Page 1

HP NonStop SSH
Reference Manual
HP Part Number: 544701-014
Published: February 2013
Edition: HP NonStop SSH 4.1
G06.21 and subsequent G-series RVUs
H06.07 and subsequent H-series RVUs
J06.03 and subsequent J-series RVUs
Hewlett-Packard Company
3000 Hanover Street
Palo Alto, CA 94304-1185
© 2013 HP
All rights reserved
Page 2

© Copyright 2013 Hewlett-Packard Development Company, L.P.
Confidential computer software. Valid license from HP required for possession, use or copying.
Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software
Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under
vendor’s standard commercial license.
The information contained herein is subject to change without notice. The only warranties for HP
products and services are set forth in the express warranty statements accompanying such products
and services. Nothing herein should be construed as constituting an additional warranty. HP shall
not be liable for technical or editorial errors or omissions contained herein.
Export of the information contained in this publication may require authorization from the U.S.
Department of Commerce.
Microsoft, Windows, and Windows NT are U.S. registered trademarks of Microsoft Corporation.
Intel, Pentium, and Celeron are trademarks or registered trademarks of Intel Corporation or its
subsidiaries in the United States and other countries.
Java is a U.S. trademark of Sun Microsystems, Inc.
Motif, OSF/1, UNIX, X/Open, and the "X" device are registered trademarks, and IT DialTone and The
Open Group are trademarks of The Open Group in the U.S. and other countries.
Open Software Foundation, OSF, the OSF logo, OSF/1, OSF/Motif, and Motif are trademarks of the
Open Software Foundation, Inc. OSF MAKES NO WARRANTY OF ANY KIND WITH REGARD TO THE OSF MATERIAL
PROVIDED HEREIN, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE. OSF shall not be liable for errors contained herein or for
incidental consequential damages in connection with the furnishing, performance, or use of this
material.
© 1990, 1991, 1992, 1993 Open Software Foundation, Inc. The OSF documentation and the OSF
software to which it relates are derived in part from materials supplied by the following:© 1987,
1988, 1989 Carnegie-Mellon University. © 1989, 1990, 1991 Digital Equipment Corporation. ©
1985, 1988, 1989, 1990 Encore Computer Corporation. © 1988 Free Software Foundation, Inc. © 1987,
1988, 1989, 1990, 1991 Hewlett-Packard Company. © 1985, 1987, 1988, 1989, 1990, 1991, 1992
International Business Machines Corporation. © 1988, 1989 Massachusetts Institute of Technology.
© 1988, 1989, 1990 Mentat Inc. © 1988 Microsoft Corporation. © 1987, 1988, 1989, 1990, 1991, 1992
SecureWare, Inc. © 1990, 1991 Siemens Nixdorf Informationssysteme AG. © 1986, 1989, 1996, 1997
Sun Microsystems, Inc. © 1989, 1990, 1991 Transarc Corporation.OSF software and documentation are
based in part on the Fourth Berkeley Software Distribution under license from The Regents of the
University of California.
OSF acknowledges the following individuals and institutions for their role in its development:
Kenneth C.R.C. Arnold, Gregory S. Couch, Conrad C. Huang, Ed James, Symmetric Computer Systems,
Robert Elz. © 1980, 1981, 1982, 1983, 1985, 1986, 1987, 1988, 1989 Regents of the University of
California.
Page 3

Contents
Preface 13
Who Should Read This Gui de ................................................................................................. 13
Related Reading ....................................................................................................................... 13
Document History .................................................................................................................... 15
Introduction 25
The SSH2 Solution .................................................................................................................. 25
The SSH Protocol .................................................................................................................... 26
Components of the SSH2 Software Package ........................................................................... 27
Architecture Overview ............................................................................................................. 28
Fully Compliant with the SSH Protocol Specification .............................................. 25
Strong Authentication and Multiple Cipher Suites .................................................... 25
Support of Full Screen Terminal Access ................................................................... 25
Built-in User Base ..................................................................................................... 25
Central Key Store ...................................................................................................... 26
Secure SFTP Transfer ................................................................................................ 26
TCP and FTP Port Forwarding .................................................................................. 26
Single Sign-on ........................................................................................................... 26
TCP/IPv6 ................................................................................................................... 26
SSH2 Running as SSH Daemon (Server) .................................................................. 28
SSH2 Running as SSH Client .................................................................................... 29
Installation & Quick Start 31
System Requirements .............................................................................................................. 31
Acquiring the Product Archives .............................................................................................. 31
Installation on the NonStop Server .......................................................................................... 32
Installing the SSH Components on the NonStop System .......................................... 32
Unlocking the Product wi th a License File ................................................................ 33
SSH2 License and Versio n Information .................................................................................. 34
Updating to a new version of the SSH2 file set ....................................................................... 34
Download of the object file set .................................................................................. 34
Installation of the new version ................................................................................... 34
Where configuration data is stored ............................................................................ 35
Migration Considerations ........................................................................................................ 35
Installation of SFTPAPI........................................................................................................... 35
Quick Start and Guided Tour ................................................................................................... 35
Quick-Starting the SSH2 System .............................................................................. 36
Secure Shell Access to the NonStop Server .............................................................. 38
Secure Shell Access from NonStop to Remote Systems ........................................... 39
Encrypted File Transfer ............................................................................................. 41
Using Public Keys to Authenticate Remote Users .................................................... 43
Using Public Keys to Logon to Remote Systems ...................................................... 44
Configuring and Running SSH2 47
HP NonStop SSH Reference Manual Contents • iii
Page 4

Configuration Overview .......................................................................................................... 47
The Configuration Fil e .............................................................................................. 48
PARAM Commands .................................................................................................. 48
Startup Line Parameters ............................................................................................ 49
Starting SSH2 .......................................................................................................................... 49
SSH2 Parameter Reference ...................................................................................................... 50
Parameter Overview .................................................................................................. 50
ALLOWEDAUTHENTICATIONS .......................................................................... 53
ALLOWEDSUBSYSTEMS ...................................................................................... 53
ALLOWFROZENSYSTEMUSER ........................................................................... 54
ALLOWINFOSSH2 .................................................................................................. 55
ALLOWPASSWORDSTORE .................................................................................. 55
ALLOWTCPFORWARDING .................................................................................. 56
AUDITCONSOLE .................................................................................................... 56
AUDITEMS .............................................................................................................. 57
AUDITFILE .............................................................................................................. 58
AUDITFILERETENTION ........................................................................................ 58
AUDITFORMAT ...................................................................................................... 59
AUDITFORMATCONSOLE .................................................................................... 59
AUDITFORMATEMS .............................................................................................. 60
AUDITFORMATFILE .............................................................................................. 60
AUDITMAXFILELENGTH ..................................................................................... 61
AUTOADDSYSTEMUSERS ................................................................................... 61
AUTOADDSYSTEMUSERSLIKE .......................................................................... 62
BACKUPCPU ........................................................................................................... 63
BANNER .................................................................................................................. 63
CIPHERS .................................................................................................................. 64
CLIENTALLOWEDAUTHENTICATIONS ............................................................ 65
COMPRESSION ....................................................................................................... 65
CONFIG .................................................................................................................... 66
CONFIG2 .................................................................................................................. 66
CPUSET .................................................................................................................... 66
CUSTOMER ............................................................................................................. 67
DISCONNECTIFUSERUNKNOWN ....................................................................... 68
ENABLESTATISTICSATSTARTUP ...................................................................... 68
FULLSSHCOMACCESSGROUP<j>....................................................................... 69
FULLSSHCOMACCESSUSER<i> .......................................................................... 69
GSSAUTH ................................................................................................................ 70
GSSGEXKEX ........................................................................................................... 71
GSSKEX ................................................................................................................... 71
GUARDIANATTRIBUTESEPARATOR ................................................................ 72
HOSTKEY ................................................................................................................ 72
INTERFACE ............................................................................................................. 73
INTERFACEOUT ..................................................................................................... 74
INTERVALLIVEPRIVATEUSERKEY ................................................................... 74
INTERVALLIVEPPUBLICUSERKEY ................................................................... 75
INTERVALPENDINGPRIVATEUSERKEY........................................................... 76
INTERVALPENDINGPUBLICUSERKEY ............................................................. 76
IPMODE .................................................................................................................... 77
LICENSE .................................................................................................................. 78
LIFECYCLEPOLICYPRIVATEUSERKEY ............................................................ 78
LIFECYCLEPOLICYPUBLICUSERKEY ............................................................... 79
LOGCACHEDUMPONABORT ............................................................................... 80
LOGCACHESIZE ..................................................................................................... 80
LOGCONSOLE ........................................................................................................ 81
LOGEMS .................................................................................................................. 81
iv • Contents HP NonStop SSH Reference Manual
Page 5

LOGEMSKEEPCOLLECTOROPENED .................................................................. 82
LOGFILE .................................................................................................................. 82
LOGFILERETENTION ............................................................................................ 83
LOGFORMAT .......................................................................................................... 83
LOGFORMATCONSOLE ........................................................................................ 84
LOGFORMATEMS .................................................................................................. 85
LOGFORMATFILE .................................................................................................. 86
LOGLEVEL .............................................................................................................. 86
LOGLEVELCACHE ................................................................................................. 87
LOGLEVELCONSOLE ............................................................................................ 87
LOGLEVELEMS ...................................................................................................... 88
LOGLEVELFILE ...................................................................................................... 88
LOGMAXFILELENGTH ......................................................................................... 89
LOGMEMORY ......................................................................................................... 89
MACS ........................................................................................................................ 90
PARTIALSSHCOMACCESSGROUP<n> ............................................................... 90
PARTIALSSHCOMACCESSUSER<k> .................................................................. 91
PORT ......................................................................................................................... 92
PTCPIPFILTERKEY ................................................................................................ 92
PTCPIPFILTERTCPPORTS ..................................................................................... 93
PTYSERVER ............................................................................................................ 93
RECORDDELIMITER ............................................................................................. 94
RESTRICTIONCHECKFAILEDDEFAULT ........................................................... 94
SAFEGUARD-PASSWORD-REQUIRED ............................................................... 95
SFTPALLOWGUARDIANCD ................................................................................. 95
SFTPCPUSET ........................................................................................................... 96
SFTPDISPLAYGUARDIAN .................................................................................... 96
SFTPEDITLINEMODE ............................................................................................ 97
SFTPEDITLINENUMBERDECIMALINCR ........................................................... 97
SFTPEDITLINESTARTDECIMALINCR ................................................................ 98
SFTPEXCLUSIONMODEREAD ............................................................................. 99
SFTPIDLETIMEOUT ............................................................................................. 100
SFTPMAXEXTENTS ............................................................................................. 100
SFTPPRIMARYEXTENTSIZE .............................................................................. 100
SFTPSECONDARYEXTENTSIZE ........................................................................ 101
SFTPUPSHIFTGUARDIANFILENAMES ............................................................ 101
SOCKETKEEPALIVE ............................................................................................ 102
SOCKETRCVBUF ................................................................................................. 102
SOCKETSNDBUF .................................................................................................. 103
SOCKTCPMINRXMT ............................................................................................ 103
SOCKTCPMAXRXMT .......................................................................................... 103
SOCKTCPRXMTCNT ............................................................................................ 104
SOCKTCPTOTRXMTVAL .................................................................................... 104
SSHAUTOKEXBYTES .......................................................................................... 105
SSHAUTOKEXTIME ............................................................................................. 105
SSHCTL .................................................................................................................. 106
SSHCTLAUDIT ...................................................................................................... 107
SSHKEEPALIVETIME .......................................................................................... 107
STOREDPASSWORDSONLY ............................................................................... 107
STRICTHOSTKEYCHECKING ............................................................................ 108
SUBNET ................................................................................................................. 108
SUPPRESSCOMMENTINSSHVERSION ............................................................. 109
TCPIPHOSTFILE ................................................................................................... 109
TCPIPNODEFILE ................................................................................................... 110
TCPIPRESOLVERNAME ...................................................................................... 110
USETEMPLATESYSTEMUSER ........................................................................... 111
HP NonStop SSH Reference Manual Contents • v
Page 6

Enabling Full TTY Access .................................................................................................... 112
Enabling 6530 Terminal Access ............................................................................................ 112
Configuring an Alternate Command Interpreter ...................................................... 112
Configuring a Service Menu.................................................................................... 113
Configuring an STN Service or Window ................................................................ 113
Forcing TACL Access via Server-side Configuration ............................................. 114
Using TELSERV as Service Provider ..................................................................... 114
Granting Access without SSH Authentication ....................................................................... 115
Single Sign-on with GSSAPI Authentication ........................................................................ 116
Overview ................................................................................................................. 116
Prerequisites ............................................................................................................ 116
Configuration of the GSSAPI Interface Process...................................................... 116
Enabling GSSAPI Authentication for a User Account ............................................ 116
Authorizing Kerberos Principals for Logon ............................................................ 117
Restricting Incom i ng and Outgoing Connecti ons .................................................................. 118
Rejecting Gateway Ports ......................................................................................... 118
Restricting External Access to SSH2 Process ......................................................... 118
Restricting Internal Access to Remote SSH2 Hosts ................................................ 118
Restricting Local Ports used for Port Forwarding ................................................... 119
Restricting Remote Hosts/Ports for Port Forwarding .............................................. 119
Restricting access to forwarding tunnels ................................................................. 119
Load Balancing ...................................................................................................................... 119
Load-Balancing Outbound SSH Sessions ............................................................... 119
Load-Balancing Inbound SSH Sessions .................................................................. 120
Fault Tolerance ...................................................................................................................... 120
Configuring SSH2 as a NonStop Process Pair......................................................... 120
Configuring SSH2 as a Generic Process ................................................................. 121
Choosing a Persistence Mechanism ........................................................................ 121
Processing of DEFINEs ......................................................................................................... 122
Setting of Environment Variables .......................................................................................... 122
TCP/IPv6 Configuration ........................................................................................................ 123
IPv6 Address Formats ............................................................................................. 123
Usage of IPv6 Addresses ......................................................................................... 124
IP Mode ................................................................................................................... 125
TCP/IPv6 Migration and Backout ......................................................................................... 125
Start Using TCP/IPv6 .............................................................................................. 125
Reverting Back to Pre-IPv6 SSH2 Release ............................................................. 125
The SSH User Database 127
Overview of SSH Operati on Modes ...................................................................................... 127
Database for Daemon Mode .................................................................................................. 128
Database for Client Mode ...................................................................................................... 130
Creating and Accessing the Database .................................................................................... 131
Exporting the Database .......................................................................................................... 131
SSHCOM Command Reference 133
SSHCOM Overview .............................................................................................................. 133
Miscellaneous commands in SSHCOM ................................................................................. 139
vi • Contents HP NonStop SSH Reference Manual
Standard NonStop Commands and Features ........................................................... 134
Startup Values for the MODE and ASSUME USER Commands ........................... 135
Security within SSHCOM ....................................................................................... 135
Ownership and Management of Client Mode Entities ............................................. 137
MODE ..................................................................................................................... 139
SET .......................................................................................................................... 139
Page 7

INFO SSH2 ............................................................................................................. 140
CLEAR LOGCACHE ............................................................................................. 142
FLUSH LOGCACHE .............................................................................................. 142
INFO DEFINE ........................................................................................................ 142
PROMPT "<text>" .................................................................................................. 143
RESOLVE HOST-NAME ....................................................................................... 143
ROLLOVER AUDITFILE ...................................................................................... 143
ROLLOVER LOGFILE .......................................................................................... 144
EXPORT SSHCTL .................................................................................................. 144
INFO HOST-KEY ................................................................................................... 145
EXPORT HOST-KEY ............................................................................................. 145
Daemon Mode Commands - Overview ................................................................................. 146
Daemon Mode Commands Operating on the USER Entity ................................................... 146
ADD USER ............................................................................................................. 146
ALTER USER ......................................................................................................... 153
DELETE USER ....................................................................................................... 159
FREEZE USER ....................................................................................................... 160
INFO USER ............................................................................................................ 160
RENAME USER ..................................................................................................... 162
THAW USER .......................................................................................................... 162
Daemon Mode Commands Operating on the RESTRICTION-PROFILE Entity .................. 162
ADD RESTRICTION-PROFILE ............................................................................ 162
ALTER RESTRICTON-PROFILE ......................................................................... 164
DELETE RESTRICTION-PROFILE ...................................................................... 166
INFO RESTRICTION-PROFILE ........................................................................... 166
RENAME RESTRICTION-PROFILE .................................................................... 166
Client Mode Commands - Overview ..................................................................................... 167
ASSUME USER ...................................................................................................... 168
INFO SYSTEM-USER ........................................................................................... 168
Client Mode Commands Operating on the KEY Entity ......................................................... 169
ALTER KEY ........................................................................................................... 169
DELETE KEY ......................................................................................................... 170
EXPORT KEY ........................................................................................................ 170
FREEZE KEY ......................................................................................................... 171
GENERATE KEY ................................................................................................... 171
IMPORT KEY ......................................................................................................... 172
INFO KEY .............................................................................................................. 173
RENAME KEY ....................................................................................................... 175
THAW KEY ............................................................................................................ 176
Client Mode Commands Operating on the PASSWORD Entity ........................................... 176
ADD PASSWORD .................................................................................................. 176
ALTER PASSWORD ............................................................................................. 177
DELETE PASSWORD ........................................................................................... 177
FREEZE PASSWORD ............................................................................................ 178
INFO PASSWORD ................................................................................................. 178
RENAME PASSWORD ......................................................................................... 179
THAW PASSWORD .............................................................................................. 180
Client Mode Commands Operating on the KNOWNHOST Entity ....................................... 180
ADD KNOWNHOST .............................................................................................. 180
ALTER KNOWNHOST ......................................................................................... 181
DELETE KNOWNHOST ....................................................................................... 181
FREEZE KNOWNHOST ........................................................................................ 182
INFO KNOWNHOST ............................................................................................. 182
RENAME KNOWNHOST ..................................................................................... 184
THAW KNOWNHOST .......................................................................................... 184
Status Commands .................................................................................................................. 185
HP NonStop SSH Reference Manual Contents • vii
Page 8

STATUS SSH2 ........................................................................................................ 185
STATUS SESSION ................................................................................................. 185
STATUS CHANNEL .............................................................................................. 187
STATUS OPENER ................................................................................................. 187
Statistics Related Commands ................................................................................................. 189
STATISTICS SESSION .......................................................................................... 189
DISABLE STATISTICS ......................................................................................... 189
ENABLE STATISTICS .......................................................................................... 189
RESET STATISTICS .............................................................................................. 189
STATUS STATISTICS ........................................................................................... 190
Abort Session Comm a nd ....................................................................................................... 190
SSH and SFTP Client Reference 191
Introduction ........................................................................................................................... 191
Starting the Guardian Client Programs .................................................................................. 191
Starting the OSS Client Programs.......................................................................................... 192
Configuring the SSH2 Process to Use ................................................................................... 194
Inquiring User Name If Not Supplied .................................................................................... 194
Suppressing the Banner printed by Clients ............................................................................ 195
Automating the SFTP/SSH clients ......................................................................................... 195
FILE I/O parameters for SFTP/SFTPOSS ............................................................................. 195
SSH Client Command Reference........................................................................................... 196
Command-Line Reference ....................................................................................... 196
Using the SSH client to create a shell controlling a remote system ........................ 200
Using the SSH client to create a port forwarding daemon ....................................... 201
Using the SSH client to create an FTP port forwarding daemon ............................. 202
SFTP Client Command Reference ......................................................................................... 203
Command-Line Reference ....................................................................................... 203
SFTP Commands ..................................................................................................... 206
Transfer Progress Meter .......................................................................................... 208
Controlling Transfer Summary ................................................................................ 208
Specifying File Names on the NonStop System ...................................................... 209
Extended Syntax for Creation of New Guardian Files ............................................ 209
Transfer Modes for Str uc t ured Guardian Files ........................................................ 210
Transferring ASCII files .......................................................................................... 211
Fix Command and Command History ..................................................................... 211
Creation of Format 2 Guardian Files ....................................................................... 213
SSH Protocol Reference 215
The SSH Protocol .................................................................................................................. 215
Implementation Overview ..................................................................................................... 215
Authentication using User Names and Passwords ................................................................. 216
Public Key Authentication ..................................................................................................... 216
STN Reference 219
Introduction ........................................................................................................................... 219
Running STN as Pseudo TTY Server for SSH2 .................................................................... 219
viii • Contents HP NonStop SSH Reference Manual
Supported Versions ................................................................................................. 215
Cipher Suites ........................................................................................................... 215
Implementation of the S SH protocol ....................................................................... 215
Introduction to Public Key Authentication, Terminology ....................................... 216
Public Key Authentication and SSH ....................................................................... 216
Assuring Host Authenticity ..................................................................................... 217
Client logon ............................................................................................................. 217
Page 9

Starting STN from TACL ........................................................................................ 219
Running STN as Persistent Process ....................................................................................... 221
STNCOM ............................................................................................................................... 222
Comments ................................................................................................................ 223
STNCOM Commands ........................................................................................................... 223
ABEND ................................................................................................................... 223
ABORT SERVICE .................................................................................................. 223
ABORT SESSION .................................................................................................. 223
ABORT WINDOW ................................................................................................. 224
ADD IPRANGE ...................................................................................................... 224
ADD SCRIPT .......................................................................................................... 224
ADD SERVICE ....................................................................................................... 225
ADD WINDOW ...................................................................................................... 231
AUDITCOLL OFF | <ems-collector> ..................................................................... 232
AUDITMSG <text> ................................................................................................ 233
AUTO_ADD_WIN DYNAMIC | STATIC | OFF ................................................... 233
AUTODEL_WAIT <seconds> ................................................................................ 233
BACKUP[CPU] <cpu> | NONE | BUDDY | ANY ................................................ 234
BANNER Y | N ....................................................................................................... 234
BANNER_TIMEOUT <minutes> ........................................................................... 234
BLAST <message> ................................................................................................. 235
BREAK_ON_DISCON Y|N ................................................................................... 235
BUFFER_SIZE ....................................................................................................... 235
CHOICE_PROMPT Y | N ....................................................................................... 235
CHOICE_TEXT <text> .......................................................................................... 235
CONN_CLR_SSH Y | N ......................................................................................... 235
DELETE IPRANGE <iprange-name> | * ................................................................ 235
DELETE SCRIPT <script-name> | * ...................................................................... 235
DELETE SERVICE <service-name> | * ................................................................. 236
DELETE WIN[DOW] <window-name> | * ............................................................ 236
DEV_SUBTYPE B05COMP | WINDOW | <nn> ................................................. 236
DYNAMIC_PRI <nnn> .......................................................................................... 236
DYN_CPU (cpu,cpu) .............................................................................................. 236
DYN_WIN_MAX <nnn> ........................................................................................ 236
EXIT ........................................................................................................................ 237
FC ............................................................................................................................ 237
FESESSDOWN <error-code> ................................................................................. 237
FRAGSIZE <n> ...................................................................................................... 237
GWN [ALLOC] ...................................................................................................... 237
HELP ....................................................................................................................... 238
IDLE_WARNING <n> ........................................................................................... 238
INFO ALL ............................................................................................................... 238
INFO IPRANGE <iprange-name> | * ..................................................................... 238
INFO PROCESS ..................................................................................................... 238
INFO SCRIPT <script-name> | * ............................................................................ 239
INFO SER[VICE] <service-name> | * .................................................................... 239
INFO STN ............................................................................................................... 240
INFO WIN[DOW] <window-name> | * .................................................................. 240
INPUT_TIMEOUT <minutes> ............................................................................... 241
KILL_DYNAMIC Y|N ........................................................................................... 242
LICENSE <location> .............................................................................................. 242
LISTOPENS ............................................................................................................ 242
MAX_OPENERS <n> ............................................................................................ 242
MAX_OUTQ <n> ................................................................................................... 243
NBOT Y|N .............................................................................................................. 243
NBOT_TIMEOUT <seconds> ................................................................................ 243
HP NonStop SSH Reference Manual Contents • ix
Page 10

NEGOT_TIMEOUT <seconds>.............................................................................. 243
OBEY <edit-file-name> .......................................................................................... 243
OPEN <STN-process-name> .................................................................................. 243
OPENER_WAIT <seconds> ................................................................................... 243
OUTPUT_RESET Y | N .......................................................................................... 244
PAUSE .................................................................................................................... 244
POOL ...................................................................................................................... 244
PROMPT "<text>" .................................................................................................. 244
PTY_REPLY_LEN <n> .......................................................................................... 245
REPLY_DELAY_MAX <seconds> ........................................................................ 245
RESET SERVICE <service-name> | * .................................................................... 245
RSCMGR_DEPTH <n> .......................................................................................... 245
SAVECFG <filename> ........................................................................................... 245
SECURITY [<letter>] ............................................................................................. 246
SHUTDOWN .......................................................................................................... 246
SSH_DEFAULT_SVC <service-name> | *NONE* ............................................... 246
START SERVICE <service-name> | * ................................................................... 246
START WINDOW <#window-name> | * ............................................................... 246
STATUS SERVICE [ <service-name> | * ] ............................................................ 246
STATUS SESSION [ <session-name> | * ] ............................................................ 247
STATUS WINDOW [ <#window-name> | * ] ........................................................ 248
STIX [RESET] ........................................................................................................ 248
STNCOM_PROMPT "<text>" ................................................................................ 248
STNLOG <text> ...................................................................................................... 250
STOP SERVICE <service-name> | * ...................................................................... 250
STOP SESSION <session-name> | * ...................................................................... 250
STOP WINDOW <#window-name> | * .................................................................. 250
TIME ....................................................................................................................... 250
TRACE .................................................................................................................... 250
VERSION ................................................................................................................ 251
WELCOME_SEQ BEFORE | AFTER | BOTH ...................................................... 251
WELCOME <filename> | OFF | LIST .................................................................... 251
WIN_AVAIL_ALWAYS Y | N .............................................................................. 252
WIN_AVAIL_C11 Y | N ...................................................................................... 252
WSINFO NONE | QUERY | REQUIRED | MATCH ............................................. 252
WINSCRIPT_FIRST Y | N ..................................................................................... 252
Session and Window Naming ................................................................................................ 253
GWN Related STNCOM Commands ...................................................................... 254
GWN Related EMS Events ..................................................................................... 255
EMS Events ........................................................................................................................... 255
Client Messages at the Remote Workstation ......................................................................... 269
STN Application I/O Handling .............................................................................................. 276
Monitoring and Auditing 279
Introduction ........................................................................................................................... 279
Log Messages ........................................................................................................................ 279
Audit Messages ...................................................................................................................... 282
x • Contents HP NonStop SSH Reference Manual
Content of Log Messages ........................................................................................ 279
Log Level ................................................................................................................ 280
Destinations for Log Messages ................................................................................ 281
Customizing the Log Format ................................................................................... 282
Content of Audit Messages ..................................................................................... 282
Destinations for Audit Messages ............................................................................. 283
Customizing the Audit Format ................................................................................ 283
Audit Reports .......................................................................................................... 283
Page 11

