Page 1

Dell PowerEdge RAID
Controller (PERC) H700
and H800
User’s Guide
Page 2

Notes, Cautions, and Warnings
NOTE: A NOTE indicates important information that helps you make better use of
your computer.
CAUTION: A CAUTION indicates potential damage to hardware or loss of data if
instructions are not followed.
WARNING: A WARNING indicates a potential for property damage, personal
injury, or death.
____________________
Information in this publication is subject to change without notice.
© 2010 Dell Inc. All rights reserved.
Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc.
is strictly forbidden.
Trademarks used in this text: Dell™, the DELL logo, PowerEdge™, PowerVault™, CacheCade™,
and OpenManage™ are trademarks of Dell Inc. Intel
in the U.S. and other countries. Microsoft
®
Vista
are either trademarks or registered trademarks of Microsoft Corporation in the United States
and/or other countries. Red Hat Enterprise Linux
of Red Hat, Inc. in the United States and/or other countries. Novell
trademarks of Novell Inc. in the United States and other countries. VMware
of VMWare, Inc. in the United States or other countries.
Other trademarks and trade names may be used in this publication to refer to either the entities claiming
the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and
trade names other than its own.
®
, Windows®, Windows Server®, MS-DOS®, and Windows
®
is a registered trademark of Intel Corporation
®
, and Enterprise Linux® are registered trademarks
®
and SUSE ™ are registered
®
is a registered trademark
Model UCP-70, UCPM-70, and UCP-71
March 2011 Rev. A02
Page 3

Contents
1 Safety Instructions . . . . . . . . . . . . . . . . . 11
General Safety Instructions . . . . . . . . . . . . . . . 11
When Working Inside Your System
. . . . . . . . . . . 12
Protecting Against Electrostatic Discharge . . . . . . 12
Battery Disposal
. . . . . . . . . . . . . . . . . . . . . 13
2Overview . . . . . . . . . . . . . . . . . . . . . . . . . 15
PERC H700 and H800 Card Descriptions. . . . . . . . . 15
PCI Architecture
Operating System Support
. . . . . . . . . . . . . . . . . . 16
. . . . . . . . . . . . . . . . 16
RAID Description . . . . . . . . . . . . . . . . . . . . 17
Summary of RAID Levels
RAID Terminology
. . . . . . . . . . . . . . 17
. . . . . . . . . . . . . . . . . . 18
3 Storage Controller Features . . . . . . . . . . 21
Physical Disk Power Management . . . . . . . . . 24
Using the SMART Feature
Initializing Virtual Disks
Background Initialization of Virtual Disks
Full Initialization of Virtual Disks
Fast Initialization of Virtual Disks
. . . . . . . . . . . . . . . . 24
. . . . . . . . . . . . . . . . . 25
. . . . . 25
. . . . . . . . . . 25
. . . . . . . . . . 26
Contents 3
Page 4

Consistency Checks . . . . . . . . . . . . . . . . . . . 26
Disk Roaming
Disk Migration
. . . . . . . . . . . . . . . . . . . . . . . 26
. . . . . . . . . . . . . . . . . . . . . . 27
Compatibility With Virtual Disks Created
on PERC 6 and H200 Cards
. . . . . . . . . . . . . 28
Migrating Virtual Disks From PERC 6 or
H200 to PERC H700 and H800 . . . . . . . . . . . . 28
Virtual Disk Write Cache Policies. . . . . . . . . . . . 29
Write-Back and Write-Through
. . . . . . . . . . . 29
Conditions Under Which
Write-Back is Employed . . . . . . . . . . . . . . 29
Conditions Under Which
Write-Through is Employed. . . . . . . . . . . . . 30
Conditions Under Which Forced Write-Back
With No Battery is Employed
Virtual Disk Read Cache Policies
Reconfiguring Virtual Disks
Fault Tolerance Features
. . . . . . . . . . . . . . . . . 33
Using Persistent Hot Spare Slots
Physical Disk Hot Swapping
Failed Physical Disk Detection
. . . . . . . . . . . . 30
. . . . . . . . . . . . 30
. . . . . . . . . . . . . . . 31
. . . . . . . . . . 34
. . . . . . . . . . . . 34
. . . . . . . . . . . 34
Redundant Path With Load
Balancing Support
. . . . . . . . . . . . . . . . . 35
Using Replace Member and
Revertible Hot Spares. . . . . . . . . . . . . . . . 35
Controller Cache Preservation
Cache Preservation With Battery
. . . . . . . . . . . 36
. . . . . . . . . . 37
Cache Preservation With
Non-Volatile Cache (NVC)
Cache Data Recovery
Battery Learn Cycle
. . . . . . . . . . . . . 37
. . . . . . . . . . . . . . . . 37
. . . . . . . . . . . . . . . . . 38
4 Contents
Page 5

Patrol Read. . . . . . . . . . . . . . . . . . . . . . . . 38
4 Installing and Configuring Hardware. . . . . 41
Installing the PERC H700 and H800 Adapters . . . . . . 41
Removing the PERC H700 and H800 Adapters
. . . . . . 46
Removing and Installing the PERC H700 Modular
Card in Dell Blade Systems
. . . . . . . . . . . . . . . 49
Removing the DIMM From a PERC H700. . . . . . . . . 51
Installing the DIMM on a PERC H700
Replacing the BBU on a PERC H700
. . . . . . . . . . 53
. . . . . . . . . . . 56
Removing the TBBU or TNVC From a
PERC H800 Adapter
. . . . . . . . . . . . . . . . . . . 58
Replacing the Battery and Battery Cable Onto
the DIMM of a PERC H800 Adapter
. . . . . . . . . . . 60
Installing the TBBU or TNVC on a
PERC H800 Adapter
. . . . . . . . . . . . . . . . . . . 61
Transferring a TBBU or TNVC Between
PERC H800 Cards
. . . . . . . . . . . . . . . . . . . . . 63
Setting up Redundant Path Support on the
PERC H800 Adapter
. . . . . . . . . . . . . . . . . . . 64
Reverting From Redundant Path Support to Single
Path Support on the PERC H800 Adapter
. . . . . . . . 67
5 Driver Installation . . . . . . . . . . . . . . . . . . 69
Installing Windows Drivers . . . . . . . . . . . . . . . 69
Creating the Driver Media
. . . . . . . . . . . . . 69
Contents 5
Page 6

Pre-Installation Requirements . . . . . . . . . . . 70
Installing Driver During a Windows Server 2003
Operating System Installation. . . . . . . . . . . . 71
Installing Driver During a Windows Server 2008,
Windows Server 2008 R2 Installation. . . . . . . . 72
Installing Windows Server 2008,
Windows Server 2008 R2, Windows
Server 2003 for a New RAID Controller. . . . . . . 72
Updating Existing Windows Server 2008,
Windows Server 2008 R2,
Windows Server 2003. . . . . . . . . . . . . . . . 73
Installing Linux Driver . . . . . . . . . . . . . . . . . . 74
Installing Red Hat Enterprise Linux
Operating System Using the DUD
. . . . . . . . . . 76
Installing SUSE Linux Enterprise Server
Using the Driver Update Diskette
. . . . . . . . . . 77
Installing the RPM Package
With DKMS Support . . . . . . . . . . . . . . . . 78
6 Configuring and Managing RAID . . . . . . 81
6 Contents
Installing Solaris Driver
. . . . . . . . . . . . . . . . . 79
Installing Solaris 10 on a PowerEdge System
Booting From a PERC H700 or H800 Card
. . . . . . 80
Adding or Updating the Driver
to an Existing System . . . . . . . . . . . . . . . . 80
Dell OpenManage Storage Management . . . . . . . . 81
BIOS Configuration Utility . . . . . . . . . . . . . . . . 82
Entering the BIOS Configuration Utility
Exiting the Configuration Utility
Menu Navigation Controls
Setting Up Virtual Disks
Virtual Disk Management
. . . . . . . . . . . . . . . 85
. . . . . . . . . . . . . . . . 88
. . . . . . . . . . . . . 83
. . . . . . . 82
. . . . . . . . . . . 83
Page 7

Creating Virtual Disks. . . . . . . . . . . . . . . . 88
Initializing Virtual Disks . . . . . . . . . . . . . . . 91
Checking Data Consistency
. . . . . . . . . . . . 91
Importing or Clearing Foreign Configurations
Using the VD Mgmt Menu . . . . . . . . . . . . . 92
Importing or Clearing Foreign Configurations
Using the Foreign Configuration View Screen
. . . . 93
Managing Preserved Cache . . . . . . . . . . . . 96
Managing Dedicated Hot Spares
Deleting Virtual Disks
. . . . . . . . . . . . . . . . 98
. . . . . . . . . . 97
Deleting Disk Groups . . . . . . . . . . . . . . . . 98
Clearing the Configuration
BIOS Configuration Utility Menu Options
. . . . . . . . . . . . . 99
. . . . . . 99
Physical Disk Management
Setting LED Blinking
Creating Global Hot Spares
. . . . . . . . . . . . . . . 108
. . . . . . . . . . . . . . . . 108
. . . . . . . . . . . . . 109
Removing Global or Dedicated Hot Spares . . . . 109
Replacing an Online Physical Disk
. . . . . . . . . 110
Stopping Background Initialization. . . . . . . . . 111
Performing a Manual Rebuild of an
Individual Physical Disk
Controller Management
Enabling Boot Support
Enabling BIOS Stop on Error
. . . . . . . . . . . . . . . 111
. . . . . . . . . . . . . . . . . 112
. . . . . . . . . . . . . . . 112
. . . . . . . . . . . . 113
Enabling Auto Import . . . . . . . . . . . . . . . . 113
Restoring Factory Default Settings
. . . . . . . . . 114
7 CacheCade . . . . . . . . . . . . . . . . . . . . . . 115
CacheCade Virtual Disk Characteristics . . . . . . . . 115
Configuring and Managing
CacheCade Virtual Disks
. . . . . . . . . . . . . . . . 116
Contents 7
Page 8

CacheCade Virtual Disk Management . . . . . . 116
Create CacheCade Virtual Disk . . . . . . . . . . 116
Delete CacheCade Virtual Disk
Reconfiguring CacheCade Virtual Disks
. . . . . . . . . . 118
. . . . . 118
8 Security Key and RAID Management. . . . 121
Security Key Implementation . . . . . . . . . . . . . 121
Configuring and Managing
Secured Virtual Disks
BIOS Configuration Utility
Security Menu Options
Security Key Management . . . . . . . . . . . . 122
Creating Secured Virtual Disks
Securing Pre-Existing Virtual Disks
Importing or Clearing Secured Foreign
Configurations and Secure Disk Migration. . . . 126
Instant Secure Erase
. . . . . . . . . . . . . . . . . 121
. . . . . . . . . . . . . . 121
. . . . . . . . . . 125
. . . . . . . . 126
. . . . . . . . . . . . . . . 128
9 Troubleshooting . . . . . . . . . . . . . . . . . . . 131
8 Contents
Troubleshooting Security Key Errors
Secured Foreign Import Errors
. . . . . . . . . 128
. . . . . . . . . . 128
Failure to Select or Configure Non
Self-Encrypting Disks (non-SED) . . . . . . . . . 129
Failure to Delete Security Key
. . . . . . . . . . 129
Failure to Instant Secure Erase
Task on Physical Disks . . . . . . . . . . . . . . 129
Post Error Messages . . . . . . . . . . . . . . . . . . 131
Degraded State of Virtual Disks
Memory Errors
. . . . . . . . . . . . . . . . . . . . . 141
. . . . . . . . . . . . 141
Page 9

Preserved Cache State . . . . . . . . . . . . . . . . . 142
General Issues
Physical Disk Related Issues
Physical Disk Failures and Rebuild Issues . . . . . . . 144
SMART Errors
Replace Member Errors
Linux Operating System Errors . . . . . . . . . . . . . 148
Disk Carrier LED Indicators
. . . . . . . . . . . . . . . . . . . . . . 142
. . . . . . . . . . . . . . 143
. . . . . . . . . . . . . . . . . . . . . . 146
. . . . . . . . . . . . . . . . . 147
. . . . . . . . . . . . . . . 151
A Regulatory Notices . . . . . . . . . . . . . . . . 153
B Corporate Contact Details
(Taiwan Only) . . . . . . . . . . . . . . . . . . . . 155
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Contents 9
Page 10

10 Contents
Page 11

1
Safety Instructions
Use the following safety guidelines to help ensure your own personal safety and to help protect
your system and working environment from potential damage.
WARNING: There is a danger of a new battery exploding if it is incorrectly installed.
Replace the battery only with the same or equivalent type recommended by the
manufacturer. See "Battery Disposal" on page 13.
NOTE: For complete information on U.S. Terms and Conditions of Sale, Limited Warranties
and Returns, Export Regulations, Software License Agreement, Safety, Environmental and
Ergonomic Instructions, Regulatory Notices, and Recycling Information, see the S
Environmental and Regulatory Information
Warranty and Support Information
(SERI),
(WSI) that shipped with your system.
End User License Agreement
General Safety Instructions
• Observe and follow service markings. Do not service any product except as explained in
your user documentation. Opening or removing covers that are marked with the triangular
symbol with a lightning bolt may expose you to electrical shock. Components inside the
compartments must be serviced only by a trained service technician.
• If any of the following conditions occur, unplug the product from the electrical outlet, and
replace the part or contact your trained service provider:
– The power cable, extension cable, or plug is damaged.
– An object has fallen in the product.
– The product has been exposed to water.
– The product has been dropped or damaged.
– The product does not operate correctly when you follow the operating instructions.
• Use the product only with approved equipment.
• Operate the product only from the type of external power source indicated on the
electrical ratings label. If you are not sure of the type of power source required, consult
your service provider or local power company.
• Handle batteries carefully. Do not disassemble, crush, puncture, short external contacts,
dispose of in fire or water, or expose batteries to temperatures higher than 60° Celsius
(140° Fahrenheit). Do not attempt to open or service batteries; replace batteries only with
batteries designated for the product.
afety,
(EULA), and
Safety Instructions 11
Page 12

When Working Inside Your System
Before you remove the system covers, perform the following steps in the sequence indicated:
CAUTION: Except as expressly otherwise instructed in Dell documentation, only trained
service technicians are authorized to remove the system cover and access any of the
components inside the system.
CAUTION: To help avoid possible damage to the system board, wait 5 seconds after
turning off the system before removing a component from the system board or disconnecting
a peripheral device.
1
Turn off the system and any connected devices.
2
Disconnect your system and devices from their power sources. To reduce the potential of
personal injury or shock, disconnect any telecommunication lines from the system.
3
Ground yourself by touching an unpainted metal surface on the chassis before touching
anything inside the system.
4
While you work, periodically touch an unpainted metal surface on the chassis to dissipate any
static electricity that might harm internal components.
In addition, take note of the following safety guidelines when appropriate:
• When you disconnect a cable, pull on its connector or on its strain-relief loop, not on the
cable itself. Some cables have a connector with locking tabs. If you are disconnecting this
type of cable, press in on the locking tabs before disconnecting the cable. As you pull
connectors apart, keep them evenly aligned to avoid bending any connector pins.
Also, when you connect a cable, make sure both connectors are correctly oriented and
aligned.
• Handle components and cards with care. Do not touch the components or contacts on
a card. Hold a card by its edges or by its metal mounting bracket. Hold a component such
as a microprocessor chip by its edges, not by its pins.
Protecting Against Electrostatic Discharge
Electrostatic discharge (ESD) events can harm electronic components inside your system. Under
certain conditions, ESD may build up on your body or an object, such as a peripheral, and then
discharge into another object, such as your system. To prevent ESD damage, you must discharge
static electricity from your body before you interact with any of your system’s internal electronic
components, such as a memory module. You can protect against ESD by touching a metal
grounded object (such as an unpainted metal surface on your system’s I/O panel) before you
interact with anything electronic. When connecting a peripheral (including handheld digital
assistants) to your system, you should always ground both yourself and the peripheral before
connecting it to the system. Additionally, as you work inside the system, periodically touch
an I/O connector to remove any static charge your body may have accumulated.
12 Safety Instructions
Page 13
You can also take the following steps to prevent damage from electrostatic discharge:
• When unpacking a static-sensitive component from its shipping carton, do not remove the
component from the antistatic packing material until you are ready to install the
component. Just before unwrapping the antistatic package, be sure to discharge static
electricity from your body.
• When transporting a sensitive component, first place it in an antistatic container
or packaging.
• Handle all electrostatic sensitive components in a static-safe area. If possible,
use antistatic floor pads and work bench pads.
Battery Disposal
Your system may use a nickel-metal hydride (NiMH), lithium coin-cell, and/or a
lithium-ion battery. The NiMH, lithium coin-cell, and lithium-ion batteries are
long-life batteries, and it is possible that you may never need to replace them.
However, should you need to replace them, see the instructions included in the
section "Configuring and Managing RAID" on page 81.
NOTE: Do not dispose of the battery along with household waste. Contact your local waste
disposal agency for the address of the nearest battery deposit site.
NOTE: Your system may also include circuit cards or other components that contain
batteries. The batteries too must be disposed of in a battery deposit site. For information about
such batteries, see the documentation for the specific card or component.
Taiwan Battery Recycling Mark
Safety Instructions 13
Page 14

14 Safety Instructions
Page 15
2
Overview
The Dell PowerEdge RAID Controller (PERC) H700 and H800 family
of cards:
• Comply with Serial-attached SCSI (SAS) 2.0 providing up to 6 Gb/sec
throughput.
• Offer RAID control capabilities which include support for
RAID levels 0, 1, 5, 6, 10, 50, and 60.
• Provide reliability, high performance, and fault-tolerant disk subsystem
management.
PERC H700 and H800 Card Descriptions
Table 2-1. PERC H700 and H800 Card Descriptions
Card Name Card Description
PERC H700 Adapter Two internal x4 SAS ports and either a battery backup
unit (BBU) or non-volatile cache (NVC).
PERC H700 Integrated Two internal x4 SAS ports and either a BBU or NVC
PERC H700 Modular One internal x4 SAS port and a BBU
PERC H800 Adapter Two external x4 SAS ports and either a transportable
battery backup unit (TBBU) or transportable nonvolatile cache (TNVC)
NOTE: Each controller supports up to 64 virtual disks.
Overview 15
Page 16

PCI Architecture
• The PERC H700 and H800 cards support a PCI-E 2.0 x8 host interface.
• The PERC H700 Modular cards support a PCI-E 2.0 x4 host interface.
Operating System Support
The
PERC H700 and H800
• Microsoft Windows Server 2003 R2
• Microsoft Windows Server 2008, including Hyper-V virtualization
• Microsoft Windows Server 2008 R2
• Red Hat Enterprise Linux version 5.5 and later (32-bit and 64-bit)
• Red Hat Enterprise Linux version 6.0 and later (64-bit)
•Sun
• SUSE Linux Enterprise Server version 10 SP3 and later (64-bit)
• SUSE Linux Enterprise Server version 11 SP1 and later (64-bit)
• VMware ESX and ESXi 4.0 Update 2
• VMware ESX and ESXi 4.1
NOTE: For the latest list of supported operating systems and driver installation
Solaris10 (64-bit)
instructions, see the system documentation at support.dell.com/manuals. For
specific operating system service pack requirements, see the Drivers and
Downloads section at support.dell.com.
cards support the following operating systems:
16 Overview
Page 17

