Page 1

D-Link Air Premier AG DI-784
11a/11g Dualband Wireless
108Mbps Router
Manual
Building Networks for People
Page 2

Contents
Package Contents ................................................................................3
Introduction............................................................................................4
Connections ..........................................................................................5
Features ...............................................................................................6
LEDs ....................................................................................................7
Wireless Basics .................................................................................... 8
Getting Started ....................................................................................10
Using the Configuration Menu.............................................................. 11
Networking Basics ..............................................................................44
Troubleshooting...................................................................................59
Technical Specifications ......................................................................65
Frequently Asked Questions ................................................................68
Contacting Technical Support .............................................................. 96
Warranty and Registration ................................................................... 97
2
Page 3

Package Contents
Contents of Package:
D-Link Air Premier AG DI-784 11a/11g Wireless 108Mbps
Router
Power Adapter – 5V DC, 3.0A
Manual on CD
Quick Installation Guide
Ethernet Cable
Note: Using a power supply with a different voltage rating than the one included with the
DI-784 will cause damage and void the warranty for this product.
If any of the above items are missing, please contact your reseller.
System Requirements For Configuration:
Computer with Windows, Macintosh, or Linux-based
operating system with an installed Ethernet adapter
3
Page 4

Introduction
At up to fifteen times the speed of previous wireless devices, you can work faster and
more efficiently, increasing productivity. With the DI-784, bandwidth-intensive applications
like graphics or multimedia will benefit significantly because large files are able to move
across the network quickly. This versatile wireless router also features four times the
number of non-overlapping channels than a device that supports only 802.11g, so more
users can access the network.
Support for all three standards (802.11g; 802.11a; 802.11b) means that you can grow
your network without having to worry about legacy wireless equipment being incompatible
with newer compliant devices from other manufacturers. This also allows network
administrators to partition the usage of the dualband by segmenting users and creating
special access privilege networks for classified document transfer and communications.
With the DI-784 you can securely connect to wireless clients on the network using
802.1x for wireless user authentication, as well as WPA (Wi-Fi Protected Access )
providing you a much higher level of security for your data and communications than
has previously been available.
Through its easy-to-use Web-based user interface, the DI-784 lets you control the
information that is accessible to those on the wireless network, whether from the Internet
or from your company’s server:
Content Filtering – Easily applied content filtering based on MAC Address, IP Address,
URL and /or Domain Name.
Filter Scheduling – Filters can be scheduled to be active on certain days or for a
duration of hours or minutes.
Network Address Translation – NAT protects the DI-784 and its users from outside
intruders gaining access to your private network
VPN Multiple/Concurrent Sessions – Supports multiple and concurrent IPSec and
PPTP sessions, so multiple users behind the DI-784 can access corporate networks
through various VPN clients more securely.
TM
4
Page 5
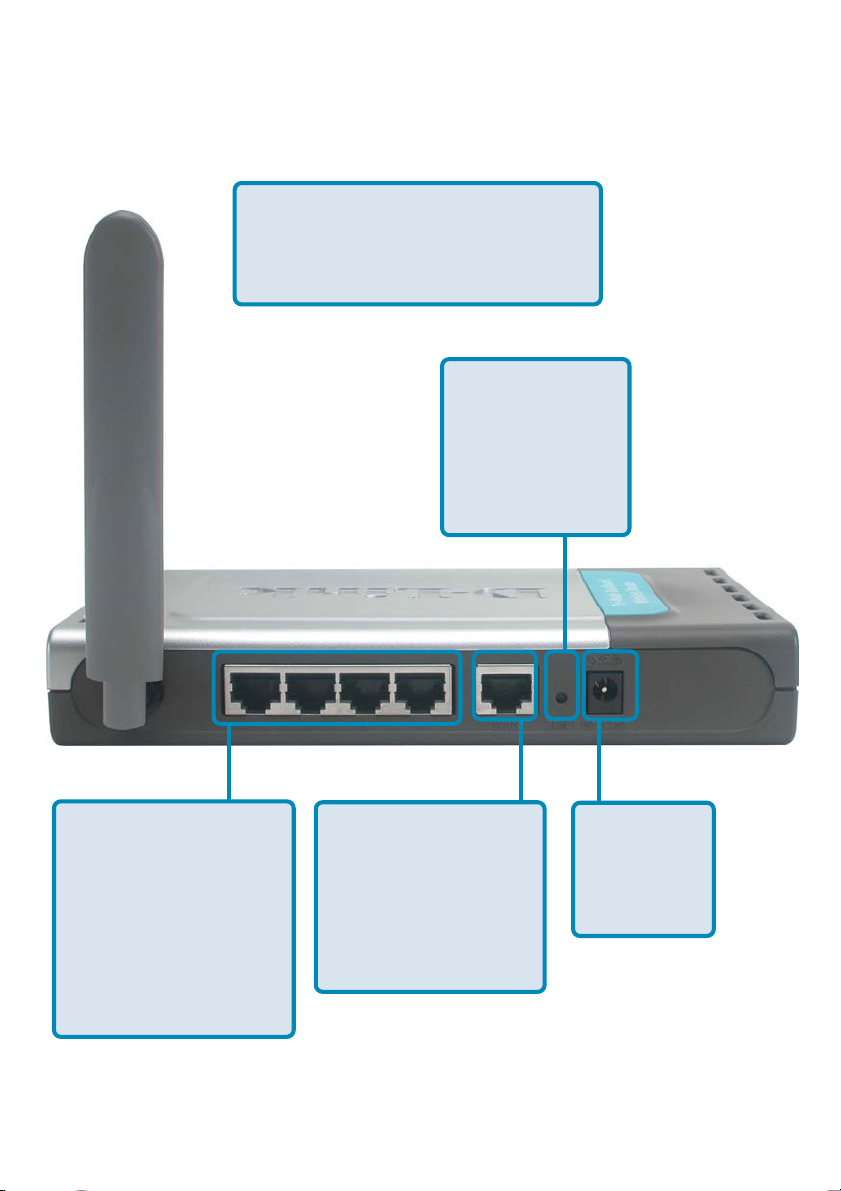
Connections - Back Panel of Unit
All Ethernet Ports (WAN and LAN)
are auto MDI/MDIX, meaning you can
use either a straight-through or a
crossover Ethernet cable.
Pressing the
Reset Button
restores the
router to its
original factory
default settings.
Auto MDI/MDIX
LAN ports
automatically
sense the cable
type when
connecting to
Ethernet-enabled
computers.
The Auto MDI/MDIX
WAN port is the
connection for the
Ethernet cable to
the Cable or DSL
modem
Receptor
for the
Power
Adapter
5
Page 6

Features
Fully compatible with the 802.11a and 802.11g standards to provide a wire-
less data rate of up to 54Mbps
Backwards compatible with the 802.11b standard to provide a wireless data
rate of up to 11Mbps
WPA (Wi Fi Protected Access ) authorizes and identifies users based on a
secret key that changes automatically at a regular interval, for example:
TKIP (Temporal Key Integrity Protocol), in conjunction with a RADIUS
server, changes the temporal key every 10,000 packets, ensuring greater
security
Pre-Shared Key mode means that the home user, without a RADIUS
server, can connect securely via a pre-shared key, vastly improving the
safety of communications on the network.
802.1x Authentication in conjunction with the RADIUS server verifies the
identity of would be clients
Utilizes OFDM technology (Orthogonal Frequency Division Multiplexing) to
ensure strong wireless signals for both 802.11g and 802.11a
User-friendly configuration and diagnostic utilities
Operates in the 2.4GHz and 5GHz frequency ranges
TM
Connects multiple computers to a Broadband (Cable or DSL) modem to
share the Internet connection
Advanced Firewall features
Supports NAT with VPN pass-through, providing added security
MAC Filtering
IP Filtering
URL Filtering
Domain Blocking
Scheduling
DHCP server supported enables all networked computers to automatically
receive IP addresses
Web-based interface for Managing and Configuring
Access Control to manage users on the network
Supports special applications that require multiple connections
Equipped with 4 10/100 Ethernet ports, 1 WAN port, Auto MDI/MDIX
6
Page 7
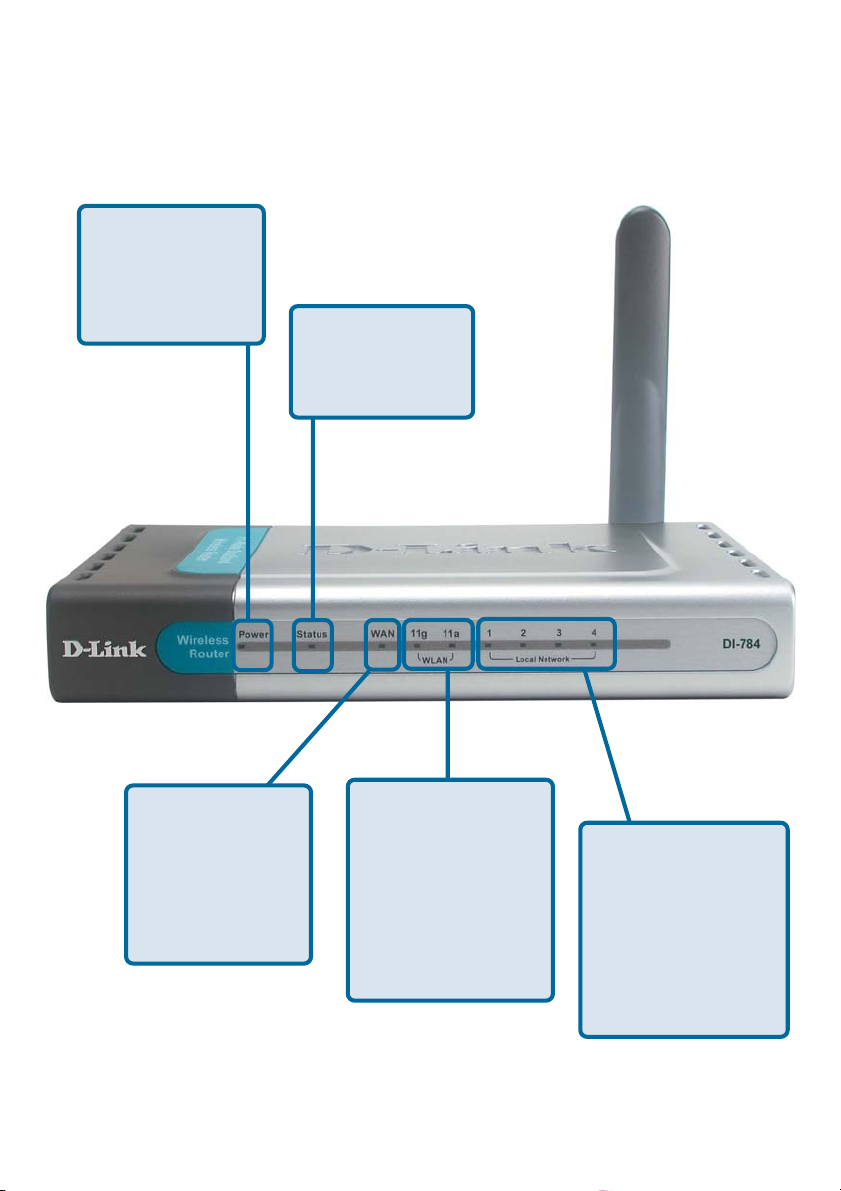
LEDs - Front Panel of Unit
LED stands for Light-Emitting Diode. The DI-784 has the following LEDs:
Power
A solid light
indicates a proper
connection to the
power supply.
Status
A blinking light
indicates that the
DI-784 is ready.
WAN LED
A solid light
indicates connection on the WAN
port. This LED
blinks during data
transmission.
WLAN LEDs for 11g
and 11a wireless net-
work segments.
A solid light indicates that the
wireless segment is
ready. The LEDs
blink during wireless
data transmission.
Local
Network LEDs
A solid light indicates
a connection to an
Ethernet-enabled
computer on ports 1-
4. The LEDs blink
during data transmission.
7
Page 8

Wireless Basics
D-Link wireless products are based on industry standards to provide easy-to-use and
compatible high-speed wireless connectivity within your home, business or public access
wireless networks. D-Link wireless products will allow you access to the data you want,
when and where you want it. You will be able to enjoy the freedom that wireless networking
brings.
A WLAN is a cellular computer network that transmits and receives data with radio
signals instead of wires. WLANs are used increasingly in both home and office
environments, and public areas such as airports, coffee shops and universities. Innovative
ways to utilize WLAN technology are helping people to work and communicate more
efficiently. Increased mobility and the absence of cabling and other fixed infrastructure
have proven to be beneficial for many users.
Wireless users can use the same applications they use on a wired network. Wireless
adapter cards used on laptop and desktop systems support the same protocols as
Ethernet adapter cards.
People use wireless LAN technology for many different purposes:
Mobility - Productivity increases when people have access to data in any location
within the operating range of the WLAN. Management decisions based on real-time
information can significantly improve worker efficiency.
Low Implementation Costs – WLANs are easy to set up, manage, change and
relocate. Networks that frequently change can benefit from WLANs ease of
implementation. WLANs can operate in locations where installation of wiring may be
impractical.
Installation and Network Expansion - Installing a WLAN system can be fast
and easy and can eliminate the need to pull cable through walls and ceilings. Wireless
technology allows the network to go where wires cannot go - even outside the home or
office.
Scalability – WLANs can be configured in a variety of topologies to meet the needs of
specific applications and installations. Configurations are easily changed and range
from peer-to-peer networks suitable for a small number of users to larger infrastructure
networks to accommodate hundreds or thousands of users, depending on the number
of wireless devices deployed.
Inexpensive Solution - Wireless network devices are as competitively priced as
conventional Ethernet network devices.
8
Page 9