List of Audit Messages ............................................................................................ 283
Log File/Audit File Rollover ................................................................................................. 293
Viewing File Contents from Guardian with SHOWLOG ...................................................... 294
Viewing File Contents from OSS .......................................................................................... 297
Performance Considerations 299
Introduction ........................................................................................................................... 299
Performance Analysis of SSH Session Establishment ........................................................... 300
Performance Running as SSH Daemon ................................................................... 300
Performance Analysis of SFTP Traffic .................................................................................. 300
SFTPSERV Performance of ls Command with Wildcards ...................................... 300
Performance When Running as SSH Client ............................................................ 301
Summary ................................................................................................................................ 301
Troubleshooting 303
Introduction ........................................................................................................................... 303
Information Needed By Support ............................................................................................ 303
General SSH2 Error Messages .............................................................................................. 304
Session Related SSH2 Errors ................................................................................................. 305
Session Related Error Messages of SSH2 Daemon ................................................. 305
Session Related Messages of SSH2 in Client Mode ................................................ 309
Client Error Messages ............................................................................................................ 312
Appendix 315
Event Summary ..................................................................................................................... 315
Event Category ERROR .......................................................................................... 315
Event Category WARNING .................................................................................... 319
Event Category INFO .............................................................................................. 330
Copyright Statements ............................................................................................................. 338
OpenSSL Copyright Sta t ement ............................................................................... 338
OpenSSH Copyright Statement ............................................................................... 340
HP NonStop SSH Reference Manual Contents • xi
Page 12

xii • Contents HP NonStop SSH Reference Manual
Page 13

Preface
Who Should Read This Guide
This document is for system administrators who are responsible for installing, configuring and maintaining SSH2
components, including those delivered with the HP NonStop SSH product (T0801), and those that come with comForte's
SecurSH or SecurFTP/SSH product.
This document also contains sections useful for users of ssh/sftp clients on NonStop systems, namely
• section “Quick Start and Guided Tour“ without sub-section “Quick-Starting the SSH2 System”
• section “SSHCOM Command Reference” (mainly regarding client mode commands)
• section “SSH and SFTP Client Reference”
Related Reading
This documentation is intended as a reference for the configuration and use of SSH components. Please also refer to
additional documentation for the other products that come with the SSH2 package:
• For HP NonStop SSH: T0801 SOFTDOC, README or Suppo rt Notes as appropriate
• For SecurFTP: SecurFTP Quick Start Guide
The following reading is seen as prerequisite documentation for administrators installing HP NonStop SSH or comForte
SecurSH and SecurFTP/SSH:
• HP NonStop documenta tion “Guardian User’ s G uide”
• HP NonStop documentation “Open System Services Shell and Utilities Reference Manual”, if using OSS
• HP NonStop documenta tion “Guardian Proce du r e E rrors and Messages Manua l ”
• HP NonStop documentation “Safeguard User’s Manual”
• HP NonStop documenta tion “Safeguard Administrator’s Manual”
• HP NonStop documentation “SCF Reference Manual for the Kernel Subsystem”
• HP NonStop documentation “TCP/IP Configuration and Management Manual”
• HP NonStop documentation "HP NonStop TCP/IPv6 Configuration and Management Manual"
• HP NonStop documenta tion “HP NonStop Cluster I/O Protocols (CIP) Configuration and Management
Manual”
• HP NonStop documenta tion “EMS Manual”
HP NonStop SSH Reference Manual Preface • 13
Page 14

The following reading is recommended documentation for NonStop users of SSH/SFTP clients and users connecting to
NonStop using remote ssh/sftp/scp clients:
• HP NonStop documenta tion “Guardian User’ s G uide”
• HP NonStop documentation “Open System Services Shell and Utilities Reference Manual”, if using OSS
• HP NonStop documentation “HP NonStop TACL Reference Manual”
• HP NonStop documenta tion “File Utility Program (FUP) Reference Manual”
Generally, users should get familiar with Guardian name space, Guardian file attributes and Guardian structured files
when connecting from remote sftp/scp clients planning to transfer Guardian specific files to and from a NonStop system.
This is not required if only files from and to the OSS environment will be transferred.
It is expected that administrators and users gain knowledge about the SSH standard before using SSH implementations.
There are many good books about SSH. Here we only mention one:
• "SSH The Secure Shell The Definitive Guide", Daniel J. Barret et. al., O'Reilly
The following links may also serve as a starting point for SSH related information:
• http://tools.ietf.org/html/rfc4251
• http://tools.ietf.org/html/draft-ietf-secsh-filexfer-02
• http://en.wikipedia.org/wiki/Secure_Shell
• http://wiki.filezilla-project.org/SFTP_specifications
• http://www.openssh.org/
The Kerberos/GSSAPI relate d li n ks s h ow n be l o w a re of i n terest if Single Sign-on will be configured (see section “Single
Sign-on with GSSAPI Authentication”):
• http://web.mit.edu/Kerberos/
• http://www.ietf.org/rfc/rfc4462.txt
The following reading prerequisite documentation for administrators configuring SSH2 for IPv6 support:
• HP NonStop documentation "TCP/IPv6 Migration Guide"
• HP NonStop documentation "TCP/IPv6 Configuration and Management Manual"
The following TCP/IPv6 related links may be helpful when preparing SSH2 IPv6 configuration:
• http://en.wikipedia.org/wiki/IPv6
• http://tools.ietf.org/html/rfc1639 - FTP Operation Over Big Address Records (FOOBAR)
• http://tools.ietf.org/html/rfc2428 - FTP Extensions for IPv6 and NATs
• http://tools.ietf.org/html/rfc2460 - Internet Protocol, Version 6 (IPv6) S p ecification
• http://tools.ietf.org/html/rfc4291 - IP Version 6 Addressing Architecture
• http://www.tcpipguide.com/free/t_IPv6Addressing.htm
• http://tools.ietf.org/html/draft-ietf-6man-text-addr-representation-04
• http://tools.ietf.org/html/rfc4038
14 • Preface HP NonStop SSH Reference Manual
Page 15

Document History
Version 4.1
Describes changes in the SSH2 release 93.
Documentation for the following new features has been added:
• Added Migration Considerations section
• Added description of new parameter SFTPDISPLAYGUARDIAN controlling the format of filenames in SFTP
informational messages.
• Added additional information displayed by the STNCOM VERSION command, and an example showing the
new startup banner and version info.
• Added SSHCOM command EXPORT SSHCTL now supporting export to an OSS directory.
• Added description of additional timestamp options in utility SHOWLOG.
• Noted that macro SSH2INFO now prints warning messages if the objects SSH2, SFTPSERV and STN do not
have a Safeguard DISKFILE entry with PRIV-LOGON set to ON. The warnings will also be logged at SSH2
startup.
• Added description of new STNCOM commands to provide for unique session and window name generation.
• Added description of the PROGRESS meter command option "?".
• The section "STNCOM Commands" has been updated to be in synch with STN help. New
commands/parameters and EMS events for session/window naming have been added. Setmode 212 and 214
have been added in the setmode table.
Changes in SSH2 release 93 that are incompatible with previous releases:
• The STN AUTO_ADD_WIN configuration parameter is no longer supported. All openers of STN must refer to
an existing window name.
• The SSHCOM STATUS SESSION brief output no longer contains the SESSION-LOG-ID field. It also now
uses abbreviated column headings.
Version 4.0
Describes changes in SSH2 release 92.
Documentation for the following new features has been added:
• Added section IPv6 and des cription of relate d pa ra meter IPMODE.
• Description for new SSH2 TCP/IP related parameters PTCPIPFILTERTCPPORTS, SOCKTCPMINRXMT,
SOCKTCPMAXRXMT, SOCKTCPRXMTCNT, and SOCKTCPTOTRXMTVAL has been added.
• Added description of new SSHCOM client mode command INFO SYSTEM-USER to section "Client Mode
Commands - Overview".
• Added description for new parameters LIFECYCLEPOLICYP UB LICUSERKEY,
INTERVALPENDINGPUBLICUSERKEY and INTERVALLIVEPUBLICUSERKEY.
• Added description for new parameter ALLOWI N FOSSH2.
• Added description for new parameters PARTIALSSHCOMACCESSGROUP<n> and
PARTIALSSHCOMACCESSUSER<k>.
• Added description for new SFTP[OSS] comma nds a ppend and lappend.
• Added description for new support for creation of format 2 files in an SFTP session.
HP NonStop SSH Reference Manual Preface • 15
Page 16

• Added description for support of option -oBindAddress for SFTP[OSS] and SSH[OSS] clients.
• Added description of option LIKE for SSHCOM command ADD RESTRICTION-PROFILE.
• Updated section "Starting SSH2" with new run modes.
• Added documentation of additional commands in section "Statistics Related Commands".
• Added sections "Transfer Progress Meter" and "Controlling Transfer Summary".
• Updated section "Viewing File Contents from Guardian with SHOWLOG".
• Added description of new commands FESESSDOWN and REPLY_DELAY_MAX in section "STNCOM
Commands".
• Added appendix "Event Summary".
Changes in SSH2 release 92 that are incompatible with previous releases:
• Output of SSHCOM commands that contains IP addresses in some form has been modified to allow for the
greater length of IPv6 addresses
Version 3.9
Describes changes in SSH2 release 91.
Documentation for the following new features has been added:
• Added description for new parameters CPUSET and SFTPCPUSET.
• Added description for param et ers AU DITEMS, AUDITFORMATCONS OLE, AUDITFORMATEMS,
AUDITFORMATFILE.
• Enhanced description of SET command in section “Miscellaneous commands in SSHCOM”
• Added description for new SFTP/SFTPOSS com mands FC and HISTORY.
• Added new sections “Checking SSH2 Installation”, "SSH2 License and Version Information", and "Installation
of SFTPAPI".
• Added description of SSHCOM command ABORT SESSION in ne w se ction “Other Session Related
Commands”.
• Added description of SSHCOM command PROMPT in section “Miscellaneous commands in SSHCOM”.
Documentation for the following already existing STN pseudo-TTY features has been added:
• Uses of STN runtime options IN/OUT.
• STNCOM: multiple line command continuation.
• Example display of INFO STN (update).
• STNCOM commands CONN_CLR_SSH, DEV_SUBTYPE, FRAGSIZE, INFO ALL, NBOT,
OPENER_WAIT, PROMPT, SAVE_CFG, STNCOM_PROMPT.
Documentation for the following new STNCOM commands has bee n a dded:
• DYN_CPU (global cpu/cpu-range specification for dynamic service processes).
• NBOT_TIMEOUT
Version 3.8a
Describes changes in SSH2 release 90a.
Documentation modified for the following enhancement:
• Alphabetically sorted help items displayed within SFTP and SFTPOSS when 'help' command entered.
16 • Preface HP NonStop SSH Reference Manual
Page 17

Version 3.8
Describes changes in SSH2 release 90.
Documentation for the following new features has been added:
• Added description for new parameters ENABLESTATISTICSATSTARTUP, INTERFACEOUT,
LOGEMSKEEPCOLLECTOROPENED, LIFECYCLEPOLICYPRIVATEUSERKEY,
INTERVALPENDINGPRIVATEUSERKEY and INTERVALLIVEPRIVATEUSERKEY.
• Added description for new host key related SSHCOM commands INFO HOS T-KEY, EXPORT HOST-KEY
• Modified description for SSHCOM client mode commands ALTER KEY, GENERATE KEY, IMPOR T KEY
and INFO KEY
• Added description for new statistics related SSHCOM command STATISTICS SESSION
• Added description of new audit event SftpServerFatalErrorEve nt
• Added section “FILE I/O parameters for SFTP/SFTPOSS”
• Enhanced section " Installation on the NonStop Server"
• Added an example for “Forwarding Remote Port to Local Port” in section "To Establish a Port Forwarding
Tunnel with the NonStop SSH Client"
Changes in SSH2 release 90 that are incompatible with previous releases:
• In previous releases the value for INTERFACE had not been used for outgoing connections, i.e. if a TCP/IP
process defined several subnets, then it was undetermined, which of the local IP addresses was used when
connecting to remote systems. Now the IP address configured via INTERFACEOUT is used or, if that is not
set, the value of parameter INTERFACE determines the local IP address selected for outgoing connections. The
previous behavior can be activated by setting the ne w parameter INTERFACEOUT to value 0.0.0.0.
• The output of SSHCOM command INFO KEY has changed: The brief information contains the life-cycle state
(header LIFE-CYCLE) instead of the LAST-MODIFIED field.
Version 3.7
Describes changes in SSH2 release 89.
Documentation for the following new features has been added:
• Description for SSH2 parameters ALLOWFROZENSYSTEMUSER, CLIENTMODEOWNERPOLICY and
SUPPRESSCOMMENTINSSHVERSION have been added.
• Description for parameter RECORDDELIMITER now lists newly supported values CR and CRLF.
• Added description for new SSH/SFTP Client parameters SUPPRESSCLIENTBANNER, SSHERRORPREFIX,
SSHINFOPREFIX and SSHQUERYPREFIX.
• Added description for new SSH/SFTP Client opt ions -Z (corresponding to SUPPRESSCLIENTBANNER), -H
(corresponding to SSHERRORPREFIX), -J (corresponding to SSHINFOPREFIX) and -K (correspo nding to
SSHQUERYPREFIX).
• Description of the SSH2 database was enhanced.
• Added description for new parameter SFTPEXCLUSIONMODEREA D.
• Added description of new USER attribute ALLOW-MULTIPLE-REMOTE-HOSTS
• Added section about modified behavior if an OBJECTTYPE USER record exists in Safeguard.
• Added section listing all audit messages.
• Added section for SSHCOM client mode commands RENAME KNOWNHOST and RENAME PASSWORD
HP NonStop SSH Reference Manual Preface • 17
Page 18

Changes in SSH2 release 89 that are incompatible with previous releases:
• Previous client mode owner policy was to use the Guardian user id to store client mode records. This
corresponds to value GUARDIA NN AM E for new parameter CLIENTMODEO WNERPOLICY. The default
value for this parameter is BOTH, i.e. in order to get the previous behavior the parameter
CLIENTMODEOWNERPOLICY must be explicitly set to GUARDIANNAME.
• With the introduction of parameter CLIENTMODEOWNERPOLICY it is no longer possible to execute
SSHCOM GENERATE KEY for an alias if CLIENTMODEOWNERPOLICY is set to GUARDIANNAME. In
previous releases thi s wa s possible although such a key had never been use d ( o nly those keys, which we re
stored under the Guardian id underlying an alias.
• Users that are frozen in Safeguard are no longer accepted per default (new parameter
ALLOWFROZENSYSTEMUSER has default value FALSE). Previous releases allowed authentication and if
that was successful (methods none, publickey and gssapi-with-mic) the user was granted access. The previous
behavior can be re-established by setting parameter ALLOWFROZENSYSTEMUSER to TRUE.
• Auditing of executed SF TP commands for outgoi ng connections has bee n a dded. Previously there wa s s uc h
support for incoming connections. If an SFTP[OSS] client of release 89 or later connects via an SSH2 process
of previous releases, an exception occurs (error 48) during audit initialization, i.e. an SFTP[OSS] client of
release 89 or later must be used with an SSH2 process of version 89 or later.
• The AUDIT messages have been modified to include the SESSION-LOG-ID to be able to relate AUDIT
messages to LOG messages and STATUS SESSION output.
• A different behavior ha s be e n implemented if an OBJE C T TYPE USER record exists in S a fe guard: parameter
sets FULLSSHCOMACCESSGROUP<j> and FULLSSHCOMACCESSUSER<i> will be ignored.
• SUPER.SUPER no longer has full access to SSHCOM if an OBJECTTYPE USER record exists which
explicitly denies SUPER.SUPER the Create authority. In previous releases SUPER.SUPER always had full
access, independent of the OBJECTTYPE USER record.
• The format of audit messages has changed. Main change is the addition of the SESSION-LOG-ID at the
beginning of each audit message (allowing to relate log messages and STATUS SESSION information to audit
messages).
• SFTP informational messages like "Uploading ..." and "Fetching ..." now display Guardian file names in
standard ssh format (Unix style with OSS prefix /G or /E) to better conform to the SFTP standard; before that,
the Guardian style was the default.
Version 3.6
Describes changes in SSH2 release 88.
Documentation for the following new features has been added:
• Description for SSH2 TCP/IP related parameters SOCKETSNDBUF and SOCKETRCVBUF have been added.
• Parameter KEEPALIVE has been renamed to SOCKETKEEPALIVE.
• The "ASLINEMODE" command has been added to SFTP client commands.
• Description of newly supported SFTP transfer modes.
• Added description for new parameter SFTPEXCLUSIONMODEREA D.
Version 3.5
Describes changes in SSH2 release 87.
Documentation for the following new features has been added:
18 • Preface HP NonStop SSH Reference Manual
Page 19

• Description for SSH2 log message memory cache related parameters LOGCACHESIZE, LOGLEVELCACHE
and LOGCACHEDUMPONABORT have been added,
• Log cache related SSHCOM commands SET LOGCACHESIZE, SET LOGLEVELCACHE, SET
LOGCACHEDUMPONABORT, FLUSH LOGCACHE and CLEAR LOGCACHE were described,
• Added description for SSHCOM commands STATUS SSH2, STATUS SESSION, STATUS CHANNEL and
STATUS OPENER,
• The document now contains a description for file retention related SSHCOM commands ROLLOVER
LOGFILE and ROLLOVER AUDITFILE.
Version 3.4
Describes changes in SSH2 release 86j.
Documentation for the following new features has been added:
• A description for SSH2 parameter ALLOWEDSUBSYSTEMS has been added,
• Parameter CLIENTALLOWEDAUTHENTICATIONS and ssh client option AllowedAuthentications has been
added,
• Finer control of full SSHCOM access via SSH2 parameters FULLSSHCOMACCESSUSER<i> and
FULLSSHCOMACCESSGROUP<j> are now described,
• The document now contains text about parameters SFTPEDITLINESTARTDECIMALINCR ,
SFTPEDITLINENUMBERDECIMALINCR and SFTPEDITLINEMODE, enhancing the control over Guardian
edit lines written to NonStop (line numbers, handling of edit lines that are too long),
• Added description for param et er SFTPUPSHIFTGUARDIANFILE N AM ES
• SSH2 parameter STOREDPASS WORDSONLY has been described.
Version 3.3
Describes changes in SSH2 release 0086.
Documentation for the following new features has been added:
• Support of GSSAPI/Kerberos-based user authentication and key exchange in accordance with the RFC 4462
standard, including capabilities such as gssapi-with-mic, gssapi-keyex user authentication, gss-group1-sha1, and
gss-gex-sha1 key exchange employing Kerberos. The new feature is addressed in new and updated
documentation of the following parameters:
o new SSH2 parameter GSSAUTH
o new SSH2 parameter GSSKEX
o new SSH2 parameter GSSGEXKEX
o extended SSH2 parameter ALLOWEDAUTHENTICATIONS
o extended USER attribute ALLOWEDAUTHENTICATIONS
o new USER attribute PRINCIPAL
• The section "Single Sign-on with GSSAPI Authentication" has been added to the chapter "Configuring and
Running SSH2"
Version 3.2
Describes changes in SSH2 release 0085.
Documentation for the following new features has been added:
• New SSH2 parameter RECORDDELIMITER
HP NonStop SSH Reference Manual Preface • 19
Page 20

Version 3.1
Describes changes in SSH2 release 0084.
Documentation for the following new features has been added:
• New environment variable INQUIREUSERNAMEIFNOTSUPPLIED checked by ssh/sftp clients.
• New ADD USER option LIKE.
• New SSH2 parameter DISCONNECTIFUSERUNKNOWN.
Version 3.0
Describes changes in SSH2 release 0083.
Documentation for the following new features has been added:
• New database object RESTRICTION-PROFILE.
• New SSHCOM commands for manipulating of RESTRICTION-PROFILE records.
• Support for EXPORT of RESTRICTION-PROFILE records.
• New SSH2 parameter RESTRICTIONCHECKFAILEDDEFAULT.
• New USER attributes RESTRICTION-PROFILE, ALLOW-GATEWAY-PORTS, PRIORITY, COMMENT,
CPU-SET and SFTP-CPU-SET.
• New attribute WIDTH for SSHCOM command EXPORT SSHCTL.
• New option FORCE for USER attributes CI-PROGRAM and SHELL-PROGRAM.
• New SSH2 parameter USETEMPLATESYSTEMUSER.
Version 2.9
Describes changes in SSH2 release 0082.
Documentation for the following new features has been added:
• Newly supported scp server functionality.
• Propagation of defines from SSH2 to shell/TACL processes started by SSH2.
• New define =SSH2^PROCESS^NAME added to shell/TACL processes started by SSH2.
• New parameter <service> after *MENU* property of USER attribute SHELL-PROGRAM.
• New USER attribute SHELL-ENVIRONMENT controlling environment for non-login shells.
• New SSH2 parameter GUARDIANATTRIBUTESEPARATOR.
A topic has been added listing the environment variables set by SSH2 when a shell is started.
Version 2.8
Describes changes in SSH2 release 0081.
Documentation for the following new features has been added:
• Documentation for new STN features: PARAM LICENSE, commands ABEND, BANNER_TIMEOUT,
INPUT_TIMEOUT, IDLE_WARNING, OUTPUT_RESET, BLAST , B UFF ER_SIZE, and ADD SCRIPT, and
ADD SERVICE parameters RESILIENT, LIMIT, HOME, USER, LOGON, DEBUGOPT, LOGAUDIT, and
SCRIPT.
• New SSHCOM commands SET AUDITFILE
• New parameter <service> after *MENU* property of USER attribute CI-PROGRAM
20 • Preface HP NonStop SSH Reference Manual
Page 21

Version 2.7
Manual has been revised to correctly reflect the way HP NonStop SSH is delivered.
Version 2.6
Describes changes in SSH2 release 0080.
Documentation for the following new features has been added:
• Configuration of an alternate command interpreter or a service menu for USERs working with a 6530 SSH
sessions
• Granting access without SSH user authentication
The chapter "STN Reference" has been added, documenting the STN pseudo TTY server.
The chapter "SFTP Client Reference" has been renamed to "SSH and SFTP Client Reference", reflecting that the chapter
does now also document the SSH client program.
Version 2.5
Describes changes in SSH2 release 0074.
• Added documentation for several new SSH2 parameters: BANNER, SAFEGUARD-PASSWORD-
REQUIRED, SSHAUTOKEXBYTES, SSHAUTOKEXTIME and SSHKEEPALIVETIME.
• Changes reflecting support of keyboard-interactive authentication in SSH2 DAEMON run mode.
The documentation now re flects that HP NonStop SSH is also delivered as an independent product for G-Series.
Version 2.4
The documentation now reflects that SSH2 is also delivered with the HP NonStop H-series release version updates
(RVU) for HP Integrity N on Stop servers (beginning with H06.11), under t he product name HP NonStop SSH.
Version 2.3
Describes changes in SSH2 release 0070.
• Added section "Enabling 6530 Terminal Access" in chapter “Configuring and Running SSH2”.
• Updated Guardian SSH description in section "Secure Shell access from NonStop to Remote Systems" to reflect
new capabilities.
Version 2.1
Describes changes in SSH2 releases 0062 and later.
The manual now reflects the additional functionality implemented for the SecurSH product, a complete SSH suite
including shell client and server capabilities with full pseudo TTY support, as well as port forwarding. The manual
contains the following major changes and additions:
• The "Installation & Quickstart" chapter has been rewritten.
• The "Configuring and Running SSH2" chapter describes additional SSH2 parameters.
• Sections for "Enabling PTY Access" and "Load Balancing" have been added.
• The "SSHCOM reference" now describes some additional USER attributes.
The following additio na l new features are also de s cribed:
• Running SSH2 as a nonstop process pair.
• The new mechanism for rolling over log and audit files.
HP NonStop SSH Reference Manual Preface • 21
Page 22

Version 1.8
The new SFTP-PRIORITY attribute of user entity allows administrators to specify the priority of the SFTPSERV
process started by SSH2. This feature enables SSH2 to run at a high priority, while SFTPSERV runs at a priority below
other critical application or system processes. This will minimize the impact SFTP transfers have on overall system
performance, while ensuring fast response times of SSH2 during SSH session establishment.
The same effect can be achieved with SFTP clients by setting the SFTP [OSS] process priority to an appropriate value.
Version 1.7
Describes changes in SSH2, releases 0044 and later:
The SFTP client now supports passwords as means as authentication. This is reflected in the following changes:
• The new entity "PASSWORD" has been added to the SSH2 user database in client mode. This is documented in
the sections "SSH User Database" and "SSHCOM Command Reference".
• The Quickstart section has been updated to reflect an easier way to configure the SFTP client for a new remote
host.
Version 1.6
Added description of new parameters, which allow setting of DEFINES per config file to enable configuration as a
generic process:
• TCPIPHOSTFILE (sets =TCPIP^HOST^FILE)
• TCPIPNODEFILE (sets =TCPIP^NODE^FILE)
• TCPIPRESOLVERNAME (sets =TC PIP^ RESOLVER^NAME)
Version 1.5
Added documentation f or t he PT C P IPFILTERKEY param et e r.
Version 1.4
Describes changes in SSH2, release 0040. This release has the following new features:
• OSS is no longer required to run the SSH2 process.
• New SSH2 configuration parameters: SFTPPRIMARYEXTENTSIZE, SFTPSECONDARYEXTENTSIZE,
SFTPMAXEXTENTS (see section "SSH2 Parameter Reference" in chapter "Configuring and Running SSH2").
• The "touch" command has been added to SFTP client commands.
• Guardian filename syntax is supported in commands working on NonStop files or subvolumes residing in the
Guardian file system (see chapter "SFTP Client Reference", section "Specifying Filenames on the NonStop
System").
• The attributes of files created on the NonStop system can be specified using an extended syntax in the get or put
commands (see chapter "SFTP client reference", section "Extended syntax for creation of new Guardian files").
Version 1.3
Describes changes in SSH2 release 0038. This release has the following new features:
• An SFTP client to run under Guardian is supplied (see chapter "SFTP Client Reference").
• The new property SFTP-GUARDIAN-FILESET has been added to the USER property of the daemon mode
database (see chapter "SSHCOM Reference").
• New commands FREEZE KEY, THAW KEY and EXPORT SSHCTL have been added to SSHCOM (see
chapter "SSHCOM Reference").
22 • Preface HP NonStop SSH Reference Manual
Page 23