RAID Description
RAID is a group of independent physical disks that provides high performance
by increasing the number of disks used for saving and accessing data.
A RAID disk subsystem offers the following benefits:
• Improves I/O performance and data availability.
• Improves data throughput because several disks are accessed
simultaneously. The physical disk group appears either as a single storage
unit or multiple logical units to the host system.
• Improves data storage availability and fault tolerance. Data loss caused by
a physical disk failure can be recovered by rebuilding missing data from the
remaining physical disks containing data or parity.
CAUTION: In the event of a physical disk failure, a RAID 0 virtual disk fails,
resulting in data loss.
Summary of RAID Levels
• RAID 0 uses disk striping to provide high data throughput, especially for
large files in an environment that requires no data redundancy.
• RAID 1 uses disk mirroring so that data written to one physical disk is
simultaneously written to another physical disk. RAID 1 is good for small
databases or other applications that require small capacity and complete
data redundancy.
• RAID 5 uses disk striping and parity data across all physical disks
(distributed parity) to provide high data throughput and data redundancy,
especially for small random access.
• RAID 6 is an extension of RAID 5 and uses an additional parity block.
RAID 6 uses block-level striping with two parity blocks distributed across
all member disks. RAID 6 provides protection against double disk failures,
and failures while a single disk is rebuilding. If you are using only one array,
deploying RAID 6 is more effective than deploying a hot spare disk.
• RAID 10 is a combination of RAID 0 and RAID 1, uses disk striping
across mirrored disks. It provides high data throughput and complete data
redundancy. RAID 10 can support up to eight spans, and up to 32 physical
disks per span.
Overview 17
Page 18
• RAID 50 is a combination of RAID 0 and RAID 5 where a RAID 0 array
Stripe element 1
Stripe element 5
Stripe element 9
Stripe element 2
Stripe element 6
Stripe element 10
Stripe element 3
Stripe element 7
Stripe element 11
Stripe element 4
Stripe element 8
Stripe element 12
is striped across RAID 5 elements. RAID 50 requires at least six disks.
• RAID 60 is a combination of RAID 0 and RAID 6 where a RAID 0 array is
striped across RAID 6 elements. RAID 60 requires at least eight disks.
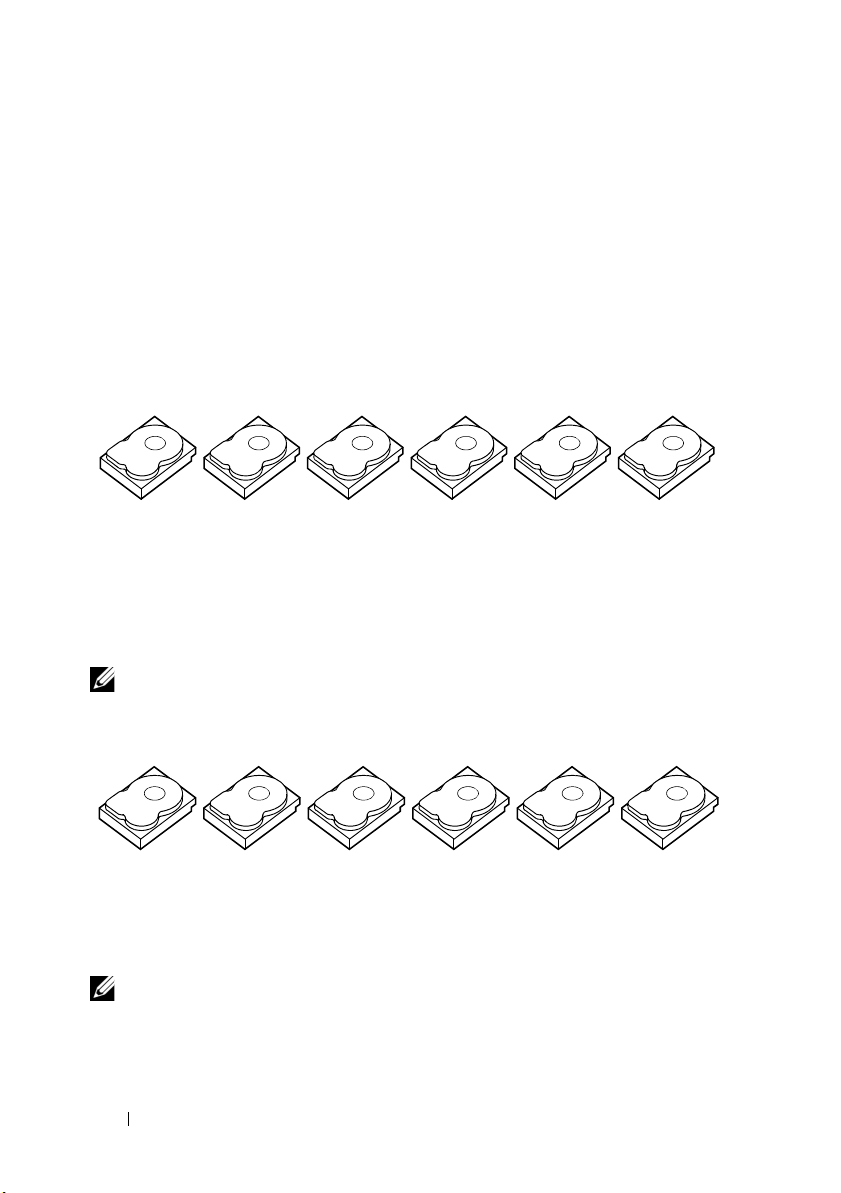
RAID Terminology
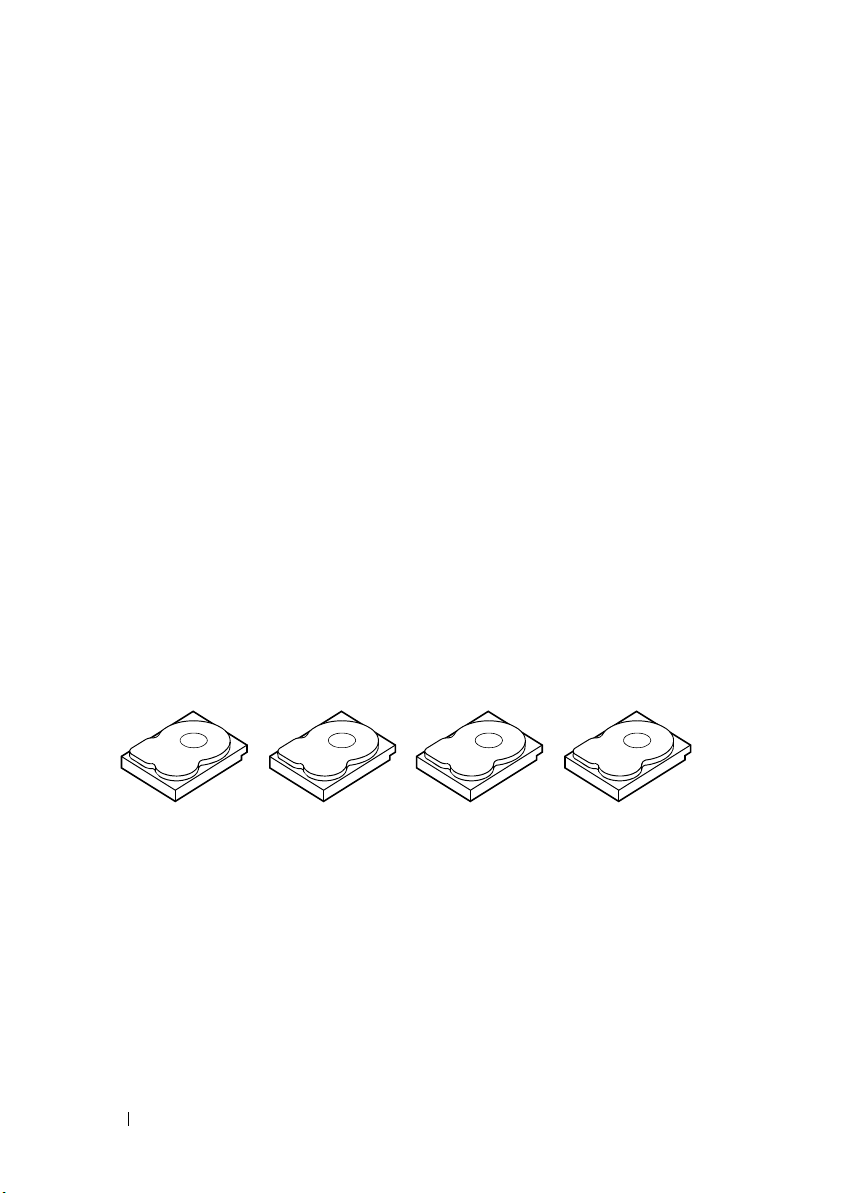
Disk Striping
Disk striping allows you to write data across multiple physical disks instead of
just one physical disk. Disk striping involves partitioning each physical disk
storage space in stripes of the following sizes: 8 KB, 16 KB, 32 KB, 64 KB,
128 KB, 256 KB, 512 KB, and 1024 KB. The stripes are interleaved in a
repeated sequential manner. The part of the stripe on a single physical disk
is called a stripe element.
For example, in a four-disk system using only disk striping (used in RAID 0),
segment 1 is written to disk 1, segment 2 is written to disk 2, and so on.
Disk striping enhances performance because multiple physical disks are
accessed simultaneously, but disk striping does not provide data redundancy.
Figure 2-1 shows an example of disk striping.
Figure 2-1. Example of Disk Striping (RAID 0)
18 Overview
Page 19
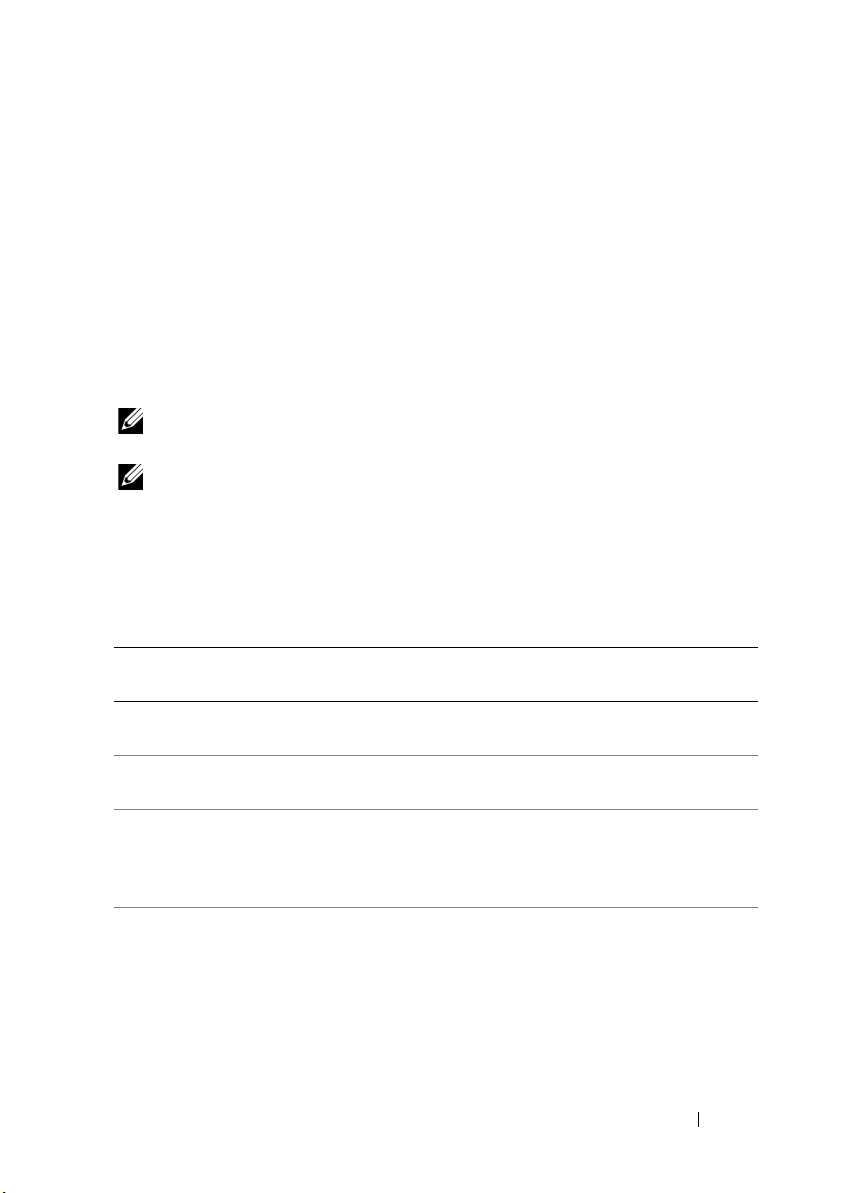
Disk Mirroring
Stripe element 1
Stripe element 2
Stripe element 3
Stripe element 1 Duplicated
Stripe element 2 Duplicated
Stripe element 3 Duplicated
Stripe element 4 Stripe element 4 Duplicated
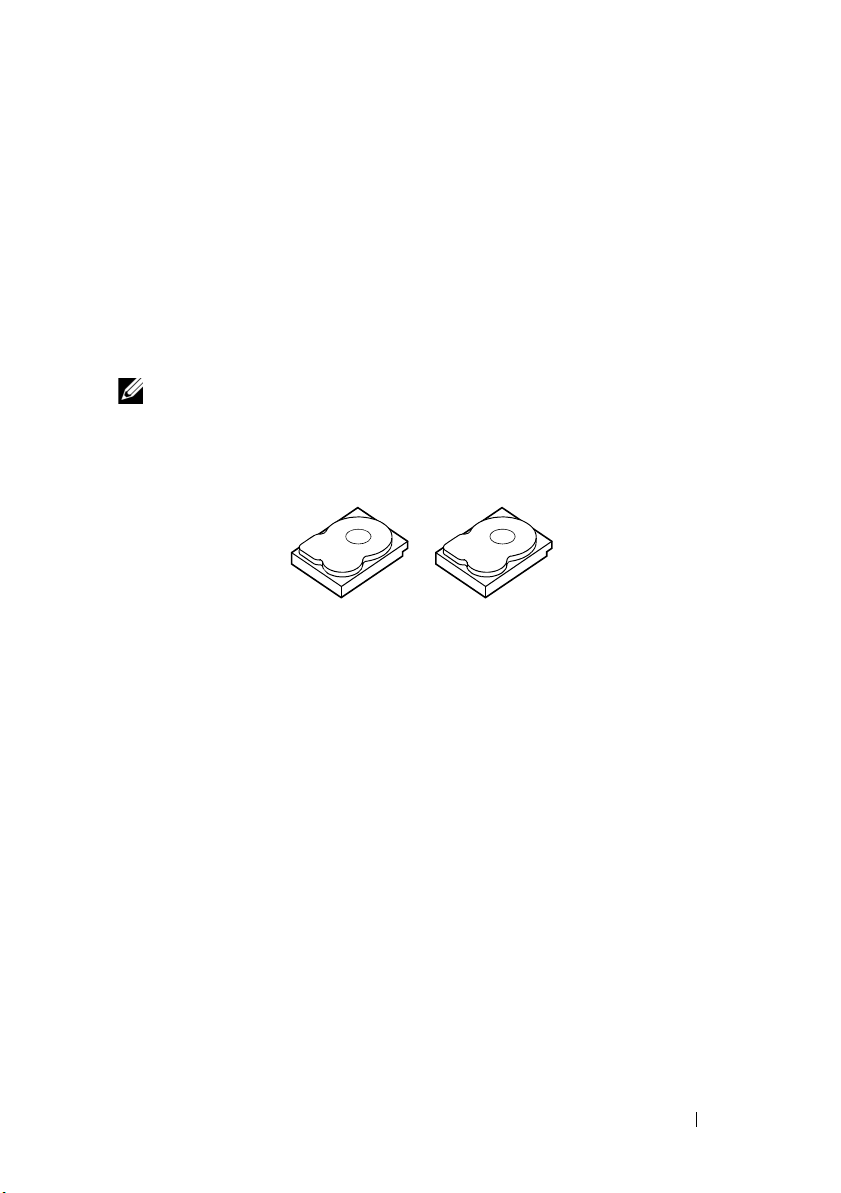
With mirroring (used in RAID 1), data written to one disk is simultaneously
written to another disk. If one disk fails, the contents of the other disk can
be used to run the system and rebuild the failed physical disk. The primary
advantage of disk mirroring is that it provides complete data redundancy.
Both disks contain the same data at all times. Either of the physical disks can
act as the operational physical disk.
Disk mirroring provides complete redundancy, but is an expensive option
because each physical disk in the system must be duplicated.
NOTE: Mirrored physical disks improve read performance by read load balance.
Figure 2-2 shows an example of disk mirroring.
Figure 2-2. Example of Disk Mirroring (RAID 1)
Spanned RAID Levels
Spanning is a term used to describe the way in which RAID levels 10, 50,
and 60 are constructed from multiple sets of basic, or simple RAID levels.
For example, a RAID 10 has multiple sets of RAID 1 arrays where each RAID 1
set is considered a span. Data is then striped (RAID 0) across the RAID 1
spans to create a RAID 10 virtual disk. Similarly, RAID 50 and RAID 60
combine multiple sets of RAID 5 or RAID 6 respectively with striping.
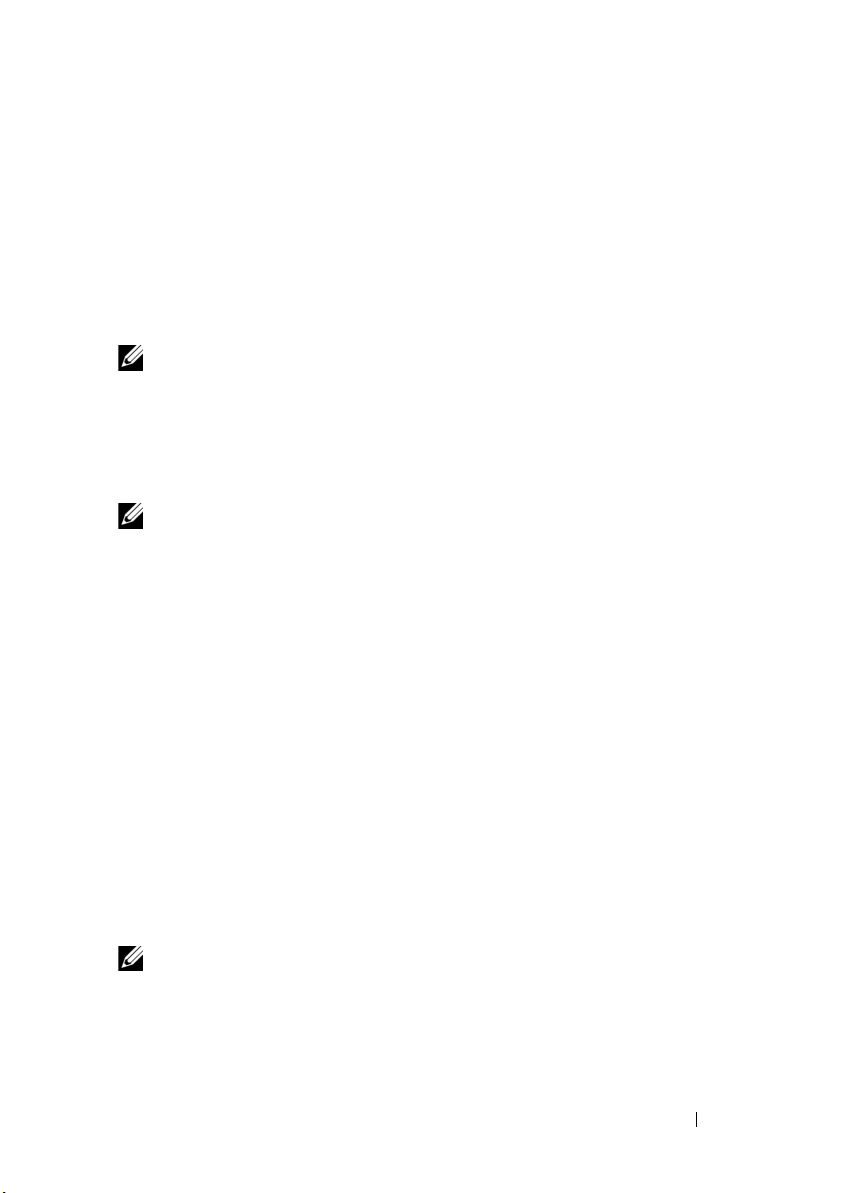
Parity Data
Parity data is redundant data that is generated to provide fault tolerance
within certain RAID levels. In the event of a disk failure the parity data can be
used by the controller to regenerate your data. Parity data is present for RAID
5, 6, 50, and 60.
Overview 19
Page 20
The parity data is distributed across all the physical disks in the system. If a
Stripe element 1
Stripe element 7
Stripe element 2
Stripe element 8
Stripe element 3
Stripe element 9
Stripe element 4
Stripe element 10
Stripe element 5
Parity (6–10)
Parity (11–15)
Parity (1–5)
Stripe element 6
Stripe element 12
Stripe element 15
Stripe element 11
Stripe element 14
Stripe element 13
Stripe element 19
Stripe element 25
Stripe element 20
Stripe element 23
Stripe element 18
Stripe element 21
Stripe element 16
Stripe element 22
Stripe element 17
Parity (21–25)
Parity (26–30)
Parity (16–20)
Stripe element 24
Stripe element 30
Stripe element 27 Stripe element 29
Stripe element 26
Stripe element 28
Stripe element 1
Stripe element 5
Stripe element 2
Stripe element 6
Stripe element 3
Parity (5–8)
Stripe element 4
Parity (5–8)
Parity (1–4)
Stripe element 7
Stripe element 10
Parity (1–4)
Stripe element 8
Stripe element 12
Stripe element 9
Stripe element 11
Parity (9–12)
Parity (9–12)
Stripe element 13 Stripe element 14 Stripe element 16Parity (13–16) Stripe element 15
Parity (13–16)
single physical disk fails, it can be rebuilt from the parity and the data on the
remaining physical disks. RAID level 5 combines distributed parity with disk
striping, as shown in Figure 2-3. Parity provides redundancy for one physical
disk failure without duplicating the contents of entire physical disks.
RAID 6 combines dual distributed parity with disk striping. This level of
parity allows for two disk failures without duplicating the contents of entire
physical disks.
Figure 2-3. Example of Distributed Parity (RAID 5)
NOTE: Parity is distributed across multiple physical disks in the disk group.
Figure 2-4. Example of Dual Distributed Parity (RAID 6)
NOTE: Parity is distributed across all disks in the array.
20 Overview
Page 21
3
Storage Controller Features
This section describes the features of the Dell PowerEdge RAID Controller
(PERC) H700 and H800 cards such as the configuration options, disk array
performance, RAID management utilities, and operating system software drivers.
The PERC H700 and H800 family of controllers support Dell-qualified
serial-attached SCSI (SAS) hard drives, SATA hard drives, and
solid-state drives (SSDs).
NOTE: Mixing SAS and SATA disks within a virtual disk is not supported.
Also, mixing hard drives and SSDs within a virtual disk is not supported.
NOTE: Mixing disks of different speed (10,000 rpm or 15,000 rpm) and bandwidth (3
Gbps or 6 Gbps) while maintaining the same drive type (SAS or SATA) and
technology (HDD or SSD) is supported.
Table 3-1 compares the hardware configurations for the PERC H700
andH800 cards.
Table 3-1. PERC H700 and H800 Card Comparisons
Specification PERC H700 Adapter PERC H700
Integrated
RAID Levels 0, 1, 5, 6, 10, 50, 60 0, 1, 5, 6, 10,
50, 60
Enclosures per
Port
Ports 2 x4 internal mini-
Processor Dell adapter SAS
N/A N/A N/A Up to 4
2 x4 internal
SAS wide ports
RAID-on-Chip, 8port with LSI 2108
chipset
mini-SAS
wide ports
Dell adapter
SAS RAIDon-Chip, 8port with LSI
2108 chipset
Storage Controller Features 21
PERC H700
Modular
0,1,5,6, and
a
10
1x4
integrated
SAS wide
port
Dell adapter
SAS RAIDon-Chip, 4lanes with
LSI 2108
chipset
PERC H800
Adapter
0, 1, 5, 6, 10, 50,
60
enclosures
2 x4 external
mini-SAS wide
ports
Dell adapter
SAS RAID-onChip, 8-port
with LSI 2108
chipset
Page 22