Wireless Basics (continued)
Standards-Based Technology
The DI-784 Wireless Broadband Router utilizes the new 802.11g standard, in addition
to the 802.11a and 802.11b standards.
The IEEE 802.11g standard is an extension of the 802.11b standard. It increases the
data rate up to 54 Mbps within the 2.4GHz band, utilizing OFDM technology.
This means that in most environments, within the specified range of this device, you will
be able to transfer large files quickly or even watch a movie in MPEG format over your
network without noticeable delays. This technology works by transmitting high-speed
digital data over a radio wave utilizing OFDM (Orthogonal Frequency Division Multiplexing)
technology. OFDM works by splitting the radio signal into multiple smaller sub-signals
that are then transmitted simultaneously at different frequencies to the receiver. OFDM
reduces the amount of crosstalk (interference) in signal transmissions.
.
Installation Considerations
The D-Link Air Premier AG DI-784 lets you access your network, using a wireless
connection, from virtually anywhere within its operating range. Keep in mind, however,
that the number, thickness and location of walls, ceilings, or other objects that the
wireless signals must pass through, may limit the range. Typical ranges vary depending
on the types of materials and background RF (radio frequency) noise in your home or
business. The key to maximizing wireless range is to follow these basic guidelines:
Keep the number of walls and ceilings between the DI-784 and other network
11
1
11
devices to a minimum - each wall or ceiling can reduce your D-Link wireless
product’s range from 3-90 feet (1-30 meters.) Position your devices so that
the number of walls or ceilings is minimized.
Be aware of the direct line between network devices. A wall that is 1.5 feet
22
2
22
thick (.5 meters), at a 45-degree angle appears to be almost 3 feet (1 meter)
thick. At a 2-degree angle it looks over 42 feet (14 meters) thick! Position
devices so that the signal will travel straight through a wall or ceiling (instead
of at an angle) for better reception.
Building Materials can impede the wireless signal - a solid metal door or
33
3
33
aluminum studs may have a negative effect on range. Try to position wireless
devices and computers with wireless adapters so that the signal passes
through drywall or open doorways and not other materials.
Keep your product away (at least 3-6 feet or 1-2 meters) from electrical
44
4
44
devices or appliances that generate extreme RF noise.
9
Page 10
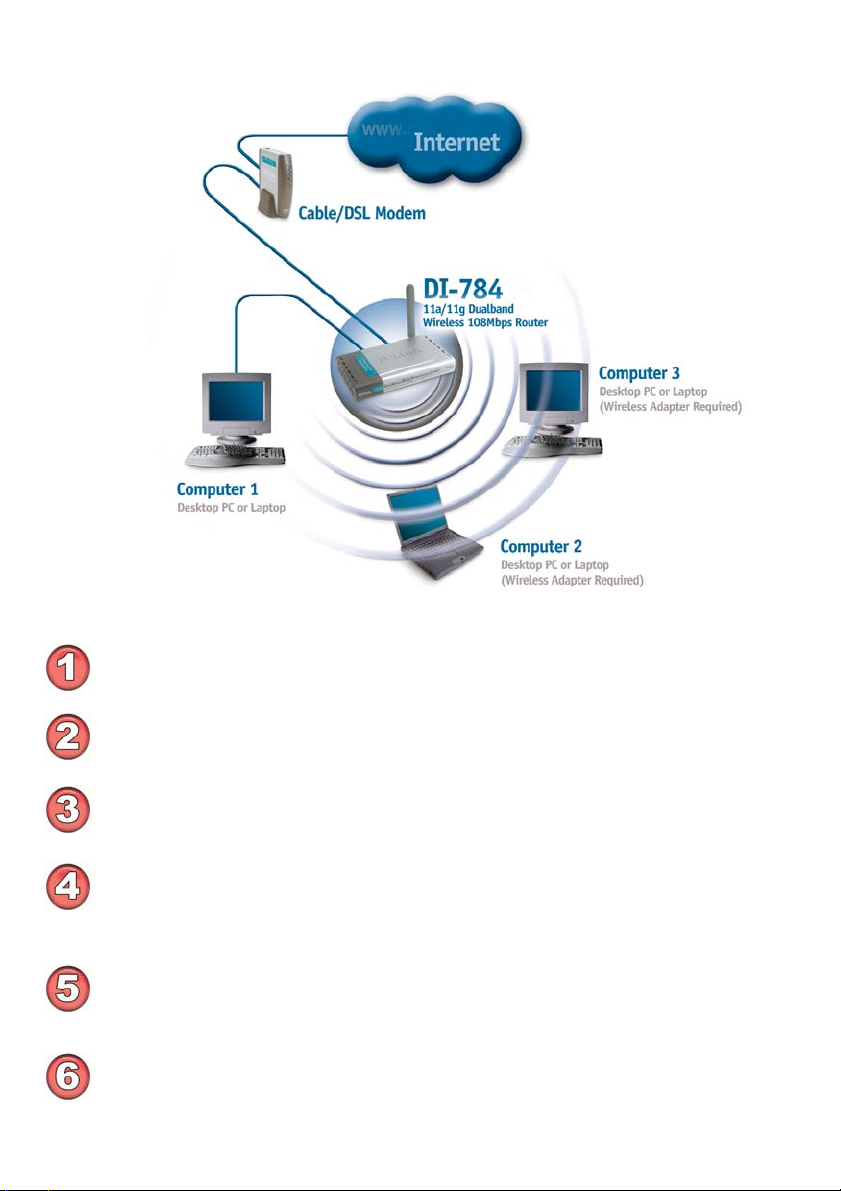
Getting Started
Setting up a
Wireless
22
2
Infrastructure
Network
66
6
66
You will need broadband Internet access (a Cable or DSL-subscriber line into
your home or office)
For a typical wireless setup at home (as shown above),
22
33
3
33
please do the following:
11
1
11
55
5
55
44
4
44
Consult with your Cable or DSL provider for proper installation of the modem
Connect the Cable or DSL modem to the DI-784 Wireless Router (see the
printed Quick Installation Guide included with your router.)
If you are connecting a desktop computer to your network, install the D-Link Air
Premier AG DWL-AG530 wireless PCI adapter into an available PCI slot on your
desktop computer.
(See the printed Quick Installation Guide included with the network adapter.)
Install the D-Link DWL-AG650S wireless Cardbus adapter into a laptop computer. (See the printed Quick Installation Guide included with the DWL-AG660.)
Install the D-Link DFE-530TX+ wireless Cardbus adapter into a desktop computer. The four Ethernet LAN ports of the DI-784 are Auto MDI/MDIX and will
work with both Straight-through and Crossover cable.
(See the printed Quick Installation Guide included with the DFE-530TX+.)
10
Page 11
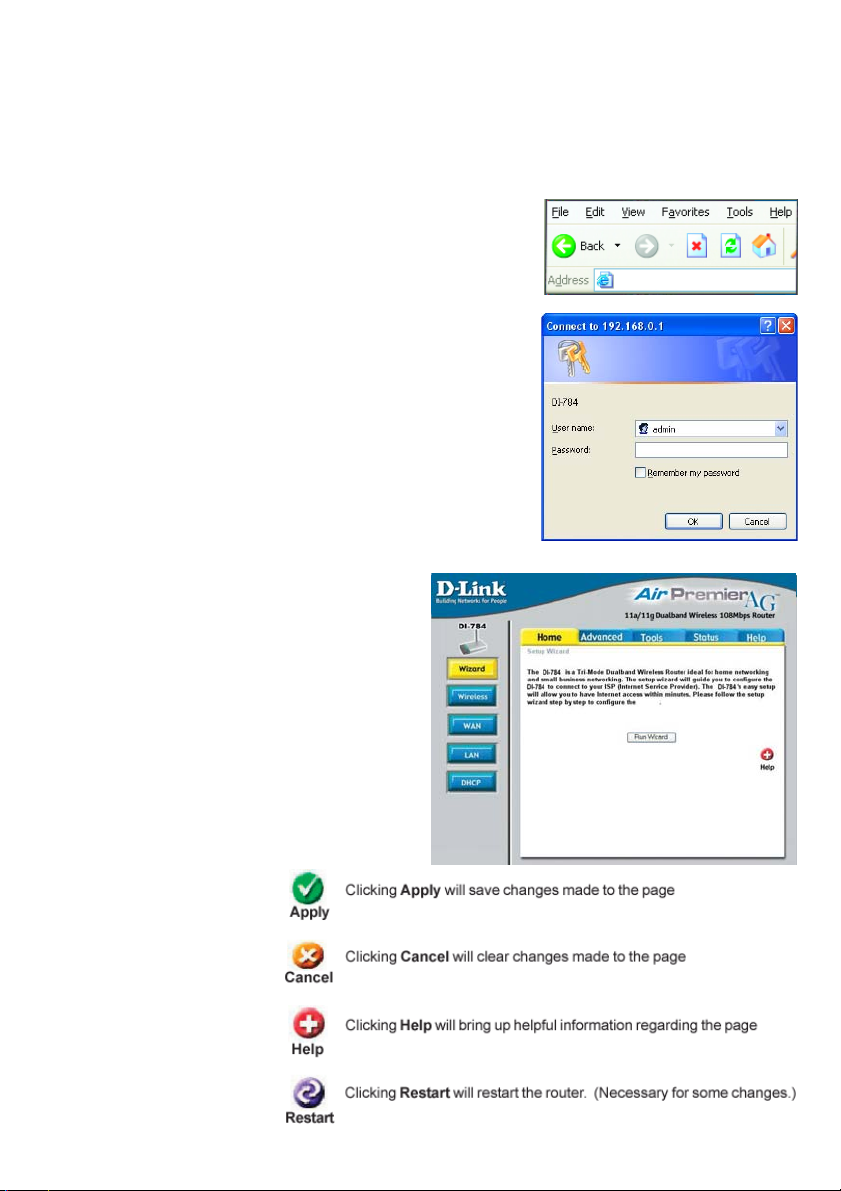
Using the Configuration Menu
Whenever you want to configure your network or the DI-784, you can access the
Configuration Menu by opening the web-browser and typing in the IP Address of the
DI-784. The DI-784 default IP Address is shown here:
Open the web browser
Type in the IP Address of
the Router (http://192.168.0.1)
Note: if you have changed the default IP Address
assigned to the DI-784, make sure to enter the
correct IP Address.
Type admin in the User
Name field
blank
Leave the Password
Click OK
Home > Wizard
The Home>Wizard screen will appear.
Please refer to the Quick Installation
Guide for more information regarding the
Setup Wizard.
http://192.168.0.1
These buttons appear
on most of the configuration screens in this
section. Please click on
the appropriate button
at the bottom of each
screen after you have
made a configuration
change.
11
Page 12
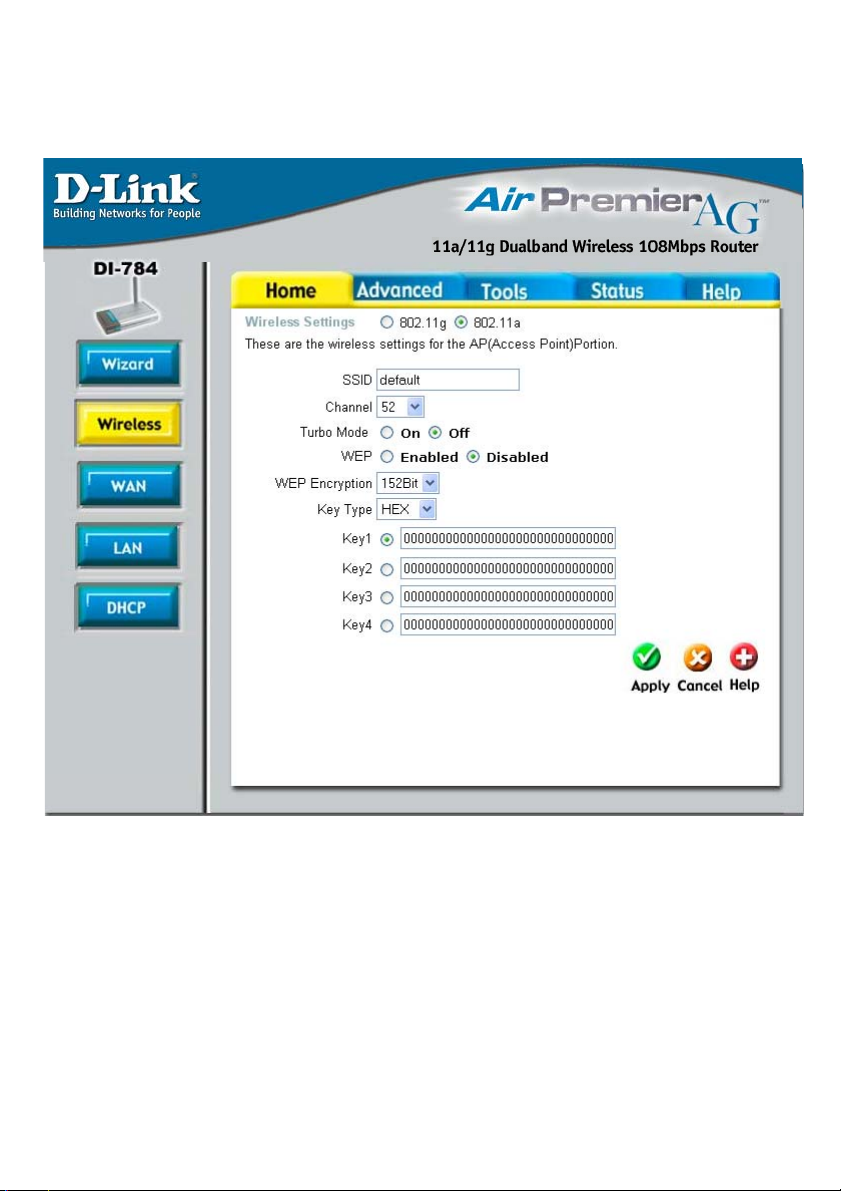
Using the Configuration Menu (continued)
Home > Wireless > Open or Shared
52
Wireless Settings-
Choose 802.11a or 802.11g. Here, 802.11a is selected.
802.11a uses the 5GHz frequency range and can support speeds of up to 54Mbps.
802.11g uses the 2.4GHz frequency range and can support speeds of up to 54Mbps.
802.11g is also backwards compatible with 802.11b.
SSID-
“default” is the default setting. All devices on the network must share the same SSID. If
you change the default setting, the SSID may be up to 32 characters long.
12
Page 13
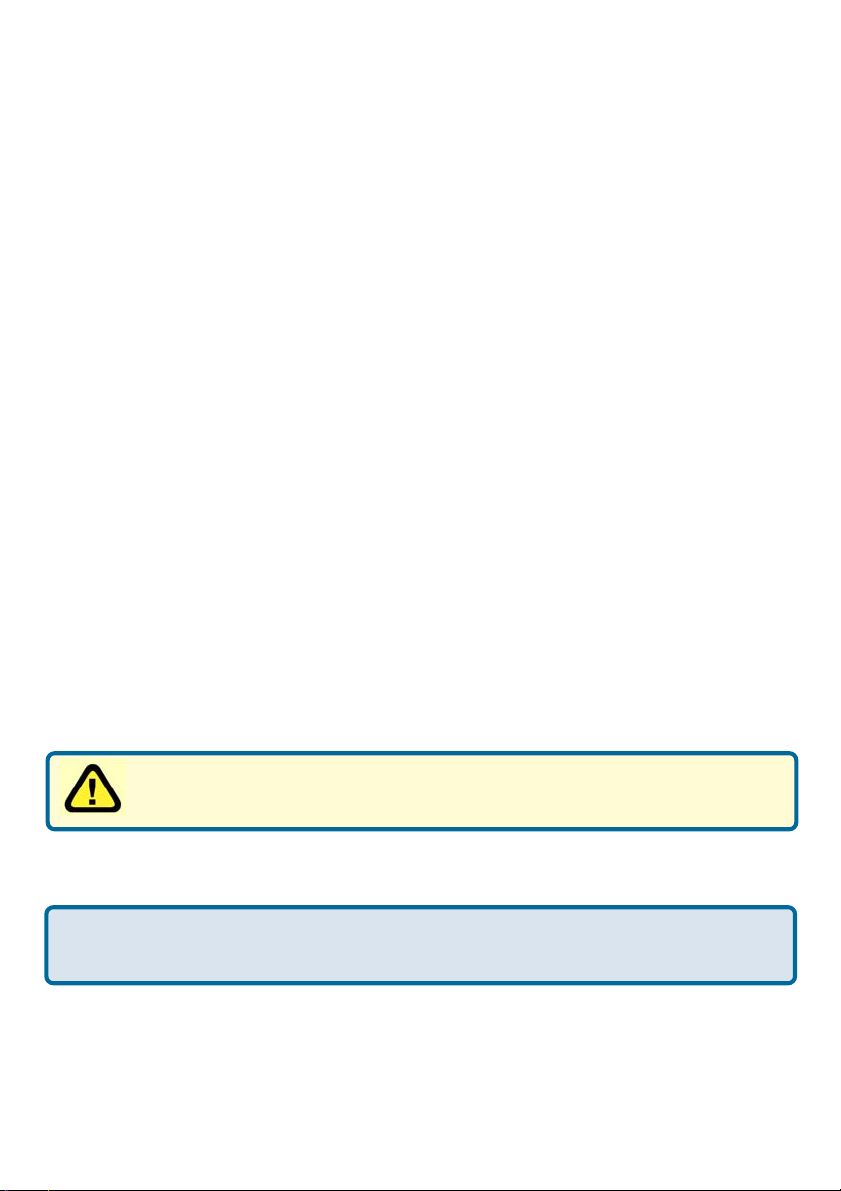
Using the Configuration Menu (continued)
Home > Wireless > Open or Shared (continued)
Channel-
52 is the default channel for 802.11a.
6 is the default channel for 802.11g.
All devices on the network must share the same channel.
Authentication- Open System - communicates the key across the network
Shared Key - devices must have identical WEP settings in or-
der to communicate in the network
WPA - Wi-Fi Protected Access authorizes and authenticates
users onto the wireless network. WPA uses stronger security
than WEP and is based on a key that changes automatically at
a regular interval. This mode requires a RADIUS server in the
network.
WPA-PSK - Pre-Shared Key mode means that the wireless client and the router must have the same passphrase in order to
establish the wireless connection. A RADIUS server is not required with PSK.
WEP-
WEP Encryption-
All the devices on your network must share the same wireless
settings in order to communicate.
Select Enabled or Disabled. Disabled is the default setting.
Select the level of encryption desired: 64, 128 or 152-bit
Key Type-
Hexadecimal digits consist of the numbers 0-9 and the letters A-F
ASCII (American Standard Code for Information Interchange) is a code for repre-
senting English letters as numbers from 0-127
Keys 1-4-
Select HEX or ASCII
Input up to 4 WEP keys; select the one you wish to use.
13
Page 14
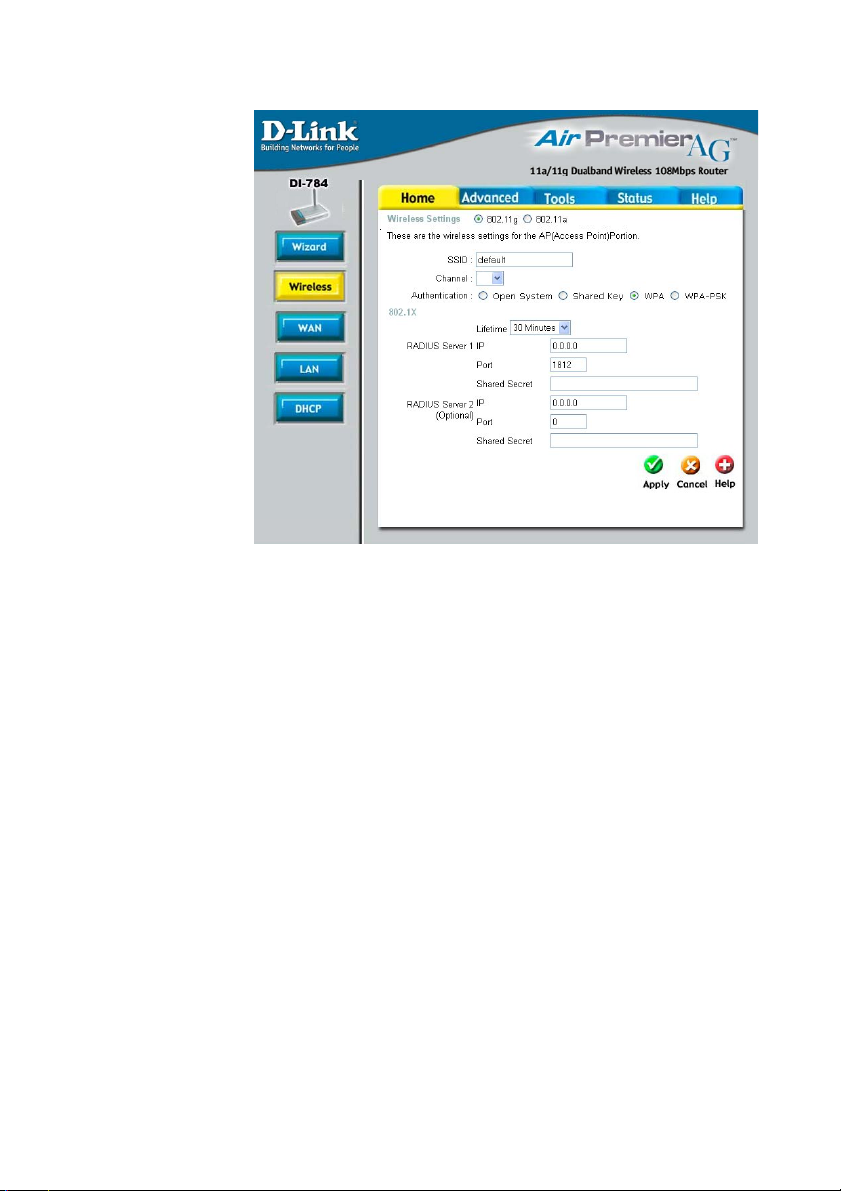
Using the Configuration Menu (continued)
Home > Wireless > WPA
1
11
Authentication-
802.1x
Lifetime-
Radius Server 1-
Radius Server 2-
WPA (Wi-Fi Protected Access) is selected.
Wi-Fi Protected Access authorizes and authenticates users onto
the wireless network. WPA uses stronger security than WEP
and is based on a key that changes automatically at a regular
interval.This mode requires the inclusion of a RADIUS server in
your network.
802.1x Authentication is a first line of defense against intrusion.
In the Authentication process the server verifies the identity of
the client attempting to connect to the network. Unfamiliar clients are denied access.
Select 5, 15, 30 minutes, or 1 or 8 hours, or 1 day for the authentication period. After this period expires, a new key will automatically be generated.
IP - Enter the IP Address of the RADIUS server.
Port - Enter the port number that your RADIUS server uses for
Authentication. The default setting of 1812 is the port setting for
many RADIUS servers.
Shared Secret - Enter the Shared Secret. The Shared Secret
must be the same as the Shared Secret on your RADIUS server.
Optional. If you have a second RADIUS server, you will
input the same information as shown above.
14
Page 15
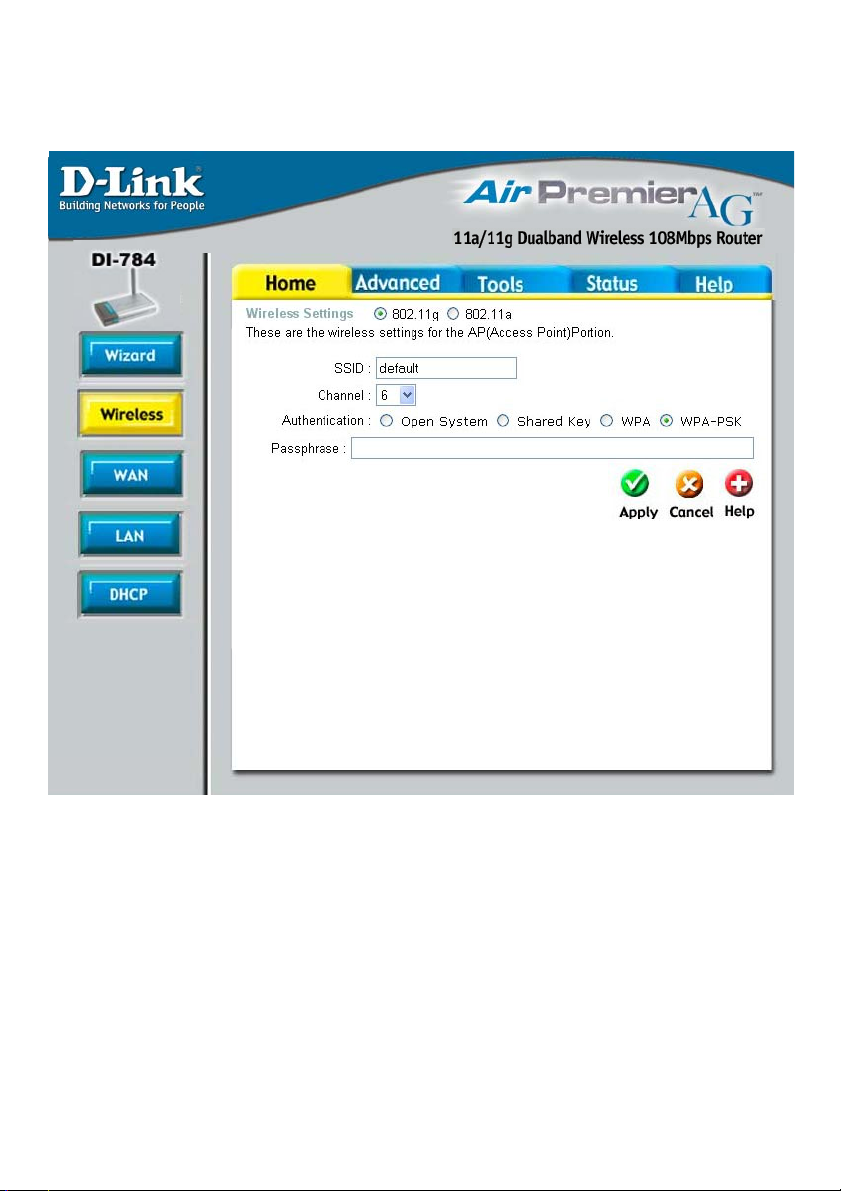
Using the Configuration Menu (continued)
Home > Wireless > WPA-PSK
1
Authentication-
Passphrase-
WPA-PSK - Pre-Shared Key mode means that the wireless cli-
ent and the router must have the same passphrase in order to
establish the wireless connection. A RADIUS server is not required with PSK.
Enter a passphrase for the router. The RADIUS server should
use the same passphrase (secret key) as the router.
15
Page 16
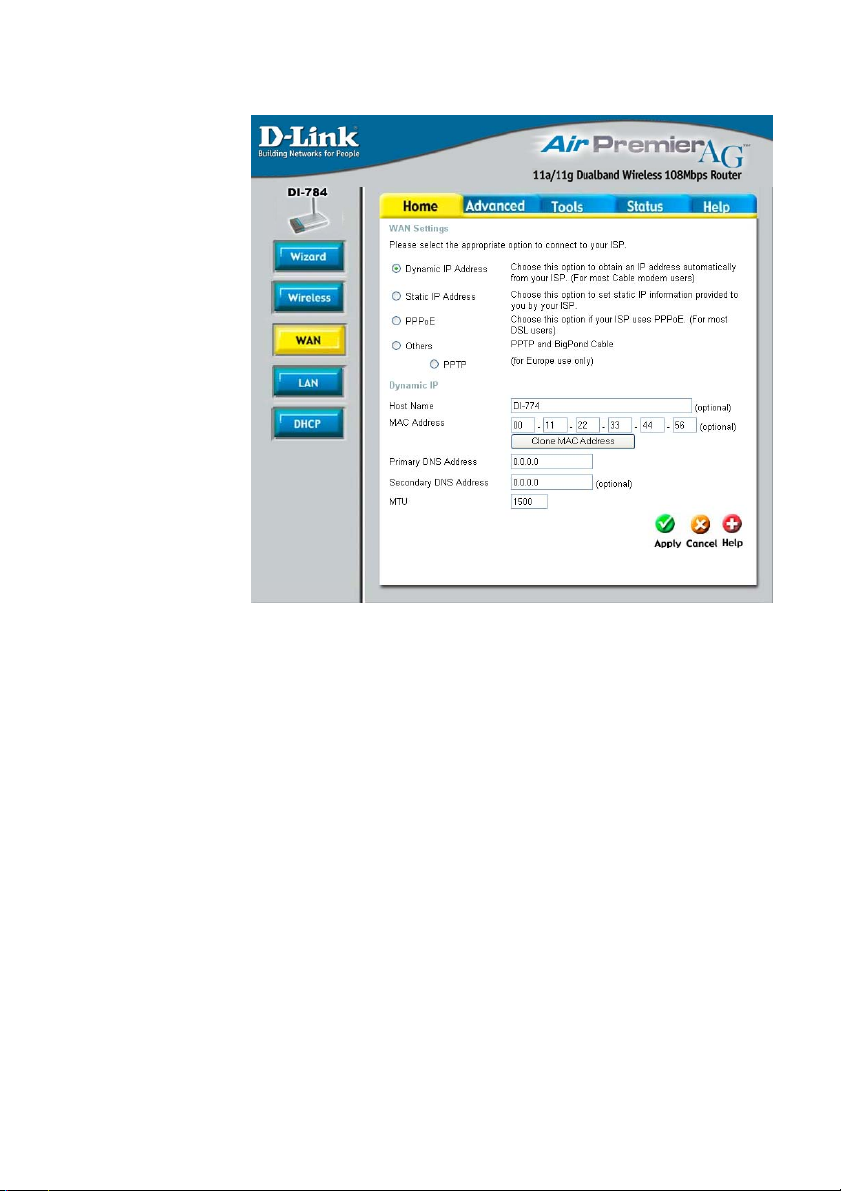
Using the Configuration Menu (continued)
Home > WAN > Dynamic IP Address
Dynamic
IP Address-
Host Name-
MAC Address-
Clone
MAC Address-
Primary/Secondary
DNS-
MTU-
Most Cable modem users will select this option to obtain an IP
Address automatically from their ISP (Internet Service Provider).
This is optional, but may be required by some ISPs. The host
name is the device name of the Router.
The default MAC Address is set to the WAN’s physical interface MAC address on the Router.
Copy the MAC address of the Ethernet card installed by your ISP,
and replace the WAN MAC address with this Ethernet card MAC
address. It is not recommended that you change the default MAC
address unless required by your ISP.
Enter a DNS Address if you do not wish to use the one provided
by your ISP. (DNS is short for Domain Name System. It trans-
lates domain names into IP Addresses).
Enter an MTU value only if required by your ISP. Otherwise,
leave this section to its default setting of 1500. (MTU is short
for Maximum Transfer Unit. Messages longer than the MTU
will be divided into smaller units for transmission).
16
Page 17
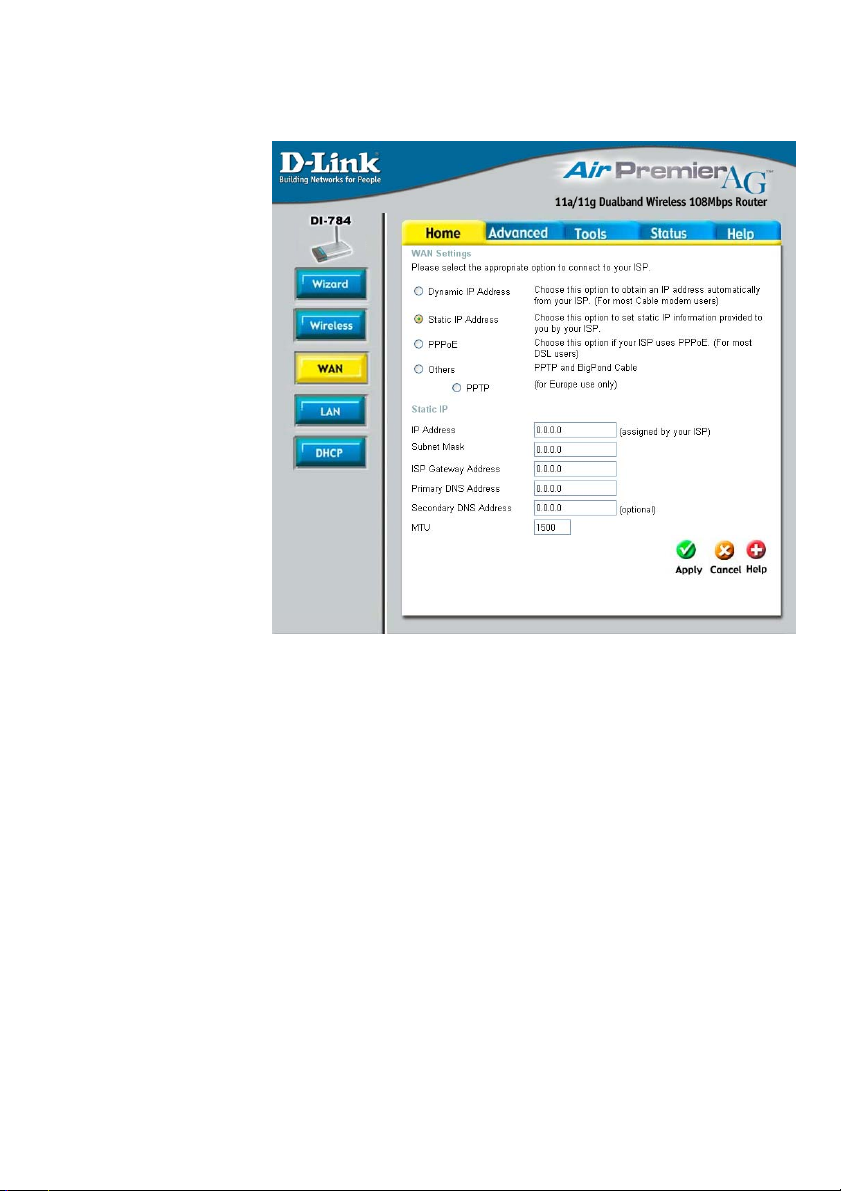
Using the Configuration Menu (continued)
Home > WAN > Static IP Address
Static IP Address-
IP Address-
Subnet Mask-
ISP
Gateway Address-
Primary/
Secondary DNS-
MTU-
Select this option to set static IP information provided to you
by your ISP.
Input the IP Address provided by your ISP
Input your Subnet mask. (All devices in the network must
have the same subnet mask.)
Input the Gateway address
Enter a DNS Address if you do not wish to use the one provided by your ISP. (DNS is short for Domain Name System. It
translates domain names into IP Addresses).
Enter an MTU value only if required by your ISP. Otherwise,
leave this section to its default setting of 1500. (MTU is short
for Maximum Transfer Unit. Messages longer than the MTU
will be divided into smaller units for transmission).
17
Page 18