Version 1.2a
• Some general improvements in layout have been implemented.
• The heading structure has been slightly revised in various places.
• Two parameters, ALLOWIP and DENYIP, have been deleted.
Version 1.2
Describes changes in SSH2 release 0036. Starting with this release, SecurFTP also supports running as an SFTP client
under OSS. Documenting this new capability resulted in changes throughout the manual.
Version 1.1
Describes changes in SSH2 release 0025.
• One user now can have multiple public keys (see SSHCOM)
• New SSH2 configuration parameter: COMPRESSION
• USERBASE and USERBASEAUDIT parameters have been renamed to SSHTCL and SSHCTLAUDIT
• INFO USER command in SSHCOM now supports brief and DETAILED version of the command
Version 1.0
This is the first version of this documentation.
HP NonStop SSH Reference Manual Preface • 23
Page 24

24 • Preface HP NonStop SSH Reference Manual
Page 25

Introduction
The SSH2 Solution
SSH2 is a set of programs delivered when the customer purchases one of the following products:
• HP NonStop SSH. HP NonStop SSH is a comprehensive, enterprise Secure Shell solution for HP NonStop
servers. In the fall of 2010, it became available from HP with the purchase of the NonStop Operating System
Kernel for H Series and J Series NonStop platforms. For G Series releases, HP NonStop SSH continues to be
available from HP as an RVU for which a license is required to obtain full functionality. For details on licensing
and availability, please contact your HP Sales representative.
• comForte SecurSH. SecurSH is identical with HP NonStop SSH. It includes a remote shell and SFTP client and
a shell server with full pseudo terminal support. It also offers SFTP, TCP and FTP port forwarding capabilities.
The complete functionality is delivered by SSH2 programs.
• comForte SecurFTP. SecurFTP provides secure file transfer for HP NonStop systems. To protect data
confidentiality across the network, it supports FTP session encryption, either via the SSL/TLS protocol
(SecurFTP/SSL) or via the SSH/SFTP protocol (Secur FTP/SSH). For SecurFTP/SSH, SSH2 delivers t he SFTP
functionality, which is a subset of the comForte SecurSH functionality.
Fully Compliant with the SSH Protocol Specification
SSH2 is fully compliant with version 2 of the SSH (Secure Shell) protocol standard as described in various Internet draft
documents (see www.ietf.org). It can be integrated with any SSH solution on UNIX, Windows or other platforms.
Strong Authentication and Multiple Cipher Suites
SSH2 supports public key authentication with key sizes of up to 2048 bits. Various ciphers, including AES and 3DES,
and MACing algorithms can be selected.
Support of Full Screen Terminal Access
SSH2 supports pseudo terminals on the NonStop platform, allowing SSH clients to execute full screen applications, such
as Emacs or vi within Secure Shell.
Built-in User Base
A built-in user base allows administrators to flexibly control who can access a system. Remote users can logon with
virtual user names ins t e a d of a Gua rdian userid, eliminating the potential exposure of system credentials to file transfer
clients. Access can be limited to a part of the file system and to a specific set of operations (e.g. only download).
HP NonStop SSH Reference Manual Introduction • 25
Page 26
Central Key Store
Instead of storing keys in the file system, SSH2 includes a key and password store with central access control, providing
maximum security for user credentials. This enables the easy and secure implementation of batch processes without
requiring the use of passwords in batch files.
Secure SFTP Transfer
SSH2 includes an OSS and a Guardian SFTP client, as well as an SFTP server that provides remote SFTP client access
to both Guardian and OSS files. All components allow users to navigate the Guardian file system and specify files using
the OSS or Guardian file name syntax, regardless of whether OSS is running. Additionally, just as with standard
NonStop FTP, attributes for ta rget files can be specified, allowing direct transfers of structured Guardian files.
TCP and FTP Port Forwarding
TCP port forwarding allows secure tunneling of Telnet sessions, as well as other connections. SSH2 also tunnels FTP
sessions, securing existing FTP procedures with minimal changes. Both local and remote forwarding are supported.
Single Sign-on
SecurSH now supports user authentication and key exchange based on the GSSAPI/Kerberos 5 standards (RFC 4462).
When used with a Kerbero s s of tware package on the NonStop server, this enables integration with Microsoft Active
Directory and other Kerberos-based single sign-on solutions.
Note: HP does not offer a Kerberos product today, it must be purchased separately from a NonStop partner.
TCP/IPv6
Starting with version 0092 SSH2 supports IPv6 specified in RFC 246 0 (Internet Protocol, Ve rs ion 6).
The SSH Protocol
SSH (Secure Shell), consisting of a suite of network connectivity protocols, is especially popular in UNIX environments.
SSH2 supports version 2 of the Secure Shell protocol. This version also includes specifications for a file transfer
protocol. Although t he na me implies otherwise , thi s s t a ndard bears no relationship to the popular fil e transfer protocol
known as FTP.
26 • Introduction HP NonStop SSH Reference Manual
Page 27

Components of the SSH2 Software Package
The SSH2 software package consists of the following components:
• The SSH2 component is the central component of the implementation. Depending on the mode it is started in, it
can serve different purposes:
o It implements a server process for the SSH2 protocol. It listens for incoming connections on a specific
TCP/IP port (typical l y port 22), authenticat e s the us er and the service and the n spawns other processes it
communicates with.
o It is opened by the SSHCOM component to maintain the SSH configuration database.
o It is opened by the SFTP or SSH client components to initiate Shell or SFTP-based file transfers to other
platforms running an SSH daemon.
The SSH2 component accesses a user database that contains the following entries for incoming SFTP
connections:
o remote user names
o the mapping of remote user names to Guardian system users
o user’s public keys
o user’s credentials on the system
o selected status information, such as the last time a user accessed the system
• The SSHOSS component implements a Secure Shell client running under OSS to connect to a remote SSH
daemon. It provides Secure Shell sessions as well as TCP and FTP port forwarding capabilities.
• The SSH component implements a Secure Shell client running under Guardian to connect to a remote SSH
daemon. It provides Secure Shell sessions as well as TCP and FTP port forwarding capabilities.
• The SFTPSERV component is started by SSH2 for each SFTP client that connects to SSH2 components. The
SFTPSERV component then handles the file I/O associated with the file transfers initiated by the SFTP client.
Because SFTPSERV is started by the SSH2 component, configuration of SFTPSERV is implicit by the
configuration of the SSH2 component.
• The SFTPOSS component implements an SFTP client running under the OSS personality.
• The SFTP component implements an SFTP client running under the Guardian personality.
• The SSHCOM component allows the maintenance of the SSH user database. To do so, it communicates with
the SSH2 component.
• The PAUTH component is used by SSH2 for authenticating user passwords against the system user base.
• The STN component is a pseudo TTY server providing full screen shell access to remote SSH clients.
• The SCPOSS component is the scp server implementation. It is started on request of a remote scp client via
shell command. The scp client on Guardian/OSS has not been added yet.
HP NonStop SSH Reference Manual Introduction • 27
Page 28

Architecture Overview
This section shows how the various components work together in different usage scenarios.
SSH2 Running as SSH Daemon (Server)
The following figure shows how the components of SSH2 work together to implement SSH server processes (often
referred to as a “daemon” in UNIX environments) on the NonStop system. These SSH processes provide shell, file
transfer and port forwarding access to remote SSH clients, such as OpenSSH on UNIX:
Figure 1: SSH2 running as SSH daemon
The SSH2 component accepts the incoming TCP/IP session and authenticates the remote user against the user database,
optionally verifying user passwords with the PAUTH process. Upon request it …
• spawns an OSS shell, TACL or SFTPS ERV process.
• allocates a PTY (a pseudo terminal) by communicating to an STN process acting as a PTY server.
• forwards TCP/IP or FTP connections from the remote SSH client to a local server process or vice versa.
The SSHCOM component is used to maintain the user database, allowing administrators to configure remote user's
public keys and control access rights to server functionality and the file system for file transfer.
28 • Introduction HP NonStop SSH Reference Manual
Page 29
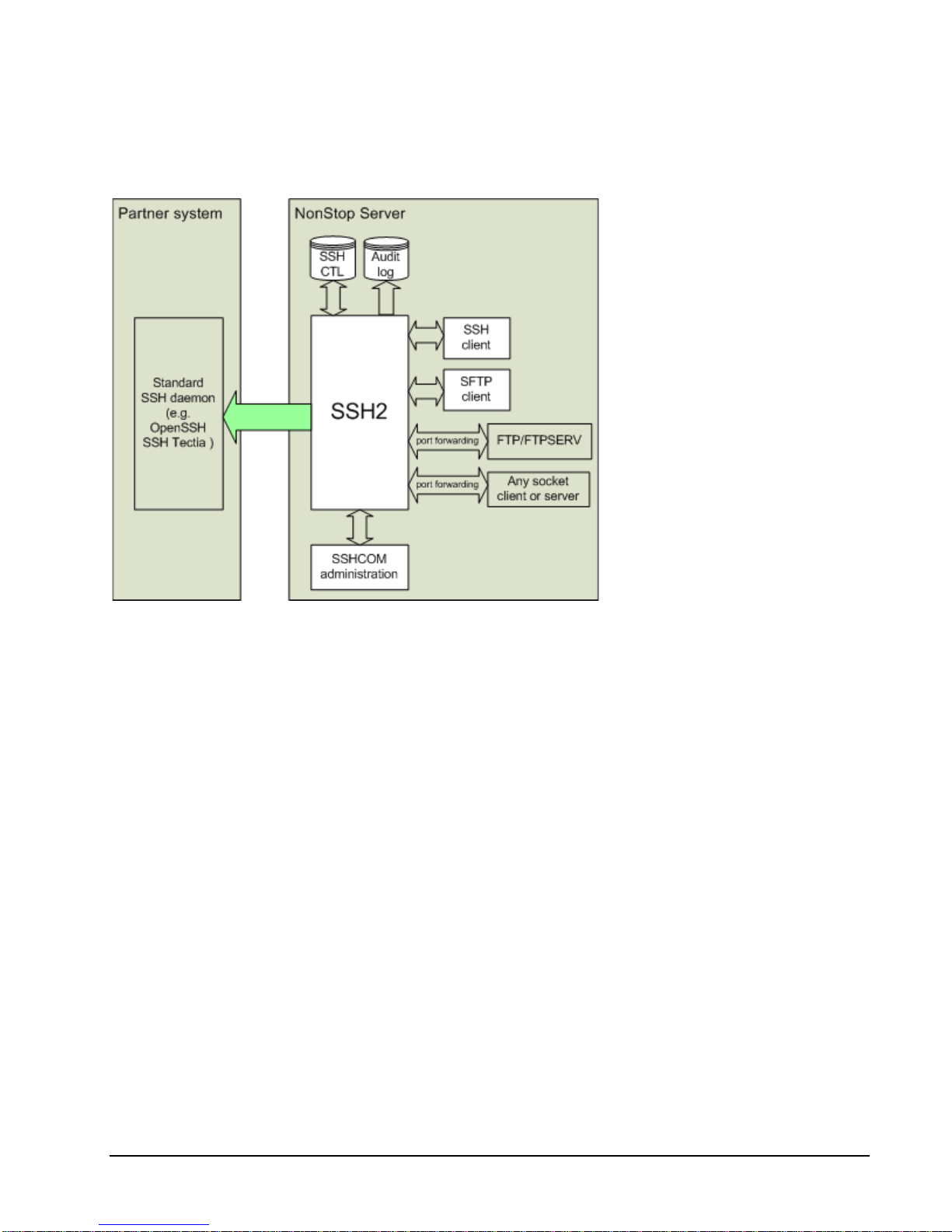
SSH2 Running as SSH Client
The following figure shows how the components of SSH2 work together to implement an SSH client running on the
NonStop platform:
Figure 2: SSH2 running as SSH client
SSH2 can interface with a range of client components, including SSH, SFTP or the equivalent OSS programs, such as
SSHOSS or SFTPOSS. With SSH2, a client component opens the SSH2 component and forwards the user commands
and the startup configuration.
The SSH2 component connects to the remote system via TCP/IP and does the setup of the SSH session. The client
component and the SSH2 component keep exchanging messages via $RECEIVE until the client is terminated by the
user.
Additionally, a client can establish port forwarding to forward TCP/IP or FTP connections from local socket programs to
the remote SSH server or vice versa.
The SSHCOM component is used to maintain the key store containing the local system user's key pairs, remote
passwords and remot e SSH host's public keys.
HP NonStop SSH Reference Manual Introduction • 29
Page 30

30 • Introduction HP NonStop SSH Reference Manual
Page 31

Installation & Quick Start
System Requirements
To run SSH2 components, associated systems must meet the following requirements:
HP NonStop host:
• G-Series: G06.21 or later.
• H-Series: H06.07 or later.
• J-Series: J06.03 or later
• OSS is not required. If present, OSS is fully supported.
Partner systems:
• An SSH client and/or daemon supporting version 2 of the SSH protocol.
Acquiring the Product Archiv es
The HP NonStop SSH product is delivered with the H-series Release Version Update (RVU) H06.11 and later, or the Jseries RVU J06.03 and later. A license file is no longer required for H06.21 and later, or J06.10 and later. These releases
correspond to SPR T0801AAQ and later. For G06.32 and G06 .32 based Time Critical Fix releases (TCFs), NonStop
SSH is only licensed for use with MR-Win6530 on the NonStop System Console (NSC) for sec ure communications with
the default IP maintenance stacks. To enable full product use you must contact your HP Sales representative for details
on licensing.
SSH2 also comes with the comForte SecurSH or SecurFTP/SSH product packages. These products require the SSH2
installation archive (SSHINST.100 or SSHINST.800, depending on the NonStop Server type) to be unpacked on the
NonStop server.
HP NonStop SSH Reference Manual Installation & Quick Start • 31
Page 32

Installation on the NonStop Server
Note(s):
• For SSH2 as part of HP NonStop SSH, the installation procedures are different and the steps outlined in
sections "Installing the SSH Components on the NonStop System" and "Quick-starting the SSH2 System"
should be skipped.
• HP NonStop SSH will be pre-installed with your H-series RVU, J-series RVU, or G-series RVU (G06.32 or
later). This enables SSH connectivity on the default TCP/IP stacks. Please refer to the SOFTDOC and support
notes details for information on enabling SSH on additional TCP/IP stacks.
• For G-Series prior to G06.32, pe rform the standard independent product installation procedure and refer to the
README file for post-installation instructions.
Both for H-Series and G-Series, the installation subvolume of HP NonStop SSH is $SYSTEM.ZSSH and the
processes are managed through the SCF Kernel manager $ZZKRN
• As of H06.22/J06.11 (SPR T0801^AAS), a configuration file named SSHMCFG has been added for exclusive
use by SSH2 processes $ZSSP0 and $ZSSP1 configured for the maintenance LANs. SSHMCFG has entries
specifying a dedicated data base SSHMDB, a dedicated host key file HOSTKEYM and log file SSHMLOG.
The original SSHCFG file can now be used for SSH2 processes configured fo r no n-m aintenance LANs, but
keep in mind that this file will be overwritten with the installation of a new RVU. A backup should be kept in
case changes have been made.
• Note that if for some reason the installation subvolume is chosen to be other than $SYSTEM.ZSSH, the startup
files (ZSSHGP, SSHCFG, SSHMCFG) must be changed to point to the correct locations. Therefore, it is
recommended to keep the production installation always in $SYSTEM.ZSSH. The executables SSH2 (SSH
server) and STN (pseudo-TTY) reside in this subvolume as well, they are not placed in $SYSTEM.SYSnn;
however, the executables SSHCOM, SSH, and SFTP are installed in $SYSTEM.SYSnn.
• The startup parameter for processes $ZSSP0 and $ZSSP1 has been modified in the ZSSHGP file for SPR
T0801^AAS, and now points to configuration file SSH MC FG instead of SSHCFG in the ADD process section
and a new ALTER process section. After a fallback to a pre-J06.11/H06.22 RVU or to an SPR prior to
T0801^AAS, the $ZSSP0 and $ZSSP1 processes will not start because their startup parameter definition points
to configuration file SSHMCFG which does not exist in pre-AAS NonStop SSH releases. The ZSSHGP file in
earlier NonStop SSH releases does not contain an ALTER section, and the "process add" commands in the
ADD section fail because the process definitions already exist. To resolve this problem, issue these commands
at a TACL prompt:
SCF DELETE PROCESS $ZZKRN.#SSH-ZTCP*
RUN ZMODGP $SYSTEM.ZSSH.ZSSHGP
SCF START PROCESS $ZZKRN.#SSH-ZTCP*
Installing the SSH Components on the NonStop System
After you have downloaded the files to your workstation, transfer the SSH2 installation archive (SSH2INS.100 or
SSHINSTI.800, depending on the NonStop Server type) to your NonStop system, alter the file code and run the
installation program.
1. Using your favorite file transfer program, transfer the SSH installation archive (SSHINST.100 or
SSHINST.800) in binary mode to your NonStop system. Copy the file to the subvolume on which you want to
install the components.
2. Alter the installation archive file code. On G-series:
FUP ALTER SSHINST, CODE 100
32 • Installation & Quick Start HP NonStop SSH Reference Manual
Page 33

On H- and J-Series
FUP ALTER SSHINST, CODE 800
3. Extract the archive by issuing the following command:
RUN SSHINST
The SSH program files will now be copied to the assigned subvolume.
4. For the Safeguard versions T9750G07^AFO/T9750H04^AFJ and later set the PRIV-LOGON bit for objects
SSH2, SFTPSERV and STN (if not already executed by DSM /SCM), e.g.:
SAFECOM ADD DISKFILE $SYSTEM.ZSSH.SSH2, PRIV-LOGON ON
SAFECOM ADD DISKFILE $SYSTEM.ZSSH.SFTPSERV, PRIV-LOGON ON
SAFECOM ADD DISKFILE $SYSTEM.ZSSH.STN, PRIV-LOGON ON
Note: Note: Macro SSH2INFO prints warning messages if the objects SSH2, SFTPSERV and STN do not have
a Safeguard DISKFILE entry with PR IV-LOGON set to ON.
The SSH2 process now also checks at startup if those objects have a Safeguard DISKFILE entry with PRIVLOGON set to ON. If this is not the case, then a warning will be logged. Without PRIV-LOGON ON, the
mentioned processes may not be able to impersonate other users correctly (needed after authentication). Not
setting PRIV-LOGON may also cause delays leading to interruption of service.
Unlocking the Product with a License File
If you did not purchase NonStop SSH with the NonStop Operating System Kernel for H Series and J Series NonStop
platforms, you will need a license file to use SSH components. The license file is tied to your system number.
The license file should be called LICENSE (which is the default name if not otherwise specified using the license
parameter) and should reside on the same subvolume as the SSH2 component. If you need to put the license file in a
different location you must use the PARAMETER LICENSE to specify the location. If there is a problem with the
license file, the SSH2 component will issue a message on startup and terminate.
If the license file is valid you will see the expiration date in a log message during startup.
Note: For HP NonStop SSH on S-Series or i f you did not purchase NonS top SSH with the NonStop Ope ra ting System
Kernel for H Series and J Series, the default SSH installation restricts the use of the product to the MR-Win6530
terminal emulator client running on a NonStop System Console, and also restricts the use of the product to certain HP
tools, such as HP Systems Insight Manager. These tools use a special key to invoke the SSH client. To unlock
functionality for gene ra l use, you will need to re quest a license file from HP. Send an email to license.manager@hp.com
and include customer name, system id, system type, and the date when the order for the software was placed.
HP NonStop SSH Reference Manual Installation & Quick Start • 33
Page 34

SSH2 License and Version Inform at ion
The SSH2 release provides a TACL macro that retrieves license and version information. After changing the current
subvolume to a subvolume containing an SSH2 installation the macro is started using the RUN command, e.g.:
VOLUME $SYSTEM.ZSSH
RUN SSH2INFO
The SSH2INFO macro will display the content of the license file (if found). First the default subvolume will be checked
when looking for the license file, then the standard installation subvolume $SYSTEM.ZSSH.
Then the macro lists the vproc information of the files SSH2, SFTPSERV, SFTP, SFTPOSS, SSH, SSHOSS, SSHCOM,
SCPOSS, STN and SHOWLOG.
For objects SFTP, SSH, SSHCOM, SHOWLOG the macro checks the default subvolume first, then subvolume
$SYSTEM.SYSnn and finally $SYSTEM.ZSSH. The vproc information of all objects found is retrieved but only the
vproc of the first object found is displayed. These objects are expected to reside in subvolume $SYSTEM.SYSnn after
the standard HP installation process.
For the other objects, namely SSH2, SFTPSERV, SFTPOSS, SSHOSS, SCPOSS, STN, the SSH2INFO macro checks
the default subvolume first, then subvolume $SYSTEM.ZSSH and finally $SYSTEM.SYSnn. The vproc information of
all objects found is retrieved but only the vproc of the first object found is displayed. These objects are expected to reside
in subvolume $SYSTEM.ZSSH after the standard HP installation process.
The retrieved vprocs ar e t he n used to execute a consistency check: A warning will be issued if an object exists in both
locations $SYSTEM.ZSSH and $SYSTEM.SYSnn and the vproc information differs.
Updating to a new version of the SSH2 fi l e set
The following describes how to upgrade to a new version of SSH2 and its related object files. It assumes that an older
version of the product is already running successfully and configured correctly.
Download of the object file set
1. Download from the comForte web site:
As first step please download the PAK archive containing the new files from the comForte web site. This will
be a single file with an extension ".100" for S-Series and extension ".800" for H-Series.
2. Transfer file to NonStop system and unPAK in scratch subvolume:
Transfer the file to the NonStop system in binary and FUP ALTER it to the file code 100/800 as indicated by
the extension. RUN the file and the new object files will be placed on the scratch subvolume.
Installation of the new version
1. Backup your existing object files.
2. Stop all SSH2 instances.
It is assumed that you have a standard way to STOP all running SSH2 instances.
3. FUP DUP the new object files from the scratch subvolume to your production subvolume.
4. Restart the SSH2 instances with the new version.
It is assumed that you have a standard way to restart the SSH2 processes.
This is the time to check that the new version of SSH2 is running properly in your environment.
5. Backing out the new version.
34 • Installation & Quick Start HP NonStop SSH Reference Manual
Page 35

In case the new version of SSH2 creates unexpected problems, revert to the old object files.
Where configuration data is stored
Other than any macros you have created, there are two data files which you want to keep in order to keep your existing
database/configuration entries: HOSTKEY stores the host key SSHCTL stores all users and configuration done through
SSHCOM.
Migration Considerations
When migrating from one NSK system to another, the original configuration can be preserved by porting the SHCTL
database, the HOSTKEY file, and the SSH configuration file to the SSH subvolume $system.zssh. The migration should
only be done for SSH2 processes associated with non-maintenance LANs. Note that the configuration file SSHCFG is a
template and will be overwritten by DSM/SCM when a new SPR is installed. Therefore, the ported configuration file
should be named differently, and the startup message in the SCF input fi l e f o r pe rs i s t ent processes (or the st a rtup obey
file) changed to point to the correct configuration file. Also take note that if a license file existed in the original
configuration, but not required any longer in the target system (SPRs >= T0801^AAQ), the customer name from the
license file must be placed as a value for parameter CUSTOMER in the configuration file.
Installation of SFTPAPI
SFTPAPI is a separately licensed module offering a programmatic interface to SFTP similar to FTPAPI for FTP.
In June, 2011, HP started to offer the SFTPAPI product which requires a special license. It enables users to easily
convert existing FTP scripts/programs to switch over to SFTP. The minimum SPR supporting this feature is
T0801^AAQ for H/J series, and T0 80 1^AAT for G-series. The HP NonStop SFTP API Reference Manual, part number
659755-nnn, describes the API in detail. Support for it is built into the SFTP client, which must be placed together with
the license into a dedicated subvolume.
Currently it is not possible to use the SSH home subvolume $SYSTEM.ZSSH because of conflicts in the license naming
and license checking. To simplify the installation process, starting with TCF T0801^AAY (H/J series) and T0801^AAZ
(G-series), the SFTP client will be distributed in $SYSTEM.SYSnn (as before) and in $SYSTEM.ZSFTPAPI. The user
needs to place the SFTPAPI license (named "LICENSE") into the $SYSTEM.ZSFTPAPI subvolume where the
additional copy of the SFTP object is located. In the program that makes the FTP API calls, the variable FTPPGM
pointing to the FTP client must be modified to point to the SFTP client $SYSTEM.ZSFTPAPI.SFTP.
Quick Start and Guided Tour
This section offers a brief example illustrating how to start SSH2. In addition, we will provide a guided tour that
illustrates how to perform various SSH related tasks with a remote SSH system.
We will base this section on some assumptions:
• OpenSSH is installed on the remote system, with sshd listening on port 22.
• The IP address of the NonStop system is 10.0.0.199.
• The IP address of the remote system is 10.0.0.201.
• The SSH2 server will listen on port 22
Some of the steps illustrated here are only covered briefly; however these steps are covered in detail in subsequent
sections of this documentation.
HP NonStop SSH Reference Manual Installation & Quick Start • 35
Page 36