Table 3-1. PERC H700 and H800 Card Comparisons
Specification PERC H700 Adapter PERC H700
Integrated
BBU (Backup
Battery Unit)
Non-Volatile
Cache
Cache Memory 512 MB DDR2 or 1
Cache
Function
Maximum
Number of
Spans per Disk
Group
Maximum
Number of
Virtual Disks
per Disk Group
Multiple
Virtual Disks
per Controller
Support for x8
2.0 PCIe Host
Interface
Online
Capacity
Expansion
Optional Optional Yes Optional,
Optional Optional No Optional,
512 MB
GB DDR2
Wri t e - Back, WriteThrough, Adaptive
Read Ahead, NoRead Ahead, Read
Ahead
88 28
16 virtual disks per
disk group
Up to 64 virtual
disks per controller
Yes Yes Yes, x4 PCIe
Ye s Ye s Ye s Ye s
DDR2 or 1
GB DDR2
Write-Back,
Wri te Through,
Adaptive
Read Ahead,
No-Read
Ahead, Read
Ahead
16 virtual
disks per disk
group
Up to 64
virtual disks
per controller
PERC H700
Modular
512 MB
Integrated
DDR2
Write -B ack,
Write Through,
Adaptive
Read Ahead,
No-Read
Ahead, Read
Ahead
16 virtual
disks per disk
group
Up to 64
virtual disks
per
controller
2.0 for host
operation
PERC H800
Adapter
Tr a ns p o r ta b l e
Tr a ns p o r ta b l e
512 MB DDR2
or 1 GB DDR2
Write-Back,
Write-Through,
Adaptive Read
Ahead, No-Read
Ahead, Read
Ahead
16 virtual disks
per disk group
Up to 64 virtual
disks per
controller
Ye s
22 Storage Controller Features
Page 23

Table 3-1. PERC H700 and H800 Card Comparisons
Specification PERC H700 Adapter PERC H700
Integrated
Dedicated and
Ye s Ye s Ye s Ye s
PERC H700
Modular
PERC H800
Adapter
Global Hot
Spares
Hot Swap
Ye s Ye s Ye s Ye s
Devices
Supported
Enclosure Hot-
b
Add
Mixed
N/A N/A N/A Yes
Ye s Ye s Ye s Ye s
Capacity
Physical Disks
Supported
Hardware XOR
Ye s Ye s Ye s Ye s
Engine
Revertible Hot
Ye s Ye s Ye s Ye s
Spares
Supported
Redundant
N/A N/A N/A Yes
Pat h Support
Maximum
c
1
112
d
number of
controllers per
server
a. The RAID configurations are only supported on select Dell modular systems.
b. Using the enclosure Hot-Add feature, you can hot plug enclosures to the PERC H800 adapter
without rebooting the system.
c. Only one boot controller (PERC H700) is supported on a server, consult the system
determine which one is the appropriate boot controller on you system.
d. Only up to two PERC H800 controller for additional storages are supported on a system, this may
be further limited by the server specifications (number of PCIe slots). Consult the system
Guide
for specifications.
User’s Guide
User’s
to
NOTE: The maximum array size is limited by the maximum number of disks per span
(32), the maximum number of spans per disk group (8), and the size of the physical
disks (array and disk group terms are equivalent).
Storage Controller Features 23
Page 24

Physical Disk Power Management
The PERC H700 and H800 cards can be configured to spin down certain hard
drives after a set amount of time of inactivity to conserve power. This
power-savings feature is disabled by default and can be enabled in the Dell
OpenManage storage management application.
The power-savings feature can be enabled so that unconfigured disks, hot
spares, or both are spun down. The amount of time to wait to spin down these
disks can also be set. The minimum amount of time to wait that can be set is
30 minutes and the maximum is 1 day. The default is 30 minutes.
Disks that are spun down automatically, spin up when they are needed for
use. When a system is rebooted, all disks spin up.
Using the SMART Feature
The Self-Monitoring Analysis and Reporting Technology (SMART) feature
monitors the internal performance of all motors, heads, and physical disk
electronics to detect predictable physical disk failures. The SMART feature
helps monitor physical disk performance and reliability. SMART-compliant
physical disks have attributes for which data can be monitored to identify
changes in values and determine whether the values are within threshold
limits. Many mechanical and electrical failures display some degradation in
performance before failure.
A SMART failure is also referred to as a predicted failure. There are numerous
factors that relate to predicted physical disk failures, such as a bearing failure,
a broken read/write head, and changes in spin-up rate. In addition, there are
factors related to read/write surface failure, such as seek error rate and
excessive bad sectors. For information on physical disk status, see "Disk
Roaming" on page 26.
NOTE: For detailed information on SCSI interface specifications, see t10.org
and for detailed information on SATA interface specifications, see t13.org.
24 Storage Controller Features
Page 25
Initializing Virtual Disks
You can initialize the virtual disks as described in the following sections.
Background Initialization of Virtual Disks
Background Initialization (BGI) is an automated process that writes the
parity or mirror data on newly created virtual disks. BGI does not run on
RAID 0 virtual disks.
NOTE: You cannot disable BGI permanently. If you cancel BGI, it automatically
restarts within five minutes. For information on stopping BGI, see "Stopping
Background Initialization" on page 111.
You can control the BGI rate in the Dell OpenManage storage management
application. Any change in the BGI rate does not take effect until the next
BGI run.
NOTE: Unlike full or fast initialization of virtual disks, background initialization does
not clear data from the physical disks.
Consistency Check (CC) and BGI perform similar functions in that they
both correct parity errors. However, CC reports data inconsistencies through
an event notification, but BGI does not. You can start CC manually, but not
BGI.
Full Initialization of Virtual Disks
Performing a full initialization on a virtual disk overwrites all blocks and
destroys any data that previously existed on the virtual disk. Full initialization
of a virtual disk eliminates the need for the virtual disk to undergo a BGI.
Full initialization can be performed after the creation of a virtual disk.
During full initialization, the host is not able to access the virtual disk.
You can start a full initialization on a virtual disk by using the Slow Initialize
option in the Dell OpenManage storage management application. For more
information on using the BIOS Configuration Utility to perform a full
initialization, see "Initializing Virtual Disks" on page 91.
NOTE: If the system reboots during a full initialization, the operation aborts and
a BGI begins on the virtual disk.
Storage Controller Features 25
Page 26

Fast Initialization of Virtual Disks
A fast initialization on a virtual disk overwrites the first and last 8 MB of the
virtual disk, clearing any boot records or partition information. The operation
takes only 2–3 seconds to complete and is recommended when you are
recreating virtual disks. To perform a fast initialization using the BIOS
Configuration Utility, see "Initializing Virtual Disks" on page 91.
NOTE: Fast Initialization is automatically executed when a virtual disk is created
with Dell OpenManage storage management application.
Consistency Checks
Consistency Check (CC) is a background operation that verifies and corrects
the mirror or parity data for fault tolerant virtual disks. It is recommended
that you periodically run a consistency check on virtual disks.
You can manually start a CC using the BIOS Configuration Utility or the
Dell OpenManage storage management application. To start a CC using the
BIOS Configuration Utility, see "Checking Data Consistency" on page 91.
You can schedule CC to run on virtual disks using a Dell OpenManage
storage management application.
Disk Roaming
Disk roaming is moving the physical disks from one cable connection or
backplane slot to another on the same controller. The controller
automatically recognizes the relocated physical disks and logically places
them in the proper virtual disks that are part of the disk group. You can
perform disk roaming only when the system is turned off.
CAUTION: Do not attempt disk roaming during RAID level migration (RLM) or
online capacity expansion (OCE). This causes loss of the virtual disk.
Perform the following steps to use disk roaming:
Turn off the power to the system, physical disks, enclosures, and system
1
components. Disconnect power cords from the system.
2
Move the physical disks to desired positions on the backplane or
the enclosure.
3
Perform a safety check. Make sure the physical disks are inserted properly.
4
Turn on the system.
26 Storage Controller Features
Page 27
The controller detects the RAID configuration from the configuration
data on the physical disks.
Disk Migration
The PERC H700 and H800 cards support migration of virtual disks from
one controller to another without taking the target controller offline.
The controller can import RAID virtual disks in optimal, degraded,
or partially degraded states. You cannot import a virtual disk that is in
an offline state.
NOTE: The source controller must be offline prior to performing the disk migration.
NOTE: Disks cannot be migrated back to previous PERC RAID controllers.
NOTE: Importing secured virtual disks is supported as long as the appropriate key
(LKM) is supplied/configured.
When a controller detects a physical disk with an existing configuration,
it flags the physical disk as foreign, and generates an alert indicating that
a foreign disk was detected.
CAUTION: Do not attempt disk roaming during RLM or online capacity
expansion (OCE). This causes loss of the virtual disk.
Perform the following steps to use disk migration:
1
Turn off the system that contains the source controller.
2
Move the appropriate physical disks from the source controller to the
target controller.
The system with the target controller can be online while inserting the
physical disks.
The controller flags the inserted disks as foreign disks.
3
Use the Dell OpenManage storage management application or the
controller
BIOS Configuration Utility
to import the detected foreign
configuration.
4
Ensure that all physical disks that are part of the virtual disk are migrated.
NOTE: For more information about compatibility, contact your Dell technical
support representative.
Storage Controller Features 27
Page 28

Compatibility With Virtual Disks Created on PERC 6 and H200 Cards
Virtual disks that are created on the PERC 6 and H200 family of controllers
can be migrated to the PERC H700 and H800 cards without risking data
or configuration loss. Migrating virtual disks from the PERC H700 and
H800 cards to PERC 6 or H200 is not supported.
NOTE: For more information about compatibility, contact your Dell technical
support representative.
Migrating Virtual Disks From PERC 6 or H200 to PERC H700 and H800
To migrate virtual disks from PERC 6 or H200 to PERC H700 and H800:
1
Turn off the system.
2
Move the appropriate physical disks from the PERC 6 or H200 card to the
PERC H700 and H800 card. If you are replacing your PERC 6 or H200 card
with a PERC H700 or H800 card, see the
shipped with your system or at
3
Boot the system and import the foreign configuration that is detected.
support.dell.com/manuals
You can do this in two ways:
• Press <F> to automatically import the foreign configuration.
• Enter the
Configuration View
NOTE: For more information on accessing the BIOS Configuration Utility,
see "Entering the BIOS Configuration Utility" on page 82
NOTE: For more information on Foreign Configuration View, see "Foreign
Configuration View" on page 108.
4
Exit the
5
Ensure all the latest drivers for the PERC H700 or H800 card (available at
support.dell.com
BIOS Configuration Utility
.
BIOS Configuration Utility
) are installed. For more information, see "Driver
Installation" on page 69.
Hardware Owner’s Manual
.
and navigate to the
.
and reboot the system.
that
Foreign
28 Storage Controller Features
Page 29

Virtual Disk Write Cache Policies
The write cache policy of a virtual disk determines how the controller handles
writes to that virtual disk. Write-Back and Write-Throug h are the two write
cache policies and can be set on virtual disks individually.
All RAID volumes are presented as Write-Through (WT) to the operating
system (Windows and Linux) independent of the actual write cache policy of
the virtual disk. The PERC cards manage the data in cache independently of
the operating system or any applications. Use Dell OpenManage or the BIOS
Configuration Utility to view and manage virtual disk cache settings.
Write-Back and Write-Through
In Writ e-Throug h caching, the controller sends a data transfer completion
signal to the host system when the disk subsystem has received all the data
in a transaction.
In Writ e-Bac k caching, the controller sends a data transfer completion signal
to the host when the controller cache has received all the data in a
transaction. The controller then writes the cached data to the storage device
in the background.
The risk of using Writ e-Ba ck cache is that the cached data can be lost if
there is a power failure before it is written to the storage device. This risk is
mitigated by using a BBU on PERC H700 or H800 cards. For information
on which controllers support a BBU, see Table 3-1.
Write-Back caching has a performance advantage over Writ e-Thr oug h caching.
NOTE: The default cache setting for virtual disks is Write-Back caching.
NOTE: Certain data patterns and configurations perform better with a
Write-Through cache policy.
Conditions Under Which Write-Back is Employed
Writ e-B ack caching is used under all conditions in which the battery is
present and in good condition.
Storage Controller Features 29
Page 30

Conditions Under Which Write-Through is Employed
Write-Through caching is used under all conditions in which the battery is
missing or in a low-charge state. Low-charge state is when the battery is not
capable of maintaining data for at least 24 hours in the case of a power loss.
This low-charge state does not apply to controllers with the optional
non-volatile cache (NVC) module present.
Conditions Under Which Forced Write-Back With No Battery is Employed
Write-Back mode is available when you select Force WB with no battery.
When Forced Write-Back mode is selected, the virtual disk is in Write- Back
mode even if the battery is not present.
CAUTION: It is recommended that you use a power backup system when forcing
Write-Back to ensure there is no loss of data if the system suddenly loses power.
Virtual Disk Read Cache Policies
The read policy of a virtual disk determines how the controller handles reads
to that virtual disk. The read policies are:
•
Always Read Ahead — A
requested data and to store the additional data in cache memory,
anticipating that the data is required soon. This speeds up reads for
sequential data, but there is little improvement when accessing random
data.
•
No Read Ahead
•
Adaptive Read Ahead
disk accesses occurred in sequential sectors. If the read requests are
random, the controller reverts to
— Disables the
llows the controller to read sequentially ahead of
Read-Ahead
— Begins using
No Read Ahead
capability.
Read-Ahead
mode.
if the two most recent
NOTE: The default read cache setting for virtual disks is Adaptive Read Ahead.
30 Storage Controller Features
Page 31

Reconfiguring Virtual Disks
An online virtual disk can be reconfigured in ways that expands its capacity
and/or change its RAID level. Spanned virtual disks such as RAID 10, 50, and
60 cannot be reconfigured.
Online Capacity Expansion (OCE) can be done in two ways. The first way is
to expand the volume using free space already in the disk group. For example,
if there is a single virtual disk in a disk group and free space is available, the
virtual disk’s capacity can be expanded within that free space. If a virtual disk
is created and it does not use the maximum size of the disk group, free space
is available and OCE is possible. Free space is also available when a disk
group’s physical disks are replaced by larger disks using the Replace Member
feature. The second method by which OCE can be done is by adding physical
disks to the disk group and using OCE to incorporate free space from the
newly added disks into the virtual disk.
RAID Level Migration (RLM) refers to changing a virtual disk’s RAID level.
Both RLM and OCE can be done at the same time so that a virtual disk can
simultaneously have its RAID level changed and its capacity increased. When
a RLM/OCE operation is complete, a reboot is not required.For a list of
RLM/OCE possibilities, see Table 3-2. The source RAID level column
indicates the virtual disk RAID level before the RLM/OCE and the target
RAID level column indicates the RAID level after the operation has
completed.
NOTE: If you configure 64 virtual disks on a controller, you cannot perform a
RAID level migration or capacity expansion on any virtual disk.
NOTE: The controller changes the write cache policy of all virtual disks undergoing
a RLM/OCE to Write-Through until the RLM/OCE is complete.
Storage Controller Features 31
Page 32