Using the Configuration Menu (continued)
Home > WAN > PPPoE
Please
be sure
to remove any
existing PPPoE
client software
installed on your
computers.
PPPoE-
Choose this option if your ISP uses PPPoE.
will select this option).
(Most DSL users
User Name-
Password-
Retype Password-
Service Name-
IP Address-
Dynamic PPPoE- receive an IP Address automaticsally from
your ISP.
Static PPPoE- you have an assigned (static) IP Address.
Your PPPoE username provided by your ISP.
Your PPPoE password provided by your ISP.
Re-enter the PPPoE password
Enter the Service Name provided by your ISP (optional).
This option is only available for Static PPPoE. Enter the static
IP Address for the PPPoE connection.
18
Page 19
Using the Configuration Menu (continued)
Home > WAN > PPPoE continued
Primary/Secondary
DNS-
Maximum
Idle Time-
MTU-
Auto-reconnect-
LAN is short for Local Area Network.
This is considered
your internal network.
These are the IP settings of the LAN interface for the DI-784.
These settings may
be referred to as Private settings. You
may change the LAN
IP Address if needed.
The LAN IP Address
is private to your internal network and
cannot be seen on
the Internet.
Enter a DNS Address if you do not wish to use the one provided
by your ISP. (DNS is short for Domain Name System. It trans-
lates domain names into IP Addresses).
Enter a maximum idle time during which Internet connection is
maintained during inactivity. To disable this feature, enter zero
or enable Auto-reconnect.
Maximum Transmission Unit-1472 is default-you may need to
change the MTU to conform with your ISP.
If enabled, the DI-784 will automatically connect to your ISP after your system is restarted or if the connection is dropped.
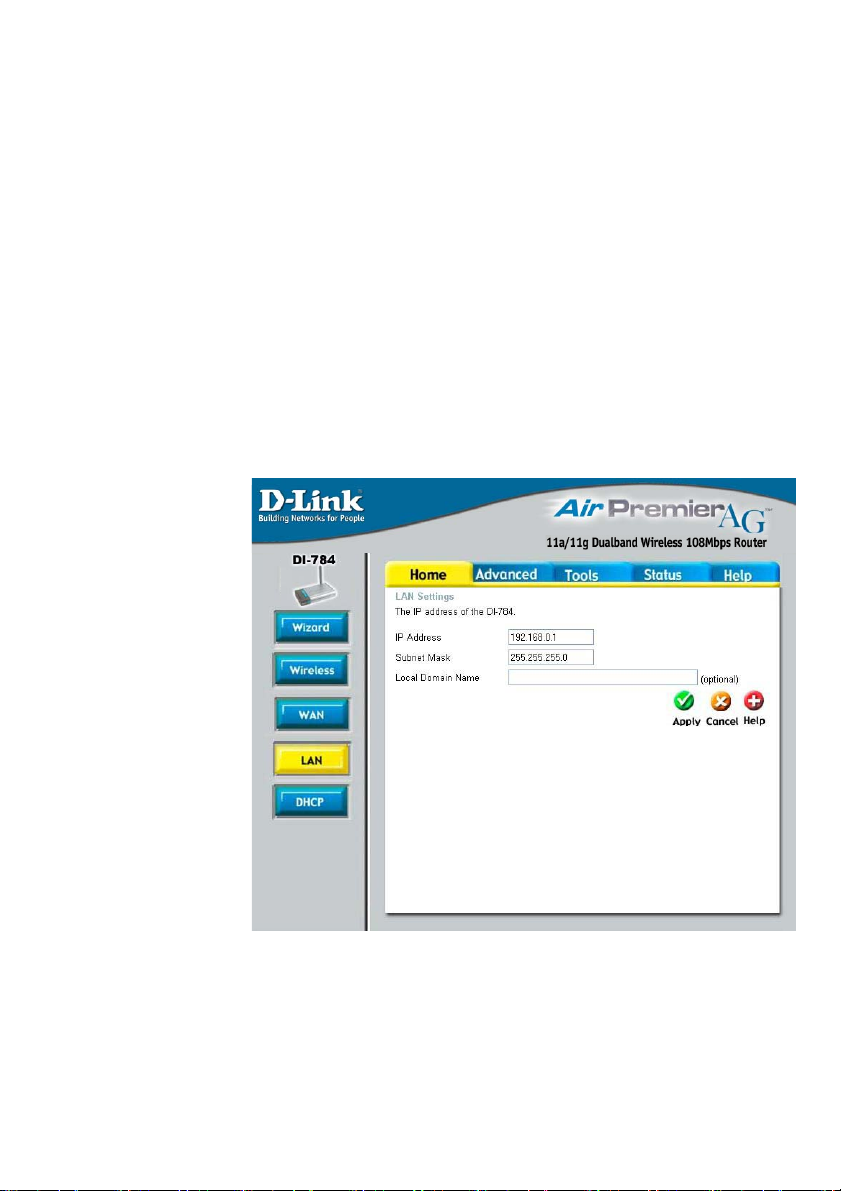
Home > LAN
IP Address-
Subnet Mask-
Local Domain
Name-
The IP Address of the LAN interface. The default IP Asddress is:
192.168.0.1.
The subnet mask of the LAN interface.
The default subnet mask is 255.255.255.0.
The domain name assigned to the router.
19
Page 20
Using the Configuration Menu (continued)
DHCP stands for
Dynamic Host
Control Protocol. The
DI-784 has a built-in
DHCP server. The
DHCP Server will
automatically assign
an IP Address to the
computers on the
LAN/private network.
Be sure to set your
computers to be
DHCP clients by
setting their TCP/IP
settings to “Obtain
an IP Address
Automatically.” When
you turn your
computers on, they
will automatically
load the proper TCP/
IP settings provided
by the DI-784. The
DHCP Server will
automatically
allocate an unused IP
Address from the IP
Address pool to the
requesting computer.
You must specify the starting and ending address of the IP Address pool.
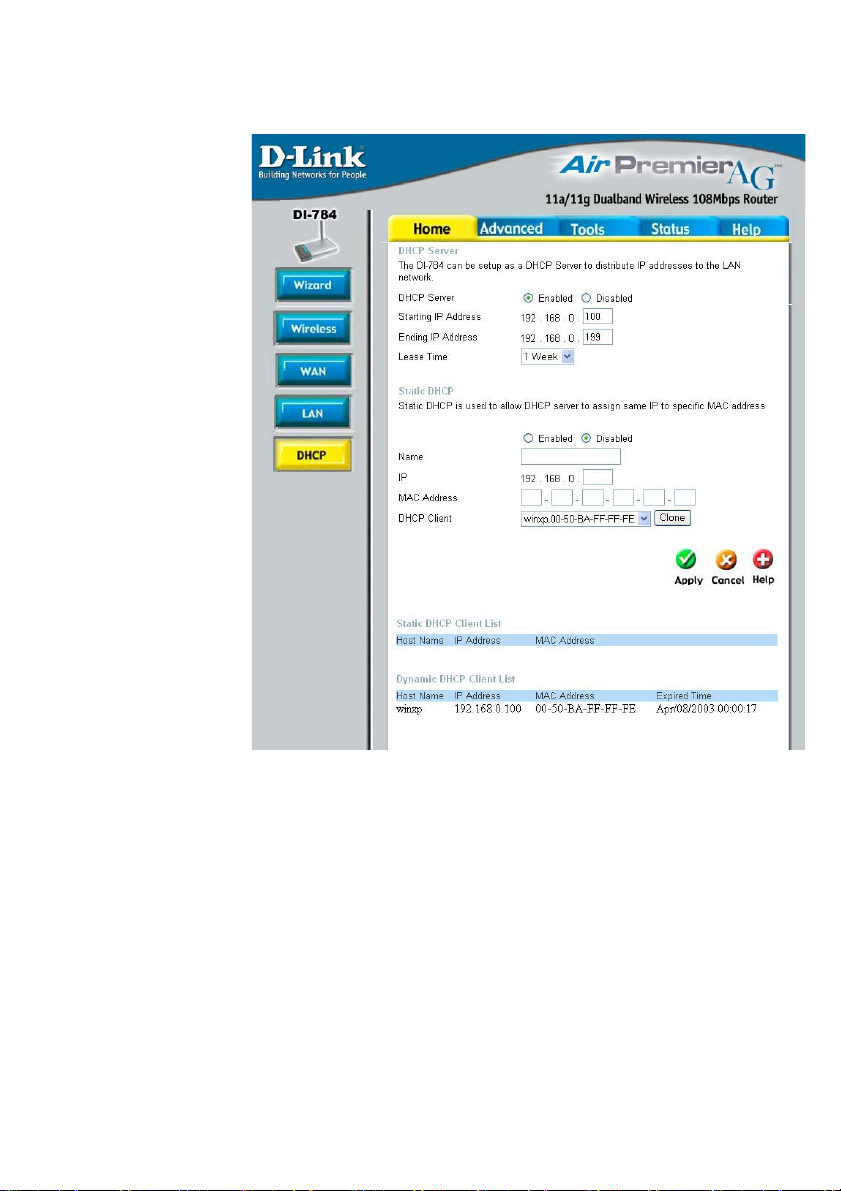
Home > DHCP
DHCP Server-
Starting
IP Address-
Ending
IP Address-
Lease Time-
Static DHCP-
Static & Dynamic
DHCP Client
Table-
Select Enabled or Disabled.
The starting IP Address for the DHCP server’s IP assignment.
The ending IP Address for the DHCP server’s IP assignment.
The length of time of the DHCP lease.
Enable the Static DHCP server to assign the same IP Address
to a MAC Address that you specify here. This prevents the problems sometimes encountered with changing IP Addresses.
Displays a list of Static and Dynamic DHCP clients assigned by
the router.
20
Page 21

Using the Configuration Menu (continued)
Advanced > Virtual Server
The DI-784 can be configured as a virtual server so that remote users accessing Web
or FTP services via the public IP Address can be automatically redirected to local
servers in the LAN (Local Area Network).
The DI-784 firewall feature filters out unrecognized packets to protect your LAN
network so all computers networked with the DI-784 are invisible to the outside world.
If you wish, you can make some of the LAN computers accessible from the Internet
by enabling Virtual Server. Depending on the requested service, the DI-784 redirects
the external service request to the appropriate server within the LAN network.
21
Page 22