Quick-Starting the SSH2 System
This section illustrates how to quickly start the SSH2 system and provides an overview of the functionality available. Fo r
production installation, you will need to consider availability, load balancing and security related issues. Please refer to
the "Configuring and Running SSH2" chapter for details.
To start the STN Pseudo Terminal Server
To enable remote SSH clients to allocate a pseudo terminal for full screen access, you will need to start an STN process
to act as a PTY server for SSH2. You may omit this step if full screen access is not required.
1. At the TACL prompt, issue the following commands:
CLEAR ALL PARAM
PARAM BACKUPCPU ANY
RUN STN/NAME $PTY, NOWAIT/
2. Verify if the process started successfully by checking its status and EMS for any error messages.
Note: For productive use of the STN component, it is recommended that you install the EMS template file ZSTNTMPL
using standard installation procedures. This will ensure that STN EMS messages will be displayed correctly.
To Start the SSH2 Component
Note: The SSH2 process must be started and run under the SUPER.SUPER logon. When started using a different user
ID, the process will issue a warning message and terminate.
1. SSH2 can be started easily. At the TACL prompt, issue the following commands:
CLEAR ALL PARAM
RUN SSH2/NAME $SSH01, CPU 1/ ALL; &
PORT 22; &
AUTOADDSYSTEMUSERS true; &
ALLOWTCPFORWARDING true; &
STRICTHOSTKEYCHECKING false
Following are details on these instructions:
• "$SSH01" is the process name of the SSH2 process. Setting the process name to "$SSHnn"—wit h nn being
the number of the CPU in which SSH2 is started—will allow the NonStop SSH and SFTP clients to
automatically find the SSH2 process handling the SSH protocol layer for them.
• In a production environment it is recommended to specify run option NOWAIT as well as run options
TERM and OUT with a virtual home terminal as value, e.g. TERM $ZHOME, OUT $ZHOME (Please
replace $ZHOME with $VHS or other process name as needed.) When you start SSH2 in NOWAIT mode,
make sure you have disabled logging to the home terminal. To do so, set PARAM LOGCONSOLE *.
• The keyword "ALL" designates that the SSH2 component will be allowing all supported functionality. (For
more information, see chapter "Configuring and Running SSH2" for details on the run modes of the SSH2
process.)
• The parameter "PORT" reflects the port number SSH2 will listen on for incoming SSH connections.
• The parameter "AUTOADDSYSTEMUSERS" controls whether remote users can log on via SSH using a
Guardian user ID or alias, without configuring them explicitly via SSHCOM in the SSHCTL.
• The parameter "ALLOWTCPFORWARDING" controls whether port forwarding is generally allowed.
• The parameter "STRICTHOSTKEYCHECKING" controls whether client access to remote systems is
limited to hosts with their public key explicitly configured as a KNOWNHOST entity in the SSHCTL.
36 • Installation & Quick Start HP NonStop SSH Reference Manual
Page 37

With this parameter set to false, users will be prompted if they want to continue a connection to an
unknown host.
Note: When you start SSH2 in NOWAIT mode, make sure you have disabled logging to the home terminal. To
do so, set the following PARAM:
PARAM LOGCONSOLE *
2. SSH2 will now start with the parameters specified in the command line. It will output initialization messages to
your terminal. Please check these messages for any errors.
Note: Set the DEFINE =TCPIP^PROCESS^NAME or the parameter SUBNET accordingly if you want to run SSH2
over a TCP/IP process other than $ZTC0.
Upon first startup, SSH2 will create a HOSTKEY for the DAEMON mode, which may take a few seconds, depending on
the speed of your system. SSH2 will also create the SSHCTL configuration data base.
Note: If you have installed SSH2 on a non-audited disk volume, SSH2 will fail to open the SSHCTL with error 80
(Invalid operation on audited file or non-audited disk volume). For testing, you may add SSHCTLAUDIT FALSE to the
startup parameters to work around this problem. For a production installation, however, it is strongly recommended that
you have SSHCTL audited. Use the SSHCTL parameter to specify a filename on an audited disk volume, if required.
A normal startup output looks similar to the following screen shot:
$SSH55|26Mar12 21:01:54.55|20|---------------------------------------------------------------$SSH55|26Mar12 21:01:54.55|10|SSH2 version T9999H06_13Mar2012_comForte_SSH2_0092
$SSH55|26Mar12 21:01:54.56|10|config file: '(none)'
$SSH55|26Mar12 21:01:54.56|20|object filename is '\NPNS01.$US.SSH92DI.SSH2'
$SSH55|26Mar12 21:01:54.56|20|object subvolume is '\NPNS01.$US.SSH92DI', priority is 11
$SSH55|26Mar12 21:01:54.70|20|dumping configuration:
[def ] ALLOWEDAUTHENTICATIONS <keyboard-interactive,password,publickey>
[def ] ALLOWEDSUBSYSTEMS <sftp,tacl>
[def ] ALLOWFROZENSYSTEMUSER <FALSE>
[def ] ALLOWINFOSSH2 <ALL>
[def ] ALLOWPASSWORDSTORE <TRUE>
[def ] ALLOWTCPFORWARDING <FALSE>
[def ] AUDITCONSOLE <*>
[def ] AUDITFILE <*>
[def ] AUDITFILERETENTION <10>
[def ] AUDITFORMAT <21>
[def ] AUDITMAXFILELENGTH <20000>
[def ] BACKUPCPU <NONE>
[def ] BANNER <*>
[def ] CIPHERS <aes256-cbc,twofish256-cbc,twofish-cbc,aes128-cbc,twofish128-cbc,blowfish-cbc,3des-cbc,arcfour,cast128-cbc>
[def ] CLIENTALLOWEDAUTHENTICATIONS <none,gssapi-with-mic,publickey,password,keyboard-interactive>
[def ] CLIENTMODEOWNERPOLICY <BOTH>
[def ] COMPRESSION <TRUE>
[def ] CONFIG <>
[def ] CONFIG2 <*>
[def ] CPUSET <>
[run ] CUSTOMER <comForte GmbH>
[def ] ENABLESTATISTICSATSTARTUP <FALSE>
[def ] EXECTACL <TRUE>
[def ] FULLSSHCOMACCESSGROUP1 <>
[def ] FULLSSHCOMACCESSUSER1 <>
[def ] GSSAUTH <*>
[def ] GSSGEXKEX <FALSE>
[def ] GSSKEX <TRUE>
[def ] GUARDIANATTRIBUTESEPARATOR <,>
[def ] HOSTKEY <HOSTKEY>
[def ] INTERFACE <0.0.0.0>
[def ] INTERFACEOUT <0.0.0.0>
[def ] INTERVALLIVEPRIVATEUSERKEY <730>
[def ] INTERVALLIVEPUBLICUSERKEY <730>
[def ] INTERVALPENDINGPRIVATEUSERKEY <0>
[def ] INTERVALPENDINGPUBLICUSERKEY <0>
[def ] IPMODE <IPV4>
[def ] LICENSE <\NPNS01.$US.SSH92DI.LICENSE>
[def ] LIFECYCLEPOLICYPRIVATEUSERKEY <DISABLED>
[def ] LIFECYCLEPOLICYPUBLICUSERKEY <DISABLED>
[def ] LOGCACHEDUMPONABORT <TRUE>
[def ] LOGCACHESIZE <1024>
[def ] LOGCONSOLE <%>
[def ] LOGEMS <*>
[def ] LOGEMSKEEPCOLLECTOROPENED <TRUE>
[def ] LOGFILE <*>
[def ] LOGFILERETENTION <10>
[def ] LOGFORMATCONSOLE <93>
[def ] LOGFORMATEMS <16>
[def ] LOGFORMATFILE <93>
[def ] LOGLEVELCACHE <50>
HP NonStop SSH Reference Manual Installation & Quick Start • 37
Page 38

[def ] LOGLEVELCONSOLE <50>
[def ] LOGLEVELEMS <20>
[def ] LOGLEVELFILE <50>
[def ] LOGMAXFILELENGTH <20000>
[def ] LOGMEMORYDETAILED <0>
[def ] MACS <hmac-sha1,hmac-md5,hmac-sha1-96,hmac-md5-96>
[def ] PARTIALSSHCOMACCESSGROUP1 <>
[def ] PARTIALSSHCOMACCESSUSER1 <>
[run ] PORT <55022>
[def ] PTCPIPFILTERKEY <*>
[def ] PTYSERVER <$PTY>
[def ] RECORDDELIMITER <LF>
[def ] RESTRICTIONCHECKFAILEDDEFAULT <FALSE>
[def ] SFTPALLOWGUARDIANCD <FALSE>
[def ] SFTPCPUSET <>
[def ] SFTPEDITLINEMODE <none>
[def ] SFTPEDITLINENUMBERDECIMALINCR <1000>
[def ] SFTPEDITLINESTARTDECIMALINCR <-1>
[def ] SFTPEXCLUSIONMODEREAD <SHARED>
[def ] SFTPIDLETIMEOUT <-1>
[def ] SFTPMAXEXTENTS <900>
[def ] SFTPPRIMARYEXTENTSIZE <2>
[def ] SFTPSECONDARYEXTENTSIZE <100>
[def ] SFTPUPSHIFTGUARDIANFILENAMES <FALSE>
[def ] SOCKETKEEPALIVE <1>
[def ] SOCKETRCVBUF <0>
[def ] SOCKETSNDBUF <0>
[def ] SOCKTCPMAXRXMT <0>
[def ] SOCKTCPMINRXMT <0>
[def ] SOCKTCPRXMTCNT <0>
[def ] SOCKTCPTOTRXMTVAL <0>
[def ] SSHAUTOKEXBYTES <1073741824>
[def ] SSHAUTOKEXTIME <3600>
[def ] SSHCTL <SSHCTL>
[def ] SSHCTLAUDIT <TRUE>
[def ] SSHKEEPALIVETIME <60>
[def ] STOREDPASSWORDSONLY <FALSE>
[def ] STRICTHOSTKEYCHECKING <TRUE>
[run ] SUBNET <$ZTC1>
[def ] SUPPRESSCOMMENTINSSHVERSION <FALSE>
[def ] TCPIPHOSTFILE <*>
[def ] TCPIPNODEFILE <*>
[def ] TCPIPRESOLVERNAME <*>
$SSH55|26Mar12 21:01:54.81|10|CRYPTOPP version T9999H06_03Mar2012_comForte_CRYPTOPP_0023
$SSH55|26Mar12 21:01:54.84|10|SSH config database SSHCTL opened.
$SSH55|26Mar12 21:01:54.85|20|parameter SUBNET was evaluated
$SSH55|26Mar12 21:01:54.85|20|DEFINE =TCPIP^PROCESS^NAME was set to <\NPNS01.$ZTC1>
$SSH55|26Mar12 21:01:54.85|20|TCP/IP process is $ZTC1
$SSH55|26Mar12 21:01:55.04|20|DEFINE =SSH2^PROCESS^NAME was set to <\NPNS01.$SSH55>
$SSH55|26Mar12 21:01:55.04|10|Initializing SSH2 ADMIN run mode.
$SSH55|26Mar12 21:01:55.05|10|Initializing SSH2 CLIENT run mode.
$SSH55|26Mar12 21:01:55.05|10|Initializing SSH2 DAEMON run mode.
$SSH55|26Mar12 21:01:55.22|10|Loading private key from HOSTKEY
$SSH55|26Mar12 21:01:55.39|30|Host key algorithm: ssh-dss
$SSH55|26Mar12 21:01:55.39|30|Host key MD5 fingerprint: 87:33:4c:98:3e:a4:
Secure Shell Access to the NonStop Server
Note: This functionality is not enabled if you purchased a license restricted to file transfer ("HP NonStop SSH –
SecureFTP" or "comForte SecurFTP/SSH").
SSH2 allows remote SSH clients to establish fully functional OSS shell sessions. SSH2 will also support the allocation
of pseudo terminals (PTYs), which allow the remote users to execute full screen applications, such as vi or Emacs.
To Open an OSS Shell Using a Remote SSH Cl ient
Note: This functionality requires OSS to be installed and running on your system.
After the STN and SSH2 processes have started successfully, you can now connect using an SSH client on a remote
system. In the SSH command, you have to specify the Guardian userid and the IP address or host name that SSH2 is
listening on:
m.horst@np-dev02:~> ssh comf.mh@10.0.0.199
The authenticity of host '10.0.0.199 (10.0.0.199)' can't be established.
DSA key fingerprint is 26:b8:77:fb:2f:22:81:3b:f6:44:4f:19:66:67:9a:be.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.0.0.199' (DSA) to the list of known hosts.
38 • Installation & Quick Start HP NonStop SSH Reference Manual
Page 39

comf.mh@10.0.0.199's password:
$ ls
a1000 emsacstm secret t10mio trace2 zrand1m
auditlog ftps sftpserv taclcstm tracecap zz10mio
bashhist fupcstm shhistor test z1000000 zz1mio
bench osstest stna48 test101 z1mio zzsa1894
benchcpu osstzip t1000 testbin z1mio2 zzsa7884
benchs2k rand1mio t10000 testbin2 z1mio3 zzz10m
benchs3k rs120157 t100000 testbin3 z1mioftp zzz1mio
cryptand scfcstm t1000000 testbin4 z50mio
$
Please note that the Guardian userid is specified on the SSH command line.
Note: The very first time you connect, you will have to verify the authenticity of the host by adding the fingerprint of the
host's public key to the trust list.
To Get a TACL Prompt Using a Remote SSH Cl ient
You can also directly establish a connection to a TACL process, without involving any OSS functionality. Direct TACL
access is provided by SSH2 as an SSH2 subsystem. You may connect to the TACL subsystem by specifying starting the
remote SSH client with the –s option and "tacl" as subsystem name. Like with an ordinary shell session, you have to
specify the Guardian userid and the IP address or host name, where SSH2 is listening on as parameters for the SSH
command:
m.horst@np-dev02:~> ssh -s comf.mh@10.0.0.199 tacl
comf.mh@10.0.0.199's password:
TACL (T9205D46 - 19OCT2004), Operating System G06, Release G06.25.00
(C)1985 Tandem (C)2004 Hewlett-Packard Development Company, L.P.
CPU 1, process has no backup
February 10, 2006 13:09:41
(Invoking $SYSTEM.SYSTEM.TACLLOCL)
(Invoking $DATA1.MHHOME.TACLCSTM)
Current volume is $DATA1.MHHOME
1>
Note: Standard SSH clients will only suppor t lin e mode interaction. You will not be able to invoke any block mode
applications or applications that use advanced 6530 terminal features, unless using a SSH client supporting 6530
terminal sessions over SSH, such as comForte's MR-Win6530.
Secure Shell Access from NonStop to Remote Systems
Note: This functionality will be not be available with the SecurFTP/SSH and SecurTN products.
SSH2 includes two SSH clients, which allow the creation of secure shell sessions with a remote SSH daemon:
• SSHOSS is the OSS version of the SSH client. It provides fully functional terminal access to remote systems
and, like SSH2 as a daemon, supports execution of full screen applications such as vi or Emacs, with the
NonStop terminal as input and output device. It also allows establishing TCP and FTP port forwarding
channels.
• SSH is the Guardian version of the SSH client. It allows you to create remote shells and execute remote
commands and it supports port forwarding channels.
Note: SSH and SSHOSS will connect to a remote SSH daemon via a SSH2 process, which handles the SSH protocol
layer.
HP NonStop SSH Reference Manual Installation & Quick Start • 39
Page 40

To Connect to a Remote SSH Daemon wi th the NonStop SSH Client
You can create shell sessions with a remote SSH daemon both with the OSS SSH client (via SSHOSS) and the Guar dian
SSH client ( via SSH).
From an OSS shell, run the SSHOSS client to create a secure shell session with a remote system as follows:
/home/mh: /G/data1/mhssh/sshoss comf.mh@10.0.0.201
comForte SSH client version T9999G06_28Dec2007_comForte_SSHOSS_ 0077
WARNING: REMOTE HOST IDENTIFICATION UNKNOWN!
The host public key fingerprint is
babble: xelol-vifez-cefis-gimiv-nepof-zemid-latut-zahoz-hyrun-hipop-hixex
MD5: 04:bb:3c:a0:66:d4:bf:e3:60:b8:f3:31:49:d9:86:a6
Continue and add the host to the knownhost store(yes/no)? yes
Trying password authentication.
Enter m.horst@10.0.0.201's password:
Add password for m.horst@10.0.0.201 to the password store (yes/no)? no
Have a lot of fun...
m.horst@np-dev:~>
Note: For a production installation you may want to copy the SSHOSS program to an OSS standard bin directory,
renaming it to "ssh". Alternatively, you may also create a symbolic link.
At the TACL prompt, run the SSH client to execute a command on a remote system as follows:
$DATA1 MHSSH 286> run ssh m.horst@10.0.0.201 whoami
comForte SSH client version T9999H06_28Dec2007_comForte_SSH_0077
You have no private keys in the key store.
Trying password authentication.
Enter m.horst@10.0.0.201's password:
Add password for m.horst@10.0.0.201 to the password store (yes/no)? no
m.horst
$SYSTEM ZSSH 287>
To Establish a Port Forwarding Tunnel with the NonStop SSH Client
Forwarding Local Port to Remote Port
You can create port forwarding channels for both the OSS SSH client (SSHOSS) and the Guardian SSH client (SSH).
The following example illustrates how to establish a port forwarding tunnel for telnet sessions over SSH, using the
Guardian SSH client:
$US SSH90 46> run ssh -N -L 5021:localhost:23 joe@10.0.0.111
SSH client version T9999H06_08Jun2011_comForte_SSH_0090
The –N option suppresses the start of a remote shell. The –L option tells SSH2 to listen on port 5021 and forward any
incoming connection to the remote SSH daemon and further to a telnet server on the same host, listening on port 23. The
"localhost" in the command line refers to the target host of the forwarding tunnel, i.e. when using -L option this is the
remote host.
After the SSH session is successfully established, the SSH process will wait until the SSH session is terminated or it is
stopped. Thus, if you hit <break>, you can get the TACL prompt back and try to connect a telnet session over the SSH
tunnel:
<break>
$US SSH90 47> telnet 127.0.0.1 5021
TELNET Client - T9558H01 - (10MAY07) - (IPMAAG)
Copyright Tandem Computers Incorporated 2004
Trying...Connected to 127.0.0.1.
Escape character is '^]'.
Welcome to SuSE Linux 8.2 (i586) - Kernel 2.4.20-4GB (0).
np-dev login:
40 • Installation & Quick Start HP NonStop SSH Reference Manual
Page 41

In this example the local telnet client connects through the tunnel to the telnet server on remote host 10.0.0.111 that
listens on loopback address 127.0.0.1, port 23.
Forwarding Remote Port to Local Port
Port forwarding channels can also be enabled in the opposite direction, i.e. from a remote port to a local port. The
following example illustrates how to establish an SSH port forwarding tunnel from a remote host to the local host, using
the Guardian SSH client:
$US SSH90A 48> run ssh -N -R 5021:localhost:23 testusr@10.0.0.234
SSH client version T9999H06_08Jun2011_comForte_SSH_0090
The –N option suppresses the start of a remote shell. The –R option tells the re mote S SH daemon on host 10.0.0.234 to
listen on port 5021 and forward any incoming connection on that port to the local SSH2 process and this local process
will further forward to a telnet server on the local host, listening on loopback address, port 23. The "localhost" in the
command line refers to the target host of the forwarding tunnel, i.e. when using -R option this is the local host.
After the SSH session is successfully established, the SSH process will wait until the SSH session is terminated or it is
stopped.
On the remote host 10.0.0.234 you can establish a telnet session over the SSH tunnel as follows:
testusr@linux-dev:~$ telnet 127.0.0.1 5021
TELNET Client - T9558G06 - (11JUL03) - (IPMAAE)
Copyright Tandem Computers Incorporated 1992-1997
Trying...Connected to 127.0.0.1.
Escape character is '^]'.
WELCOME TO npns01 [PORT $ZTC1 #23 WINDOW $ZTN0.#PTYSYNS]
TELSERV - T9553H01 - (25SEP2009) - (IPMAEP)
Available Services:
OSS TACL EXIT
Enter Choice>
In this example the remote telnet client started on host 10.0.0.234 connects through the tunnel to the telnet server on the
local host that listens on loopback address 127.0.0.1, port 23.
Encrypted File Transfer
You can implement encrypted file transfers over SSH in various ways:
• Use the SFTP or SFTPOSS clients to initiate and control SFTP sessions from the NonStop server
• Use an SFTP client on a remote system to initiate and control SFTP sessions to the NonStop server from a
remote system.
• Forward FTP connections over an SSH session.
To Connect a Remote SFTP Client to the NonStop Server
You can connect with an SFTP client on a remote system to SSH2 listening on the NonStop server as follows:
m.horst@np-dev02:~> sftp comf.mh@10.0.0.199
Connecting to 10.0.0.199...
comf.mh@10.0.0.199's password:
sftp> dir
a1000 auditlog bashhist bench benchcpu benchs2k benchs3k cryptand
emsacstm ftps fupcstm osstest osstzip rand1mio rs120157 scfcstm
secret sftpserv shhistor ssh stna48 t1000 t10000 t100000
t1000000 t10mio taclcstm test test101 testbin testbin2 testbin3
testbin4 trace2 tracecap z1000000 z1mio z1mio2 z1mio3 z1mioftp
HP NonStop SSH Reference Manual Installation & Quick Start • 41
Page 42

z50mio zrand1m zz10mio zz1mio zzsa1894 zzsa7884 zzshgd zzz10m
zzz1mio
sftp>
To Connect to a Remote SSH Daemon from the NonStop Server Using a
NonStop SFTP Client
At the TACL prompt, run the SFTP client to create an SFTP session with a remote system as follows:
$DATA1 MHSSH 20> run sftp m.horst@10.0.0.201
comForte SFTP client version T9999G06_27Jan2006_comForte_SFTP_A01_0060
Connecting to 10.0.0.201...
You have no private keys in the key store.
Trying password authentication.
Enter m.horst@10.0.0.201's password:
Add password for m.horst@10.0.0.201 to the password store (yes/no)? no
sftp> ls -l
drwxr-xr-x 0 509 100 824 Jan 19 15:03 .
drwxr-xr-x 0 0 0 688 Nov 24 19:57 ..
-rw-r--r-- 0 509 100 6340 Jun 19 2003 .Xdefaults
drwxr-xr-x 0 509 100 168 Jun 19 2003 Documents
-rw-r--r-- 0 509 100 990000 Jan 19 15:00 ktest2
-rwxr-xr-x 0 509 100 1000000 Jan 19 14:58 ktestbig
drwxr-xr-x 0 509 100 80 Jun 19 2003 public_html
drwxr-xr-x 0 509 100 192 Nov 23 08:13 sshtest
sftp>
To Create an FTP Port Forwarding Tunnel wit h a NonStop SSH Client
You can establish FTP port forwarding channels for both the OSS SSH client (SSHOSS) and the Guardian SSH client
(SSH). The following example illustrates this using the Guardian SSH client:
Run SSH as follows:
$DATA1 MHSSH 5> run ssh -N -L ftp/5021:localhost:21 m.horst@10.0.0.201
comForte SSH client version T9999G06_27Jan2006_comForte_SSH_A01_0060
You have no private keys in the key store.
Trying password authentication.
Enter m.horst@10.0.0.201's password:
Add password for m.horst@10.0.0.201 to the password store (yes/no)? no
The –N option suppresses the start of a remote shell. The -L ftp/5021:localhost:21 option tells SSH2 to listen on port
5021 and forward any incoming FTP connection to the remote SSH daemon and further to an FTP server on the same
host, listening on port 21.
After the SSH session is successfully established, the SSH process will quietly wait until the SSH session is terminated
or it is stopped. Thus, if you hit <break>, you can get the TACL prompt back and try to connect an FTP session over the
SSH tunnel:
<break>
$DATA1 MHSSH 19> ftp
FTP Client - T9552G07 - (29JUL2005) - COPYRIGHT TANDEM COMPUTERS INCORPORATED 20
05
ftp> open 127.0.0.1 5021
Connecting to 127.0.0.1.........Established.
220 np-dev.np-comforte.de FTP server (Version 6.5/OpenBSD, Linux port 0.3.3) rea
dy.
Name (127.0.0.1:user): m.horst
331 Password required for m.horst.
Password:
230- Have a lot of fun...
230 User m.horst logged in.
ftp> dir
200 PORT command successful.
150 Opening BINARY mode data connection for '/bin/ls'.
total 2062
-rw-r--r-- 1 m.horst users 6340 Jun 19 2003 .Xdefaults
42 • Installation & Quick Start HP NonStop SSH Reference Manual
Page 43

drwxr-xr-x 5 m.horst users 168 Jun 19 2003 Documents
-rw-r--r-- 1 m.horst users 990000 Jan 19 15:00 ktest2
-rwxr-xr-x 1 m.horst users 1000000 Jan 19 14:58 ktestbig
drwxr-xr-x 2 m.horst users 80 Jun 19 2003 public_html
drwxr-xr-x 3 m.horst users 192 Nov 23 08:13 sshtest
226 Transfer complete.
1766 bytes received in 0.05 seconds (34.49 Kbytes/s)
ftp>
Due to the nature of the FTP protocol the forwarding of an FTP session is more complex than for example a telnet
session (an FTP session usually consists of a data and a control channel, each established in a different direction). The
remote SSH daemon must support the forwarding of FTP sessions (not all SSH daemon implementations are able to
handle FTP forwarding).
Similar to the example under “Forwarding Remote Port to Local Port” in section "To Establish a Port Forwarding Tunnel
with the NonStop SSH Client", the -R option can be used to forward an FTP connection from a remote host to the local
host.
To Connect a Remote SCP Client to the NonStop Server
The SCPOSS object must be available in OSS name space under the name scp and must be found via the PATH
environment variable. This can be achieved by creating a symbolic link to the installation location, e.g.
ln -s /G/system/zssh/scposs /usr/bin/scp
The environment variable ENV must be set via user attribute SHELL-ENVIRONMENT to ensure the PATH
environment variable gets set appropriately. This can be achieved, e.g. by altering the user as follows (/etc/profile is just
an example and often not a good choice):
ALTER USER test.us, SHELL-ENVIRONMENT /etc/profile
Ensure that shell scripts executed via ENV do not produce any output on stdout.
After the preparation is done you can connect with an SCP client on a remote system to SSH2 listening on the NonStop
server as follows:
test@np-dev02:~/testsftp> rm bigtxt
test@np-dev02:~/testsftp> scp test.us@10.0.0.196:bigtxt .
test.us@10.0.0.196's password:
bigtxt 100% 640KB 640.0KB/s 00:00
test@np-dev02:~/testsftp> ls bigtxt
bigtxt
Using Public Keys to Authenticate Remote Users
This section describes how SSH2 can authenticate remote users using public keys. This involves creating a public key
for the user on the remote system, and making the public key known to SSH2 on the NonStop server. After performing
the steps described below, you should be able to connect to the NonStop server with your remote SSH or SFTP client
using only the public key, without entering the NonStop user's password (you may still be prompted for the private key
passphrase, though).
For additional information on public key authentication, please refer to the "Public Key Authentication" section in the
"SSH Protocol Reference" chapter.
To Generate a Key Pair on an OpenSSH System
On the remote system, use the following command of OpenSSH (for details of key generation, please refer to the
OpenSSH documentation):
>ssh-keygen -t dsa -C "comf.mh@10.0.0.199"
Generating public/private dsa key pair.
Enter file in which to save the key (/home/m.horst/.ssh/id_dsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
HP NonStop SSH Reference Manual Installation & Quick Start • 43
Page 44