Table 3-2. RAID Level Migration
Source
RAID
Level
RAID 0RAID 01 2 or more Yes Increases capacity by
RAID 0RAID 11 2 No Converts
RAID 0 RAID 5 1 or more 3 or more Yes At least one disk
RAID 0 RAID 6 1 or more 4 or more Yes At least two disks need
RAID 1RAID 02 2 or more Yes Removes redundancy
RAID 1 RAID 5 2 3 or more Yes Maintains redundancy
RAID 1RAID 62 4 or more Yes Two disks required to
RAID 5 RAID 0 3 or more 3 or more Yes Converts to a
RAID 5RAID 53 4 or more Yes Increases capacity by
Target
RAID
Level
Required
Number of
Physical Disks
(Beginning)
Number of
Physical
Disks (End)
Capacity
Expansion
Possible
Description
adding disks
non-redundant
virtual disk into a
mirrored virtual disk
by adding one disk.
needs to be added for
distributed parity data.
to be added for dual
distributed parity data.
while increasing
capacity.
while doubling
capacity.
be added for
distributed parity data.
non-redundant virtual
disk and reclaims
disk space used for
distributed parity data.
adding disks
32 Storage Controller Features
Page 33

Table 3-2. RAID Level Migration
(continued)
Source
RAID
Level
RAID 5 RAID 6 3 or more 4 or more Yes At least one disk needs
RAID 6 RAID 0 4 or more 4 or more Yes Converts to a
RAID 6 RAID 5 4 or more 4 or more Yes Removes one set of
RAID 6 RAID 6 4 5 or more Yes Increases capacity by
Target
RAID
Level
NOTE: The total number of physical disks in a disk group cannot exceed 32. You
cannot perform RAID level migration and/or expansion on RAID levels 10, 50, and
60.
Required
Number of
Physical Disks
(Beginning)
Number of
Physical
Disks (End)
Capacity
Expansion
Possible
Description
to be added for dual
distributed parity data.
non-redundant
virtual disk and
reclaims disk space
used for distributed
parity data.
parity data and
reclaims disk space
used for it.
adding disks
Fault Tolerance Features
The list of features of the controller cards that provide fault tolerance to
prevent data loss is as follows:
• Support for SMART
• Support for Patrol Read
• Redundant path support (for PERC H800 only)
• Physical disk failure detection
• Physical disk rebuild using hot spares
• Parity generation and checking (for RAID 5, 50, 6, and 60 only)
Storage Controller Features 33
Page 34

• Battery and optional Non-Volatile Cache backup of controller cache to
protect data
• Detection of batteries with low charge after boot up
The next sections describe some methods to achieve fault tolerance.
Using Persistent Hot Spare Slots
The H700 and H800 cards can be configured so that system backplane or
storage enclosure disk slots are dedicated as hot spare slots. This feature can
be enabled using the Dell OpenManage storage management application.
Once enabled, any slots with hot spares configured automatically become
persistent hot spare slots. If a hot spare disk fails or is removed, a replacement
disk that is inserted into the same slot automatically becomes a hot spare with
the same properties as the one it is replacing. If the replacement disk does not
match the disk protocol and technology, it does not become a hot spare.
NOTE: Any hot spares assigned to an encrypted Virtual Disk must also be capable
of encryption (SED).
Physical Disk Hot Swapping
Hot swapping is the manual replacement of a disk while the H700 and H800
cards are online and performing their normal functions.
The following requirements must be met before hot swapping a physical disk:
• The system backplane or enclosure must support hot swapping for the
PERC H700 and H800 cards to support hot swapping.
• The replacement disk must be of the same protocol and disk technology.
For example, only a SAS hard drive can replace a SAS hard drive; only a
SATA SSD can replace a SATA SSD.
• The replacement disk must be of equal or greater capacity than the one
it is replacing.
Failed Physical Disk Detection
Failed physical disks are detected and rebuilds automatically start to new
disks that are inserted into the same slot. Automatic rebuilds can also happen
transparently with hot spares. If you have configured hot spares, the
controllers automatically try to use them to rebuild failed physical disks.
34 Storage Controller Features
Page 35

Redundant Path With Load Balancing Support
The PERC H800 adapter can detect and use redundant paths to disks
contained in enclosures. This provides the ability to connect two SAS cables
between a controller and an enclosure for path redundancy. The controller is
able to tolerate the failure of a cable or Enclosure Management
Module (EMM) by utilizing the remaining path.
When redundant paths exist, the controller automatically balances I/O load
through both paths to each disk. Load balancing increases throughput to
virtual disks in storage enclosures and is automatically turned on when
redundant paths are detected. The ability to load balance I/O can be disabled
using the Dell OpenManage storage management application. To set up your
hardware to support redundant paths, see "Setting up Redundant Path
Support on the PERC H800 Adapter" on page 64.
NOTE: The hardware support for redundant paths refer to path-redundancy only
and not to controller-redundancy.
Using Replace Member and Revertible Hot Spares
The Replace Member functionality allows a previously commissioned hot
spare to be reverted to a usable hot spare. When a disk failure occurs within
a virtual disk, an assigned hot spare (dedicated or global) is commissioned
and begins rebuilding until the virtual disk is optimal. After the failed disk is
replaced (in the same slot) and the rebuild to the hot spare is complete,
the controller automatically starts to copy data from the commissioned hot
spare to the newly-inserted disk. After the data is copied, the new disk is a
part of the virtual disk and the hot spare is reverted to being a ready hot spare.
This allows hot spares to remain in specific enclosure slots. While the
controller is reverting the hot spare, the virtual disk remains optimal.
NOTE: The controller automatically reverts a hot spare only if the failed disk is
replaced with a new disk in the same slot. If the new disk is not placed in the same
slot, a manual Replace Member operation can be used to revert a previously
commissioned hot spare.
Storage Controller Features 35
Page 36

Automatic Replace Member with Predicted Failure
A Replace Member operation can occur when there is a SMART predictive
failure reporting on a physical disk in a virtual disk. The automatic Replace
Member is initiated when the first SMART error occurs on a physical disk
that is part of a virtual disk. The target disk needs to be a hot spare that
qualifies as a rebuild disk. The physical disk with the SMART error is marked
as failed only after the successful completion of the Replace Member. This
avoids putting the array in degraded status.
If an automatic Replace Member occurs using a source disk that was
originally a hot spare (that was used in a rebuild), and a new disk added for
the Replace Member operation as the target disk, the hot spare reverts to the
hot spare state after a successful Replace Member operation.
NOTE: To enable the automatic Replace Member, use the Dell OpenManage
storage management application. For more information on automatic Replace
Member, see "Dell OpenManage Storage Management" on page 81.
NOTE: For information on manual Replace Member, see "Replacing an Online
Physical Disk" on page 110.
Controller Cache Preservation
The controller is capable of preserving its cache in the event of a system
power outage or improper system shutdown. The PERC H700 controllers are
attached to a Battery Backup Unit (BBU) that provides backup power during
system power loss to preserve the controller's cache data. The PERC H800 has
a transportable version of the BBU attached to it called the Transportable
Battery Backup Unit (TBBU) which enables the entire cache module to be
transported to a new controller if necessary. If the card has the optional nonvolatile cache (NVC) or transportable non-volatile cache (TNVC) module,
the cache data is preserved using flash storage instead of battery power.
36 Storage Controller Features
Page 37

Cache Preservation With Battery
The lithium-ion battery included in the BBU/TBBU of the controller is an
inexpensive way to protect data in cache memory. If the controller has data in
cache memory during a power outage or improper system shutdown, battery
power is used to preserve cache data until power is restored or the battery is
depleted. Under the 1-year limited warranty, the battery provides at least 24
hours of backup power coverage in normal operating conditions during the
warranty period. To prolong battery life, do not store or operate the battery in
temperatures that exceed 60 degrees C.
Cache Preservation With Non-Volatile Cache (NVC)
The NVC module allows controller cache data to be stored indefinitely, an
advantage over the 24 hours that battery backup provides. If the controller
has data in cache memory during a power outage or improper system
shutdown, a small amount of power from a battery is used to transfer cache
data to non-volatile flash storage where it remains until power is restored and
the system is booted.
Cache Data Recovery
The dirty cache LED that is located on the H700 and H800 cards cannot be
used to determine if cache data is being preserved. If a system power loss or
improper system shutdown has occurred, restore system power and boot the
system. During the boot, enter the controller's BIOS Configuration Utility
(<Ctrl><R>) to ensure that there is no cache data being preserved. This
can be done by entering into the controller menu and selecting Managed
Preserved Cache. If there are no virtual disks listed here, all preserved cache
data has been written to disk successfully.
In the event of a PERC H800 card failure, the entire TBBU/TNVC module
can be safely transferred to a new PERC H800 card without putting preserved
cache data at risk. See the applicable sections in "Installing and Configuring
Hardware" on page 41 for instructions on removing and installing the
TBBU/TNVC, then follow the instructions above on recovering cache data.
Storage Controller Features 37
Page 38

Battery Learn Cycle
Learn cycle is a battery calibration operation performed by the controller
periodically to determine the condition of the battery. This operation
cannot be disabled.
NOTE: Virtual disks automatically switch to Write-Through mode when the battery
charge is low because of a learn cycle.
Learn Cycle Completion Time Frame
The time frame for completion of a learn cycle is a function of the battery
charge capacity and the discharge/charge currents used. For PERC H700 or
H800 cards, the expected time frame for completion of a learn cycle is
approximately seven hours and consists of the following parts:
• Learn cycle discharge: approximately three hours
• Learn cycle charge: approximately four hours
NOTE: For additional information, see the Dell OpenManage storage management
application.
During the discharge phase of a learn cycle, the PERC H700 or H800 battery
charger is disabled and remains disabled until the battery is discharged.
After the battery is discharged, the charger is re-enabled.
Patrol Read
The Patrol Read feature is designed as a preventative measure to ensure
physical disk health and data integrity. Patrol Read scans for and resolves
potential problems on configured physical disks. The Dell OpenManage
storage management application can be used to start Patr ol Read and
change its behavior.
The following is an overview of Patrol Read behavior:
•
Patrol Re a d
part of a virtual disk, including hot spares.
•
Patrol Re a d
or are in
38 Storage Controller Features
runs on all disks on the controller that are configured as
does not run on physical disks that are not part of a virtual disk
Ready
state.
Page 39
•
Pat rol Read
Pat rol Re ad
if the system is busy processing I/O operation, then
adjusts the amount of controller resources dedicated to
operations based on outstanding disk I/O. For example,
Patrol Re a d
uses
fewer resources to allow the I/O to take a higher priority.
•
Pat rol Read
does not run on any disks involved in any of the
following operations:
–Rebuild
– Replace Member
– Full or Background Initialization
–CC
–RLM or OCE
NOTE: By default, Patrol Read automatically runs every seven days on configured
SAS and SATA hard drives. Patrol Read is not necessary on SSD and is disabled by
default.
Storage Controller Features 39
Page 40

40 Storage Controller Features
Page 41

Installing and Configuring Hardware
WARNING: All work must be performed at an Electrostatic Discharge (ESD)-safe
workstation to meet the requirements of EIA-625-Requirements For Handling
Electrostatic Discharge Sensitive Devices. All actions must be performed
following the IPC-A-610 latest revision ESD recommended practices.
CAUTION: Many repairs may only be done by a certified service technician.
You should only perform troubleshooting and simple repairs as authorized in
your product documentation, or as directed by the online or telephone service and
support team. Damage due to servicing that is not authorized by Dell is not
covered by your warranty. Read and follow the safety instructions that came
with the product.
NOTE: For complete information on U.S. Terms and Conditions of Sale, Limited
Warranties and Returns, Export Regulations, Software License Agreement, Safety,
Environmental and Ergonomic Instructions, Regulatory Notices, and Recycling
Information, see the
End User License Agreement
that shipped with your system.
Safety, Environmental and Regulatory Information
(EULA), and
Warranty and Support Information
(SERI),
4
(WSI)
Installing the PERC H700 and H800 Adapters
1
Unpack the Dell PowerEdge RAID Controller (PERC) and check
for damage.
NOTE: Contact Dell technical support if the controller is damaged.
2
Turn off the system and attached peripherals, and disconnect the system
from the electrical outlet. For more information on preparing your system
for hardware changes, see the
your system or at:
3
Disconnect all attached devices and remove the system cover.
For more information on opening the system, see your system’s
Hardware Owner’s Manual
4
Select an empty PCI-E slot. Remove the blank filler bracket on the back of
the system aligned with the PCI-E slot you have selected.
support.dell.com/manuals
Hardware Owner’s Manual
.
.
Installing and Configuring Hardware 41
shipped with
Page 42

NOTE: The PERC H700 Integrated and H700 Modular cards have a dedicated
1
2
3
4
storage slot. For details on the correct PCI-E location, see the
Owner's Manual
documentation available at support.dell.com/manuals.
5
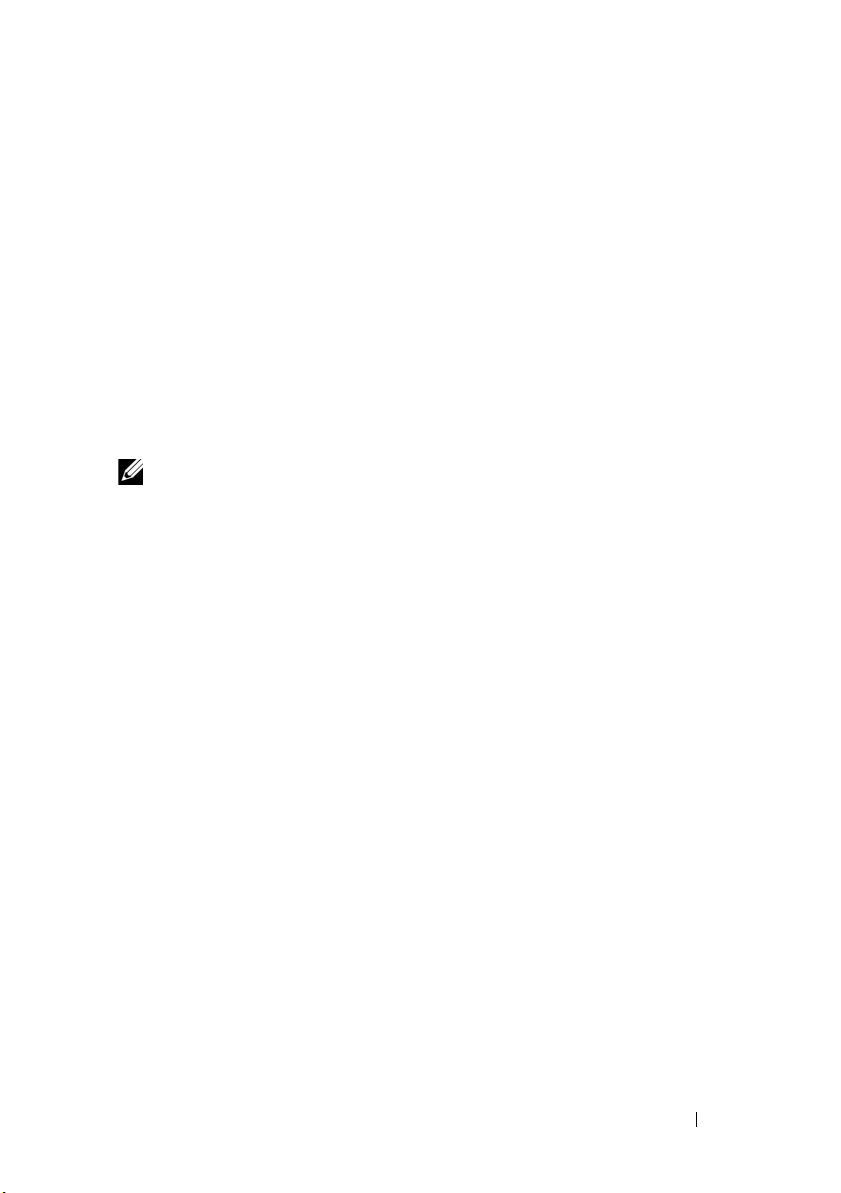
Align the PERC H700 or H800 card to the PCI-E slot you have selected.
CAUTION: Never apply pressure to the adapter module while inserting it in the
PCI-E slot. Applying pressure could break the adapter module.
6
Insert the controller gently, but firmly, until the controller is firmly seated
that shipped with your system or see the appropriate
Hardware
in the PCI-E slot. For more information on installing the PERC H800
adapter, see Figure 4-1. For more information on installing the PERC
H700 adapter, see Figure 4-2.
Figure 4-1. Installing a PERC H800 Adapter
1 PCI-e slot 2 PERC H800 adapter
3 filler bracket 4 bracket screw
42 Installing and Configuring Hardware
Page 43
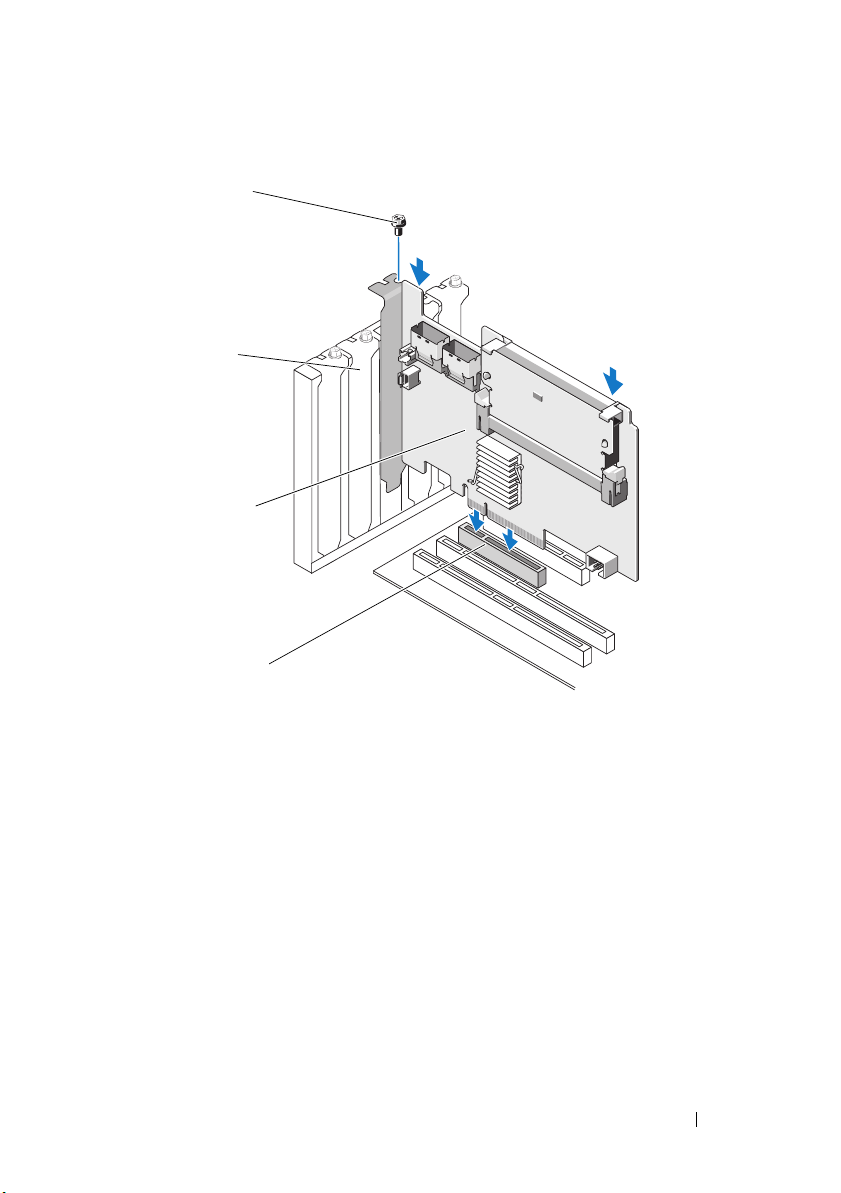
Figure 4-2. Installing a PERC H700 Adapter
4
3
1
2
1 PCI-e slot 2 PERC H700 adapter
3 filler brackets 4 bracket screw
7
Tighten the bracket screw, if any, or use the system’s retention clips
to secure the controller to the system’s chassis.
8
Replace the cover of the system. For more information on closing the
system, see the
support.dell.com/manuals
9
For the PERC H800 adapter, connect the cable from the external enclosure
Hardware Owner’s Manual
.
shipped with your system or at
to the controller. For more information, see Figure 4-3.
Installing and Configuring Hardware 43
Page 44