Using the Configuration Menu (continued)
Advanced > Virtual Server continued
The DI-784 is also capable of port-redirection meaning incoming traffic to a particular
port may be redirected to a different port on the server computer.
Each virtual service that is created will be listed at the bottom of the screen in the
Virtual Servers List. There are pre-defined virtual services already in the table. You
may use them by enabling them and assigning the server IP to use that particular
virtual service.
Virtual Server-
Name-
Private IP-
Select Enabled or Disabled.
Enter the name referencing the virtual service.
The server computer in the LAN (Local Area Network) that will be
providing the virtual services.
Protocol Type- The protocol used for the virtual service.
Private Port-
Public Port-
Schedule-
The port number of the service used by the Private IP computer.
The port number on the WAN (Wide Area Network)side that will
be used to access the virtual service.
The schedule of time when the virtual service will be enabled.
The schedule may be set to Always, which will allow the
particular service to always be enabled. If it is set to Time,
select the time frame for the service to be enabled. If the
system time is outside of the scheduled time, the service will
be disabled.
Example #1:
If you have a Web server that you wanted Internet users to access at all times, you
would need to enable it. Web (HTTP) server is on LAN (Local Area Network)
computer 192.168.0.25. HTTP uses port 80, TCP.
Name: Web Server
Private IP: 192.168.0.25
Protocol Type: TCP
Private Port: 80
Public Port: 80
Schedule: always
22
Page 23
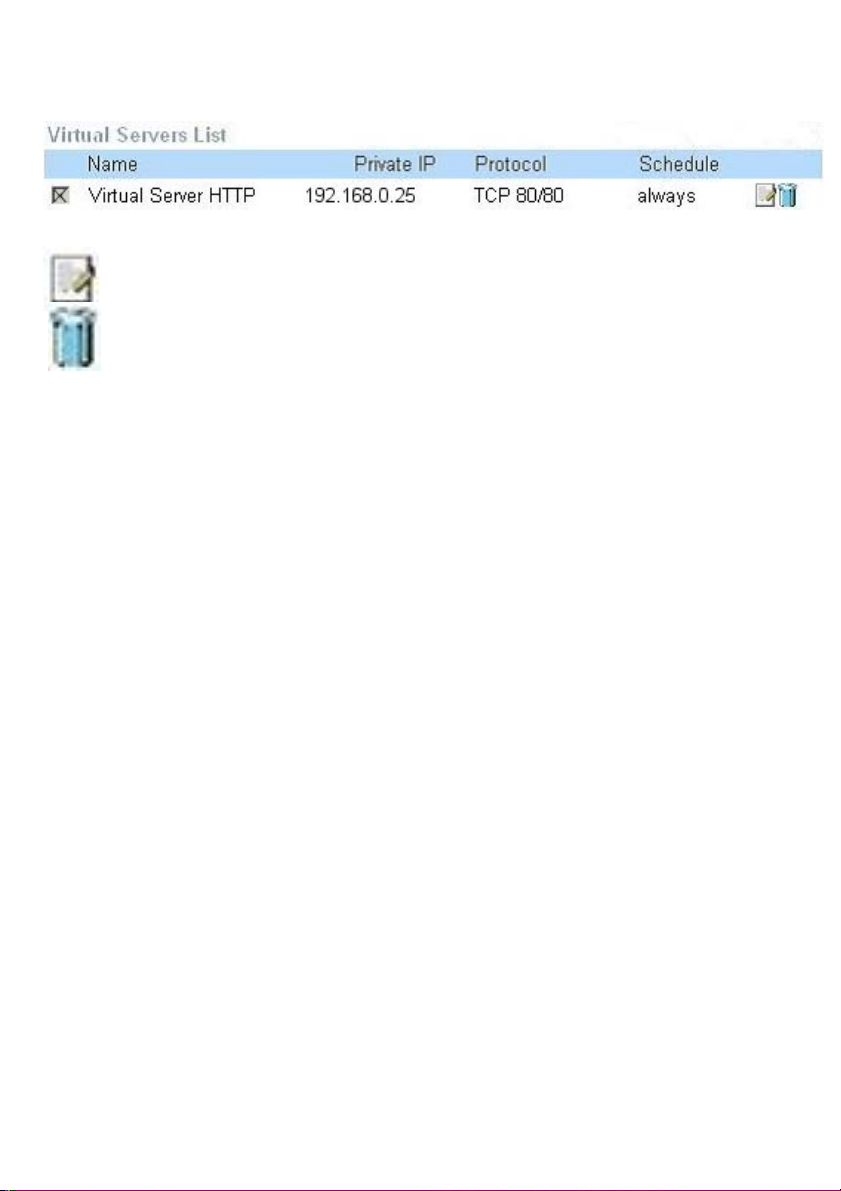
Using the Configuration Menu (continued)
Advanced > Virtual Server continued
Click on this icon to edit the virtual service
Click on this icon to delete the virtual service
Example #2:
If you have an FTP server that you wanted Internet users to access by WAN port
2100 and only during the weekends, you would need to enable it as such. FTP
server is on LAN computer 192.168.0.30. FTP uses port 21, TCP.
Name: FTP Server
Private IP: 192.168.0.30
Protocol Type: TCP
Private Port: 21
Public Port: 2100
Schedule: From: 01:00AM to 11:00PM, Sat to Sun
All Internet users who want to access this FTP Server
must connect to it from port 2100. This is an example of
port redirection and can be useful in cases where there
are many of the same servers on the LAN network.
23
Page 24
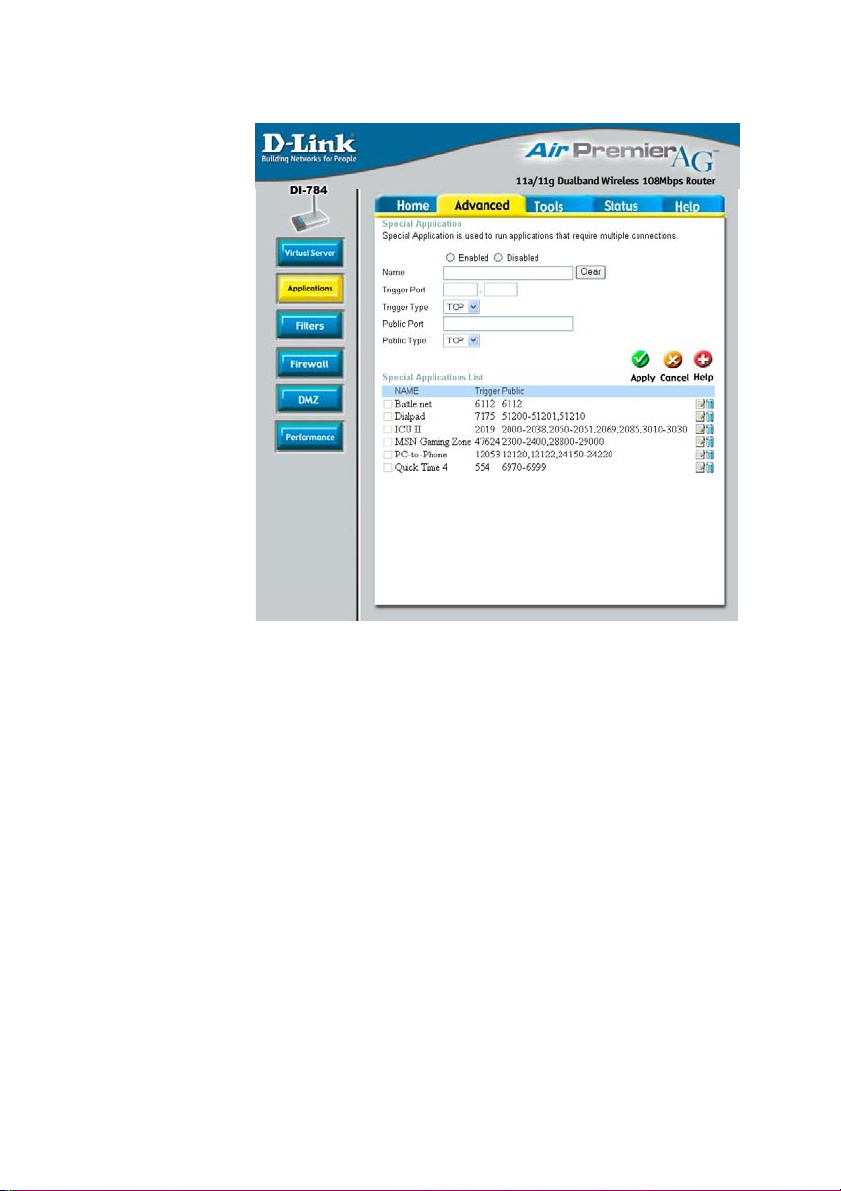
Using the Configuration Menu (continued)
Advanced > Applications
Some applications require multiple connections, such as Internet gaming, video
conferencing, Internet telephony and others. These applications have difficulties
working through NAT (Network Address Translation). Special Applications makes
some of these applications work with the DI-784. If you need to run applications that
require multiple connections, specify the port normally associated with an application
in the “Trigger Port” field, select the protocol type as TCP or UDP, then enter the
public ports associated with the trigger port to open them for inbound traffic.
The DI-784 provides some predefined applications in the table on the bottom of the
web page. Select the application you want to use and enable it.
Note! Only one PC can use each Special Application tunnel.
Name:
Trigger Port:
This is the name referencing the special application.
This is the port used to trigger the application. It can be either
a single port or a range of ports.
Trigger Type: This is the protocol used to trigger the special application.
Public Port:
This is the port number on the WAN side that will be used to
access the application. You may define a single port or a
range of ports. You can use a comma to add multiple ports or
port ranges.
Public Type: This is the protocol used for the special application.
24
Page 25
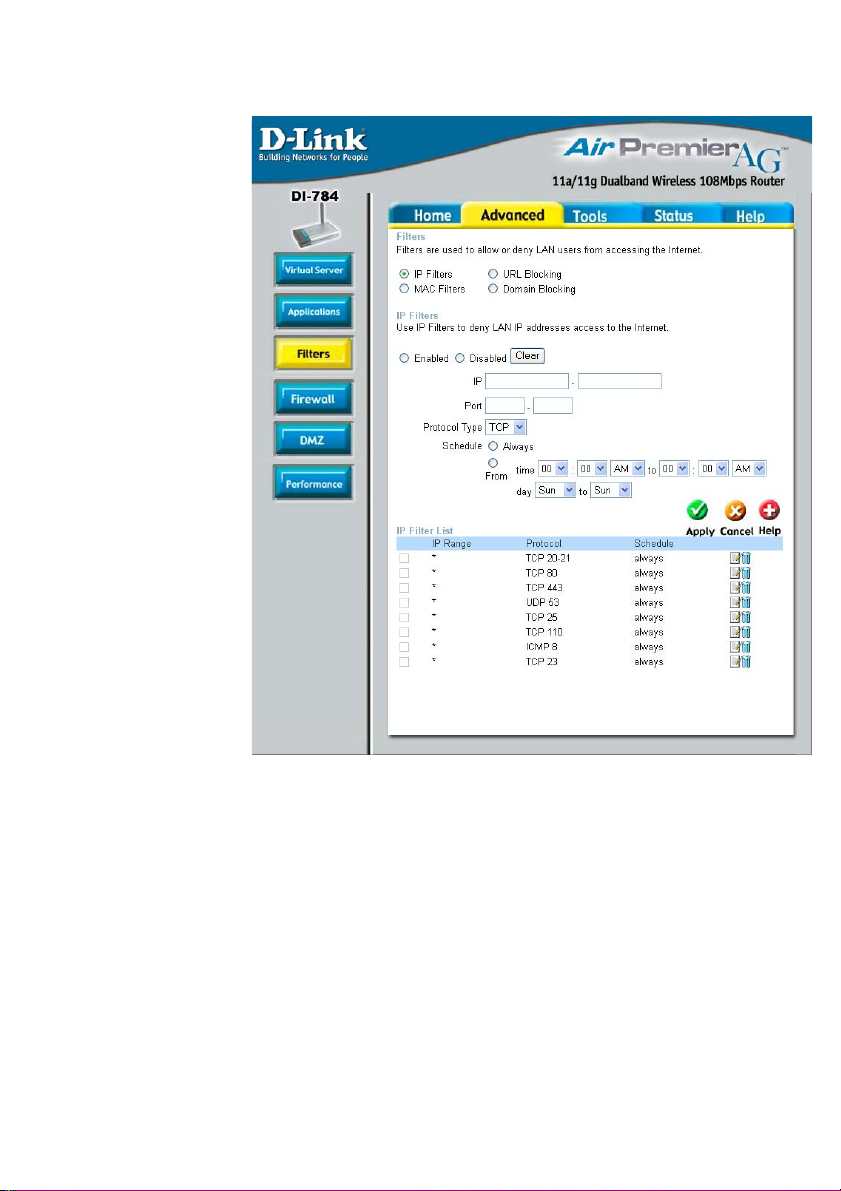
Using the Configuration Menu (continued)
Advanced > Filters > IP Filters
Filters are used to deny or allow LAN (Local Area Network) computers from accessing
the Internet. The DI-784 can be setup to deny internal computers by their IP or MAC
addresses. The DI-784 can also block users from accessing restricted web sites.
IP Filters-
IP-
Port-
Protocol Types-
Schedule-
Use IP Filters to deny LAN IP Addresses from accessing the
Internet. You can deny specific port numbers or all ports for
the specific IP Address.
The IP Address of the LAN computer that will be denied
access to the Internet.
The single port or port range that will be denied access to the
Internet.
Select the protocol type.
This is the schedule of time when the IP Filter will be enabled.
25
Page 26
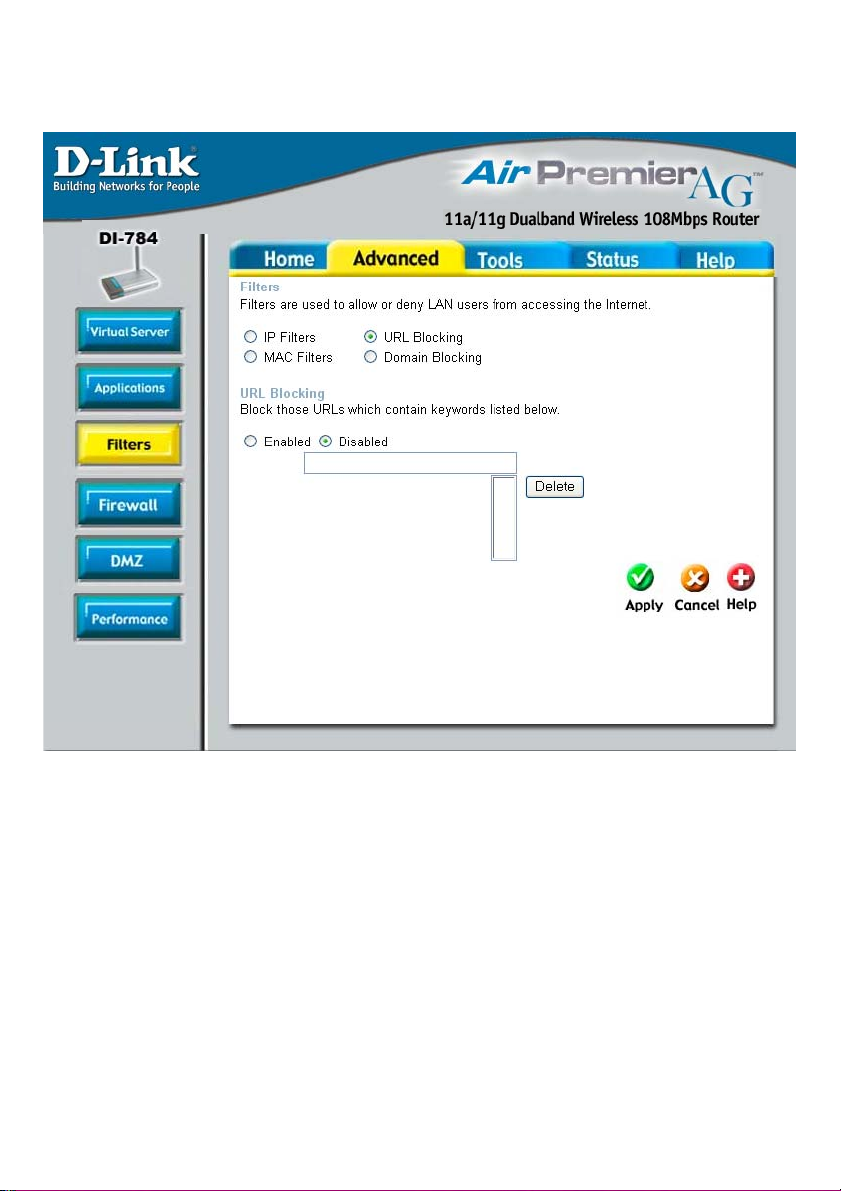
Using the Configuration Menu
Advanced > Filters > URL Blocking
URL Blocking is used to deny LAN computers from accessing specific web sites. A
URL is a specially formatted text string that defines a location on the Internet. If any
part of the URL contains the blocked word, the site will not be accessible and the web
page will not display.
Filters-
URL Blocking-
Keywords-
Select the filter you wish to use; in this case, URL Blocking
was chosen.
Select Enabled or Disabled.
Block URLs which contain the keywords listed below.
Enter the keywords in this space.
26
Page 27
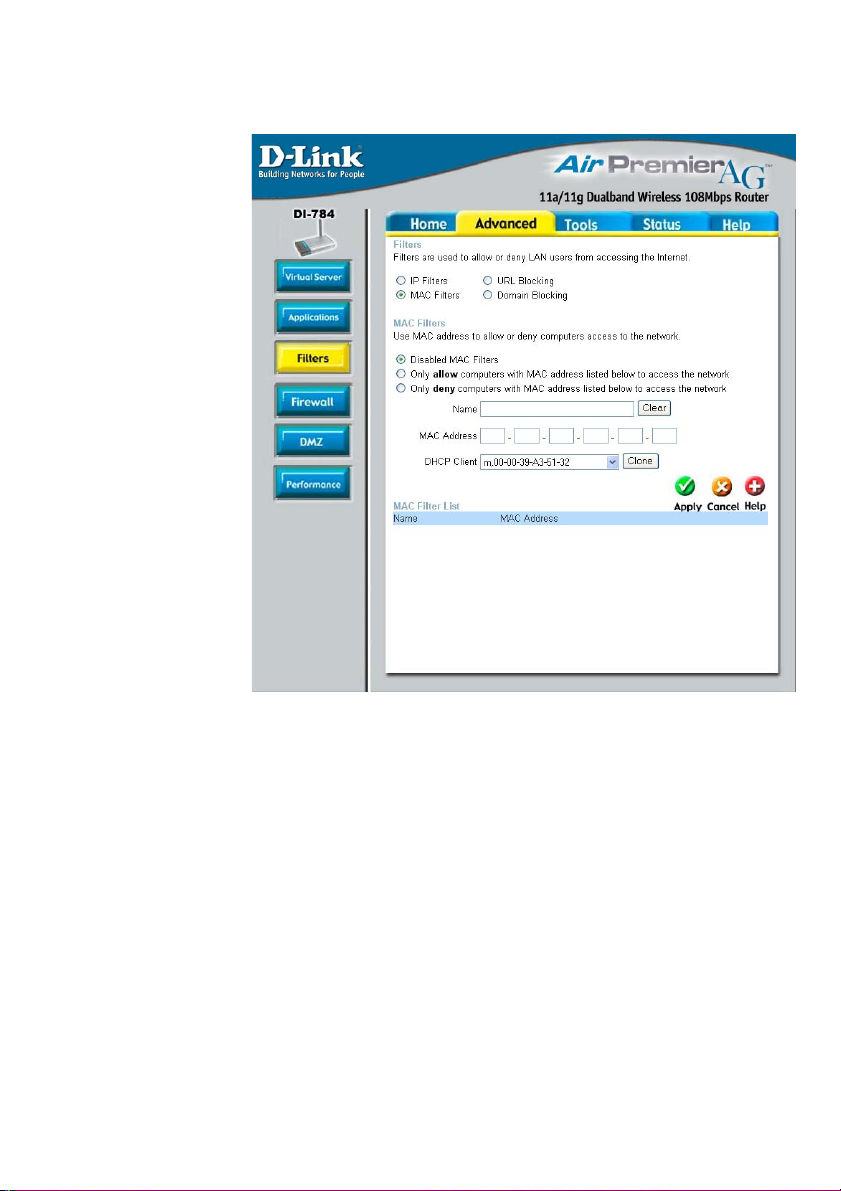
Using the Configuration Menu
Advanced > Filters > MAC Filters
Use MAC (Media Access Control) Filters to allow or deny LAN (Local Area Network)
computers by their MAC addresses from accessing the Internet. You can either
manually add a MAC address or select the MAC address from the list of clients that
are currently connected to the Broadband Router.
Filters-
MAC Filters-
Name-
MAC Address-
DHCP Client-
Select the filter you wish to use; in this case, MAC filters was
chosen.
Choose to Disable MAC filters, or choose to allow or deny
MAC addresses listed below.
Enter the name here.
Enter the MAC Address of the client that will be allowed or denied access.
Select a DHCP client from the pull-down list; click Clone to
copy that MAC Address.
27
Page 28
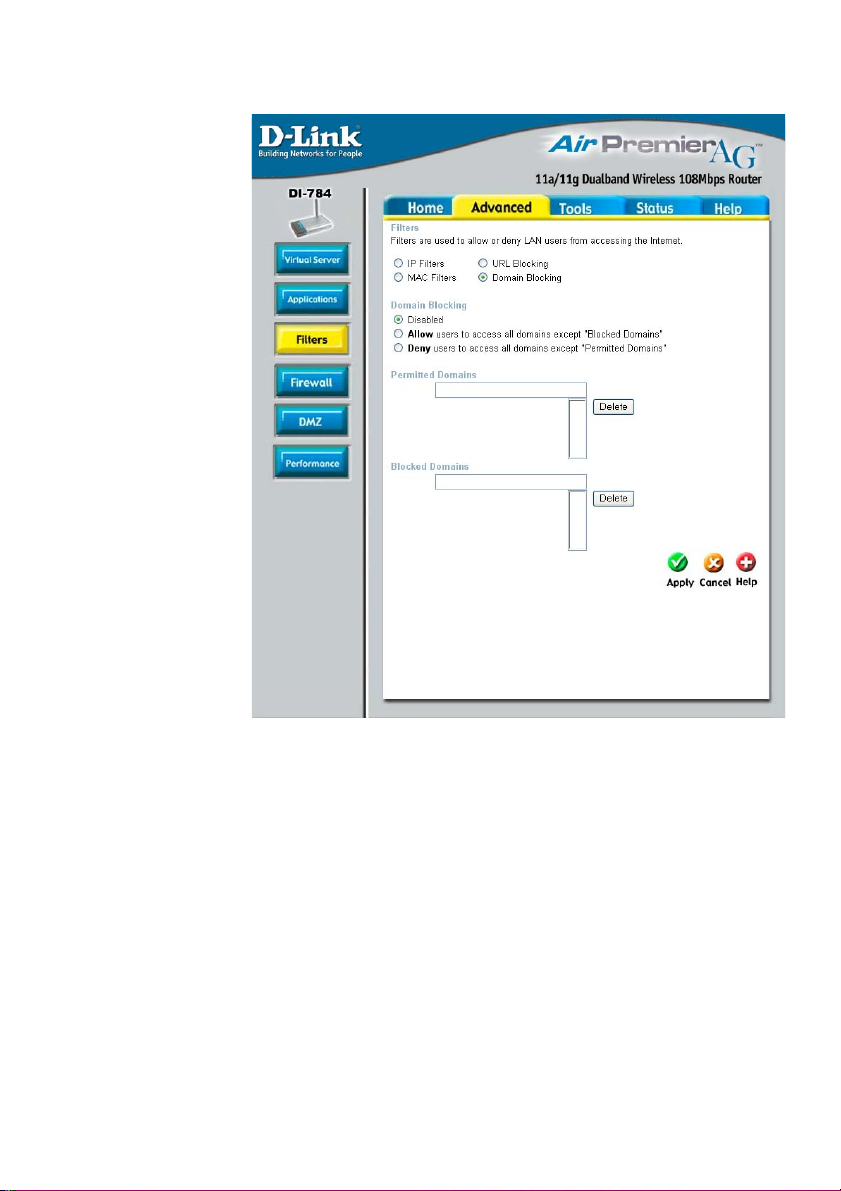
Using the Configuration Menu (continued)
Advanced > Filters > Domain Blocking
Domain Blocking is used to allow or deny LAN (Local Area Network) computers from
accessing specific domains on the Internet. Domain blocking will deny all requests to a
specific domain such as http and ftp. It can also allow computers to access specific
sites and deny all other sites.
Filters-
Select the filter you wish to use; in this case, Domain Blocking
was chosen.
Domain Blocking
Disabled-
Allow-
Deny-
Select Disabled to disable Domain Blocking.
Allows users to access all domains except Blocked Domains.
Denies users access to all domains except Permitted Domains.
Permitted
Domains-
Blocked Domains-
Enter the Permitted Domains in this field.
Enter the Blocked Domains in this field.
28
Page 29
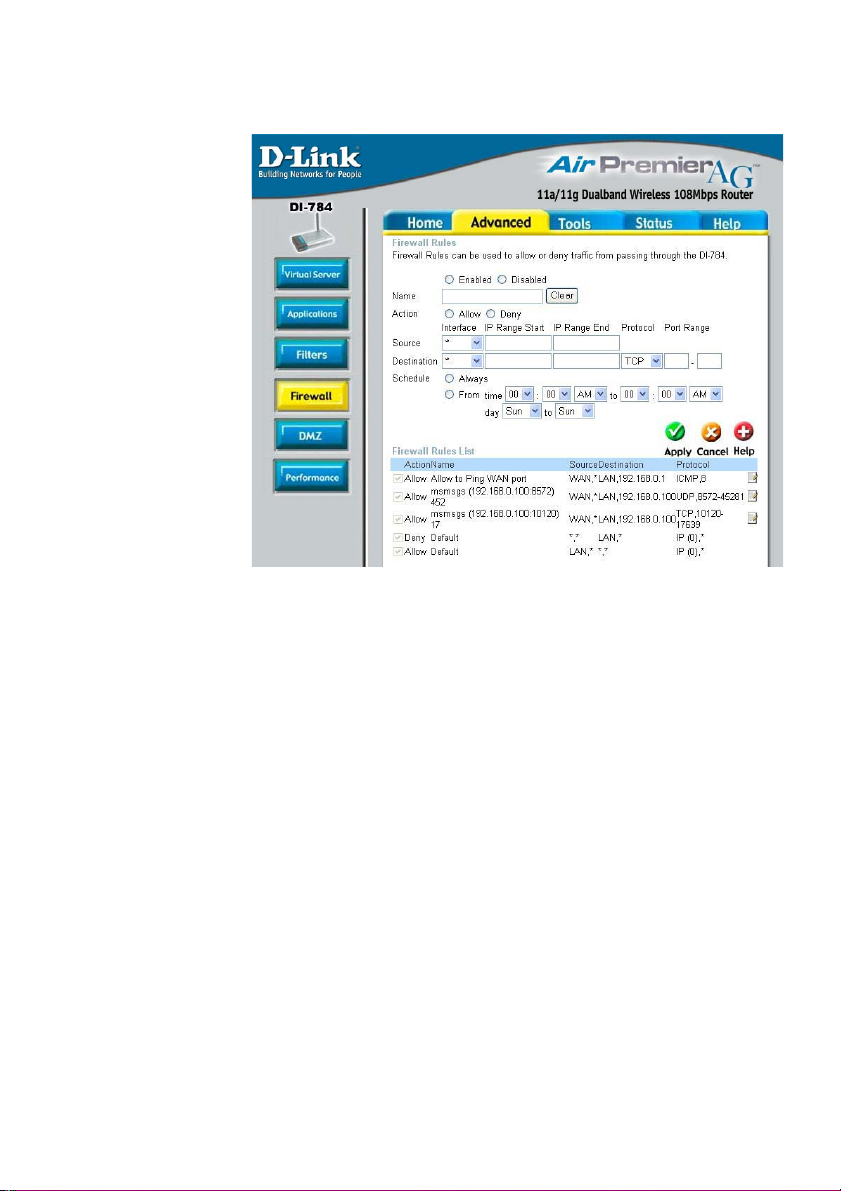
Using the Configuration Menu (continued)
Advanced > Firewall
Firewall Rules is an advanced feature used to deny or allow traffic from passing
through the DI-784. It works in the same way as IP Filters with additional settings.
You can create more detailed access rules for the DI-784. When virtual services are
created and enabled, it will also display in Firewall Rules. Firewall Rules contains all
network firewall rules pertaining to IP (Internet Protocol).
In the Firewall Rules List at the bottom of the screen, the priorities of the rules are
from top (highest priority) to bottom (lowest priority.)
Note: The DI-784 MAC Address filtering rules have precedence over the Firewall
Rules.
Firewall Rules-
Name-
Action-
Source-
Destination-
Schedule-
Enable or disable the Firewall Rules.
Enter a name for the rule.
Allow or deny IP traffic through the router.
Enter the IP Address range.
Enter the IP Address range, the Protocol,
and the Port Range.
Select Always or enter the Time.
29
Page 30
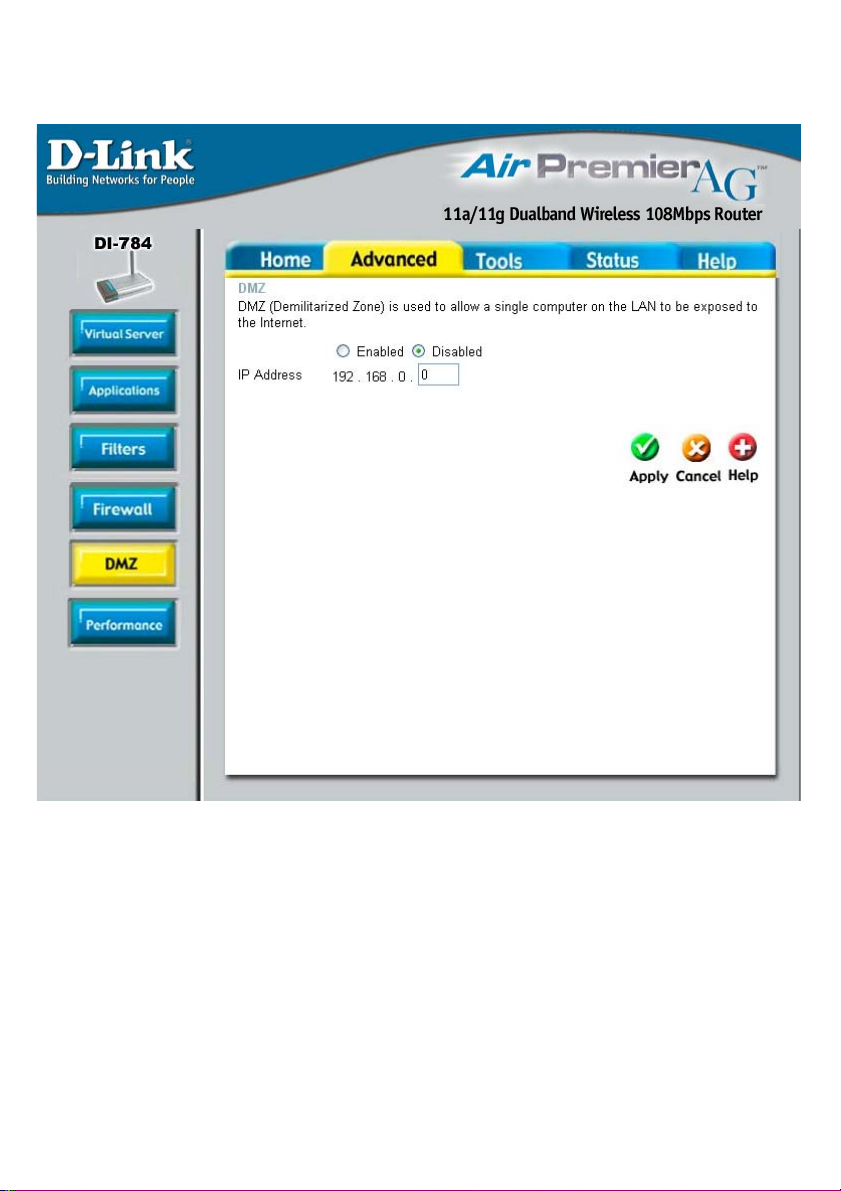
Using the Configuration Menu (continued)
Advanced > DMZ
If you have a client PC that cannot run Internet applications properly from behind the
DI-784, then you can set the client up to unrestricted Internet access. It allows a
computer to be exposed to the Internet. This feature is useful for gaming purposes.
Enter the IP Address of the internal computer that will be the DMZ host. Adding a
client to the DMZ (Demilitarized Zone) may expose your local network to a variety of
security risks, so only use this option as a last resort.
DMZ-
IP Address-
Enable or disable the DMZ. The DMZ (Demilitarized Zone)
allows a single computer to be exposed to the Internet.
Enter the IP Address of the computer to be in the DMZ.
30
Page 31