Your identification has been saved in /home/m.horst/.ssh/id_dsa.
Your public key has been saved in /home/m.horst/.ssh/id_dsa.pub.
The key fingerprint is:
87:34:41:65:e5:df:e3:30:f6:46:22:02:19:24:1e:f2 comf.mh@10.0.0.199
>
Now the SFTP client will use this key whenever it connects to 10.0.0.199.
To Add the Public Key to the NonStop SSH2 User Database
Before a user can connect using public key authentication, the public key needs to be added to the user database. Using
the SSHCOM component on the NonStop server, add the public key to the user as shown in the following example (note
that the fingerprint was copied from the output of the previous step):
$DATA1 SSH2 12> sshcom $ssh01
T9000B03_02DEC2009_SSHCOM
OPEN $ssh01
% ALTER USER comf.mh, publickey key1 fingerprint
87:34:41:65:e5:df:e3:30:f6:46:22:02:19:24:1e:f2, sftp-initial-directory /home/mh
OK, user comf.mh altered
% exit
exit
$DATA1 SSH2 13>
Note: The ALTER USER command will only work if the user already exists in the SSH2 userbase. This will be the case
if you followed the other quick tour steps. You may also create a new user with the SSHCOM ADD USER command.
After this step you can now retry the step "To connect to a remote SSH daemon with the NonStop SSH client ". You will
not be prompted for the NonStop user's password . Ins t e ad, SSH2 will authent icate the user with the pu blic key
configured for the rem ote user.
Using Public Keys to Logon to Remote Systems
This section explains the steps required to use public keys to authenticate to the remote system with a NonStop SSH or
SFTP client. This involves generating a key pair for the NonStop user and configuring the public key on the remote
system.
For additional information on public key authentication, please refer to the "Public Key Authentication" section in the
"SSH Protocol Reference" chapter.
Note: The commands illustrated in the following steps will implicitly depend on the user issuing the commands. It is
assumed all commands executed under the same user ID.
To Generate a Key Pair for a NonStop User
First, we will generate the key pair and store the private key in the SSH2 user database using SSHCOM from a TACL
prompt:
$DATA1 SSH2 7> run sshcom $ssh01
T9000B03_02DEC2009_SSHCOM
OPEN $ssh01
% mode client
mode client
OK, switched to client mode
% generate key test1, type rsa, comment "Thomas key"
generate key comf.tb:test1, type rsa, comment "Thomas key"
OK, key comf.tb:test1 successfully generated
%
Now the key has been generated and stored in the database. The next step will export that key and configure it on the
remote system.
44 • Installation & Quick Start HP NonStop SSH Reference Manual
Page 45

To Export the Public Key and Configure it on the Remote System
The following command within SSHCOM will export the public part of the key just generated and write it into a file:
$DATA1 SSH2 7> run sshcom $ssh01
T9000B03_02DEC2009_SSHCOM
OPEN $ssh01
% export key comf.tb:test1, file $data1.tbtmp.tbkey, format openssh
export key comf.tb:test1, file $data1.tbtmp.tbkey, format openssh
OK, key comf.tb:test1 exported
%
Note: If you are executing SSHCOM as SUPER.SUPER, you will need to switch to CLIENT mode before exporting the
key. Please issue following command before the EXPORT KEY command:
MODE CLIENT
The file $data1.tbtmp.tbkey now needs to be transferred to the remote system in BINARY mode. Note that the file
contains only the public key and therefore contains no sensitive information.
The public key exported to the tbkey file can now be transferred to the remote system. The next step will configure the
public key for the remote user.
To Configure the Public Key on the Remote System
The OpenSSH implementation keeps a directory called ".ssh" for each user. A file named "authorized keys" is located in
the .ssh directory that contains the public key of each trusted key of a remote system. In order to add the public key
contained in the file created in the prior step, the UNIX command "cat" can be used to add the content to the existing
content in the file. The following commands are again executed on the remote system, this time using "normal user"
logon credentials.
burgt@np-dev:~> pwd
/home/burgt
burgt@np-dev:~> cd .ssh
burgt@np-dev:~/.ssh> more pubkey
ssh-rsa
AAAAB3NzaC1yc2EAAAABEQAAAIEAkdR/ncHRVEJteOC1EMSkMgrrXpdcc6Lkejp7mcFKYNa0tMqP4eknTyFXUX
2jm1K7AKDh1Je52aqNJTBAIPIM
Bt+HboBKwjuZtb2+f1HG4LEA71NymoVcuABVyr1DvWPtpNzCNjaD0qdkR9yMlDZH/DCD/OqdneLJQ8B3RXbKl1
U= TB's RSA key
burgt@np-dev:~/.ssh> cat pubkey >> authorized_keys
burgt@np-dev:~/.ssh>
In the commands above
• The user's home directory is /home/burgt .
• The public key was transferred to the remote system under the location /home/burgt/.ssh/pubkey .
• The final command adds pubkey to authorized_keys. Please note the double '>>'; if you use only one '>', you
will overwrite authorized_keys with the content of pubkey.
After this step you can now retry the step "To connect with a remote SSH client". You will not be prompted for the
remote user's password. Instead, SSH2 will use the key pair configured for your NonStop user ID.
HP NonStop SSH Reference Manual Installation & Quick Start • 45
Page 46

46 • Installation & Quick Start HP NonStop SSH Reference Manual
Page 47

Configuring and Running SSH2
Configuration Overview
Administrators can specify configuration parameters of SSH2 processes through each of the following means:
• A configuration file
• PARAM commands
• Startup command line parameters
These different options enable system administrators to easily manage installations with multiple SSH2 processes,
including those running on multiple TCP/IP processes and ports as well as in different modes. For example, several
SSH2 processes that have identical SSH configurations can share the same configuration file, which streamlines
administration. On the other hand, process-unique parameters, such as the port to listen on, can be specified on the
command line.
On startup, SSH2 parses the sources of configuration parameter. A single parameter may be specified in multiple
sources, e.g. in the configuration file and on the startup command line. In this case, SSH2 will process parameters with
the following precedence (highest to lowest):
1. PARAM parameter
2. Parameter from configuration file 2 (CONFIG2)
3. Parameter from configuration file 1 (CONFIG)
4. Startup line parameter
This means that a parameter given in the configuration file will override the value given for the same parameter on the
startup line. Likewise, a parameter value given as a PARAM command will override any value specified in the
configuration file.
All SSH2 parameters can be specified in any of the configuration parameter sources, except in the following instances:
• The run mode of an SSH2 process is specified explicitly on the command line as the first startup line parameter.
This parameter defines the general functionality the SSH2 process will provide. (See the "Starting SSH2"
section for details.)
• The configuration file to be used as a parameter source can only be specified as a PARAM or startup line
parameter, not in a configuration file.
It is important to note that parameter names are case insensitive, regardless of the manner in which way they are
specified.
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 47
Page 48

The Configuration File
Configuration files can be modified with a standard NonStop editor, such as TEDIT. The name of the file that a SSH2
process should use as the configuration source is passed to the program during startup. (See the "Starting SSH2" section
for details.)
The file contains entries in the following form:
parameter-name parameter-value
Like in the standard TCP/IP configuration files, any lines starting with a "#" character are interpreted as comments.
Following is a sample configuration file for running SSH2 as a server that provides SFTP functionality:
# sample configuration file for a SSH2 server
#--------------------------------------------------------------------------------# general settings
# TCP/IP process the server runs on
SUBNET $ZTC1
# port where SSH2 listens for incoming SSH connections
# we use the well-known SSH port
PORT 22
# file name of host key file
HOSTKEY hostkey
# file name of user database file
SSHCTL SSHCTL
#--------------------------------------------------------------------------------# log configuration
# set the level
LOGLEVEL 50
# enable console logging to $0
LOGCONSOLE $0
# additionally log to file
LOGFILE $data1.ssh2.ssh2log
PARAM Commands
The following PARAM command can be used to set SSH2 configuration parameters:
PARAM <parameter name> <parameter value>
If the parameter value contains one or more commas, it must be included in double quotes (see PARAM command in the
NonStop "TACL Reference Manual" for use of comma as separator):
PARAM <parameter name> "<parameter value>"
All available SSH2 parameters can be specified using PARAM commands. But please be aware of the limitations
described in the TACL Reference Manual: "TACL reserves 1024 bytes of internal storage for parameters and their
values. The number and length of parameters in effect are limited by this storage area."
The following example demonstrates how to use a PARAM command to start an SSH2 server listening on $ZTC03, port
22:
> PARAM PORT 22
> PARAM SUBNET $ZTC03
> RUN SSH2/ NAME $SSH02 / SERVER
48 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 49

Startup Line Parameters
SSH2 configuration parameters can be passed on the startup line as follows:
<parameter name> <parameter value>; <parameter name> <parameter value>; ...
The following example demonstrates how to start multiple SSH2 instances that share the same SSHCONF configuration
file listening on different subnets using the same port:
> PARAM CONFIG SSHCONF
> RUN SSH2 /NAME $SSH00, CPU 0, NOWAIT/ SERVER; SUBNET $ZTC0; PORT 22
> RUN SSH2 /NAME $SSH01, CPU 1, NOWAIT/ SERVER; SUBNET $ZTC1; PORT 22
> RUN SSH2 /NAME $SSH02, CPU 2, NOWAIT/ SERVER; SUBNET $ZTC2; PORT 22
> RUN SSH2 /NAME $SSH03, CPU 3, NOWAIT/ SERVER; SUBNET $ZTC3; PORT 22
For a complete description of the RUN SSH2 command, see the "Starting SSH2" section.
Starting SSH2
Note: The SSH2 process must be started and run under the SUPER.SUPER logon. When started using a different user
ID, the process will issue a warning message and terminate.
You create a SSH2 process by issuing a TACL RUN command using the following syntax:
RUN SSH2 / runoptions / mode [ ; paramname paramvalue; ... ]
Following is a description of each aspect:
• runoptions are the standard Guardian RUN options, such as IN, CPU, or TERM.
• mode defines the "run mode" of the SSH2 process. The so-called run mode defines which functionality that
instance will allow. The following run modes are defined:
DAEMON
DAEMON_ADMIN combines the run modes DAEMON and ADMIN
CLIENT
CLIENT_ADMIN combines the run modes CLIENT and ADMIN
ADMIN
NOADMIN combines the run modes DAEMON and CLIENT
ALL combines all run modes
runs a daemon process that provides the SFTP service to remote clients. No other
functionality is provided.
runs a process that allows local SFTP clients to connect to the SSH2 process. No other
functionality is provided.
runs a process that allows SSHCOM instances to connect to the SSH2 process and to
configure the user database. No other functionality is provided.
(SERVER can be used instead of DAEMON)
• paramname paramvalue ; ... is a list of SSH2 configuration parameter settings as described in the previous
section.
Note: When you start SSH2 in NOWAIT mode, make sure you have disabled logging to the home terminal. To do so,
set the following PARAM:
PARAM LOGCONSOLE *
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 49
Page 50

SSH2 Parameter Reference
This section describes all available SSH2 parameters in alphabetical order. Note that parameter names are case
insensitive, regardless of the source in which they appear.
Some of the parameters are also valid for clients, please reference section "FILE I/O parameters for SFTP/SFTPOSS".
Parameter Overview
The following table lists all available SSH2 parameters and their meanings:
Parameter Meaning
ALLOWEDAUTHENTICATIONS Sets the list of allowed authentications for users automatically added to SSHCTL
ALLOWEDSUBSYSTEMS
ALLOWFROZENSYSTEMUSER
ALLOWINFOSSH2 Controls who is allowed to execute SSHCOM command INFO SSH2.
ALLOWPASSWORDSTORE
ALLOWTCPFORWARDING Allows global configuration of TCP port forwarding.
AUDITCONSOLE Determines whether audit messages are written to the console.
AUDITEMS Determines whether audit messages are written to EMS.
AUDITFILE Determines whether audit messages are written to a file.
AUDITFILERETENTION Controls audit file rollover.
AUDITFORMAT Controls the format of the audit messages that are written.
AUDITFORMATCONSOLE Controls the format of the audit messages that are written to the console.
AUDITFORMATEMS Controls the format of the audit messages that are written to EMS.
AUDITFORMATFILE Controls the format of the audit messages that are written to a file.
AUDITMAXFILELENGTH Controls the maximum size of the audit file.
AUTOADDSYSTEMUSERS
AUTOADDSYSTEMUSERSLIKE
BACKUPCPU Specifies a backup CPU for running SSH2 as a NonStop process pair.
BANNER
CIPHERS Details the list of cipher suites that will be accepted.
CLIENTALLOWEDAUTHENTICATIONS
CLIENTMODEOWNERPOLICY Defines security granularity for client mode SSH2 database.
COMPRESSION Specifies whether compressed SSH sessions are supported.
CONFIG Specifies the file name of an SSH2 configuration file.
CONFIG2 Specifies the file name of a second configuration file for an SSH2 process.
CPUSET Specifies the default value for USER attribute CPU-SET.
CUSTOMER
DISCONNECTIFUSERUNKNOWN Controls the handling of unknown user names in incoming connections.
Sets the list of allowed subsystems which globally restricts the users' settings of
ALLOWED-SUBSYSTEMS attribute.
Controls whether ssh users with a frozen Safeguard user configured as
SYSTEM-USER are allowed to authenticate.
Controls whether users are allowed to use stored passwords for connections to
remote SSH daemons.
Controls whether remote users can log on via SSH using a Guardian user ID or
alias, without configuring them explicitly via SSHCOM in the SSHCTL.
Allows definition of a default user configuration when users are automatically
added to SSHCTL.
Configures an authentication banner message to be displayed to SSH clients
connecting to the SSH2 daemon.
Allows restriction of possible authentication methods used by NonStop ssh
clients
Allows setting the customer name or overwriting the customer name in the
license file.
50 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 51

Parameter Meaning
ENABLESTATISTICSATSTARTUP Enables or disables statistics at startup.
FULLSSHCOMACCESSGROUP<j>
Parameter set allows granting administrative SSHCOM command privileges to
groups.
FULLSSHCOMACCESSUSER<i>
Parameter set allows granting administrative SSHCOM command privileges to
users.
GSSAUTH Enables or disables GSSAPI authentication.
GSSGEXKEX Enables or disables GSSAPI key exchange with group exchange.
GSSKEX Enables or disables GSSAPI key exchange.
GUARDIANATTRIBUTESEPARATOR Specifies an additional separator character for Guardian file attributes.
HOSTKEY Specifies the file name of host key file.
INTERFACE
Specifies the local IP address SSH2 should listen on for incoming SSH
connections.
INTERFACEOUT Specifies the local IP address SSH2 should use for outgoing connections.
INTERVALLIVEPRIVATEUSERKEY
Determines the period a newly generated user private key is in state ‘LIVE’
(before getting ‘EXPIRED’).
INTERVALPENDINGPRIVATEUSERKEY
Determines the period a newly generated user private key is in state ‘PENDING’
(before getting ‘LIVE’).
IPMODE Specifies IP mode of the SSH2 process
LICENSE Specifies the location for the license file of SSH2.
LIFECYCLEPOLICYPRIVATEUSERKEY Controls life cycle of user generated private keys.
LOGCACHEDUMPONABORT
Determines if the internal log cache is written to the log file in case of process
aborting.
LOGCACHESIZE Determines the size of the internal log cache.
LOGCONSOLE Determines whether log messages are written to a console.
LOGEMS Determines whether log messages are written to EMS.
LOGEMSKEEPCOLLECTOROPENED Controls opening/closing of the EMS collector.
LOGFILE Determines whether log messages are written to a file.
LOGFILERETENTION Controls log file rollover.
LOGFORMAT Controls the format of the log messages that are written.
LOGFORMATCONSOLE Controls the format of the log messages that are written to the console.
LOGFORMATEMS Controls the format of the log messages that are written to EMS.
LOGFORMATFILE Controls the format of the log messages that are written to a file.
LOGLEVEL Sets the general logging level.
LOGLEVELCACHE Determines whether log messages are written to the internal log cache.
LOGLEVELCONSOLE Determines which messages will be written to the console.
LOGLEVELEMS Determines which messages will be written to EMS.
LOGLEVELFILE Determines which messages will be written to the log file.
LOGMAXFILELENGTH Controls the maximum size of the log file.
LOGMEMORY Allows regular logging of SSH2’s memory usage to the log output.
MACS Allows message authentication codes.
PORT The port the SSH2 server listens on for incoming connections.
PTCPIPFILTERKEY Sets the filter key to enable round-robin filtering.
PTCPIPFILTERTCPPORTS Same effect as DEFINE =PTCPIP^FILTER^TCP^PORTS
PTYSERVER
Specifies the name of an STN process that functions as a pseudo terminal (PTY)
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 51
Page 52

Parameter Meaning
server.
RECORDDELIMITER
Allows configuring the end-of-record marker used in binary file transfers into a
structured NonStop file.
RESTRICTIONCHECKFAILEDDEFAULT
Allows all connection restriction checks to fail if a record for the Guardian user
could not be found.
SAFEGUARD-PASSWORD-REQUIRED
Should be enabled if Safeguard is configured with PASSWORD-REQURED
ON.
SFTPALLOWGUARDIANCD Controls whether SFTPSERV allows a Guardian style CD command.
SFTPCPUSET Specifies the default value for USER attribute SFTP-CPU-SET.
SFTPDISPLAYGUARDIAN
Controls output format (Guardian or OSS style) for SFTP informational
messages.
SFTPEDITLINEMODE
Controls handling of Guardian edit lines that are longer than the maximum
Guardian edit line length.
SFTPEDITLINENUMBERDECIMALINCR Controls the Guardian edit line number decimal increment.
SFTPEDITLINESTARTDECIMALINCR Defines at which line decimal incrementing of Guardian edit line numbers starts.
SFTPEXCLUSIONMODEREAD Defines file open exclusion mode of structured files.
SFTPIDLETIMEOUT Controls whether SFTPSERV stops after specified user idle time.
SFTPMAXEXTENTS Default value for MAXEXTENTS for files created on the NonStop system.
SFTPPRIMARYEXTENTSIZE Default primary extend size for files created on the NonStop system.
SFTPSECONDARYEXTENTSIZE Default secondary extend size for files created on the NonStop system.
SFTPUPSHIFTGUARDIANFILENAMES Defines that all Guardian file names are to be treated all upper or all lower case.
SOCKETKEEPALIVE Specifies whether keep alive messages are enabled for TCP/IP sockets.
SOCKETRCVBUF For setting the receive buffer size (socket option).
SOCKETSNDBUF Allows setting the send buffer size (socket option).
SOCKTCPMAXRXMT Allows setting maximum time for TCP retransmission timeout (socket option)
SOCKTCPMINRXMT Allows setting minimum time for TCP retransmission timeout (socket option)
SOCKTCPRXMTCNT
Allows setting maximum number of continuous retransmissions prior to
dropping a TCP connection (socket option)
SOCKTCPTOTRXMTVAL
Allows setting maximum continuous time spent retransmitting without receiving
an acknowledgement from the other endpoint (socket option)
SSHAUTOKEXBYTES
Controls the frequency of key re-exchange on SSH sessions depending on the
number of transferred bytes.
SSHAUTOKEXTIME
Controls the frequency of key re-exchange on SSH sessions depending on a
timer.
SSHCTL File name of user database.
SSHCTLAUDIT
Determines whether the user database file will be created as an audited file or
not.
SSHKEEPALIVETIME Controls the frequency of SSH "keepalive" messages.
STOREDPASSWORDSONLY
Disabling password prompt for authentication method password, allowing only
to use stored passwords.
STRICTHOSTKEYCHECKING Determines if local users are allowed to connect to unknown hosts.
SUBNET Specifies the TCP/IP process to use.
SUPPRESSCOMMENTINSSHVERSION
Controls if SSH2 version is suppressed in the comment part of the ssh protocol
version string exchanged between ssh client and ssh server
TCPIPHOSTFILE Same effect as DEFINE =TCPIP^HOST^FILE.
TCPIPNODEFILE Same effect as DEFINE =TCPIP^NODE^FILE.
52 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 53

Parameter Meaning
TCPIPRESOLVERNAME Same effect as DEFINE =TCPIP^RESOLVER^NAME.
USETEMPLATESYSTEMUSER
Allows using the same (dummy) Guardian user or *NONE* for automatically
added users.
ALLOWEDAUTHENTICATIONS
Use this parameter to specify the authentication mechanisms that are allowed for system users that are automatically
added to the SSHCTL database upon first login.
Parameter Syntax
ALLOWEDAUTHENTICATIONS (method[,method,...])
Arguments
method
Specifies an SSH authentication method to be allowed. Valid values are…
o password
Password for the NonStop system's authentication mechanism. The password is validated against the
SYSTEM-USER's password.
o publickey
Public key authentication using the PUBLIC-KEYs configured for this user.
o keyboard-interactive
Authentication according to RFC 4256 mapped to the standard GUARDIAN user authentication dialog
verifying the SYSTEM-USER’s password.
o gssapi-with-mic
GSSAPI user authentication in accordance with the RFC 4462 standard. Including this method will also
enable “gssapi-keyex” authentication, if the initial key exchange was performed over GSSAPI. See section
"Single Sign-on with GSSAPI Authentication" for further details.
Default
If omitted, ALLOWEDAUTHEN T ICATIONS will be set to (keyboar d-interactive,password,publickey).
Considerations
• ALLOWEDAUTHENTICATIONS is only relevant if AUTOADDSYSTEMUSERS is set to TRUE.
• ALLOWEDAUTHENTICATIONS will not override any list of authentication methods explicitly configured
for a user (using SSHCOM ADD USER or ALT ER USER).
Example
ALLOWEDAUTHENTICATIONS (keyboard-interactive,publickey)
See also:
AUTOADDSYSTEMUSERS
ALLOWEDSUBSYSTEMS
This parameter can be used to globally restrict the SSH user settings to those subsystems listed in the value for
ALLOWEDSUBSYSTEMS, which is a comma separated list of subsystem names. If a subsystem is not mentioned in
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 53
Page 54

both this global list and the SSH user's attribute ALLOWED-SUBSYSTEMS, then the incoming subsystem request will
be denied.
Parameter Syntax
ALLOWEDSUBSYSTEMS subsystem[,subsystem,...]
Double quotes are required when setting the parameter via PARAM and more than one subsystem is listed:
PARAM ALLOWEDSUBSYSTEMS "sftp,tacl"
Arguments
subsystem
Specifies an SSH subsystem to be allowed for incoming connections. Valid values are…
o tacl
o sftp
Default
If omitted, ALLOWEDSUBSYSTEMS will be set to "sftp,tacl".
Considerations
• In an environment with more than one SSH2 process accessing the same SSHCTL database this parameter can
be used to force users to use one SSH2 process for SFTP sessions and the other SSH2 process for TACL
sessions.
• Although shell/exec requests are not subsystem requests, the parameter ALLOWEDSUBSYSTEMS can be
used to generally prevent a user from starting a TACL: If parameter ALLOWEDSUBSYSTEM does not
include subsystem tacl, then any request for a TACL is prevented even when ALLOW-CI is set to TRUE.
If in this case CI-PROGRAM is configured as “*MENU* …” or “telnet …”, i.e. a TACL is not directly started,
then the telnet service menu or the telnet forwarding is processed as configured.
Example
ALLOWEDSUBSYSTEMS sftp
ALLOWFROZENSYSTEMUSER
This parameter controls the behavior when SSH2 detects that the configured SYSTEM-USER of the ssh user is in state
FROZEN in Safeguard.
Parameter Syntax
ALLOWFROZENSYSTEMUSER [TRUE|FALSE]
Arguments
[TRUE|FALSE]
Specifies whether Safeguard users in state frozen are allowed to access the NonStop. Valid values are:
o TRUE: A frozen user is not rejected, i.e. can authenticate via configured authentication methods.
o FALSE: Authentication fails without trying any of the configured authentication methods if a Safeguard
user is in state FROZEN.
Default
If omitted, ALLOWFROZENSYSTEMUSER will be set to FALSE. This is a change compared to releases prior to 0089
as frozen users were allowed before version 0089.
Considerations
54 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 55

• This parameter shoul d be set to TRUE only if compatibility to previous behavior is required.
• Even if ALLOWFROZENSYSTEMUSER is set to TRUE, the methods password and keyboard-interactive will
always fail due to the FROZEN state (because Safeguard is involved and will not authenticate a frozen user).
Example
ALLOWFROZENSYSTEMUSER FALSE
ALLOWINFOSSH2
This parameter defines the set of users that are allowed to execute the SSHCOM command INFO SSH2.
Parameter Syntax
ALLOWINFOSSH2 [ALL|PARTIALSSHCOMACCESS|FULLSSHCOMACCESS]
Arguments
[ALL|PARTIALSSHCOMACCESS|FULLSSHCOMACCESS]
Valid values are:
o ALL: Every user is allowed to execute SSHCOM command INFO SSH2.
o PARTIALSSHCOMACCESS: Only users configured with partial SSHCOM access are allowed to execute
SSHCOM command INFO SSH2.
o FULLSSHCOMACCESS: Only users having full SSHCOM access are allowed to execute SSHCOM
command INFO SSH2.
Default
If omitted, ALLOWINFOSSH2 will be set to ALL. This is compatible with the behavior before introduction of the
parameter (i.e. prior to version 0092).
Considerations
Example
FULLSSHCOMACCESSUSER<i>, FULLSSHCOMACCESSGROUP<j>, PARTIALSSHCOMACCESSUSER<k>,
PARTIALSSHCOMACCESSGROUP<n>
ALLOWPASSWORDSTORE
This parameter controls whether users are allowed to use stored passwords for connections to remote SSH daemons.
Parameter Syntax
ALLOWPASSWORDSTORE [TRUE|FALSE]
Arguments
[TRUE|FALSE]
Specifies whether to allow password storage. Valid values are...
o TRUE: Any PASSWORDs stored for remote user ID will be automatically used for SSH password
authentication. If no PASSWORD is stored for a connection, the user will be prompted after a successful
authentication if a password should be stored in the password store.
o FALSE: Any stored PASSWORD will be ignored and users will not be prompted to interactively store
passwords.
Default
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 55
Page 56