Figure 4-3. Connecting the Cable From the External Enclosure
2
3
1
1 connector on the controller 2 cable from the external enclosure
3system
10
For the PERC H700 adapter, connect the cables from the backplane of the
system to the controller. The primary SAS connector is labeled
the secondary SAS connector is labeled
SAS_B
. For more information, see
SAS_A
Figure 4-4.
and
44 Installing and Configuring Hardware
Page 45

Figure 4-4. Connecting Cables to the Controller
1
4
5
2
3
1 cable 2 Port B
3 Port A 4 PERC H700 adapter
5 connector
11
Replace the cover of the system. For more information on closing the
system, see the
support.dell.com/manuals
12
Reconnect the power and network cables, and turn on the system.
Hardware Owner’s Manual
.
shipped with your system or at
Installing and Configuring Hardware 45
Page 46

Removing the PERC H700 and H800 Adapters
NOTE: In the event that the SAS cable is accidentally pulled out when the
system is operational, reconnect the cable and see the online help of
your Dell OpenManage storage management application for the required recovery
steps.
NOTE: Before beginning with the procedure, press <Ctrl><R> when the system is
booting to verify that no cache is preserved.
1
Perform a controlled reboot of the system and enter the
Configuration Utility
to ensure that there is no data present in cache. See
the "Cache Data Recovery" on page 37 for more details. Later, perform a
controller shutdown of the system as well as any attached storage
controllers.
2
Disconnect the system from the electrical outlet and remove the system
cover.
CAUTION: Running a system without the system cover installed may cause
damage due to improper cooling.
NOTE: For more information on removing peripherals installed in the system’s
PCI-E slots, see the
support.dell.com/manuals.
Hardware Owner’s Manual
shipped with your system or at
For instructions on removing a PERC H800 adapter, go to step 3.
For instructions on removing a PERC H700 adapter, go to step 5.
3
Locate the PERC H800 adapter in the system and disconnect the
external cables from the adapter.
4
Remove any retention mechanism, such as a bracket screw, that may
be holding the PERC H800 in the system and gently lift the controller
from the system’s PCI-E slot. For more information, see Figure 4-5.
PERC BIOS
46 Installing and Configuring Hardware
Page 47

Figure 4-5. Removing the PERC H800 Adapter
5
4
2
1
3
1 bracket screw 2 memory module
3 battery 4 Dirty Cache LED
5 PERC H800 Adapter
5
Disconnect the data cables and battery cable from the PERC H700.
Remove any retention mechanism, such as a bracket screw, that might
be holding the PERC H700 in the system, and gently lift the controller
from the system’s PCI-E slot.
Installing and Configuring Hardware 47
Page 48
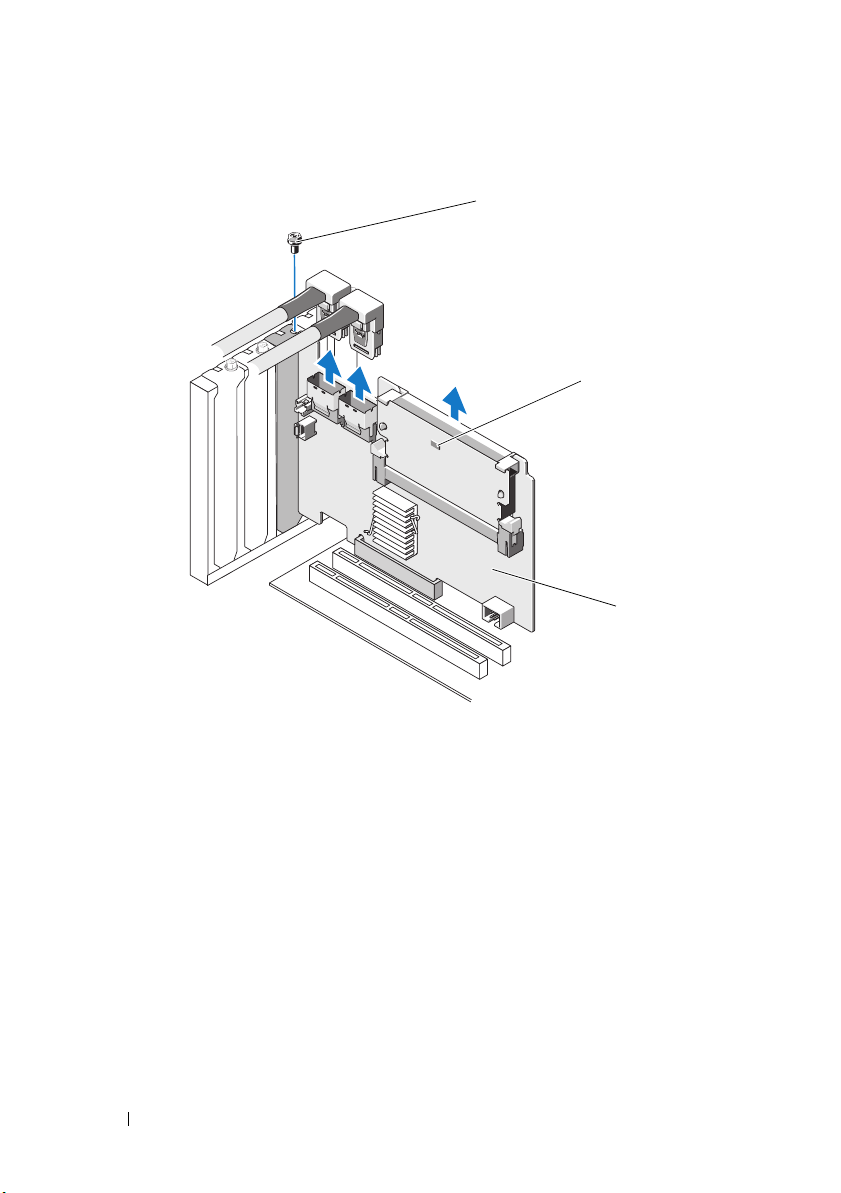
Figure 4-6. Removing the PERC H700 Adapter
3
1
2
1 bracket screw 2 Dirty Cache LED
3 PERC H700 controller
48 Installing and Configuring Hardware
Page 49

Removing and Installing the PERC H700 Modular Card in Dell Blade Systems
NOTE: For more information on removing and installing blade system parts, see
your system’s
website at support.dell.com.
The storage controller card is located below the disk bays of the Dell Blade
system.
To remove the storage controller card:
1
Remove the Dell Blade system from the Blade system chassis.
2
Remove the system cover of the Blade system.
3
Remove the system board and place it on a stable and flat surface.
4
Determine whether the dirty cache LED on the controller is illuminated.
For location of the LED, see Figure 4-7.
If the LED is illuminated, re-insert the system board, replace the system
cover, reconnect the system to power, turn on the system, and repeat step 1
through step 3. If the LED is not illuminated, continue with the next step.
5
Open the release lever to disconnect the storage controller card edge
connector from the system board connector as illustrated in Figure 4-7.
6
Lift the storage controller card straight up from the system board as
illustrated in Figure 4-7.
Hardware Owner’s Manual
or the
User’s Guide
from the Dell Support
Installing and Configuring Hardware 49
Page 50

Figure 4-7. Removing and Installing the Storage Controller Card
2
3
1
4
1 battery cable connector 2 storage controller card
3 release lever 4 dirty cache LED
To install your new storage controller card:
1
Unpack the new storage controller card and check for damage.
NOTE: If the card is damaged, contact Dell technical support.
2
Place the storage controller card onto the system board. Align the storage
controller card such that the tabs on the system board tray fit through the
notches on the edges of the storage controller card.
3
Slide the storage controller card towards the connector on the system
board until the storage controller clicks in place.
4
Reinstall the system board. For more information on reinstalling
the system board, see your system’s
the
User’s Guide
.
50 Installing and Configuring Hardware
Hardware Owner’s Manual
or
Page 51

5
Close the top cover of the Blade system. For more information on closing
the top cover of the Modular Blade system, see your system’s
Owner’s Manual
6
Reinstall the Blade system in the Blade system chassis. For more
or the
User’s Guide
.
Hardware
information on reinstalling the Blade system in the Blade system chassis,
see your system’s
NOTE: For the latest list of firmware and installation instructions, see the
Dell Support website at support.dell.com.
Hardware Owner’s Manual
or the
User’s Guide
Removing the DIMM From a PERC H700
CAUTION: PERC H700 Modular cards, shipped in PowerEdge blade systems,
have an integrated DIMM module which cannot be removed. Do not attempt
the following procedure on a PERC H700 Modular controller card.
1
Perform a controlled reboot of the system and enter the
BIOS Configuration Utility
to ensure that there is no data present in
cache. See the "Cache Data Recovery" on page 37 for more details. Later,
shut down the system.
WARNING: Running a system without the system cover installed may cause
damage due to improper cooling.
2
Disconnect the system from the electrical outlet and remove the
system cover.
NOTE: The location of the PERC H700 controller varies from system to system.
For more information on PERC H700 location, see the
Manual
that shipped with your system or see the appropriate documentation
available at support.dell.com/manuals.
3
Remove the PERC H700 from the system. See "Removing the PERC H700
and H800 Adapters" on page 46.
4
Remove the
DIMM
DIMM
by pressing down on the tabs at each edge of the
connector and lift the
DIMM
off the controller. See Figure 4-8.
PERC H700
Hardware Owner's
.
NOTE: Do not exert excessive pressure on the connector of the DIMM while
removing the DIMM.
Installing and Configuring Hardware 51
Page 52

Figure 4-8. Removing the DIMM From a PERC H700
1
2
5
3
4
1 DIMM support 2 dirty cache LED
3 DIMM 4 tab
5 PERC H700 Adapter
52 Installing and Configuring Hardware
Page 53

Installing the DIMM on a PERC H700
1
2
CAUTION: PERC H700 Modular cards, shipped in PowerEdge blade systems,
have an integrated DIMM module which cannot be removed. Do not attempt the
following procedure on a PERC H700 Modular controller card.
1
Unpack the DIMM and follow all antistatic procedures.
NOTE: Do not use excessive pressure on the connector on the DIMM while
installing the DIMM.
2
If the DIMM support is not mounted onto the DIMM, perform the
following steps to replace the DIMM support before mounting on a
PERC H700:
a
With the old DIMM removed from the controller, press out on
the DIMM support clips inserted through the DIMM rotating the
DIMM support out of the DIMM. See Figure 4-9.
Figure 4-9. Removing the DIMM Support From the DIMM
1 DIMM 2 DIMM support
To mount, place the top edge of the DIMM support over the top edge
b
of the DIMM so that the arms on the side of the DIMM support fit
into their sockets on the DIMM. See Figure 4-10.
Installing and Configuring Hardware 53
Page 54

Figure 4-10. Mounting the DIMM Support onto the DIMM
1
2
1 DIMM 2 DIMM support
3
Align the keyed edge of the
DIMM
to the physical divider on the memory
socket to avoid damage to the module.
4
Insert the DIMM in the memory socket. Apply a constant, downward
pressure on both ends or the middle of the DIMM until the retention clips
fall in the allotted slots on either side of the DIMM. See Figure 4-11.
54 Installing and Configuring Hardware
Page 55
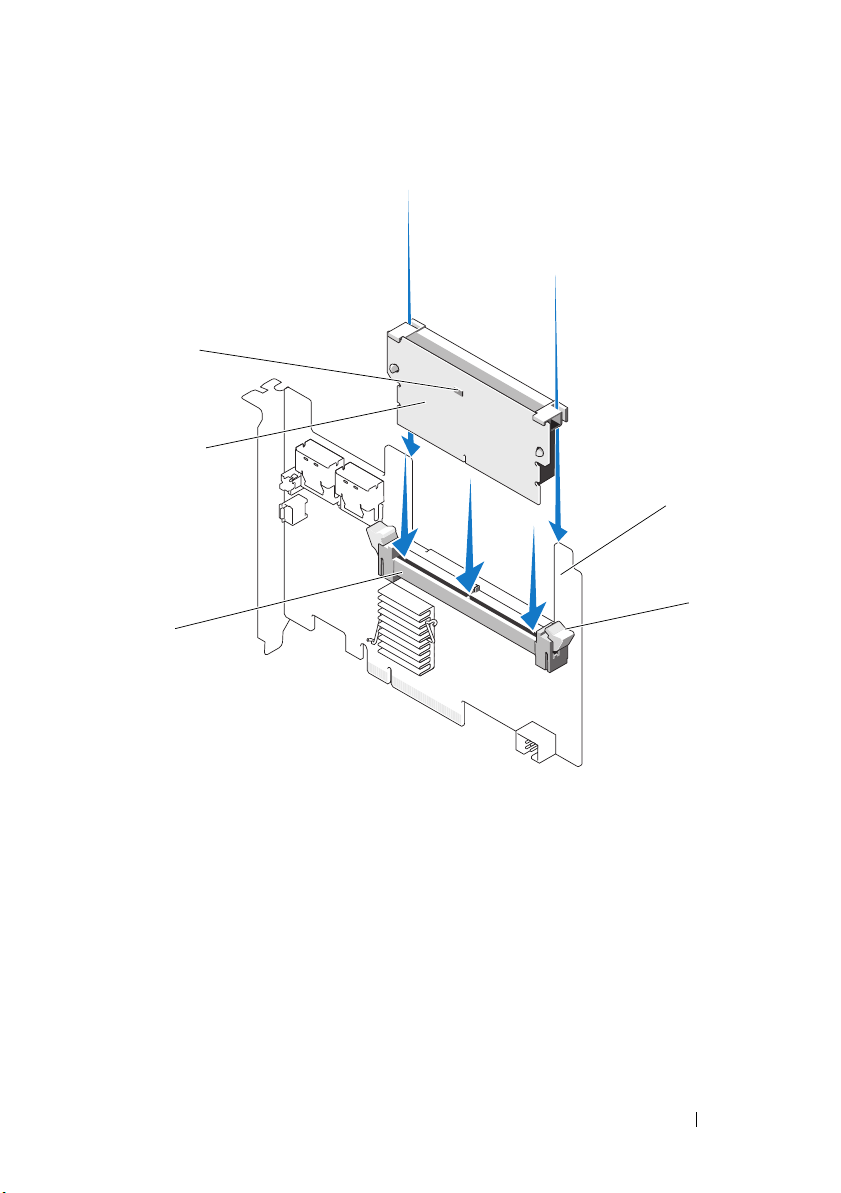
Figure 4-11. Installing a DIMM on a PERC H700
1
2
3
4
5
1 PERC H700 2 retention clip
3 memory socket 4 DIMM
5 dirty cache LED
Installing and Configuring Hardware 55
Page 56

Replacing the BBU on a PERC H700
1
2
3
1
Perform a controlled reboot of the system and enter the
BIOS Configuration Utility
to ensure that there is no data present in
cache. See the "Cache Data Recovery" on page 37 for more details. Later,
shut down the system.
WARNING: Running a system without the system cover installed may cause
damage due to improper cooling.
2
Disconnect the system from the electrical outlet and remove the
system cover.
NOTE: The locations of the PERC H700 and BBU vary from system to system.
For more information on PERC H700 card and BBU locations, see the
Hardware Owner’s Manual
documentation available at support.dell.com/manuals.
Figure 4-12. Dirty Cache LED and Battery Cable Connector
shipped with your system or see the appropriate
PERC H700
1 battery cable connector 2 PERC H700 Adapter
3 dirty cache LED
56 Installing and Configuring Hardware
Page 57

Figure 4-13. PERC H700 (Modular) Dirty Cache LED Location
2
1
3
1 battery cable connector 2 dirty cache LED
3 PERC H700 Modular Adapter
3
Locate the battery cable connection near the edge of the controller,
and disconnect the battery. For the location of the battery cable connector,
see Figure 4-12 and Figure 4-13.
4
Remove the battery from the plastic mounting shroud in your system and
disconnect the battery cable. For more information on the location of the
BBU in your system and instructions on how to replace the BBU, see the
Hardware Owner’s Manual
NOTE: Connect the battery cable to the new BBU before mounting it to the
plastic shroud in your system.
5
Re-connect the battery to the controller by inserting the end of the battery
that shipped with the system.
cable into the connector on the controller.
NOTE: Do not exert excessive pressure connecting the cable. It is a keyed
connector and it fits only one way.
Installing and Configuring Hardware 57
Page 58

Removing the TBBU or TNVC From a PERC H800 Adapter
NOTE: Both the TBBU and TNVC on the PERC H800 Adapter consists of the DIMM
and a battery.
1
Perform a controlled reboot of the system and enter the
Configuration Utility
"Cache Data Recovery" on page 37 for more details. Later, perform a
controller shutdown of the system as well as any attached storage
controllers.
2
Disconnect the system from the electrical outlet and remove the system
cover.
3
Remove the
see "Removing the PERC H700 and H800 Adapters" on page 46.
4
Press down on the tabs at each edge of the DIMM slot and lift the TBBU
or TNVC assembly off the PERC H800 Adapter. See Figure 4-14.
PERC H800
to ensure that there is no data present in cache. See
Adapter from the system. For more information,
PERC BIOS
58 Installing and Configuring Hardware
Page 59
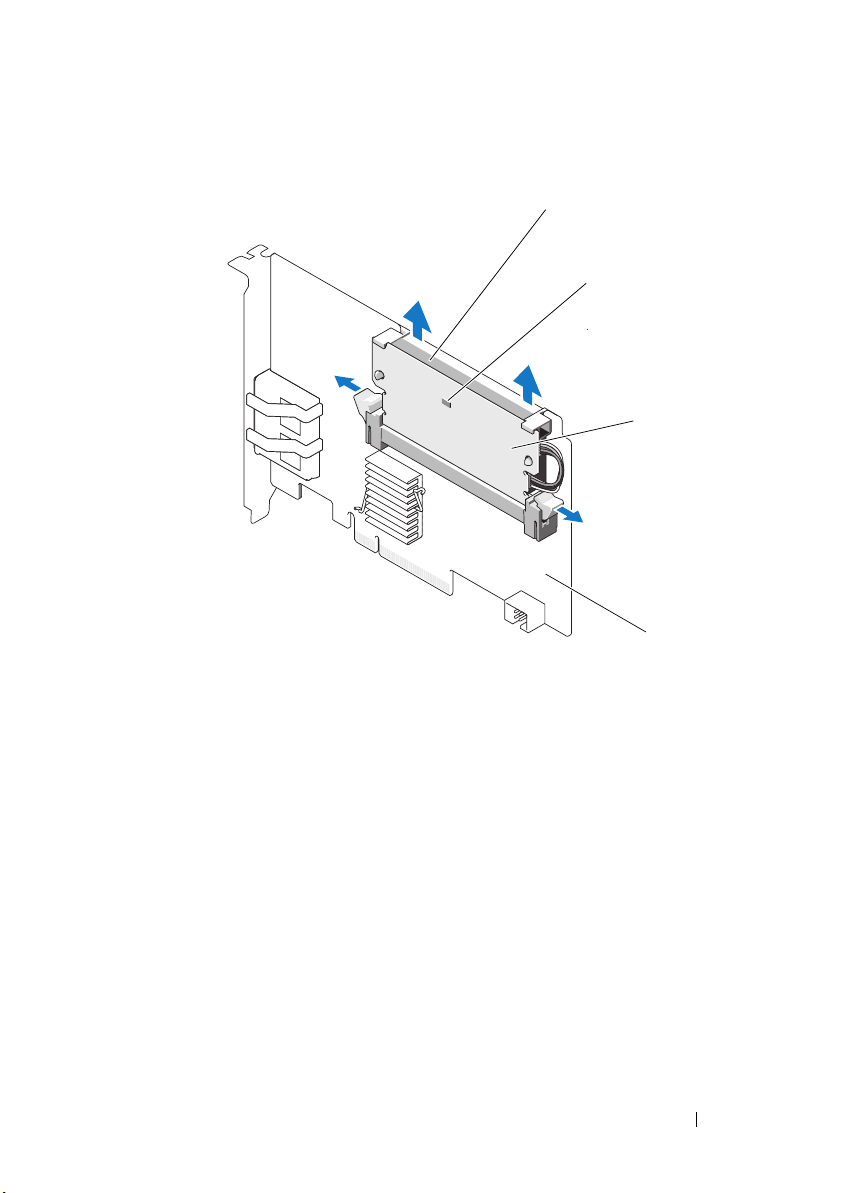
Figure 4-14. Removing the TBBU From a PERC H800 Adapter
1
2
4
3
1 battery 2 dirty cache LED
3 DIMM 4 PERC H800 Adapter
Installing and Configuring Hardware 59
Page 60

