target and the Source Appliances.
This tab contains an Enabled check box that, when selected, allows administrators to lock the ability
to create share and library mappings. When the Replication wizard is run and mappings are
configured, the Target will only have access to a list of sources that are allowed to replicate to it.
The tab also incorporates a wizard that becomes active when an administrator adds a new source
appliance to list, as described in the procedure below.
To configure access permissions to source appliances (administrators only)
1. Click Edit and check the Enabled box.
2. Click Update.
A wildcard entry in the Source Appliances list allows configuration of permissions across all
source appliances. However, this does not set permissions for individual appliances.
56 Replication functions
Page 57

Table 13 Source Appliances parameters
Serial Number
Appliance Name
Appliance Status
Appliance Address
Configured Mappings
The serial number for the required Service Set. This information can be found on the
top-level HP StoreOnce page.
The name of the appliance for which you have specified the serial number and cannot
be altered.
The status of the appliance for which you have specified the serial number and cannot
be altered.
The address of the appliance for which you have specified the serial number and
cannot be altered.
Indicates whether any mappings have been configured on the source appliance. This
is important because any mappings that already exist will be retained regardless of
any access permissions you subsequently set up for libraries and shares on that
appliance.
3. Click Add. A wizard prompts the necessary steps to add a new source appliance to the list.
Provide the serial number of the appliance and specify initial access permissions for all libraries
and all shares on that appliance.
4. Once the appliance is added to the list of Source Appliances, permissions can be configured
for it.
To configure permissions (administrators only)
1. Select the source appliance in the list. There are two tabs; one for Libraries, and one for
Shares.
2. Click Edit. Check the Access box for those shares and libraries to which access should be
granted. These are the shares and libraries that will be displayed when the mapping
configuration step is run in the Replication wizard. It will not be possible to create a new share
or library from the wizard.
3. Click Update to apply the permissions.
Local Settings (Replication) tab
This tab contains three additional tabs that show the settings for the local HP StoreOnce Backup
system:
• General Settings tab (page 58)
• Bandwidth Limiting tab (page 59)
• Blackout Windows tab (page 60)
Local Settings (Replication) tab 57
Page 58

General settings tab
Users with an Admin login may edit and maintain these settings. Other users may only view them.
1. Select the General Settings tab.
2. Click Edit to make the fields editable. See Table 14.
3. Click Apply to apply the settings.
Table 14 General Settings (Replication)
Appliance
Maximum Jobs
Synchronization Progress
Logging
Out of Sync Notification
Settings
The name of the appliance, its current status, and the product class. You can only edit the
appliance name. The default name is the network host name of the appliance (as configured
at installation). You can change this to something more user friendly and easier to identify
the appliance on the Management Console of the local and partner appliances. The name
can be anything meaningful to the user, such as the geographical location of the appliance.
The Appliance Supported Protocol Version shows which versions of replication protocol are
supported, so in the unlikely event of incompatible versions it will be visible to the user.
Replication auto negotiates to the lowest supported protocol on either end.
The maximum number of source and target jobs that can run concurrently. If running backups
at the same time as replication, the default value of target jobs can be reduced to avoid
using too much WAN bandwidth and overloading the target appliance and reserve appliance
performance.
An event is generated each time a mapping goes out of sync and goes back into sync. This
field applies to periodic sync progress updates while the mapping remains out of sync
resulting in emails (if emails are configured) but not SNMP traps. Use these fields to enable
progress logging for Library and Share synchronization and to specify the logging interval.
While the library or share is out of sync, emails are sent periodically indicating how many
slots or entries are still out of sync. This information is also logged to the user Event Log. One
email is sent for each log entry made for each library or share that is out of sync.
Use these fields to specify the amount of time a mapping needs to be out of sync before a
sync issue is shown in the Issue tab. When an event is generated it results in an entry in the
user Event Log and an email and/or an SNMP trap if the appliance is configured to send
these. These notifications are in addition to a standard notification email sent whenever a
mapping first becomes unsynchronized and another when synchronization is achieved.
Configure Replication
Ports
58 Replication functions
Replication ports should only be changed if replication is blocked by a router on the WAN.
The ports must be the same on both source and target appliances. If in doubt, do NOT
change the port configuration.
Page 59

IMPORTANT: If replication takes place through a firewall, the network administrator must open
(TCP) ports 9387 (Command protocol) and 9388 (Data protocol) to allow the replication traffic
to pass to and from the HP StoreOnce Backup systems.
Bandwidth Limiting tab
This tab allows users with an Admin login to apply a general bandwidth setting and configure
bandwidth limiting windows.
Bandwidth limiting can be used to avoid saturating the WAN with low bandwidth replication to
free up bandwidth for other processes and applications. A minimum of 2Mb/s per concurrent job
is recommended. At least 512Kbps per concurrent job is required for reliable operation. These
limits apply to all outbound replication jobs from this local appliance.
1. Display the Bandwidth Limiting tab.
2. Check the General Limit Enabled box. Determine the recommended general bandwidth limit,
which is a simple calculation of:
(Max WAN Speed) x (Max Desired WAN Usage%).
A Bandwidth Limit Calculator is provided on this tab to work out limit values.
3. Click Edit to edit the Bandwidth Limiting Windows.
Configure up to two windows for each day. Use the spinners to select the Start Of Restriction
and End Of Restriction times. Enter the appropriate Bandwidth Limit in each required window.
(If you use the Bandwidth Limit Calculator, enter the value from the Recommended Limit field.)
Check the appropriate Apply First/Second Restriction check boxes. This ensures the specified
times are enabled. If it is not checked, the times are ignored.
NOTE: All settings are applied to the HP StoreOnce Backup system, not for individual jobs.
The Bandwidth Limit windows override the General Limit when the time specified for the
window is active. Outside of Bandwidth Limit windows the General Limit applies.
Local Settings (Replication) tab 59
Page 60

4. Click Apply.
Blackout Windows tab
This option allows users with an Admin login to specify times when replication should not occur,
for example during planned maintenance or heavy network traffic. You can configure multiple
blackout windows.
NOTE: This setting relates to the local appliance in its role as a source or target device. No
replication jobs will start if the Source or Target Appliance for a mapping is in blackout, and any
running jobs for the mapping will be paused.
1. Select the Blackout Windows tab.
2. Click Edit.
3. Check the box next to the required day of the week.
4. The time boxes become editable. Use the spinner menus to select the appropriate hours.
5. Set up as many blackout windows as required.
6. Verify the Apply First Time Restriction box is checked. This ensures the specified times are
enabled. If not checked, the times are ignored.
7. To enable a second blackout window, ensure the Apply Second Time Restriction box is checked.
The second blackout window for each day must occur after the first blackout window for that
day.
8. Click Apply. On the Appliance tab, the calendar for the Source and Target Appliances reflects
the changes.
Pause replication jobs
The Pause Replication Jobs button on the Blackout Windows tab places all replication jobs on hold
immediately. Click a second time to resume replication jobs.
Event History (Replication) tab
This page shows the log of all completed replication events on the appliance.
60 Replication functions
Page 61

This page presents a time and date stamped list of significant replication events with severity status
and associated messages. It also displays source and target details for the replication event. The
most recent information is at the top of the list.
• Select an event in the list to view its details below.
• The Clear Event History button may be used to clear the list.
• The History will be maintained if the HP StoreOnce Backup system is power cycled.
Searching the event history
Click + Show Search Box to display a Filter field and two drop-down menus. Use the right-hand
drop-down menu to filter for Severity, for example, to display all Error messages. Use the middle
drop-down menu to select a column (or All) and then type a search string into the Filter box.
VT Mappings (Replication)
This page displays details of all replication mappings between source and target libraries. Admin
users may use the two wizards on this page to configure replication mappings and recover mappings
after a disaster. (NAS share mappings are managed on a separate page.)
VT Mappings (Replication) 61
Page 62