Using the Configuration Menu (continued)
Advanced > Performance > 802.11a
Wireless
Performance-
Select 802.11a or 802.11g.
Here, 802.11a has been
chosen. This screen displays
the wireless performance
features of the Access Point
portion of the DI-784.
Data Rate-
Auto is the default selection.
Select from the drop down menu
for your selection.
Transmit Power-
Beacon interval-
RTS Threshold-
Fragmentation-
DTIM interval-
Authentication-
Open System -
Shared Key -
SSID Broadcast-
Full is the default selection. Select from the drop down menu for
your selection.
Beacons are packets sent by the DI-784 to synchronize a wireless network. Specify a value. 100 is the default setting and is
recommended.
This value should remain at its default setting of 2346. If inconsistent data flow is a problem, only a minor modification should
be made.
This value should also remain at its default setting of 2346. If you
experience a high packet error rate, you may slightly increase
your Fragmentation value within the range of 256-2346. Setting
the Fragmentation value too low may result in poor performance.
(Delivery Traffic Indication Message) 1 is the default setting. A
DTIM is a countdown informing clients of the next window for
listening to broadcast and multicast messages.
Select Open system or Shared Key
The DI-784 will be visible to all devices on the network. This is
the default setting
In this mode, in order to access the DI-784 on the network, the
device must be listed in the MAC Address Control List
Choose Enabled to broadcast the SSID across the network.
All devices on a network must share the same SSID (Service
Set Identifier) to establish communication. Choose Disabled
if you do not wish to broadcast the SSID over the network.
31
Page 32

Using the Configuration Menu (continued)
Advanced > Performance > 802.11a (Continued)
Super A Mode-
Disabled-
Super A without
Turbo-
Super A with
Dynamic Turbo-
Super A with
Static Turbo-
Wireless
Super A is a group of performance enhancement features that
increase end user application throughput in an 802.11a network.
Super A is backwarsd compatible to standard 802.11a devices.
For top performance, all wirelss devices on the network should
be super A capable. Select either Disabled, Super A without Turbo,
Super A with Dynamic Turbo, or Super A with Static Turbo.
Standard 802.11a support, no enhanced capabilities.
Capable of Packet Bursting, FastFrames, Compression, and no
Turbo mode.
Capable of Packet Bursting, FastFrames, Compression, and
Dynamic Turbo. This setting is backwards compatible with nonTurbo (legacy) devices. Dynamic Turbo mode is only enabled
when all nodes on the wireless network is Super A with Dynamic
Turbo enabled.
Capable of Packet Bursting, FastFrames, Compression, and
Static Turbo. This setting is not backwards compatible with nonTurbo (legacy) devices. Static turbo mode is always on and is
only enabled when all nodes on the wireless network is Super A
with Static Turbo enabled.
Advanced > Performance > 802.11g
Performance-
Select 802.11a or 802.11g.
802.11g is selected here. Dis-
played in this window are the
Wireless Performance features for the Access Point portion of the DI-784.
TX Rates-
Auto is the default selec-
tion. Select from the drop
down menu for your selection.
Transmit Power-
Beacon interval-
Beacons are packets sent by the DI-784 to synchronize a wireless network. Specify a value. 100 is the default setting and is
recommended.
Full is the default selection. Select from the drop down menu for
your selection.
32
Page 33

Using the Configuration Menu (continued)
Advanced > Performance > 802.11g (Continued)
RTS Threshold-
Fragmentation-
DTIM interval-
Open System - The DI-784 will be visible to all devices on the network. This is
Shared Key -
SSID Broadcast-
Super G Mode-
This value should remain at its default setting of 2346. If inconsistent data flow is a problem, only a minor modification should
be made.
This value should also remain at its default setting of 2346. If you
experience a high packet error rate, you may slightly increase
your Fragmentation value within the range of 256-2346. Setting
the Fragmentation value too low may result in poor performance.
(Delivery Traffic Indication Message) 1 is the default setting. A
DTIM is a countdown informing clients of the next window for
listening to broadcast and multicast messages.
Select Open system or Shared KeyAuthentication-
the default setting
In this mode, in order to access the DI-784 on the network, the
device must be listed in the MAC Address Control List
Choose Enabled to broadcast the SSID across the network.
All devices on a network must share the same SSID (Service
Set Identifier) to establish communication. Choose Disabled
if you do not wish to broadcast the SSID over the network.
Super G is a group of performance enhancement features that
increase end user application throughput in an 802.11g network.
Super G is backwarsd compatible to standard 802.11g devices.
For top performance, all wirelss devices on the network should
be Super G capable. Select either Disabled, Super G without
Turbo, Super G with Dynamic Turbo, or Super G with Static Turbo.
Disabled-
Super G without
Turbo-
Super G with
Dynamic Turbo-
Super G with
Static Turbo-
Standard 802.11g support, no enhanced capabilities.
Capable of Packet Bursting, FastFrames, Compression, and no
Turbo mode.
Capable of Packet Bursting, FastFrames, Compression, and
Dynamic Turbo. This setting is backwards compatible with nonTurbo (legacy) devices. Dynamic Turbo mode is only enabled
when all nodes on the wireless network is Super G with Dynamic Turbo enabled.
Capable of Packet Bursting, FastFrames, Compression, and
Static Turbo. This setting is not backwards compatible with nonTurbo (legacy) devices. Static turbo mode is always on and is
only enabled when all nodes on the wireless network is Super G
with Static Turbo enabled.
33
Page 34

Using the Configuration Menu (continued)
Advanced > Performance > 802.11g (continued)
CTS Mode-
802.11g only mode-
CTS (Clear To Send) is a function used to minimize collisions
among wireless devices on a wireless local area network (LAN).
CTS will make sure the wireless network is clear before a wireless client attempts to send wireless data. Enabling CTS will
add overhead and may lower wireless throughput.
None- CTS is typically used in a pure 802.11g environment.
If CTS is set to “None” in a mixed mode environment
populated by 802.11b clients, wireless collisions may
occur frequently.
Always-
Auto-
Select this mode to restrict your network to only those devices
that employ the 802.11g standard. Enabling this mode will ensure that you maintain the highest connectivity rate, unhampered
by any connection to an 802.11b device.
CTS will always be used to make sure the wireless
LAN is clear before sending data.
CTS will monitor the wireless network and automatically decide whether to implement CTS based on
the amount of traffic and collisions that occurs on
the wireless network.
Tools> Admin
Administrator
Login Name-
user (lower case) is the default login name
for the user account. The user account has
read-only access to the router.
User
Login Name-
admin (lower case) is the default login
name for the admin account. The admin
account has read/write access to the
router.
Admin Password-
User Password-
The default setting is blank - no password. To change the pass-
word, enter and confirm the new password.
The default setting is blank - no password. To change the pass-
word, enter and confirm the new password.
34
Page 35

Using the Configuration Menu (continued)
Tools> Admin (continued)
Remote Management
Remote Management allows the DI-784 to be configured from the Internet by a web
browser. A username and password is still required to access the Web-Management
interface. In general, only a member of your network can browse the built-in web pages
to perform “Administrator” tasks. This feature enables you to perform “Administrator”
tasks from the remote (Internet) host.
IP Address: Internet IP Address of the computer that has access to the Router. It is not
recommended that you set the IP Address to * (star), because this allows any Internet
IP Address to access the Router, which could result in a loss of security for your network.
If you elect to enable Remote Management, make sure to enter the IP Address of the
remote computer allowed to configure the DI-784.
Port: For security purposes, select a separate port number used to access the Router.
(The following is an example only; you may use a different port number.)
Example: http://x.x.x.x:8080 where x.x.x.x is the WAN IP Address of the Router and
8080 is the port used for the Web-Management interface.
Tools > Time
Time settings-
Default
NTP Server-
In this window you can choose the time zone; set the time;
and enable or disable Daylight Savings Time.
NTP is short for Network Time Protocol. NTP synchronizes computer clock times in a network of computers.
This field is optional.
35
Page 36