Replacing the Battery and Battery Cable Onto the
2
1
DIMM of a PERC H800 Adapter
1
With the old TBBU or TNVC removed from the controller, disconnect the
battery cable from both ends and press out on the battery clips inserted
through the DIMM rotating the battery out of the DIMM. See
Figure 4-15.
Figure 4-15. Removing the Battery and Battery Cable From a PERC H800 Adapter
1 DIMM 2 battery
2
Unpack the new TBBU or TNVC and follow all antistatic procedures.
3
Insert one end of the battery cable into the connector on the
the other end into the connector on the new battery.
NOTE: Do not exert excessive pressure connecting the cable. It is a keyed
connector and it fits only one way.
4
Place the top edge of the battery over the top edge of the
the arms on the side of the battery fit into their sockets on the
See Figure 4-16.
60 Installing and Configuring Hardware
DIMM
DIMM
so that
DIMM
and
.
Page 61

Figure 4-16. Installing the Battery and Battery Cable onto the DIMM
2
1
3
4
5
1 connector on the DIMM 2 DIMM
3 battery 4 connector on the battery
5 battery cable
Installing the TBBU or TNVC on a PERC H800 Adapter
NOTE: Both the TBBU and TNVC on the PERC H800 Adapter consists of the DIMM
and a battery.
1
Check the battery attachment to the DIMM and battery cable connection.
For more information, see "Replacing the Battery and Battery Cable Onto
the DIMM of a PERC H800 Adapter" on page 60.
CAUTION: Do not touch the gold leads and do not bend the memory module.
Installing and Configuring Hardware 61
Page 62
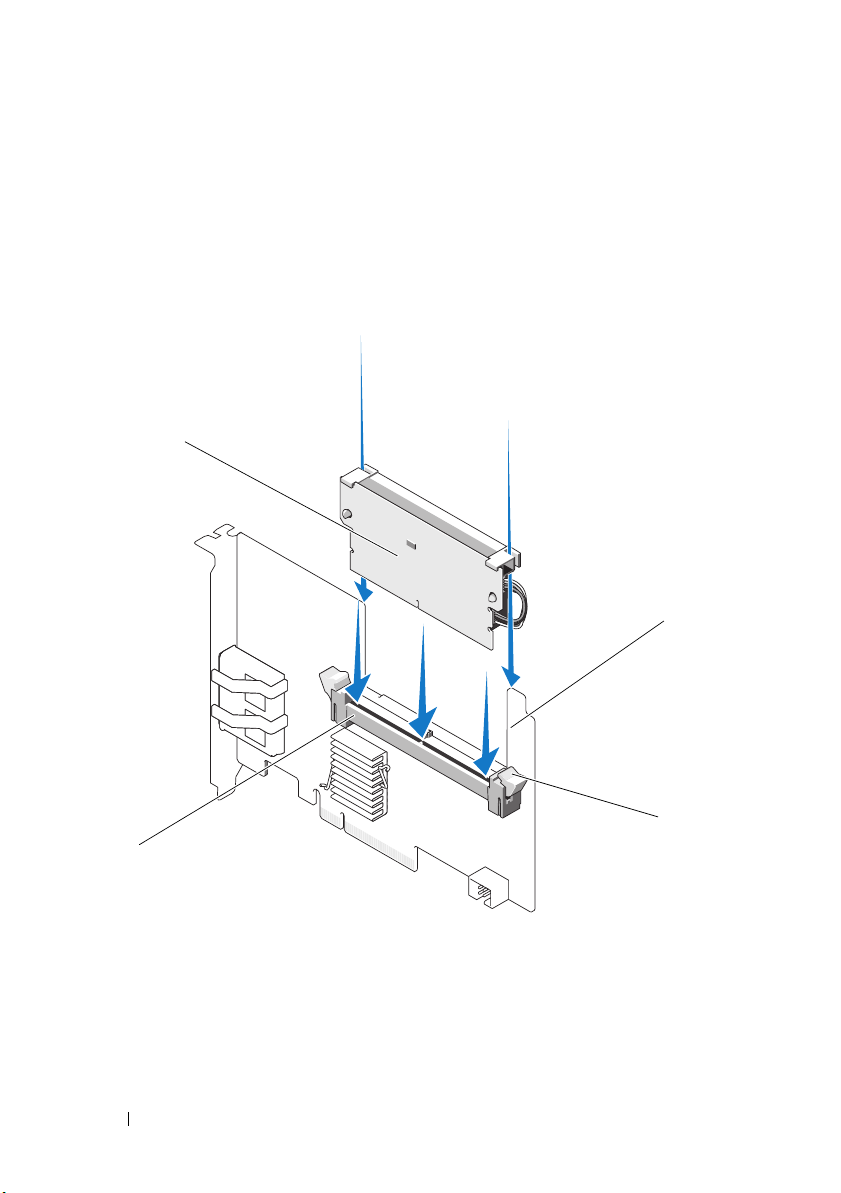
2
1
2
3
4
Align the keyed edge of the
DIMM
to the physical divider on the memory
socket to avoid damage to the module.
3
Insert the
pressure on both ends or the middle of the
fall in the allotted slots on either side of the
Figure 4-17. Installing the TBBU on a PERC H800 Adapter
DIMM
in the memory socket. Apply a constant, downward
DIMM
DIMM
until the retention clips
. See Figure 4-17.
1 PERC H800 2 retention clip
3 memory socket 4 DIMM
62 Installing and Configuring Hardware
Page 63

Transferring a TBBU or TNVC Between PERC H800 Cards
The TBBU or TNVC provides uninterrupted power supply for up to 48 hours
to a cache memory module. If the controller fails as a result of a power failure,
you can move the TBBU or TNVC to a new controller and recover the data.
The controller that replaces the failed controller should not have any prior
configuration.
Perform the following steps to replace a failed controller with data in the
TBBU:
1
Perform a controlled shutdown on the system in which the PERC H800 is
installed, as well as any attached storage enclosures.
2
Disconnect the system from the electrical outlet and remove the system
cover.
3
Remove the controller that has the TBBU or TNVC.
4
Remove the TBBU or TNVC from the controller.
5
Insert the TBBU or TNVC in the new controller.
For more information on installing the TBBU or TNVC, see "Installing the
TBBU or TNVC on a PERC H800 Adapter" on page 61.
6
Insert the replacement controller in the system.
See the relevant sections on installing controllers under "Installing the
PERC H700 and H800 Adapters" on page 41.
7
Reconnect all external storage enclosures as they were originally connected
and turn on the enclosures.
8
Replace the system cover, re-connect the system to the electrical outlet
and turn on the system.
The controller flushes the cache data to the virtual disks.
Installing and Configuring Hardware 63
Page 64
Setting up Redundant Path Support on the PERC H800 Adapter
The PERC H800 adapter can detect and use redundant paths to disks
contained in enclosures. With redundant paths to the same device, if one
path fails, another path can be used to communicate between the controller
and the device. For more information about redundant paths, see "Redundant
Path With Load Balancing Support" on page 35.
To set up a configuration with redundant paths, both ports on a controller
must be cabled to the In ports of a single enclosure.
To add multiple enclosures, both Out ports of the first enclosure must be
cabled to the In ports of the next enclosure.
If the connection between an Out port on the controller and an In port on an
enclosure fails, an alternate path exists through the second Out port on the
controller and the second In port on the enclosure. For more information,
seeFigure4-18 to Figure4-21.
NOTE: The PERC H800 adapter supports redundant paths when used with
Dell PowerVault MD1200 and Dell PowerVault MD1220 disk storage enclosures.
Perform the following steps to configure the hardware to utilize redundant
paths on the PERC H800 adapter:
1
Set up an enclosure on the PERC H800 adapter.
2
Connect two SAS cables from the
to the
In
ports of the external enclosure. For more information,
see
Figure 4-18
.
Out
ports on your PERC H800 adapter
NOTE: For information on Unified Mode, see the enclosure documentation
that was shipped with the enclosure.
3
To add multiple enclosures, cable both
both
In
ports of the next enclosure.
After you set up the hardware, the controller detects the redundant paths and
automatically utilizes them to balance the I/O load.
64 Installing and Configuring Hardware
Out
ports of the first enclosure to
Page 65

Figure 4-18 displays redundant path storage configuration with one enclosure.
Storage
Storage
Server
Server
Storage
Storage
Storage
Storage
Server Server
Figure 4-18. Redundant Path Support Configuration With One Enclosure
Figure 4-19 displays redundant path storage configuration with two
enclosures.
Figure 4-19. Redundant Path Support Configuration With Two Enclosures
Installing and Configuring Hardware 65
Page 66

Figure 4-20 displays redundant path storage configuration with
Storage
Storage
Storage
Storage
Storage
Storage
Server Server
three enclosures.
Figure 4-20. Redundant Path Support Configuration With Three Enclosures
Figure 4-21 displays redundant path storage configuration with four
enclosures. A single PERC H800 adapter can support up to four disk storage
enclosures in a redundant path configuration.
66 Installing and Configuring Hardware
Page 67
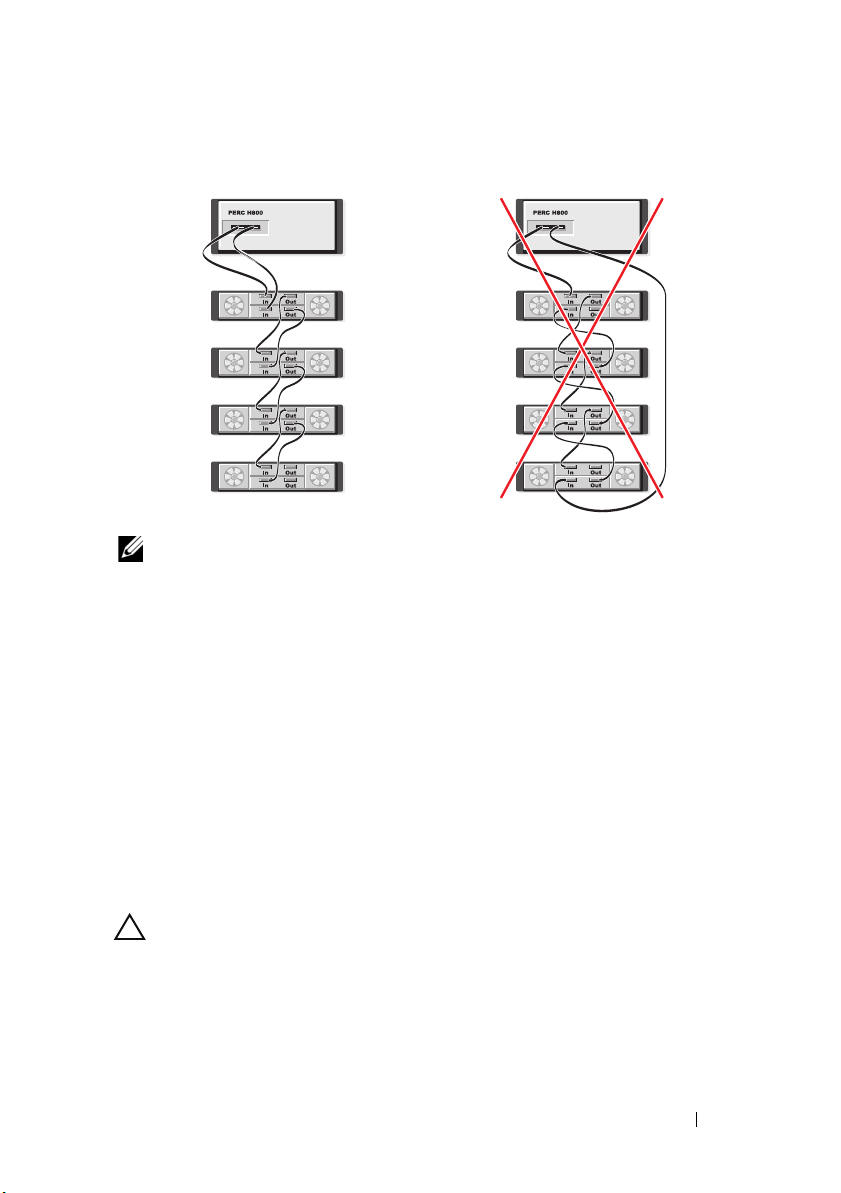
Figure 4-21. Redundant Path Support Configuration With Four Enclosures
Server Server
Storage
Storage
Storage
Storage
Storage
StorageStorage
Storage
NOTE: Ensure that the latest firmware version is installed on your storage
controller. You can find the latest firmware and installation instructions on
the Dell Support website at support.dell.com.
Reverting From Redundant Path Support to Single Path Support on the PERC H800 Adapter
If you need to revert from redundant path support to single path support,
shut down the system and remove the exact same cables that were added to
support redundant path support, leaving only one connection between the
controller and enclosures. After you remove the cable and power up the
system, ensure that there are no warning messages during boot, and that all
virtual disks are online and optimal. If you are using Dell OpenManage,
see the Dell OpenManage documentation at support.dell.com/manuals for
additional instructions.
CAUTION: If you remove any cables other than the ones added to enable
redundant path support, the enclosure and disks can get disconnected, and virtual
disk may fail.
Installing and Configuring Hardware 67
Page 68

68 Installing and Configuring Hardware
Page 69

5
Driver Installation
The Dell PowerEdge RAID Controller (PERC) H700 and H800 cards require
software drivers to operate with the supported operating systems.
This chapter contains the procedures for installing the drivers for the PERC
H700 and H800 cards.
NOTE: For more information on VMware ESX drivers, see the VMware ESX
documentation at support.dell.com/manuals.
NOTE: To check operating system compatibility, see the Dell Support website
at support.dell.com/manuals.
The two methods for installing a driver discussed in this chapter are:
•
Installing a driver during operating system installation
method if you are performing a new installation of the operating system
and want to include the drivers.
•
Updating existing drivers
PERC H700 and PERC H800 family of controllers are already installed and
you want to update to the latest drivers.
— Use this method if the operating system and
Installing Windows Drivers
— Use this
Creating the Driver Media
Perform the following steps to create the driver media:
1
Browse to the download section for the system at
2
Locate and download the latest PERC H700 or H800 driver to the system.
3
Follow the instructions for extracting the driver to the media.
support.dell.com
Driver Installation 69
.
Page 70

Pre-Installation Requirements
Before you install the operating system:
• Read the Microsoft
operating system.
• Ensure that your system has the latest BIOS, firmware, and driver updates.
If required, download the latest BIOS, firmware, and driver updates from
the Dell Support website at
• Create a device driver media (diskette, USB drive, CD, or DVD).
Creating the Device Driver Media
Use one of the following two methods to create the device driver media.
Downloading Drivers From the Dell Systems Service and Diagnostic Tools Media
1
Insert the
The
2
Select your system model and operating system (Microsoft Windows
Dell Systems Service and Diagnostics Tools
Welcome to Dell Service and Diagnostic Utilities
Server 2008).
3
Click
Continue
4
From the list of drivers displayed, select the driver you require. Select the
self-extracting zip file and click
CD, DVD, or USB drive. Repeat this step for all the drivers you require.
5
During the operating system installation, use the media that you created
with the
Load Driver
information on reinstalling the operating system, see the relevant section
for your operating system below.
Getting Started
document that shipped with your
support.dell.com
.
media in a system.
.
Run
. Copy the driver to a diskette drive,
option to load mass storage drivers. For more
screen is displayed.
Downloading Drivers From the Dell Support Website
1
Go to
support.dell.com
2
Select your line of business.
3
Click
Drivers and Downloads
4
Enter the service tag of your system in the
.
.
select your system’s model.
70 Driver Installation
Choose by Service Tag
field or
Page 71

5
Select the
Category
6
The drivers that are applicable to your selection are displayed. From the
System Type, Operating System, Driver Language, and
from the drop-down list.
available list, download the drivers that you require to a diskette drive,
USB drive, CD, or DVD.
7
During the operating system installation, use the media that you created
with the
Load Driver
option to load mass storage drivers. For more
information on reinstalling the operating system, see the relevant section
for your operating system below.
Installing Driver During a Windows Server 2003 Operating System Installation
1
Boot the system using the Windows Server 2003 media.
2
When the message
RAID driver
immediately.
Within a few minutes, a screen is displayed asking for additional
controllers in the system.
3
Press the <S> key.
The system prompts for the driver media to be inserted.
NOTE: The driver can be provided using a properly formatted USB key.
For additional details on the driver, go the Dell Support website
at support.dell.com.
4
Insert the driver media in the media drive and press <Enter>.
A list of PERC H700 and H800 cards is displayed.
Press F6 if you need to install a third party SCSI or
is displayed in the bottom of the screen, press the <F6> key
5
Select the right driver for the installed controller and press <Enter> to
load the driver.
NOTE: For Windows Server 2003, a message may appear that states that the
driver that you provided is older or newer than the existing Windows driver.
Press <S> to use the driver that is on the media.
6
Press <Enter> again to continue the installation process as usual.
Driver Installation 71
Page 72

Installing Driver During a Windows Server 2008, Windows Server 2008 R2 Installation
1
Boot the system using the Windows Vista, Windows Server 2008,
Windows 7 Server or Windows Server 2008 R2 media.
2
Follow the on-screen instructions until you reach
install Vista/2008/7
3
The system prompts you to insert the media. Insert the installation media
window and then select
Where do you want to
Load driver
.
and browse to the proper location.
4
Select the appropriate PERC H700 or H800 card from the list, click
Next
and continue installation.
NOTE: The Windows Server 2008 R2 operating system includes native drivers
for the PERC H700 and H800 cards. For driver updates, see the Drivers and
Downloads section at support.dell.com.
Installing Windows Server 2008, Windows Server 2008 R2, Windows Server 2003 for a New RAID Controller
Perform the following steps to configure the driver for the RAID controller on
a system that already has Windows installed:
1
Turn off the system.
2
Install the new RAID controller in the system.
For detailed instructions on installing and cabling the RAID controller in
the system, see "Installing and Configuring Hardware" on page 41.
3
Turn on the system.
4
The
Found New Hardware Wizard
device.
NOTE: Windows Server 2008 R2 has native drivers for the PERC adapters. The
system automatically detects the controller and installs the drivers. Check the
version of the driver and update if required.
5
Click
Next
.
6
On the
my device
7
Browse and select the drivers from the
8
Click
Locate device driver
and click
Next
.
Next
72 Driver Installation
screen, select
.
screen displays the detected hardware
Search for a suitable driver for
Locate Driver Files
screen.
Page 73