Use this page to:
• View source and target library mappings (all users), see Source and target library
mappings (page 62).
Admin users may also remove slot mappings and edit slot mappings.
• Run the Replication Wizard to create new mappings (Admin users only), see Running the
replication wizard (virtual tape devices) (page 64).
• Run the Recovery Wizard to restore mappings (Admin users only), see Recovering a source
appliance, VTL devices (page 67).
NOTE: Only administrators can manage mappings. You can only map and replicate libraries
of the same version.
Source and target library mappings
The top part of the VT Mappings page contains a list of all available local libraries. Local libraries
are the libraries configured on this HP StoreOnce Backup system.
• Non-replicating: a library on this HP StoreOnce Backup system with slots not yet mapped for
replication. Replication and Recovery Wizards are available only with non-replicating libraries.
• Replication Source: a library on this HP StoreOnce Backup system with cartridges mapped for
replication. You do not have to map all cartridges in a Replication-Source Library, and the
Replication-Target Library need not contain the same number of cartridges as the
Replication-Source Library.
• Replication Target: a library on this HP StoreOnce Backup system with slots that hold cartridges
replicated from a Replication-Source library. The option is available to recover individual
cartridges from Replication-Target libraries.
62 Replication functions
Page 63

NOTE: When selecting a non-replicating library, you can run the Replication or Recovering
wizard.
• Use the Replication wizard to create slot mappings for the non-replicating library to make the
library a Source library. See Running the replication wizard (virtual tape devices) for more
information.
• Use the Recovery wizard to recover cartridges from a Target Library. See Recovering a source
appliance, VTL devices for more information.
Table 15 Replication library parameters
The name of the library, defined when the library device was created.Name
Replication Role
Mapped/Total Slots
Replication status
The role, which may be Non-replicating, Replication-Source, or
Replication-Target. All library devices are initially Non-replicating until slots
have been configured using this page.
The status of the local library (such as online).Status
The amount of user data stored.User Data Stored
The amount of space used on the disk.Size On Disk
The number of slots that have been mapped out of the total number of slots
configured on the library device.
The emulation type configured for that library.Device Type
The longest time out of sync.Longest Time Out Of Sync
The version number of the library.Library Version
Replication status, which may be Synchronised, Synchronising, or Pending
Synchronisation.
Slot mappings
Select a local library to display slot mappings for that library.
Users with an Admin login may also remove a slot mapping by clicking the Remove button.
Table 16 Slot mapping parameters
Replication-Source or Replication-Target library selected
Slot Mapping Name
Source/Target Appliance Serial
Number
Source/Target Library Name
Blackout Window Active
The slot mapping name. It is created when you run the wizard to define the
grouping of slots that you select.
The name of the Target Appliance to which cartridges will be replicated.Source/Target Appliance Name
The IP address of the Target Appliance to which cartridges will be replicated.Source/Target Appliance Address
Indicates whether a replication link is established with the partner appliance.Source/Target Appliance Online
The serial number of the Target Appliance to which cartridges will be
replicated.
The name of the library to which cartridges will be replicated on the Target
Appliance.
The status of the partner library (such as online).Source/Target Library Status
Time in hours that replication has been out of sync.Time Out Of Sync
Relates to the local appliance in its role as a source or target appliance. No
replication jobs will be started if the source or target appliance for a mapping
are in blackout, and any running jobs for the mapping will be paused.
Shows whether the mapping is synchronized or not.Replication Status
VT Mappings (Replication) 63
Page 64

Slot mapping details
The tabs at the bottom of this page show more detailed mapping information for the selected library
and slot mapping.
Mapping details tab
This tab details mapping details between source and target libraries. If a source library is selected,
it will indicate if Recovery is in process. If a target library is selected, it will indicate if the target
library is visible to the host. All other information is identical for both source and target libraries.
For example, use this tab to determine:
• The number of mapped slots and replication status.
• The average throughput of data.
NOTE: Multiple VTL Library sources can replicate into a single VTL Library target offering
consolidation benefits. This process is known as Fan-in.
Users with an Admin login may edit the Mapping Name on this tab.
Slot details
This tab displays details for each mapped slot in the selected slot mapping. It includes average
throughput data for each slot. When selecting a source library, users with an Admin login can:
• Edit the Target Slot to which a Source Slot is mapped.
• Enable the Recover First checkbox, which enables a user to request that a mapped slot be
recovered from Target to Source, if required (this is sometimes known as reverse replication).
Running the replication wizard (virtual tape devices)
When selecting a non-replicating library, you can run the Replication or Recovery Wizard.
The Replication Wizard is used to create new mappings between non-replicating libraries (which
become Replication Source Libraries) and either existing or new Target Libraries.
IMPORTANT: The Replication Wizard does not allow creation of an encrypted target library. To
replicate from an encrypted Source library, first create the Target library and enable encryption
so the Target library is also encrypted.
1. Create a non-replicating library on the Source Appliance.
2. Create a backup rotation scheme and allow the first full backup to run.
3. Decide how to seed the first full backup on the Target Appliance. Are you seeding across the
WAN or can you colocate the Target Appliance on the same LAN as the Source Appliance?
See the HP StoreOnce Backup system Concepts and Configuration Guide for a more detailed
discussion about seeding.
4. Go to the Replication—VT Mappings page and select a non-replicating library to be converted
to a Replication Source Library.
5. Click Start Replication Wizard. At the Welcome screen, click Next.
64 Replication functions
Page 65

TIP: Click show/hide details box to check how many target appliances are permitted and
the number of target appliances currently configured.
6. Select a Target Appliance from the list and click Next.
NOTE: To select an appliance not yet on the list, click Add Target Appliance. Enter the Target
Appliance IP Address or fully qualified domain name. The default values for the Command
and Data Protocol Port Numbers cannot be edited. (If replication takes place through a firewall,
the network administrator must open (TCP) ports 9387 (Command protocol) and 9388 (Data
protocol) to allow the replication traffic to pass to and from the HP StoreOnce Backup systems.)
Click Add Target Appliance.
See How do I identify the IP address of a service set? (page 51).
7. The wizard then moves to the Select Target Library step. Select a library on the target appliance
and click Next.
VT Mappings (Replication) 65
Page 66

NOTE: To create a new library on the target appliance, click Create New Target Library.
Configure details as done with creating a new library device.
When creating libraries on a target device it is possible to create libraries with 0 (zero) drives.
Attempting to create a library with more drives than those available on the target will fail with
a suggestion that there may be too many drives already in use on the target.
You cannot create a new target library if Source Appliance Permissions is enabled on the
selected target appliance. Instead, the library must first be created on the target before mapping
from the source.
The Replication Wizard does not allow creation of an encrypted target library. To replicate
from an encrypted Source library, first create the Target library and enable encryption so that
the Target library is also encrypted.
8. At the Edit Slot Mapping step, enter a Slot Mapping Name. The slot number and barcodes of
all source cartridges are displayed. A new barcode is generated on the target library (these
barcodes will be overwritten with those of the source when replication starts). By default, all
slots on the Source are selected for mapping and mapped to available slots on the Target
library. To deselect cartridges from this slot mapping configuration, select Unmapped from
the Target Slot Name drop-down menu.
66 Replication functions
Page 67

9. Click Next to display a summary of the replication configuration that you have created.
10. Click Apply to create the slot mapping configuration. Click OK at the Wizard Complete
prompt.
Replication of cartridges will start as soon as the libraries have been synchronised. Look at
the Replication Status field on the Library Details section of the VT Mappings page. It changes
from “Pending Synchronisation” to “Synchronising” to “Synchronized”.
NOTE: If unable to colocate the Target Appliance on the same LAN as the Source Appliance
to improve replication performance, relocate the Target Appliance to the target site as soon
as the cartridges are synchronized.
NOTE: VTLs configured as non-deduplicating can replicate to both deduplicating and
non-deduplicating target libraries. For example, this can be useful to:
• Replicate data that does not deduplicate, such as compressed files.
• Replicate a copy of critical data needed for instant recovery.
Recovering a Source Appliance (Virtual Tape devices)
The Replication Recovery wizard allows Admin users to recover mapping configurations after a
disaster.
VT Mappings (Replication) 67
Page 68