Using the Configuration Menu (continued)
Tools > System
System Settings
Save Settings to
Local Hard Drive-
Load Settings from
Local Hard Drive-
Restore to Factory
Default Settings-
Click Save to save the current settings to the local Hard Drive.
Click Browse to find the settings, then click Load.
Click Restore to restore the factory default settings.
36
Page 37

Using the Configuration Menu (continued)
Tools > Firmware
Firmware
Upgrade-
Browse-
Click on the link in this screen to find out if there is an updated
firmware; if so, download the new firmware to your hard drive.
After you have downloaded the new firmware, click Browse in
this window to locate the firmware update on your hard drive.
Click Apply to complete the firmware upgrade.
37
Page 38

Using the Configuration Menu (continued)
Tools > Misc
DDNS-
Dynamic
Domain Name
System is a
method to
keep domain
names linked
to changing IP
Addresses. In
this way,
changing IP
Addresses
(e.g., via
DHCP) will not
interfere with
network
connectivity.
Ping Test-
Restart Device-
Block WAN Ping-
Discard Ping
from WAN side-
VPN
Pass Through-
DDNS-
The Ping Test is used to send Ping packets to test if a computer
is on the Internet. Enter the IP Address that you wish to Ping,
and click Ping.
Click Reboot to restart the DI-784.
If you choose to block WAN Ping, the WAN IP Address of the DI784 will not respond to pings. Blocking the Ping may provide
some extra security from hackers.
Click Enabled to block the WAN ping.
The DI-784 supports VPN (Virtual Private Network) pass-through
for both PPTP (Point-to-Point Tunneling Protocol) and IPSec (IP
Security). Once VPN pass-through is enabled, there is no need
to open up virtual services. Multiple VPN connections can be
made through the DI-784. This is useful when you have many
VPN clients on the LAN network.
PPTP- select Enabled or Disabled
IPSec- select Enabled or Disabled
Fill in the required fields to use the Dynamic Domain Name Service (DDNS) feature.
38
Page 39

Using the Configuration Menu (continued)
Tools > Cable Test
Cable Test
Cable Test
Cable Test is an advanced feature that integrates a LAN cable tester on every
Ethernet port on the router. Through the graphical user interface (GUI), Cable Test
can be used to remotely diagnose and report cable faults such as opens, shorts,
swaps, and impedance mismatch. This feature significantly reduces service calls and
returns by allowing users to easily troubleshoot their cable connections.
Ports – The Ethernet port names associated to the physical ports.
Link Status – The current link status of the Ethernet cable connected to the respective
Ethernet port.
More Info – Click on More Info for detailed information about the cable link status.
Refresh – Click on Refresh to run the Cable test. Allow the router a few seconds to
complete the test.
39
Page 40

Using the Configuration Menu (continued)
Status > Device Info
Device Information-
View Log-
Log Settings-
This screen displays information about the DI-784.
Status > Log
This screen displays the activity on the DI-784.
For advanced features, click on Log Settings.
40
Page 41

Using the Configuration Menu (continued)
Status > Log > Log Settings
SMTP Server/
IP Address-
Enter the proper SMTP Server information or the IP Address.
Email Address-
Log Type-
Enter the email address of the recipient who will receive the
email logs.
The administrator can specify which surveillance they want to
log. Check mark the box for specific activities.
41
Page 42

Using the Configuration Menu (continued)
Status > Stats
Traffic Statistics-
Connected
Wireless
Client List-
Displays the receive and transmit packets that are passing through
the DI-784. Click on Refresh, for the most recent information.
Click Reset to reset the counters back to zero.
Status > Wireless
Displays the wireless clients that are connected to the Access
Point function of the DI-784.
42
Page 43

Using the Configuration Menu (continued)
Help
Help-
Displays the complete Help menu. For help at anytime, click
the Help tab in the Configuration menu.
43
Page 44

Networking Basics
Using the Network Setup Wizard in Windows XP
In this section you will learn how to establish a network at home or work, using
Microsoft Windows XP.
Note: Please refer to websites such as http://www.homenethelp.com
and http://www.microsoft.com/windows2000 for information about networking
computers using Windows 2000, ME or 98.
Go to Start>Control Panel>Network Connections
Select Set up a home or small office network
When this screen appears, Click Next.
44
Page 45

Networking Basics
Please follow all the instructions in this window:
Click Next
In the following window, select the best description of your computer. If your
computer connects to the internet through a gateway/router, select the second option
as shown.
Click Next
45
Page 46

Networking Basics
Enter a Computer description and a Computer name (optional.)
Click Next
Enter a Workgroup name. All computers on your network should have the same
Workgroup name.
Click Next
46
Page 47

Networking Basics
Please wait while the Network Setup Wizard applies the changes.
When the changes are complete, click Next.
Please wait while the Network Setup Wizard configures the computer.
This may take a few minutes.
47
Page 48

Networking Basics
In the window below, select the option that fits your needs. In this example, Create a
Network Setup Disk has been selected. You will run this disk on each of the
computers on your network. Click Next.
Insert a disk into the Floppy Disk drive, in this case drive A.
Format the disk if you wish, and click Next.
48
Page 49

Networking Basics
Please wait while the Network Setup Wizard copies the files.
Please read the information under Here’s how in the screen below. After you complete the Network Setup Wizard you will use the Network Setup Disk to run the
Network Setup Wizard once on each of the computers on your network. To continue
click Next.
49
Page 50

Networking Basics
Please read the information on this screen, then click Finish to complete the
Network Setup Wizard.
The new settings will take effect when you restart the computer. Click Yes to restart
the computer.
You have completed configuring this computer. Next, you will need to run the Network
Setup Disk on all the other computers on your network. After running the Network
Setup Disk on all your computers, your new wireless network will be ready to use.
50
Page 51

Networking Basics
Naming your Computer
To name your computer, please follow these directions:In Windows XP:
Click Start (in the lower left corner of the screen)
Right-click on My Computer
Select Properties and click
Select the Computer
Name Tab in the System
Properties window.
You may enter a Computer Description if you
wish; this field is optional.
To rename the computer
and join a domain, Click
Change.
51
Page 52

Networking Basics
Naming your Computer
In this window, enter the
Computer name
Select Workgroup and enter
the name of the Workgroup
All computers on your network
must have the same
Workgroup name.
Click OK
Checking the IP Address in Windows XP
The wireless adapter-equipped computers in your network must be in the same IP Address range (see Getting Started in this manual for a definition of IP Address Range.) To
check on the IP Address of the adapter, please do the following:
Right-click on the
Local Area
Connection icon
in the task bar
Click on Status
52
Page 53

Networking Basics
Checking the IP Address in Windows XP
This window will appear.
Click the
Support tab
Click Close
Assigning a Static IP Address in Windows XP/2000
Note: Residential Gateways/Broadband Routers will automatically assign IP Addresses to the computers on the network, using DHCP (Dynamic Host Configuration Protocol) technology. If you are using a DHCP-capable Gateway/Router you
will not need to assign Static IP Addresses.
If you are not using a DHCP capable Gateway/Router, or you need to assign a Static IP
Address, please follow these instructions:
Go to Start
Double-click on
Control Panel
53
Page 54

Networking Basics
Assigning a Static IP Address in Windows XP/2000
Double-click on
Network
Connections
Right-click on Local Area
Connections
Double-click on
Properties
54
Page 55

Networking Basics
Assigning a Static IP Address
in Windows XP/2000
Click on Internet Protocol
(TCP/IP)
Click Properties
Select Use the following
IP address in the Internet
Protocol (TCP/IP)
Properties window (shown
below)
Input your IP address and
subnet mask. (The IP
Addresses on your network
must be within the same
range. For example, if one
computer has an IP Address
of 192.168.0.2, the other
computers should have IP
Addresses that are
sequential, like 192.168.0.3
and 192.168.0.4. The
subnet mask must be the
same for all the computers
on the network.
Enter the IP Address
of the Default
Gateway (in this case
it is 192.168.0.1 for
the DI-784)
Input your DNS server
address.
The DNS server address will be supplied by your ISP (Internet Service Provider).
If the DNS Server address is not available from your ISP, you may input 192.168.0.1
in this field.
Click OK
192 168 0 1
55
Page 56

Networking Basics
Assigning a Static IP Address with Macintosh OSX
Go to the Apple Menu and se-
lect System Preferences
cClick on Network
Select Built-in Ethernet in the
Show pull-down menu
Select Manually in the
Configure pull-down menu
Input the Static IP Address,
the Subnet Mask and the
Router IP Address in the
appropriate fields
Input the Domain Name
Server address. Your ISP
(Internet Service Provider)
will provide the IP address of
the DNS Server. If the DNS
Server address is not available from your ISP, you may
input 192.168.0.1 in this field.
Click Apply Now
56
Page 57

Networking Basics
Selecting a Dynamic IP Address with Macintosh OSX
Go to the Apple Menu and select
System Preferences
Click on Network
Select Built-in Ethernet in the
Show pull-down menu
Select Using DHCP in the
Configure pull-down menu
Click Apply Now
The IP Address, Subnet
mask, and the Router’s IP
Address will appear in a few
seconds
57
Page 58

Networking Basics
Checking the Wireless Connection by Pinging in Windows XP and
2000
Go to Start > Run >
type cmd. A window
similar to this one
will appear. Type
ping
xxx.xxx.xxx.xxx,
where xxx is the IP
Address of the
Wireless Router or
Access Point. A
good wireless
connection will show
four replies from the
Wireless Router or
Acess Point, as
shown.
Checking the Wireless Connection by Pinging in Windows Me
and 98
Go to Start > Run
> type command.
A window similar to
this will appear.
Type ping
xxx.xxx.xxx.xxx
where xxx is the IP
Address of the
Wireless Router or
Access Point. A
good wireless
connection will
show four replies
from the wireless
router or access
point, as shown.
58
Page 59

Troubleshooting
This Chapter provides solutions to problems that can occur during the installation and
operation of the DI-784 Wireless Broadband Router. We cover various aspects of the
network setup, including the network adapters. Please read the following if you are having
problems.
Note: It is recommended that you use an Ethernet connection to
configure the DI-784 Wireless Broadband Router.
1.The computer used to configure the DI-784 cannot access the
Configuration menu.
Check that the Ethernet LED on the DI-784 is ON. If the LED is not
ON, check that the cable for the Ethernet connection is securely
inserted.
Check that the Ethernet Adapter is working properly. Please see
item 3 (Check that the drivers for the network adapters are
installed properly) in this Troubleshooting section to check that
the drivers are loaded properly.
Check that the IP Address is in the same range and subnet as the
DI-784. Please see Checking the IP Address in Windows XP in the
Networking Basics section of this manual.
Note: The IP Address of the DI-784 is 192.168.0.1. All the computers on the
network must have a unique IP Address in the same range, e.g., 192.168.0.x.
Any computers that have identical IP Addresses will not be visible on the
network. They must all have the same subnet mask, e.g., 255.255.255.0
Do a Ping test to make sure that the DI-784 is responding. Go to
Start>Run>Type Command>Type ping 192.168.0.1. A successful
ping will show four replies.
Note: If you have changed
the default IP Address,
make sure to ping the correct IP Address assigned
to the DI-784.
59
Page 60

Troubleshooting
2. The wireless client cannot access the Internet in the
Infrastructure mode.
Make sure the wireless client is associated and joined with the correct Access
Point. To check this connection: Right-click on the Local Area Connection icon
in the taskbar> select View Available Wireless Networks. The Connect to
Wireless Network screen will appear. Please make sure you have selected the
correct available network, as shown in the illustrations below.
default
Check that the IP Address assigned to the wireless adapter is within the
same IP Address range as the access point and gateway. (Since the DI-
784 has an IP Address of 192.168.0.1, wireless adapters must have an
IP Address in the same range, e.g., 192.168.0.x. Each device must have
a unique IP Address; no two devices may have the same IP Address.
The subnet mask must be the same for all the computers on the
network.) To check the IP Address assigned to the wireless adapter,
double-click on the Local Area Connection icon in the taskbar >
select the Support tab and the IP Address will be displayed. (Please
refer to Checking the IP Address in the Networking Basics section of
this manual.)
If it is necessary to assign a Static IP Address to the wireless adapter,
please refer to the appropriate section in Networking Basics. If you are
entering a DNS Server address you must also enter the Default
Gateway Address. (Remember that if you have a DHCP-capable router,
you will not need to assign a Static IP Address. See Networking
Basics: Assigning a Static IP Address.)
60
Page 61

Troubleshooting
3. Check that the drivers for the network adapters are
installed properly.
You may be using different network adapters than those illustrated here, but this
procedure will remain the same, regardless of the type of network adapters you are
using.
Select the
Hardware
Tab
Click Device
Manager
61
Page 62

Troubleshooting
Double-click
on Network
Adapters
Right-click on D-Link
AirPro DWL-A650
Wireless Cardbus
Adapter (In this example,
the DWL-A650 is used;
you may be using another
network adapter, but the
procedure will remain the
same.)
Select Properties
to check that the
drivers are
installed properly
Look under Device
Status to check that the
device is working
properly
Click OK
62
Page 63

Troubleshooting
4. What variables may cause my wireless products to lose reception?
D-Link products let you access your network from virtually anywhere you want. However,
the positioning of the products within your environment will affect the wireless range.
Please refer to Installation Considerations in the Wireless Basics section of this manual
for further information about the most advantageous placement of your D-Link wireless
products.
5. Why does my wireless connection keep dropping?
Antenna Orientation- Try different antenna orientations for the DI-784. Try to
keep the antenna at least 6 inches away from the wall or other objects.
If you are using 2.4GHz cordless phones, X-10 equipment or other home secu-
rity systems, ceiling fans, and lights, your wireless connection will degrade dramatically or drop altogether. Try changing the Channel on your Router, Access
Point and Wireless adapter to a different Channel to avoid interference.
Keep your product away (at least 3-6 feet) from electrical devices that generate
RF noise, like microwaves, Monitors, electric motors, etc.
6. Why can’t I get a wireless connection?
To establish a wireless connection, while enabling Encryption on the DI-784, you must
also enable encryption on the wireless client.
For 802.11a, the Encryption settings are: 64, 128 or 152 bit. Make sure that the
encryption bit level is the same on the Router and the Wireless Client.
For 802.11g, the Encryption settings are: 64, 128, or 152 bit. Make sure that the
encryption bit level is the same on the Router and the Wireless Client.
Make sure that the SSID on the Router and the Wireless Client are exactly the same. If
they are not, wireless connection will not be established. Please note that there are two
separate SSIDs for 802.11a and 802.11g. The default SSID for both 802.11a and 802.11g
is default.
63
Page 64

Troubleshooting
7. Resetting the DI-784 to Factory Default Settings
After you have tried other methods for troubleshooting your network, you may
choose to Reset the DI-784 to the factory default settings. Remember that D-Link
Air Premier AG products network together, out of the box, at the factory default
settings.
To hard-reset the D-Link Air Premier AG DI-784 to Factory Default Settings, please do
the following:
Locate the Reset button on the back of the DI-784.
Use a paper clip to press the Reset button.
Hold for about 10 seconds and then release.
After the DI-784 reboots (this may take a few minutes) it will
be reset to the factory Default settings.
64
Page 65

Technical Specifications
Standards:
IEEE 802.11g
IEEE 802.11b
IEEE 802.11a
IEEE 802.3 and IEEE 802.3u
VPN Pass Through/Multi-Sessions:
PPTP
L2TP
IPSec
Advanced Firewall Features:
Supports NAT with VPN pass-through, for added security
MAC Filtering
IP Filtering
URL Filtering
Domain Blocking
Scheduling
Device Management:
Web-based -Internet Explorer v6 or later; Netscape Navigator
v6 or later; or other Java-enabled browsers
DHCP Server and Client
Wireless Data Rates with Automatic Fallback:
54Mbps
36Mbps
24Mbps
18Mbps
12Mbps
11Mbps
9Mbps
6Mbps
5.5Mbps
2Mbps
1Mbps
D-Link 108 AG 108Mbps
48Mbps
65
Page 66

Technical Specifications (continued)
Security:
64-, 128-, 152-WEP
WPA -Wi-Fi Protected Access (WEP with TKIP, MIC, IV
Expansion, Shared Key Authentication)
Media Access Control:
CSMA/CA with ACK
Wireless Frequency Range:
2.400GHz to 2.500GHz
5.150GHz to 5.850GHz
Wireless Operating Range:
Indoors: Up to 328 feet (100 meters)
Modulation Technology:
Orthogonal Frequency Division Multiplexing (OFDM)
Complementary Code Keying (CCK)
Receiver Sensitivity:
54Mbps OFDM, 10% PER,-73dBm
48Mbps OFDM, 10% PER,-76dBm
36Mbps OFDM, 10% PER,-82dBm
24Mbps OFDM, 10% PER,-85dBm
18Mbps OFDM, 10% PER,-88dBm
12Mbps OFDM, 10% PER,-89dBm
11Mbps CCK, 8% PER,-91dBm
9Mbps OFDM, 10% PER,-90dBm
6Mbps OFDM, 10% PER,-91dBm
5.5Mbps CCK, 8% PER,-92dBm
2Mbps QPSK, 8% PER,-93dBm
1Mbps BPSK, 8% PER,-94dBm
66
Page 67

Technical Specifications (continued)
Wireless Transmit Power:
15dBm ± 2dB
LEDs:
Power
Status
WAN
WLAN (Wireless Connection) - 802.11a, 802.11g
Local Network (Ports 1-4)
External Antenna Type:
Single Non-Detachable Antenna
Operating Temperature:
32°F to 131°F (0°C to 55°C)
Humidity:
95% maximum (non-condensing)
Power Input:
Ext. Power Supply DC 5V, 3.0A
100-240V~50-60Hz
Safety and Emissions:
FCC
Dimensions:
L = 7.56 inches (192mm)
W = 4.65 inches (118mm)
H = 1.22 inches (31mm)
Weight:
10.8 oz. (0.3kg)
Warranty:
3 years
67
Page 68

Frequently Asked Questions
Why can´t I access the web based configuration?
When entering the IP Address of the DI-784 (192.168.0.1), you are not connecting to
the Internet or have to be connected to the Internet. The device has the utility built-in
to a ROM chip in the device itself. Your computer must be on the same IP subnet to
connect to the web-based utility.
To resolve difficulties accessing a web utility, please follow the steps below.
Step 1
you do not get a solid link light, try using a different cable or connect to a different
port on the device if possible. If the computer is turned off, the link light may not be
on.
Verify physical connectivity by checking for solid link lights on the device. If
What type of cable should I be using?
The following connections require a Crossover Cable:
Computer to Computer
Computer to Uplink Port
Computer to Access Point
Computer to Print Server
Computer/XBOX/PS2 to DWL-810
Computer/XBOX/PS2 to DWL-900AP+
Uplink Port to Uplink Port (hub/switch)
Normal Port to Normal Port (hub/switch)
The following connections require a Straight-through Cable:
Computer to Residential Gateway/Router
Computer to Normal Port (hub/switch)
Access Point to Normal Port (hub/switch)
Print Server to Normal Port (hub/switch)
Uplink Port to Normal Port (hub/switch)
Rule of Thumb:
”If there is a link light, the cable is right.”
68
Page 69