If omitted, ALLOWPASSWORDSTORE will be set to TRUE.
Considerations
• If ALLOWPASSWORDSTORE is set to TRUE, passwords can be added manually to the user's password store
using the SSHCOM ADD PASSWORD command.
Passwords can also be a dded interactively, when users are prompted after a successful SSH password
authentication with a remote SSH daemon.
Example
ALLOWPASSWORDSTORE TRUE
ALLOWTCPFORWARDING
Use this parameter to specify whether the SSH2 daemon will completely reject TCP port forwarding through SSH or
allow TCP port forwarding depending on user configuration.
Parameter Syntax
ALLOWTCPFORWARDING [TRUE|FALSE]
Arguments
[TRUE|FALSE]
Specifies whether to allow port forwarding or not. Valid values are
o TRUE: port forwarding will be allowed unless user attribute ALLOW-TCP-FORWARDING is set to NO
for a specific user.
o FALSE: port forwarding will be generally denied, independent of the value of user attribute ALLOW-TCP-
FORWARDING.
Default
If omitted, SSH2 will reject port forwarding.
Considerations
This SSH2 parameter specifies on a global scope whether TCP port forwarding is allowed. Even if you set this parameter
to TRUE, you may allow or deny port forwarding at the user level by setting the ALLOW-TCP-FORWARDING USER
attribute. See the SSHCOM Reference for details.
Example
ALLOWTCPFORWARDING TRUE
AUDITCONSOLE
Use this parameter to define if and to what console device SSH2 audit messages are written to.
Parameter Syntax
AUDITCONSOLE * | % | $0 | auditdevice
Arguments
*
Signifies that no audit messages are written to a console.
%
Means that audit messages are written to the home terminal of the SSH2 process.
56 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 57

$0
Specifies that audit messages are written to $0.
auditdevice
Log messages are writt e n the given device (e.g. $DEV.#SUBDEV).
Default
By default, no audit messages will be written ("*").
Considerations
• Although it is possible to specify a collector setting AUDITCONSOLE to a collector name is not recommended
because a collector will cut long messages after 108 characters.
• If writing audit messages to a collector is required, then use parameter AUDITEMS instead.
See also:
• AUDITEMS, AUDITFILE, AUDITFORMATCONSOLE
• "Audit Messages" in chapter "Monitoring and Auditing"
AUDITEMS
Use this parameter to define whether SSH2 audit messages are written to EMS.
Parameter Syntax
AUDITEMS collector | *
Arguments
*
Means that no audit messages are written to EMS.
collector
Specifies the name of the collector to which audit messages are written.
Default
By default, no audit messages are written to EMS ("*").
Considerations
• The AUDITFORMATEMS parameter controls the log message format.
• The parameter can be chan ged without having to res t a r t S SH2, using the SSHCOM c ommand interpreter
(command SET AUDITEMS).
• To send audit messages to the default collector $0 use AUDITEMS $0.
• If the EMS collector specified cannot be opened during startup, SSH2 will write to the collector $0.
• If the EMS collector cannot be opened after it has been changed through SSHCOM, the original collector will
stay active.
See also:
AUDITFORMATEMS
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 57
Page 58

AUDITFILE
Use this parameter to define whether SSH2 audit messages are written, and, if so, to what file.
Parameter Syntax
AUDITFILE * | filenameprefix
Arguments
*
Means that no audit log messages are written to a file.
filenameprefix
Specifies the prefix of the audit message file set. The actual audit file names are constructed from
filenameprefix, which is appended by a number controlled by the AUDITFILERETENTION parameter.
Default
By default, no audit messages are written to a file ("*").
See also:
• AUDITCONSOLE, AUDITFILERETENTION, AUDITFORMAT, AUDITMAXFILELENGTH
• "Audit Messages" in chapter "Monitoring and Auditing"
AUDITFILERETENTION
Use this parameter to control how many audit files SSH2 keeps when logfile rollover occurs.
Parameter Syntax
AUDITFILERETENTION n
Arguments
n
Specifies the number of audit files to keep.
Default
By default, 10 files are kept.
Considerations
• Setting the parameter to a value 0 disables log file retention.
• If log file retention is enabled, a minimum of 10 is enforced by this parameter.
• See section "Logfile/Auditfile Rollover" in the "Monitoring and Auditing" chapter for details on file rollover.
• The file security set for the current audit file (e.g. via FUP SECURE command) will be used for subsequently
created audit files. The very first audit file will have the default file security of user SUPER.SUPER.
See also:
AUDITMAXFILELENGTH, AUDITFILE
58 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 59

AUDITFORMAT
This parameter can be used to control the format of the audit messages that are written to the console and file. Set
parameter AUDITFORMATCONSOLE and AUDITFORMATFILE to configure the audit format for console and file
independently.
Parameter Syntax
AUDITFORMAT format
Arguments
format
A number is used to represent a bit mask that controls the format. Following are the values and their
corresponding format:
bit 1 (decimal 1): Date
bit 2 (decimal 2): header (log messages a pre-fixed with "[log]")
bit 3 (decimal 4): Time
bit 4 (decimal 8): Milliseconds
bit 5 (decimal 16): Process name
bit 7 (decimal 64) Log level of message
Default
The default audit log format is 21 (date, time, process name).
Example
Display date, time, and milliseconds only:
AUDITFORMAT 13
Display date and time only:
AUDITFORMAT 5
See also:
• AUDITCONSOLE, AUDITEMS, AU DI TFILE, AUDITFORMATCONS OL E, AUDITFORMATEMS,
AUDITFORMATFILE
• "Audit Messages" in the chapter entitled "Monitoring and Auditing"
AUDITFORMATCONSOLE
Use this parameter to control the format of the audit messages that are written to the console.
Parameter Syntax
AUDITFORMATCONSOLE format
Arguments
format
A number is used to represent a bit mask that controls the format. Following are the values and their
corresponding format:
Bit 1 (decimal 1) Date
Bit 2 (decimal 2) Header (log messages a pre-fixed with "[log]")
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 59
Page 60

Bit 3 (decimal 4) Time
Bit 4 (decimal 8) Milliseconds
Bit 5 (decimal 16) Process ID (name or PIN)
Bit 7 (decimal 64) Log level of message
Default
The default audit format is 21 (date, time, process name).
See also:
• AUDITCONSOLE, AUDITFORMATEMS, AUDITFORMATFILE
• "Audit Messages" in the chapter entitled "Monitoring and Auditing"
AUDITFORMATEMS
Use this parameter to control the format of the audit messages that are written to EMS.
Parameter Syntax
AUDITFORMATEMS format
Arguments
format
A number is used to represent a bit mask that controls the format. Following are the values and their
corresponding format:
Bit 1 (decimal 1) Date
Bit 2 (decimal 2) Header (log messages a pre-fixed with "[log]")
Bit 3 (decimal 4) Time
Bit 4 (decimal 8) Milliseconds
Bit 5 (decimal 16) Process ID (name or PIN)
Bit 7 (decimal 64) Log level of message
Default
The default audit format for EMS is 0 (none of the header fields).
See also:
• AUDITEMS, AUDITFORMATCONSOLE, AUDITFORMATFILE
• "Audit Messages" in the chapter entitled "Monitoring and Auditing"
AUDITFORMATFILE
Use this parameter to control the format of the audit messages that are written to the log file.
Parameter Syntax
AUDITFORMATFILE format
Arguments
format
60 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 61

A number is used to represent a bit mask that controls the format. Following are the values and their
corresponding format:
Bit 1 (decimal 1) Date
Bit 2 (decimal 2) Header (log messages a pre-fixed with "[log]")
Bit 3 (decimal 4) Time
Bit 4 (decimal 8) Milliseconds
Bit 5 (decimal 16) Process ID (name or PIN)
Bit 7 (decimal 64) Log level of message
Default
The default log format is 21 (date, time, process name).
See also:
• AUDITFILE, AUDITFORMATCO NSOLE, AUDITFORMATEMS
• "Audit Messages" in the chapter entitled "Monitoring and Auditing"
AUDITMAXFILELENGTH
Use this parameter to control the maximum size of an audit file.
Parameter Syntax
AUDITMAXFILELENGTH length
Arguments
length
A number representing the maximum log file length in kilobytes. Values must fall within the following
constraints:
Maximum: 40.000 or 40 MB
Minimum: 100 KB
Default
The default length is 20000 KB.
Considerations
• Once a current audit file reaches the maximum size, a log rollover will occur. The current file will be closed and
a new file will be opened. The new file will be named based on the audit round robin file set specified by the
AUDITFILE and AUDITRETENTION parameters. If the file name already exists, any existing contents will be
purged.
See also:
• AUDITCONSOLE, AUDITFILE, AU DITFILERETENTION
• "Audit Messages" in the chapter titled "Monitoring and Auditing"
AUTOADDSYSTEMUSERS
Use this parameter to control whether remote users can log on via SSH using a Guardian user ID or alias, without
configuring them explicitly via SSHCOM in the SSHCTL.
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 61
Page 62

Parameter Syntax
AUTOADDSYSTEMUSERS [TRUE|FALSE]
Arguments
[TRUE|FALSE]
Specifies whether users logging on with a system User ID are automatically added to SSHCTL. Following are
the two valid options:
o TRUE: system users are automatically added upon first login
o FALSE: logons of any user not contained in the SSHCTL will be denied.
Considerations
• Values of parameters AUTOADDSYSTEMUSERS, AUTOADDSYSTEMUSERSLIKE and
USETEMPLATESYSTEMUSER are used together for automatic addition of SSH USER records:
o If AUTOADDSYSTEMUSERS is FALSE, then the other two parameters will not be looked at, i.e. no SSH
USER record added automatically.
o If AUTOADDSYSTEMUSERS is TRUE and AUTOADDSYSTEMUSERSLIKE is not set, then parameter
USETEMPLATESYSTEMUSER is not looked at. Assuming a client command like ssh <ssh-user>@host,
the value of <ssh-user> is taken as SYSTEM-USER and a system user <ssh-user> must exist in order to
successfully add the SSH USER entry automatically. All but SSH USER attributes user name and
SYSTEM-USER are set to default values (ALLOWED-AUTHENTICATIONS attribute is taken from
parameter ALLOWEDAUTHENTICATIONS if that is defined).
o If AUTOADDSYSTEMUSERS is TRUE and AUTOADDSYSTEMUSERSLIKE is set, then parameter
USETEMPLATESYSTEMUSER is checked: If parameter USETEMPLATESYSTEMUSER is FALSE,
then the value of <ssh-user> is taken as SYSTEM-USER and a system user <ssh-user> must exist in order
to successfully add the SSH USER entry automatically. All USER attributes but the SSH USER name and
the SYSTEM-USER attribute are taken from the template user entry in this case. If parameter
USETEMPLATESYSTEMUSER is TRUE, then all USER attributes but the SSH USER name, are taken
from the template user entry, i.e. including the SYSTEM-USER attribute.
Default
If omitted, AUTOADDSYSTEMUSERS is set to FALSE.
Example
AUTOADDSYSTEMUSERS TRUE
See also:
AUTOADDSYSTEMUSERSLIKE, USETEMPLATESYSTEMUSER
AUTOADDSYSTEMUSERSLIKE
Use this parameter to specify a user whose configuration in SSHCTL is used as default configuration when automatic
adding of users to SHCTL is enabled (i.e. if parameter AUTOADDSYSTEMUSERS has a value of TRUE).
Parameter Syntax
AUTOADDSYSTEMUSERSLIKE <user-name>
Arguments
<user-name>
The name of a user. The user must exist in the SSHCTL at the time a new user tries to logon and
AUTOADDSYSTEMUSERS has a value of TRUE.
62 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 63

Considerations
• Any automatically added user will have the same attributes as the default user, except user name and system-
user.
• In case the parameter AUTOADDSYSTEMUSERSLIKE is set to the name of a user not defined in SSHCTL
and AUTOADDSYSTEMUSERS has a value of TRUE, then any authentication of a new user will be rejected.
Default
If omitted, a user is adde d with hard-coded default values if AUTOADDSYSTEMUSERS has a value of TRUE.
Example
AUTOADDSYSTEMUSERSLIKE comf.us
See also:
AUTOADDSYSTEMUSERS, USETE M PLATESYSTEMUSER
BACKUPCPU
Use this parameter to run as a NonStop process pair.
Parameter Syntax
BACKUPCPU [NONE|ANY|cpu]
Arguments
NONE
SSH2 will not run as a process pair.
ANY
SSH2 will run as a nonstop process pair and will automatically select an available CPU for the backup process.
cpu
A number value that represents a CPU on your system. SSH2 will run as a nonstop process pair and will start
the backup process in the specified CPU.
Considerations
To learn more about how SSH2 can help users leverage the fundamentals of the NonStop system to provide nonstop SSH
access, please refer to the "NonStop Availability" section.
Default
If omitted, BACKUPCPU is set to NONE.
Example
BACKUPCPU ANY
BANNER
Use this parameter to configure an authentication banner message to be displayed to SSH clients connecting to the SSH2
daemon.
Parameter Syntax
BANNER * | filename
Arguments
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 63
Page 64

*
Means no authenticat ion banner is displayed .
filename
Specifies the file name containing the authentication banner to be displayed.
Considerations
• The BANNER file can be an edit file containing multiple lines.
Default
If omitted, BANNER is set to *.
Example
BANNER $SYSTEM.SSH2.BANNER
CIPHERS
Use this parameter to specify which cipher suites are admissible for the SSH2 server.
Parameter Syntax
CIPHERS suite [, suite, ...]
Arguments
suite
Specifies a cipher suite. Currently the following cipher suites are supported by SSH2:
o aes256-cbc: AES (Rijndael) in CBC mode, with 256-bit key
o aes128-cbc: AES with 128-bit key
o twofish256-cbc: Twofish in CBC mode, with 256-bit key
o twofish128-cbc: Twofish with 128-bit key
o twofish-cbc: alias for "twofish256-cbc" (Note: this is being retained for historical reasons)
o blowfish-cbc: Blowfish in CBC mode
o 3des-cbc: three-key 3DES in CBC mode
o arcfour: the ARCFOUR stream cipher
o cast128-cbc: CAST-128 in CBC mode
Considerations
For details about the ciphers listed above, please refer to standard SSH documentation, such as the manual for the RFCs
available.
Default
If omitted, SSH2 will accept all ciphers mentioned above.
Example
CIPHERS 3des-cbc
This will enforce the use of only 3DES-encryption.
64 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 65

CLIENTALLOWEDAUTHENTICATIONS
Use this parameter to restrict the authentication methods the NonStop ssh clients (SSH[OSS], SFTP[OSS]) can try.
Parameter Syntax
CLIENTALLOWEDAUTHENTICATIONS [ method | "method,method,…" ]
Arguments
method
A supported authentication method
Considerations
• The value (list of authentication methods) is only relevant for outgoing ssh connections. For incoming
connections the list of authentication methods is configured for each user (attribute ALLOWED-
AUTHENTICATIONS).
• The authentication methods actually allowed at the client side consist of those methods that are specified in the
client side option "AllowedAuthentications" as well as in the value of SSH2 parameter
CLIENTALLOWEDAUTHENTICATIONS.
Default
The default value is to allow all methods that are supported.
Examples
CLIENTALLOWEDAUTHENTICATIONS "password,keyboard-interactive"
CLIENTALLOWEDAUTHENTICATIONS publickey
See also:
• Ssh clients option AllowedAuthentications, see section "SSH and SFTP Client Reference", General Runtime
options.
• User attribute ALLOWED-AUTHENTICATIONS
COMPRESSION
Use this parameter to specify whether compressed SSH sessions will be supported.
Parameter Syntax
COMPRESSION [TRUE|FALSE]
Arguments
[TRUE|FALSE]
The following arguments can be used to specify whether compression of the SSH session will be supported:
o TRUE: allows compressed sessions.
o FALSE: denies compressed sessions.
Default
If omitted, SSH2 will allow compressed sessions.
Example
COMPRESSION FALSE
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 65
Page 66

CONFIG
Use this parameter to specify a configuration file for an SSH2 process.
Parameter Syntax
CONFIG file
Arguments
file
Specifies the name of the configuration file.
Default
If omitted, SSH2 will not use a configuration file.
Example
CONFIG $DATA1.SSH2.SSHCONF
Considerations
• This parameter can only be specified as PARAM or on the startup line. It is not valid within a configuration file.
• Parameters specified in the configuration file can be overwritten by PARAM or startup line settings.
CONFIG2
Use this parameter to specify a second configuration file for an SSH2 process.
Parameter Syntax
CONFIG2 file2
Arguments
file2
Specifies the name of the second configuration file.
Default
If omitted, SSH2 will not use a second configuration file.
Example
CONFIG2 $DATA1.SSH2.SSHCONF2
Considerations
• The second configuration file has precedence over the first one.
• This parameter can only be specified as PARAM or on the startup line. It is not valid within a configuration file.
• Parameters specified in the configuration file can be overwritten by PARAM or startup line settings.
CPUSET
This parameter allows configuring the default set of CPUs the SSH2 process starts non-SFTPSERV user processes in.
Parameter Syntax
CPUSET cpu-set
66 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 67

Arguments
cpu-set
A comma separated list of CPU numbers or CPU number ranges defining a llowed CPUs.
Default
If omitted, SSH2 will start all non-SFTPSERV processes in the CPU the SSH2 process is running in unless the USER
record specifies a different CPU set for a specific user via attribute CPU-SET.
Example
CPUSET 2,4-6,9
Considerations
• A value configured in USE R a t tribute CPU-SET has higher pri ority than the value def i ned in the SSH2
parameter CPUSET.
• CPU restrictions for processes dynamically started by STN can be established using option CPU of the ADD
SERVICE STNCOM command. Please refer to the "STNCOM Commands" section for further details.
See also:
SFTPCPUSET
CUSTOMER
Use this parameter to set the customer name or overwrite the customer name in the license file. If a customer name is set,
either via license file or via parameter CUSTOMER, it will be used for encryption/decryption of the SSHCTL database
records and the HOSTKEY file.
Parameter Syntax
CONFIG customer
Arguments
customer
Specifies the customer name. If spaces are included, then If the parameter value contains one or more commas or
spaces, it must be included in double quotes.
Example
CUSTOMER "comForte 21 GmbH"
Considerations
• The parameter CUSTOMER has precedence over the customer name in the license file.
• When you plan to duplicate the host key and user database onto other NonStop systems (such as a disaster
recovery system), you need to make sure the parameter CUSTOMER or the license file of that other system has
the same customer name in it. Otherwise, the host key file and user data base cannot be used on the other
system. If you purge the HOSTKEY and SSHCTL files and restart the SSH2 process, a new HOSTKEY and
SSHCTL file will be created using either the value of parameter CUSTOMER or, if that does not exist, the
customer name from the license file, if that exists.
• Although a license file is no longer required for NonStop SSH on H and J operating systems, any existing
HOSTKEY and SSHCTL file requires the customer name that was used to create the file. If a license file exists,
the customer name will be extracted from that file (entry SSH2.customer), unless parameter CUSTOMER is set
in which case the value of CUSTOMER is used. If a license file does not exist and an existing HOSTKE Y or
SSHCTL file is accessed, the parameter CUSTOMER must be set to the original value for the customer name.
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 67
Page 68

• For new installations without license file that include creation of new SSHCTL and HOSTKEY, there is no
reason to set the CUSTOMER parameter.
See also:
• HOSTKEY, SSHCTL
DISCONNECTIFUSERUNKNOWN
Use this parameter to specify that incoming connections are immediately disconnected when the supplied SSH user name
could not be found in the User Database.
Parameter Syntax
DISCONNECTIFUSERUNKNOWN [TRUE|FALSE]
Arguments
TRUE
The session will be disconnected immediately with indication "Access denied".
FALSE
A list of all supported authentication methods is sent back (this avoids returning the information that the user
does not exist).
Default
The default for this parameter is FALSE.
Example
DISCONNECTIFUSERUNKNOWN TRUE
Considerations
• RFC 4252 allows both ways of processing request s of u nknown users.
• If the parameter is not specified or is set to FALSE, the behavior is the same as before the parameter was
introduced.
ENABLESTATISTICSATSTARTUP
This Boolean parameter allows enabling gathering statistics at startup of the SSH2 process.
Parameter Syntax
ENABLESTATISTICSATSTARTUP [TRUE|FALSE]
Arguments
TRUE
Statistics will be gathered immediately after the SSH2 process has started.
FALSE
Gathering statistical data will be enabled only after SSHCOM command ENABLE STATISTICS was issued.
Default
The default for this parameter is FALSE.
Example
ENABLESTATISTICSATSTARTUP TRUE
68 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 69

Considerations
• Maintaining statistics may slow down the SSH2 process.
FULLSSHCOMACCESSGROUP<j>
This parameter set allows granting administrative SSHCOM command privileges to groups rather than just than
super.super. Admin groups are defined via the parameter set FULLSSHCOMACCESSGROUP<j> where <j> is a
number between 1 and 99.
Parameter Syntax
FULLSSHCOMACCESSGROUP<j> <group>
Arguments
<group>
A Guardian group name. All members of the group will have full SSHCOM access.
Default
By default, none of the parameters are set, i.e. only users configured in the Safeguard OBJECTTYPE USER record (if
such exists) and super.super (unless explicitly denied in OBJECTTYPE USER) can access privileged commands.
Example
FULLSSHCOMACCESSGROUP1 admin
FULLSSHCOMACCESSGROUP2 super
Considerations
• Some of the privileged commands in SSHCOM are critical to the security of the system. Therefore granting
access to other user accounts than super.super must be carefully considered.
• The parameters must be set contiguously, i.e. if one parameter FULLSSHCOMACCESSGROUP<k> is not
defined the checking of FULLSSHCOMACCESSGROUP<i> parameters stops.
• This parameter set is disabled if a thawed OBJECTTYPE USER record exists in Safeguard, i.e. any
FULLSSHCOMACCESSGROUP<j> parameter configuration is ignored in this case.
See also:
• FULLSSHCOMACCESSUSER<i>
• See table in “SSHCOM Access Summary” in s ec tion "SSHCOM Command Reference".
FULLSSHCOMACCESSUSER<i>
This parameter set allows granting administrative SSHCOM command privileges to users other than super.super. Admin
users are defined via the parameter set FULLSSHCOMACCESSUSER<i> where <i> is a number between 1 and 99.
Parameter Syntax
FULLSSHCOMACCESSUSER<i> <group>.<user>
Arguments
<group>.<user>
The Guardian logon name of the account that will have full SSHCOM access. Logon ids and alias names are not
supported.
Default
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 69
Page 70

By default, none of the parameters are set, i.e. only users configured in the Safeguard OBJECTTYPE USER record (if
such exists) and super.super (unless explicitly denied in OBJECTTYPE USER) can access privileged commands.
Example
FULLSSHCOMACCESSUSER1 admin.joe
FULLSSHCOMACCESSUSER2 admin.jim
FULLSSHCOMACCESSUSER3 super.jane
Considerations
• Some of the privileged commands in SSHCOM are critical to the security of the system. Therefore granting
access to other user accounts than super.super must be carefully considered.
• The user super.super has always full access to all SSHCOM commands unless explicitly denied in
OBJECTTYPE USER record. Therefore it is not required to add super.super to the list of
FULLSSHCOMACCESSUSER parameters.
• The parameters must be set contiguously, i.e. if one parameter FULLSSHCOMACCESSUSER<k> is not
defined the checking of FULLSSHCOMACCESSUSER<i> parameters stops.
• This parameter set is disabled if a thawed OBJECTTYPE USER record exists in Safeguard, i.e. any
FULLSSHCOMACCESSUSER<i> parameter configuration is ignored in this case.
See also:
• FULLSSHCOMACCESSGROUP<j>
• See table in “SSHCOM Access Summary” in section "SSHCOM Command Reference".
GSSAUTH
Use this parameter to enable GSSAPI authentication in accordance with the RFC 4462.
Parameter Syntax
GSSAUTH [ * | gssauth-process-name ]
Arguments
*
GSSAPI user authentication is disabled
Gssauth-process-name
The process name of the GSSAUTH interface process that provides the GSSAPI functionality for SSH2.
Default
By default, GSSAPI authentication is disabled (*).
Example
GSSAUTH $GSS
Considerations
• The GSSAUTH interface process is part of the Kerberos installation on your NonStop Server.
See also:
• GSSKEX, GSSGEXKEX, ALLOWE DA U T HENTICATIONS
• Section "Single Sign-on with GSSAPI Authentication".
70 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 71

GSSGEXKEX
Use this parameter to enable GSSAPI key exchange with group exchange, in accordance with the RFC 4462 standard
(gss-gex-sha1-* key exchange algorithms).
Parameter Syntax
GSSGEXKEX [TRUE|FALSE]
Arguments
TRUE
GSSAPI kex with group exchange is enabled.
FALSE
GSSAPI kex with group exchange is disabled.
Default
By default, GSSAPI key exchange with group exchange is disabled (FALSE).
Considerations
• GSSGEXKEX is ignored if GSSAUTH is set to “*” (disabled) or GSSKEX is set to FALSE (disabled).
• Enabling GSSGEXKEX may cause problems with an SSH client if there is a faulty implementation of GSS key
exchange with group exc hange.
See also:
• GSSAUTH, GSSKEX, ALLOWEDAUTHENTICATIONS
• Section "Single Sign-on with GSSAPI Authentication".
GSSKEX
Use this parameter to enable GSSAPI key exchange in accordance with RFC 4462.
Parameter Syntax
GSSKEX [TRUE|FALSE]
Arguments
TRUE
GSSAPI key exchange is enabled.
FALSE
GSSAPI key exchange is disabled.
Default
By default, GSSAPI key exchange is enabled (TRUE).
Considerations
• GSSKEX only takes effect if GSSAPI authentication is enabled. GSSKEX is ignored if GSSAUTH is set to “*”
(disabled).
See also:
• GSSAUTH, GSSGEXKEX, ALLOWEDAUTHENTICATIONS
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 71
Page 72