For example: the remote site has lost both the host servers and the StoreOnce system. New hardware
was purchased and installed, and the administrator now wants to recover data to the StoreOnce
Backup system and then restore to the host server. Before the failure, a mapping existed between
a Source Library on the remote site StoreOnce Backup system and a Target Library on the Data
Center StoreOnce Backup system. After the failure, the Source Library is missing but the mapping
may or may not still exist.
CAUTION: If you replace the disks in the source StoreOnce Backup system and keep the original
appliance, the source to target mapping will still exist on the repaired StoreOnce Backup system.
You MUST BREAK this mapping BEFORE carrying out recovery. If the mapping is left unbroken,
the now-blank Source Library (on the replacement disks) will overwrite the data on the Target
Library, effectively losing backup data on both Source and Target Libraries.
1. Create a new non-replicating library on the Source Appliance (either by running the Installation
wizard or by using the Devices page).
2. Go to the Replication–VT Mappings page and select the new non-replicating library.
3. Click Start Recovery Wizard. At the Welcome screen, click Next.
4. At the Select Target Appliance Step, select Add the Target Appliance and provide the IP
address of the previous replication target device.
5. Select the existing Target Library, or the non-replicating library that was the Target Library
before mapping was broken, from which slots should be recovered.
TIP: Use the Click to show/hide details box to view further information about configured
and maximum shares, libraries, and mappings.
68 Replication functions
Page 69

6. If the library is an existing Target Library, select the Slot Mapping that was configured and
click Next. If the mapping was broken and the source library reverted to non-replicating, you
can add a new slot mapping.
If the Target Library supports multiple library Fan In, the library may still be a Replication
Target if other mappings exist. Recover by adding the mapping back to map the unmapped
slots to the new Source Library.
7. All slots in the Target Library are selected by default, but you can deselect any cartridges that
should not be recovered to the Source Library by checking the Pending One off Recovery box.
8. Click Next to display the Summary page.
VT Mappings (Replication) 69
Page 70

9. Click Apply to run reverse replication.
10. As soon as reverse replication completes for each slot, the data may be recovered to the host
using the original backup application. This can take time because ALL the data must reverse
replicate over the WAN link.
11. New backups can now run to the Source Appliance and replication will run normally without
further configuration.
NAS Mappings (Replication)
This page displays details of all replication mappings between source and target shares. Admin
users may use the two wizards on this page to configure replication mappings and recover mappings
after a disaster. (VT library mappings are managed on a separate page.)
Use this page to:
• View source and target share mappings (all users). See Source and target share
details (page 71).
Admin users may also remove share mappings and edit share mappings.
• Run the Replication Wizard to create new share mappings (Admin users only). See Running
the replication wizard (NAS) (page 72).
• Run the Replication Recovery Wizard to recover share mappings. See Recovering a source
appliance (NAS shares) (page 76).
NOTE: Only administrators can manage mappings. You can only map and replicate deduplicating
shares and map shares of the same version.
70 Replication functions
Page 71

NOTE: The above example shows the page layout when mappings were created and a Replication
Source or a Replication Target share is selected. If a non-replicating share is selected, no mappings
are configured and the screen displays the Replication and Recovery Wizards.
Source and target share details
The top half of the NAS Mappings page contains a list of all available NAS shares that were
configured on this HP StoreOnce Backup system.
• Non-replicating: a share on this HP StoreOnce Backup system that has not yet been mapped
for replication. Replication and Recovering Wizards are available only with non-replicating
shares.
• Replication Source: a share on this HP StoreOnce Backup system that has been mapped for
replication.
• Replication Target: a share on this HP StoreOnce Backup system that has been replicated from
a Replication-Source share.
NOTE: When selecting a non-replicating share, you can run the Replication or Recovery Wizard.
• Use the Replication Wizard to create slot mappings for the non-replicating share; it becomes
a Source share. See Running the replication wizard (NAS) (page 72) for more information.
• Use the Recovery Wizard to recover files from a Target share. See Recovering a source
appliance (NAS shares) (page 76) for more information.
Table 17 Local share parameters
DescriptionField
The name of the share, defined when the share was created.Name
Replication Role
Access Protocol
Replication Status
The role, which may be Non-replicating, Replication Source, or Replication
Target. All shares are initially non-replicating until mappings have been
configured using this page.
The status of the local share, such as Online.Status
The amount of user data stored.User Data Stored
The amount of space used on the disk.Size On Disk
The access protocol that was configured when the NAS share was created:
CIFS or NFS.
The longest time out of sync.Longest Time Out Of Sync
The share version number.Share Version
Replication status, which may be Synchronised, Synchronising, or Pending
Synchronisation.
Share mappings
Select a local share to display its mapping.
Users with an Admin login may also remove a share mapping by clicking on the Remove button.
CAUTION: Do not delete a replication mapping while a backup or restore operation is in progress,
because the source device is temporarily taken offline and any backup or restore jobs will fail.
NAS Mappings (Replication) 71
Page 72

Table 18 Share mapping parameters
Replication-Source or Replication-Target share selected
Mapping Name
Source/Target Appliance Online
Number
Source/Target Share Name
Blackout Window Active
The share mapping name. It is created when you run the wizard to create the
share mapping.
The name of the Target Appliance to which entries will be replicated.Source/Target Appliance Name
The IP address of the Target Appliance to which entries will be replicated.Source/Target Appliance Address
Indicates whether a replication link is established with the partner appliance
or not.
The serial number of the Target Appliance to which entries will be replicated.Source/Target Appliance Serial
The name of the share to which entries will be replicated on the Target
Appliance.
The status of the partner share, such as Online.Source/Target Share Status
Relates to the local appliance in its role as a source or target appliance. No
replication jobs will be started if the source or target appliance for a mapping
are in blackout, and any running jobs for the mapping will be paused.
Shows the amount of time in hours that replication has been out of sync.Time Out Of Sync
Shows whether the mapping is synchronized.Replication Status
Share mapping details
The two tabs at the bottom of this page show more detailed mapping information for the selected
share and share mapping.
Mapping Details tab
This tab details mapping details between source and target shares. If a source share is selected,
it will tell you whether Recovery is in process. All other information is identical for both source and
target shares. For example, use this tab to find out:
• The status of mappings.
• The average throughput of data.
Administrators may edit the Mapping Name on this tab.
File Details tab
This tab displays mapping details for each directory and files within it including average throughput
data for each file. You cannot edit any details on this tab, but you can click on any column heading
to sort by that column.
Running the replication wizard (NAS)
The Replication Wizard creates new mappings between non-replicating NAS shares (which become
Replication Source shares) and existing or new Target shares. (See Recovering a source appliance
(NAS shares) (page 76) for information about the Recovery wizard.)
NOTE: NAS replication is a 1:1 relationship from the source to the target. Fan-in, replicating
from multiple sources to a single target (available for VTL and Catalyst replication), is not available
with NAS replication.
1. Create a non-replicating share on the Source Appliance.
2. Allow the first full backup to run.
72 Replication functions
Page 73

3. Decide how to seed the first full backup on the Target Appliance. (See the HP StoreOnce
Backup system Concept Guide.)
• If seeding across the WAN or can colocate the Target Appliance on the same LAN as
the Source Appliance, go to step 4.
• If seeding using physical media:
1. Create the share on the Remote Site share.
2. Map to the NAS share on the Source Appliance and copy the files from the NAS
share to a USB disk.
3. Transport the USB disk to the replication target site.
4. Insert the USB disk into a host server on the same sub-net as the Target Appliance.
Map to the NAS Share on the Target Appliance and copy the files across from the
USB disk at the source site.
4. Go to the NAS Mappings page.
5. Select a non-replicating share to be converted to a Replication Source Share and click Start
Replication Wizard.
6. Proceed to the Select Target Appliance step.
TIP: Click show/hide details box to check how many target appliances are permitted and
the number of target appliances that are currently configured.
7. Select a Target Appliance from the list and click Next.
NAS Mappings (Replication) 73
Page 74

NOTE: To select an appliance not yet on the list, click Add Target Appliance. Enter the Target
Appliance IP Address or fully qualified domain name. The default values for the Command
and Data Protocol Port Numbers may not be edited. (If replication needs to take place through
a firewall, the network administrator will need to open (TCP) ports 9387 (Command protocol)
and 9388 (Data protocol) to allow the replication traffic to pass to and from the HP StoreOnce
Backup systems.) Click Add Target Appliance.
See also How do I identify the IP address of a service set? (page 51).
8. The wizard then moves to the Select Target Share step. Select a share on the target appliance
and click Next.
74 Replication functions
Page 75