9
The wizard detects and installs the appropriate device drivers for the new
RAID controller.
10
Click
Finish
to complete the installation.
11
Reboot the system when prompted.
Updating Existing Windows Server 2008, Windows Server 2008 R2, Windows Server 2003
NOTE: Close all applications on your system before you update the driver.
1
Insert the media (CD, DVD, or USB drive) containing the driver.
2
Select
Start
The
System Properties
NOTE: The path to System might vary depending on the operating system family.
3
Click on the
4
Click
Device Manager
The
Device Manager
NOTE: The path to Device Manager might vary depending on the operating
system family.
5
Expand
clicking on the plus symbol next to
NOTE: In Windows 2008 and Windows Vista, the PERC adapter is listed under
Storage Controllers.
6
Double-click the RAID controller for which you want to update the driver.
7
Click the
The screen to update the device driver wizard is displayed.
Settings
Control Panel System
screen is displayed.
Hardware
tab.
.
screen is displayed.
SCSI and RAID Controllers
SCSI and RAID Controller
Driver
tab and click
Update Driver
.
by double-clicking the entry or by
.
.
8
Select
Install from a list or specific location
9
Click
Next.
10
Follow the steps in the wizard and browse to the location of the driver files.
11
Select the INF file from the driver media (CD, DVD, or other media).
12
Click
Next
and continue the installation steps in the wizard.
13
Click
Finish
to exit the wizard and reboot the system for the changes to
.
take place.
Driver Installation 73
Page 74

NOTE: Dell provides the Dell Update Package (DUP) to update drivers on systems
running Windows Server 2003, Windows Server 2008, and Windows Server 2008 R2
operating system. DUP is an executable application that updates drivers for specific
devices. DUP supports command line interface and silent execution. For more
information, see support.dell.com.
Installing Linux Driver
NOTE: PERC H700/H800 cards and both the PERC 5 and PERC 6 family of controllers
use the same driver and do not require separate driver installations.
Use the procedures in this section to install the driver for Linux. The driver
is updated frequently. To ensure that you have the current version of the
driver, download the updated Linux driver from the Dell Support website at
support.dell.com
NOTE: The driver update disk (DUD) images are created only for those operating
system releases in which the native (in-box) driver is insufficient for installation.
In the event that an operating system is being installed with a corresponding DUD
image, follow the instructions below. If not, proceed with using the native device
driver and then skip to "Installing the RPM Package With DKMS Support" on
page 78.
Creating a DUD
Before beginning the installation, copy the drivers from the Service and
Diagnostic Utilities media or download the driver appropriate for Linux from
support.dell.com. The driver package includes driver RPM (Red Hat Package
Managers) file, the DKMS (Dynamic Kernel Module Support) RPM file,
driver source code, and release notes.
For more information on DKMS, go to support.dell.com/manuals.
The package is a gzipped tar file. After downloading the package to
a Linux system, perform the following steps:
1
Unzip the package using
2
Untar the file using
The Driver Update Disk (DUD) image can be transferred to a USB flash
key, a system floppy disk slot, or a USB floppy device depending upon
availability and operating system.
.
gunzip
.
tar -xvf
.
74 Driver Installation
Page 75
USB key method
(Red Hat Enterprise Linux only): Transfer the
appropriate .img file to a USB key.
System Floppy Disk slot method
: Use the dd command to create a driver
update disk. Use the appropriate image for the purpose.
a
Insert a floppy disk into the system floppy disk slot.
b
At a terminal prompt, do the following:
# dd if=
<image_file_name> of=/dev/fd0
USB Floppy device method
: Use the dd command to create a driver
update disk. Use the appropriate image for the purpose.
a
Put a floppy disk into a USB floppy device and plug the device into a
USB slot of the system under test. Use
device this USB floppy is enumerated to (for example,
dmesg
to find out which
sdb, sdc
on).
b
Transfer the driver image to the floppy:
# dd if=
<image_file_name> of=/dev/sdx
NOTE: You can create a driver update disk on a Windows system using the
program dcopynt.
3
Use the diskette for operating system installation. For Red Hat Enterprise
Linux, see "Installing Red Hat Enterprise Linux Operating System Using the
DUD" on page 76. For SUSE Linux Enterprise Server, see "Installing SUSE
Linux Enterprise Server Using the Driver Update Diskette" on page 77.
, and so
Driver Installation 75
Page 76

Creating a Driver Update Diskette Using DKMS
Perform the following steps to create the Driver Update Diskette (DUD)
using the DKMS tool:
NOTE: The driver must be installed on the system where this procedure is performed.
1
Install the DKMS-enabled
2
Type the following command in any directory:
megaraid_sas
driver rpm package.
dkms mkdriverdisk –m megaraid_sas –v <driver
version> -k <kernel version> -d <distro>
NOTE: The values for the –d option are suse for Suse Linux Enterprise
Server diskettes and redhat for RHEL diskettes.
NOTE: For more information on usage of DKMS, see the DKMS main page.
This starts the process to create the
megaraid_sas
DUD image. After the
DUD image has been built, you can find it in the DKMS tree for the
megaraid_sas
driver. See the output of the
dkms mkdriverdisk
command for the exact path.
Installing Red Hat Enterprise Linux Operating System Using the DUD
Perform the following steps to install Red Hat Enterprise Linux (versions 4
and 5) and the appropriate driver:
1
Boot normally from the Red Hat Enterprise Linux installation media.
2
At the command prompt, type:
3
When the install prompts for additional drivers, insert the diskette
or USB key and press <Enter>.
For information about creating a driver diskette, see "Creating a DUD" on
page 74.
linux expert dd
4
Complete the installation as directed by the installation program.
76 Driver Installation
Page 77

Installing SUSE Linux Enterprise Server Using the Driver Update Diskette
NOTE: For information about creating a driver diskette, see "Creating a DUD" on
page 74.
To install SUSE Linux Enterprise Server using the DUD:
1
Insert the appropriate SUSE Linux Enterprise Server Service Pack media
in the system.
2
For SUSE Linux Enterprise Server 10, select <F5> for the DUD. For
SUSE Linux Enterprise Server 11, select <F6>.
The system displays three options:
the driver.
3
Select
Installation
4
Press <Enter> to load the Linux kernel.
5
At the prompt
click
OK
.
from the menu.
Please insert the driver update floppy
The system selects the driver from the diskette and installs it. The system
then displays the message
Ye s, No
, and
File
. Choose
Yes
to install
,
DRIVER UPDATE ADDED
6
Click OK.
with the description of the driver module.
If you want to install from another driver update medium, continue with
the following steps.
7
The system displays the message
MEDIUM
8
Select the appropriate driver update medium.
.
PLEASE CHOOSE DRIVER UPDATE
The system selects the driver from the disk and installs it.
Driver Installation 77
Page 78

Installing the RPM Package With DKMS Support
Perform the following steps to install the RPM package with DKMS support:
1
Uncompress the gzipped tarball driver release package.
2
Install the DKMS package using the command:
<version>.noarch.rpm
3
Install the driver package using the command:
megaraid_sas-<version>.noarch.rpm
rpm –ihv dkms-
rpm –ihv
NOTE: Use rpm -Uvh
4
If the previous device driver is in use, you must reboot the system for the
<package name>
when updating an existing package.
updated driver to take effect.
5
Verify that the driver has been loaded with the following system
commands:
Upgrading the Kernel
modinfo megaraid_sas
and
dkms status
.
When upgrading to a new kernel, you must reinstall the DKMS-enabled
driver packages. Perform the following steps to update or install the driver for
the new kernel:
1
In a terminal window, type the following:
dkms build -m <module_name> -v <module version>
-k <kernel version>
dkms install -m <module_name> -v <module version>
-k <kernel version>
2
To check whether the driver is successfully installed in the new kernel, type:
dkms status
You see a message similar to the following one:
<driver name>, <driver version>, <new kernel
version>: installed
3
If the previous device driver is in use, you must reboot the system for the
updated driver to take effect.
78 Driver Installation
Page 79
Installing Solaris Driver
NOTE: The DUD images are created only for those operating system releases in
which the native (in-box) driver is insufficient for installation. In the event that an
operating system is being installed with a corresponding DUD image, follow the
instructions below. If not, proceed with the operating system installation using the
native device driver and then skip to "Adding or Updating the Driver to an Existing
System" on page 80.
Use the procedures in this section to install the driver for Solaris 10. To ensure
that you have the current version of the driver, download the updated Solaris
driver from the Dell Support website at support.dell.com.
The package is a gzipped .tar file. Download the package to a Solaris system,
and perform the following steps:
1
Extract the package contents:
c <driver_package.tgz> | tar xvf –
2
Use the dd command to create a driver update disk. Use the appropriate
image for the purpose. Type:
/<diskette drive device node> bs=32k
NOTE: If you are uncertain which device node corresponds to your diskette
drive, execute the rmformat command and search for the correct Logical
Node.
NOTE: You can create a DUD on a system running the Windows operating
system using the program dcopynt.
3
If you prefer, you may use the cdrecord command to create a CDROM
instead of a floppy image. Type:
<bus>,<target>,<lun> mega_sas_cd.iso
gunzip -
dd if=./mega_sas.img of=
cdrecord dev=
NOTE: To identify the correct location of the bus, target, and logical unit
number (LUN) combination, execute the following command:
cdrecord --scanbus
Driver Installation 79
Page 80

Installing Solaris 10 on a PowerEdge System Booting From a PERC H700 or H800 Card
To install the driver during Solaris 10 operating system installation:
1
Boot the system from the Solaris installation media and select the
preferred console.
2
After Solaris finishes configuring devices, a menu is displayed.
Select
Apply Driver Updates
3
Select [1] if you created a CD from the
4
Select [2] if you created a diskette from the
using a traditional diskette drive.
5
Select [3] if you created a diskette from the
using a removable (USB) diskette drive.
6
Follow instructions presented by
7
The following message is displayed:
was successful
8
Select [e] to end
9
Follow the instructions on the screen to complete installation.
.
.
mega_sas_cd.iso
mega_sas.img
mega_sas.img
Driver Update
Installation of <megasas>
installer.
file.
file and you are
file and you are
Adding or Updating the Driver to an Existing System
1
To ad d t he
version of the driver, you must unarchive the driver package and execute
the installation script:
tar xvf x86_64.tar
mega_sas
driver to an existing system, or to upgrade to a newer
cd x86_64
./install.sh
2
Restart your Solaris system to start using the new driver. To confirm the
mega_sas
modinfo | grep mega_sas
3
Ensure that the driver version is correct.
80 Driver Installation
driver is loaded, run the following command:
Page 81

6
Configuring and Managing RAID
Dell OpenManage Storage Management applications enable you to manage
and configure the RAID system, create and manage multiple disk groups,
control and monitor multiple RAID systems, and provide online maintenance.
The management applications for PERC H700 and H800 include:
• Dell OpenManage Storage Management
• BIOS Configuration Utility (<Ctrl><R>)
NOTE: Dell Serial Attached SCSI (SAS) RAID Storage Manager is not supported for
SED management.
Dell OpenManage Storage Management
The Dell OpenManage Storage Management is a storage management
application for Dell systems that provides enhanced features for configuring a
system's locally-attached RAID and non-RAID disk storage. The Dell
OpenManage storage management application enables you to perform controller
and enclosure functions for all supported RAID controllers and enclosures from a
single graphical or command-line interface without requiring the use of the
controller BIOS utilities. The graphical user interface (GUI) is wizard-driven
with features for novice and advanced users, and detailed online help. Using the
Dell OpenManage storage management application, you can protect your data
by configuring data-redundancy, assigning hot spares, or rebuilding failed
physical disks. The command line interface available on selected operating
systems to perform RAID management tasks is fully featured and scriptable. For
more information, see the Dell OpenManage Storage Management User's Guide
at support.dell.com/manuals.
Configuring and Managing RAID 81
Page 82

BIOS Configuration Utility
The BIOS Configuration Utility, also known as
<Ctrl><R>
, is a storage
management application embedded on the PERC H700 or PERC H800 cards
that configures and maintains RAID disk groups and virtual disks.
<Ctrl><R>
NOTE: Use the BIOS Configuration Utility for initial setup and disaster recovery.
You can use advanced features through Dell OpenManage storage management
application and Dell SAS RAID storage manager.
is independent of the operating system.
The following sections provide information about using the BIOS Configuration
Utility. For more information, see the online help option by pressing <F1>.
NOTE: The PERC H700 or PERC H800 card configuration utility refreshes the screen
to show changes to information. The refresh occurs when you press <F5> or every
15 seconds.
Entering the BIOS Configuration Utility
Perform the following steps to enter the BIOS Configuration Utility when
you boot the system:
1
Turn on the system.
A BIOS screen displays information about the controller and
configuration.
2
During startup, press <Ctrl><R> when prompted by the BIOS screen.
After you press <Ctrl><R>, if there is only one controller, the
Disk Management
screen for that controller is displayed. If there are more
than one controllers, the main menu screen is displayed. The screen lists
the RAID controllers. Use the arrow keys to select the RAID controller you
want to configure, and press <Enter> to access the management menus
for the controller.
Virtual
NOTE: You can access multiple controllers through the BIOS Configuration Utility
by pressing <F12>.
NOTE: You can access PERC 6, and PERC H700 or H800 cards from the same BIOS if
the PERC 6 firmware is 6.2.0-0013 or later.
82 Configuring and Managing RAID
Page 83

Exiting the Configuration Utility
To ex it th e BIOS Configuration Utility, press <Esc> at any menu screen.
If there is only one controller, then a dialog box is displayed to confirm your
choice. Select OK to exit and press <Enter>.
I
f multiple controllers are present, then the <Esc> key brings you to the
Controller Selection screen. Press <Esc> again to reach the exit screen.
A
dialog box is displayed to confirm your choice. Select OK to exit
and press
<Enter>.
Menu Navigation Controls
Table 6-1 displays the menu keys you can use to move between the different
screens in the BIOS Configuration Utility.
Table 6-1. Menu Navigation Keys
Notation Meaning and Use Example
right-arrow
key
left-arrow
key
up-arrow
key
Use the right-arrow key to open a submenu, move
from a menu heading to the first submenu, or move
to the first item in that submenu. If you press the
right-arrow key at a menu heading, the submenu
expands. Press it again to go to the first item in the
submenu. The right-arrow key is also used to close a
menu list in a popup window. Word wrap is
supported.
Use the left-arrow key to close a submenu, move
from a menu item to the menu heading for that
item, or move from a submenu to a higher level
menu. If you press the left-arrow key at a menu
heading, the submenu collapses. Press it again to go
to the higher-level menu. Word wrap is supported.
Use the up-arrow key to move to the upper menu
items within a menu or to a higher level menu. You
can also use the up-arrow key to close a menu list in a
popup window, such as the stripe element size menu.
Word wrap is supported.
Start
Programs
Controller 0
Disk Group 1
Virtual Disk 1
Virtual Disk 4
Configuring and Managing RAID 83
Page 84

Table 6-1. Menu Navigation Keys
Notation Meaning and Use Example
down-arrow
key
<Enter> After you highlight a menu item, press <Enter> to
<Esc> After you expand a pop-up window, press <Esc> to
<Tab> Press <Tab> to move the cursor to the next control
<Shift>
<Tab>
<Ctrl>
<N>
Use the down-arrow key to move to the lower menu
items within a menu or to a lower level menu. You
can also use the down-arrow key to open a menu list
in a popup window, such as the stripe element size
menu, and select a setting. Word wrap is supported.
select that item. An options menu for the menu item
opens. It applies to only certain menu items, such as
Virtual Disk #. In a list of options for that item,
such as the write policy for a virtual disk, highlight a
setting, such as Wri te-Throu gh, and press <Enter>
to select it.
close the window. You can continue to press <Esc>
to exit the BIOS Configuration Utility.
on a dialog box or page.
Press <Shift><Tab> to move the cursor to the
previous control on a dialog or page.
Press <Ctrl><N> to move to the next menu screen
among the main menu screens: VD Mgmt, PD
Mgmt, Ctrl Mgmt, and Foreign View.
(continued)
Virtual Disk 1
Virtual Disk 4
Select Add New
VD and press
<Enter> to
create a new
virtual disk.
Press <Esc> to
return to the VD
Mgmt screen.
Press <Tab> to
move the cursor
to the next
parameter you
want to change.
Press
<Shift><Tab>
to move the
cursor from Sort
By to the
previously
selected PD in
the PD Mgmt
screen
Press
<Ctrl><N> on
the VD Mgmt
screen to move to
the PD Mgmt
screen.
84 Configuring and Managing RAID
Page 85

Table 6-1. Menu Navigation Keys
Notation Meaning and Use Example
<Ctrl>
<P>
<F1> Press <F1> to access Help information. The Help
<F2> Press <F2> to access the context menu, which
<F5> Press <F5> to refresh the information on the
<F11> Switch between two controllers. <F11>
<F12> Press <F12> to display a list of controllers. <F12>
Spacebar Press the spacebar to select an item. Press the
Press <Ctrl><P> to move to the previous menu
screen among the main menu screens: VD Mgmt, PD
Mgmt, Ctrl Mgmt, and Foreign View.
screens display a glossary of topics you can use to
access information about navigation, RAID levels,
and general topics.
displays the list of options.
screen.
(continued)
Press
<Ctrl><P> on
the PD Mgmt
screen to return
to the VD Mgmt
screen.
<F1>
<F2>
<F5>
<spacebar> to
select or deselect
a controller
setting in the
Ctrl Mgmt View.
Setting Up Virtual Disks
You can set up a disk group and create virtual disks using the procedures
contained in this section. Each of the following procedures are explained
individually in this section in detail.
1
Create the virtual disks and select the virtual disk options.
2
Designate hot spares (optional).
For more information, see "Managing Dedicated Hot Spares" on page 97.
3
Initialize the virtual disks.
NOTE: When you use one physical disk group to create multiple virtual disks,
all the virtual disks must be configured with the same RAID level.
Configuring and Managing RAID 85
Page 86

When you define the virtual disks, you can set the following virtual disk
parameters:
•RAID level
• Stripe element size
•Read policy
•Write policy
• Type of initialization
• Hot spare configuration
NOTE: The default hard drive cache policy for a virtual disk composed with SAS
disabled
hard drives is
parameter can not be changed in the BIOS configuration Utility.
and with SATA hard drives is
enabled
. The Virtual Disk
Table 6-2 shows the parameters that you can configure when defining
virtual disks.
Table 6-2. Virtual Disk Parameters and Descriptions
Parameter Description
RAID Level RAID Level specifies whether the virtual disk is RAID 0, 1, 5, 6, 10,
50, or 60. The number of disks, disk capacity, the requirements for
fault tolerance, performance, and capacity should be considered when
selecting the RAID level. For more information, see "Summary of
RAID Levels" on page 17.
Stripe
Element Size
Stripe Element Size specifies the size of the segments written to each
physical disk in a RAID 0, 1, 5, 6, 10, 50, and 60 virtual disk. You can
set the stripe element size to 8 KB, 16 KB, 32 KB, 64 KB, 128 KB,
256 KB, 512 KB, or 1024 KB. The default and recommended stripe
element size is 64 KB.
A larger stripe element size provides better read performance if your
system mostly does sequential reads.
86 Configuring and Managing RAID
Page 87