• Section "Single Sign-on with GSSAPI Authentication".
GUARDIANATTRIBUTESEPARATOR
The value (which should only consist of one character) is used as additional separator character between Guardian file
name and Guardian file attributes.
Use this parameter to specify additional separator character between Guardian file name and Guardian file attributes. The
standard separator is always supported.
Parameter Syntax
GUARDIANATTRIBUTESEPARATOR separator
Arguments
separator
The character to be allowed as a separator of Guardian file attributes.
Considerations
• Use this parameter if a SFTP client does not support using commas in remote filenames.
• The configured separator character does not replace the default (which is comma) but is an alternate.
• Either the configured separator or the standard separator (comma) is supported but not a mix of both.
Default
If omitted, the only separator character is the comma.
Examples
GUARDIANATTRIBUTESEPARATOR GUARDIANATTRIBUTESEPARATOR "&"
HOSTKEY
Use this parameter to specify the filename of the host key file.
Parameter Syntax
HOSTKEY filename
Arguments
filename
Specifies the name of the host key file.
Considerations
• The host key is the private key that is used to authenticate the host against the clients. The fingerprint of the host
key will need to be configured on the remote systems that connect to the SSH2 process running on the NonStop
system. The fingerprint of the host key file is displa ye d during startup of the process.
• In order to prevent unauthorized usage of the host key file (i.e. moving it to other systems), the file is stored in a
proprietary format and encrypted. The host key file is secured as "----".
• The customer name configured via parameter CUSTOMER or, if that does not exist, the customer name held
within the license file for the SSH2 program is used as an input for host-based key encryption. When you plan
to duplicate the host key and user database onto other NonStop systems (such as a disaster recovery system),
you need to make sure the parameter CUSTOMER or the license file of that other system has the same customer
72 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 73

name in it. Otherwise, the host key file and user data base cannot be used on the other system. If you purge the
HOSTKEY and SSHCTL files and restart the SSH2 process, a new HOSTKEY and SSHCTL file will be
created using either the value of parameter CUSTOMER or, if that does not exist, the customer name from the
license file.
• Although a license file is no longer required for NonStop SSH on H and J operating systems, any existing
HOSTKEY and SSHCTL file requires the customer name that was used to create the file. If a license file exists,
the customer name will be extracted from that file (entry SSH2.customer), unless parameter CUSTOMER is set
in which case the value of CUSTOMER is used. If a license file does not exist and an existing HOSTKEY or
SSHCTL file is accessed, the parameter CUSTOMER must be set to the original value for the customer name.
• The host key uses the DSA algorithm and has a length of 1024 bits. The fingerprint of the host key is displayed
on startup.
• The public key part of the host key can be exported using the SSHCOM daemon mode command EXPORT
HOST-KEY.
• If multiple SSH2 processes started from the same subvolume but used for different purposes, t hen not only
separate SSH database files (configured via SSHCTL) but separate host key files (configured via HOSTKEY)
should be configured. Example: SSH for maintenance and public network.
Default
If omitted, SSH2 will use a file name of HOSTKEY.
Example
HOSTKEY $SYSTEM.SSH2.SSHKEY
See also:
• CUSTOMER
INTERFACE
Use this parameter to specify the local IP address SSH2 should listen on for incoming SSH connections.
Parameter Syntax
INTERFACE ip-address
Arguments
ip-address
Specifies the local IP address SSH2 should listen on.
Default
If omitted, SSH2 will listen on all local IP addresses of the configured TCPIP process (SUBNET), which corresponds to
INTERFACE value 0.0. 0.0 or, in case of IPv6, 0:: 0.
Examples
INTERFACE 10.0.0.196
INTERFACE fe80::a00:8eff:fe00:d14e
INTERFACE ::FFFF:222.1.41.90
Considerations
• The value must be set consistent with the value of parameter IPMODE.
• If IPMODE parameter is set to DUAL, then an IPv6 address must be used (IPv4-mapped IPv6 address for IPv4
addresses)
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 73
Page 74

• Both values for INTERFACE and INTERFACEOUT must exist in the same TCP/IP process configured via
parameter SUBNET or define =TCPIP^PROCESS^NAME
See also:
SUBNET, INTERFACEOUT, IPMODE
INTERFACEOUT
Use this parameter to specify the local IP address SSH2 should bind to for outgoing SSH connections.
Parameter Syntax
INTERFACEOUT <ip-address>
Arguments
<ip-address>
Specifies the local IP address SSH2 binds the TCP/IP socket to before connecting to a remote system..
Default
If omitted, SSH2 will bind to the IP address configured via parameter INTERFACE. If neither parameter
INTERFACEOUT nor INTERFACE is set (or configured with value 0.0.0.0 / 0::0), any local IP addresses of the
configured TCPIP process (SUBNET) will be used, selected by the TCPIP process.
Considerations
• The value must be set consistent with the value of parameter IPMODE.
• If IPMODE parameter is set to DUAL, then an IPv6 address must be used (IPv4-mapped IPv6 address for IPv4
addresses)
• Both values for INTERFACE and INTERFACEOUT must exist in the same TCP/IP process configured via
parameter SUBNET or define =TCPIP^PROCESS^NAME
Example
INTERFACEOUT 10.0.0.197
See also:
INTERFACE, SUBNET, IPMODE
INTERVALLIVEPRIVATEUSERKEY
This parameter is related to a user private key’s life-cycle (configuration of database entity KEY). It determines the
length of the interval a user private key stays in state ‘LIVE’.
Parameter Syntax
INTERVALLIVEPRIVATEUSERKEY number-of-days
Arguments
number-of-days
The number of days a newly generated user private key will be in state ‘LIVE’ after leaving state ’PENDING’
and before reaching state ‘EXPIRED’.
Default
The default value for this parameter is 730, i.e. 2 years.
74 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 75

Example
INTERVALLIVEPRIVATEUSERKEY 1460
Considerations
• The life-cycle configuration of existing user private keys will not be modified due to this parameter. If existing
keys need to participate in life-cycle control, then they must be configured via ALTER KEY command
specifying the LIVE-DATE and EXPIRE-DATE command options.
• Parameter value is ignored if life-cycle for user private keys is disabled (i.e. if
LIFECYCLEPOLICYPRIVATEUSERKEY is set to DISABLED).
• Parameter value is ignored if KEY attributes LIVE-DATE and EXPIRE-DATE are specified in GENERATE
KEY and IMPORT KEY commands (if a user is allowed to specify these attributes according to the key life-
cycle policy).
See also:
LIFECYCLEPOLICYPRIVATEUSERKEY, INTERVALPENDINGPRIVATEUSERKEY
INTERVALLIVEPPUBLICUSERKEY
This parameter is related to a user public key’s life-cycle (configuration of database entity USER). It determines the
length of the interval a user public key stays in state ‘LIVE’.
Parameter Syntax
INTERVALLIVEPPUBLICUSERKEY number-of-days
Arguments
number-of-days
The number of days a user public key will be in state ‘LIVE’ after leaving state ’PENDING’ and before
reaching state ‘EXPIRED’.
Default
The default value for this parameter is 730, i.e. 2 years.
Example
INTERVALLIVEPUBLICUSERKEY 1460
Considerations
• The life-cycle configuration of existing user public keys will not be modified due to this parameter. If existing
keys need to participate in life-cycle control, then they must be configured via ALTER USER, PUBLICKEY
command specifying the LIVE-DATE and EXPIRE-DATE command options.
• Parameter value is ignored if life-cycle for user public keys is disabled (i.e. if
LIFECYCLEPOLICYPUBLICUSERKEY is set to DISABLED).
• Parameter value is ignored if USER PUBLICKEY attributes LIVE-DATE and EXPIRE-DATE are specified in
ALTER USER PUBLICKEY commands (if a user is allowed to specify these attributes according to the key
lifecycle policy).
See also:
LIFECYCLEPOLICYPUBLICUSERKEY, INTERVALPENDINGPUBLICUSERKEY
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 75
Page 76

INTERVALPENDINGPRIVATEUSERKEY
This parameter is related to a user private key’s life-cycle (configuration of database entity KEY). It determines the
length of the interval a user private key stays in state ‘PENDING’ after creation before it switches to state ‘LIVE’.
Parameter Syntax
INTERVALPENDINGPRIVATEUSERKEY number-of-days
Arguments
number-of-days
The number of days a newly generated user private key will be in state ‘PENDING’ after creation and before
reaching state ‘LIVE’.
Default
The default value for this parameter is 0, i.e. newly generated key will go into state ‘LIVE’ immediately if this parameter
is not set to a different value than 0.
Example
INTERVALPENDINGPRIVATEUSERKEY 30
Considerations
• The life-cycle configuration of existing user private keys will not be modified due to this parameter. If existing
keys need to participate in life-cycle control, then they must be configured via ALTER KEY command
specifying the LIVE-DATE and EXPIRE-DATE command options.
• Parameter value is ignored if life-cycle for user private keys is disabled (i.e. if
LIFECYCLEPOLICYPRIVATEUSERKEY is set to DISABLED).
• Parameter value is ignored if KEY attributes LIVE-DATE and EXPIRE-DATE are specified in GENERATE
KEY and IMPORT KEY commands (if a user is allowed to specify these attributes according to the key life-
cycle policy).
See also:
LIFECYCLEPOLICYPRIVATEUSERKEY, INTERVALLIVEPRIVATEUSERKEY
INTERVALPENDINGPUBLICUSERKEY
This parameter is related to a user public key’s life-cycle (configuration of database entity USER). It determines the
length of the interval a user public key stays in state ‘PENDING’ after creation before it switches to state ‘LIVE’.
Parameter Syntax
INTERVALPENDINGPUBLICUSERKEY number-of-days
Arguments
number-of-days
The number of days a user public key will be in state ‘PENDING’ after creation and before reaching state
‘LIVE’.
Default
The default value for this parameter is 0, i.e. newly added user public keys will go into state ‘LIVE’ immediately if this
parameter is not set to a different value than 0.
Example
76 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 77

INTERVALPENDINGPUBLICUSERKEY 30
Considerations
• The life-cycle configuration of existing user public keys will not be modified due to this parameter. If existing
keys need to participate in life-cycle control, then they must be configured via ALTER USER PUBLICKEY
command specifying the LIVE-DATE and EXPIRE-DATE command options.
• Parameter value is ignored if life-cycle for user public keys is disabled (i.e. if
LIFECYCLEPOLICYPUBLICUSERKEY is set to DISABLED).
• Parameter value is ignored if USER PUBLICKEY attributes LIVE-DATE and EXPIRE-DATE are specified in
ALTER USER PUBLICKEY commands (if a user is allowed to specify these attributes according to the key
lifecycle policy).
See also:
LIFECYCLEPOLICYPUBLICUSERKEY, INTERVALLIVEPUBLICUSERKEY
IPMODE
This parameter is used to set the IP mode the SSH2 process is running in. Depending on this parameter the SSH2 process
supports IPv4 only, IPv6 only, or both.
Parameter Syntax
IPMODE ip-mode
Arguments
ip-mode
The IP mode the SSH2 process will be running in. The following IP modes are supported:
o IPV4 – TCP/IP version 4 is supported only
o IPV6 – TCP/IP version 6 is supported only
o DUAL – Both TCP/IP versi ons 4 and 6 are supported
Default
The default value for this parameter is IPV4.
Example
IPMODE IPv6
Considerations
• The IPMODE parameter of SSH2 corresponds to the TCP/IP monitor process option FAMILY. The
configuration of SSH2 parameter SUBNET or define =TCPIP^PROCESS^NAME must not contradict the value
of IPMODE, i.e. if IPMODE is set to IPv4, then the TCP/IP process cannot be configured with FAMILY IPv6
and vice versa.
• Similarly, the configuration of SSH2 parameters INTERFACE and INTERFACEOUT must be set consistently
with setting of parameter IPMODE.
See also:
SUBNET, INTERFACE, INTERFA C EOUT
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 77
Page 78

LICENSE
Use this parameter to specify a different location for the SSH2 license file.
Note: If you purchased NonStop SSH with the NonStop Operating System Kernel for H Series and J Series NonStop
platforms, you will not need a license file anymore.
Parameter Syntax
LICENSE file
Arguments
file
Specifies the name of the SSH2 license file.
Considerations
• If the file name is not fully qualified, SSH2 will add the home subvolume of the object file to the file name.
• A license is no longer required for TNS/E systems. If a license file exists, then the customer name will be
extracted from it.
• Please see the section on the HOSTKEY parameter for more information on the interaction of the license file
with the host key file.
• Please see the section on the SSHCTL parameter for more information on the interaction of the license file with
the SSH2 database.
Default
If omitted, an SSH2 proce s s will search for a file named "LICENSE" on the s ub volume where the SSH2 object resides.
LIFECYCLEPOLICYPRIVATEUSERKEY
This parameter controls the life-cycle of user generated private keys. If enabled, a ‘not valid before date’ and a ‘not valid
after date’ can be defined for each individual key. This can be achieved by setting the dates explicitly via entity KEY
attributes LIVE-DATE and EXPIRE-DATE or implicitly via globally defined length of the key pending time period after
key generation and length of the period a key is in ‘LIVE’ state. Only a key in ‘LIVE’ state may be part of a publickey
authentication of the us er owning a private key.
Parameter Syntax
LIFECYCLEPOLICYPRIVATEUSERKEY [DISABLED|FIXED|VARIABLE]
Arguments
DISABLED
Life-cycle control for user generated private keys will not be enabled. When a key is generated it is immediately
in state ‘LIVE’ and it will never expire.
FIXED
Users without full SSHCOM access cannot set or alter KEY attributes LIVE-DATE and EXPIRE-DATE. Both
dates will be determined by the CREATION-DATE and the values of parameters
INTERVALPENDINGPRIVATEUSERKEY and INTERVALLIVEPRIVATEUSERKEY.
VARIABLE
A user can specify the LIVE-DATE and EXPIRE-DATE when generating or importing a private key or when
altering the private key. By not specifying these attributes in a GENERATE KEY or IMPORT KEY command,
the values for LIVE-DATE and EXPIRE-DATE will be automatically set depending on the CREATION-DATE
78 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 79

and the values of parameters INTERVALPENDINGPRIVATEUSERKEY and
INTERVALLIVEPRIVATEUSERKEY.
Default
The default for this parameter is DISABLED resulting in the same behavior as before the introduction of this parameter.
Example
LIFECYCLEPOLICYPRIVATEUSERKEY FIXED
Considerations
• Users with full SSHCOM access can set or modify KEY attributes LIVE-DATE and EXPIRE-DATE even
when the life-cycle policy for user private keys is set to FIXED.
See also:
INTERVALLIVEPRIVATEUSERKEY , INTERVALPENDINGPRIVATEUSERKEY
LIFECYCLEPOLICYPUBLICUSERKEY
This parameter controls the life-cycle of user public keys. If enabled, a ‘not valid before date’ and a ‘not valid after date’
can be defined for each individual key. This can be achieved by setting the dates explicitly via entity USER
PUBLICKEY attributes LIVE-DATE and EXPIRE-DATE or implicitly via globally defined length of the key pending
time period after key addition and length of the period a key is in ‘LIVE’ state. Only a key in ‘LIVE’ state may be part of
a public key authentication of the user configured with the key.
Parameter Syntax
LIFECYCLEPOLICYPUBLICUSERKEY [DISABLED|FIXED|VARIABLE]
Arguments
DISABLED
Life-cycle control for user public keys will not be enabled. When a public key is added, it is immediately in
state ‘LIVE’ and it will never expire.
FIXED
Users without full SSHCOM access cannot set or alter KEY attributes LIVE-DATE and EXPIRE-DATE. Both
dates will be determined by the CREATION-DATE and the values of parameters
INTERVALPENDINGPUBLICUSERKEY and INTERVALLIVEPUBLICUSERKEY.
VARIABLE
Users with partial access can specify the LIVE-DATE and EXPIRE-DATE when adding a user public key or
when altering the public key. By not specifying these attributes in an ALTER USER PUBLICKEY command,
the values for LIVE-DATE and EXPIRE-DATE will be automatically set depending on the CREATION-DATE
and the values of parameters INTERVALPENDINGPUBLICUSERKEY and
INTERVALLIVEPUBLICUSERKEY.
Default
The default for this parameter is DISABLED resulting in the same behavior as before the introduction of this parameter.
Example
LIFECYCLEPOLICYPUBLICUSERKEY FIXED
Considerations
• Users with full SSHCOM access can set or modify USER PUBLICKEY attributes LIVE-DATE and EXPIRE-
DATE even when the life-cycle policy for user public keys is set to FIXED.
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 79
Page 80

See also:
INTERVALLIVEPUBLICUSERKEY, INTERVALPENDINGPUBLICUSERKEY, FULLSSHCOMACCESSUSER<i>
and FULLSSHCOMACCESSGROUP<j> PARTIALSSHCOMACCESSUSER<k>,
PARTIALSSHCOMACCESSGROUP<n>
LOGCACHEDUMPONABORT
Use this parameter to define whether SSH2 writes the log messages held in the log cache are written to the log file in
case of an abort.
Parameter Syntax
LOGCACHEDUMPONABORT [TRUE|FALSE]
Arguments
TRUE
In case of abort the content of the log cache will be written to the configured log file.
FALSE
The content of the log cache will be discarded on process abort.
Default
The default for this parameter is FALSE.
Considerations
• The log cache content can be written to the log file at any time via SSHCOM command FLUSH LOGCACHE.
See also:
• LOGCACHESIZE, LOGLEVELCACHE, LOGFILE
• "Log Messages" in the "Monitoring and Auditing" chapter.
• Commands FLUSH LOGCACHE and CLEAR LOGCACHE in the "SSHCOM Command Reference" chapter.
LOGCACHESIZE
Use this parameter to define how many lines of log messages are held in log cache.
Parameter Syntax
LOGCACHESIZE <lines>
Argument
<lines>
The number of log messages (lines) to be held in the log cache. The minimum value is 1024 and the maximum
value is 1048576 (1024 * 1024).
Considerations
• The LOGLEVELCACHE parameter controls what messages are written to the log cache.
Default
By default, the minimum value (1024) is used.
80 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 81

See also:
• LOGLEVELCACHE
• Commands SET LOGCACHESIZE in the "SSHCOM Command Reference" chapter.
LOGCONSOLE
Use this parameter to define whether SSH2 log messages are written to a console device, and, if so, which device.
Parameter Syntax
LOGCONSOLE * | % | $0 | logdevice
Arguments
*
Means that no log messages are written to a console device.
%
Results in log messages being written to the home terminal of the SSH2 process.
$0
Specifies that log messages are written to $0.
logdevice
Specifies that log messages are written to a given device (e.g. $DEV.#SUBDEV).
Considerations
• The LOGLEVELCONSOLE parameter controls what messages are produced by SSH2.
• Log messages are automatically cut by the collector when using value $0 for LOGCONSOLE. Please use
LOGEMS to enable logging to an EMS collector.
Default
By default, log messages are written to the home terminal ("%").
See also:
• LOGEMS, LOGFILE, LOGLEVELCONSOLE
• "Log Messages" in the "Monitoring and Auditing" chapter.
LOGEMS
Use this parameter to define whether SSH2 log messages are written to EMS.
Parameter Syntax
LOGEMS collector | *
Arguments
*
Means that no log messages are written to EMS.
collector
Specifies the name of the collector to which log messages are written.
Default
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 81
Page 82

By default, no log messages are written to EMS ("*").
Considerations
• The LOGLEVELEMS parameter controls what messages are produced by SSH2.
• The LOGFORMATEMS parameter controls the log message format.
• The parameter can be chan ged without having to res t a r t S SH2, using the SSHCOM c ommand interpreter.
• To send messages to the default collector $0 use LOGEMS $0.
• If the EMS collector specified cannot be opened during startup, SSH2 will write to the collector $0.
• If the EMS collector cannot be opened after it has been changed through SSHCOM, the original collector will
stay active.
See also:
LOGLEVELEMS, LOGFORMATEMS
LOGEMSKEEPCOLLECTOROPENED
This Boolean parameter controls if the configured EMS collector (see LOGEMS) will be opened and closed for every
log message.
Parameter Syntax
LOGEMSKEEPCOLLECTOROPENED [TRUE|FALSE]
Arguments
TRUE
The EMS collector will be opened once (and re-opened after errors only)
FALSE
The EMS collector will be opened and closed for each log message written to the EMS collector (configured via
parameter LOGEMS)
Default
The default for this parameter is FALSE resulting in the same behavior as before the introduction of this parameter.
Example
LOGEMSKEEPCOLLECTOROPENED TRUE
Considerations
• Keeping the EMS collector open instead of opening and closing it for every log message will reduce overhead.
• Closing the collector for every log message is only required if the collector's supported maximum number of
event message issuers is reached.
LOGFILE
Use this parameter to define whether SSH2 log messages are written, and, if so, to which file.
Parameter Syntax
LOGFILE * | file
Arguments
82 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 83

*
Means that no log messages are written to a file.
filenameprefix
Specifies the prefix of the log file set. The actual audit file names are constructed based on the prefix assigned
and by a number generated based on the settings of the LOGFILERETENTION parameter.
Default
By default, no log messages are written to a file ("*").
Considerations
• The LOGLEVELFILE parameter controls what messages are produced by SSH2.
• The LOGFORMATFILE parameter controls the log message format.
See also:
• LOGCONSOLE, LOGLEVELFILE, LOGFORMATFILE, LOGMAXFILELENGTH, LOGFILERETENTION
• "Log Messages" in the chapter entitled "Monitoring and Auditing".
LOGFILERETENTION
Use this parameter to control how many log files SSH2 keeps when log file rollover occurs.
Parameter Syntax
LOGFILERETENTION n
Arguments
n
Specifies the number of log files to keep.
Default
By default, 10 files are kept.
Considerations
• Setting the parameter to a value 0 disables log file retention.
• If log file retention is enabled, a minimum of 10 is enforced by this parameter.
• See section "Logfile/Auditfile Rollover" in the "Monitoring and Auditing" chapter for details on file rollover.
• The file security set for the current log file (e.g. via FUP SECURE command) will be used for subsequently
created log files. The very first log file will have the default file security of user super.super.
See also:
LOGMAXFILELENGTH, LOGFIL E
LOGFORMAT
Use this parameter to control the format of the log messages that are written to the console or log file.
Parameter Syntax
LOGFORMAT format
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 83
Page 84

Arguments
format
A number is used to represent a bit mask that controls the format. Following are the values and their
corresponding format:
bit 1 (decimal 1): Date
bit 2 (decimal 2): Header (log messages a pre-fixed with "[log]")
bit 3 (decimal 4): Time
bit 4 (decimal 8): Milliseconds
bit 5 (decimal 16): Process name
Bit 7 (decimal 64) Log level of message
Default
The default log format is 93 (process name, date, time, milliseconds, and log level).
Example
Display date, time, and milliseconds only:
LOGFORMAT 13
Display date and time only:
LOGFORMAT 5
Considerations
• This parameter is retained for downward compatibility only and has been replaced by the parameters
LOGFORMATCONSOLE and LOGFORMATFILE.
• If no value is set for the parameters LOGFORMATCONSOLE or LOGFORMATFILE, they will inherit their
value from the parameter LOGFORMAT.
• If both LOGFORMATCONSOLE and LOGFORMATFILE are set with a value, the parameter of
LOGFORMAT becomes meaningless.
See also:
LOGFORMATCONSOLE, LOGFORMATEMS, LOGFORMATFILE
LOGFORMATCONSOLE
Use this parameter to control the format of the log messages that are written to the console.
Parameter Syntax
LOGFORMATCONSOLE format
Arguments
format
A number is used to represent a bit mask that controls the format. Following are the values and their
corresponding format:
Bit 1 (decimal 1) Date
Bit 2 (decimal 2) Header (log messages a pre-fixed with "[log]")
Bit 3 (decimal 4) Time
Bit 4 (decimal 8) Milliseconds
84 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 85

Bit 5 (decimal 16) Process ID (name or PIN)
Bit 7 (decimal 64) Log level of message
Default
The default log format is 93 (date, time, milliseconds, process ID, and log level).
Example
Display date, time, and milliseconds only:
LOGFORMATCONSOLE 13
Display date and time only:
LOGFORMATCONSOLE 5
See also:
LOGFORMATFILE, LOGFORMATEMS
LOGFORMATEMS
Use this parameter to control the format of the log messages that are written to EMS.
Parameter Syntax
LOGFORMATEMS format
Arguments
format
A number is used to represent a bit mask that controls the format. Following are the values and their
corresponding format:
bit 1 (decimal 1) Date
bit 2 (decimal 2) Header (log messages a pre-fixed with "[log]")
bit 3 (decimal 4) Time
bit 4 (decimal 8) Milliseconds
bit 5 (decimal 16) Process ID (name or PIN)
bit 7 (decimal 64) Log level of message
Default
The default log format is 93 (date, time, milliseconds, process ID, and log level).
Example
Display date, time, and milliseconds only:
LOGFORMATEMS 13
Display date and time only:
LOGFORMATEMS 5
See also:
LOGFORMATCONSOLE, LOGFORMATFILE
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 85
Page 86

LOGFORMATFILE
Use this parameter to control the format of the log messages that are written to the log file.
Parameter Syntax
LOGFORMATFILE format
Arguments
format
A number is used to represent a bit mask that controls the format. Following are the values and their
corresponding format:
bit 1 (decimal 1) Date
bit 2 (decimal 2) Header (log messages a pre-fixed with "[log]")
bit 3 (decimal 4) Time
bit 4 (decimal 8) Milliseconds
bit 5 (decimal 16) Process ID (name or PIN)
bit 7 (decimal 64) Log level of message
Default
The default log format is 93 (date, time, milliseconds, process ID, and log level).
Example
Display date, time, and milliseconds only:
LOGFORMATFILE 13
Display date and time only:
LOGFORMATFILE 5
See also:
LOGFORMATCONSOLE, LOGFORMATEMS
LOGLEVEL
Use this parameter to control the level of detail of messages that are written to the console or log file.
Parameter Syntax
LOGLEVEL detail
Arguments
detail
A number is used to represent the level of detail desired. Following is more information about the values
allowed:
• A valid number must be bet w e e n 0, indicating no messa ge s, and 100. The value of 100 indicates the
maximum amount of messages. The maximum number should not to be used in production environments.
• The recommended level of detail is 30, indicating only startup and problem messages are written, or 50,
specifying some usage messages are also written.
Considerations
86 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 87