NOTE: To create a new share on the target appliance, click Create New Target Share. Set
up the details as you would normally do when creating a new share. You cannot create a
new target share if the appliance to be used as the target has Replication Source Permissions
enabled.
When creating a new share, a warning indicates that it will take a few seconds for the new
share to come online. Click OK.
NOTE: The share version of the source and target NAS shares must be the same. You can
change a share from version 1 to version 2, but you cannot change from version 2 to version
1. In addition, you cannot change from version 1 to version 2 if replication mapping is in
place; you must first remove the replication mapping, ensure both the source and target devices
are on StoreOnce software version 3.11.00 or higher (upgrade if necessary), change the
source and target shares to version 2, and then reapply the replication mapping.
9. Give the Share Mapping a name and click Next.
NAS Mappings (Replication) 75
Page 76

10. The Summary screen is displayed. Click Apply to create the share mapping configuration.
Replication of files will start immediately.
NOTE: If you can colocate the Target Appliance on the same LAN as the Source Appliance
to improve replication performance, relocate the Target Appliance to the target site as soon
as the files are synchronized.
Recovering a Source Appliance (NAS shares)
There are two ways of recovering NAS shares mappings after a disaster.
• Reverse replication using the wizard (page 76)
• Promotion of Target share over the WAN (page 79)
IMPORTANT: If you replace the disks in the source StoreOnce Backup system and keep the
original appliance, the source to target mapping will still exist on the repaired StoreOnce Backup
system. You MUST BREAK this mapping BEFORE carrying out recovery. If the mapping is left
unbroken, the now blank Source Share (on the replacement disks) will overwrite the data on the
Target Share, effectively losing backup data on both Source and Target Shares.
Reverse replication using the wizard
IMPORTANT: If you replace the disks in the source StoreOnce Backup system and keep the
original appliance, the source to target mapping will still exist on the repaired StoreOnce Backup
system. You MUST BREAK this mapping BEFORE carrying out recovery. If the mapping is left
unbroken, the now blank Source Share (on the replacement disks) will overwrite the data on the
Target Share, effectively lose backup data on both Source and Target Shares.
In this example, the remote site lost both the host servers and the StoreOnce Backup system. New
hardware was purchased and installed, and the administrator must recover data to the StoreOnce
Backup system and restore to the host server. Before the failure, a mapping existed between a
Source Share on the remote site StoreOnce Backup system and a Target Share on the Data Center
StoreOnce Backup system. After the failure, the Source Share is missing; the mapping may or may
not still exist.
1. Create a new non-replicating share on the Source Appliance (using the Create button on the
NAS Shares page).
76 Replication functions
Page 77

2. Reverse seed the first full restore. The simplest way to do this is to use a USB disk, as described
below. It is also possible to recover across the WAN, but this may place an unacceptable
load on bandwidth or time availability.
It is possible to reverse seed the first full restore using a USB disk, as follows:
• Map from the host at the target site to the NAS share on the HP StoreOnce Backup system
and copy the share to a USB disk attached to the host.
• Transport the media to the Replication Source site and attach it to a host.
• Map from a host at the source site to the new share on the Replication Source and copy
across the data from the USB disk before running the Recovery Wizard.
3. Go to the Replication—NAS Mappings page and select the new non-replicating share.
4. Click Start Recovery Wizard.
5. At the Select Target Appliance step, select Add Target Appliance and provide the IP address
of the previous replication target device.
6. Select the existing Target. This is the Target NAS share from which files should be recovered.
Click Next.
NAS Mappings (Replication) 77
Page 78

NOTE: If the mapping has been broken, an entry will indicate non-replicating share (instead
of Replication Target).
7. At the Edit Share Mapping step, either adopt the mapping that had been configured or create
a new mapping and click Next.
8. The Summary screen is displayed. Click Adopt to run reverse replication.
78 Replication functions
Page 79

9. As soon as reverse replication completes, the data may be recovered to the host using the
original backup application.
10. New backups can now run to the Source Appliance and replication will run normally without
further configuration.
Promoting a Target Share over the WAN using NAS
In this example, the remote source site lost both the host servers and the StoreOnce system. New
server hardware was purchased and installed, and the administrator must recover data to the
server. The administrator has not installed a new StoreOnce Backup system and is going to recover
data directly to the server from the Data Center StoreOnce appliance over the WAN (which will
take a long time).
NOTE: The procedure described below retains the ability to back up to the Target Share. If this
is not required, an easier solution may be to recover data from the Target Share, which is read-only.
NOTE: Keep in mind that recovering high volumes of data by this method (over the WAN) will
take a considerable amount of time. Recovering data at the data centre is much faster and once
recovered it can be transported to the remote site.
Before the failure, a mapping existed between a Source Share on the remote site StoreOnce Backup
system and a Target Share on the Data Center StoreOnce Backup system. After the failure, the
mapping still exists but the Source Share is missing. The Target Share on the Data Center StoreOnce
Backup system is still in Target Share mode, it has not had its mappings removed.
1. On the Target Appliance in the Data Center, go to the Replication—NAS Mappings page,
select the Target Share, and remove the mapping between it and the lost Source Share.
2. The Target Share becomes a non-replicating share.
3. Make sure the backup application is targeting the newly non-replicating share at the data
centre and recover the data using the backup application at the data center.
4. At this point there is no HP StoreOnce Source Appliance at the remote site. If one is installed
at a later date, reverse recover the data and configure replication as described in Reverse
replication using the wizard (page 76).
NAS Mappings (Replication) 79
Page 80

6 HP StoreOnce Catalyst functions
The following StoreOnce Catalyst functions are available:
• Viewing and managing StoreOnce Catalyst settings, StoreOnce Catalyst (page 81)
• Viewing and managing Catalyst stores, Catalyst Stores (page 87)
For general information about StoreOnce Catalyst, see What is HP StoreOnce Catalyst (page 80).
NOTE: With the current version of the software there are no equivalent CLI commands available
for the tasks described in this section.
IMPORTANT: If Catalyst operations pass through a firewall, the network administrator must open
(TCP) ports 9387 (Command protocol) and 9388 (Data protocol) to allow the Catalyst traffic to
pass to and from the HP StoreOnce Backup systems.
Licensing requirements
OST/Catalyst devices require a license to be used at both source and target but do NOT require
an additional replication license. To use the security features Data at Rest Encryption or Secure
Erase, you must apply a Security license.
OST plug-in
For supported Symantec Netbackup and Backup Exec backup products, a free plug-in application
is required on each backup application media server that will use the Catalyst functionality. This
can be downloaded from https://www.software.hp.com/kiosk. The plug-in required is different
for Netbackup and Backup Exec.
Login credentials are:
User Name: STOREONCE_KIOSK
Password: STOREONCEAPPS
What is HP StoreOnce Catalyst?
HP StoreOnce Catalyst is a StoreOnce function that allows:
• Backup applications to back up data to a target store on the HP StoreOnce Backup system.
Deduplication may occur on the media server or on the HP StoreOnce Backup system.
• Backup applications to copy jobs between HP StoreOnce Backup systems. All configuration
is carried out from the backup application, which makes this an attractive alternative to using
the replication function on the HP StoreOnce Backup system.
This function requires a backup application that supports HP StoreOnce Catalyst. The HP OST
plugins should also be installed on any Media Servers that will be transferring data to the StoreOnce
Backup system. Refer to http://www.hp.com/go/ebs for up-to-date details on supported
applications.
IMPORTANT: Much of the information displayed on the HP StoreOnce Catalyst pages is taken
directly from the backup application. It is strongly recommended to give jobs and media server
groupings names on the backup application that will be meaningful when displayed on the
StoreOnce Catalyst pages.
80 HP StoreOnce Catalyst functions
Page 81