Frequently Asked Questions (continued)
Why can´t I access the web based configuration? (continued)
What type of cable should I be using? (continued)
What´s the difference between a crossover cable and a straight-through
cable?
The wiring in crossover and straight-through cables are different. The two types
of cable have different purposes for different
LAN configurations. EIA/TIA 568A/568B
define the wiring standards and allow for
two different wiring color codes as
illustrated in the following diagram.
*The wires with colored backgrounds may
have white stripes and may be denoted
that way in diagrams found elsewhere.
How to tell straight-through cable from
a crossover cable:
The main way to tell the difference
between the two cable types is to compare
the wiring order on the ends of the cable. If
the wiring is the same on both sides, it is
straight-through cable. If one side has opposite wiring, it is a crossover cable.
All you need to remember to properly configure the cables is the pinout order of
the two cable ends and the following rules:
A straight-through cable has identical ends
A crossover cable has different ends
It makes no functional difference which standard you follow for straight-through
cable ends, as long as both ends are the same. You can start a crossover cable
with either standard as long as the other end is the other standard. It makes no
functional difference which end is which. The order in which you pin the cable is
important. Using a pattern other than what is specified in the above diagram
could cause connection problems.
When to use a crossover cable and when to use a straight-through cable:
Computer to Computer – Crossover
Computer to an normal port on a Hub/Switch – Straight-through
Computer to an uplink port on a Hub/Switch - Crossover
Hub/Switch uplink port to another Hub/Switch uplink port – Crossover
Hub/Switch uplink port to another Hub/Switch normal port - Straight-through
69
Page 70

Frequently Asked Questions (continued)
Why can´t I access the web based configuration? (continued)
Step 2 Disable any internet security software running on the computer. Software
firewalls like Zone Alarm, Black Ice, Sygate, Norton Personal Firewall, etc. might
block access to the configuration pages. Check the help files included with your
firewall software for more information on disabling or configuring it.
Step 3 Configure you internet settings.
Go to Start>Settings>Control Panel. Double click
the Internet Options Icon. From the Security tab,
click the button to restore the settings to their
defaults.
Click to the Connection tab and set the dialup option to Never Dial a Connection. Click
the LAN Settings button.
Nothing should be checked. Click OK.
Go to the Advanced tab and click the
button to restore these settings to their
defaults.
Click OK. Go to the desktop and close any open
windows.
70
Page 71

Frequently Asked Questions (continued)
Why can´t I access the web based configuration? (continued)
Step 4 Check your IP Address. Your computer must have an IP Address in the same
range as the device you are attempting to configure. Most D-Link devices use the
192.168.0.X range.
How can I find my IP Address in Windows 95, 98, or
ME?
Step 1 Click on Start, then click on Run.
Step 2 The Run Dialogue Box will appear. Type winipcfg in the window as shown
then click OK.
Step 3 The IP Configuration window will appear, displaying your Ethernet
Adapter Information.
Select your adapter from the drop down menu.
If you do not see your adapter in the drop down menu, your adapter is
not properly installed.
Step 4 After selecting your adapter, it will display your IP Address, subnet
mask, and default gateway.
Step 5 Click OK to close the IP Configuration window.
71
Page 72

Frequently Asked Questions (continued)
Why can´t I access the web based configuration? (continued)
Step 4 (continued) Check your IP Address. Your computer must have an IP Address
in the same range of the device you are attempting to configure. Most D-Link devices
use the 192.168.0.X range.
How can I find my IP Address in Windows 2000/XP?
Step 1 Click on Start and select Run.
Step 2 Type cmd then click OK.
Step 3 From the Command Prompt, enter ipconfig. It will return your IP
Address, subnet mask, and default gateway.
Step 4 Type exit to close the command prompt.
72
Page 73

Frequently Asked Questions (continued)
Why can´t I access the web based configuration? (continued)
Step 4 (continued) Check your IP Address. Your computer must have an IP Address
in the same range of the device you are attempting to configure. Most D-Link devices
use the 192.168.0.X range.
How can I assign a Static IP Address in Windows XP?
Step 1
Click on Start > Control Panel > Network and Internet Connections >
Network connections.
Step 2 See Step 2 for Windows 2000 and continue from there.
How can I assign a Static IP Address in Windows 2000?
Step 1 Right-click on My Network
Places and select Properties.
Step 2 Right-click on the Local
Area Connection which represents
your network card and select
Properties.
Highlight Internet Protocol (TCP/
IP) and click Properties.
73
Page 74

Frequently Asked Questions (continued)
Why can´t I access the web based configuration? (continued)
How can I assign a Static IP Address in Windows 2000?
(continued)
Click Use the following IP Address and
enter an IP Address that is on the same
subnet as the LAN IP Address on your
router. Example: If the router´s LAN IP
Address is 192.168.0.1, make your IP
Address 192.168.0.X where X = 2-99.
Make sure that the number you choose is
not in use on the network.
Set the Default Gateway to be the
same as the LAN IP Address of your
router (192.168.0.1).
Set the Primary DNS to be the same as
the LAN IP Address of your router
(192.168.0.1).
The Secondary DNS is not needed or enter a DNS server from your ISP.
Click OK twice. You may be asked if you want to reboot your computer. Click
Yes .
How can I assign a Static IP
Address in Windows 98/Me?
Step 1 From the desktop, right-click on the
Network Neigborhood icon (Win ME - My
Network Places) and select Properties
Highlight TCP/IP and click the Properties
button. If you have more than 1 adapter,
then there will be a TCP/IP “Binding” for
each adapter. Highlight TCP/IP > (your
network adapter) and then click
Properties.
74
Page 75

Frequently Asked Questions (continued)
Why can´t I access the web based configuration? (continued)
How can I assign a Static IP Address in Windows
98/Me? (continued)
Step 2 Click Specify an IP Address.
Enter in an IP Address that is on the same
subnet as the LAN IP Address on your router.
Example: If the router´s LAN IP Address is
192.168.0.1, make your IP Address
192.168.0.X where X is between 2-99. Make
sure that the number you choose is not in
use on the network.
Step 3 Click on the Gateway tab.
Enter the LAN IP Address of your router
here (192.168.0.1).
Click Add when finished.
Step 4 Click on the DNS Configuration tab.
Click Enable DNS. Type in a Host (can be
any word). Under DNS server search order,
enter the LAN IP Address of your router
(192.168.0.1). Click Add.
Step 5 Click OK twice.
When prompted to reboot your computer,
click Yes.
After you reboot, the computer will now have
a static, private IP Address.
Step 5 Access the web management. Open your web
browser and enter the IP Address of your D-Link device in
the address bar. This should open the login page for the web
management. Follow instructions to login and complete the configuration.
75
Page 76

Frequently Asked Questions (continued)
How can I setup my router to work with a Cable modem connection?
Dynamic Cable connection
(IE ATnT-BI, Cox, Adelphia, Rogers, Roadrunner, Charter, and Comcast).
Note: Please configure the router with the computer that was last connected directly
to the cable modem.
Step 1 Log into the web based configuration by typing in the IP Address of the router
(default:192.168.0.1) in your web browser. The username is admin (all lowercase) and
the password is blank (nothing).
Step 2 Click the Home tab and click the
WAN button. Dynamic IP Address is the
default value, however, if Dynamic IP Address
is not selected as the WAN type, select
Dynamic IP Address by clicking on the radio
button. Click Clone Mac Address. Click on
Apply and then Continue to save the
changes.
DI-784
76
Page 77

Frequently Asked Questions (continued)
How can I setup my router to work with a Cable modem connection?
(continued)
Step 3 Power cycle the cable modem and router:
Turn the cable modem off (first) . Turn the router off Leave them off for 2 minutes.**
Turn the cable modem on (first). Wait until you get a solid cable light on the cable
modem. Turn the router on. Wait 30 seconds.
** If you have a Motorola (Surf Board) modem, leave off for at least 5 minutes.
Step 4 Follow step 1 again and log back into the web configuration. Click the Status
tab and click the Device Info button. If you do not already have a public IP Address
under the WAN heading, click on the DHCP Renew and Continue buttons.
Static Cable Connection
Step 1 Log into the web based configuration by
typing in the IP Address of the router
(default:192.168.0.1) in your web browser. The
username is admin (all lowercase) and the password
is blank (nothing).
Step 2 Click the Home tab and click the WAN
button. Select Static IP Address and enter your static
settings obtained from the ISP in
the fields provided.
DI-784
If you do not know your settings,
you must contact your ISP.
Step 3 Click on Apply and then
click Continue to save the
changes.
Step 4 Click the Status tab and
click the Device Info button. Your
IP Address information will be
displayed under the WAN heading.
77
Page 78

Frequently Asked Questions (continued)
How can I setup my router to work with Earthlink DSL or any PPPoE
connection?
Make sure you disable or uninstall any PPPoE software such as WinPoet or Enternet
300 from your computer or you will not be able to connect to the Internet.
Step 1 Upgrade Firmware if needed.
(Please visit the D-Link tech support website at: http://support.dlink.com for the latest
firmware upgrade information.)
Step 2 Take a paperclip and perform a hard reset. With the unit on, use a paperclip
and hold down the reset button on the back of the unit for 10 seconds. Release it and
the router will recycle, the lights will blink, and then stabilize.
Step 3 After the router stabilizes, open your browser and enter 192.168.0.1 into the
address window and hit the Enter key. When the password dialog box appears, enter
the username admin and leave the password blank. Click OK.
If the password dialog box does not come up repeat Step 2.
Note: Do not run Wizard.
Step 4 Click on the WAN tab on left-hand side of the screen. Select PPPoE.
Step 5 Select Dynamic PPPoE (unless your ISP supplied you with a static IP
Address).
Step 6 In the username field enter ELN/username@earthlink.net and your
password, where username is your own username.
For SBC Global users, enter username@sbcglobal.net.
For Ameritech users, enter username@ameritech.net.
For BellSouth users, enter username@bellsouth.net.
For Mindspring users, enter username@mindspring.com.
For most other ISPs, enter username.
Step 7 Maximum Idle Time should be set to zero. Set MTU to 1492, unless
specified by your ISP, and set Autoreconnect to Enabled.
Note: If you experience problems accessing certain websites and/or email issues,
please set the MTU to a lower number such as 1472, 1452, etc. Contact your ISP for
more information and the proper MTU setting for your connection.
78
Page 79

Frequently Asked Questions (continued)
How can I setup my router to work with Earthlink DSL or any PPPoE
connection? (continued)
Step 8 Click Apply. When prompted, click Continue. Once the screen refreshes,
unplug the power to the D-Link router.
Step 9 Turn off your DSL modem for 2-3 minutes. Turn back on. Once the modem
has established a link to your ISP, plug the power back into the D-Link router. Wait
about 30 seconds and log back into the router.
Step 10 Click on the Status tab in the web configuration where you can view the
device info. Under WAN , click Connect. Click Continue when prompted. You should
now see that the device info will show an IP Address, verifying that the device has
connected to a server and has been assigned an IP Address.
Can I use my D-Link Broadband Router to share my Internet
connection provided by AOL DSL Plus?
In most cases yes. AOL DSL+ may use PPPoE for authentication bypassing the
client software. If this is the case, then our routers will work with this service. Please
contact AOL if you are not sure.
To set up your router:
Step 1 Log into the web-based configuration (192.168.0.1) and configure the WAN
side to use PPPoE.
Step 2 Enter your screen name followed by @aol.com for the user name. Enter your
AOL password in the password box.
Step 3 You will have to set the MTU to 1400. AOL DSL does not allow for anything
higher than 1400.
Step 4 Apply settings.
Step 5 Recycle the power to the modem for 1 minute and then recycle power to the
router. Allow 1 to 2 minutes to connect.
If you connect to the Internet with a different internet service provider and want to use
the AOL software, you can do that without configuring the router’s firewall settings.
You need to configure the AOL software to connect using TCP/IP.
Go to http://www.aol.com for more specific configuration information of their software.
79
Page 80

Frequently Asked Questions (continued)
How do I open ports on my router?
To allow traffic from the internet to enter your local network, you will need to open up
ports or the router will block the request.
Step 1 Open your web browser
and enter the IP Address of
your D-Link router
(192.168.0.1). Enter username
(admin) and your password
(blank by default).
Step 2 Click on Advanced on
top and then click Virtual
Server on the left side.
Step 3 Check Enabled to
activate entry.
Step 4 Enter a name for your virtual server entry.
Step 5 Next to Private IP, enter the IP Address of the computer on your local
network that you want to allow the incoming service to.
Step 6 Choose Protocol Type - either TCP, UDP, or both. If you are not sure, select
both.
Step 7 Enter the port information next to Private Port and Public Port. The private
and public ports are usually the same. The public port is the port seen from the WAN
side, and the private port is the port being used by the application on the computer
within your local network.
Step 8 Enter the Schedule information.
Step 9 Click Apply and then click Continue.
Note: Make sure DMZ host is disabled. If DMZ is enabled, it will disable all Virtual
Server entries.
Because our routers use NAT (Network Address Translation), you can only open a
specific port to one computer at a time. For example: If you have 2 web servers on
your network, you cannot open port 80 to both computers. You will need to configure
1 of the web servers to use port 81. Now you can open port 80 to the first computer
and then open port 81 to the other computer.
80
Page 81

Frequently Asked Questions (continued)
What is DMZ?
Demilitarized Zone:
In computer networks, a DMZ (demilitarized zone) is a computer host or small
network inserted as a neutral zone between a company´s private network and the
outside public network. It prevents outside users from getting direct access to a
server that has company data. (The term comes from the geographic buffer zone that
was set up between North Korea and South Korea following the UN police action in
the early 1950s.) A DMZ is an optional and more secure approach to a firewall and
effectively acts as a proxy server as well.
In a typical DMZ configuration for a small company, a separate computer (or host in
network terms) receives requests from users within the private network for access to
Web sites or other companies accessible on the public network. The DMZ host then
initiates sessions for these requests on the public network. However, the DMZ host is
not able to initiate a session back into the private network. It can only forward packets
that have already been requested.
Users of the public network outside the company can access only the DMZ host. The
DMZ may typically also have the company´s Web pages so these could be served to
the outside world. However, the DMZ provides access to no other company data. In
the event that an outside user penetrated the DMZ hosts security, the Web pages
might be corrupted but no other company information would be exposed. D-Link, a
leading maker of routers, is one company that sells products designed for setting up
a DMZ
How do I configure the DMZ Host?
The DMZ feature allows you to forward all incoming ports to one computer on the local
network. The DMZ, or Demilitarized Zone, will allow the specified computer to be
exposed to the Internet. DMZ is useful when a certain application or game does not
work through the firewall. The computer that is configured for DMZ will be completely
vulnerable on the Internet, so it is suggested that you try opening ports from the
Virtual Server or Firewall settings before using DMZ.
Step 1 Find the IP address of the computer you want to use as the DMZ host.
To find out how to locate the IP Address of the computer in Windows XP/2000/ME/9x
or Macintosh operating systems please refer to Step 4 of the first question in this
section (Frequently Asked Questions).
81
Page 82

Frequently Asked Questions (continued)
How do I configure the DMZ Host? (continued)
Step 2 Log into the web based
configuration of the router by typing in the IP
Address of the router (default:192.168.0.1) in
your web browser. The username is admin
(all lowercase) and the password is blank
(nothing)
Step 3 Click the Advanced tab and then
click on the DMZ button. Select Enable and
type in the IP Address you found in step 1.
Step 4 Click Apply
and then Continue
to save the changes.
Note: When DMZ is
enabled, Virtual
Server settings will
still be effective.
Remember, you
cannot forward the
same port to multiple
IP Addresses, so the
Virtual Server
settings will take
priority over DMZ
settings.
DI-784
admin
82
Page 83

Frequently Asked Questions (continued)
How do I open a range of ports on my router using Firewall rules?
Step 1 Access the router’s web configuration by entering the router’s IP Address in
your web browser. The default IP Address is 192.168.0.1. Login using your password.
The default username is “admin” and the password is blank.
If you are having difficulty accessing web management, please see the first question
in this section.
Step 2 From the web management Home page, click the Advanced tab then click
the Firewall button.
Step 3 Click on
Enabled and type in
a name for the new
rule.
Step 4 Choose WAN
as the Source and
enter a range of IP
Addresses out on the
internet that you
would like this rule
applied to. If you
would like this rule to
allow all internet
users to be able to
access these ports,
then put an Asterisk
in the first box and
leave the second box
empty.
Step 5 Select LAN as the Destination and enter the IP Address of the computer on
your local network that you want to allow the incoming service to. This will not work
with a range of IP Addresses.
Step 6 Enter the port or range of ports that are required to be open for the incoming
service.
Step 7 Click Apply and then click Continue.
Note: Make sure DMZ host is disabled.
Because our routers use NAT (Network Address Translation), you can only open a
specific port to one computer at a time. For example: If you have 2 web servers on
your network, you cannot open port 80 to both computers. You will need to configure
1 of the web servers to use port 81. Now you can open port 80 to the first computer
and then open port 81 to the other computer.
83
Page 84

Frequently Asked Questions (continued)
What are virtual servers?
A Virtual Server is defined as a service port, and all requests to this port will be
redirected to the computer specified by the server IP. For example, if you have an FTP
Server (port 21) at 192.168.0.5, a Web server (port 80) at 192.168.0.6, and a VPN
server at 192.168.0.7, then you need to specify the following virtual server mapping
table:
Server Port
Server IP
Enable
21 192.168.0.5 X
80 192.168.0.6 X
1723 192.168.0.7 X
How do I use PC Anywhere with my router?
You will need to open 3 ports in the Virtual Server section of your D-Link router.
Step 1 Open your web browser and enter the IP Address of the router (192.168.0.1).
Step 2 Click on Advanced at the top and then click Virtual Server on the left side.
Step 3 Enter the
information as seen
below. The Private IP is
the IP Address of the
computer on your local
network that you want to
connect to.
Step 4 The first entry
will read as shown here:
Step 5 Click Apply
and then click Continue.
84
Page 85

Frequently Asked Questions (continued)
How do I use PC Anywhere with my router? (continued)
Step 6 Create
a second entry
as shown here:
Step 7 Click
Apply and then
click Continue.
Step 8 Create
a third and final
entry as shown
here:
Step 9 Click Apply and then click Continue.
Step 10 Run PCAnywhere from the remote site and use the WAN IP Address of the
router, not your computer´s IP Address.
85
Page 86

Frequently Asked Questions (continued)
How can I use eDonkey behind my D-Link router?
You must open ports on your router to allow incoming traffic while using eDonkey.
eDonkey uses three ports (4 if using CLI):
4661 (TCP) To connect with a server
4662 (TCP) To connect with other clients
4665 (UDP) To communicate with servers other than the one you are connected to.
4663 (TCP) *Used with the command line (CLI) client when it is configured to allow
remote connections. This is the case when using a Graphical Interface (such as the
Java Interface) with the client.
Step 1 Open your web browser and enter the IP Address of your router
(192.168.0.1). Enter username (admin) and your password (leave blank).
Step 2 Click on Advanced and then click Firewall.
Step 3 Create a new firewall rule:
Click Enabled.
Enter a name
(edonkey).
Click Allow.
Next to Source,
select WAN under
interface. In the first
box, enter an *. Leave
the second box
empty.
Next to Destination,
select LAN under
interface. Enter the IP
Address of the
computer you are
running eDonkey
from. Leave the
second box empty.
Under Protocol,
select *. In the port
range boxes, enter
4661 in the first box
and then 4665 in the
second box. Click
Always or set a schedule.
Step 4 Click Apply and then Continue.
.
edonkey
.
WAN
LAN
*
192.168.0.100
4665
4661
*
86
Page 87

Frequently Asked Questions (continued)
How do I set up my router for SOCOM on my Playstation 2?
To allow you to play SOCOM and hear audio, you must download the latest firmware
for the router (if needed), enable Game Mode, and open port 6869 to the IP Address of
your Playstation.
Step 1 Upgrade firmware (follow link above).
Step 2 Open your web browser and enter the IP Address of the router (192.168.0.1).
Enter username (admin) and your password (blank by default).
Step 3 Click on the Advanced tab and then click on Virtual Server on the left side.
Step 4 You will now create a new Virtual Server entry. Click Enabled and enter a
name (socom). Enter the IP Address of your Playstation for Private IP.
Step 5 For Protocol Type select Both. Enter 6869 for both the Private Port and
Public Port. Click Always. Click Apply to save changes and then Continue
socom
192.168.0.100
Both
6869
6869
Step 6 Click on the Tools tab and then Misc on the left side.
Step 7 Make sure Gaming Mode is Enabled. If not, click Enabled. Click Apply
and then Continue.
87
Page 88