• This parameter is retained for downward compatibility only and has been replaced by the
LOGLEVELCONSOLE and LOGLEVELFILE parameters.
• If no value is set for the LOGLEVELCONSOLE or LOGLEVELFILE parameters, they will inherit their value
from the LOGLEVEL parameter.
• If both LOGLEVELCONSOLE and LOGLEVELFILE parameters are assigned a value, the LOGLEVEL
parameter becomes meaningless.
See also:
LOGLEVELCONSOLE, LOGLEVELEMS, LOGLEVELFILE
LOGLEVELCACHE
Use this parameter to control what messages are written to the log cache.
Parameter Syntax
LOGLEVELCACHE detail
Arguments
detail
A number specifying the detail level.
Default
A default of 50 is used.
Considerations
• Using the LOGLEVELCACHE parameter allows users to set a different log level for the log messages written
to the log cache than for the output written to LOGFILE.
• Writing log messages to the log cache and writing the current content to the log file sporadically as required can
reduce the number of dis k operations needed fo r logging.
• The size of the log cache can be configured.
• The content of the log cache can be written to the configured LOGFILE.
• The format of log message written to the log cache is determined by the setting of LOGFORMATFILE.
See also:
LOGLEVELSIZE, LOGLEVELFILE
LOGLEVELCONSOLE
Use this parameter to control what messages are written to the log console.
Parameter Syntax
LOGLEVELCONSOLE detail
Arguments
detail
A number specifying the detail level.
Default
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 87
Page 88

For downward compatibility, the default log level is taken from the parameter LOGLEVEL if present. If no LOGLEVEL
parameter is present, a default of 50 is used.
Considerations
• Using the LOGLEVELCONSOLE parameter allows users to set a different log level for the output written to
LOGCONSOLE than for the output written to LOGFILE.
See also:
LOGCONSOLE, LOGLEVELFILE, LOGFORMATCONSOLE
LOGLEVELEMS
Use this parameter to control which messages are written to EMS.
Parameter Syntax
LOGLEVELEMS detail
Arguments
detail
A number specifying the detail level.
Default
For downward compatibility, the default log level is taken from the LOGLEVEL parameter, if present. Otherwise, a
default of 50 is used.
Considerations
• Different log levels can be used for the outputs to LOGCONSOLE, LOGEMS, and LOGFILE.
• Using the SSHCOM command interpreter, you can change parameters without having to restart SSH2.
See also:
LOGEMS, LOGLEVELCONSOLE, LOGLEVELFILE, LOGFORMATEMS
LOGLEVELFILE
Use this parameter to control which messages are written to the log file.
Parameter Syntax
LOGLEVELFILE detail
Arguments
detail
A number specifying the detail level.
Default
For downward compatibility, the default log level is taken from the LOGLEVEL parameter, if present. Otherwise, a
default of 50 is used.
Considerations
• Different log levels can be used for the outputs to LOGCONSOLE, LOGEMS, and LOGFILE.
• With the SSHCOM command interpreter, users can change parameters without having to restart SSH2.
88 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 89

See also:
LOGFILE, LOGLEVELCONSOLE, LOGMAXFILELENGTH, LOGFORMATFILE
LOGMAXFILELENGTH
Use this parameter to control the maximum size of a log file.
Parameter Syntax
LOGMAXFILELENGTH length
Arguments
length
Represents the maximum log file length in kilobytes. Following are the ranges allowed:
Maximum: 40.000 or 40 MB
Minimum: 100 KB
Default
The default length is 20,000 KB.
Considerations
• After the current log file reaches the maximum size, a log rollover will occur. The current log file will be
renamed by appending a number to its name. A new file with the LOGFILE name will be created for
subsequent log output.
See also:
• LOGFILE, LOGLEVELFILE, LOGF ILE R ETENTION
• "Log Messages" in the "Monitoring and Auditing" chapter.
LOGMEMORY
Use this parameter to include SSH2 memory usage statistics in the log output at regular intervals.
Parameter Syntax
LOGMEMORY number_of_ios
Arguments
number_of_ios
A number that represents how many I/O operations are to be conducted before SSH2 includes its memory usage
in the log output
Default
The default is 0, meaning that memory usage will not be logged.
Considerations
• Provides an easy way to correlate between memory usage of SSH2 and events in the log output. Do not use if
memory usage of SSH2 is not of interest to you.
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 89
Page 90

MACS
Use this parameter to specify which message authentication codes (MAC) are admissible for the SSH2 server.
Parameter Syntax
MACS mac [, mac, ...]
Arguments
mac
Specifies a MAC. Currently the following MACs are supported by SSH2:
o hmac-sha1: HMAC-SHA1 (digest length=key length=20 bytes=160 bits)
o hmac-md5: HMAC-MD5 (digest length=key length=16 bytes=12 8 bi ts)
o hmac-sha1-96: first 96 bits of HMAC-SHA1 (digest length=12 bytes=96 bits, key length=20 bytes=160
bits)
o hmac-md5-96: first 96 bits of HMAC-MD5 (digest length=12 bytes=96 bits, key length=16 bytes=128 bits)
Considerations
For details about the MACs listed above, please refer to standard SSH documentation, such as the available RFCs.
Default
If this parameter is omitted, SSH2 will accept all MACs listed above.
Example
MACS hmac-sha1-96
This will enforce the use of the hmac-sha1-96 MAC algorithm.
PARTIALSSHCOMACCESSGROUP<n>
This parameter set allows granting limited administrative SSHCOM command privileges to groups rather than just
super.super. Admin groups with limited SSHCOM access are defined via the parameter set
PARTIALSSHCOMACCESSGROUP<n> where <n> is a number between 1 and 99.
Limited administrative SSHCOM access includes viewing and altering USER records, i.e. execution of daemon mode
commands INFO USER and ALTER USER. All USER attributes can be modified except the most critical ones, which
are ALLOWED-AUTHENTICATIONS and SYSTEM-USER. These fields can only be modifie d by users with full
SSHCOM access.
Additional restrictions apply depending on the setting of parameter LIFECYCLEPOLICYPUBLICUSERKEY: Users
with partial SSHCOM access can specify the LIVE-DATE and EXPIRE-DATE when adding or altering a user’s public
key only if LIFECYCLEPOLICYPUBLICUSERKEY is set to VARIABLE.
Parameter Syntax
PARTIALSSHCOMACCESSGROUP<j> <group>
Arguments
<group>
A Guardian group name. All members of the group will have partial SSHCOM access.
Default
By default, none of the parameters are set, i.e. only users with full SSHCOM access can execute privileged commands.
Example
90 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 91

PARTIALSSHCOMACCESSGROUP1 admin
PARTIALSSHCOMACCESSGROUP2 super
Considerations
• Some of the privileged commands in SSHCOM are critical to the security of the system. Therefore granting
access to other user accounts than super.super must be carefully considered.
• The parameters must be set contiguously, i.e. if one parameter PARTIALSSHCOMACCESSGROUP<p> is not
defined the checking of PARTIALSSHCOMACCESSGROUP<n> parameters stops.
• This parameter set is valid whether a thawed OBJECTTYPE USER record exists in Safeguard or not. But if a
user is configured with C access in the OBJECTTYPE USER record as well as included in the parameter set
PARTIALSSHCOMACCESSGROUP<n>, then the user has full SSHCOM access.
• If a user is included in parameter sets PARTIALSSHCOMACCESSGROUP<n> as well as sets
FULLSSHCOMACCESSUSER<i> or FULLSSHCOMACCESSGROUP<j>, then the user has full SSHCOM
access.
See also:
• PARTIALSSHCOMACCESSUSER<i>, FULLSSHCOMACCESSUSER<i>,
FULLSSHCOMACCESSGROUP<j>, LIFECYCLEPOLICYPUBLICUSERKEY
• See table in “SSHCOM Access Summary” in section "SSHCOM Command Reference".
PARTIALSSHCOMACCESSUSER<k>
This parameter set allows granting limited administrative SSHCOM command privileges to users other than super.super.
Admin users with limited SSHCOM access are defined via the parameter set PARTIALSSHCOMACCESSUSER<k>
where <k> is a number between 1 and 99.
Limited administrative SSHCOM access includes viewing and altering USER records, i.e. execution of daemon mode
commands INFO USER and ALTER USER. All USER attributes can be modified but the most critical ones, which are
ALLOWED-AUTHENTICATIONS and SYSTEM-USER. These fields can only be modified by users with full
SSHCOM access.
Additional restrictions apply depending on the setting of parameter LIFEC YCL EPOLICYPUBLICUSERKEY: Use rs
with partial SSHCOM access can specify the LIVE-DATE and EXPIRE-DATE when adding or altering a user’s public
key only if LIFECYCLEPOLICYPUBLICUSERKEY is set to VARIABLE.
Parameter Syntax
PARTIALSSHCOMACCESSUSER<k> <group>.<user>
Arguments
<group>.<user>
The Guardian logon name of the account that will have partial SSHCOM access. Logon ids and alias names are
not supported.
Default
By default, none of the parameters are set, i.e. only users with full SSHCOM access can execute privileged commands.
Example
PARTIALSSHCOMACCESSUSER1 admin.joe
PARTIALSSHCOMACCESSUSER2 admin.jim
PARTIALSSHCOMACCESSUSER3 super.jane
Considerations
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 91
Page 92

• Some of the privileged commands in SSHCOM are critical to the security of the system. Therefore granting
access to other user accounts than super.super must be carefully considered.
• The parameters must be set contiguously, i.e. if one parameter FULLSSHCOMACCESSUSER<k> is not
defined the checking of FULLSSHCOMACCESSUSER<i> parameters stops.
• This parameter set is valid whether a thawed OBJECTTYPE USER record exists in Safeguard or not. But if a
user is configured with C access in the OBJECTTYPE USER record as well as mentioned in the parameter set
PARTIALSSHCOMACCESSUSER<k>, then the user has full SSHCOM access.
• If a user is included in parameter sets PARTIALSSHCOMACCESSGROUP<n> as well as sets
FULLSSHCOMACCESSUSER<i> or FULLSSHCOMACCESSGROUP<j>, then the user has full SSHCOM
access.
See also:
• PARTIALSSHCOMACCESSGROUP<n>, F ULL SSHCOMACCESSUSER<i>,
FULLSSHCOMACCESSGROUP<j>, LIFECYCLEPOLICYPUBLICUSERKEY
• See table in “SSHCOM Access Summary” in section "SSHCOM Command Reference".
PORT
Use this parameter to specify the port number a SSH2 server should listen on for incoming connections.
Parameter Syntax
PORT number
Arguments
number
Refers to the decimal number of a TCP/IP port.
Default
The default for this parameter is 22.
Considerations
• The ICANN manages a list of "well-known" port numbers for va rious protocols (see
http://www.iana.org/assignments/port-numbers). 22 is the well-known port for the SSH protocol.
• The choice for the port value in your specific environment will depend on the applications already running on
your NonStop systems, the ports in use, and your firewall configuration.
PTCPIPFILTERKEY
Use this parameter to specify a filter key to enable round-robin filtering with parallel library TCP/IP or TCP/IPV6.
Parameter Syntax
PTCPIPFILTERKEY password | *
Arguments
password
A password that serves as a key to enable round-ro bin filtering of multiple instances of SSH2 servers listening
on the same port. The password will override the value of the DEFINE =PTCPIP^FILTER^KEY, which may
have been passed to SSH2 at startup.
*
92 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 93

No filter key will be set. However, any DEFINE =PTCPIP^FILTER^KEY passed to SSH2 at startup will
remain in effect.
Default
The default for this parameter is *.
Considerations
• Use this parameter to enable round-robin filtering for multiple SSH2 servers configured to run as generic
processes. (DEFINEs cannot be propagated to generic processes.)
PTCPIPFILTERTCPPORTS
Use this parameter to limit port sharing in case round-robin filtering is enabled.
Parameter Syntax
PTCPIPFILTERTCPPORTS Pstartport.Pendport | *
Arguments
Pstartport.Pendport
A port range from startport to endport that restricts shared ports to the configured port range. The configuration
is only effective if round-robin is enabled, i.e. if either the DEFINE =PTCPIP^FILTER^KEY or the SSH2
parameter PTCPIPFILTERKEY is set.
*
Shared ports will not be limited. However, any DEFINE =PTCPIP^FILTER^TCP^PORTS passed to SSH2 at
startup will remain in effect.
Default
The default for this parameter is *.
Considerations
• Use this parameter to limit shared ports when round-robin filtering is enabled for multiple SSH2 servers
configured as generic processes.
PTYSERVER
Use this parameter to specify the name of an STN process serving as a pseudo terminal (PTY) server.
Parameter Syntax
PTYSERVER processname
Arguments
processname
Specifies the name of an STN process.
Default
The default for this parameter is $PTY.
Considerations
• Please refer to the "Enabling Full TTY Access" section for details.
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 93
Page 94

RECORDDELIMITER
Use this SFTP related parameter to define the end-of-record indicator in files transferred from a remote host to a
structured file on NonStop. The parameter is relevant if the SFTP server on NonStop is used for file transfer or if the
SFTP client on NonStop is used and the SFTP command ASCII is not issued before the file transfer (i.e. the transfer is
made in binary mode).
Parameter Syntax
RECORDDELIMITER [LF|CR|CRLF|ANY]
Arguments
LF
End of Record is indicated by an LF (hexadecimal 0A, escape character \n)
CR
End of Record is indicated by a CR (hexadecimal 0D, escape character \r).
CRLF
End of Record is indicated by a CR followed by an LF (hexadecimal 0D0A, escape characters \n\r).
ANY
End of Record can be CR (0D), LF (0A) or CRLF (0D0A).
Considerations:
• In SSH2 versions before 0085 the default processing was ANY. If files transferred and directly stored in a
structured NonStop us e other end-of-record delimiters, i.e. CR (0D) or CRLF (0D 0A), then the parameter
RECORDDELIMITER must now be set with a value of ANY.
• The SFTP client on NonStop supports the command ASCII with additional options (see chapter "SFTP Client
Command Reference") allowing setting the accepted end of record delimiter (ASCII MAC corresponds to CR,
ASCII DOS to CRLF and ASCII UNIX to LF). That is, for the SFTP client the setting of parameter
RECORDDELIMITER is just the default setting, which can be overwritten using the SFTP client command
ASCII.
• The characters LF and CR cannot occur inside the record data if the value of RECORDDELIMITER is ANY.
The character LF (0A) is not allowed in the record data if the parameter is set to LF. The character CR (0D) is
not allowed in the record data if the parameter is set to CR.
• The record delimiter is a local setting, i.e. there is no negotiation of the record delimiter between ssh client and
ssh server in the supported sftp protocol. The entity reading from a structured file or Guardian edit file must add
the record delimiter to each record read. The entity writing to a structured file or Guardian edit file must split
the received data accordingly and remove the record delimiter before writing the record.
Default
The default for this parameter is LF.
RESTRICTIONCHECKFAILEDDEFAULT
Use this parameter to define the outcome of restriction checks (related to RESTRICTION-PROFILE) in cases in which
no USER record was found for the Guardian user starting an outgoing SSH connection.
Parameter Syntax
RESTRICTIONCHECKFAILEDDEFAULT [TRUE|FALSE]
Arguments
TRUE
94 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 95

Restriction checks will fail if a USER record could not be found.
FALSE
Restriction checks will not fail if a USER record could not be found.
Default
The default for this parameter is FALSE.
SAFEGUARD-PASSWORD-REQUIRED
For G-Series and H-Series RVU prior to H06.11, set this parameter according to the Safeguard PASSWORDREQUIRED configuration.
Parameter Syntax
SAFEGUARD-PASSWORD-REQUIRED [TRUE|FALSE]
Arguments
TRUE
Safeguard PASSWORD-REQUIRED is ON.
FALSE
Safeguard PASSWORD-REQUIRED is OFF.
Considerations
• G-Series and H-Series RVU prior to H06.11 do not support PRIV logon of a Safeguard ALIAS. Hence, SSH2
can only impersonate an ALIAS if a password is provided. If this parameter is set to TRUE, SSH2 will always
request that users mapped to an ALIAS perform password authentication, even after a successful public key
authentication.
• Do not set this parameter for H06.11 RVU or later.
Default
If omitted, the default will be FALSE.
Example
SAFEGUARD-PASSWORD-REQUIRED TRUE
SFTPALLOWGUARDIANCD
Use this parameter to enable the usage of a Guardian style CD command with SFTPSERV.
Parameter Syntax
SFTPALLOWGUARDIANCD [TRUE|FALSE]
Arguments
TRUE
SFTP clients can use Guardian-style CD commands, such as "CD $data05.mysvol".
FALSE
SFTP clients can only use Unix-style CD commands.
Considerations
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 95
Page 96

• The mechanism for resolving Guardian-style sub-volume names may cause problems with some SFTP clients,
such as FileZilla.
• The CD command with Guardian volume and sub-volume only works in the Guardian name space (path starts
with /G). Switching from OSS name space to Guardian name space requires either to put /G in front of the sub-
volume (e.g. cd /G/$us.temp) or to issue a separate cd /G command. This is required only once. When in
Guardian name space a simple cd <sub-volume>, e.g. cd $us.temp, is sufficient.
Default
If omitted, the default will be FALSE.
Example
SFTPALLOWGUARDIANCD TRUE
SFTPCPUSET
This parameter allows configuring the default set of CPUs the SSH2 process starts SFTPSERV user processes in.
Parameter Syntax
SFTPCPUSET cpu-set
Arguments
cpu-set
A comma separated list of CPU numbers or CPU number ranges defining a llowed CPUs.
Default
If omitted, SSH2 will start all SFTPSERV processes in the CPU the SSH2 process is running in unless the USER record
specifies a different CPU set for a specific user via attribute SFTP-CPU-SET.
Example
SFTPCPUSET 2-4,7,10,13-15
Considerations
• A value configured in USE R a t tribute SFTP-CPU-SET has higher priority than the value defined in the SSH2
parameter SFTPCPUSET.
See also:
CPUSET
SFTPDISPLAYGUARDIAN
Use this parameter to control file name format (Guardian or OSS) in SFTP informational messages like "Uploading ..."
and "Fetching ...". Alternately, define =SFTP^DISPLAY^GUARDIAN can be set; define overrides PARAM.
Parameter Syntax
SFTPDISPLAYGUARDIAN [TRUE | FALSE ]
Arguments
TRUE
Guardian file name format is used.
FALSE
96 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 97

File names are displayed in standard ssh format (Unix style with OSS prefix /G or /E).
Default
The default value is FAL SE .
Considerations
• Note that the default Unix style was introduced in SPR T0801^AAS to better conform to the SFTP standard;
before that, the Guardian style was the default.
SFTPEDITLINEMODE
Use this parameter to control the handling of Guardian edit lines that are too long when a file transfer is made to a
Guardian edit file on the NonStop server.
Parameter Syntax
SFTPEDITLINEMODE [ none | cut | wrap ]
Arguments
none
No special handling is done. A long line is treated as an error.
cut
The long line will be cut to ensure a maximum line length of 239 characters.
wrap
The long line will be wrapped, i.e. the first part of the line will be written in 239 character chunks until less than
240 characters are left, which will be written last.
Default
The default value is none.
Considerations
• The setting of this parameter is only relevant if parameter SFTPEDITLINESTARTDECIMALINCR is set to a
number between 0 and 9999 999.
• This parameter is only considered when a Guardian edit file is written, i.e. either if a remote sftp client issues a
put command to the SSH2 server on Nonstop specifying a Guardian destination file with code 101 or if a sftp
client on a NonStop server issues a get command specifying a local Guardian destination file with file code 101.
• If a get command is executed by a sftp client on the NonStop server, then the parameter must be set in the
environment of the sftp client (as PARAM for SFTP running in the Guardian environment or as environment
variable for SFTPOSS running in the OSS environment).
• The parameter SFTPEDITLINEMODE defines the default behavior when Guardian edit files are created. The
handling of lines that are too long can be altered by issuing the command ASLINEMODE at the NonStop SFTP
client prompt. The ASLINEMODE command takes one of the values none, cut and wrap as parameter.
See also:
SFTPEDITLINENUMBERDECIMALINCR, SFTPEDITLINESTARTDECIMALINCR
SFTPEDITLINENUMBERDECIMALINCR
Use this parameter to define the decimal increment used to calculate the next Guardian edit line number when a file
transfer is made to a Guardian edit file on the NonStop server.
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 97
Page 98

Parameter Syntax
SFTPEDITLINENUMBERDECIMALINCR <number>
Arguments
<number>
The value is 1000 times the increment. See documentation for Guardian procedure call INCREMENTEDIT.
Default
The default value is 100 0, i.e. the line numbers a r e incremented by 1)
Examples
Increment by 0.003:
SFTPEDITLINENUMBERDECIMALINCR 3
Increment by 0.1:
SFTPEDITLINENUMBERDECIMALINCR 100
Considerations
• The setting of this parameter is only relevant if parameter SFTPEDITLINESTA RTDE CIMALINCR is set to a
number between 0 and 9999 999.
• Previously, all Guardian edit files were written starting with line number 1 and increment 1.000, which allowed
a maximum of 99999 lines. This behavior is still the default.
• The default increment (1.000) is used for all lines less than the value of parameter
SFTPEDITLINESTARTDECIMALINCR. In order to get the same result as the NonStop FTP server the
parameter SFTPEDITLINENUMBERDECIMALINCR must be set to 100 and the value of
SFTPEDITLINESTARTDECIMALINCR to 40000000.
• This parameter is only considered when a Guardian edit file is written, i.e. either if a remote sftp client issues a
put command to the SSH2 server on Nonstop specifying a Guardian destination file with code 101 or if a sftp
client on a NonStop server issues a get command specifying a local Guardian destination file with file code 101.
• If a get command is executed by a sftp client on the NonStop server, then the parameter must be set in the
environment of the sftp client (as PARAM for SFTP running in the Guardian environment or as environment
variable for SFTPOSS running in the OSS environment).
See also:
SFTPEDITLINEMODE, SFTPEDITLINESTARTDECIMALINCR
SFTPEDITLINESTARTDECIMALINCR
This parameter controls at which line number the decimal increment defined by parameter
SFTPEDITLINENUMBERDECIMALINCR starts.
Parameter Syntax
SFTPEDITLINESTARTDECIMALINCR <number>
Arguments
<number>
The value is 1000 times the line number.
Default
The default value is -1, i.e. decimal increment is not used.
98 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
Page 99

Examples
Start decimal increment at line number 40000:
SFTPEDITLINENUMBERDECIMALINCR 40000000
Start decimal increment at line number 0.000:
SFTPEDITLINENUMBERDECIMALINCR 0
Considerations
• The setting of this parameter is only relevant if parameter SFTPEDITLINESTARTDECIMALINCR is set to a
number between 0 and 9999 999.
• Previously, all Guardian edit files were written starting with line number 1 and increment 1.000, which allowed
a maximum of 99999 lines. This behavior is still the default.
• The default increment (1.000) is used for all lines less than the value of parameter
SFTPEDITLINESTARTDECIMALINCR. In order to get the same result as the NonStop FTP server the
parameter SFTPEDITLINENUMBERDECIMALINCR must be set to 100 and the value of
SFTPEDITLINESTARTDECIMALINCR to 40000000.
• Setting SFTPEDITLINESTARTDECIMALINCR 0 and SFTPEDITLINENUMBERDECIMALINCR to 1
allows for the maximum possible number of lines in Guardian edit files.
• This parameter is only considered when a Guardian edit file is written, i.e. either if a remote sftp client issues a
put command to the SSH2 server on Nonstop specifying a Guardian destination file with code 101 or if a sftp
client on a NonStop server issues a get command specifying a local Guardian destination file with file code 101.
• If a get command is executed by a sftp client on the NonStop server, then the parameter must be set in the
environment of the sftp client (as PARAM for SFTP running in the Guardian environment or as environment
variable for SFTPOSS running in the OSS environment).
See also:
SFTPEDITLINEMODE, SFTPEDITLINENUMBERDECIMALINCR
SFTPEXCLUSIONMODEREAD
Use this parameter to set the exclusion mode of structured files that are opened for read via system procedure
FILE_OPEN_().
Parameter Syntax
SFTPEXCLUSIONMODEREAD <exclusion>
Arguments
<exclusion>
The file open exclusion mode for read operations. Valid values are SHARED, EXCLUSIVE and PROTECTED
Considerations
• If a file is open for write by anther process (shared or protected) and this file is to be read by SFTP or
SFTPSERV, then reading this file will only fail if parameter is set to a different value than SHARED. It can be
required to force a failure in this scenario to ensure the process writing the file closes the file before the file
transfer.
• If a get command is executed by a sftp client on the NonStop server, then the parameter must be set in the
environment of the sftp client (as PARAM for SFTP running in the Guardian environment or as environment
variable for SFTPOSS running in the OSS environment).
Default
HP NonStop SSH Reference Manual Configuring and Running SSH2 • 99
Page 100

If omitted, value SHARED will be used, which was the value used prior to adding parameter
SFTPEXCLUSIONMODEREAD.
Example
SFTPEXCLUSIONMODEREAD EXCLUSIVE
SFTPIDLETIMEOUT
Use this parameter to control how long SFTPSERV keeps running without any SFTP protocol traffic before terminating
itself.
Parameter Syntax
SFTPIDLETIMEOUT <seconds>
Arguments
<seconds>
The time in seconds the SFTPSERV waits after the last SFTP command before it stops serving the client.
Considerations
• The SFTP client will not be able to issue further SFTP commands.
Default
If omitted, there is no SFTP idle timeout. The SFTPSERV will be running until the STP client ends the session.
Example
SFTPIDLETIMEOUT 180
SFTPMAXEXTENTS
Use this parameter to specify the MAXEXTENTS value for files that are created on the NonStop system.
Parameter Syntax
SFTPMAXEXTENTS maxextents
Arguments
maxextents
Specifies the value to be used.
Considerations
• The value can be overridden in "put" and "get" commands using the extended syntax described in "SFTP Client
Reference" chapter, in the section entitled "Extended Syntax for Creation of New Guardian Files".
Default
If omitted, SSH2 will use a value of 900.
Example
SFTPMAXEXTENTS 950
SFTPPRIMARYEXTENTSIZE
Use this parameter to specify the primary extent size for files that are created on the NonStop system.
100 • Configuring and Running SSH2 HP NonStop SSH Reference Manual
 Loading...
Loading...