Benefits of HP StoreOnce Catalyst
• The backup application is in full control of data for the full lifecycle of the backup data.
• The backup application has full visibility of all items and jobs on the HP StoreOnce Backup
system.
• Deduplication can occur on either the media server or HP StoreOnce Backup system, which
ensures efficient use of the available bandwidth.
• There is no limiting geometry, such as cartridges for VTL libraries.
• There is no enforced limit on the number of items within a store.
• Copy jobs are instigated from the application and have none of the complexities of replication
mapping.
• Space reclamation is much more automated and easier to implement if catalyst devices types
are used.
StoreOnce Catalyst terminology
• StoreOnce Catalyst: the name of the StoreOnce function.
• StoreOnce Catalyst stores: the targets/device types in which backups are stored on the HP
StoreOnce Backup system.
• StoreOnce Catalyst items: the items stored in the StoreOnce Catalyst stores on the HP StoreOnce
Backup system.
• StoreOnce Catalyst clients: the generic term for applications that connect using the StoreOnce
Catalyst interface.
• Data jobs: any backup or restore job.
• StoreOnce Catalyst Optimized Backups: one of the main advantages of HP StoreOnce Catalyst
is that deduplication may occur on either the media server or the HP StoreOnce Backup system.
If deduplication occurs on the media server, only unique data is sent to the HP StoreOnce
Backup system and a low bandwidth network link is adequate. If the media server sends all
the data and deduplication is carried out on the HP StoreOnce Backup system, a high
bandwidth network link is required. It is often faster to deduplicate on the media server due
to the combined CPU power of multiple media servers and reduced network traffic. However,
actual performance varies depending upon the data and disk I/O speeds.
• Copy jobs: allow backup applications to create true copies of the data and not mirror images.
The backup application specifies the store on the source StoreOnce Backup system for the
outbound copy job and a target store on the destination StoreOnce Backup system for the
inbound copy job. Once copied, the two versions are independent of each other; on either
the source or destination StoreOnce Backup system data may subsequently be deleted, moved,
or added to, as required, from the backup application.
• StoreOnce Catalyst Optimized Copy: all copy jobs are optimized. This means that the copy
job is completed in a bandwidth-efficient manner. The two stores negotiate so that only unique
data is transferred.
StoreOnce Catalyst page
This page has a number of tabs that provide access to the following StoreOnce Catalyst functions:
• StoreOnce Catalyst status tab (page 82)
• StoreOnce Catalyst settings tab (page 83)
• StoreOnce Catalyst clients tab (page 84)
StoreOnce Catalyst terminology 81
Page 82

• StoreOnce Catalyst blackout windows tab (page 85)
• StoreOnce Catalyst bandwidth limiting windows tab (page 86)
Select StoreOnce Catalyst from the Navigator to display the StoreOnce Catalyst page and associated
tabs.
NOTE: Click + to expand the StoreOnce Catalyst topic in the Navigator and access the Catalyst
Stores topic.
StoreOnce Catalyst Status tab
The Status tab displays details about:
• StoreOnce Catalyst Status and Protocol Versions
• StoreOnce Catalyst Copy and Data Job Throughput Totals
• Active Sessions
Details refresh every 10 seconds, so this information provides a useful overview of Catalyst activity
on the StoreOnce Backup system. The data displayed on this status page is generally for information
purposes only; do not make inferences based on the values shown.
Table 19 Throughput totals and active sessions
DescriptionField
The left-hand column shows throughput averages for Catalyst Copy and Data Jobs.StoreOnce Catalyst
Copy and Data Job
Throughput Totals
(recent averages)
Active Sessions
Bandwidth indicates the actual physical network bandwidth being used. Throughput indicates
the perceived or logical network bandwidth used (it includes the efficiency achieved through
deduplication). These are aggregate numbers (). The throughput numbers should correlate with
those shown on the graphs on the Activity page.
The right-hand column shows the number of jobs of each type that are running. See StoreOnce
key parameters (page 137) for more information about the maximum number of different job
types.
Data Jobs Running shows the number of backup and restore jobs that are running on the
appliance.
Outbound Copy Jobs Running shows the number of copy jobs running to another appliance.
Inbound Copy Jobs Running shows the number of copy jobs coming in from another appliance.
More about Job types
Different backup applications can use different terminology for data transfers. From a Catalyst
perspective, if data is being moved between the HP StoreOnce Backup system and a media or
application server, this is a data job. If the transfer is between two HP StoreOnce Backup systems,
this is a Catalyst Copy job. For Copy jobs, the HP StoreOnce Backup system is responsible for all
data movement (although the process is initiated by the backup application software). For data
jobs the backup application is responsible for the data movement.
82 HP StoreOnce Catalyst functions
Page 83

If the copy job numbers are high (close to the maximum), no user action is required. Copy activities
happen under the control of the StoreOnce Backup system and it will optimize the queuing and
running of jobs based on the resources available. If the Data job count starts getting high, the HP
StoreOnce Backup system is being loaded quite heavily. You may see jobs failing to start or running
slowly (although the aggregate performance across the many jobs should still be high) due to
insufficient resources being available.
NOTE: The maximum data jobs value is not guaranteed in all cases. In some situations, such as
when heavily loaded, the actual maximum may be less (based on resources available to the box
at that time).
StoreOnce Catalyst Settings tab
The StoreOnce Catalyst Settings tab is used to view the settings that apply to Catalyst functions
and jobs for all nodes on the HP StoreOnce Backup system. Users with an Admin login may also
edit these settings.
IMPORTANT: First enable Client Access Permission Checking on this page to assign permissions
when subsequently configuring clients and stores. (If you do not set permissions, all clients can
access all stores.) Client access is also enabled in the ISV backup software.
To edit settings (administrators only)
1. Click Edit.
2. Amend fields as required and click Update.
Table 20 StoreOnce Catalyst Settings fields
DescriptionField
Client Access Permission Checking
Maximum Concurrent Outbound Copy
Jobs
Maximum Concurrent Data and
Inbound Copy Jobs
When enabled, the Clients tab is active and the Permissions tab on the Stores
page is active. These tabs enable control over which clients (backup
applications) can access which stores on the StoreOnce Backup system. If you
do not set permissions, all clients will be able to access all stores.
The maximum number of outbound copy jobs that can be processed
concurrently. Copy jobs are placed in a queue and processed as soon as
volume of jobs and any configured blackout windows or bandwidth limiting
allow. The backup application polls the HP StoreOnce Backup system to identify
when copy jobs are complete. It is recommended to limit the maximum number
of concurrent outbound copy jobs to 1 per 512 kbps of available bandwidth.
The maximum number of data and inbound copy jobs that can be processed
concurrently. Blackout windows and bandwidth limiting do not apply to these
jobs.
This defaults to 9387 and cannot be edited.Command Protocol Port Number
This defaults to 9388 and cannot be edited.Data Protocol Port Number
StoreOnce Catalyst page 83
Page 84

IMPORTANT: If Catalyst operations pass through a firewall, the network administrator must open
(TCP) ports 9387 (Command protocol) and 9388 (Data protocol) to allow the Catalyst traffic to
pass to and from the HP StoreOnce Backup systems.
StoreOnce Catalyst Clients tab
This tab is only active if the Client Access Permission Checking box on the Settings tab is enabled.
It allows setting up a list of clients (backup applications) that will be displayed on the Permissions
tab to restrict client access to a store.
NOTE: The client backup application must first be configured with a client identifier before you
can add details to this tab. See the client backup application documentation for more information
about configuring identifiers.
To add a client (administrators only)
1. Click Add.
2. Enter the name of the client and a description.
NOTE: The client application must be configured with a client identifier, such as
MediaServer1. This identifier is entered in the Client field. Note that no spaces are allowed
in the Client field.
3. Check the features that you desire (if they are supported by the client application):
• Enter a password and confirm the password.
• Check Allow Store Creation.
• Check Manage Server Properties.
• Check Manage Client Permissions.
NOTE: Only enable features on the Clients tab that are supported by your client application.
4. Click Update.
Table 21 StoreOnce Catalyst Clients fields
Client
84 HP StoreOnce Catalyst functions
DescriptionField
The client identifier is a user-defined string set through the backup application
software which can be used on the HP StoreOnce Backup system to identify a
client. For example, there may be multiple media servers sharing the same ID;
Page 85