Table 6-2. Virtual Disk Parameters and Descriptions
Parameter Description
Write Policy Write Policy specifies the controller write policy. You can set the write
policy to Write- Bac k or Wri te-Thr ough .
In Write-B ack caching, the controller sends a data transfer
completion signal to the host when the controller cache has received
all the data in a transaction.
(continued)
NOTE: If a Battery Backup Unit (BBU) is present, the default cache
setting is Write-Back. If no BBU is present, the default cache policy
default setting is Write-Through.
NOTE: If Write-Back is enabled and the system is quickly turned off and
then on, the controller may pause as the system flushes cache memory.
Controllers that contain a battery backup default to Write-Back caching.
In Write-Through caching, the controller sends a data transfer
completion signal to the host when the disk subsystem has received
all the data in a transaction.
Read Policy Read-Ahead enables the read ahead feature for the virtual disk.
You can set the parameter to Read-Ahead, No-Read-Ahead,
or Adaptive. The default is Adaptive-Read-Ahead.
Read-Ahead specifies that the controller uses Read-Ahead for the
current virtual disk. Read-Ahead capability allows the controller to
read sequentially ahead of requested data and store the additional
data in cache memory, anticipating that the data is required soon.
No-Read-Ahead specifies that the controller does not use read ahead
for the current virtual disk.
Adaptive specifies that the controller begins using Read-Ahead if the
two most recent disk accesses occurred in sequential sectors.
If all read requests are random, the algorithm reverts to
No-Read-Ahead; however, all requests are still evaluated for
possible sequential operation.
Configuring and Managing RAID 87
Page 88

Virtual Disk Management
Creating Virtual Disks
NOTE: Combining SAS and SATA hard drives within a virtual disk is not supported.
Also, combining hard drives and SSDs within a virtual disk is not supported.
NOTE: To create secured virtual disks, see "Security Key and RAID Management"
on page 121.
Perform the following steps to create a virtual disk:
1
During host system bootup, press <Ctrl><R> when the BIOS screen
is displayed.
The
Virtual Disk Management
one controller, the main menu screen is displayed. Select a controller, and
press <Enter>. The
selected controller.
2
Use the arrow keys to highlight
3
Press <F2>
The list of available actions is displayed.
4
Select
Create New VD
The
Create New VD
option.
Virtual Disk Management
and press <Enter>.
screen is displayed. The cursor is on the
screen is displayed. If there is more than
screen is displayed for the
Controller #
or
Disk Group #
.
RAID Levels
When adding a virtual disk to a Disk Group, the
screen is displayed. Skip to step 11 to change the basic settings of the
virtual disk.
5
Press <Enter> to display the possible RAID levels, based on the physical
disks available.
6
Press the down-arrow key to select a RAID level and press <Enter>.
7
When creating a spanned virtual disk (RAID 10, 50 or 60), enter the
number of physical disks per span in the
<Enter>.
NOTE: Creating a 22 physical disk RAID 10 virtual disk is possible by selecting
RAID 10 and populating the PD per Span field with
8
Press <Tab> to move the cursor to the list of physical disks.
88 Configuring and Managing RAID
PD per Span
Add VD in Disk Group
field and press
22.
Page 89

9
Use the arrow key to highlight a physical disk and press the spacebar,
<Alt>, or <Enter> to select the disk.
10
Select additional disks, if required.
11
Press <Tab> to move the cursor to the
12
Set the virtual disk size in the
VD Size
Basic Settings
field.
box.
The virtual disk size is displayed in GB format.
NOTE: You can use part of the available disk space to create one virtual disk
and then use the rest of the disk space to create another virtual disk or disks.
13
Press <Tab> to access the
14
Press <Tab> to move the cursor to
15
Press the spacebar to make the settings active so that you can change
VD Size
field, and type a virtual disk name.
Advanced Settings
.
them.
An X is displayed beside
element size
,
read policy, and write policy
options such as forcing the cache policy to
Advanced Settings
. The settings are the
. You can also choose advanced
Write-Back
, initializing the
virtual disk, and configuring a dedicated hot spare.
The defaults parameters are displayed. You can accept the defaults or
change them. For detailed information about the virtual disk parameters,
see "Virtual Disk Parameters and Descriptions" on page 86.
16
Perform the following steps to select the virtual disk parameters:
a
Press <Tab> to move the cursor to the parameters you want to
change.
b
Press the down-arrow key to open the parameters and scroll down the
list of settings.
c
To change the stripe element size, press <Tab> to highlight
Element Size
d
Press <Enter> to display the list of stripe element sizes (
32 KB, 64 KB, 128 KB, 256 KB, 512 KB
.
8 KB, 16 KB
, and
1024 KB
). Press the
down-arrow key to highlight the desired option and press <Enter>.
The default is
e
If you need to change the read policy, press <Tab> to move the cursor
to
Read Policy
64 KB
.
.
stripe
Stripe
,
Configuring and Managing RAID 89
Page 90

f
Press <Enter> to display the options (
or
Adaptive Read Ahead
). Press the down-arrow key to highlight the
No Read Ahead, Read Ahead,
desired option and press <Enter>.
g
If you need to change the write policy, press <Tab> to move the
cursor to
h
Press <Enter> to display the options (
Write Policy
.
Wri te-Through, Wri te Back
).
Press the down-arrow key to highlight an option and press <Enter>.
i
Press <Tab> to move the cursor to
press <Enter>. If you chose
Force WB with no battery
Wri te-Through
as the write policy, then
and
the option is not available.
j
Press <Tab> to move the cursor to
CAUTION: Do not initialize virtual disks when attempting to recreate an existing
configuration.
NOTE: The initialization performed at the stage is fast initialization.
k
Press <Tab> to move the cursor to
Initialize
and press <Enter>.
Configure HotSpare
and press
<Enter>.
NOTE: The hot spare created at the stage is a dedicated hot spare.
l
If you have chosen to create hot spares in the earlier steps, a pop-up
window is displayed where disks with appropriate sizes are displayed.
Press the spacebar to select the disk size.
m
After you select the disk size, click OK to finalize the selection or click
Cancel
to forfeit the selection.
n
Select OK to accept the settings and press <Enter> to exit the
window or select
Cancel
and press <Enter> to exit if you do not want
to change any virtual disk parameters.
90 Configuring and Managing RAID
Page 91

Initializing Virtual Disks
CAUTION: A Full Initialization permanently destroys any existing data on that
virtual disk.
Perform the following steps to initialize virtual disks:
1
On the
VD Mgmt
screen, select
Virtual Disk #
and press <F2> to display
the menu of available actions.
2
Select
Initialization
3
Select
Initialization
Start Init.
and press the right-arrow key to display the
submenu options.
to begin a regular initialization or select
Fast Init.
to begin a fast initialization.
4
A pop-up windows is displayed indicating that the virtual disk has
been initialized.
5
Repeat the procedures from step 1 to step 4 to configure another
virtual disk.
The PERC H700 or PERC H800 cards support up to 64 virtual disks per
controller. The currently configured virtual disks display on the screen.
Checking Data Consistency
Select the Consistency Check (CC) option in the configuration utility to
verify the redundancy data in virtual disks that use RAID levels 1, 5, 6, 10, 50,
and 60. (RAID 0 does not provide data redundancy.)
If you attempt to run a Consistency Check on a virtual disk that has not been
initialized, the following error message is displayed:
The virtual disk has not been initialized. Running a
consistency check may result in inconsistent messages
in the log. Are you sure you want to continue?
You can select Ye s or No. If you select Ye s, the CC operation continues. If you
select No, the operation ends.
Perform the following steps to run a Consistency Check:
1
Press <Ctrl><N> to access the
2
Press the down-arrow key to highlight
VD Mgmt
Configuring and Managing RAID 91
menu screen.
Virtual Disk #
.
Page 92

3
Press <F2> to display the menu of available actions.
4
Press the down-arrow key to select
5
Press the right-arrow key to display the available actions (
6
Select
Start
and press <Enter> to run a
The
Consistency Check
runs and checks the redundancy data in the
Consistency Check.
Consistency Check
Start, Stop
.
).
virtual disks.
7
After you start the
Consistency Check
, press <Esc> to display the
previous menu if needed.
Importing or Clearing Foreign Configurations Using the VD Mgmt Menu
When a foreign configuration exists, the BIOS screen displays the message
Foreign configuration(s) found on adapter. In addition,
a foreign configuration is displayed on the right side of the Ctrl Mgmt screen.
You can use the VD Mgmt menu to import the existing configuration to the
RAID controller or clear the existing configuration. In addition, you can view
the foreign configuration from the Foreign View tab without importing the
configuration.
NOTE: The controller does not allow an import of configurations that results in
more than 64 virtual disks.
NOTE: To import a secured foreign configuration, see "Security Key and RAID
Management" on page 121.
Perform the following steps to import or clear foreign configurations:
1
During bootup, press <Ctrl><R> when prompted by the BIOS screen.
The
VD Mgmt
screen is displayed by default.
2
On the
3
Press <F2> to display the available actions.
VD Mgmt
screen, highlight the
92 Configuring and Managing RAID
Controller #
.
Page 93
4
Navigate to the
display the available actions:
NOTE: Ensure that your virtual disk has all the physical disks by verifying that
there are no physical disks marked as Missing in the foreign view page and
that all the disks appear as expected before importing them.
5
Select
Import
Foreign Config
option and press the right arrow key to
Import
and
Clear
.
to import the foreign configuration or
Clear
to delete the
foreign configuration and then press <Enter>.
If you import the configuration, the
VD Mgmt
screen displays detailed
configuration information. It includes information about the disk groups,
virtual disks, physical disks, space allocation, and hot spares.
Importing or Clearing Foreign Configurations Using the Foreign Configuration View Screen
NOTE: To import a secured foreign configuration, see "Security Key and RAID
Management" on page 121.
If one or more physical disks are removed from a configuration, the
configuration on those disks is considered a foreign configuration by the
RAID controller.
You can use the Foreign Configuration View screen to view information
about the foreign configuration, such as disk groups, virtual disks, physical
disks, space allocation, and hot spares. The foreign configuration data is
displayed in the same format as configurations on the
Yo u c an u s e t h e
importing.
VD Mgmt
screen to view the foreign configuration before
After you view the foreign configuration, you can either clear or
import to the RAID controller.
VD Mgmt
screen.
NOTE: Before you import the foreign configuration, review the configuration on the
screen to ensure that it is the end result that you require.
You can use the Foreign Configuration View screen to manage foreign
configurations in the following cases:
• All the physical disks in a configuration are removed and re-inserted.
• Some of the physical disks in a configuration are removed and re-inserted.
• All the physical disks in a virtual disk are removed, but at different times,
and then re-inserted.
• The physical disks in a non-redundant virtual disk are removed.
Configuring and Managing RAID 93
Page 94

The following constraints apply to the physical disks that are considered
for import:
• The disk state of a physical disk can change from the time the foreign
configuration is scanned to when the actual import occurs. The foreign
import occurs only on disks that are in the
Unconfigured Good
state.
• Disks in the failed or offline state cannot be imported.
• The firmware does not allow you to import more than eight foreign
configurations.
Perform the following procedures on the Foreign Configuration View screen
to manage foreign configurations in each specific case:
1
If all or some of the physical disks in a configuration are removed and
reinserted, the controller considers the disks to have foreign
configurations. Perform the following steps:
a
Select
Foreign Configuration View to
foreign configuration information on the
display the
Foreign Configuration
View screen.
b
Press <F2> to display the options (
NOTE: You must have all the disks in the system before you perform the
import operation.
Select
Import
c
select
Clear
to import the foreign configuration to the controller or
to delete the foreign configuration(s) from the re-inserted
Import, Clear
).
disk(s).
In the
Preview Configuration Data
disk that needs to be rebuilt is displayed as
window, the status of a physical
Rebuild
.
NOTE: When you import a foreign configuration, the dedicated hot spares in
the configuration are imported as dedicated hot spares on two conditions —
the associated virtual disk is already present or the associated virtual disk is
also imported along with the configuration.
NOTE: Start a consistency check immediately after the rebuild is complete to
ensure data integrity for the virtual disks. For more information about
checking data consistency, see "Checking Data Consistency" on page 91.
94 Configuring and Managing RAID
Page 95

2
If all the physical disks in a virtual disk are removed at different times and
re-inserted, the controller considers the disks to have foreign
configurations. Perform the following steps:
a
Select
Foreign Configuration View to
display the complete virtual
disk, across different foreign configurations and allow foreign
configurations to be imported.
b
Press <F2> to display the options
NOTE: You must have all the drives in the system before you perform
the import operation.
c
Select
Import
to merge the foreign configurations with the existing
configuration on the controller or
Import
and
Clear
Clear
to delete the foreign
.
configuration(s) from the re-inserted disk(s).
If you select
Import
, all drives that were pulled before the virtual disk
became offline are imported, and then automatically rebuilt.
NOTE: Start a consistency check immediately after the rebuild is
complete to ensure data integrity for the virtual disks. For more information
about checking data consistency, see "Checking Data Consistency" on
page 91.
3
If the physical disks in a non-redundant virtual disk are removed,
the controller considers the disks to have foreign configurations.
Perform the following steps:
a
Select
Foreign Configuration View to
display the complete foreign
configuration information.
b
Press <F2> to display the options
c
Select
Import
to import the foreign configuration to the virtual disk or
Clear
to delete the foreign configuration(s) from the re-inserted
Import
and
Clear
.
disk(s).
No rebuilds occur after the import operation because there is no
redundant data to rebuild the disks with.
Configuring and Managing RAID 95
Page 96

Managing Preserved Cache
If a virtual disk becomes offline or is deleted because of missing physical
disks, the controller preserves the dirty cache from the virtual disk.
The preserved dirty cache, known as pinned cache, is preserved until you
import the virtual disk or discard the cache.
NOTE: Certain operations, such as creating a new virtual disk, cannot be
performed if preserved cache exists. You have to enter the BIOS Configuration
Utility to resolve the situation before you boot to the operating system. Messages
are displayed notifying you that you must enter the BIOS Configuration Utility to
discard the preserved cache or import the virtual disks with the preserved cache.
CAUTION: If there are any foreign configurations, it is strongly advised that you
import the foreign configuration before you discard the preserved cache.
Otherwise, you might lose data that belongs with the foreign configuration.
Perform the following steps to select whether to import the virtual disk or
discard the preserved cache:
1
On the
2
Press <F2> to display the menu of available actions.
3
Select
A message is displayed advising you to import the foreign configuration
before you discard the preserved cache to avoid losing data belonging to
the foreign configuration. Confirm whether you want to continue. The
Manage Preserved Cache
VD Mgmt
screen, click on a controller icon.
Manage Preserved Cache
screen displays the affected virtual disks.
.
4
You can choose to discard the cache on the
screen. If you press
Cache Retained
Cancel
, the process is cancelled and the
dialog box is displayed.
Manage Preserved Cache
If you choose to discard the cache, you are prompted to confirm your
choice. If you choose to retain the cache, a message is displayed to notify
you that you cannot perform certain operations while the cache exists.
Click
OK
to continue.
96 Configuring and Managing RAID
Preserved
Page 97

Managing Dedicated Hot Spares
A dedicated hot spare automatically replaces a failed physical disk only in the
selected disk group which the hot spare is part of. A dedicated hot spare is
used before a global hot spare is used. You can create dedicated hot spares or
delete them on the VD Mgmt screen. Perform the following steps to create or
delete dedicated hot spares:
1
On the
VD Mgmt
the menu of available actions.
The available menu options appear.
2
Select
Manage Ded. HS
A screen displays a list of the current dedicated hot spares with an
them and the physical disks that are available to create dedicated hot spares.
NOTE: The utility allows only disks of the same disk technology and of equal
or greater size to be selected as dedicated hot spare.
3
Use the following instructions to create or delete a dedicated hot spare:
•
Creating a dedicated hot spare
a
Press the down-arrow key to highlight an available physical disk.
b
Press the spacebar to select the disk.
c
Repeat step a to step b for each dedicated hot spare that you want
to create.
An
X
is displayed beside the selected physical disk(s).
screen, select
and press <Enter>.
Disk Group #
and press <F2> to display
X
beside
•
Deleting a dedicated hot spare
a
Use the down-arrow key to highlight a current hot spare.
b
Press the spacebar to de-select the disk.
c
Repeat step a to step b for each dedicated hot spare that you want
to delete.
4
Press <Enter> to confirm the changes.
The
VD Mgmt
Hot spares
NOTE: If a global hot spare or dedicated hot spare is removed, reinserted and
imported, it regains its status as a hot spare. A dedicated hot spare becomes
a global hot spare when the disk group it was assigned to protect is no longer
present during import.
screen displays the updated list of hot spares under the
heading.
Configuring and Managing RAID 97
Page 98

Deleting Virtual Disks
NOTE: You cannot delete a virtual disk during an initialization.
NOTE: Warning messages appear stating the effect of deleting a virtual disk.
Click OK twice to complete the virtual disk deletion.
To delete virtual disks, perform the following steps in the BIOS
Configuration Utility:
1
Press <Ctrl><N> to access the
2
Use the arrow keys to move the cursor to the
3
Press <F2>.
VD Mgmt
screen.
Virtual Disks
heading.
The action menu is displayed.
4
Select
Delete VD
5
If there are multiple virtual disks in a
Capacity
for the Disk Group in the
The total amount of free space available in the
and press <Enter>.
VD Mgmt
Disk Group
screen.
Disk Group
, select
Total Free
is displayed.
Deleting Disk Groups
You can delete disk groups using the BIOS Configuration Utility. When you
delete a disk group, the utility also removes the virtual disks in that disk
group.
To delete disk groups, perform the following steps in the BIOS
Configuration Utility:
1
Press <Ctrl><N> to access the
2
Use the arrow keys to move the cursor to the
3
Press <F2>.
The action menu is displayed.
VD Mgmt
screen.
Virtual Disks
heading.
4
Select
Delete Disk Group
and press <Enter>.
The disk group is deleted.
When you delete a disk group, the remaining disk groups with higher
numbers are automatically renumbered. For example, if you delete disk
group #2, then disk group #3 is automatically renumbered as disk group #2.
98 Configuring and Managing RAID
Page 99

Clearing the Configuration
You can delete all virtual disks on the RAID controller by performing
the operation.
To clear the configuration, perform the following steps in the BIOS
Configuration Utility:
1
Press <Ctrl><N> to access the
2
Use the arrow keys to move the cursor to the
3
Press <F2>. The action menu is displayed.
4
Select
Clear Config
A pop-up window is displayed prompting for confirmation to delete all
virtual disks.
5
Select NO to delete the virtual disks or
configuration.
.
VD Mgmt
YES
screen.
Controller
to retain the existing
heading.
BIOS Configuration Utility Menu Options
The first menu that is displayed when you access the BIOS Configuration
Utility is the main menu screen. It lists the controller, controller number, and
other information, such as the slot number. On the screen, you can use the
arrow keys to select the RAID controller you want to configure. Press
<Enter> to access the controller.
This section describes the options for the BIOS Configuration Utility for
each of the major menus:
•
Virtual Disk Management (VD Mgmt)
Physical Disk Management (PD Mgmt)
•
•
Controller Management (Ctrl Mgmt)
•
Foreign
Configuration
View (Foreign View)
menu
menu
menu
menu
Configuring and Managing RAID 99
Page 100

Most menus consist of two panels:
• A left panel with the menu options
• A right panel with details of the items selected in the left panel
The following sections describe the menu and submenu options for each of
the major menus:
Virtual Disk Management (VD Mgmt)
The Virtual Disk Management screen, VD Mgmt, is the first screen that is
displayed when you access a RAID controller from the main menu screen on
the BIOS Configuration Utility. The left panel displays the menus for the
virtual disk management, which are:
•
Controller #
•
Disk Group #
•
Virtual Disks
•
Physical Disks
•
Total Free Capacity
(virtual disk size and free space you can use
to create a virtual disk)
•
Hot Spares
(global and dedicated)
The right panel displays detailed information for the selected controllers,
disk groups, virtual disks, physical disks, total free capacity, and hot spares, as
shown in Table 6-3.
Table 6-3. Information on the Virtual Disk Management Screen
Menu Item Selected
in Left Panel
Controller Controller Properties:
Information Displayed in Right Panel
• Number of disk groups (DG)
• Number of virtuals disks (VD)
• Number of physical disks (PD)
100 Configuring and Managing RAID
 Loading...
Loading...