Frequently Asked Questions (continued)
How can I use Gamespy behind my D-Link router?
Step 1 Open your web browser
and enter the IP Address of the
router (192.168.0.1). Enter
admin for the username and
your password (blank by
default).
Step 2 Click on the Advanced
tab and then click Virtual Server
on the left side.
Step 3 You will create 2
entries.
Step 4 Click Enabled and enter
Settings:
NAME - Gamespy1
PRIVATE IP - The IP
Address of your computer
that you are running
Gamespy from.
PROTOCOL TYPE - Both
gamespy1
192.168.0.100
3783!
3783
PRIVATE PORT - 3783
PUBLIC PORT - 3783
SCHEDULE - Always.
Click Apply and then continue
Step 5 Enter 2nd entry:
Click Enabled
NAME - Gamespy2
PRIVATE IP - The IP
Address of your computer
that youare running
Gamespy from.
PROTOCOL TYPE - Both
PRIVATE PORT - 6500
PUBLIC PORT - 6500
SCHEDULE - Always.
Click Apply and then continue.
gamespy2
192.168.0.100
Both
6500
6500
88
Page 89

Frequently Asked Questions (continued)
How do I configure my router for KaZaA and Grokster?
The following is for KaZaA, Grokster, and others using the FastTrack P2P file sharing
system.
In most cases, you do not have to configure anything on the router or on the Kazaa
software. If you are having problems, please follow steps below:
Step 1 Enter the IP Address of your router in a web browser (192.168.0.1).
Step 2 Enter your username (admin) and your password (blank by default).
Step 3 Click on Advanced and then click Virtual Server.
Step 4 Click Enabled and then enter a Name (kazaa for example).
Step 5 Enter the IP Address of the computer you are running KaZaA from in the
Private IP box. Select TCP for the Protocol Type.
Step 6 Enter 1214 in the Private and Public Port boxes. Click Always under
schedule or set a time range. Click Apply.
Make sure that you did not enable proxy/firewall in the KaZaA software.
89
Page 90

Frequently Asked Questions (continued)
How do I configure my router to play Warcraft 3?
You must open ports on your router to allow incoming traffic while hosting a game in
Warcraft 3. To play a game, you do not have to configure your router.
Warcraft 3 (Battlenet) uses port 6112.
For the DI-604, DI-614+. DI-624, DI-754, DI-764, or DI-784:
Step 1 Open your web browser
and enter the IP Address of your
router (192.168.0.1). Enter
username (admin) and your
password (leave blank).
Step 2 Click on Advanced
and then click Virtual Server.
Step 3 Create a new entry:
warcraft3
192.168.0.100
Both
6112
6112
Click Enabled. Enter a name
(warcraft3). Private IP - Enter
the IP Address of the computer
you want to host the game.
Select Both for Protocol Type
Enter 6112 for both Private Port
and Public Port Click Always or
set a schedule.
Step 4 Click Apply and then
Continue.
Note: If you want multiple computers from you LAN to play in the same game that
you are hosting, then repeat the steps above and enter the IP Addresses of the other
computers. You will need to change ports. Computer #2 can use port 6113, computer
#3 can use 6114, and so on.
You will need to change the port information within the Warcraft 3 software for
computers #2 and up.
Configure the Game Port information on each computer:
Start Warcraft 3 on each computer, click Options > Gameplay. Scroll down and you
should see Game Port. Enter the port number as you entered in the above steps.
90
Page 91

Frequently Asked Questions (continued)
How do I use NetMeeting with my D-Link router?
Unlike most TCP/IP applications, NetMeeting uses DYNAMIC PORTS instead of
STATIC PORTS. That means that each NetMeeting connection is somewhat different
than the last. For instance, the HTTP web site application uses port 80. NetMeeting
can use any of over 60,000 different ports.
All broadband routers using (only) standard NAT and all internet sharing programs like
Microsoft ICS that use (only) standard NAT will NOT work with NetMeeting or other
h.323 software packages.
The solution is to put the router in DMZ.
Note: A few hardware manufacturers have taken it on themselves to actually provide
H.323 compatibility. This is not an easy task since the router must search each
incoming packet for signs that it might be a netmeeting packet. This is a whole lot
more work than a router normally does and may actually be a weak point in the
firewall. D-Link is not one of the manufacturers.
To read more on this visit http://www.HomenetHelp.com
How do I set up my router to use iChat? -for Macintosh users-
You must open ports on your router to allow incoming traffic while using iChat.
iChat uses the following ports: 5060 (UDP) 5190 (TCP) File Sharing 16384-16403
(UDP) To video conference with other clients
Step 1 Open your web browser and enter the IP Address of your router
(192.168.0.1). Enter username (admin) and your password (leave blank).
Step 2 Click on Advanced and then click Firewall.
91
Page 92

Frequently Asked Questions (continued)
How do I set up my router to use iChat? -for Macintosh users(continued)
Step 3 Create a new
firewall rule:
Click Enabled.
Enter a name
(ichat1).
Click Allow.
Next to Source,
select WAN under
interface.
In the first box,
enter an *.
Leave the second
box empty.
Next to Destination,
select LAN under
interface.
Enter the IP
Address of the
computer you are
running iChat from.
.
ichat1
.
WAN
LAN
.
192.168.0.100
UDP
5060
Leave the second box empty. Under Protocol, select UDP. In the port range boxes,
enter 5060 in the first
box and leave the
second box empty.
Click Always or set a
schedule.
Step 4 Click Apply
and then Continue.
Step 5
.
ichat2
.
WAN
LAN
.
192.168.0.100
UDP
16384
16403
Repeat steps 3 and 4
enter ichat2 and open
ports 16384-16403
(UDP).
92
Page 93

Frequently Asked Questions (continued)
How do I set up my router to use iChat? -for Macintosh users(continued)
For File Sharing:
Step 1 Click on Advanced and
then Virtual Server.
Step 2 Check Enabled to
activate entry.
Step 3 Enter a name for your
virtual server entry (ichat3).
Step 4 Next to Private IP, enter
ichat3
192.168.0.100
5190
5190
the IP Address of the computer
on your local network that you
want to allow the incoming
service to.
Step 5 Select TCP for Protocol
Type.
Step 6 Enter 5190 next to
Private Port and Public Port.
Step 7 Click Always or
configure a schedule.
Step 8 Click Apply and then Continue.
If using Mac OS X Firewall, you may need to temporarily turn off the firewall in
the Sharing preference pane on both computers.
To use the Mac OS X Firewall, you must open the same ports as in the router:
Step 1 Choose Apple menu > System Preferences.
Step 2 Choose View > Sharing.
Step 3 Click the Firewall tab.
Step 4 Click New.
Step 5 Choose Other from the Port Name pop-up menu.
Step 6 In the Port Number, Range or Series field, type in: 5060, 16384-16403.
Step 7 In the Description field type in: iChat AV
Step 8 Click OK.
93
Page 94

Frequently Asked Questions (continued)
How do I send or receive a file via iChat when the Mac OSX firewall
is active? -for Macintosh users- Mac OS X 10.2 and later
The following information is from the online Macintosh AppleCare knowledge base:
“iChat cannot send or receive a file when the Mac OS X firewall is active in its default
state. If you have opened the AIM port, you may be able to receive a file but not send
them.
In its default state, the Mac OS X firewall blocks file transfers using iChat or America
Online AIM software. If either the sender or receiver has turned on the Mac OS X firewall,
the transfer may be blocked.
The simplest workaround is to temporarily turn off the firewall in the Sharing preference
pane on both computers. This is required for the sender. However, the receiver may keep
the firewall on if the AIM port is open. To open the AIM port:
Step 1 Choose Apple menu > System Preferences.
Step 2 Choose View > Sharing.
Step 3 Click the Firewall tab.
Step 4 Click New.
Step 5 Choose AOL IM from the Port Name pop-up menu. The number 5190
should already be filled in for you.
Step 6 Click OK.
If you do not want to turn off the firewall at the sending computer, a different file sharing
service may be used instead of iChat. The types of file sharing available in Mac OS X are
outlined in technical document 106461, "Mac OS X: File Sharing" in the AppleCare Knowl-
edge base online.
Note: If you use a file sharing service when the firewall is turned on, be sure to click the
Firewall tab and select the service you have chosen in the "Allow" list. If you do not do
this, the firewall will also block the file sharing service. “
94
Page 95

Frequently Asked Questions (continued)
What is NAT?
NAT stands for Network Address Translator. It is proposed and described in RFC1631 and is used for solving the IP Address depletion problem. Each NAT box has a
table consisting of pairs of local IP Addresses and globally unique addresses, by
which the box can “translate” the local IP Addresses to global address and vice versa.
Simply put, it is a method of connecting multiple computers to the Internet (or any
other IP network) using one IP Address.
D-Link´s broadband routers support NAT. With proper configuration, multiple users can
access the Internet using a single account via the NAT device.
For more information on RFC-1631: The IP Network Address Translator (NAT), visit
http://www.faqs.org/rfcs/rfc1631.html
95
Page 96

Technical Support
You can find software updates and user documentation on the D-Link website.
D-Link provides free technical support for customers within the United States and
within Canada for the duration of the warranty period on this product.
U.S. and Canadian customers can contact D-Link technical support through our web
site, or by phone.
Tech Support for customers within the United States:
D-Link Technical Support over the Telephone:
(877) 453-5465
24 hours a day, seven days a week.
D-Link Technical Support over the Internet:
http://support.dlink.com
email:support@dlink.com
Tech Support for customers within Canada:
D-Link Technical Support over the Telephone:
(800) 361-5265
Monday to Friday 8:30am to 9:00pm EST
D-Link Technical Support over the Internet:
http://support.dlink.ca
email:support@dlink.ca
When contacting technical support, please provide the following information:
• Serial number of the unit
• Model number or product name
• Software type and version number
96
Page 97

Warranty and Registration
(USA only)
Subject to the terms and conditions set forth herein, D-Link Systems, Inc. (“D-Link”) provides this Limited
warranty for its product only to the person or entity that originally purchased the product from:
• D-Link or its authorized reseller or distributor and
• Products purchased and delivered within the fifty states of the United States, the District of
Columbia, U.S. Possessions or Protectorates, U.S. Military Installations, addresses with an
APO or FPO.
Limited Warranty: D-Link warrants that the hardware portion of the D-Link products described
below will be free from material defects in workmanship and materials from the date of original retail
purchase of the product, for the period set forth below applicable to the product type (“Warranty
Period”), except as otherwise stated herein.
3-Year Limited Warranty for the Product(s) is defined as follows:
• Hardware (excluding power supplies and fans) Three (3) Years
• Power Supplies and Fans One (1) Year
• Spare parts and spare kits Ninety (90) days
D-Link’s sole obligation shall be to repair or replace the defective Hardware during the Warranty Period
at no charge to the original owner or to refund at D-Link’s sole discretion. Such repair or replacement will
be rendered by D-Link at an Authorized D-Link Service Office. The replacement Hardware need not be
new or have an identical make, model or part. D-Link may in its sole discretion replace the defective
Hardware (or any part thereof) with any reconditioned product that D-Link reasonably determines is
substantially equivalent (or superior) in all material respects to the defective Hardware. Repaired or
replacement Hardware will be warranted for the remainder of the original Warranty Period from the date
of original retail purchase. If a material defect is incapable of correction, or if D-Link determines in its sole
discretion that it is not practical to repair or replace the defective Hardware, the price paid by the original
purchaser for the defective Hardware will be refunded by D-Link upon return to D-Link of the defective
Hardware. All Hardware (or part thereof) that is replaced by D-Link, or for which the purchase price is
refunded, shall become the property of D-Link upon replacement or refund.
Limited Software Warranty: D-Link warrants that the software portion of the product (“Software”)
will substantially conform to D-Link’s then current functional specifications for the Software, as set forth
in the applicable documentation, from the date of original retail purchase of the Software for a period of
ninety (90) days (“Warranty Period”), provided that the Software is properly installed on approved
hardware and operated as contemplated in its documentation. D-Link further warrants that, during the
Warranty Period, the magnetic media on which D-Link delivers the Software will be free of physical
defects. D-Link’s sole obligation shall be to replace the non-conforming Software (or defective media)
with software that substantially conforms to D-Link’s functional specifications for the Software or to
refund at D-Link’s sole discretion. Except as otherwise agreed by D-Link in writing, the replacement
Software is provided only to the original licensee, and is subject to the terms and conditions of the
license granted by D-Link for the Software. Software will be warranted for the remainder of the original
Warranty Period from the date or original retail purchase. If a material non-conformance is incapable of
correction, or if D-Link determines in its sole discretion that it is not practical to replace the nonconforming Software, the price paid by the original licensee for the non-conforming Software will be
refunded by D-Link; provided that the non-conforming Software (and all copies thereof) is first returned
to D-Link. The license granted respecting any Software for which a refund is given automatically
terminates.
Non-Applicability of Warranty: The Limited Warranty provided hereunder for hardware and software
of D-Link’s products will not be applied to and does not cover any refurbished product and any product
purchased through the inventory clearance or liquidation sale or other sales in which D-Link, the sellers,
or the liquidators expressly disclaim their warranty obligation pertaining to the product and in that case,
the product is being sold “As-Is” without any warranty whatsoever including, without limitation, the
Limited Warranty as described herein, notwithstanding anything stated herein to the contrary.
Submitting A Claim: The customer shall return the product to the original purchase point based on its
return policy. In case the return policy period has expired and the product is within warranty, the
customer shall submit a claim to D-Link as outlined below:
97
Page 98

• The customer must submit with the product as part of the claim a written description of the
Hardware defect or Software nonconformance in sufficient detail to allow D-Link to confirm
the same.
• The original product owner must obtain a Return Material Authorization (“RMA”) number from
the Authorized D-Link Service Office and, if requested, provide written proof of purchase of
the product (such as a copy of the dated purchase invoice for the product) before the
warranty service is provided.
• After an RMA number is issued, the defective product must be packaged securely in the
original or other suitable shipping package to ensure that it will not be damaged in transit, and
the RMA number must be prominently marked on the outside of the package. Do not include any
manuals or accessories in the shipping package. D-Link will only replace the defective portion
of the Product and will not ship back any accessories.
• The customer is responsible for all in-bound shipping charges to D-Link. No Cash on Delivery
(“COD”) is allowed. Products sent COD will either be rejected by D-Link or become the
property of D-Link. Products shall be fully insured by the customer. D-Link will not be held
responsible for any packages that are lost in transit to D-Link. The repaired or replaced
packages will be shipped to the customer via UPS Ground or any common carrier selected by
D-Link, with shipping charges prepaid. Expedited shipping is available if shipping charges are
prepaid by the customer and upon request.
• Return Merchandise Ship-To Address
USA: 17595 Mt. Herrmann, Fountain Valley, CA, 92708
Canada: 2180 Winston Park Drive, Oakville, ON, L6H 5W1 (Visit http://www.dlink.ca for detailed
warranty information within Canada)
D-Link may reject or return any product that is not packaged and shipped in strict compliance with the
foregoing requirements, or for which an RMA number is not visible from the outside of the package. The
product owner agrees to pay D-Link’s reasonable handling and return shipping charges for any product
that is not packaged and shipped in accordance with the foregoing requirements, or that is determined
by D-Link not to be defective or non-conforming.
What Is Not Covered: This limited warranty provided by D-Link does not cover: Products, if in D-Link’s
judgment, have been subjected to abuse, accident, alteration, modification, tampering, negligence, misuse,
faulty installation, lack of reasonable care, repair or service in any way that is not contemplated in the
documentation for the product, or if the model or serial number has been altered, tampered with, defaced
or removed; Initial installation, installation and removal of the product for repair, and shipping costs;
Operational adjustments covered in the operating manual for the product, and normal maintenance;
Damage that occurs in shipment, due to act of God, failures due to power surge, and cosmetic damage;
Any hardware, software, firmware or other products or services provided by anyone other than DLink; Products that have been purchased from inventory clearance or liquidation sales or other sales in
which D-Link, the sellers, or the liquidators expressly disclaim their warranty obligation pertaining to the
product. Repair by anyone other than D-Link or an Authorized D-Link Service Office will void this
Warranty.
Disclaimer of Other Warranties: EXCEPT FOR THE LIMITED WARRANTY SPECIFIED HEREIN, THE
PRODUCT IS PROVIDED “AS-IS” WITHOUT ANY WARRANTY OF ANY KIND WHATSOEVER INCLUDING,
WITHOUT LIMITATION, ANY WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE
AND NON-INFRINGEMENT. IF ANY IMPLIED WARRANTY CANNOT BE DISCLAIMED IN ANY TERRITORY
WHERE A PRODUCT IS SOLD, THE DURATION OF SUCH IMPLIED WARRANTY SHALL BE LIMITED TO
NINETY (90) DAYS. EXCEPT AS EXPRESSLY COVERED UNDER THE LIMITED WARRANTY PROVIDED
HEREIN, THE ENTIRE RISK AS TO THE QUALITY, SELECTION AND PERFORMANCE OF THE PRODUCT IS
WITH THE PURCHASER OF THE PRODUCT.
98
Page 99

LIABILITY OF D-LINK UNDER THIS WARRANTY IS LIMITED TO THE PURCHASE PRICE OF THE PRODUCT
COVERED BY THE WARRANTY. THE FOREGOING EXPRESS WRITTEN WARRANTIES AND REMEDIES
ARE EXCLUSIVE AND ARE IN LIEU OF ANY OTHER WARRANTIES OR REMEDIES, EXPRESS, IMPLIED OR
STATUTORY.
Governing Law: This Limited Warranty shall be governed by the laws of the State of California. Some
states do not allow exclusion or limitation of incidental or consequential damages, or limitations on how
long an implied warranty lasts, so the foregoing limitations and exclusions may not apply. This limited
warranty provides specific legal rights and the product owner may also have other rights which vary
from state to state.
Trademarks: D-Link is a registered trademark of D-Link Systems, Inc. Other trademarks or registered
trademarks are the property of their respective manufacturers or owners.
Copyright Statement: No part of this publication or documentation accompanying this Product may
be reproduced in any form or by any means or used to make any derivative such as translation,
transformation, or adaptation without permission from D-Link Corporation/D-Link Systems, Inc., as
stipulated by the United States Copyright Act of 1976. Contents are subject to change without prior
notice. Copyright© 2002 by D-Link Corporation/D-Link Systems, Inc. All rights reserved.
CE Mark Warning: This is a Class B product. In a domestic environment, this product may cause radio
interference, in which case the user may be required to take adequate measures.
FCC Statement: This equipment has been tested and found to comply with the limits for a Class B
digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable
protection against harmful interference in a residential installation. This equipment generates, uses, and
can radiate radio frequency energy and, if not installed and used in accordance with the instructions,
may cause harmful interference to radio communication. However, there is no guarantee that interference
will not occur in a particular installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and on, the user is encouraged
to try to correct the interference by one or more of the following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that to which the receiver is
connected.
• Consult the dealer or an experienced radio/TV technician for help.
For detailed warranty outside the United States, please contact corresponding local
D-Link office.
FCC Caution:
The manufacturer is not responsible for any radio or TV interference caused by unauthorized
modifications to this equipment; such modifications could void the user’s authority to operate the
equipment.
(1) The devices are restricted to indoor operations within the 5.15 to 5.25GHz range. (2) For this
device to operate in the 5.15 to 5.25GHz range, the devices must use integral antennas.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two
conditions: (1) This device may not cause harmful interference, and (2) this device must accept
any interference received, including interference that may cause undesired operation.
IMPORTANT NOTE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled
environment. The antenna(s) used for this equipment must be installed to provide a separation
distance of at least eight inches (20 cm) from all persons.
This equipment must not be operated in conjunction with any other antenna.
Register your D-Link product online at http://support.dlink.com/register/
(08/04/2003)
99
 Loading...
Loading...