Table 21 StoreOnce Catalyst Clients fields (continued)
DescriptionField
so, the identifier is not a client machine name or a name generated by the
software. Best practice is to ensure that the name created on the backup
application is meaningful for use in searches on the StoreOnce Backup system.
Description
Password
Allow Store Creation
Manage Server Properties
Manage Client Permissions
This is a description that can be included on the StoreOnce Backup system
when the administrator adds a client.
If the client backup application supports this, you can provide a client password
(client passwords are optional and can also be left blank). Once set, any client
that connects will need to supply the password along with their client id. Refer
to your client application's documentation for further details.
If the client application supports it, you may also enable clients to create stores
remotely from this tab. Refer to your client application's documentation for
further details.
If the client backup application supports this, you can manage the server from
the client backup application rather than the HP StoreOnce Backup system.
When enabled, four settings can be managed through the backup application:
Blackout Windows, Throttling Windows, Max number of Data jobs, and Max
number of Copy Jobs. Refer to your client application's documentation for
further details.
If the backup application supports this, you can remotely manage which Client
IDs exist in the system and which Client IDs are able to access which stores.
Only enable this if the backup software supports this feature. Refer to your client
application's documentation for further details.
WARNING! When enabled, this feature allows anyone with access to the
backup application the ability to change the Client ID settings, thereby giving
users on one system control over and full access to all backup targets.
NOTE: A Client ID must be defined from the GUI and then enabled for this
feature before a backup application using that Client ID can connect to the
StoreOnce appliance and further manipulate data for other Client IDs.
StoreOnce Catalyst Blackout Windows tab
The fields at the top of this tab show the System Time and whether a Blackout Window is currently
active or not. The information below displays the start and stop times of any blackout windows
that have been configured for outbound copy jobs.
Users with an Admin login may specify times when outbound copy jobs should not occur, for
example during planned maintenance or heavy network traffic. Multiple blackout windows may
be configured.
Blackout windows override any attempts by ISV software to perform Catalyst Copies. ISV software
will retry continually until a blackout window is finished.
NOTE: Blackout windows are available on most StoreOnce functions to ensure all StoreOnce
services run efficiently and do not compete for resources. For example, if running backup, restore,
replication, and Catalyst Store operations with no break (24 hours a day), housekeeping cannot
complete and performance will suffer. This is a complex subject; see also HP StoreOnce Backup
system Concepts and Configuration Guidelines.
StoreOnce Catalyst page 85
Page 86

To edit StoreOnce Catalyst blackout windows (administrators only)
1. Select the Blackout Windows tab.
2. Click Edit.
3. Check the box next to the required day of the week.
4. The time boxes become editable. Use the spinner menus to select the appropriate hours.
5. Set up as many blackout windows, as required.
6. Make sure the Apply First Time Restriction box is checked. This ensures the times that have
been specified are enabled. If it is not checked, the times are ignored.
7. To enable a second blackout window, make sure the Apply Second Time Restriction box is
checked. The second blackout window for each day must occur after the first blackout window
for that day.
8. Click Apply.
To pause copy jobs (administrators only)
The Pause Copy Jobs button on the Blackout Windows tab places all outbound copy jobs on hold
immediately. Click Pause Copy Jobs a second time to resume outbound copy jobs.
StoreOnce Catalyst Bandwidth Limiting Windows tab
There are four sections to this tab, all of which relate to bandwidth limiting on outbound copy jobs.
• Status: details the current bandwidth limit, if any.
• General bandwidth limit: administrator users may enable and apply a general bandwidth
limit. This is a simple calculation of:
(Max WAN Speed) x (Max Desired WAN Usage%).
• Bandwidth limit calculator: provided to help work out limit values for the general bandwidth
limit and the bandwidth limiting windows.
• Bandwidth limiting windows: administrator users may specify certain times when different
bandwidth limits may apply. Any bandwidth limit entered will overwrite the general bandwidth
limit.
Bandwidth limiting can be used to avoid saturating the WAN to free up bandwidth for other
processes and applications. A minimum of 2Mbps per concurrent job is recommended. At least
512Kbps per concurrent job is required for reliable operation. These limits apply to all outbound
copy jobs from this .
86 HP StoreOnce Catalyst functions
Page 87

To edit bandwidth limiting (administrators only)
1. Display the Bandwidth Limiting Windows tab.
2. Check the General Limiting Enabled box and determine the recommended general bandwidth
limit, which is a simple calculation of:
(Max WAN Speed) x (Max Desired WAN Usage%).
Use the bandwidth limit calculator provided on this page to work out limit values, if required.
3. Click Edit to edit the Bandwidth Limiting Windows.
Configure up to two windows for each day.
Verify the appropriate Apply First/Second Restriction check boxes are checked. This ensures
the specified times are enabled. If not checked, the times are ignored. Then manually enter
the required Bandwidth Limit in each required window.
Use the bandwidth limit calculator provided on this page to work out limit values, if required.
NOTE: All settings are applied to the HP StoreOnce Backup system and not for individual
jobs. The Bandwidth Limit windows override the General Limit when the time specified for the
window is active. The General Limit applies outside of Bandwidth Limit windows.
4. Click Apply.
Catalyst Stores page
Select StoreOnce Catalyst—Stores from the Navigator to display the Stores page and tabs.
The top half of the Stores page shows all stores configured for the appliance. Click on a store to
display its details in the lower half of the page. Users with an Admin login may edit these settings
or delete stores, and may also create new stores.
The lower half of the page has the following tabs:
• Store Details tab (page 88), includes functions for creating and managing stores
• Permissions tab (page 90)
Catalyst Stores page 87
Page 88

• Item Summary tab (page 90)
• Data jobs tab (page 92)
• Outbound copy jobs tab (page 95)
• Inbound copy jobs tab (page 99)
Table 22 Store fields
Name
Status
Items
User Data Stored
Size On Disk
Dedupe Ratio
Store details tab
The Store Details tab displays the details that were specified when the store was created. Users
with an Admin logon may create and edit store details and delete stores.
DescriptionField
The name of the store. This may be created manually through the HP StoreOnce Backup system
or generated by the backup application.
The version of the store.Version
The status of the store. When you create a store you will see the status change until it becomes
Online.
The date and time that the store was created.Created
The number of Catalyst items contained within the store.Number of Catalyst
The amount of data stored. This is the amount of data that the user has backed up and reconciles
with the logical data recorded on the backup application.
The size of the store on the disk. This is the physical disk space consumed; the actual size after
deduplication.
The dedupe ratio which is the ratio of duplicate data against new data identified in the data
job.
88 HP StoreOnce Catalyst functions
Page 89

Table 23 Store details
DescriptionField
Name
Data Job Retention
Period (Days)
Inbound Copy Job Log
Retention Period
(Days)
Outbound Copy Job
Log Retention Period
(Days)
Transfer Policy
Secondary Transfer
Policy
The name of the store. This may be created manually through the HP StoreOnce Backup system
or generated by the backup application.
A description for the store.Description
The retention period for information about data jobs. This information is displayed on the Data
Jobs tab, which provides a log of all data job activity. The default is 90 days.
The retention period for information about inbound copy jobs. This information is displayed
on the Inbound Copy Jobs tab, which provides a log of all data job activity. The default is 90
days.
The retention period for information about outbound copy jobs. This information is displayed
on the Outbound Copy Jobs tab, which provides a log of all data job activity. The default is
90 days.
This may be High or Low.Primary (Default)
• High means all data is sent from the media server and deduplicated on the HP StoreOnce
Backup system. This can also be described as target-side deduplication.
• Low means that the media server deduplicates the data and sends only unique data. This
can also be described as source-side deduplication.
The primary transfer policy is the default transfer policy for the server. Each media server may
be configured individually to use the most efficient transfer policy. As long as the two transfer
policies have different values, the media server will determine which is the most bandwidth
efficient transfer policy to use.
This may be High or Low (see definitions in row above) and is normally the opposite to the
Primary transfer policy so that the media server can choose to use which is most appropriate.
However, if you wish to enforce the transfer policy that the media server uses, set both Primary
and Secondary transfer policies to the same value.
Secure Erase Mode
Once the library is created and the correct license is applied, the Secure Erase Mode box
appears on the Store Details tab. The selection box defaults to None, meaning Secure Erase
is disabled. To enable Secure Erase, select the preferred number of Overwrite Passes (1, 3,
5, or 7). If enabled, this feature allows you to securely erase confidential data that may have
unintentionally been backed up as part of a regular backup job. See “Security
Features” (page 12) and “Licensing” (page 12) for more information.
To create a new store (administrators only)
1. Click Create at the top right of the StoreOnce Catalyst Stores page.
2. Provide the store details as described in Table 23 (page 89).
NOTE: If the proper license was applied, an Encryption Enabled check boxis displayed. To
enable encryption for the new store, you must do it at this time by checking the Encryption
Enabled box. See “Security Features” (page 12) and “Licensing” (page 12) for more
information.
When you have completed the store details, click Create.
Catalyst Stores page 89
Page 90

3. The store is created and displayed in the Stores list where its status changes from Creating to
Online. To enable the Secure Erase feature (if you have a license), see “To edit store details
(administrators only)” (page 90).
To edit store details (administrators only)
1. Select the store in the list to display its details and then click Edit.
2. Amend details as appropriate and click Update to apply them.
NOTE: Once the store is created and if the proper license is applied, a Secure Erase Mode
box is displayed. If enabled, this feature allows you to securely erase confidential data that
may have unintentionally been backed up as part of a regular backup job. See “Security
Features” (page 12) and “Licensing” (page 12) for more information.
To delete a store (administrators only)
Select the required store and then click on Delete in the Store Details tab to delete it. You will be
prompted to confirm that this is what you wish to do; click Delete to delete the store, or click Cancel
to cancel the command.
Permissions tab (administrators only)
This tab is only active if the Client Access Permission Checking box has been enabled on the Settings
tab. The Client list is only populated with individual clients or client groupings if you configured
clients on the Clients tab.
You can set the Physical Data Size Quota and Logical Data Size Quota (on the Store Details tab)
to use in conjunction with Client-Permissions. This allows you to effectively define how much space
a particular user is allowed to use on the HP StoreOnce Backup system. This may be useful with
many users using the same system and you wish to control how much disk space is available to
individual users.
1. Click Edit to change the permissions.
2. The default setting is No Access, which means that the client cannot access the store for data
or copy jobs. Click the appropriate Access button for the client(s) who should have access,
then click Update.
Item summary tab
This tab provides summary details of each item in the store.
• Use the filter options to locate the required item(s).
• By default, 50 items are displayed per page. This can be changed from the Items Per Page
drop-down. Use the scroll bar to scroll through all items on the page or use the Prev or Next
buttons to display more pages.
• Once items are displayed, Admin users may use the Delete button to delete a selected item.
NOTE: This is not recommended. It is better to let the backup application remove items to
ensure integrity within backup catalog. Only use Delete as a last resort.
• All users may use the buttons under the item details to show Related Data Jobs, Outbound
Copy Jobs, or Inbound Copy Jobs for the selected item.
90 HP StoreOnce Catalyst functions
Page 91

NOTE: This tab provides a report; it is not automatically refreshed.
1. If necessary, click + to display the filter options.
Check the boxes against the options that you wish to use. Specify as many options as possible
to narrow the search results. Wild cards or boolean logic (AND/OR filters) are not supported.
• The item name is a unique identifier that is always defined on the backup application.
• Sub-string matches are supported, so the filter will return any item that contains the
character string that has been entered. With Item Name you can also specify that it should
be an Exact Match.
• With the Created and Last Modified fields, enter a range of dates.
• The Tag Lists allow you to filter any tags that the client may have added to the data. You
may enter as many tags as required; they should be space separated, with no commas.
If you leave All Match unchecked, the filter will retrieve all items that have any of the tags
specified. If you check All Match, it will retrieve only those items that have all the tags
specified.
2. Click Show Items.
3. A report listing items is displayed.
Table 24 Item summary fields
DescriptionField
The name of the item. This is the name that is generated by the backup application.Item Name
The date that the item was created.Created
The date that the item was last modified.Last Modified
Catalyst Stores page 91
Page 92

Table 24 Item summary fields (continued)
DescriptionField
A list of any tags to include or exclude when searching for the item.Tag List
The size of the data within the item.Data Size
4. Click on an item within a list to display further details about it in the lower part of the page.
Table 25 Item summary details
DescriptionField
The name of the item. This is the name that is generated by the backup application.Item Name
The date that the item was created.Created
A list of any tags that are attached to this item.Tag List
The date that the item was last modified.Last Modified
The size of the data within the item.Data Size
The version of the item. Currently, this is always 1.Version
Meta Data Size
Data jobs tab
This tab provides a log with details about data jobs for the selected store.
• Use the filter options to locate the required job(s).
• By default, 50 items are displayed per page. This may be changed from the Items Per Page
drop-down. Either use the scroll bar to scroll through all items on the page or use the Prev or
Next buttons to display more pages.
• Values that you set in Settings control how long data jobs are retained for (default is 90 days).
NOTE: This tab provides a report; it is not automatically refreshed.
The size of the meta data associated with the item. Meta data is created by the backup
application.
The dedupe block size. Currently, the block value is always Variable.Dedupe Block Size
92 HP StoreOnce Catalyst functions
Page 93

1. If necessary, click + to display the filter options.
Check the boxes against the options that you wish to use. Specify as many options as possible
to narrow the search. Wild cards and boolean logic (AND/OR filters) are not supported.
• The name of the item is a unique identifier that is always defined on the backup
application. Similarly, the client name is defined on the backup application. Best practice
is to ensure that client names are also meaningful for use in searches on the StoreOnce
Backup system.
• Sub-string matches are supported, so the filter will return any item that contains the
character string that has been entered. With Item Name and Client you can also specify
that it should be an Exact Match.
• With the Start Time and End Time fields, enter a range of dates and times.
• Select a Status which may be Running, Completed or Cancelled.
2. Click Show Jobs.
3. A report listing data jobs is displayed. Use the Sort Results option to sort the results
alphabetically.
Catalyst Stores page 93
Page 94

Table 26 Data job fields
DescriptionField
Item Name
Data Written
Write Throughput
The name of the item within data job. This name is created by the backup application.
Each data job may have multiple items.
The status of the data job item, which may be:Status
• Running: in progress
• Completed: the item has completed successfully, this does not mean the data job has
completed, only the item, and does not reconcile with the backup application job
completion status
• Cancelled: the Status Information provides more details, for example, the data
connection has been lost between the HP StoreOnce Backup system and the media
server (this is unlikely to occur)
• Unexpected error: the StoreOnce Backup system has experienced a problem whole
processing the item
• Insufficient disk space: it will be necessary to clear some disk space or add more storage
• Link failure: IP connectivity has been lost and the backup application must retry the job
• System shutdown: System has been shut down
NOTE: The backup application must be configured to tidy up any incomplete or orphaned
items before retrying the job.
The amount of user data that was written. This reconciles with the information in the backup
application's log, but note that a backup job may span multiple items.
The write throughput speed. The first figure, expressed in MB/s, is the logical bandwidth;
the second figure, expressed in Mb/s is the physical bandwidth consumed. The %
bandwidth saving depends upon whether the store has been configured for source-side
deduplication with a low-bandwidth transfer policy, or target-side deduplication with a
high-bandwidth transfer policy. See Store Details tab (page 88).
Read Throughput
Client Identifier
The amount of user data that was read.Data Read
The read throughput speed. This only has one value because read throughput is always
high throughput without any % saving.
The client that initiated the data job, as defined on the backup application. The IP address
in the brackets is for information and not part of the client name. It is best practice to
ensure that a meaningful name is given to the client within the backup application. If no
client was defined on the backup application, only the IP address is shown.
The time the job started.Start Time
The time the job ended.End Time
94 HP StoreOnce Catalyst functions
Page 95

4. Click on an item within a list to display further details about it in the lower part of the page.
Table 27 Data job details
DescriptionField
Item Name
Status
Data Written
The name of the item within data job. This name is created by the backup application.
Each data job may have multiple items.
The status of the data job item, as described in the previous table.
NOTE: The backup application must be configured to tidy up any incomplete or orphaned
items before retrying the job.
Status information, as appropriate to the Status reported.Status Information
The time the job started.Start Time
The time the job ended.End Time
A name that identifies the client user who created the item.Client Identifier
Displays the IP address of the server that created the item.Client Address
The name of the application that created the item.Application Identifier
The deduplication ratio.Deduplication Ratio
The amount of user data that was written. This reconciles with the information in the backup
application's log, but note that a backup job may span multiple items.
The length of time that data was written in MB/s.Write Duration
The write throughput speed, expressed in MB/s, is the logical bandwidth.Write Throughput
The amount of data transferred.Data Transferred
Bandwidth Saving
Read Throughput
Outbound copy jobs tab
This tab provides a log with details of all outbound copy jobs for the selected store.
• Use the filter options to locate the required job(s).
• By default, 50 items are displayed per page. This may be changed from the Items per Page
drop-down. Either use the scroll bar to scroll through all items on the page; or use the Prev or
Next buttons to display more pages.
• Values that you set in Settings control how long outbound copy jobs are retained for (default
is 90 days).
NOTE: This tab provides a report; it is not automatically refreshed.
The bandwidth utilisation in Mb/s. This is the physical bandwidth consumed.Bandwidth Utilisation
The amount of bandwidth saved. The % bandwidth saving depends upon whether the
store has been configured for source-side deduplication with a low-bandwidth transfer
policy, or target-side deduplication with a high-bandwidth transfer policy. See Store Details
tab (page 88).
The amount of data read.Data Read
The length of time that data was read in MB/s.Read Duration
The read throughput speed. Read throughput is always high throughput without any %
saving.
Catalyst Stores page 95
Page 96

1. If necessary, click + to display the filter options.
Check the boxes against the options that you wish to use. Specify as many options as possible
to narrow the search. Wild cards and boolean logic (AND/OR filters) are not supported.
• The name of the item is a unique identifier that is always defined on the backup
application. Similarly, the client name is defined on the backup application. Best practice
is to ensure that client names are also meaningful for use in searches on the StoreOnce
Backup system.
• Sub-string matches are supported, so the filter will return any item that contains the
character string that has been entered. With Item Name and Client you can also specify
that it should be an Exact Match.
• With the Start Time and End Time fields, enter a range of dates and times.
• Select a Status which may be Pending, Running, Paused, Completed, or Cancelled.
2. Click Show Jobs.
3. A report listing outbound copy jobs is displayed. Use the Sort Results option to sort the results
alphabetically.
Table 28 Outbound copy job fields
DescriptionField
Item Name
Status
The name of the item being copied from the outbound copy job. This name is created by
the backup application.
The status of the outbound copy job, which may be Queued, Paused, Running, Cancelled,
or Completed. If the status information displays —, no further information is available.
NOTE: The backup application must be configured to tidy up any incomplete or orphaned
items before retrying the job.
96 HP StoreOnce Catalyst functions
The amount of data to be copied in the copy job.Data Size
The copy speed.Copy Throughput
Page 97

Table 28 Outbound copy job fields (continued)
DescriptionField
Target Appliance
Target Store
Target Item Name
Client Identifier
The address of the target server. The target is the other StoreOnce Backup system to which
the job is being copied from the this HP StoreOnce Backup system. All target details are
specified by the backup application when the outbound copy job is created.
The name of the target store on the StoreOnce Backup system to which the job is being
copied.
The name of the target item on the StoreOnce Backup system to which the job is being
copied. All item names are defined by the backup application.
The client that initiated the outbound copy job. The client name is defined in the backup
application.
The time the job was queued.Queued Time
The time the job started.Started Time
The time the job ended.Stopped Time
Catalyst Stores page 97
Page 98

4. Click on an item within a list to display further details about it in the lower part of the page.
Table 29 Outbound copy job fields
DescriptionField
Item Name
Status
Status Information
Client Identifier
Time
The name of the item being copied from the outbound copy job. This name is created by
the backup application.
The status of the outbound copy job, which may be Queued, Paused, Running, Cancelled,
or Completed. If the status information displays —, no further information is available.
NOTE: The backup application must be configured to tidy up any incomplete or orphaned
items before retrying the job.
Status information. This will be a — unless the job has been cancelled or paused. See
System Information messages (page 103) for more information about events that may cause
a job to be cancelled or paused.
The percentage of the copy job that has been completed.Percent Complete
The client that initiated the outbound copy job. The client name is defined in the backup
application.
Displays the IP address of the server that created the item.Client Address
The name of the application that created the item.Application Identifier
The time the copy job was queued.Queued Time
The time the copy job was started.Started Time
The time the job ended.Stopped Time
The estimated completion time, if the copy job is still running.Estimated Completion
Target Appliance
Target Store
Target Item Name
Source Item Size
Source Item Last
Modified
Offset
Size
Copy Offset
The address of the target server. The target is the other StoreOnce Backup system to which
the job is being copied from the this HP StoreOnce Backup system. All target details are
specified by the backup application when the outbound copy job is created.
The name of the target store on the StoreOnce Backup system to which the job is being
copied.
The name of the target item on the StoreOnce Backup system to which the job is being
copied. All item names are defined by the backup application.
The copy speed.Copy Throughput
The size of the source item to be copied; this may be larger than the data size value (but
no smaller).
The date that the source item was last modified. This is useful if you need to check whether
the source item might have been modified during the copy attempt. An error message is
also generated if the source item is modified whilst copying.
This identifies where the data to be copied occurs within the source item.Source Item Copy
This identifies the size of the data to be copied within the source item.Source Item Copy
This identifies where the data to be copied should be placed within the destination item.Destination Item
The amount of time taken to copy the data.Copy Duration
Bandwidth Saving
98 HP StoreOnce Catalyst functions
The amount of data copied, which should match the data size.Data Copied
The bandwidth utilisation in Mb/s. This is the physical bandwidth consumed.Bandwidth Utilisation
The amount of bandwidth saved. The % bandwidth saving depends upon whether the
store has been configured for source-side deduplication with a low-bandwidth transfer
Page 99

Table 29 Outbound copy job fields (continued)
DescriptionField
policy, or target-side deduplication with a high-bandwidth transfer policy. See Store Details
tab (page 88).
Unsuccessful Retry
Attempts
Time
Cancelled
To cancel a copy job
HP recommends canceling copy jobs via the backup application and only using the GUI as a last
resort. This ensures that the backup application catalog stays in sync with the backup images.
1. Select the job to be cancelled in the outbound copy job list.
2. Click Cancel Job.
3. At the confirmation prompt, click OK.
Inbound copy jobs tab
This tab provides a log with details about inbound copy jobs for the selected store.
• Use the filter options to locate the required job(s).
• By default, 50 items are displayed per page. This may be changed from the Items per Page
drop-down. Either use the scroll bar to scroll through all items on the page; or use the Prev or
Next buttons to display more pages.
If there are multiple unsuccessful attempts, a network link may be down or a blackout
window may be scheduled.
This is the time that the next copy will be attempted, if the previous one was unsuccessful.Next Copy Attempt
This indicates whether the user has cancelled the copy job or not.Copy Operation
• Values that you set in Settings control how long inbound copy jobs are retained for (default
is 90 days).
NOTE: This tab provides a report; it is not automatically refreshed.
Catalyst Stores page 99
Page 100

1. If necessary click + to display the filter options.
Check the boxes against the options that you wish to use. Specify as many options as possible
to narrow the search. Wild cards and boolean logic (AND/OR filters) are not supported.
• The name of the item is a unique identifier that is always defined on the backup
application. Similarly, the client name is defined on the backup application. Best practice
is to ensure that names are also meaningful for use in searches on the StoreOnce Backup
system.
• Sub-string matches are supported, so the filter will return any item that contains the
character string that has been entered. With Item Name and Client you can also specify
that it should be an Exact Match.
• With the Start Time and End Time fields, enter a range of dates and times.
• Select a Status which may be Pending, Running, Paused, Completed, or Cancelled.
2. Click Show Jobs.
3. A report listing inbound copy jobs is displayed. Use the Sort Results option to sort the results
alphabetically.
100 HP StoreOnce Catalyst functions
 Loading...
Loading...